Page 1

VMware vCenter Configuration Manager Installation
and Getting Started Guide
vCenter Configuration Manager 5.4
This document supports the version of each product listed and supports all
subsequent versions until the document is replaced by a new edition. To
check for more recent editions of this document, see
http://www.vmware.com/support/pubs.
EN-000485-01
Page 2

vCenter Configuration Manager Installation and Getting Started Guide
You can find the most up-to-date technical documentation on the VMware Web site at:
http://www.vmware.com/support/
The VMware Web site also provides the latest product updates.
If you have comments about this documentation, submit your feedback to:
docfeedback@vmware.com
© 2006-2010 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and
intellectual property laws. VMware products are covered by one or more patents listed at
http://www.vmware.com/go/patents.
VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All
other marks and names mentioned herein may be trademarks of their respective companies.
VMware, Inc.
3401 Hillview Ave.
Palo Alto, CA 94304
www.vmware.com
2 VMware, Inc.
Page 3

Contents
Updated Information 9
About This Book 11
Preparing for Installation 13
Use Installation Manager 14
Understand Installation Configurations 14
Understand Tools Installation 15
Check Prerequisites for Installation 15
Hardware and Software Requirements 15
Administration Rights 15
Default Network Authority Account 15
Collector Services Account 16
VMware Application Services Account 16
VCM Remote Virtual Directory 16
Secure Communications Certificates 16
Server Authentication 17
Understand Use of FIPS Cryptography by VCM 19
VCM Use of Microsoft Cryptographic Service Providers (CSPs) for Windows Machines 19
Cryptography for UNIX/Linux Platforms 19
Cryptography used in VCM Software Components 20
Supported Windows and UNIX Platforms 20
Installing VCM 21
Using Installation Manager 21
Installing and Configuring the OS Provisioning Server and Components 23
Installing the Operating System Provisioning Server 23
Best Practices 23
Install the OS Provisioning Server 23
Preparing Boot Images for Windows Provisioning 28
Create Windows Boot Image 28
Copy the VCM Certificate to the OS Provisioning Server for Linux Provisioning 29
Importing Distributions into the OS Provisioning Server Repository 29
Create Directories for Windows Distributions 29
Import Windows Distributions 30
Import Linux/ESX Distributions 31
basicimport Command Options 32
Configuring the OS Provisioning Server Integration with the VCM Collector 32
Configure Stunnel on the OS Provisioning Server 33
Configure Stunnel on the VCM Collector 34
Confirm Stunnel Configuration 36
Maintaining Operating System Provisioning Servers 37
Backup the OS Provisioning Repository 37
Restore the OS Provisioning Repository From Backup 38
Managing the OS Provisioning Server System Logs 43
Upgrading or Migrating vCenter Configuration Manager 45
VMware, Inc. 3
Page 4

vCenter Configuration Manager Installation and Getting Started Guide
Upgrade and Migration Scenarios 45
Prerequisites 46
Back up Your Databases 47
Back up Your Files 47
Back up Your Certificates 47
Software Supported by the VCMCollector 47
Migration Process 48
Prerequisites 48
Foundation Checker Must Run Successfully 48
Use the SQLMigration Helper Tool 48
Migrate Only Your Database 48
Replace your existing 32-Bit Environment with the Supported 64-bit Environment 49
How to Recover Your Machine if the Migration is not Successful 49
Migrate a 32-bit environment running VCM 5.3 or earlier to VCM 5.4 50
Migrate a 64-bit environment running VCM 5.3 or earlier to VCM 5.4 51
Migrate a split installation of VCM 5.3 or earlier to a single-server installation 52
After You Migrate VCM 52
Upgrade Process 52
After You Upgrade VCM 53
Upgrading Existing Windows Agents 53
Upgrading Existing Remote Clients 54
Upgrading Existing UNIX Agents 54
To Upgrade the UNIX Agent(s) with a Local Package 55
To Upgrade the UNIX Agent(s) with a Remote Package 56
Upgrading VCM for Virtualization 56
Upgrading an Agent Proxy Machine 57
Upgrade the vSphere Client VCM Plug-In 59
Getting Started with VCM Components and Tools 61
Understanding User Access 61
Do Not Use the Collector as a Web Console 62
Starting and Logging Onto VCM 62
How to Start VCM and Log On 62
Getting Familiar with the Portal 63
General Information Bar 64
Portal Toolbar 64
Sliders 65
Where to Go Next 67
Getting Started with VCM 69
Discover, License, and Install Windows Machines 69
Verifying Available Domains 69
Checking the Network Authority 70
Assigning Network Authority Accounts 71
Discovering Windows Machines 72
Licensing Windows Machines 75
Installing the VCM Windows Agent on your Windows Machines 77
Performing an Initial Collection 83
Exploring Windows Collection Results 84
Getting Started Collecting Windows Custom Information 88
Discover, License, and Install UNIX/Linux Machines 97
Adding UNIX/Linux Machines 97
Licensing UNIX/Linux Machines 98
Installing the Agent on UNIX/Linux Machines 99
Performing a UNIX/Linux Collection 106
Exploring UNIX/Linux Collection Results 107
Discover, License, and Install Mac OS X Machines 110
4 VMware, Inc.
Page 5

Contents
Getting Started with VCM for Mac OS X 110
Adding Mac OS X Machines 111
Licensing Mac OS X Machines 112
Installing the Agent on Mac OS X Machines 113
Performing a Mac OS X Collection 119
Exploring Mac OS X Collection Results 121
Discover, License, and Collect Oracle Data from UNIX Machines 123
Adding UNIX Machines Hosting Oracle and Installing the Agent 124
Discovering Oracle Instances 124
Creating the Oracle Collection User Account 125
Performing an Oracle Collection 129
Exploring Oracle Collection Results 129
Reference Information about Oracle 129
Customize VCM for your Environment 130
How to Set Up and Use VCM Auditing 131
Getting Started with VCM for Virtualization 133
Virtual Environments Configuration 133
ESX/ESXi Server Collections 134
vCenter Server Collections 135
Configuring vCenter Server Data Collections 135
vCenter Server Collection Upgrade Considerations 135
vCenter Server Collection Prerequisites 135
Collect vCenter Server Data 137
Reviewing Collected vCenter Server Data 137
Troubleshooting vCenter Server Data Collections 138
Configuring VM Host Collections 138
Configure the Collector as an Agent Proxy 138
License and Configure VMHosts 139
Copy Files to the ESX/ESXi Servers 141
Perform an Initial Virtualization Collection 142
Reviewing Virtualization Collection Results 143
Configuring the vSphere Client VCM Plug-In 143
Register the vSphere Client VCM Plug-In 143
Configuring the vSphere Client VCM Plug-In Integration Settings 144
Manage Machines from the vSphere Client 145
Upgrade the vSphere Client VCM Plug-In 145
Troubleshooting the vSphere Client VCM Plug-In Registration 146
Getting Started with VCM Remote 149
Getting Started with VCM Remote 149
Installing the VCM Remote Client 150
Installing the Remote Client manually 151
Making VCM Aware of VCM Remote Clients 158
Configuring VCM Remote Settings 158
Creating Custom Collection Filter Sets 158
Specifying Custom Filter Sets in the VCM Remote Settings 158
Performing a Collection Using VCM Remote 159
Exploring VCM Remote Collection Results 159
Getting Started with VCM Patching 161
VCM Patching for Windows and UNIX/Linux 161
VCM Patching for Windows 161
VCM Patching for UNIX/Linux 162
Minimum System Requirements 162
About UNIXPatch Assessment and Deployment 162
Getting Started with VCM Patching 165
VMware, Inc. 5
Page 6

vCenter Configuration Manager Installation and Getting Started Guide
Running VCM Patching Reports 174
Customize Your Environment for VCM Patching 175
Getting Started with Operating System Provisioning 177
About OS Provisioning 177
OS Provisioning Components 177
Provision Machines Workflow 178
Collect OS Distributions 179
Discover Provisionable Machines 179
Provision Machines 180
Configure ESX and ESXi Machines 181
Change Agent Communication 182
Working with Provisioned Machines 182
Re-Provision Machines 182
Getting Started with Software Provisioning 185
Introduction to VCM Software Provisioning 185
Using Package Studio to Create Software Packages and Publish to Repositories 185
Software Repository for Windows 185
Package Manager for Windows 185
Installing the Software Provisioning Components 186
Install Software Repository for Windows 187
Install Package Studio 188
Install Package Manager on Managed Machines 190
Using Package Studio to Create Software Packages and Publish to Repositories 190
Creating Packages 191
Using VCM Software Provisioning for Windows 192
Prerequisites 192
Collect Package Manager Information from Machines 193
Collect Software Repository Data 193
Add Repository Sources to Package Managers 194
Install Packages 195
Related Software Provisioning Actions 196
Viewing Provisioning Jobs in the Job Manager 196
Creating Compliance Rules based on Provisioning Data 196
Creating Compliance Rules containing Provisioning Remediation Actions 197
Further Reading 199
186
Getting Started with VCM Management Extensions for Assets 201
Getting Started with VCM Management Extensions for Assets 201
Review Hardware and Software Configuration Item Fields 201
Modifying Hardware Configuration Item Fields 202
Modifying Software Configuration Item Fields 204
Adding Hardware Configuration Items 205
Editing Values for Devices 205
Modifying Other Devices 206
Adding Software Configuration Items 207
Further Reading 208
Getting Started with VCM Service Desk Integration 209
Getting Started with Service Desk Integration 209
Service Desk Integration in the Console 209
Service Desk Integration in Job Manager 210
Further Reading 211
Getting Started with VCM for Active Directory 213
6 VMware, Inc.
Page 7

Contents
Making VCM Aware of Domain Controllers 213
Confirming the Presence of Domains 214
Adding and Assigning Network Authority Accounts 215
Discovering Domain Controllers 215
Verifying Domain Controller Machines in Available Machines 217
Licensing and Deploying the VCM Agent 217
Performing a Machine Data Type Collection 220
Configuring VCM for Active Directory as an Additional Product 221
Deploying VCM for AD to the Domain Controllers 221
Running the Determine Forest Action 222
Running the Setup DCs Action 223
Performing an Active Directory Data Collection 225
Exploring Active Directory Collection Results 227
Further Reading 230
Accessing Additional Compliance Content 231
Locating the Content Directory 231
Launching the Content Wizard to Import Relevant Content 231
Exploring Imported Content Results in the Portal 231
Installing and Getting Started with VCM Tools 233
Installing the VCM Tools Only 233
Foundation Checker 234
VCM Import/Export and Content Wizard (CW) 234
VCM Import/Export 235
Content Wizard 236
Maintaining VCM After Installation 237
Customize VCM and Component-specific Settings 237
Configure Database File Growth 239
Configure Database Recovery Settings 240
Create a Maintenance Plan for SQL Server 2008 R2 240
Incorporate the VCM CMDB into your Backup and Disaster Recovery Plans 248
Troubleshooting Problems with VCM 249
Evaluating Missing UNIX Patch Assessment Results 249
Resolving Reports and Node Summaries Problems 250
To Resolve the Problem 250
Resolving Protected Storage Errors 250
Resetting the Required Secure Channel (SSL) 251
Updating the VCM Virtual Directory 251
Updating the IIS Settings in VCM 251
Resolving a Report Parameter Error 252
Index 253
VMware, Inc. 7
Page 8

vCenter Configuration Manager Installation and Getting Started Guide
8 VMware, Inc.
Page 9
Updated Information
VCM Installation and Getting Started Guide is updated with each release of the product or when necessary.
This table provides the update history of the vCenter Configuration Manager Installation and Getting Started
Guide.
Revision Description
EN-000485-01
n
"Maintaining Operating System Provisioning Servers" on page 37
added to provide information regarding backup and recovery
instructions, and file maintenance requirements.
n
"Confirm Stunnel Configuration" on page 42 removed the final
confirmation step as it was redundant of the procedure in
"Confirm Stunnel Configuration" on page 42.
n
"Provision Machines" on page 180 and "Re-Provision Machines" on
page 182 updated to indicate that the step 6 information regarding
the use of DHCP and the host name resolving to localhost applies
only to ESX and ESXi machines. Additionally, the PostProvisioning Action at the end of the procedure now includes
Windows 2008 SP1 and SP2 as operating systems requiring
Internet access to complete the license activation process.
EN-000485-00 Initial Release.
VMware, Inc. 9
Page 10

vCenter Configuration Manager Installation and Getting Started Guide
10 VMware, Inc.
Page 11

About This Book
The VMware vCenter Configuration Manager Installation and Getting Started Guide describes the steps
necessary for a successful VCM installation.
This document contains the following information:
n
Preparing for the VCM installation.
n
Installing VCM.
n
Getting started with VCM and its components.
n
Maintenance and troubleshooting.
Read this document and complete the associated procedures to prepare for a successful installation.
The VMware vCenter Configuration Manager Installation and Getting Started Guide applies to VCM,
Foundation Checker, and Service Desk Connector.
Intended Audience
This information is written for experienced Windows or UNIX/Linux/Mac OS X system administrators
who are familiar with managing network users and resources and with performing system maintenance.
To use this information effectively, you must have a basic understanding of how to configure network
resources, install software, and administer operating systems. You also need to fully understand your
network’s topology and resource naming conventions.
Document Feedback
VMware welcomes your suggestions for improving our documentation. If you have comments, send
your feedback to docfeedback@vmware.com.
VMware VCM Documentation
The vCenter Configuration Manager (VCM) documentation consists of the VCM Hardware and Software
Requirements Guide, VCM Foundation Checker User's Guide, VCM Installation and Getting Started Guide, VCM
online Help, and other associated documentation.
VMware, Inc. 11
Page 12
vCenter Configuration Manager Installation and Getting Started Guide
Technical Support and Education Resources
The following technical support resources are available to you. To access the current version of this book
and other books, go to http://www.vmware.com/support/pubs.
Online and Telepho ne
Supp ort
Supp ort Offerings To find out how VMware support offerings can help meet your business needs, go to
VMware Prof ession al
Services
To use online support to submit technicalsupport requests,view your product and contract
information, and register your products, go to http://www.vmware.com/support.
Customers with appropriate support contracts should use telephone support for priority 1
issues. Go to http://www.vmware.com/support/phone_suppor t.html.
http://www.vmware.com/support/services.
VMware Education Services courses offer extensive hands-on labs, case study examples,
and course materials designed to be used as on-the-job reference tools. Courses are
available onsite, in the classroom, and live online. For onsite pilot programs and
implementation best practices, VMwar e Consulting Services providesofferings to help you
assess, plan, build, and manage your virtual environment. To access information about
education classes, certification programs, and consulting services, go to
http://www.vmware.com/services.
12 VMware, Inc.
Page 13
Preparing for Installation
Use this information to help you prepare to install VCM components and tools in your enterprise.
n
Use Installation Manager: Provides an overview of Installation Manager, which is used to install and
activate all VCM components and tools.
n
Understand Installation Configurations: Describes the supported installation configurations for VCM.
n
Understand Tools Installation: Explains how VCM tools are installed.
n
Check Prerequisites for Installation: Lists the prerequisites you should complete prior to using VCM
Installation Manager to perform the installation.
For an overview of the security precautions you should take before installing VCM, see the VCM Security
Environment Requirements White Paper on the Download VMware vCenter Configuration Manager.
This document assumes that your hardware and software configuration meets the requirements described
in the VCM Hardware and Software Requirements Guide. If you have not already done so, verify that your
configuration meets the installation requirements by performing a Tools Only installation of VCM
Foundation Checker, and then running it after it is installed. If VCM Foundation Checker does not return
any errors, then you are ready to proceed. For more information on performing a Tools only installation,
see "Installing and Getting Started with VCM Tools" on page 233.
1
VMware, Inc. 13
Page 14
vCenter Configuration Manager Installation and Getting Started Guide
Use Installation Manager
Use Installation Manager to perform new installations as well as upgrades. Installation Manager provides a
highly simplified process for installing components and tools, and steps you through the entire installation
or upgrade process. Installation Manager:
n
Performs checks to ensure the machine(s) meets the hardware and software prerequisites necessary for
installation.
n
Provides confirmation of the license file you apply during installation.
n
Installs VCM and all of its components and tools in the appropriate order on your machine(s).
n
Tests each progressive step during the installation to ensure that all components are successfully
installed and that the licensed components are successfully activated.
Installation Manager operates with minimal user input and provides clear feedback on progress
throughout the entire installation process.
Installation Manager installs VCM and all of its components on your machine, even components that you
have not purchased. However, only the components that you have purchased are licensed by your license
file, which enables you to purchase more licenses later, and thereby activate additional components that
are already installed.
To install VCM and all of its components and tools for the first time, follow the procedures in "Installing
VCM" on page 21.
IMPORTANT You can use Installation Manager to upgrade from VMware VCM 5.3, EMC Ionix SCM 5.0 or
greater, or Configuresoft ECM 4.11.1 or greater to VCM 5.4.
When performing a new installation or a migration, you must have the previous license file available and
specify the path to the license file during the installation. Installation Manager will use the license file to
activate the components that you have purchased. If you do not have the license file from VCM 4.11.1 or
later, contact VMware Customer Support.
Understand Installation Configurations
Before proceeding, you must have already configured your hardware and installed all of the prerequisite
software based on the information in the VCM Hardware and Software Requirements Guide.
As of VCM 5.4, split installations are not supported. To migrate a split installation of VCM 5.3 or earlier to
a single-server installation, see the section on migrating VCM. For more information, contact VMware
Customer Support.
For a detailed diagram of a complete installation, see the VCM Hardware and Software Requirements Guide.
14 VMware, Inc.
Page 15
Understand Tools Installation
Several tools are installed with automatically VCM. These tools include:
n
Foundation Checker
n
Import/Export Tool and Content Wizard Tool
n
Package Studio
You may install VCM tools separately on a non-Collector machine as needed. To install the Tools only, use
the installation procedures in "Installing and Getting Started with VCM Tools" on page 233.
Check Prerequisites for Installation
Complete these prerequisites prior to using Installation Manager.
Hardware and Software Requirements
Before you can install VCM, your hardware and software configuration must meet the requirements in
the VCM Hardware and Software Requirements Guide.
IMPORTANT Installation Manager runs Foundation Checker automatically during the VCM installation,
which checks the machine to verify that all of the prerequisites are satisfied for a successful installation of
VCM. Running Foundation Checker as part of the Installation Manager process, rather than running it as a
standalone tool, captures common issues that are difficult to remediate as well as issues related to specific
components and the version of VCM being installed. Because Foundation Checker verifies componentspecific issues against VCM, you should use Installation Manager to run Foundation Checker. Foundation
Checker must run without producing before you can proceed with the VCM installation. For more
information about the standalone Foundation Checker, see "Installing and Getting Started with VCM
Tools" on page 233).
Preparing for Installation
If you install the Agent on HP-UX 11.11, you must also install Patch PHSS_30966, which is required. If you
need assistance, contact VMware Customer Support.
Administration Rights
The User Account of the person performing your installation or upgrade must be all of the following:
n
A system administrator on the machine(s) on which the installation or upgrade is being performed, and
n
A system administrator on the database instance that will be used, and
n
A member of a domain.
The installing User Account should not be the account used to run the SQL Server Services; nor, after
installation, should you create a VCM user with the SQL Server Services account credentials.
Default Network Authority Account
You must specify the default network authority account during the installation. The default network
authority account, which is often the system administrator’s account (for example, a Domain Admin in the
Local Admin Group), must be set up in the Local Administrators group on each machine prior to
installation. You should have already completed this step by following the checklist in the VCM Hardware
and Software Requirements Guide.
VMware, Inc. 15
Page 16
vCenter Configuration Manager Installation and Getting Started Guide
The Local System account named NT AUTHORITY\System has unrestricted access to all local system
resources. This account is a member of the Windows Administrators group on the local machine, and a
member of the SQL Server sysadmin fixed server role. If the NT AUTHORITY\System account does not
have access to the VCM installation binary files (possibly because someone removed the account or
inherently removed access), the installation will result in an “access denied” error on the first step. Details
of this error are not stored in the VCM error log. The solution is to grant access to the NT
AUTHORITY\System account from the installation source directory, and then run the installation again
(right-click the folder, select the Security tab, and make sure the user or user’s group has Full Control of
the file/folder).
NOTE The network authority account can be changed later in VCM at Administration > Settings >
Network Authority.
Collector Services Account
The Collector Services Account must be specified during the installation process. This account, which may
not necessarily be the system administrator’s, must exist in the Local Administrators group on the
Collector machine. In addition, this account must not be the LocalSystem account.
IMPORTANT If the password for your services account changes, you must also change the password in
both the Services Management and Component Services DCOM Config consoles.
To change your services password in the Services Management console, click Administrative Tools >
Services. Locate all of the services that use the services account to log on. Right-click each of these services
and select Properties. Click the Log On tab and update the password field to reflect your new password.
To change your services password in the Component Services DCOM Config console, click
Administrative Tools > Component Services. Expand the Component Services node and select
Computers > My Computer > DCOM Config. Right click the LicenseDcom file and select Properties.
Click the Identity tab and update the password field to reflect your new password.
VMware Application Services Account
The VMware Application Services Account must be a domain user. Because this account will have full
administrative authority for the CSI_Domain database, you should never use it as a VCM login or for any
other purpose.
VCM Remote Virtual Directory
You must specify the VCM Remote Virtual Directory account during the installation. To reduce the
chances of a security risk to accounts, this account should not be the same account that you used for your
Default Network Authority Account and/or your Services Account.
NOTE If necessary, you can change the service account later using the IIS Management console.
Secure Communications Certificates
VCM uses Transport Layer Security (TLS) to secure all HTTP communication with Windows and UNIX
Agents in HTTP mode (includes all UNIX Agents and Windows Agents in HTTP mode). TLS uses
certificates to authenticate the Collector and Agents to each other. You must specify certificates for the
Collector and for the Enterprise during the installation. If you plan to use your own certificates, familiarize
yourself with the certificate names so that you can select them during installation.
16 VMware, Inc.
Page 17

