Page 1

Manual
WAGO ETHERNET Accessories 852
852-1305
8/4
Industrial
Slots
Version 1.2.0
-Port 1000BASE-T/1000BASE-SX/LX
-Managed-Switch, 8 Ports 1000BASE-T,4
1000BASE-SX/LX
Page 2
2 WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
© 2019 WAGO Kontakttechnik GmbH & Co. KG
All rights reserved.
WAGO Kontakttechnik GmbH & Co. KG
Hansastraße 27
D-32423 Minden
Phone: +49 (0) 571/8 87 – 0
Fax: +49 (0) 571/8 87 – 1 69
E-Mail: info@wago.com
Web: www.wago.com
Technical Support
Phone: +49 (0) 571/8 87 – 4 45 55
Fax: +49 (0) 571/8 87 – 84 45 55
E-Mail: support@wago.com
Every conceivable measure has been taken to ensure the accuracy and
completeness of this documentation. However, as errors can never be fully
excluded, we always appreciate any information or suggestions for improving the
documentation.
E-Mail: documentation@wago.com
We wish to point out that the software and hardware terms as well as the
trademarks of companies used and/or mentioned in the present manual are
generally protected by trademark or patent.
WAGO is a registered trademark of WAGO Verwaltungsgesellschaft mbH.
Manual
Version 1.2.0
Page 3

WAGO ETHERNET Accessories 852 Table of Contents 3
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Table of Contents
1 Notes about this Documentation ........................................................... 10
1.1 Validity of this Documentation............................................................... 10
1.2 Copyright .............................................................................................. 10
1.3 Symbols ............................................................................................... 11
1.4 Number Notation .................................................................................. 13
1.5 Font Conventions ................................................................................. 13
2 Important Notes ...................................................................................... 14
2.1 Legal Bases .......................................................................................... 14
2.1.1 Subject to Changes .......................................................................... 14
2.1.2 Personnel Qualification .................................................................... 14
2.1.3 Proper Use of the Industrial Switches .............................................. 14
2.1.4 Technical Condition of Specified Devices......................................... 15
2.1.5 Standards and Regulations for Operating the Industrial Switches .... 15
2.2 Safety Advice (Precautions) ................................................................. 16
2.3 Special Use Conditions for ETHERNET Devices .................................. 19
3 General .................................................................................................... 20
3.1 Scope of Supply ................................................................................... 20
3.2 Industrial ETHERNET Technology ....................................................... 20
3.3 Switching Technology ........................................................................... 21
4 Device Description .................................................................................. 23
4.1 View ..................................................................................................... 24
4.1.1 Front View ........................................................................................ 24
4.1.2 Top View .......................................................................................... 26
4.2 Connectors ........................................................................................... 27
4.2.1 Power Supply (PWR/RPS) ............................................................... 27
4.2.2 Network Connectors......................................................................... 28
4.2.2.1 RJ-45 Port ................................................................................... 29
4.2.2.2 1000BASE SX/LX Ports .............................................................. 29
4.2.2.3 10/100/1000BASE T Ports ........................................................... 29
4.3 Display Elements .................................................................................. 30
4.3.1 Device LEDs .................................................................................... 30
4.3.2 Port LEDs ........................................................................................ 32
4.4 Operating elements .............................................................................. 33
4.4.1 DIP Switches ................................................................................... 33
4.4.2 Reset Button .................................................................................... 34
4.5 Label .................................................................................................... 35
4.5.1 Hardware and Software Version ...................................................... 35
4.6 Technical Data ..................................................................................... 36
4.6.1 Device Data ..................................................................................... 36
4.6.2 System Data .................................................................................... 36
4.6.3 Power Supply ................................................................................... 36
4.6.4 Communication ................................................................................ 37
4.6.5 Environmental Conditions ................................................................ 37
4.7 Approvals ............................................................................................. 38
5 Mounting .................................................................................................. 39
Manual
Version 1.2.0
Page 4

4 Table of Contents WAG O ETHERN ET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
5.1 Installation Site ..................................................................................... 39
5.2 Installation on a Carrier Rail ................................................................. 39
5.3 Removal from Carrier ail ....................................................................... 39
6 Connect Devices ..................................................................................... 40
6.1 Power Supply ....................................................................................... 40
6.2 External Alarm Contact Port ................................................................. 41
6.3 Console Port Cable Connection ............................................................ 41
6.4 1000Base-SX/LX Port, Fiber Optic ....................................................... 42
6.5 10/100/1000BASE-T Ports ................................................................... 43
7 Enhanced Features ................................................................................. 44
7.1 Default Settings .................................................................................... 44
7.1.1 Jumbo Frame ................................................................................... 44
7.1.2 SNTP ............................................................................................... 44
7.1.3 Management Host ............................................................................ 45
7.1.4 MAC Management ........................................................................... 45
7.1.4.1 Static MAC Settings ..................................................................... 46
7.1.4.2 Refusal MAC Settings ................................................................. 46
7.1.5 Port Mirroring ................................................................................... 47
7.1.6 Port Setting s .................................................................................... 47
7.2 Advanced Settings ................................................................................ 51
7.2.1 Bandwidth Limitation ........................................................................ 51
7.2.1.1 QoS ............................................................................................. 51
7.2.1.2 Rate Limitation ............................................................................ 58
7.2.1.2.1 Storm Control .......................................................................... 58
7.2.1.2.2 Rate Limitation ........................................................................ 58
7.2.2 IGMP Snooping ................................................................................ 59
7.2.2.1 MVR ............................................................................................ 62
7.2.2.2 Multicast Address ........................................................................ 65
7.2.3 VLAN ............................................................................................... 68
7.2.3.1 Port Isolation ............................................................................... 70
7.2.3.2 GARP/GVRP ............................................................................... 71
7.2.3.3 Q-in-Q ......................................................................................... 73
7.2.3.3.1 Port-Based Q-in-Q .................................................................. 75
7.2.3.3.2 Selective Q-in-Q...................................................................... 76
7.2.4 DHCP Relay .................................................................................... 77
7.2.5 DHCP Relay Option 82 .................................................................... 79
7.2.6 Dual Ring ......................................................................................... 81
7.2.7 ERPS ............................................................................................... 82
7.2.8 Dual Homing .................................................................................... 85
7.2.9 Link Aggregation .............................................................................. 86
7.2.9.1 Static Trunk ................................................................................. 86
7.2.9.2 LACP ........................................................................................... 86
7.2.10 LLDP ................................................................................................ 87
7.2.11 Loop Detection ................................................................................. 88
7.2.12 Jet Ring............................................................................................ 89
7.2.13 STP .................................................................................................. 90
7.2.14 Xpres s Ring ..................................................................................... 95
7.3 Security ................................................................................................ 96
7.3.1 IP Source Guard .............................................................................. 96
Manual
Version 1.2.0
Page 5

WAGO ETHERNET Accessories 852 Table of Contents 5
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.3.1.1 DHCP Snooping .......................................................................... 97
7.3.1.1.1 Server Screening .................................................................... 99
7.3.1.2 Binding Table .............................................................................. 99
7.3.1.3 ARP Inspection .......................................................................... 100
7.3.1.3.1 Filter Table ............................................................................ 101
7.3.2 Access Control List (ACL) .............................................................. 102
7.3.3 802.1x ............................................................................................ 103
7.3.4 Port Security .................................................................................. 106
7.4 Monitor ............................................................................................... 107
7.4.1 Alarm Informa ti o n ........................................................................... 107
7.4.2 Monitor Information ........................................................................ 107
7.4.3 RMON Statistics ............................................................................. 107
7.4.4 SFP ................................................................................................ 107
7.4.4.1 DDM .......................................................................................... 108
7.4.5 Traffic Monitor ................................................................................ 108
7.5 Management ...................................................................................... 109
7.5.1 SNMP ............................................................................................ 109
7.5.2 SNMP Trap .................................................................................... 110
7.5.3 Auto Provision ................................................................................ 110
7.5.4 Mail Alarm ...................................................................................... 112
8 Configuration ........................................................................................ 113
8.1 Overview of Configuration Options ..................................................... 113
8.1.1 Telnet Port ..................................................................................... 114
8.2 Console Port ....................................................................................... 115
9 Configuring in the Web-Based Management System ......................... 116
9.1 System Status .................................................................................... 119
9.1.1 System Informationen .................................................................... 119
9.2 Basic Settings ..................................................................................... 121
9.2.1 General Settings ............................................................................ 121
9.2.1.1 System ...................................................................................... 121
9.2.1.2 Jumbo Frame ............................................................................ 123
9.2.1.3 SNTP......................................................................................... 124
9.2.1.4 Management Host ..................................................................... 127
9.2.2 MAC Management ......................................................................... 128
9.2.2.1 Static MAC Settings ................................................................... 128
9.2.2.2 MAC Table ................................................................................ 130
9.2.2.3 Age Time Setting ....................................................................... 131
9.2.2.4 Refusal MAC Settings ............................................................... 132
9.2.3 Port Mirroring ................................................................................. 133
9.2.4 Port Setting s .................................................................................. 135
9.2.4.1 General Settings ........................................................................ 135
9.2.4.2 Information ................................................................................ 137
9.3 Advanced Settings .............................................................................. 138
9.3.1 Bandwidth Control .......................................................................... 138
9.3.1.1 QoS ........................................................................................... 138
9.3.1.1.1 Port Priority ........................................................................... 138
9.3.1.1.2 IP DiffServ (DSCP) ............................................................... 139
9.3.1.1.3 Priority/Queue Mapping ........................................................ 140
9.3.1.1.4 Schedule Mode ..................................................................... 141
Manual
Version 1.2.0
Page 6

6 Table of Contents WAG O ETHERN ET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
9.3.1.2 Rate Limitation .......................................................................... 143
9.3.1.2.1 Storm Control ........................................................................ 143
9.3.1.2.2 Bandwidth Limitation ............................................................. 145
9.3.2 IGMP Snooping .............................................................................. 146
9.3.2.1 IGMP Snooping ......................................................................... 146
9.3.2.1.1 General Settings ................................................................... 146
9.3.2.1.2 Port Setting s ......................................................................... 148
9.3.2.1.3 Querier Settings .................................................................... 150
9.3.2.2 IGMP Filtering ........................................................................... 151
9.3.2.2.1 General Settings ................................................................... 151
9.3.2.2.2 Group Settings ...................................................................... 152
9.3.2.2.3 Port Setting s ......................................................................... 153
9.3.2.3 MVR .......................................................................................... 154
9.3.2.3.1 MVR Settings ........................................................................ 154
9.3.2.3.2 Group Settings ...................................................................... 156
9.3.2.4 Multicast Address ...................................................................... 157
9.3.2.5 Multicast IP Statistics ................................................................. 158
9.3.3 VLAN ............................................................................................. 159
9.3.3.1 Port Isolation ............................................................................. 159
9.3.3.2 VLAN ......................................................................................... 161
9.3.3.2.1 VLAN Settings ...................................................................... 161
9.3.3.2.2 Tag Settings .......................................................................... 163
9.3.3.2.3 Port Setting s ......................................................................... 164
9.3.3.3 GARP/GVRP ............................................................................. 166
9.3.3.3.1 GVRP ................................................................................... 166
9.3.3.3.2 GARP Timer ......................................................................... 168
9.3.3.4 IP-Subnet-VLAN ........................................................................ 170
9.3.3.5 MAC VLAN ................................................................................ 171
9.3.3.6 Protocol VLAN ........................................................................... 172
9.3.3.7 Q-in-Q ....................................................................................... 173
9.3.3.7.1 VLAN Stacking ...................................................................... 173
9.3.3.7.2 Port-based Q-in-Q ................................................................. 175
9.3.3.7.3 Selective Q-in-Q.................................................................... 176
9.3.4 DHCP Relay .................................................................................. 178
9.3.5 DHCP Options ............................................................................... 179
9.3.5.1 Option 82 ................................................................................... 179
9.3.6 Dual Homing .................................................................................. 180
9.3.7 Dual Ring ....................................................................................... 181
9.3.8 ERPS ............................................................................................. 183
9.3.8.1 Ring Settings ............................................................................. 183
9.3.8.2 Instance Settings ....................................................................... 187
9.3.9 Link Aggregation ............................................................................ 188
9.3.9.1 Static Trunk ............................................................................... 188
9.3.9.2 LACP ......................................................................................... 190
9.3.9.3 LACP Info. ................................................................................. 192
9.3.10 LLDP .............................................................................................. 194
9.3.10.1 Settings ..................................................................................... 194
9.3.10.2 Neighbor .................................................................................... 196
9.3.11 Loop Detection ............................................................................... 197
9.3.12 Jet Ring.......................................................................................... 199
Manual
Version 1.2.0
Page 7

WAGO ETHERNET Accessories 852 Table of Contents 7
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
9.3.13 MODBUS ....................................................................................... 200
9.3.14 STP ................................................................................................ 201
9.3.14.1 General Settings ........................................................................ 201
9.3.14.2 Port Parameters ........................................................................ 203
9.3.14.3 STP Status ................................................................................ 206
9.3.15 Xpres s Ring ................................................................................... 207
9.4 Security .............................................................................................. 209
9.4.1 IP Source Guard ............................................................................ 209
9.4.1.1 DHCP Snooping ........................................................................ 209
9.4.1.1.1 DHCP Snooping ................................................................... 209
9.4.1.1.2 Port Setting s ......................................................................... 211
9.4.1.1.3 Server Screening .................................................................. 212
9.4.1.2 Binding Table ............................................................................ 213
9.4.1.2.1 Static Entry ........................................................................... 213
9.4.1.2.2 Binding Table ........................................................................ 215
9.4.1.3 ARP Inspection .......................................................................... 216
9.4.1.3.1 ARP Inspection ..................................................................... 216
9.4.1.3.2 Filter Table ............................................................................ 218
9.4.2 Access Control List ........................................................................ 219
9.4.3 802.1x ............................................................................................ 223
9.4.3.1 Global Settings .......................................................................... 223
9.4.3.2 Port Setting s .............................................................................. 226
9.4.4 Port Security .................................................................................. 229
9.5 Monitor ............................................................................................... 231
9.5.1 Alarm Informa ti o n ........................................................................... 231
9.5.2 Monitor Information ........................................................................ 232
9.5.3 Port Statistics ................................................................................. 234
9.5.4 Port Utilization ................................................................................ 235
9.5.5 RMON Statistics ............................................................................. 236
9.5.6 SFP Informati on ............................................................................. 239
9.5.7 Traffic Monitor ................................................................................ 241
9.6 Management ...................................................................................... 243
9.6.1 SNMP ............................................................................................ 243
9.6.1.1 SNMP ........................................................................................ 243
9.6.1.1.1 SNMP Settings ..................................................................... 243
9.6.1.1.2 Community Name ................................................................. 244
9.6.1.2 SNMP Trap ............................................................................... 246
9.6.1.2.1 Trap Receiver Settings.......................................................... 246
9.6.1.3 Auto Provision ........................................................................... 247
9.6.1.3.1 Mail Alarm ............................................................................. 248
9.6.1.3.2 Maintenance ......................................................................... 250
9.6.1.3.3 Configuration ........................................................................ 250
9.6.2 Firmware ........................................................................................ 252
9.6.3 Reboot ........................................................................................... 253
9.6.4 Server ............................................................................................ 254
9.6.4.1 System Log ............................................................................... 256
9.6.4.2 User Account ............................................................................. 258
10 Appendix ............................................................................................... 260
10.1 Console Port (RJ-45 to DB9) .............................................................. 260
Manual
Version 1.2.0
Page 8

8 Table of Contents WAG O ETHERN ET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
10.2 RJ-45 Cable ....................................................................................... 261
10.3 Configuring in the Command Line Interface (CLI) ............................... 262
10.3.1 System Status ................................................................................ 262
10.3.1.1 System Information.................................................................... 262
10.3.2 Default Settings .............................................................................. 263
10.3.2.1 System ...................................................................................... 263
10.3.2.2 Jumbo Frame ............................................................................ 263
10.3.2.3 SNTP......................................................................................... 264
10.3.2.4 Management Host ..................................................................... 265
10.3.2.5 MAC Management..................................................................... 265
10.3.2.6 Blackhole MAC .......................................................................... 266
10.3.2.7 Port Mirroring ............................................................................. 266
10.3.2.8 Port Setting s .............................................................................. 267
10.3.3 Advanced Settings ......................................................................... 268
10.3.3.1 Bandwidth Control ..................................................................... 268
10.3.3.2 QoS ........................................................................................... 268
10.3.3.3 Rate Limitation .......................................................................... 268
10.3.3.4 Storm Control ............................................................................ 269
10.3.3.5 IGMP Snooping ......................................................................... 270
10.3.3.6 MVR .......................................................................................... 271
10.3.3.7 Multicast Address ...................................................................... 271
10.3.3.8 VLAN ......................................................................................... 272
10.3.3.8.1 Port Isolation ......................................................................... 272
10.3.3.8.2 VLAN Settings ...................................................................... 273
10.3.3.9 GARP/GVRP ............................................................................. 274
10.3.3.10 Q-in-Q ....................................................................................... 275
10.3.3.10.1 VLAN Stacking ...................................................................... 275
10.3.3.11 DHCP Relay .............................................................................. 276
10.3.3.12 Dual Homing.............................................................................. 277
10.3.3.13 Link Aggregation ....................................................................... 277
10.3.3.14 LACP ......................................................................................... 278
10.3.3.15 LLDP ......................................................................................... 279
10.3.3.16 Loop Detection .......................................................................... 280
10.3.3.17 STP ........................................................................................... 281
10.3.3.18 Xpres s Ring ............................................................................... 282
10.3.4 Security .......................................................................................... 283
10.3.4.1 DHCP Snooping ........................................................................ 283
10.3.4.2 Server Screening ....................................................................... 284
10.3.4.3 Binding Table ............................................................................ 284
10.3.4.4 ARP Inspection .......................................................................... 285
10.3.4.5 Filter Table ................................................................................ 285
10.3.4.6 Access Control List .................................................................... 286
10.3.4.7 802.1x ....................................................................................... 288
10.3.4.8 Port Security .............................................................................. 289
10.3.5 Monitor ........................................................................................... 290
10.3.5.1 Alarm ......................................................................................... 290
10.3.5.2 Monitor Information.................................................................... 290
10.3.5.3 RMON Statistics ........................................................................ 290
10.3.5.4 SFP Informati on ........................................................................ 290
10.3.5.5 Traffic Monitor ........................................................................... 291
Manual
Version 1.2.0
Page 9

