Page 1

WatchGuard
®
Firebox® SOHO 6
Wireless
User Guide
SOHO 6 firmware version 6.2
Page 2

Using this Guide
To use this guide you need to be familiar with your computer’s
operating system. If you have questions about navigating in your
computer’s environment, please refer to your system user manual.
The following conventions are used in this guide.
Convention Indication
Bold type Menu commands, dialog box options, Web page
NOTE Important information, a helpful tip or additional
options, Web page names. For example: “On the
System Information page, select Disabled.”
instructions.
ii WatchGuard Firebox SOHO 6 Wireless
Page 3

Abbreviations used in this user guide
3DES Triple Data Encryption Standard
DES Data Encryption Standard
DNS Domain Name Service
DHCP Dynamic Host Control Protocol
DSL Digital Subscriber Line
IP Internet Protocol
IPSec Internet Protocol Security
ISDN Integrated Services Digital Network
ISP Internet Service Provider
MAC Media Access Control
MUVPN Mobile User Virtual Private Network
NAT Network Address Translation
PPP Point-to-Point Protocol
PPPoE Point-to-Point Protocol over Ethernet
TCP Transfer Control Protocol
UDP User Datagram Protocol
URL Universal Resource Locator
VPN Virtual Private Network
WAN Wide Area Network
WSEP WatchGuard Security Event Processor
User Guide iii
Page 4

Certifications and Notices
FCC Certification
This appliance has been tested and found to comply with limits for
a Class A digital appliance, pursuant to Part 15 of the FCC Rules.
Operation is subject to the following two conditions:
•This appliance may not cause harmful interference.
•This appliance must accept any interference received,
including interference that may cause undesired operation.
IMPORANT NOTICE: Changes or modifications not expressly
approved by the party responsible for compliance could void the
user's authority to operate the equipment.
This equipment has been tested and found to comply with the
limits for a Class A digital device, pursuant to Part 15 of the FCC
Rules. These limits are designed to provide reasonable protection
against harmful interference when the equipment is operated in a
commercial environment. This equipment generates, uses, and can
radiate radio frequency energy and, if not installed and used in
accordance with the instruction manual, may cause harmful
interference to radio communications. Operation of this equipment
in a residential area is likely to cause harmful interference in which
case the user will be required to correct the interference at his own
expense.
iv WatchGuard Firebox SOHO 6 Wireless
Page 5

CE Notice
The CE symbol on your WatchGuard Technologies equipment
indicates that it is in compliance with the Electromagnetic
Compatibility (EMC) directive and the Low Voltage Directive
(LVD) of the European Union (EU).
Industry Canada
This Class A digital apparatus meets all requirements of the
Canadian Interference-Causing Equipment Regulations.
Cet appareil numerique de la classe A respecte toutes les exigences
du Reglement sur le materiel broulleur du Canada.
CANADA RSS-210
The term “IC:” before the radio certification number only signifies
that Industry of Canada technical specifications were met.
Operation is subject to the following two conditions:
• This device may not cause interference.
• This device must accept any interference, including
interference that may cause undesired operation of the
device.
User Guide v
Page 6

VCCI Notice Class A ITE
vi WatchGuard Firebox SOHO 6 Wireless
Page 7

Declaration of Conformity
User Guide vii
Page 8

WATCHGUARD SOHO SOFTWARE
END-USER LICENSE AGREEMENT
WATCHGUARD SOHO SOFTWARE
END-USER LICENSE AGREEMENT
IMPORTANT - READ CAREFULLY BEFORE ACCESSING WATCHGUARD SOFTWARE
This WatchGuard SOHO Software End-User License Agreement
("EULA") is a legal agreement between you (either an individual or a single
entity) and WatchGuard Technologies, Inc. ("WATCHGUARD") for the
WATCHGUARD SOHO software product, which includes computer
software (whether installed separately on a computer workstation or on the WatchGuard hardware
product) and may include associated media, printed materials, and on-line
or electronic documentation, and any updates or modifications thereto, including those received
through the WatchGuard LiveSecurity service (or its equivalent) (the "SOFTWARE PRODUCT").
WATCHGUARD is willing
to license the SOFTWARE PRODUCT to you only on the condition that you
accept all of the terms contained in this EULA. Please read this EULA
carefully.
By installing or using the SOFTWARE PRODUCT you agree to be bound by
the terms of this EULA. If you do not agree to the terms of this EULA,
WATCHGUARD will not license the SOFTWARE PRODUCT to you, and you will
not have any rights in the SOFTWARE PRODUCT. In that case, promptly
return the SOFTWARE PRODUCT, along with proof of payment, to the
authorized dealer from whom you obtained the SOFTWARE PRODUCT for a full
refund of the price you paid.
1. Ownership and License.
The SOFTWARE PRODUCT is protected by copyright laws and international
copyright treaties, as well as other intellectual property laws and
treaties. This is a license agreement and NOT an agreement for sale.
All title and copyrights in and to the SOFTWARE PRODUCT (including but
not limited to any images, photographs, animations, video, audio, music,
text, and applets incorporated into the SOFTWARE PRODUCT), the accompanying
printed materials, and any copies of the SOFTWARE PRODUCT are owned by
WATCHGUARD or its licensors. Your rights to use the SOFTWARE PRODUCT are
as specified in this EULA, and WATCHGUARD retains all rights not expressly
granted to you in this EULA. Nothing in this EULA constitutes a waiver
of our rights under U.S. copyright law or any other law or treaty.
2. Permitted Uses.
You are granted the following rights to the SOFTWARE PRODUCT:
(A) You may use the SOFTWARE PRODUCT solely for the purpose of operating
the SOHO hardware product in accordance with the SOHO or user documentation.
viii WatchGuard Firebox SOHO 6 Wireless
Page 9

If you are accessing the SOFTWARE PRODUCT via a Web based installer program,
you are granted the following additional rights to the SOFTWARE PRODUCT:
(A) You may install and use the SOFTWARE PRODUCT on any computer with an associated
connection to the SOHO hardware product
in
accordance with the SOHO user documentation;
(B) You may install and use the SOFTWARE PRODUCT on more than one computer
at once without licensing an additional copy of the SOFTWARE PRODUCT for each
additional computer on which you want to use it, provided that each computer on which you install
the SOFTWARE PRODUCT has an associated connection to the same SOHO hardware product
; and
(C) You may make a single copy of the SOFTWARE PRODUCT for backup or
archival purposes only.
3. Prohibited Uses.
You may not, without express written permission from WATCHGUARD:
(A) Reverse engineer, disassemble or decompile the SOFTWARE PRODUCT;
(B) Use, copy, modify, merge or transfer copies of the SOFTWARE PRODUCT or
printed materials except as provided in this EULA;
(C) Use any backup or archival copy of the SOFTWARE PRODUCT (or allow someone
else to use such a copy) for any purpose other than to replace the original
copy in the event it is destroyed or becomes defective;
(D) Sublicense, lend, lease or rent the SOFTWARE PRODUCT; or
(E) Transfer this license to another party unless
(i) the transfer is permanent,
(ii) the third party recipient agrees to the terms of this EULA, and
(iii) you do not retain any copies of the SOFTWARE PRODUCT.
4. Limited Warranty.
WATCHGUARD makes the following limited warranties for a period of ninety (90)
days from the date you obtained the SOFTWARE PRODUCT from WATCHGUARD or an
authorized dealer;
(A) Media. The disks and documentation will be free from defects in materials
and workmanship under normal use. If the disks or documentation fail to
conform to this warranty, you may, as your sole and exclusive remedy,
obtain a replacement free of charge if you return the defective disk or
documentation to us with a dated proof of purchase; and
(B) SOFTWARE PRODUCT. The SOFTWARE PRODUCT will materially conform to the
documentation that accompanies it. If the SOFTWARE PRODUCT fails to
operate in accordance with this warranty, you may, as your sole and
exclusive remedy, return all of the SOFTWARE PRODUCT and the documentation
to the authorized dealer from whom you obtained it, along with a dated
proof of purchase, specifying the problems, and they will provide you
with a new version of the SOFTWARE PRODUCT or a full refund at their
User Guide ix
Page 10

election.
Disclaimer and Release.
THE WARRANTIES, OBLIGATIONS AND LIABILITIES OF WATCHGUARD, AND
YOUR REMEDIES, SET FORTH IN PARAGRAPHS 4, 4(A) AND 4(B) ABOVE
ARE EXCLUSIVE AND IN SUBSTITUTION FOR, AND YOU HEREBY WAIVE,
DISCLAIM AND RELEASE ANY AND ALL OTHER WARRANTIES, OBLIGATIONS
AND LIABILITIES OF WATCHGUARD AND ITS LICENSORS AND ALL OTHER RIGHTS,
CLAIMS AND
REMEDIES YOU MAY HAVE AGAINST WATCHGUARD AND ITS LICENSORS, EXPRESS
OR IMPLIED,
ARISING BY LAW OR OTHERWISE, WITH RESPECT TO ANY NONCONFORMANCE
OR DEFECT IN THE SOFTWARE PRODUCT (INCLUDING, BUT NOT LIMITED
TO, ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A
PARTICULAR PURPOSE, ANY IMPLIED WARRANTY ARISING FROM COURSE OF
PERFORMANCE, COURSE OF DEALING, OR USAGE OF TRADE, ANY WARRANTY
OF NONINFRINGEMENT, ANY WARRANTY THAT THIS SOFTWARE PRODUCT WILL
MEET YOUR REQUIREMENTS, ANY WARRANTY OF UNINTERRUPTED OR
ERROR-FREE OPERATION, ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR
REMEDY IN TORT, WHETHER OR NOT ARISING FROM THE NEGLIGENCE
(WHETHER ACTIVE, PASSIVE OR IMPUTED) OR FAULT OF WATCHGUARD AND
ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR REMEDY FOR LOSS OR
DAMAGE TO, OR CAUSED BY OR CONTRIBUTED TO BY, THE SOFTWARE
PRODUCT).
Limitation of Liability.
WATCHGUARD'S LIABILITY (WHETHER IN CONTRACT, TORT, OR OTHERWISE;
AND NOTWITHSTANDING ANY FAULT, NEGLIGENCE, STRICT LIABILITY OR
PRODUCT LIABILITY) WITH REGARD TO THE SOFTWARE PRODUCT WILL IN
NO EVENT EXCEED THE PURCHASE PRICE PAID BY YOU FOR SUCH PRODUCT. THIS
WILL BE TRUE EVEN IN THE EVENT OF THE FAILURE OF AN AGREED REMEDY.
IN NO EVENT WILL WATCHGUARD BE LIABLE TO YOU OR ANY THIRD PARTY,
WHETHER ARISING IN CONTRACT (INCLUDING WARRANTY), TORT
(INCLUDING ACTIVE, PASSIVE OR IMPUTED NEGLIGENCE AND STRICT
LIABILITY AND FAULT), FOR ANY INDIRECT, SPECIAL, INCIDENTAL, OR
CONSEQUENTIAL DAMAGES (INCLUDING WITHOUT LIMITATION LOSS OF
BUSINESS PROFITS, BUSINESS INTERRUPTION, OR LOSS OF BUSINESS
INFORMATION) ARISING OUT OF OR IN CONNECTION WITH THIS WARRANTY
OR THE USE OF OR INABILITY TO USE THE SOFTWARE PRODUCT, EVEN IF
WATCHGUARD HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THIS
WILL BE TRUE EVEN IN THE EVENT OF THE FAILURE OF AN AGREED REMEDY.
5. United States Government Restricted Rights.
The enclosed SOFTWARE PRODUCT and documentation are provided with
x WatchGuard Firebox SOHO 6 Wireless
Page 11