Preparing for Installation
To be valid, a Collector certificate must be:
n
Located in the local machine personal certificate store.
n
Valid for Server Authentication. If any Enhanced Key Usage extension or property is present, it must
include the Server Authentication OID 1.3.6.1.5.5.7.3.1. If the Key Usage extension is present, it must
include DIGITAL_SIGNATURE.
n
Active, and not expired.
Alternatively, Installation Manager can generate the Collector and Enterprise certificates for you; select the
Generate option during installation.
NOTE If you will install more than one Collector that will communicate with the same Agent(s), or plan
to replace/renew your certificates later, special considerations are required to generate and select
certificates in VCM Installation Manager. For details about VCM and Transport Layer Security (TLS), see
Transport Layer Security Implementation for VCM.
Server Authentication
Server Authentication is a method of authenticating the server to the client. VCM supports server
authentication. In VCM environments where TLS is employed, VCM Agents verify the identity of the
Collector(s) through the use and verification of certificates (over HTTP).
Typically, the server authenticates a client/user by requiring information such as a user name and
password. When server authentication is used, the client/user verifies that the server is valid. To
accomplish this verification using TLS, the server provides a certificate issued by a trusted authority, such
as Verisign®. If your client web browser has the Verisign® Certified Authority certificate in its trusted
store, it can trust that the server is actually the Web site you access.
TLS uses certificates managed by a public key infrastructure (PKI) to guarantee the identity of servers and
clients. A certificate is a package containing a public key and information that identifies the owner and
source of that key, and one or more certifications (signatures) to verify that the package is authentic. To
sign a certificate, an issuer adds information about itself to the information already in the certificate
request. The public key and identifying information are hashed and signed using the private key of the
issuer’s certificate.
Certificates are defined by the X.509 RFC standard, which includes fields that form a contract between the
creator and consumer. The Enhanced Key Usage extension specifies the use for which the certificate is
valid, including Server Authentication.
Enterprise and Collector Certificates
An Enterprise Certificate and one or more Collector Certificates enable secure HTTP Collector-Agent
communication in VCM. The Enterprise Certificate enables VCM to operate in a multi-Collector
environment. Agents have the Enterprise Certificate in their trusted certificate stores, which they use
implicitly to validate any certificate issued by the Enterprise Certificate. All Collector Certificates are
expected to be issued by the Enterprise Certificate, which is critical in environments where a single Agent
is shared between two collectors.
Server Authentication is required to establish a TLS connection with an Agent. All Collectors should have a
common Enterprise Certificate. Each Collector Certificate is issued by the Enterprise Certificate, and is
capable of Server Authentication.
VMware, Inc. 17
Page 18

vCenter Configuration Manager Installation and Getting Started Guide
n
The Collector Certificate is used to initiate and secure a TLS communication channel with an HTTP
Agent. The Agent must be able to establish that the Collector Certificate can be trusted, which means
that the Collector Certificate is valid and the certification path starting with the Collector Certificate
ends with a trusted certificate. By design, the Enterprise Certificate is installed in the Agent’s trusted
store, and the chain ends with the Enterprise Certificate.
n
A Collector Certificate can also be used to issue Agent certificates. As long as all Collector Certificates
are issued by the same Enterprise Certificate, any Agent Certificate may be issued by any Collector
Certificate, and all Agents will be able to trust all Collectors. Similarly, all collectors will be able to
validate all Agent Certificates. Agent Certificates are used for Mutual Authentication only. Mutual
authentication is supported, but requires interaction with VMware Customer Support and a Collector
Certificate that also has certificate signing capability.
n
The Collector Certificate and associated private key must be available to the Collector. This certificate is
stored in the (local machine) personal system store.
Collector Certificates in VCM must adhere to the requirements specified above in Secure Communications
Certificates.
Delivering Initial Certificates to Agents
VCM Agents use the Enterprise Certificate to validate Collector Certificates. Therefore, the Agent must
have access to the Enterprise Certificate as a trusted certificate. In most cases, VCM will deliver and install
the Enterprise Certificate as needed.
n
Installing the Agent from a Disk (Windows only): The VCM Installation DVD does not contain
customer-specific certificates. If HTTP is specified, the manual VCM Installer requests the location of the
Enterprise Certificate file during the installation. You must have this file available at installation time.
The certificate file (with a .pem extension) can be copied from the CollectorData folder of the Collector.
This will be the case whether you run the manual installer directly (CMAgentInstall.exe) or use the
“Agent Only” option from the DVD auto-run program.
n
Using CMAgentInstall.exe to Install the Agent (Windows only): CMAgentInstall.exe or
CMAgent[version].msi is the manual Agent installer program. The manual installer will request the
location of the Enterprise Certificate file, if HTTP is specified. You must have this file available at
installation time. The certificate file can be copied from the CollectorData folder of the Collector.
n
MSI Install Package: If HTTP is specified, the MSI agent install package also requires access to the .pem
file.
n
Installing the Agent for UNIX/Linux: See Installing the VCM Agent on UNIX/Linux Machines in this
document.
Installing the Agent Using a Provisioning System
For Windows®, the manual installation program is available in .exe and .msi formats. Both versions allow
the Enterprise Certificate file to be specified with a command line switch. You may also omit the certificate
installation step by use of a command line switch. When these programs are run through a provisioning
system, you must ensure that the Enterprise Certificate is available (and still secure), and configure the
program options appropriately. Alternatively, you may choose to push the Enterprise Certificate to
Agents by some other means and configure the provisioning system to omit certificate installation.
For UNIX/Linux, each UNIX/Linux installation package is targeted for one or more supported platforms.
To install the UNIX/Linux Agent using a provisioning system, extract the installation package as
appropriate and then deploy the extracted file with the provisioning system. The Enterprise Certificate is
embedded in the installation package on the Collector.
18 VMware, Inc.
Page 19

For more information about Installing the Agent on UNIX/Linux Machines and UNIX/Linux packages and
platforms, refer to section Installing the VCM Agent on UNIX/Linux Machines.
Understand Use of FIPS Cryptography by VCM
Federal Information Processing Standards (FIPS) are developed by the US National Institute of Standards
(NIST) and the Canadian Communications Security Establishment (CSE). VCM incorporates cryptographic
service providers that conform to these FIPS standards:
n
FIPS 140-2: Security Requirements for Cryptographic Modules
n
FIPS 46-3: Data Encryption Standard (DES)
n
FIPS 81: DES Modes of Operation
n
FIPS 113: Computer Data Authentication
n
FIPS 171: Key Management
n
FIPS 180-1: Secure Hash Standard (SHA-1)
n
FIPS 186-2: Digital Signature Standard (DSA) and Random Number Generation (RNG)
n
FIPS 198: Message Authentication Codes (MACs) using SHA-1
n
FIPS 197: Advanced Encryption Standard (AES) Cipher
Preparing for Installation
n
FIPS 200: Federal Information Security Management Act (FISMA)
n
SP 800-2: Public Key Cryptography (including RSA)
n
SP 800-20: Triple DES Encryption (3DES) Cipher
VCM Use of Microsoft Cryptographic Service Providers (CSPs) for Windows Machines
On Windows machines, VCM uses cryptography by way of the Microsoft CryptoAPI, which is a
framework that dispatches to Microsoft Cryptographic Service Providers (CSPs). CSPs are not shipped
with VCM or installed by VCM, but instead are part of the security environment included with Microsoft
Windows. In the configurations supported by VCM, these CSPs are FIPS 140-2 validated. An up-to-date
table of FIPS certificate numbers is at: http://technet.microsoft.com/en-us/library/cc750357.aspx.
Cryptography for UNIX/Linux Platforms
On UNIX/Linux platforms, the VCM Agent uses the cryptography of the OpenSSL v0.9.7 module. This
cryptographic library is installed with the VCM Agent.
VMware, Inc. 19
Page 20

vCenter Configuration Manager Installation and Getting Started Guide
Cryptography used in VCM Software Components
VCM uses various software components that also use cryptography. Microsoft IIS, Internet Explorer, and
SChannel (SSL/TLS) systems call the CryptoAPI, and thus use the Windows FIPS-validated modules. VCM
for Virtualization uses ActiveX COM components from WeOnlyDo! Software (WOD) for SSH and SFTP
services. WOD utilizes the FIPS 140-2 compliant OpenSSL library.
Table 1-1. Installed or Used Crytography Modules
System
UI Windows Used
VCMServer Windows Installed Used
Virt Proxy Windows Installed Used
AD Agent Windows Used
Win Agent Windows Used
UNIX Agent HP/UX Installed Installed
Platform
AIX Installed Installed
Solaris Installed Installed
OpenSSLFIPS 1.1.2 OpenSSLFIPS 1.1.1 OpenSSLCrypt 0.9.7 Crypto++ CryptoAPI
Debian Installed Installed
Red Hat Installed Installed
SUSE Installed Installed
ESX Server All No cryptography modules are used or installed on ESX.
Supported Windows and UNIX Platforms
Supported Windows and UNIX platforms, and their architectures, are listed in the VCM Hardware and
Software Requirements Guide. For information about TLS, see Transport Layer Security (TLS) Implementation
for VCM on the Download VMware vCenter Configuration Manager.
20 VMware, Inc.
Page 21
Installing VCM
Use Installation Manager to install VCM and all of its components and tools.
To install only the VCM tools, follow the installation procedures in "Installing and Getting Started with
VCM Tools" on page 233.
IMPORTANT Before you migrate VCM to VCM 5.4, read Migrating VCM and Related Components.
VMware vCenter Configuration Manager (VCM) Installation Manager is a standalone application that
checks your machine to ensure it is properly configured and configures licensed components during the
installation process.
When you install VCM and related components, read about each configurable component to ensure you
supply the appropriate information. The default settings may not fit your configuration exactly. If you
migrate VCM or SQL Server, or migrate to a 64-bit system, see "Upgrading or Migrating vCenter
Configuration Manager" on page 45.
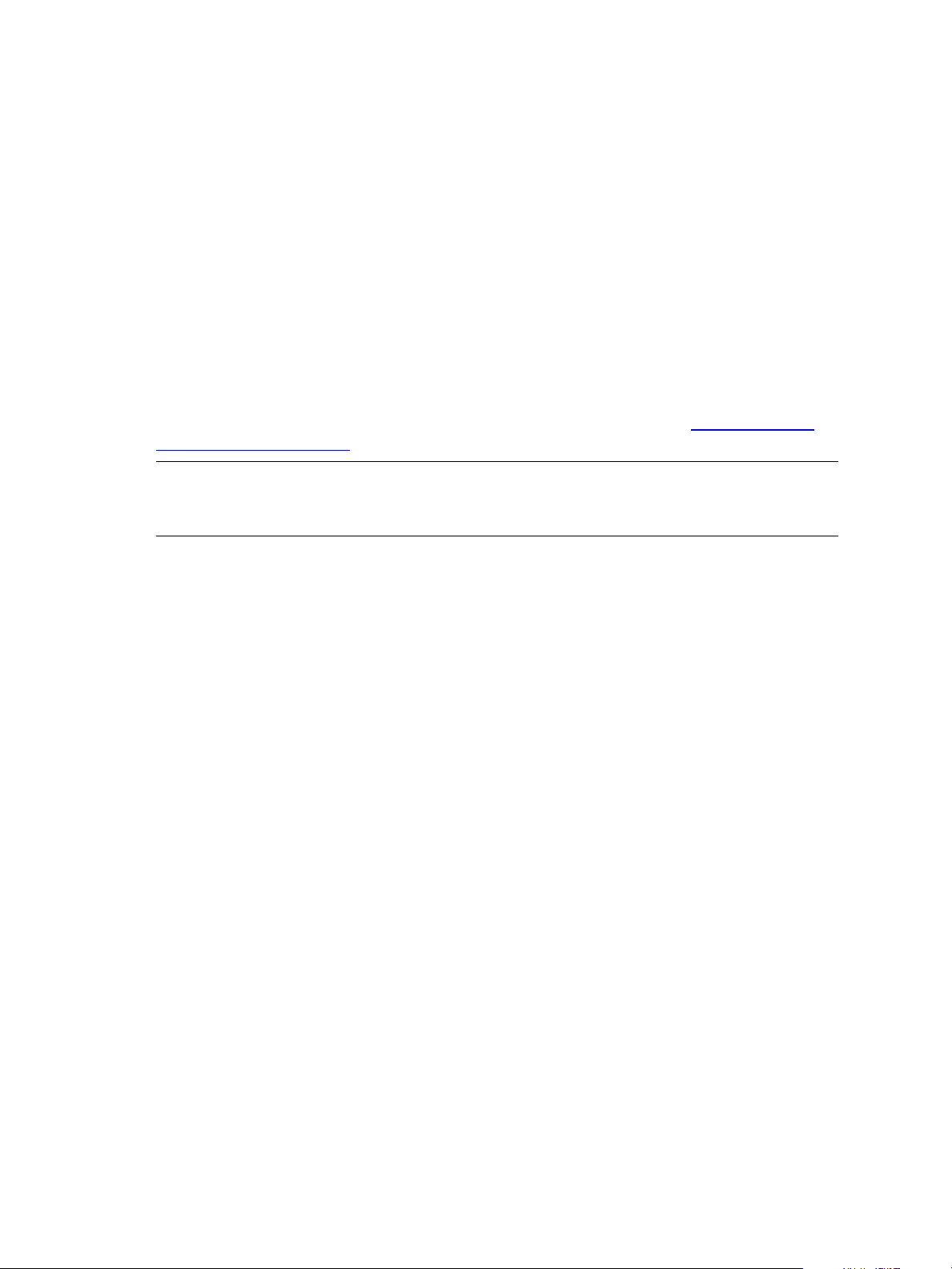
When you insert the installation CD into the machine to install VCM, the initial installation screen appears
and displays several options.
2
If the installation screen does not appear automatically, or if you begin the installation from a network
location, navigate to the CD root directory or the file share and double-click setup.exe.
VMware, Inc. 21
Page 22
vCenter Configuration Manager Installation and Getting Started Guide
1. Select one of these options:
n
Run Installation Manager. Starts Installation Manager and begins the installation.
n
View Help. Displays the Installation Manager Help, which describes the selections that appear
during the installation.
n
Browse Contents of Installation CD. Starts Windows Explorer and displays the content of the
installation CD, which includes documentation.
n
Contact Support Team. Displays instructions to contact VMware Customer Support.
n
Exit. Closes Installation Manager.
2. Click Run Installation Manager to begin the installation process.
3. Follow the steps through the wizard to complete the installation. For details about the installation
options, see the Installation Manager Help.
After the installation completes, configure SQL Server settings to configure the database file growth and
database recovery settings to fine-tune your VCM Database. See the instructions in "Maintaining VCM
After Installation" on page 237.
CAUTION During the installation, a folder containing VCM-related MSI files is added to
%windir%\Installer\. If you move or delete the contents of this folder, you will not be able to use
Installation Manager to upgrade, repair, or uninstall VCM successfully.
22 VMware, Inc.
Page 23
Installing and Configuring the OS Provisioning Server and Components
The Operating System (OS) Provisioning server installs OS distributions on target machines. The OS
Provisioning server is installed and configured on a Red Hat server, and then operating systems are
imported into the OS Provisioning Server repository. After the distributions are imported, the server
manages the installation process.
When the OS Provisioning server is installed, configured, and OS distributions have been imported, you
then use VCM to provision target machines with an operating system. See "About OS Provisioning" on
page 177 for more information.
Installing the Operating System Provisioning Server
VCM OS provisioning supports one instance of VCM with one instance of the Operating System (OS)
Provisioning Server.
You must first configure the server to meet the prerequisites specified in the VCM Hardware and Software
Requirements Guide, install the OS Provisioning Server application, and then perform post-install
configurations.
3
Best Practices
Configure your OS Provisioning Server in a private or restricted network. When provisioning machines,
connect the machines to the private network. This practice maintains security during the provisioning
process.
For additional security information, see VMware vCenter Configuration Manager Security Environment
Requirements White Paper.
Install the OS Provisioning Server
The OS Provisioning Server manages the installation of operating system distributions on target machines.
You install the OS Provisioning Server using supplied media or media images. The installation must be run
as the root user for the installation to complete correctly.
Prerequisites
n
Ensure the machine meets all the prerequisites to installation specified in the VCM Hardware and
Software Requirements Guide.
n
Disable SELinux to allow the loading of shared libraries.
VMware, Inc. 23
Page 24

vCenter Configuration Manager Installation and Getting Started Guide
Procedure
1. Mount the VCM-OS-Provisioning-Server-<version number>.iso by either attaching to the media image
or mounting the image.
When mounting the image, do not use the no-exec option.
2. Change the directory to where the image is located.
cd /<OS Provisioning Server ISO>
where <OS Provisioning Server ISO> is the path to the mounted file.
3. Run the # ./INSTALL-ME-FIRST command to install the database package.
When completed, "The installation completed successfully" message is displayed.
For more information about the process if it fails, see the DB2 installation log at /tmp/db2setup.log.
4. Run the # ./INSTALL-ME-SECOND command to install the OS Provisioning Server software.
The autoinstall -d -a y utility can be used for unattended installation of OS Provisioning
Server.
5. In the Nixstaller window, click Next.
6. On the dialog box, click Continue.
7. When the installation is completed, click Close.
8. Click Finish.
9. Run the # service FastScale status command to verify that the installation has completed
successfully.
A successful installation displays results similar to the following (pid values vary):
FSrepository does not implement a status command
rsyslogd (pid 3335) is running...
fsmesgd (pid 3517) is running...
fsrepod (pid 3683) is running...
fsadmin (pid 12618 12617 12614 3785 3784 3783 3782 3781 3778 3777 3776 3753)
is running...
dhcpd (pid 3786) is running...
Checking Basic Server: EMC HomeBase Server (Database) is running (PID: 3951).
Checking Basic Server: EMC HomeBase Server is running (PID: 4143).
fsjobd (pid 4237) is running...
fshinvd (pid 4249) is stopped...
stunnel (pid 4262 4261 4260 4259 4258 4257) is running...
An unsuccessful installation either displays the following error message:
“FastScale: unrecognized service”
or a few of the above mentioned services might not be running. If so, review the logs to determine
possible problems.
10. Run the commands to create the repository database.
This action destroys any existing repository information.
24 VMware, Inc.
Page 25
Installing and Configuring the OS Provisioning Server and Components
# su - fsrepo
[fsrepo@<machine name>~]$ create-repository
11. When the action completes, run the [fsrepo@<machine name>~]$ exit command.
If necessary you can review the /opt/FastScale/home/fsrepo/fscreate-repo.log.
The OS Provisioning Server maintenance commands can also be added to the root user's path. The
default shell profiles are modified by OS Provisioning Server to add /opt/FastScale/sbin to the
root account. When the user is root, the maintenance commands in /opt/FastScale/sbin are
available in the default path and are available when the profile is reloaded.
12. Reboot the OS Provisioning Server to ensure that all related services are started in the correct order.
13. Run the # service FastScale status command to verify the OS Provisioning Server services
after reboot.
A successful installation displays the same results as above.
What to do next
When you install the OS Provisioning Server, specific OS Provisioning users were created.
n
fsrepo: Used to create the repository.
n
vcmuser: Used to run basicimport of distributions and for communication with VCM.
The ensure proper security, you must set the password for the vcmuser. See "Set the vcmuser Password"
on page 25.
Set the vcmuser Password
The vcmuser is used when importing distributions into the OS Provisioning repository and for
communication between VCM and the OS Provisioning Server. You must not delete the user or change
the permissions, but you should set the vcmuser password based on your corporate standards.
Prerequisit es
The OS Provisioning Server is installed.
Procedu re
1. Log on to the OS Provisioning Server as root.
2. Run the passwd vcmuser command.
3. Type the new password, and then confirm the password.
Configure DHCP
The recommended configuration for OS provisioning is to use a private isolated network set up specifically
for OS provisioning. When using a private provisioning network, the best practice is to configure the
DHCP server included with the OS Provisioning Server to provide addresses and network boot
information to nodes connected to this isolated network. If, however, you are provisioning systems on a
network shared for other uses, you will likely already have a DHCP server on the network. In this case,
you must disable the OS Provisioning Server's DHCP server and configure your regular DHCP server to
provide network boot information for machines to be provisioned. See "Configure a DHCP Server other
than the OS Provisioning Server" on page 26 for more information.
VMware, Inc. 25
Page 26

vCenter Configuration Manager Installation and Getting Started Guide
Whether you use a private provisioning network or a shared network you can use either the OS
Provisioning Server DHCP server or a separate DHCP server; however, only one DHCP server should be
active on any network, and the DHCP server will need to be able to “point” new systems to the OS
Provisioning Server for discovery and provisioning.
The OS Provisioning Server provides DHCP services on the provisioning network by default. The DHCP
server must be configured to listen on the private provisioning network interface.
Procedu re
1. Open the /opt/FastScale/etc/dhcpd.conf file and configure the settings as necessary for your
environment.
Option Description
subnet The IP address subnet of the private network interface. Default value: 10.11.12.0
netmask The netmask of the subnet. Default value: 255.255.255.0
address range The range of allocated IP addresses for the provisioned nodes. Default value:
10.11.12.100 – 10.11.12.200
broadcast-
The broadcast address on the subnet. Default value: 10.11.12.255
address
next-server The IP address of the private network interface. Default value: 10.11.12.1
Configure a DHCP Server other than the OS Provisioning Server
If you are provisioning using an external DHCP server, you must modify your regular DHCP network
using this procedure.
Configuring the corporate DHCP server to use the IP address of the OS Provisioning Server for PXE Boot
allows the nodes to connect to the OS Provisioning Server after DHCP had completed. When the nodes
are set to NetBoot (PXE) on startup, the nodes download the boot kernel through TFTP from the OS
Provisioning Server. For this process to work, you must turn off DHCP on the OS Provisioning Server.
Prerequisit e
Turn off DHCP on the OS Provisioning Server.
Procedu re
1. On the OS Provisioning Server, log in as root and edit /etc/sysconfig/FSdhcpd to prevent the
DHCP resetting after a reboot.
Change DHCPD_CONF=/opt/FastScale/etc/dhcpd.conf
to DHCPD_CONF=/opt/FastScale/etc/dhcpd.conf.none
2. On the OS Provisioning Server, run the following command:
/opt/FastScale/etc/init.d/FSdhcpd stop
26 VMware, Inc.
Page 27

