Page 1

Transcendent IP
Transcendent Series 4 Megapixel
4MP Cameras
Indoor/Outdoor WDR IP Dome
Cameras with IR Illumination
OPERATION MANUAL
VITEK
VITEK
FEATURES
• 1/3” 4.0 Megapixel Progressive Scan CMOS image sensor
• Up to 30fps live view @ 4 MegaPixel (2592x1520)
• Motorized Varifocal & Fixed Lens Options
• Infrared IR LED Illumination
• 120dB Super Wide Dynamic Range (WDR)
• True Mechanical Day/Night function by ICR
• XD-DNR (2D-DNR & 3D-DNR) Noise Reduction
• Fully Programmable Intelligent Analytics including Object Removal/
Museum Search, Line Crossing, and Area Intrusion Detection
• H.265/H.264/MJPEG Triple Streaming
• Secondary Video Output (CVBS)
• Remote Viewing via CMS, Internet Explorer, and iOS & Android Apps
• IP66 Weather Resistance & IK10 Impact Rating
• ONVIF Compliant
• Optional Mounts Available
• 12VDC & PoE (Power over Ethernet) Operation
Page 2

Transcendent IP Cameras v4: Operation Manual
1
n Please use the specified power supply to connect.
n Do not attempt to disassemble the camera; in order to prevent electric shock, do not remove
screws or covers.
n There are no user-serviceable parts inside. Please contact the nearest service center as soon as
possible if there is any failure.
n Avoid from incorrect operation, shock vibration, heavy pressing which can cause damage to
product.
n Do not use corrosive detergent to clean main body of the camera. If necessary, please use soft dry
cloth to wipe dirt; for hard contamination, use neutral detergent. Any cleanser for high grade
furniture is applicable.
n Avoid aiming the camera directly towards extremely bright objects, such as, sun, as this may
damage the image sensor.
n Please follow the instructions to install the camera. Do not reverse the camera, or the reversing
image will be received.
n Do not operate it incase temperature, humidity and power supply are beyond the limited
stipulations.
n Keep away from heat sources such as radiators, heat registers, stove, etc.
n Do not expose the product to the direct airflow from an air conditioner.
n This is product instructions not quality warranty. We may reserve the rights of amending the
typographical errors, inconsistencies with the latest version, software upgrades and product
improvements, interpretation and modification. These changes will be published in the latest
version without special notification.
n When this product is in use, the relevant contents of Microsoft, Apple and Google will be
involved in. The pictures and screenshots in this manual are only used to explain the usage of our
product. The ownerships of trademarks, logos and other intellectual properties related to
Microsoft, Apple and Google belong to the above-mentioned companies.
n This manual is suitable for IR water-proof network camera. All pictures and examples used in the
manual are for reference only.
Page 3

Transcendent IP Cameras v4: Operation Manual
2
Table of Contents
1 Introduction ...................................................................................................................... 4
2 IE Remote Access ............................................................................................................ 5
2.1 LAN ........................................................................................................................ 5
1.1.1 Access through IP-Tool ................................................................................................................... 5
1.1.2 Directly Access through IE .............................................................................................................. 6
2.2 WAN ....................................................................................................................... 8
3 Remote Preview ............................................................................................................. 11
4 Remote Live Surveillance .............................................................................................. 12
1.2 System Configuration ............................................................................................... 12
1.2.1 Basic Information ........................................................................................................................... 12
1.2.2 Date and Time ............................................................................................................................... 12
1.2.3 Local Config .................................................................................................................................. 13
1.2.4 Storage .......................................................................................................................................... 13
1.3 Image Configuration ................................................................................................. 14
1.3.1 Display Configuration .................................................................................................................... 14
1.3.2 Video / Audio Configuration ........................................................................................................... 15
1.3.3 OSD Configuration ........................................................................................................................ 17
1.3.4 Video Mask .................................................................................................................................... 17
1.3.5 ROI Configuration .......................................................................................................................... 18
1.4 Alarm Configuration .................................................................................................. 19
1.4.1 Motion Detection ........................................................................................................................... 19
1.4.2 Alarm Server ................................................................................................................................. 21
1.5 Event Configuration .................................................................................................. 21
1.5.1 Object Removal ............................................................................................................................. 21
1.5.2 Exception ....................................................................................................................................... 23
1.5.3 Line Crossing ................................................................................................................................ 25
1.5.4 Intrusion ......................................................................................................................................... 26
1.6 Network Configuration .............................................................................................. 28
1.6.1 TCP/IP ........................................................................................................................................... 28
1.6.2 Port ................................................................................................................................................ 29
1.6.3 Server Configuration ..................................................................................................................... 30
1.6.4 DDNS ............................................................................................................................................ 30
1.6.5 SNMP ............................................................................................................................................ 31
1.6.6 RTSP ............................................................................................................................................. 32
1.6.7 UPNP ............................................................................................................................................ 33
1.6.8 Email ............................................................................................................................................. 33
1.6.9 FTP ................................................................................................................................................ 34
4.1 Security Configuration ....................................................................................... 35
1.6.10 User Configuration ...................................................................................................................... 35
1.6.11 Online User ................................................................................................................................. 37
1.6.12 Block and Allow Lists ................................................................................................................... 37
Page 4

