WiNetworks WiN5213-2, WiN5235-2 User Manual And Installation Manual

M/N: MDOC
-
CPE4
310
User’s Manual & Installation Guide for:
WiN5200 Series Outdoor CPE
WiNetworks Win-MaxTM 802.16e
Version: 4.3
Revision: 1.1
Date: July 2008

THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO
CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL
ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KI ND, EXPRESSED
OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS.
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN
THE INFORMATION PACKET SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS
REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT
YOUR WiNETWORKS REPRESENTATIVE FOR A COPY.
NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE
SUPPLIERS ARE PROVIDED “AS IS”WITH ALL FAULTS. WiNETWORKS AND ITS SUPPLIERS SUPPLIERS
DISCLAIM ALL WARRANTIES,EXPRESSED OR IMPLIED, INCLUDING,WITHOUT LIMITATION, THOSE OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A
COURSE OF DEALING, USAGE, OR TRADE PRACTICE.
IN NO EVENT SHALL WiNETWORKS OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL,
CONSEQUENTIAL, OR INCIDENTAL DAMAGES,INCLUDING,WITHOUT LIMITATION,LOST PROFITS OR LOSS OR
DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF WiNETWORKS
OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
COPYRIGHT ©2007 WINETWORKS. ALL RIGHTS RESERVED.
WINETWORKS AND WIN-MAX™ ARE REGISTERED TRADEMARKS OF WINETWORKS AND/OR ITS AFFILIATES
IN THE U.S.AND CERTAIN OTHER COUNTRIES.
ALL OTHER TRADEMARKS MENTIONED IN THIS DOCUMENT OR WEB SITE ARE THE PROPERTY OF THEIR
RESPECTIVE OWNERS. THE USE OF THE WORD PARTNER DOES NOT IMPLY A PARTNERSHIP RELATIONSHIP
BETWEEN WINETWORKS AND ANY OTHER COMPANY.

Table of Contents
Introduction ...................................................................................................... 5
1.1 About this Manual ............................................................................................................... 6
1.2 General Description ............................................................................................................ 6
1.2.1 Features .................................................................................................................... 7
1.3 Package Components and Unpacking ............................................................................ 7
1.4 Safety Information ............................................................................................................... 7
Product Description ......................................................................................... 9
2.1 Introduction ........................................................................................................................ 10
2.2 IEEE 802.16e Mobile WiMAX Compliance ................................................................... 11
2.3 Block Diagram ................................................................................................................... 11
2.4 Features ............................................................................................................................. 12
2.4.1 Mobile WiMAX Wave 2 MIMO Features ............................................................ 12
2.4.2 Security ................................................................................................................... 14
2.4.3 Time Division Duplexing (TDD) ........................................................................... 17
2.4.4 Coding Rate ............................................................................................................ 17
2.4.5 Modulation .............................................................................................................. 17
2.4.6 Convolution Coding Error Correction .................................................................. 17
2.5 Deployment Models .......................................................................................................... 18
2.5.1 PTP Deployment .................................................................................................... 18
2.5.2 PMP Deployment ................................................................................................... 18
2.5.3 Non Line-of-Sight ................................................................................................... 18
2.5.4 Channelization ....................................................................................................... 18
2.6 Service Flows .................................................................................................................... 19
2.6.1 Service Flow Classification................................................................................... 19
2.6.2 Dynamic Service Addition .................................................................................... 19
2.6.3 Default Service Flows ........................................................................................... 19
2.6.4 Scheduling .............................................................................................................. 20
2.7 Physical Description ......................................................................................................... 21
WiN5200 Table of Contents | 3

2.7.1 Physical Interfaces Description ........................................................................... 21
2.7.2 LED Indication Description ................................................................................... 22
Mounting ......................................................................................................... 23
3.1 General ............................................................................................................................... 24
3.2 Site Survey ......................................................................................................................... 24
3.3 Pole Mounting .................................................................................................................... 25
3.4 Wall Mounting .................................................................................................................... 25
Installation Procedure .................................................................................... 26
4.1 Safety Hazards .................................................................................................................. 27
4.2 Tools and Cables Required for the Installation ............................................................ 27
4.3 Installing the WiN5200 ..................................................................................................... 27
4.3.1 Pole Mounting ........................................................................................................ 28
4.3.2 Wall Mount .............................................................................................................. 29
4.4 Cable Connections ........................................................................................................... 31
4.4.1 Installing the WiN1010 data adapter for WiN5200 ........................................... 31
Equipment Configuration and Monitoring .................................................... 34
5.1 Configuring WiN5200 Basic Parameters ....................................................................... 35
5.2 Aligning the CPE Antenna ............................................................................................... 37
5.2.1 CPE Antenna Alignment Procedure.................................................................... 38
5.2.2 Link Indication ........................................................................................................ 39
Management ................................................................................................... 40
6.1 General ............................................................................................................................... 41
6.2 SW Download/Upgrade ................................................................................................... 41
6.3 Web-page Management .................................................................................................. 42
6.4 SNMP Management ......................................................................................................... 46
Appendix A – Product Specification ............................................................. 47
Appendix B – IDU to ODU Cable Specifications ........................................... 48
List of Acronyms ............................................................................................ 49
WiN5200 Table of Contents | 4

1
Introduction
WiN5200 Introduction | 5
1.1 About this Manual
This manual describes the installation procedures of WiN5200 Outdoor CPE with Ethernet
interface and is written for the installers and operators.
