Watchguard Firebox X6500E, Firebox X55E, Firebox X10E, Firebox X Peak e-Series, Firebox X Core e-Series Reference Manual
...Page 1

Reference Guide
Firebox X Core/Peak e-Series
with WatchGuard System Manager/Fireware v10.0
Firebox X Edge e-Series v10.0
Revised: 2/1/2008
Page 2
Notice to Users
Information in this guide is subject to change without notice. Companies, names, and data used in examples
herein are fictitious unless otherwise noted. No part of this guide may be reproduced or transmitted in any
form or by any means, electronic or mechanical, for any purpose, without the express written permission of
WatchGuard Technologies, Inc.
Copyright, Trademark, and Patent Information
Copyright© 1998 - 2008 WatchGuard Technologies, Inc. All rights reserved.
Complete copyright, trademark, patent, and licensing
information can be found in Chapter 7 of this Reference Guide.
A copy of this book is automatically installed into a subfolder of
the installation directory called Documentation. You can also
find it online at:
http://www.watchguard.com/help/documentation/
All trademarks or trade names mentioned herein, if any, are the property of their respective owners.
ABOUT WATCHGUARD
Since 1996, WatchGuard Technologies has provided reliable, easy to manage
security appliances to hundreds of thousands of businesses worldwide. Our
Firebox X family of unified threat management (UTM) solutions provides the
best combination of strong, reliable, multi-layered security with the best ease
of use in its class. All products are backed by LiveSecurity® Service, a
ground-breaking support and maintenance program. WatchGuard is a
privately owned company, headquartered in Seattle, Washington, with offices
throughout North America, Europe, Asia Pacific, and Latin America. For
more information, please call 206.613.6600 or visit www.watchguard.com
ii
ADDRESS
505 Fifth Avenue South
Suite 500
Seattle, WA 98104
SUPPORT
www.watchguard.com/support
U.S. and Canada +877.232.3531
All Other Countries +1.206.521.3575
.
SALES
U.S. and Canada +1.800.734.9905
All Other Countries +1.206.613.0895
WatchGuard System Manager
Page 3

Contents
CHAPTER 1
Internet Protocol Reference
Internet Protocol Header ...............................................................................2
IP header number list ..................................................................................3
Internet Protocol Options ..............................................................................6
Transfer Protocols ........................................................................................6
UDP .........................................................................................................6
TCP..........................................................................................................7
ICMP........................................................................................................7
Other protocols ..........................................................................................7
........................................................................1
Standard Ports and Random Ports.................................................................8
CHAPTER 2
MIME Content Types
....................................................................................9
CHAPTER 3
Services and Ports
Ports Used by WSM and Fireware ................................................................21
Ports Used by Microsoft Products ................................................................22
Well-Known Services List ............................................................................23
.....................................................................................21
CHAPTER 4
WebBlocker Content
Searching for Blocked Sites ........................................................................31
WebBlocker Categories ...............................................................................32
..................................................................................31
Reference Guide iii
Page 4

CHAPTER 5
Types of Policies in Fireware
Packet Filter Policies ..................................................................................39
Any........................................................................................................39
Archie ....................................................................................................40
auth.......................................................................................................40
BGP .......................................................................................................40
Citrix ......................................................................................................40
Clarent-Command .....................................................................................41
Clarent-Gateway........................................................................................41
CU-SeeMe ...............................................................................................42
DHCP-Server or DHCP-Client ........................................................................42
DNS.......................................................................................................42
Entrust ...................................................................................................42
finger .....................................................................................................43
FTP........................................................................................................43
Gopher ...................................................................................................43
GRE .......................................................................................................43
HBCI ......................................................................................................44
HTTP......................................................................................................44
HTTPS ....................................................................................................44
IDENT.....................................................................................................45
IGMP......................................................................................................45
IMAP......................................................................................................45
IPSec .....................................................................................................45
IRC ........................................................................................................46
Intel-Video-Phone ......................................................................................46
Kerberos-v4 and Kerberos-v5.......................................................................46
L2TP ......................................................................................................46
LDAP......................................................................................................47
LDAP-SSL................................................................................................47
Lotus Notes .............................................................................................47
MS-SQL-Monitor........................................................................................47
MS-SQL-Server .........................................................................................47
MS-Win-Media ..........................................................................................48
NetMeeting .............................................................................................48
NFS .......................................................................................................48
NNTP .....................................................................................................48
NTP .......................................................................................................49
OSPF......................................................................................................49
pcAnywhere.............................................................................................49
Ping .......................................................................................................49
POP2 and POP3 .......................................................................................50
PPTP ......................................................................................................50
RADIUS and RADIUS-RFC............................................................................50
......................................................................39
iv
WatchGuard System Manager
Page 5

RADIUS-Accounting and RADIUS-Acct-RFC.......................................................51
RDP .......................................................................................................51
RIP ........................................................................................................51
RSH.......................................................................................................51
RealPlayerG2 ...........................................................................................52
Rlogin ....................................................................................................52
SecurID ..................................................................................................52
SMB (Windows Networking).........................................................................52
SMTP .....................................................................................................53
SNMP.....................................................................................................53
SNMP-Trap ..............................................................................................53
SQL*Net .................................................................................................53
SQL-Server ..............................................................................................53
SSH .......................................................................................................54
SSL-VPN .................................................................................................54
SunRPC ..................................................................................................54
Syslog ....................................................................................................54
TACACS...................................................................................................55
TACACS+.................................................................................................55
TCP........................................................................................................55
TCP-UDP .................................................................................................55
Telnet .....................................................................................................55
Timbuktu ................................................................................................56
Time ......................................................................................................56
Tra ceroute ...............................................................................................56
UDP .......................................................................................................56
UUCP .....................................................................................................57
WAIS ......................................................................................................57
WinFrame ...............................................................................................57
WG-Auth .................................................................................................57
WG-Firebox-Mgmt......................................................................................58
WG-Logging .............................................................................................58
WG-Mgmt-Server.......................................................................................58
WG-SmallOffice-Mgmt ................................................................................58
WG-WebBlocker ........................................................................................58
WHOIS....................................................................................................59
X11 .......................................................................................................59
Reference Guide v
Page 6

Proxy Policies.............................................................................................60
DNS-proxy ...............................................................................................60
FTP-proxy ................................................................................................60
H323-proxy..............................................................................................60
HTTP-proxy ..............................................................................................61
HTTPS-proxy ............................................................................................61
POP3-proxy..............................................................................................61
SIP-proxy.................................................................................................62
SMTP-proxy .............................................................................................62
TCP-UDP-proxy..........................................................................................62
TFTP-proxy...............................................................................................63
CHAPTER 6
Resources
Publishers .................................................................................................66
Books .......................................................................................................66
Non-Fiction ..............................................................................................66
Fiction....................................................................................................66
Mailing Lists ..............................................................................................67
General IT and Security Web Sites ...............................................................67
White Hat Web Sites...................................................................................69
Grey Hat Sites............................................................................................70
Other Web Sites.........................................................................................71
...................................................................................................65
Dictionaries of Computer Terminology ..........................................................71
RSS Feeds.................................................................................................72
Security Feeds .........................................................................................72
IT Related Feeds.......................................................................................72
Fun Feeds ...............................................................................................73
Web Logs (Blogs) ......................................................................................73
Web Logs (Blogs) ......................................................................................74
vi
WatchGuard System Manager
Page 7

CHAPTER 7
Copyright, Patent, Trademark, and Licensing Information
Copyright Information .................................................................................75
Patents .....................................................................................................75
Trademarks................................................................................................75
Licensing...................................................................................................76
Apache License (1.1) .................................................................................76
Apache License (2.0) .................................................................................77
GNU General Public License (GPL) ................................................................80
GNU Lesser General Public License (LGPL) .....................................................84
GNU Library General Public License (Library GPL) ............................................90
Java Platform, Standard Edition License.........................................................96
bzip2 .....................................................................................................99
BusyBox ...............................................................................................100
CGIC ....................................................................................................100
ctengine ...............................................................................................100
curl......................................................................................................100
dhcp ....................................................................................................101
dmalloc ................................................................................................101
ElementTree ..........................................................................................102
expat and libexpat ..................................................................................102
free-extractor .........................................................................................103
freeradius-client......................................................................................103
iputils...................................................................................................105
iText.....................................................................................................106
javasqlite ..............................................................................................106
Java 2D API Samples ...............................................................................107
JAXB ....................................................................................................107
JDom ...................................................................................................112
junit.....................................................................................................112
jython...................................................................................................115
kazlib ...................................................................................................117
libarchive ..............................................................................................117
libcurl...................................................................................................117
libpcap .................................................................................................118
lightppd ................................................................................................118
Linux....................................................................................................119
Lua......................................................................................................120
madwifi ................................................................................................120
net-SNMP..............................................................................................121
NumPy .................................................................................................124
OpenLDAP.............................................................................................125
OpenNTPD ............................................................................................125
OpenSSL...............................................................................................127
........................75
Reference Guide vii
Page 8

OpenVPN ..............................................................................................128
ossp_mm ..............................................................................................129
PCRE ...................................................................................................130
PPP .....................................................................................................130
PostgreSQL Database Management System..................................................136
py lib....................................................................................................136
pysqlite .................................................................................................137
Python..................................................................................................137
redboot ................................................................................................138
sasl .....................................................................................................144
tinyxpath...............................................................................................145
traceroute .............................................................................................145
uClibc...................................................................................................145
wvstreams.............................................................................................146
xpp3 ....................................................................................................146
zlib ......................................................................................................147
viii
WatchGuard System Manager
Page 9

1
Internet Protocol Reference
Internet Protocol (IP) sets the format of packets and the address pattern for sending data through the
Internet. It operates as a postal system, and allows you to address a package and drop it into the
system. But, there is no direct link between you and the recipient. In other words, there is no package.
Most networks mix IP with higher level protocols such as Transmission Control Protocol (TCP). TCP/IP
makes a connection between two host servers. Then, they can send messages to each other. TCP/IP
supplies the “packaging.”
Reference Guide 1
Page 10
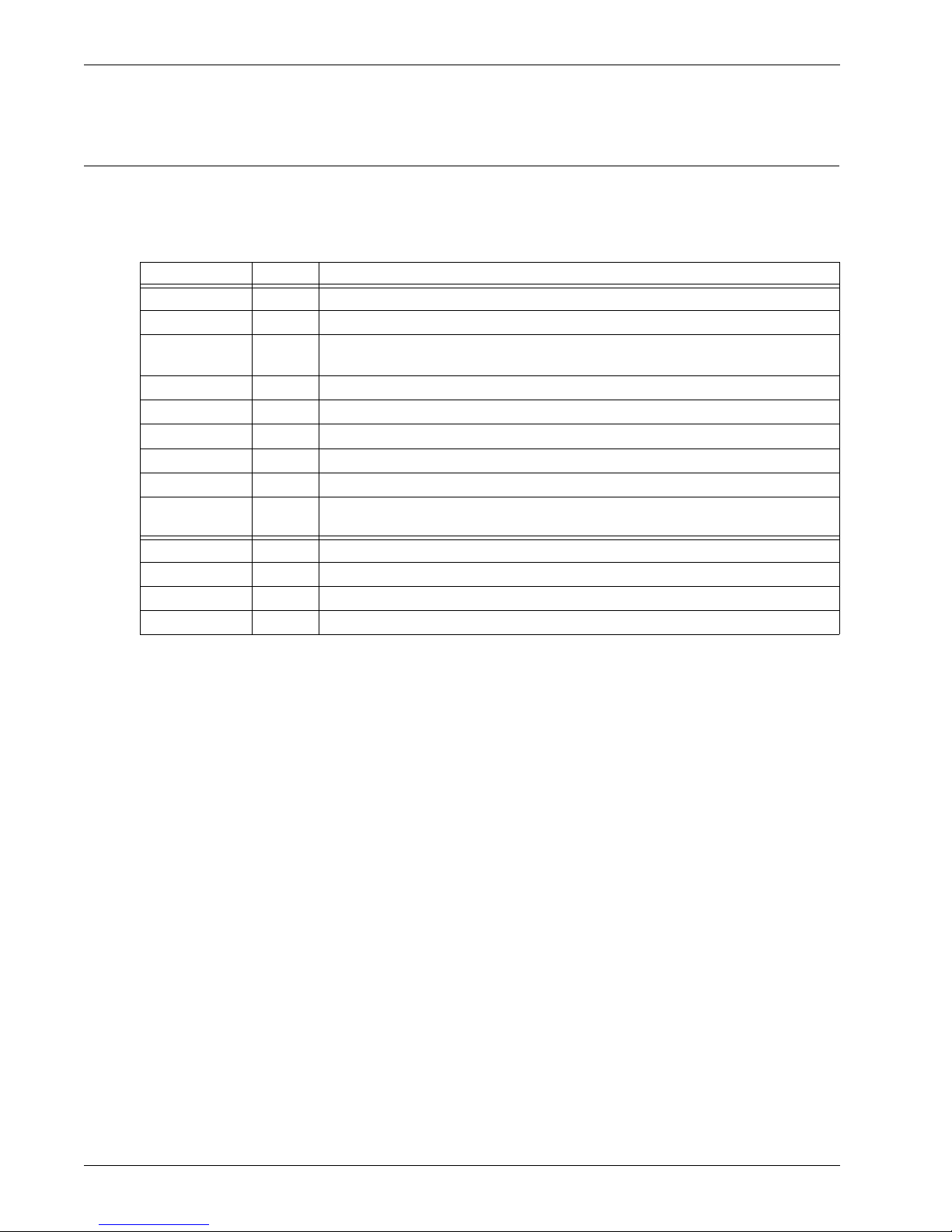
Internet Protocol Header
Internet Protocol (IP) is an Internet standard that enables the sending of datagrams — packets of
information that include an address and instructions on how to send the datagram to its destination.
IP prepends a header to each datagram. The IP header contains a minimum of 12 properties, and other
optional properties.
Property Size Description
Version 4 bits IP format number (Current version = 4)
IHL 4 bits Header length in 32-bit words (Minimum = 5)
TOS 8 bits Type of service sets routing priorities. It is usually not used because not many
application layers can set it.
To t_ Len 16 bits Total length of packet measured in octets. It is used to assemble fragments.
ID 16 bits Packet ID, used to assemble fragments.
Flags 3 bits Miscellaneous flags
Frag_Off 13 bits Identifies fragment part for this packet.
TTL 8 bits Time to live. It sets the maximum time the datagram remains alive in the system.
Protocol 8 bits IP protocol number. Indicates which of TCP, UDP, ICMP, IGMP, or other Transport
protocol is inside.
Check 16 bits Checksum for the IP header
Sour_Addr 32 bits Source IP address
Dest_Addr 32 bits Destination IP address
Options 24 bits IP Options (Present if IHL is 6)
2
WatchGuard System Manager
Page 11
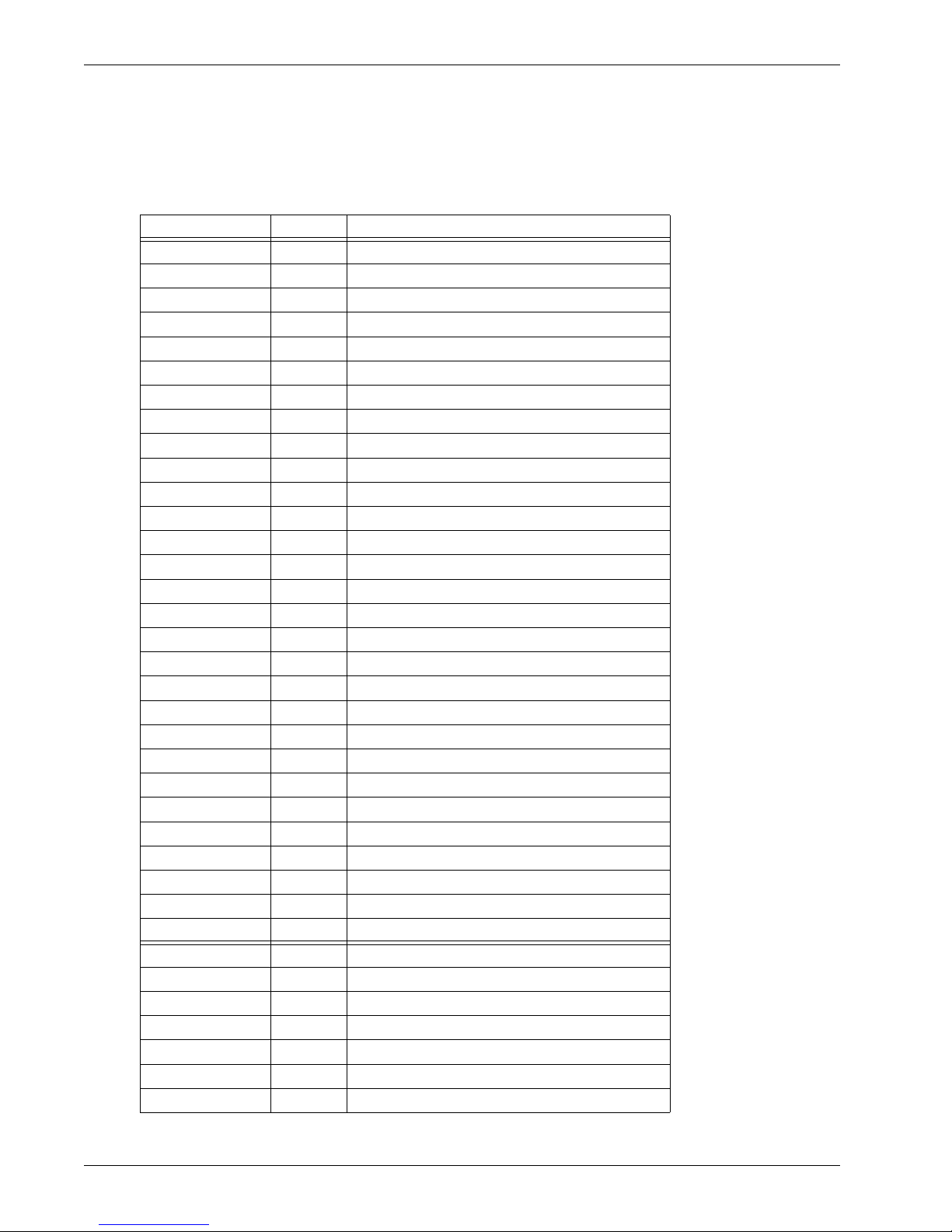
IP header number list
The IP Protocol header contains an 8-bit field that identifies the protocol for the transport layer for the
datagram.
Keyword Number Protocol
0 Reserved
ICMP 1 Internet Control Message
IGMP 2 Internet Group Management
GGP 3 Gateway-to-Gateway
IP 4 IP-within-IP (encapsulation)
ST 5 Stream
TCP 6 Transmission Control Protocol
UCL 7 UCL
EGP 8 Exterior Gateway Protocol
IGP 9 Any private interior gateway
BBN-RCC-MON 10 BBN RCC Monitoring
NVP-II 11 Network Voice Protocol
PUP 12 PUP
ARGUS 13 ARGUS
EMCON 14 EMCON
XNET 15 Cross Net Debugger
CHAOS 16 Chaos
UDP 17 User Datagram Protocol
MUX 18 Multiplexing
DCN-MEAS 19 DCN Measurement Subsystems
HMP 20 Host Monitoring
PRM 21 Packet Radio Measurement
XNS-IDP 22 XEROX NS IDP
TRUNK-1 23 Tr unk-1
TRUNK-2 24 Tr unk-2
LEAF-1 25 Leaf-1
LEAF-2 26 Leaf-2
RDP 27 Reliable Data Protocol
IRTP 28 Internet Reliable Transaction
ISO-TP4 29 ISO Transport Protocol Class 4
NETBLT 30 Bulk Data Transfer Protocol
MFE-NSP 31 MFE Network Services Protocol
MERIT-INP 32 MERIT Internodal Protocol
SEP 33 Sequential Exchange Protocol
3PC 34 Third Party Connect Protocol
IDPR 35 Inter-Domain Policy Routing Protocol
Reference Guide 3
Page 12
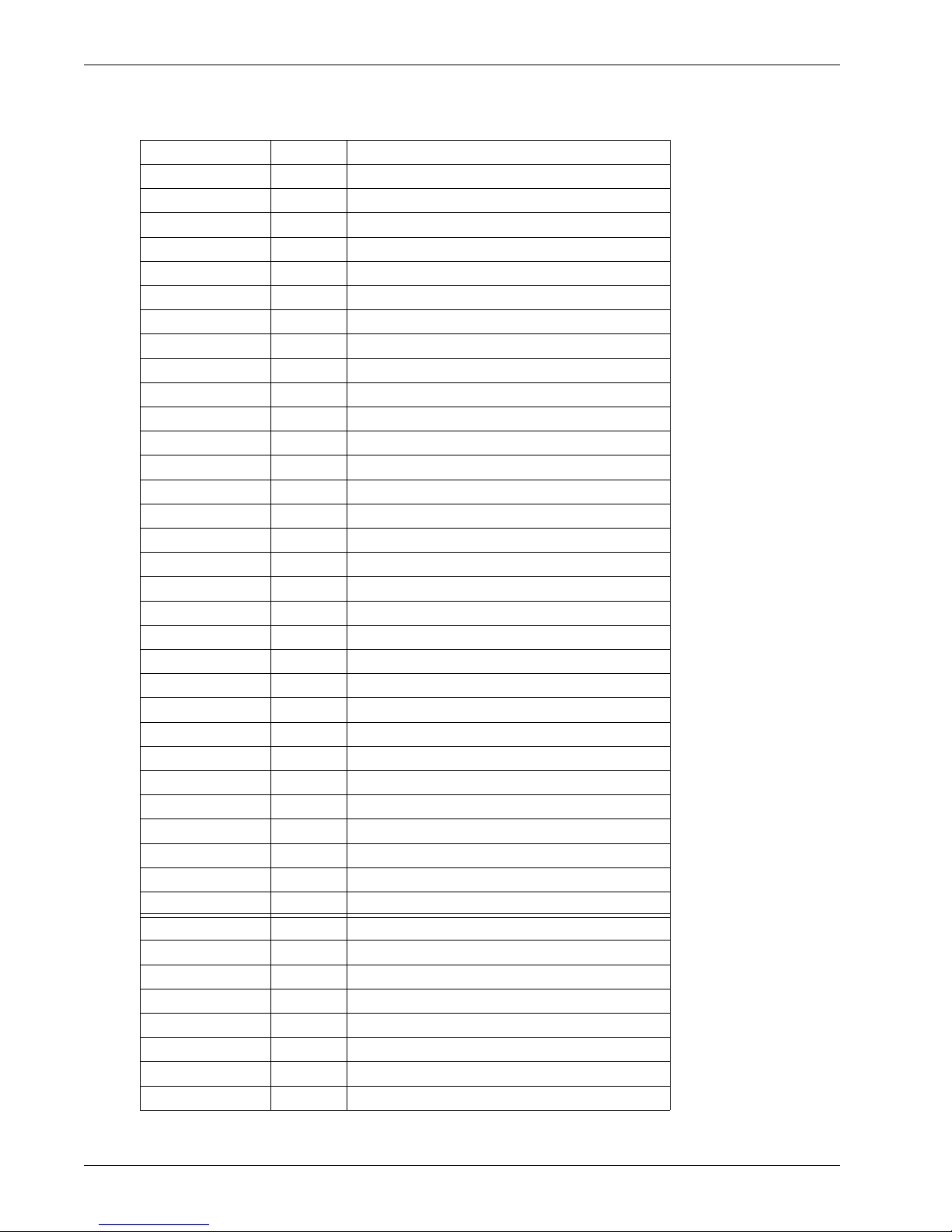
Keyword Number Protocol
XTP 36 XTP
DDP 37 Datagram Delivery Protocol
IDPR-CMTP 38 IDPR Control Message Transport Protocol
TP++ 39 TP++ Transport Protocol
IL 40 IL Transport Protocol
SIP 41 Simple Internet Protocol
SDRP 42 Source Demand Routing Protocol
SIP-SR 43 SIP Source Route
SIP-FRAG 44 SIP Fragment
IDRP 45 Inter-Domain Routing Protocol
RSVP 46 Reservation Protocol
GRE 47 General Routing Encapsulation
MHRP 48 Mobile Host Routing Protocol
BNA 49 BNA
ESP 50 Encapsulated Security Payload
AH 51 Authentication Header
I-NLSP 52 Integrated Net Layer Security TUBA
SWIPE 53 IP with Encryption
NHRP 54 NBMA Next Hop Resolution Protocol
55-60 Unassigned
61 Any host internal protocol
CFTP 62 CFTP
63 Any local network
SAT-EXPAK 64 SATNET and Backroom EXPAK
KRYPTOLAN 65 Kryptolan
RVD 66 MIT Remote Virtual Disk Protocol
IPPC 67 Internet Pluribus Packet Core
68 Any distributed file system
SAT-MON 69 SATNET Monitoring
VISA 70 VISA Protocol
IPCV 71 Internet Packet Core Utility
CPNX 72 Computer Protocol Network Executive
CPHB 73 Computer Protocol Heart Beat
WSN 74 Wang Span Network
PVP 75 Packet Video Protocol
BR-SAT-MON 76 Backroom SATNET Monitoring
SUN-ND 77 SUN NDPROTOCOL-Temporary
WB-MON 78 WIDEBAND Monitoring
WB-EXPAK 79 WIDEBAND EXPAK
4
WatchGuard System Manager
Page 13
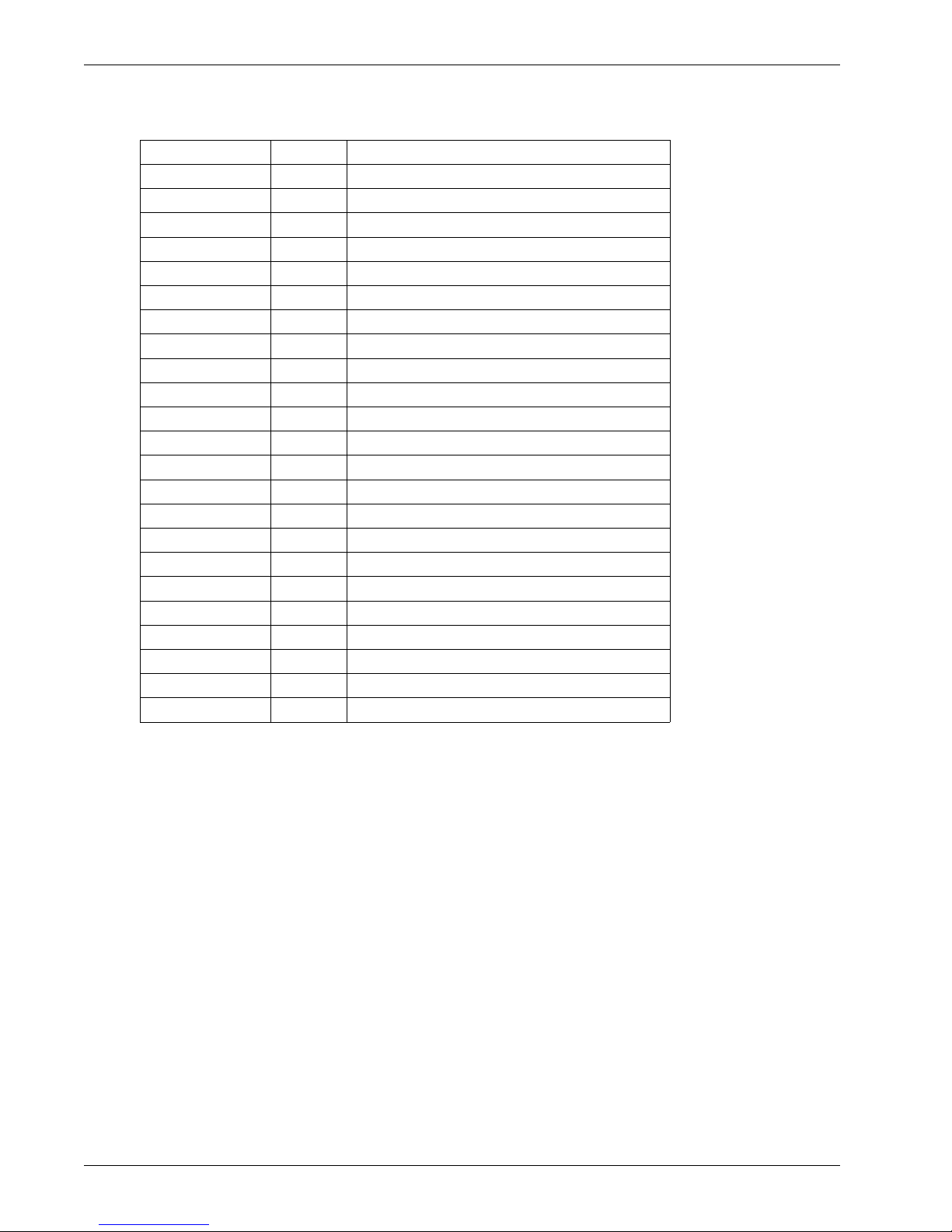
Keyword Number Protocol
ISO-IP 80 ISO Internet Protocol
VMTP 81 VMTP
SECURE-VMTP 82 SECURE-VMTP
VINES 83 VINES
TTP 84 TTP
NSFNET-IGP 85 NSFNET-IGP
DGP 86 Dissimilar Gateway Protocol
TCF 87 TCF
IGRP 88 IGRP
OSPFIGP 89 OSPFIGP
SPRITE-RPC 90 Sprite RPC Protocol
LARP 91 Locus Address Resolution Protocol
MTP 92 Multicast Transport Protocol
AX.25 93 AX.25 Frames
IPIP 94 IP-within-IP Encapsulation Protocol
MICP 95 Mobile Internetworking Control Protocol
SCC-SP 96 Semaphore Communications Security Protocol
ETHERIP 97 Ethernet-within-IP Encapsulation
ENCAP 98 Encapsulation Header
99 Any private encryption scheme
GMTP 100 GMTP
101-254 Unassigned
255 Reserved
Reference Guide 5
Page 14