WAGO ETHERNET Accessories 852 Table of Contents 9
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
10.3.6 Management .................................................................................. 292
10.3.6.1 SNMP ........................................................................................ 292
10.3.6.2 Auto Provision ........................................................................... 293
10.3.6.3 Mail Alarm ................................................................................. 293
10.3.6.4 Maintenance .............................................................................. 294
10.3.6.5 System Log ............................................................................... 294
10.3.6.6 User Account ............................................................................. 295
10.4 MODBUS/TCP Tables ........................................................................ 296
10.4.1 Data Format and Function Code .................................................... 296
10.4.2 MODBUS Registers ....................................................................... 296
List of Figures ................................................................................................ 308
List of Tables .................................................................................................. 311
Manual
Version 1.2.0
Page 10
10 Not es about this Documentation WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
1 Notes about this Documentation
Always retain this documentation!
This documentation is part of the product. Therefore, retain the documentation
during the entire service life of the product. Pass on the documentation to any
subsequent user. In addition, ensure that any supplement to this documentation
is included, if necessary.
1.1 Validity of this Docu me nta tion
This documentation is only applicable to WAGO ETHERNET accessory products
“8/4-Port 1000BASE-T/1000BASE-SX/LX” (852-1305).
1.2 Copyright
This Manual, including all figures and illustrations, is copyright-protected. Any
further use of this Manual by third parties that violate pertinent copyright
provisions is prohibited. Reproduction, translation, electronic and phototechnical
filing/archiving (e.g., photocopying) as well as any amendments require the
written consent of WAGO Kontakttechnik GmbH & Co. KG, Minden, Germany.
Non-observance will involve the right to assert damage claims.
Manual
Version 1.2.0
Page 11
WAGO ETHERNET Accessories 852 Notes about this Documentation 11
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
1.3 Symbols
Personal Injury!
Indicates a high-risk, imminently hazardous situation which, if not avoided, will
result in death or serious injury.
Personal Injury Caused by Electric Current!
Indicates a high-risk, imminently hazardous situation which, if not avoided, will
result in death or serious injury.
Personal Injury!
Indicates a moderate-risk, potentially hazardous situation which, if not avoided,
could result in death or serious injury.
Personal Injury!
Indicates a low-risk, potentially hazardous situation which, if not avoided, may
result in minor or moderate injury.
Damage to Property!
Indicates a potentially hazardous situation which, if not avoided, may result in
damage to property.
Damage to Property Caused by Electrostatic Discharge (ESD)!
Indicates a potentially hazardous situation which, if not avoided, may result in
damage to property.
Important Note!
Indicates a potential malfunction which, if not avoided, however, will not result in
damage to property.
Manual
Version 1.2.0
Page 12

12 Not es about this Documentation WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Additional Information:
Refers to additional information which is not an integral part of this
documentation (e.g., the Internet).
Manual
Version 1.2.0
Page 13

WAGO ETHERNET Accessories 852 Notes about this Documentation 13
Table 1: Number Notation
Number Code
Example
Note
Decimal
100
Normal notation
Hexadecimal
0x64
C notation
Binary
'100'
'0110.0100'
In quotation marks, nibble separated
with dots (.)
Table 2: Font Conventions
Font Type
Indicates
italic
Names of paths and data files are marked in italic-type.
Menu
Menu items are marked in bold letters.
e.g.: Save
>
A greater-than sign between two names means the selection of a
e.g.: File > New
Input
Designation of input or optional fields are marked in bold letters,
Start of measurement range
“Value”
Input or selective values are marked in inverted commas.
Start of measurement range
[Button]
Pushbuttons in dialog boxes are marked with bold letters in square
e.g.: [Input]
[Key]
Keys are marked with bold letters in square brackets.
e.g.: [F5]
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
1.4 Number Notation
1.5 Font Conventions
e.g.: C:\Program Files\WAGO Software
menu item from a menu.
e.g.:
e.g.: Enter the value “4 mA” under
brackets.
.
Manual
Version 1.2.0
Page 14

14 Important Notes WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
2 Important Notes
This section includes an overall summary of the most important safety
requirements and notes that are mentioned in each individual section. To protect
your health and prevent damage to devices as well, it is imperative to read and
carefully follow the safety guidelines.
2.1 Legal Bases
2.1.1 Subject t o Changes
WAGO Kontakttechnik GmbH & Co. KG reserves the right to provide for any
alterations or modifications. WAGO Kontakttechnik GmbH & Co. KG owns all
rights arising from the granting of patents or from the legal protection of utility
patents. Third-party products are always mentioned without any reference to
patent rights. Thus, the existence of such rights cannot be excluded.
2.1.2 Personnel Qualification
All sequences implemented on Series 852 devices may only be carried out by
electrical specialists with sufficient knowledge in automation. The specialists must
be familiar with the current norms and guidelines for the devices and automated
environments.
All changes to the controller should always be carried out by qualified personnel
with sufficient sufficient skills in PLC programming.
2.1.3 Proper Use of the Industrial Switches
The device is designed for the IP30 protection class. It is protected against the
insertion of solid items and solid impurities up to 2.5 mm in diameter, but not
against water penetration. Unless otherwise specified, the device must not be
operated in wet and dusty environments.
Manual
Version 1.2.0
Page 15

WAGO ETHERNET Accessories 852 Important Notes 15
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
2.1.4 Technical Condition of Specified Devices
The devices to be supplied ex works are equipped with hardware and software
configurations, which meet the individual application requirements. These
modules contain no parts that can be serviced or repaired by the user. The
following actions will result in the exclusion of liability on the part of WAGO
Kontakttechnik GmbH & Co. KG:
• Repairs,
• Changes to the hardware or software that are not described in the
operating instructions,
• Improper use of the components.
Further details are given in the contractual agreements. Please send your
request for modified and new hardware or software configurations directly to
WAGO Kontakttechnik GmbH & Co. KG.
2.1.5 Standards and Regul a t ions for Operating the Industrial Switches
Please observe the standards and regulations that are relevant to installation:
• The data and power lines must be connected and installed in compliance
with the standards to avoid failures on your installation and eliminate any
danger to personnel.
• For installation, startup, maintenance and repair, please observe the
accident prevention regulations of your machine (e.g., DGUV Regulation
“Electrical Installations and Equipment”).
• Emergency stop functions and equipment must not be deactivated or
otherwise made ineffective. See relevant standards (e.g., DIN EN 418).
• Your installation must be equipped in accordance to the EMC guidelines so
electromagnetic interferences can be eliminated.
• Please observe the safety measures against electrostatic discharge
according to DIN EN 61340-5-1/-3. When handling the modules, ensure
that environmental factors (persons, workplace and packing) are well
grounded.
• The relevant valid and applicable standards and guidelines regarding the
installation of switch cabinets must be observed.
Manual
Version 1.2.0
Page 16
16 Important Notes WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
2.2 Safety Advice (Precautions)
For installing and operating purposes of the relevant device to your system the
following safety precautions shall be observed:
Do not work on devices while energized!
All power sources to the device shall be switched off prior to performing any
installation, repair or maintenance work.
Only install in appropriate housings, cabinets or electrical operation
rooms!
WAGO's 852 Series ETHERNET Switches are considered exposed operating
components. Therefore, only install these switches in lockable housings, cabinets
or electrical operation rooms. Access must be limited to authorized, qualified staff
having the appropriate key or tool.
Ensure a standard connection!
To minimize any hazardous situations resulting in personal injury or to avoid
failures in your system, the data and power supply lines shall be installed
according to standards, with careful attention given to ensuring the correct
terminal assignment. Always adhere to the EMC directives applicable to your
application.
Do not use in telecommunication circuits!
Only use devices equipped with ETHERNET or RJ-45 connectors in LANs.
Never connect these devices with telecommunication networks.
Replace defective or damaged devices!
Replace defective or damaged device/module (e.g., in the event of deformed
contacts), since the long-term functionality of device/module involved can no
longer be ensured.
Manual
Version 1.2.0
Page 17
WAGO ETHERNET Accessories 852 Important Notes 17
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Protect the components against materials having seeping and insulating
properties!
The components are not resistant to materials having seeping and insulating
properties such as: aerosols, silicones and triglycerides (found in some hand
creams). If you cannot exclude that such materials will appear in the component
environment, then install the components in an enclosure being resistant to the
above-mentioned materials. Clean tools and materials are imperative for
handling devices/modules.
Clean only with permitted materials!
Clean housing and soiled contacts with propanol.
Do not use any contact spray!
Do not use any contact spray. The spray may impair contact area functionality in
connection with contamination.
Do not reverse the polarity of connection lines!
Avoid reverse polarity of data and power supply lines, as this may damage the
devices involved.
Avoid electrostatic discharge!
The devices are equipped with electronic components that may be destroyed by
electrostatic discharge when touched. Please observe the safety precautions
against electrostatic discharge per DIN EN 61340-5-1/-3. When handling the
devices, please ensure that environmental factors (personnel, work space and
packaging) are properly grounded.
Laser radiation warning!
Do not stare into openings of the connections when no cable is connected, so as
not to expose the radiation.
It can emit invisible radiation.
It concerns here a laser class 1 according EN 60825-1.
Manual
Version 1.2.0
Page 18

18 Important Notes WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Radio interference in residential areas
This is a Class A device. This device can cause radio interference in residential
areas; in this case, the operator can be required to take appropriate measures to
prevent such interference.
Manual
Version 1.2.0
Page 19

WAGO ETHERNET Accessories 852 Important Notes 19
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
2.3 Special Use Conditions for ETHERNET Devices
If not otherwise specified, ETHERNET devices are intended for use on local
networks. Please note the following when using ETHERNET devices in your
system:
• Do not connect control components and control networks to an open
network such as the Internet or an office network. WAGO recommends
putting control components and control networks behind a firewall.
• Limit physical and electronic access to all automation components to
authorized personnel only.
• Change the default passwords before first use! This will reduce the risk of
unauthorized access to your system.
• Regularly change the passwords used! This will reduce the risk of
unauthorized access to your system.
• If remote access to control components and control networks is required,
use a Virtual Private Network (VPN).
• Regularly perform threat analyses. You can check whether the measures
taken meet your security requirements.
• Use “defense-in-depth” mechanisms in your system's security configuration
to restrict the access to and control of individual products and networks.
Manual
Version 1.2.0
Page 20

20 General WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
3 General
3.1 Scope of Supply
• 1 Industrial managed switch with multipoint connector
• Protective covers for unused ports
• Data cable RS-232 for CLI
3.2 Industrial ETHERNET Technology
The ra nge of WAGO switches ensures scalability of your network infrastructure
with outstanding electrical and mechanical characteristics. These robust devices
are designed for industrial use and they are fully compliant with IEEE 802.3,
802.3u, 802.3w, 802.3z, 802.3x, 802.3ab, 802.3ad, 802.1d, 802.1q, 802.1p and
802.1x standards.
They have voltage supply with a supply voltage range of 12 … 60 V.
Characteristics such as auto-negotiation and auto-MDI/MDIX (crossover) on all
10/100/1000BASE-T ports are also realized.
Manual
Version 1.2.0
Page 21

WAGO ETHERNET Accessories 852 General 21
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
3.3 Switching Technology
Industrial ETHERNET primarily uses switching technology. This technology
allows any network subscriber to send at any time because the subscriber always
has an open peer-to-peer connection to the next switch. The connection is
bidirectional, i.e., the subscriber can send and receive at the same time (full
duplex).
The targeted use of switching technology can increase real-time capability
because the peer-to-peer connection prevents collisions in network
communication.
The Industrial Managed Switch was developed for easy installation in a
manufacturing environment where vibration, shock, heat and radio frequency
interference are common.
Due to its compact size, the Industrial Managed Switch makes mounting on the
DIN rail particularly sim p le a n d in s tallation possible in environments with limited
space.
Two or more switches can be added in series to the Industrial Managed Switch.
Since all ports support 100 Mbit/, this series connection is possible for the
industrial managed switch from every port and with any number of switches.
The Industrial Managed Switch is also equipped with a variety of management
functions that let you configure communication parameters as you desire to
monitor network behavior in different ways. In addition, the Industrial Managed
Switch is built with dual redundant power inputs for maximum reliability and
network availability. Other integrated features of the switch such as Autonegotiation, Rate limitation, Port isolation, etc. optimize your network
performance and provide a secure network, offering a cost-effective solution in a
small but powerful package.
The 1000BASE SX/LX ports are designed to connect Gigabit SFP modules that
support network speeds of 100/1000 Mbit/s.
Manual
Version 1.2.0
Page 22

22 General WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Other key features are:
• Eight (8) 10/100/1000BASE-T, four (4) 1000BASE-SX/LX (SFP type fiber
transceivers) and one (1) Console port (RJ-45)
• Diagnostic LEDs on the front
• Web-based/SNMP Management
• Redundant DC power supply
• Large voltage range: 12 … 60 V
• DIP switches to set alarm functions
• Full compliance with IEEE 802.3, 802.3u, 802.3z, 802.3x, 802.3ad,
802.3ab, 802.1d, 802.1q, 802.1p, 802.1w, 802.1x standards
• Implemented functions:
- Dual ring
- ERPS
- Jet ring
- Xpress Ring (redundant ring) with less than 50 ms recovery time
• Non-blocking, store-and-forward switching, rapid spanning tree protocol
(RSTP)
• Auto-negotiation on all 10/100/1000Base-T ports
• Auto-MDI/MDIX (crossover) on all 10/100/1000BASE-T ports
• VLAN (802.1q) VID
• IGMP snooping for multicast filtering
• Port configuration status and statistics
• Port trunking
• SNMP v1/v2 and RMON
• Rugged IP30 metal housing
• Operable in vibration / shock
Manual
Version 1.2.0
Page 23