WiN5213-2 and WiN5235-2 products will be referred in this manual as WiN5200 from now
.
on
The WiNetworks WiN5200 is a member of the Win-Max™ E family, a line of mobile WiMAX
broadband wireless access systems based on the 802.16e mobile WiMAX standard. The WinMax™ E family is detailed in the System Description manual of WiNetworks.
This manual assumes that users have some experience with WiMAX technologies and
procedures.
While some safety precautions are reviewed here, this manual assumes that installers have
been trained in safe installation practices. Users, who are new to WiMAX technologies and
service procedures, should not rely on this manual for comprehensive guidance.
1.2 General Description
The WiNetworks WiN5200 ODU is a member of the Win-Max™ E
family, a line of WiMAX Broadband Wireless Access systems based
on the 802.16e mobile WiMAX standard, specially designed for
quadruple-play applications.
WiN5200 is a high-performance outdoor unit that provides
WiN5200 Introduction | 6
complete 802.16e mobile WiMAX broadband wireless access
functionality to a range of indoor multi-service gateways.
The WiN5200 enables the full scope of triple-play (including
telephony, data, Video-on-Demand) over the WiMAX network. In
the home, triple play services are distributed to a single gateway
for a simple home-networking solution.
The WiN5200 is based on the IEEE 802.16e standards to effectively
meet the unique requirements of the wireless Metropolitan Area
Network (MAN) environment and to deliver broadband access
services to a wide range of customers. Specifically designed for
point-to-multipoint broadband wireless access applications, the
WiN5200 provides efficient use of the wireless spectrum,
supporting a range of user environments. The access and
bandwidth allocation mechanisms accommodate hundreds of
subscriber units per sector, supporting differentiated services to a
multiple of end-users.

1.2.1 Features
• Intelligent WiMAX subscriber unit for wireless triple-play service delivery
• Outdoor unit with ETH interface to indoor unit
• Automatic, self-configured, plug-n-play
• Supporting 1.X, 2.X and 3.X GHz bands
1.3 Package Components and Unpacking
Check that the package contains:
1. WiN52xx ODU with integrated flat antenna
2. Pole/wall mounting hardware
In case of damage, contact the shipping company.
1.4 Safety Information
RF Exposure
The WiN5200, an outdoor CPE, is compliant with the requirements set forth in CFR 47 section
1.1307, addressing RF Exposure from radio frequency devices as defined in OET Bulletin 65.
The outdoor CPE should be positioned more than 0.6 feet (20 cm) from humans.
Lightning Protection
When WiN5200 is installed in an outdoor location, all indoor components (Ethernet, power
supply) should be connected through a lightning protector.
The purpose of the lightning protection is to protect people and equipment located indoors
from lightning that might strike the WiN5200 or its outdoor cables. Therefore, the lightning
protector device should be installed indoors, as close as possible to the point where the cables
enter the building. The lightning protector can also be installed outdoors, as long as the cables
that lead from it indoors are well protected from lightning between the box and the building
entrance.