Transfer Protocols
Internet Protocol Options
Internet Protocol (IP) options are additions to the standard IP header that can be of different lengths.
Enabling IP options can be dangerous. Hackers can use them to create routing that helps them get
access to your network. Because most software applications make it very difficult to use IP options,
they are not frequently used.
There are different types of IP options:
Security
These options control the routing of IP packets that transmit sensitive data. Security options are
not frequently supported.
Stream ID (SID)
The stream ID option is not frequently supported.
Source Routing
The loose source route option and the strict source route option enable the source of an Internet
packet to give routing information. Source routing options can be very dangerous, because an
attacker could use them to masquerade as a different user. But, loose source route option and
the traceroute tool can also help debug some unusual routing problems.
Record Route
The record route option was first used to do tests on the Internet. But, record route can record
only ten IP addresses. On the current Internet, a typical connection can include 20 or 30 different
routers, making the record route option out of date.
Time Stamp
The time stamp option measures the time for a packet to make one full cycle (source -->
destination --> source). Higher level time protocols or time stamp messages do this task better
than the time stamp option.
Transfer Protocols
The Internet Protocol (IP) includes information kept in the transport layer. The transport layer has
different protocols that tell how to transmit data between software applications: for example, UDP, TCP,
ICMP, and others.
UDP
User Datagram Protocol (UDP) is a datagram protocol that does not use connections. It is a very fast
protocol, and it does not use much bandwidth or CPU. But, you cannot trust that datagrams will get to
their destination. A software application that uses UDP must make sure that the full message gets to its
destination in the correct sequence.
Characteristics of UDP include:
• Frequently used for services that include the exchange of small quantities of data where sending
a datagram more than one time is not a problem.
• Used for services such as time synchronization in which a missing packet does not have an effect
on continued operation. Many systems using UDP send packets again at a constant rate to tell
other systems about unusual events.
• Frequently used on LANs. Because of its low system and bandwidth requirements, it gives a large
performance advantage to Network File System (NFS) services users. Network File System is a
popular TCP/IP service for supplying shared file systems over a network.
• Gives supports to broadcasts.
6
WatchGuard System Manager
Page 15

Transfer Protocols
• Gives abstraction of ports. A connection is made of its source and destination ports and its
source and destination IP addresses. In typical use, port numbers less than 1024 are saved for
well-known services (destinations). The client side can use ports higher than 1023 for the source
of the connection. But, this rule has many exceptions: NFS (port 2049) and Archie (port 1525) use
server ports at numbers higher than 1024. Some services use the same source and destination
port for server to server connections. Examples include DNS (53), NTP (123), syslog (514), and RIP
(520).
TCP
Transmission Control Protocol (TCP) enables two hosts to make a connection and send streams of data
to each other. TCP makes sure that the data that is sent gets to its destination. It also makes sure that
packets are put in the same sequence as when they were sent.
TCP manages connections with properties that control the condition of a connection. Three very
important properties of TCP packets are the SYN, ACK, and FIN bits. The SYN bit is set only on the first
packet sent in each direction for a given connection. The ACK bit is set when the other side gets the
data. The FIN bit is set when the source or destination closes the connection.
ICMP
The Internet Control Message Protocol (ICMP) is used most frequently to supply error information
about other services. It operates by using the same method as UDP. That is, ICMP does not use
connections and does not make sure that packets reach their destination. One dangerous ICMP packet
is the ICMP redirect packet, which can change routing information on the devices that receive it.
Other protocols
Most traffic on the Internet uses TCP, UDP, or ICMP protocols. Some other protocols are as follows:
IGMP (Internet Group Multicast Protocol)
A protocol used by a host on multicast access networks to notify a locally attached router to
which group the router belongs.
IPIP (IP-within-IP)
An encapsulation protocol that is used to assemble virtual networks on the Internet.
GGP (Gateway-Gateway Protocol
A routing protocol that is used between different systems.
GR
A protocol used for PPTP.
ES
An encryption protocol used for IPSec.
Reference Guide 7
Page 16

Transfer Protocols
Standard Ports and Random Ports
UDP and TCP use encapsulation of information contained in the application layer. The software
application procedures are specified by source ad destination port numbers. These port numbers,
together with the source and destination IP addresses, supply a unique connection on the Internet.
For example, you can have two telnet sessions from one host to a different host. Because telnet uses a
well-known service port number of 23, something must be different between these two connections.
The other port in these conditions is a port that is usually larger than 1023. The operating system on
the client side assigns this port number automatically.
Random ports can cause problems if they match a well-known service on a port higher than 1023. If
some client computer assigns a random port of 2049, no connection can be made. This type of
problem frequently occurs with the X Window and Archie services.
Most operating systems assign port numbers between 1024 and 2100 so this problem does not occur
frequently.
8
WatchGuard System Manager
Page 17
2
MIME Content Types
Software applications use content type headers to identify the type of data they receive. Content type
headers tell the software application how to correctly identify and display video clips, images, sound,
or other data. Usually, people are most familiar with the MIME content types used in email.
Some of the available proxy policies in your Firebox configuration can use content type headers to
determine whether to allow or deny traffic. This chapter contains a list of many common MIME content
types for your reference.
New, registered MIME content types appear regularly. We recommend frequent checks of an online
source for the most current list. One source of current MIME types is:
www.iana.org/assignments/media-types/
Note that software applications can use incorrect content types, or content types that are not
registered.
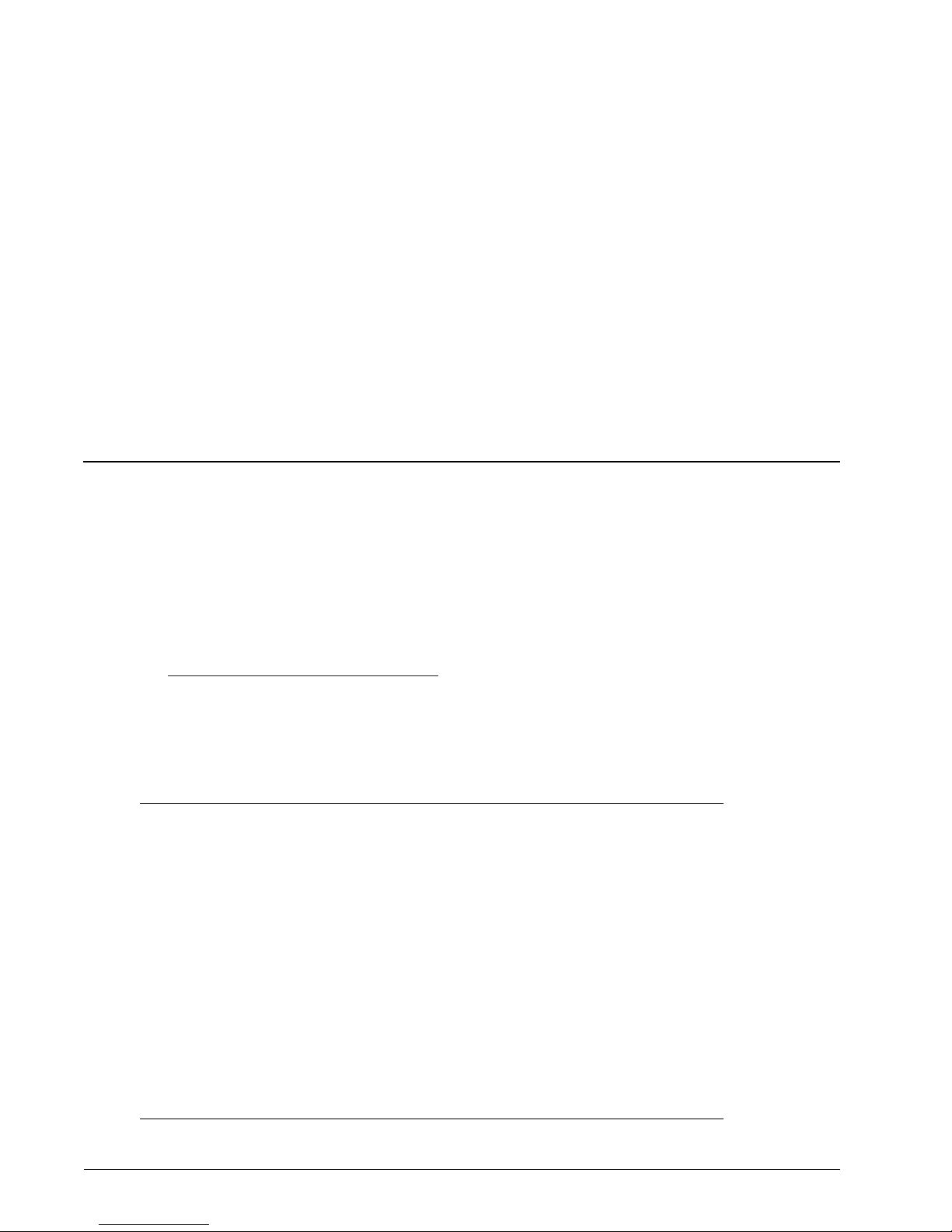
Common MIME content types
Typ e Subtype Reference (where available)
application *
application activemessage Shapiro
application andrew-inset Borenstein
application applefile Fal strom
application astound
application atomicmail Borenstein
application cals-1840 RFC 1895
application commonground Glazner
application cybercash Eastlake
application dca-rft Campbell
application dec-dx Campbell
application eshop Katz
Reference Guide 9
Page 18

Typ e Subtype Reference (where available)
application hyperstudio Domino
application iges Parks
application mac-binhex40 Fal strom
application macwriteii Lindner
application marc RFC 2220
application mathematica Van Nostern
application ms-excel
application mspowerpoint
application msword Lindner
application news-message-id RFC 1036, Spencer
application news-transmission RFC 1036, Spencer
application octet-stream RFC 2045, RFC 2046
application oda RFC 2045, RFC 2046
application olescript
application pdf RFC 3778
application pgp-encrypted RFC 3156
application pgp-keys RFC 3156
application pgp-signature RFC 3156
application pkcs10 RFC 2311
application pkcs7-mime RFC 2311
application pkcs7-signature RFC 2311
application postscript RFC 2045, RFC 2046
application prs.alvestrand.titrax-sheet Alvestrand
application prs.cww Rungchavalnont
application prs.nprend Doggett
application realnetworksupgrade
application remote-printing RFC 1486, Rose
application riscos Smith
application rtf Lindner
application set-payment Korver
application set-payment-initiation Korver
application set-registration Korver
application set-registration-initiation Korver
application sgml RFC 1874
application sgml-open-catalog Grosso
application slate
application vis5d
application vnd.3M.Post-it-Notes O’Brien
application vnd.FloGraphIt Floersch
10
WatchGuard System Manager
Page 19

Typ e Subtype Reference (where available)
application vnd.acucobol Lubin
application vnd.anser-web-certificate-issue-initiation Mori
application vnd.answer-web-funds-transfer-initiation Mori
application vnd.audiograph Slusanschi
application vnd.businessobjects Imoucha
application vnd.claymore Simpson
application vnd.commerce-battelle Applebaum
application vnd.commonspace Chandhok
application vnd.cosmocaller Dellutri
application vnd.cybank Helmee
application vnd.dna Searcy
application vnd.dxr Duffy
application vnd.ecdis-update Buettgenbach
application vnd.ecowin.chart Olsson
application vnd.ecowin.filerequest Olsson
application vnd.ecowin.fileupdate Olsson
application vnd.ecowin.series Olsson
application vnd.ecowin.seriesrequest Olsson
application vnd.ecowin.seriesupdate Olsson
application vnd.enliven Santinelli
application vnd.epson.quickanime Gu
application vnd.epson.salt Nagatomo
application vnd.fdf Zilles
application vnd.ffsns Holstage
application vnd.framemaker Wexler
application vnd.fujitsu-oasys To ga sh i
application vnd.fujitsu-oasys2 To ga sh i
application vnd.fujitsu-oasys3 Okudaira
application vnd.fujitsu-oasysgp Sugimoto
application vnd.fujitsu-oasysprs Ogita
application vnd.fujixerox.docuworks Tag uc hi
application vnd.fut-misnet Pruulmann
application vnd.hp-HPGL Pentecost
application vnd.hp-PCL Pentecost
application vnd.hp-PCLXL Pentecost
application vnd.hp-hps Aubrey
application vnd.ibm.MiniPay Herzberg
application vnd.ibm.modcap Hohensee
application vnd.intercon.formnet Gurak
Reference Guide 11
Page 20

Typ e Subtype Reference (where available)
application vnd.intertrust.digibox To ma se ll o
application vnd.intertrust.nncp Tom as el lo
application vnd.intu-qbo Scratchley
application vnd.is-xpr Natarajan
application vnd.japannet-directory-service Fujii
application vnd.japannet-jpnstore-wakeup Yo s hi ta k e
application vnd.japannet-payment-wakeup Fujii
application vnd.japannet-registration Yo sh it ak e
application vnd.japannet-registration-wakeup Fujii
application vnd.japannet-setstore-wakeup Yo sh it a ke
application vnd.japannet-verification Yo sh it a ke
application vnd.japannet-verification-wakeup Fujii
application vnd.loan Cole
application vnd.lotus-1-2-3 Wattenberger
application vnd.lotus-approach Wattenberger
application vnd.lotus-freelance Wattenberger
application vnd.lotus-organizer Wattenberger
application vnd.lotus-screencam Wattenberger
application vnd.lotus-wordpro Wattenberger
application vnd.meridian-slingshot Wedel
application vnd.mif Wexler
application vnd.minisoft-hp3000-save Bartram
application vnd.mitsubishi.misty-guard.trustweb Tan ak a
application vnd.ms-artgalry Slawson
application vnd.ms-asf Fleischman
application vnd.ms-powerpoint Gill
application vnd.ms-project Gill
application vnd.ms-tnef Gill
application vnd.ms-works Gill
application vnd.ms.wms-hrd.asfv1 Gill
application vnd.music-niff Butler
application vnd.musician Adams
application vnd.netfpx Mutz
application vnd.noblenet-directory Solomon
application vnd.noblenet-sealer Solomon
application vnd.noblenet-web Solomon
application vnd.novadigm.EDM Swenson
application vnd.novadigm.EDX Swenson
application vnd.novadigm.EXT Swenson
12
WatchGuard System Manager
Page 21