WAGO ETHERNET Accessories 852 Device Description 23
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4 Device Description
The 852-1305 is an indust rial ETHERNET switch with 8 10/100/1000BASE-T
ports, with autonegotiation and auto-MDI-/MDI-X detection at every port.
Using the Industrial Managed Switch's 8 ports, several segments can be set up
for reducing network load and a dedicated bandwidth assigned to each user
node.
In addition, the 852-1305 Industrial Managed Switch has 4 ports with SFP
1000BASE-SX/LX to connect multi-mode or single-mode fiber optic cables for
wave lengths of 850 nm (SX), 1310 nm (LX) and 1550 nm (ZX).
The 852-1305 is a cost-effect solution to keep up with the constant demands of
IP-based, industrial communication needs.
The Industrial Managed Switch is easy to configure and install and is best suited
for small to medium-sized networks.
Manual
Version 1.2.0
Page 24
24 De vice De s c ription W AGO ETHERNET Accessories 852
Table 3: Legend for the Figure “Front View of the Industrial Managed Switch”
Descrip-
tion
“Device Description” >
“Display Elements”
“Device Description” >
“Display Elements”
“Device Description” >
“Display Elements”
“Device Description” >
“Display Elements”
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.1 View
4.1.1 Front View
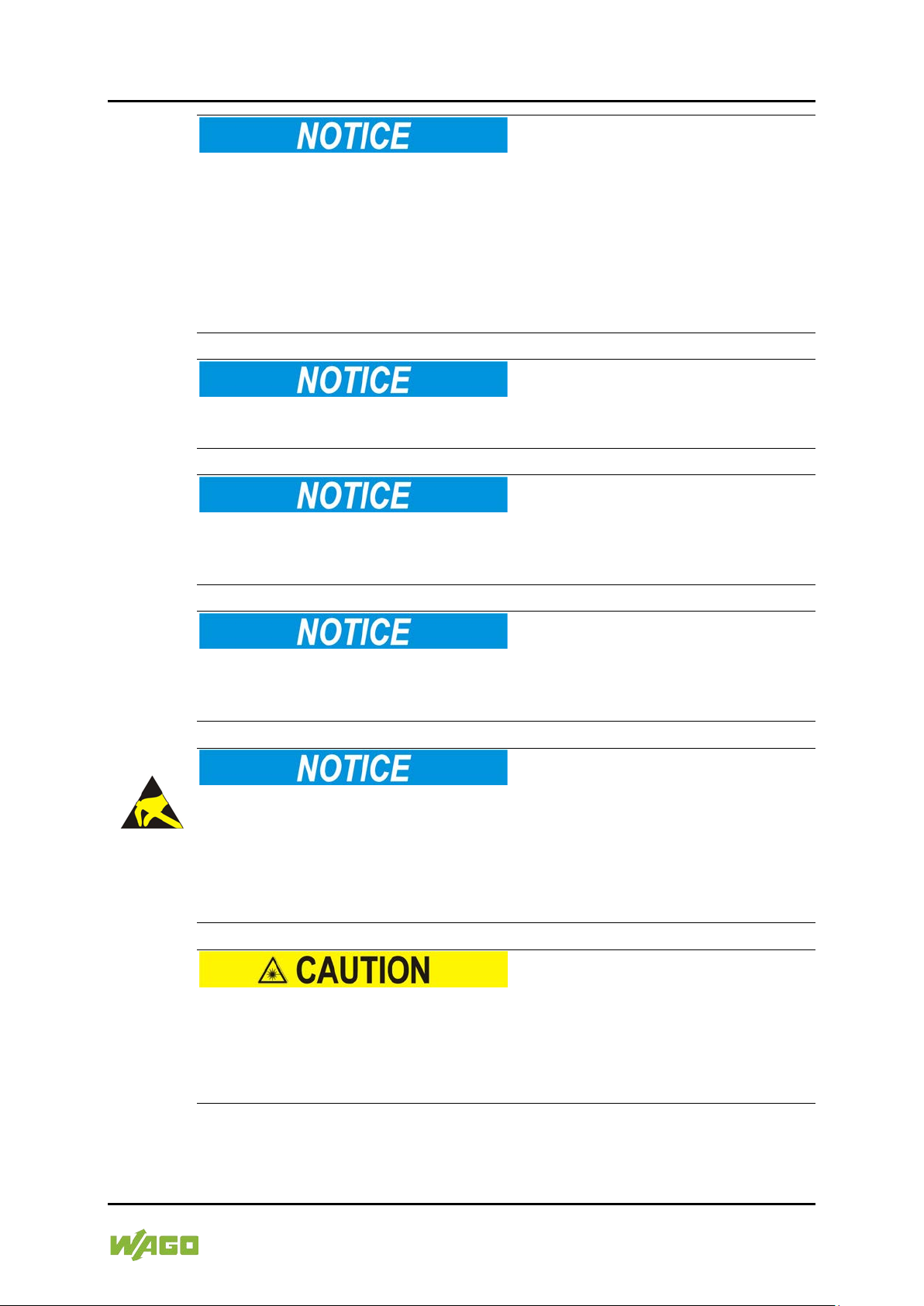
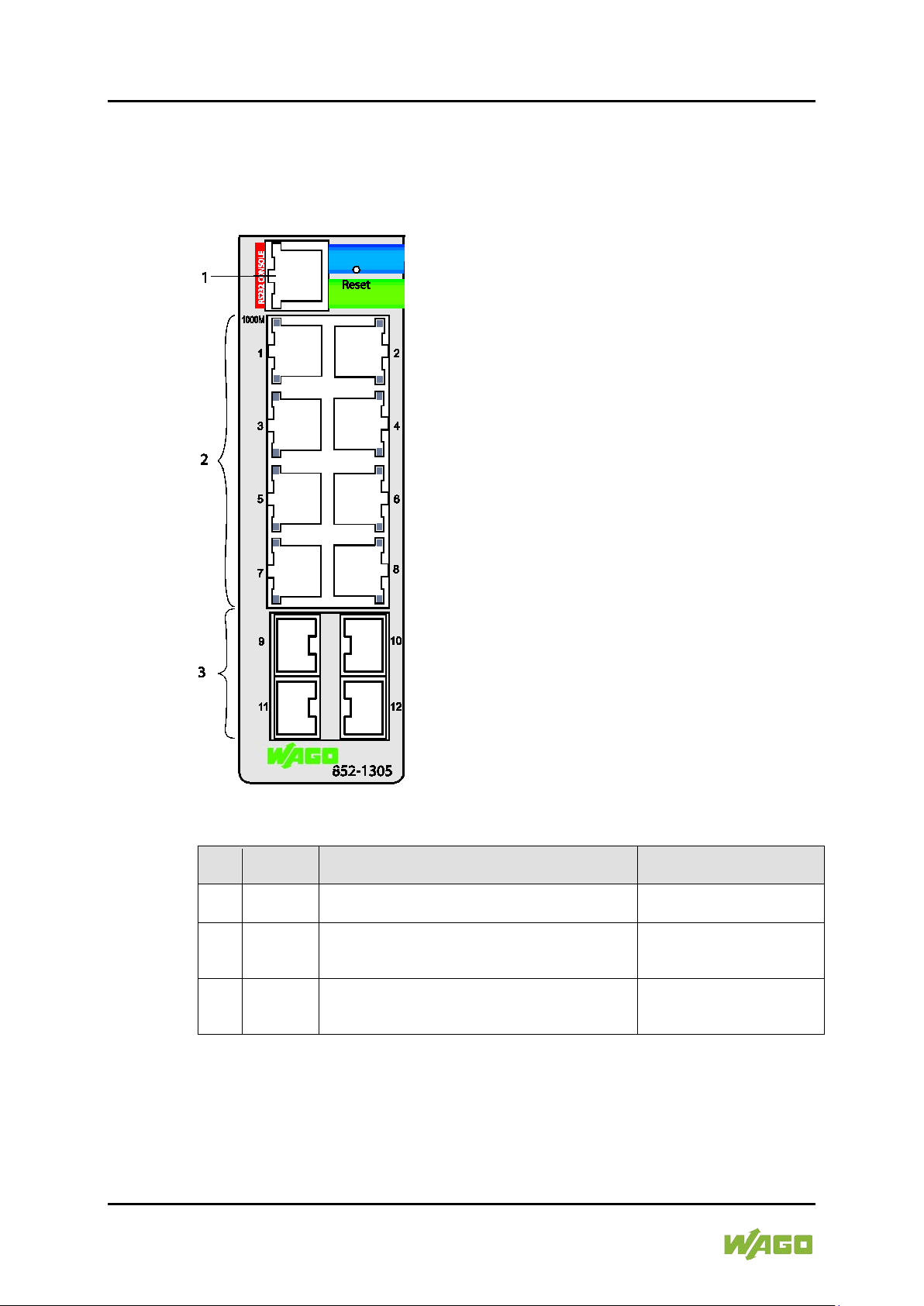
Figure 1: Front View of the Industrial Managed Switch
No.
1 PWR Status LED, supply voltage
2 RPS Status LED, redundant, supply voltage
3 ALM Status LED, alarm
4 POST Status LED, POST
Meaning For Details see Section
Manual
Version 1.2.0
Page 25
WAGO ETHERNET Accessories 852 Device Description 25
Table 3: Legend for the Figure “Front View of the Industrial Managed Switch”
Descrip-
tion
"Device Description" >
Status LED TX Port 1000 Mbit/s
(1 LED for each port)
“Device Description” >
“Display Elements”
Status LED TX Port 10/100 Mbit/s
(1 LED for each port)
“Device Description” >
“Display Elements”
"Device Description" >
"Device Description" >
"Connections"
"Device Description" >
"Connections"
“Device Description” >
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
No.
5 Reset R eset butto n
6 -
7 -
8 - Port 4 x SFP (1000BASE-SX/LX, fiber optic)
9 - Port 8 x RJ-45 (10/100/1000BASE-T ports)
10 - Port 1 x RJ-45 (RS-232 port switch)
11 SFP Status LED SFP port LNK/ACT (4)
Meaning For Details see Section
"Operating Elements"
"Connections"
“Display Elements”
Manual
Version 1.2.0
Page 26
26 De vice De s c ription W AGO ETHERNET Accessories 852
Table 4: Legend for the Figure “Front View of the Industrial Managed Switch”
Descrip-
tion
1 - Grounding lug
-
Connector (male) for power consumption
(PWR/RPS/ALM) and potential-free alarm contact
"Device Description" >
"Connections"
"Device Description" >
"Operating Elements"
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.1.2 Top View
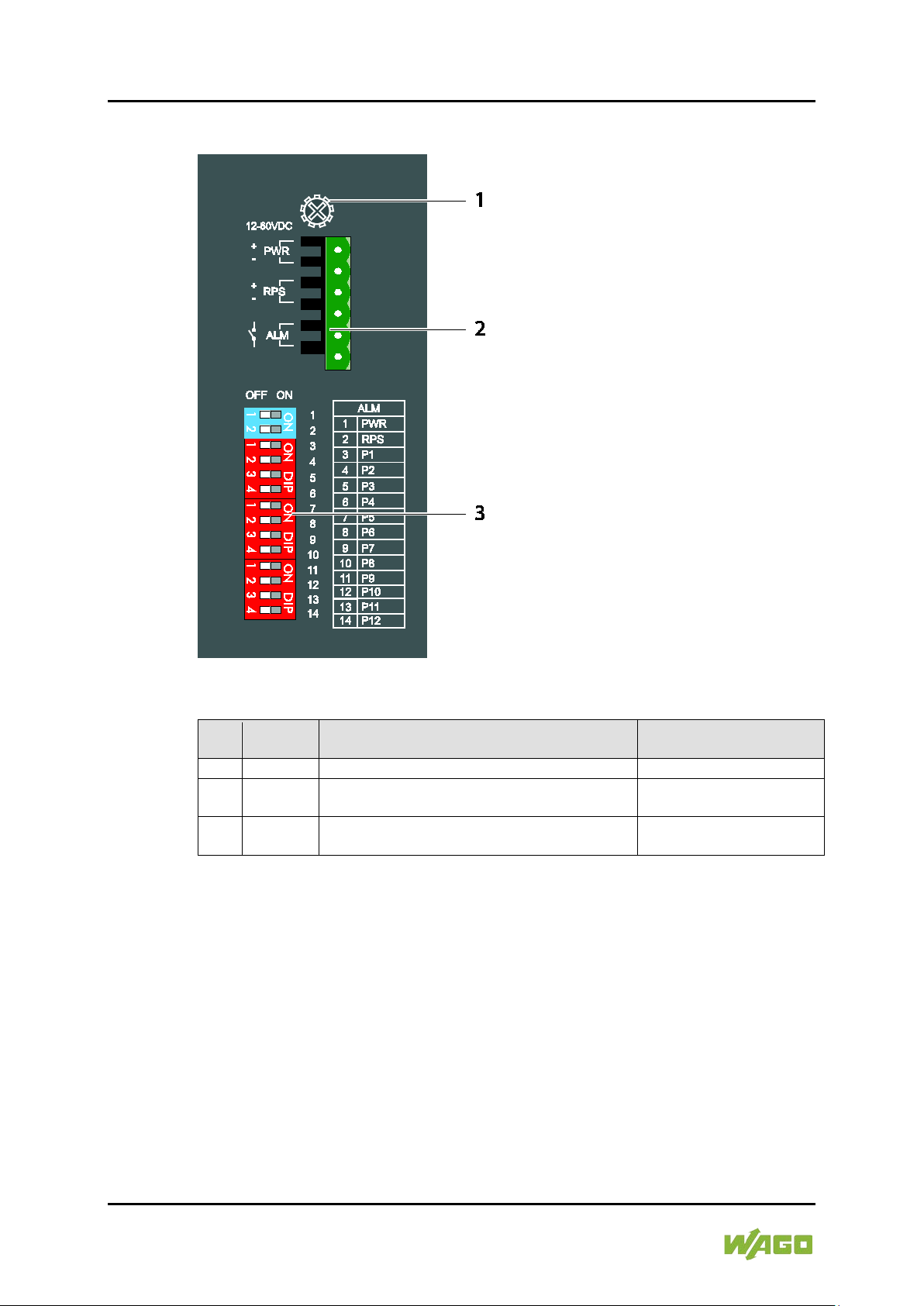
Figure 2: Top View of the industrial ECO switch
No.
2 -
3 - DIP Switches
Meaning For Details see Section
Manual
Version 1.2.0
Page 27
WAGO ETHERNET Accessories 852 Device Description 27
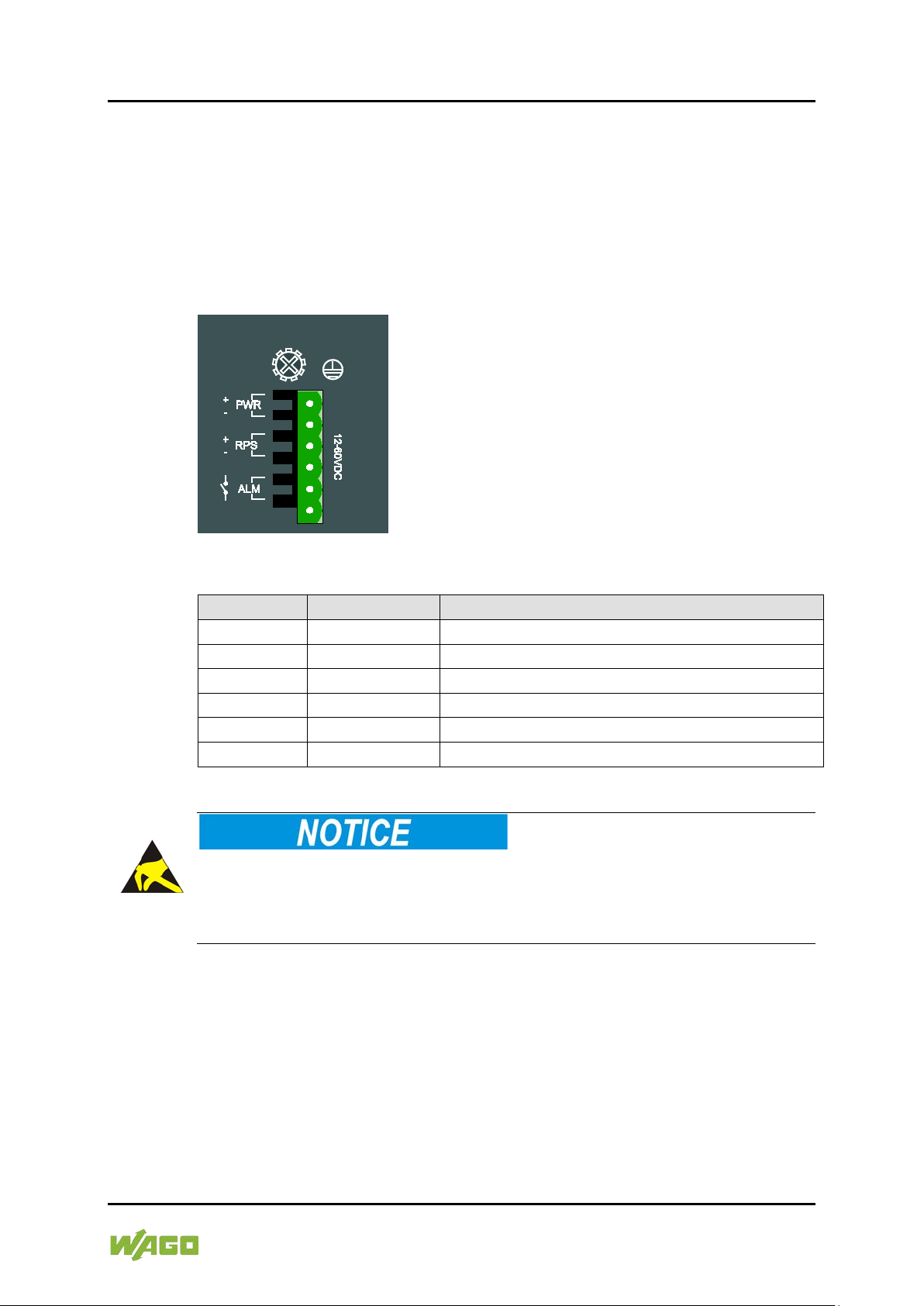
Table 5: Legend for Figure “Power Supply (PWR/RPS)”
Connection
Description
Description
+
PWR
Primary DC input
-
PWR
Primary DC input
+
RPS
Secondary DC input
-
RPS
Secondary DC input
ALM
Contact for external alarm
ALM
Contact for external alarm
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.2 Connectors
4.2.1 Power Supply (PWR/RPS)
The female connector (Item No. 2231-106/026-000) can easily be connected to
the 6-pole male connector located on the top of the switch.
The male connector shows the following pin assignment:
Figure 3: Power Supply (PWR/RPS)
Warning: Damage to property caused by electrostatic discharge (ESD)!
DC Powered Switch: Power is supplied through an external DC power source.
Since the switch does not include a power switch, plugging its power adapter into
a power outlet will immediately power it on.
Manual
Version 1.2.0
Page 28
28 De vice De s c ription W AGO ETHERNET Accessories 852
Table 6: Legend for Figure “Network Connections”
Descrip-
tion
“Device Description”
“Device Description”
“Device Description
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.2.2 Network Connectors
This Industrial Managed Switch utilizes ports with fiber or copper port connectors
functioning under ETHERNET and/or Fast ETHERNET protocols.
Figure 4: Network connectors
No.
1 - Connection 1 x RJ-45 (RS-232 port)
3 -
2 - Connections 8 x RJ-45 (10/100Base-T ports)
Manual
Version 1.2.0
Meaning For Details see Section
Connection 4 x SFP (1000Base-SX/LX, fiber
optic)
> … > “RJ-45 Port”
> … > “1000BASE SX/LX
Ports”
”> … > “10/100BASE T
Ports”
Page 29

WAGO ETHERNET Accessories 852 Device Description 29
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.2.2.1 RJ-45 Port
The connection to ETHERNET-based fieldbuses is made via the RJ-45
connector (also called “Western plugs”), which are connected to the fieldbus
controller via an integrated switch.
The integrated switch works in store-and-forward mode and for each port,
supports transmission speeds 10/100 Mbit/s as well as the full and half-duplex
transmission modes.
The RJ-45 socket is wired in accordance with 100Base TX requirements.
It is mandatory to use a Category 5e twisted-pair cable from the ETHERNET
standard as a connecting cable. Cable types S-UTP (Screened Unshielded
Twisted Pair) and STP (Shielded Twisted Pair) with a maximum segment length
of 100 m can be used.
The connection point is designed for mounting into an 80 mm-high switchgear
cabinet after connector attachment.
4.2.2.2 1000BASE SX/LX Ports
The 1000BASE SX/LX ports are designed to connect Fast ETHERNET or gigabit
SFP modules that support network speeds of 1000 Mbit/s.
4.2.2.3 10/100/1000BASE T Ports
The 10/100/1000BASE T ports support network speeds of 10 Mbit/s and
1000 Mbit/s and can be operated in half and full-duplex transmission modes.
These ports also provide automatic crossover detection (Auto-MDI/MDI-X) with
plug&play capabilities. Simply plug the network cables into the ports; they then
adapt to the end node devices. We recommend the following cables for the RJ45 ports.
• 10 m – Cat 3 or higher / 100 m – Cat 5e or higher
Manual
Version 1.2.0
Page 30
30 De vice De s c ription W AGO ETHERNET Accessories 852
Table 7: Legend for Figure “Device LEDs”
LED
Name
Status
Description
PWR
Primary Power
Green
The industrial managed switch uses
the primary power supply.
OFF
The primary power supply has been
RPS
Redundant Power
Green
The industrial managed switch uses
the redundant power supply.
OFF
The redundant power supply has been
switched off or a fault has occurred.
ALM
Alarm LED
Red
Lights up in the event of network,
OFF
No alarm to report.
POST
Power On Self Test
Flashe
s
Green
The Switch is operational.
OFF
The Switch is not operational.
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.3 Display Elements
The industrial managed switch is equipped with device LEDs and port LEDs. You
can see the status of the switch at a quick glance of the device LEDs, while the
port LEDs provide information about connection actions.
4.3.1 Device LEDs
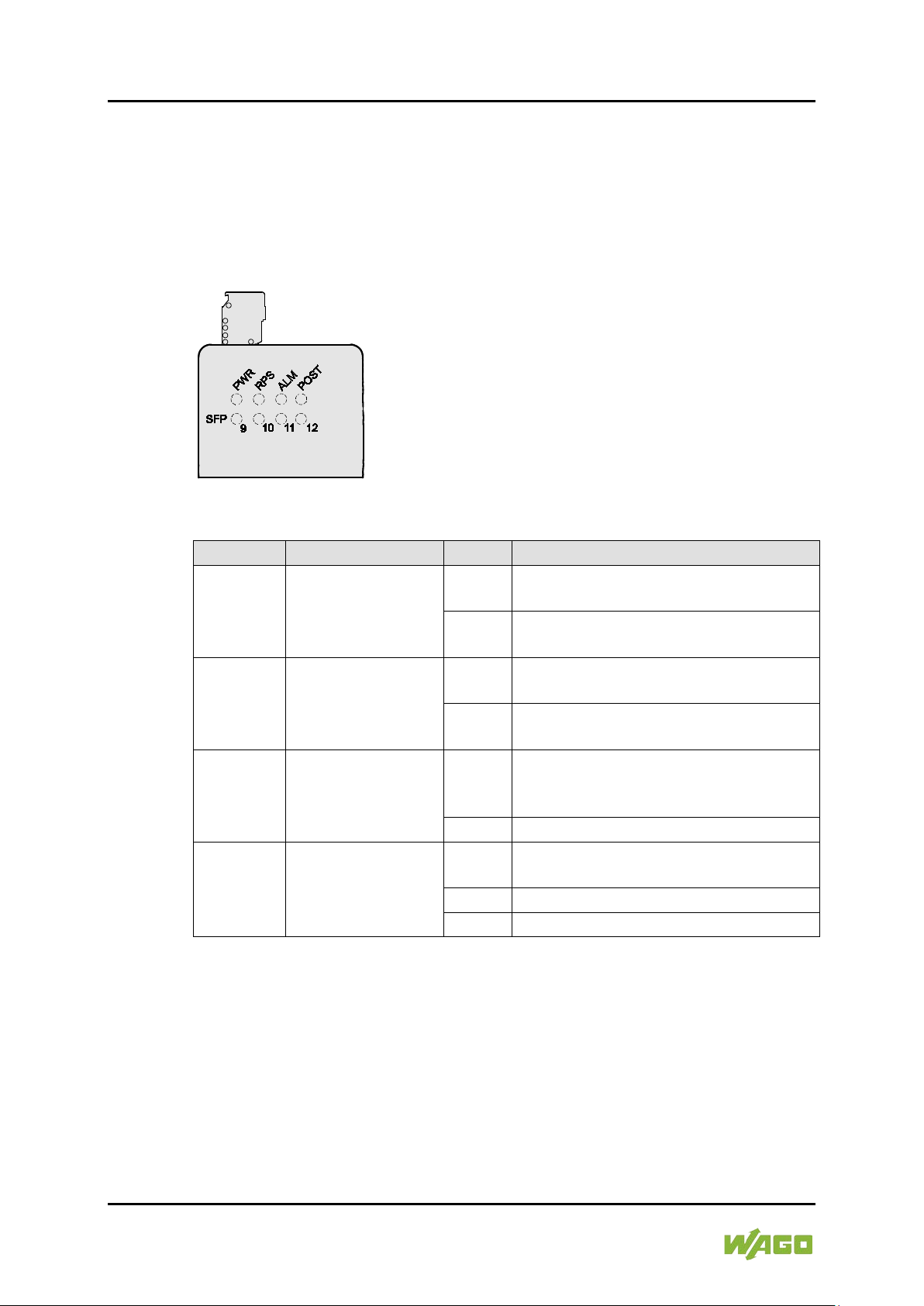
Figure 5: Device LEDs
LED
System LED
LED
switched off or a fault has occurred.
connection or ring errors (for Arbiter
nodes).
The Self Test is running.
Manual
Version 1.2.0
Page 31

