Page 1

Scan Features
Minimum Requirements Guide
WorkCentre M123/M128
WorkCentre Pro 123/128
701P42081
Page 2

© 2004. All rights reserved.
Copyright protection claimed includes all forms and matters o f copyrighted material and information now allowed
by statutory or judicial law or hereinafter granted, including without limitations, material generated from the
software programs which are displayed on the screen, such as icons, screen displays, looks etc.
®
Xerox
, The Document Company®, the digital X®and all Xerox products mentioned in this publication are
trademarks of Xerox Corporation. Product names and trademarks of other companies are hereby acknowledged.
See the About License section for detailed information on licensed products.
The information in this document is correct at the time of publication. Xerox reserves the right at any time to
change the information without notice. Changes and technical updates will be added in subsequent editions of the
documentation. For the latest information go to www.xerox.com
.
Page 3

WorkCentre Pro 123/128
Minimum Requirements
To enable Scanning Features
6/28/04
Version 1.1
701P42081
Page 3 of 28 701P42081
Page 4

Table of Contents
GENERAL NETWORK SETUP................................................................................................................................................................. 5
ADVANCED NETWORK SETUP .............................................................................................................................................................. 6
REREQUISITE.......................................................................................................................................................................................... 6
P
REMOTE AUTHENTICATION SETUP...................................................................................................................................................... 8
CAN TO E-MAIL:...................................................................................................................................................................................... 8
S
CAN TO FTP/SMB:................................................................................................................................................................................. 8
S
N
ETWORK SCANNING:............................................................................................................................................................................... 9
REREQUISITE.......................................................................................................................................................................................... 9
P
LDAP SETUP .......................................................................................................................................................................................... 10
REREQUISITE........................................................................................................................................................................................ 10
P
SCAN TO EMAIL/IFAX/RECEIVE EMAIL/MAIL NOTIFICATION SETUP.............................................................................................. 15
REREQUISITE........................................................................................................................................................................................ 15
P
SCAN TO FTP/SMB SETUP................................................................................................................................................................... 21
REREQUISITE........................................................................................................................................................................................ 21
P
NETWORK SCANNING SETUP ............................................................................................................................................................. 23
REREQUISITE........................................................................................................................................................................................ 23
P