Power Cord Protection
The WiN5200 should always be connected to the WiN1010 data adapter for both power
supply and data transfer purposes.
Any other type of connection/application of the WiN5200 and/or WiN1010 is not allowed.
Route all power supply cords so that people cannot walk on them, or place objects on or
against them. This can pinch or damage the cords.
WiN5200 Introduction | 7

Servicing
Do not open the cover of this product and perform corrective actions unless instructed to do
so in the operating instructions.
Outdoor Grounding System
Verify that the antenna or cable system is grounded (earthed).
The antenna is an integral part of the CPE.
The CPE (antenna) installation must be as per Article 810 of the NEC. Of particular note is the
requirement that the grounding conductor not be less than 10 AWG (Cu). The scheme should
be either in accordance with UL 96 and 96A. Lightning Protection Components and
Installation Requirements for Lightning Protection Systems, or tested in accordance with UL
50 and UL 497.
CAUTION
To reduce the risk of fire, use only No. 26AWG or larger telecommunication line cord
between the indoor and outdoor units.
NOTE:
This equipment has been tested and found to comply with the limits for a Class B digital
device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable
protection against harmful interference in a residential installation. This equipment generates,
uses and can radiate radio frequency energy and, if not installed and used in accordance with
the instructions, may cause harmful interference to radio communications. However, there is
no guarantee that interference will not occur in a particular installation. If this equipment
does cause harmful interference to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try to correct the interference by
one or more of the following measures:
- Reorient or relocate the receiving antenna.
- Increase the separation between the equipment and receiver.
- Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
- Consult the dealer or an experienced radio/TV technician for help.
Changes or modifications to this equipment not expressly approved by WiNetworks Ltd.
could void the user’s authority to operate the equipment.
WiN5200 Introduction | 8

2
Product Description
WiN5200 Product Description | 9
2.1 Introduction
The WiN5200 ODU CPE is an IEEE 802.16-2005 compliant wireless device for deployment of
point-to-multipoint (PMP) and point-to-point (PTP) network architectures.
