Watchguard Firebox X20E, Firebox X55E, Firebox X10E-W, Firebox X55E-W, Firebox X10E User Manual
...
WatchGuard
®
Firebox® X Edge e-Series
User Guide
Firebox X Edge e-Series - Firmware Version 8.6
All Firebox X Edge e-Series Standard and Wireless Models

Notice to Users
Information in this guide is subject to change without notice. Companies, names, and data used in examples herein are fictitious
unless otherwise noted. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or
mechanical, for any purpose, without the express written permission of WatchGuard Technologies, Inc.
Copyright, Trademark, and Patent Information
Copyright© 1998 - 2007 WatchGuard Technologies, Inc. All rights reserved.
.
Complete copyright, trademark, patent, and licensing information can be
found in an appendix at the end of this book. You can also find it online at:
http://www.watchguard.com/help/documentation/
All trademarks or trade names mentioned herein, if any, are the property of their respective owners.
.
This product is for indoor use only.
End-User License Agreement
IMPORTANT - READ CAREFULLY BEFORE ACCESSING WATCHGUARD SOFTWARE:
This Firebox Software End-User License Agreement (“AGREEMENT”) is a legal agreement between you (either an individual or a
single entity) and WatchGuard Technologies, Inc. (“WATCHGUARD”) for the WATCHGUARD Firebox software product, which
includes computer software components (whether installed separately on a computer workstation or on the WATCHGUARD
hardware product or included on the WATCHGUARD hardware product) and may include associated media, printed materials,
and on-line or electronic documentation, and any updates or modifications thereto, including those received through the
WatchGuard LiveSecurity Service (or its equivalent), (the “SOFTWARE PRODUCT”). WATCHGUARD is willing to license the
SOFTWARE PRODUCT to you only on the condition that you accept all of the terms contained in this Agreement. Please read this
Agreement carefully. By installing or using the SOFTWARE PRODUCT you agree to be bound by the terms of this Agreement. If
you do not agree to the terms of this AGREEMENT, WATCHGUARD will not license the SOFTWARE PRODUCT to you, and you will
not have any rights in the SOFTWARE PRODUCT. In that case, promptly return the SOFTWARE PRODUCT, along with proof of
payment, to the authorized dealer from whom you obtained the SOFTWARE PRODUCT for a full refund of the price you paid. The
WATCHGUARD hardware product is subject to a separate agreement and limited hardware warranty included with the
WATCHGUARD hardware product packaging and/or in the associated user documentation.
1. Ownership and License. The SOFTWARE PRODUCT is protected by copyright laws and international copyright treaties, as well
as other intellectual property laws and treaties. This is a license agreement and NOT an agreement for sale. All title and
copyrights in and to the SOFTWARE PRODUCT (including but not limited to any images, photographs, animations, video, audio,
music, text, and applets incorporated into the SOFTWARE PRODUCT), the accompanying printed materials, and any copies of the
SOFTWARE PRODUCT are owned by WATCHGUARD or its licensors. Your rights to use the SOFTWARE PRODUCT are as specified
in this AGREEMENT, and WATCHGUARD retains all rights not expressly granted to you in this AGREEMENT. Nothing in this
AGREEMENT constitutes a waiver of our rights under U.S. copyright law or any other law or treaty.
2. Permitted Uses. You are granted the following rights to the SOFTWARE PRODUCT:
(A) You may install and use the SOFTWARE PRODUCT on any single WATCHGUARD hardware product at any single location
and may install and use the SOFTWARE PRODUCT on multiple workstation computers.
(B) To use the SOFTWARE PRODUCT on more than one WATCHGUARD hardware product at once, you must purchase an
additional copy of the SOFTWARE PRODUCT for each additional WATCHGUARD hardware product which you want to use it. To
the extent that you install copies of the SOFTWARE PRODUCT on additional WATCHGUARD hardware products in accordance
with the prior sentence without installing the additional copies of the SOFTWARE PRODUCT included with such WATCHGUARD
hardware products, you agree that use of any software provided with or included on the additional WATCHGUARD hardware
products that does not require installation will be subject to the terms and conditions of this AGREEMENT. You must also
maintain a current subscription to the WatchGuard LiveSecurity Service (or its equivalent) for each additional WATCHGUARD
hardware product on which you will use a copy of an updated or modified version of the SOFTWARE PRODUC T received through
the WatchGuard LiveSecurity Service (or its equivalent).
(C) In addition to the copies described in Section 2(A), you may make a single copy of the SOFTWARE PRODUCT for backup or
archival purposes only.
3. Prohibited Uses. You may not, without express written permission from WATCHGUARD:
ii Firebox X Edge e-Series

(A) Use, copy, modify, merge or transfer copies of the SOFTWARE PRODUCT or printed materials except as provided in this
AGREEMENT;
(B) Use any backup or archival copy of the SOFTWARE PRODUCT (or allow someone else to use such a copy) for any purpose
other than to replace the original copy in the event it is destroyed or becomes defective;
(C) Sublicense, lend, lease or rent the SOFTWARE PRODUCT;
(D) Transfer this license to another party unless
(i) the transfer is permanent,
(ii) the third party recipient agrees to the terms of this AGREEMENT, and
(iii) you do not retain any copies of the SOFTWARE PRODUCT; or
(E) Reverse engineer, disassemble or decompile the SOFTWARE PRODUCT.
4. Limited Warranty. WATCHGUARD makes the following limited warranties for a period of ninety (90) days from the date you
obtained the SOFTWARE PRODUCT from WATCHGUARD or an authorized dealer:
(A) Media. The disks and documentation will be free from defects in materials and workmanship under normal use. If the disks or
documentation fail to conform to this warranty, you may, as your sole and exclusive remedy, obtain a replacement free of
charge if you return the defective disk or documentation to WATCHGUARD with a dated proof of purchase.
(B) SOFTWARE PRODUCT. The SOFTWARE PRODUCT will materially conform to the documentation that accompanies it. If the
SOFTWARE PRODUCT fails to operate in accordance with this warranty, you may, as your sole and exclusive remedy, return all of
the SOFTWARE PRODUCT and the documentation to the authorized dealer from whom you obtained it, along with a dated proof
of purchase, specifying the problems, and they will provide you with a new version of the SOFTWARE PRODUCT or a full refund,
at their election.
Disclaimer and Release. THE WARRANTIES, OBLIGATIONS AND LIABILITIES OF WATCHGUARD, AND YOUR REMEDIES, SET FORTH
IN PARAGRAPHS 4, 4(A) AND 4(B) ABOVE ARE EXCLUSIVE AND IN SUBSTITUTION FOR, AND YOU HEREBY WAIVE, DISCLAIM AND
RELEASE ANY AND ALL OTHER WARRANTIES, OBLIGATIONS AND LIABILITIES OF WATCHGUARD AND ITS LICENSORS AND ALL
OTHER RIGHTS, CLAIMS AND REMEDIES YOU MAY HAVE AGAINST WATCHGUARD AND ITS LICENSORS, EXPRESS OR IMPLIED,
ARISING BY LAW OR OTHERWISE, WITH RESPECT TO ANY NONCONFORMANCE OR DEFECT IN THE SOFTWARE PRODUCT
(INCLUDING, BUT NOT LIMITED TO, ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE,
ANY IMPLIED WARRANTY ARISING FROM COURSE OF PERFORMANCE, COURSE OF DEALING, OR USAGE OF TRADE, ANY
WARRANTY OF NONINFRINGEMENT, ANY WARRANTY THAT THE SOFTWARE PRODUCT WILL MEET YOUR REQUIREMENTS, ANY
WARRANTY OF UNINTERRUPTED OR ERROR-FREE OPERATION, ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR REMEDY IN TORT,
WHETHER OR NOT ARISING FROM THE NEGLIGENCE (WHETHER ACTIVE, PASSIVE OR IMPUTED) OR FAULT OF WATCHGUARD
AND ITS LICENSORS AND ANY OBLIGATION, LIABILITY, RIGHT, CLAIM OR REMEDY FOR LOSS OR DAMAGE TO, OR CAUSED BY OR
CONTRIBUTED TO BY, THE SOFTWARE PRODUCT).
Limitation of Liability. WATCHGUARD'S LIABILITY (WHETHER IN CONTRACT, TORT, OR OTHERWISE; AND NOTWITHSTANDING
ANY FAULT, NEGLIGENCE, STRICT LIABILITY OR PRODUCT LIABILITY) WITH REGARD TO THE SOFTWARE PRODUCT WILL IN NO
EVENT EXCEED THE PURCHASE PRICE PAID BY YOU FOR SUCH PRODUCT. THIS SHALL BE TRUE EVEN IN THE EVENT OF THE
FAILURE OF AN AGREED REMEDY. IN NO EVENT WILL WATCHGUARD BE LIABLE TO YOU OR ANY THIRD PARTY, WHETHER
ARISING IN CONTRACT (INCLUDING WARRANTY), TORT (INCLUDING ACTIVE, PASSIVE OR IMPUTED NEGLIGENCE AND STRICT
LIABILITY AND FAULT), FOR ANY INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES (INCLUDING WITHOUT
LIMITATION LOSS OF BUSINESS PROFITS, BUSINESS INTERRUPTION, OR LOSS OF BUSINESS INFORMATION) ARISING OUT OF OR
IN CONNECTION WITH THIS WARRANTY OR THE USE OF OR INABILITY TO USE THE SOFTWARE PRODUCT, EVEN IF WATCHGUARD
HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. THIS SHALL BE TRUE EVEN IN THE EVENT OF THE FAILURE OF AN
AGREED REMEDY.
5. United States Government Restricted Rights. The SOFTWARE PRODUCT is provided with Restricted Rights. Use, duplication or
disclosure by the U.S. Government or any agency or instrumentality thereof is subject to restrictions as set forth in subdivision
(c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013, or in subdivision (c)(1) and (2) of
the Commercial Computer Software -- Restricted Rights Clause at 48 C.F.R. 52.227-19, as applicable. Manufacturer is WatchGuard
Technologies, Inc., 505 5th Ave. South, Suite 500, Seattle, WA 98104.
6. Export Controls. You agree not to directly or indirectly transfer the SOFTWARE PRODUCT or documentation to any country to
which such transfer would be prohibited by the U.S. Export Administration Act and the regulations issued thereunder.
7. Termination. This license and your right to use the SOFTWARE PRODUCT will automatically terminate if you fail to comply with
any provisions of this AGREEMENT, destroy all copies of the SOFTWARE PRODUCT in your possession, or voluntarily return the
SOFTWARE PRODUCT to WATCHGUARD. Upon termination you will destroy all copies of the SOFTWARE PRODUCT and
documentation remaining in your control or possession.
8. Miscellaneous Provisions. This AGREEMENT will be governed by and construed in accordance with the substantive laws of
Washington excluding the 1980 United National Convention on Contracts for the International Sale of Goods, as amended. This
is the entire AGREEMENT between us relating to the SOFTWARE PRODUCT, and supersedes any prior purchase order,
communications, advertising or representations concerning the SOFTWARE PRODUCT AND BY USING THE SOFTWARE PRODUCT
YOU AGREE TO THESE TERMS. IF THE SOFTWARE PRODUCT IS BEING USED BY AN ENTITY, THE INDIVIDUAL INDICATING
AGREEMENT TO THESE TERMS REPRESENTS AND WARRANTS THAT (A) SUCH INDIVIDUAL IS DULY AUTHORIZED TO ACCEPT THIS
AGREEMENT ON BEHALF OF THE ENTITY AND TO BIND THE ENTITY TO THE TERMS OF THIS AGREEMENT; (B) THE ENTITY HAS THE
FULL POWER, CORPORATE OR OTHERWISE, TO ENTER INTO THIS AGREEMENT AND PERFORM ITS OBLIGATIONS UNDER THIS
User Guide iii