Restricted Rights. Use, duplication or disclosure by the U.S Government
or any agency or instr umentality thereof is subject to restrictions as
set forth in subdivision (c)(1)(ii) of the Rights in Technical Data and
Computer Software clause at DFARS 252.227-7013, or in subdivision (c)(1)
and (2) of the Commercial Computer Software -- Restricted Rights
Clause at 48 C.F.R. 52.227-19, as applicable. Manufacturer is WatchGuard
Technologies, Incorporated, 505 5th Ave. South, Suite 500,Seattle,
WA 98104.
6. Export Controls.
You agree not to directly or indirectly transfer the SOFTWARE PRODUCT or
documentation to any countr y to which such transfer would be prohibited
by the U.S. Export Administration Act and the regulations issued thereunder.
7. Termination.
This license and your right to use the SOFTWARE PRODUCT will automatically
terminate if you fail to comply with any provisions of this EULA, destroy
all copies of the SOFTWARE PRODUCT in your possession, or voluntarily return
the SOFTWARE PRODUCT to WATCHGUARD. Upon termination you will destroy all
copies of the SOFTWARE PRODUCT and documentation remaining in your control
or possession.
8. Miscellaneous Provisions. This EULA will be governed by and construed
in accordance with the substantive laws of Washington excluding the 1980
United National Convention on Contracts for the International Sale of Goods,
as amended. This is the entire EUL A between us relating to the contents of
this package, and supersedes any prior purchase order, communications,
advertising or representations concerning the SOFTWARE PRODUCT
AND BY USING THE SOFTWARE PRODUCT YOU AGREE TO THESE TERMS. IF THE
SOFTWARE PRODUCT IS BEING USED BY AN ENTITY, THE INDIVIDUAL INDICATING
AGREEMENT TO THESE TERMS REPRESENTS AND WARRANTS THAT (A) SUCH
INDIVIDUAL IS DULY AUTHORIZED TO ACCEPT THIS EULA ON BEHALF OF THE ENTITY
AND TO BIND THE ENTITY TO THE TERMS OF THIS EULA; (B) THE ENTITY HAS THE
FULL POWER, CORPORATE OR OTHERWISE, TO ENTER INTO THIS EULA AND PERFORM
ITS OBLIGATIONS UNDER THIS EULA AND; (C) THIS EULA AND THE PERFORMANCE OF
THE ENTITY’S OBLIGATIONS UNDER THIS EULA DO NOT VIOLATE ANY THIRD-PARTY
AGREEMENT TO WHICH THE ENTITY IS A PARTY.
No change or modification of this EULA will be valid unless it is in
writing, and is signed by WATCHGUARD.
User Guide xi
Page 12

Notice to Users
Information in this guide is subject to change without notice. Companies, names, and data used in
examples herein are fictitious unless otherwise noted. No part of this guide may be reproduced or
transmitted in any form or by any means, electronic or mechanical, for any purpose, without the
express written permission of WatchGuard Technologies, Inc.
Copyright, Trademark, and Patent Information
Copyright© 1998 - 2002 WatchGuard Technologies, Inc. All rights reserved.
AppLock®, AppLock®/Web, Designing peace of mind®, Firebox®, Firebox® 1000, Firebox®
2500, Firebox® 4500, Firebox® II, Firebox® II Plus, Firebox® II FastVPN, Firebox® III,
Firebox® SOHO, Firebox® SOHO 6, Firebox® SOHO 6tc, Firebox® SOHO|tc, Firebox® V100,
Firebox® V80, Firebox® V60, Firebox® V10, LiveSecurity®, LockSolid®, RapidStream®,
RapidCore®, ServerLock®, WatchGuard®, WatchGuard® Technologies, Inc., DVCP™
technology, Enforcer/MUVPN™, FireChip™, HackAdmin™, HostWatch™, Make Security Your
Strength™, RapidCare™, SchoolMate™, ServiceWatch™, Smart Security. Simply Done.™,
Vcontroller™, VPNforce™ are either registered trademarks or trademarks of WatchGuard
Technologies, Inc. in the United States and/or other countries.
© Hi/fn, Inc. 1993, including one or more U.S. Patents: 4701745, 5016009, 5126739, and
5146221 and other patents pending.
Microsoft®, Internet Explorer®, Windows® 95, Windows® 98, Windows NT® and Windows®
2000 are either registered trademarks or trademarks of Microsoft Corporation in the United
States and/or other countries.
Netscape and Netscape Navigator are registered trademarks of Netscape Communications
Corporation in the United States and other countries.
RC2 Symmetric Block Cipher, RC4 Symmetric Stream Cipher, RC5 Symmetric Block Cipher,
BSAFE, TIPEM, RSA Public Key Cryptosystem, MD, MD2, MD4, and MD5 are either
trademarks or registered trademarks of RSA Data Security, Inc. Certain materials herein are
Copyright © 1992-1999 RSA Data Security, Inc. All rights reserved.
RealNetworks, RealAudio, and RealVideo are either a registered trademark or trademark of
RealNetworks, Inc. in the United States and/or other countries.
Java and all Jave-based marks are trademarks or registered trademarks of Sun Microsystems,
Inc. in the United States and other countries. All right reserved.
© 1995-1998 Eric Young (eay@cryptsoft). All rights reserved.
© 1998-2000 The OpenSSL Project. All rights reserved. Redistribution and use in source and
binary forms, with or without modification, are permitted provided that the following conditions
are met:
xii WatchGuard Firebox SOHO 6 Wireless
Page 13

1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this software must display the following
acknowledgment: "This product includes software developed by the OpenSSL Project for use in the
OpenSSL Toolkit. (http://www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used to endorse or promote
products derived from this software without prior written permission. For written permission,
please contact openssl-core@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor may "OpenSSL" appear in
their names without prior written permission of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This
product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit (http:/
/www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY
EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR ITS
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com). This product includes software written by Tim
Hudson (tjh@cryptsoft.com).
© 1995-1998 Eric Young (eay@cryptsoft.com)
All rights reserved.
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com).
The implementation was written so as to conform with Netscapes SSL.
This library is free for commercial and non-commercial use as long as the following conditions are
aheared to. The following conditions apply to all code found in this distribution, be it the RC4,
RSA, lhash, DES, etc., code; not just the SSL code. The SSL documentation included with this
distribution is covered by the same copyright terms except that the holder is Tim Hudson
(tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in the code are not to be
removed. If this package is used in a product, Eric Young should be given attribution as the author
of the parts of the library used. This can be in the form of a textual message at program startup or
in documentation (online or textual) provided with the package. Redistribution and use in source
User Guide xiii
Page 14

and binary forms, with or without modification, are permitted provided that the following
conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of conditions and the
following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this software must display the following
acknowledgement: "This product includes cryptographic software written by Eric Young
(eay@cryptsof t.com)" The word 'cryptographic' can be left out if the routines from the library
being used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from the apps directory
(application code) you must include an acknowledgement: "This product includes software written
by Tim Hudson (tjh@cryptsoft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND ANY EXPRESS OR
IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR
OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The licence and distribution terms for any publicly available version or derivative of this code
cannot be changed. i.e. this code cannot simply be copied and put under another distribution
licence [including the GNU Public Licence.]
The mod_ssl package falls under the Open-Source Software label because it's distributed under a
BSD-style license. The detailed license information follows.
Copyright (c) 1998-2001 Ralf S. Engelschall. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. All advertising materials mentioning features or use of this software must display the following
acknowledgment:
"This product includes software developed by Ralf S. Engelschall <rse@engelschall.com> for use
in the mod_ssl project (http://www.modssl.org/)."
xiv WatchGuard Firebox SOHO 6 Wireless
Page 15

4. The names "mod_ssl" must not be used to endorse or promote products derived from this
software without prior written permission. For written permission, please contact
rse@engelschall.com.
5. Products derived from this software may not be called "mod_ssl" nor may "mod_ssl" appear in
their names without prior written permission of Ralf S. Engelschall.
6. Redistributions of any form whatsoever must retain the following acknowledgment: "This
product includes software developed by Ralf S. Engelschall <rse@engelschall.com> for use in the
mod_ssl project (http://www.modssl.org/)."
THIS SOFTWARE IS PROVIDED BY RALF S. ENGELSCHALL ``AS IS'' AND ANY
EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL RALF S. ENGELSCHALL OR HIS
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO,
PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The Apache Software License, Version 1.1
Copyright (c) 2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3. The end-user documentation included with the redistribution, if any, must include the following
acknowledgment:
"This product includes software developed by the Apache Software Foundation (http://
www.apache.org/)." Alternately, this acknowledgment may appear in the software itself, if and
wherever such third-party acknowledgments normally appear.
4. The names "Apache" and "Apache Software Foundation" must not be used to endorse or promote
products derived from this software without prior written permission. For written permission,
please contact apache@apache.org.
User Guide xv
Page 16

5. Products derived from this software may not be called "Apache", nor may "Apache" appear in
their name, without prior written permission of the Apache Software Foundation.
THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED.
IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION OR ITS CONTRIBUTORS BE
LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the
Apache Software Foundation. For more information on the Apache Software Foundation, please
see <http://www.apache.org/>.
Portions of this software are based upon public domain software originally written at the National
Center for Supercomputing Applications, University of Illinois, Urbana-Champaign.
All other trademarks or trade names mentioned herein, if any, are the property of their respective
owners.
Limited Hardware Warranty
This Limited Hardware Warranty (the “Warranty”) applies to the enclosed WatchGuard hardware
product (the “Product”), not including any associated software which is licensed pursuant to a
separate end-user license agreement and warranty. BY USING THE PRODUCT, YOU AGREE TO
THE TERMS HEREOF. If you do not agree to these terms, please return this package, along with
proof of purchase, to the authorized dealer from which you purchased it for a full refund.
WatchGuard Technologies, Inc. (”WatchGuard”) and you agree as follows:
1. Limited Warranty. WatchGuard warrants that upon delivery and for one (1) year thereafter (the
“Warranty Period”): (a) the Product will be free from material defects in materials and
workmanship, and (b) the Product, when properly installed and used for its intended purpose and
in its intended operating environment, will perform substantially in accordance with WatchGuard
applicable specifications.
This warranty does not apply to any Product that has been: (i) altered, repaired or modified by any
party other than WatchGuard; or (ii) damaged or destroyed by accidents, power spikes or similar
events or by any intentional, reckless or negligent acts or omissions of any party. You may have
additional warranties with respect to the Product from the manufacturers of Product components.
However, you agree not to look to WatchGuard for, and hereby release WatchGuard from any
xvi WatchGuard Firebox SOHO 6 Wireless
Page 17