The WiN5200 ODU CPE is an outdoor device. The WiN5200 ODU CPE is WiMAX Forum
802.16e Wave 2 (MIMO) Certified subscribers. Each subscriber registers and establishes a bidirectional data link with the base station sector controller.
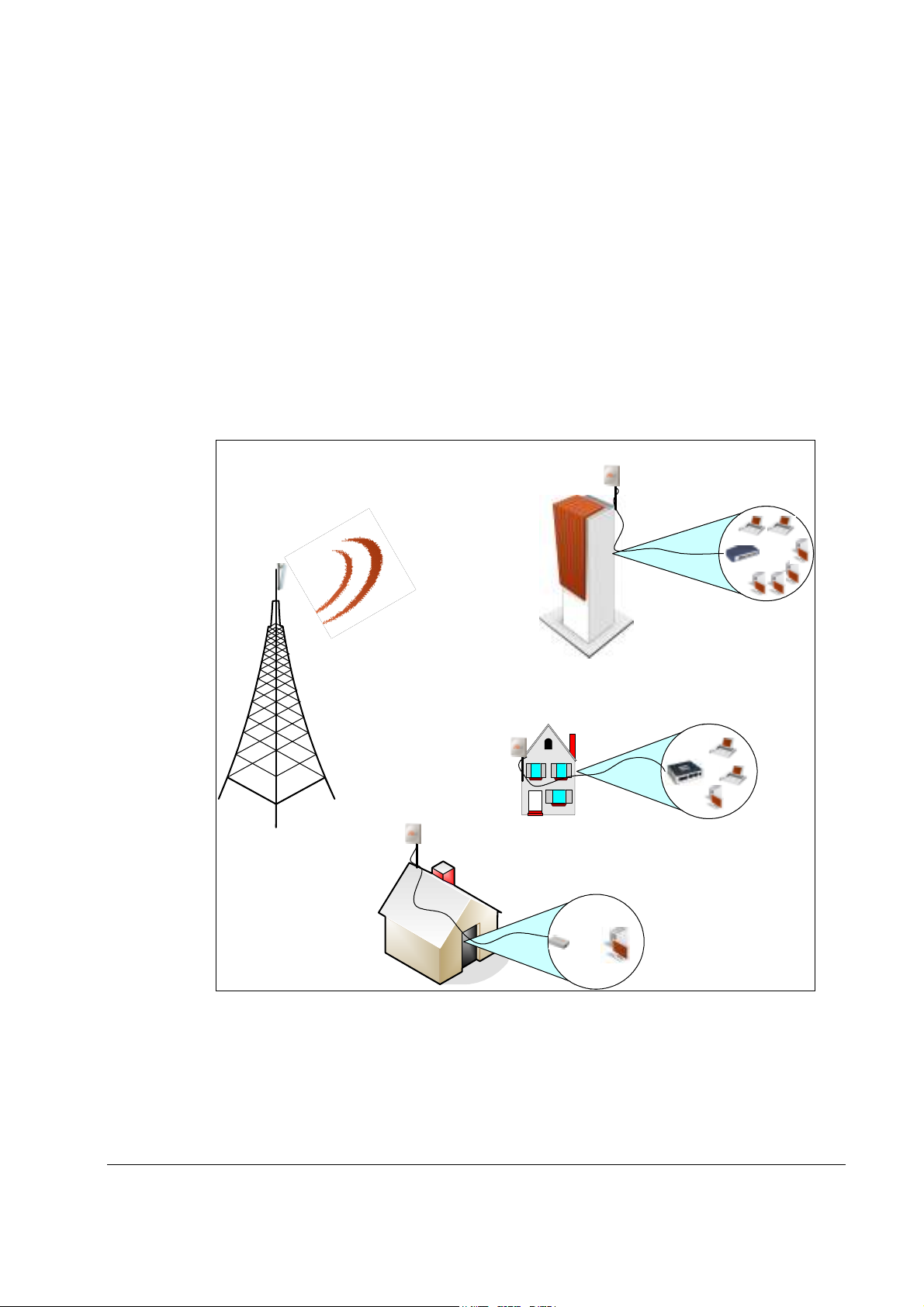
The CPE terminals are grouped into two classes, Outdoor CPEs and Residential Gateways
(RG) which are indoor units. The relationship between all the units is illustrated below.
BST
WiN70xx
CPE
WiN52xx
RG
WiN1030-1
CPE
WiN52xx
Figure 2-1: Functional Overview of the CPEs
CPE
WiN52xx
RG
WiN1020-1
House
RG
WiN1010-1
WiN5200 Product Description | 10

The base station is connected to the head-end over IP Backhaul or via wireless channels. The
outdoor CPEs are connected to the base station over wireless channels. The outdoor CPE is
connected to the indoor residential gateway over Ethernet or coaxial networks.
2.2 IEEE 802.16e Mobile WiMAX Compliance
The IEEE 802.16-2005 specifications describe a PMP broadband wireless access standard for
systems. This standard includes descriptions for both the Media Access Control (MAC) and
the physical (PHY) layers.
The WiN5200 ODU CPE is compliant to IEEE 802.16-2005 WiMAX forum Wave 2 profile.
Note
The 802.16e standards are subject to amendment, and Win-MaxTM product family design compliance
applies to a specific revision of the standard. The Win-MaxTM product family does not support mesh
communication (direct subscriber-to-subscriber).
WiNetworks is an active member of the IEEE 802.16e standards committee and has been
instrumental in creating the original 802.16e standards. WiNetworks is also active in
recommending, writing and following-up on new amendments to the 802.16e specifications.
WiNetworks is an active member of the WiMAX Forum™ and is participating in
interoperability testing in the WiMAX Forum.
2.3 Block Diagram
The CPE consists of the following modules:
1. Base-Band board – including the WiMAX 16e MIMO Base-Band SoC (running the 16e
MAC + PHY) plus the User Interface plus the analog front end that interface the RF
module.
2. Power Supply board– DC/DC power supply. Converts the 48VDC to the various voltages
that are feeding the Digital and the RF modules
3. RF board - Single transmit dual receive module that modulate the analog WiMAX signal
input from the Base-Band modem to the high frequency RF output. Several RF modules
exist - each supporting different frequency band.