AGREEMENT AD// (C) THIS AGREEMENT AND THE PERFORMANCE OF THE ENTITY’S OBLIGATIONS UNDER THIS AGREEMENT DO
NOT VIOLATE ANY THIRD-PARTY AGREEMENT TO WHICH THE ENTITY IS A PARTY. No change or modification of this AGREEMENT
will be valid unless it is in writing and is signed by WATCHGUARD.
Firmware Version: 8.6
Guide Version: 8.6
354-2540-005
Abbreviations Used in this Guide
3DES Triple Data Encryption Standard
BOVPN Branch Office Virtual Private Network
DES Data Encryption Standard
DNS Domain Name Service
DHCP Dynamic Host Configuration
Protocol
DSL Digital Subscriber Line
IP Internet Protocol
IPSec Internet Protocol Security
ISDN Integrated Services Digital Network
ISP Internet Service Provider
MAC Media Access Control
MUVPN Mobile User Virtual Private Network
NAT Network Address Translation
PPP Point-to-Point Protocol
PPPoE Point-to-Point Protocol over
Ethernet
TCP Transfer Control Protocol
UDP User Datagram Protocol
URL Universal Resource Locator
VPN Virtual Private Network
WAN Wide Area Network
WSM WatchGuard System Manager
iv Firebox X Edge e-Series

Contents
1 Introduction to Network Security
Network Security .....................................................................................................1
About Networks .......................................................................................................1
Clients and servers ..................................................................................................2
Connecting to the Internet ......................................................................................2
Protocols .................................................................................................................2
How Information Travels on the Internet ................................................................2
IP Addresses ...........................................................................................................3
Network addressing .................................................................................................4
About DHCP ...........................................................................................................4
About PPPoE ..........................................................................................................4
Default gateway ......................................................................................................4
Domain Name Service (DNS) .................................................................................4
Services and Policies ..............................................................................................4
Ports ........................................................................................................................5
Firewalls ..................................................................................................................6
The Firebox X Edge and Your Network ..................................................................7
2 Installation
Installation Requirements .......................................................................................9
Package Contents ...................................................................................................9
Registering Your Firebox & Activating LiveSecurity Service ................................10
Identifying Your Network Settings .........................................................................11
About network addressing ......................................................................................11
Static addresses, DHCP, and PPPoE ......................................................................11
TCP/IP properties ..................................................................................................12
PPPoE settings .....................................................................................................13
Web Browser HTTP Proxy Settings .....................................................................13
Web Browser Pop-up Blocking Settings ...............................................................14
Connecting the Firebox X Edge ............................................................................15
Connecting the Edge to more than four devices ......................................................16
About user licenses ...............................................................................................17
Setting Your Computer to Connect to the Edge ...................................................17
Using DHCP .........................................................................................................17
Using a static IP address .......................................................................................18
Using the Quick Setup Wizard ..............................................................................19
3 Navigation
Connecting to the Firebox X Edge ........................................................................21
User Guide v

Navigating the Firebox X Edge User Interface .....................................................22
System Status page ...............................................................................................23
Network page ........................................................................................................23
Firebox Users page ...............................................................................................24
Administration page ...............................................................................................25
Firewall page ........................................................................................................26
Logging page ........................................................................................................27
WebBlocker page ..................................................................................................27
spamBlocker page .................................................................................................28
GAV/IPS page .......................................................................................................28
VPN page .............................................................................................................29
Wizards page ........................................................................................................29
Monitoring the Firebox X Edge .............................................................................30
ARP Table ............................................................................................................30
Authentications .....................................................................................................31
Connections ..........................................................................................................31
Components List ...................................................................................................32
DHCP Leases .......................................................................................................32
Disk Usage ...........................................................................................................32
Dynamic DNS .......................................................................................................33
Hostile Sites ..........................................................................................................33
Interfaces .............................................................................................................33
License .................................................................................................................33
Memory ................................................................................................................34
Processes .............................................................................................................34
Protocols ..............................................................................................................34
Routes ..................................................................................................................34
Security Services ..................................................................................................35
Syslog ..................................................................................................................35
Traffic Control .......................................................................................................35
VPN Statistics .......................................................................................................36
Wireless Statistics .................................................................................................36
4 Configuration and Management Basics
Factory Default Settings .......................................................................................37
Restoring the Firebox to the factory default settings .................................................38
Restarting the Firebox ...........................................................................................38
Local restart ..........................................................................................................39
Remote restart ......................................................................................................39
Setting the System Time .......................................................................................39
Enabling the Edge for SNMP Polling ....................................................................41
Using MIBs ...........................................................................................................42
Selecting HTTP or HTTPS for Management ........................................................42
Changing the HTTP server port ..............................................................................43
Setting up WatchGuard System Manager Access ...............................................43
Renaming the Firebox X Edge e-Series ..................................................................44
Enabling centralized management with WSM v9.1 ...................................................44
Enable remote management with WFS v7.3 or earlier ..............................................45
Allowing Traffic From A Management Server .......................................................46
Updating the Firebox X Edge Software ................................................................47
Method 1: Installing software automatically .............................................................47
vi Firebox X Edge e-Series