liability for, performance of, enforcement of, or damages or other relief on account of, any such
warranties or any breach thereof.
2. Remedies. If any Product does not comply with the WatchGuard warranties set forth in Section
1 above, WatchGuard will, at its option, either (a) repair the Product, or (b) replace the Product;
provided, that you will be responsible for returning the Product to the place of purchase and for all
costs of shipping and handling. Repair or replacement of the Product shall not extend the
Warranty Period. Any Product, component, part or other item replaced by WatchGuard becomes
the property of WatchGuard . WatchGuard shall not be responsible for return of or damage to any
software, firmware, information or data contained in, stored on, or integrated with any returned
Products.
3. Disclaimer and Release. THE WARRANTIES, OBLIGATIONS AND LIABILITIES OF
WATCHGUARD, AND YOUR REMEDIES, SET FORTH IN PARAGRAPHS 1 AND 2 ABOVE
ARE EXCLUSIVE AND IN SUBSTITUTION FOR, AND YOU HEREBY WAIVE, DISCLAIM
AND RELEASE ANY AND ALL OTHER WARRANTIES, OBLIGATIONS AND LIABILITIES OF
WATCHGUARD AND ALL OTHER RIGHTS, CLAIMS AND REMEDIES YOU MAY HAVE
AGAINST WATCHGUARD, EXPRESS OR IMPLIED, ARISING BY LAW OR OTHERWISE,
WITH RESPECT TO ANY NONCONFORMANCE OR DEFECT IN THE PRODUCT
(INCLUDING, BUT NOT LIMITED TO, ANY IMPLIED WARRANTY OF MERCHANTABILITY
OR FITNESS FOR A PARTICULAR PURPOSE, ANY IMPLIED WARRANTY ARISING FROM
COURSE OF PERFORMANCE, COURSE OF DEALING, OR USAGE OF TRADE, ANY
WARRANTY OF NONINFRINGEMENT, ANY WARRANTY OF UNINTERRUPTED OR ERRORFREE OPERATION, ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR REMEDY IN TORT,
WHETHER OR NOT ARISING FROM THE NEGLIGENCE (WHETHER ACTIVE, PASSIVE OR
IMPUTED) OR FAULT OF WATCHGUARD OR FROM PRODUCT LIABILITY, STRICT
LIABILITY OR OTHER THEORY, AND ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR
REMEDY FOR LOSS OR DAMAGE TO, OR CAUSED BY OR CONTRIBUTED TO BY,THE
PRODUCT).
4. Limitation of Liability. WATCHGUARD TECHNOLOGIES’ LIABILITY (WHETHER ARISING
IN CONTRACT (INCLUDING WARRANTY), TORT (INCLUDING ACTIVE, PASSIVE OR
IMPUTED NEGLIGENCE AND STRICT LIABILITY AND FAULT) OR OTHER THEORY) WITH
REGARD TO ANY PRODUCT WILL IN NO EVENT EXCEED THE PURCHASE PRICE PAID
BY YOU FOR SUCH PRODUCT. THIS SHALL BE TRUE EVEN IN THE EVENT OF THE
FAILURE OF ANY AGREED REMEDY. IN NO EVENT WILL WATCHGUARD
TECHNOLOGIES BE LIABLE TO YOU OR ANY THIRD PARTY (WHETHER ARISING IN
CONTRACT (INCLUDING WARRANTY), TORT (INCLUDING ACTIVE, PASSIVE OR
IMPUTED NEGLIGENCE AND STRICT LIABILITY AND FAULT) OR OTHER THEORY) FOR
COST OF COVER OR FOR ANY INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL
DAMAGES (INCLUDING WITHOUT LIMITATION LOSS OF PROFITS, BUSINESS, OR DATA)
ARISING OUT OF OR IN CONNECTION WITH THIS WARRANTY OR THE USE OF OR
INABILITY TO USE THE PRODUCT, EVEN IF WATCHGUARD TECHNOLOGIES HAS BEEN
User Guide xvii
Page 18

ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THIS SHALL BE TRUE EVEN IN
THE EVENT OF THE FAILURE OF ANY AGREED REMEDY.
5. Miscellaneous Provisions. This Warranty will be governed by the laws of the state of
Washington, U.S.A., without reference to its choice of law rules. The provisions of the 1980
United Nations Convention on Contracts for the International Sales of Goods, as amended, shall
not apply. You agree not to directly or indirectly transfer the Product or associated documentation
to any country to which such transfer would be prohibited by the U.S. Export laws and regulations.
If any provision of this Warranty is found to be invalid or unenforceable, then the remainder shall
have full force and effect and the invalid provision shall be modified or partially enforced to the
maximum extent permitted by law to effectuate the purpose of this Warranty. This is the entire
agreement between WatchGuard and you relating to the Product, and supersedes any prior
purchase order, communications, advertising or representations concerning the Product AND BY
USING THE PRODUCT YOU AGREE TO THESE TERMS. No change or modification of this
Agreement will be valid unless it is in writing, and is signed by WatchGuard.
Software Version Number: 6.2
Part No 1230-000
xviii WatchGuard Firebox SOHO 6 Wireless
Page 19

Contents
CHAPTER 1 Introduction ..................................................1
Package contents ......................................................2
How does a firewall work? ........................................2
How does information travel on the Internet? ..........4
How does the SOHO 6 Wireless process
information? ..........................................................5
How Does Wireless Networking Work? ....................5
SOHO 6 Wireless hardware description ...................6
CHAPTER 2 Installation ..................................................13
Before you Begin the Installation ............................14
Physically Connect to the SOHO 6 Wireless ...........21
Setting up the Wireless Network ............................26
Setting up the Wireless Access Point ......................27
Configuring the Wireless Card on your computer ..27
User Guide xvii
Page 20

CHAPTER 3 SOHO 6 Wireless basics ...........................29
SOHO 6 Wireless System Status page ...................29
Factory default settings ...........................................31
Register your SOHO 6 Wireless and activate the
LiveSecurity Service ............................................ 33
Reboot the SOHO 6 Wireless ................................. 34
CHAPTER 4 Configure the Network Interfaces ...........37
External Network Configuration .............................37
Configure the Trusted Network ..............................42
Configure the Optional Network for Wireless
Networking .........................................................46
Configure the Wireless Network .............................49
Configure static routes ............................................ 54
View network statistics ............................................55
Configure the dynamic DNS Service ....................... 56
CHAPTER 5 Administrative options ..............................59
The System Security page ......................................59
Set up VPN manager access ................................... 63
Update the firmware ...............................................65
Activate the SOHO 6 Wireless upgrade options .... 66
View the configuration file ...................................... 69
CHAPTER 6 Configure the Firewall Settings ................71
Firewall settings ......................................................71
Configure incoming and outgoing services ............71
Block external sites .................................................75
Firewall options ....................................................... 77
xviii WatchGuard Firebox SOHO 6 Wireless
Page 21

Enable override MAC address for the external
network ...............................................................82
Create an Unrestricted Pass Through .....................82
CHAPTER 7 Configure logging .....................................85
View SOHO 6 Wireless log messages ....................86
Set up logging to a WatchGuard Security Event
Processor log host ..............................................87
Set up logging to a Syslog host ..............................88
Set the system time .................................................90
CHAPTER 8 SOHO 6 Wireless WebBlocker .................93
How WebBlocker works ..........................................93
Purchase and activate SOHO 6 Wireless
WebBlocker ........................................................95
Configure the SOHO 6 Wireless WebBlocker .........95
WebBlocker Categories ........................................101
CHAPTER 9 VPN—Virtual Private Networking ..........105
What You Need .....................................................106
Step-by-step instructions to configure a SOHO 6
Wireless VPN tunnel ......................................... 109
Frequently Asked Questions .................................110
Set Up multiple SOHO-SOHO VPN tunnels .........111
Configure split tunneling ...................................... 116
MUVPN Clients .....................................................117
View the VPN Statistics ......................................... 118
User Guide xix
Page 22

CHAPTER 10 MUVPN Clients ........................................119
Configure the SOHO 6 Wireless for
MUVPN Clients .................................................120
Prepare the Remote Computers for the MUVPN
Client ................................................................123
Install and Configure the MUVPN Client ..............137
Connect and Disconnect the MUVPN Client ........147
Monitor the MUVPN Client Connection ...............151
The ZoneAlarm Personal Firewall ..........................153
Use the MUVPN Client to Enforce your Corporate
Policy ................................................................157
Troubleshooting Tips ............................................167
CHAPTER 11 Support resources ...................................171
Troubleshooting tips ............................................. 171
Contact technical support ..................................... 180
Online documentation and FAQs .........................180
Special notices ......................................................180
Index ................................................................. 181
xx WatchGuard Firebox SOHO 6 Wireless
Page 23

CHAPTER 1 Introduction
This manual shows how to use your WatchGuard® Firebox®
SOHO 6 Wireless or SOHO 6tc Wireless security appliance for
secure access to the Internet.
User Guide 1
Page 24

The only difference between these two appliances is the VPN
feature. VPN is available as an upgrade option for the SOHO 6
Wireless. The SOHO 6tc Wireless includes the VPN upgrade
option.
The SOHO 6 Wireless provides security and wireless networking
when your computer is connected to the Internet with a highspeed cable modem, DSL modem, leased line, or ISDN.
The newest installation and user information is available from the
WatchGuard Web site:
http://support.watchguard.com/sohoresources/
Package contents
Make sure that the package contains all of these items:
• SOHO 6 Wireless QuickStart Guide
• Wireless User Guide
• LiveSecurity Service
• Hardware Warranty card
• AC adapter (12 V, 1.2 A)
®
activation card
• Straight-through Ethernet cable
• SOHO 6 Wireless security appliance
• Two 5dBi detachable antennae
How does a firewall work?
The Internet connects your network to resources. Some examples
of resources are the World Wide Web, email and video/audio
2 WatchGuard Firebox SOHO 6 Wireless
Page 25
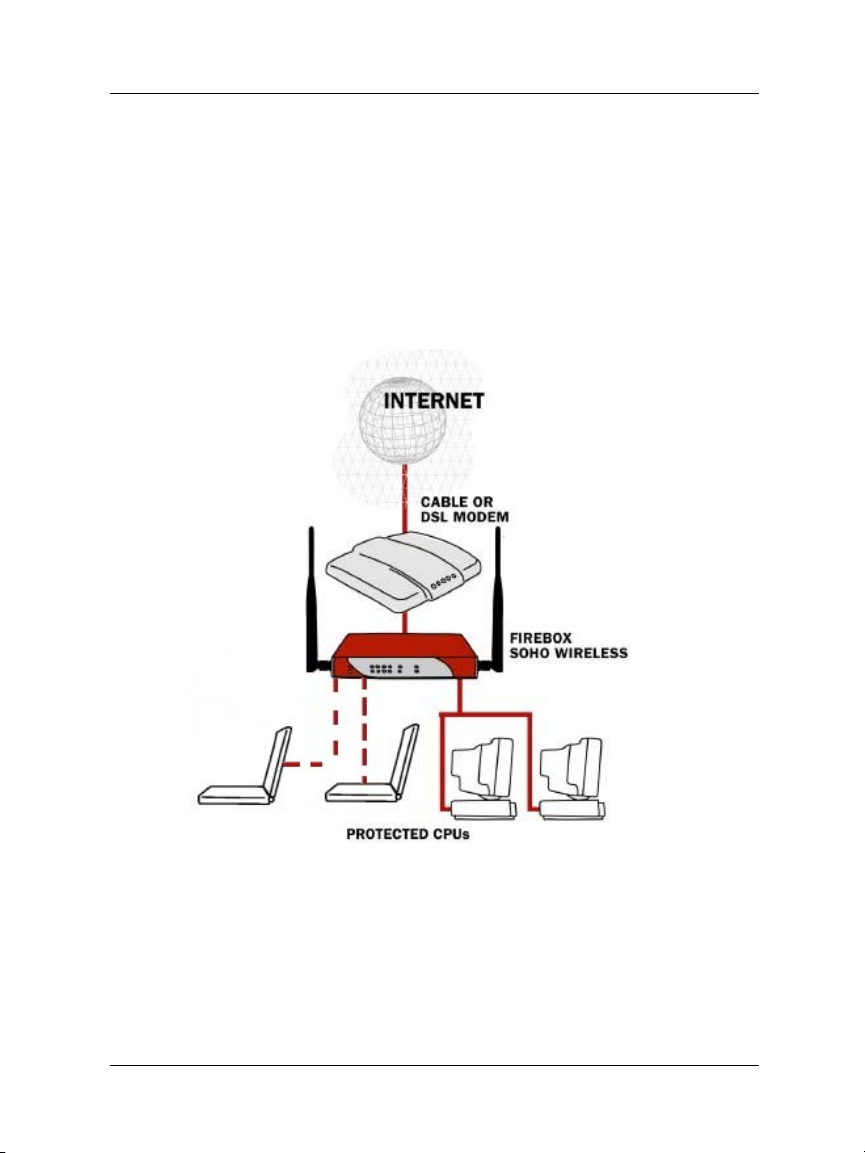
How does a firewall work?
conferencing. A connection to the Internet is dangerous to the
privacy and the security of your network. A firewall divides your
internal network from the Internet to reduce this danger. The
appliances on the trusted side of your SOHO 6 Wireless firewall
are protected. The illustration below shows how the SOHO 6
Wireless physically divides your trusted network from the
Internet.
The SOHO 6 Wireless controls all traffic between the external
network (the Internet) and the trusted network (your computers).
All suspicious traffic is stopped. The rules and policies that
identify the suspicious traffic are shown in “Configure incoming
and outgoing services” on page 71.
User Guide 3
Page 26