4. Chassis
5. Antenna – Integrated dual polarization antenna to support the MIMO schemes
WiN5200 Product Description | 11
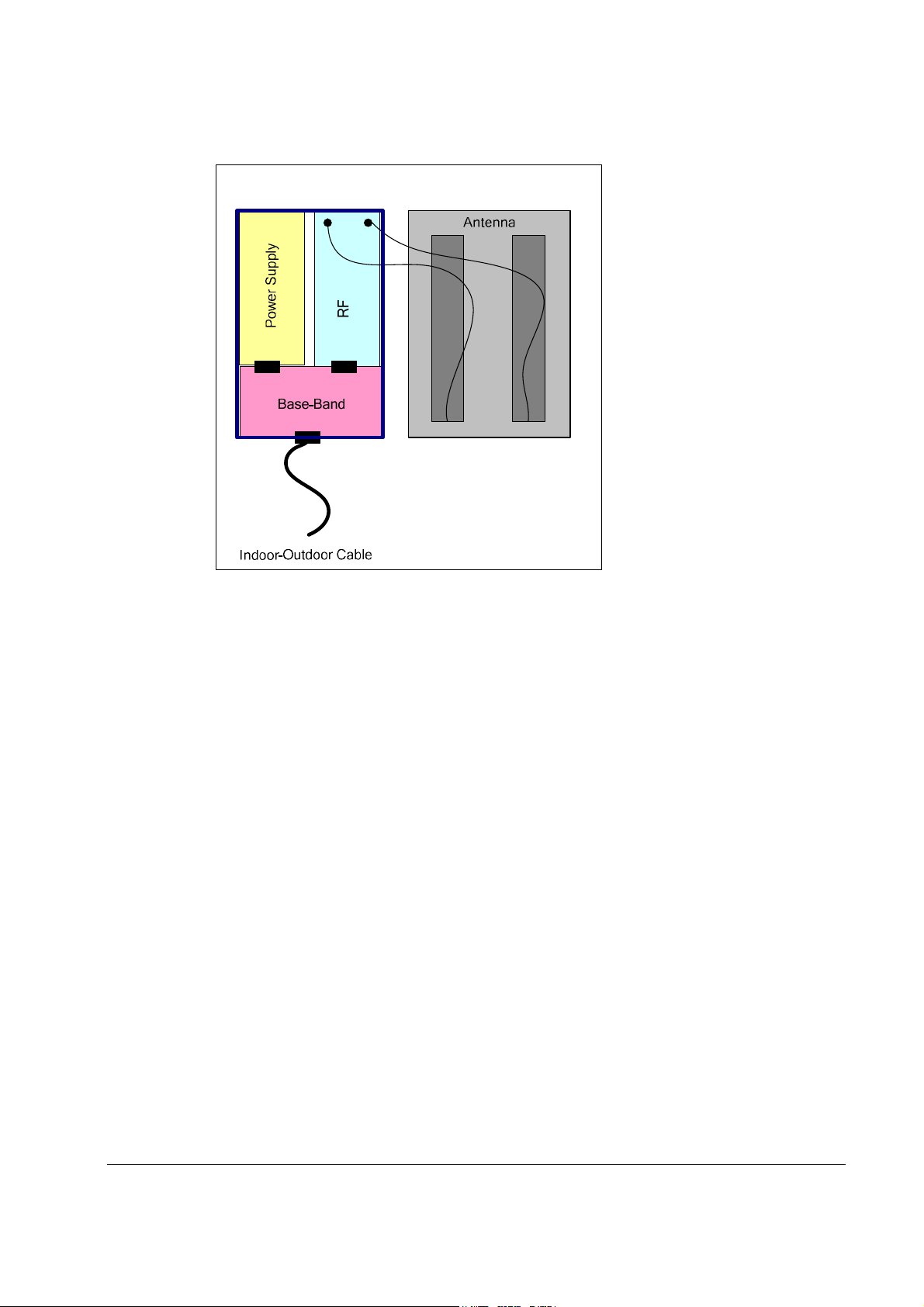
Figure 2-2: WiN5200 Block Diagram
2.4 Features
2.4.1 Mobile WiMAX Wave 2 MIMO Features
Multiple-Input, Multiple-Output (MIMO) describes systems that use more than one radio and
antenna system at each end of the wireless link. In the past it was too costly to incorporate
multiple antennas and radios in a subscriber terminal. Recent advances in radio
miniaturization and integration technology now makes it feasible and cost effective.