Installing and Configuring the OS Provisioning Server and Components
3. On the corporate DHCP server, update the dhcpd.conf file with the following options:
allow bootp;
allow booting;
next-server <IP address of the OS Provisioning Server>; where <IP address of the OS
Provisioning Server> is replaced with the specified IP address.
Configure TFTP
The OS Provisioning Server provides TFTP services on the provisioning network, which, by default, has a
private IP address. The TFTP server must be configured to listen on this private network interface.
Procedu re
1. Open the /opt/FastScale/homebase-server/etc/channels/TFTP.xml file and configure the
settings as necessary for your environment.
Option Description
connectionActive Enables or disables TFTPserver. A value of true enables the server, and a value of false
disables the server. The default value is true.
localHost The IP address of the private network interface. The default value is 10.11.12.1.
The utility fstftp_conf, located in /opt/FastScale/sbin, can also be used to update the file.
2. If you make changes, restart the basic service using the service FastScale FSbasic restart
command.
Uninstall the OS Provisioning Server
Uninstall the OS Provisioning Server by first mounting the OS Provisioning Server media, and then
running the uninstall command. These programs must be run as the root user for the uninstall process to
complete correctly.
CAUTION The uninstall process removes the application and deletes all the data stored in the database.
Procedu re
1. Mount the OS Provisioning Server ISO by either attaching to the media image or mounting the image.
2. Change the directory to where the image is located.
cd /<OS Provisioning Server ISO Location>
where <OS Provisioning Server ISO Location> is the path to the mounted media.
3. Run the following command to uninstall the application:
./UNINSTALL-ME
4. Type Yes.
The following is a sample of the uninstall log:
[Thu Jul 22 08:57:06 IST 2010] UNINSTALL-ME: Starting uninstallation of
Application Stack Manager...
[Thu Jul 22 08:57:08 IST 2010] UNINSTALL-ME: FastScale service is running
[Thu Jul 22 08:57:08 IST 2010] UNINSTALL-ME: Stopping FastScale service
VMware, Inc. 27
Page 28

vCenter Configuration Manager Installation and Getting Started Guide
[Thu Jul 22 08:57:08 IST 2010] UNINSTALL-ME: Command : /sbin/service FastScale
stop
Shutting down FSnetfs: [ OK ]
Shutting down FSsyslog: [ OK ]
Shutting down FSmesgd: [ OK ]
Shutting down FSdhcpd: [ OK ]
..........
[Thu Jul 22 09:00:44 IST 2010] UNINSTALL-ME: Uninstallation complete!
Preparing Boot Images for Windows Provisioning
It is necessary to prepare a Windows boot image to successfully provision target Windows machines. The
boot image, created once on a Windows machine and applied to the OS Provisioning Server, is used to
meet the booting needs of the Windows distribution installations on target machines.
Create Windows Boot Image
You must create a Windows boot image and add it the OS Provisioning Server. The image is created on a
Windows machine and deployed to the OS Provisioning Server.
Prerequisites
n
Verify that the Windows Automated Install Kit (WAIK) is installed.
n
Verify that Java Virtual Machine (JVM), version 1.6.0 or later, is installed.
n
Verify that the OS Provisioning Server is accessible on the network to the Windows machine, usually
the Collector, on which you are creating the image.
Procedure
1. Copy /opt/FastScale/homebase-server from the OS Provisioning Server to a directory on the
Windows machines. For example, c:\Program Files (x86)\VMware\VCM\Tools\homebase-
server.
2. On the OS Provisioning Server, import a supported Windows operating system using the basicimport
command.
See "Import Windows Distributions" on page 30 for more information.
3. On the Windows machine, change the directory to the bin directory in the homebase-server directory.
For example, c:\Program Files (x86)\VMware\VCM\Tools\homebase-server\bin.
4. Run the create command.
hbd create windows --waik <Path to WAIK> -l <OS Provisioning Server Public IP>
--deploymenturl <OS Provisioning Server Private IP Address> -u <HB User> -p
<HB password>
Option Description
<Path to
WAIK>
<OS OS Provisioning Server's Public Interface IP Address.
28 VMware, Inc.
Path to the WAIK installation. For example, "c:\Program Files (x86)\Windows AIK".
Page 29

Option Description
Provisioning
Server
Public IP>
Installing and Configuring the OS Provisioning Server and Components
<OS
Provisioning
Server
Private IP>
<HB User> HomeBaseServer configured username. The default username is "admin".
<HB
password>
OS Provisioning Server's Private Interface IP Address. The default configuration is 10.11.12.1. If
the Windows AIK machine is connected to OS Provisioning Server using the d eployment
network, then the '--deploymenturl' option is not necessary. Instead, you should specify the
deployment IP address as the argument to the '-l' option.
HomeBaseServer configured password. T he default password is "admin".
5. Verify that the boot image files are created on the OS Provisioning Server in
/opt/FastScale/homebase-server/deployment.
Copy the VCMCertificate to the OS Provisioning Server for Linux
Provisioning
If you are using the OS Provisioning Server to install Linux distributions, you must copy the VCM
certificate file to the OS Provisioning Server to ensure the certificate is included with the VCM Agent when
the configured session is created prior to provisioning.
Procedure
1. Copy the VCM certificate, VMware_VCM_Enterprise_Certificate_*.pem, located on the VCM
Collector in \Program Files (x86)\VMware\VCM\CollectorData, to the OS Provisioning Server
/opt/FastScale/var/fsadmin/basic/directory.
Importing Distributions into the OS Provisioning Server Repository
Operating system distributions must be imported into the OS Provisioning Server repository before you
can use VCM to install them on target machines. The basicimport command uses an -i option to specify an
.iso and a -d option to specify directories.
The supported operating systems are listed in VCM Hardware and Software Requirements Guide.
Create Directories for Windows Distributions
Some Windows operating systems distribution files are issued on multiple CDs. Due to the dependencies
within the packages, multiple CDs cannot be loaded using separate basicimport commands for each CD.
You must create a single directory out of multiple Windows operating system CDs before importing.
Procedure
1. On the OS Provisioning Server, create a directory to contain the files from both CDs by typing:
# mkdir -p /tmp/<directory name>
For example, # mkdir -p /tmp/Win2003-R2-SP2-Standard
2. Insert the first CD in the drive and type:
# cp -R /media/cdrom/<source directory name> /tmp/<directory name>
VMware, Inc. 29
Page 30

vCenter Configuration Manager Installation and Getting Started Guide
For example, # cp -R /media/cdrom/Win2003-R2-SP2-Standard /tmp/Win2003-R2-SP2-Standard
3. Replace the first CD with the second CD and type:
# cp -R /media/cdrom/<source directory name> /tmp/<directory name>
For example, # cp -R /media/cdrom/Win2003-R2-SP2-Standard /tmp/Win2003-R2-SP2-Standard
When importing the second CD, do not replace any files if prompted during the copy operation.
Import Windows Distributions
Distributions are the operating system installation files. You must import each OS distribution into the OS
Provisioning repository before you can use VCM to install it on target machines.
NOTE Importing distributions with spaces in the file name is not supported. Before importing, remove
the spaces or replace the spaces with underscores.
Procedure
1. Mount the ISO by either attaching to the media image or mounting the image. For Windows 2008 and
Windows 7, use -t udf mount type and do not include any spaces in the path. For all other Windows,
use loopback. For example, $ mount -oloop /<iso_file.iso> /<mount point>
NOTE Do not use -t iso9660 when mounting the image. Some automounted media will not import. If
you receive a fingerprint error message during basicimport, unmount the directory and manually
mount it without the -t iso9660 option.
2. Log in as vcmuser.
3. For your first import, type the command:
# basicimport -d /mnt/<directory name> -l <OS Provisioning Server IP address>
NOTE Changing the OS Provisioning Server IP address at a later time is not currently supported. If the
initial IP address of the OS Provisioning Server after install is not the address you intend for it to have
when it is put into production, you must change its address, and related DHCP and TFTP
configurations, before you import any OS distributions.
For subsequent imports, the -l option is not necessary:
# basicimport -d /mnt/<directory name>/
Where the <directory name> is the file name. For example, Win2k3SE-R2-SP2-i386. If you created a
/tmp/ directory for a multi-CD distribution, include the path. For example /tmp/<directory name>, or
/tmp/Win2003-R2-SP2-Standard.
4. Type the Family Name.
For example, Windows. You must provide a unique family name to perform the basicimport of
different operating systems in the same family. No other family can exist with the same combination
of name, version, and architecture values.
5. Type the Family Version.
For example, 2008R2.
6. Type the Family Architecture, either i386 or x86_64
7. Type the Provenance.
For example, CD, hotfix, or SP.
30 VMware, Inc.
Page 31

Installing and Configuring the OS Provisioning Server and Components
8. The script runs as follows with a specific example:
Importing data into repository...
Importing source data...
No recipes are accessible.
Adding new recipe WINSERVER2003_std_r2_sp2BasicRecipe-2
Creating UCI WINSERVER2003_std_r2_sp2-BasicUCI.
Attaching UCI WINSERVER2003_std_r2_sp2-BasicUCI to recipe 2.
UCI WINSERVER2003_std_r2_sp2-BasicUCI is attached to recipe 2.
Updating the Summary data...
Import Linux/ESX Distributions
Distributions are the operating system installation files. You must import each OS distribution into the OS
Provisioning repository before you can use VCM to install it on target machines.
NOTE Importing distributions with spaces in the file name is not supported. Before importing, remove
the spaces or replace the spaces with underscores.
Linux, or ESX distributions use the following procedure. The SUSE distribution is issued on multiple DVDs;
however, only the first disk is required and must be imported using the following procedure.
Procedure
1. On the OS Provisioning Server, log in as vcmuser.
2. For your first import, type the command:
# basicimport -i <distribution name>.iso -l <OS Provisioning Server IP
address>
NOTE Changing the OS Provisioning Server IP address at a later time is not currently supported. If the
initial IP address of the OS Provisioning Server after install is not the address you intend for it to have
when it is put into production, you must change its address, and related DHCP and TFTP
configurations, before you import any OS distributions.
For subsequent imports, the -l option is not necessary:
# basicimport -i <distribution name>.iso
Where the <distribution name> is the iso file name. For example, ESX-4.0.0-update01-208167.
3. Type the Family Name.
For example, ESX. You must provide a unique family name to perform the basicimport of different
operating systems in the same family. No other family can exist with the same combination of name,
version, and architecture values.
4. Type the Family Version.
For example, 4.0ul.
5. Type the Family Architecture, either i386 or x86_64.
6. Type the Provenance.
For example, CD, hotfix, or SP.
VMware, Inc. 31
Page 32

vCenter Configuration Manager Installation and Getting Started Guide
7. The script runs as follows:
Importing data into repository...
Importing source data...
No recipes are accessible.
Adding new recipe ESX4.0ulBasicRecipe-2
Creating UCI ESX4.0ul-BasicUCI.
Attaching UCI ESX4.0ul-BasicUCI to recipe 2.
UCI ESX4.0ul-BasicUCI is attached to recipe 2.
Updating the Summary data...
#
basicimport Command Options
Use the basicimport command line options to import UNIX, Linux, ESX, or Windows distributions into
the OS Provisioning repository.
Table 3-1. basicimport Command Options
Option Description
-h Help. Displays the basicimport options.
-d Directory. Path to the media source directory. A required option when importing OS distributions
-i ISO file. Path and image name for the distribution. Used with importing distributions issued on one
-l IP address of the OS Provisioning Server.
-n Family name. For example, ESX or Windows.
-V Family version. For example, 4.0u1 or 2008r2sp2.
-a Family Architecture. For example, i386 or x86_64.
-p Provenance. Distribution source. For example, CD, hotfix, or SP.
issued on more than one media item, such as multiple DVDs.
media source, such as a Red Hat distribution on a single DVD.
Configuring the OS Provisioning Server Integration with the VCM Collector
Stunnel is used to establish secure communication between VCM and the OS Provisioning Server SOAP
services. Use the following procedures, which include configuration information, to securely set up the
Stunnel channel. These procedures assume the following:
32 VMware, Inc.
Page 33

Installing and Configuring the OS Provisioning Server and Components
n
All private keys are RSA keys.
Certificates are created or obtained, and copied to the required locations using industry best practices.
n
On the VCM Collector:
Copy certificate to c:\Program Files (x86) \VMware\VCM\Tools\sTunnel\certs\vcm_stunnel_
cert.pem.
Copy private key to c:\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\vcm_stunnel_
pk.pem.
n
On the OS Provisioning Server: Copy certificate to /opt/FastScale/var/certs/vcm_stunnel_cert.pem
n
All directories where these keys and certificates are stored are appropriately secured.
Configure Stunnel on the OS Provisioning Server
Stunnel is used to establish secure communication between VCM and the OS Provisioning Server SOAP
services. On the OS Provisioning Server, you copy the certificates to the locations specified in the
stunnel.conf file.
Procedure
1. Log into the OS Provisioning Server as root.
2. Place the VCM stunnel certificate validation chain in /opt/FastScale/var/certs as described in
/opt/FastScale/etc/stunnel.conf.
All of the files in this directory are owned by root and have permissions of -rw-r--r--.
The stunnel configuration file on the OS Provisioning Server is
/opt/FastScale/etc/stunnel.conf.
; stunnel configuration file for server proxy
; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
; debug = 7
cert = /opt/FastScale/var/certs/service.pem
key = /opt/FastScale/var/certs/private/service.key
; Either CAfile or CAPath, but not both, should be defined
; CAfile = /opt/FastScale/var/certs/ca-cert.pem
; Certificate Authority directory
; This is the directory in which stunnel will look for certificates
when using the verify.
; Note that the certificates in this directory should be named
; XXXXXXXX.0 where XXXXXXXX is the hash value of the DER encoded
subject of the
; cert (the first 4 bytes of the MD5 hash in least significant byte
order).
VMware, Inc. 33
Page 34

vCenter Configuration Manager Installation and Getting Started Guide
; The hash can be obtained with the command: openssl x509 -noout -in
cert.pem -hash
CApath = /opt/FastScale/var/certs
client = no
foreground = no
output = /opt/FastScale/logs/stunnel.log
pid = /opt/FastScale/logs/stunnel.pid
[fsmesgds]
accept = 40610
connect = localhost:21310
; Authentication stuff
verify = 3
[fsrepods]
accept = 40607
connect = 127.0.0.1:21307
; Authentication stuff
verify = 3
3. Restart stunnel.
service FastScale restart
What to do next
After configuring the Stunnel on the OS Provisioning server, you must configure the communication on
the VCM Collector. See "Configure Stunnel on the VCM Collector" on page 40.
Configure Stunnel on the VCM Collector
The VCM Collector installation installs Stunnel files to establish secure communication between VCM and
the OS Provisioning Server SOAP services. You perform this configure Stunnel to ensure the connection
on the Collector is operational.
Prerequisites
n
Before placing the VCM Stunnel certificate and the VCM Stunnel private key, you must ensure the
files are secured according to your corporate best practices.
n
Verify that you have a [C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\
directory. If the directory does not exist, create it.
n
Verify that you have a [C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\
directory. If the directory does not exist, create it.
34 VMware, Inc.
Page 35

Installing and Configuring the OS Provisioning Server and Components
Procedure
1. Place the VCM Stunnel certificate in
[C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\vcm_stunnel_cert.pem.
2. Place the VCM Stunnel RSAprivate key in
[C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\vcm_stunnel_pk.pem.
3. Place the OS Provisioning Server Stunnel CA certificate validation chain in the file(s) and directory
specified in the stunnel.conf file.
The VCM Stunnel configuration file on the VCM application server is [C:]\Program Files
(x86)\VMware\VCM\Tools\stunnel.conf.
In Stunnel.conf, you should update the path for cert, key, CAfile or CApath, depending on
where you installed VCM.
cert = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\vcm_stunnel_
cert.pem
key = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\vcm_stunnel_pk.pem
;; Use stunnel in client mode
client = yes
;; FIPS mode can be enabled as desired
fips = no
;; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
;; Either CAfile or CAPath, but not both, should be defined
;; CAfile contains the certificate chains needed to verify the certificates of
remote connections
;CAfile = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\ca-cert.pem
;; CApath = directory
;; Certificate Authority directory
;; This is the directory in which stunnel will look for certificates when
using the verify.
;; Note that the certificates in this directory should be named
;; XXXXXXXX.0 where XXXXXXXX is the hash value of the DER encoded subject of
the
;; cert (the first 4 bytes of the MD5 hash in least significant byte order).
;; The hash can be obtained with the command: openssl x509 -noout -in cert.pem
-hash
CApath = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs
;; Some debugging stuff useful for troubleshooting
;debug = 7
;output = stunnel.log
VMware, Inc. 35
Page 36

vCenter Configuration Manager Installation and Getting Started Guide
;; verify = level
;; level 1 - verify peer certificate if present
;; level 2 - verify peer certificate
;; level 3 - verify peer with locally installed certificate
;; default - no verify
verify = 3
;; limit connections to certain ciphers
ciphers = AES128-SHA:DES-CBC3-SHA :@STRENGTH
;; asm_hostname_or_ip_address must be replaced with the correct value for the
OS Provisioning Server
[fsrepo]
accept = 127.0.0.1:21307
connect = asm_hostname_or_ip_address:40607
4. Update the accept and connect values in the [fsrepo] section.
Value Action
accept = 21307
connect = asm_hostname_or_ip_
address:40607
Update to accept = 127.0.0.1:21307
Update to the hostname or the IP address of the OS
Provisioning Server
5. Run the commands from the Stunnel directory to register and start the Stunnel service.
cd c:\Program Files (x86)\VMware\VCM\Tools\sTunnel
stunnel –install
net start stunnel
What to do next
Verify that the communication between the OS Provisioning server and the VCMCollector is properly
configured. See "Confirm Stunnel Configuration" on page 42.
Confirm Stunnel Configuration
You must confirm that Stunnel communication between the OS Provisioning server and the VCM
Collector is configured and active before provisioning machines.
Prerequisites
n
Configure Stunnel on the OS Provisioning Server as described in "Configure Stunnel on the OS
Provisioning Server " on page 39.
n
Configure Stunnel on the VCMCollector as described in "Configure Stunnel on the VCM Collector" on
page 40.
36 VMware, Inc.
Page 37

Installing and Configuring the OS Provisioning Server and Components
Procedure
1. From the VCM Collector, start Internet Explorer and go to http://localhost:21307/.
If the connection is properly configured, the following message is displayed.
<?xml version="1.0" encoding="UTF-8" ?>
- <SOAP-ENV:Envelope xmlns:SOAP-
ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-
ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:t="urn:types.fastscale.com"
xmlns:dos="urn:bobdos.fastscale.com" xmlns:wsns="http://tempuri.org/wsns.xsd"
xmlns:fst="urn:bob.fastscale.com">
- <SOAP-ENV:Body>
- <SOAP-ENV:Fault>
<faultcode>SOAP-ENV:Client</faultcode>
<faultstring>HTTP GET method not implemented</faultstring>
</SOAP-ENV:Fault>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
If the connection is not working, the page displays Web page not found. Review your Stunnel
configuration files and make any necessary corrections.
Maintaining Operating System Provisioning Servers
The maintenance of the OS Provisioning server includes backing up the repository, restoring the
repository after a disaster or machine failure, and managing system logs.
Backup the OS Provisioning Repository
The OS Provisioning server includes a repository containing your imported OS distributions. To avoid
recreating the distributions if the server fails, you should back up the repository as part of your recovery
plan.
Prerequisites
n
Ensure that you have sufficient disk space available on your machine for the backed up files. Use the du
–sk /opt/FastScale command to check the amount of space used by the OS Provisioning Server
files.
n
Make certain no OS Provisioning actions are currently in progress. The backup process forces all
applications to exit, including OS Provisioning daemons, FSadmin, and FSrepod.
VMware, Inc. 37
Page 38

vCenter Configuration Manager Installation and Getting Started Guide
Procedure
1. Log in as the fsrepo user.
# su - fsrepo
2. Run the backup command to backup the repository files to /temp/fs-backup.
[fsrepo@localhost~]$ mkdir /tmp/fs-backup
[fsrepo@localhost~]$ db2 CONNECT TO FSREPO;
[fsrepo@localhost~]$ db2 QUIESCE DATABASE IMMEDIATE FORCE CONNECTIONS;
[fsrepo@localhost~]$ db2 CONNECT RESET;
[fsrepo@localhost~]$ db2 BACKUP DATABASE FSREPO TO /tmp/fs-backup WITH 2
BUFFERS BUFFER 1024 PARALLELISM 1 COMPRESS WITHOUT PROMPTING;
[fsrepo@localhost~]$ db2 CONNECT TO FSREPO;
[fsrepo@localhost~]$ db2 UNQUIESCE DATABASE;
[fsrepo@localhost~]$ db2 CONNECT RESET;
[fsrepo@localhost~]$ exit
# service FastScale restart
3. Using a backup manager, one that preserves siblings, permissions, and ownership of files, create
backup copies of the required files and directories.
n /opt/FastScale/homebase-server/deployment
n /opt/FastScale/homebase-server/etc/
n /opt/FastScale/homebase-server/keys/
n /opt/FastScale/homebase-server/packages
n /opt/FastScale/homebase-server/profiles
n /opt/FastScale/var/fsadmin/basic
4. Go to /opt/FastScale/homebase-server/bin and run the command to make a snapshot of the
database contents.
./hbs.sh db dump –u admin -p admin <zip file>
Restore the OS Provisioning Repository From Backup
To recover from a OS Provisioning server failure, you reload the databases and restore the files you back
up as part of your recovery plan.
Prerequisites
Verify that the OS Provisioning Server is installed.
Procedure
1. Log in as the fsrepo user.
# su - fsrepo
2. Run the command to restore the database from the backup directory.
[fsrepo@localhost~]$ db2 CONNECT TO FSREPO;
[fsrepo@localhost~]$ db2 QUIESCE DATABASE IMMEDIATE FORCE CONNECTIONS;
38 VMware, Inc.
Page 39

