Page 1

Bluetooth USB Adapter User’s Guide
BT-510
Page 2

Copyright Statement
No part of this publication may be reproduced, stored in a retrieval system, or transmitted in
any form or by any means, whether electronic, mechanical, photocopying, recording or
otherwise without the prior writing of the publisher.
Windows
™
95/98SE/ME/2000/XP are trademarks of Microsoft® Corp.
Pentium is trademark of Intel.
Bluetooth and the Bluetooth logos are trademarks of Bluetooth SIG, Inc., U.S.A.
All copyright reserved.
1
Page 3

Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide
reasonable protection against harmful interference in a residential installation. This
equipment generates, uses and can radiate radio frequency energy and, if not installed
and used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a
particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the
user is encouraged to try to correct the interference by one of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
- Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: To assure continued compliance, (example - use only shielded interface
cables when connecting to computer or peripheral devices) any changes or
modifications not expressly approved by the party responsible for compliance could void
the user's authority to operate this equipment.
This device complies wi th Par t 15 of the FCC Rules. Operati o n i s su bj ect t o the following
two conditions: (1) This device may not cause harmful interference, and (2) this device
must accept any interference received, including interference that may cause undesired
operation.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled
environment. End-users must follow the specific oper ating i nstructi ons for satis fying RF
exposure compliance.
This transmitter must not be co-located or operating in conjunction with any other
antenna o r transmitter.
2
Page 4

Table of Contents
TABLE OF CONTENTS.............................................................................................................. 3
1. INTRODUCTION..................................................................................................................... 5
BOUT BLUETOOTH DONGLE
1.1 A
IT CONTENTS
1.2 K
CONS USED
1.3 I
....................................................................................................................... 5
........................................................................................................................... 5
2. STEP-BY-STEP INSTALLATION GUIDE...........................................................................7
NSTALLATION
2.1 I
NINSTALLATION
2.2 U
........................................................................................................................ 7
................................................................................................................. 12
3. BASIC OPERATIONS...........................................................................................................13
INDING BLUETOOTH DEVICES
3.1 F
INDING A SERVICE
3.2 F
ONNECTION’S STATUS
3.3 C
.............................................................................................................. 14
................................................................................................ 5
............................................................................................ 13
........................................................................................................ 15
EW CONNECTION
3.4 N
LUETOOTH TRAY
3.5 B
AIRING DEVICES
3.6 P
REAKING A PAIRED DEVICE RELATIONSHIP
3.7 B
ETTING SECURITY FOR LOCAL SERVICES
3.8 S
ONNECTING TO A SECURED SERVICE
3.9 C
3.10 S
HARING SECURED LOCAL SERVICES
............................................................................................................... 16
............................................................................................................... 19
................................................................................................................ 20
....................................................................... 23
........................................................................... 24
.................................................................................. 26
................................................................................. 29
4. CLIENT APPLICATIONS .................................................................................................... 31
ETWORK ACCESS
4.1 N
............................................................................................................... 31
4.1.1 Network Access Server-side Setup (for Windows 2000).............................................. 31
4.1.2 Configuring the server................................................................................................. 31
LUETOOTH SERIAL PORT
4.2 B
IAL-UP NETWORKING
4.3 D
.................................................................................................... 31
........................................................................................................ 32
4.4 FAX...................................................................................................................................... 33
ILE TRANSFER
4.5 F
.................................................................................................................... 33
4.5.1 File Transfer Operations ............................................................................................. 34
NFORMATION EXCHANGE
4.6 I
NFORMATION SYNCHRONIZATION
4.7 I
.................................................................................................... 34
....................................................................................... 35
5. LOCAL SERVICES...............................................................................................................36
6. CONFIGURATION PANEL.................................................................................................. 37
3
Page 5

CCESSIBILITY TAB
6.1 A
............................................................................................................. 37
6.1.1 Adding and Deleting Devices....................................................................................... 38
ISCOVERY TAB
6.2 D
ENERAL TAB
6.3 G
ARDWARE TAB
6.4 H
NFORMATION EXCHANGE TAB
6.5 I
OCAL SER VICES TAB
6.6 L
OTIFICATIONS TAB
6.7 N
ERSION INFO TAB
6.8 V
.................................................................................................................. 39
...................................................................................................................... 41
.................................................................................................................. 42
............................................................................................ 44
.......................................................................................................... 45
............................................................................................................. 47
.............................................................................................................. 48
7. SECURITY.............................................................................................................................. 49
UTHENTICATION
7.1 A
UTHORIZATION
7.2 A
NCRYPTION
7.3 E
EVELS OF SECURITY
7.4 L
INK KEY
7.5 L
AIRING DEVICES
7.6 P
............................................................................................................................. 50
................................................................................................................ 49
.................................................................................................................. 49
........................................................................................................................ 49
........................................................................................................... 50
................................................................................................................ 50
ASSKEY
7.7 P
ECURITY REQUEST DIALOG BOX
7.8 S
UTHORIZATION REQUEST DIALOG BOX
7.9 A
.............................................................................................................................. 50
....................................................................................... 50
DVANCED BUTTON
, A
........................................... 51
8. BLUEMUX.............................................................................................................................. 52
9. CONNECTION WITH MOBILE PHONE T68.................................................................. 55
10. SPECIFICATIONS............................................................................................................... 57
4
Page 6