Method 2: Installing software manually ...................................................................47
Activating Upgrade Options ..................................................................................48
Upgrade options ....................................................................................................48
Adding a feature to your Firebox X Edge .................................................................49
Enabling the Model Upgrade Option ....................................................................50
Viewing the Configuration File ..............................................................................50
5 Network Settings
Using the Network Setup Wizard ..........................................................................53
Configuring the External Network .........................................................................54
If your ISP uses DHCP ..........................................................................................54
If your ISP uses static IP addresses ........................................................................55
If your ISP uses PPPoE .........................................................................................56
External network advanced settings .......................................................................57
Configuring the Trusted Network ..........................................................................59
Changing the IP address of the trusted network ......................................................59
Using DHCP on the trusted network .......................................................................60
Setting trusted network DHCP address reservations ................................................61
Configuring the trusted network for DHCP relay ......................................................61
Using static IP addresses for trusted computers ......................................................62
Adding computers to the trusted network ................................................................62
Allowing wireless connections to the trusted interface ..............................................63
Restricting access to the Edge trusted interface by MAC address .............................63
Configuring the Optional Network .........................................................................65
Enabling the optional network ................................................................................65
Using DHCP on the optional network ......................................................................66
Setting optional network DHCP address reservations ..............................................67
Configuring the optional network for DHCP relay .....................................................67
Using static IP addresses for optional computers .....................................................68
Adding computers to the optional network ...............................................................68
Allowing wireless connections to the optional interface ............................................68
Restricting access to the Edge optional interface by MAC address ...........................69
Making Static Routes ............................................................................................69
Using slash notation ..............................................................................................69
Making a static route .............................................................................................70
Registering with the Dynamic DNS Service .........................................................70
Using the WAN Failover Option ............................................................................72
Understanding WAN Failover .................................................................................72
WAN Failover and DNS .........................................................................................73
Configuring WAN Failover with a Second Broadband Connection .............................73
Configuring the Edge for Serial Modem Failover ......................................................76
Configuring your Modem for WAN Failover .............................................................77
Configuring BIDS ..................................................................................................79
6 Firebox X Edge e-Series Wireless Setup
Installing the Firebox X Edge e-Series Wireless ..................................................81
Understanding Wireless Configuration Settings ...................................................82
Setting the SSID ...................................................................................................82
Controlling SSID broadcasts ..................................................................................83
Logging authentication events ................................................................................83
User Guide vii

Setting the fragmentation threshold ........................................................................83
Setting the RTS threshold ......................................................................................83
Configuring Wireless Security Settings ................................................................83
Setting the wireless authentication method .............................................................84
Configuring encryption ...........................................................................................84
Allowing Wireless Connections to the Trusted Interface ......................................85
Allowing Wireless Connections to the Optional Interface ....................................86
Enabling a Wireless Guest Network .....................................................................87
Configuring Wireless Radio Settings ....................................................................88
Setting the operating region and channel ................................................................88
Setting the wireless mode of operation ...................................................................89
Configuring the Wireless Card on Your Computer ...............................................89
7 Firewall Policies
Understanding Policies .........................................................................................91
Incoming and outgoing traffic .................................................................................92
Policy rules ...........................................................................................................92
Precedence ..........................................................................................................92
Enabling Common Packet Filter Policies .............................................................93
Editing Common Packet Filter Policies ................................................................94
Incoming settings ..................................................................................................95
Outgoing settings ..................................................................................................96
Configuring Custom Packet Filter Policies ...........................................................96
Adding a custom policy using the wizard .................................................................97
Adding a custom packet filter policy manually ..........................................................97
Filtering incoming traffic for a custom policy ............................................................98
Filtering outgoing traffic for a custom policy .............................................................99
Configuring Policies for the Optional Network ....................................................100
Controlling traffic from the trusted to optional network ............................................100
Disabling traffic filters between trusted and optional networks ................................101
8 Proxy Settings
Proxy Policies ......................................................................................................103
Understanding the HTTP proxy ............................................................................103
Understanding the FTP proxy ...............................................................................104
Understanding the POP3 proxy ............................................................................104
Understanding the SMTP proxy ............................................................................104
Creating proxy policies ........................................................................................104
Using the HTTP Proxy ........................................................................................105
Configuring the HTTP Proxy ...............................................................................105
Setting access control options ..............................................................................106
Setting proxy limits ..............................................................................................106
Filtering web content ...........................................................................................109
Using the FTP Proxy ...........................................................................................111
Configuring the FTP Proxy .................................................................................112
Setting access control options ..............................................................................112
Setting proxy limits ..............................................................................................113
Filtering content ..................................................................................................114
Using the POP3 Proxy ........................................................................................115
viii Firebox X Edge e-Series

Configuring the POP3 Proxy ...............................................................................116
Setting access control options ..............................................................................117
Setting proxy limits ..............................................................................................117
Filtering email content .........................................................................................119
Using the SMTP Proxy .......................................................................................120
Configuring the SMTP Proxy ..............................................................................120
Setting access control options ..............................................................................121
Setting proxy limits ..............................................................................................121
Deny Message ....................................................................................................122
Filtering email by address pattern .........................................................................123
Filtering email content .........................................................................................123
Adding a Custom Proxy Policy ...........................................................................125
Adding a custom SMTP proxy policy .....................................................................126
Using Additional Services for Proxies ................................................................126
Gateway AntiVirus/Intrusion Prevention Service ....................................................126
WebBlocker ........................................................................................................126
spamBlocker .......................................................................................................126
9 Intrusion Prevention
Adding a Site to the Permanent Blocked Sites List ............................................127
Blocking Sites Temporarily ..................................................................................128
Blocking Ports .....................................................................................................129
Avoiding problems with blocked ports ...................................................................130
Adding a port to the blocked ports list ...................................................................130
Preventing Denial-of-Service Attacks .................................................................131
Dropping Flood Attacks .......................................................................................131
Distributed Denial-of-Service Prevention ...............................................................132
Configuring Firewall Options ...............................................................................133
10 Traffic Management
About Network Traffic ..........................................................................................135
Causes for slow network traffic .............................................................................135
Traffic Categories ................................................................................................136
Interactive traffic ..................................................................................................136
High priority ........................................................................................................136
Medium priority ...................................................................................................136
Low priority .........................................................................................................136
Traffic Marking .....................................................................................................136
Configuring Traffic Control ..................................................................................138
Enabling traffic control .........................................................................................139
Adding a traffic control filter ..................................................................................140
Editing a traffic control filter ..................................................................................141
Changing the priority of a traffic control filter ..........................................................142
Removing a traffic control filter .............................................................................142
Working with Firewall NAT ..................................................................................142
NAT types ...........................................................................................................142
NAT behavior ......................................................................................................143
Secondary IP addresses ......................................................................................143
Using 1-to-1 NAT .................................................................................................143
User Guide ix

11 Logging and Certificates
Viewing Log Messages .......................................................................................147
Logging to a WatchGuard Log Server ................................................................148
Logging to a Syslog Host ....................................................................................149
About Certificates ................................................................................................150
Creating a certificate or signing request ................................................................150
Using OpenSSL to Generate a CSR ..................................................................150
Using Microsoft CA to Create a Certificate .........................................................151
Sending the certificate request .............................................................................151
Issuing the certificate ...........................................................................................151
Downloading the certificate ..................................................................................152
Using Certificates on the Firebox X Edge ..........................................................152
Importing a certificate ..........................................................................................152
Removing a certificate .........................................................................................152
Examining a certificate .........................................................................................153
12 User and Group Management
About User Licenses ...........................................................................................155
When a user license is used ................................................................................156
When a user license is not used ...........................................................................156
About User Authentication ..................................................................................156
Setting authentication options for all users ............................................................156
Using Local Firebox Authentication ....................................................................158
Configuring an individual user account ..................................................................158
Authenticating to the Edge ...................................................................................159
Setting a WebBlocker profile for a user .................................................................161
Changing a user account name or password .........................................................161
Using LDAP/Active Directory Authentication ......................................................162
Configuring the LDAP/Active Directory authentication service ................................162
Using the LDAP authentication test feature ...........................................................164
Configuring groups for LDAP authentication ..........................................................164
Adding a group ...................................................................................................164
Setting a WebBlocker profile for a group ...............................................................165
LDAP authentication and MUVPN ........................................................................166
Seeing Current Sessions and Users ..................................................................166
Firebox Users settings .........................................................................................166
Active Sessions ...................................................................................................166
Stopping a session ..............................................................................................166
Local User Accounts ............................................................................................167
Allowing Internal Devices to Bypass User Authentication ..................................168
13 WebBlocker
How WebBlocker Works .....................................................................................169
Configuring Global WebBlocker Settings ...........................................................169
Creating WebBlocker Profiles .............................................................................171
WebBlocker Categories ......................................................................................173
Determining a category ........................................................................................180
Adding, removing, or changing a web site category ...............................................180
Allowing Certain Sites to Bypass WebBlocker ...................................................181
x Firebox X Edge e-Series