Installing and Configuring the OS Provisioning Server and Components
[fsrepo@localhost~]$ db2 CONNECT RESET;
[fsrepo@localhost~]$ db2 RESTORE DATABASE FSREPO FROM /tmp/fs-backup TAKEN AT
<timestamp> WITH 2 BUFFERS BUFFER 1024 PARALLELISM 1 WITHOUT PROMPTING;
[fsrepo@localhost~]$ db2 CONNECT TO FSREPO;
[fsrepo@localhost~]$ db2 UNQUIESCE DATABASE;
[fsrepo@localhost~]$ db2 CONNECT RESET;
[fsrepo@localhost~]$ exit
3. Restore the required files from the backup location to the OS Provisioning server.
n /opt/FastScale/homebase-server/deployment
n /opt/FastScale/homebase-server/etc/
n /opt/FastScale/homebase-server/keys/
n /opt/FastScale/homebase-server/packages
n /opt/FastScale/homebase-server/profiles
n /opt/FastScale/var/fsadmin/basic
4. Go to /opt/FastScale/homebase-server/bin and run the command to restore the database
snapshot.
./hbs.sh db load –u admin -p admin <zip file>
5. Reboot the OS Provisioning server.
What to do next
After restoring the repository, you must configure the communications. See "Configure Stunnel on the OS
Provisioning Server " on page 39.
Configure Stunnel on the OS Provisioning Server
Stunnel is used to establish secure communication between VCM and the OS Provisioning Server SOAP
services. On the OS Provisioning Server, you copy the certificates to the locations specified in the
stunnel.conf file.
Procedu re
1. Log into the OS Provisioning Server as root.
2. Place the VCM stunnel certificate validation chain in /opt/FastScale/var/certs as described in
/opt/FastScale/etc/stunnel.conf.
All of the files in this directory are owned by root and have permissions of -rw-r--r--.
The stunnel configuration file on the OS Provisioning Server is
/opt/FastScale/etc/stunnel.conf.
; stunnel configuration file for server proxy
; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
; debug = 7
cert = /opt/FastScale/var/certs/service.pem
VMware, Inc. 39
Page 40

vCenter Configuration Manager Installation and Getting Started Guide
key = /opt/FastScale/var/certs/private/service.key
; Either CAfile or CAPath, but not both, should be defined
; CAfile = /opt/FastScale/var/certs/ca-cert.pem
; Certificate Authority directory
; This is the directory in which stunnel will look for certificates
when using the verify.
; Note that the certificates in this directory should be named
; XXXXXXXX.0 where XXXXXXXX is the hash value of the DER encoded
subject of the
; cert (the first 4 bytes of the MD5 hash in least significant byte
order).
; The hash can be obtained with the command: openssl x509 -noout -in
cert.pem -hash
CApath = /opt/FastScale/var/certs
client = no
foreground = no
output = /opt/FastScale/logs/stunnel.log
pid = /opt/FastScale/logs/stunnel.pid
[fsmesgds]
accept = 40610
connect = localhost:21310
; Authentication stuff
verify = 3
[fsrepods]
accept = 40607
connect = 127.0.0.1:21307
; Authentication stuff
verify = 3
3. Restart stunnel.
service FastScale restart
What to do next
After configuring the Stunnel on the OS Provisioning server, you must configure the communication on
the VCM Collector. See "Configure Stunnel on the VCM Collector" on page 40.
Configure Stunnel on the VCM Collector
The VCM Collector installation installs Stunnel files to establish secure communication between VCM and
the OS Provisioning Server SOAP services. You perform this configure Stunnel to ensure the connection
on the Collector is operational.
40 VMware, Inc.
Page 41

Installing and Configuring the OS Provisioning Server and Components
Prerequisit es
n
Before placing the VCM Stunnel certificate and the VCM Stunnel private key, you must ensure the
files are secured according to your corporate best practices.
n
Verify that you have a [C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\
directory. If the directory does not exist, create it.
n
Verify that you have a [C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\
directory. If the directory does not exist, create it.
Procedu re
1. Place the VCM Stunnel certificate in
[C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\vcm_stunnel_cert.pem.
2. Place the VCM Stunnel RSAprivate key in
[C:]\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\vcm_stunnel_pk.pem.
3. Place the OS Provisioning Server Stunnel CA certificate validation chain in the file(s) and directory
specified in the stunnel.conf file.
The VCM Stunnel configuration file on the VCM application server is [C:]\Program Files
(x86)\VMware\VCM\Tools\stunnel.conf.
In Stunnel.conf, you should update the path for cert, key, CAfile or CApath, depending on
where you installed VCM.
cert = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\vcm_stunnel_
cert.pem
key = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\key\vcm_stunnel_pk.pem
;; Use stunnel in client mode
client = yes
;; FIPS mode can be enabled as desired
fips = no
;; Some performance tunings
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
;; Either CAfile or CAPath, but not both, should be defined
;; CAfile contains the certificate chains needed to verify the certificates of
remote connections
;CAfile = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs\ca-cert.pem
;; CApath = directory
;; Certificate Authority directory
;; This is the directory in which stunnel will look for certificates when
using the verify.
;; Note that the certificates in this directory should be named
;; XXXXXXXX.0 where XXXXXXXX is the hash value of the DER encoded subject of
the
VMware, Inc. 41
Page 42

vCenter Configuration Manager Installation and Getting Started Guide
;; cert (the first 4 bytes of the MD5 hash in least significant byte order).
;; The hash can be obtained with the command: openssl x509 -noout -in cert.pem
-hash
CApath = C:\Program Files (x86)\VMware\VCM\Tools\sTunnel\certs
;; Some debugging stuff useful for troubleshooting
;debug = 7
;output = stunnel.log
;; verify = level
;; level 1 - verify peer certificate if present
;; level 2 - verify peer certificate
;; level 3 - verify peer with locally installed certificate
;; default - no verify
verify = 3
;; limit connections to certain ciphers
ciphers = AES128-SHA:DES-CBC3-SHA :@STRENGTH
;; asm_hostname_or_ip_address must be replaced with the correct value for the
OS Provisioning Server
[fsrepo]
accept = 127.0.0.1:21307
connect = asm_hostname_or_ip_address:40607
4. Update the accept and connect values in the [fsrepo] section.
Value Action
accept = 21307
connect = asm_hostname_or_ip_
address:40607
Update to accept = 127.0.0.1:21307
Update to the hostname or the IP address of the OS
Provisioning Server
5. Run the commands from the Stunnel directory to register and start the Stunnel service.
cd c:\Program Files (x86)\VMware\VCM\Tools\sTunnel
stunnel –install
net start stunnel
What to do next
Verify that the communication between the OS Provisioning server and the VCMCollector is properly
configured. See "Confirm Stunnel Configuration" on page 42.
Confirm Stunnel Configuration
You must confirm that Stunnel communication between the OS Provisioning server and the VCM
Collector is configured and active before provisioning machines.
42 VMware, Inc.
Page 43

Installing and Configuring the OS Provisioning Server and Components
Prerequisit es
n
Configure Stunnel on the OS Provisioning Server as described in "Configure Stunnel on the OS
Provisioning Server " on page 39.
n
Configure Stunnel on the VCMCollector as described in "Configure Stunnel on the VCM Collector" on
page 40.
Procedu re
1. From the VCM Collector, start Internet Explorer and go to http://localhost:21307/.
If the connection is properly configured, the following message is displayed.
<?xml version="1.0" encoding="UTF-8" ?>
- <SOAP-ENV:Envelope xmlns:SOAP-
ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-
ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:t="urn:types.fastscale.com"
xmlns:dos="urn:bobdos.fastscale.com" xmlns:wsns="http://tempuri.org/wsns.xsd"
xmlns:fst="urn:bob.fastscale.com">
- <SOAP-ENV:Body>
- <SOAP-ENV:Fault>
<faultcode>SOAP-ENV:Client</faultcode>
<faultstring>HTTP GET method not implemented</faultstring>
</SOAP-ENV:Fault>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
If the connection is not working, the page displays Web page not found. Review your Stunnel
configuration files and make any necessary corrections.
Managing the OS Provisioning Server System Logs
The OS Provisioning server generates the log files in the /opt/FastScale/log directory. You should
monitor the space used and truncate the files if they begin to consume too much disk space on the server.
n
fsadmin.err: Contains messages from the Apache web server.
n
fsadmin.log: Lists internal commands from the Apache web server.
n
FSjobd.log: Contains messages generated during the job build process.
n
FSmesgd.log: Contains messages generated by the message daemon.
n
FSnetfs.log: Contains messages from the FSnetfs service.
n
FSrepod.log: Contains messages generated by the repository database server.
n
php.log: Contains messages from the php interpreter used by the web server and the jobs build
program.
VMware, Inc. 43
Page 44

vCenter Configuration Manager Installation and Getting Started Guide
44 VMware, Inc.
Page 45

Upgrading or Migrating vCenter Configuration Manager
When you migrate vCenter Configuration Manager (VCM), you must consider all aspects of your
environment. Before you install VCM 5.4 and the related components and tools in your enterprise, you
must make sure the Collector machine meets the requirements for the new version.
Upgrade and Migration Scenarios
A migration to VCM 5.4 means you will install a new 64-bit environment, including the operating system,
SQL Server, and SQL Server Reporting Services, and possibly new hardware. Then you will migrate your
existing VCM, SCM, or ECM installation to this new environment. An upgrade uses an existing Collector
installation and upgrades the operating system, SQL Server, and VCM to the versions associated with the
VCM 5.4 release.
Supported migration paths include:
n
Migrate from a 32-bit or 64-bit environment running VCM, SCM, or ECMto VCM 5.4
n
Migrate a split installation to a single-server installation of VCM 5.4
The only supported upgrade path is:
4
n
Upgrade from a 64-bit single-server installation environment running VCM, SCM, or ECMto VCM 5.4
Supported versions for migration include:
n
VMware VCM 5.3 or later
n
EMCIonix SCM 5.0 or later
n
Configuresoft ECM 4.11.1 or later
VMware, Inc. 45
Page 46

vCenter Configuration Manager Installation and Getting Started Guide
Prerequisites
VCM 5.4 now supports 64-bit environments only, which include 64-bit hardware, a 64-bit operating
system, and SQL Server 2008 R2. If you migrate from a 32-bit environment to a 64-bit environment, you
must prepare your 64-bit environment for a VCM installation. For details about configuring a 64-bit
machine as a Collector, see the VCM Hardware and Software Requirements Guide.
Before you migrate to VCM 5.4:
n
Your version of VCM must be VMwareVCM 5.3, EMC Ionix SCM 5.0 or later, or Configuresoft ECM
4.11.1 or later.
n
The current VCM installation must be functional.
n
Back up your content, including databases, the CMFILES$ share, any files used to customize the
Collector, any reports that are exported to a non-default location, and certificates.
n
All running jobs must be complete and jobs must not be scheduled to begin during the migration
process. The migration process stops the SQLAgent service, which prevents any new jobs from
starting.
n
All users must be logged off, and users must not attempt to access VCM for the duration of the
migration process.
n
To simplify the steps to reconfigure scheduled jobs and product logins, download the VCM SQL
Migration Helper Tool from the VMware download site.
n
If you upgrade VCM Remote, and want older agents to function properly, you must use the same
name for the new Remote virtual directory that was used in your previous installation. If you change
the Remote virtual directory name, all corresponding agents must be updated to reflect the new virtual
directory.
n
Your existing environment must include Microsoft .NET Framework required versions.
n
Existing 32-bit environments must include SQL Server 2005 and SP3.
n
Existing 64-bit environments must include 64-bit SQL Server 2005 and SP2 and 32-bit SQL Server
Reporting Services and SSRS SP3. Prior to VCM 5.4, only the 32-bit of SSRS was supported in 64-bit
VCM environments.
CAUTION Before you begin the migration, to avoid any potential loss of data you must back up your
content, including databases, the CMFILES$ share, any files used to customize the Collector, any reports
that are exported to a non-default location, and certificates.
46 VMware, Inc.
Page 47

Back up Your Databases
Back up all of the databases used in your configuration. Depending on which version you migrate, the
database names differ slightly.
Before you migrate from a previous version of VCM, back up these databases:
Table 4-1. Before You Migrate, Back Up Your Databases
If you migrate from Back up these databases
VMware VCM CSI_Domain, VCM, VCM_Coll, VCM_UNIX, ReportServer, master, and msdb
EMC Ionix SCM CSI_Domain, SCM, SCM_Coll, SCM_UNIX, ReportServer, master, and msd b
Upgrading or Migrating vCenter Configuration Manager
Configuresoft ECM
(versions 4.11.1 to 5.0)
CSI_Domain, ECM, ECM_Coll, ECM_UNIX, ReportServer, master, and msdb
Back up Your Files
Back up the entire content of the CMFILES$ share. The default location is C:\Program Files
(x86)\VMware\VCM\WebConsole\L1033\Files\ on 64-bit systems, or C:\Program
Files\VMware\VCM\WebConsole\L1033\Files\ on 32-bit systems.
If your Collector was originally installed as EMC Ionix SCM or as Configuresoft ECM, this default path will
be different.
If you customized the Collector, back up the relevant files.
If you exported reports to a non-default location, back up the relevant files.
Back up Your Certificates
Export and back up your Collector and Enterprise certificates.
Software Supported by the VCMCollector
The migration to VCM 5.4 requires that the VCM Collector be upgraded or migrated to:
n
Windows Server 2008 R2
n
SQL Server 2008 R2
n
SQL Server 2008 R2 Reporting Services
NOTE Because Windows Server 2008 R2 is supported only on 64-bit hardware, if your Collector is
currently installed on a 32-bit platform, see the VCM Hardware and Software Requirements Guide for
information about system specifications.
For a complete list of requirements, see the VCM Hardware and Software Requirements Guide.
For questions about any of the migration procedures, contact VMware Customer Support before you
begin the migration.
VMware, Inc. 47
Page 48

vCenter Configuration Manager Installation and Getting Started Guide
Migration Process
You can migrate these environments to support VCM 5.4:
n
"Migrate a 32-bit environment running VCM 5.3 or earlier to VCM 5.4" on page 50
n
"Migrate a 64-bit environment running VCM 5.3 or earlier to VCM 5.4" on page 51
n
"Migrate a split installation of VCM 5.3 or earlier to a single-server installation" on page 52
To install VCM,you must obtain the installation package from the VMware download site or use the VCM
5.4 CD.
Prerequisites
For a list of prerequisites to install a new Collector, see the VCM Hardware and Software Requirements Guide.
Foundation Checker Must Run Successfully
As part of the migration process, Installation Manager runs Foundation Checker when you install VCM
5.4. Foundation Checker must complete successfully to ensure your machine is ready for the VCM 5.4
migration.
To run Foundation Checker as a standalone utility, see the VCM Hardware and Software Requirements Guide.
If errors occur when you run Foundation Checker, you must resolve the errors using the Foundation
Checker online Help and the VCM Hardware and Software Requirements Guide.
Use the SQLMigration Helper Tool
When you migrate from one of the supported scenarios to VCM 5.4, to simplify the steps to recreate
scheduled jobs and membership logins, use the SQL Migration Helper Tool, which you download from the
VMware Web site.
Migrate Only Your Database
You can migrate the VCM database from version 4.11.1 or later. To migrate the database, you must:
1. Move the database to a prepared machine that has 64-bit SQL Server 2008 R2.
2. Attach the database to SQL Server 2008 R2.
3. Ensure that sa or the VCM service account is the owner of the newly attached database.
4. Install VCM 5.4.
48 VMware, Inc.
Page 49

Upgrading or Migrating vCenter Configuration Manager
Replace your existing 32-Bit Environment with the Supported 64-bit Environment
A 32-bit environment must be functional before you migrate to VCM 5.4. Before you start the migration,
you must:
1. Replace the 32-bit architecture with 64-bit hardware.
2. Install Windows Server 2008 R2.
Prepare the Hardware
To prepare your hardware for the migration to VCM 5.4, you must replace your 32-bit Collector machine
with a 64-bit machine.
Prepare the Software
To prepare your software for the migration to VCM 5.4:
1. Ensure that the existing installation of VCM is version 4.11.1 or later, and if not, use previous version
installation packages and documentation to upgrade the installation to version 4.11.1 or later.
2. Install the supported 64-bit Windows Server 2008 R2 operating system.
Make Sure these Software Components are Installed
Older versions of VMware VCM, EMC Ionix SCM, and Configureoft ECM supported older versions of
SQL Server. To migrate a 32-bit environment to VCM 5.4, the 32-bit environment must include these
components, which must be installed in this order:
n
SQL Server 2005
n
32-bit version of SQL Server Reporting Services
n
SQL Server 2005 SP3
n
VMware VCM 5.3, EMC Ionix SCM 5.0 or later, or Configuresoft ECM 4.11.1 or later
How to Recover Your Machine if the Migration is not Successful
If the migration is not successful, you must:
n
Reinstall the versions of software that were installed on the machine before you started the migration.
n
Reconnect the databases from your backed up copies.
n
Recopy the files to the CMFILES$ share.
Before you attempt to migrate to VCM 5.4 again, contact VMware Customer Support to help you identify
the causes of an unsuccessful migration. For questions about any of the migration procedures, contact
VMware Customer Support.
VMware, Inc. 49
Page 50

vCenter Configuration Manager Installation and Getting Started Guide
Migrate a 32-bit environment running VCM 5.3 or earlier to VCM 5.4
Your 32-bit environment must be functional before you migrate to VCM 5.4.
CAUTION Before you begin the migration, to avoid any potential loss of data you must back up your
content, including databases, the CMFILES$ share, any files used to customize the Collector, any reports
that are exported to a non-default location, and certificates.
Procedure
1. Install Windows Server 2008 R2 on the machine that is to be the new 64-bit VCM Collector.
2. Install SQL Server 2008 R2.
3. Stop the VCM services, including the VCM Collector and VCM Patch Management services.
4. Use the SQL Migration Helper Tool to script any scheduled jobs on your old Collector so that you can
import them into the new Collector.
5. Use the SQL Migration Helper Tool to build a script that contains the existing login and role
membership information on the old Collector so that you can import the membership information
into the new Collector.
6. Detach the databases.
7. Attach or restore the VCM databases to SQL Server 2008 R2 on the new Collector.
8. Make sure that the owner for the restored or attached databases is sa or the VCM service account.
(Optional) Use the built-in sp_changedbowner stored procedure to change the ownership of the
databases.
9. Start the VCM 5.4 installation and select the Install option.
Make sure all of the components are marked for installation. If a component cannot be upgraded, the
check box is cleared and a note appears indicating the reason. This situation can occur due to an invalid
upgrade or an incomplete copy of the install image.
At the start of the installation, Foundation Checker will gather information about the machine to
prepare it for the installation. For the upgrade to proceed, the results must be successful. If the system
checks encounter errors, you must resolve the errors before you proceed.
CAUTION When you begin the VCMinstallation, do not select the Repair option unless you are
directed by VMware Customer Support. The repair process requires access to your original
installation media to check for missing files and settings, and replaces them.
10. During the installation, select the existing databases to migrate them to VCM 5.4, and follow the
wizard to complete the upgrade. If you arrive at a step where the installation wizard asks you to create
a new database, back out of this wizard and ensure that you have selected your existing database that
you attached in the step above.
11. During the installation, do not select SSL unless your machine is already configured for SSL.
12. After the upgrade completes, copy the contents of WebConsole\L1033\Files from the previous
Collector so that any remote commands, and discovery and imported template files, will be available
on the new Collector.
13. On the Collector, run the script you created to import VCM scheduled jobs.
14. On the Collector, run the script you created to import VCM membership logins.
15. Re-import any custom SSRS report RDL files.
50 VMware, Inc.
Page 51