SCAN TO MAILBOX ............................................................................................................................................................................... 24
REREQUISITE........................................................................................................................................................................................ 24
P
APPENDIX A................................ .. .. .. .. .. ... .. .. .. .. ... .. .. .. .. .. ... .. .. .. .. .......................... ... .. .. .. .. .. ....................................................................... 26
XAMPLES OF CONFIGURING THE LDAP FIELDS ON DIFFERENT SEVERS..................................................................................................... 26
E
Page 4 of 28 701P42081
Page 5
Purpose
y
This document is intended to help the support centers and analysts in enabling Networking and Scanning features for use on a M123/M128 device.
This document is not a substitute for the system administrator’s guide or the user guide, rather it is intended to be used as a quick reference or
checklist when enabling the scanning features.
GGeenneerraall NNeettwwoorrkk SSeettuupp
These are the minimal settings required to enable the device on the network.
General Network Setup
Field Name Description Location Value
Host Name The device’s SMB Host Name. WUI :
Properties Æ Protocol Settings Æ TCP/IP
Enable “TCP/IP”
Port
Get IP Address The Method used to get an IP address.
IP Address
Page 5 of 28 701P42081
Port by which TCP/IP client
communicates with the TCP/IP server
Examples are;
•
DHCP or
• Manual,
• Etc.
This is Sheeta’s TCP/IP Address.
The IP Address is a unique address
that identifies a device in a network.
WUI :
Properties Æ Port Settings
LUI :
System Settings Æ System Settings Æ Network
Settings Æ Port Settings
WUI :
Properties Æ Protocol Settings Æ TCP/IP
LUI :
System Settings Æ System Settings Æ Network
Settings Æ Protocols Settings
WUI :
Properties Æ Protocol Settings Æ TCP/IP
LUI :
stem Settings Æ System Settings Æ Network
S
Ex: XRXxxxxxxxxxxxxxx
Default is DHCP Auto.
Note: If set for anything
other than Manual, skip
IP Address, Subnet
Mask and Gateway
fields.
_____._____._____._____
Ex: 192.168.1.50
Page 6
General Network Setup
Field Name Description Location Value
Settings Æ Protocols Settings
Subnet Mask The Subnet mask address of the
device. The Subnet Mask identifies
which part of the IP Address contains
the Subnet Address and which part
contains the host (or device) address.
Gateway
Address
The Gateway Address is the IP
Address of the gateway, or ro ut e r , th at
the machine will use to access devices
on other subnets.
WUI :
Properties Æ Protocol Settings Æ TCP/IP
LUI :
System Settings Æ System Settings Æ Network
Settings Æ Protocols Settings
WUI :
Properties Æ Protocol Settings Æ TCP/IP
LUI :
System Settings Æ System Settings Æ Network
Settings Æ Protocols Settings
_____._____._____._____
Ex: 255.255.255.0
_____._____._____._____
Ex: 192.168.1.1
AAddvvaanncceedd NNeettwwoorrkk SSeettuupp
DNS and WINS information has to be populated if a server name has been specified. DNS and WINS are protocols that allow the device to use
names rather then IP addresses when specifying the hosts of services that the device uses (ex: LDAP Host, Kerberos Host, SMTP/ pop3 Host, etc).
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup
Advanced Network Setup
Field Name Description Location Value
DNS Server
Address (up to 3
DNS server
addresses can be
specified)
Page 6 of 28 701P42081
Dynamic Name Service. Specifying
hosts by IP address is error prone and
difficult. DNS allows names to be
assigned to IP addresses. A DNS
server allows a client (like
WUI :
Properties Æ Protocol Settings Æ TCP/IP
_____._____._____._____
Ex: 192.168.1.2
If DHCP box is check via
Web UI, then DNS address
Page 7
Advanced Network Setup
Field Name Description Location Value
M123/M128) to ask the DNS server
to look up the IP address for hosts
specifie d b y na me.
DNS Address 1-3 These three fields allow the entry of
DNS server IPs. For the device to use
any Hostname…
DNS Name This is the Domain name of the
device.
Domain Name
(up to 3 DNS
Domain Names
addresses can be
specified).
WINS Server Used in Microsoft Networking