How does information travel on the Internet?
The data that is sent through the Internet is divided into packets.
To make sure that the packets are received at the destination,
information is added to the packets. The protocols for these tasks
are called TCP and IP. TCP disassembles and reassembles the data,
for example an email message or a program file. IP adds
information to the packets, which includes the destination and the
handling requirements.
IP addresses
An IP address identifies a computer on the Internet that sends and
receives packets. Each computer on the Internet has an address.
The SOHO 6 Wireless is also a computer and has an IP address.
When you configure a service behind a firewall, you must include
the trusted network IP address for the computer that supplies the
service.
A URL (Uniform Resource Locator) identifies each IP address on
the Internet. An example of a URL is:
http://www.watchguard.com/.
Protocols
A protocol defines how a packet is assembled and transmitted
through a network. The most frequently used protocols are TCP
and UDP (User Datagram Protocol). There are other IP protocols
that are less frequently used.
Port numbers
During the communication between computers, port numbers
identify which programs or applications are connected.
4 WatchGuard Firebox SOHO 6 Wireless
Page 27

How does the SOHO 6 Wireless process information?
How does the SOHO 6 Wireless process
information?
Services
A service is the group of protocols and port numbers for a
specified program or type of application. The standard
configuration of the SOHO 6 Wireless contains the correct settings
for many standard services.
Network Address Translation
All connections from the trusted network to the external network
through a SOHO 6 Wireless use dynamic NAT. Dynamic NAT
prevents that private IP addresses from your trusted network are
sent through the Internet.
The SOHO 6 Wireless replaces the private IP addresses with the
public IP address to protect the trusted network. Each packet sent
through the Internet contains IP address information. Packets sent
through the SOHO 6 Wireless with Dynamic NAT include only the
public IP address of the SOHO 6 Wireless and not the private IP
address of the computer in the trusted network. Because only the
IP address of the SOHO 6 Wireless is sent to the external network,
unauthorized access by the computers in the public network to the
computers in the trusted network is prevented.
How Does Wireless Networking Work?
Wireless networking creates a network by transmitting and
receiving data as radio-frequency signals between your computers
and the SOHO 6 Wireless using the 802.11b standard defined by
User Guide 5
Page 28
the Institute of Electrical and Electronics Engineers (IEEE) and is
part of a series of wireless standards.
Unless adequately protected, a wireless network is susceptible to
access from the outside by unauthorized users to compromise your
machine or simply to access a free Internet connection.
Increase your corporate network security by forcing users to
authenticate with a Mobile User VPN client, creating a secure
IPSec tunnel from the wireless computer to the SOHO 6 Wireless.
Separation of the trusted network from the optional network
further protects the connection from the wireless computer to the
SOHO 6 Wireless. For information on how to configure this, see
Chapter 11 “MUVPN Clients” on page 119.
SOHO 6 Wireless hardware description
The hardware of the SOHO 6 Wireless uses newer technology than
earlier SOHO models.
Faster Processor
The SOHO 6 Wireless has a new network processor that
runs at a speed of 150 MHz. Ethernet and encryption
technology are included.
Ethernet ports
The SOHO 6 Wireless has five 10/100 Base TX ports. The
Ethernet ports have the labels 0 through 3 and WAN.
6 WatchGuard Firebox SOHO 6 Wireless
Page 29

SOHO 6 Wireless hardware description
Wireless
Wireless operating range--indoors (these values are
approximations):
100 feet at 11 Mbps
165 feet at 5.5 Mbps
230 feet at 2 Mbps
300 feet at 1 Mbps
Understanding IEEE 802.11b Wireless Communication
In general, transmitted RF power and signal bandwidth place an
upper limit on the rate that data can be transmitted over a wireless
link. The basic equation to determines the maximum data rate is:
Channel Capacity =
Channel Bandwidth x Log2(1 + Signal Strength/Noise Level
This equation says the maximum amount of data (bits/s) that can
be transmitted over a given channel depends on:
• The Channel Bandwidth: (22Mbits/s) for 802.11b
• The Signal Strength: (15dBm transmitted) for Soho6 Wireless
• The Noise Level: Depends on the channel environment and
the receiver design.
Data rate cannot exceed channel capacity. Channel capacity
depends on signal strength, noise, and transmitted power.
User Guide 7
Page 30

Noise Level (watts)
The more in-band RF noise there is the less data can be
transmitted over a given channel (wireless link). The noise
level is primarily due to three factors:
First, there is a minimum level of background noise due to
the ambient temperature of the channel (atmosphere) and
the bandwidth.
Second, the 802.11b receiver will have an innate noise level
due to its own components operating temperature.
Third, there are many unlicensed transmitters using the
same frequency bands as 802.11. Some of these are:
- Cordless phones,
- Other 802.11b devices operating on adjacent channels.
Note that only channels 1, 6, and11 are unique. All other
channels overlap because while the center frequencies
increment by 5MHz per channel, the bandwidths are
22MHz.
-Microwave ovens,
- Sodium type lighting systems (fusion lamps),
- Arc welders (broadband spark gap transmitters)
- Blue-Tooth transmitters. Note that a Blue-Tooth
transmitter operates at lower power levels and would
need to be near an 802.11b receiver to interfere with it.
- Industrial, Scientific, and Medical equipment can also use
these bands.
Signal Strength (watts)
The signal strength depends primarily on:
- How much RF signal power is transmitted
8 WatchGuard Firebox SOHO 6 Wireless
Page 31

SOHO 6 Wireless hardware description
- How much directional antenna gain there is at the
transmitter and receiver
- The signal attenuation (path-loss) between the transmitter
and receiver.
Path Loss:
The path-loss is directly proportional to line-of-site
distance between transmitter and receiver, and inversely
proportional to the wavelength of the transmitted signal.
The equation for Signal Loss is:
Loss = 20xLog10(4xpi x(Distance/Wavelength)).
- Wavelength = (speed-of-light/ frequency). This means
that the higher the frequency the shorter the wavelength
and the greater the path-loss will be for a given frequency.
- For an average office environment, a rule-of-thumb is that
line-of-sight signal loss will only pertain to about the first
20 feet and will then increase by about 30 dB per 100 feet,
due the effect of walls, and cubicles and widows, etc.
Second, the signals can arrive by different paths depending
on how many surfaces reflect the signal. This is called
multi-path. Many surfaces will reflect a signal at 2.4 GHz.
The problem is that some combinations of reflected signals
will result in cancellation at a given point, thus by moving a
receiver by as little as ½ wavelength, the signal could vary
by as much as 30dB. The effect is called fading due to
multi-path reflections.
The signal fading effect is highly dependent on antenna
position, so the SOHO 6 Wireless uses antenna receiver
diversity (2 antennas spaced more than ½ wavelength
apart) to reduce the effect of multi-path fading. On the
SOHO 6 Wireless the antenna receiving the stronger signal
is selected automatically.
User Guide 9
Page 32

NOTE
Laptop computers typically have one antenna, which is more susceptible
to signal fading depending on position. This can lead to a situation where
the SOHO 6 Wireless hears the laptop’s signal, but the laptop doesn’t
hear the access point.
Antenna Directional Gain:
Antenna Gain is the result of how directional the radiation
(transmit/receive signal strength) pattern is. The higher the
gain, then the more directional the antenna is.
The SOHO 6 Wireless ships with 5dBi antennas. This
means they have a maximum 5 dBi gain pattern
perpendicular to the antenna position. A laptop computer
antenna gain will vary but might be as low as -10dBi for
embedded wireless antennas.
Transmitted Power:
SOHO 6 Wireless transmits at 15dBm (0.032 watts), which
is compatible with US and European and other
requirements. In the USA 802.11b devices may transmit at
up to (1 watt) and up to (0.1 watt) in Europe. Allocated
channels vary for USA and Europe.
Signal strength is a function, both of how much power was
transmitted, and how much power was received. This is impacted
by the antenna gain at the transmitter and receiver as well as the
distance and the environment in between them. Due principally to
the effect of cluttered environment, signal loss increases faster in
an office building than it would for line-of-sight transmission.
Channel Bandwidth:
This varies with the type of modulation scheme. 802.11b devices
use CCK (11 Mbps, 5.5 Mbps), DQPSK (2 Mbps), and DBPSK
10 WatchGuard Firebox SOHO 6 Wireless
Page 33

SOHO 6 Wireless hardware description
(1Mbps). The factor that determines which modulation scheme is
used is the Packet Error Rate (PER). The modulation scheme
switches automatically to maintain the PER at or below 8% by
using slower data rates (different modulation schemes) as
necessary.
SOHO 6 Wireless front and rear views
There are 14 indicator lights on the front panel of the SOHO 6
Wireless. The illustration below shows the front view.
PWR
PWR is lit while the SOHO 6 Wireless is connected to a
power supply.
Status
Status is lit while a management connection is in use.
Link
Link indicators are lit while there is an active physical
connection to the related Ethernet port. A link indicator
flashes when data flows through the Ethernet port.
100
The 100 indicator is lit when a port is in use at 100 Mb. The
100 indicator is not lit when a port is in use at 10 Mb.
User Guide 11
Page 34

WAN
WAN is lit while there is an active physical connection to
the WAN port. The indicator flashes when data flows
through the port.
Mode
Mode is lit while there is a connection to the Internet.
There are five Ethernet ports, a reset button, and a power input on
the rear of the SOHO 6 Wireless. The illustration below shows the
rear view.
RESET button
Push the reset button to reset to the SOHO 6 Wireless to the
factory default configuration. See “Reset the SOHO 6
Wireless to the factory default settings” on page 32 for
more information about this procedure.
WAN port
The WAN port is for the external interface.
Four numbered ports (0-3)
These Ethernet ports are for the trusted network
connections.
Power input
Connect the power input to a power supply using the 12
volt 1.2a AC adapter supplied with the SOHO 6 Wireless.
12 WatchGuard Firebox SOHO 6 Wireless
Page 35

CHAPTER 2 Installation
The SOHO 6 Wireless protects computers that are connected to it
by Ethernet cable or wireless connection. Follow the procedures in
this chapter to install the SOHO 6 Wireless and set up the wireless
network.
Because WatchGuard is concerned about the security of your
network, the wireless feature is turned off on the SOHO 6 Wireless
we ship you. This allows you to enable the wireless network after
you set up the desired security.
To install the SOHO 6 Wireless, you complete the following steps:
• Identify and record your TCP/IP settings.
• Disable the HTTP proxy setting of your Web browser.
•Enable your computer for DHCP.
• Make the physical connections between the SOHO 6
Wireless and your network.
User Guide 13
Page 36

To set up the wireless network, you complete the following steps:
• Set up the Wireless Network
• Set up the Wireless Access Point
• Configure the Wireless Card on your computer
See the SOHO 6 Wireless QuickStart Guide included with the
SOHO 6 Wireless for a summary of this information.
Before you Begin the Installation
Before you install the SOHO 6, Wireless, make sure you have:
• DSL/cable modem
• Firebox SOHO 6 Wireless with Ethernet cables and power
supply
• Computer connected by Ethernet cable to the Firebox SOHO
6 Wireless
• Computer with wireless card (for Wireless)
You also need to follow these steps:
1 Make sure there are a 10/100BaseT Ethernet card or an 802.11b
wireless networking card installed in your computer.
2 Make sure you have a functional Internet connection. If the
Internet connection is not functional, call your ISP. The Internet
connection must be a cable modem or DSL modem with a 10/
100BaseT port, an ISDN router, or a direct LAN connection.
3 Make sure there are two straight-through Ethernet network
cables with RJ-45 connectors available. Crossover cables, which
are often red or orange in color, are not satisfactory. The
SOHO 6 Wireless package includes one cable. Make sure that
the cables are of sufficient length to connect the modem or
14 WatchGuard Firebox SOHO 6 Wireless
Page 37