WAGO ETHERNET Accessories 852 Device Description 31
Table 7: Legend for Figure “Device LEDs”
LED
Name
Status
Description
SFP Port LNK/ACT
Green
Lights up when the port is linked.
Flashe
Off
No proper link established at the port.
SFP Port LNK/ACT
Green
Lights up when the port is linked.
Flashe
s
Off
No proper link established at the port.
SFP Port LNK/ACT
Green
Lights up when the port is linked.
Flashe
s
Off
No proper link established at the port.
SFP Port LNK/ACT
Green
Lights up when the port is linked.
Flashe
Off
No proper link established at the port.
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
LED
9
Data traffic being routed via the port.
s
LED
10
Data traffic being routed via the port.
SFP
LED
11
Data traffic being routed via the port.
LED
12
Data traffic being routed via the port.
s
Manual
Version 1.2.0
Page 32

32 De vice De s c ription W AGO ETHERNET Accessories 852
Table 8: Legend for Figure “Port LEDs”
LED
Name
Status
Description
1000M
1000BASE T Ports
Green
Port in operation at 1000 Mbit/s.
Flashes
Data traffic being routed over the port.
Connection in operation at less than
100 Mbit/s.
10/100BASE T Ports
Green
Lights up when the ports are linked.
Flashes
Data traffic being routed over the port.
OFF
No proper link established at the port.
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.3.2 Port LEDs
Figure 6: Port LEDs
LED
(1 LED for each port)
10/100
LED
(1 LED for each port)
OFF
Manual
Version 1.2.0
Page 33

WAGO ETHERNET Accessories 852 Device Description 33
Table 9: Legend for Figure “DIP Switches
No.
Name
Status
Description
1
PWR
ON
The alarm reporting function for the primary power supply
is activated.
OFF
The alarm reporting function for the primary power supply
2
RPS
ON
The alarm reporting function for the secondary power
supply is activated.
OFF
The alarm reporting function for the secondary power
supply is deactivated.
3 …
P1 …
ON
The alarm reporting function for the port x connection is
activated.
OFF
The alarm reporting function for the port x connection is
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.4 Operating elements
4.4.1 DIP Switc hes
On the top side of the industrial switch there are DIP switches to configure th e
alarm and arbiter configurations.
The meaning of the DIP switch settings are described below:
Figure 7: DIP Switches
14
P12
is deactivated.
deactivated.
Manual
Version 1.2.0
Page 34

34 De vice De s c ription W AGO ETHERNET Accessories 852
Table 10: Legend for Figure “Reset Button”
Name
Status
Description
Reset
Press the Reset button for 2
seconds and release.
The system is restarted.
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
DIP switches let the user manually turn ON/OFF any port, the external alarm, or
the redundant power supply.
The DIP switch must be “ON” to activate the port alarm function. The default
setting is “OFF”.
The following is the recommended procedure for configuring and setting DIP
switches during initial installation:
1 Turn all DIP switches to “OFF”.
2 Install the industrial managed switch in your network.
3 Select the port(s) to be monitored or the alarm to be activated.
4 Set the DIP switch of the corresponding port to “ON”.
5 Turn the industrial managed switch ON.
4.4.2 Reset Button
Figure 8: Reset Button
Important Note!
Use a suitable object, e.g., ballpoint pen or straightened paper clip, to press the
Reset button.
Manual
Version 1.2.0
Page 35

WAGO ETHERNET Accessories 852 Device Description 35
Table 11: Legend for Figure “Label”
No.
“Serial NO” Description
02
Firmware version
01
Hardware version
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.5 Label
4.5.1 Hardware and Software Version
There is a label with the “MAC Address” and “Serial NO” on the back of the
industrial managed switch.
Figure 9: Label (Example)
Manual
Version 1.2.0
Page 36

36 De vice De s c ription W AGO ETHERNET Accessories 852
Table 12: Technical Data – Device Data
Width
Carrier rail mounting
50 mm
Height
Carrier rail mounting
120 mm (from the top edge of the
Depth
Carrier rail mounting
162 mm
Weight
910 g
Degree of protection
IP30
Table 13: Technical Data – System Data
MAC table
Up to 16000 addresses
VLAN
Port based and tag based (4094 VIDs)
Jumbo Frame Size
10240 bytes
Wavelength optical fibers
Depends on SFP module
Maximum lengths
10/100/
RS-232: 15 m
Table 14: Technical Data – Power Supply
Supply voltage
12 … 60 VDC
Power consumption, max.
18 W
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.6 Technical Data
4.6.1 Device Data
carrier rail)
4.6.2 System Data
4.6.3 Power Supply
1000BASE-TX: 100 m;
Fiber optic: 2 km to 80 km
Manual
Version 1.2.0
Page 37

WAGO ETHERNET Accessories 852 Device Description 37
Table 15: Technical Data – Communication
Ports
8 x 10/100/1000BASE-T (RJ-45);
1 x RS-232 (RJ-45)
Standards
IEEE 802.3u 100BASE-TX/FX;
IEEE 802.1x Port Authentication
Topology
Ring and star
Table 16: Technical Data ‒ Environmental Conditions
Surrounding air temperature, operation
-40 °C … +7 0 °C
Surrounding air temperature, operation,
DNV GL (Temperature class D)
-25 °C … +7 0 °C
Surrounding air temperature, stor age
-40 °C … +80 °C
Relative humidity (without
condensation)
95 %
Vibration resistance
Acc. IEC 60068-2-6
Shock resistance
Acc. IEC 60068-2-27
EMC-1 immunity to interference
Acc. EN 61000-6-2
EMC-1 Emission of interference
Acc. EN 61000-6-4
Standard Compass Safe Distance 0.3
Degree deflection
Steering, Standby, Emergency
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.6.4 Communication
4 x SFP 1000BASE-SX/LX, fiber optic;
IEEE 802.3ad Link Aggregation;
IEEE 802.3 10BASE-T;
IEEE 802.1d Spanning Tree Protocol;
IEEE 802.3x Flow Control;
IEEE 802.1p CoS Prioritization;
IEEE 802.1q VLAN Tagging;
IEEE 802.3ab LLDP;
IEEE 802.3ab 1000BASE-T;
IEEE 802.3w RSTP;
IEEE 802.3z 1000BASE-SX/LX;
4.6.5 Environmenta l Conditions
Compass Safe Distance 1.0 Degree
deflection
750 mm
500 mm
Manual
Version 1.2.0
Page 38

38 De vice De s c ription W AGO ETHERNET Accessories 852
Conformity Marking
DNV GL
Enclosure: A]
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
4.7 Approvals
The following approvals have been granted for the WAGO ETHERNET
accessory product “8/4-Port 1000BASE-T/1000BASE-SX/LX” (852-1305):
The following approvals are pending for WAGO ETHERNET accessory products
“8/4-Port 1000BASE-T/1000BASE-SX/LX” (852-1305):
Ordinary
Locations
The following ship approvals have been granted for the WAGO ETHERNET
accessory product “8/4-Port 1000BASE-T/1000BASE-SX/LX” (852-1305):
UL61010-2-201
[Temperature: D, Humidity: B, Vibration: C, EMC: B,
Manual
Version 1.2.0
Page 39

WAGO ETHERNET Accessories 852 Mounting 39
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
5 Mounting
5.1 Installation Site
The location selected to install the industrial managed switch may greatly affect
its performance. When selecting a site, we recommend considering the following
rules:
• Install the industrial managed switch at an appropriate place. See section
“Device Description” > … > “Technical Data“ for the acceptable
temperature and humidity operating ranges.
Make sure that the heat output from the industrial managed switch and ventilation
around it is adequate. Do not place any heavy objects on the industrial managed
switch.
5.2 Installation on a Carrier Rail
The carrier rail must optimally support the EMC measures integrated into the
system and the shielding of the internal data bus connections.
Place the industrial managed switch onto the DIN rail from the top and snap it
into position.
5.3 Removal from Carrier ail
To remove the industrial managed switch from the carrier rail, insert a suitable
tool into the metal tab under the switch and deflect the metal tab downward.
You can then release the switch down from the carrier rail and remove it
upwards.
Manual
Version 1.2.0
Page 40

40 Connect Devices WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
6 Connect Devices
6.1 Power Supply
The industrial managed switch uses direct current power supply for 12 … 60 V.
The primary and secondary network link is established via a 6-pin plug-in
connection located on the top of the industrial managed switch.
The female connector is composed of six connecting terminals and can be
inserted and removed easily by hand to connect to the 6-pin plug connector
located on the top of the switch.
The power supply for the industrial managed switch automatically adjusts to the
local power source and can also be switched On if no or not all patch cables are
connected.
1 Check whether the power LED on the front lights up when the device is
switched ON. If not, check that the power cable is correctly and securely
plugged in.
2 If a secondary power supply is connected, the RPS LED lights up.
3 PWR +/- conductors:
To connect or disconnect the conductors, actuate the spring in the female
connector directly using a screwdriver or an operating tool and insert or
remove the conductor.
4 For the backup DC connection, follow the same procedure as above.
Attach power wires to the female connector (in the position marked “RPS
+/-”).
5 Plug the female connector into the male connector of the switch if it has not
already been plugged in.
6 Check whether the power LED on the top of the device lights up when
power is supplied to the device. If not, check to ensure that the power cable
is plugged in correctly and fits securely.
Manual
Version 1.2.0
Page 41

WAGO ETHERNET Accessories 852 Connect Devices 41
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
6.2 External Alarm Contact Port
The industrial managed switch has an alarm contact connection on the top panel.
For detailed instructions on how to connect the alarm contact power wires to the
two ALM contacts of the 6-pin female connector, please refer to section “Power
Supply (PWR/RPS)” (it is the same procedure).
You can connect the alarm circuit to any warning device already installed in the
user's control room or factory floor. When a fault occurs, the industrial switch
sends a signal through the alarm contact to activate the external alarm. The
alarm contact has two ports that form a fault circuit for connecting to alarm
systems.
An alarm is signaled in the following cases:
1 Link failure (e.g., cable disconnected, device breakdown, etc.)
2 PWR/RPS:
a Power failure (power cord is disconnected, power supply malfunction,
etc.)
b Input power falls outside specification
(12 … 60 V)
3 Failure in jet ring or ERPS ring (Enhancement mode).
6.3 Console Port Cable Connection
The console port (RJ-45) provides the local management facility.
1. Insert the RJ-45 side of the (8 pin RJ-45 to DB9) cable into the RJ-45
console port on the Industrial Managed Switch and the other end into the
COM port of the computer.
2. Configure the Hyper Terminal settings as mentioned in chapter
“Configuration“ > … > “Console Port”.
For console port (8 pin RJ-45) pin assignment, please see in the chapter
“Appendix“ > …> “Console Port (RJ-45 to DB9)”.
Manual
Version 1.2.0
Page 42

42 Connect Devices WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
6.4 1000Base-SX/LX Port, Fiber Optic
When connecting a fiber optic cable to a 1000Base-SX/LX port on the industrial
managed switch, make sure to use the right connector type (LC) and SFP
module.
There are various types of multi-mode, single mode or WDM SFP modules.
Follow the steps below to connect the fiber optic cable properly:
Rubber covers
Remove and safely store the rubber covers of the fiber optic port (LC).
If no fiber optic cable is connected, the rubber cover should be installed to protect
the fiber optics.
1 Insert the respective SFP modules.
2 Ensure that the fiber optic ports are clean. You can clean the cable
connectors by wiping them with a clean cloth or a cotton ball soaked with a
little ethanol. Dirty fiber optic cables affect the quality of the light transmitted
via the cable and leads to reduced performance at the port.
3 Connect one end of the fiber optic cable to the LC port of the industrial
managed switch and the other end to the fiber optic port of the other
device.
Proper connection of the fiber optic cable to the SFP module
For a proper connection, snap the connector of the fiber optic cable into the SFP
module audibly.
4 Check the respective port LED on the industrial managed switch that the
connection is established (see section “Device Description” > … > “Display
Elements”).
Manual
Version 1.2.0
Page 43

WAGO ETHERNET Accessories 852 Connect Devices 43
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
6.5 10/100/1000BASE-T Ports
The 10/100BASE-T ports (RJ-45 ETHERNET ports) of the industrial managed
switch support both autosensing and autonegotiation.
1 Connect one end of the twisted pair cable of the type Category 3/4/5/5e to
an available RJ-45 port on the industrial managed switch and the other end
to the port of the selected network node.
2 Check the respective port LED on the industrial managed switch that the
connection is established.
(see section “Display Elements” > … > “Port LEDs”).
Manual
Version 1.2.0
Page 44

44 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7 Enhanced Features
7.1 Default Settings
7.1.1 Jumbo Frame
“Jumbo Frames” are ETHERNET frames with a size of more than 1500 bytes.
Jumbo frames can increase data transmission efficiency in a network. The bigger
the “Jumbo Frame”, the better the network performance.
“Jumbo Frame” settings
The “Jumbo Frame” settings apply to all ports.
If the size of a packet exceeds the size of the “Jumbo Frame”, the packet is
dropped.
7.1.2 SNTP
SNTP (“Simple Network Time Protocol”) is a protocol for synchronizing clocks in
computer systems. It is a less complex implementation of an NTP (“Network Time
Protocol”).
SNTP uses “Coordinated Universal Time” (French: “Temps Universel
Coordonné”). No information on time zones or daylight savings time is
transmitted. This information falls outside the protocol range and must be
obtained separately.
The SNTP port is 123.
1. T he SNTP server always replies the current UTC time.
2. If t he switch receives the SNTP reply time, it adjusts the time to the time
zone configuration and configures the time for the switch accordingly.
3. If the time server's IP address is not configured, the switch does not send
an SNTP request packet.
4. If t he switch does not receive an SNTP reply packet, it repeats the
challenge indefinitely every ten seconds.
5. If t he switch receives an SNTP reply, it repeats the time request from the
NTP server every hour.
6. If t he time zone and NTP server changes, the switch repeats the request
process.
7. No default SNTP server.
Manual
Version 1.2.0
Page 45

WAGO ETHERNET Accessories 852 Enhanced Features 45
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.1.3 Manageme nt Host
The management host limits the number of hosts that the switch can manage.
There is no “Management Host” in the default settings. Any host can manage the
switch via Telnet or web browser. If a user has configured one or more hosts,
only those hosts can manage the switch. The function allows users to configure
up to three entries for the management IPs.
7.1.4 MAC Management
The MAC address (“Media Access Control”) is the unique hardware number in a
network.
Dynamic Address
When receiving frames, the switch records the source MAC address, receiving
port, VLAN and an “Age Time” in the address table. When the “Age Time” is
expired, the address entry is deleted from the address table.
Static Address
A static address set by the user does not include the “age time” and is not
deleted by the switch. The static address can only be deleted by a user. The
switch supports an address table at up to 16 K.
Static and dynamic addresses share the same address table.
MAC Table
The “MAC Table” (MAC address table, also known as a filter database) shows
which frames are forwarded to the switch's ports or which frames are filtered out.
If a device that belongs to a VLAN group sends a data packet that is forwarded to
a port on the switch, the MAC address of the device is read from the switch's
MAC address table.
It also shows whether the MAC address is dynamic (assigned by the switch) or
static (set manually).
MAC Address Table
The switch uses the MAC address table to determine how to forward frames (see
figure below).
1. The switch checks a received frame and detects the port from which the
MAC source address originates.
2. The switch checks if the frame's destination MAC address matches a
source MAC address already detected in the MAC address table.
• If t he switch already knows the port for this MAC address, the it
forwards the frame to that port.
Manual
Version 1.2.0
Page 46

46 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
• If the switch does not already know the port for this MAC address, it
forwards the frame to all ports. “Port Flooding” (forwarded too often to
all ports) can lead to network congestion.
• If t he switch already knows the port for this MAC address and the
destination port is the same as the input port, the frame is filtered.
Figure 10: MAC Address Table Flowchart
7.1.4.1 Static MAC Settings
Static MAC Addresses
A static MAC address is an address that has been manually entered in the MAC
address table. Static MAC addresses have no “Age Time”. When you set up rules
for static MAC addresses, you are setting static MAC addresses for a port. This
may reduce data transmission needs.
7.1.4.2 Refusal MAC Settings
This type of MAC address entries is configured manually. The switch ignores
packets that have such MAC addresses as the source or destination contained in
“Blackhole” MAC address entries. “Blackhole” entries are configured to filter
frames with specific source or destination MAC addresses.
Manual
Version 1.2.0
Page 47

WAGO ETHERNET Accessories 852 Enhanced Features 47
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.1.5 Port Mirroring
Port mirroring is used on switches to copy sent/received network packets from
one or more areas of network monitoring or to send them to another switch port
(monitor port).
Port mirroring is used in network systems that require monitoring of network
traffic as in an IDS (“Intrusion Detection System”).
Port mirroring, together with an NTA (“Network Traffic Analyzer”) can help to
monitor network traffic. Users can monitor incoming and/or outgoing data packets
on selected ports (“Source Ports”).
Source Mode
• “Ingress”: The incoming data packets are copied and
forwarded to the monitor port.
• “Egress”: The outgoing data packets are copied and
forwarded to the monitor port.
• Both: Bot h incom ing and outgoing data packets are
copied and forwarded to the monitor port.
1. T he monitor port cannot be a member of a “Truck Port” group.
2. T he monitor port cannot be an ingress or egress port.
3. If a port has been configured as a source port and a user then
configures it as a destination port, the port is automatically deleted
from the source ports.
7.1.6 Port Settings
Duplex Mode
A duplex communication system is a system composed of two connected devices
that can communicate with each other in both directions.
Half-Duplex
A half-duplex system provides for communication in both directions, but only one
direction at a time (not simultaneously).
One device receives a signal and must wait for the other device to stop
transmitting before replying.
Manual
Version 1.2.0
Page 48

48 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Figure 11: Half-Duplex Mode
Full-Duplex
A full-duplex system (also known as a double-duplex system) can communicate
simultaneously in both directions.
Fixed-line telephone networks, for example, are full-duplex since both callers can
talk and listen at the same time.
Figure 12: Full-Duplex Mode
Loopback Test
In a “Loopback” test, a signal is sent from and then returned to a communication
device (“looped back”).
The test checks the proper function of the device and looks for faulty nodes in the
network.
For one type of “Loopback” test, a special plug (so-called “wrap plug”) is plugged
into a communications device. The plug causes transmitted (output) data to be
returned as received (input) data, simulating a closed communication circuit
using a single computer.
Manual
Version 1.2.0
Page 49