Transcendent IP Cameras v4: Operation Manual
3
4.2 Maintenance Configuration ............................................................................... 37
1.6.13 Backup and Restore .................................................................................................................... 37
1.6.14 Reboot ......................................................................................................................................... 38
1.6.15 Upgrade ....................................................................................................................................... 38
1.6.16 Operation Log .............................................................................................................................. 39
5 Record Search ................................................................................................................ 40
5.1 Photo Search ...................................................................................................... 40
5.2 Photo Search ...................................................................................................... 40
5.3 Video Search ....................................................................................................... 41
1.6.17 Local Video Search ..................................................................................................................... 41
1.6.18 SD Card Video Search ................................................................................................................ 42
1.6.19 This feature is camera dependent; some cameras do not have an SD card slot. ....................... 42
6 Specifications ................................................................................................................. 43
Page 5
Transcendent IP Cameras v4: Operation Manual
4
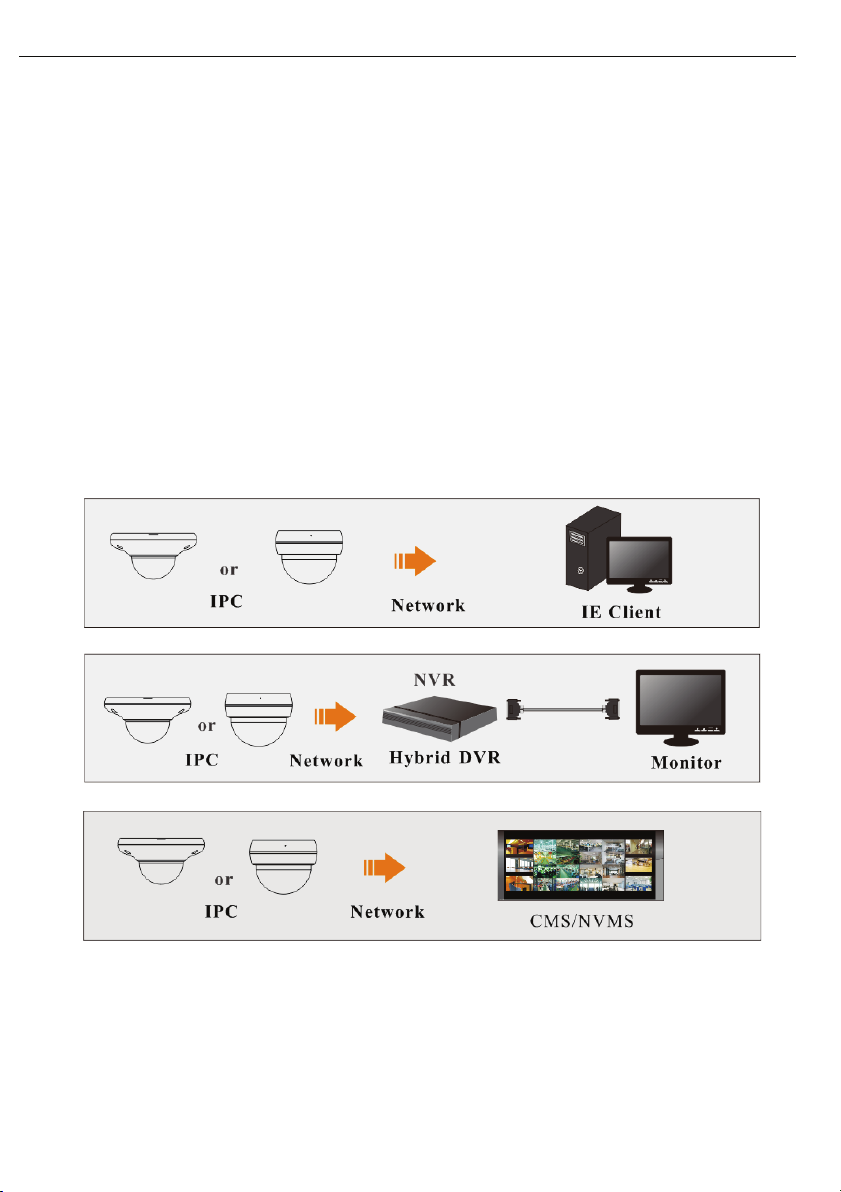
1 Introduction
This IP camera is designed for high performance CCTV solutions. It adopts state of the art video
processing chips. It utilizes most advanced technologies, such as video encoding and decoding
technology, complies with the TCP/IP protocol, SoC, etc to ensure this system is more stable and
reliable.
Main Features
l ICR auto switch, true day/night
l 3D DNR, digital WDR
l ROI coding
l BLC, Defog, Anti-flicker
l Supports smart phones & tablets for remote monitoring
Surveillance Application
Page 6

Transcendent IP Cameras v4: Operation Manual
5
2 IE Remote Access
2.1 LAN
In LAN, there are two ways to access the IP-Cam: 1. access through IP-Tool; 2. directly access through
IE browser.
1.1.1 Access through IP-Tool
Network connection:
� Make sure the PC and IP-Cam are connected to the LAN and the IP-Tool is installed in the PC from
the CD.
Double click the IP-Tool icon on the desktop to run this software as shown below:
②
Modify the IP address. The default IP address of this camera is 192.168.226.201. Click the
③
information of the camera listed in the above table to show the network information on the right side.
Modify the IP address and gateway of the camera and make sure its network address is in the same
local network segment as that of the computer. Please modify the IP address of your device according
to the practical situation.
Page 7