Before you Begin the Installation
router to the SOHO 6 Wireless and the SOHO 6 Wireless to
your computer.
4 Attach the two antennae supplied with the SOHO 6 Wireless.
NOTE
The SOHO 6 Wireless
of at least 20 centimeters from all persons and must not be collocated or
operating in conjunction with any other antenna or transmitter.
must
be installed to provide a separation distance
5 Call your ISP to determine the method of network address
assignment. The possible methods are static addressing, DHCP,
or PPPoE. This information is necessary during the installation
procedure. See “External Network Configuration” on page 37
for more information.
6 Make sure that the Web browser program installed on your
computer is Netscape Navigator (version 4.77 or higher) or
Internet Explorer (version 5.0 or higher).
7 Record the SOHO 6 Wireless serial number. The serial number
is found on the bottom of the appliance.
Examine and record the current TCP/IP settings
Examine the current TCP/IP settings of your computer, and record
the settings in the table below. Follow the instructions for the
operating system that is installed on your computer.
Microsoft Windows 2000 and Windows XP
1Click Start => Programs => Accessories => Command Prompt.
2 At the prompt, type
ipconfig /all, then press Enter.
3 Record the TCP/IP settings in the table provided.
4Click Cancel.
User Guide 15
Page 38

Microsoft Windows NT
1Click Start => Programs => Command Prompt.
2 At the default prompt, type
ipconfig /all, then press Enter.
3 Record the TCP/IP settings in the table provided.
4Click Cancel.
Microsoft Windows 95 or 98 or ME
1Click Start => Run.
2Type:
winipcfg.
3Click OK.
4 Select the “Ethernet Adapter”.
5 Record the TCP/IP settings in the table provided.
6Click Cancel.
Macintosh
1Click the Apple m e n u => Control Panels => TCP/IP.
2 Record the TCP/IP settings in the table provided.
3Close the window.
Other operating systems (Unix, Linux)
1 Consult your operating system guide to locate the TCP/IP
screen.
2 Record the TCP/IP settings in the chart provided.
3 Exit the TCP/IP configuration screen.
16 WatchGuard Firebox SOHO 6 Wireless
Page 39

Before you Begin the Installation
TCP/IP Setting Value
IP Address
Subnet Mask
Default Gateway
DHCP Enabled Yes No
DNS Server(s) Primar y
Secondary
. . .
. . .
. . .
. . .
. . .
NOTE
If you must connect more than one computer to the trusted network
behind the SOHO 6 Wireless, determine the TCP/IP settings for each
computer.
Enable your computer for DHCP
To open the configuration pages for the SOHO 6 Wireless,
configure your computer to receive its IP address through DHCP.
See “Network addressing” on page 37 for more information about
network addressing and DHCP.
NOTE
These configuration instructions are for the Windows 2000® operating
system.
1Click Start => Settings => Control Panel.
The control panel window opens.
User Guide 17
Page 40

2 Double-click the Network & Dial-up Connections icon.
3 Double-click the connection you use to connect to the Internet.
The network connection dialog box opens.
4Click Properties.
The network connection properties dialog box opens.
18 WatchGuard Firebox SOHO 6 Wireless
Page 41

Before you Begin the Installation
5 Double-click the Internet Protocol (TCP/IP) component.
The Internet Protocol (TCP/IP) Properties dialog box opens.
6 Click to select the obtain an IP address automatically
checkbox.
7 Click to select the Obtain DNS server address automatically
checkbox.
8Click OK to close the Internet Protocol (TCP/IP) Properties
dialog box.
9Click OK again to close the Network Connection Properties
dialog box.
Disable the HTTP proxy setting of your Web browser
To configure a SOHO 6 Wireless, you must access the
configuration pages in the SOHO 6 Wireless with your browser. If
User Guide 19
Page 42

the HTTP proxy setting in your browser is enabled, you can not
open these pages to complete the configuration procedure.
If the HTTP proxy setting is enabled, the browser only sees Web
pages found on the Internet, and not pages in other locations. If the
HTTP proxy setting is disabled, you can open the configuration
pages in the SOHO 6 Wireless and Web pages on the Internet.
The instructions below show how to disable the HTTP proxy
setting in three browser applications. If a different browser is used,
use the help menus of the browser program to find the necessary
information.
Netscape 4.7
1 Open Netscape.
2Click Edit => Preferences.
The Preferences window opens.
3 A list of options is shown at the left side of the window. Click
the + symbol to the left of the Advanced option to expand the
list.
4Click Proxies.
5 Make sure the Direct Connection to the Internet option is
selected.
6Click OK to save the settings.
Netscape 6.x
1 Open Netscape.
2Click Edit => Preferences.
The Preferences window opens.
3 A list of options is shown at the left side of the window. Click
the arrow symbol to the left of the Advanced heading to
expand the list.
20 WatchGuard Firebox SOHO 6 Wireless
Page 43

Physically Connect to the SOHO 6 Wireless
4Click Proxies.
5 Make sure the Direct Connection to the Internet option is
selected.
6Click OK to save the settings.
Internet Explorer 5.0, 5.5, and 6.0
1 Open Internet Explorer.
2Click Tools => Internet Options.
The Internet Options window opens.
3Click the Advanced tab.
4 Scroll down the page to HTTP 1.1 Settings.
5 Disable all of the check boxes.
6Click OK to save the settings.
Physically Connect to the SOHO 6 Wireless
The SOHO 6 Wireless protects computers that are connected to it
by Ethernet cable or wireless connection. This section discusses
how to connect computers to the SOHO 6 Wireless by using
Ethernet cables.
The SOHO 6 Wireless protects one computer or a multi-computer
network and can also function as a hub to connect other
computers.
If you want to set up a wireless network, you still need to connect a
computer to the SOHO 6 using an Ethernet cable. You use this
connection to turn on the wireless network. For more information
on setting up a wireless network, see Figure , “Setting up the
Wireless Network,” on page 26.
User Guide 21
Page 44

Cabling the SOHO 6 Wireless for one to four
appliances
A maximum of four computers, printers, scanners, or other
network peripherals can connect directly to the SOHO 6 Wireless.
These connections use the four trusted network ports (0-3). To
connect a maximum of four appliances, use the SOHO 6 Wireless
as a network hub.
1 Shut down your computer.
2 If you connect to the Internet through a DSL modem or cable
modem, disconnect the power supply to this device.
22 WatchGuard Firebox SOHO 6 Wireless
Page 45

Physically Connect to the SOHO 6 Wireless
3 Disconnect the Ethernet cable that connects your DSL modem,
cable modem or other Internet connection to your computer.
Connect this cable to the WAN port on the SOHO 6 Wireless.
The SOHO 6 Wireless is connected directly to the modem or other Internet
connection.
4 Connect one end of the straight-through Ethernet cable
supplied with your SOHO 6 Wireless to a trusted network port
(0-3) on the SOHO 6 Wireless. Connect the other end to the
Ethernet port of your computer.
The SOHO 6 Wireless is connected to the Internet and your computer.
5 If you connect to the Internet through a DSL modem or cable
modem, reconnect the power supply to this device. The
indicator lights flash and then stop. The modem is ready for
use.
6 Attach the AC adapter to the SOHO 6 Wireless. Connect the AC
adapter to a power source.
7 Restart the computer.
See “Factory default settings” on page 31 for the factory default
configuration options. See “External Network Configuration” on
page 37 and “Configure the Trusted Network” on page 42 for
special configurations.
Cabling the SOHO 6 Wireless for more than four
appliances
Although the SOHO 6 Wireless has only four trusted network
ports (0-3), you can connect more than four appliances. Use one or
more network hubs to make more connections.
User Guide 23
Page 46

The base model SOHO 6 Wireless includes a ten-seat license. This
license allows a maximum of ten appliances on the trusted
network to connect to the Internet at the same time. There can be
more than ten appliances on the trusted network, but the SOHO 6
Wireless will only allow ten Internet connections. A seat is in use
when an appliance connects to the Internet and is free when the
connection is broken. License upgrades are available from the
WatchGuard Web site:
http://www.watchguard.com/sales/buyonline.asp
To connect more than four appliances to the SOHO 6 Wireless,
these items are necessary:
• an Ethernet hub;
• a straight-through Ethernet cable, with RJ-45 connectors, for
each computer;
24 WatchGuard Firebox SOHO 6 Wireless
Page 47

Physically Connect to the SOHO 6 Wireless
• a straight-through Ethernet cable to connect each hub to the
SOHO 6 Wireless.
1 Shut down your computer. If you connect to the Internet
through a DSL modem or cable modem, disconnect the power
supply from this device.
2 Disconnect the Ethernet cable that runs from your DSL
modem, cable modem or other Internet connection to your
computer. Connect the Ethernet cable to the WAN port on the
SOHO 6 Wireless.
The SOHO 6 Wireless is connected directly to the modem or other Internet
connection.
3 Connect one end of the straight-through Ethernet cable
supplied with your SOHO 6 Wireless to one of the trusted
network ports (0-3) on the SOHO 6 Wireless. Connect the other
end to the uplink port of the Ethernet hub.
The SOHO 6 Wireless is connected to the Internet and your Ethernet hub.
4 Connect an Ethernet cable between each of the computers and
an uplink port on the Ethernet hub.
5 If you connect to the Internet through a DSL modem or cable
modem, reconnect the power supply to this device. The
indicator lights flash and then stop. The modem is ready for
use.
6 Attach the AC adapter to the SOHO 6 Wireless. Connect the AC
adapter to a power supply.
7 Restart your computer.
See “Factory default settings” on page 31 for the factory default
configuration options. See “External Network Configuration” on
page 37 and “Configure the Trusted Network” on page 42 for
special configurations.
User Guide 25
Page 48

Setting up the Wireless Network
The SOHO 6 Wireless protects computers that are connected to it
by Ethernet cable or wireless connection. Because WatchGuard is
concerned about the security of your network, the wireless feature
is turned off on the SOHO 6 Wireless we ship you. This allows you
to enable the wireless network after you set up the desired
security.
Now that you have installed the SOHO 6 Wireless device, you can
set up the optional wireless network.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless.
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select Network =>
Optional (802.11b).
The Optional Network Configuration page appears.
3 Select the Enable Optional Network checkbox to turn on the
wireless network.
4 Type the IP Address and Subnet Mask of the wireless network.
The default IP Address is 192.168.112.1. The default Subnet Mask is
255.255.255.0.
5 Select Enable DHCP Server on the Optional Network
checkbox.
6 Type the First address for DHCP server.
The default is 192.168.112.2.
For more information on the Optional Network Configuration
page, see “Configure the Optional Network for Wireless
Networking” on page 46.
26 WatchGuard Firebox SOHO 6 Wireless
Page 49

Setting up the Wireless Access Point
Setting up the Wireless Access Point
1 From the navigation bar on the left side, select Network =>
Wireless Configuration.
The Wireless Network Configuration page appears.
2 From the Encryption drop-down list, select Disabled.
3 From the Authentication drop-down, select Open System.
4 From Basic Settings, write down the number in the SSID text
box for later use.
The SSID is the wireless devices identification number, and it is used to
create the wireless connection. The default SSID is the 5 digit serial
number for your SOHO 6 Wireless device.
5Click Submit.
For more information on configuring the wireless network, see
“Configure the Wireless Network” on page 49.
Configuring the Wireless Card on your computer
The following instructions are for the Windows XP operating
system. Refer to the WatchGuard SOHO 6 Wireless User Guide for
instruction on other operating systems.
1Click Start => Control Panel => Network Connections.
The Network Connections dialog box appears.
2 Double-click on the Wireless Network Connection.
The Wireless Network Connection dialog box appears.
3Click Advanced.
The Wireless Network Connection Properties dialog box appears with the
Wireless Networks tab selected.
4 In the Preferred networks section, click Add.
The Wireless Network Properties dialog box appears.
User Guide 27
Page 50