WAGO ETHERNET Accessories 852 Enhanced Features 49
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Auto MDI/MDIX
MDI (“Medium-Dependent Interface”) is part of the transmitter/receiver unit
(transceiver) of a network device.
Auto-MDIX (“Automatic Medium-Dependent Interface Crossover”) is a network
technology integrated in the port that automatically detects the required network
cable type (“Straight-Through” or “Crossover” cable) and configures the
connection accordingly.
“Crossover” cables are then unnecessary for connecting devices.
The interface corrects incorrect cabling automatically.
For Auto-MDIX to work properly, the speed of the interface and in the duplex
settings must be set to “Auto”.
Auto-Negotiation
Auto-negotiation is a method in which two interconnected ETHERNET network
ports (e.g., the network port of a PC and a port of a router, hub or switch that is
connected to it) that independently negotiate and configure the maximum
transmission speed and the duplex process.
Auto-negotiation only applies to twisted-pair cables, but not to WLAN, fiber optic
or coaxial cable connections.
If the port does not support auto-negotiation or the function is disabled, the switch
determines the connection speed by detecting the signal on the cable and using
half-duplex mode.
If auto-negotiation is enabled on the switch, a port uses its pre-configured
settings for speed and duplex mode when establishing the connection.
This should ensure that the same settings have been made on the port, allowing
the connection to be established.
Flow Control
“Flow Control” regulates the transmission of signals by adjusting them to the
bandwidth on the input port.
Higher data traffic on the port decreases the bandwidth and can overflow the
buffer memory, which can lead to packet and frame loss.
According to IEEE802.3x, the switch uses “Flow Control” in full-duplex mode and
“Backpressure Flow Control” in half-duplex mode.
Manual
Version 1.2.0
Page 50

50 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
For “Flow Control”, the switch sends a pause signal in full-duplex mode to the
sending port, causing it to temporarily stop sending signals when the buffer
memory of the receiving port is full.
For “Backpressure Flow Control”, the switch sends a collision signal to the
sending port in half-duplex mode (mimicking a state of packet collision), causing
the sending port to temporarily stop sending signals and to resend the signals
later.
Support for “Force Mode”
1000 Base-T does not support “Force Mode”.
Manual
Version 1.2.0
Page 51

WAGO ETHERNET Accessories 852 Enhanced Features 51
Priority
0 1 2 3 4 5 6 7 Queue
2 0 1 3 4 5 6
7
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2 Advanced Settings
7.2.1 Bandwidth Limitation
7.2.1.1 QoS
Each egress port supports up to eight “Transmit Queues”. Each “Transmit
Queue” contains a list specifying the packet transmission order. Each incoming
frame is forwarded to one of the eight “Transmit Queues” of the assigned egress
port based on its priority. The egress port transmits packets from each of the
eight “Transmit Queues” according to a configurable sequence algorithm, which
can be a combination of SP (“Strict Priority”) and/or WRR (“Weighted Round
Robin”).
Normally, networks operate on a best-effort delivery basis, i.e., all data traffic has
equal priority and an equal chance of being transmitted in a timely manner.
If congestion occurs, all data traffic has an equal chance of being dropped.
When configuring the QoS (“Quality of Service”) function, you can select a
specific data traffic, prioritize it according to its relative importance and use
congestion management and congestion-avoidance techniques to give
preferential treatment.
Implementing QoS in a network improves network predictability and increases
bandwidth utilization.
The industrial managed switch supports “802.1p Priority Queuing”.
The switch has eight “Priority Queues”. These priority queues are numbered,
where Class 7 is the highest and Class 0 the lowest priority queue. The eight
priority classes specified in IEEE 802.1p (p0 to p7) are mapped to the switches
priority queues as follows:
The “Priority Scheduling” is implemented in “Priority Queues”. The switch
operates the four “Hardware Priority Queues” sequentially, where it starts with the
highest “Priority Queue” (3) and ends with the lowest (0). Each “Hardware
Queue” transmits all packets in its buffer before the next lower priority is allowed
to transmit its packets. If the lowest “Hardware Priority Queue” transmits all its
packets, the highest starts to transmit its packets again that it received in the
meantime.
Manual
Version 1.2.0
Page 52

52 Enhanced Features WAGO ETHERNET Accessories 852
6 6 2
42-1496
4
DA
SA
Type / Length
Data
FCS
6 6 4
2
42-1496
4
DA
SA
802.1Q Tag
Type / Length
Data
FCS
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
QoS Enhancement
You can configure the switch to prioritize data traffic even if the incoming packets
are not marked with “IEEE 802.1p Priority Tags” or change the existing ׅ◌ “Priority
Tags” based on the criteria you select. The switch allows you to choose one of
the following methods for assigning priority to incoming packets:
• 802.1p Tag Priority
- Assign priority to packets based on the packet's “802.1p Tag Priority”.
• Port-based QoS
- Assign priority to packets based on the incoming port on the switch.
• DSCP-based QoS
- Assign priority to packets based on their DSCP (“Differentiated
Services Code Points”).
Advanced QoS Methods
Advanced QoS methods only affect the internal “Priority Queue” mapping for the
switch. The switch does not modify the IEEE 802.1p value for the egress frames.
You can choose one of these options above to alter the way incoming packets
are prioritized or you can choose not to use any QoS extension setting on the
switch.
802.1p Priority
When using the 802.1p priority mechanism, the packet is examined for the
presence of a valid “802.1p Priority Tag”. If it has a tag, the packet is designated
to a configurable “Egress Queue” based on its priority value. The “Tag Priority”
can be designated to any of the available “Queues”.
ETHERNET Packet
Manual
Version 1.2.0
Page 53

WAGO ETHERNET Accessories 852 Enhanced Features 53
2 bytes
2 bytes
Tag Protocol Identifier (TPID)
Tag Control Information (TCI)
16 bits
3 bits
1 bits
12 bits
TPID (0x8100)
Priority
CFI
VID
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
802.1Q Tag:
• TPID (“Tag Protocol Identifier”)
A 16-bit field is set to the value of 0x8100 to identify the frame as an “IEEE
802.1Q Tag Frame”.
• TCI (“Tag Control Information”)
- PCP (“Priority Code Point”)
A 3-bit field that refers to the IEEE 802.1p priority. It indicates the frame
priority level from 0 (lowest) to 7 (highest), which can be used to
prioritize different classes of traffic (voice, video, data, etc.).
- CFI (“Canonical Format Indicator”)
A 1-bit field. If the value of this field is 1, the MAC address is in noncanonical format. If the value is 0, the MAC address is in canonical
format. It is always set to 0 for ETHERNET switches. CFI is used for
compatibility between ETHERNET and “Token Ring” networks. If a
frame received at an ETHERNET port has a CFI of 1, the frame should
not be output to an untagged port.
- VID (“VLAN Identifier”)
A 12-bit field specifying the VLAN to which the frame belongs. A value
of 0 means that the frame does not belong to any VLAN; in this case,
the “802.1Q Tag” specifies only a priority and is referred to as a
“Priority Tag”. A hexadecimal value of 0xFFF is reserved for
implementation purposes. All other values may be used as “VLAN
Identifiers”, allowing support for up to 4094 VLANs. On “Bridges”,
VLAN 1 is often reserved for management.
Manual
Version 1.2.0
Page 54

54 Enhanced Features WAGO ETHERNET Accessories 852
Table 17: Priority Levels
PCP
Network Priority
Traffic Characteristics
1
0 (lowest)
“Background”
0 1 “Best Effort”
2 2 “Excellent Effort”
3 3 “Critical Applicat ion s ”
4 4 Video, < 100 ms latency
5 5 Video, < 10 ms latency
6 6 Internetwork Control
7
7 (highest)
Network Control
Version
IHL
Type of Service
Total Length
Marking
Flags
Fragment Offset
Time t o Live
Protocol
Header Checksum
Source Address
Destination Address
Options
Padding
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Priority Levels
PCP (“Priority Code Point”):
DiffServ (DSCP)
DiffServ (“Differentiated Services”) is a computer networking architecture that
specifies a simple, scalable and coarse-grained mechanism, managing network
traffic and providing (“Quality of Service”) guarantees in modern IP networks.
DiffServ can, for example, be used to provide low-latency, guaranteed service
(“Guaranteed Service”) to critical network traffic such as voice or video data while
providing simple “Best Effort” traffic guarantees to non-critical services such as
web traffic or file transfers.
DSCP (“Differentiated Services Code Point”) is a 6-bit field in the header of IP
packets for packet classification purposes. DSCP replaces the outdated IP
precedence, a 3-bit field in the “Type of Service” byte of the IP header originally
used to classify and prioritize types of traffic.
When using the DiffServ priority mechanism, a packet is classified based on the
DSCP field in the IP header. If the tag is present, the packet is assigned to a
programmable “Egress Queue” based on the value of the “Tagged Priority”. The
“Tagged Priority” can be designated to any available “Queue”.
Example Internet Data Packet Header
“Type of Service” in the IP header: 8-bit
Manual
Version 1.2.0
The “Type of Service” field provides an indication of the abstract parameters of
the “Quality of Service” desired. These parameters are to be used to guide the
Page 55

WAGO ETHERNET Accessories 852 Enhanced Features 55
Bit 0 … 2
Precedence.
Bit 3
0 = Normal delay,
1 = Low delay.
Bit 4
0 = Normal throughput,
1 = High throughput.
Bit 5
0 = Normal reliability,
1 = High reliability.
Bit 6 … 7
Reserve for future use.
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
manual selection of the actual service parameters when transmitting a data
packet through a particular network. Several networks offer service precedence,
which treats high precedence traffic as more important than other traffic
(generally by accepting only traffic above certain precedence at time of high
load). The most favorable choice is a compromise between low delay, high
reliability and high throughput.
0 1 2 3 4 5 6 7 0 1 2 3
4 5 6 7
+-----+-----+-----+-----+-----+-----+-----+-----+
| PRECEDENCE | D | T | R | 0 | 0 |
+-----+-----+-----+-----+-----+-----+-----+-----+
Precedence
111 – Network Control
110 – Internetwork Control
101 – CRITIC/ECP
100 – Flash Override
011 – Flash
010 – Immediate
001 – Priority
000 – Routine
Specifying the Delay, Throughput and Reliability parameters can increase the
service cost. In many networks, preference for one parameter means a
disadvantage for another. Except for very unusual cases, two of three
parameters should be specified at most.
The “Type of Service” is used to specify the type of processing of the data packet
while it is transmitted through a network. Example mappings of the “Internet Type
of Service” to the actual service provided in networks, such as AUTODIN II,
ARPANET, SATNET and PRNET are specified in “Service Mappings”.
Manual
Version 1.2.0
The Network Control precedence designation should only be used within a
network. The actual use and control of that designation depends on the
respective network. The Internetwork Control designation should only be
changed by the initiators of the gateway control.
Page 56

56 Enhanced Features WAGO ETHERNET Accessories 852
DSCP
Priority
DSCP
Priority
DSCP
Priority
0 0 1 0 2 0 …
60 0 61 0 62 0 62 0
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
If these precedence designations apply to a specific network, it is the
responsibility of that network to control access to and the use of those
designations.
Example:
IP Header
DSCP=50 -> 45 C8 …
Manual
Version 1.2.0
Page 57

WAGO ETHERNET Accessories 852 Enhanced Features 57
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Queuing Algorithms
“Queuing Algorithms” can be used to maintain separate “Queues” for packets
that can be derived from any single source or any data flow, thus preventing a
source from monopolizing the bandwidth.
SPQ
With SPQ (“Strict Priority Queuing”), the four “Hardware Priority Queues” are
processed sequentially – the highest priority (3) first and the lowest (0) last. Each
“Hardware Queue” transmits all packets in the buffer before the next lower priority
is allowed to transmit its packets. If the lowest “Hardware Priority Queue”
transmits all its packets, the highest starts to transmit its packets again that it
received in the meantime.
WRR
RR (“Round Robin”) is a scheduling service that queues packets on a rotating
basis and is only activated when a port has more traffic than it can handle. A
“Queue” is given an amount of bandwidth irrespective of the incoming traffic on
that port. This “Queue” then moves to the back of the list. The next “Queue” is
given an equal amount of bandwidth and then moves to the end of the list and so
on until all “Queues” are processed. The entire process works in a looping
fashion until a “Queue” is empty.
WRR (“Weighted Round Robin”) scheduling uses the same algorithm as “Round
Robin” scheduling, but services “Queues” based on their priority and queue
weight (the number you configure in the “Weight Value” field) rather than a fixed
amount of bandwidth. WRR is activated only when a port has more traffic than it
can handle. “Queues” with larger weights get more service than those with
smaller weights. This queuing mechanism is highly efficient in that it divides any
available bandwidth across the different “Traffic Queues” and returns to queues
that have not yet emptied.
DiffServ Function
DiffServ is disabled on the industrial managed switch.
If the DiffServ is disabled, the “802.1p Tag Priority” is used.
Manual
Version 1.2.0
Page 58

58 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.1.2 Rate Limitation
7.2.1.2.1 Storm Control
A broadcast storm means that the network is overwhelmed with constant
broadcast or multicast traffic. Broadcast storms can eventually lead to a complete
loss of network connectivity as the packets proliferate.
“Storm Control” protects the switch bandwidth from packet flooding, including
broadcast packets, multicast packets and DLF (“Destination Lookup Failure”).
The Rate is a threshold that limits the total number of specific packet types. For
example, if the broadcast and multicast options are selected, the total number of
packets transmitted per second for those two types is not exceed.
“Broadcast Storm Control” limits the number of broadcast, multicast and unknown
unicast (also referred to as “Destination Lookup Failure” or DLF) packets the
switch receives per second on the ports. If the maximum number of packets per
second is reached, all subsequent packets are discarded. Enable this function to
reduce the number of these packets in the network.
The “Storm Control” unit is 625 pps (packets per second).
7.2.1.2.2 Rate Limitati o n
The “Rate Limitation” is used to control the rate of traffic sent or received on a
network interface.
Manual
Version 1.2.0
Page 59

WAGO ETHERNET Accessories 852 Enhanced Features 59
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.2 IGMP Snooping
“IGMP Snooping” (“Internet Group Management Protocol Snooping”) is used for
multicast data traffic. The switch can passively “snoop” on IGMP packets
transmitted between IP multicast routers/switches and IP multicast hosts to learn
the IP multicast group membership. “IGMP Snooping” allows a switch to detect
multicast groups without a user having to manually configure them.
It checks IGMP packets passing through it, reads the group registration
information and configures multicasting accordingly.
The switch forwards multicast traffic to its multicast destination groups (that it has
detected from “IGMP Snooping” or that you have manually configured) to ports
that are members of those groups. “IGMP Snooping” generates no additional
network traffic, allowing you to significantly reduce multicast traffic passing
through the switch.
The switch can perform “IGMP Snooping” on up to 4094 VLANs. You can
configure the switch to automatically detect multicast group membership in all
VLANs. The switch then performs “IGMP Snooping” on the first VLANs that send
IGMP packets.
This is referred to as “Auto Mode”. Alternatively, you can specify the VLANs that
“IGMP Snooping” should be performed on. This is referred to as “Fixed Mode”. In
“Fixed Mode”, the switch does not detect multicast group membership of any
VLANs other than those explicitly added as an “IGMP Snooping” VLAN.
Immediate Leave
If you enable the “IGMP Immediate Leave” function, the switch immediately
deletes a port when it receives a “Leave message” with IGMP Version 2 on that
port. You should use the “Immediate Leave” function only when there is a single
receiver present on every port in the VLAN (“Immediate Leave” is only supported
on IGMP Version 2 hosts).
The switch uses the “Immediate Leave” function with “IGMP Snooping” to remove
an interface from the forwarding table that sends a “Leave Message” without the
switch sending group-specific queries to the interface. The VLAN interface is
deleted from the multicast tree for the multicast group specified in the original
“Leave Message”. “Immediate Leave” ensures optimal bandwidth management
for all hosts in a switched network, even when multiple multicast groups are
simultaneously in use.
Manual
Version 1.2.0
Page 60

60 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Fast Leave
The switch allows you to configure a delay time. When the delay time is expired,
the switch deletes the interface from the multicast group.
Last Member Query Interval
The “Last Member Query Interval” is the maximum response time in groupspecific queries sent in response to “Leave Group” messages, and also shows
the time between group-specific query messages.
If the switch receives an “IGMP Leave Message” from a subscriber on a receiver
port without the “Immediate Leave” function being enabled, the switch sends an
IGMP-specific query on this port and waits for IGMP group membership reports.
If the switch receives no messages within a configured period, the receiver port is
removed from the multicast group.
IGMP Querier
There is normally only one “Querier” per physical network. All multicast routers
start up as a “Querier” on each attached network. If a multicast router receives a
“Query Message” from a router with a lower IP address, it MUST become a non“Querier” in that network. If a router does not receive any “Query Messages” from
another router over a certain period of time [“Other Querier Present Interval”], it
assumes the role of “Querier”. Routers periodically [“Query Interval”] send a
“General Query” in all attached networks for which the router is the “Querier” to
solicit membership information. At startup, a router SHOULD send [“Startup
Query Count”] “General Queries” spaced closely together [“Startup Query
Interval”] to quickly and reliably determine membership information. A “General
Query” is addressed to an all-systems multicast group (224.0.0.1), has a group
address field of 0 and has a maximum response time of [“Query Response
Interval”].
Manual
Version 1.2.0
Page 61

WAGO ETHERNET Accessories 852 Enhanced Features 61
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Port IGMP Querier Mode
• Auto
- The switch uses the port as an “IGMP Query Port” if the port receives
“IGMP Query” packets.
• Fixed
- The switch always uses the port(s) as “IGMP Query Port(s)”. This
mode is used when connecting an IGMP multicast server to the port(s).
- The switch always forwards the clients “Report/Leave” packets to the
port. Normally, the port is connected to an IGMP server.
• Edge
- The switch does not use the port as an “IGMP Query Port”.
- The “IGMP Query” packets received on this port are dropped.
Normally, the port is connected to an IGMP client.
Forwarding “IGMP Join/Leave” packets
The industrial managed switch will forward the “IGMP Join/Leave” packets to the
query port.
IGMP Proxy Snooping
The “IGMP Proxy Snooping” can reduce the number of “Reports” and “Leaves”
sent through an IGMP router.
Configurations
Users can enable/disable “IGMP Snooping” on the switch. This also applies to
specific VLANs. If “IGMP Snooping” on the switch is disabled, it is disabled on all
VLANs even when enabled on some VLANs.
VLAN States
There is a global state and individual VLAN states.
If the global state is disabled, “IGMP Snooping” on the switch is disabled even if
individual VLAN states have been enabled.
If the global state is enabled for “IGMP Snooping”, the function must be
individually enabled by the user for specific VLANs.
Manual
Version 1.2.0
Page 62

62 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.2.1 MVR
MVR (“Multicast VLAN Registration”) through which a media server can transmit
a multicast stream in an individual multicast VLAN and in which the clients
receiving the VLAN stream can be located in different VLANs. Clients in different
VLANs can join or leave the multicast group simply by sending an “IGMP Join
Message” or “IGMP Leave Message” to a receiver port. The receiver port
belonging to a multicast groups can receive the multicast stream from the media
server. Without MVR support, the multicast stream from the media server and
subscriber would have to be in the same VLAN.
• Source ports : T he source ports of the stream.
• Receiver ports: The reports of the clients.
• Ports with tag : Configure ports with tags to designate them as
source ports or receiver ports.
MVR Mode
• Dynamic Mode
If dynamic mode is enabled in the MVR settings, the “IGMP Report
Message” is transmitted from the receiver port to the source ports of the
multicast router. The multicast router can detect dynamically which
multicast groups are on which interface.
• Compatibility Mode
If compatibility mode is enabled in the MVR settings, the “IGMP Report
Message” send by the receiver port is not transmitted to the source ports of
the multicast router. The multicast router must be statically configured.
• Operating Mode
Join Operation
A subscriber sends an “IGMP Report Message” to the switch to join a
respective multicast. The next step depends on whether the “IGMP Report
Message” matches the multicast MAC address configured on the switch. If
it matches, the switch CPU modifies the hardware address table to include
the receiver port and the VLAN as a forwarding destination for the MVLAN.
• Leave Operation
A subscriber sends an “IGMP Leave Message” to the switch to leave the
multicast. The switch CPU sends a group-specific “IGMP Query” to the
receiver port of the VLAN. If there is another subscriber in the VLAN, the
subscriber must respond within the maximum response time. If there is no
subscriber, the switch deletes the receiver port.
Manual
Version 1.2.0
Page 63