1. Introduction
1.1 About Bluetooth Dongle
Thank you for purchasing Bluetooth USB Adapter, Bluetooth Dongle. With the features of
small, lightweight and easy plug-and play, Bluetooth USB Adapter enables the integration of
Bluetooth technology into your personal computers.
Features:
! Bluetooth 1.1 Spec. Compliant
! Data Speed of up to 1Mbps
! Range of up to 10 meters
! Multiple functions such as Dial-up networking, File transfer, LAN Access…
! 2.4 GHz FHSS technology
! Easy to expand the network
! Small size and easy installation
! Extensive security: Authorization / Authentication / Encryption.
! Supports Windows 95/98SE, ME, 2000, and XP
As a Bluetooth Client, Bluetooth USB Adapter provides:
! To locate other Bluetooth-enabled devices in the vicinity
! To discover the services of those devices
! Connect to, use, and disconnect from those services.
As a Bluetooth Server, Bluetooth USB Adapter provides:
! To include or exclude individual services in the list of services provided to clients.
1.2 Kit Contents
! Bluetooth USB Adapter
! Installation Software CDROM
1.3 Icons Used
By changing color, Bluetooth icons help you to distinguish a device or service’s status.
Device icons
Icons with blue-color indicates “normal” state. Icons with green-color indicates
“Connected” state. Icons with a check mark indicate that devices are paired with this
computer.
5
Page 7
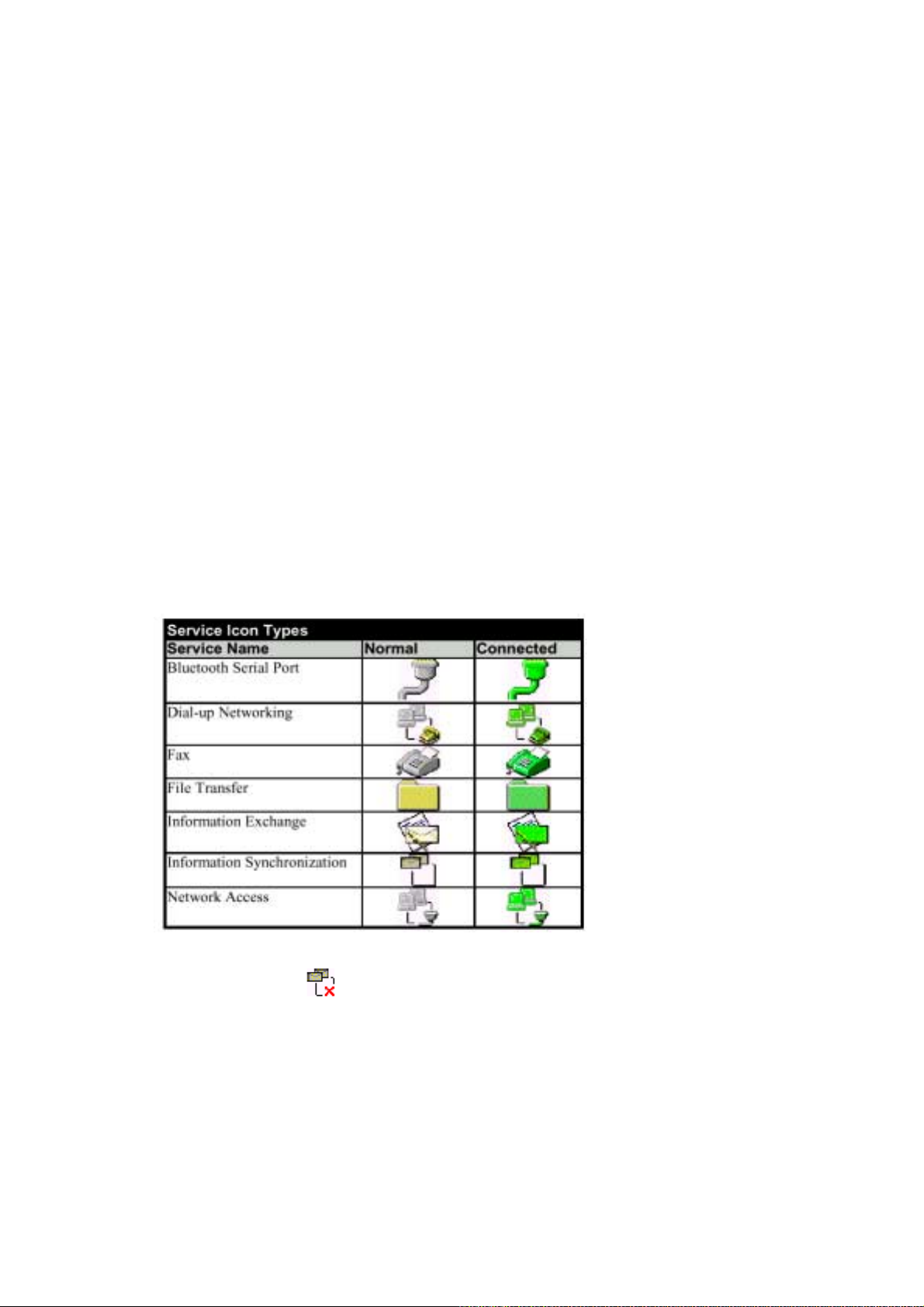
Service icons
Icons with gray or yellow-color indicates “normal” state. Icons with green-color indicates
“Connected” state.
Icons with a red “X” indicate “not available”.
6
Page 8
2. Step-by-Step Installation Guide
This chapter shows you in details of installing and uninstalling Bluetooth USB Adapter.
2.1 Installation
Before installation, make sure the previous version of Bluetooth USB Adapter software has
been uninstalled. See Chapter 2.2 Uninstallation.
1. Insert the installation software CDROM into the CDROM drive on the computer. The
auto-run option starts. You may manually start the setup process: click
Start>Run>setup.exe. When the Welcome screen displays, click “Next”.
2. Read the License Agreement and tick “I accept the terms in the license agreement”.
Click “Next”.
7
Page 9
3. Enter a name for your computer, and select a device type. Click “Next”.
4. Click “Next” to install to this folder, or click “Change” to install to a different folder.
8
Page 10
5. Click “Install” to begin installation.
6. Installing…
9
Page 11
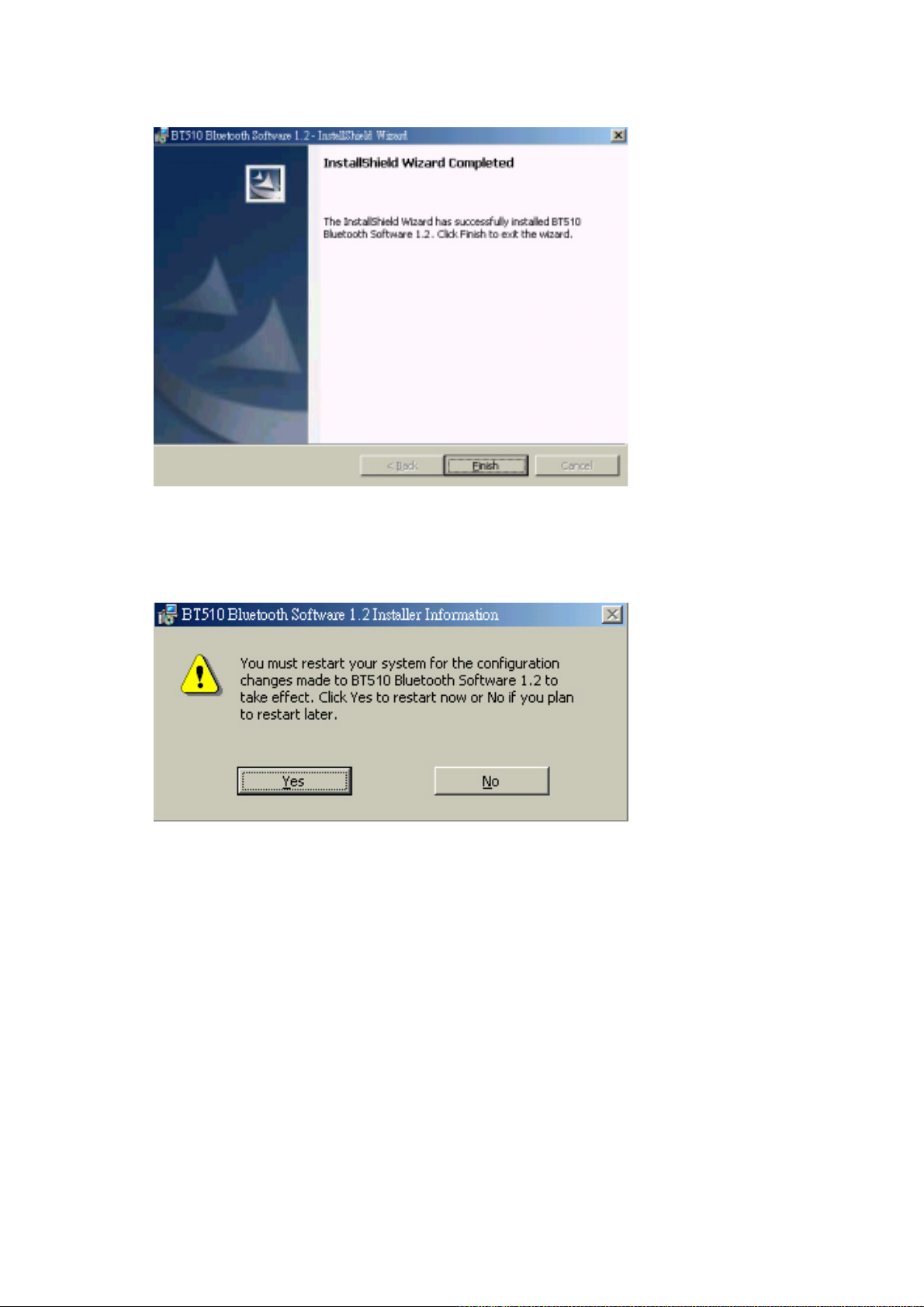
7. Installation completed. Click “Finish” to exit the InstallShield Wizard.
8. Click “Yes” to restart your computer.
10
Page 12
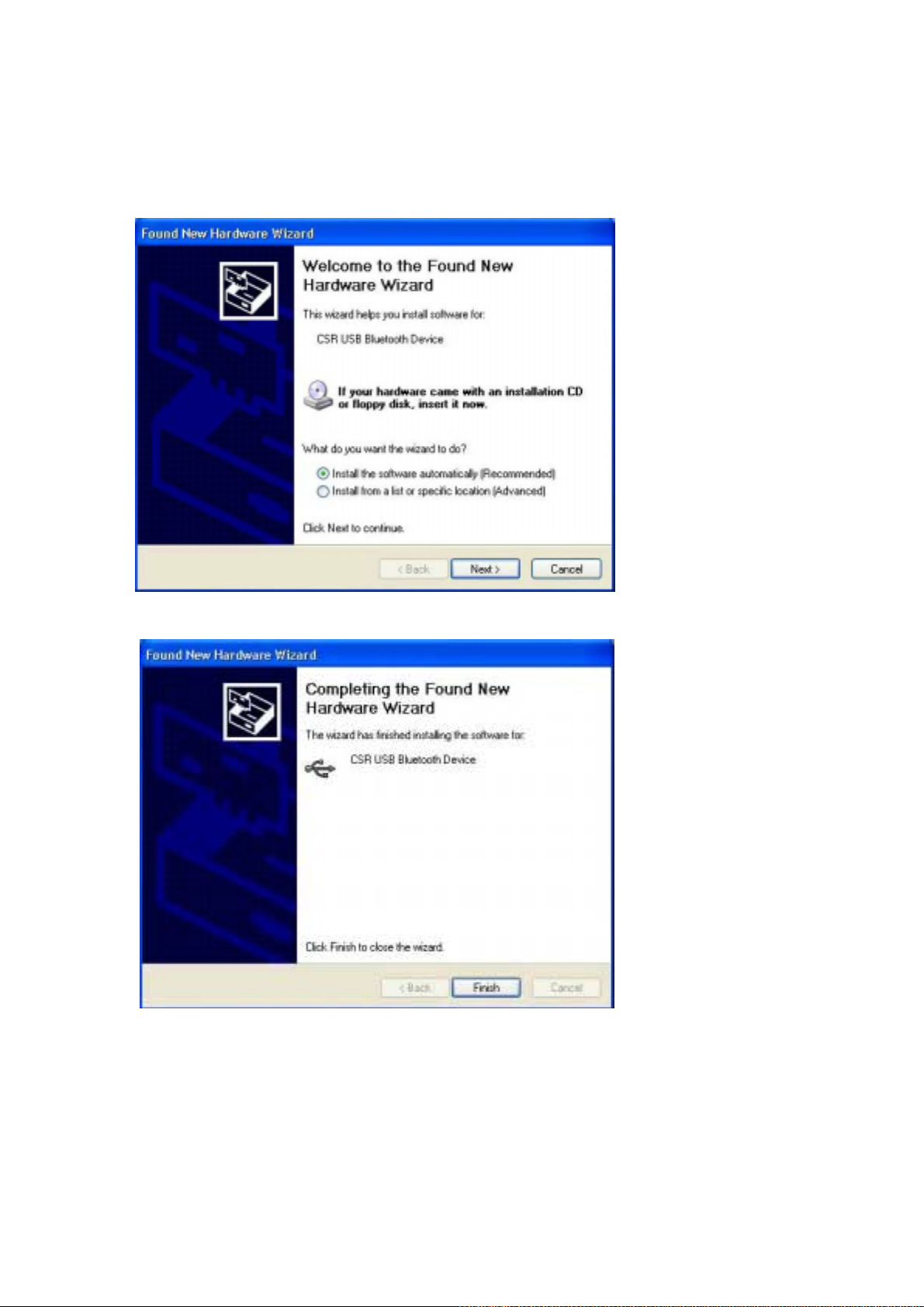
Additional Notes for Windows XP:
! For the first time inserting the BT510, the system will ask you to install the driver again.
Click “Next” and then “Finish”.
! If your laptop notebook has 2 USB ports, you have to install the driver again for the first
time inserting BT510 into either port. Click “Next” and then “Finish”.
11
Page 13