Upgrading or Migrating vCenter Configuration Manager
For information about the sp_changedbowner stored procedure, see SQL Server 2008 R2 Books Online.
Migrate a 64-bit environment running VCM 5.3 or earlier to VCM 5.4
An existing 64-bit Collector can be migrated to VCM 5.4. In the migration, you install a new system, copy
over the VCM database and other components, and then install VCM 5.4 pointing to the existing database
so that its configuration is preserved and its structure is updated.
Use this option when you want to refresh or replace the VCM hardware as part of the VCM 5.4
installation process, to change editions of the operating system, or if a fresh install of the operating system
is preferred over an upgrade.
Your existing 64-bit environment must be functional before you migrate to VCM 5.4.
CAUTION Before you begin the migration, to avoid any potential loss of data you must back up your
content, including databases, the CMFILES$ share, any files used to customize the Collector, any reports
that are exported to a non-default location, and certificates.
Procedure
1. Install Windows Server 2008 R2 on the machine that is to be the new 64-bit VCM Collector.
2. Install SQL Server 2008 R2.
3. Stop the VCM services, including the VCM Collector and VCM Patch Management services.
4. Use the SQL Migration Helper Tool to script any scheduled jobs on your old Collector so that you can
import them into the new Collector.
5. Use the SQL Migration Helper Tool to build a script that contains the existing login and role
membership information on the old Collector so that you can import the membership information
into the new Collector.
6. Detach the databases.
7. Attach or restore the VCM databases to SQL Server 2008 R2 on the new Collector.
8. Make sure that the owner for the restored or attached databases is sa or the VCM service account.
(Optional) Use the built-in sp_changedbowner stored procedure to change the ownership of the
databases.
9. Start the VCM 5.4 installation and select the Install option.
Make sure all of the components are marked for installation. If a component cannot be upgraded, the
check box is cleared and a note appears indicating the reason. This situation can occur due to an invalid
upgrade or an incomplete copy of the install image.
At the start of the installation, Foundation Checker will gather information about the machine to
prepare it for the installation. For the upgrade to proceed, the results must be successful. If the system
checks encounter errors, you must resolve the errors before you proceed.
CAUTION When you begin the VCMinstallation, do not select the Repair option unless you are
directed by VMware Customer Support. The repair process requires access to your original
installation media to check for missing files and settings, and replaces them.
10. During the installation, select the existing databases to migrate them to VCM 5.4, and follow the
wizard to complete the upgrade. If you arrive at a step where the installation wizard asks you to create
a new database, back out of this wizard and ensure that you have selected your existing database that
you attached in the step above.
VMware, Inc. 51
Page 52

vCenter Configuration Manager Installation and Getting Started Guide
11. During the installation, do not select SSL unless your machine is already configured for SSL.
12. After the upgrade completes, copy the contents of WebConsole\L1033\Files from the previous
Collector so that any remote commands, and discovery and imported template files, will be available
on the new Collector.
13. On the Collector, run the script you created to import VCM scheduled jobs.
14. On the Collector, run the script you created to import VCM membership logins.
15. Re-import any custom SSRS report RDL files.
Migrate a split installation of VCM 5.3 or earlier to a single-server
installation
A split installation is a previously supported configuration of VCM, where all of the databases except the
main Collector database reside on a database server machine that is physically separate from the VCM
Collector machine. In a split installation, the databases are located on two machines:
n
Collector machine. Includes the VCM_Coll database only.
n
Database Server machine. Includes the VCM, VCM_UNIX, ReportServer, master, and msdb databases.
If your previous environment was a split installation, you must migrate to a single-server installation for
VCM 5.4. A single-server installation places all of the databases on the Collector machine.
CAUTION Before you begin the migration, to avoid any potential loss of data you must back up your
content, including databases, the CMFILES$ share, any files used to customize the Collector, any reports
that are exported to a non-default location, and certificates.
To migrate a split installation to a single-server installation, during the installation you must select to attach
the databases from the Database Server to SQL Server 2008 R2. See "Migrate a 32-bit environment running
VCM 5.3 or earlier to VCM 5.4" on page 50 for instructions.
After You Migrate VCM
After you migrate VCM:
n
Import custom SRS reports.
n
Import dashboard RDLs.
n
If you did not use the SQL Migration Helper Tool, recreate your scheduled jobs and VCM user accounts
and logins.
n
Configure the SQL Server settings, including the VCM database file growth and database recovery
settings to fine-tune your VCM database, as described in the chapter on maintaining VCMafter
installation.
Upgrade Process
You can upgrade your 64-bit environment that is running VCM 5.3 or earlier to VCM 5.4. Before starting
an upgrade, you should perform the backup tasks mentioned in the prerequisites of this section, and you
must verify that your existing Collector system meets the hardware requirements from the VCM
Hardware and Software Requirements Guide.
To upgrade VCM,you must obtain the installation package from the VMware download site or use the
VCM 5.4 CD.
52 VMware, Inc.
Page 53

Upgrading or Migrating vCenter Configuration Manager
To upgrade to VCM 5.4:
1. Upgrade the operating system to Windows Server 2008 R2.
2. Uninstall the 32-bit version of SQLServer Reporting Services (SSRS) 2005.
3. Upgrade SQL Server 2005 to SQL Server 2008 R2.
4. Run the SQL Server 2008 R2 installation again to add SQLServer Reporting Services 2008.
5. Select Start > All Programs >Microsoft SQLServer 2008 R2 > Configuration Tools > Reporting
Services Configuration Manager and configure SSRS 2008 to use the existing ReportServer database.
a. Select to use the existing ReportServer database.
b. Configure the Web Service and Report Manager URLs.
c. Use the Encryption Keys option to delete encrypted content so that the new installation of SSRS
can use the existing SSRS database.
6. Run the VCM Installation Manager to upgrade the existing VCM installation to version 5.4.
After the installation completes, log in and begin using VCM.
After You Upgrade VCM
After you upgrade VCM, configure the SQL Server settings, including the VCM database file growth and
database recovery settings to fine-tune your VCM database, as described in the chapter on maintaining
VCM after installation.
Upgrading Existing Windows Agents
Use the Upgrade Agent wizard to upgrade the Agent files on one or more machines.
To upgrade an Agent:
1. Click Administration > Machines Manager > Licensed Machines > Licensed Windows Machines.
2. Select the machine or machines you are upgrading, and then click the Upgrade Agent icon on the
Licensed Windows Machines toolbar. The Machines page appears.
3. Select a machines option.
Option Defin ition
All machines Upgrade the Agent on all machines that appear in the list of licensed
machines.
Filtered
machines only
Selected
machine(s)
only
4. Click Next. The Install Options page appears.
5. In the Install From field, select or verify the necessary information. Note that vCenter inspections will
not work until you deploy the VCM5.4 agent on the vCenter server system(s).
This option is available only if the Licensed Machines list is being filtered.
Upgrade the Agent on all machines that appear in the filtered list of
machines.
Upgrade the Agent only on select individual machines. Use the standard
selection method to select individual machines.
The default source of the Agent files is the Collector machine. If you have created an Alternate
Source, you can select it from the drop-down list.
The Upgrade process:
VMware, Inc. 53
Page 54

vCenter Configuration Manager Installation and Getting Started Guide
n
Will fail for any machine on which an Agent does not already exist.
n
Will use an Agent's current settings. For example, if the Agent uses DCOM, the Upgrade will
maintain that setting, or if the Agent uses HTTP on Port 26542 the Upgrade will maintain that
setting.
n
Will not upgrade components that do not require upgrading.
6. Click Next. The Schedule page appears.
7. Schedule the operation. You can enter the Date in the specified format or click the Calendar icon.
8. Click Next. The Important page appears.
9. Verify the actions that will be performed and then click Finish.
Upgrading Existing Remote Clients
VMware recommends that you upgrade your Remote client versions. When the automatic upgrade
setting (Will Remote automatically upgrade old Remote clients) is set to Yes, the next client-server
contact automatically downloads and installs the upgrade files.
If the Remote client does not have a certificate, the upgrade process will automatically extract the
certificate and send it to the client, along with the new Agent.
To automatically upgrade your remote clients:
1. Click Administration > Settings > General Settings > VCM Remote.
2. Select Will Remote automatically upgrade old Remote clients.
3. Click Edit Setting. The Edit Setting wizard appears.
4. Change the setting to Yes.
5. Click Next. The confirmation page appears.
6. Click Finish. The setting change is saved.
Upgrading Existing UNIX Agents
Upgrade packages are available to update the UNIX Agents on various platforms. To upgrade the UNIX
Agents to the latest software release, use one of these methods:
n
Upgrade the UNIX Agent(s) with the Local Package
n
Upgrade the UNIX Agent(s) with a Remote Package
VCM supports TLS for UNIX/Linux. For more information, see the VCM TLS Implementation white
paper, posted on the Download VMware vCenter Configuration Manager.
If you install the Agent on HP-UX 11.11, you must also install Patch PHSS_30966, which is required. If you
need assistance, contact VMware Customer Support.
Upgrading Red Hat Workstations
In previous versions of VCM, either Red Hat workstations or servers were licensed as Red Hat servers.
Beginning with VCM version 5.2.0, Red Hat machines were licensed as either workstations or servers.
When you upgrade to 5.2.0 or later, the workstations previously managed with server licenses will be
unmanaged in VCM. The unmanaged Red Hat workstations should be listed in the Available UNIX
Machines list. To manage the machines in VCM, select Administration > Machines Manager > Available
Machines > Available UNIX Machines and re-license the machines using Linux/Mac Workstation licenses.
If you are not able to identify your unmanaged Red Hat machines, contact VMware Customer Support.
54 VMware, Inc.
Page 55

Upgrading or Migrating vCenter Configuration Manager
Platforms Not Supported for Upgrade to 5.4 Agent
Installing or upgrading on the following platforms is supported only to the 5.1.3 UNIX Agent. You can
install the 5.4 Agent. However, these platforms are not tested with any additional 5.4 functionality.
Platform Supp orted Agent Version Agen t File Name
AIX 4.3.3 5.1.3 CMAgent.5.1.0.AIX.4
Red Hat 2.1 5.1.3 CMAgent.5.1.0.Linux.2.1
Solaris 2.5 5.1.3 Contact VMware Customer Support if you are
installing or upgrading the Agent on this
platform.
Solaris 2.6 5.2.1 Contact VMware Customer Support if you are
installing or upgrading the Agent on this
platform.
To Upgrade the UNIX Agent(s) with a Local Package
To upgrade the UNIX Agent(s) using the local upgrade package, follow these steps:
1. Locate the AgentUpgradeLocal.sh file in \Program Files
(x86)\VMware\VCM\WebConsole\L1033\Files\UNIX_Remote_Command_Files.
2. Open the AgentUpgradeLocal.sh file with a text editor like Wordpad.
3. In the AgentUpgradeLocal.sh file, locate the following entry:
CSI_INSTALL_PACKAGE_LOCATION = CHANGE_THIS_TO_A_LOCAL_OR_NFS_DIRECTORY
4. Change this entry to point to either a local directory or an NFS directory where the VCM Agent Install
Packages are located (for example, /tmp/VCMu_Agent).
Agent install packages are installed on the Collector machine at \Program Files
(x86)\VMware\VCM\Installer\Packages.
5. Save and close the AgentUpgradeLocal.sh file.
6. Log into VCM and open the Console slider. Navigate to Console > UNIX Remote Commands >
UNIX Agent Upgrade. The UNIX Agent Upgrade data grid appears.
7. Select Agent Upgrade - Local Package.
8. Click Run. The Remote Commands wizard appears.
9. Select the machine(s) on which you want to upgrade the agent.
To determine which Agent is currently on a UNIX machine, navigate to Administration > Machines
Manager > Licensed Machines > Licensed UNIX Machines. To determine the latest version number
for the Agent, select About > Versions.
10. Click the arrow button to move the machines from the Available list to the Selected list. Click Next.
11. Select whether you want to upgrade the Agent now or later. To change the date, click the Calendar
icon. When you schedule the action, it is placed in the Administration > Job Manager > Scheduled list.
The Time of Day settings you choose are based on your User time zone. All VCM jobs run based on
the VCM Database time zone. You must account for the time and date differences between your VCM
User time and your VCM Database time. For example, if your VCM Database server is in the Eastern
time zone, and your VCM User is in the Pacific time zone, to run your job at midnight, you would
enter 9 PM.
12. Click Next, and then click Finish.
VMware, Inc. 55
Page 56

vCenter Configuration Manager Installation and Getting Started Guide
To Upgrade the UNIX Agent(s) with a Remote Package
This method sends the upgrade package with the remote command to execute on the UNIX machine. The
following remote upgrade packages are designed specifically for the various operating systems where the
Agent(s) can be upgraded:
n
AIX 4.3.3 Agent Upgrade (use only CMAgent.5.1.0.AIX.4)
n
AIX 5 Agent Upgrade
n
HP-UX (Itanium) Agent Upgrade
n
HP-UX (PA-RISC) Agent Upgrade
n
Red Hat Enterprise 2.1 Agent Upgrade (use only CMAgent.5.1.0.Linux.2.1)
n
Red Hat Enterprise 3.0, 4.0, 5.0, 5.1, 5.2, SUSE Enterprise 9 and above Agent Upgrade
n
Solaris (SPARC) Agent Upgrade
n
Solaris (x86) Agent Upgrade
To upgrade the UNIX Agent(s) using one of the remote upgrade packages, follow these steps:
1. Select Console > UNIX Remote Commands > UNIX Agent Upgrade. The UNIX Agent Upgrade data
grid appears.
2. Click to highlight the remote upgrade package that is appropriate for the operating system and
version of the machine(s) that you want to upgrade.
3. Click Run and follow the wizard instructions to send the remote command and the upgrade package
to the Agent(s) on the selected machine(s). The Agent will then execute the upgrade package.
Because the UNIX Agents are using TLS, the Enterprise Certificate is embedded in the Agent package. If
multiple Collectors need to talk to a single Agent, all of the Collectors should share an Enterprise
Certificate. If the Collectors have different Enterprise Certificates, the Enterprise Certificate from each
Collector must be uploaded to the Agent. For more information, see the VCM TLS Implementation white
paper, located on the Download VMware vCenter Configuration Manager.
Upgrading VCM for Virtualization
When upgrading vCenter collections, you must install the VCM 5.4 Agent or later on the Windows
machines running vCenter. For more information, see "Configuring vCenter Server Data Collections" on
page 135.
When upgrading a Collector to VCM 5.4, the Agent Proxy on the Collector is automatically upgraded,
and the Agent Proxy protected storage and user account configuration settings are preserved. However,
for existing non-Collector Agent Proxy machines, you must upgrade VCM for Virtualization and select to
retain the Secure Communication settings.
To upgrade the VCM for Virtualization Agent Proxy on non-Collector machines, you must use one of
these methods, depending on your configuration:
n
Manually Upgrade VCM for Virtualization on a non-Collector Agent Proxy Machine
n
Use VCM to Upgrade VCM for Virtualization on a non-Collector Agent Proxy Machine
56 VMware, Inc.
Page 57

Upgrading or Migrating vCenter Configuration Manager
CAUTION When upgrading VCM for Virtualization, take the following precautions:
Do not change the password for the CSI Communication Proxy service. Doing so may require the Agent
Proxy to be reinstalled and reconfigured.
Avoid installing the Agent Proxy and the Active Directory product on the same machine. The operations
involved to install, uninstall, upgrade, and reinstall these products may result in the Agent Proxy needing
to be reinstalled and reconfigured.
If you plan to uninstall VCM for Virtualization manually, make sure that you execute
RetainSecureCommSettings.exe before uninstalling it. Otherwise, the Agent Proxy configuration settings
will be removed, and the Agent Proxy will need to be reconfigured. The RetainSecureCommSettings.exe is
located at: C:\Program Files (x86)\VMware\VCM\Installer\Packages, or in the path relative to
where you installed the software.
Platform Not Supported for Upgrade to 5.4 Agent Proxy
You can install or upgrade an Agent Proxy machine only to the 5.1.3 Agent if it is collecting from this
platform. This platform is not tested with the 5.4 functionality.
Platform Suppo rted Agent Version Agen t File Name
ESX 2.5 5.1.3
Upgrading an Agent Proxy Machine
If a new version of the Agent Proxy becomes available, the upgrade process installs the newer version on
your agent proxy machine.
1. Click Administration > Machines Manager > Additional Components > VCM for Virtualization >
Agent Proxies. The Agent Proxies data grid appears.
2. Select the machine or machines on which you are upgrading the Agent Proxy.
3. Click Upgrade. The Machines page of the Upgrade Agent Proxies wizard appears.
4. The available machines are displayed in the upper list. The selected machines are displayed in the lower
list. You can perform these actions:
n
All Machines: Selects the option to run the process on all eligible machines.
n
Selected Machines Only: (Default option) Selects the option to run the process on all machines
listed in the lower pane.
n
Filtered Machines: Click Define to create a filter based on Machine Name or Domain Name, and
then select the Filtered Machines option.
n
Arrow buttons: Selects a machine name in one of the panes and use the arrow buttons to move it
from one pane to the other. Additionally, you may double-click a machine name to move it
between panes.
5. Click Next. The Option page appears.
6. Configure the following options:
n
Install From: In the drop-down list, select the name of the Collector used to manage virtual
machines.
n
Schedule: Select Run Action now to install immediately, or select Schedule the Action to run
later and configure the settings to run at a designated time.
VMware, Inc. 57
Page 58

vCenter Configuration Manager Installation and Getting Started Guide
7. Click Next. The Important page appears. Review the contents, click Back to make any necessary
alterations.
8. Click Finish. The Agent Proxy is upgraded at the time specified.
9. To verify the completion of the upgrade process, click Jobs on the Portal toolbar to access the Jobs
Summary. You can also verify jobs for the past 24 hours if you think that you may have missed it. Go
to Administration > Job Manager > History > Other Jobs > Past 24 Hours.
Manually Upgrading an Agent Proxy Machine
The steps in this section provide an optional upgrade method if you choose not to use the Upgrade option
in VCM. To manually upgrade an Agent Proxy machine, you must have already upgraded your Collector
machine to VCM 5.4. Then you will uninstall the VCM Agent, select to retain the Secure Communication
settings, install the VCM Agent (version 5.4), and then install VCM for Virtualization, as described in these
steps.
1. The following executable must be accessible from your non-Collector Agent Proxy Machine. The path
to this file on the Collector machine is as follows, or is in the path relative to where you installed the
software.
C:\Program Files (x86)\VMware\VCM\AgentFiles\CMAgentInstall.exe
Execute CMAgentInstall.exe on your Agent Proxy machine.
2. The installer detects the previous version of VCM, and then requests permission to uninstall it. Select
Yes.
3. The installer detects that Secure Communication is installed, and requests whether you want to retain
your settings. Select Yes. The installer proceeds to remove the VCM Virtualization product and VCM
Agent from your Agent Proxy machine. During this process, your Secure Communication settings are
retained.
4. When the installer displays the license agreement, read and accept the conditions.
5. The installer prompts whether to perform the installation of the VCM Windows Agent in HTTP mode.
Allowing HTTPcommunication will allow the Agent to communicate through the HTTP port specified
if DCOM is not available. Locking an Agent will prevent the Agent from being removed or upgraded.
To use this mode, select Allow HTTP and click Next.
58 VMware, Inc.
Page 59

Upgrading or Migrating vCenter Configuration Manager
6. The installer proceeds with the installation. When the VCM Windows Agent has been successfully
installed, click Finish.
7. Copy the following executable from your upgraded Collector machine to any location on your nonCollector Agent Proxy machine. The path to this file on the Collector machine is as follows, or is in the
path relative to where you installed the software.
C:\Program Files
(x86)\VMware\VCM\AgentFiles\Products\VirtualizationProductInstall.exe
Run VirtualizationProductInstall.exe on your non-Collector Agent Proxy machine. This step
begins the installation of VCM for Virtualization.
8. Proceed through the installation screens to install VCM for Virtualization.
9. The installer proceeds to install VCM for Virtualization. When VCM for Virtualization has installed
successfully, click Finish. You can now begin collecting using your upgraded Agent Proxy.
NOTE If you have previously used this Agent Proxy to perform a collection from your upgraded
Collector, the first collection may fail due to a password encryption issue. If so, try resetting the VM
Host password at Administration > Machines Manager > Additional Components > VCM for
Virtualization > Licensed VM Hosts. You may set the password for multiple hosts at the same time if
desired.
All VCM-managed Windows machines will include the VCM Agent extension for VCM Provisioning,
which is a separate installation.
For Agent Proxy machines, if the Virtualization proxy and VCM Agent extensions for Provisioning are
installed, you must run ProvisioningProductInstall.exe from the Collector.
Upgrade the vSphere Client VCM Plug-In
Upgrading the plug-in is necessary only if you have a vSphere Client VCM Plug-In version 5.3 or earlier,
or if the URL to the VCM instance has changed.
Prerequisites
Unregister the previous version of the vSphere Client VCM Plug-In. See "Unregister the Previous Version
of the vSphere Client VCM Plug-In" on page 146.
Procedure
1. Upgrade VCM.
What to do next
Register the new vSphere Client VCM Plug-In by following the instructions in "Register the vSphere Client
VCM Plug-In" on page 143.
Unregister the Previous Version of the vSphere Client VCM Plug-In
You must unregister a previous version of the vSphere Client VCM Plug-In before you can upgrade to the
new version provided when you upgraded VCM. The upgrade to VCM removes files for the previous
plug-in and installs the new plug-in files in new locations and with new names, but it does not register the
new plug-in with the vSphere Client.
VMware, Inc. 59
Page 60

vCenter Configuration Manager Installation and Getting Started Guide
Procedu re
1. Go to https://vCenter machine name/mob/?moid=ExtensionManager.
vCenter machine name represents the name of your vCenter Server 4.0 instance.
2. In the Methods area, click the UnregisterExtension link.
3. Type the string value for extensionKey:
com.CM.VirtualCenterCompliancePlugIn
4. Click Invoke Method.
The plug-in is unregistered.
60 VMware, Inc.
Page 61