Transcendent IP Cameras v4: Operation Manual
6
For example, the IP address of your computer is 192.168.1.4. So the IP address of the camera shall be
changed to 192.168.1.X. After modification, please input the ADMIN password of the administrator
and click “Modify” button to modify the setting.
F
browser will ask to download the Active X control. After downloading, a login window will pop up as
shown below.
Input the username and password to log in.
F
The default password of the administrator is “123456”.
Double click the IP address and then the system will pop up IE browser to connect IP-CAM. IE
④
The default username is “admin”; the default password is “123456”.
1.1.2 Directly Access through IE
The default network settings are as shown below:
IP address: 192.168.226.201
Subnet Mask: 255.255.255.0
Gateway: 192.168.226.1
HTTP: 80
Data port: 9008
Page 8
Transcendent IP Cameras v4: Operation Manual
7
You may use the above default settings when you log in the camera for the first time. You may directly
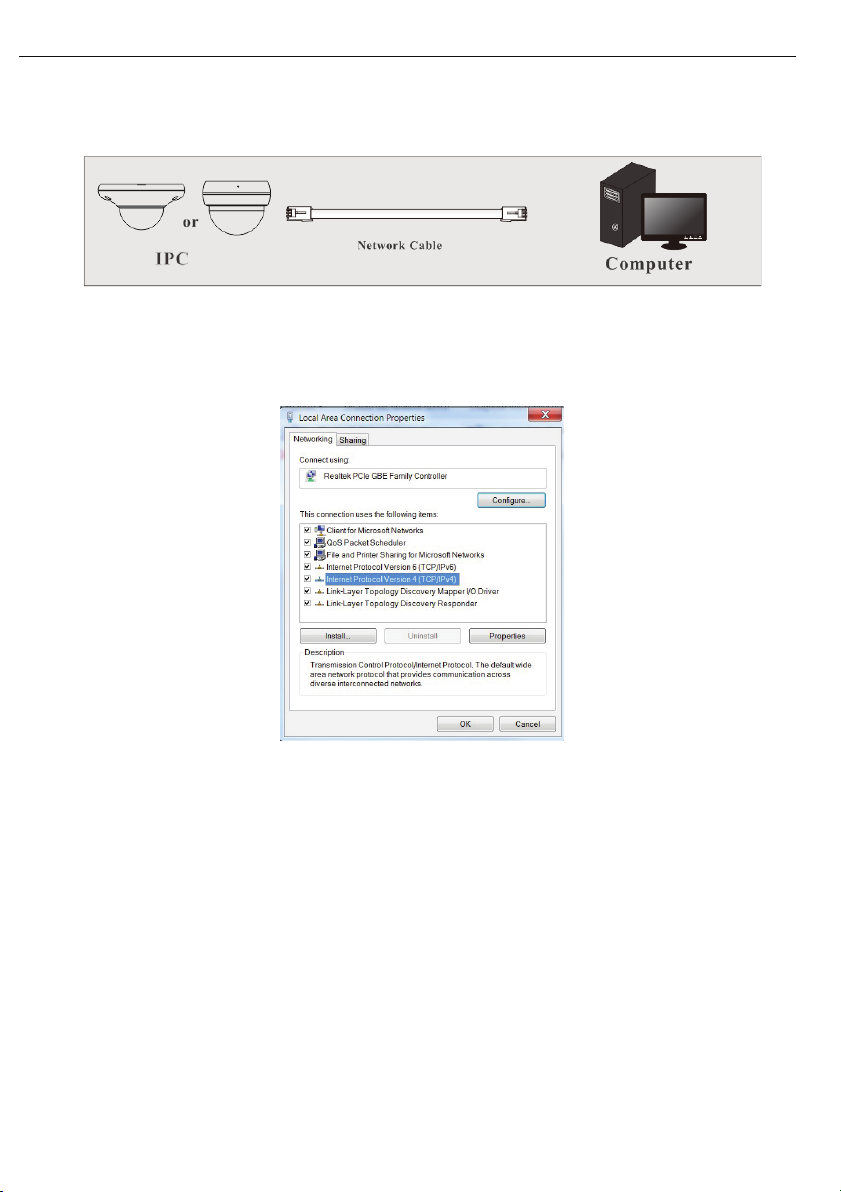
connect the camera to the computer through network cable.
� Manually set the IP address of the PC as the network segment should be as the same as the default
settings of the IP camera. Open the network and share center. Click “Local Area Connection” to pop
up the following window.
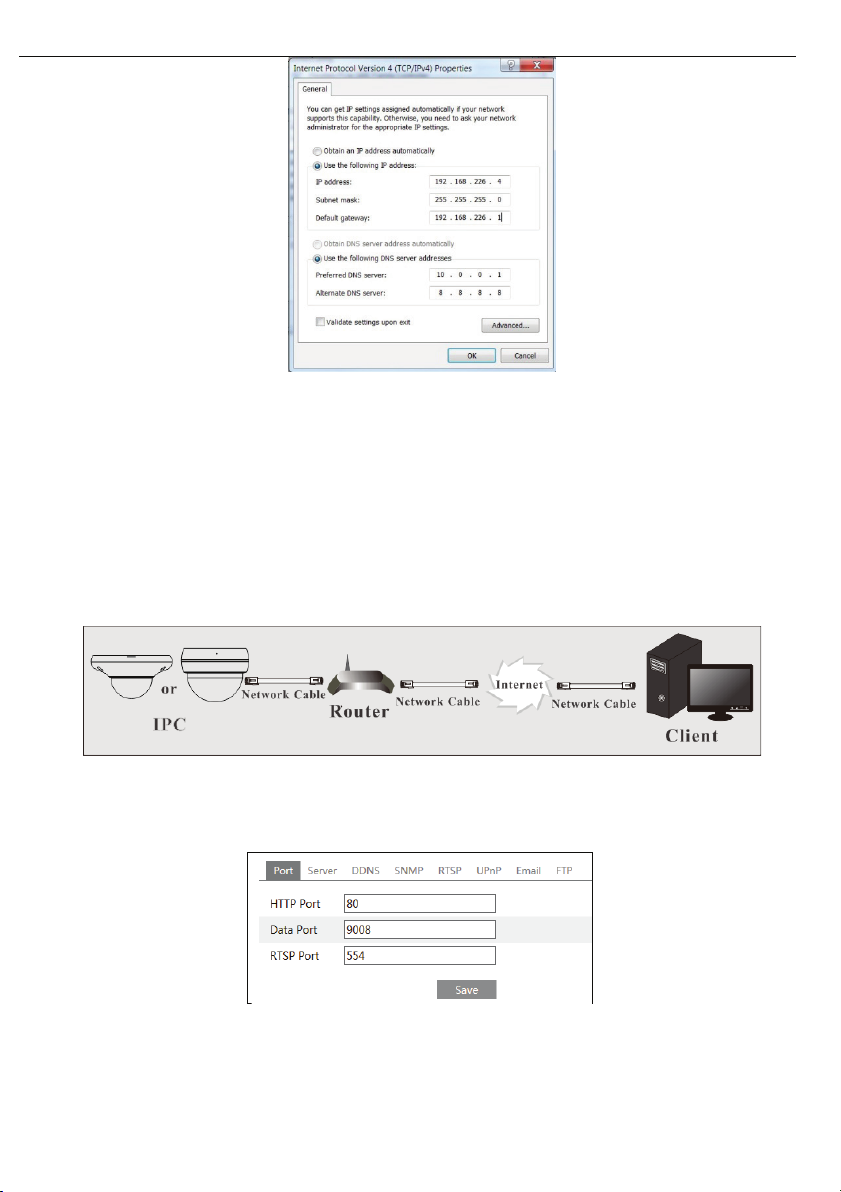
Select “Properties” and then select internet protocol according to the actual situation (for example:
IPv4). Next, click “Properties” button to set the network of the PC.
Page 9
Transcendent IP Cameras v4: Operation Manual
8
Open IE browser and input the default address of IP-CAM and confirm. IE browser will ask to
②
download the Active X control.
After downloading the Active X control, the login dialog box will pop up.
③
Input the default username and password and then enter to view.
④
2.2 WAN
Ø Access through the router or virtual server
� Make sure the camera is connected via LAN and then log into the camera via LAN and go to
ConfigàNetworkàPort to set the port number.
Port Setup
Go to ConfigàNetworkàTCP/IP menu to modify the IP address.
②
Page 10
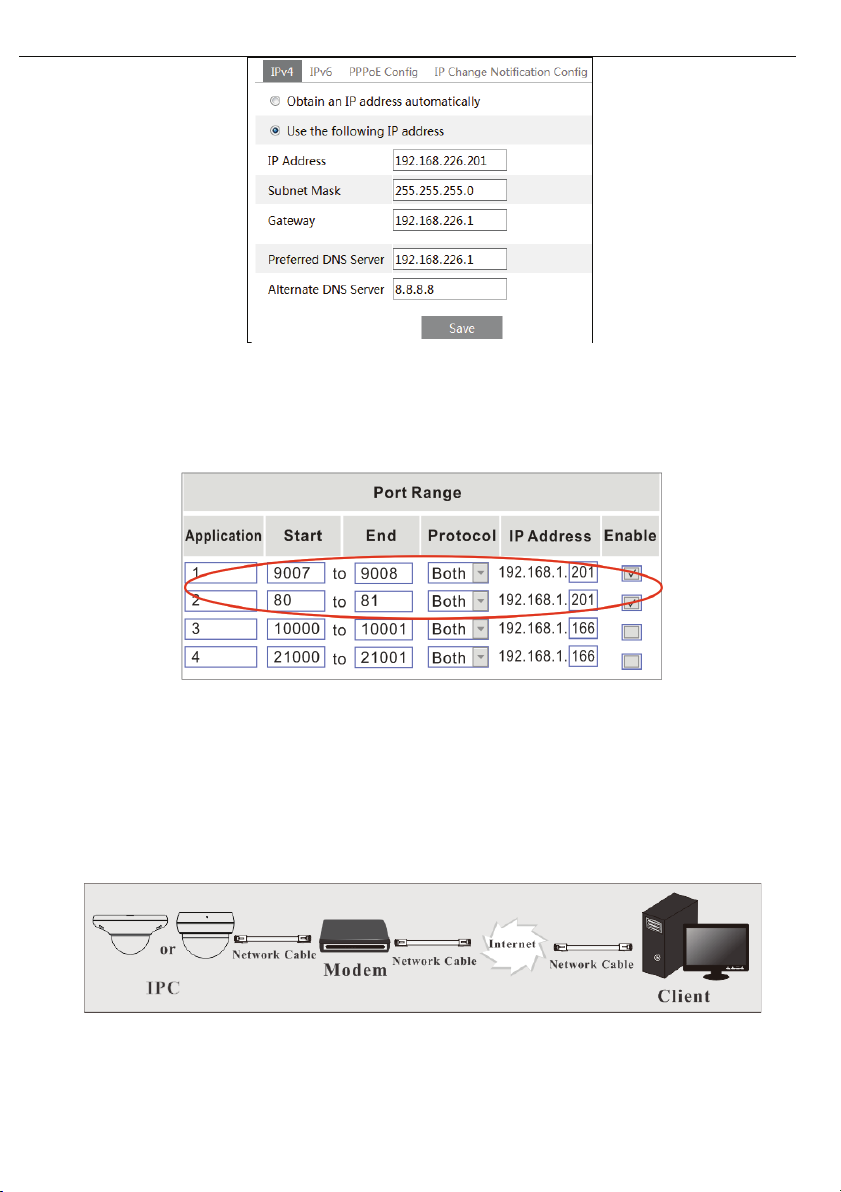
Transcendent IP Cameras v4: Operation Manual
9
IP Setup
Go to the router’s management interface through IE browser to forward the IP address and port of
③
the camera. Please check your router manual for instructions on port forwarding.
Router Setup
Open IE browser and input its WAN IP and http port to access.
④
Ø Access through PPPoE dial-up
Network connection
You may access the camera through PPPoE auto dial-up. The setting steps are as follow:
Go to ConfigàNetworkàPort to set the port number.
①
Page 11
Transcendent IP Cameras v4: Operation Manual
10
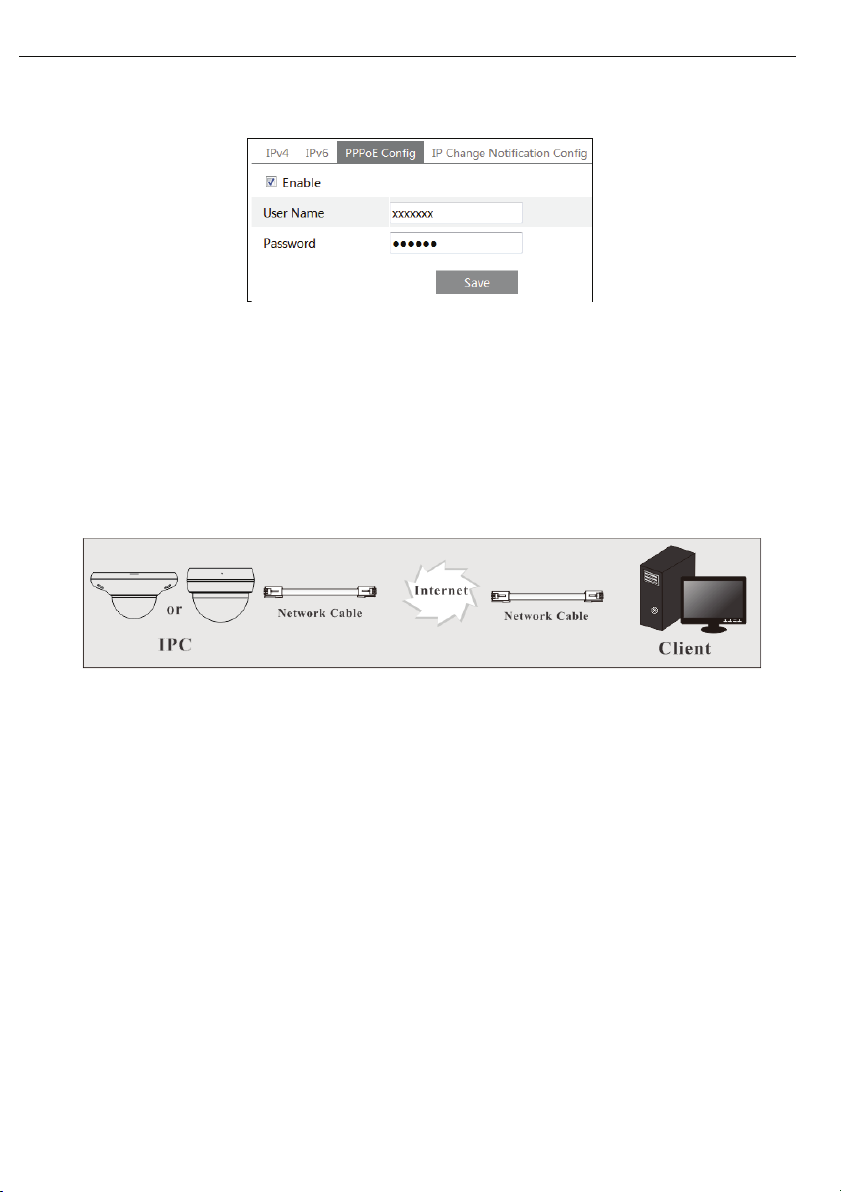
Go to ConfigàNetworkàTCP/IPà PPPoE Config menu. Enable PPPoE and then input the user
②
name and password which you can get from your internet service provider.
Go to ConfigàNetworkàDDNS menu. Before you configure the DDNS, please apply for a
③
domain name first. Please refer to DDNS configuration for detail information.
Open IE browser and input the domain name and http port to access.
④
Ø Access through static IP
Network connection
The setting steps are as follow:
� Go to ConfigàNetworkàPort to set the port number.
� Go to ConfigàNetworkàTCP/IP menu to set the IP address. Check “Use the following IP address”
and then input the static IP address and other parameters.
�Open IE browser and input its WAN IP and http port to access.
Page 12
Transcendent IP Cameras v4: Operation Manual
11
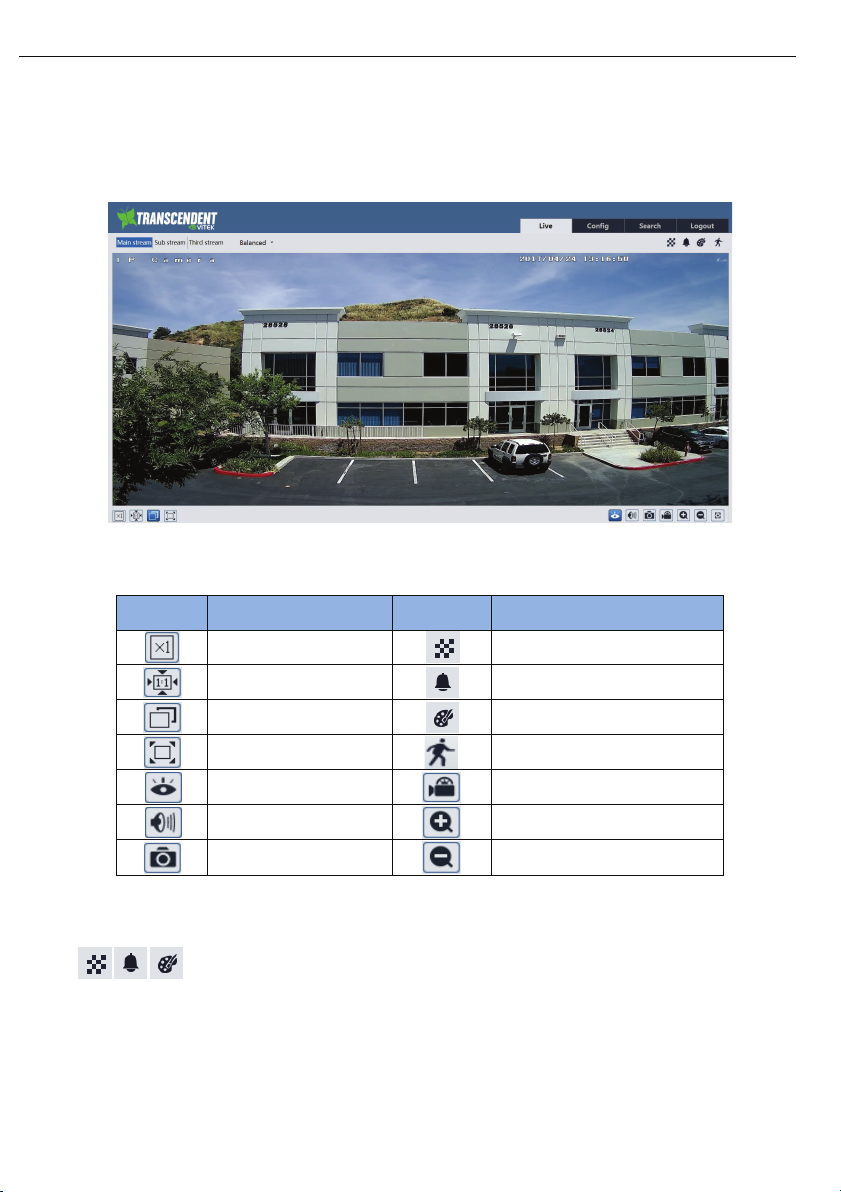
3 Remote Preview
After you log in, you will see the following window.
The following table is the instructions of the icons on the remote live interface.
Icon Description Icon Description
Original size
Appropriate size
Auto
Full screen
Start/stop live view
Enable/disable audio
Snap
When motion detection alarm is triggered, the people icon will turn red.
l
l In full screen mode, double click to exit.
l icons may not be displayed for some versions without intelligent analysis function.
Scene change indicator icon
Abnormal clarity indicator icon
Color abnormal indicator icon
Motion alarm indicator icon
Start/stop recording
Zoom in
Zoom out
Page 13
Transcendent IP Cameras v4: Operation Manual
12
4 Remote Live Surveillance
1.2 System Configuration
The “System” configuration includes four submenus: Basic Information, Date and Time, Local Config
and storage.
1.2.1 Basic Information
In the “Basic Information” interface, you can check the relative information of the device.
1.2.2 Date and Time
Go to ConfigàSystemàDate and Time. Please refer to the following interface.
You can select the time zone and DST as required.
Click “Date and Time” tab to set the time mode.
Page 14
Transcendent IP Cameras v4: Operation Manual
13
1.2.3 Local Config
Go to ConfigàSystemàLocal Config. You can set the storage path of the captured pictures and video
records. You can also enable or disable the video audio.
1.2.4 Storage
Go to ConfigàSystemàStorage to go to the interface as shown below.
The first time you use the SD card, you should click “Format” button to format the SD card.
Click “Pop Up” button to stop writing data to SD card. Then the SD card can be ejected safely.
F
Go to ConfigàSystemàStorageàRecord to go to the interface as shown below. You can set the SD
Note: Using the SD card function should be coordinated with motion alarm.
When alarm is triggered, the system will automatically snap picture and save
the picture or record into SD card.
Page 15
Transcendent IP Cameras v4: Operation Manual
14
card record stream. Set the pre record time if you enable pre record. Click “Save” button to save the
settings.
Pre Record Time: Set the time to record before the actual recording begins.
1.3 Image Configuration
Image Configuration includes Display, Video/Audio, OSD, Video Mask, ROI Config and
Zoom/Focus.
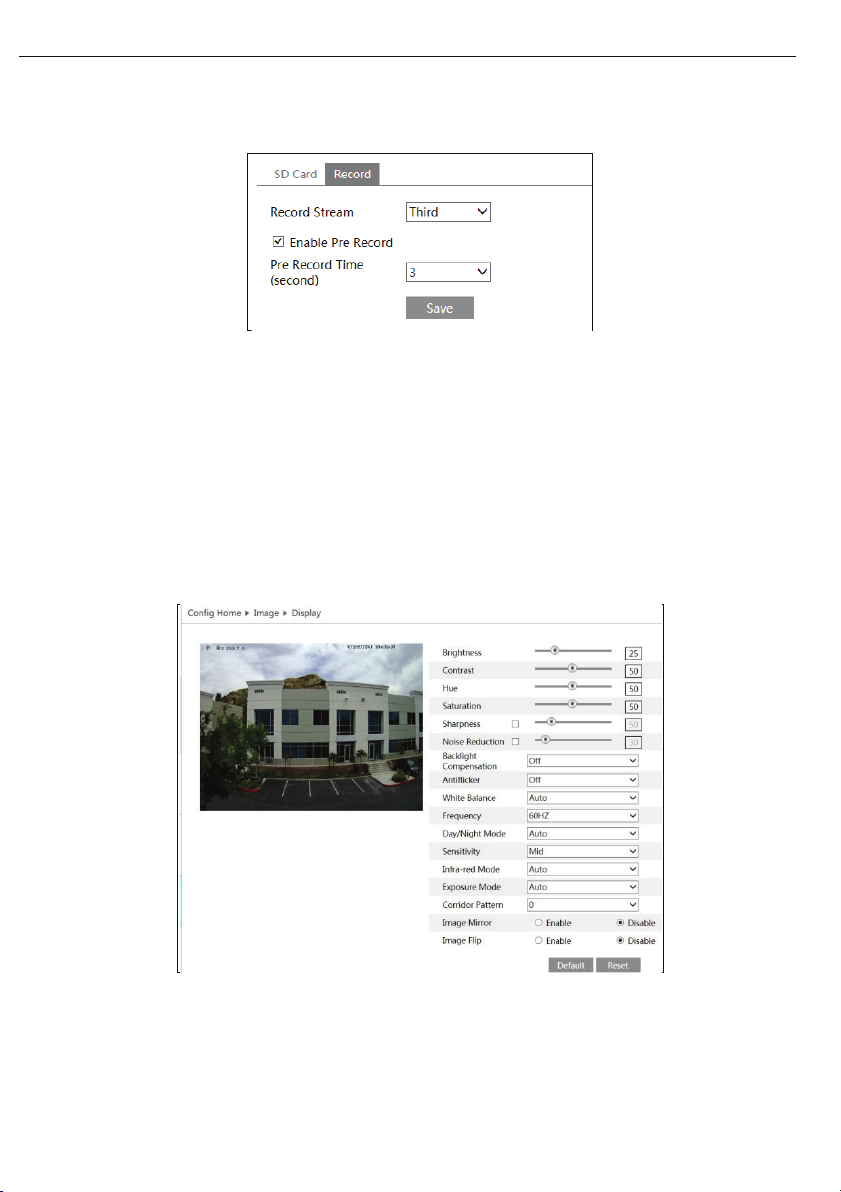
1.3.1 Display Configuration
Go to ImageàDisplay interface as shown below. You can set and adjust the picture’s brightness,
contrast, hue and saturation, etc.
Brightness: Set the brightness level of the camera’s image.
Contrast: Set the color difference between the brightest and darkest parts.
Hue: Set the total color degree of the image.
Saturation: Set the degree of color purity. The purer the color is, the brighter the image is.
Sharpness: Set the resolution level of the image plane and the sharpness level of the image edge.
Page 16