WAGO ETHERNET Accessories 852 Enhanced Features 63
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
• Immediate Leave Operation
A subscriber sends an “IGMP Leave Message” to the switch to leave the
multicast. The subscribers do not need to wait for the switch CPU to send a
group-specific “IGMP Query” to the receiver port of the VLAN. The switch
immediately deletes the receiver port.
Figure 13: MOD without MVR
Figure 14: MOD supports MVR
Default configuration for a new MVR:
MVR VLAN information
VLAN ID: 2
Name: MVR2
Active: Enabled
Mode: Dynamic
Source port(s): None
Receiver port(s): None
Port(s) with tag: None
Manual
Version 1.2.0
Page 64

64 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
The switch allows the user to create up to 250 groups.
The switch allows the user to create up to 16 MVRs.
• “IGMP Snooping” and MVR can be enabled independently.
• “IGMP Snooping” and MVR use the same IGMP timer.
• MVR can recognize IGMPv3 reports.
• The switch as wells as the following group record types do not treat group
entries such as an IGMPv3 report as membership reports. The group
record types are “MODE_IS_INCLUDE”,
“CHANG E_ TO_INCLUDE_MODE”, “ALLOW_NEW_SOURCES” and
“BLOCK_OLD_SOURCES”.
• Do not use group address X.0.0.1 for your multicast stream. The system
detects and logs the address 224.0.0.1 for the dynamic “Querier Port”.
The group address X.0.0.1 could cause a conflict with 224.0.0.1.
• The lower 23 bits of the 28-bit multicast IP address are mapped to the
23 bits of the available ETHERNET address space.
When configuring the group address, the swit c h only compares the lower
23 bits.
• The CLI command “group 1 start-address 224.1.1.1 6” creates 6 groups.
That is, one IP, one group.
• The MVR name should be a combination of numbers and letters.
• The group name should be a combination of numbers and letters.
Manual
Version 1.2.0
Page 65

WAGO ETHERNET Accessories 852 Enhanced Features 65
Table 18: Multicast C lasses and Address Ranges
Class
Address Range
Support
Class A
1.0.0.1 to
Supports 16 million hosts on each of 127
Class B
128.1.0.1 to
191.255.255.254
Supports 65,000 hosts on each of 16,000
networks.
Class C
192.0.1.1 to
223.255.254.254
Supports 254 hosts on each of 2 million
networks.
Class D
224.0.0.0 to
239.255.255.255
Reserved for multicast groups.
Class E
240.0.0.0 to
Reserved for future use or research and
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.2.2 Multicast Address
A multicast address is associated with a group of interested receivers. According
to RFC 3171, addresses 224.0.0.0 to 239.255.255.255 (formerly Class D
addresses) are reserved as multicast addresses in IPv4.
The first octet (01) includes the broadcast/multicast bit. The lower 23 bits of the
28-bit multicast IP address are mapped to the 23 bits of the available
ETHERNET address space. This means that there is ambiguity in delivering
packets. If two hosts on the same subnet each subscribe to different multicast
groups whose addresses differ only in the first 5 bits, ETHERNET packets for
both multicast groups are sent to both hosts, requiring the network software in
the hosts to discard the unnecessary packets.
126.255.255.254
254.255.255.254
networks.
development purposes.
Manual
Version 1.2.0
Page 66

66 Enhanced Features WAGO ETHERNET Accessories 852
Table 19: IP Multicast Addresses
IP multicast address
Description
224.0.0.0
Base address (reserved)
224.0.0.1
“All Hosts Multicast” group that contains all systems on
the same network segment.
224.0.0.2
“All Routers Multicast” group that contains all routers on
224.0.0.5
The “Open Shortest Path First” (OSPF protocol), the
to all OSPF routers on a network segment
224.0.0.6
The “OSPF AllDRouters” address. Used to send OSPF
network segment
224.0.0.9
The RIP (“Routing Information Protocol”) Version 2 of the
224.0.0.10
The EIGRP group address. Used to send EIGRP routing
information to all EIGRP routers on a network segment.
224.0.0.13
PIM Version 2 (“Protocol Independent Multicast”)
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Figure 15: Multicast Address
the same network segment.
“AllSPFRouters” address. Used to send “Hello Packets”
routing information to “OSPF Designated Routers” on a
group address. Used to send routing information to all
RIPv2-compatible rout ers on a network segment.
Manual
Version 1.2.0
Page 67

WAGO ETHERNET Accessories 852 Enhanced Features 67
Table 19: IP Multicast Addresses
IP multicast address
Description
224.0.0.18
Virtual Router Redundancy Protocol
224.0.0.19 - 21
IS-IS over IP
224.0.0.22
IGMP Version 3 (“Internet Group Management Protocol”)
224.0.0.102
Hot Standby Router Protocol Version 2
224.0.0.251
Multicast DNS address
224.0.0.252
“Link-local Multicast Name Resolution”-address
224.0.1.1
“Network Time Protocol” address
224.0.1.39
“Cisco Auto-RP-Announce” address
224.0.1.40
“Cisco Auto-RP-Discovery” address
224.0.1.41
“H.323 Gatekeeper Discovery” address
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Manual
Version 1.2.0
Page 68

68 Enhanced Features WAGO ETHERNET Accessories 852
TPID
User Priority
CFI
VLAN ID
2 bytes
3 Bit
1 bits
12 bits
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.3 VLAN
A VLAN (“Virtual LAN”) is a group of hosts with a common set of requirements
that communicate as if they were attached to a broadcast domain, regardless of
their physical location. A VLAN has the same attributes as a physical LAN, but it
allows for end stations to be grouped together even if they are not located on the
same network switch. Networks can be reconfigured through software instead of
spatially offset devices.
VID (“VLAN-ID”) is the identification of a VLAN that is generally used by the
802.1Q standard. It has 12 bits and allows the identification of 4096 (2^12)
VLANs. Of the 4096 possible VIDs, VID 0 is used to identify “Priority Frames” and
value 4095 (FFF) is reserved, so the maximum possible VLAN configurations are
4094.
A “Tagged VLAN” uses an explicit tag (VLAN ID) in the MAC header to identify
the VLAN membership of a frame across “Bridges” - they are not confined to the
switch on which they were created. VLANs can be created statically (manually by
users) or dynamically via the GVRP (“GARP VLAN Registration Protocol”). The
VLAN ID associates a frame with a specific VLAN and provides the information
that switches need to process the frame across the network. A tagged frame is
four bytes longer than an untagged frame and contains two bytes of TPID (“Tag
Protocol Identifier”, residing within the type/length field of the “ETHERNET
Frame”) and two bytes of TCI (“Tag Control Information”, starts after the source
address field of the “ETHERNET Frame”).
The CFI (“Canonical Format Indicator”) is a single-bit flag, always set to zero for
ETHERNET switches. If a frame received at an ETHERNET port has a CFI of 1,
the frame should not be output to an untagged port. The remaining 12 bits define
the VLAN ID, giving a possible maximum number of 4096 VLANs. Note that user
priority and VLAN ID are independent of each other. A frame with VID (VLAN
Identifier) of null (0) is called a “Priority Frame”, i.e., only the priority level is
relevant and the default VID of the ingress port is used as the VID of the frame.
Of the 4096 possible VIDs, a VID of 0 is used to identify “Priority Frames” and
value 4095 (FFF) is reserved, so the maximum possible VLAN configurations are
4094.
Manual
Version 1.2.0
Page 69

WAGO ETHERNET Accessories 852 Enhanced Features 69
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
• Forwarded Tagged and Untagged Frames
Each port on the switch is capable of forwarding tagged or untagged frames. To
forward a frame from an 802.1Q VLAN-aware switch to an 802.1Q VLANunaware switch, the switch first decides where to forward the frame and then
strips off the VLAN tag. To forward a frame from an 802.1Q VLAN-unaware
switch to an 802.1Q VLAN-aware switch, the switch first decides where to
forward the frame and then inserts a VLAN tag reflecting the ingress port's
default VID. The default PVID is “VLAN 1” for all ports, but this can be changed.
A broadcast frame (or a multicast frame for a multicast group that is known by the
system) is duplicated only on ports that are subscribers of the VID (except the
ingress port itself), thus confining the broadcast to a specific domain.
• Port-Based 802.1Q VLAN
As a subscriber of a port-based VLAN, the port is assigned to a specific VLAN
independent of the user or system attached to the port. This means all users
attached to the port should be subscribers of the same VLAN. The network
administrator typically performs the VLAN assignment. The port configuration is
static and cannot be automatically changed to another VLAN without manual
reconfiguration.
As with other VLAN approaches, the packets forwarded using this method are
not transmitted to other VLAN domains or networks. After a port has been
assigned to a VLAN, the port cannot send to or receive from devices in another
VLAN without the intervention of a Layer 3 device.
The device that is attached to the port likely has no understanding that a VLAN
exists. The device simply knows that it is part of a subnet and that the device
should be able to talk to all other network subscribers by simply sending
information via the cable connection. The switch is responsible for identifying that
the information came from a specific VLAN and for ensuring that the information
gets to all other subscribers of the VLAN. The switch is also responsible for
ensuring that ports in a different VLAN do not receive the information.
This approach is quite simple, fast and easy to manage in that there are no
complex lookup tables required for VLAN segmentation. If the “Port-to-VLAN”
connection is designed with an application-specific integrated circu it (ASIC),
performance is very good. An ASIC allows “Port-to-VLAN” mapping at the
hardware level.
Manual
Version 1.2.0
Page 70

70 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.3.1 Port Isolation
“Port Isolation” is a port-based virtual LAN function. It partitions the switching
ports into virtual private domains designated on a per port basis. Data switching
outside of the switch's private domain is not allowed. VLAN tag information of the
packets is ignored.
This function can be used to configure one or more egress ports that allow t he
data received by the specific port to forward it. If the CPU port (port 0) is not an
egress port for a specific port, the host connected to the specific port cannot
manage the switch.
If you want to allow communication between two subscriber ports, you must
define the egress port for both ports. CPU refers to the switch management port.
By default, it forms a VLAN with all ETHERNET ports. If it does not form a VLAN
with a specific port, then the switch cannot be managed from that port.
Manual
Version 1.2.0
Page 71

WAGO ETHERNET Accessories 852 Enhanced Features 71
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.3.2 GARP/GVRP
GARP (“Generic Attribute Registration Protocol“) and GVRP (“GARP VLAN
Registration Protocol“ or “Generic VLAN Registration Protocol”) are industry-
standard protocols described in IEEE 802.1p. GVRP is a GARP application that
provides 802.1Q-compliant “VLAN Pruning” and dynamic VLAN creation on
“802.1Q Trunk Ports”.
With GVRP, the switch can exchange VLAN configuration information with other
GVRP switches, prune unnecessary broadcast and unknown unicast traffic, and
dynamically create and manage VLANs on switches that are connected through
“802.1Q Trunk Ports”.
GVRP makes use of GID (“Group Identification”) and GIP, which provide the
common “State Machine Descriptions” and the common information propagation
mechanisms defined for use in GARP-based applications. GVRP runs only on
“802.1Q Trunk Links”. GVRP prunes “Trunk Links” so that only active VLANs are
transmitted across trunk connections. GVRP expects to hear join messages from
the switches before it will add a VLAN to the trunk. GVRP updates and hold
timers can be altered. GVRP ports run in various modes to control how they will
prune VLANs. GVRP can be configured to dynamically add and manage VLANS
in the VLAN database for “Trunking” purposes.
In other words, GVRP allows the propagation of VLAN information from device to
device. With GVRP, a single switch is manually configured for all VLANs required
for the network and all other switches on the network learn detect the VLANs
dynamically. End nodes can be plugged into any switch and connected to the
required VLAN. For end nodes to make use of GVRP, they need GVRP-aware
network interface cards (NICs). The GVRP-aware NIC is configured with the
desired VLAN or VLANs, then connected to a GVRP-enabled switch. The NIC
communicates with the switch once connectivity is established between the NIC
and switch.
Registration Mode:
• Normal
The “normal” registration mode allows dynamic creation (if dynamic VLAN
creation is enabled), registration and deregistration of VLANs on the trunk
port. “Normal” mode is the default setting.
• Forbidden
The “forbidden” registration mode deregisters all VLANs (except VLAN 1)
and prevents further creation or registration of VLANs on the trunk port.
• Fixed
The “fixed” registration mode allows manual creation and registration of
VLANs, prevents VLAN deregistration and registers all known VLANs on
other ports on the trunk port. (Same applies to the static VLAN)
Manual
Version 1.2.0
Page 72

72 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
GVRP Timer:
• Join Timer
The “Join Timer” specifies the maximum time in milliseconds that interface
waits before sending VLAN messages.
• Leave Timer
The “Leave Timer” specifies the number maximum time in milliseconds an
interface waits after receiving a “Leave Message” before the interface
leaves the VLAN specified in the message.
• Leaveall Timer
The “Leaveall Timer” specifies the interval in milliseconds at which
“Leaveall Messages” are sent on interfaces. “Leaveall Messages” help to
maintain current GVRP VLAN subscriber information in the network.
Manual
Version 1.2.0
Page 73

WAGO ETHERNET Accessories 852 Enhanced Features 73
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.3.3 Q-in-Q
“Q-in-Q Tunneling” is also known as “VLAN Stacking”. Both of them use 802.1Q
double tagging technology. Q-in-Q is used by ISPs (Internet Service Providers)
that need TLS (“Transparent LAN Services”) and that have their own set of
VLAN, independent of customer VLANs. Normally, each service provider VLAN
interconnects a group of sites belonging to a customer. However, a service
provider VLAN could also be shared by a set of customers sharing the same end
points and QoS requirements of the VLAN. “Double Tagging” is considered to be
a relatively simpler way of implementing a transparent LAN. This is accomplished
by encapsulating “ETHERNET Frames”. A second or outer VLAN tag is inserted
in “ETHERNET Frames” sent over the ingress PE (“Provider Edge”). This VLAN
tag corresponds to the VLAN of the service provider. If the frame reaches the
destination PE, the service provider VLAN opens. The destination address of the
encapsulated frame and VLAN ID are used for other L2 decisions, similar to an
“ETHERNET Frame” that arrives from a physical ETHERNET port. The service
provider VLAN tag determines the membership in the VPLS (“Virtual Private LAN
Service”). Double tagging aggregates multiple VLANs within another VLAN and
allows a private dedicated ETHERNET connection between customers who want
to reach their subnet transparently across multiple networks. Service providers
can create their own VLANs without coming in contact with customer VLANs via
“Double Tagging”. This allows customers to connect to ISPs and ASPs
(“Application Service Providers”).
The ports that are connected to the service provider VLANs are called “Tunnel
Ports” and the ports that are connected to the customer VLANs are called
“Access Ports”. If a port is configured as “Tunnel Port”, all outgoing packets on
this port are transmitted with an SPVLAN tag (SPVID and 1p priority) tag. The
incoming packet can have two tags (SPVLAN + CVLAN), one tag (SPVLAN or
CVLAN), or no tag. In all cases, the packet is sent out with a SPVLAN tag. If a
port is configured as an “Access Port”, the incoming traffic can have only a
CVLAN tag (CVID and 1p priority) or no tag. Hence, all the packets that are being
sent from “Access Ports” are untagged or single tagged (CVLAN). If a port is
configured as a normal port, it ignores “Double Tagging Frames”.
Manual
Version 1.2.0
Page 74

74 Enhanced Features WAGO ETHERNET Accessories 852
TPID
Priority
VID
Untagged frame
DA
Len or
Etype
Data
FCS
Single-tagged
frame
DA
SA
TPID
P
VID
Len or
Etype
Data
FCS
Double-tagged
DA
SA
Tunnel
P
VID
TPID
P
VID
Len or
Data
FCS
DA
Destination Address
SA
Source Address
Tunnel TPID
“Tag Protocol Identifier” added to a “Tunnel Port”
VID
VLAN ID
Len or Etype
Length or ETHERNET frame type
Data
Frame data
FCS
Frame Check Sequence
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Double Tagging Format
A VLAN tag (service provider “VLAN Stacking” or customer IEEE 802.1Q)
consists of the following three fields:
TPID
TPID (“Tag Protocol Identifier”) is a standard ETHERNET code identifying the
frame and indicating whether the frame contains IEEE 802.1Q tag information.
The value of this field is 0x8100 as described in IEEE 802.1Q. Other providers
may use a different value, such as 0x9100.
“Tunnel TPID” is the “VLAN Stacking” tag type the switch adds to the outgoing
frames sent through a “Tunnel Port” of the service provider's PE devices
Priority
Priority refers to the IEEE 802.1p standard that allows the service provider to
prioritize traffic based on the class of service (CoS) the customer has paid for. "0"
is the lowest priority level and "7" is the highest.
VID
VID (“VLAN ID”). SP VID is the VID for the second or outer VLAN tag (of the
service provider). CVID is the VID for the first or inner VLAN tag (of the
customer).
The fr ame form ats for an untagged “ETHERNET Fram e” a single-tagged 802.1Q
frame (customer) and a double-tagged 802.1Q frame (service provider) are
shown as follows.
frame
TPID
Etype
Manual
Version 1.2.0
Page 75

WAGO ETHERNET Accessories 852 Enhanced Features 75
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
VLAN Stacking Port Roles
For “VLAN Stacking”, each port can have one of three “roles”: Normal, “Access
Port” or “Tunnel Port”.
• Select “normal” for normal (no “VLAN Stacking”) IEEE 802.1Q frame
switching.
• Select “Access Port” for ingress ports on PE devices of the service
provider. The incoming frame is treated as "untagged", so a second VLAN
tag (outer VLAN tag) can be added.
• Select “Tunnel Port” for egress ports in the PE range of the provider's
network. All VLANs belonging to a customer can be aggregated into a
single service provider's VLAN (using the outer VLAN tag defined by SP
VID).
Q-in-Q Configuration
For the double-tagged frames to switch correctly, users have to configure a
service provider’s VLAN (SPVLAN) on the Q-in-Q switch. Then, the doubletagged frames can be switched according to the SP VID. The SPVLAN should
include all related “Tunnels” and “Access Ports”. In addition, the “Tunnel Ports”
must be configured as tagged ports and the “Access Ports” as untagged ports.
7.2.3.3.1 Port-Based Q-in-Q
Q-in-Q encapsulation can be used to convert a single-tagged 802.1Q packet into
a double-tagged Q-in-Q packet. The Q-in-Q encapsulation can be based on port
or traffic. Port-based Q-in-Q can be used to encapsulate all incoming packets to
a port with the same SPVID outer tag. This mode is less flexible.
In the following example figure, both X and Y are Service Provider’s Network
(SPN) customers with VPN tunnels between their head offices and branch offices
respectively. Both have an identical VLAN tag for their VLAN group. The service
provider can separate these two VLANs within its network by adding tag 100 to
distinguish customer X and tag 200 to distinguish customer Y at PE device A and
then stripping those tags at PE device B as the data frames leave the network.
Manual
Version 1.2.0
Page 76