Blocking Additional Web Sites ............................................................................182
Bypassing WebBlocker .......................................................................................183
14 spamBlocker
Understanding How spamBlocker Works ...........................................................185
spamBlocker categories .......................................................................................186
spamBlocker actions ...........................................................................................186
spamBlocker exceptions ......................................................................................186
Configuring spamBlocker ....................................................................................186
Enabling spamBlocker .........................................................................................187
Configuring spamBlocker Settings .....................................................................187
Creating exceptions .............................................................................................188
Adding Trusted Email Forwarders .........................................................................189
Configuring Rules For Your Email Reader .........................................................189
Sending spam or bulk email to special folders in Outlook .......................................189
15 Gateway AntiVirus and Intrusion Prevention Service
Understanding Gateway AntiVirus Settings .......................................................191
Understanding Intrusion Prevention Service Settings ........................................192
Configuring Gateway AV/IPS ..............................................................................192
Gateway AntiVirus settings ..................................................................................193
Intrusion Prevention Service settings ....................................................................194
POP3 proxy deny messages and Gateway AV/IPS ................................................194
Updating Gateway AV/IPS ..................................................................................194
16 Branch Office Virtual Private Networks
About This Chapter .............................................................................................197
What You Need to Create a VPN .......................................................................197
About VPN Failover ............................................................................................198
Managed VPNs ...................................................................................................199
Manual VPN: Setting Up Manual VPN Tunnels .................................................199
What you need for Manual VPN ...........................................................................199
To create Manual VPN tunnels on your Edge ........................................................201
Phase 1 settings .................................................................................................201
Phase 2 settings .................................................................................................204
VPN Traffic Control .............................................................................................205
VPN Keep Alive ..................................................................................................205
Viewing VPN Statistics ........................................................................................206
Frequently Asked Questions ...............................................................................206
17 Mobile User Virtual Private Networks
Configuring IPSec Mobile User VPN ..................................................................209
Using IPSec MUVPN ...........................................................................................210
Configuring MUVPN client settings .......................................................................210
Enabling MUVPN access for a Firebox user account .............................................212
Distributing the software and the .wgx file .............................................................213
Preparing remote computers for IPSec MUVPN ....................................................214
Windows 2000 setup ...........................................................................................215
Windows XP setup ..............................................................................................216
User Guide xi

Installing and configuring the IPSec MUVPN client ................................................218
Connecting and disconnecting the IPSec MUVPN client ........................................220
Monitoring the IPSec MUVPN Client Connection ...................................................221
The ZoneAlarm Personal Firewall .........................................................................222
Using IPSec MUVPN on a Firebox X Edge e-Series Wireless network ....................224
Troubleshooting Tips ...........................................................................................224
Configuring PPTP Mobile User VPN ..................................................................226
Enabling PPTP ....................................................................................................226
Enabling PPTP access for firewall users ...............................................................228
Preparing the client computers .............................................................................228
Using PPTP and Accessing the Internet ................................................................230
A Firebox X Edge e-Series Hardware
Package Contents ...............................................................................................231
Specifications ......................................................................................................232
Hardware Description .........................................................................................233
Front panel .........................................................................................................233
Rear view ...........................................................................................................234
Side panels .........................................................................................................234
AC power adapter ...............................................................................................235
About the Firebox X Edge e-Series Wireless. ....................................................235
Antenna directional gain ......................................................................................235
Signal attenuation ...............................................................................................236
Channel data rate ................................................................................................236
B Legal Notifications
Copyright, Trademark, and Patent Information ..................................................237
Certifications and Notices ...................................................................................284
Declaration of Conformity ...................................................................................288
Limited Hardware Warranty ................................................................................288
xii Firebox X Edge e-Series

1
Introduction to Network Security
Thank you for your purchase of the WatchGuard® Firebox® X Edge e-Series. This security device helps
protect your computer network from threat and attack.
This chapter gives you basic information about networks and network security. This information can
help you when you configure the Firebox X Edge. If you are experienced with computer networks, we
recommend that you go to the subsequent chapter.
Network Security
Although the Internet gives you access to a large quantity of information and business opportunity, it
also opens your network to attackers. A good network security policy helps you find and prevent
attacks to your computer or network.
Attacks are costly. Computers may need to be repaired or replaced. Employee time and resources are
used to fix problems created by attacks. Valuable information can be taken from the network.
Many people think that their computer holds no important information. They do not think that their
computer is a target for a hacker. This is not correct. A hacker can use your computer as a platform to
attack other computers or networks or use your account information to send email spam or attacks.
Your personal information and account information is also vulnerable and valuable to hackers.
About Networks
A network is a group of computers and other devices that are connected to each other. It can be two
computers that you connect with a serial cable, or many computers around the world connected
through the Internet. Computers on the same network can work together and share data.
A LAN (Local Area Network) is a connected group of computers that use the same method of communication to share data.
A WAN (Wide Area Network) is a connected group of computers that can be far apart in different loca-
tions.
User Guide 1

Connecting to the Internet
Clients and servers
Clients and servers are components of a network. A server makes its resources available to the network.
Some of these resources are documents, printers, and programs. A client uses the resources made
available by the server. A computer can be a server or a client, or it can be a server for some functions
and a client for other functions.
Connecting to the Internet
ISPs (Internet service providers) are companies that give access to the Internet through network connections. Bandwidth is the rate at which a network connection can send data: for example, 3 megabits
per second (Mbps).
A high-speed Internet connection, such as a cable modem or a DSL (Digital Subscriber Line), is known
as a broadband connection. Broadband connections are much faster than dial-up connections. The
bandwidth of a dial-up connection is less than .1 Mbps, while a cable modem can be 5 Mbps or more.
Typical speeds for cable modems are usually lower than the maximum speeds, because each computer
in a neighborhood is a member of a LAN. Each computer in that LAN uses some of the bandwidth.
Because of this “shared-medium” system, cable modem connections can become slow when more
users are on the network.
DSL connections supply constant bandwidth, but they are usually slower than cable modem connections. Also, the bandwidth is only constant between your home or office and the DSL central office. The
DSL central office cannot guarantee a constant connection bandwidth to a web site or network.
Protocols
A protocol is a group of rules that allow computers to connect across a network. Protocols are the
“grammar” of the language that computers use when they speak to each other across a network.
The standard protocol when you connect to the Internet is the IP (Internet Protocol). This protocol is
the usual language of computers on the Internet.
A protocol also tells how data is sent through a network. The most frequently used protocols are TCP
(Transmission Control Protocol) and UDP (User Datagram Protocol).
TCP/IP is the basic protocol used by computers that connect to the Internet. You must know some settings of TCP/IP when you set up your Firebox® X Edge. For more information on TCP/IP, see “Finding
your TCP/IP properties” on page 15.
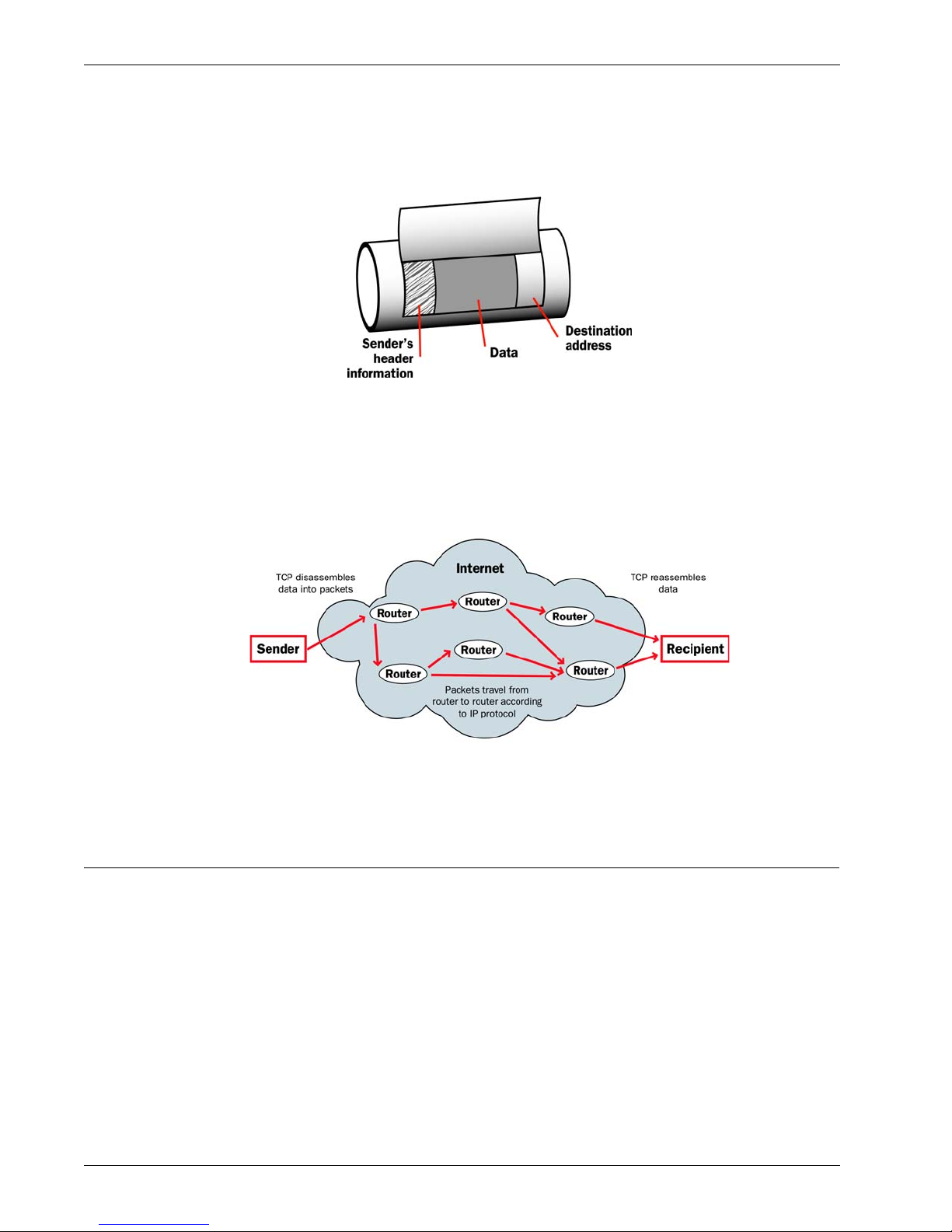
How Information Travels on the Internet
The data that you send through the Internet is cut into units, or packets. Each packet includes the Internet address of the destination. The packets that make up a connection can use different routes
through the Internet. When they all get to their destination, they are assembled back into the original
2 Firebox X Edge e-Series
IP Addresses
order. To make sure that the packets get to the destination, address information is added to the packets.
Data packet
The TCP and IP protocols are used to send and receive these packets. TCP disassembles the data and
assembles it again. IP adds information to the packets, such as the sender, the recipient, and any special instructions.
IP Addresses
To send ordinary mail to a person, you must first know his or her street address. For one computer to
send data to a different computer, it must first know the address of that computer. A computer address
is known as an IP address. Only one device can use an IP address at a time.
An IPv4 address is commonly referred to in dotted decimal format contained within four octets, separated by periods. Some examples of IP addresses are:
• 192.168.0.11
• 10.1.20.18
• 208.15.15.15
User Guide 3
Packets traveling on the Internet