2.2 Uninstallation
Two ways of uninstallation:
1. When installing an upgraded version, the InstallShield Wizard automatically uninstalls
the previous version.
2. Manually uninstall the software:
a. Close any open applications.
b. From the Windows taskbar, click Start>Settings>Control Panel.
c. Double click “Add/Remove Programs”.
d. On the Add/Remove Programs window, select the Software entry.
e. Click “Change/Remove”. The InstallShield Wizard starts.
f. On the Confirm File Deletion window, click “OK” to remove the software.
g. Click “Restart” and then click “Finish”.
12
Page 14
3. Basic Operations
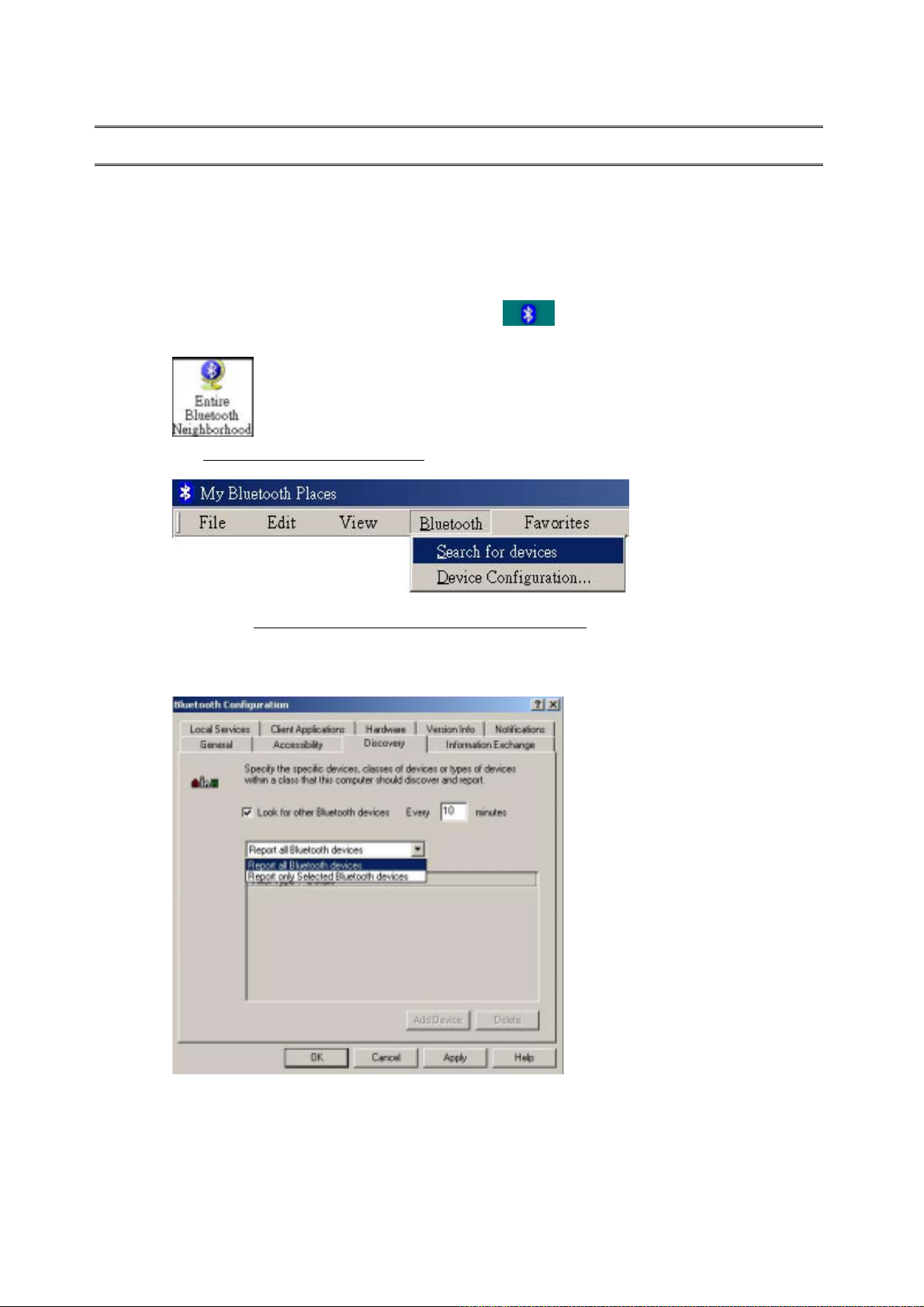
3.1 Finding Bluetooth Devices
Follow the steps below to use the submenu “Search for Devices” to find any available
Bluetooth devices in the vicinity:
1. Double click on “My Bluetooth Places” icon on the desktop.
2. Double click “Entire Bluetooth Neighborhood”. The devices found are displayed.
3. Click Bluetooth>Search for devices to search most recent available Bluetooth devices.
You may go to Bluetooth>Device Configuration>Discovery to make your computer to
automatically search for devices on a regular basis. Doing so can guarantee you that the
displayed list of devices in the neighborhood is current.
Note! If there are some devices within connection range not found in the list, it might
because of:
1. Those devices are set to be non-discoverable. (From those unfound devices, go to
Bluetooth Configuration Panel and select “Accessibility” tab to change the
13
Page 15
settings.)
2. Your device is configured to search for only specific types or classes of devices.
(From your device, go to Bluetooth Configuration Panel, and select “Discovery” tab
to change the settings.)
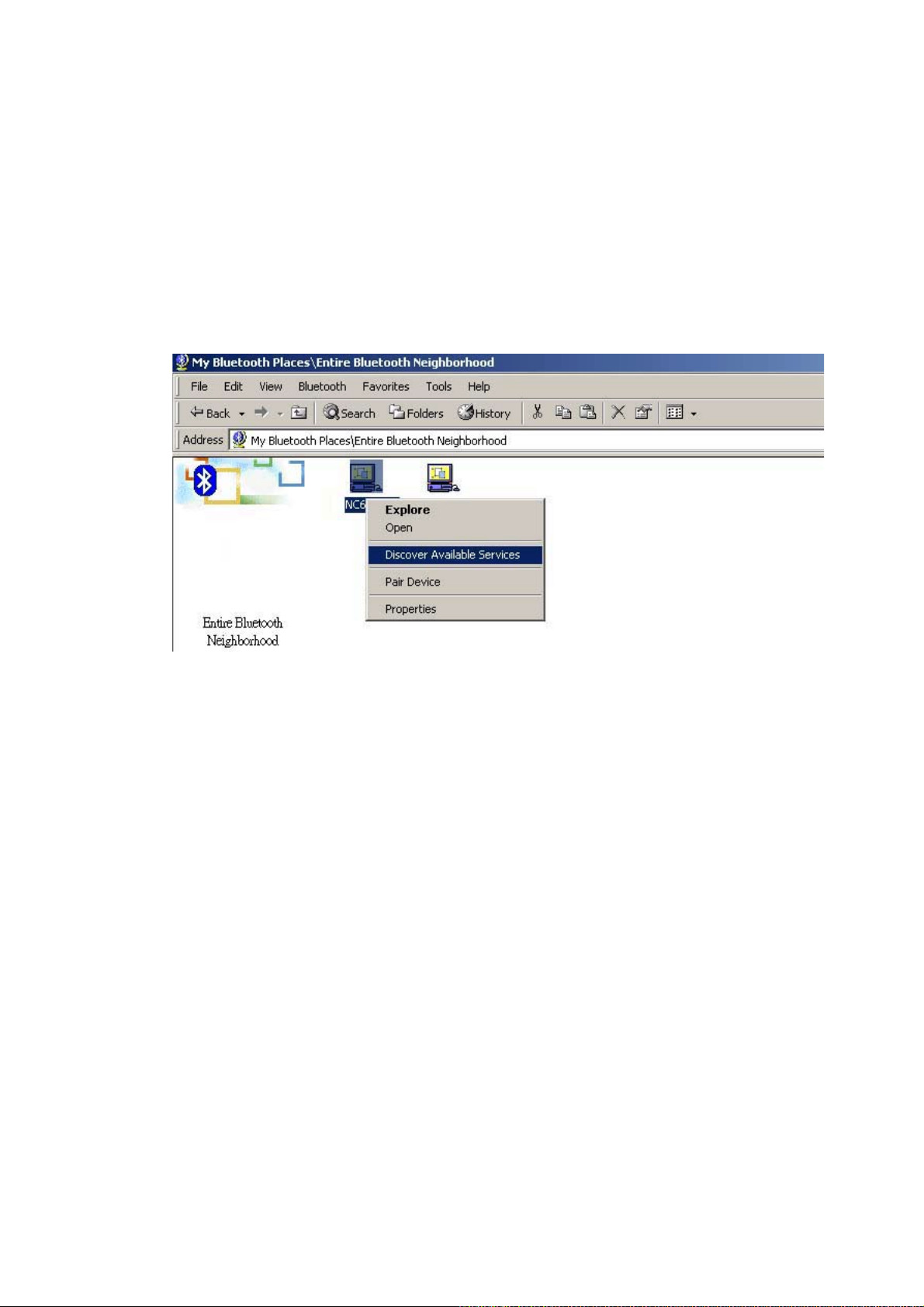
3.2 Finding a Service
To find a service: In the Folders pane of My Bluetooth Places, double-click on the device,
or right-click on the device and select “Discover Available Services” from the pop-up menu.
The followings are possible available services:
! Bluetooth Serial Port – allows two devices to build a Bluetooth wireless connection.
This service provides a wireless connection being used by applications as if a physical
serial cable connected the devices.
! Dial-up networking – Allows a Bluetooth client to use a modem that is attached to the
Bluetooth server.
! Fax – Allows a Bluetooth client to send a fax using a device that is attached to the
Bluetooth server.
! File Transfer – Allows your computer to wirelessly perform file system operations
(browse, drag, open, copy, etc.) on another Bluetooth device.
! Information Exchange – Allows two Bluetooth devices to wirelessly exchange
personal information manager data such as email messages, notes, business cards and
calendar items.
! Network Access – Allows a Bluetooth client to wireless connect to a server that is
physically connected to the LAN. If the client has user name and password for the
LAN, the wireless connection can be used as though the client were hardwired to the
LAN.
Note! Note every Bluetooth server provides all of these services.
14
Page 16
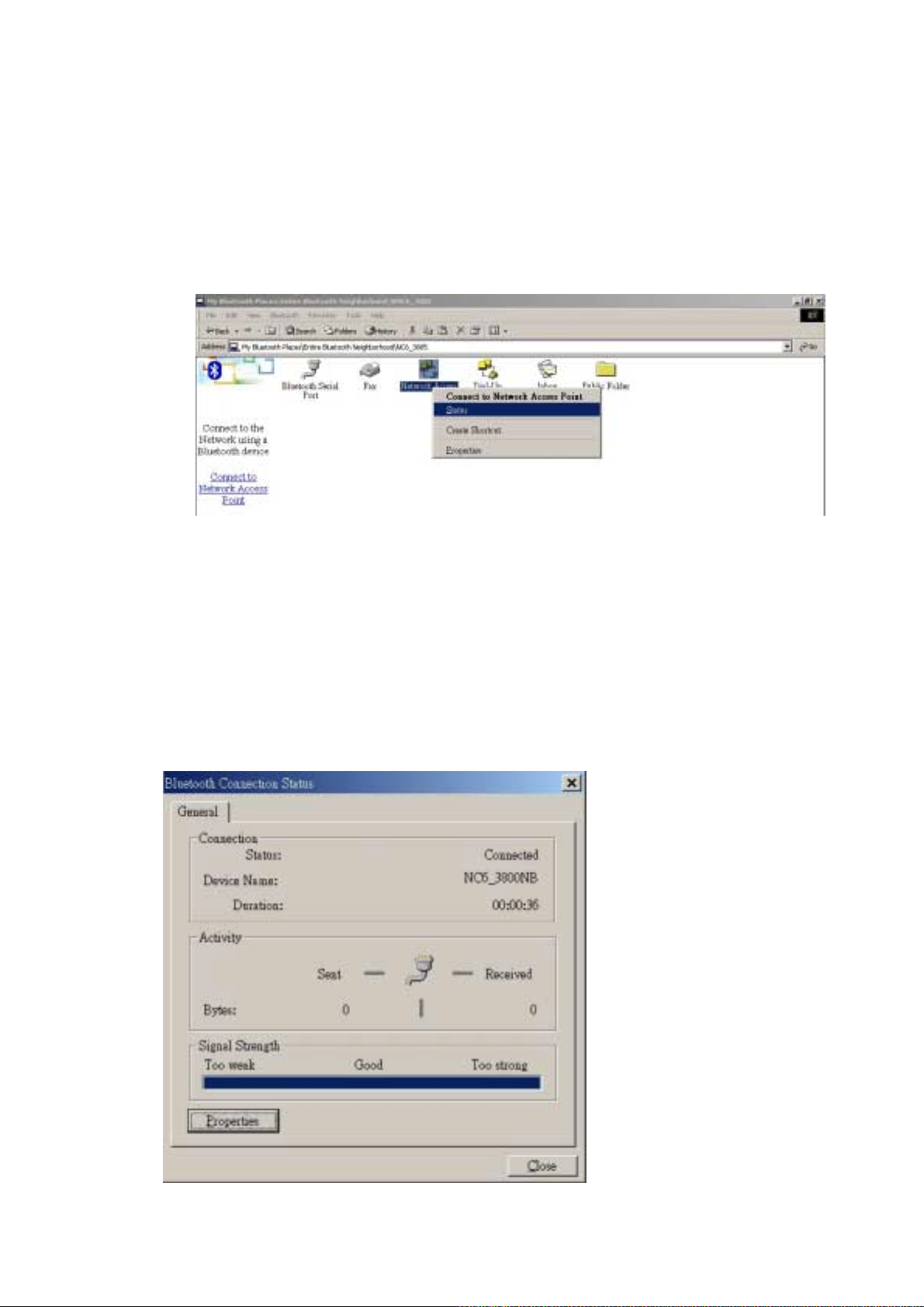