If DNS Server Address (IP address)
is left blank, then the DNS domain
names need to be specified
(SMB). WINS allow names to be
assigned to IP addresses. A WINS
server allows a client (like Shee ta) to
ask the WINS server to look up the
IP address for hosts specified by
name
WUI :
Properties Æ Protocol Settings Æ TCP/IP
WUI :
Properties Æ Protocol Settings Æ TCP/IP
WUI :
Properties Æ Protocol Settings Æ TCP/IP
WUI :
Properties Æ Protocol Settings Æ TCP/IP
information is populated
automatically.
_____._____._____._____
Ex: 192.168.1.2
Ex:
<DNSName>.<company>.com
Ex:
<DNSName>.<company>.com
Ex:
<DNSName>.<company>.com
If DHCP box is check via
Web UI, then WINS address
information is populated
automatically.
Page 7 of 28 701P42081
Page 8
RReemmoottee AAuutthheennttiiccaattiioonn SSeettuupp
The M123/M128 device performs user authentication using Kerberos for windows and Kerberos for Solari s. When enabled, user access to scanning
features (excluding scan to mailbox) will be prevented for un-authorized users. Access to the scanning features will be enabled once the user is
authenticated by Kerberos.
However, since the username/password provided to utilize the scanning features (i.e. Scan to SMB, Scam to FTP, e-mail, Network Scanning) IS
NOT the same username / password used to au thenticate with the Kerberos server, trac king each user when accessing the netwo rking features of the
device will not be possible.
The following procedure describes how Kerberos works with different scanning functions.
Scan to E-Mail:
• The user selects <Scan to email>
•
A login/password popup is displayed requiring the user to provide a username and password to the Kerberos server.
• The user enters the login and password.
• The device passes the login and password to the Kerberos server and if a match is found the user is successfully authenticated.
•
“From:” field of the e-mail is automatically populated with the device login name and e-mail address created at the time of the device
configuration.
•
If SMTP server requires authentication, the device will use the SMTP username/passw ord c reated at the configuration of the device to send an
email to the server.
Scan to FTP/SMB:
• The user selects <Scan to FTP/SMB>
• A login/password popup will be displayed to authenticate users with the Kerberos server.
•
The user enters the login and passwo r d.
• The login and password is passed on to the Kerberos serv er and if a match is found the user is successfully authenticated.
• The user needs to enter a valid login and password for the FTP/SMB server. This may or may not be the use r’s Ke rberos login/password,
rather it is a login/password that is accepted by the FTP/SMB server.
Page 8 of 28 701P42081
Page 9
Network Scanning:
• The user selects <Network Scanning>
• A login/password popup will be displayed to authenticate users with the Kerberos server.
•
User enters the login and password.
•
The login and password is passed on to the Kerberos server and if a match is found the user is successfully authenticated.
• Through the templates/reposito ries, the users will enter a valid login/password for FTP/SMB servers. This may or may not be the user
login/password; rather it is a login/password that is accepted by the FTP/SMB server.
• Public templates are accessible to any user. Private templates require a password that may or may not be different from the Kerberos
password.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup
Complete DNS/WINS set up if Host names are provided for the mail servers, rather than IP addresses. Refer to Æ Ad vanced Network Setup
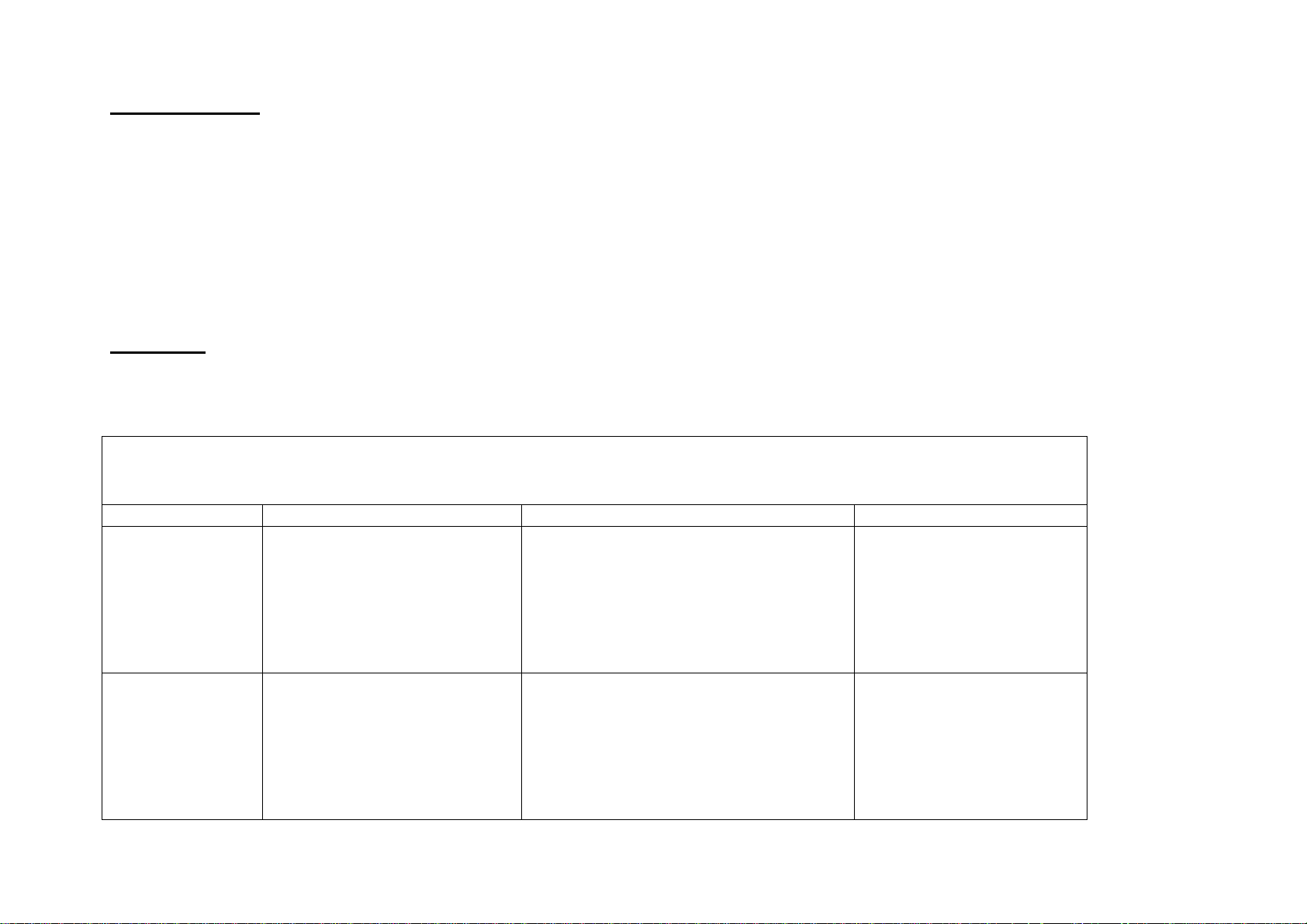
Remote Authentication Setup
Field Name Description Location Value
Remote Setup login Enable Remote Authentica tion LUI:
System Settings Æ Login setup/Auditron
Administration Æ Remote Login Setup
Remote Server IP
Address or Server
name.
The IP address or the host name
of the Kerberos server.
Note: If server host name is used
instead of the IP address, refer to
Advanced Network Setup for
DNS / WINS settings.
LUI:
System Settings Æ System Settings Æ
Network Settings Æ Remote
Authentication
Default:
ON:
Guest ON:
_____._____._____._____
Ex of the IP address:
192.168.1.2
Ex of the host name:
Ex:<name>..<company>.com
Page 9 of 28 701P42081
Page 10