Domain Name Service (DNS)
Network addressing
ISPs (Internet service providers) assign an IP address to each device on their network. The IP address
can be static or dynamic. Each ISP has a small number of IP addresses.
Static IP addresses are permanently assigned to a device. These addresses do not change automatically, and are frequently used for servers.
Dynamic IP addresses are assigned automatically and can change with time. If a dynamic address is not
in use, it can be automatically assigned to a different device.
Your ISP can tell you how their system assigns IP addresses.
About DHCP
Many ISPs assign dynamic IP addresses through DHCP (Dynamic Host Configuration Protocol). When a
computer connects to the network, a DHCP server at the ISP automatically assigns that computer an IP
address. It is not necessary to assign IP addresses manually when you use DHCP.
About PPPoE
Some ISPs assign their IP addresses through Point-to-Point Protocol over Ethernet (PPPoE). PPPoE
expands a standard dial-up connection to add some of the features of Ethernet and PPP. This network
protocol allows the ISP to use the billing, authentication, and security systems of their dial-up infrastructure with DSL modem and cable modem products.
Default gateway
A default gateway is a node on a computer network that serves as an access point to another network.
Usually, the default gateway address is the IP address of the router that is between your network and
the Internet. After you install the Firebox X Edge on your network, the Edge acts as the default gateway
for all computers connected to its trusted or optional interfaces.
Domain Name Service (DNS)
If you do not know the address of a person, you can frequently find it in the telephone directory. On the
Internet, the equivalent to a telephone directory is the DNS (Domain Name Service). Each web site has
a domain name (such as “mysite.com”) that maps to an IP address. When you type a domain name to
show a web site, your computer gets the IP address from a DNS server.
A URL (Uniform Resource Locator) includes a domain name and a protocol. An example of a URL is:
http://www.watchguard.com/
In summary, the DNS is the system that translates Internet domain names into IP addresses. A DNS
server is a server that performs this translation.
Services and Policies
You use a service to send different types of data (such as email, files, or commands) from one computer
to another across a network or to a different network. These services use protocols. Frequently used
Internet services are:
• World Wide Web access uses Hypertext Transfer Protocol (HTTP)
4 Firebox X Edge e-Series
Ports
Ports
• Email uses Simple Mail Transfer Protocol (SMTP) or Post Office Protocol (POP3 v3)
• File transfer uses File Transfer Protocol (FTP)
• Resolving a domain name to an Internet address uses Domain Name Service (DNS)
• Remote terminal access uses Telnet or SSH (Secure Shell)
When you allow or deny a service, you must add a policy to your Firebox X Edge configuration. Each
policy you add can also add a security risk. To send and receive data, you must “open a door” in your
computer, which puts your network at risk. We recommend that you add only the policies that are necessary for your business.
Usually, a port is a connection point where you use a jack and cables to connect devices. Computers
also have ports that are not physical locations. These ports are where programs transmit data.
Some protocols, such as HTTP, have ports with assigned numbers. For example, many computers
transmit email on port 110 because the POP3 protocol is assigned to port 110. Other programs are
assigned port numbers dynamically for each connection. The IANA (Internet Assigned Numbers
Authority) keeps a list of well known ports. You can see this list at:
www.iana.org/assignments/port-numbers
Most policies are given a port number in the range from 0 to 1024, but possible port numbers range
from 0 to 65535.
User Guide 5
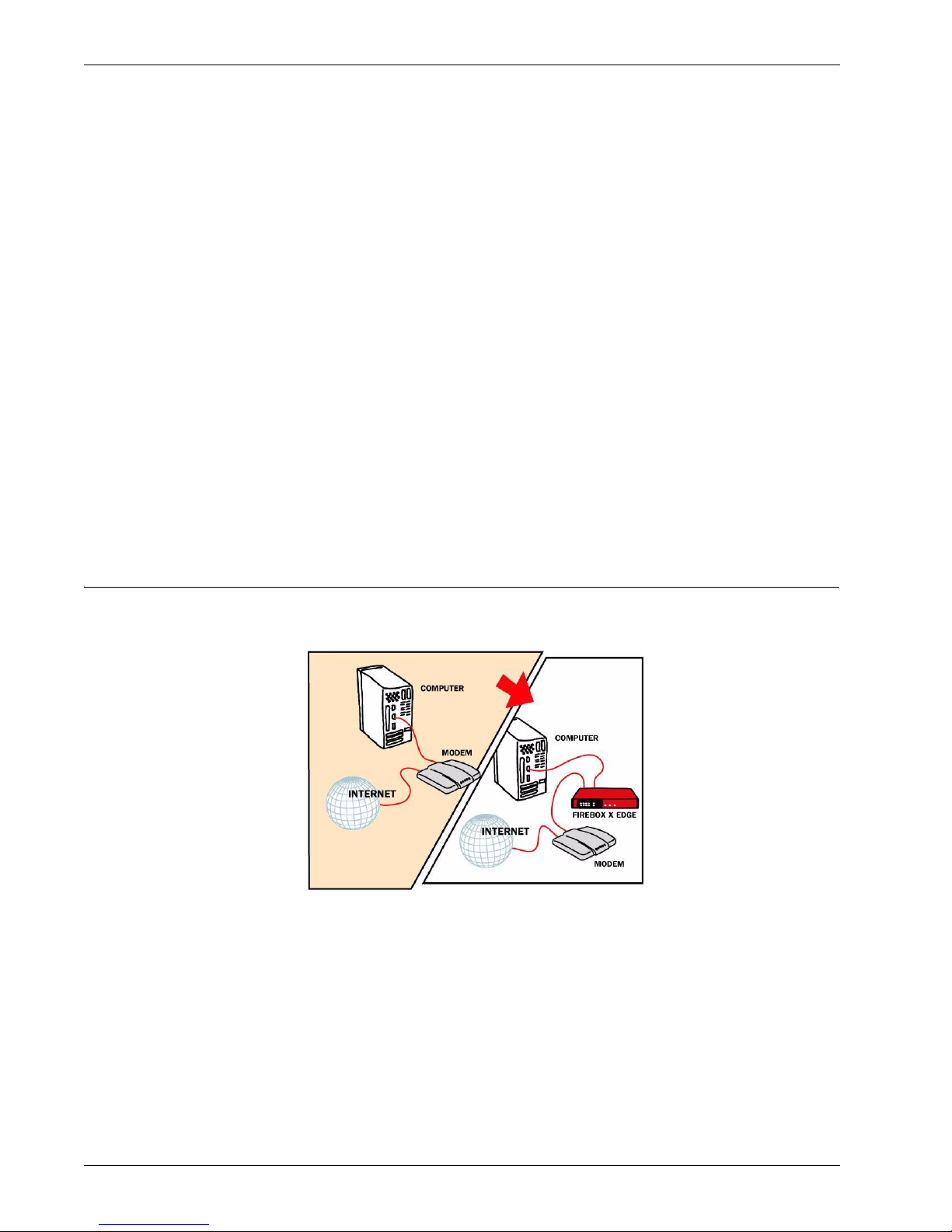
Firewalls
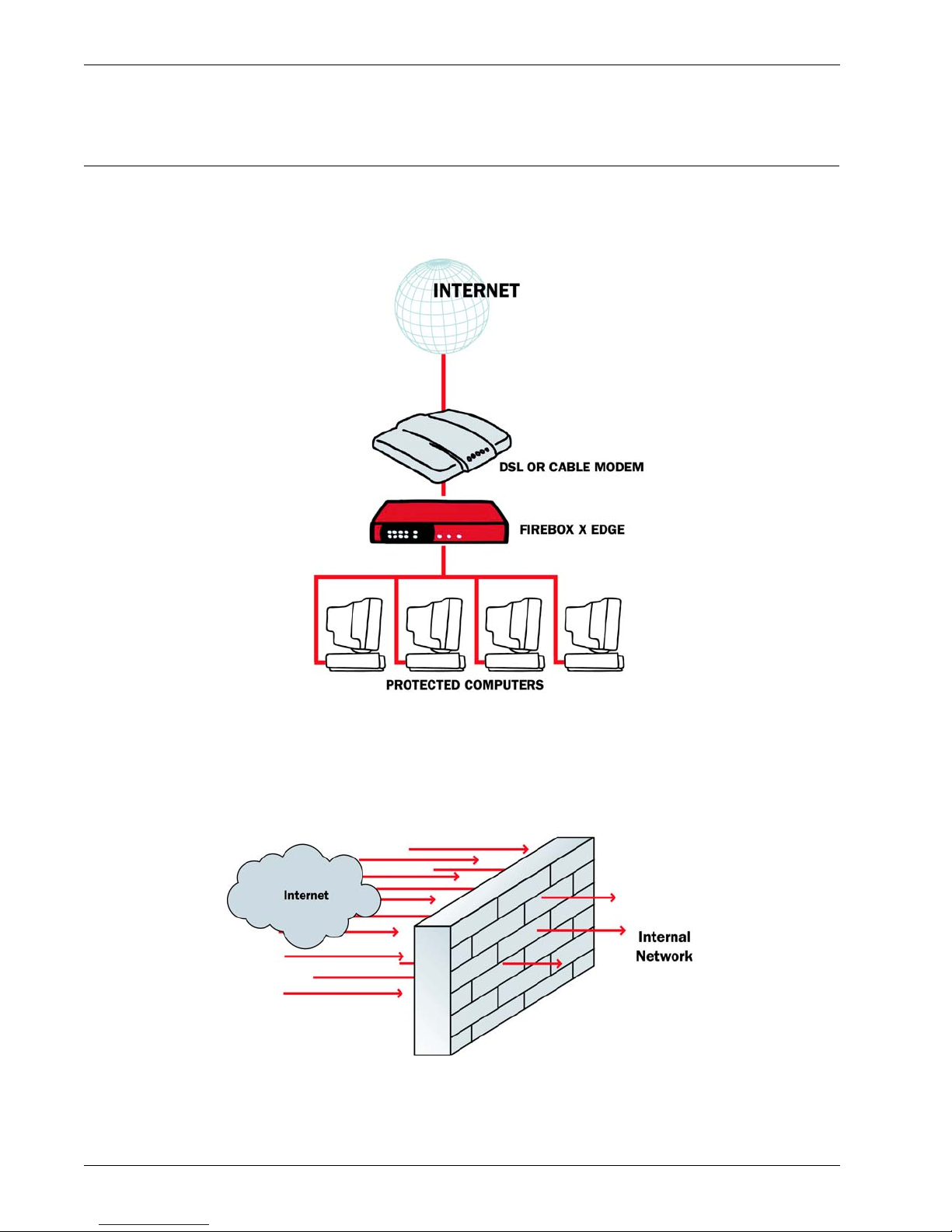
Firewalls
A firewall separates your trusted computers on the internal network from the external network, or the
Internet, to decrease risk of an external attack. The figure below shows how a firewall divides the
trusted computers from the Internet.
Firewalls use access policies to identify and filter different types of information. They can also control
which policies or ports the protected computers can use on the Internet (outbound access). Many firewalls have sample security policies, and users can select the policy that is best for them. With others,
including the Firebox® X Edge e-Series, the user can customize these policies.
Firewalls can be in the form of hardware or software. A firewall protects private networks from
unauthorized users on the Internet. All traffic that enters the trusted or protected networks must
6 Firebox X Edge e-Series