Transcendent IP Cameras v4: Operation Manual
15
Noise Reduction: Decrease the noise and make the image more thorough. Increasing the value will
make the noise reduction effect better but it will reduce the image resolution.
Backlight Compensation:
l Off: Close the backlight compensation function. It is the default mode.
l WDR
u As to the WDR scene, WDR will help the camera provide clear images when there are both very
bright and very dark areas simultaneously in the field of view by lowering the brightness of the bright
area and increasing the brightness of the lowlight area. High, middle and low can be selected.
u There will be some recording lost for a few seconds during mode changing from non-WDR to
WDR mode.
l HLC: Lower the brightness of the whole image by suppressing the brightness of the image’s
highlight area and reducing the size of the halo area.
l BLC: The exposure will begin automatically according to the scene for the goal of seeing the
darkest area of the image.
HFR:High frame rate mode. You may enable or disable it as needed.
Antiflicker:
l Off: Close the anti-flicker function.
l 50Hz: Makes sure the horizontal stripes will not appear in the image while the device is adjusting
the exposure automatically according to the brightness of the scene when the electric supply is 50Hz.
l 60Hz: Makes sure the horizontal stripes will not appear in the image while the device is adjusting
the exposure automatically according to the brightness of the scene when the electric supply is 60Hz.
White Balance: Adjust the color temperature according to the environment automatically.
Frequency: 50Hz and 60Hz (50Hz= PAL(Europe) 60Hz= NTSC (North America)).
Day/night Mode: Please choose the mode as needed.
Auto= will change to Black & White in low light
Day= Camera will be in color all the time
Night= Camera will be in Black & White all the time
Schedule= set a particular time the camera switches to Night mode or Day mode
Sensitivity: High, middle and low can be selected.
Infrared Mode: You may choose “ON”, “OFF” and “Auto” as required.
Exposure Mode: You may choose “Auto” or “Manual” as required.
Corridor Pattern: You can change the direction of the video image by using this function. 0, 90, 180
and 270 are available. The default value is 0. The video resolution should be 1080P or under 1080P if
you use this function.
Image Mirror: Reverse the current video image right and left.
Image Flip: Turn the current video image upside down.
1.3.2 Video / Audio Configuration
Go to ImageàVideo / Audio interface as shown below. In this interface, you can set the resolution,
frame rate, bitrate type, video quality and so on subject to the actual network condition.
Page 17