Combining two or more received signals has the immediate benefit of improving received
signal strength, but MIMO also enables transmission of parallel data streams or greater
throughput. For example, in a 2 x 2 MIMO (two transmit and two receive elements), dual
polarization point-to-point system, the carrier’s allocated frequency can be used twice,
effectively doubling the throughput data rate.
In point-to-multipoint systems employing MIMO, each base station antenna transmits a
different data stream and each subscriber terminal receives various components of the
transmitted signals with each of its subscriber antennas as illustrated in the figure below. By
using appropriate algorithms, the subscriber terminal is able to separate and decode the
parallel simultaneously received data streams.
WiN5200 Product Description | 12
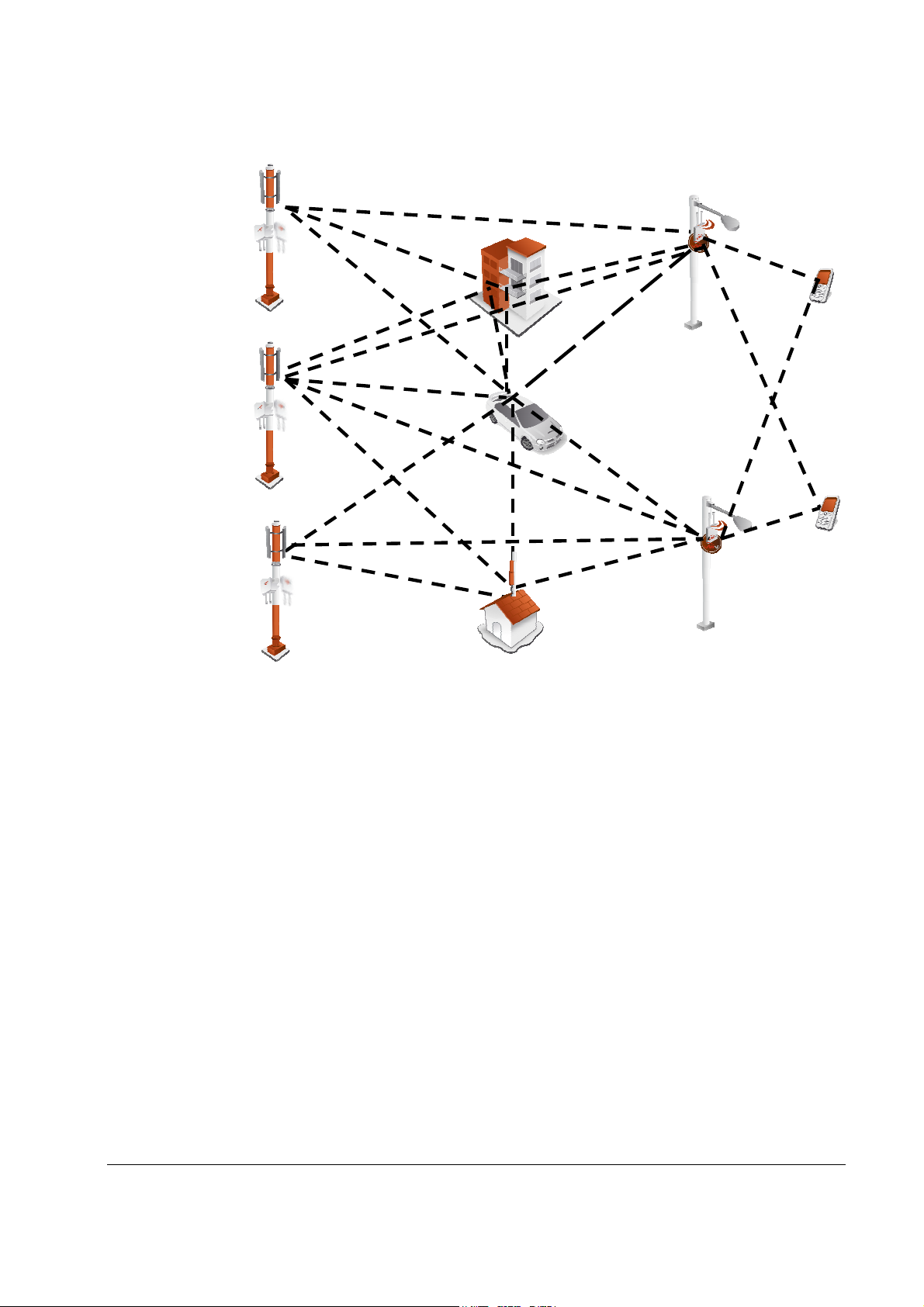
MiMo
MiMo
Figure 2-3: MiMo Antenna System
2.4.1.1 Space-Time Coding
Space-time coding (STC) is a technique for implementing transmission diversity. Mobile
WiMAX uses transmit diversity in the downlink direction to provide spatial diversity that
enhances the signal quality to a specific subscriber located anywhere within the range of the
antenna beam. Although providing less signal gain than beam-forming, transmit diversity is
more robust for mobile users since it does not require prior knowledge of the path
characteristics of a subscriber’s particular frequency channel. One such STC technique,
known as the Alamouti Code, was published in 1998[4] and has been incorporated into the
WiMAX 16e standard.