go through the firewall. The firewall examines each message and denies those that do not match
the security criteria or policies.
In some closed, or “default-deny” firewalls, all network connections are denied unless there is a
specific rule to allow the connection. To deploy this type of firewall, you must have detailed
information about the network applications required to meet your organization’s needs. Other
firewalls allow all network connections that have not been explicitly denied. This type of open
firewall is easier to deploy, but it is not as secure.
The Firebox X Edge and Your Network
The Firebox® X Edge controls all traffic between the external network and the trusted network. The
Edge also includes an optional network interface that is separate from the trusted network. Use the
optional network for computers with “mixed trust.” For example, customers frequently use the
optional network for their remote users or for public servers such as a web server or email server. Your
firewall can stop all suspicious traffic from the external network to your trusted and optional networks.
The rules and policies that identify the suspicious traffic appear in “Firewall Policies” on page 91.
The Firebox X Edge e-Series is a firewall for small and remote offices. Some customers who purchase an
Edge do not know much about computer networks or network security. The Edge provides wizards
and many self-help tools for these customers. Advanced customers can use integration features to
connect an Edge to a larger wide area network. The Edge connects to a cable modem, DSL modem, or
ISDN router.
The Firebox X Edge and Your Network
The web-based user interface of the Firebox X Edge lets you manage your network safely. You can
manage your Edge from different locations and at different times. This gives you more time and
resources to use on other components of your business.
User Guide 7

The Firebox X Edge and Your Network
8 Firebox X Edge e-Series

2
Installation
To install the WatchGuard® Firebox® X Edge e-Series in your network, you must complete these steps:
• Register your Firebox and activate the LiveSecurity® Service.
• Identify and record the TCP/IP properties for your Internet connection.
• Disable the HTTP proxy properties of your web browser.
• Connect the Edge to your network.
• Connect your computer to the Edge.
• Use the Quick Setup Wizard to configure the Edge.
Installation Requirements
To install the Firebox® X Edge e-Series, you must have:
• A computer with a 10/100BaseT Ethernet network interface card to configure the Edge.
• A web browser. You can use Internet Explorer 6.0 or later, Netscape 7.0 or later, or an equivalent
browser.
• Serial number of the Edge.
You can find the serial number on the bottom of the device. You use the serial number to register
the Edge.
• Internet connection.
The external network connection can be a cable or DSL modem with a 10/100BaseT port, an
ISDN router, or a direct LAN connection. If you have problems with your Internet connection, call
your ISP (Internet Service Provider) to correct the problem before you install the Firebox X Edge.
Package Contents
Make sure that the package for your Firebox® X Edge e-Series includes these items:
• Firebox X Edge e-Series User Guide on CD-ROM
• Firebox X Edge e-Series Quick Start Guide
User Guide 9
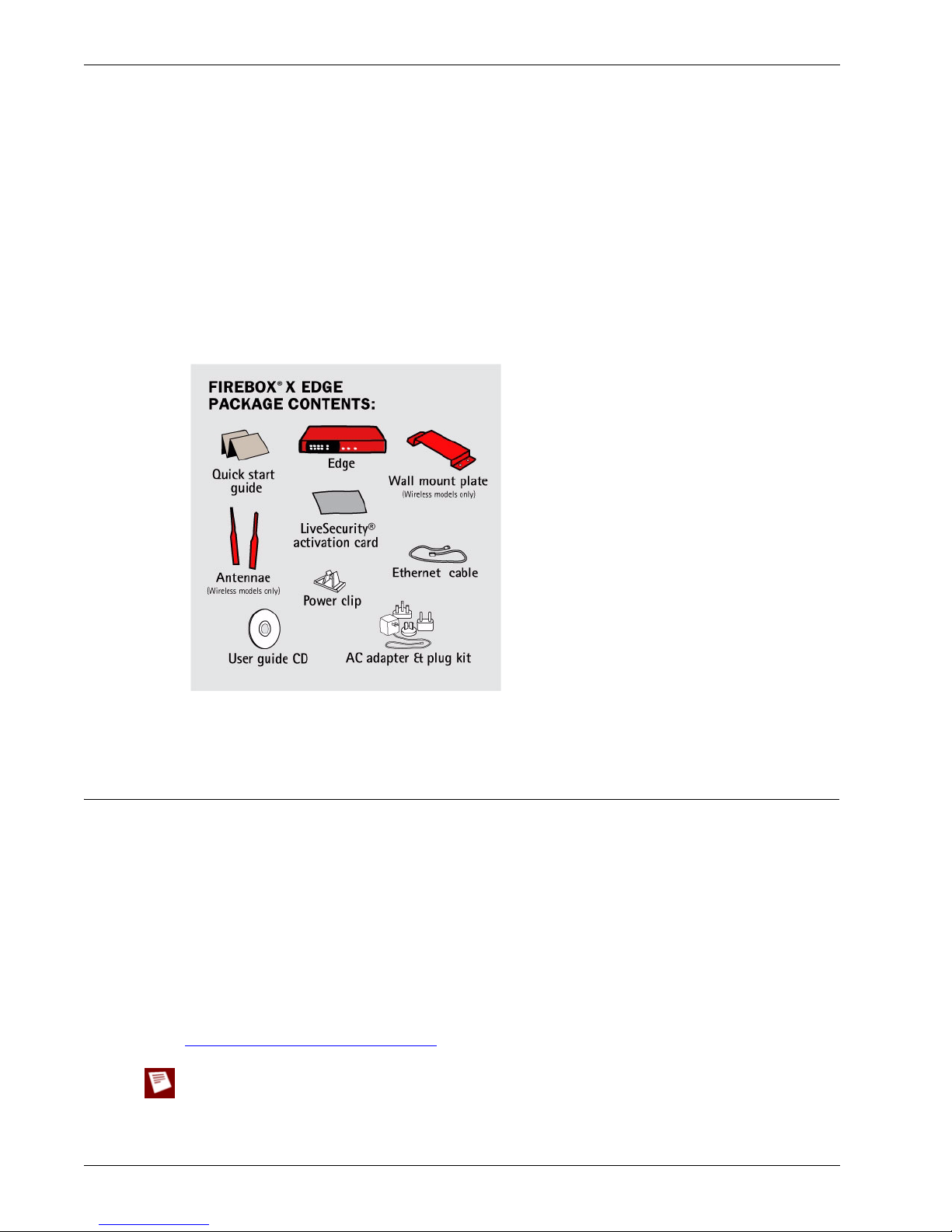
Registering Your Firebox & Activating LiveSecurity Service
• LiveSecurity® Service activation card
• Hardware warranty card
• AC power adapter (12 V/1.2A) with international plug kit
• Power cable clip
Use this clip to attach the cable to the side of the Edge. This decreases the tension on the power
cable.
• One green straight-through Ethernet cable
• Wall mount plate (wireless models only)
• Two antennae (wireless models only)
Registering Your Firebox & Activating LiveSecurity
Service
To enable all of the features on your Firebox® X Edge, you must first register on the Watchguard Live
Security web site and retrieve your feature key. You have only one user license (seat license) until you
apply your feature key. See “About user licenses” on page 17 for more information. You must also use
your feature key to apply any additional upgrades that you purchase.
When you register, you also activate your free 90-day LiveSecurity® Service subscription. The LiveSecurity Service gives you threat alert notifications, security advice, virus protection information, software
updates, technical support by web or telephone, and access to online help resources and the WatchGuard® user forum.
To register your Firebox X Edge:
1 Use your browser to go to:
http://www.watchguard.com/activate/
To activate the LiveSecurity Service, your browser must have JavaScript enabled.
10 Firebox X Edge e-Series