Transcendent IP Cameras v4: Operation Manual
16
Click “Audio” tab to go to the interface as shown below.
Three video streams can be adjustable.
Resolution: The higher the resolution is, the clearer the image is.
Frame rate: The higher the frame rate is, the more fluid the video is. However, more storage room
will be taken up.
Bitrate type: Including CBR and VBR. CBR means that no matter how the video changes, the
compression bitrate keeps constant. This will not only facilitate the image quality better in a constant
bitrate but also help to calculate the capacity of the recording. VBR means that the compression bitrate
can be adjustable according to the change of the video resources. This will help to optimize the
network bandwidth.
Bitrate: Please choose it according to the actual network situation.
Video Quality: When VBR is selected, you need to choose image quality. The higher the image
quality you choose, the more bitrate will be required.
I Frame interval: It is recommended to use the default value. If the value is to high, the read speed of
the group of pictures will be slow resulting in the quality loss of the video.
Video Compression: H264 and H265 are optional. Higher quality of image can be transferred under
limited network bandwidth by using H265 video encoding; however, higher quality of the hardware is
required.
Profile: Baseline, main/high profiles are optional. Baseline profile is mainly used in interactive
application with low complexity and delay. Main/high profile is mainly used for higher coding
requirement.
Send Snapshot: Please select according to the actual situation.
Video encode slice split: If enabled, you may get a more fluid image even though using a
low-performance PC.
Watermark: If enabled, input the watermark content. You may check the watermark when playing
back the local recording in the search interface, unless the recording file has been tampered with.
Audio Encoding: G711A and G711U are selectable.
Audio Type: MIC and LIN are selectable.
Page 18