76 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Figure 16: Port-Based Q-in-Q
This example shows how to configure switch A with port 1 on the switch to tag
incoming frames with the service provider’s VID of 200 (ports are connected to
customer X network) and configure port 7 to the service provider’s VID of 100
(ports are connected to customer Y network). This example also shows how t o
set the priority for port 1 to 3 and port 7 to 4.
7.2.3.3.2 Selective Q-in-Q
The traffic-based Q-in-Q is also called selective Q-in-Q. Selective Q-in-Q allows
the switch to add different outer VLAN tags to the incoming frames received on
one port according to their inner VLAN tags. In Selective Q-in-Q mode, the switch
performs traffic classifies the incoming traffic on a port based on the VLAN ID.
When a user uses different VLAN IDs for different services, traffic can be
classified according to the VLAN ID. Example: VLAN ID 100 for surfing on the
Internet on a PC, VLAN ID 200 for IPTV and VLAN ID 300 for VIP customers.
After receiving user data, the switch labels the traffic for surfing on the Internet on
a PC with 500 as a SPVID outer tag, IPTV with 600 and VIP customers with 700.
This following example shows how to configure port 3 on the switch to tag
incoming frames with the different service provider’s VID and priority.
Figure 17: Configuration Example
Manual
Version 1.2.0
Page 77

WAGO ETHERNET Accessories 852 Enhanced Features 77
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.4 DHCP Rela y
Because the “DHCPDISCOVER” message is a broadcast message and
broadcasts only cross other segments when they are explicitly routed, you might
have to configure a “DHCP Relay Agent” on the router interface so that all
“DHCPDISCOVER” messages can be forwarded to your DHCP server.
Alternatively, you can configure the router to forward DHCP messages and
BOOTP message. In a routed network, you would need “DHCP Relay Agents” if
you plan to implement only one DHCP server.
The “DHCP Relay” that is either a host or an IP router waits for DHCP client
messages being broadcast on a subnet and then forwards those DHCP
messages directly to a configured DHCP server. The DHCP server sends DHCP
response messages directly back to the “DHCP Relay Agent”, which then
forwards them to the DHCP client. The DHCP administrator uses “DHCP Relay
Agents” to centralize DHCP servers, avoiding the need for a DHCP server on
each subnet.
Most of the time in small networks, DHCP uses broadcasts, but there are some
circumstances where unicast addresses are used. This can be the case when
networks have a single DHCP server that provides IP addresses for multiple
subnets. A router for such a subnet receives the DHCP broadcasts, converts
them to unicast (with a MAC/IP destination address of the configured DHCP
server, MAC/IP source address of the router itself). The GIADDR field on the
main DHCP page contains the IP address of the interface on the router it
received the DHCP request on. The DHCP server uses the GIADDR field to
identify the subnet the device and selects an IP address from the correct pool.
The DHCP server then sends the “DHCP OFFER” back to the router via unicast,
which then converts it back to a broadcast and out to the correct subnet
containing the device requesting an address.
Configurations
A user can enable/disable the “DHCP Relay” on the switch. It can also be
enabled/disabled on a specific VLAN. If the “DHCP Relay” on the swit c h is
disabled, it is disabled on all VLANs, even if enabled for individual VLANs.
Applications
• Application 1 (via a router)
DHCP client 1 and DHCP client 2 are in different IP segments. However,
they receive IP address from the same DHCP server.
Manual
Version 1.2.0
Page 78

78 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Figure 18: Application 1 (via a Router)
• Application 2 (local in different VLANs)
DHCP client 1 and DHCP client 2 ar e in different VLANs. However, they
receive IP address from the same DHCP server.
Figure 19: Application 2 (Local in Different VLANs)
VLAN 1: Port 1, 2 (Management VLAN)
VLAN 2: Port 3, 4
VLAN 3: Port 5, 6
VLAN 4: Port 7, 8
DHCP Server -> Port 1.
DHCP Client -> Port 2, 3, 4, 5, 6, 7, 8.
Result: Hosts connected to port 2, 3, 4, 5, 6, 7 and 8 receive an IP from
the DHCP server .
DHCP Server Connection
The DHCP server must be connected to the subscriber ports of the management
VLAN.
The “DHCP Relay” in the management VLAN must be enabled.
Manual
Version 1.2.0
Page 79

WAGO ETHERNET Accessories 852 Enhanced Features 79
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.5 DHCP Rela y Option 82
“DHCP Option 82” (“DHCP Relay Agent Information Option”). Option 82 was
designed to allow a “DHCP Relay Agent” to insert circuit-specific information into
a request that is being forwarded to a DHCP server. Specifically, the option
works by setting two sub-options: “Circuit ID” and “Remote ID”.
“DHCP Option 82” operates on the basis of “DHCP Snooping” or/and “DHCP
Relay”.
The switch monitors the DHCP packets and append some information under
“DHCPDISCOVER” and “DHCPREQ UEST” packets. The switch delet es “DHCP
Option 82” from the “DHCPOFFER” and “DHCPACK” packets. The DHCP server
then assigns an IP domain to the client based on this information.
The maximum length of the information is 32 characters.
In residential, metropolitan ETHERNET-access environments, DHCP can
centrally manage the IP address assignments for a large number of subscribers.
If the “DHCP Option 82” function is enabled on the switch, a subscriber device is
identified by the switch port through which it connects to the network (in addition
to its MAC address). Multiple hosts on the subscriber LAN can be connected to
the same port on the switch and are uniquely identified.
If you enable “DHCP Snooping Information Option 82” on the switch, the
sequence of events is:
• The host (DHCP Client) generates a DCHP request and broadcasts it on
the network.
• If the switch receives the DHCP request, it adds the “Option 82” information
in the packet. The information contains the switch MAC address (the
“Remote ID” sub-option), “Port Identifier” and “VLAN-Mod-PORT”, from
which the packet is received (the “Circuit ID” sub-option).
• If the IP address of the “Relay Agent” has been configured, the switch adds
the IP address in the DHCP packet.
• The switch forwards the DHCP request that includes the Option 82 field to
the DHCP server.
• The DHCP server receives the packet. If the server is Option 82 capable, it
can use the “Remote ID”, “Circuit ID” or both to assign IP addresses and
implement policies, such as restricting the number of IP addresses that can
be assigned to a single “Remote ID” or “Circuit ID”. The DHCP server then
echoes the Option 82 field in the DHCP reply.
• The DHCP server forwards the reply to the switch as a unicast if the
request was relayed to the server by the switch. If the client and server are
on the same subnet, the server broadcasts the reply. The switch verifies
the Option 82 data originally entered by checking the “Remote ID” and
“Circuit ID” fields. The switch deletes the Option 82 field and forwards the
packet to the switch port that connects to the DHCP client that sent the
DHCP request.
Manual
Version 1.2.0
Page 80

80 Enhanced Features WAGO ETHERNET Accessories 852
Table 20: Option Frame Format
Code
Len
Agent Information Field
82
N
i1
i2
i3
i4 … iN
Table 21: Option Frame Format
Sub-Option
Len
Sub-Option Value
1
N
s1
s2
s3
s4 … sN
Table 22: Frame Format of the “Circuit ID” Sub-Option
Sub-Option
Length
“Circuit ID”
Length
VLAN
Module
Port
1 6 0 4 2 1 1
Table 23: Frame Format of the “Remote ID” Sub-Option
Sub-Option
Type
Length
“Circuit ID”
Type
Length
MAC address
2 8 0
6
6
Table 24: Format of the “Circuit ID” Sub-Option
Code
Len
Sub-Option
Type
Length
Slot ID
Port ID
VLAN
ID
Information
0x52
0x0c
0x01
0x0a
0x01
0x01
0x0002
justin
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Option Frame Format
The “Agent Information Field” consists of a sequence of SubOpt/Length/Value
tuples for each sub-option, encoded in the following manner:
DHCP Agent Sub-O pt ion De s c r ipt ion
Sub-Option Code
-------------------------- ------------------------------------ 1 “Agent Circuit ID” sub-option
2 “Agent Remote ID” sub-option
Type
Type
Manual
Version 1.2.0
Page 81

WAGO ETHERNET Accessories 852 Enhanced Features 81
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.6 Dual Ring
The “Dual Ring” function can be used to connect 2 neighboring rings to each
other on a switch without needing additional ports or cables. This configuration
reduces the total number of required ports and wiring costs are saved because
no additional wiring is required.
Figure 20: Dual Ring Switch ABC
Figure 21: Dual Ring Switch AB
Manual
Version 1.2.0
Page 82

82 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.7 ERPS
The ERPS (“ETHERNET Ring Protection Switching”) function implements a
protection switching mechanism for ETHERNET layer ring topologies according
to ITU-T standard G.8032. The ERP (“ETHERNET Ring Protection”) protects
ETHERNET traffic in a ring topology and ensures that no loops are within the ring
in the ETHERNET later. Looping is prevented by blocking traffic on either a
predetermined link or a failed link.
The ETHERNET ring protection functionality includes the following:
• Loop avoidance
• Use of learning, forwarding and filter database (FDB) mechanisms
Loop avoidance in an ETHERNET ring is achieved by guaranteeing that, at any
time, traffic may flow on all but one of the ring links. This particular ring link
serves as a reserve connection and is called an RPL (“Ring Protection Link”). In
normal operation, it is blocked and not used for service traffic. A specific
ETHERNET ring node, the “RPL Owner” node, is responsible for blocking traffic
at one end of the RPL. Under an ETHERNET ring failure condition, the “RPL
Owner” node is responsible for unblocking its end of the RPL, unless the RPL
has failed, allowing the RPL to be used for traffic. The ETHERNET ring node
adjacent to the RPL, the “RPL Neighbor” node, may also participate in blocking
or unblocking its end of the RPL.
The ETHERNET rings can support a multi-ring/ladder network that consists of
conjoined ETHERNET rings by one or more interconnection points. The
protection switching mechanisms and protocol defined in this recommendation
can be used for a multi-ring/ladder network under the following conditions:
• R-APS channels are not shared across ETHERNET ring connections;
• On each ring port, each traffic channel and each R-APS channel is
controlled (e.g., for blocking or flushing) by the ETHERNET ring protection
control process (“ERP Control Process”) of only one ETHERNET ring.
• Each main ring or sub-ring has its own RPL.
In an ETHERNET ring without congestion with all ETHERNET ring nodes in the
idle state (i.e., no detected failure, no active automatic or external command and
receiving only R-APS (NR, RB) messages) with less than 1,200 km of ring fiber
circumference and fewer than 16 ETHERNET ring nodes, the switch completion
time (transfer time as defined in [ITU-T G.808.1]) for a failure on a ring link shall
be less than 50 ms.
The ring protection architecture relies on the existence of an APS protocol to
coordinate ring protection actions in an ETHERNET ring.
The switch supports up to six rings.
Manual
Version 1.2.0
Page 83

WAGO ETHERNET Accessories 852 Enhanced Features 83
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Guard Timer
All ring subscribers use a “Guard Timer”. It prevents the possibility of forming a
closed loop and prevents ring subscribers from using outdated R-APS messages.
The “Guard Timer” is enabled if a ring subscriber received information on a local
switching request, such as after SF (“Switch Fail”), MS (“Manual Switch”) or FS
(“Forced Switch”) commands. When the timer expires, the ring subscriber begins
executing actions it received from the R-APS. This timer cannot be manually
stopped.
WTR Timer
The “WTR Timer” (“Wait To Restore Timer”) is used by the “RPL Owner”. The
“WTR Timer” applies to the reset mode to prevent frequent triggering of the
protection switching due to port flapping or intermittent signal failure defects.
When the timer expires, the “RPL Owner” sends an R-APS (NR, RB) message
through the ri ng.
WTB Timer
The “WTB Timer” (“Wait To Block Timer”) is enabled on the “RPL Owner”. The
“RPL Owner” uses “WTB Timers” before initiating an RPL block and then
reverting to the idle state after operator-initiated commands, such as for FS or
MS conditions, are entered. Because multiple FS commands are allowed to coexist in a ring, the “WTB Timer” ensures that clearing a single FS command does
not trigger the re-blocking of the RPL. The “WTB Timer” should be 5 seconds
longer than the “Guard Timer”, enough time to allow a reporting ring subscriber to
receive two R-APS messages and to allow the ring to identify the latent state.
When clearing a MS command, the “WTB Timer” prevents the formation of a
closed loop because the “RPL Owner” node does not respond to an outdated
remote MS request during the recovery process.
Hold-off Timer
Each ring subscriber uses a “Hold-off Timer” to delay reporting a port failure.
When the timer expires, the ring subscriber checks the port status. If the problem
persists, a failure is reported. If the issue does not persist, nothing is reported.
ERPS revertive and non-revertive switching
ERPS uses revertive and non-revertive operation. In revertive operation after the
conditions causing a switch have cleared, the traffic channel is restored to the
working transport entity, i.e., blocked on the RPL. Once an error condition is
cleared, the traffic channel is switched back only after expiration of a “WTR
Timer” to prevent protecting states from toggling due to intermittent errors.
without revertive operation, the traffic channel continues to use RPL after a
switch condition is cleared if the RPL has not failed.
Manual
Version 1.2.0
Page 84

84 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Control VLAN
The “Control VLAN” is a domain in which only ERPS control packets are
transmitted. Because no other packets are transmitted in the VLAN, there are no
delays for the ERPS. Therefore, when configuring a control VLAN for a ring,
make sure it is a new VLAN. The ERPS creates the control VLAN and its
subscriber ports automatically. A subscriber port should have a right and left port
only.
In ERPS, control packets and data packets are separated in different VLANs.
The control packets are transmitted in a control VLAN.
Instance
For ERPS Version 2, an instance is a profile that specifies a control VLAN and
one or more data VLANS for the ERPS. The control and data packets in ERPS
are separated in different VLANs. The control packets are transmitted in the
control VLAN and the data packets in one or more data VLANs. In this way, a
user can easily assign an instance to an ERPS ring.
If a port is blocked by ERPS in ERPS Version 1, all packets are blocked.
If a port is blocked by an ERPS ring in ERPS Version 2, only the packets
belonging to the VLANs in this instance are blocked.
Control VLAN and Instance
In CLI or Web configurations, there are settings for the control VLAN or instance.
If the control VLAN is configured for a ring and an instance should be configured
for the ring, the control VLAN must be the same for the instance as that of the
ring. Otherwise, an error is displayed. If you still want to use this instance, you
can first change the control VLAN so that it is the same as that of the instance.
You can the configure the instance.
Manual
Version 1.2.0
Page 85

WAGO ETHERNET Accessories 852 Enhanced Features 85
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.8 Dual Homing
“Dual Homing” is a network topology in which a device is connected to the
network by way of two independent access points (“Points of Attachment”). One
access point establishes the primary connection, and the other is a reserve if the
primary connection fails.
Figure 22: Dual Homing
Primary and secondary connections, for example, can be connected to the
Internet in different ways. The primary connection could be connected to a
physical network and the secondary to a wireless network. If the “Dual Homing”
function is enabled, a device connects via the primary connection be default,
while the secondary connection remains suspended. If the port or all ports of the
primary connection fail, the devices switches to the secondary connection. If the
secondary connection also fails, the device remains inactive. The secondary
connection only works if the primary connection is interrupted.
Manual
Version 1.2.0
Page 86

86 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.9 Link Aggregation
7.2.9.1 Static Trunk
“Ling Aggregation” (also called “Trunking”), parallel link bundling) is the grouping
of physical ports into one logical ling with higher capacity. When bundling ports, it
can be more cost effective to use multiple lower-speed links than to underutilize a
high-speed, but expensive “Port Link”.
However, the more ports you aggregate, the fewer available ports you have. A
“Trunk Group” is one logical link containing multiple ports. The switch supports
both static and dynamic “Link Aggregation”.
“Link Aggregation”
In a well-planned network, only static “Link Aggregation” is recommended. This
ensures increased network stability and control over “Trunk Groups” on your
switch.
7.2.9.2 LACP
The switch supports static and dynamic (LACP) “Port Trunking” according to
IEEE 802.3ad. The IEEE 802.3ad standard describes LACP (“Link Aggregation
Control Protocol”) for dynamic creation and management of “Trunk Groups”.
When you enable “LACP Link Aggregation” on a port, the port can automatically
negotiate with the ports at the remote end of a link to establish “Trunk Groups”.
LACP also allows port redundancy, i.e., if an operational port fails, then one of
the “standby” ports becomes operational without user intervention
The following should be noted:
• All ports must be connected peer-to-peer to the same ETHERNET switch
and configured for “LACP Trunking”.
• LACP only works on full-duplex links.
• All ports in the same “Trunk Group” must have the same media type,
speed, duplex mode and settings for “Flow Control”.
• Configure the “Trunk Groups” or LACPs before you connect to the
ETHERNET switch to prevent looping in the network topology.
Manual
Version 1.2.0
Page 87

WAGO ETHERNET Accessories 852 Enhanced Features 87
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
System Priority
LACP system priority is used to determine membership in an LAG (“Link
Aggregation Group”) and identifies the device for other switches during LAG
negotiations.
The switch with the lowest system priority (and lowest port number if system
priority is the same) becomes the LACP “Server”. The server controls the
operation of the LACP settings. The smaller the number, the higher the priority
level.
System ID
The “LACP System ID” is a combination of the LACP system priority value and
the MAC address of the router.
Administrative Key
The “Administrative Key” defines the ability of a port to aggregate with other
ports. This ability is determined by the following factors:
• The physical properties of the port, e.g., data rate, duplex capability and
peer-to-peer or shared transmission medium.
• The configuration restrictions that you establish.
Port Prio rity
Port priority determines which ports should go into standby mode if there is a
hardware limitation that prevents all compatible ports from bundling.
7.2.10 LLDP
The LLDP (“Link Layer Discovery Protocol”) described in this standard allows
stations connected to a LAN acc. IEEE 802® to send information to other stations
connected to the same LAN. The information includes essential system functions,
including the management address or addresses of an entity or entities that
provide management of these functions, as well as identification of the station's
access point to the IEEE802 LAN required by the management entity or entities.
The information distributed via this protocol is stored by the recipients in a normal
MIB (“Management Information Base”). That allows an NMS (“Network
Management System”) to access the information using a management protocol
such as SNTP (“Simple Network Management Protocol”).
Manual
Version 1.2.0
Page 88

88 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.11 Loop Detection
“Loop Detection” handles problems with loops in the network periphery. These
problems can occur if a port is connected to a switch that is in a loop st ate. A
loop state occurs as a result of user error. It happens when two ports on a switch
are connected with the same cable. When a switch in loop state sends out
broadcast messages, the messages loop back to the switch and are re-broadcast
again and again causing a “Broadcast Storm”.
The “Loop Detection” function sends probe packets periodically to detect if the
port is connected to a network in loop state. The switch shuts down a por t if the
switch detects that probe packets loop back to the same port.
Loop Recovery
When “Loop Detection” is enabled, the switch sends a probe packet every two
seconds and waits to receive the packet. If it receives the packet at the same
port, the switch disables the port. After the time period (“Recovery Time”), the
switch enables the port and executes “Loop Detection” again.
The switch generates a “Syslog” (system log), internal log messages and “SNMP
Traps” if it disables a port after “Loop Detection”.
Manual
Version 1.2.0
Page 89