Typ e Subtype Reference (where available)
application vnd.osa.netdeploy Klos
application vnd.powerbuilder6 Guy
application vnd.powerbuilder6-s Guy
application vnd.publishare-delta-tree Ben-Kiki
application vnd.rapid Szekely
application vnd.rn-realplayer
application vnd.seemail Webb
application vnd.shana.informed.formdata Selzler
application vnd.shana.informed.formtemplate Selzler
application vnd.shana.informed.interchange Selzler
application vnd.shana.informed.package Selzler
application vnd.street-stream Levitt
application vnd.svd Becker
application vnd.swiftview-ics Widener
application vnd.truedoc Chace
application vnd.uplanet.alert Martin
application vnd.uplanet.alert-wbxml Martin
application vnd.uplanet.bearer-choi-wbxml Martin
application vnd.uplanet.bearer-choice Martin
application vnd.uplanet.cacheop Martin
application vnd.uplanet.cacheop-wbxml Martin
application vnd.uplanet.channel Martin
application vnd.uplanet.channel-wbxml Martin
application vnd.uplanet.list Martin
application vnd.uplanet.list-wbxml Martin
application vnd.uplanet.listcmd Martin
application vnd.uplanet.listcmd-wbxml Martin
application vnd.uplanet.signal Martin
application vnd.visio Sandal
application vnd.webturbo Rehem
application vnd.wrq-hp3000-labelled Bartram
application vnd.wt.stf Wohler
application vnd.xara Matthewman
application vnd.yellowriver-custom-menu Yello
application vnd.wita
application vnd.workperfect5.1
application write
application x-alpha-form
application x-asap
Reference Guide 13
Page 22

Typ e Subtype Reference (where available)
application x-bcpio
application x-chat
application x-cpio
application x-sch
application x-cu-seemee
application x-demoshield
application x-director
application x-dvi
application x-framemaker
application x-gtar
application x-ica
application x-installshield
application x-javascript
application x-koan
application x-latex
application x-mif
application x-msaddr
application x-mms-framed
application x-mswallet
application x-net-install
application x-nokia-9000-add-on-software
application x-ns-proxy-autoconfig
application x-oleobject
application x-olescript
application x-p3d
application x-pcn
application x-pdf
application x-perl
application x-pn-realaudio
application x-pn-realmedia
application x-pointplus
application x-rad-powermedia
application x-sh
application x-shar
application x-shockwave-flash
application x-sprite
application x-stuffit
application x-tar
application x-tcl
14
WatchGuard System Manager
Page 23

Typ e Subtype Reference (where available)
application x-tex
application x-texinfo
application x-troff
application x-troff-man
application x-troff-me
application x-troff-ms
application x-ustar
application x-wais-source
application x-watchguard-cloaked
application x-webbasic
application x-wintalk
application x-wls
application x-wms-LogStats
application x400-bp
application xml RFC 3023
application zip Lindner
audio *
audio 32kadpcm RFC 2421, RFC 2422
audio basic RFC 2045, RFC 2046
audio echospeech
audio vnd.qcelp
audio voxware
audio x-aiff
audio x-mpeg
audio x-mpeg-2
audio x-wav
chemical *
chemical x-cdx
chemical x-cif
chemical x-chem3d
chemical x-cmdf
chemical x-cml
chemical x-daylight-smiles
chemical x-csml
chemical x-galactic-spc
chemical x-gaussian-input
chemical x-gaussian-cube
Reference Guide 15
Page 24

Typ e Subtype Reference (where available)
chemical x-isostar
chemical x-jcamp-dx
chemical x-kinemage
chemical x-mdl-molfile
chemical x-mdl-rxnfile
chemical x-macmolecule
chemical x-macromode1-input
chemical x-mopac-input
chemical x-pdb
chemical x-xyz
chemical x-vmd
drawing *
drawing x-dwf
graphics *
graphics x-inventor
image *
image cgm Francis
image fif
image g3fax
image gif RFC 2045, RFC 2046
image ief RFC 1314
image jpeg RFC 2045, RFC 2046
image naplps Ferber
image png Randers-Pehrson
image prs.btif Simon
image tiff
image vnd.dwg Moline
image vnd.dxf Moline
image vnd.fastbidsheet Becker
image vnd.fpx Spencer
image vnd.net-fpx Spencer
image vnd.svf Moline
image vnd.xiff S. Martin
image wavelet
image x-cals
image x-cmu-raster
16
WatchGuard System Manager
Page 25

Typ e Subtype Reference (where available)
image x-cmx
image x-dwg
image x-dxf
image x-mgx-dsf
image x-ms-bmp
image x-photo-cd
image x-pict
image x-png
image x-portable-anymap
image x-portable-bitmap
image x-portable-graymap
image x-portable-pixmap
image x-rgb
image x-svf
image x-xbitmap
image x-xwindowdump
image xpm
message *
message delivery-status RFC 1894
message disposition-notification RFC 2298
message external-body RFC 2045, RFC 2046
message http RFC 2616
message news RFC 1036, H. Spencer
message partial RFC 2045, RFC 2046
message rfc822 RFC 2045, RFC 2046
model *
model iges Parks
model mesh RFC 2077
model vnd.dwf Pratt
model vrml RFC 2077
multipart *
multipart alternative RFC 2045, RFC 2046
multipart appledouble Fals trom
multipart byteranges RFC 2068
multipart digest RFC 2045, RFC 2046
multipart encrypted RFC 1847
Reference Guide 17
Page 26

Typ e Subtype Reference (where available)
multipart form-data RFC 2388
multipart header-set Crocker
multipart mixed RFC 2045, RFC 2046
multipart parallel RFC 2045, RFC 2046
multipart related RFC 2387
multipart report RFC 1982
multipart signed RFC 1847
multipart voice-message RFC 2421, RFC 2423
text *
text css RFC 2318
text enriched RFC 1896
text html RFC 2854
text javascript
text plain RFC 2046, RFC 3676
text richtext RFC 2045, RFC 2046
text sgml RFC 1874
text tab-separated-values Lindner
text uri-list RFC 2483
text vbscript
text vnd.abc Allen
text vnd.fmiflexstor Hurtta
text vnd.in3d.3dml Powers
text vnd.in3d.spot Powers
text vnd.latex-z Lubos
text x-setext
text x-speech
text xml RFC 3023
video *
video mpeg RFC 2045, RFC 2046
video mpeg-2
video quicktime Lindner
video vdo
video vivo Wolfe
video vnd.motorola.video McGinty
video vnd.motorola.videop McGinty
video vnd.vivo
video x-ms-asf
18
WatchGuard System Manager
Page 27

Typ e Subtype Reference (where available)
video x-msvideo
video x-sgi-movie
workbook *
workbook formulaone
x-conference x-cooltalk
x-form x-openscape
x-model x-mesh
x-music x-midi
x-script x-wfxclient
x-world *
x-world x-3dmf
x-world x-svr
x-world x-vream
x-world x-vrml
x-world x-vrt
x-world x-wvr
Reference Guide 19
Page 28

20
WatchGuard System Manager
Page 29
3
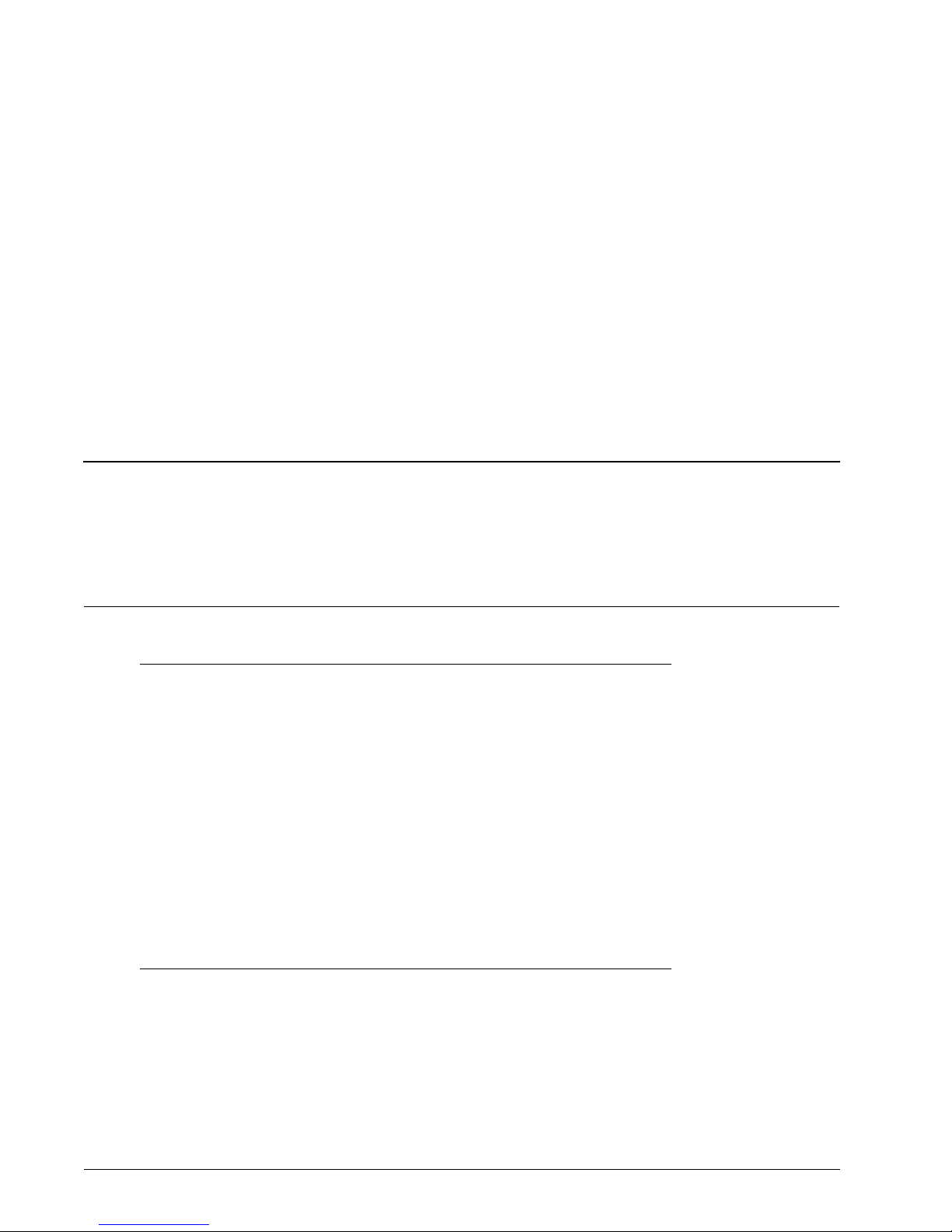
Services and Ports
Well-known services are a mixture of port number and transport protocol for specified, standard
software applications. This chapter contains tables that list service names, port number, protocol, and
description.
Ports Used by WSM and Fireware
The WatchGuard Firebox, management station, and WatchGuard servers use specified ports during
usual operations.
Port # Protocol Purpose
4100 TCP Authentication service
4107
4115
4103
4105
4117
4118
4110
4112
4113
4109 TCP Secure access to SOHO and Edge Fireboxes with a
5003 TCP and UDP WebBlocker
TCP WatchGuard Log Server
TCP WatchGuard Firebox configuration and
management
TCP WatchGuard Management Server
web browser
Reference Guide 21
Page 30

Ports Used by Microsoft Products
Ports Used by Microsoft Products
Many Firebox users want to create policies that specifically allow or block Microsoft applications. Here
is a list of ports used by some Microsoft products.
Port # Protocol Purpose
137, 138 UDP Browsing
67, 68 UDP DHCP Lease
135 TCP DHCP Manager
138
139
135 TCP DNS Administration
53 UDP DNS Resolution
139 TCP Event Viewer
139 TCP File Sharing
137, 138
139
138 UDP NetLogon
137, 138
139
139 TCP Performance Monitor
1723
47
137, 138
139
139 TCP Registry Editor
139 TCP Server Manager
137, 138
139
139 TCP User Manager
139 TCP WinNT Diagnostics
137, 138
139
42 TCP WINS Replication
135 TCP WINS Manager
137 TCP WINS Registration
UDP
TCP
UDP
TCP
UDP
TCP
TCP
IP
UDP
TCP
UDP
TCP
UDP
TCP
Directory Replication
Logon Sequence
Pass Through Validation
PPTP
Printing
Tru sts
WinNT Secure Channel
Port(s) Protocol Purpose
135 TCP Client/Server Communications
135 TCP Exchange Administrator
143 TCP IMAP
993 TCP IMAP (SSL)
389 TCP LDAP
22
WatchGuard System Manager
Page 31

Port(s) Protocol Purpose
636 TCP LDAP (SSL)
102 TCP MTA - X.400 over TCP/IP
110 TCP POP3
995 TCP POP3 (SSL)
135 TCP RCP
25 TCP SMTP
137 UDP SMB
138 UDP SMB
139 TCP SMB
445 TCP/UDP MS-DS (Directory Services)
119 TCP NNTP
563 TCP NNTP (SSL)
Well-Known Services List
Well-Known Services List
In addition to the ports used by services described above, WatchGuard supplies a list of well-known
services. Because software companies regularly add new services, this is not a full list of all possible
services. For more information, refer to:
www.iana.org/assignments/port-number
Service Name Port # Protocol Description
tcpmux 1 TCP/UDP TCP Port Service Multiplexer
compressnet 2,3 TCP/UDP Management Utility
rje 5 TCP/UDP Remote Job Entry
echo 7 TCP/UDP Echo
discard 9 TCP/UDP Discard
systat 11 TCP/UDP Active Users
daytime 13 TCP/UDP Daytime
qotd 17 TCP/UDP Quote of the Day
msp 18 TCP/UDP Message Send Protocol
chargen 19 TCP/UDP Character Generator
ftp-data 20 TCP/UDP File Transfer [Default Data]
ftp 21 TCP/UDP File Transfer [Control]
ssh 22 TCP/UDP SSH Remote Login Protocol
telnet 23 TCP/UDP Te ln et
smtp 25 TCP/UDP Simple Mail Transfer
nsw-fe 27 TCP/UDP NSW User system FE
msg-icp 29 TCP/UDP MSG ICP
msg-auth 31 TCP/UDP MSG Authentication
s
Reference Guide 23
Page 32

Well-Known Services List
Service Name Port # Protocol Description
dsp 33 TCP/UDP Display Support Protocol
time 37 TCP/UDP Time
rap 38 TCP/UDP Route Access Protocol
rlp 39 TCP/UDP Resource Location Protocol
graphics 41 TCP/UDP Graphics
nameserver 42 TCP/UDP Host Name Server
nicname 43 TCP/UDP whois
mpm-flags 44 TCP/UDP MPM Flags
mpm 45 TCP/UDP MPM
mpm-snd 46 TCP/UDP MPM Send
ni-ftp 47 TCP/UDP NI FTP
auditd 48 TCP/UDP Digital Audit Daemon
tacacs 49 TCP/UDP Login Host Protocol (TACACS)
re-mail-ck 50 TCP/UDP Remote Mail Checking Protocol
la-maint 51 TCP/UDP IMP Logical Address Maintenance
xns-time 52 TCP/UDP XNS Time Protocol
domain 53 TCP/UDP Domain Name Server
xns-ch 54 TCP/UDP XNS Clearinghouse
isi-gl 55 TCP/UDP ISI Graphics Language
xns-auth 56 TCP/UDP XNS Authentication
xns-mail 58 TCP/UDP XNS Mail
ni-mail 61 TCP/UDP NI MAIL
acas 62 TCP/UDP ACA Services
whois++ 63 TCP/UDP whois++
covia 64 TCP/UDP Communications Integrator (CI)
tacacs-ds 65 TCP/UDP TACACS-Database Service
sql*net 66 TCP/UDP Oracle SQL*NET
bootps 67 TCP/UDP Bootstrap Protocol Server
bootpc 68 TCP/UDP Bootstrap Protocol Client
tftp 69 TCP/UDP Trivial File Transfer
gopher 70 TCP/UDP Gopher
netrjs-1 71 TCP/UDP Remote Job Service
netrjs-2 72 TCP/UDP Remote Job Service
netrjs-3 73 TCP/UDP Remote Job Service
netrjs-4 74 TCP/UDP Remote Job Service
deos 76 TCP/UDP Distributed External Object Store
vettcp 78 TCP/UDP vettcp
finger 79 TCP/UDP Finger
www-http 80 TCP/UDP World Wide Web HTTP
24
WatchGuard System Manager
Page 33

Service Name Port # Protocol Description
hosts2-ns 81 TCP/UDP HOSTS2 Name Server
xfer 82 TCP/UDP XFER utility
mit-ml-dev 83 TCP/UDP MIT ML device
ctf 84 TCP/UDP Common Trace Facility
mit-ml-dev 85 TCP/UDP MIT ML device
mfcobol 86 TCP/UDP Micro Focus Cobol
kerberos 88 TCP/UDP Kerberos
sug-mit-tug 89 TCP/UDP SU/MIT Telnet gateway
dnsix 90 TCP/UDP DNSIX Secure Application Token Map
mit-dov 91 TCP/UDP MIT Dover Spooler
npp 92 TCP/UDP Network Printing Protocol
dcp 93 TCP/UDP Device Control Protocol
objcall 94 TCP/UDP Tivoli Object Dispatcher
supdup 95 TCP/UDP SUPDUP
dixie 96 TCP/UDP DIXIE Protocol Specification
swift-rvf 97 TCP/UDP Swift Remote Virtual File Protocol
tacnews 98 TCP/UDP TAC News
metagram 99 TCP/UDP Metagram Relay
newacct 100 TCP [unauthorized use]
hostname 101 TCP/UDP NIC Host Name Server
iso-tsap 102 TCP/UDP ISO-TSAP
gppitnp 103 TCP/UDP Genesis Point-to-Point Trans Net
acr-nema 104 TCP/UDP ACR-NEMA Digital Imag. Comm. 300
cso 105 TCP/UDP CCSO name server protocol
csnet-ns 105 TCP/UDP Mailbox Name Nameserver
3com-tsmux 106 TCP/UDP 3COM-TSMUX
rtelnet 107 TCP/UDP Remote Telnet Service
snagas 108 TCP/UDP SNA Gateway Access Server
pop2 109 TCP/UDP Post Office Protocol - Version 2
pop3 110 TCP/UDP Post Office Protocol - Version 3
sunrpc 111 TCP/UDP SUN Remote Procedure Call
mcidas 112 TCP/UDP McIDAS Data Transmission Protocol
auth(ident) 113 TCP/UDP Authentication Service
audionews 114 TCP/UDP Audio News Multicast
sftp 115 TCP/UDP Simple File Transfer Protocol
ansanotify 116 TCP/UDP ANSA REX Notify
uucp-path 117 TCP/UDP UUCP Path Service
sqlserv 118 TCP/UDP SQL Services
nntp 119 TCP/UDP Network News Transfer Protocol
Well-Known Services List
Reference Guide 25
Page 34

Well-Known Services List
Service Name Port # Protocol Description
cfdptkt 120 TCP/UDP CFDPTKT
erpc 121 TCP/UDP Encore Expedited RPC
smakynet 122 TCP/UDP SMAKYNET
ntp 123 TCP/UDP Network Time Protocol
ansatrader 124 TCP/UDP ANSA REX Trader
locus-map 125 TCP/UDP Locus PC-Interface Net Map
unitary 126 TCP/UDP Unisys Unitary Login
locus-con 127 TCP/UDP Locus PC-Interface Conn Server
gss-xlicen 128 TCP/UDP GSS X License Verification
pwdgen 129 TCP/UDP Password Generator Protocol
cisco-fna 130 TCP/UDP cisco FNATIVE
cisco-tna 131 TCP/UDP cisco TNATIVE
cisco-sys 132 TCP/UDP cisco SYSMAINT
statsrv 133 TCP/UDP Statistics Service
ingres-net 134 TCP/UDP INGRES-NET Service
epmap 135 TCP/UDP DCE-RPC Endpoint resolution
profile 136 TCP/UDP PROFILE naming system
netbios-ns 137 TCP/UDP NETBIOS Name Service
netbios-dgm 138 TCP/UDP NETBIOS Datagram Service
netbios-ssn 139 TCP/UDP NETBIOS Session Service
imap 143 TCP/UDP Internet Message Access Protocol
news 144 TCP/UDP NewS
jargon 148 TCP/UDP Jargon
sql-net 150 TCP/UDP SQL-NET
bftp 152 TCP/UDP Background File Transfer
sgmp 153 TCP/UDP SGMP
sqlsrv 156 TCP/UDP SQL Service
pcmail-srv 158 TCP/UDP PCMail Server
sgmp-traps 160 TCP/UDP SGMP-TRAPS
snmp 161 TCP/UDP SNMP
snmptrap 162 TCP/UDP SNMPTRAP
cmip-man 163 TCP/UDP CMIP/TCP Manager
cmip-agent 164 TCP CMIP/TCP Agent
smip-agent 164 UDP CMIP/TCP Agent
namp 167 TCP/UDP NAMP
rsvd 168 TCP/UDP RSVD
send 169 TCP/UDP SEND
xyplex-mux 173 TCP/UDP Xyplex MUX
xdmcp 177 TCP/UDP X Display Manager Control Protocol
26
WatchGuard System Manager
Page 35