5 Type the SSID that you wrote down from the Wireless
Network Configuration page into the Network Name (SSID)
text box.
6Click OK to close the Wireless Network Properties dialog box.
7Click Refresh.
The operating system looks for all wireless connections and list them in the
Available Networks text box. Select the SSID of the wireless computer
that you configured to access the SOHO 6 Wireless.
8Click OK to enable the wireless connections.
The wireless network connection should now show that your wireless
network is active.
9 Set up the wireless computer to use DHCP. For information on
setting up DHCP, see Figure , “Enable your computer for
DHCP,” on page 17.
Your Windows operating system should automatically look for
the wireless connection, and if more than one wireless network
is found, a dialog box will appear listing all wireless devices in
the area. Select the wireless computer that you configured to
access the SOHO 6 Wireless device.
Your SOHO 6 Wireless is now protecting wired and wireless
computers from security hazards. To learn how to enhance your
security setting, see “Configure the Wireless Network” on page 49.
28 WatchGuard Firebox SOHO 6 Wireless
Page 51

CHAPTER 3 SOHO 6 Wireless
basics
The configuration of the SOHO 6 Wireless is made through Web
pages contained in the software of the SOHO 6 Wireless. You can
connect to these configuration page with your Web browser.
SOHO 6 Wireless System Status page
Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
The System Status page opens.
User Guide 29
Page 52

The System Status page is the main configuration page of the
SOHO 6 Wireless. A display of information about the SOHO 6
Wireless configuration is shown. This information includes the
following:
• The firmware version
• The serial number of the appliance
• The status of the following SOHO 6 Wireless features:
- WSEP Logging
- VPN Manager Access
-Syslog
- Pass Through
• The status of the upgrade options;
30 WatchGuard Firebox SOHO 6 Wireless
Page 53

Factory default settings
• Configuration information for the trusted network and the
external network
• Configuration information for firewall settings (incoming
services and outgoing services)
• A reboot button to restart the SOHO 6 Wireless
NOTE
If the external network is configured to use the PPPoE protocol, the
System Status page displays a connect button or a disconnect button. Use
these buttons to start or terminate the PPPoE connection.
Factory default settings
The default network settings and configuration settings for the
SOHO 6 Wireless:
External network
The external network settings use DHCP.
Trusted network
The default IP address of the trusted interface is
192.168.111.1.
The IP addresses for the computers on the trusted network
are assigned through DHCP.
Firewall settings
All incoming services are blocked.
An outgoing service allows all outbound traffic.
All of the firewall options are disabled.
The DMZ pass-through is disabled.
User Guide 31
Page 54

System Security
The System Security is disabled. The system administrator
name and system administrator passphrase are not set. All
computers on the trusted network can access the
configuration pages.
SOHO 6 Wireless Remote Management is disabled.
VPN Manager Access is disabled.
The remote logging is not configured.
WebBlocker
The WebBlocker is disabled and the settings are not
configured.
Upgrade Options
The upgrade options are disabled until the license keys are
entered into the configuration page.
Reset the SOHO 6 Wireless to the factory default
settings
Reset the SOHO 6 Wireless to the factory default settings if it is not
possible to correct a configuration problem. A reset to the factory
default settings is required if the system security passphrase is
unknown or the firmware of the SOHO 6 Wireless is damaged by a
power interruption. Follow these steps to reset the SOHO 6
Wireless to the factory default settings:
1 Disconnect the power supply.
2 Press and hold the reset button.
3 Connect the power supply.
4 Continue holding the button until the red LED on the front of
the SOHO 6 Wireless goes on and then off.
5 Disconnect the power supply.
32 WatchGuard Firebox SOHO 6 Wireless
Page 55

Register your SOHO 6 Wireless and activate the LiveSecurity Service
6 Connect the power supply.
The PWR indicator is on and the reset is complete.
The base model SOHO 6 Wireless
The base model SOHO 6 Wireless includes a ten-seat license. This
license allows a maximum of ten computers on the trusted
network to connect to the Internet at the same time. There can be
more than ten computers on the trusted network, but the SOHO 6
Wireless will only allow ten Internet connections. See “Cabling the
SOHO 6 Wireless for more than four appliances” on page 23 for
additional information.
Register your SOHO 6 Wireless and activate
the LiveSecurity Service
After the SOHO 6 Wireless is installed and configured, register the
SOHO 6 Wireless and activate your LiveSecurity Service
subscription. LiveSecurity Service provides threat alert
notifications, security advice, free virus protection, software
updates, technical support by Web or telephone, and access to
online help resources and the WatchGuard user forum. A
subscription to the LiveSecurity Service is required to get the
license keys for the upgrades that you purchase.
You must have the serial number of your SOHO 6 Wireless to
register. The SOHO 6 Wireless serial number is located on the
bottom of the appliance. Record the serial number in the table
below:
Serial Number:
User Guide 33
Page 56

Register you SOHO 6 Wireless with the LiveSecurity Service at the
WatchGuard Web site:
http://www.watchguard.com/activate
NOTE
To activate the LiveSecurity Service, your browser must have JavaScript
enabled.
If you have a user profile on the WatchGuard Web site, enter your
user name and password. If you do not have a user profile on the
WatchGuard Web site, create a new account. Select your product
and follow the instructions for product activation.
Record your LiveSecurity Service user profile information in the
table below:
User name:
Password:
Keep this information confidential.
Reboot the SOHO 6 Wireless
To reboot a SOHO 6 Wireless located on the local network, use one
of these methods:
34 WatchGuard Firebox SOHO 6 Wireless
Page 57

Reboot the SOHO 6 Wireless
NOTE
The SOHO 6 Wireless requires 30 seconds to reboot. The Mode indicator
on the front of the SOHO 6 Wireless will go off and then come on.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2Click Reboot.
or
2 Disconnect and reconnect the power supply.
To reboot a SOHO 6 Wireless located on a remote system, use one
of these methods:
NOTE
The remote SOHO 6 Wireless must be configured to allow incoming
HTTP (Web) or FTP traffic from the Internet. See “Configure incoming
and outgoing services” on page 71 for information about how to
configure a SOHO 6 Wireless to receive incoming traffic.
3 Type the external network IP address of the remote SOHO 6
Wireless in your browser window to connect to the System
Status page of the remote SOHO 6 Wireless.
4Click Reboot.
or
4 Send an FTP command to the remote SOHO 6 Wireless. Use an
FTP program to connect to the remote SOHO 6 Wireless, and
enter the command:
quote rebt
User Guide 35
Page 58

36 WatchGuard Firebox SOHO 6 Wireless
Page 59

CHAPTER 4 Configure the
Network Interfaces
External Network Configuration
When you configure the external network, you select the method
of communication between the SOHO 6 Wireless and the ISP.
Make this selection based on the method of network address
distribution in use by your ISP. The possible methods are static
addressing, DHCP, or PPPoE.
Network addressing
To connect to a TCP/IP network, each computer must have an IP
address. The assignment of IP addresses is dynamic or static.
• If the assignment is dynamic, the ISP assigns a different IP
address to a computer each time the computer connects to
the network. When the computer disconnects, the IP address
is made available to a different computer.
User Guide 37
Page 60

• If the assignment is static, all computers on the network have
a permanently assigned IP address. There are no computers
that have the same IP address.
Most ISPs make dynamic IP address assignments through DHCP
(Dynamic Host Configuration Protocol). When a computer
connects to the network, a DHCP server at the ISP assigns that
computer an IP address. The manual assignment of IP addresses is
not necessary with this system.
Some ISPs assign the IP addresses through PPPoE (Point-to-Point
Protocol over Ethernet). PPPoE emulates a standard dial-up
connection to provide some of the features of Ethernet and PPP.
This system allows the ISP to use the billing, authentication, and
security systems designed for dial-up, DSL modem and cable
modem service. When the SOHO 6 Wireless is configured to use
PPPoE, a button on the System Status page controls the connection
to the external network.
Your ISP can tell you how their system assigns the IP addresses.
Configure the SOHO 6 Wireless external network
for dynamic addressing
The default configuration sets the SOHO 6 Wireless to get the
external address information through DHCP. If your ISP supports
this method, the SOHO 6 Wireless gets IP address information
from the ISP when the SOHO 6 Wireless reboots and connects to
the Internet. The SOHO 6 Wireless does not require any additional
configuration.
Configure the SOHO 6 Wireless external network
for static addressing
If your ISP assigns static IP address, you must move the IP address
data from your computer to the SOHO 6 Wireless. This
38 WatchGuard Firebox SOHO 6 Wireless
Page 61

External Network Configuration
configuration causes the ISP to communicate with the SOHO 6
Wireless and not your computer.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Network => External.
The External Network configuration page opens.
3 From the Configuration Mode drop-down list, select
Manual Configuration.
The page refreshes.
4 Type the TCP/IP settings you recorded from your computer
during the installation process. Refer to the table, “Examine
and record the current TCP/IP settings” on page 15.
User Guide 39
Page 62

5Click Submit.
The configuration change is saved to the SOHO 6 Wireless.
Configure the SOHO 6 Wireless external network
for PPPoE
If your ISP assigns IP addresses through PPPoE, your PPPoE login
name and password are required to configure the SOHO 6
Wireless.
To configure the SOHO 6 Wireless for PPPoE:
1 Open your Web browser and click Stop.
Because the Internet connection is not configured, the browser can not
load your home page from the Internet. The browser can open the
configuration pages in the SOHO 6 Wireless.
2 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
3 From the navigation bar on the left side, select
Network => External.
The External Network configuration page opens.
4 From the Configuration Mode drop-down list, select PPPoE
Client.
The page refreshes.
40 WatchGuard Firebox SOHO 6 Wireless
Page 63

External Network Configuration
5 Type the PPPoE login name and domain supplied by your ISP.
6 Type the PPPoE password supplied by your ISP.
7 Type the time delay before inactive TCP connections are
disconnected.
8Click Automatically restore lost connections.
This option keeps a constant flow of traffic between the SOHO 6 Wireless
and the PPPoE server. This option allows the SOHO 6 Wireless to keep the
PPPoE connection open during a period of frequent packet loss. If the flow
of traffic stops, the SOHO 6 Wireless reboots. A reboot frequently restores
the connection. The ISP sees this constant flow of traffic as a continuous
connection. The regulations and billing policy of the ISP determine if you
can use this option. Watchguard Technical Support uses this feature as a
solution to some problems.
9Click Enable PPPoE debug trace to activate PPPoE debug
trace.
10 Click Submit.
The configuration change is saved to the SOHO 6 Wireless.
User Guide 41
Page 64

Configure the Trusted Network
The DHCP Server option sets the SOHO 6 Wireless to assign IP
addresses to the computers on the trusted network. The SOHO 6
Wireless uses DHCP to make the assignments. When the SOHO 6
Wireless receives a request from a new computer on the trusted
network, the SOHO 6 Wireless assigns the computer an IP address.
If you use a DHCP server to assign IP addresses, enable the DHCP
Relay option. This option causes the SOHO 6 Wireless to forward
the DHCP request to the specified DHCP server.
Configure DHCP server and DHCP relay
To configure DHCP server:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Network => Trusted.
The Trusted Network configuration page opens.
42 WatchGuard Firebox SOHO 6 Wireless
Page 65

Configure the Trusted Network
3 Type the IP address and the subnet mask in the applicable
fields.
4 Click to select the Enable DHCP Server on the Trusted
Network check box.
5 Type the first IP address that is available for the computers that
connect to the trusted network.
6 Type the WINS Server address, DNS Server primary address,
DNS Server secondary address, and DNS Domain server
suffix.
7Click Submit.
8 Reboot the SOHO 6 Wireless if necessary.
User Guide 43
Page 66

To configure the DHCP relay server:
1 From the Trusted Network configuration page, click the
Enable DHCP Relay checkbox.
2 Type the IP address of the DHCP relay server.
3Click Submit.
4 Reboot the SOHO 6 Wireless.
The SOHO 6 Wireless receives a DHCP request from a computer on
the trusted network . The reques t is se nt from th e SOHO 6 Wireless to
the remote DHCP server. The SOHO 6 Wireless receives the IP
address sent from the DHCP server. The IP address is sent from the
SOHO 6 Wireless to the computer that made the request. If the
SOHO 6 Wireless can not contact the remote DHCP server in less
than 30 seconds, the SOHO 6 Wireless uses its internal DHCP server
to respond to the computer on the trusted network.
Configure additional computers on the trusted network
The SOHO 6 Wireless accepts the direct connection of a maximum
of four computers, printers, scanners, or other network
peripherals. The use of one or more 10BaseT Ethernet hubs with
RJ-45 connectors allows the connection of additional appliances.
Follow these steps to add a computer to the trusted network:
1 Make sure that the computer has an Ethernet card installed.
2 Shut down the computer.
3 Connect the computer to the network as shown in section
“Cabling the SOHO 6 Wireless for more than four appliances”
on page 23.
4 Restart the computer.
5 Set the computer to get its address through DHCP as shown in
section “Enable your computer for DHCP” on page 17.
44 WatchGuard Firebox SOHO 6 Wireless
Page 67