3.3 Connection’s Status
Follow the steps below to open Bluetooth Connection Status dialog box that allows you to
view the connection status or to disconnect an active connection:
1. In My Bluetooth Places, highlight a device.
2. In the right pane of My Bluetooth Places, right-click on a service name and select
“Status” from the pop-up menu.
The following information is provided:
! Status: Shows you the connected or disconnected status.
! Device Name: Shows you the name of the device with which this computer is
connected.
! Duration: Shows you the time it took to build the connection. The connection
may be disabled after a specific period of inactivity.
! Activity: Gives you the number of bytes sent and received over the connection.
! Signal Strength: Shows you the signal strength – Too Weak, Good or Too Strong.
15
Page 17
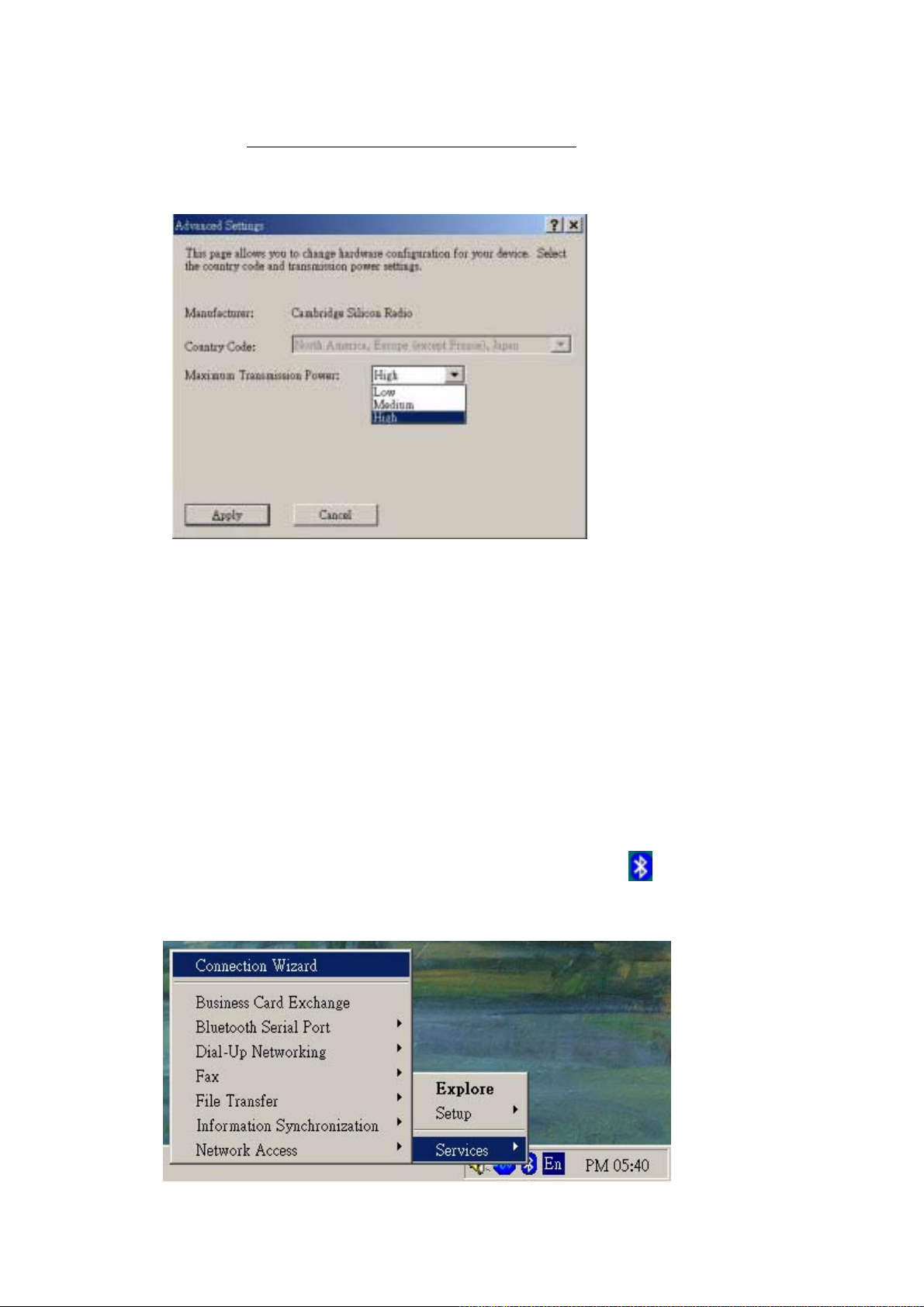
To change the power transmission level of this computer:
1. Go to Bluetooth>Device Configuration>Hardware.
2. Click “Advanced”.
3. Change the setting in the Maximum Power Transmission drop-down list.
The following control buttons are provided:
! Properties: Click this button to display the Bluetooth Properties dialog box.
! Disconnect: Click this button to disable this connection (see status of “Network
Access” and “Dial-Up Networking”).
! Close: Click this button to close this dialog box.
3.4 New Connection
Connection Wizard helps you to easily set up a new Bluetooth connection with another
device. To active the connection, double-click the shortcut that is placed in the right pane
of My Bluetooth Places. Follow the steps below to set up a new connection:
1. In the Windows system tray, right-click on the Bluetooth icon , and select
“Services” from the pop-up menu. Select “Connection Wizard” from the submenu,
and the first Connection Wizard screen displays.
16
Page 18
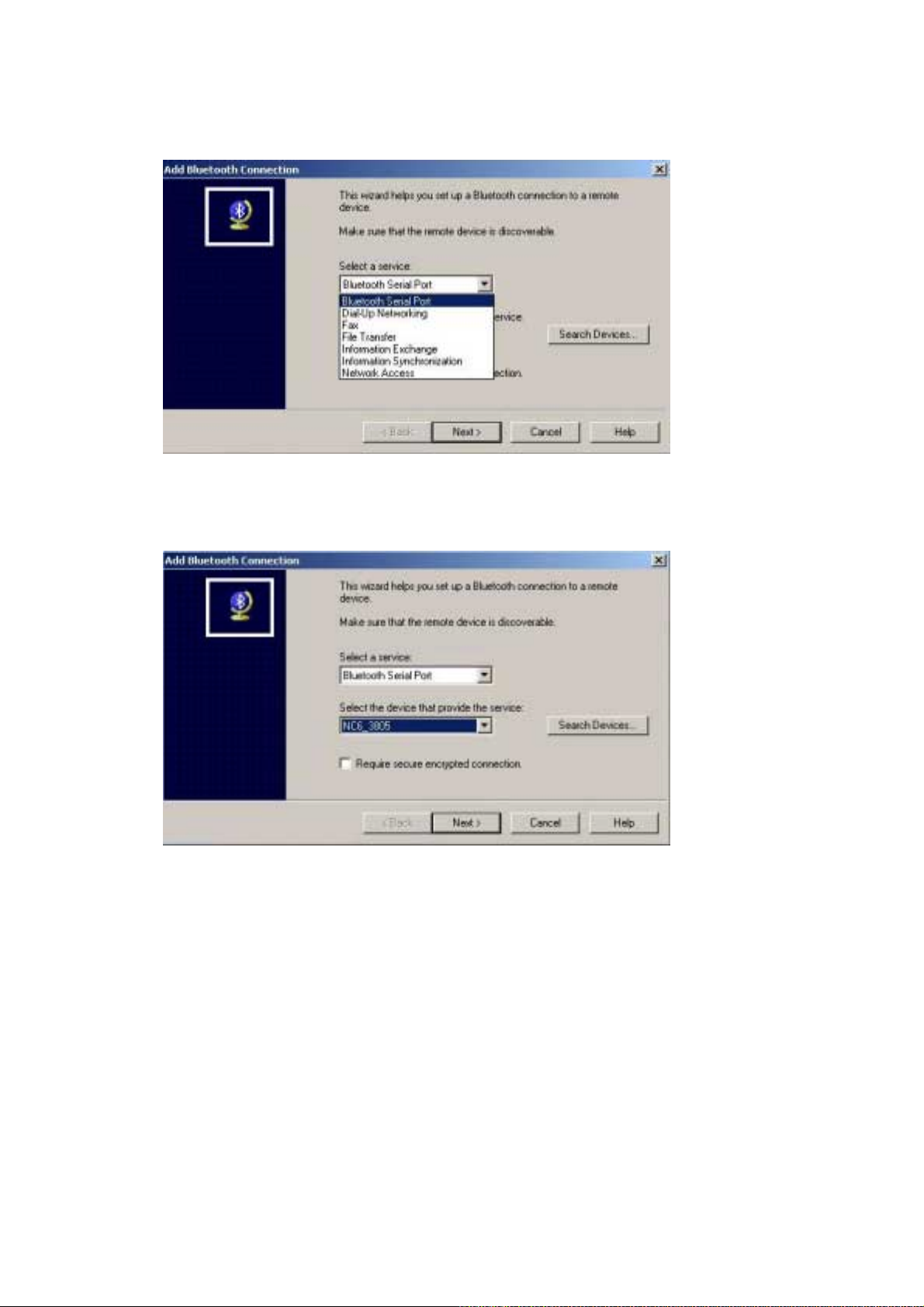
2. From the “Select a Service” drop-down menu, choose the type of connection that will be
established. (You may select a specific service later.)
3. From the “Select a device that provides the service” drop-down menu, select the device
that will provide the service. (To update the list of devices found, follow the steps in
Chapter 3.1 Finding Bluetooth Devices.)
4. Select the “Require secure encrypted connection” option to enable Authentication and
Encryption for this connection. Click “Next” to go to next screen.
5. If there is more than one service in the “Select a Service” drop-down menu of the
selected device, choose the specific service to be used. Click “OK” to close the dialog
box. On the other hand, if there is only one service of the type selected in the dropdown menu, the next Connection Wizard screen appears.
6. If you choose “Require secure encrypted connection”, a security screen appears. You
need to enter your Personal ID Number in the PIN Code field of the security screen to
establish a paired relationship with the remote device. Click “Next”. However, if this
is the first time connection, leave the PIN Code field blank in the security screen, and
click “Next”.
17
Page 19