Transcendent IP Cameras v4: Operation Manual
17
1.3.3 OSD Configuration
Go to ImageàOSD interface as shown below.
You can set the time stamp, device name and OSD content here. After enabling the corresponding display
and entering the content, drag them to change their position. Then click “Save” button to save the settings.
1.3.4 Video Mask
Go to ImageàVideo Mask interface as shown below. You can set 4 mask areas at most.
To set up video mask:
1. Enable video mask.
2. Click “Draw Area” button and then drag the mouse to draw the video mask area.
3. Click “Save” button to save the settings.
4. Return to live view to see the following picture.
Page 19

Transcendent IP Cameras v4: Operation Manual
18
Clear the video mask:
Go to video mask interface and then click “Clear” button to delete the current video mask area.
1.3.5 ROI Configuration
Go to ImageàROI Config interface as shown below.
1. Check “Enable” and then click “Draw Area” button.
2. Drag the mouse to set the ROI area.
3. Set the level.
4. Click “Save” button to save the settings.
Now, you will see the selected ROI area is clearer than other areas especially in a low bitrate condition.
Page 20

Transcendent IP Cameras v4: Operation Manual
19
1.4 Alarm Configuration
Alarm configuration includes two submenus: Motion Detection and Alarm Server.
1.4.1 Motion Detection
Go to AlarmàMotion Detection to set motion detection alarm.
1. Check “Enable Alarm” check box to activate motion based alarm, choose alarm holding time and set
alarm trigger options.
Trigger Snap: If selected, the system will snap images on an alarm and save the images to the SD
card.
Trigger SD Recording: If selected, the recording will be triggered and saved to the SD card on an
alarm.
Trigger Email: If “Trigger Email” and “Attach Picture” checkbox is checked (email address shall be
set first in the Email configuration interface), the captured pictures and triggered event will be sent to
those addresses.
Trigger FTP: If “Trigger FTP” and “Attach Picture” checkbox is checked, the captured pictures will
be sent to the FTP server address. Please refer to FTP configuration chapter for more details.
2. Set motion detection area and sensitivity. Click “Area and Sensitivity” tab to go to the interface as
shown below.
Page 21

Transcendent IP Cameras v4: Operation Manual
20
Move the “Sensitivity” scroll bar to set the sensitivity.
Select “Add” and click “Draw” button and drag mouse to select the motion detection area; Select
“Erase” and drag the mouse to clear motion detection area.
Select “Select All” to select the whole image for motion
Select “Clear All” to undo the whole picture
Select “Invert” to reverse the motion area
After that, click “Save” to save the settings.
3. Set the schedule of the motion detection. Click “Schedule” tab to go to the interface as shown below.
Week schedule
Page 22