Getting Started with VCM Components and Tools
This chapter covers global getting started procedures for VCM and all of its components and tools. After
completing this chapter, proceed to the specific getting started chapters that apply to the components you
have licensed and the VCM tools you plan to use. The remaining getting started chapters build on this one.
Therefore, you should have a solid understanding of the content in this chapter before you proceed to the
remaining chapters.
This chapter describes:
l
Understanding User Access
l
Launching and Logging onto VCM
l
Getting Familiar with the Portal
l
Where to Go Next
Understanding User Access
After your installation is complete, the user who performed the installation is explicitly granted access and
is placed in the roles of ADMIN and USER. This user is also placed into the Admin role. Hence, this user
can immediately log in using the Admin role. The role of AD_Admin allows full administration access to
AD objects only.
5
Other user accounts can then be added after the Admin user logs in by going to Administration > User
Manager > VCM Logins. For instructions on how to add user accounts, see the online Help.
Whenever a user is either added to the Admin role in VCM, or granted access to the Administration >
User Manager node, the user is placed in the fixed machine roles Security Administrators and Bulk Insert
Administrators Groups. They are also added to the database roles public, ADMIN, and User on the VCM
Database.
Users who will not have access to the Administration > User Manager node will be assigned to public.
Depending on the functions granted to any particular user, more or fewer privileges may be needed in
order for their role to function properly.
VMware, Inc. 61
Page 62

vCenter Configuration Manager Installation and Getting Started Guide
All VCM user accounts must have the following rights on the VCM Collector machine:
n
Ability to log on locally to access IIS.
n
Read access to the System32 folder.
n
Write access to the CMFiles$\Exported_Reports folder for exporting reports.
n
If default permissions have been changed, read access to the C:\Program Files
(x86)\VMware\VCM\WebConsole directory, along with all subdirectories and files. In addition, any
users who will be adding machines to VCM from a file or through the Add Machines action on
Available Machines will need write access to CMFiles$\Discovery_Files.
Do Not Use the Collector as a Web Console
By default for localhost, Internet Explorer on Windows Server 2008 R2 runs with Protected Mode enabled.
If you are logged in as an Administrator, because Protected Mode is enabled, problems can occur with the
SQLServer Reporting Service (SSRS) Web service interface components such as dashboards and node
summaries, or when using the License Manager Click Once application.
When you update a VCM license using the License Manager application from the Collector's Web console,
you must run Internet Explorer as administrator.
CAUTION Although you should not use the Collector as a Web console, to restore the SSRS and License
Manager functionality you can run Internet Explorer as administrator or disable Protected Mode for the
zone of the Collector (localhost). If you perform either of these actions, you must take additional
precautions to protect the Collector because of the increased exposure to attacks on the Collector through
the Web browser, such as cross-site scripting.
Starting and Logging Onto VCM
If you have not already started VCM after closing Installation Manager, follow the procedure detailed
below to start and log onto VCM.
IMPORTANT Before you start VCM, you must either configure Internet Explorer Pop-up Blocker Settings
to add your Collector to your list of allowed web sites, or disable Pop-up Blocker. Click Internet Explorer
> Tools > Popup Blocker Settings and then add the path for your Collector in the allowable address field.
How to Start VCM and Log On
1. If you are starting VCM on the Collector Machine, go to Start > All Programs > VMware vCenter
Configuration Manager > Web Console. If you prefer to connect to VCM from another machine on
your network, you may do so by pointing your browser to http://<name_of_Collector_
machine>/VCM. For the specific browsers that are supported, see the VCM Hardware and Software
Requirements Guide. The Logon screen appears.
62 VMware, Inc.
Page 63

Getting Started with VCM Components and Tools
2. Depending on your browser security settings, you may have to supply your user network credentials.
3. (Optional) Select Automatically log on using this role to have VCM automatically log you on without
prompting you for a role in future logons.
4. Click Log On. The Portal appears.
In the future, your VCM user account may have multiple roles. At that time, if you have the Automatically
log on using this role option checked, VCM will automatically log you on as the User Role displayed on
the Logon screen. To change roles, you must use the Logoff button in the top right corner of the Console.
This action will return you to the Logon screen so you can use the drop-down menu to select a different
role.
Getting Familiar with the Portal
The VCM portal provides access to all VCM features to manage your enterprise.
The portal uses a browser-based interface to run from any Windows machine that is running Internet
Explorer, or Mozilla Firefox with the Internet Explorer tab plug in, that has access to the machine where
VCM is installed.
Several major areas and controls exist in the Portal.
VMware, Inc. 63
Page 64

vCenter Configuration Manager Installation and Getting Started Guide
General Information Bar
The general information bar displays the VCM Collector’s (active SQL Server) name, your VCM user
name and active Role, and these buttons:
n
Log Out. Exits the Portal. The Portal closes, and the VCM Logon screen appears again.
n
About. Displays information about how to contact VMware Customer Support. It also displays version
information for VCM and all of its components. This information may be important when contacting
VMware Customer Support.
n
Help. Launches the online Help for the currently-active display.
Portal Toolbar
The global toolbar provides you with easily-accessible options to enhance control of your environment
and data.
The left and right arrow buttons navigate to the previous or next page in the data
area.
The Jobs button launches the Jobs Running status window. This button also
provides access to the Collector status and allows you to stop/restart the Collector
service.
The Collect button launches a wizard allowing you to define and initiate data
collections.
The Remote Commands button allows you to invoke the Remote Commands wizard
from the toolbar without having to access the node.
The Refresh data grid view button refreshes the data grid view. Pressing F5 on the
keyboard accomplishes this as well.
The View row cells button displays a vertically scrolling view of a single row of
data rather than the table-based data grid view in a separate window, and allows
you to move between records.
The Select all displayed data rows button selects all the rows in the data grid.
64 VMware, Inc.
Page 65

Getting Started with VCM Components and Tools
The Copy button is used to copy information from the s elected rows in the data grid
to the clipboard.
The Copy link to clipboard button is used to copy the link of the content on-screen
to the clipboard.
Click the View data grid in separate window button to display the data grid in a
separate window.
The Export displayed d ata button exports data to a CSV formatted file. This file is
exported to
Reports
The Options button opens the User Options window. These s ettings pertain to the
User who is logged on to VCM. All VCM Users will want to configure these to their
individual preferences.
\\<name_of_Collector_machine>\CMfiles$\Exported
.
Sliders
The sliders on the left side of the Portal include the items listed and described in the following table. The
individual items that you see in VCM will vary, depending on the components that you have licensed.
For detailed instructions about any of these features, see the online Help.
Select: If you want to :
Console
n
View, export, or print enterprise-wide, summary information.
n
Review or acknowledge current alert notifications.
n
Manage both VCM discovered and non-VCM discovered hardware and software
assets.
n
Review changes that occurred from one collection to the next.
n
Create, edit, or run remote commands on a VCM managed Windows or UNIX
machine.
n
View information about VCM discovered domains.
n
Navigate and manage VCM-integrated service desk events.
n
Manage VCM-managed virtual machines.
n
View your Windows NT Domain and Active Directory related data.
n
View information for enterprise-level applications.
n
Review non-security related UNIX machine-specific information.
n
Review UNIX security data to ensure consistent security configurations across your
enterprise.
Compliance
n
Create and manage Compliance rule groups and templates based on either AD
objects* or machine group data.
Active Directory*nView, export, or print enterprise-wide, summary information for Active Directory
objects.
n
Review alert notifications for the selected AD location.
n
Review Active Directory-related changes that occurred from one collection to the
next.
n
View collected information about Active Directory objects such as Users, Groups,
Contacts, Computers, Printers, Shares, and Organizational Units.
n
Review Active Directory site lists, including Site Links, Site Link Bridges, Subnets,
Intersite Transports, Servers, Connections and Licensing.
VMware, Inc. 65
Page 66

vCenter Configuration Manager Installation and Getting Started Guide
Select: If you want to :
n
View Active Directory Group Policy Container Settings.
n
View information about Active Directory Domains, DCs, and Trusts.
n
Track and display access control entries and security descriptor data on all collected
objects.
n
View Active Directory Schema information.
Reports
Patching(**)
n
Run "out-of-the-box" reports against your collected data.
n
Write your own SQL and SSRS reports using VCM’s report wizard.
n
Review a list of Microsoft bulletins available to VCM.
n
Create, run, or import VCM Patching templates to show which machines require the
patches described in each bulletin.
n
Select machines to license, set options for assessment and deployment, or monitor
VCM Patching jobs.
n
Deploy patches.
Administration***nManage basic configuration options for VCM.
n
Establish filters to limit the data you collect from machines in your enterprise.
n
Manage your VCM licenses.
n
Organize and manage your enterprise using VCM.
n
Manage VCM Logins and Roles.
n
View the status of jobs that are currently running, scheduled to run, or completed.
n
Configure VCM to notify you of certain conditions in your enterprise.
* Available only when VCM for Active Directory (AD) is licensed. This slider is viewable based on your
role.
** Available only when VCM Patching is licensed. This slider is viewable based on your role.
*** Visible only to users with Administrative rights to VCM as part of their VCM role.
66 VMware, Inc.
Page 67

Where to Go Next
You are now ready to proceed to Getting Started with VCM to start using VCM and all of its components
and tools.
After you have completed the steps in Getting Started with VCM, you must proceed to the next applicable
chapter that is relevant to the components you have licensed in your installation. VMware has
intentionally ordered the instructions in the remainder of this guide such that they build upon one another
as you proceed through this guide; therefore, it is imperative that you proceed in order.
You can skip any chapters that do not pertain to your installation as you proceed through this guide in
order.
NOTE If you choose to license another VCM component at a later date, you will be able to go back and
configure it at that time.
Getting Started with VCM Components and Tools
VMware, Inc. 67
Page 68

vCenter Configuration Manager Installation and Getting Started Guide
68 VMware, Inc.
Page 69

Getting Started with VCM
Before you can begin using VCM to manage the machines in your enterprise, you must complete the
following steps:
1. Discover, License, and Install Windows Machines.
2. Discover, License, and Install UNIX/Linux Machines.
3. Discover, License, and Install Mac OS X Machines.
4. Discover, License, and Collect Oracle Data from UNIX Machines.
5. Customize VCM for your Environment.
6. Set up and use VCM auditing.
Discover, License, and Install Windows Machines
The following steps must be performed before collecting data from Windows machines:
1. Verifying Available Domains
6
2. Checking the Network Authority
3. Assigning Network Authority Accounts
4. Discovering Windows machines.
5. Licensing Windows machines.
6. Installing the VCM Agent on your Windows machines.
7. Performing an initial Windows collection.
8. Exploring the Windows collection results.
These steps are explained in the following subsections.
Verifying Available Domains
The VCM Collector must gain access to each domain in order to interact with all enterprise Windows
machines. During installation, VCM discovered all of the domains that the Network Authority Account
you provided had access to.
To view a list of these discovered domains in VCM, navigate to Administration > Settings > Network
Authority > Available Domains. VCM displays the available domains in the data grid.
VMware, Inc. 69
Page 70

vCenter Configuration Manager Installation and Getting Started Guide
If the Windows machines that you want to manage belongs to a domain that is not shown in this list, then
you must add that domain manually. Click Add, then follow the steps in the Add Domain wizard to
manually add that domain. Once the domain is shown in the Available Domains list, you will be able to
manage Windows machines in that domain.
Checking the Network Authority
Your VCM Collector has to gain access to each domain to interact with the Windows machines in your
enterprise. An account having Domain Administrator rights must be created for each domain that has
Windows machines you want to manage. An initial account (your default Network Authority Account)
was specified through VCM Installation Manager during installation; you may need to create others. Once
an account has been created, it must be assigned to domains or machine groups (see Assign Network
Authority Accounts).
The following procedure enables you to check for available accounts and add new ones if necessary.
70 VMware, Inc.
Page 71

1. Click Administration > Settings > Network Authority > Available Accounts.
2. If you need to add a new account, click Add and follow the prompts.
Getting Started with VCM
NOTE Repeat the Network Authority Available Accounts wizard, creating a specific account for each
domain that has machines that you intend to manage through VCM.
Assigning Network Authority Accounts
VCM offers considerable flexibility in assigning Network Authority Accounts to domains and machine
groups. You can assign one account to all domains and machine groups, or assign a different account to
each. You can even assign multiple accounts to each domain and machine group.
VMware, Inc. 71
Page 72

vCenter Configuration Manager Installation and Getting Started Guide
The following procedure illustrates how to assign Network Authority to accounts by NetBios domain.
However, you can also assign Network Authority by Active Directory Domain, or even by Machine
Group (Administration > Settings > Network Authority > Assigned Accounts > By Machine Group).
For more information on these options, see the online Help.
1. Click Administration > Settings > Network Authority > Assigned Accounts > By Domain and then
select NetBIOS.
2. Select a listed domain.
3. Click Edit Assigned Accounts and follow the prompts.
Discovering Windows Machines
The discovery process identifies which machines can be accessed on your network. VCM uses one or more
Discovery Rules to discover the machines that are present on your network and available to VCM. The
Discovery Rules can be very general to discover many machines, or very precise to discover a particular
subset of your machines.
72 VMware, Inc.
Page 73

Getting Started with VCM
Your initial discovery can take anywhere from one afternoon to a couple of days, depending on the size of
your network. You may not have a 100% success rate with the first discovery process you run because
some machines may not be available during that time (for example, laptops that are not currently on the
network). It may, therefore, take a few days to coordinate and resolve scenarios in order for you to
discover the machines in your enterprise.
NOTE It is not necessary to complete the discovery of every machine in your enterprise before you
proceed with licensing machines. If you choose to move forward and license a subset of your machines, be
sure to review these chapters when you discover additional machines at a later time.
All discovered Windows machines will be placed in the Administration > Machines Manager > Available
Windows Machines list, and all discovered UNIX/Linux machines will be placed in the Administration >
Machines Manager > Available UNIX Machines list.
NOTE A Discovered Machines Import Tool (DMIT) is available from VMware Customer Support to assist
you with the following process. This tool imports machines discovered by the Network Mapper (Nmap)
into the configuration database. To use the tool, contact VMware Customer Support; otherwise, use the
following process.
After the initial discovery, VMware recommends that you generally perform a discovery about once each
week to keep the list of available machines current. You can schedule these future discoveries during your
organization’s off-hours, if you prefer.
NOTE To schedule a VCM job for discovery, go to Administration > Job Manager > Scheduled and
follow the Wizard. Refer to the online Help for more information.
Use the following procedure to discover machines.
1. Click Administration > Machines Manager > Discovery Rules.
2. Click Add to create a Discovery Rule. The Discovery Rules wizard appears.
VMware, Inc. 73
Page 74

vCenter Configuration Manager Installation and Getting Started Guide
3. Type a Name and Description for this new Discovery Rule, then click Next. The Discovery Method
page appears.
4. If you have Active Directory in your environment, VMware recommends a discovery that is targeted
for Active Directory. Select By Active Directory.
5. For an initial discovery, do not select Also discover the presence and version of the VCM Agent
when this rule is run. Because the VCM Agent is not present on the machines yet, you cannot
discover the Agent version.
6. Click Next. If you used By Active Directory, the AD Domain page appears.
7. Specify the AD Domain, accept the defaults, and then click Next. The Discovery Filters page appears.
74 VMware, Inc.
Page 75

Getting Started with VCM
8. Create the filter. For more specific filtering of machines for discovery and other advanced features,
refer to the online Help. Click Next. The Important page appears.
9. Select Yes so that you can run the Discovery Rule immediately. Because you are discovering machines
for the first time, you want to run the discovery now. Leave License and Install Agent on Discovered
Machines unselected. If the box is checked, VCM will proceed with licensing and installing the Agent
on each machine discovered, potentially exceeding your license count. For future scheduled
discoveries, VMware suggests checking the box, but not for your initial discovery.
10. Click the Jobs button at the top of the Portal to verify that your discovery job has completed before
proceeding to the next step. The Jobs Running window appears, listing your job name and summary
information. If the job has completed, it will not appear here.
NOTE You can also verify jobs for the past 24 hours if you think that you may have missed your
running discovery job by going to Administration > Job Manager > History > Other Jobs > Past 24
Hours. Refer to the online Help for additional information regarding VCM Jobs.
Licensing Windows Machines
You are now ready to license the Windows machines you have discovered. In the following sections, you
will license, install VCM Agents on, and collect data from your Windows machines. Later, we will guide
you through these actions on your UNIX/Linux machines.
VMware, Inc. 75
Page 76

vCenter Configuration Manager Installation and Getting Started Guide
VCM requires that you specify the machines you want to manage. Remember, the number of licenses you
have purchased may not match the number of machines that have been discovered and are visible in
Administration > Machines Manager > Available Machines > Available Windows Machines or
Administration > Machines Manager > Available UNIX Machines.
IMPORTANT If the machine type (that is, workstation or server) of a discovered Windows machine is
indeterminate, then the machine cannot be licensed. The machine type is visible in the second column of
the Available Machines Data Grid found at Administration > Machines Manager > Available Machines >
Available Windows Machines. If you need assistance resolving the machine type for machines you plan
to license, contact VMware Customer Support for guidance.
Use the following procedure to license your Windows machines.
1. Select Administration > Machines Manager > Available Machines > Available Windows Machines.
NOTE Remember, discovered machines with an indeterminate Machine Type will not be licensed if
they are included in your selection.
2. Select the machine(s) you want to license. To select multiple machines, use Shift-click or Ctrl-click.
3. Click License. The Available Machines License dialog box appears.
76 VMware, Inc.
Page 77

Getting Started with VCM
4. Leave the Install VCM Agents for the selected machines box unchecked during your first pass at
licensing machines. Once you have more experience licensing machines and deploying the VCM
Windows Agent, you may choose to check this box when licensing. The machines that you selected
appear in the Selected area. Click Next to view your Product License Details. The licensed machine
count has increased by the number of machines that you have selected to license.
5. Click Next. VCM confirms that the licenses you requested will be applied to the selected machine(s).
6. Click Finish.
Installing the VCM Windows Agent on your Windows Machines
Before you can collect data from a machine, the VCM Windows Agent must be installed on your licensed
Windows machine. You can install the VCM Windows Agent through VCM or manually. Both methods
are described here.
Machines that will be affected are those that are listed in the Administration > Machines Manager >
Licensed Machines > Licensed Windows Machines view.
The following procedure describes how to install the VCM Windows Agent on your licensed Windows
machines.
NOTE If you are installing the Agent on Windows 7, 2008, 2008 R2, or Vista, you may need to disable the
UAC during installation. See"Disabling UAC for Agent Installation" on page 81 for information.
Use the following steps to install the VCM Windows Agent on your licensed Windows machines.
1. Navigate to Administration > Machines Manager > Licensed Machines > Licensed Windows
Machines.
2. Select the Windows machine(s) on which you want to install the VCM Windows Agent. To select
multiple machines, use Shift-click or Ctrl-click.
VMware, Inc. 77
Page 78

vCenter Configuration Manager Installation and Getting Started Guide
3. Click Install and follow the prompts.
NOTE To use advanced options such as HTTP communication for your agent, or to deploy the agent
from an alternate source, refer to the online Help. To access the online Help at any time during the
wizard, click the Help button in the lower left corner of the dialog box.
4. Verify that your agent installation job has completed. To check the status of an active job, click the Jobs
button at the top of the Portal window to access the Jobs Summary.
NOTE You can also verify jobs for the past 24 hours if you think that you may have missed your
running discovery job by going to Administration > Job Manager > History > Other Jobs > Past 24
Hours. Refer to the online Help for details regarding VCM Jobs.
Manually Installing the VCM Windows Agent
You can manually install the VCM Windows Agent using either the EXE (.exe, executable) file or the MSI
(.msi, Microsoft Installer) file that is supplied with VCM. Choose your install method based on the
following:
n
EXE files detect an existing software version and provide the option to uninstall the existing version.
EXE files can also be used for unattended silent installations.
n
MSI files are database files executed by the Windows MSIEXEC.EXE executable, which reads data in the
MSI file and executes the installation. MSI files can be used for unattended, silent installations. The MSI
installer will also uninstall an existing agent (non-msi), but it does not ask. If you run it again, you have
the option of removal only. If you upgrade an MSI-installed agent with the new MSI, the old agent is
uninstalled.
The VCM Enterprise Certificate, which is selected during the initial installation of VCM, is installed in the
certificate store on the Agent machine during the Agent installation process if HTTP is selected. The
Collector root certificate (Enterprise Certificate) is used to authenticate requests from a collector (using the
Collector Certificate and its established trust to the Enterprise Certificate) on the Agent machine before a
collection/change request is processed.
Using the .exe
To manually install the VCM Windows base Agent (CMAgentInstall.exe) on a target machine using the
.exe file, follow these steps.
78 VMware, Inc.
Page 79