WiN5200 Product Description | 13

2.4.2 Security
Security was a key failing of older broadband wireless systems of the past. The why of it is
easy to comprehend---any network that transmits its data across wireless signals rather than
wires is inherently more open to interference, intrusion or assault. This does not mean solid
broadband wireless security is impossible, just much more difficult.
As broadband wireless networks have matured security features have improved. With the
advent of WiMAX, the security toolsets available to broadband wireless service providers
have reached all time highs of functionality. Today's WiMAX networks can be secured more
effectively than ever before.
WiMAX and IEEE 802.16 Security Sub layer provides for privacy, authentication and
confidentiality across the broadband wireless network. Defined initially by IEEE 802.16-2004
and then corrected and amended by Corrigendum 1 and IEEE 802.16e-2005 respectively, the
Security Sub layer now supports Fixed and Mobile operation.
There are two major differences between the standards. The first difference is that the security
mechanism of the IEEE 802.16-2004 is based on the DOCSIS standard. In the 802.16e-2005
many changes have been made in the security mechanisms. The second difference is in the
flexibility of SS's connection characteristics with the BST. The IEEE 802.16-2004 only supports
fixed access. In fixed access, an SS cannot mitigate to the air interface of a new Base Station
(BST) without performing the network entry again after a connection termination. The IEEE
802.16e-2005 supports mobile access. Mobile access enables an SS to move between various
BST cells while keeping the connection established.
There are five primary aspects of WiMAX security that should be considered when designing
a security plan for a WiMAX network. These range from mitigation techniques at the physical
layer to improved wireless authentication and encryption to intrusion protection and data
transport security. At each level, choices in implementation and security levels can be made;
although in the case of the physical layer options are limited.
2.4.2.1 Physical Layer Security
There are two basic types of attacks that can affect the physical layer of WiMAX. One is
jamming and the other is packet scrambling. The first is relatively straightforward, and is
sometimes the result of interference rather than an attack. Jamming consists of a stronger
signal than the WiMAX network overwhelming network data feeds either in intermittent
bursts or with sustained carrier waves.
Since most WiMAX network services are delivered over licensed bands (currently 3.5 GHz
internationally and 2.5 GHz both internationally and in the US), this offers spectrum
relatively quiet from accidental interference. Accidental interference in licensed spectrum
cannot always be completely discounted as there is a possibility of second and third harmonic
interference waves, for example, from much lower frequency signals if those are in close
proximity to the WiMAX antenna systems or that cross them with a signal close enough in
physical proximity to locally overload the WiMAX signal. In practice, this is rare.
WiN5200 Product Description | 14

Packet scrambling is an attack that occurs when control packets in the respective downlink
and uplink subframes are sniffed then scrambled and returned to the network. This attack is
much harder to mount than a jamming attack. Since most WiMAX networks today use time
division duplexing (TDD), to include the Win-Max™ system, an attacker can parse this
timing sequence and capture control data, the preamble and map, scramble them and send
them back with correct timing to interrupt legitimate signal, resulting in slowdowns and
effectively lowered bandwidth. Intercepted and scrambled packets are possible with
frequency division duplexing (FDD) as well which transmits both the uplink and downlink
simultaneously, but it is even harder to exploit this attack than with TDD systems.