Note! You will not see the Security screen if the devices have been paired.
7. From the last Connection Wizard screen, you can see the basic information about the
new connection (includes the name of the device providing service and the name of the
service). If the information is not correct, go back to the previous screen and modify
the selection.
8. Enter a name for the connection in the “Connection Name” field. For example,
“Bluetooth Serial Connection to Molly’s Laptop”.
18
Page 20

3.5 Bluetooth Tray
You can find the Bluetooth Tray in the Windows System Tray (usually in the lower-right
corner of the screen). Double click on the Bluetooth icon allows you to access “My
Bluetooth Places”.
Right click on the Bluetooth icon, you can find the following functions:
! Configuration: Go to Setup>Configuration to access the Bluetooth Configuration
Panel.
! Security: Go to Setup>Security to access the Bluetooth Security dialog box
! Connection Wizard: Go to Services>Connection Wizard to active Connection
Wizard.
! Business Card Exchange: Go to Services>Business Card Exchange to enable
exchanging Business Cards with another Bluetooth computer.
! Other services: Go to Services and choose the desired service from the submenu
(includes Bluetooth Serial Port, Dial-up Networking, Fax, File Transfer,
Information Synchronization and Network Access). Additional submenu will
appear, includes:
" Find Devices…
or
" Other Devices…and one or more device names. The device names appear
because the computer used to use this service and connect via this technique
before. Select the device from the additional submenu will re-initialize the
connection.
19
Page 21

3.6 Pairing Devices
1. Right click on the Bluetooth icon in the Windows System Tray. Choose “Setup” and select
“Security” from the submenu.
2. Click “Refresh” button to update the list of available Bluetooth devices in
vicinity.
3. From the list of Found Devices, click the device’s name.
20
Page 22

4. Click “Execute Pairing” button .
5. When Bluetooth Passkey Request dialog box appears, enter a passkey in the Bluetooth
Passkey field. You can type within 16 alphanumeric characters (for example: 0000). Click
“OK”.
6. From the other Bluetooth device, a message pops up informing you that a Bluetooth
connection request is detected. Click the Bluetooth icon in the Windows System Tray.
7. In the Bluetooth Passkey field, enter the passkey. The passkey for both of the paired
devices should be the same (“0000” in this example). Click “OK”.
21
Page 23

8. After pairing, the Paired Device’s name is listed in the Paired Devices pane. Click “Done”
button to close the “Bluetooth Security” dialog box.
9. Devices remain paired until the pairing relationship is terminated on BOTH devices.
22
Page 24

3.7 Breaking a Paired Device Relationship
1. Right click the Bluetooth icon in the Windows System Tray. Choose “Setup” and select
“Security” from the submenu.
2. From the Paired Devices pane, select the device. Click “Delete”. .
3. Click “Done” .
4. Repeat Step1~Step3 on the other Bluetooth device.
23
Page 25

3.8 Setting Security for Local Services
1. Right-click the Bluetooth icon in the Windows System Tray. Select “Setup” and then
“Configuration”.
2. Click “Local Services” tab. Double click a service name to set its security. For example:
Bluetooth Serial Port.
3. In the “Service Properties” dialog box, select the check boxes of “Authorization”,
“Authentication”, “Startup” or “Encryption”. Select a COM Port. Click “OK”.
24
Page 26

4. Click “Apply” and then “OK” to save and implement the new settings.
25
Page 27

3.9 Connecting to a Secured Service
1. Double click the shortcut icon, My Bluetooth Places, on the desktop.
2. Double click “Entire Bluetooth Neighborhood”. All available Bluetooth devices are then
listed.
3. Right-click the chosen device (“NC6_3805” in this case) and select “Discover Available
Services”.
26
Page 28

4. Double click one service (“Bluetooth Serial Port” in this case).
5. From the other device (“NC638” in this case), a message pops up informing that
“NC6_3805” is trying to connect to the secured service.
6. If the user of “NC638” allows this connection, he/she will click the Bluetooth icon in the
Windows System Tray and then create a Bluetooth Passkey. You need this passkey to
access this service.
27
Page 29

7. Once you get the permission for the connection, from your device, a message pops up asking
for the passkey.
Enter the passkey and then click “OK”.
8. Click “OK” to complete the service connection.
The “Bluetooth Serial Port” icon changes the color to green.
28
Page 30

3.10 Sharing Secured Local Services
1. When you see a message pops up telling you that there’s one Bluetooth device (“NC6_3805”
in this case) is trying to connect to one of your secured service, click the Bluetooth icon in
the Windows System Tray.
2. If you would like to allow this connection, enter a passkey. (The user of “NC6_3805” will
need to know this passkey.) Click “OK”.
3. When the message below pops up, click the Bluetooth icon.
29
Page 31

4. Click “OK” to permit this connection. Or, you may click “Advanced>>” button to select the
services that the connecting device is allowed to access without authorization.
5. Click “OK”.
30
Page 32