Getting Started with VCM
1. On your Collector, navigate to the Agent files directory at:
C:\Program Files (x86)\VMware\VCM\AgentFiles
2. Locate the CMAgentInstall.exe file, and then install it from a network share or copy it to the target
machine.
3. Navigate to the Collector data directory at c:\Program Files
(x86)\VMware\VCM\CollectorData. Locate the Enterprise Certificate .pem file. This file must be
accessible during the agent installation. The path used here is the default location. If your files are not
in the default location, click Administration > Settings > General Settings > Collector. In the data
grid, go to the Root directory for all collector files. The current path is displayed in the Value column.
NOTE If the Enterprise Certificate has been distributed by a mechanism outside of the scope of VCM,
such as a corporate Public Key Infrastructure (PKI), you may not need to include the Enterprise
Certificate file.
4. In Windows Explorer, double-click the CMAgentInstall.exe. You will be asked for the certificate
path and port.
If you are performing a silent install, on the target machine run the CMAgentInstall.exe using the
following parameters:
CMAgentInstall.exe /s INSTALLPATH=%Systemroot%\CMAgent PORTNUMBER=26542
CERTIFICATEFILE=<filename>
NOTE The %Systemroot% environment variable specifies the directory where Windows is installed
(typically \WINNT or \WINDOWS).
Where:
n
CMAgentInstall.exe is the executable used to install the Agent.
n
/s indicates a silent install, which means that popups and menus do not appear. When running
this command from the command line, VMware recommends using the /s option. When
performing a silent install, if the VCM Windows Agent is found locked, the installation will fail.
To unlock the Agent so that the installation will proceed, use the -UNLOCK option. When used,
the Agent will remain unlocked when the installation completes. The syntax is:
CMAgentInstall.exe /s -UNLOCK INSTALLPATH=%Systemroot%\CMAgent
PORTNUMBER=26542 CERTIFICATEFILE=<filename>
NOTE To re-lock your machine, submit a lock request from the VCM Collector.
n
INSTALLPATH is the location where the Agent will be installed.
n
PORTNUMBER is specified for HTTP Agents. If the PORT parameter is not present, the protocol
will be DCOM. In this case, the communication socket listener service will not be installed and
the certificate is not required.
n
CERTIFICATEFILE is the certificate that was generated or specified on the Collector during the
Collector installation. The location of the certificate file will be in the path relative to where you
installed the software on the Collector, and by default is C:\Program Files
(x86)\VMware\VCM\CollectorData\[certificate name].pem. If you specify a
PORTNUMBER, but do not want to use a certificate, you must use the parameter
CERTIFICATEFILE=SKIP to allow an HTTP Agent without a valid CERTIFICATEFILE path.
VMware, Inc. 79
Page 80

vCenter Configuration Manager Installation and Getting Started Guide
NOTE For Vista, Windows7, and Windows 2008 only: If you set compatibility mode on any Agent
executables to a prior version of Windows, the operating system may be reported incorrectly in VCM.
To Manually Uninstall the VCM Windows Agent
The VCM Windows Agent uninstall executable will be present only if the Agent was installed manually
using CMAgentInstall.exe or CMAgentInstall.msi. To uninstall the VCM Windows Agent manually,
execute the following command (this command assumes the default installation directory was selected):
%SystemRoot%\CMAgent\Uninstall\Packages\CMAgentInstall\UnCMAgentInstall.exe
Using the .msi
To manually install the VCM Windows base Agent (CMAgent[Version].msi) on a target machine using
the .msi file, follow these steps:
1. On your Collector, navigate to the agent files directory. The location of the .msi will be in the path
relative to where you installed the software on the Collector, and by default is
c:\Program Files (x86)\VMware\VCM\AgentFiles.
2. Locate the CMAgent[Version].msi file. This file must be accessible by the target machine.
3. Navigate to the Collector data directory at c:\Program Files
(x86)\VMware\VCM\CollectorData. Locate the VCM Enterprise Certificate .pem file, and then
copy this file to the target machine in a secure manner.
NOTE If your Collector is operating in a full Public Key Infrastructure (PKI), and the client can validate
the Collector root certificate (Enterprise Certificate), the .pem file is not necessary.
4. On the target machine, double-click the .msi or run the .msi file using the command line syntax.
Command line options and parameters are described below.
msiexec /Option <Required Parameter> [Optional Parameter]
For example:
msiexec.exe /qn /i "[PathToFile]\CMAgent[Version].msi" [PORTNUMBER=<available
port>] [INSTALLDIR="<new path>"]
When executing the Windows installer file with default options, any existing Window Agent is removed.
The new VCM Windows Agent is then installed in the %SystemRoot%\CMAgent directory, and will use
DCOM to communicate. The %SystemRoot% variable defaults to C:\WinNT or C:\Windows.
For HTTP installs, where PORTNUMBER is set, you must also specify an Enterprise Certificate. To do so, use
this syntax: CERTIFICATEFILE=”x:\[mypath]\[mycert].pem”. If you specify PORTNUMBER, you must
also provide CERTIFICATEFILE with either SKIP or the path to a certificate file.
Command line options, showing required and optional parameters, include the following. These options
are all parameters to msiexec.
n
/qb - Runs the command in a basic user interface, displaying the progress and error messages.
n
/qn - Runs the command in quiet mode; no user interaction is required.
n
/i - Specifies the command as an installation.
n
/x - Specifies the command as an uninstall process.
80 VMware, Inc.
Page 81

Getting Started with VCM
n
PORTNUMBER: Installs the Windows Agent on the port number specified, using HTTP instead of
DCOM. For HTTP installs, where PORTNUMBER is set, you must also specify a certificate file using the
syntax: CERTIFICATEFILE=”x:\[mypath]\[mycert].pem”. For example:
msiexec.exe /qn /i "C:\temp\CMAgent[VersionNumber].msi" PORTNUMBER=2666
CERTIFICATEFILE=”x:\mypath\mycert.pem”
n
INSTALLDIR: Changes the default root directory specification (%SystemRoot%\CMAgent). For
example:
msiexec.exe /qn /i "C:\temp\CMAgent[VersionNumber].msi" INSTALLDIR="C:\VCM"
n
CERTIFICATEFILE: Specifies the Enterprise Certificate. For example:
CERTIFICATEFILE=”x:\[mypath]\[mycert].pem” or CERTIFICATEFILE=”SKIP”
For more information about the command line options and descriptions, click Start > Run > msiexec or
visit http://www.microsoft.com.
You must specify optional parameters using UPPERCASE letters, following the required "/i" parameter.
Quotation marks are necessary only when a path includes spaces. For example, when one or more spaces
exist in the source file location and the INSTALLDIR parameter. The optional parameters can be specified
in any combination and order.
Disabling UAC for Agent Installation
The following steps are required only if you are installing the Agent on a Windows 2008 or Vista machine.
When installing the Agent on Windows 2008 or Vista, you must disable the User Account Control (UAC),
install the Agent, and then re-enable the UAC.
Disabling UAC on One Machine
1. On the target Windows 2008 machine, click Start > Run. The Run dialog box appears.
2. Type msconfig in the Open text box.
3. Click OK. The System Configuration dialog box appears. (This dialog box differs for Windows 2008
R2 machines.)
4. Click the Tools tab.
5. In the Tool Name list, select Disable UAC.
6. Click Launch. A Command window displays the running action. When the command is completed,
close the window.
7. Close the System Configuration dialog box.
VMware, Inc. 81
Page 82

vCenter Configuration Manager Installation and Getting Started Guide
8. Restart the machine to apply the changes.
9. Install the Agent as specified in Licensing and Deploying the VCM Agent.
10. After installing the Agent on the target machine, re-enable UAC. To enable, perform the steps
specified above. In Step 5, select Enable UAC in the Tool Name list.
11. Restart the machine to apply the changes.
Disabling UAC using Group Policy
Use the following procedure to disable the UACon multiple machines. The instructions assume you have
configured the Windows 2008 and Vista machines targeted for Agent install in a common Active Directory
domain/OU.
1. On a Domain Controller, click Start > Run. The Run dialog box appears.
2. Type mmc in the Open text box.
3. Click OK. The Console window appears.
4. Select Console Root, and then click File > Add/Remove Snap-in. The Add or Remove Snap-ins
dialog box appears.
5. In the Available snap-ins list, double-click Group Policy Management Editor. The Select Group
Policy Object dialog box appears.
6. Click Browse. The Browse for a Group Policy Object dialog box appears.
7. On the Domains/OUs tab, select the domain/OU to which the target machines belong, and then click
OK.
8. On the Select Group Policy Object dialog box, click Finish.
9. On the Add or Remove Snap-Ins dialog box, click OK.
10. The domain/OU policy is added to the Console Root in the left pane.
11. Expand the added domain/OU and browse to Computer Configuration > Policies > Windows
Settings > Security Settings > Local Policies > Security Options.
12. In the right pane, locate the User Access Control policies. On each of the policies specified below, rightclick and select Properties. Configure as follows:
n
User Account Control: Behavior of the elevation prompt for administration in Admin
Approval Mode: Elevate without prompting.
n
User Account Control: Detect application installations and prompt for elevation: Disabled
n
User Account Control: Run all administrators in Admin Approval Mode: Disabled
13. Restart the machine to apply the changes.
14. Install the Agent as specified in the previous section, "Licensing and Deploying the VCM Agent".
15. After installing the Agent on the target machines, re-enable UAC. To enable, perform the steps
specified above. In Step 5, change the policies to Enabled.
16. Restart the machine to apply the changes.
82 VMware, Inc.
Page 83

Getting Started with VCM
Performing an Initial Collection
You are now ready to collect data. VMware recommends using the default filter set, which collects a
general view of the licensed Windows machines in your enterprise configuration, until you are ready to
build specific filters and target your collections. The first time you use the default filter set for a collection,
the VCM Agent will return all of the data (as specified by the filters in the default filter set) to be stored in
the VCM database. Subsequent collections using the default filter set will return only a delta collection
(meaning the differences between the data found on the target machine and what is already stored in the
VCM database), unless you specify within the Collect Wizard to return the full collection. The delta
collection feature makes subsequent collections run faster and more efficiently than the initial collection
with that particular filter set.
IMPORTANT You can run Compliance Templates and perform reporting on data that has been collected
and stored in VCM. Therefore, it is necessary to perform collections on a regular basis. This ensures that
the data you are reporting on is current. When performing a full collection on your entire enterprise, you
may want to run VCM overnight because the collection could potentially affect the performance of your
machines. Once the initial collection completes, any future delta collections should be unnoticed by users.
Be sure to perform collections on a routine basis to ensure accurate reporting.
1. Click Collect, located on the main Portal toolbar. The Collection Type page of the wizard appears.
2. Select Machine Data, and then click OK. The Machines page appears.
3. Select the machine(s) from which you want to collect data. To select multiple machines, use Shift-click
or Ctrl-click. Use the double arrow to move all visible machines to the selection window, 500 at a time.
Leave the default options selected, then click Next.
IMPORTANT To collect from machines running Windows XP SP2 or Vista using DCOM, you must
either enable ICMP pings in the firewall settings, or disable ICMP pings in the Portal. Refer to the
online Help for more information.
4. The Data Types dialog box appears. Check the Select All checkbox, then confirm that the Use default
filters option button is also selected. Click Next.
VMware, Inc. 83
Page 84

vCenter Configuration Manager Installation and Getting Started Guide
5. For initial collections, there should be no conflicts with previously scheduled or running jobs
containing the same data types. Click Finish.
6. Verify that your collection job has completed before proceeding to the next step. To do so, click the
Jobs button at the top of the Portal window to access the Jobs Summary.
NOTE You can also verify jobs for the past 24 hours if you think that you may have missed your
collection job by going to Administration > Job Manager > History > Instant Collections > Past 24
Hours. Refer to the online Help for additional detail regarding Jobs.
TIP Collecting certain Windows data types the first time results in a secondary SID lookup (looks up user
accounts associated with a user ID) query back to the machine from which the data type was collected. To
speed up initial collections that require a SID lookup, first collect the Accounts and the Groups data types
from the Primary Domain Controller (PDC) of each domain. The PDCs have the necessary account
information, and doing so automatically resolves the SIDs. The data types that cause the automatic
additional query are:
• User Rights
• Registry Key Permissions
• Directory Permissions
• Share Permissions
• Disk Quota
• Event Log
• Services
• Processes
Exploring Windows Collection Results
Now that you have performed an initial Windows collection, you can explore that data in the VCM Portal.
VCM presents summary information in graphical SSRS charts, for machines in the active machine group,
which you can view, export, or print. The individual VCM Dashboards visible in the VCM Portal will vary,
based upon which VCM components you have licensed. Each VCM Dashboard is run only when the node
is selected against the current data available in the CMDB for machines in the active machine group.
Therefore, Dashboard data is only current as of the time when it was collected. In addition, it may take
time for the data to display based upon the volume or complexity of the data requested.
84 VMware, Inc.
Page 85

Getting Started with VCM
1. Begin by looking at the Windows Operating Systems Dashboard under Console > Dashboards >
Windows > Operating Systems.
2. Note that several other Windows Dashboards are also available. Take time to familiarize yourself with
the remainder of the Windows Dashboards. Windows Collection Results are also available to you in a
more “raw” format by data class. This level of “reporting” is more relevant for day-to-day operations,
troubleshooting, and analysis, and can be viewed in a Summary report or data grid format.
3. Now take a look at your Windows Operating System Information by clicking the Windows tab in the
Console. Then, click Operating System > Machines.
VMware, Inc. 85
Page 86

vCenter Configuration Manager Installation and Getting Started Guide
4. When you select the node, you will see a Summary Report as displayed above of the data class that
you selected. Click View Data Grid to go directly to the data grid, or click an area of the Summary
Report to filter the data before the data grid is displayed.
86 VMware, Inc.
Page 87

Getting Started with VCM
TIP The default view is the Summary Report; however, at any time you may switch the default
view to go directly to the data grid by using the ’Enable/Disable Summary’ feature on the data
grid view. See About Data Grids in the online Help for more information on how to filter and
sort your data and get full use of the data grid.
Several other categories (called “data classes”) of information regarding your Windows Collection
are available under the Windows tab, which is located in the Console. This is where the remainder
of your collected Windows data is visible through the Portal.
An alternative way to view your collected Windows data is by running Reports or creating your
own custom reports using the reporting wizard. To begin exploring VCM’s Reporting functionality,
go to the Reports slider, then click Machine Group Reports > Windows.
Like Dashboards, Reports are run against the current data available in the CMDB for machines in
the active machine group, and therefore are only as current as the last collection. In addition, the
report may require significant time to generate based upon the volume or complexity of the data
requested. Refer to the online Help for more information on how to schedule and disseminate
reports.
5. You may now begin to check Compliance for your collected data. To run a Compliance check, click the
Compliance slider, then follow the steps as described in the online Help to create rule groups, rules,
filters, and templates.
VMware, Inc. 87
Page 88

vCenter Configuration Manager Installation and Getting Started Guide
Getting Started Collecting Windows Custom Information
As a System Administrator, you can extend the data that VCM can collect by using a script, which will
allow you to view, report on, alert on, detect change on, and run compliance against data not currently
exposed by VCM. This extension allows you to view, report on, alert on, detect change on, and run
compliance against custom data not currently exposed by VCM.
You can use the Windows Custom Information data type to perform user-defined, script-based collections
from VCM-managed machines. To collect the custom data, you build a collection filter, which includes a
script and other parameters relating to the execution of the script and the handling of its results. When this
filter is used in a collection, the VCM agent will call a script engine to run the script, and will then parse the
results so they can be returned to the VCM database and displayed in the VCM console. As of this release,
VCM supports PowerShell scripting and XML output.
During the collection process, the VCM Agent launches PowerShell to execute the script, which in turn
generates an XML result file. The Agent then parses the XML result into a format that can be checked for
changes (deltas), and then those changes are returned to the Collector.
Prerequisites
Before collecting Windows Custom Information (WCI), you must ensure the following prerequisites are
met.
88 VMware, Inc.
Page 89

Getting Started with VCM
n
You must obtain or write a PowerShell script that will return data in a VCM-compatible elementnormal XML format.
n
The VCM agent (for VCM 5.3 or later) must be installed on each VCM-managed machine used to
collect the Windows custom information. Older agents must first be upgraded.
n
PowerShell must be installed on each VCM-managed machine. PowerShell is installed by default on
Windows 2008 R2 and Windows 7 machines. For Windows XP, 2003, 2003 R2, 2008, and Vista machines,
PowerShell must be installed separately. You cannot install PowerShell on Windows 2000 or NT4
machines. In cases where PowerShell is not installed on the target VCM-managed machine, the WCI
collection will return a "Not Executed" success status. See Job Status Reporting for WCI.
n
Windows Custom Information supports PowerShell version 2.0, and should work with later versions of
PowerShell as well.
n
After installing PowerShell on a VCM-managed machine, you must reboot the machine to ensure that
collections will work properly.
n
If the VCM Collector will be used as a client for WCI collections, ensure that PowerShell is installed on
the Collector machine.
n
VCM ships with default Administration settings for Agent Thread (default is set to below normal
thread priority) and Agent Data Retention (default is 15-day change log). However, you can change
these settings if you desire.
n
Before file-based PowerShell scripts can be executed by the WCI collection filter on the VCM Collector
and/or the VCM-managed machine, you change the execution policy on the VCM-managed machines.
The PowerShell execution policy on the VCM machine must be set to Remote Signed, All Signed, or
Unrestricted. If the policy is set to All Signed, the scripts must be signed, and the appropriate
certificates distributed before collections can be run.
Procedure
To collect and view Windows Custom Information from VCM-managed machines, follow these steps.
1. Obtain PowerShell script(s) from VMware Professional Services or another source (or you can write
your own). For more information about scripts, see Getting Started with PowerShell Scripts.
2. Select Administration > Collection Filters > Filters.
3. Click Add Filter to add a collection filter. The Collection Filter Wizard appears.
4. Enter a name for the filter, and then click Next. The Data Type page appears.
5. Select Windows, and then the Custom Information (Win) data type. Click Next. The Windows
Custom Information Filter page appears.
6. Select your Script Type, which defaults to PowerShell v1.0 Text Output.
7. Select the Output Type of Element Normal XML.
8. Specify the Timeout in seconds. This setting specifies how long the Agent will allow a PowerShell script
to run before attempting to end the process. The purpose of this setting is to prevent blocked or
excessively long-running scripts from blocking other Agent requests.
9. In the Script area, paste the content of your user-defined PowerShell script, which contains statements
specific to the data type you will be collecting. Depending on your script, parameters to be configured
may exist near the top of the script.
10. VCM handles violations of any duplicate path attributes in the PowerShell scripts through the
Duplicate Handling settings. In the Duplicate Handling area, select one of the following: Discard,
Increment, or Fail with Error.
VMware, Inc. 89
Page 90

vCenter Configuration Manager Installation and Getting Started Guide
11. Click Next and then Finish.
12. Run a collection using your new collection filter.
13. Ensure the job completes.
14. View data in the Custom Information nodes ( Console > Windows > Operating System > Custom
Information).
When the Windows Custom Information data is available in the VCM database, you can generate reports
and enforce compliance.
Change Detection in Windows Custom Information Data
Deltas in WCI are maintained on a per-filter basis at the client side, which means that if multiple filters
return data under the same top-level element name (such as NetStat), each filter will have its own change
detection.
In the following example, using multiple filters that collect the same open ports data and return it under
the NetStat top-level element name, if a client machine has just started listening on port 80, each filter will
report this new data as a newly created value the first time the filter “sees” this data. The best practice is to
avoid this type of overlap of filters.
For example, two copies of the File Permission With Audit filter could be created in order to collect file
permissions data from different parts of the file system, but they should not overlap. Having one filter get
data from C:\ and another filter get data from C:\Windows would be a good practice. However, having
one filter get data from C:\Windows with audit information and another filter get data from C:\Windows
without audit information would not be a good practice because both filters would generate "new file" and
"deleted file" events each time a new file was added or removed.
n
For an element such as NetStat, only one filter should be used.
n
For an element such as NTFS file system (NTFSDirectory), multiple filters would likely be used. For
example, one filter would be used to obtain the details under C:\, and another filter would be used for
C:\Windows\System. Both would merge under the NTFSDirectory top-level element, but there
should be no overlap; instead they would each collect separate parts of the file structure to avoid
“extra” change reporting.
Purge for Windows Custom Information
As with other data types, purge for WCI will purge all data for a machine. This means that if a single WCI
filter is collected with the “Do not limit to delta” option selected, all WCI data for that machine will be
purged from the client’s master file and from the VCM database, and it will be replaced with the resulting
data from the single filter.
Job Status Reporting for WCI
Job status reporting for WCI is provided on a per script/filter level, and includes detailed reporting about
exit codes and process standard error output. As each script/filter is executed, VCM captures detailed
results information during the execution of the WCI collection filter scripts.
You can view the detailed information in the VCM user interface in the Administration > Job Manager >
History node by selecting the executed job and then selecting View Details in the Job History Machine
Detail pane of a collection job that includes WCI data.
90 VMware, Inc.
Page 91