2 If you are a new customer, you must create a user profile. If you are an existing customer, log in
with your LiveSecurity Service user name and password.
3 Follow the online instructions to register your Firebox X Edge. You must have the serial number.
You can find the serial number on the bottom of the Edge or on the box it is packaged in.
4 When you enter your serial number, you receive a feature key. Copy and save this text to a file on
your local drive. You need it when you use the Quick Setup Wizard.
5 We recommend that you also download the latest software at this time.
6 If a model upgrade key is included with your model, activate it at:
http://www.watchguard.com/upgrade
Identifying Your Network Settings
To configure your Firebox® X Edge, you must know some information about your network. (For an
overview of network basics, see “About Networks” on page 1.) Use this section to learn how to identify
your network settings.
About network addressing
Identifying Your Network Settings
Speak with your ISP or corporate network administrator to learn how your computer gets its external IP
address. Use the same method to connect to the Internet with the Firebox X Edge that you use with
your computer. If you connect your computer directly to the Internet with a broadband connection,
you can put the Edge between your computer and the Internet and use the network configuration
from your computer to configure the Edge external interface. You can use a static IP address, DHCP, or
PPPoE to configure the Edge external interface.
Your computer must have a web browser. You use the web browser to configure and manage the Firebox X Edge. Your computer must have an IP address on the same network as the Edge.
In the factory default configuration, the Firebox X Edge assigns your computer an IP address with
DHCP (Dynamic Host Configuration Protocol). You can set your computer to use DHCP and then you
can connect to the Edge to manage it. You can also give your computer a static IP address that is on the
same network as the trusted IP address of the Edge. For more information, see “Setting Your Computer
to Connect to the Edge” on page 17.
Static addresses, DHCP, and PPPoE
Your ISP gives you an IP address using one of these methods:
• Static: A static IP address is an IP address that always stays the same. If you have a web server, FTP
server, or other Internet resource that must have an address that cannot change, you can get a
static IP address from your ISP. A static IP address is usually more expensive than a dynamic IP
address, and some ISPs do not supply static IP addresses. You must configure a static IP address
manually.
• DHCP: A dynamic IP address is an IP address that an ISP lets you use temporarily. ISPs use DHCP
(Dynamic Host Configuration Protocol) to assign you a dynamic IP address. With DHCP, your
computer does not always use the same IP address. Each time you connect to the ISP, a DHCP
server assigns you an IP address. It could be the same IP address you had before, or it could be a
new one. When you close an Internet connection that uses a dynamic IP address, the ISP can
assign that IP address to a different customer.
User Guide 11

Identifying Your Network Settings
• PPPoE: An ISP also can use PPPoE (Point-to-Point Protocol over Ethernet) to assign you an IP
address. Usually, a PPPoE address is dynamic. You must have a user name and a password to use
PPPoE.
The ISP assigns a subnet mask (also known as the netmask) to a computer. A subnet mask divides a
larger network into smaller networks. A subnet mask is a string of bits that “mask” one section of an IP
address to show how many IP addresses can be on the smaller network. For example, a large network
subnet mask looks like this: 255.255.0.0. Each zero shows that a range of IP addresses from 1 to 255 is
available. Each decimal place of 255 represents an IP address range that is in use. In a network with a
subnet mask of 255.255.0.0, there are 65,025 IP addresses available. A smaller network subnet mask is
255.255.255.0. In this example, only 254 IP addresses are available.
Read your DSL or cable modem instructions or speak to your ISP to learn if you have a dynamic IP
address or a static IP address.
TCP/IP properties
To learn about the properties of your network, look at the TCP/IP properties of your computer or any
other computer on the network. You must have the following information to install your
Firebox X Edge:
• IP address
• Subnet mask
• Default gateway
• Whether your computer has a static or dynamic IP address
• IP addresses of primary and secondary DNS servers
If your ISP assigns your computer an IP address that starts with 10, 192.168, or 172.16 to 172.31, then your
ISP uses NAT (Network Address Translation) and your IP address is private. We recommend that you get a
public IP address for your Firebox X Edge external IP address. If you use a private IP address, you can have
problems with some features, such as virtual private networking.
To find your TCP/IP properties, use the following instructions for your computer operating system.
Finding your TCP/IP properties on Microsoft Windows Vista
1 Select Start > Programs > Accessories > Command Prompt.
The Command Prompt window appears.
2 At the command prompt, type ipconfig /all and press Enter.
3 Record the values that you see for the primary network adaptor.
Finding your TCP/IP properties on Microsoft Windows 2000, Windows
2003, and Windows XP
1 Select Start > All Programs > Accessories > Command Prompt.
The Command Prompt window appears.
2 At the command prompt, type ipconfig /all and press Enter.
3 Record the values that you see for the primary network adaptor.
Finding your TCP/IP properties on Microsoft Windows NT
1 Select Start > Programs > Command Prompt.
The Command Prompt window appears.
12 Firebox X Edge e-Series

Web Browser HTTP Proxy Settings
2 At the command prompt, type ipconfig /all and press Enter.
3 Record the values that you see for the primary network adaptor.
Finding your TCP/IP properties on Macintosh OS 9
1 Select the Apple menu > Control Panels > TCP/IP.
The TCP/IP window appears.
2 Record the values that you see for the primary network adaptor.
Finding your TCP/IP properties on Macintosh OS X
1 Select the Apple menu > System Preferences, or select the icon from the Dock.
The System Preferences window appears.
2 Click the Network icon.
The Network preference pane appears.
3 From the Show drop-down list, select the network adapter you use to connect to the Internet.
4 Record the values that you see for the primary network adaptor.
Finding your TCP/IP properties on other operating systems (Unix, Linux)
1 Read your operating system guide to find the TCP/IP settings.
2 Record the values that you see for the primary network adaptor.
PPPoE settings
Many ISPs use Point to Point Protocol over Ethernet (PPPoE) because it is easy to use with a dial-up
infrastructure. If your ISP uses PPPoE to assign IP addresses, you must get the following information:
• Login name
• Domain (optional)
• Password
Web Browser HTTP Proxy Settings
Many web browsers are configured to use an HTTP proxy server to increase the download speed of
web pages. To manage or configure the Firebox® X Edge e-Series, your browser must connect directly
to the Edge. If you use an HTTP proxy server, you must temporarily disable the HTTP proxy setting in
your browser. You can reenable the HTTP proxy server setting in your browser after you set up the
Edge.
Use these instructions to disable the HTTP proxy in Firefox, Netscape, Safari, or Internet Explorer. If you
are using a different browser, use the browser Help system to find the necessary information. Many
browsers automatically disable the HTTP proxy feature.
Disabling the HTTP proxy in Internet Explorer 6.x or 7.x
1 Open Internet Explorer.
2 Select Tools > Internet Options.
The Internet Options window appears.
3 Click the Connections tab.
User Guide 13