Remote Authentication Setup
Field Name Description Location Value
Remote Server Port
number
Remote Server
Realm Name
This is the Port Number use d.
Default is 88.
Fully qualified d omain which
Kerberos serv er supports
Ex:
Kerberos.<company>.com
LLDDAAPP SSeettuupp
LDAP, Lightweight Directory Access Protocol, is an I nternet protocol that email programs use to look up contact information from a server. LDAPaware" client programs can ask LDAP servers to look up entries in a wide variety of ways. LDAP servers index all the data in their entries, and
"filters"(ex. Search root entr y DN) may be used to select just the person or grou p you want, and return just the information you want. LDAP servers
also provide an "authentication" service so that only authenticated users can access the LDAP server. However, most LDAP servers do not requires
authentication.
Please refer to Appendix A for som e examples on custom fields format as required by dif ferent servers.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup
Complete DNS/WINS set up if a Host name is provided for the LDAP servers, rather than IP addresses. Refer to Æ Advanced Network Setup
Page 10 of 28 701P42081
Page 11
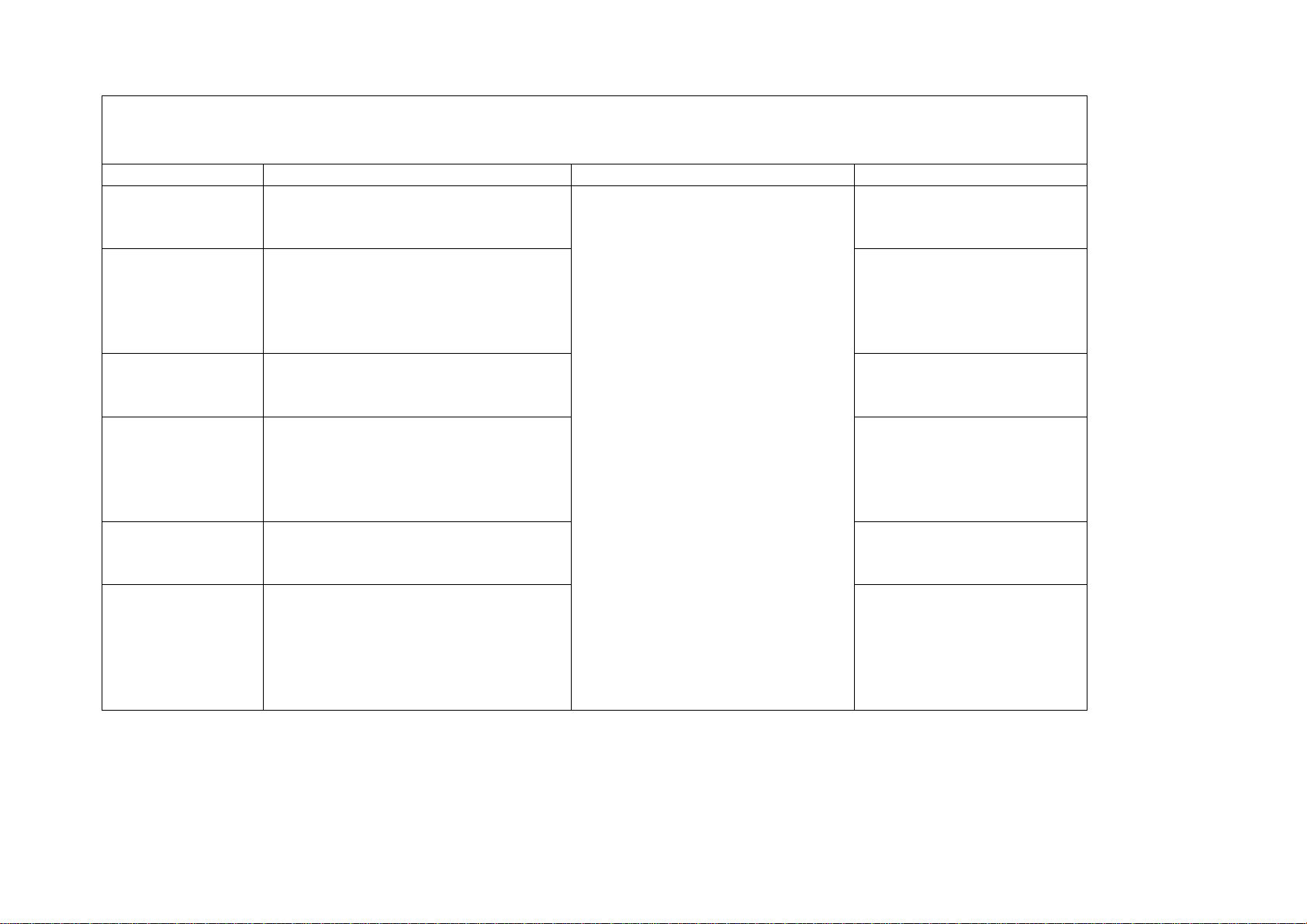
LDAP Setup
Field Name Description Location Value
Directory Server
(LDAP)
Primary Server The Primary IP address of the LDAP
Primary Server Port
Number
Secondary Server The Secondary IP address of the LDAP
Secondary Server
Port Number
Login/password Login and password information
Enable LDAP
server or server Name. If server name
is used, ensure that DNS information is
properly populated via Centreware
Internet Services.
Port number of the primary LDAP
Server
server or server Name
Port number of the primary LDAP
Server
required connecting to the LDAP
server
. Note: most LDAP servers don’t
require authentication, and therefore
the login and password is usually
optional.
LUI:
System Settings Æ System Settings
Æ E- Mail / Fax Settings Æ
Address Search (Directory Service)
_____._____._____._____
Ex: 192.168.1.2
OR
Ex:<name>.<company>.com
Ex: Port 389
_____._____._____._____
Ex: 192.168.1.2
OR
Kerberos.<company>.com
Ex: Port 389
Page 11 of 28 701P42081
Page 12