Configure the Trusted Network
6 Shut down and restart the computer.
Configure the trusted network with static addresses
To disable the SOHO 6 Wireless DHCP server and make static
address assignments, follow these steps:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Network => Trusted.
The Trusted Network configuration page opens.
User Guide 45
Page 68

3 Type the IP address and the subnet mask in the applicable
fields.
4 Reset the Enable DHCP Server on the Trusted Network check
box.
5Click Submit
6 Reboot the SOHO 6 Wireless as necessary.
7 Configure the appliances on the trusted network with static
addresses.
Configure the Optional Network for Wireless Networking
To turn on the wireless network, you must enable the optional
network.
Follow these instructions to complete the configuration:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
46 WatchGuard Firebox SOHO 6 Wireless
Page 69

Configure the Optional Network for Wireless Networking
2 From the navigation bar on the left side, select
Network => Optional (802.11b).
The Optional Network Configuration page opens.
3Click the Enable Optional Network checkbox.
To turn on the wireless network, you need to enable the optional network.
4 Type the IP address and subnet mask of the optional network.
The default IP Address is 192.168.112.1. The default Subnet Mask is
255.255.255.0.
User Guide 47
Page 70

5 Select Enable DHCP Server on the Optional Network
checkbox.
6 Type the First address for DHCP server.
The default is 192.168.112.2.
7 Type the WINS Server address, DNS Server primary address,
DNS Server secondary address, and DNS Domain server
suffix.
8 To enable the DHCP Relay on the optional network, click
Enable DHCP Relay checkbox and enter the IP address of the
DHCP relay server in the text box.
9 To allow traffic between the optional network and trusted
network, click the Allow traffic between Optional Network
and Trusted Network checkbox.
If you select this checkbox, all wireless devices that are connected to the
optional network can access the computers on your trusted network.
10 To require encrypted MUVPN connections through the
wireless interface, click to select the Requires Encrypted
MUVPN connections on this interface checkbox.
You may want to enable this feature after the initial connection between
your wireless computers and the SOHO 6 Wireless. This feature secures
your network from unauthorized users using your wireless network. If this
checkbox is enabled, only computer with the MUVPN software can access
your SOHO 6 Wireless network. You need to configure the MUVPN
software on the SOHO 6 Wireless device and wireless computer. For more
information on configuring MUVPN, see Chapter 11 “MUVPN Clients”
on page 119.
11 Click Submit.
48 WatchGuard Firebox SOHO 6 Wireless
Page 71

Configure the Wireless Network
Configure the Wireless Network
Once you turned on the wireless network by enabling the optional
network, you can set up the security setting for your wireless
connection.
Configure Security
The SOHO 6 Wireless uses the industry standard security protocol,
Wired Equivalent Privacy (WEP), specified by the IEEE standard
802.11b. WEP is designed to provide a wireless local area network
(WLAN) with a level of security and privacy comparable to that
usually expected of a wired local area network (LAN). A wired
LAN is generally protected by physical security, such as login
credentials, that are only effective for a controlled physical
environment, because the radio transmissions of a WLAN are not
bound by the walls containing the network. WEP achieves security
by encrypting the data transmitted over the WLAN. Data
encryption protects the vulnerable wireless connection between
computers and access points; once this measure has been taken,
other typical LAN security mechanisms such as password
protection, virtual private networks (VPNs), and authentication
can be used to ensure privacy.
Follow these instructions to set up wireless security:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
User Guide 49
Page 72

2 From the navigation bar on the left side, select Network =>
Wireless Configuration.
The Wireless Network Configuration page appears.
3From the Encryption drop-down list, select the level of
encryption you want applied to your wireless connections.
The options are Disabled, 40/64 bit WEP, and 128 bit WEP.
50 WatchGuard Firebox SOHO 6 Wireless
Page 73

Configure the Wireless Network
Disabled
The default is Disabled, and you should use this option for
the initial connection. Your wireless connection is not using
WEP when Disabled is selected.
40/64 bit WEP or128 bit WEP
Once you complete the initial connection between your
wireless computer and SOHO 6 Wireless, you can change
this option to add WEP. Select either 40/64 bit or128 bit
based on what the wireless card in your computer
supports.
4 If you are using WEP encryption, type a hexadecimal number
in the Key text boxes.
You can type up to four keys that the wireless network will use to connect.
If you have 40/64 bit WEP, the key can be up to 10 characters. If you have
128 bit WEP, the key can be up to 26 characters.
5 If you typed more than one key, select which key you want to
use as the default key from the Default Key drop-down list.
6 Select the Authentication mode you want to use for your
wireless network connection.
The options are Open System, Shared Key, and Both.
Open System
This option does not support shared keys. If you disable
encryption, this is the only option.
Shared Key
This option supports shared keys. If you enabled WEP, this
option is enabled.
Change the Basic Settings
The SSID is the SOHO 6 Wireless identification number, and it is
used to create the wireless connection with the wireless computers.
User Guide 51
Page 74

To change the SSID of the SOHO 6 Wireless:
• In the Basic Settings section, type a new identification in
SSID text box.
The default SSID is the 5 digit serial number for your SOHO 6 Wireless
device. The first four digits of the serial number are the product code and
are not part of the SSID. The next five digits after the product code are
the serial number. The remaining characters are an encoded hash for
security uses. The maximum identification length is 20 characters.
To change the Channel:
•From the Channel drop-down list, select the channel you
want to use in your wireless connection.
Restrict Access by Hardware Address
You can change the settings of how the SOHO 6 Wireless
communicates with your wireless computer and other settings.
1 If you want to restrict access to the SOHO 6 Wireless by the
computer hardware address, select Enabled in the Restrict
Access by Hardware Address drop-down list.
2Click Edit
The Allowed Hardware Addresses page appears.
3 Type the MAC Address of the computer you want to connect
to the SOHO 6 Wireless.
4Click Submit.
OR
1 If you do not want to restrict access to the SOHO 6 Wireless by
the computer hardware address, select Disabled.
52 WatchGuard Firebox SOHO 6 Wireless
Page 75

Configure the Wireless Network
Configure the Beacon Rate
1In the AP Beacon Rate text box, type the beacon rate in
milliseconds (100 through 10,000) that you want the SOHO 6
Wireless to use.
The beacon rate is the rate the SOHO 6 Wireless sends out broadcasts so
that the wireless computers can find it.
2 If you want the SOHO 6 Wireless to broadcast a beacon rate,
select Enabled from the Broadcast SSID in AP Beacon Frames.
If you do not want to broadcast the beacon rate, select
Disabled.
3 If you want the SOHO 6 Wireless to respond to request from
the wireless computers, select Enabled in the Respond to SSID
Query Requests. If you do not want the SOHO 6 Wireless to
respond, select Disabled.
The wireless computers send out query requests to find if there are any
wireless access points that it can connect to.
Log Authentication Events
If you want the SOHO 6 Wireless to log when a wireless computer
tries to access it, select Enabled. If you do not want to log
authentication events, select disabled.
Set Advanced Settings
‘You can change Maximum Transmit Rate and Fragmentation
Threshold.
• To change the Maximum Transmit Rate, select the rate per
Mbits per second from the Maximum Transmit Rate dropdown list.
• To change the Fragmentation Threshold, type a value of 256
to 4096 in the Fragmentation Threshold text box.
User Guide 53
Page 76

Configure static routes
To send the specified packets to different segments of the trusted
network connected through a router or switch, configure static
routes.
Follow these instructions to configure static routes:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Network => Routes.
The Routes page opens.
3Click Add.
The Add Route page opens.
54 WatchGuard Firebox SOHO 6 Wireless
Page 77

View network statistics
4 From the Type drop-down list, select either Host or Network.
5 Type the IP address and the gateway of the route in the
applicable fields.
The gateway of the route is the local interface of the router.
6Click Submit.
To remove a route, select the route and click Remove.
View network statistics
The Network Statistics page gives information about network
performance. This page is useful during troubleshooting.
Follow these instructions to access the Network Statistics page:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
User Guide 55
Page 78

2 From the navigation bar on the left side, select
Network => Network Statistics.
The Network Statistics page opens.
Configure the dynamic DNS Service
This feature allows you to register the external IP address of the
SOHO 6 Wireless with the dynamic DNS (Domain Name Server)
service DynDNS.org. A dynamic DNS service makes sure that the
IP address attached to your domain name is changed when your
ISP assigns you a new IP address.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
56 WatchGuard Firebox SOHO 6 Wireless
Page 79

Configure the dynamic DNS Service
NOTE
WatchGuard is not affiliated with dyndns.org.
2 From the navigation bar on the left side, select
Network => DynamicDNS.
The Dynamic DNS client page opens.
3 Select the Enable Dynamic DNS client checkbox.
4 Type the domain, name, and password in the applicable fields.
5Click Submit.
User Guide 57
Page 80

58 WatchGuard Firebox SOHO 6 Wireless
Page 81

CHAPTER 5 Administrative
options
Use the SOHO 6 Wireless Administration page to configure access
to the SOHO 6 Wireless. The System Security, SOHO 6 Wireless
Remote Management
configured from the Administration page. The firmware updates,
upgrade activation, and display of the SOHO 6 Wireless
configuration file in a text format are done from the
Administration page.
TM
feature, and VPN Manager Access are
The System Security page
The System Security page contains the settings that control access
to the configuration of the SOHO 6 Wireless. Set a system
administrator name and passphrase to limit access to the
configuration pages. Enable remote management to allow the
configuration of the SOHO 6 Wireless from the external network.
User Guide 59
Page 82

System security
A passphrase prevents access to the configuration of the SOHO 6
Wireless by an unauthorized user on the trusted network. The use
of a passphrase is important to the security of your network.
NOTE
Record the system administrator name and passphrase in a safe location.
When system security is enabled, the system administrator name and
passphrase are required to access the configuration pages. If the system
administrator name and passphrase are unknown, you must reset the
SOHO 6 Wireless to the factory default settings. See “Factory default
settings” on page 31 for additional information.
Change the System Administrator passphrase every month. Select
a combination of eight letters, numbers, and symbols. Do not use a
word. Use at least one special symbol, a number, and a mixture of
upper-case and lower-case letters for increased security.
Follow these instructions to enable system security:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Administration => System Security.
The System Security page opens.
60 WatchGuard Firebox SOHO 6 Wireless
Page 83

The System Security page
3Verify that the HTTP Server Port is set to 80.
4 Click to select the Enable System Security check box.
5Type a System Administrator Passphrase and then type it
again to confirm.
6Click Submit.
SOHO 6 Wireless Remote Management
Both the SOHO 6 Wireless and SOHO 6tc Wireless come equipped
with the SOHO 6 Wireless Remote Management feature. This
feature uses the MUVPN client or Pocket PC to establish a secure
User Guide 61
Page 84

connection, using Internet Protocol Security (IPSec), over an
unsecured network from your remote computer in order to
remotely manage your SOHO 6 Wireless.
For example, the MUVPN client is installed and configured on
your computer. You then establish a standard Internet connection
and activate the MUVPN client. The MUVPN client creates an
encrypted tunnel to your SOHO 6 Wireless. You can now access
the SOHO 6 Wireless configuration pages without compromising
security. Another way to remotely manage your SOHO 6 Wireless,
is using a Pocket PC. First you establish a standard Internet
connection using your Pocket PC, and then you can access the
SOHO 6 Wireless configuration page.
1 First, follow the steps above to configure System Security.
2 Enable the checkbox labeled Enable SOHO 6 Wireless
Wireless Remote Management.
3 Type the Virtual IP address which will be used by the remote
management computer when connecting to the SOHO 6
Wireless in the appropriate field.
4In the Authentication Algorithm drop list, specify the
authentication: MD5-HMAC (128-bit authentication) or SHA1HMCA (160-bit authentication).
5In the Encryption Algorithm drop list, specify the type of
encryption: DES-CBC or 3DES-CBC.
6In the VPN Client Type drop list, specify the type of VPN
client: Mobile User (MUVPN) or Pocket PC.
7Click Submit.
8 Next, you must install and configure the MUVPN client on
your remote computer.
For this information, see Chapter 10, “MUVPN Clients” on page 119.
9 Once you have installed and configured the MUVPN client,
establish an Internet connection through either Dial-Up
62 WatchGuard Firebox SOHO 6 Wireless
Page 85