Service Name Port # Protocol Description
NextStep 178 TCP/UDP NextStep Window Server
bgp 179 TCP/UDP Border Gateway Protocol
unify 181 TCP/UDP Unify
irc 194 TCP/UDP Internet Relay Chat Protocol
at-rtmp 201 TCP/UDP AppleTalk Routing Maintenance
at-nbp 202 TCP/UDP AppleTalk Name Binding
at-3 203 TCP/UDP AppleTalk Unused
at-echo 204 TCP/UDP AppleTalk Echo
at-5 205 TCP/UDP AppleTalk Unused
at-zis 206 TCP/UDP AppleTalk Zone Information
at-7 207 TCP/UDP AppleTalk Unused
at-8 208 TCP/UDP AppleTalk Unused
qmtp 209 TCP/UDP Quick Mail Transfer Protocol
z39.50 210 TCP/UDP ANSI Z39.50 (WAIS)
ipx 213 TCP/UDP IPX
imap3 220 TCP/UDP Interactive Mail Access Protocol v3
fln-spx 221 TCP/UDP Berkeley rlogind with SPX auth
rsh-spx 222 TCP/UDP Berkeley rshd with SPX auth
backweb 371 UDP BackWeb
ulistserv 372 TCP/UDP Unix Listserv
netware-ip 396 TCP/UDP Novell Netware over IP
biff 512 UDP Used by mail system to notify users
exec 512 TCP Remote process execution
login 513 TCP/UDP Login Host Protocol
who 513 UDP Maintains databases showing who’s
who
cmd 514 TCP Like exec, but automatic
syslog 514 UDP logging facilities
printer 515 TCP/UDP Spooler
talk 517 TCP/UDP Talk protocol
ntalk 518 TCP/UDP another Talk
utime 519 TCP/UDP Unixtime
router 520 UDP RIP local routing process (on site)
timed 525 TCP/UDP Timeserver
tempo 526 TCP/UDP Newdate
courier 530 TCP/UDP Rpc
conference 531 TCP/UDP Chat
netnews 532 TCP/UDP Readnews
netwall 533 TCP/UDP For emergency broadcasts
uucp 540 TCP/UDP Uucpd
Well-Known Services List
Reference Guide 27
Page 36

Well-Known Services List
Service Name Port # Protocol Description
uucp-rlogin 541 TCP/UDP Uucp-rlogin Stuart Lynne
klogin 543 TCP/UDP Kerberos (v4/v5)
kshell 544 TCP/UDP krcmd Kerberos (v4/v5)
dhcpv6-client 546 TCP/UDP DHCPv6 Client
dhcpv6-server 547 TCP/UDP DHCPv6 Server
cybercash 551 TCP/UDP Cybercash
remotefs 556 TCP/UDP Rfs server
9pfs 564 TCP/UDP Plan 9 file service
whoami 565 TCP/UDP Whoami
msn 569 TCP Microsoft Network
doom 666 TCP/UDP Doom Id Software
kerberos-adm 749 TCP/UDP Kerberos administration
webster 765 TCP/UDP Network dictionary
phonebook 767 TCP/UDP Phone
socks 1080 TCP/UDP Socks
hermes 1248 TCP/UDP Hermes
lotusnote 1352 TCP/UDP Lotus Notes
netware-csp 1366 TCP/UDP Novell NetWare Comm Service Platform
novell-lu6.2 1416 TCP/UDP Novell LU6.2
netopia 1419
ms-sql-s 1433 TCP/UDP Microsoft-SQL-Server
ms-sql-m 1434 TCP/UDP Microsoft-SQL-Monitor
winframe 1494 TCP WinFrame
watcom-sql 1498 TCP/UDP Watcom-SQL
ingreslock 1524 TCP/UDP Ingres
groupwise 1677 TCP GroupWise
nfs 2049 TCP/UDP Network File Server
www-dev 2784 TCP/UDP World Wide Web - development
Squid 3128 TCP/UDP Web proxy/caching service --
ccmail 3264 TCP/UDP Cc:mail/lotus
ICQ 2109
Firstclass 3000
compuserve 4144 TCP CompuServe Online
rfe 5002 TCP/UDP Radio free ethernet
aol 5190 TCP America Online
x11 6000 TCP/UDP X Window System (through 6063)
font-service 7100 TCP/UDP X Font Service
8000
4000
30004
UDP
TCP
TCP
UDP
TCP FirstClass (ftp channel on 510 TCP)
Netopia Virtual Office
frequently scanned for vulnerabilities
Used for chat
28
WatchGuard System Manager
Page 37

Service Name Port # Protocol Description
nas 8000 TCP/UDP NCD Network Audio Server
iphone 6670 TCP for connecting to the phone server
iphone 22555 UDP for audio
iphone 25793 TCP for the address server, in 4.x and 5.0
iphone 1490 TCP for the conference engine in 4.x and 5.0
Well-Known Services List
Reference Guide 29
Page 38

Well-Known Services List
30
WatchGuard System Manager
Page 39

4
WebBlocker Content
WatchGuard WebBlocker, together with the HTTP proxy and the HTTPS proxy, supplies web site
filtering for the content of the web pages your users open in their browsers. WebBlocker uses a URL
database created and controlled by SurfControl.
Searching for Blocked Sites
To see whether WebBlocker is blocking a web site as part of a category block, go to WatchGuard
Test-a-Site on the SurfControl web site.
1 Open a web browser and go to:
http://mtas.surfcontrol.com/mtas/WatchGuardTest-a-Site.asp
2 Type the URL or IP address of the site to check.
3 Click Test Site.
The search engine tells you whether the site is on the SurfControl list. You can also request that
the URL be added to the SurfControl list.
Reference Guide 31
Page 40

Searching for Blocked Sites
WebBlocker Categories
The WebBlocker database contains 11 groups of categories with 54 individual categories. A web site is
added to a category when the contents of the web site meet the correct criteria. Web sites that give
opinion or educational material about the subject matter of the category are not included. For
example, the illegal drugs category denies sites that tell how to use marijuana. It does not deny sites
with information about the historical use of marijuana.
Group Category Description of Content
Adult Adult/Sexually
Explicit
Alcohol &
Tobacco
• Sexually oriented or erotic full or partial nudity
• Depictions or images of sexual acts, including inanimate objects
used in a sexual manner
• Erotic stories and textual descriptions of sex acts
• Sexually exploitive or sexually violent text or graphic
• Bondage, fetishes, genital piercing
• Adult products including sex toys, CD-ROMs, and videos
• Adult services including videoconferencing, escort services, and
strip clubs
• Explicit cartoons and animation
• Recipes, instructions, or kits for manufacturing or growing illicit
substances, including alcohol, for purposes other than industrial
usage
• Glamorizing, encouraging, or instructing on the use of, or
masking the use of, alcohol, tobacco, illegal drugs, or othe
rsubstances that are illegal to minors
• Alcohol and tobacco manufacturers’ commercial Web sites
• Information on “legal highs”: glue sniffing, misuse of
prescription drugs, or abuse of other legal substances
• Distributing alcohol, illegal drugs, or tobacco free or for a charge
• Displaying, selling, or detailing use of drug paraphernalia
Gambling
Intimate Apparel
& Swimwear
Sex Education
Note: SurfControl does not include sites that discuss medicinal drug
use, industrial use, or public debate on the issue of legalizing certain
drugs. SurfControl also does not include sites sponsored by a public or
private agency that provide educational information on drug use.
• Online gambling or lottery web sites that invite the use of real
money
• Virtual casinos and offshore gambling ventures
• Virtual sports leagues, sports picks, and betting pools
• Lingerie, negligee, or swimwear modeling
• Model fan pages; fitness models/sports celebrities
• Fashion or glamour magazines online; clothing catalogs
• Beauty and cosmetics
• Modeling information and agencies
• Pictures or text advocating the proper use of contraceptives,
including condom use, the correct way to wear a condom, and
how to put a condom in place
• Sites related to discussion about the use of the Pill, IUDs, and
other types of contraceptives
• Discussion sites on how to talk to your partner about diseases,
pregnancy, and respecting boundaries
Note: Not included in this category are commercial sites that sell sexual
paraphernalia. These sites are filtered through the Adult category.
32
WatchGuard System Manager
Page 41

Searching for Blocked Sites
Group Category Description of Content
Tasteless &
Offensive
• Offensive or violent language, including through jokes, comics, or
satire
• Excessive use of profanity or obscene gesticulation
Crime Criminal Activity Advocating, instructing, or giving advice on performing illegal acts,
such as:
• Phone service theft
• Evading law enforcement
• Lock-picking
• Fraud
• Plagiarism/cheating
• Burglary techniques
Hacking
• Promotion, instruction, or advice on the questionable or illegal
use of equipment and/or software for purpose of hacking
passwords, creating viruses, or gaining access to other computers
and/or computerized communication systems
• Sites that provide instruction or work-arounds for our filtering
software
• Cracked software
• Pirated software download sites
• Multimedia download sites
Intolerance &
Hate
• Advocating or inciting degradation of or attacks on specified
populations or institutions based on associations such as religion,
race, nationality, gender, age, disability, or sexual orientation
• Promoting a political or social agenda that is supremacist in
nature or exclusionary of others based on their race, religion,
nationality, gender, age, disability, or sexual orientation
• Holocaust revisionist/denial sites
• Coercion or recruitment for membership in a gang* or cult**
• Militancy, extremist
Violence
Note: SurfControl does not include news, historical, or press incidents
that may include the above criteria in this category (except in graphic
examples).
*A gang is defined as a group whose primary activities are the
commission of felonious criminal acts, which has a common name or
identifying sign or symbol, and whose members individually or
collectively engage in criminal activity in the name of the group.
**A cult is defined as a group whose followers have been deceptively
and manipulatively recruited and retained through undue influence
such that followers’ personalities and behavior are altered. Leadership is
all-powerful, ideology is totalistic, the will of the individual is
subordinate to the group, and the group is outside society.
• Portraying, describing, or advocating physical assault against
humans, animals, or institutions
• Depictions of torture, mutilation, gore, or horrific death
• Advocating suicide or self-mutilation
• Instructions, recipes, or kits for making bombs or other harmful
or destructive devices
• Excessive use of profanity or obscene gesticulation
Note: We do not block news, historical, or press incidents that may
include the above criteria (except in graphic examples).
Reference Guide 33
Page 42

Searching for Blocked Sites
Group Category Description of Content
Entertainment Entertainment
Weapons
Spyware
Phishing & Fraud
Illegal Drugs
Games
Hobbies &
Recreation
Kids’ Sites
• Online purchasing or ordering information, including lists of
prices and dealer locations
• Any page or site predominantly containing, or providing links to,
content related to the sale of guns, weapons, ammunition, or
poisonous substances
• Displaying or detailing the use of guns, weapons, ammunition or
poisonous substances
Note: Weapons are defined as something (as a club, knife, or gun) used
to injure, defeat, or destroy.
• Sites that provide or promote information gathering or tracking
that is unknown to, or without the explicit consent of, the end user
or the organization
• Sites that carry maicious executables or viruses
• 3rd party monitoring and other unsolicited commercial software
• Spyware and Malware “Phone Home” destinations
• Phishing
• Phone service theft advice
• Plagaiarism & chating, including the sale of research papers
• Recipes, instructions, or kits for manufacturing or growing illicit
substances for purposes other than industrial usage
• Glamorizing, encouraging, or instructing in the use of or masking
the use of alcohol, tobacco, illegal drugs, or other substances that
are illegal to minors
• Information on “legal highs”: glue sniffing, misuse of
prescription drugs, or abuse of other legal substances
• Distributing illegal drugs free or for a charge
• Displaying, selling, or detailing the use of drug paraphernalia
• Television, movies, music, and video programming guides
• Comics, jokes, movie, video, or sound clips
• Discussion forums on television, movies, music, and videos
• Online magazines and reviews on the entertainment industry
• Circuses, theatre, variety magazines, and radio
• Broadcasting firms and technologies (satellite, cable, etc.)
• Book reviews and promotions, publising houses, comic books, and
poetry
• Jokes, comedians, any site designed to be funny or satirical
• Online museums, galleries, artist sites (including sculpture,
photography, etc.)
• Celebrity fan sites
• Horoscopes
• City Guides
• Game playing or downloading; game hosting or contest hosting
• Tips and advice on games or obtaining cheat codes (“cheatz”)
• Journals and magazines dedicated to game playing
• Recreational pastimes such as collecting, gardening, or kit
airplanes
• Outdoor recreational activities such as hiking, camping, or rock
climbing
• Tips or trends focused on a specific art, craft, or technique
• Online publications on a specific pastime or recreational activity
• Online clubs, associations, or forums dedicated to a hobby
• Child-centered sites and sites published by children
34
WatchGuard System Manager
Page 43

Group Category Description of Content
Sports
• Team or conference web sites
• National, international, college, or professional scores and
schedules
• Sports-related online magazines or newsletters
Streaming Media
• Streaming media files or events (any live or archived audio or
video file)
• Internet TV and radio
Travel
• Airlines and flight booking agencies
• Accommodation information
• Travel package listings
• City guides and tourist information
• Weather bureaus
• Car rentals
Arts
• Museums, galleries, artist sites (including sculpture,
photography, etc.)
• Performing arts (theatre, vaudeville, opera, symphonies, etc.)
• Dance companies, studios, and training
• Book reviews and promotions, variety magazines, and poetry
Personal Education
• Educational institutions, including pre-, elementary, secondary,
and high schools; universities
• Educational sites: pre-, elementary, secondary, and high schools;
universities
• Distance education and trade schools
• Online teacher resources (lesson plans, etc.)
• Topic-specific search engines (e.g. anthropology)
Society & Culture
• Home life and family-related topics, including parenting tips,
gay/lesbian/bisexual (non-pornographic sites), weddings, births,
and funerals
• Foreign cultures, socio-cultural information
Job Search &
Career
Development
Personals &
Dating
Religion
• Employment agencies, contractors, job listings, career
information
• Career searches, career-networking groups
• Singles listings, matchmaking and dating services
• Advice for dating or relationships; romance tips and suggestions
• Churches, synagogues, and other houses of worship
• Any faith or religious beliefs, including non-traditional religions
such a Wicca and witchcraft
Philanthropic &
Professional
Orgs.
• Philanthropic and charity organizations
• Environmental organizations
• Professional associations
• Labor unions
• Social organizations
Fashion & Beauty
• Fashion or glamour magazines online
• Beauty and cosmetics
Shopping Advertisements
Food & Drink
• Banner ad servers
• Recipes, cooking instruction and tips, food products, and wine
advisors
• Restaurants, cafes, eateries, pubs, and bars
• Food/drink magazines and reviews
• Manufacturers and distillers
Searching for Blocked Sites
Reference Guide 35
Page 44

Searching for Blocked Sites
Group Category Description of Content
Computers Chat Web-based chat
Motor Vehicles
Real Estate
Shopping
Computing &
Internet
Hosting Sites
Proxies &
Translator s
Web-based Email
Downloads
Ringtones/
Mobile Phone
Downloads
Peer-to-Peer
• Car reviews, vehicle purchasing or sales tips, parts catalogs
• Auto trading, photos, discussion of vehicles including
motorcycles, boats, cars, trucks, and RVs
• Journals and magazines on vehicle modification, repair, and
customization
• Online automotive enthusiast clubs
• Home, apartment, and land listings
• Rental or relocation services
• Tips on buying or selling a home
• Real estate agents
• Home improvement
• Internet malls and online auctions
• Department stores, retail stores, company catalogs online
• Online downloadable product warehouses; specialty items for sale
• Freebies, shareware, and software downloads
• Freebies or merchandise giveaways
• Reviews, information, computer buyer’s guides, computer parts
and accessories, and software
• Computer/software/Internet companies, industry news, and
magazines
• Sites that desing and/or maintain web pages including individual
web designers
• Design and/or maintain web pages including web designers
• Personal storage or backup
• Pay-to-surf sites
• Web sites that host business and individual web pages
• Remote proxies or anonymous surfing
• Peer-to-peer sharing
• Web-based e-mail accounts
• Downloadable (non-streaming) movie, video, or sound clips
• Downloadable PDA software, including themes and graphics
• Freeware and shareware sites
• Personal storage or backup
• Clip art, fonts, and animated gif pages
• Providers of mobile phone downloads, including:
- Ringtones,
- Logos
- Backgrounds
- Screensavers
- Games
• Peer-to-peer file sharing clients
• Peer-to-peer file sharing servers
36
WatchGuard System Manager
Page 45

Group Category Description of Content
Spam URLs
• URLs found in spam, including these topics:
- Computing
- Finance & Stocks
- Entertainment
- Games
- Health & Medicine
- Humor & Novelties
- Personal & Dating
- Products & Services
- Shopping
- Travel
Infrastructure
• Content delivery networks
• XML Reference Schemas
• Web analytics and statistics services
• Transaction servers
• Corporate image servers
News News
• Newspapers online
• Headline news sites, newswire services, and personalized news
services
• Weather sites
Blogs & Forums
• Weblogs (blog) sites
• Newsgroups
• Opinion or discussion forums
Search Photo Searches
Search Engines
Research Finance &
Investment
• Sites that provide resources for photo and image searches
• General search engines (Yahoo, AltaVista, Google, AOL)
• Stock quotes, stock tickers, and fund rates
• Online stock or equity trading
• Investing advice or contacts for trading securities
• Money management/investment services or firms
• General finances and companies that advise thereof
• Accountants, actuaries, banks, mortgages, and general insurance
companies
Government
• Government services such as taxation, armed forces, customs
bureaus, and emergency services
• Local government sites
• Political debate, canvassing, election information, and results
• Local, national, and international political sites
Health &
Medicine
• General health such as fitness and well-being
• Alternative and complementary therapies
• Medical information about ailments, conditions, and drugs
• Medical reference
• Hospital, medical insurance
• Dentistry, optometry, and other medical-related sites
• General psychiatry and mental well-being sites
• Promoting self-healing of physical and mental abuses, ailments,
and addictions
• Psychology, self-help books, and organizations
Reference
• Personal, professional, or educational reference
• Online dictionaries, maps, and language translation sites
• Census, almanacs, and library catalogues
• Topic-specific search engines
Searching for Blocked Sites
Reference Guide 37
Page 46

Searching for Blocked Sites
Group Category Description of Content
Other
Uncategorized
Politics
Business
• Political parties
• Political debate, canvassing, election information and results
• Conspiracy theorists & alternative government views that are not
hate-based
• General business corporate web sites
• International and multi-national large general business corporate
sites
• Business Associations
• Basic business sites, such a s FedEx, that enable organizations to
manage their necessary daily business tasks.
• Sites that are not included in the defined categories
• Sites that are not categorized
38
WatchGuard System Manager
Page 47

5
Types of Policies in Fireware
This chapter gives a list of the pre-defined policies included with your Firebox management software,
their protocols, and their ports. It also gives special information about circumstances that could have
an effect on the security of some policies.
In this chapter, policies are divided into two groups—policies that are controlled by a packet filter and
policies that are controlled by a proxy.
Packet Filter Policies
Packet filter policies examine the source and destination headers of each packet. Packets are allowed or
denied based on if the headers appear to come from and go to trusted addresses.
Any
Use an Any policy only to allow all traffic between two specified trusted IP or network addresses. An
Any policy opens a “hole” through the Firebox, and allows all traffic to flow freely between specified
hosts. We recommend that the Any policy be used only for traffic through a VPN.
The Any policy is different from other policies. For example, if you allow FTP only to a specified host, all
other FTP sessions to other hosts are denied by that policy (unless you have also configured other FTP
policies). The Any policy does not deny like other policies.
You also cannot use an Any policy unless specified IP addresses, network addresses, host aliases, group
names, or user names are used in the From or To lists. If not, the Any policy does not operate.
Characteristics
• Internet Protocol(s): Any
• Port Number(s): Any port
User Guide 39
Page 48

Packet Filter Policies
Archie
Archie is a search protocol used to find files on FTP servers. We recommend that you use the available
web interfaces to Archie. Search the Internet to find a current list of Archie servers.
External hosts can be spoofed. The Firebox cannot make sure that these packets were sent from the
correct location. You can configure your Firebox to add the source IP address to the Blocked Sites list
when an incoming archie connection is denied. You can use all of the usual log options with archie.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 1525
auth
The Authentication Server protocol (AUTH) is now called the Identification Protocol (IDENT). Refer to
IDENT for more information about this policy.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 113
BGP
Border Gateway Protocol (BGP) is the routing protocol used across most of the Internet. It is a highly
configurable protocol that can add redundancy to links to and from the Internet for LANs. We
recommend that you use this service only if you have enabled and configured BGP in the dynamic
routing processes in the Fireware® configuration.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 179
Citrix
Citrix, or Independent Computing Architecture (ICA), is an application protocol used by Citrix software
applications such as Winframe and Metaframe Presentation Server (MPS). Winframe gives access to a
Windows computer from different types of clients that use TCP port 1494. Citrix MPS 3.0 uses ICA with
Session Reliability over TCP port 2598. If you use Citrix MPS, you must add a custom policy for TCP port
2598. If you add the Citrix policy, you could put your network security at risk because it allows remote
access to computers through the firewall without authentication. The threat to a Winframe or MPS
server includes denial-of-service attacks. We recommend that you use VPN options to give more
security for ICA connections. You can use all of the usual log options with WinFrame.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 1494
40
WatchGuard System Manager
Page 49