While it may seem the physical layer is inherently most vulnerable as the security elements of
WiMAX are located at higher layers, the fact is hackers can often find lower hanging fruit in
terms of useful exploits higher in the stack, because as WiMAX supports multiple selections
on what service providers can choose to implement in terms of authentication, sometimes the
door can be left open for them by the choices made.
2.4.2.2 Authentication
Traditionally the first level of security authentication for older broadband wireless
technologies has been MAC authentication and WiMAX supports this, although providers
don't settle for this method. This technique allowed service providers to log permitted MAC
device addresses and allow only those addresses to access the network. Hackers long ago
figured out how to spoof these. If a base station is not set up with adequate authentication
measures, an attacker can capture control packets and pose as a legitimate subscriber even
with older MAC device authentication enabled.
A second, newer and much better choice, embraced by the Win-Max™ system, is the built in
support for X.509 device certificates embedded with the use of extensible authentication
protocol---transport layer security (EAP-TTLS) method, added with the 802.16e standard and
WiMAX Forum.
Enter the EAP-TLTS authentication method. This technique allows both the subscriber and
the base station to authenticate each other using an X.509 method for both, in addition to a
subscriber authentication which is based on well-known subscriber authentication techniques
such PAP and MS-CHAP. MAC control headers are never encrypted in WiMAX, however
with EAP carriers can choose to authenticate them (but they don't necessarily have to). This
capability adds an additional layer of authentication confirmation. It's an operator specific
guideline decision and is tunable in the Win-Max™ system.
2.4.2.3 Encryption
Clearly the first layer of defense for WiMAX operators is to authenticate a legitimate user on
its network. However, WiMAX, with its 802.16e ratification, offers top line tools for
encryption of data. Older wireless iterations used the data encryption standard (DES) which
relied on a 56-bit key for encryption. This is largely considered obsolete. WiMAX 802.16e
certainly supports DES (3DES) but it also adds support for the Advanced Encryption
WiN5200 Product Description | 15

Standard (AES) which supports, 128-bit, 192-bit or 256-bit encryption keys. Also AES meets
the Federal Information Processing Standard (FIPS) 140-2 specification, required by
numerous governmental branches. This technology, which requires dedicated processors on
board base stations, is robust and highly effective.
Traffic encryption may be employed per 802.16 Service Flow and is subject to operator policy.
The relevance of encryption to the network operator deployment is questionable. In the past,
for example, many cellular carriers focused on authentication and mostly ignored encryption.
Whether that will change as mobile service providers ramp up more broadband applications
is an open question.
The downside to these heavy computing tasks (i.e. authentication and encryption) is that all
of this requires processor cycles, which may affect the performance of the system.
Nevertheless, the Win-Max™ system and especially, the SS and BST, which are the entities
that take active role in heavy security-related computations, were built bottom to top with a
design goal of offloading heavily computing tasks from the host processor to a specific circuit.
Consequently, no performance degradation is neglected.
2.4.2.4 Third Party Intrusion Protection
We examined WiMAX authentication schemes, which are a major component of a secure
network. And we also spoke of data encryption. Clearly, WiMAX possesses solid tools
already built in. But there are considerations beyond just good security that can drive a
migration to third party intrusion detection and protection tools---namely business case
elements. Intrusion protection is however, not data protection. These are two different classes
of solution. Certainly, a good third party intrusion protection can monitor and secure a
network's authentication. However, many solutions also offer worm protection, Trojan horse
protection, defenses against viruses, backdoor exploits and denial of service attacks to name a
few. Some of these elements are almost a business necessity for a wireless service provider
and may justify the cost of an additional security suite initially. For other companies, a
migration strategy to enhanced tools makes the most cost effective sense.
A good place to start is examining market and service scenarios. If your customer base is
highly sensitive to data integrity (financial sector or hospital customers) third party intrusion
prevention systems can help segment customers from each other better as well as secure them
from outside attack.
Or in another example, a mobile network that offers just Internet access and voice may wish
to abrogate responsibility for data encryption and use session initiation protocol (SIP)
signaling for its VoIP and WiMAX native authentication tools.
Referring to encryption, clearly an AES supported data encryption system gives WiMAX
excellent security in this regard. However, additional solutions that meet customer needs
such as virtual private networks may enhance the business model and provide additional
source of revenue.
WiN5200 Product Description | 16
 Loading...
Loading...