LDAP Setup
Field Name Description Location Value
Search Root entry
DN (Distinguished
Name
The format of the naming context will
vary depending on the LDAP Server
being used.
A DN identifies an entry in an LDAP
directory. Because directories are
hierarchical, DNs identify the entry by
its location as a path in a hierarchical
tree (much as a path in a file system
identifies a file). Generally, a DN
begins with a specific common name,
and proceeds with increasingly
broader areas of identification until
the country name is specified.
CN=common name,
[OU=organizational unit,
O=organization, L=locality,
ST=state or province], C=country
name
LUI:
System Settings Æ System Settings
Æ E- Mail / Fax Settings Æ
Address Search (Directory Service)
Ex for Active Directory
Server:
Rodc.Xerox.com
dc=rodc,dc=Xerox, dc=com
Page 12 of 28 701P42081
Page 13

LDAP Setup
Field Name Description Location Value
Scope of Search Search scope determines how far down
the directory tree to search. There are
three values that can be set for scope:
base, which; onelevel, which, and
subtree which
This field narrows the search criteria as
defined by the Search Root entry.
Options are:
• Root Entry Only -- only
searches the same level as the
DN defined by the base DN
setting
•
One level below Root Entr y
only -- will search one level
below the base and does not
include the root entry
•
All levels below root entry -searches the base entry and
everything below the base
Object class of
search target
Server Application The choices are
This is like the Wild card. If one enters
a string of characters for search criteria
then all names that contain that string
will be returned.
Active Directory
Netware
Other Application (ex. Domino)
LUI:
System Settings Æ System Settings
Æ E- Mail / Fax Settings Æ
Address Search (Directory Service)
Ex:
*
Page 13 of 28 701P42081
Page 14

LDAP Setup
Field Name Description Location Value
Attribute type of
Recipient name
Attribute type of
Last Name
Attribute type of
First Name
Attribute type of E
Mail Address
Attribute type of
Custom Item 1
Attribute Name of
Custom Item 1
Attribute type of
Custom Item 2
Attribute Name of
Custom Item 2
Directory searches are often done by
searching for a partial name in the
common name (cn) attribute.
This is the surname (last name).
This is the given name
LUI:
System Settings Æ System Settings
Email address
Æ E- Mail / Fax Settings Æ
Address Search (Directory Service)
These fields can be customized. The
type holds the value of the field
These fields can be customized. The
Name field displays the word
These fields can be customized. The
type holds the value of the field
These fields can be customized. The
Name field displays the word
Ex: searching for "Flint"
within the cn would turn up
this entry.
Williams Flintson
Barb Flintson
Wilma Flintson
Etc.
Ex:
Flintson
Ex:
Wilma
Ex:
dino@bedrock.com
Ex:
telephoneNumber
Ex:
Telephone Number
Ex:
hysicalDeliveryOfficeName
P
Ex:
Office
Page 14 of 28 701P42081
Page 15

LDAP Setup
Field Name Description Location Value
Attribute type of
Custom Item 3
Attribute Name of
Custom Item 3
Maximum search
results
Search time Out The amount of time it waits to get a
These fields can be customized. The
type holds the value of the field
These fields can be customized. The
Name field displays the word
The number of requests that LDAP will
return (maximum is 100)
response from the LDAP server.
Ex:
department
Ex:
Department
SSccaann ttoo EEmmaaiill//iiFFaaxx//RReecceeiivvee EEmmaaiill//MMaaiill NNoottiiffiiccaattiioon
Email, iFax, and Receive email at the device requires SMTP (for sending mail) and POP3 (receiving mail) to be populated correctly. If host names
are entered for the email servers (i.e. SMTP and POP3) then DNS / WINS information need to be populated correctly.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup
Complete DNS/WINS set up if Host names are provided for the mail servers, rather than IP addresses. Refer to Æ Ad vanced Network Setup
R : Required
NR : Not Required
Page 15 of 28 701P42081
n SSeettuupp
Page 16