Web Browser Pop-up Blocking Settings
4 Click the LAN Settings button.
The Local Area Network (LAN) Settings window appears.
5 Clear the check box labeled Use a proxy server for your LAN.
6 Click OK two times.
Disabling the HTTP proxy in Firefox 2.x
1 Open the browser software.
2 Select Tools > Options.
The Options window appears.
3 Click the Advanced icon.
4 Select the Network tab. Click Settings.
5 Click the Connection Settings button.
The Connection Settings dialog box appears.
6 Make sure the Direct Connection to the Internet option is selected.
7 Click OK two times.
Disabling the HTTP proxy in Safari 2.0
1 Open the browser software.
2 From the application menu, select Preferences.
The Safari preferences window appears.
3 Click the Advanced icon.
4 Click the Change Settings button.
The System Preference window appears.
5 Clear the Web Proxy (HTTP) check box.
6 Click Apply Now.
Web Browser Pop-up Blocking Settings
The Firebox® X Edge e-Series uses pop-up windows for many features, including the Quick Setup Wizard. If you block pop-up windows, you must disable this function when you connect to the Edge.
Use these instructions to disable the pop-up blocking option in Firefox, Netscape, Safari, or Internet
Explorer. If you are using a different browser, use the browser Help system to find the necessary information.
Disabling the pop-up blocker in Internet Explorer 6.x or 7.x
1 Open Internet Explorer.
2 Select Tools > Pop-Up Blocker > Turn Off Pop-Up Blocker.
Disabling the pop-up blocker in Firefox 2.x
1 Open the browser software.
2 Select Tools > Options.
The Options window appears.
14 Firebox X Edge e-Series
Connecting the Firebox X Edge
3 Click the Content icon.
4 Make sure the Block pop-up windows option is not selected.
5 Click OK.
Disabling the pop-up blocker in Netscape 8.1
1 Open the browser software.
2 Select Tools > Options.
The Options window appears.
3 Click the Site Controls icon.
The Site Controls preference window appears.
4 Select the Allow unrequested pop-up windows check box.
5 Click OK.
Disabling the pop-up blocker in Safari 2.0
1 Open the browser software.
2 Click Application. Make sure that the Block Pop-Up Windows menu item is not selected.
Connecting the Firebox X Edge
Many people configure their Firebox® X Edge e-Series on one computer before they put it on the network.
Use this procedure to connect a computer to your Firebox® X Edge:
1 Shut down your computer.
2 If you use a DSL or cable modem to connect to the Internet, disconnect its power supply.
User Guide 15

Connecting the Firebox X Edge
3 Find the Ethernet cable between the modem and your computer. Disconnect this cable from
your computer and connect it to the Edge external interface (labeled WAN 1).
4 Find the green Ethernet cable supplied with your Edge. Connect this cable to a trusted interface
(LAN0-LAN2) on the Edge. Connect the other end of this cable to the Ethernet interface of your
computer.
5 If you use a DSL or cable modem, connect its power supply.
6 Find the AC adapter supplied with your Edge. Connect the AC adapter to the Edge and to a
power source.
The Edge power indicator light comes on, then the WAN indicator lights flash and then come on.
Use only the supplied AC adapter for the Firebox X Edge.
Connecting the Edge to more than four devices
The Firebox X Edge e-Series has three Ethernet ports (LAN0-LAN2) for the trusted network, and one
Ethernet port (OPT) for the optional network. You can connect devices directly to the Edge, or use a
hub or switch to connect more than four devices. The number of devices that can connect to the external network is limited by the number of session licenses available. See the subsequent section, ”About
user licenses” for more information.
To connect more than four devices to the Edge, you must have:
• An Ethernet 10/100Base TX hub or switch
• Straight-through Ethernet cables, with RJ-45 connectors, for each computer
• A straight-through Ethernet cable to connect each hub to the Firebox X Edge
To connect more devices to the Firebox X Edge:
1 Shut down your computer.
2 If you use a DSL or cable modem to connect to the Internet, disconnect its power supply.
3 Disconnect the Ethernet cable that comes from your DSL modem, cable modem, or other
Internet connection to your computer. Connect the Ethernet cable to the WAN1 port on the
Firebox X Edge.
The Firebox X Edge is connected directly to the modem or other Internet connection.
4 Connect one end of the straight-through Ethernet cable supplied with your Firebox X Edge to
one of the four Ethernet ports on the Edge. Connect the other end to the uplink port of the
Ethernet hub or switch.
The Firebox X Edge is connected to the Internet and your Ethernet hub or switch.
16 Firebox X Edge e-Series

Setting Your Computer to Connect to the Edge
5 Connect an Ethernet cable between each computer and one of the ports on the Ethernet hub,
and make sure the link lights are lit on the devices when they are turned on.
6 If you connect to the Internet through a DSL modem or cable modem, connect the power supply
to this device. The indicator lights flash and then stop.
7 Attach the AC adapter to the Firebox X Edge. Connect the AC adapter to a power supply.
About user licenses
Your Firebox® X Edge firewall is enabled with a set number of user licenses. The total number of available sessions is determined by the Edge model you have, and any upgrade licenses you apply. The
number of licenses limits the number of sessions. To control the number of users at any time, close one
or more sessions. When you close a session, you make that user license available for another user.
There are several procedures to close a session:
• If you require users to authenticate, a Firebox User can manually log out and return his or her
license.
• The Edge Administrator can close the session manually. He or she can close the session for an
individual user or close all sessions.
• If you require users to authenticate, you can assign a maximum timeout and an idle timeout for
each user.
• The Edge administrator can set a global session maximum timeout.
• Reboot the Edge to close all sessions.
For more information about user licenses, see the “User and Group Management” chapter.
License upgrades are available from your reseller or from the WatchGuard® web site:
http://www.watchguard.com/products/purchaseoptions.asp
Setting Your Computer to Connect to the Edge
Before you can use the Quick Setup Wizard, you must configure your computer to connect to the Firebox® X Edge. You can set your network interface card to use a static IP address, or use DHCP to get an IP
address automatically.
Using DHCP
This procedure configures a computer with the Windows XP operating system to use DHCP. If your
computer does not use Windows XP, read the operating system help for instructions on how to set
your computer to use DHCP.
1 Select Start > Control Panel.
The Control Panel window appears.
2 Double-click the Network Connections icon.
3 Double-click the Local Area Connection icon.
The Local Area Connection Status window appears.
4 Click the Properties button.
The Local Area Connection Properties window appears.
5 Double-click the Internet Protocol (TCP/IP) list item.
The Internet Protocol (TCP/IP) Properties dialog box appears.
User Guide 17

Setting Your Computer to Connect to the Edge
6 Select the Obtain an IP address automatically and the Obtain DNS server address
automatically options.
7 Click OK to close the Internet Protocol (TCP/IP) Properties dialog box.
8 Click OK to close the Local Area Network Connection Properties dialog box. Close the Local
Area Connection Status, Network Connections, and Control Panel windows.
Your computer is ready to connect to the Firebox X Edge.
9 When the Edge is ready, start your Internet browser.
10 Type https://192.168.111.1/ into the URL entry field of your browser and press Enter. If you are
asked to accept a security certificate, click OK.
The Quick Setup Wizard starts.
11 Run the Quick Setup Wizard.
Using a static IP address
This procedure configures a computer with the Windows XP operating system to use a static IP
address. If your computer does not use Windows XP, read the operating system help for instructions on
how to set your computer to use a static IP address.
You must select an IP address on the same subnet as the trusted network.
1 Select Start > Control Panel.
The Control Panel window appears.
2 Double-click the Network Connections icon.
3 Double-click the Local Area Connection icon.
The Local Area Connection Status window appears.
4 Click the Properties button.
The Local Area Connection Properties window appears.
5 Double-click the Internet Protocol (TCP/IP) list item.
The Internet Protocol (TCP/IP) Properties dialog box appears.
6 Select the Use the following IP address option.
7 In the IP address field, type an IP address on the same network as the Edge trusted interface. We
recommend 192.168.111.2.
The default trusted interface network is 192.168.111.0. The last number can be between 2 and
254.
8 In the Subnet Mask field, type 255.255.255.0.
9 In the Default Gateway field, type the IP address of the Edge trusted interface.
The default Edge trusted interface address is 192.168.111.1.
10 Click OK to close the Internet Protocol (TCP/IP) Properties dialog box.
11 Click OK to close the Local Area Network Connection Properties dialog box. Close the Local
Area Connection Status, Network Connections, and Control Panel windows.
Your computer is ready to connect to the Firebox X Edge.
12 When the Edge is ready, start your Internet browser.
13 Type https://192.168.111.1/ into the URL entry field of your browser and press Enter. If you are
asked to accept a security certificate, click OK.
The Quick Setup Wizard starts.
14 Use the Quick Setup Wizard, as shown in the subsequent section.
18 Firebox X Edge e-Series
 Loading...
Loading...