Getting Started with VCM
The Job History Machine Detail view displays a single row for each WCI filter included in the collection
job. These rows provide information about the execution of the WCI scripts and the parsing of the script
results. In cases where the script cannot be executed because prerequisite components are not installed or
available (such as PowerShell is not installed), the status for a row will be “Not Executed.” This status does
not result in a failure for the inspection because PowerShell (or other script engines) are optional
components and may not even be installable on all VCM-supported OS versions.
If a WCI collection job encounters errors on a machine, detailed information about the failure will be
reported. The failure could occur during the launch of PowerShell, during script execution, or during the
interpretation of the script results. For example, an error could occur in the PowerShell launch process if
PowerShell is not installed on the VCM-managed machine. However, since PowerShell is an optional
component, such a failure does not roll up as an error to the job level, although the job details will show
Not Executed to show such skipped steps. On the other hand, if a PowerShell script generates errors due
to syntactical or typographical defects in the script itself, these errors will roll up to a “completed with
errors…” status at the collection job level.
Running Reports
Several reports are included for reporting on Windows Custom Information, including:
n
Netstat Open Ports:Reports port and protocol information from the netstat –A command.
n
SQLSMO Database: Reports database details collected.
n
SQL SMO Instance: Reports basic information about SQL Server instances collected.
These reports are in Reports > Machine Group Reports > Windows > Custom Information.
Getting Started with PowerShell Scripts
The Windows Custom Information data type (WCI) uses extensions to the VCM Windows agent to allow
the agent to invoke scripts that are passed down as part of a collection filter’s parameters, and then parse
the results. As a result, these extensions are very flexible in that they use filter parameters to detail the
command line to invoke the scripting engine, and a COM class name to specify the parser the Agent will
need in order to parse the script output. This allows the eventual extension of the system to support
multiple different scripting engines/languages and multiple options for output format.
For this version of WCI, the base requirement supports PowerShell for the scripting engine and a specific
XML format, named Element Normal XML, as the output.
This topic describes:
n
Executing PowerShell Scripts
n
Developing Custom Collection Scripts
n
Example of Developing a Custom PowerShell Script for Use with the WCI Data Type
n
Troubleshooting Custom PowerShell Filter Scripts
VMware, Inc. 91
Page 92

vCenter Configuration Manager Installation and Getting Started Guide
Executing PowerShell Scripts
PowerShell contains built-in policies, which limit its use as an attack vector. The primary policy is for script
execution. By default the script execution policy is set to Restricted, which means that PowerShell can only
be used interactively or for executing commands directly from the command line. The additional policy
settings are as follows:
n
AllSigned: Any PowerShell script (.ps1 is the typical extension) must be signed by a verifiable certificate
(from the SPC certificate store)
n
RemoteSigned: Any PowerShell script that is downloaded from the Internet (by a supporting browser
such as Internet Explorer) must be signed. Script files that are created locally, or scripts that are
downloaded by a means that does not support flagging of the file source, do not need to be signed.
n
Unrestricted: All PowerShell script files will be executed regardless of whether they are signed.
In addition, PowerShell 2.0 adds the capability to set different script signing policies at the machine, user,
and process (single execution of powershell.exe) scopes.
WCI uses Script Type information in the collection filter definition to indicate how PowerShell should be
executed and how the script should be passed to it. The primary ways a WCI script may be passed to
PowerShell is either in-line or through a script file
n
In-line: Requires a collection script that can be represented as a single line of PowerShell code. In-line
scripts can be run regardless of the execution policy; because an in-line script is run on the PowerShell
command line rather than from a file, the execution policy does not apply. The default WCI filter uses
an in-line script to collect basic information about the PowerShell version, .NET version, and execution
policy settings of a system.
n
Script file: Requires that the execution policy be set to Remote Signed at the most restrictive, since the
script is being run from a file locally on the client system. Because of its additional ability to have
execution policy set at the process level, PowerShell 2.0 is the base requirement for WCI in VCM. The
default script type command line used for script based filters in WCI includes options to set the processlevel execution policy to Remote Signed. This allows WCI to execute collection scripts against systems
whose machine and user level signing policies may be anything, without having to change the setting.
Out-of-the-box VCM WCI non-in-line collection filters will fail if executed against PowerShell 1.0 client
systems.
VMware recommends that you upgrade from PowerShell 1.0 to PowerShell 2.0, which introduced a
number of useful functions. PowerShell 2.0 is also supported on all platforms that support PowerShell 1.0.
It is possible to execute WCI PowerShell collection scripts against PowerShell 1.0 systems as well, although
it has not been tested, and is not officially supported. In-line WCI filters that do not employ PowerShell 2.0
commands should work directly. For script file based filters to work, you must create them with the
PowerShell v1.0 Text Output script type, and the system must already have its execution policy set to
Remote Signed, at the most restrictive, with un-signed scripts, or to All Signed with signed scripts (see
below). This setting can be accomplished by the Group Policy Object (GPO), through the use of a VCM
Remote Command, or by using a registry change action or enforceable compliance to set the policy
directly. For example:
HKLM\Software\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell
"ExecutionPolicy"="RemoteSigned"
92 VMware, Inc.
Page 93

Getting Started with VCM
For additional information about Windows PowerShell and signing scripts, see:
n
Scripting with Windows PowerShell: http://technet.microsoft.com/en-us/scriptcenter/dd742419.aspx
n
Windows PowerShell Owner's Manual: http://technet.microsoft.com/en-us/library/ee176949.aspx
n
Signing Windows PowerShell Scripts: http://technet.microsoft.com/en-
us/magazine/2008.04.powershell.aspx
n
Execution Policies: http://technet.microsoft.com/en-us/library/dd347641.aspx
n
Registry value that controls execution policy: http://msdn.microsoft.com/en-
us/library/bb648598(VS.85).aspx
Developing Custom Collection Scripts
Development of custom collection scripts requires planning the data structure. WCI internally stores data
hierarchically, as displayed in the Tree View - Standard node. The collection script is required to provide all
of the structure that can be seen in any branch under this node.
The root element in the XML result data set will become a top level (root) element in the WCI data type
node. Child elements will appear in the same locations in the VCMuser interface as the locations they
populate in the XML document that is returned by the script.
When developing custom collection scripts, follow these guidelines:
n
XML element names must be unique at their level (for example, two "Child1" nodes can exist, as long as
they are not siblings).
n
Attributes must be unique at their level.
n
Element and attribute names used must be valid XML when returned by the script. If data is to be
returned as an element or an attribute name that is not valid for XML, the name can be encoded using
the [ToCMBase64String] function. The inserter will recognize names encoded with this function and
will decode them during the raw insert process. The inserter is a Collector job that is executed during
each collection. It is responsible for parsing the Agent results files and putting the data into a new raw
database table. The raw data is then transformed into the data that appears in the nodes in the user
interface.
function ToCMBase64String([string]$input_string)
{
return [string]("cmbase64-" +
[Sys-
tem.Co-
nvert]::ToBase64String([System.Text.Encoding]::UNICODE.GetBytes($input_
string))).replace("=","-")
}
n
If a script has configurable parameters, they should be described in a comment block near the top of
the script, along with configurable entries of the parameters near the top of the script, so that a user
who is cloning a WCI collection filter can easily see and set the parameters in the Edit Filter wizard (in
Administration > Collection Filters > Filters).
n
Declaration of variables, and any other tasks in a script that produce output that is not part of the XML
result set, should be redirected to out-null, such as:
[reflection.assembly]::LoadWithPartialName("Microsoft.SqlServer.Smo") > out-
null
VMware, Inc. 93
Page 94

vCenter Configuration Manager Installation and Getting Started Guide
n
The default WCI filter returns PowerShell version information from VCM-managed machines.
n
Do not include any formatting white space. For example, do not use CR LF at the end of elements,
nodes, or attributes.
See also the example below of developing a custom PowerShell script for use with the WCI data type.
Example of Developing a Custom PowerShell Script for Use with the WCI Data Type
In this example, the objective is to collect scheduled tasks information from Windows clients. On newer
systems, Windows conveniently provides the schtasks.exe utility to report on scheduled tasks created
either through the Task Scheduler user interface or through use of the AT command.
n
Running schtasks by itself returns only basic data about tasks.
n
Adding the /query /v switches provides additional information, but the formatting is difficult for
automated processing.
n
The schtasks /query /? command provides additional possibilities.
n
The option set of schtasks /query /v /fo:csv is selected as the source for the data for the
collection script. These options give full details for all tasks in a comma-separated value result set.
PowerShell makes working with tabular result sets from commands easy. A first step for this script is to
run a command similar to:
$schtasks = schtasks /query /v /fo:csv
Since the data returned from schtasks includes multiple rows, PowerShell makes the $schtasks
variable into an array. As such, $schtasks[0] represents the first row returned from the command.
Viewing the result set by looking at $schtasks[n] shows that that the first line, $schtasks[0], is blank;
$schtasks[1] contains column names, and $schtasks[2] is the first row of task data. The goal, then, is
to parse this data into a structure compatible with VCM’s XML format for return to the Collector.
The Scheduled Tasks script uses the split method of PowerShell strings to separate the columns of the
$schtasks rows into separate values in arrays. The column names row provides the names to use for
attributes, and the corresponding data from the scheduled task rows provide the values to use for these
attributes.
Once parsed, the XML returned by the script should look something like:
<schtasks>
<taskname1>
<attribute1>Value1</attribute1>
<attribute2>Value2</attribute2>
…
</taskname1>
<taskname2>
<attribute1>Value1</attribute1>
<attribute2>Value2</attribute2>
…
</taskname2>
…
</schtasks>
94 VMware, Inc.
Page 95

Getting Started with VCM
The <schtasks> top-level name is an arbitrary name picked to distinguish the results of this script from
others. A couple of additional challenges must also be overcome with this data, related to column names
returned by the schtasks command, and the fact that the schtasks command does not include any
unique and repeatable identifier for specific task entries. Details about these challenges are described next.
The first challenge can be seen by looking at the column names returned by the schtasks command.
Even the basic schtasks command (no options) has a column name of Next Run Time. Since this column
name includes spaces, it cannot be used as-is as an attribute name in an XML document. Other column
names returned by the more verbose execution of schtasks have similar problems. To preserve these
column names in the form that they are returned from the schtasks command, but still allow for XML
handling, the names are encoded with the ToCMBase64String function:
function ToCMBase64String([string]$input_string)
{
return [string]("cmbase64-" +
[Sys-
tem.Co-
nvert]::ToBase64String([System.Text.Encoding]::UNICODE.GetBytes($input_
string))).replace("=","-")
}
This function uses Unicode base64 encoding, along with some character substitution (a dash instead of an
equal sign) to create an XML-legal form of any element or attribute name. The string is prefixed with
cmbase64- to indicate to the VCM inserter that the data will need to be decoded prior to loading it into
the VCM database. The end result is that rather than containing invalid data like this:
<Next Run Time>
12:32:00, 5/26/2010
</Next Run Time>
The XML will contain this:
<cmbase64-TgBlAHgAdAAgAFIAdQBuACAAVABpAG0AZQA->
12:32:00, 5/26/2010
</cmbase64-TgBlAHgAdAAgAFIAdQBuACAAVABpAG0AZQA->
The second problem is that the <schtasks> command does not include any unique and repeatable
identifier for specific task entries. For example, many test systems observed had more than one task with
the name: GoogleUpdateTaskMachineCore. Unique element names are a requirement for valid VCM
XML, and repeatable identifiers are desirable to prevent false indications of changes at the VCM Collector.
For example, if the script was to arbitrarily label rows as Task1, Task2, …, and Task1 was deleted, Task2
would then become Task1, and VCM would show a lot of changed details for Task1 (command line
changed, next run time changed, etc), when in fact, that task had not changed at all – it had only changed
places in the sequence.
One way to handle creation of unique and repeatable names for elements is to create a name based on a
hash of the data contained in the row. That is useful for data that has no name-type attribute at all. In this
case, however, there is a task name, but it is not guaranteed to be unique. Since the task name is userfriendly and useful, it is desirable to try to preserve and use it through the collection script. To preserve it,
VMware, Inc. 95
Page 96

vCenter Configuration Manager Installation and Getting Started Guide
the task name is used as the element name for task rows, but the “increment” option is selected for
duplicate handling when creating a collection filter based on this script. This action allows the collection
process to add an incremental entry to a list of multiple entries with the same task name: the first example
of GoogleUpdateTaskMachineCore, while the second example will be relabeled as
GoogleUpdateTaskMachineCore_1.
It is still possible that reordering the list among tasks that have the same name, will cause “extra” changes
to be reported, but regardless of these changes, it is reasonable to have VCMdisplay the friendly task
names in the user interface. Because task names also can contain characters that would not be valid for
XML element names, the task names, as with the column names, are encoded using the
ToCMBase64String function.
Troubleshooting Custom PowerShell Filter Scripts
You can interactively test a custom PowerShell script using the following procedures.
Procedu re
Verify the script runs correctly within a PowerShell shell.
1. Start PowerShell from the command line on a VCM-managed machine.
2. Paste the inspection script into the PowerShell shell window.
3. Depending on the last character, it may require one extra hit of the Enter key to start the script
4. The script should run to completion without throwing any errors (red text in the command line based
powershell.exe environment).
5. Once completed, the script should return a set of XML, without any formatting white space (no CR LF
at the end of elements, nodes, or attributes).
6. When this test is successful, run the script from a file.
Procedu re
After you have verified the script runs correctly within PowerShell, run the script from a file:
1. Save the script to a .ps1 file.
2. From a command line run the script directly:
n
For PowerShell 2.0, execute: PowerShell –command set-executionpolicy RemoteSigned –
scope Process ; scriptname.ps1 > resultfile.xml
n
For PowerShell 1.0 (with the execution policy already set to Remote Signed or less restrictive),
execute: PowerShell –file scriptname.ps1 > resultfile.xml
When the script is complete, the XML result file should be created.
3. Verify that the XML file in question can be opened in Internet Explorer (you may have to allow
blocked content in order to see the entire file). If the XML file cannot be parsed by Internet Explorer,
the formatting errors in the XML from the script will need to be corrected before the script can be used
as a collection filter script. Visual Studio can be a useful tool for finding formatting errors in larger XML
files.
For details the job status reporting for WCI, see Getting Started Collecting Windows Custom Information.
96 VMware, Inc.
Page 97

Discover, License, and Install UNIX/Linux Machines
The following steps must be performed before collecting data from UNIX/Linux machines:
1. Add UNIX/Linux machines.
2. License your UNIX/Linux machines.
3. Install the VCM Agent on your UNIX/Linux machines.
4. Perform an initial UNIX/Linux collection.
5. Explore the UNIX/Linux collection results.
These steps are explained in the following subsections.
Adding UNIX/Linux Machines
Before you can collect data from your UNIX/Linux machines, they must be displayed in the Available
UNIX Machines list located in the Portal under Administration > Machines Manager > Available
Machines.
NOTE A Discovered Machines Import Tool (DMIT) is available from VMware Customer Support to assist
you with the following process. This tool imports machines discovered by the Network Mapper (Nmap)
into the configuration database. To use the tool, contact VMware Customer Support; otherwise, use the
following process.
Getting Started with VCM
1. Click Administration > Machines Manager > Available Machines > Available UNIX Machines.
2. Click Add Machines. The Add Machines page appears.
VMware, Inc. 97
Page 98

vCenter Configuration Manager Installation and Getting Started Guide
3. Select Basic, and then click Next. The Manually Add Machines - Basic page appears.
NOTE When you expand your UNIX/Linux collections to a broader set of machines, you may want to
use other methods to add your UNIX/Linux machines. Refer to the online Help for the advanced
features such as importing from a file or using IP Discovery.
4. Enter the Machine and the Domain, and then select DNS for Type. For Machine Type, select the
appropriate operating system. Modify the port number if you are not using the default.
NOTE The port number specified must be the same number used when the Agent is installed on the
managed UNIX/Linux machine.
5. Click Add to add the entry to the list.
6. Repeat for any other machines.
7. Click Next and accept the changes.
NOTE If your Collector cannot resolve a host name with a DNS Server, be sure to use an IP address in
place of a Machine name for your machines as you enter them.
Licensing UNIX/Linux Machines
When the UNIX/Linux machines are displayed in your Available UNIX Machines list, you may begin
licensing these machines.
Upgrading Red Hat Workstations
In previous versions of VCM, either Red Hat workstations or servers were licensed as Red Hat servers.
Beginning with VCM version 5.2.0, Red Hat machines were licensed as either workstations or servers.
When you upgrade to 5.2.0 or later, the workstations previously managed with server licenses will be
unmanaged in VCM. The unmanaged Red Hat workstations should be listed in the Available UNIX
Machines list. To manage the machines in VCM, select Administration > Machines Manager > Available
Machines > Available UNIX Machines and re-license the machines using Linux/Mac Workstation licenses.
If you are not able to identify your unmanaged Red Hat machines, contact VMware Customer Support.
Use the following procedure to license your UNIX/Linux machines.
1. Click Administration > Machines Manager > Available Machines > Available UNIX Machines.
98 VMware, Inc.
Page 99

Getting Started with VCM
NOTE Remember, discovered machines with an indeterminate Machine Type will not be licensed if
they are included in your selection.
2. Select the machine(s) you want to license. To select multiple machines, use Shift-click or Ctrl-click.
3. Click License. The Machines page appears.
4. The machines that you specified appear in the Selected area. Add or remove machines from the list as
needed.
5. Click Next. The Product License Details page appears.
6. The licensed machine count has increased by the number of machines that you have selected to license.
7. Click Next. The Important page appears.
8. Review the information.
9. Click Finish.
Installing the Agent on UNIX/Linux Machines
Before collecting data from your UNIX/Linux machines, you must install the VCM Agent on each licensed
UNIX/Linux machine. For information about upgrading existing Agents, see the online Help.
IMPORTANT The Collector should be installed before the Agents are installed. The configuration
parameter CSI_USER assigns the account used to run the Agent daemon or service. If the parameter is
changed, the user account must not have a valid login shell. You must be logged in to a target UNIX/Linux
machine as root.
NOTE If you have copied your custom configuration file from a previous installation, follow the optional
step provided in this procedure. If you are using a custom configuration file, perform the installation in
Silent Mode.
Installing the Agent on UNIX/Linux machines is a manual operation.
NOTE A Deployment Tool is available from Customer Support to assist you with the following process
for UNIX/Linux. To use the tool, contact support; otherwise, follow the steps in the following process.
IMPORTANT To install the UNIX Agent on SUSE and Red Hat machines, you may need to disable or
reconfigure firewalls.
Platforms Not Supported for Upgrade to 5.4 Agent
Installing or upgrading on the following platforms is supported only to the 5.1.3 UNIX Agent. You can
install the 5.4 Agent. However, these platforms are not tested with any additional 5.4 functionality.
Platform Supp orted Agent Version Agen t File Name
AIX 4.3.3 5.1.3 CMAgent.5.1.0.AIX.4
Red Hat 2.1 5.1.3 CMAgent.5.1.0.Linux.2.1
Solaris 2.5 5.1.3 Contact VMware Customer Support if you are
installing or upgrading the Agent on this
platform.
Solaris 2.6 5.2.1 Contact VMware Customer Support if you are
installing or upgrading the Agent on this
platform.
VMware, Inc. 99
Page 100

vCenter Configuration Manager Installation and Getting Started Guide
Use the following steps to install the Agent.
1. Verify that the machine on which you intend to install the agent has enough free disk space. For more
information, see the VCM Hardware and Software Requirements Guide.
2. When VCM is installed on the VCM Collector machine, the necessary Agent packages are created in
the following locations:
\Program Files (x86)\VMware\VCM\Installer\Packages
or
The following agent binaries are available for the associated operating systems:
Operating SystemVersion Agen t Binary
Red Hat (Enterprise) Linux Edition (Version 2.1)
Red Hat (Enterprise) Linux Edition (Version 3.0, 4.0,
5.0, 5.1, 5.2, 5.3, 5.4, 5.5)
SUSE Linux Enterprise Server (9, 10),
Debian (4)
Solaris (Versions 8, 9, and 10 supported on Sparc)
Solaris (Version 10 for x86)
HP-UX 11i Versions 1.0, 2.0, 3.0 (11.11, 11.23, and
11.31; Supported on PA-RISC)
HP-UX 11i Version 2.0, 3.0 (11.23 and 11.31Supported on Itanium)
AIX Version 4.3.3
AIX Version 5L (5.1, 5.2, 5.3, and 6L (6.1))
CMAgent.<version>.Linux.2.1
CMAgent.<version>.Linux
CMAgent.<version>.SunOS
CMAgent.<version>.SunOS.x86.5.10
CMAgent.<version>.HP-UX.11.pa
CMAgent.<version>.HPUX.11.ia64
CMAgent.<version>.AIX.4
CMAgent.<version>.AIX.5
3. Copy the installation package to the machine on which you want to install the agent. You can use ftp,
sftp, or cp using an NFS share.
NOTE If you use ftp to copy the package to your machine, be sure to use binary mode.
4. Use chmod u+x <filename> to change the permissions on the agent binary file.
5. In the directory where you copied the file, execute the agent binary package to create the necessary
directory structure and extract the files. The command and output will look similar to the following
example, with differing file names depending on the operating system:
# ./CMAgent.<version>.SunOS
UnZipSFX 5.51 of 22 May 2004, by Info-ZIP (http://www.info-zip.org).
creating: CSIInstall/
creating: CSIInstall/packages/
inflating: CSIInstall/packages/Agent.1.0.SunOS
inflating: CSIInstall/packages/CFC.1.0.SunOS
inflating: CSIInstall/packages/ECMu.1.0.SunOS
inflating: CSIInstall/packages/ThirdParty.1.0.SunOS
inflating: CSIInstall/packages/cis.1.0.SunOS
extracting: CSIInstall/packages/package.sizes.SunOS
inflating: CSIInstall/packages/python.23.SunOS
creating: CSIInstall/scripts/
inflating: CSIInstall/scripts/checksum
inflating: CSIInstall/scripts/BootStrapInstall.sh
inflating: CSIInstall/scripts/AltSource_filesystem.sh
100 VMware, Inc.
 Loading...
Loading...