4. Client Applications
4.1 Network Access
Network Access service allows a Bluetooth client to use a Local Area Network connection
that is physically connected to another Bluetooth device (the server). Network Access
servers can be Bluetooth-enabled computers that have a hardwired Ethernet connection, or
Stand-alone Bluetooth Network Access Points. The server must be configured to provide
the Network Access service. Once the device is configured as a Network Access server, it
cannot act as a Network Access client without being re-configured.
4.1.1 Network Access Server-side Setup (for Windows 2000)
! Click Start>Settings>Control and select Network and Dial-up Connections.
! Right-click the “Local Area Connection” icon and choose Properties.
! Choose Sharing tab. In the Local Area Connection Properties dialog box, select
“Enable Internet Connection Sharing” for this connection. Click “OK”.
! Click “Yes”.
4.1.2 Configuring the server
! Click Start>Settings>Control>Network
! From Configuration tab, select TCP/IP > Bluetooth LAN Access Server Driver
! Click Properties and select IP Address tab.
! Select “Specify an IP address”
! Enter an IP Address and a Subnet Mask (check with the network administrator for the
value).
! Click “OK” twice.
! Click “Yes” to restart the computer.
4.2 Bluetooth Serial Port
Bluetooth Serial Port service allows two devices to build a Bluetooth wireless connection.
This service provides a wireless connection being used by applications as if a physical serial
cable connected the devices. A Bluetooth serial port connection is initiated from the client.
Follow the steps below to establish a connection:
1. Double click on “My Bluetooth Places” icon on the desktop. Double click
“Entire Bluetooth Neighborhood”.
2. Right-click anywhere except on a device name. When the pop-up menu shows up,
select “Refresh”.
3. Right-click on the server you want to connect with. When the pop-up menu shows up,
31
Page 33

select “Discover Available Services” to update the available services list.
4. Double-click “Bluetooth Serial Port”. The communications port number assigned to
this connection by the client is displayed in the pop-out dialog box. The application
using this connection must be configured to send data to this port.
The application on the server must use the correct communications port.
Follow the steps below to determine and configure the communications port being used by
the service:
! On the server, in “My Bluetooth Places”, right-click “My Device”. When the
pop-up menu appears, choose Properties. “Bluetooth Configuration” panel
appears.
! Click “Local Services”.
! Double-click “Bluetooth Serial Port” in the Service Name column to display its
Service Properties dialog box in which you can find the communications port the
connection is using.
To close a Bluetooth serial port connection from the client, follow the steps below:
! On the client, in “My Bluetooth Places”, highlight the device providing the
Bluetooth Serial Port service.
! In “My Bluetooth Places”, right-click “Bluetooth Serial Port”. Select
“Disconnect Bluetooth Serial Port” from the pop-up menu.
To close a connection from the server (not recommended), follow the steps below:
! On the server, in “My Bluetooth Places”, right-click “Bluetooth Serial Port” and
select “Stop”. Re-start the service before it is ready to remote devices (rightclick “Bluetooth Serial Port” and select “Start” from the pop-up menu).
4.3 Dial-Up Networking
Dial-Up Networking service allows a Bluetooth client to use a modem that is attached to the
Bluetooth server. The client can use the server’s modem as if it were a local device on the
client.
Follow the steps below to establish a Dial-Up Networking session (a connection is initiated
from the client):
1. On the client, in “My Bluetooth Places”, double-click “Entire Bluetooth
Neighborhood”.
2. In “Entire Bluetooth Neighborhood”, right-click anywhere except on a device
name and choose “Refresh” from the pop-up menu.
32
Page 34

3. In “My Bluetooth Places”, right-click the server that will provide the Dial-Up
Networking service. When the pop-up menu appears, choose “Discover Available
Services” to update the available services list.
4. In “My Bluetooth Places”, double-click “Dial-Up Networking”.
5. In “Connect To” dialog box, enter your user name, password, and the phone
number to be dialed, and click “Dial”. Select the Save password check box and
then the dialog box will not appear for subsequent connections to the same phone
number.
6. Now you can open the web browser and connect to the Internet.
Follow the steps below to close a Dial-Up Networking connection:
1. On the client, in “My Bluetooth Places”, highlight the device that is providing the
Dial-Up Networking service.
2. In “My Bluetooth Places”, right-click Dial-Up Networking. When the pop-up
menu appears, select Disconnect Dial-Up Networking.
4.4 Fax
Fax service allows a Bluetooth client to send a fax using a device that is physically attached
to the Bluetooth server.
Follow the steps below to send a fax (the connection is initiated from the client):
1. On the client, in “My Bluetooth Places”, double-click “Entire Bluetooth
Neighborhood”.
2. In “Entire Bluetooth Neighborhood”, right-click anywhere except on a device
name and choose “Refresh” from the pop-up menu.
3. In “My Bluetooth Places”, right-click the server that will provide the fax service.
Select “Discover Available Services” when the pop-up menu appears. The
available services list is updated.
4. In “My Bluetooth Places”, double-click Fax.
5. Open or create the document to be faxed. Use “Print” or “Send to Fax Recipient”
option available in most applications.
6. The Fax connection will be closed automatically after the transmission is complete.
4.5 File Transfer
File Transfer service allows your computer to wirelessly perform file system operations
(browse, drag, open, copy, etc.) on another Bluetooth device.
Follow the steps below to perform an operation on a folder or file (on the device from
which the File Transfer service will be used):
33
Page 35

1. In “My Bluetooth Places”, double-click “Entire Bluetooth Neighborhood”.
2. In “Entire Bluetooth Neighborhood”, right-click anywhere except on a device name.
Choose “Refresh” from the pop-up menu.
3. In “My Bluetooth Places”, right-click the device you want to transfer files with.
Choose “Discover Available Services” when the pop-up menu appears.
4. In “My Bluetooth Place”, click “+” in front of Public Folder to expand that folder. If
there are additional folders inside the expanded folder, those folders may have to be
expanded.
4.5.1 File Transfer Operations
In the right pane of “My Bluetooth Places”, right-click on a folder item, and choose an
option from the pop-up menu. A dialog box displays. The status line (in the bottom of
the dialog box) shows the operational step that is being carried out.
There are 8 types of operations can be accomplished: Open, Print, Send to, Cut, Copy,
Delete, Rename and Properties.
Other options may be available (depends on the context the menu appears in):
! Update: updates a folder’s contents
! New Folder: creates a new folder on the server
! Abort FTP Operation: aborts an in-process File Transfer operation
4.6 Information Exchange
Information Exchange service allows two Bluetooth devices to wirelessly exchange
personal information manager data such as email messages, notes, business cards and
calendar items.
Three types of operations are available: Send, Receive and Exchange.
The supported Outlook items are:
! Business cards (~.vcf, ~.vcd)
! Calendar entries (~.vcs)
! Notes (*.vnt)
! Messages (~.vmg)
In the Bluetooth Configuration Panel, you can configure the default location for placing
your business card and receiving items.
To send/receive/exchange an item, you can right-click the Inbox icon of the remote device
(from “My Bluetooth Places”), and choose an option from the pop-up menu.
To send Calendar Items, Notes, and Message, navigate to that folder and select the item.
Click “Open”.
34
Page 36

4.7 Information Synchr onization
Information Synchronization service enables the information synchronized between a
Bluetooth client and a Bluetooth server.
For the first time using Information Synchronization service with a new application may
take a few minutes to synchronize the database. The data from both devices must be
merged. After deleting duplicate entries, the updated database will be copied back to both
devices. From the second time using this service with the same application will be much
faster, because it exchanges only those changes that have been made since the database
were synchronized last time.
Follow the steps below to use Information Synchronization service:
1. On the client, in “My Bluetooth Places”, double-click “Entire Bluetooth
Neighborhood”.
2. In “Entire Bluetooth Neighborhood”, right click anywhere except on a device name.
Select “Refresh” when the pop-up menu appears.
3. In “My Bluetooth Places”, right-click the server that will be synchronized with and
choose “Discover Available Services” from the pop-up menu, which will update
the available services list.
4. In “My Bluetooth Places”, double-click “Information Synchronization”.
When the process is complete, a dialog box displays and shows you that synchronization
has successfully completed, and then the connection closes automatically.
35
Page 37

5. Local Services
Local Services are services that a Bluetooth server can provide, including Bluetooth Serial Port,
Dial-Up Networking, Fax, File Transfer, Information Exchange, Information Synchronization
and Network Access.
The server might not be able to provide all displayed services. For example, without a fax
modem, Fax service cannot be executed.
The services are set to be started automatically once the Bluetooth USB Adapter is initialized.
However, the automatic start-up can be turned off for individual services, and the services can be
started manually by right-clicking the service and selecting “Start” from the pop-up menu.
To terminate a local service, you can right-click the service and choose “Stop” from the pop-up
menu.
When a Local Device is selected, the Details view of Explorer provides the following basic
information of each local service:
! Service: shows the name of the service
! Startup: has 2 options (Automatic or Manual)
! Status:
" Started (COM): means that the service is running and ready to use COM#
" Not Started: means that the service is not running (not available for use by clients)
" Connected (COM#): means that the service is in use, and the local port is COM#
! Device name (if connected):
" Empty field: indicates that the service is not connected
" A device name and/or Bluetooth Device Address: shows the name and the address
of the device that is using the service.
Two ways to interrupt a connection from the server:
! Right-click the local service. Choose “Stop” from the pop-up menu.
! Right-click the local service. Choose “Start” from the pop-up menu to restart the
service.
36
Page 38

6. Configuration Panel
Bluetooth Configuration Panel allows you to view or modify the settings for Bluetooth services,
hardware and security and for event notification.
To access the Configuration Panel, click Start>Settings>Control>Bluetooth Configuration, or
right-click the Bluetooth icon in the Windows System Tray and select Setup>Configuration.
6.1 Accessibility Tab
From Accessibility tab, you can specify which remote devices to access this computer. The
security settings (in General, Local Services and Client Applications tabs) will also affect
which devices can access to this computer.
To permit other Bluetooth devices to find and report this computer: select “Let other
Bluetooth devices discover this computer”.
To allow only specific type of devices to connect to this computer
From the Allow drop-down menu, there are 4 options as follows:
! No devices to connect: no remote devices are allowed to initiate a connection with
this computer. The computer can initiate connections (as a client) with remote
Bluetooth devices.
! All devices to connect: allows all remote devices to connect to this computer.
! Only paired devices to connect: allows devices been paired with this computer
can connect to this computer.
37
Page 39