Scan to Email/iFax/Receive Email/Mail Notification Setup
Field Name Description Location Scan
To
Email
Enable “Send
Email Port”
Enable Receive
Email Port
Enable SOAP
Port
Page 16 of 28 701P42081
Without
enabling this
port, Scan to
email option will
not be made
available.
Without
enabling this
port, Scan to
email option will
not be made
available.
SOAP is a
simple XML
based protocol to
let applications
exchange
information over
HTTP.
Or more simply:
SOAP is a
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ Port
Settings
WUI:
Properties Æ
Port Settings
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ Port
Settings
WUI:
Properties Æ
Port Settings
R R NR R
NR R R NR
R NR NR NR
iFax Receive
Email
Mail
Notification
Value
Page 17

Scan to Email/iFax/Receive Email/Mail Notification Setup
Field Name Description Location Scan
To
Email
protocol for
accessing a Web
Service
Administrator
Email Address
Machine Email
Address
SMTP Server
Address
OR
SMTP Server
Page 17 of 28 701P42081
Address used to
receive mail
notification
when device can
not connect to
the SMTP Server
This is the Email
address of the
device.
The IP address
of the SMTP
server.
WUI:
Properties Æ
Machine Details
WUI:
Properties Æ
Machine Details
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ
Machine Email
Address
WUI:
Properties Æ
Protocol
Settings Æ
Email
R R R R
R R R R
R R NR R _____._____._____.____
iFax Receive
Email
Mail
Notification
Value
Ex:
admin@<company>.com
Ex:
machine@<company.com
Ex – Server Address:
192.168.1.2
Page 18

y q
Scan to Email/iFax/Receive Email/Mail Notification Setup
Field Name Description Location Scan
To
Email
Name (it is
better to use the
fully qualified
domain name)
SMTP User
Name and
Password
POP3 Server
Address
OR
POP3 Server
Name (it is
better to use the
full
Page 18 of 28 701P42081
ualified
This is the
SMTP server
authentication.
If SMTP server
requires
authentication,
the a login and
password is
required for the
SMTP server
The IP address
of the POP3
server.
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ
SMTP Settings
WUI:
Properties Æ
Protocol
Settings Æ
Email
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ
SMTP Settings
WUI:
Properties Æ
Protocol
Settings Æ
Email
LUI:
System Settings
Æ System
R R NR R
NR R R NR _____._____._____.____
iFax Receive
Email
Mail
Notification
Value
Ex – Server Name:
Name.<company>.com
Ex – Server Address:
192.168.1.2
Ex – Server Name:
Name.<company>.com
Page 19

Scan to Email/iFax/Receive Email/Mail Notification Setup
Field Name Description Location Scan
To
Email
domain name) Settings Æ
Network
Settings Æ
POP3 Settings
POP3 User
Name and
Password
This is the POP3
server
authentication.
If POP3 server
requires
authentication,
the a login and
password is
required for the
POP3server
WUI:
Properties Æ
Protocol
Settings Æ
Email
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ
POP3 Settings
NR R R NR
iFax Receive
Email
Mail
Notification
Value
Page 19 of 28 701P42081
Page 20
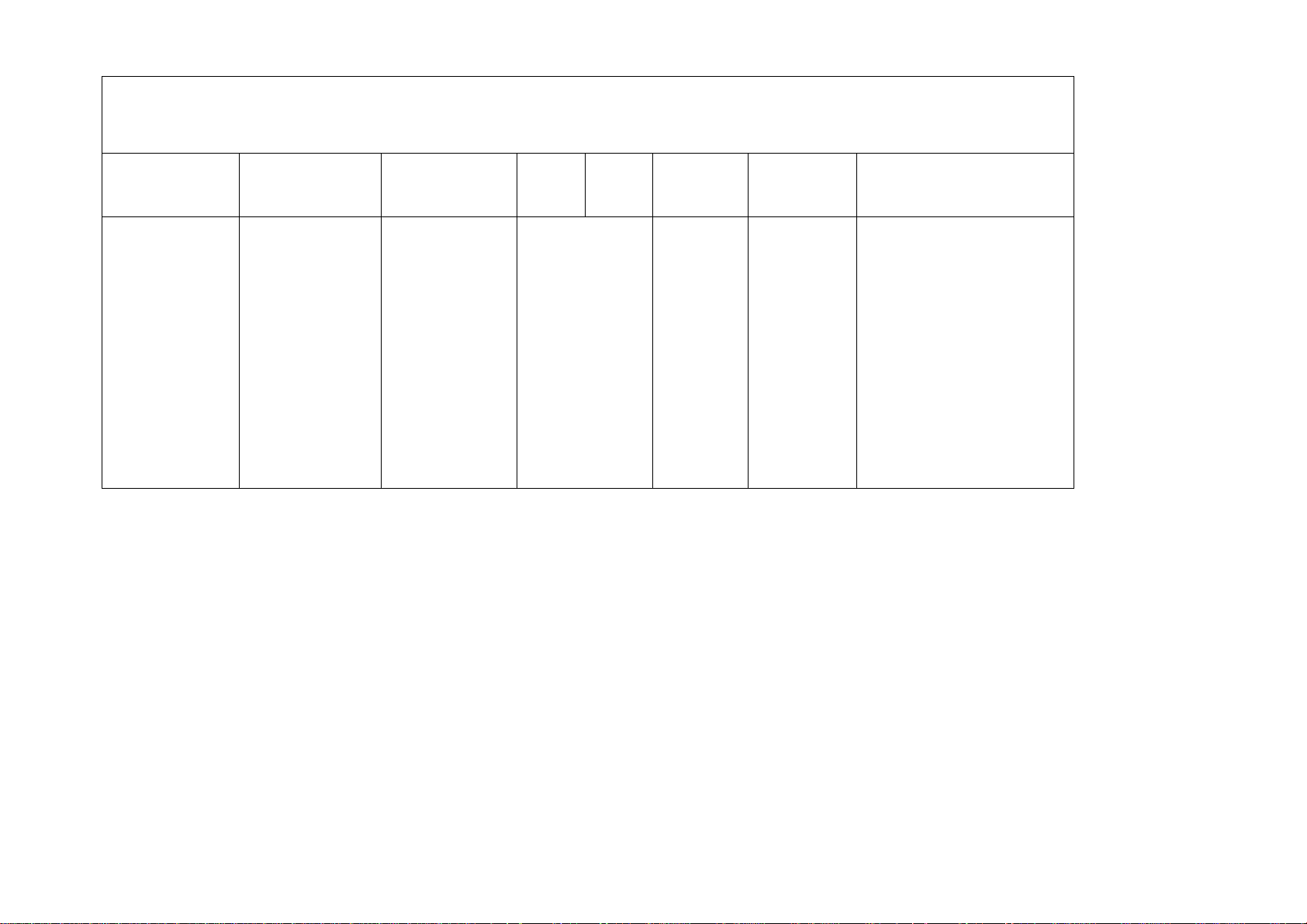
Scan to Email/iFax/Receive Email/Mail Notification Setup
Field Name Description Location Scan
To
Email
LDAP Remote Address
Book directory
server supports
Windows 2000
Active
Directory,
Exchange Server
2000, and
Exchange Server
2003 and Novel
Netware 5
WUI:
Properties Æ
Protocol
Settings Æ
LDAP
LUI:
System Settings
Æ System
Settings Æ
Network
Settings Æ
Email Settings
Should be set if
Global search is
required
iFax Receive
Email
NR NR
Mail
Notification
Value
Page 20 of 28 701P42081
Page 21