Packet Filter Policies
Clarent-Command
Clarent Corporation supplies IP telephone technology to mainstream carriers and service providers.
Clarent products allow voice-over-IP between Clarent gateways across the Internet. This policy gives
support to the Clarent v3.0 product and later.
Clarent products use two sets of ports, one for gateway-to-gateway communications (UDP ports 4040,
4045, and 5010) and one for gateway-to-command center communications (UDP ports 5001 and
5002). Use the Clarent-command policy for the gateway-to-command center communications.
Allow incoming connections only from specified external gateways to your gateway or command
center.
Clarent also gives support for the use of PCAnywhere for management. Refer to the PCAnywhere policy
notes for more information.
The Clarent-command policy could put network security at risk because it allows traffic inside the
firewall based only on network address. This is not a trusted method of authentication. In addition,
your Clarent server could receive denial-of-service attacks in this configuration. Where possible, we
recommend that you use VPN options to give more security for Clarent-command connections.
Characteristics:
• Internet Protocol(s): UDP
• Port Numbers(s): 5001, 5002
Clarent-Gateway
Clarent Corporation supplies IP telephone technology to mainstream carriers and service providers.
Clarent products allow voice-over-IP between Clarent gateways across the Internet. This policy gives
support to the Clarent v3.0 product and later.
Clarent products use two sets of ports, one for gateway-to-gateway communications (UDP ports 4040,
4045, and 5010) and one for gateway-to-command center communications (UDP ports 5001 and
5002). Use the Clarent-command policy for the gateway-to-command center communications.
Allow incoming connections only from specified external gateways to your gateway or command
center.
Clarent also gives support for the use of PCAnywhere for management. Refer to the PCAnywhere policy
notes for more information.
The Clarent-gateway policy could put network security at risk because it allows traffic inside the
firewall based only on network address. This is not a trusted method of authentication. In addition,
your Clarent server could receive denial-of-service attacks in this configuration. Where possible, we
recommend that you use VPN options to give more security for Clarent-gateway connections.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 4040, 4045, 5010
User Guide 41
Page 50

Packet Filter Policies
CU-SeeMe
CU-SeeMe is a software application used to do video conferencing through the Internet. For CU-SeeMe
to operate through the Firebox, you must make sure that you are not on a network that uses outgoing
dynamic NAT.
The CU-SeeMe protocol makes you configure this policy for traffic going in to and out of your network.
The CU-SeeMe policy uses the correct ports to allow the use of CU-SeeMe versions 2.X and 3.X.
CU-SeeMe Version 2.X operates on UDP port 7648. Version 3.X operates on UDP port 7648, UDP port
24032 (for H.323 conferences), and TCP port 7648 (video conference directories).
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Numbers(s): TCP 7648, UDP 7648, UDP 24032
DHCP-Server or DHCP-Client
Dynamic Host Configuration Protocol (DHCP) gives a way to allocate dynamic IP addresses to devices
on a network.
Characteristics
• Internet Protocol(s): TCP
• DHCP-Server Port Number(s): 67
• DHCP-Client Port Number(s): 68
DNS
Domain Name Service (DNS) matches host names to IP addresses. A DNS policy is enabled in the
default configuration. The DNS policy allows UDP DNS traffic, as well as TCP zone transfers, to occur as
specified. All of the usual log options can be used with DNS.
Characteristics
• Internet Protocol(s): TCP (for server-server zone transfers), UDP (for client-server lookups)
• Port Number(s): TCP 53, UDP 53
Entrust
The Entrust Authority Public Key distribution application protocol passes public keys to a trusted
third-party organization for verification.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 709, 710
42
WatchGuard System Manager
Page 51

Packet Filter Policies
finger
finger is an application protocol used to get information about users on a given host. It is easy for a
hacker to use this information against you. We do not recommend that you put finger servers on the
trusted interface.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 79
FTP
File Transfer Protocol (FTP) is used to move files across the Internet. An FTP packet filter will not apply
the FTP proxy rule set to any traffic. To proxy FTP traffic, use the FTP proxy policy. We recommend that
incoming FTP be allowed only to public FTP servers located behind the Firebox.
External hosts can be spoofed. WatchGuard cannot verify that these packets were actually sent from
the correct location. You can configure the Firebox to add the source IP address to the Blocked Sites list
whenever an FTP connection to a computer protected by the Firebox is denied. The packet filter and
proxy policy included in WatchGuard Policy Manager both handle the data channel for active and
passive FTP sessions. All of the usual log options can be used with FTP.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 21
Gopher
Gopher is a data-retrieval protocol developed at the University of Minnesota. Gopher is not frequently
used, as most users use HTML.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 70, but servers can be configured to use other ports
GRE
Generic Routing Encapsulation Protocol (GRE) is used together with Point-to-Point Tunneling Protocol
(PPTP) to create virtual private networks (VPNs) between clients or between clients and servers.
Characteristics
• Internet Protocol(s): GRE
User Guide 43
Page 52

Packet Filter Policies
HBCI
The Home Banking Computer Interface (HBCI) is a standard created for bank customers and
manufacturers of banking products.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 3000
HTTP
An HTTP packet filter will not apply the HTTP proxy rule set to any traffic. To proxy HTTP traffic, use the
HTTP proxy policy. We recommend that HTTP be allowed only to public HTTP servers located behind
the Firebox.
External hosts can be spoofed. WatchGuard cannot verify that these packets were actually sent from
the correct location. You can configure the Firebox to add the source IP address to the Blocked Sites list
whenever an HTTP connection to a computer protected by the Firebox is denied. All of the usual log
options can be used with HTTP.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 80
HTTPS
HTTPS is a secure and encrypted version of the HTTP protocol. The client and the web server set up an
encrypted session on TCP port 443. Because this session is encrypted, the proxy cannot examine
packet contents using a proxy. This policy uses a packet filter to examine the connection.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 443
44
WatchGuard System Manager
Page 53

Packet Filter Policies
IDENT
The Identification Protocol (IDENT) is a protocol used to match TCP connections to a user name. It is
used most frequently by large public SMTP and FTP servers. It is used for logs, but you cannot trust the
information it gives, as attackers can change their servers to have them send back incorrect
information. IDENT uses false information to hide internal user information.
When you use incoming static NAT with SMTP, you might see packets that come from the remote mail
server being denied with destination port 113. In these cases, you can add an IDENT policy to Policy
Manager. Configure IDENT to allow incoming connections to: Firebox. This enables outgoing mail
messages from behind the Firebox to the few SMTP servers on the Internet that use IDENT.
If you are not using dynamic NAT, allow IDENT to the IP address of your email server.
We recommend that IDENT policies be allowed to and from the Firebox, but know that hackers can use
IDENT to collect user names.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 113
IGMP
The Internet Group Management Protocol (IGMP) is the standard for IP multicasting on the Internet. It
is used to control host memberships in multicast groups on a single network.
Characteristics
• Internet Protocol(s): IGMP
IMAP
Internet Mail Access Protocol (IMAP) is an application layer protocol for getting email or bulletin board
messages on a remote email server as if the messages were local. You can access email stored on an
IMAP server from many locations (such as home, work, or laptop) without moving messages.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 143
IPSec
Internet Protocol Security (IPSec) is a framework for a set of protocols for security at the network or
packet layer of network communications. It is a VPN tunneling protocol with encryption.
Characteristics
• Internet Protocol(s): UDP, encapsulated security payload (ESP), authentication header (AH)
• Port Number(s): UDP 4500
User Guide 45
Page 54

Packet Filter Policies
IRC
Internet Relay Chat (IRC) is a system for Internet chatting. To use IRC you must have an IRC client and
Internet access. The IRC client is a software application on your computer that sends and receives
messages to and from an IRC server. The IRC server makes sure that all messages are sent to all users in
the chat session.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 6667
Intel-Video-Phone
Intel Video Phone is a real-time multimedia application based on H.323. H.323 is an international
standard for conferencing over TCP/IP networks. This policy does not filter for dangerous content. It
does not support QpS or RSVP protocol, and it does not support NAT.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 522, 1720
Kerberos-v4 and Kerberos-v5
The Kerberos network authentication protocol is an authentication system developed by the
Massachusetts Institute of Technology (MIT). Kerberos enables two computers to exchange private
information across an open network using authentication for security.
Characteristics
• Internet Protocol(s): TCP, UDP
• Kerberos v 4 Port Numbers(s): UDP 750
• Kerberos v 5 Port Number(s): TCP 88, UDP 88
L2TP
Layer 2 Tunneling Protocol (L2TP) is an extension to the PPP protocol that enables ISPs to operate
virtual private networks.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 1701
46
WatchGuard System Manager
Page 55

Packet Filter Policies
LDAP
Lightweight Directory Access Protocol (LDAP) is an open-standard protocol for using online directory
services. The protocol operates with Internet transport protocols, such as TCP. You can use LDAP to
access stand-alone directory servers or X.500 directories.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 389
LDAP-SSL
Lightweight Directory Access Protocol over TLS/SSL (LDAP-SSL) is used with Windows 2000 to give
more security when you access Active Directory.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 636
Lotus Notes
Lotus Notes is a client/server platform for conferencing, databases, and email. It is also used to create
and use documents. This policy enables the proprietary Lotus Notes protocol. Because the protocol
uses encapsulation and tunneling, and gives access to internal data, we do not recommend the Lotus
Notes policy for addresses out of your trusted networks.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 1352, UDP 1352
MS-SQL-Monitor
Microsoft SQL Monitor is used to monitor Microsoft SQL databases.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 1434, UDP 1434
MS-SQL-Server
Microsoft SQL Server is usually used to make a remote connection to a Microsoft SQL database.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 1433, UDP 1433
User Guide 47
Page 56

Packet Filter Policies
MS-Win-Media
Microsoft Windows Media Server is a proprietary protocol developed by Microsoft to supply unicast
streams. It enables bidirectional connections that enable users to go forward, go back, or pause the
playback of unicast streams.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 80, 1755
NetMeeting
NetMeeting is a product developed by Microsoft Corporation that enables groups to teleconference
across the Internet. It is included with Microsoft’s Internet Explorer web browser. This policy is based on
the H.323 protocol and does not filter for dangerous content. It does not support QoS or RSVP protocol,
and it does not support NAT.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 389, 1720
NFS
The Network File System (NFS) protocol is a client server software application created by Sun
Microsystems to allow all network users to get access to shared files kept on computers of different
types.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 2049, UDP 2049
NNTP
Network News Transfer Protocol (NNTP) is used to transmit Usenet news articles.
The best procedure to use NNTP is to set internal hosts to internal news servers and external hosts to
news feeds. In most conditions, NNTP must be enabled in two directions. If you operate a public
newsfeed, you must allow NNTP connections from all external hosts. WatchGuard cannot make sure
that these packets were sent from the correct location.
You can configure the Firebox to add the source IP address to the Blocked Sites list when an incoming
NNTP connection is denied. All of the usual log options can be used with NNTP.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 119
48
WatchGuard System Manager
Page 57

Packet Filter Policies
NTP
Network Time Protocol (NTP) is a protocol built on TCP/IP that controls local timekeeping. It
synchronizes computer clocks with other clocks located on the Internet.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 123 , UDP 123
OSPF
Open Shortest Path First (OSPF) is a routing protocol developed for IP networks based on the link-state
algorithm. OSPF is quickly replacing the use of RIP on the Internet because it gives smaller, more
frequent updates to routing tables and makes networks more stable.
Characteristics
• Internet Protocol(s): OSPF
• Port Number(s): Any port
pcAnywhere
pcAnywhere is a software application used to get remote access to Windows computers. To enable this
protocol, add the PCAnywhere policy. Then, allow access from the hosts on the Internet that must get
access to internal pcAnywhere servers, and to the internal pcAnywhere servers.
pcAnywhere is not a very secure policy and can put network security at risk, because it allows traffic
through the firewall without authentication. Also, your pcAnywhere server can receive denial-ofservice attacks. We recommend that you use VPN options to give more security.
Characteristics
• Internet Protocol(s): UDP, TCP
• Port Number(s): UDP 22, TCP 5631, UDP 5632, TCP 65301
Ping
You can use ping to confirm if a host can be found and is operating on the network. To find DOS-based
or Windows-based traceroute packets, configure a ping policy.
Outgoing ping is a good tool for troubleshooting. We do not recommend you allow ping connections
to your trusted network.
Characteristics
• Internet Protocol(s): ICMP (type: 8, code: 255)
User Guide 49
Page 58

Packet Filter Policies
POP2 and POP3
POP2 and POP3 (Post Office Protocol) are email transport protocols, usually used to get a user’s email
from a POP server.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 109 (POP2), and 110 (POP3)
PPTP
PPTP is a VPN tunnel protocol with encryption. It uses one TCP port (for negotiation and authentication
of a VPN connection) and one IP protocol (for data transfer) to connect the two peers in a VPN.
Configure the PPTP policy to allow access from Internet hosts to an internal network PPTP server. PPTP
cannot get access to hosts’ static NAT because NAT cannot forward IP protocols. Because this policy
enables a tunnel to the PPTP server and the Firebox cannot examine packets in the tunnel, use of this
policy must be controlled. Be sure to use the most current version of PPTP.
Characteristics
• Transport Protocol(s): TCP
• Internet Protocol(s): GRE
• PPTP Negotiation Port Number(s): 1723
RADIUS and RADIUS-RFC
The Remote Authentication Dial-In User Service (RADIUS) supplies remote users with secure access to
corporate networks. RADIUS is a client-server system that keeps authentication information for users,
remote access servers, and VPN gateways in a central user database that is available to all servers.
Authentication for the network occurs from one location. RADIUS uses an authentication key that
identifies an authentication request to the RADIUS client.
In RFC 2865, the server port used by RADIUS changed from port 1645 to 1812. Make sure you select the
policy that matches your implementation.
Characteristics
• Internet Protocol(s): UDP
• RADIUS policy Port Number(s): UDP 1645
• RADIUS-RFC policy Port Number(s): UDP 1812
50
WatchGuard System Manager
Page 59

Packet Filter Policies
RADIUS-Accounting and RADIUS-Acct-RFC
The Remote Authentication Dial-In User Service (RADIUS) Accounting policy supplies accounting
information to administrators of networks that use RADIUS authentication. RADIUS is a client-server
system that keeps authentication information for users, remote access servers, and VPN gateways in a
central user database that is available to all servers. The RADIUS server is also notified when the
authenticated session starts and stops. This information can be helpful for accounting.
In RFC 2866, the server port used by RADIUS changed from port 1646 to 1813. Make sure you select the
policy that matches your implementation.
Characteristics
• Internet Protocol(s): UDP
• RADIUS-Accounting policy Port Number(s): UDP1646
• RADIUS-ACCT-RFC policy Port Number(s): UDP 1813
RDP
The Microsoft Remote Desktop Protocol (RDP) supplies remote display and input abilities over network
connections for Windows software applications that operate on a server.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 3389
RIP
Routing Information Protocol (RIP) is a link state routing protocol developed in the early years of
routing. Its limitations make it inappropriate for use in the Internet, but it can be useful in small
networks. We recommend that you use this service only if you have enabled and configured RIP in the
dynamic routing processes in the Fireware configuration.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 520
RSH
Remote Shell (RSH) is used access the command line of a remote host computer. Because it is not
encrypted, we do not recommend you allow any RSH connections to computers protected by the
Firebox without the use of a VPN.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 514
User Guide 51
Page 60

Packet Filter Policies
RealPlayerG2
Media streaming protocol v7 and v8.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 80, 554
Rlogin
Remote login (RLogin) is a UNIX command that allows an approved user to log in to other UNIX
computers on a network. After the login, the user can do all the operations the host has approved, such
as read, edit, or delete files. Because it does not use encryption, we recommend you do not allow
Rlogin connections to computers protected by the Firebox.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 513
SecurID
RSA SecurID Two-Factor Authentication give more security to the user authentication procedure.
Created by Security Dynamics Technologies, Inc., it uses SecurID tokens to generate codes and ACE/
Server software to corroborate the codes.
Characteristics
• Internet Protocol(s): TCP and UDP
• Port Number(s): TCP 5510, UDP 5500
SMB (Windows Networking)
Windows uses Server Message Block (SMB) to share files, computers, printers, and other network
resources.
If you set up replication, you can see many attempts to use the port mapper service on port 135. When
this fails, SMB begins to use port 42. Refer to the RFC for DCE for more instructions.
SMB through the Firebox is not secure and we do not recommend it, unless used through a VPN
connection. These configuration settings are to be used only if there is no other alternative, and
policy settings must specify internal and external hosts.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 139, TCP 445, UDP 137, UDP 138, UDP 445
52
WatchGuard System Manager
Page 61

Packet Filter Policies
SMTP
The SMTP packet filter policy allows SMTP traffic (email) without using the SMTP proxy.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 25
SNMP
Simple Network Management Protocol (SNMP) is used to collect information about and to configure
remote computers. This can be dangerous. Many Internet attacks use SNMP. Because SNMP can cause
changes in a network if enabled, carefully review alternatives and record logs for all connections.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 161
SNMP-T rap
Simple Network Management Protocol (SNMP) traps are notification messages that an SNMP agent (for
example, a router) sends to a network management station. These messages usually report an
important event that must be examined.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s):162
SQL*Net
Oracle uses one port for its SQL*Net software. By default, this port is 1526/TCP or port 1521/TCP. Or, edit
the tnsnames.ora file to change the port. To allow SQL*Net through the Firebox, set up a policy for the
port that your SQL*Net server uses, with a protocol of TCP, and a client port of ignore. Then set up
incoming access from the allowed external hosts to the SQL*Net server.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 1521, 1526
SQL-Server
The SQL-Server policy is used to give access to SYBASE Central and SQL Advantage software.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 10000
User Guide 53
Page 62

Packet Filter Policies
SSH
Secure Shell (ssh) is a free application protocol that allows remote login, command control, and the
movement of files between computers. It gives strong authentication and secure (encrypted)
connections. We recommend the use of ssh because it is more secure than more vulnerable protocols
such as telnet, rssh, and rlogin.
UNIX versions are available from www.ssh.com, and information on versions for Windows can be found
at F-Secure (http://www.f-secure.com
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 22
SSL-VPN
This is the built-in policy template for SSL-VPN.
Characteristics
• Internet Protocol(s): TCP
).
• Port Number(s): 443
SunRPC
Sun Remote Procedure Call (Sun RPC) was developed by Sun Microsystems for connections between
clients and servers in the Sun network file system.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 111, UDP 111
Syslog
Syslog is a policy used to record operating system events on UNIX hosts. Syslog data is usually enabled
on a firewall to collect data from a host outside the firewall.
The Syslog port is blocked in the default Firebox configuration. To allow one log host to collect logs
from more than one Firebox:
• Remove port 514 from the Blocked Ports list
• Add the WatchGuard® Logging policy to Policy Manager
It is usually not secure to allow syslog traffic through the Firebox. It is possible for hackers to fill
syslogs with log entries. If the syslog is full, it is more difficult to see an attack. Also, the disk
frequently fills up and the attack is not recorded.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 514
54
WatchGuard System Manager
Page 63

Packet Filter Policies
TACACS
TACACS user authentication is a system that uses user accounts to authenticate users into a dial-up
modem pool. This removes the need to keep copies of accounts on a UNIX system. TACACS does not
support TACACS+ or RADIUS.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 49
TACACS+
TACACS+ user authentication is a system that uses user accounts to authenticate users into a dial-up
modem pool. This eliminates the need to keep copies of accounts on a UNIX system. TACACS+
supports RADIUS.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 49
TCP
This policy serves as the default policy for all TCP connections, and other policies override it. TCP
connections that do not match your specified policies do not complete unless you also configure
TCP-UDP, TCP, or the TCP Proxy. This policy does not enable FTP, which operates only with an FTP policy.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 0 (Any)
TCP-UDP
This policy serves as the default policy for all TCP and UDP connections, and other policies override it.
Connections that do not match specified policies in Policy Manager do not complete unless TCP-UDP,
TCP and UDP, or the TCP Proxy are also configured in Policy Manager. This policy does not enable active
mode FTP, which operates only with an FTP policy.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 0 (Any), UDP 0 (Any)
Telnet
The telnet policy is used to log in to a remote computer. It is almost the same as dial-up access, but the
connection is made across a network.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 23
User Guide 55
Page 64

Packet Filter Policies
Timbuktu
Timbuktu Pro is remote control and file transfer software used to get access to Windows computers.
The protocol uses TCP port 1417 and UDP port 407. Add the Timbuktu policy and allow access from the
hosts on the Internet that must get access to internal Timbuktu servers, and to the internal Timbuktu
servers.
Timbuktu is not a very secure software application and can put network security at risk. It allows traffic
inside the firewall without authentication. In addition, the Timbuktu server can receive denial-ofservice attacks. We recommend that you use VPN options for more security.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 1417, UDP 407
Time
The Time policy is almost the same as NTP. It is used to synchronize clocks between hosts on a network.
Time is usually less accurate and less efficient than NTP across a WAN. We recommend that you use NTP.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 37, UDP 37
Traceroute
Traceroute is a software application that creates maps of networks. It is used for network
troubleshooting, network route troubleshooting, and finding the Internet service provider of a site. The
WatchGuard Traceroute policy controls UNIX-based, UDP-style Traceroute only. For a DOS-based or
Windows-based Traceroute packet filter, use the Ping policy. For more information about the Ping
policy, see “Ping” on page 49.
Traceroute uses ICMP and UDP packets to create paths across networks. It uses the UDP TTL field to
send back packets from each router and computer between a source and a destination. If you allow
traceroute to computers protected by your Firebox®, this can enable a hacker to create a map of your
private network.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): 33401-65535
UDP
This policy serves as the default policy for all UDP connections, and other policies override it. UDP
connections that do not match specified policies in Policy Manager do not complete unless UDP, TCPUDP, or the TCP Proxy are also configured in Policy Manager.
• Internet Protocol(s): UDP
• Port Number(s): 0 (Any)
56
WatchGuard System Manager
Page 65

Packet Filter Policies
UUCP
Unix-to-Unix Copy (UUCP) is a UNIX tool and protocol that enables one computer to send files to
another computer. This tool is not used frequently, as users more often use FTP, SMTP, and NNTP to
transfer files.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 540
WAIS
Wide Area Information Services (WAIS) is a protocol you can use to find documents on the Internet.
Thinking Machines Incorporated first developed WAIS. Some web sites use WAIS to look for searchable
indices, but it is not used frequently.
WAIS is created on the ANSI Z39.50 search protocol, and the words Z39.50 and WAIS refer to the same
technology.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 210, but servers can be (and frequently are) configured on other ports, much like
HTTP servers
WinFrame
Citrix ICA is a protocol used by Citrix for its software applications, which includes the Winframe
product. Winframe gives access to Windows from different types of clients. Citrix uses TCP port 1494 for
its ICA protocol. Citrix MPS 3.0 uses Session Reliability by default. This changes the ICA protocol to use
TCP 2598. If you use Citrix MPS, you must add a policy for TCP port 2598.
A WinFrame policy could put your network security at risk because it allows traffic through the firewall
without authentication. In addition, your Winframe server can receive denial-of-service attacks. We
recommend that you use VPN options to give more security for ICA connections. You can use all of the
usual log options with WinFrame.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 1494
WG-Auth
The WatchGuard Authentication policy allows users to authenticate to the Firebox.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 4100
User Guide 57
Page 66