! Only devices listed below to connect: allows only the listed devices to connect to
this computer.
6.1.1 Adding and Deleting Devices
To allow only specific remote devices to access to your computer: from Bluetooth menu,
choose “Device Configuration”, click “Accessibility” tab, and select “Only devices listed
below to connect” from “Allow” drop-down menu.
To add an unfound device to the list of devices:
! From Bluetooth Configuration Panel, select “Accessibility” tab, and select “Only
devices listed below to connect” from “Allow” drop-down menu. Click “Add
Device”, and “Devices with access…” dialog box displays.
! From the “Devices with access…” dialog box, select the devices and click “OK”.
(Use “Shift + click” or “Ctrl + click” to select multiple devices at the same time.)
To delete a device from the list of devices allowed for connection:
! From “Bluetooth Configuration Panel”, choose “Accessibility” tab
! In the list of devices, click the name of the device and click “Delete” to remove
that device.
38
Page 40

6.2 Discovery Tab
Discovery Tab allows you to modify the settings of your computer:
! To look for other Bluetooth devices automatically
! How often it looks
! What type of devices it looks for
To perform a periodic Search for Device: Select “Look for other Bluetooth devices”.
Highlight the existing time and enter a new time. The time can be an integer from 1 to 60
minutes. For the first time opening “My Bluetooth Places” (even when “Look for other
Bluetooth devices” is not enabled) the computer automatically searches for devices.
You have two options to report the devices:
! Report all Bluetooth devices
! Report only selected Bluetooth devices.
You can modify the settings to report only specific devices, specific classes of devices, or
specific types of devices within a class.
To report only specific devices:
! In Bluetooth Configuration Panel, choose “Discovery” tab, and select “Report
only selected Bluetooth devices” from the drop-down menu. Click “Add
Device”.
! In the “Discoverable devices…” dialog box, select the device to be discovered.
Click “OK”. You can choose multiple devices at the same time.
39
Page 41

To report only a specific class of device:
! In Bluetooth Configuration Panel, choose “Discovery” tab, and select “Report
only selected Bluetooth devices” from the drop-down menu. Click “Add
Device”, and “Discoverable devices…” dialog box displays.
! From the “Discoverable devices…” dialog box, select “Allow this computer to
discover all devices of a specific class or a specific type of device within a
specific class”.
! Select a class of devices to be discovered from the “Class” drop-down list, and
click “OK”.
To report only a specific type of device within a class:
! In Bluetooth Configuration Panel, choose “Discovery” tab, and select “Report
only selected Bluetooth devices” from the drop-down menu. Click “Add
Device”.
! From the “Discoverable devices…” dialog box, select “Allow this computer to
discover specific devices or types of devices within a class”.
! Select a class of devices to be discovered from the “Class” drop-down list.
! From the “Discoverable devices…”dialog box, select the specific type of devices
to be reported from the “Type” drop-down menu, and click “OK”.
To temporarily override the discovery of specific devices: From Bluetooth Configuration
Panel, select “Discovery” tab, and choose “Report all Bluetooth devices”.
To re-enable specific device discovery: re-select “Report only selected Bluetooth devices”.
When all devices are deleted and “Report all Bluetooth devices” is not selected, an error
message appears.
40
Page 42

6.3 General Tab
In “General” tab, you may view or modify the settings of “Computer Name”, “Computer
type” and “Security mode”.
! Computer Name: Enter a unique name for this computer. This field cannot be left
blank.
! Computer type: From the drop-down menu, you may choose either “Desktop” or
“Laptop”.
! Security mode: “Medium” is the default setting. In Medium security mode, the
security is configured at the service-level, which means that each individual service
must have its security settings set independently. “High” security mode requires
Bluetooth devices to authenticate before allowing a connection to be built. The data
exchange between your computer and the connected Bluetooth device is done through
security settings.
! If the “Medium” security mode is selected and service-level security is not configured,
any Bluetooth devices in the range will be able to discover your computer and use it’s
services.
41
Page 43

6.4 Hardware Tab
To view basic information about the Bluetooth hardware installed on this computer, choose
“Hardware” tab from the Bluetooth Configuration Panel.
! Devices:
" Name: shows the name of the device.
" Type: shows the type of the device
! Device Properties:
" Manufacturer: shows the name of the company that manufactured the device
selected in the Devices section of this dialog box.
" Firmware Revision: shows the manufacturer’s firmware version number.
" Device status: shows that the device is operating properly or that there’s a
conflict.
" Device Address: shows the Bluetooth Device Address programmed into this
device when it was manufactured.
" HCI Version: shows the version number of the Bluetooth Specification that the
Host Controller Interface complies with.
" HCI Revision: shows the revision number of the Bluetooth Specification that the
Host Controller Interface complies with.
" LMP Version: shows the version number of the Bluetooth Specification that the
Link Manager Protocol complies with.
" LMP Sub Version: shows the sub-version number of the Bluetooth Specification
42
Page 44

that the Link Manger Protocol complies with.
! Advanced: Clicking on “Advanced” displays the Advanced Settings dialog box, and
from which you can select the country code and transmission power settings. This
option is not available on all systems. However, the “Advanced” button my not be
present depends on the country where the hardware is sold.
You may choose one country code from 2 options:
" North America, Europe (except France), and Japan
" France and China
Three options of Maximum Transmission Power are available: High, Medium and
Low.
Click “Apply” to save and implement the modification of the settings. A message
appears to inform you that this computer must to be reset to allow the changes take
effect.
Click “Yes” to reset the Bluetooth device, and all open Bluetooth connections will be
closed.
43
Page 45

6.5 Information Exchange Tab
Settings in “Information Exchange” tab of Bluetooth Configuration Panel configure:
! The highest-level directory on this computer that a remote device has permission to
access - My Shared Directory
The directory configured in this section and its sub directories are displayed in the
remote device’s My Bluetooth Places. Click “Browse” to choose a directory that will
be used as My Shared Directory.
! The path to your electronic business card - My Business Card
Select “Send Business Card on Request” to allow remote devices to obtain your
business card. Click “Browse” to choose a directory that contains your business card.
! The path to the directory that will be used to save incoming - My Inbox Directory:
" Business cards
" Calendar items
" Email Message
" Notes
Select the types of items you wish to accept, and then click “Browse” to choose a
directory where they will be saved. Select “Save Object in Personal Information
Manager” to save incoming objects directly in the PIM.
44
Page 46

6.6 Local Services Tab
The settings in this tab determine the configuration of the services provided by your
computer to remote devices. The Local Service names include: Bluetooth Serial Port,
Dial-Up Networking, Fax, File Transfer, Information Exchange, Information
Synchronization and Network Access. Each service can be configured individually for
security, name and other settings.
Property setting which are common to all of the local services
All local services have settings for:
! Service Name
! Startup
! Authorization
! Authentication
! Encryption
Some services have their specific additional setting:
! Network Access service has an additional setting for the maximum number of
connections allowed at any time.
! Dial-Up Networking service has an additional setting for selecting the modem
that will be used by the service.
! Fax service has an additional setting for selecting the modem that will be used by
the service.
! Bluetooth Serial Port has an additional setting for selecting the communications
45
Page 47

that will be used by the service.
Adding an additional Bluetooth Serial Port
1. In Bluetooth Configuration Panel, choose “Local Services” tab, and click “Add
Serial Service”. The Service Properties dialog box displays.
2. Enter a unique name.
3. Select the appropriate security settings.
4. Select “Startup” if you want the service to start automatically when Bluetooth
connection initializes.
5. Choose a communications port that is not assigned to any other service from the
COM Port drop-down menu.
Removing a user-defined Bluetooth Serial Port
From Bluetooth Configuration Panel, choose “Local Services” tab. Highlight the port
to be removed, and click “Delete”.
To change a local service’s properties: from Bluetooth Configuration Panel, choose
“Local Services” tab and double-click the service name.
Select or clear the appropriate check boxes and click “OK”.
The service properties that can be changed include:
! Startup: The default setting is enabled. If Startup is not enabled, the service
can still be started manually.
! Authorization: when this option is selected, the server operator requires a
confirmation before a remote device is allowed to connect to this service.
When Authorization is enabled, Authentication is automatically enabled.
The default of Authorization setting is disabled.
! Encryption: When this option is selected, the data exchanged by the
Bluetooth server and the Bleutooth client is encrypted. Encryption affects
only those data exchanged through Bluetooth connection. Data exchanged
through modem, Local Area Network, etc., will not be affected by this
setting. When Encryption is enabled, Authentication is automatically
enabled.
! Authentication: When this setting is enabled, a passkey or Link Key is
required. The default setting is disabled. Devices are paired automatically
when authentication is complete.
! Service Name: Enter a service name in this field. Although in most cases
the default service name will serve, you may customize the service name
when there’s more than one device of the same type or one device provides
more than one service of the same type in the environment.
46
Page 48

6.7 Notifications Tab
In this tab, you can associate a sound (~.wav file) with specific Bluetooth events such as:
! When a PIN code is required
! When a remote device attempts to access:
" Files on this computer
" A Bluetooth port
" The Dial-up network service
" The LAN Access service
" The Fax service
! When a remote device attempts to send information items or Synchronization
information.
Follow the steps below to associate a sound with a Bluetooth event:
1. In Bluetooth Configuration Panel, choose “Notifications” tab
2. Select the check box associated with the event from the Notify column of the
events list.
3. In the Sound area of the Notifications tab, click “Browse” to navigate to the sound
file (~.wav) to be used. Click play button to preview the sound file.
4. Click “OK” to close Bluetooth Configuration Panel.
Note! The sound will not play even though it has been assigned, unless the Notify
check box is selected.
47
Page 49