SSccaann ttoo FFTTPP//SSMMBB SSeettuupp
Files can be scanned on the M123/M128 de vice an d r o u ted on to a server or a client using FTP or SMB protocol. Directory structures (repositories)
need to be created on the server to hold t he sc anned documents. It is assumed that an FTP server/client or an SMB server/client exists and is
configured on the network.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup
Complete DNS/WINS set up if Host names are provided for the mail servers, rather than IP addresses. Refer to Æ Advanced Network Setup
Scan to FTP/SMB Setup
Field Name Description Location Scan
To
FTP
Enable
“TCP/IP” Port”
Enable “FTP
Client” Port
Enable “SMB
Port”
Port by which TCP/IP client
communicates with the
TCP/IP server
Port by which FTP client
communicates to the FTP
server
Port by which SMB client
communicates to the SMB
server
WUI:
Properties Æ Port Settings
LUI:
System Settings Æ System Settings Æ
Network Settings Æ Port Settings
WUI:
Properties Æ Port Settings
LUI:
System Settings Æ System Settings Æ
Network Settings Æ Port Settings
WUI:
Properties Æ Port Settings
LUI:
R R
R NR
NR R
Scan To
SMB
Value
Page 21 of 28 701P42081
Page 22

Scan to FTP/SMB Setup
Field Name Description Location Scan
To
FTP
System Settings Æ System Settings Æ
Network Settings Æ Port Settings
Enable
“SNMP” Port.
Enable
“SOAP” Port
FTP login and
User name
SMB Login
and User Name
Repositories
Simple Network
Management Protocol
SOAP is a simple XML
based protocol to let
applications exchange
information over HTTP.
Or more simply: SOAP is a
protocol for accessing a Web
Service
Login and password required
by the FTP server for
Authentication.
Login and password required
by the SMB server for
Authentication.
A folder containing the
Scanned images.
WUI:
Properties Æ Port Settings
LUI:
System Settings Æ System Settings Æ
Network Settings Æ Port Settings
WUI:
Properties Æ Port Settings
LUI:
System Settings Æ System Settings Æ
Network Settings Æ Port Settings
LUI:
All Services Æ Scan to FTP
LUI:
All Services Æ Scan to FTP
WUI:
Services Æ Job Templates Æ Display
Job Templates Screen Æ File
Repository Setup
R R
R R
R NR
NR R
R R
Scan To
SMB
Value
Page 22 of 28 701P42081
Page 23