Packet Filter Policies
WG-Firebox-Mgmt
The WatchGuard Firebox Management policy allows configuration and monitoring connections to be
made to the Firebox. We recommend that you allow this policy only to the management station. The
policy is usually set up on the trusted interface.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 4103, 4105, 4117, 4118
WG-Logging
The WatchGuard Logging policy is necessary only if a second Firebox must access a Log Server on the
trusted interface of a Firebox. If there is only one Firebox, this policy is not necessary.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 4107, 4115
WG-Mgmt-Server
When you use the WatchGuard Management Server Setup wizard to configure a Management Server,
the wizard automatically adds this policy to the gateway Firebox. It controls incoming connections to
the Management Server.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 4110, 4112, 4113
WG-SmallOffice-Mgmt
The WatchGuard Small Office Management policy allows you to make a secure connection to SOHO
and Firebox X Edge devices from WatchGuard System Manager.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): TCP 4109
WG-WebBlocker
The WatchGuard WebBlocker policy allows connections to the WebBlocker Server.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 5003, UDP 5003
58
WatchGuard System Manager
Page 67

Packet Filter Policies
WHOIS
The WHOIS protocol gives information about the administrator of web sites and networks. It is
frequently used to find the administrator of a different web site.
To filter WHOIS traffic, add a WHOIS policy that allows connections to the WHOIS server (such as
rs.internic.net).
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 43
X11
The X Windows System Protocol has components that are used to create graphic desktops, which
include windows, colors, displays, and screens. X11 also supplies a flow of events that show the
interaction between a user and a computer input device (such as a mouse, keyboard, and so on).
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 6000-6063
User Guide 59
Page 68

Packet Filter Policies
Proxy Policies
This section reviews the proxy policies supplied by the WatchGuard® System Manager. A proxy policy
opens packets, strips out forbidden data types in the packet content, and assembles the packets again
using the source and destination headers of the proxy.
You configure and activate proxies the same way you add packet filter policies.
DNS-proxy
Domain Name Service (DNS) matches host names to IP addresses. The DNS proxy policy examines the
contents of DNS packets to help protect your DNS servers from hackers. It puts limits on the type of
operations allowed in a DNS query and can look for specified patterns in query names.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 53, UDP 53
FTP-proxy
File Transfer Protocol (FTP) is used to send files from one computer to a different computer over a TCP/
IP network. The FTP client is usually a computer. The FTP server can be a resource that keeps files on the
same network or on a different network. The FTP client can be in one of two modes for data transfer:
active or passive. In active mode, the server starts a connection to the client on source port 20. In
passive mode, the client uses a previously negotiated port to connect to the server. The Fireware FTP
proxy monitors and scans these FTP connections between your users and the FTP servers they
connect to.
Characteristics
• Internet Protocol(s): TCP
• Port Number: 21
H323-proxy
If you use Voice-over-IP (VoIP) in your organization, you can add an H.323 proxy policy to open the
ports necessary to enable VoIP through your Firebox. This proxy policy has been created to work in a
NAT environment to maintain security for privately addressed conferencing equipment behind the
Firebox.
H.323 is used commonly on older videoconferencing equipment and voice installations. With H.323,
the key component of call management is known as the “GateKeeper.” The H.323 proxy supports only
peer-to-peer connections.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 1720, UDP 1719
60
WatchGuard System Manager
Page 69

Packet Filter Policies
HTTP-proxy
Hyper Text Transfer Protocol (HTTP) is a request/response protocol between clients and servers. The
HTTP client is usually a web browser. The HTTP server is a remote resource that keeps or creates HTML
files, images, and other content. When the HTTP client starts a request, it establishes a Transmission
Control Protocol (TCP) connection on port 80. An HTTP server listens for requests on port 80. When it
receives the request from the client, the server replies with the requested file, an error message, or
some other information.
The WatchGuard policy “HTTP Proxy” is not the same as an HTTP caching proxy. An HTTP
caching proxy controls the caching of Web data. If you use an external caching proxy, you must
enable (by adding policies) any outgoing policies that are necessary for your organization. If
you do not, outgoing TCP connections do not operate correctly.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 80 (but servers can operate on any port, a common alternative is 8080)
HTTPS-proxy
HTTPS (Hypertext Transfer Protocol over Secure Socket Layer, or HTTP over SSL) is a request/response
protocol between clients and servers used for secure communications and transactions. HTTPS is more
secure than HTTP because HTTPS uses a digital certificate to encrypt and decrypt user page requests
as well as the pages that are returned by the web server. The HTTPS client is usually a web browser. The
HTTPS server is a remote resource that keeps or creates HTML files, images, and other content.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 443
POP3-proxy
Post Office Protocol v.3 (POP3) is a protocol that moves email messages from an email server to an
email client on a TCP connection on port 110. Most Internet-based email accounts use POP3. With
POP3, an email client contacts the email server and checks for any new email messages. If it finds a new
message, it downloads the email message to the local email client. After the message is received by the
email client, the connection is closed.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 110
User Guide 61
Page 70

Packet Filter Policies
SIP-proxy
If you use Voice-over-IP (VoIP) in your organization, you can add a SIP (Session Initiation Protocol) proxy
policy to open the ports necessary to enable VoIP through your Firebox. These proxy policies have
been created to work in a NAT environment to maintain security for privately-addressed conferencing
equipment behind the Firebox.
SIP is a newer standard that is more common in hosted environments, where only endpoint devices
such as phones are hosted at your business location and a VoIP provider manages the connectivity.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 5060, UDP 5060
SMTP-proxy
Simple Mail Transfer Protocol (SMTP) is the Internet standard protocol used to transmit and receive
email messages. Usually SMTP servers are public servers.
messages and email content. The proxy scans SMTP messages for a number of filtered parameters, and
compares them against the rules set in the proxy configuration.
You use the SMTP proxy to control email
When you use incoming static NAT with SMTP, you might see packets that come from the remote mail
server being denied with destination port 113. In these cases, you can add an IDENT policy to Policy
Manager. Configure IDENT to allow incoming connections to: Firebox. This enables outgoing mail
messages from behind the Firebox to the few SMTP servers on the Internet that use IDENT.
If you do not want to use the SMTP proxy but want to use SMTP and have SMTP operate correctly, add a
packet filter SMTP policy that uses TCP protocol and port 25.
Characteristics
• Internet Protocol(s): TCP
• Port Number(s): 25
TCP-UDP-proxy
The TCP-UDP proxy is included for these protocols on non-standard ports: HTTP, HTTPS, SIP, and FTP.
For these protocols, the TCP-UDP proxy relays the traffic to the correct proxies for the protocols or
allows you to allow or deny traffic. For other protocols, you can select to allow or deny traffic.
Characteristics
• Internet Protocol(s): TCP, UDP
• Port Number(s): TCP 0 (Any), UDP 0 (Any)
62
WatchGuard System Manager
Page 71

Packet Filter Policies
TFTP-proxy
Trivial File Transfer Protocol (TFTP) is a simple form of FTP that uses very small amounts of memory. It is
used to transfer small files between hosts on the same network. Some manufacturers use the TFTP
protocol to send periodic updates to VoIP equipment under management. If your equipment requires
TFTP for updates, make sure you add a TFTP policy to your Firebox configuration to allow these
connections.
Characteristics
• Internet Protocol(s): UDP
• Port Number(s): UDP 69
User Guide 63
Page 72

Packet Filter Policies
64
WatchGuard System Manager
Page 73

6
Resources
Many resources are available to help you learn more about network security. This chapter gives
different sources of information frequently used by the development and technical support teams at
WatchGuard to learn more about network security. The editorial comments included in this chapter are
supplied to help you decide which resources are most helpful to you. These comments are from the
LiveSecurity editorial team. For more information like this, log in to the LiveSecurity site and look over
the LiveSecurity archive at:
www.watchguard.com/archive
The types of resources included in this chapter are:
• Publishers
• Non-fiction books
• Fiction books
• White papers and requests for comments
• Mailing lists
• General information technology and security web sites
• White hat web sites
• Gray hat web sites
• Other useful web sites
• Dictionaries of computer terminology
• RSS feeds and blogs
• Podcasts
Reference Guide 65
Page 74

Publishers
Publishers
Some publishers focus on network security in their works.
Syngress
O'Reilly
No Starch
Books
Non-Fiction
Zwicky, Elizabeth D. et al; Building Internet Firewalls. Sebastopol: O'Reilly & Associates, 2000. ISBN
1565928717.
Publishes almost exclusively about networks and network security.
www.syngress.com/
Publishes many books on network security.
www.oreilly.com/pub/topic/security
Publishes selectively on secuirty, usually in-depth and with a quirky tone.
www.nostarch.com
Cheswick, et al; Firewalls and Internet Security: Repelling the Wily Hacker. Reading, MA: Addison Wesley
Longman, Inc., 2003. ISBN 020163466X.
Garfinkel and Spafford, Simson Garfinkel and Gene Spafford. Practical Unix and Internet Security.
Sebastopol: O'Reilly & Associates, 2003. ISBN 0596003234.
Kozierok, Charles. The TCP/IP Guide. San Francisco: No Starch Press, 2005. ISBN 159327047x.
McClure, Stewart; Scambray, Joel; and Kurtz, George. Hacking Exposed. Fifh Edition. McGraw-Hill
Publishing, 2005. ISBN 0072260815.
Schneier, Bruce. Applied Cryptography. Second Edition. New York: John Wiley & Sons, Inc., 1996. ISBN
0471117099.
Stevens, W. Richard. TCP/IP Illustrated. Reading MA: Addison Wesley Longman, Inc., 1994. ISBN
0201633469. (Note: This is a 3-volume set.)
Stoll, Cliff. Cuckoo’s Egg. Pocket Books, 1995. ISBN 0671726889.
Fiction
Mitnick, Kevin and Mullen, Timothy, et al. Stealing the Network: How to Own a Continent. Cambridge,
MA: Elsevier/Syngress, 2004. ISBN 1931836051.
Mullen, Timothy and Russell, Ryan, et al. Stealing the Network: How to Own an Identity. Cambridge, MA:
Elsevier/Syngress, 2005. ISBN 1597490067.
Russell, Ryan and Dubrawksky, Ido, et al. Stealing the Network: How to Own the Box. Cambridge, MA:
Elsevier/Syngress, 2005. ISBN 1931836876.
Levy, Johnny and Russell, Ryan, et al. Stealing the Network: How to Own a Shadow. Cambridge, MA:
Elsevier/Syngress, 2007. ISBN 1597490814.
Stephenson, Neal. Cryptonomicon. New York, NY: HarperCollins Publishers, 1999. ISBN 0060512806.
66
WatchGuard System Manager
Page 75

Mailing Lists
wg-users@watchguard.com
WatchGuard sponsors a listserv for our customers. For more information, see the Technical
Support chapter in the User Guide.
firewall-wizards@nfr.net
Firewall gurus from around the world discuss and answer all types of questions.
Full Disclosure
When Symantec bought Security Focus and its lists, suspicious security experts and network
administrators fled. Where did they go? Largely to Full Disclosure. Pros: Cannot be biased by any
vendor because it's completely unmoderated. First choice for posting latest discoveries by some
big-name researchers. Black-hat hackers like to harass this list, inadvertently providing useful
perspective on the "script kiddie" mindset. Con: Because it's unmoderated, this high-volume list
will drown you in 20 irrelevant flame-war e-mails for every on-topic comment. Net: You get what
you pay for, and this list is free. Try it briefly to familiarize yourself with it, but use Outlook rules to
divert Full Disclosure e-mail messages to a folder you can read at leisure.
VulnWatch and VulnDiscuss
These lists are, respectively, moderated and unmoderated. Pro: You can not only get security
advisories from vendors, you can also see what the rest of the IT community thinks and feels
about them. Con: Fairly large volume of highly technical alerts difficult for newcomers to
understand. Net: While you wouldn't want this as your only source of security news, it provides a
solid source for confirmation and alternate opinions on security trends.
Mailing Lists
General IT and Security Web Sites
First, a note to any intrepid beginner who is reading this: Not all of these sites are sponsored by good
guys. Some of them post malicious code that hackers use. Do not download or execute anything you
do not fully understand.
WatchGuard Frequently Asked Questions
www.watchguard.com/support/faqs
www.cerias.purdue.edu/
The Center for Education and Research in Information Assurance and Security (CERIAS) is
currently viewed as one of the world’s largest centers for research and education in areas of
information security that are crucial to the protection of critical computing and communication
infrastructure. CERIAS is unique among such national centers in its multidisciplinary approach to
the problems, ranging from purely technical issues (e.g., intrusion detection, network security,
etc.) to ethical, legal, educational, communicational, linguistic, and economic issues, and the
subtle interactions and dependencies among them.
www.gocsi.com
The Computer Security Institute (CSI) is the world's leading membership organization specifically
dedicated to serving and training the information, computer and network security professional.
Since 1974, CSI has been providing education and aggressively advocating the critical
importance of protecting information assets.
www.cerias.purdue.edu/homes/spaf/
Dr. Eugene Spafford is a professor of computer sciences and electrical and computer engineering
at Purdue University, where he has served on the faculty since 1987. He serves on a number of
advisory and editorial boards, and is internationally-known for his writing, research, and
speaking on issues of security and ethics. Spafford's current research interests are primarily in the
areas of information security, computer crime investigation and information ethics.
Spaf (as he is known to his friends, colleagues, and students) is Executive Director of the Purdue
CERIAS (Center for Education and Research in Information Assurance and Security), and was the
founder and director of the (superseded) COAST Laboratory. This is his homepage.
Reference Guide 67
Page 76

General IT and Security Web Sites
project.honeynet.org
The Honeynet Project is a non-profit research organization of security professionals dedicated to
information security. They have no products, services or employees, and all research is done on a
volunteer basis. Their goal is to learn the tools, tactics, and motives of the blackhat community
and share these lessons learned. Founded in October, 1999, all work is OpenSource and shared
with the security community.
www.infosecuritymag.com
Information Security is the enterprise security and risk managers' leading source of critical,
objective information on strategic and practical security issues. Information Security's team of
veteran security journalists and experts break down the security problems challenging
enterprises and provide practical resolutions.
www.interhack.net/pubs/fwfaq
This collection of Frequently Asked Questions and answers about Internet firewalls has been
compiled over the years from fora such as Usenet, mailing lists, and Web sites. If you have a
question, looking here to see whether it has been answered before posting your question is
good form. Don’t send your questions to the FAQ maintainers.
www.cerias.purdue.edu/coast/firewalls
This site provides the comprehensive list of resources associated with Internet firewalls. The list is
divided into sections to make finding information easier.
www.microsoft.com/technet/security
The Microsoft homepage for computer security resources.
csrc.nist.gov
National Institute of Standards and Technology, Computer Security Division.
www.networkcomputing.com
Network Computing magazine, part of the tech web business technology network, features
content covering general networking topics as well as specific security topics.
www.securityfocus.com
Formerly the preferred clearing house for security vulnerability announcements, Security Focus
lost prestige after Symantec bought them (many readers assumed Symantec would bias the
reporting). We haven't noticed any dramatic decline in quality, and we routinely use the site -especially its acclaimed Bugtraq list -- for information about new vulnerabilities. Pro: Often the
first place security researchers post their advisories. Has a great "Basics" reading room for IT
beginners. Cons: Advisories are posted in dense jargon difficult for beginners to comprehend.
Poorly organized site can make finding a specific item tricky. Net: Authoritative, comprehensive,
definitely a useful arrow in any sys admin's quiver.
NewsNow
NewsNow's UK-based spiders and bots automatically search over 15,000 news sources and
return live links with the results, updated every five minutes. They offer dozens of newsfeeds (but
do we really need to hear the latest on Michael Jackson every five minutes?). The feed you want
is called "Security" (listed under "Internet" in the left column. Don't choose "Hacking;" you'll get
countless articles about various hackers in legal trouble.) Pro: Comprehensive, up-to-the-minute
survey of worldwide Internet security. Con: The same information repeats countless times as
various online sources report it. Net: A great glimpse of security issues worldwide.
68
WatchGuard System Manager
Page 77

The Register
This is not the first place you'll learn of emerging threats, but when you hear of one, depend on
The Reg for the most honest, no-hype summary of the issue. Pro: Plain-English writing style is
great for IT beginners. Check out their "BOFH" series for hilariously bleak parodies of a network
administrator's life. Con: Their scathing anti-Microsoft bias can get heavy-handed. Net: If you
have to explain a new vulnerability to non-technical superiors, you'll appreciate The Register's
style.
Secunia
Pro: This list notifies on every vulnerability under the sun. Con: Secunia mostly reproduces
vendor releases, without analysis or suggested remediation for IT beginners. And did I mention
they report on everything under the sun? If you don't know Linux/Unix, you won't understand a
lot of the bulletins. Net: High volume, but all on topic (unlike FullDisclosure). Try it to see if it's for
you.
White Hat Web Sites
American cinema of the 1930s, 40s, and early 50s, with their endless stream of big-city gangsters and
singing cowboys, popularized the metaphorical idea that "good guys" wear white hats and "bad guys"
reliably identify themselves by wearing black hats. Extending the tradition today, "white hat" computer
security researchers find security holes in commercial software, but instead of telling everyone, they
first inform the manufacturer of the flaw. Then they cooperate with the manufacturer in getting the
flaw fixed before announcing their discovery to the public. We appreciate the efforts of these good
guys.
White Hat Web Sites
Crypto-Gram
Bruce Schneier has two gifts you rarely see in one person: he is a bona fide cryptographic expert,
and he can write in clear English. This free e-newsletter is not an alert service. Rather, Schneier's
insights on security issues will, over time, teach you how to think about security in general; for
example, how to assess whether a "cure" costs more than the risk it addresses, and how to resist
falling for a great-sounding plan that doesn't actually provide added security.
Insecure.org
Check out the online home of the well-known security researcher Fyodor, who authored nmap,
the best port scanning tool available. From this site you can download nmap and 74 other
security tools from others, many of them excellent. Insecure.org serves as a repository for
numerous other security lists which may not have an archive of their own (such as
FullDisclosure). If you don't want to fill your Favorites with every security list (BugTraq,
FullDisclosure, Pen Test, and so on), bookmark this one site and you can find them all from here.
Microsoft TechNet
IT professionals running a Windows network look here for the latest Microsoft security bulletins.
Pro: Authoritative source for Microsoft security fixes. Con: Microsoft's alerts minimize the truly
bad implications of some vulnerabilities, sometimes unfairly. Bring a suspicious mind to the part
of each alert that talks about "mitigating factors" that supposedly reduce risk. Net: If you use
Windows, you've got to visit here at least monthly.
CERT.org
This government-funded source of security advisories describes itself as "a center to coordinate
communication among experts during security emergencies and to help prevent future
incidents." Pro: CERT does an excellent job of coordinating information when vulnerabilities are
found in the most commonly-used Internet resources. Con: Because their work is "official" and
because so many vendors can have a say in CERT's advisories, this is often the last entity to issue
a security advisory. Net: Pretty much the final word on anything Internet-related and not owned
by a private vendor. A must for your arsenal of resources.
Reference Guide 69
Page 78

Grey Hat Sites
Grey Hat Sites
We characterize these security researchers as "grey hats" because, unlike white hats, they might not
inform the appropriate manufacturer before publicly revealing their findings and posting exploit code
(often passed off euphemistically as "proof of concept" code). Technically they're not breaking laws or
acting maliciously, like "black hats." But announcing security holes before vendors can fix them is like
giving an army a map of the castle they're attacking, with a big red arrow marking the secret entrance.
Grey hats commonly claim their behavior contributes to overall security by making vendors watch
themselves more diligently. Whether that is true is a battle we'll leave to someone else.
Nonetheless, "grey hat" sites are worth inspecting when you want to understand more about how a
particular vulnerability works. These sites are often the first to reveal new vulnerabilities, much sooner
than you'll get the info from the appropriate vendor. When trying to prioritize how urgently you need
to patch flawed software on your network, flaws where the exploit code is publicly posted should go to
the top of your list. To learn whether exploit code is publicly available, monitor our LiveSecurity® alerts,
and check some of the following sites.
Ryan1918.com
On this site, you’ll find hackers selling and trading exploits, including botnets and trojans. In true
script-kiddy style, this forum in not online 100% of the time. If not, try again later - so far, it has
always returned.
Packetstormsecurity.org
This site offers a repository of the Top 20 security tools, advisories, and exploits, updated
throughout the week.
K-otik.com
This French site is usually the first place you’ll find significant exploit code. They also archive
notable white papers in various languages, so multilingual administrators can get a world of
security instruction here.
2600.com
This Web site supplements the printed journal 2600 , the seminal, well-known "hacker's
quarterly," where programmers inform one another of new flaws, exploits, and attacks on
everything from networks to phone systems. Worth a read so you can realistically assess the
strength of your countermeasures.
Governmentsecurity.org
Despite its name, this site is not sponsored by a government. Like many of the other sites we've
recommended, it archives daily security news. But our favorite feature is the moderated security
forums, where you can discuss relevant topics (ranging from general network security, to how to
compile and run specific exploits) with other network administrators.
70
WatchGuard System Manager
Page 79