6.8 Version Info Tab
You may view the name and version number of the software components from Version Info
tab.
48
Page 50

7. Security
Each service the server provides can be configured to require “Authorization”, “Authentication”
and “Encryption”. The default setting for Authorization, Authentication and Encryption is
disabled.
7.1 Authentication
Authentication is used to verify identify which requires a passkey or Link Key from the
remote device. The local operator can open a dialog box that provides “The user-friendly
name of the device attempting access” and “A place for the local operator to enter a
Bluetooth passkey”.
The operator of the remote system has to enter the identical passkey, otherwise the access
will be denied.
If the notification is ignored, access is denied after a preset timeout. When devices are
“paired”, those devices automatically exchanged a Link Key and Authentication is carried
out without operator intervention.
7.2 Authorization
The server operator will see or hear a warning when a remote device is attempting to
connect. The server operator responds by clicking the Bluetooth icon in the Windows
system tray to open a dialog box that displays “The user-friendly name of the device
attempting to connect” and “The local service to which the remote device is attempting to
connect”. By clicking an on-screen button, the server operator may grant or deny access to
the service. If the server operator ignores the Authorization notification access will be
denied after a preset timeout.
7.3 Encryption
Encrypting translates data into an unreadable format with a secret key or password. To
decrypt the data, the same key or password that was used to encrypt are required. The
passkey or Link Key of encryption is based on those for Authentication. Therefore, if
Authentication is not enabled, the key is not available and encryption will not take place.
Follow the steps below to enable Encryption for service:
1. Right-click a service name and the pop-up menu displays. Select Properties to
display the Bluetooth Properties dialog box.
2. Select Encryption.
3. Click “OK” to close the dialog box.
49
Page 51

7.4 Levels of Security
The configuration options include:
! Startup-Automatic or Manual
! Authorization
! Authentication
! Encryption
To access the security settings for a local service, select “Local Services” tab from
Bluetooth Configuration Panel, and double-click the service name.
7.5 Link Key
A Link Key is an access code. When devices are paired or when Authentication is enabled,
the Link Keys are generated automatically. Combining “The Passkey”, “The Bluetooth
Device Address” and “An internally generated random number” creates link Keys.
7.6 Pairing Devices
“Pairing” can avoid entering access information each time a connection is attempted.
Paired devices share a unique Link Key that is exchanged when connecting.
The mate of paired devices will always appear in “My Bluetooth Places”, even if the mate is
not turned on or is out of connection range. Paired devices remain paired even when that
one of the devices is not powered up, or a service connection is interrupted, or the service
stopped or one or both devices are rebooted.
Follow the steps in Chapter 3.6 and Chapter 3.7 to pair devices and break a paired device
relationship.
7.7 Passkey
A passkey can be a number of up to 16 characters in length. Passkeys are used in the
Authentication and Encryption process.
7.8 Security Request Dialog Box
When either Authorization or Authentication is enabled, a “Bluetooth Authorization” or
“Bluetooth Passkey Request” dialog box may appear when a connection is attempted.
In the dialog box, you can find:
! Device Name: Shows the name of the device attempting to connect.
! Request to access: Shows the service the remote device is attempting to access.
50
Page 52

Click “OK” to allow the connection, or click “Cancel” to deny the connection. You may
select the check box to grant the connecting device access to all of the services on this
computer.
7.9 Authorization Request Dialog Box, Advanced Button
The check box on the main page of Bluetooth Authorization dialog box, when selected,
allows the device attempting to connect to access all services on this computer when
attempting to connect in the future.
Follow the steps below to limit the services the connecting device may use:
1. Click “Advanced”.
2. From the expanded dialog box, select the services that the connecting device is
allowed to use. Once selected, the service will not require authorization in the
future.
3. Click “OK”.
51
Page 53

8. BlueMux
BlueMux is a software that allows two or more Client PCs, using their own keyboards and mice,
to wirelessly operate the Server PC as if using Server PC’s keyboard and mouse. When
“Accept multiple connection” is selected (described below), you can connect seven Client PCs at
the same time to the Server PC. Once connected, any one of the seven Client PCs can operate
the Server PC.
Using BlueMux:
1. From BOTH the Server PC and Client PC(s), click Start>Programs>BT510>BlueMux.
2. From the Windows System Tray, double-click the BlueMux icon.
3. From the toolbar of the BlueMux Management window, click the Inquiry Button to search
52
Page 54

vicinity Bluetooth devices.
4. From the device list, double-click the Server PC to build the connectivity between the Client
and the Server.
5. From the Client PCs, you have 4 ways to turn on the remote control function:
(1) Press Ctrl + F1
(2) From the Windows System Tray, right-click on the BlueMux icon , and select “HID
Switch”.
(3) From the Toolbar of the BlueMux Management window, click “HID Switch” button.
(4) Enable Automatic Switch. From the Toolbar of the BlueMux Management window,
click “Configuration” button, and select “Enable Automatic Switch”. If the Client
PC(s) is set to enable “Automatic Switch”, when the cursor reaches the border of the
screen, it automatically switches on the remote control function. If the remote control
function is on and both the Client and Server are set to enable “Automatic Switch”,
53
Page 55

when the cursor reaches the border of the Server’s screen border, it automatically
switches off the remote function.
Note! You can only turn on or off the remote control function from the Client PCs, not
from the Server PC.
Configuring BlueMux:
1. Automatic Switch: Click Configuration button and select “Enable Automatic Switch” from
the drop-down menu. If the Client PC(s) is set to enable “Enable Automatic Switch”, when
the cursor reaches the border of the screen, it automatically switches on the remote control
function. If the remote control function is on and both the Client and Server are set to
enable “Enable Automatic Switch”, when the cursor reaches the border of the Server’s screen
border, it automatically switches off the remote function.
2. Multiple Connection: From the Server PC, click Configuration button and select “Accept
multiple connection” to allow up to seven Client PCs to connect to the Server PC, otherwise
only one Client PC is allowed for the connection. When this function is disabled, the
connected Client PCs will remain connected until they decide to exit.
54
Page 56

9. Connection with Mobile Phone T68
Pairing and connecting Bluetooth USB Adapter with Sony Ericsson's mobile phone T68:
1. Press the “Function Key” of your T68.
2. Select “Connect” from the display and press “Yes”.
3. Select “Bluetooth” from the display and press “Yes”.
Connect
1. Infrared port
2. Bluetooth
3. Synchronization
4. Networks
5. Data comm..
4. Select “Discover” from the display and press “Yes”. “Searching” is displayed.
Bluetooth
1. Discoverable
2. Paired devices
3. Discover
4. Operation mode
5. The T68 seeks all Bluetooth™ devices in the vicinity and displays all available devices.
Select the desired device to connect with and press “Yes”.
6. Select “Add to paired” and press “Yes”.
7. Enter a Passkey (e.g. ‘1234’), and press “Yes”.
8. From your laptop computer, double click the Bluetooth icon on in the Windows System Tray.
A “Bluetooth connection request detected” message might pop up.
55
Page 57

9. In the Bluetooth Passkey field, input the same number as that entered for T68 (‘1234’ in this
example). Click “OK”.
10. “Pairing succeeded” is displayed on T68.
11. On T68, click “Yes” to add this pairing into the list. “Added to Paired Devices” is
displayed.
12. On the desktop of your laptop computer, double click the Bluetooth icon .
13. From your laptop, double click “Entire Bluetooth Neighborhood”.
14. From your laptop, double click the T68 icon.
15. On your laptop computer, double click “Dial-Up Networking”.
16. T68 dials the number wirelessly transmitted from your laptop computer. (You can see the
dial-up number displayed on your T68).
Note:
Note: If “Discover” function of T68 is disabled, please follow the steps below to
Note: Note:
turn on the function.
1. Press Function Key of your T68.
2. Select “Connect” from the display and press “Yes”.
3. Select “Bluetooth” from the display and press “Yes”.
Connect
1. Infrared port
2. Bluetooth
3. Synchronization
4. Networks
5. Data comm..
4. Select “Operation mode” from the display and press “Yes”.
Bluetooth
1. Discoverable
2. Paired devices
3. Discover
4. Operation mode
5. Select “On” and press “Yes”.
56
Page 58

10. Specifications
Hardware
Host Interface USB ver.1.1
Input Voltage / Current DC5V/ 150 mA (Typical)
Current Consumption (Typical) - Standby mode, Ista: 30mA
- Transmission mode, Itx: 120mA
Data Transfer Rate 1.0 Mbps (Max)
Antenna Meander IFA
RF
Frequency Range 2.402 GHz ~ 2.480 GHz
Channel Spacing 1 MHz
Power Class Class 2
Tx Power (Typical) 0 dBm
Rx Sensitivity 0.1% BER/Pin: -70dBm
Antenna Load 50 Ohm
Software
Operation System Windows™ 95/98SE, ME and Windows™ 2000, XP
Core Protocol Stack -HCI (Host Control Interface)
-L2CAP (Logical Link Control and Adaptation Protocol)
-RFCOMM (RS232 Serial Cable Emulation Profile)
-SDP (Service Discovery Protocol)
-OBEX (Object Exchange)
Profile Pack -GAP (General Access Profile)
-SDGP (Service Discovery Application Profile)
-SPP (Serial Port Profile) Client & Server
-LAN Access Client & Server
-DUN (Dial-Up Networking) Client & Server
-FAX Profile Client
-GOEP (Generic Object Exchange Profile)
-FTP (File Transfer Profile) Client & Server
-OPP (Object Push Profile) Client & Server
-SYNC (Synchronization Profile)
57
Page 59

58
 Loading...
Loading...