WAGO ETHERNET Accessories 852 Enhanced Features 89
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.12 Jet Ring
Setting up the Jet Ring function (redundant connection) in a network better
protects critical connections against errors and network loops. In addition,
network downtime is reduced to less than 300 ms.
The Jet Ring function can be used to set up a secondary path to the network. A
data transmission safety route is then provided in case there is an abrupt
interruption in a connection. This function is extremely important for industrial
applications because connection errors without safeguards for network downtime
can last several minutes and result in heavy losses.
The Jet Ring protocol is used to optimize secondary communication links and to
ensure very short connection recovery time. The Jet Ring function is used to
automatically identify a switch as the network “Master” and to automatically block
connections. This prevents packets from being broadcast to all secondary loop
segments of a network. If a ring segment is separated from the rest of the
network due to a connection error, the Jet Ring protocol automatically adjust the
ring again to restore the connection between the part of the network that was
separated with the rest of the network.
Step 1
The Jet Ring function in the graphic below is applicable to connecting industrial
managed switches.
Figure 23: Jet Ring
Step 2
The Jet Ring function is used to automatically select the Arbiter switch. The
network then ready for operation.
Manual
Version 1.2.0
Page 90

90 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.2.13 STP
The (R)STP (“(Rapid) Spanning Tree Protocol)”) can detect and stop network
loops, as well as provide “Backup Links” between switches, bridges or routers. It
allows a switch to interact with other (R)STP-compliant switches in the network to
ensure that only one path exists between any two stations on the network.
The switch supports both STP and RSTP as defined in the following standards:
• IEEE 802.1D Spanning Tree Protocol
• IEEE 802.1w Rapid Spanning Tree Protocol
The switch uses IEEE 802.1w RSTP that allows faster convergence of the
“Spanning Tree” than STP (the switch is also backwards compatible with STPonly aware bridges). In RSTP, topology change information is directly propagated
throughout the network from the device that generates the topology change. In
STP, there are longer delays because the device that causes a topology change
first notifies the “Root Bridge” and then the network. Both RSTP and STP remove
unwanted learned addresses from the filtering database.
• STP has the port states “Blocking”, “Listening”, “Learning” and
“Forwarding”.
• RSTP has the port states in RSTP “Discarding”, “Learning” and
“Forwarding”.
STP Switch Port States
• “Blocking”
If a port causes a “Switching Loop” (looping connection between two ports),
user data can no longer be sent or received. However, the port can go into
the “Forwarding” state if the other active connections fail and the “Spanning
Tree” algorithm determines that the port may transition to that state. BPDU
data is still received and sent in the “Blocking” state.
• “Listening”
The switch processes BPDUs and waits for possible new information that
would cause it to return to the “Blocking” state.
• “Learning”
Even if the port does not yet forward any frames (packets), it can learn
source addresses from frames received and add them to the filter database
(“Switching Database”).
Manual
Version 1.2.0
Page 91

WAGO ETHERNET Accessories 852 Enhanced Features 91
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
• “Forwarding”
The port is in normal operating mode and receives and sends data. STP
still monitors incoming BPDUs that would indicate that the port should
return to the “Blocking” state to prevent a loop.
• “Disabled”
It is not strictly part of the STP because a network administrator can
manually disable a port.
RSTP Bridge Port Roles
• “Root”
The “Root Port” is a forwarding port that can best transmit data from the
“Non-Root Bridge” to the “Root Bridge”.
• “Designated”
This is a forwarding port for every LAN segment.
• “Alternate”
This port represents an alternate path to the “Root Bridge”. However, the
path is different than the “Root Port”.
• “Backup”
This port is used as a backup/redundant path to a segment to which
another “Bridge Port” is already connected.
• “Disabled”
This is not actually part of STP because a network administrator can
manually disable a port.
STP/RSTP
In this document, “STP” refers to both STP and RSTP.
STP Terminology
Root Bridge
The “Root Bridge” is the “Base” of the spanning tree.
Path Cost
The path costs are the costs for transmitting a frame through the port in the LAN.
This value should be adjusted to the transmission speed.
The valid range is 1 to 200000000. A path with higher costs is more likely to be
blocked by SSTP if a network look is detected.
- “Path Cost Short” is the original size with a 16-bit value.
Only speeds up to 10 GBit can be considered.
- “Path Cost Long” stands for a 32-bit value.
Speeds up to 10 TBit are supported.
Manual
Version 1.2.0
Page 92

92 Enhanced Features WAGO ETHERNET Accessories 852
Table 25: STP Path Costs
Transmission Speed
Recommended Value
Recommended Range
Permissible Range
4 Mbps
250
100 … 1000
1 … 65535
10 Mbps
100
50 … 600
1 … 65535
16 Mbps
62
40 … 400
1 … 65535
100 Mbps
19
10 … 60
1 … 65535
1 Gbps
4
3 … 10
1 … 65535
10 Gbps
2
1 … 5
1 … 65535
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
• Each “Bridge” communicates with the “Root Bridge” via the “Root Port”. The
“Root Port” is the port on the switch with the lowest path costs to the “Root
Bridge” (the “Root Path Cost”). If there is no “Root Port”, then the switch
becomes the “Root Bridge” for the “Spanning Tree” network
• A “Designated Bridge” is selected for each LAN segment. This bridge has
the lowest cost to the “Root Bridge” among the bridges connected to the
LAN.
Forward Time (Forward Delay)
The “Forward Time” is the maximum time (in seconds) that the switch wats
before it changes states. This delay is required because every switch must first
receive information on topology changes before it forwards frames. In addition,
each port needs time to receive information on conflicts that would make it return
to the blocking state. Otherwise, temporary data loops might result. The valid
range is 4 to 30 seconds.
Max Age
The “Max Age” is the maximum time (in seconds) that the switch can wait without
receiving a BPDU (“Bridge Protocol Data Unit”, configuration me ssage) before
attempting to reconfigure. All switch ports (except for “Designated Ports”) receive
BPDUs at regular intervals. Each port that ages out STP information (from the
last BPDU) becomes the “Designated Port” for the attached LAN. If it is a “Root
Port”, a new “Root Port” is selected from among the switch ports attached to the
network.
Hello Time
The “Hello Time” is the time interval in seconds between configuration messages
(BDPU “Bridge Protocol Data Unit”) sent from the root switch.
Manual
Version 1.2.0
Page 93

WAGO ETHERNET Accessories 852 Enhanced Features 93
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
STP
After a bridge determines the lowest cost “Spanning Tree” with STP, it enables
the “Root Port” and “Designated Ports” for connected LANs, and disables all
other ports that participate in STP. Network packets are therefore only forwarded
between enabled ports, eliminating any possible network loops.
STP-aware switches exchange BPDUs periodically. If the topology changes in a
LAN coupled via bridge, a new tree is spanned. Once a stable network topology
has been established, all bridges listen for “Hello BPDUs” transmitted from the
“Root Bridge”. If a bridge does not get a “Hello BPDU” after a predefined interval
(“Max Age”), the bridge assumes that the link to the “Root Bridge” is down. This
bridge then initiates negotiations with other bridges to reconfigure the network to
re-establish a valid network topology.
Edge Port
“Edge Ports” are attached to a LAN that has no other bridges attached. These
ports can transition directly to the “Forwarding” state. RSTP still continues to
monitor the port for BPDUs in case a bridge is connected. RSTP can also be
configured to automatically detect “Edge Ports”. As soon as the bridge detects a
BPDU coming to an “Edge Port”, the port loses its status as an “Edge Port”.
Forward Delay
The “Forward Delay” is the maximum time (in seconds) that the root devices
waits before changing states (e.g., from “Listening” to “Learning” to “Forwarding”).
The valid range is from 4 to 30 seconds.
Transmission Limit
The “Transmission Limit” is used to configure the minimum interval between the
transmission of consecutive RSTP BPDUs. This function can only be enabled in
RSTP mode. The valid range is from 1 to 10 seconds.
Bridge Priority
“Bridge Priority” is used in selecting the root switch, root port and “Designated
Port”. The switch with the highest priority becomes the STA root switch. If all
switches have the same priority, however, the switch with the lowest MAC
address becomes the root switch.
Manual
Version 1.2.0
Page 94

94 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
Port Prio rity
The port priority is configured on the switch. A low numeric value indicates a high
priority. A port with lower priority is more likely to be blocked by STP if a network
loop is detected. The valid range is from 0 to 240.
BPDU Guard
This setting is configured individual for each port. If the port is enabled in “BDU
Guard” and receives a BPDU, the port is switched to the “Disabled” state to
prevent a faulty environment. The user must manually enable the port.
BPDU Filter
This function is used to set up a filter for sending or receiving BPDUs on a switch
port. If the port receives BPDUs, the BPDUs are dropped. If both of the “BPDU
Filter” and “BPDU Guard” are enabled, the “BPDU Filter” has the higher priority.
BPDU Filter and BPDU Guard
If both of the “BPDU Filter” and “BPDU Guard” are enabled, the “BPDU Filter”
has the higher priority.
Root Guard
The “Root Guard” function forces an interface to become a “Designated Port” to
prevent neighboring switches from becoming a root switch. This function provides
a way to specify the selection of a “Root Bridge” in a network. It prevents a
“Designated Port” from becoming the “Root Port”. If a port with the “Root Guard”
function receives a superior BPDU, the port moves to a root-inconsistent state
(effectively equal to the “Listening” state) to maintain the status of the current
“Root Bridge”. The port can be moved to the “Forwarding” state if no superior
BPDU received over the period of three “Hello Times”.
Manual
Version 1.2.0
Page 95

WAGO ETHERNET Accessories 852 Enhanced Features 95
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
MSTP
The MSTP (“Multiple Spanning Tree Protocol”) is an RSTP extension. It allows
different spanning tree instances in conjunction with VLANs (“Virtual Local Area
Networks”).
For a VLAN or group of VLANs, STP instances can be created independent ly
that user their own different spanning trees within a LAN.
With the MSTP approach, a root bridge and the lowest path costs between the
root bridge and the root ports offered of the individual bridges are determined.
The root bridge sends Bridge Protocol Data Units (BPDU) to all bridges and
determines the network configuration from the configuration data contained in the
BPDU data packets.
7.2.14 Xpress Ring
The Xpress Ring is a fast-acting, self-healing ring recovery technology that
enables networks to recover from link failure within 50 ms.
Fast Link Recovery and Ring Redundancy are important functions for increasing
the reliability of non-stop systems.
A well-planned network with an Arbiter switch and ring ports can recover from
segment failure within a very short time.
A switch in the Xpress Ring has only two roles: either “Forwarder” or “Arbiter”.
There can be only one Arbiter switch while all other switches are “Forwarders”.
One of the ring ports of an Arbiter switch is set to the blocking state. If one of the
ring connections fails, the blocked port is set to the forwarding state.
Manual
Version 1.2.0
Page 96

96 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.3 Security
7.3.1 IP Source Guard
“IP Source Guard” is a security function that restricts IP traffic on untrusted
Layer2 ports by filtering traffic based on a “DHCP Snooping” database
connection or a manually configured IP source connection. This function helps
prevent access such as “IP Snooping” (sending IP packets with a spoofed sender
IP address) if a host attempts to spoof the IP address of another host. Any IP
traffic coming into the interface with a source IP address other than that assigned
(via DHCP or static configuration) is filtered out on untrusted Layer2 ports.
This function is used on untrusted Layer2 interfaces in combination with “DHCP
Snooping”. An IP source binding table is manually configured (static IP source
binding) or created from information from the “DHCP Snooping” function and
used. Each entry in this table contains the IP address and associated MAC and
VLAN addresses. The “IP Source Guard” only supports Layer2 ports, including
“Access Ports” and “Trunk Ports”.
The “IP Source Guard” includes the following functions:
1. DHCP Snooping
2. DHCP Binding Table
3. ARP Inspection
4. Blacklist Filter (ARP inspection with MAC address filter table)
Manual
Version 1.2.0
Page 97

WAGO ETHERNET Accessories 852 Enhanced Features 97
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.3.1.1 DHCP Snooping
“DHCP Snooping” is a DHCP security function that increases network security by
filtering untrusted DHCP messages and creating and using a “DHCP Snooping”
database connection (also called “DHCP Snooping” binding table).
“DHCP Snooping” acts like a firewall between untrusted hosts and DHCP
servers. It can be used to differentiate between untrusted interfaces connected to
end users and trusted interfaces connected to a DHCP server or another swit ch.
The “DHCP Snooping” binding table contains the MAC address, IP address,
“Lease Time”, mount type, VLAN number and information on the local untrusted
interfaces of a switch.
If a switch receives a packet from an untrusted interface and the interface
belongs to a VLAN in which “DHCP Snooping” is enabled, the switch compares
the MAC source address to the hardware address of the DHCP client. If the
addresses match (as is normal), the switch forwards the packet. If the addresses
do not match, the switch drops the packet.
The switch drops a DHCP packet when one of the following situations occur:
• A packet from a DHCP server , such as a DHCPOFFER, DHCPACK,
DHCPNAK, or DHCPLEASEQUERY packet, is received from the untrusted
port.
• A packet is received on an untrusted interface, and the source MAC
address and the DHCP client hardware address do not match any of the
current bindings.
“DHCP Snooping” can be used to filter unauthorized DHCP packets on the
network and to dynamically create a binding table. This can prevent clients from
getting IP addresses from unauthorized DHCP servers.
Trusted vs. Untrusted Ports
Every port is either a “Trusted Port” or an “Untrusted Port” for “DHCP Snooping”.
This setting is independent of the “Trusted/Untrusted” setting for ARP inspection.
You can also specify the maximum number for DHCP packets that each port
(“trusted” or “untrusted”) can receive each second.
“Trusted Ports” are connected to DHCP servers or switches. The switch only
drops DHCP packets from “Trusted Ports” if the transmission rate of th e DH CP
packets received is too high. The switch learns the dynamic bindings from the
“Trusted Ports”.
DHCP Requests
The switch drops all DHCP requests if “DHCP Snooping” is enabled, but there
are no “Trusted Ports”.
Manual
Version 1.2.0
Page 98

98 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
“Untrusted Ports” are connected to subscribers. The switch discards DHCP
packets from untrusted ports in the following situations:
• The packet is a DHCP server packet (e.g., “OFFER”, “ACK” or “NACK”).
• The source MAC address and source IP address in a packet do not match
any of the current bindings.
• The source MAC address and source port in a “RELEASE” or “DECLINE”
packet do not match any of the current bindings.
• The transmission rate of the DHCP packets received are too high.
DHCP Snooping Database
The switch stores the binding table in volatile memory. If the switch restarts, it
loads the static bindings from non-volatile memory, but loses the dynamic
bindings, so that the devices in the network have to send DHCP requests again.
Configuring DHCP Snooping
Follow the steps below to configure “DHCP Snooping” on the switch:
1. Enable “DHCP Snooping” on the switch.
2. Enable “DHCP Snooping” for each VLAN.
3. Configure “Trusted Ports” and “Untrusted Ports”.
4. Configure the static bindings.
DHCP Snooping
The switch drops all DHCP requests if “DHCP Snooping” is enabled, but there
are no “Trusted Ports”.
If the port link fails, the entries from this port are deleted from the “DHCP
Snooping” binding table.
You must first enable global “DHCP Snooping” and “DHCP Snooping” for VLANs.
Manual
Version 1.2.0
Page 99

WAGO ETHERNET Accessories 852 Enhanced Features 99
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
The main purposes of the “DHCP Snooping” are:
1 To create and maintain a binding table for the ARP Inspection function.
2 To filter packets from DHCP servers that are connected to an “Untrusted
Port”.
Figure 24: DHCP Snooping
The packets from DHCP servers connected to an “Untrusted Port” are filtered.
7.3.1.1.1 Server Screening
The switch supports “Server Screening”, a function that denies access to “Rogue
DHCP Servers” (unauthorized, invalid DHCP servers). That is, when one or more
DHCP servers are present on the network and both provide DHCP services to
different distinct groups of clients, the valid DHCP server’s packets are passed to
the client.
If this function is enabled, the “DHCP Snooping” function must also be enabled
beforehand. The switch allows users to configure up to three valid DHCP servers.
If no DHCP servers are configured, it means all DHCP server are valid.
7.3.1.2 Binding Table
The “DHCP Snooping” binding table records the host information learned from
“DHCP Snooping” (dynamic) or set by user (static). The ARP inspection uses this
table to decide if to forward or drop ARP packets. ARP packets sent from by
invalid hosts are dropped. Once the “Lease Time” expires, the entry is deleted
from the table.
Static bindings are uniquely identified by the MAC address and VLAN ID. Each
MAC address and VLAN ID can only be in one static binding. If you create a
static binding with the MAC address and VLAN ID of an existing binding, the new
static binding replaces the original on.
Bindings are used by “DHCP Snooping” and ARP inspection to distinguish
between authorized and unauthorized packets in the network. The switch detects
the dynamic bindings by “snooping” DHCP packets and from static information
from the manual entries in the “Static Entry Settings” menu.
Manual
Version 1.2.0
Page 100

100 Enhanced Features WAGO ETHERNET Accessories 852
852-1305 8/4-Port 1000BASE-T/1000BASE-SX/LX
7.3.1.3 ARP Inspection
The dynamic “ARP Inspection” (“Address Resolution Protocol Inspection”) is a
security function in which ARP packets are inspected in a network. Dynamic ARP
inspections validates the packet by performing IP-to-MAC address binding
inspection stored in a trusted database (the “DHCP Snooping” database) before
forwarding the packet. Dynamic ARP intercepts, logs, and discards ARP packets
with invalid IP-to-MAC address bindings. This function protects the network from
certain “Man-in-the-Middle” attacks.
Dynamic ARP inspection ensures that only valid ARP requests and responses
are relayed.
The switch executes the following processes:
• Interception of all ARP requests and responses on untrusted ports.
• Inspection of all intercepted packets for valid IP-to-MAC address binding
before updating the local ARP cache or forwarding a packet to the
respective destination.
Trusted Port and Untrusted Port
• This setting is independent of the “Trusted/Untrusted” setting for “DHCP
Snooping”.
• The switch does not drop ARP packets from “Trusted Ports” for any reason.
• The switch drops ARP packets from “Untrusted Ports” if the information
from the sender in the ARP packets does not match any current bindings.
• Normally, the “Trusted Ports” are the “Uplink Ports” and the “Untrusted
Ports” are connected to subscribers.
Configurations
Users can enable/disable the ARP Inspection on the switch. It can also be
enabled/disabled on a specific VLAN. If ARP Inspection is disabled on the s witch,
ARP Inspection is disabled on all VLANs, even if enabled for individual VLAN.
Global State/VLAN State
There is a global state and individual VLAN states.
If the global state is disabled, ARP Inspection is disabled on the switch, even if
individual VLAN states are enabled.
If the global state for ARP Inspection is enabled, this function must be enabled by
the user for specific VLANs.
Manual
Version 1.2.0
 Loading...
Loading...