NNeettwwoorrkk SSccaannnniinngg SSeettuupp
Files can be scanned on the M123/M128 device an d r o u ted on to a server using FTP or SMB protocol. Directory structures (repositories) need to be
created on the server to hold the scanned documents. Templates have to be created on the device. The information in the templates will be used to
specify the transfer protocol (FPT/SMB) as well as the attributes of the scanned document.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup.
Complete DNS/WINS set up if Host names are provided for the mail servers, rather than IP addresses. Refer to Æ Advanced Network Setup
Complete Scan To FTP/SMB dependin g on the type of the protocol that is used by network environment. Refer to Æ Scan To FTP/SMB
Templates and repositories must be created through CentreWare Internet Services (r efer to User Guide) or CentreWare Scanning Services.
R: Required
O: Optional
Network Scanning Setup
Field Name Description Location Network
Scanning
Templates
Repositories A folder contai ning the Scanned
Centerware
Network Scanning
Page 23 of 28 701P42081
Templates define the attributes for a
particular job, as well as the
destination(s) of the sca nned
document. Templates can be created
using Centerware Internet Services, or
Centerware Network Scanning.
images.
Can be used to create templates Must be installed via CD
LUI:
Services Æ Job Templates
Æ Display Job Templates
Screen Æ Template
LUI:
Services Æ Job Templates
Æ Display Job Templates
Screen Æ File Repository
Setup
ROM
R
R
O
Value
Page 24

SSccaann ttoo MMaaiillbbooxx
p
This feature will allow documents to be stored in to a mailbox for future processing. Internet Services and scan driver utility can be used to create,
view, and print documents stored in a mailbox.
Prerequisite
Complete the Network Installation. Refer to Æ General Network Setup.
Scan to Mailbox
Field Name Description Location Scan To
Mailbox
Enable
“Salutation” Port
Enable “HTTP”
Port
Scan Driver Utility
Centerware
Internet Services
Mailboxes must be
created.
This port is used for
discovering and polling of
scanners
WUI:
The Utility that will be
installed on the client and
allows users to view/print
the scanned documents
within a mailbox
Allows users to view/print
the scanned documents
within a mailbox
Mailboxes need to be
created via UI or Internet
LUI:
System Settings Æ System
Settings Æ Network Settings Æ
Port Settings
Protocols Æ Port Settings
LUI:
System Settings Æ System
Settings Æ Network Settings Æ
Port Settings
Must be installed via CD ROM O
Using a browser, enter the
Machines IP address.
LUI:
All Services Æ Setu
Menu Æ
R
R
O
R
Value
Page 24 of 28 701P42081
Page 25

Scan to Mailbox
Field Name Description Location Scan To
Mailbox
Services Mailbox
LUI:
System Settings Æ Setup Menu Æ
Mailbox
Value
Page 25 of 28 701P42081
Page 26

AAppppeennddiixx AA
Examples of Configuring the LDAP Fields on different Severs
This section provides an example of how different LDAP fields can be configured on differe nt servers. Please note that this section does not describe
every LDAP field supported by M123/128 device.
Choosing the type of LDAP Server
The SA/KO shall be allowed to choose the type of LDAP server that is being used via the Remote UI from:
•
Exchange
• Domino
• Netscape Directory Services
•
ADS LDAP
• NetWare LDAP
Based on this selection, the user shall be presented with a default mapping of the device display item to the corresponding LDAP field as follows:
NetWare LDAP Default Mapping
Display Item Default LDAP Mapping
Name fullName
Email Address mail
IFax Address
Business Phone telephoneNumber
Business Address postalAddress
Office physicalDeliveryOfficeName
City l
State st
zip code postal code
country co (no entry in client)
UID uid
Page 26 of 28 701P42081
Page 27

Domino Default Mapping
Display Item Default LDAP Mapping
Name cn
Email Address mail
IFax Address
Business Phone telephonenumber
Business Address postaladdress
Office officestreetaddress
City l
State st
zip code postalcode
country co
UID shortname
Exchange Default Mapping
Display Item Default LDAP Mapping
Name cn
Email Address mail
IFax Address
Business Phone telephoneNumber
Business Address postalAddress
Office physicalDeliveryOfficeName
City l
State st
zip code postalCode
country co
UID uid
ADS Default Mapping
Display Item Default LDAP Mapping
Name cn
Page 27 of 28 701P42081
Page 28

Display Item Default LDAP Mapping
Email Address mail
IFax Address
Business Phone telephoneNumber
Business Address postalAddress
Office physicalDeliveryOfficeName
City l
State st
zip code postalCode
country co
UID SAMAccountName
Netscape Default Mapping
Display Item Default LDAP Mapping
Name cn
Email Address mail
IFax Address
Business Phone telephonenumber
Business Address postalAddress
Office physicalDeliveryOfficeName
City l
State st
zip code postalCode
country co
UID uid
Page 28 of 28 701P42081
 Loading...
Loading...