Set up VPN manager access
Networking or directly through a local area network (LAN) or
wide area network (WAN).
From the Windows desktop system tray:
10 Verify the MUVPN client status–it must be activated. If it is
not, right-click the icon and select Activate Security Policy.
For information on how to determine the status of the MUVPN icon, see
Chapter 11, “The Mobile User VPN client icon” on page 148.
Then, from the Windows desktop system tray:
11 Right-click the icon and select Connect.
The WatchGuard Mobile User Connect widow appears.
12 Click the Yes button.
13 Finally, enter the IP address of the external network in your
browser window to connect to the System Status page of the
SOHO 6 Wireless.
Set up VPN manager access
The VPN Manager Access page configures the SOHO 6 Wireless to
allow remote configuration of the SOHO 6 Wireless by the
WatchGuard VPN Manager software. The WatchGuard VPN
Manager software configures and manages VPN tunnels.
The VPN Manager software is a separate product and must run on
a WatchGuard Firebox II/III. Additional information about the
VPN Manager product is available on the WatchGuard Web site:
https://www.watchguard.com/products/vpnmanager.asp
Follow these instructions to configure VPN Manager access:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
User Guide 63
Page 86

2 From the navigation bar on the left side, select
Administration => VPN Manager Access.
The VPN Manager Access page opens.
3 Select Enable VPN Manager Access.
4 Type the Status Passphrase.
5 Type the Status Passphrase again to confirm.
6 Type the Configuration Passphrase.
7 Type the Configuration Passphrase again to confirm.
NOTE
These passphrases must match the passphrases used in the VPN Manager
software or the connection will fail.
8Click Submit.
64 WatchGuard Firebox SOHO 6 Wireless
Page 87

Update the firmware
Update the firmware
Check regularly for SOHO 6 Wireless firmware updates on the
WatchGuard Web site:
http://support.watchguard.com/sohoresources/
Download the .exe or .wgd files that contain the firmware update.
The .exe file is an installer and the .wgd file is a binary file. The
.wgd file is an advanced installation method.
NOTE
The .exe file is not available for firmware previous to the 6.0 release.
To install the .exe file:
1 Save the .exe file to your computer.
2 Double-click the .exe file.
The installer will install the updated firmware.
To install the .wgd file:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2Click Update.
NOTE
If you configure your SOHO 6 Wireless from a computer that does not use
the Windows operating system, for example Macintosh or Linux, you
must update your firmware with this procedure.
3 Read the End-User License Agreement. Then set the I accept
the above license agreement check box at the bottom of the
page.
User Guide 65
Page 88

4 Type the location of the .wgd firmware files on your computer.
OR
4Click Browse and locate the .wgd firmware files on your
computer.
NOTE
Check your SOHO 6 Wireless firewall settings to make sure that your
firewall allows .wgd files.
5Click Update.
Follow the instructions provided by the update wizard.
NOTE
The update wizard requests a user name and password. Type the system
administrator name and passphrase configured on the System Security
page. The default values are “user” and “pass”.
Activate the SOHO 6 Wireless upgrade
options
Every SOHO 6 Wireless includes the software for all upgrade
options. To activate an upgrade option, you must enter a license
key in the configuration of the SOHO 6 Wireless. To receive a
license key, purchase and activate an upgrade option at the
66 WatchGuard Firebox SOHO 6 Wireless
Page 89

Activate the SOHO 6 Wireless upgrade options
LiveSecurity Service Web site. See “Register your SOHO 6 Wireless
and activate the LiveSecurity Service” on page 33 for more
information.
Follow these steps to activate an upgrade option:
1 Go to the upgrade page of the WatchGuard Web site:
http://www.watchguard.com/upgrade
2 Type your User Name and Password.
3Click Log In.
4 Follow the instructions provided on the Web site to activate
your license key.
5 Copy the license key from the LiveSecurity Service Web site.
6 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
7 From the navigation bar on the left side, select
Administration => Upgrade.
The Upgrade page opens.
8 Paste the license key in the applicable field.
9Click Submit.
User Guide 67
Page 90

Upgrade options
Seat licenses
A seat license upgrade allows more connections between
the trusted or optional network and the external network.
A wired connection goes to the trusted and the wireless
connection goes to the optional. For example, a 25-seat
license allows 25 wired or wireless connections instead of
the standard 10 connections.
IPSec Virtual Private Networking (VPN)
The VPN upgrade is necessary to configure virtual private
networking. The SOHO 6tc Wireless includes a VPN
upgrade license key. The SOHO 6 Wireless does not
include a VPN upgrade license key.
WebBlocker
The WebBlocker upgrade enables the Web filtering option.
MUVPN Client
The MUVPN Client upgrade allows remote users to
connect to the SOHO 6 Wireless through a secure (IPSec)
VPN tunnel. The MUVPN client creates an encrypted
tunnel to your trusted or optional network depending on if
it is a wired or wireless connection. A wired connection
goes to the trusted and the wireless connection goes to the
optional. If you have a wireless network, you can configure
the wireless network to require wireless computers to have
an encrypted MUVPN connection to access the SOHO 6
Wireless. The SOHO 6 Wireless includes several MUVPN
client licenses. You can add more MUVPN connections
with the MUVPN Client upgrade. For more information on
configuring a wireless network to require MUVPN
connections, see “Configure the Optional Network for
Wireless Networking” on page 46.
68 WatchGuard Firebox SOHO 6 Wireless
Page 91

View the configuration file
LiveSecurity Service subscription renewals
Purchase a LiveSecurity subscription renewal for a period
of one or two years from your reseller or the WatchGuard
online store. Go to the renew page of the WatchGuard Web
site to purchase or activate a subscription renewal:
http://www.watchguard.com/renew/
Follow the instructions on the Web site.
View the configuration file
The contents of the SOHO 6 Wireless configuration file is available
in text format from the View Configuration File page.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Administration => View Configuration File.
The View Configuration File page opens.
User Guide 69
Page 92

70 WatchGuard Firebox SOHO 6 Wireless
Page 93

CHAPTER 6 Configure the
Firewall Settings
Firewall settings
The configuration settings of the SOHO 6 Wireless control the flow
of traffic between the trusted network and the external network.
The configuration you select depends on the types of risks that are
acceptable for the trusted network.
The SOHO 6 Wireless lists many standard services on the
configuration page. A service is the combination of protocol and
port numbers for a type of application or type of communication.
Configure incoming and outgoing services
The default configuration of the SOHO 6 Wireless prevents the
transmission of all packets from the external network to the trusted
network. Change the configuration to select the types of traffic that
User Guide 71
Page 94

are permitted. For example, to operate a Web server behind the
SOHO 6 Wireless, add an incoming Web service.
Select carefully the number and the types of services that you add.
The added services decrease the security of your network.
Compare the value of access to each service against the security
risk caused by that service.
Common services
Follow these steps to change the configuration of the incoming
filters for common services:
1 From the navigation bar on the left side, select
Firewall => Incoming or Outgoing.
The Filter Incoming Traffic page opens.
72 WatchGuard Firebox SOHO 6 Wireless
Page 95

Configure incoming and outgoing services
2 Locate a pre-configured service, such as FTP, Web, or Telnet,
then select either Allow or Deny from the drop-down list.
The illustration shows the HTTP service configured to allow incoming
traffic.
3 Type the trusted network IP address of the computer to which
this rule applies.
The illustration shows the HTTP service configured to allow incoming
traffic to the computer with IP address 192.168.111.2.
4Click Submit.
Create a custom service
If you need to allow a service that is not listed in the common
services, configure a custom service based on a TCP port, a UDP
port, or a protocol.
Follow these steps to configure a custom service:
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Firewall => Custom Service.
The Custom Service page opens.
User Guide 73
Page 96

3 Type a name for the service in the Service name field.
4 Select TCP Port, UDP Port, or Protocol from the drop-down list
below the Protocol Settings.
The Custom Service page refreshes.
5 In the fields separated by the word To, enter the port number
or the range of port numbers, or enter the protocol number.
NOTE
For a TCP port or a UDP port, specify a port number. For a protocol,
specify a protocol number. You cannot specify a port number for a
protocol.
74 WatchGuard Firebox SOHO 6 Wireless
Page 97

Block external sites
6Click Add.
The following steps determine how the service is filtered.
7 Select Allow or Deny from the Incoming Filter and Outgoing
Filter drop-down lists.
8 Select Host IP Address, Network IP Address, or Host Range
from the drop-down list at the bottom of the page.
The Custom Service page refreshes.
9 Type a single host IP address, a network IP address, or the start
and end of a range of host IP addresses in the address field.
10 Click Add.
Repeat the previous three steps until all of the address information for this
custom service is set.
11 Click Submit.
Block external sites
The default configuration of the SOHO 6 Wireless:
• allows the transmission of all packets from the trusted
network to the external network;
• prevents the transmission of all packets from the external
network to the trusted network.
You can change the configuration to prevent access to specified
Internet sites. Follow these steps to configure the blocked sites:
1 From the navigation bar on the left side, select
Firewall => Blocked Sites.
The Blocked Sites page opens.
User Guide 75
Page 98

2 Select either Host IP Address, Network IP Address, or Host
Range from the drop-down list.
The Blocked Sites page refreshes.
3 Type a single host IP address, a network IP address, or the start
and end of a range of host IP addresses in the address field.
The illustration shows the selection Host IP Address and the IP address
207.68.172.246.
4Click Add.
The address information appears in the Blocked Sites field.
5Click Submit.
76 WatchGuard Firebox SOHO 6 Wireless
Page 99

Firewall options
Firewall options
The previous sections described how to allow or deny complete
classes of services. The Firewall Options page allows the
configuration of general security policies.
1 Type the IP address of the trusted network in your browser
window to connect to the System Status page of the SOHO 6
Wireless:
The default IP address is: http://192.168.111.1
2 From the navigation bar on the left side, select
Firewall => Firewall Options.
The Firewall Options page opens.
User Guide 77
Page 100

Ping requests received from the external network
You can configure the SOHO 6 Wireless to deny all ping packets
received on the external interface.
1 Set the Do not respond to PING requests received on External
Network check box.
2Click Submit.
Denying FTP access to the trusted network interface
You can configure the SOHO 6 Wireless to prevent FTP access to
the computers on the trusted network by the computers on the
external network.
1Set Do not allow FTP access to Trusted Network check box.
2Click Submit.
SOCKS implementation for the SOHO 6 Wireless
The SOHO 6 Wireless functions as a SOCKS network proxy server.
An application that uses more than one socket connection and
implements the SOCKS version 5 protocol can communicate
through the SOHO 6 Wireless. SOCKS supplies a secure, two-way
communication channel between a computer on the external
network and a computer on the trusted network. To use a SOCKScompatible application, configure the application with the
necessary information about the SOHO 6 Wireless.
The SOHO 6 Wireless supports SOCKS version 5 only. The
SOHO 6 Wireless does not support authentication or DNS
(Domain Name System) resolution.
78 WatchGuard Firebox SOHO 6 Wireless
 Loading...
Loading...