Other Web Sites
www.howstuffworks.com
Simple explanations of how all kinds of things, including system and network components,
work.
www.zebra.org/zebra/index.html
Online gnu zebra configuration document for Firebox users using dynamic routing protocols.
www.watchguard.com/support/advancedfaqs/log_sniffing.asp
Check here for information on a useful Network Packet Analyzer.
www.iana.org
Look here for lists of protocol number assignments and TCP and UDP port numbers.
www.telusplanet.com/public/sparkman/netcalc.htm
A network calculator.
www.winguides.com/registry/
A good site for information about the Windows registry.
www.watchguard.com/glossary/?nav=ic
Online glossary of security terms.
Dictionaries of Computer Terminology
vmyths.com
Some viruses you hear about are not real. Though each of virus vendor has a “virux hoax” page,
when we have to prove to a hysterical user that a problem doesn’t really exist, we like the writeups here.
slashdot.org
For fun, no self-respecting geek should miss viewing science, pop culture, and the world of
computers through the perspective of the IT-minded community (millions strong!) who
contribute to Slashdot.
Dictionaries of Computer Terminology
www.webopedia.com
www.whatis.com
info.astrian.net.jargon/
www.techweb.com/encylopedia/
Reference Guide 71
Page 80

Dictionaries of Computer Terminology
RSS Feeds
Rich Site Summary (RSS) is an XML-based Web standard for easily distributing news and other
information in syndication. In other words, RSS provides a format that delivers news from many sources
directly to your desktop.
Furthermore, WatchGuard® provides a free RSS feed, WatchGuard Wire, that covers many security
topics and, when combined with LiveSecurity® or LiveSecurity Informer, keeps you up to date with the
latest breaking security news.
During a network administrator's hectic day, it can be hard to find the time to browse the Web for all
the latest IT and network security news. Yet, sometimes this news could help you save your network
from the latest virulent worm. An RSS reader can provide you with a convenient, one-stop shop
consolidating news from all your favorite sources. Try out RSS and WatchGuard Wire. They are free, and
keep you informed while saving you time.
Resources:
www.watchguard.com/rss/Aboutrss.aspx
An introduction to the WatchGuard Wire RSS feed.
www.watchguard.com/rss/list.aspx
A Web archive of the latest WatchGuard Wire articles.
Security Feeds
www.watchguard.com/rss/watchguardwire.xml
WatchGuard Wire
www.securityfocus.com/rss/vulnerabilities.xml
SecurityFocus Latest Vulnerabilities
www.securityfocus.com/rss/news.xml
SecurityFocus news
www.sophos.com/virusinfo/infofeed/tenalerts.xml
Sophos Ten Latest Virms
www.sophos.com/virusinfo/infofeed/hoax.xml
Sophos Top Virus Hoaxes
www.sophos.com/virusinfo/infofeed/topten.xml
Sophos Top Virms Last Month
www.microsoft.com/technet/security/bulletin/secrss.aspx
Microsoft Security Bulletin Feed
www.2600.com/rss.xml
2600 (Hacker journal)
IT Related Feeds
slashdot.org/slashdot.rss
news.com.com/2547-1_3-0-5.xml
CNET News Main News Feed
news.com.com/2547-7343_3-0-5.xml
CNET News Enterprise Software Feed
72
WatchGuard System Manager
Page 81

news.com.com/2547-1001_3-0-5.xml
news.com.com/2547-1009_3-0-5.xml
news.com.com/2547-1035_3-0-5.xml
Fun Feeds
www.wired.com/news/feeds/rss2/0,2610,,00.xml
www.wired.com/news/feeds/rss2/0,2610,3,00.xml
www.wired.com/news/feeds/rss2/0,2610,2,00.xml
www.wired.com/news/feeds/rss2/0,2610,4,00.xml
dwlt.net/tapestry/dilbert.rdf
Dictionaries of Computer Terminology
CNET News Enterprise Hardware Feed
CNET News Security Feed
CNET News Networking Feed
Wired top stories
Wired technology stories
Wired culture stories
Wired political stories
Daily Dilbert
dwlt.net/tapestry/pa.rdf
Penny Arcade
Web Logs (Blogs)
F-Secure
This blog covers any kind of malware that spreads, and often has useful screen shots so you
know exactly what to watch out for.
Microsoft Security Resource Center (MSRC)
Run by the team that puts out Microsoft Security Bulletins, this is where you’ll get early
notification of what they plan to patch each month. After Patch Day, get more in-depth
explanation of Microsoft vulnerabilities at their Security Vulnerability R&D blog.
SANS Internet Storm Center
A great place to look for the earliest warning of emerging threats, especially if you prefer facts
over FUD. The “Handler’s Diary” is updated at least every day, sometimes more often.
The Security Skeptic
Dave Piscitello is a very knowledgeable security consultant who currently works as a Fellow of
ICANN’s Security and Stability Advisory Committee. His seasoned observations of network
security range from small-scale practical tips to questions about how to keep the Internet
working for decades to come.
Sunbelt
Sunbelt makes anti-spyware and anti-spam products, which means they survey the malware
scene every day. This is the spot where we often first hear of new threats. Though this is one of
the earliest places a new problem might be reported, the information is fact-based and reliable.
Reference Guide 73
Page 82

Dictionaries of Computer Terminology
Web Logs (Blogs)
Radio Free Security
WatchGuard’s podcast covers network secuirty issues of interest to small- to medium-sized
businesses. Learn how to prioritze threats by hearing the LiveSecurity reporters pick the
“Security Story of the Month”; then keep it on play to hear the renowned industry experts assess
the latest threats and give practical tips and insights. Get the feed directly or from iTunes.
Risky Business
This secuirty podcast from Australia provides a veteran perspective on secuirty issues all over the
world, and is the best-paced podcast we’ve found for busy administrators.
www.getmon.com
This site aggregates all the best-known network security podcasts. Let the listener beware -some of the more popular podcasts, such as Security Now, have been known to broadcast
technically inaccurate information. Not for everyone, but worth sampling: Pauldotcom, and
Security Bites. If you are a podcast addict, this is your candy store.
74
WatchGuard System Manager
Page 83

Copyright Information
7
Copyright, Patent, Trademark, and
Licensing Information
Copyright Information
Copyright© 1998 - 2008 WatchGuard Technologies, Inc. All rights reserved.
© Hi/fn, Inc. 1993, including one or more U.S. Patents 4701745, 5016009, 5126739, and 5146221 and
other patents pending.
Jcchart copyright © 1999 by KL Group Inc. All rights reserved.
Matplotlib copyright © 2002-2004 John D. Hunter; All Rights Reserved.
Cyberons_SNMP copyright © 2000 by NETAPHOR SOFTWARE, INC.
Jasper Reports copyright © 2000-2008 JasperSoft Corporation.
JDom copyright 2001 © werken digital. All Rights Reserved.
Patents
U.S. Patent Nos. 6,493,752; 6,597,661; 6,618,755; D473,879. Other Patents Pending.
Trademarks
WatchGuard, the WatchGuard logo, Firebox, LiveSecurity, and any other mark listed as a trademark in
the “Terms of Use” portion of the WatchGuard Web site that is used herein are either registered
trademarks or trademarks of WatchGuard Technologies, Inc. and/or its subsidiaries in the United States
and/or other countries. All other trademarks are the property of their respective owners.
Microsoft®, Internet Explorer®, Windows® 95, Windows® 98, Windows NT®, Windows® 2000, Windows®
XP, and Windows® Vista are either registered trademarks or trademarks of Microsoft Corporation in the
United States and/or other countries.
Netscape and Netscape Navigator are registered trademarks of Netscape Communications Corporation
in the United States and other countries.
RealNetworks, RealAudio, and RealVideo are either a registered trademark or trademark of
RealNetworks, Inc. in the United States and/or other countries.
Reference Guide 75
Page 84

Licensing
Java and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. in the
United States and other countries. All right reserved.
"OpenVPN" is a trademark of OpenVPN Solutions LLC.
WatchGuard, the WatchGuard logo, Firebox, LiveSecurity, and any other mark listed as a trademark in
the “Terms of Use” portion of the WatchGuard Web site that is used herein are either registered
trademarks or trademarks of WatchGuard Technologies, Inc. and/or its subsidiaries in the United States
and/or other countries. All other trademarks are the property of their respective owners.
Licensing
Some components of the WatchGuard System Manager software are distributed with source code
covered under one or more third party or open source licenses. We include below the full text of the
licenses as required by the terms of each license.
To get the source code covered by these licenses, contact WatchGuard Technical Support at:
877.232.3531 from the United States or Canada
+1.360.482.1083 from all other countries
You can download the source code at no charge. If you request a compact disc, there is a $35 charge for
administration and shipping.
Apache License (1.1)
Each of the following programs are wholly or partially licensed under version 1.1 of the Apache License:
Apache XMLRPC, log4j, Xerces, xmlrpc-epi toolkit.
Specific copyright information for the above software, if any, can be found in subsequent pages of this
Reference Guide.
The Apache Software License, Version 1.1
Copyright © 2000 The Apache Software Foundation. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted
provided that the following conditions are met:
1 Redistributions of source code must retain the above copyright notice, this list of conditions and
the following disclaimer.
2 Redistributions in binary form must reproduce the above copyright notice, this list of conditions
and the following disclaimer in the documentation and/or other materials provided with the
distribution.
3 The end-user documentation included with the redistribution, if any, must include the following
acknowledgment:
“This product includes software developed by the Apache Software Foundation (http://
www.apache.org/)."
Alternately, this acknowledgment may appear in the software itself, if and wherever such third-
party acknowledgments normally appear.
4 The names "Apache" and "Apache Software Foundation" must not be used to endorse or
promote products derived from this software without prior written permission. For written
permission, please contact apache@apache.org.
5 Products derived from this software may not be called "Apache", nor may "Apache" appear in
their name, without prior written permission of the Apache Software Foundation.
76
WatchGuard System Manager
Page 85

THIS SOFTWARE IS PROVIDED ``AS IS'' AND ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT
NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE APACHE SOFTWARE FOUNDATION OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED
OF THE POSSIBILITY OF SUCH DAMAGE.
This software consists of voluntary contributions made by many individuals on behalf of the Apache
Software Foundation. For more information on the Apache Software Foundation, please see
<http://www.apache.org/>.
Portions of this software are based upon public domain software originally written at the National
Center for Supercomputing Applications, University of Illinois, Urbana-Champaign.
Apache License (2.0)
Each of the following programs are wholly or partially licensed under version 2.0 of the Apache License:
Apache ant, Apache web server, Apache FOP, Apache Commons, Apache POI.
Licensing
Specific copyright information for the above software, if any, can be found in subsequent pages of this
Reference Guide.
Apache License
Version 2.0, January 2004
http://www.apache.org/licenses/
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
1 Definitions.
"License" shall mean the terms and conditions for use, reproduction, and distribution as defined
by Sections 1 through 9 of this document.
"Licensor" shall mean the copyright owner or entity authorized by the copyright owner that is
granting the License.
"Legal Entity" shall mean the union of the acting entity and all other entities that control, are
controlled by, or are under common control with that entity. For the purposes of this definition,
"control" means (i) the power, direct or indirect, to cause the direction or management of such
entity, whether by contract or otherwise, or (ii) ownership of fifty percent (50%) or more of the
outstanding shares, or (iii) beneficial ownership of such entity.
"You" (or "Your") shall mean an individual or Legal Entity exercising permissions granted by this
License.
"Source" form shall mean the preferred form for making modifications, including but not limited
to software source code, documentation source, and configuration files.
"Object" form shall mean any form resulting from mechanical transformation or translation of a
Source form, including but not limited to compiled object code, generated documentation, and
conversions to other media types.
"Work" shall mean the work of authorship, whether in Source or Object form, made available
under the License, as indicated by a copyright notice that is included in or attached to the work
(an example is provided in the Appendix below).
Reference Guide 77
Page 86

Licensing
"Derivative Works" shall mean any work, whether in Source or Object form, that is based on (or
derived from) the Work and for which the editorial revisions, annotations, elaborations, or other
modifications represent, as a whole, an original work of authorship. For the purposes of this
License, Derivative Works shall not include works that remain separable from, or merely link (or
bind by name) to the interfaces of, the Work and Derivative Works thereof.
"Contribution" shall mean any work of authorship, including the original version of the Work and
any modifications or additions to that Work or Derivative Works thereof, that is intentionally
submitted to Licensor for inclusion in the Work by the copyright owner or by an individual or
Legal Entity authorized to submit on behalf of the copyright owner. For the purposes of this
definition, "submitted" means any form of electronic, verbal, or written communication sent to
the Licensor or its representatives, including but not limited to communication on electronic
mailing lists, source code control systems, and issue tracking systems that are managed by, or on
behalf of, the Licensor for the purpose of discussing and improving the Work, but excluding
communication that is conspicuously marked or otherwise designated in writing by the
copyright owner as "Not a Contribution."
"Contributor" shall mean Licensor and any individual or Legal Entity on behalf of whom a
Contribution has been received by Licensor and subsequently incorporated within the Work.
2 Grant of Copyright License. Subject to the terms and conditions of this License, each
Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free,
irrevocable copyright license to reproduce, prepare Derivative Works of, publicly display, publicly
perform, sublicense, and distribute the Work and such Derivative Works in Source or Object form.
3 Grant of Patent License. Subject to the terms and conditions of this License, each Contributor
hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable
(except as stated in this section) patent license to make, have made, use, offer to sell, sell, import,
and otherwise transfer the Work, where such license applies only to those patent claims
licensable by such Contributor that are necessarily infringed by their Contribution(s) alone or by
combination of their Contribution(s) with the Work to which such Contribution(s) was submitted.
If You institute patent litigation against any entity (including a cross-claim or counterclaim in a
lawsuit) alleging that the Work or a Contribution incorporated within the Work constitutes direct
or contributory patent infringement, then any patent licenses granted to You under this License
for that Work shall terminate as of the date such litigation is filed.
4 Redistribution. You may reproduce and distribute copies of the Work or Derivative Works
thereof in any medium, with or without modifications, and in Source or Object form, provided
that You meet the following conditions:
a You must give any other recipients of the Work or Derivative Works a copy of this License; and
b You must cause any modified files to carry prominent notices stating that You changed the
files; and
c You must retain, in the Source form of any Derivative Works that You distribute, all copyright,
patent, trademark, and attribution notices from the Source form of the Work, excluding those
notices that do not pertain to any part of the Derivative Works; and
d If the Work includes a "NOTICE" text file as part of its distribution, then any Derivative Works
that You distribute must include a readable copy of the attribution notices contained within
such NOTICE file, excluding those notices that do not pertain to any part of the Derivative
Works, in at least one of the following places: within a NOTICE text file distributed as part of
the Derivative Works; within the Source form or documentation, if provided along with the
Derivative Works; or, within a display generated by the Derivative Works, if and wherever
such third-party notices normally appear. The contents of the NOTICE file are for
informational purposes only and do not modify the License. You may add Your own
attribution notices within Derivative Works that You distribute, alongside or as an addendum
to the NOTICE text from the Work, provided that such additional attribution notices cannot
be construed as modifying the License.
78
WatchGuard System Manager
Page 87

Licensing
You may add Your own copyright statement to Your modifications and may provide additional or
different license terms and conditions for use, reproduction, or distribution of Your
modifications, or for any such Derivative Works as a whole, provided Your use, reproduction, and
distribution of the Work otherwise complies with the conditions stated in this License.
5 Submission of Contributions. Unless You explicitly state otherwise, any Contribution
intentionally submitted for inclusion in the Work by You to the Licensor shall be under the terms
and conditions of this License, without any additional terms or conditions. Notwithstanding the
above, nothing herein shall supersede or modify the terms of any separate license agreement
you may have executed with Licensor regarding such Contributions.
6 Trademarks. This License does not grant permission to use the trade names, trademarks, service
marks, or product names of the Licensor, except as required for reasonable and customary use in
describing the origin of the Work and reproducing the content of the NOTICE file.
7 Disclaimer of Warranty. Unless required by applicable law or agreed to in writing, Licensor
provides the Work (and each Contributor provides its Contributions) on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied, including,
without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT,
MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. You are solely responsible for
determining the appropriateness of using or redistributing the Work and assume any risks
associated with Your exercise of permissions under this License.
8 Limitation of Liability. In no event and under no legal theory, whether in tort (including
negligence), contract, or otherwise, unless required by applicable law (such as deliberate and
grossly negligent acts) or agreed to in writing, shall any Contributor be liable to You for damages,
including any direct, indirect, special, incidental, or consequential damages of any character
arising as a result of this License or out of the use or inability to use the Work (including but not
limited to damages for loss of goodwill, work stoppage, computer failure or malfunction, or any
and all other commercial damages or losses), even if such Contributor has been advised of the
possibility of such damages.
9 Accepting Warranty or Additional Liability. While redistributing the Work or Derivative Works
thereof, You may choose to offer, and charge a fee for, acceptance of support, warranty,
indemnity, or other liability obligations and/or rights consistent with this License. However, in
accepting such obligations, You may act only on Your own behalf and on Your sole responsibility,
not on behalf of any other Contributor, and only if You agree to indemnify, defend, and hold each
Contributor harmless for any liability incurred by, or claims asserted against, such Contributor by
reason of your accepting any such warranty or additional liability.
END OF TERMS AND CONDITIONS
Reference Guide 79
Page 88

Licensing
GNU General Public License (GPL)
Each of the following programs are wholly or partially licensed under the GPL: bpalogin, bridge-utils,
BusyBox, hostapd, iproute, ipset, iptables, JAXB, libiconv, Linux, LZO, OpenVPN, oprofile, pptpd,
psycopg, readline, rp-pppoe, TAP-Win32 distributions, termcap, wireless_tools, wpa_supplicant.
Specific copyright information for the above software, if any, can be found in subsequent pages of this
Reference Guide.
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright © 1989, 1991 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor
Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it
is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users. This General Public License applies to
most of the Free Software Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by the GNU Library General Public
License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are
designed to make sure that you have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it if you want it, that you can change
the software or use pieces of it in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to
ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the
recipients all the rights that you have. You must make sure that they, too, receive or can get the source
code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license which
gives you legal permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone understands that
there is no warranty for this free software. If the software is modified by someone else and passed on,
we want its recipients to know that what they have is not the original, so that any problems introduced
by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger
that redistributors of a free program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any patent must be licensed for
everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
80
WatchGuard System Manager
Page 89

Licensing
Terms and Conditions for Copying, Distribution, and Modification
1 This License applies to any program or other work which contains a notice placed by the
copyright holder saying it may be distributed under the terms of this General Public License. The
"Program", below, refers to any such program or work, and a "work based on the Program" means
either the Program or any derivative work under copyright law: that is to say, a work containing
the Program or a portion of it, either verbatim or with modifications and/or translated into
another language. (Hereinafter, translation is included without limitation in the term
"modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by this License; they
are outside its scope. The act of running the Program is not restricted, and the output from the
Program is covered only if its contents constitute a work based on the Program (independent of
having been made by running the Program). Whether that is true depends on what the Program
does.
2 You may copy and distribute verbatim copies of the Program's source code as you receive it, in
any medium, provided that you conspicuously and appropriately publish on each copy an
appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to
this License and to the absence of any warranty; and give any other recipients of the Program a
copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.You may modify your copy or copies of the Program or
any portion of it, thus forming a work based on the Program, and copy and distribute such
modifications or work under the terms of Section 1 above, provided that you also meet all of
these conditions:
- You must cause the modified files to carry prominent notices stating that you changed the
files and the date of any change.
- You must cause any work that you distribute or publish, that in whole or in part contains or is
derived from the Program or any part thereof, to be licensed as a whole at no charge to all
third parties under the terms of this License.
- If the modified program normally reads commands interactively when run, you must cause it,
when started running for such interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a notice that there is no
warranty (or else, saying that you provide a warranty) and that users may redistribute the
program under these conditions, and telling the user how to view a copy of this License.
(Exception: if the Program itself is interactive but does not normally print such an
announcement, your work based on the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work
are not derived from the Program, and can be reasonably considered independent and separate
works in themselves, then this License, and its terms, do not apply to those sections when you
distribute them as separate works. But when you distribute the same sections as part of a whole
which is a work based on the Program, the distribution of the whole must be on the terms of this
License, whose permissions for other licensees extend to the entire whole, and thus to each and
every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or
with a work based on the Program) on a volume of a storage or distribution medium does not
bring the other work under the scope of this License.
Reference Guide 81
Page 90

Licensing
3 You may copy and distribute the Program (or a work based on it, under Section 2) in object code
or executable form under the terms of Sections 1 and 2 above provided that you also do one of
the following:
- Accompany it with the complete corresponding machine-readable source code, which must
be distributed under the terms of Sections 1 and 2 above on a medium customarily used for
software interchange; or,
- Accompany it with a written offer, valid for at least three years, to give any third party, for a
charge no more than your cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be distributed under the terms
of Sections 1 and 2 above on a medium customarily used for software interchange; or,
- Accompany it with the information you received as to the offer to distribute corresponding
source code. (This alternative is allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such an offer, in accord with
Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it.
For an executable work, complete source code means all the source code for all modules it
contains, plus any associated interface definition files, plus the scripts used to control
compilation and installation of the executable. However, as a special exception, the source code
distributed need not include anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the operating system on which
the executable runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated
place, then offering equivalent access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not compelled to copy the source
along with the object code.
4 You may not copy, modify, sublicense, or distribute the Programexcept as expressly provided
under this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program
is void, and will automatically terminate your rights under this License. However, parties who
have received copies, or rights, from you under this License will not have their licenses
terminated so long as such parties remain in full compliance.
5 You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Program or its derivative works. These actions
are prohibited by law if you do not accept this License. Therefore, by modifying or distributing
the Program (or any work based on the Program), you indicate your acceptance of this License to
do so, and all its terms and conditions for copying, distributing or modifying the Program or
works based on it.
6 Each time you redistribute the Program (or any work based on the Program), the recipient
automatically receives a license from the original licensor to copy, distribute or modify the
Program subject to these terms and conditions. You may not impose any further restrictions on
the recipients' exercise of the rights granted herein. You are not responsible for enforcing
compliance by third parties to this License.
7 If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you
from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent license would not permit royaltyfree redistribution of the Program by all those who receive copies directly or indirectly through
you, then the only way you could satisfy both it and this License would be to refrain entirely from
distribution of the Program.
82
WatchGuard System Manager
Page 91

Licensing
If any portion of this section is held invalid or unenforceable under any particular circumstance,
the balance of the section is intended to apply and the section as a whole is intended to apply in
other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting
the integrity of the free software distribution system, which is implemented by public license
practices. Many people have made generous contributions to the wide range of software
distributed through that system in reliance on consistent application of that system; it is up to
the author/donor to decide if he or she is willing to distribute software through any other system
and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the
rest of this License.
8 If the distribution and/or use of the Program is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Program under this
License may add an explicit geographical distribution limitation excluding those countries, so
that distribution is permitted only in or among countries not thus excluded. In such case, this
License incorporates the limitation as if written in the body of this License.
9 The Free Software Foundation may publish revised and/or new versions of the General Public
License from time to time. Such new versions will be similar in spirit to the present version, but
may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number
of this License which applies to it and "any later version", you have the option of following the
terms and conditions either of that version or of any later version published by the Free Software
Foundation. If the Program does not specify a version number of this License, you may choose
any version ever published by the Free Software Foundation.
10 If you wish to incorporate parts of the Program into other free programs whose distribution
conditions are different, write to the author to ask for permission. For software which is
copyrighted by the Free Software Foundation, write to the Free Software Foundation; we
sometimes make exceptions for this. Our decision will be guided by the two goals of preserving
the free status of all derivatives of our free software and of promoting the sharing and reuse of
software generally.
NO WARRANTY
11 BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE
PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED
IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS"
WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH
YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY
SERVICING, REPAIR OR CORRECTION.
12 IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM
TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Reference Guide 83
Page 92

Licensing
GNU Lesser General Public License (LGPL)
Each of the following programs are wholly or partially licensed under the GNU Library General Public
License (Library GPL): JDIC, JFreeChart, libnl, scew, SwingX, SwingWorker, pyOpenSSL.
Specific copyright information for the above software, if any, can be found in subsequent pages of this
chapter.
GNU Lesser General Public License
Version 2.1, February 1999
Copyright © 1991, 1999 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor
Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it
is not allowed.
[This is the first released version of the Lesser GPL. It also counts as the successor of the GNU Library
Public License, version 2, hence the version number 2.1.]
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users.
This license, the Lesser General Public License, applies to some specially designated software
packages--typically libraries--of the Free Software Foundation and other authors who decide to use it.
You can use it too, but we suggest you first think carefully about whether this license or the ordinary
General Public License is the better strategy to use in any particular case, based on the explanations
below.
When we speak of free software, we are referring to freedom of use, not price. Our General Public
Licenses are designed to make sure that you have the freedom to distribute copies of free software
(and charge for this service if you wish); that you receive source code or can get it if you want it; that
you can change the software and use pieces of it in new free programs; and that you are informed that
you can do these things.
To protect your rights, we need to make restrictions that forbid distributors to deny you these rights or
to ask you to surrender these rights. These restrictions translate to certain responsibilities for you if you
distribute copies of the library or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the
recipients all the rights that we gave you. You must make sure that they, too, receive or can get the
source code. If you link other code with the library, you must provide complete object files to the
recipients, so that they can relink them with the library after making changes to the library and
recompiling it. And you must show them these terms so they know their rights.
We protect your rights with a two-step method: (1) we copyright the library, and (2) we offer you this
license, which gives you legal permission to copy, distribute and/or modify the library.
To protect each distributor, we want to make it very clear that there is no warranty for the free library.
Also, if the library is modified by someone else and passed on, the recipients should know that what
they have is not the original version, so that the original author's reputation will not be affected by
problems that might be introduced by others.
84
WatchGuard System Manager
Page 93

Licensing
Finally, software patents pose a constant threat to the existence of any free program. We wish to make
sure that a company cannot effectively restrict the users of a free program by obtaining a restrictive
license from a patent holder. Therefore, we insist that any patent license obtained for a version of the
library must be consistent with the full freedom of use specified in this license.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public License.
This license, the GNU Lesser General Public License, applies to certain designated libraries, and is quite
different from the ordinary General Public License. We use this license for certain libraries in order to
permit linking those libraries into non-free programs.
When a program is linked with a library, whether statically or using a shared library, the combination of
the two is legally speaking a combined work, a derivative of the original library. The ordinary General
Public License therefore permits such linking only if the entire combination fits its criteria of freedom.
The Lesser General Public License permits more lax criteria for linking other code with the library.
We call this license the "Lesser" General Public License because it does Less to protect the user's
freedom than the ordinary General Public License. It also provides other free software developers Less
of an advantage over competing non-free programs. These disadvantages are the reason we use the
ordinary General Public License for many libraries. However, the Lesser license provides advantages in
certain special circumstances.
For example, on rare occasions, there may be a special need to encourage the widest possible use of a
certain library, so that it becomes a de-facto standard. To achieve this, non-free programs must be
allowed to use the library. A more frequent case is that a free library does the same job as widely used
non-free libraries. In this case, there is little to gain by limiting the free library to free software only, so
we use the Lesser General Public License.
In other cases, permission to use a particular library in non-free programs enables a greater number of
people to use a large body of free software. For example, permission to use the GNU C Library in nonfree programs enables many more people to use the whole GNU operating system, as well as its
variant, the GNU/Linux operating system.
Although the Lesser General Public License is Less protective of the users' freedom, it does ensure that
the user of a program that is linked with the Library has the freedom and the wherewithal to run that
program using a modified version of the Library.
The precise terms and conditions for copying, distribution and modification follow. Pay close attention
to the difference between a "work based on the library" and a "work that uses the library". The former
contains code derived from the library, whereas the latter must be combined with the library in order
to run.
Terms and Conditions for Copying, Distribution, and Modification
1 This License Agreement applies to any software library or other program which contains a notice
placed by the copyright holder or other authorized party saying it may be distributed under the
terms of this Lesser General Public License (also called "this License"). Each licensee is addressed
as "you".
A "library" means a collection of software functions and/or data prepared so as to be
conveniently linked with application programs (which use some of those functions and data) to
form executables.
The "Library", below, refers to any such software library or work which has been distributed under
these terms. A "work based on the Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a portion of it, either verbatim or
with modifications and/or translated straightforwardly into another language. (Hereinafter,
translation is included without limitation in the term "modification".)
Reference Guide 85
Page 94

Licensing
"Source code" for a work means the preferred form of the work for making modifications to it.
For a library, complete source code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to control compilation and installation
of the library.
Activities other than copying, distribution and modification are not covered by this License; they
are outside its scope. The act of running a program using the Library is not restricted, and output
from such a program is covered only if its contents constitute a work based on the Library
(independent of the use of the Library in a tool for writing it). Whether that is true depends on
what the Library does and what the program that uses the Library does.
2 You may copy and distribute verbatim copies of the Library's complete source code as you
receive it, in any medium, provided that you conspicuously and appropriately publish on each
copy an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that
refer to this License and to the absence of any warranty; and distribute a copy of this License
along with the Library.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
3 You may modify your copy or copies of the Library or any portion of it, thus forming a work based
on the Library, and copy and distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
- The modified work must itself be a software library.
- You must cause the files modified to carry prominent notices stating that you changed the
files and the date of any change.
- You must cause the whole of the work to be licensed at no charge to all third parties under the
terms of this License.
- If a facility in the modified Library refers to a function or a table of data to be supplied by an
application program that uses the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that, in the event an application
does not supply such function or table, the facility still operates, and performs whatever part
of its purpose remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely
well-defined independent of the application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must be optional: if the
application does not supply it, the square root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work
are not derived from the Library, and can be reasonably considered independent and separate
works in themselves, then this License, and its terms, do not apply to those sections when you
distribute them as separate works. But when you distribute the same sections as part of a whole
which is a work based on the Library, the distribution of the whole must be on the terms of this
License, whose permissions for other licensees extend to the entire whole, and thus to each and
every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written
entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or
collective works based on the Library.
In addition, mere aggregation of another work not based on the Library with the Library (or with
a work based on the Library) on a volume of a storage or distribution medium does not bring the
other work under the scope of this License.
86
WatchGuard System Manager
Page 95

Licensing
4 You may opt to apply the terms of the ordinary GNU General Public License instead of this
License to a given copy of the Library. To do this, you must alter all the notices that refer to this
License, so that they refer to the ordinary GNU General Public License, version 2, instead of to this
License. (If a newer version than version 2 of the ordinary GNU General Public License has
appeared, then you can specify that version instead if you wish.) Do not make any other change
in these notices.
Once this change is made in a given copy, it is irreversible for that copy, so the ordinary GNU
General Public License applies to all subsequent copies and derivative works made from that
copy.
This option is useful when you wish to copy part of the code of the Library into a program that is
not a library.
5 You may copy and distribute the Library (or a portion or derivative of it, under Section 2) in
object code or executable form under the terms of Sections 1 and 2 above provided that you
accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for
software interchange.
If distribution of object code is made by offering access to copy from a designated place, then
offering equivalent access to copy the source code from the same place satisfies the requirement
to distribute the source code, even though third parties are not compelled to copy the source
along with the object code.
6 A program that contains no derivative of any portion of the Library, but is designed to work with
the Library by being compiled or linked with it, is called a "work that uses the Library". Such a
work, in isolation, is not a derivative work of the Library, and therefore falls outside the scope of
this License.
However, linking a "work that uses the Library" with the Library creates an executable that is a
derivative of the Library (because it contains portions of the Library), rather than a "work that
uses the library". The executable is therefore covered by this License. Section 6 states terms for
distribution of such executables.
When a "work that uses the Library" uses material from a header file that is part of the Library, the
object code for the work may be a derivative work of the Library even though the source code is
not. Whether this is true is especially significant if the work can be linked without the Library, or if
the work is itself a library. The threshold for this to be true is not precisely defined by law.
If such an object file uses only numerical parameters, data structure layouts and accessors, and
small macros and small inline functions (ten lines or less in length), then the use of the object file
is unrestricted, regardless of whether it is legally a derivative work. (Executables containing this
object code plus portions of the Library will still fall under Section 6.)
Otherwise, if the work is a derivative of the Library, you may distribute the object code for the
work under the terms of Section 6. Any executables containing that work also fall under Section
6, whether or not they are linked directly with the Library itself.
7 As an exception to the Sections above, you may also combine or link a "work that uses the
Library" with the Library to produce a work containing portions of the Library, and distribute that
work under terms of your choice, provided that the terms permit modification of the work for the
customer's own use and reverse engineering for debugging such modifications.
You must give prominent notice with each copy of the work that the Library is used in it and that
the Library and its use are covered by this License. You must supply a copy of this License. If the
work during execution displays copyright notices, you must include the copyright notice for the
Library among them, as well as a reference directing the user to the copy of this License. Also,
you must do one of these things:
Reference Guide 87
Page 96

Licensing
- Accompany the work with the complete corresponding machine-readable source code for
the Library including whatever changes were used in the work (which must be distributed
under Sections 1 and 2 above); and, if the work is an executable linked with the Library, with
the complete machine-readable "work that uses the Library", as object code and/or source
code, so that the user can modify the Library and then relink to produce a modified
executable containing the modified Library. (It is understood that the user who changes the
contents of definitions files in the Library will not necessarily be able to recompile the
application to use the modified definitions.)
- Use a suitable shared library mechanism for linking with the Library. A suitable mechanism is
one that (1) uses at run time a copy of the library already present on the user's computer
system, rather than copying library functions into the executable, and (2) will operate properly
with a modified version of the library, if the user installs one, as long as the modified version is
interface-compatible with the version that the work was made with.
- Accompany the work with a written offer, valid for at least three years, to give the same user
the materials specified in Subsection 6a, above, for a charge no more than the cost of
performing this distribution.
- If distribution of the work is made by offering access to copy from a designated place, offer
equivalent access to copy the above specified materials from the same place.
- Verify that the user has already received a copy of these materials or that you have already
sent this user a copy.
For an executable, the required form of the "work that uses the Library" must include any data
and utility programs needed for reproducing the executable from it. However, as a special
exception, the materials to be distributed need not include anything that is normally distributed
(in either source or binary form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component itself accompanies the
executable.
It may happen that this requirement contradicts the license restrictions of other proprietary
libraries that do not normally accompany the operating system. Such a contradiction means you
cannot use both them and the Library together in an executable that you distribute.
8 You may place library facilities that are a work based on the Library side-by-side in a single library
together with other library facilities not covered by this License, and distribute such a combined
library, provided that the separate distribution of the work based on the Library and of the other
library facilities is otherwise permitted, and provided that you do these two things:
- Accompany the combined library with a copy of the same work based on the Library,
uncombined with any other library facilities. This must be distributed under the terms of the
Sections above.
- Give prominent notice with the combined library of the fact that part of it is a work based on
the Library, and explaining where to find the accompanying uncombined form of the same
work.
9 You may not copy, modify, sublicense, link with, or distribute the Library except as expressly
provided under this License. Any attempt otherwise to copy, modify, sublicense, link with, or
distribute the Library is void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under this License will not have
their licenses terminated so long as such parties remain in full compliance.
10 You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Library or its derivative works. These actions
are prohibited by law if you do not accept this License. Therefore, by modifying or distributing
the Library (or any work based on the Library), you indicate your acceptance of this License to do
so, and all its terms and conditions for copying, distributing or modifying the Library or works
based on it.
88
WatchGuard System Manager
Page 97

Licensing
11 Each time you redistribute the Library (or any work based on the Library), the recipient
automatically receives a license from the original licensor to copy, distribute, link with or modify
the Library subject to these terms and conditions. You may not impose any further restrictions
on the recipients' exercise of the rights granted herein. You are not responsible for enforcing
compliance by third parties with this License.
12 If, as a consequence of a court judgment or allegation of patent infringement or for any other
reason (not limited to patent issues), conditions are imposed on you (whether by court order,
agreement or otherwise) that contradict the conditions of this License, they do not excuse you
from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your
obligations under this License and any other pertinent obligations, then as a consequence you
may not distribute the Library at all. For example, if a patent license would not permit royaltyfree redistribution of the Library by all those who receive copies directly or indirectly through
you, then the only way you could satisfy both it and this License would be to refrain entirely from
distribution of the Library.
If any portion of this section is held invalid or unenforceable under any particular circumstance,
the balance of the section is intended to apply, and the section as a whole is intended to apply in
other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right
claims or to contest validity of any such claims; this section has the sole purpose of protecting
the integrity of the free software distribution system which is implemented by public license
practices. Many people have made generous contributions to the wide range of software
distributed through that system in reliance on consistent application of that system; it is up to
the author/donor to decide if he or she is willing to distribute software through any other system
and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the
rest of this License.
13 If the distribution and/or use of the Library is restricted in certain countries either by patents or
by copyrighted interfaces, the original copyright holder who places the Library under this
License may add an explicit geographical distribution limitation excluding those countries, so
that distribution is permitted only in or among countries not thus excluded. In such case, this
License incorporates the limitation as if written in the body of this License.
14 The Free Software Foundation may publish revised and/or new versions of the Lesser General
Public License from time to time. Such new versions will be similar in spirit to the present version,
but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Library specifies a version number
of this License which applies to it and "any later version", you have the option of following the
terms and conditions either of that version or of any later version published by the Free Software
Foundation. If the Library does not specify a license version number, you may choose any
version ever published by the Free Software Foundation.
15 If you wish to incorporate parts of the Library into other free programs whose distribution
conditions are incompatible with these, write to the author to ask for permission. For software
which is copyrighted by the Free Software Foundation, write to the Free Software Foundation;
we sometimes make exceptions for this. Our decision will be guided by the two goals of
preserving the free status of all derivatives of our free software and of promoting the sharing and
reuse of software generally.
Reference Guide 89
Page 98

Licensing
NO WARRANTY
16 BECAUSE THE LIBRARY IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE LIBRARY,
TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING
THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE LIBRARY "AS IS" WITHOUT
WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.
THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE LIBRARY IS WITH YOU.
SHOULD THE LIBRARY PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY
SERVICING, REPAIR OR CORRECTION.
17 IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY
COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE
LIBRARY AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL,
SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO
USE THE LIBRARY (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED
INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE LIBRARY TO
OPERATE WITH ANY OTHER SOFTWARE), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
GNU Library General Public License (Library GPL)
Each of the following programs are wholly or partially licensed under the GNU Library General Public
License (Library GPL): etdFTPj, iText, libpthread, Linux, uClibc, wvdial, wvstreams.
Specific copyright information for the above software, if any, can be found in subsequent pages of this
chapter.
GNU Library General Public License
Version 2, June 1991
Copyright © 1991 Free Software Foundation, Inc.
51 Franklin Street, Fifth Floor
Boston, MA 02110-1301, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it
is not allowed.
[This is the first released version of the library GPL. It is numbered 2 because it goes with version 2 of
the ordinary GPL.]
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public Licenses are intended to guarantee your freedom to share and
change free software--to make sure the software is free for all its users.
This license, the Library General Public License, applies to some specially designated Free Software
Foundation software, and to any other libraries whose authors decide to use it. You can use it for your
libraries, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are
designed to make sure that you have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it if you want it, that you can change
the software or use pieces of it in new free programs; and that you know you can do these things.
90
WatchGuard System Manager
Page 99

Licensing
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to
ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you
distribute copies of the library, or if you modify it.
For example, if you distribute copies of the library, whether gratis or for a fee, you must give the
recipients all the rights that we gave you. You must make sure that they, too, receive or can get the
source code. If you link a program with the library, you must provide complete object files to the
recipients so that they can relink them with the library, after making changes to the library and
recompiling it. And you must show them these terms so they know their rights.
Our method of protecting your rights has two steps: (1) copyright the library, and (2) offer you this
license which gives you legal permission to copy, distribute and/or modify the library.
Also, for each distributor's protection, we want to make certain that everyone understands that there is
no warranty for this free library. If the library is modified by someone else and passed on, we want its
recipients to know that what they have is not the original version, so that any problems introduced by
others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger
that companies distributing free software will individually obtain patent licenses, thus in effect
transforming the program into proprietary software. To prevent this, we have made it clear that any
patent must be licensed for everyone's free use or not licensed at all.
Most GNU software, including some libraries, is covered by the ordinary GNU General Public License,
which was designed for utility programs. This license, the GNU Library General Public License, applies
to certain designated libraries. This license is quite different from the ordinary one; be sure to read it in
full, and don't assume that anything in it is the same as in the ordinary license.
The reason we have a separate public license for some libraries is that they blur the distinction we
usually make between modifying or adding to a program and simply using it. Linking a program with a
library, without changing the library, is in some sense simply using the library, and is analogous to
running a utility program or application program. However, in a textual and legal sense, the linked
executable is a combined work, a derivative of the original library, and the ordinary General Public
License treats it as such.
Because of this blurred distinction, using the ordinary General Public License for libraries did not
effectively promote software sharing, because most developers did not use the libraries. We
concluded that weaker conditions might promote sharing better.
However, unrestricted linking of non-free programs would deprive the users of those programs of all
benefit from the free status of the libraries themselves. This Library General Public License is intended
to permit developers of non-free programs to use free libraries, while preserving your freedom as a
user of such programs to change the free libraries that are incorporated in them. (We have not seen
how to achieve this as regards changes in header files, but we have achieved it as regards changes in
the actual functions of the Library.) The hope is that this will lead to faster development of free
libraries.
The precise terms and conditions for copying, distribution and modification follow. Pay close attention
to the difference between a "work based on the library" and a "work that uses the library". The former
contains code derived from the library, while the latter only works together with the library.
Note that it is possible for a library to be covered by the ordinary General Public License rather than by
this special one.
Reference Guide 91
Page 100

Licensing
Terms and Conditions for Copying, Distribution, and Modification
1 This License Agreement applies to any software library which contains a notice placed by the
copyright holder or other authorized party saying it may be distributed under the terms of this
Library General Public License (also called "this License"). Each licensee is addressed as "you".
A "library" means a collection of software functions and/or data prepared so as to be
conveniently linked with application programs (which use some of those functions and data) to
form executables.
The "Library", below, refers to any such software library or work which has been distributed under
these terms. A "work based on the Library" means either the Library or any derivative work under
copyright law: that is to say, a work containing the Library or a portion of it, either verbatim or
with modifications and/or translated straightforwardly into another language. (Hereinafter,
translation is included without limitation in the term "modification".)
“Source code" for a work means the preferred form of the work for making modifications to it.
For a library, complete source code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to control compilation and installation
of the library.
Activities other than copying, distribution and modification are not covered by this License; they
are outside its scope. The act of running a program using the Library is not restricted, and output
from such a program is covered only if its contents constitute a work based on the Library
(independent of the use of the Library in a tool for writing it). Whether that is true depends on
what the Library does and what the program that uses the Library does.
2 You may copy and distribute verbatim copies of the Library's complete source code as you
receive it, in any medium, provided that you conspicuously and appropriately publish on each
copy an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that
refer to this License and to the absence of any warranty; and distribute a copy of this License
along with the Library.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
3 You may modify your copy or copies of the Library or any portion of it, thus forming a work based
on the Library, and copy and distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
- The modified work must itself be a software library.
- You must cause the files modified to carry prominent notices stating that you changed the
files and the date of any change.
- You must cause the whole of the work to be licensed at no charge to all third parties under the
terms of this License.
- If a facility in the modified Library refers to a function or a table of data to be supplied by an
application program that uses the facility, other than as an argument passed when the facility
is invoked, then you must make a good faith effort to ensure that, in the event an application
does not supply such function or table, the facility still operates, and performs whatever part
of its purpose remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely
well-defined independent of the application. Therefore, Subsection 2d requires that any
application-supplied function or table used by this function must be optional: if the
application does not supply it, the square root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work
are not derived from the Library, and can be reasonably considered independent and separate
works in themselves, then this License, and its terms, do not apply to those sections when you
distribute them as separate works. But when you distribute the same sections as part of a whole
which is a work based on the Library, the distribution of the whole must be on the terms of this
92
WatchGuard System Manager
 Loading...
Loading...