Transcendent IP Cameras v4: Operation Manual
21
Set the alarm time from Sunday to Saturday for alarm everyday in one week. The lengthwise means
one day of a week; the rank means 24 hours of a day. Green means selected area. Blank means
unselected area.
“Add”: Add the schedule.
“Erase”: Delete schedule.
Holiday Schedule
Set time for alarm in Holiday time line.
Set a date in the “Date” box, click “Add” button to add that date to the list box on the right side and
then drag the scroll bar to set the schedule of that day.
Select a date in the list box on the right side, and click “Delete” to remove the schedule on that day.
Click “Save” button to save the settings.
1.4.2 Alarm Server
Go to AlarmàAlarm Server interface as shown below.
Input the alarm server address and port. When an alarm happens, the camera will automatically transfer
the alarm event to the alarm server. If the alarm server is not used, there is no need for you to configure
here.
1.5 Event Configuration
Event configuration includes four submenus: Object Removal, Exception, Line Crossing and Intrusion.
Note: Some software versions of this series of cameras may not support the following functions.
Please take actual displayed interface as final.
1.5.1 Object Removal
To set object removal:
Go to ConfigàEventàObject Removal interface as shown below.
Page 23

Transcendent IP Cameras v4: Operation Manual
22
1. Enable object removal detection and then select the detection type.
Enable Left Detection: The relevant alarms will be triggered if there are items left in the pre-defined
alarm area.
Enable Item Missing Detection: The relevant alarms will be triggered if there are items missing in the
pre-defined alarm area.
2. Set the alarm holding time and alarm trigger options. The setting steps are the same as that of motion
detection. Please refer to motion detection chapter for details.
3. Click “Save” button to save the settings.
4. Set the alarm area of the object removal detection. Click “Area” tab to go to the interface as shown
below.
Set the alarm area number and then input the alarm area name on the right side. You can add 4 alarm
areas at most.
Click “Draw Area” button and then click around the area where you want to set as the alarm area in the
image on the left side (the alarm area should be a closed area). Click “Stop Draw” button to stop
Page 24

Transcendent IP Cameras v4: Operation Manual
23
running on the road,
drawing. Click “Clear” button to delete the alarm area. Click “Save” button to save the settings.
5. Set the schedule of the object removal detection. The setting steps of the schedule are the same with
that of motion detection. Please refer to motion detection chapter for details.
※
Application Scenario Illustration
1. Object removal detection cannot determine the objects’ ownership. For instance, there is an
unattended package in the station. Object removal detection can detect the package itself but it cannot
determine ownership of the package.
2. Try not to enable object removal detection when light changes dramatically in the scene.
3. Try not to enable object removal detection if there are complex and dynamic environments in the
scene.
4. Adequate light and clear scenery are very important to object removal detection.
Here we take some improper application scenarios for instance.
There are so many trees
near the road and cars
which make the scene too
complex to detect the
objects removal.
1.5.2 Exception
To set exception detection:
Go to ConfigàEventàException interface as shown below.
Page 25

Transcendent IP Cameras v4: Operation Manual
24
1. Enable the relevant detection as required.
Scene Change Detection: The relevant alarms will be triggered if the scene of the monitor video has
changed.
Video Blur Detection: The relevant alarms will be triggered if the monitor video is blurry.
Video Cast Detection: The relevant alarms will be triggered if color cast happens to the monitor
video.
2. Set the alarm holding time and alarm trigger options. The setting steps are the same with that of
motion detection. Please refer to motion detection chapter for details.
3. Click “Save” button to save the settings.
4. Set the sensitivity of the exception detection. Click “Sensitivity” tab to go to the interface as shown
below.
Drag the slider to set the sensitivity value or directly input the sensitivity value in the textbox. Click
“Save” button to save the settings.
The sensitivity value of Scene Change Detection: The higher the value is, the more sensitive the
system responds to the amplitude of the scene change.
The sensitivity value of Video Blur Detection: The higher the value is, the more sensitive the system
responds to the defocus of the device image. You should adjust the value according to the real
situation.
The sensitivity value of Video Cast Detection: The higher the value is, the more sensitive the system
responds to the color cast of the device image. You should also consider other factors.
※
Application Scenario Illustration
Page 26

Transcendent IP Cameras v4: Operation Manual
25
1. Auto-focusing function should not been enabled for exception detection.
2. Try not to enable object removal detection when light changes dramatically in the scene.
1.5.3 Line Crossing
Line Crossing: The relevant alarms will be triggered if someone or something crosses the pre-defined
alarm lines.
Go to ConfigàEventàLine Crossing interface as shown below.
1. Enable line crossing alarm and set the alarm holding time.
2. Set alarm trigger options. The setting steps are the same with that of motion detection. Please refer
to motion detection chapter for details.
3. Click “Save” button to save the settings.
4. Set area and sensitivity of the line crossing alarm. Click “Area and Sensitivity” tab to go to the
interface as shown below.
Page 27

Transcendent IP Cameras v4: Operation Manual
26
Set the cordon number and direction. You can add 4 cordons at most.
Direction:A<->B, A->B and A<-B optional. It is the crossing direction of the intruder who crosses
over the alarm line.
A<->B: The alarm will be triggered when the intruder crosses over the alarm line from B to A or from
A to B.
A->B: The alarm will be triggered when the intruder crosses over the alarm line from A to B.
A<-B: The alarm will be triggered when the intruder crosses over the alarm line from B to A.
Click “Draw” button and then drag the mouse to draw a cordon in the image on the left side. Click
“Stop” button to stop drawing. Click “Clear” button to delete the cordons. Click “Save” button to save
the settings.
5. Set the schedule of the line crossing alarm. The setting steps of the schedule are the same with that
of motion detection. Please refer to motion detection chapter for details.
※
Application Scenario Illustration
1. Auto-focusing function should not been enabled for line crossing detection. If enabled, the video
image will change so greatly that the algorithm will stop working temporarily.
2. Try not to enable line crossing detection when light changes dramatically in the scene.
3. Adequate light and clear scenery are very important to line crossing detection.
4. Adjust the camera to make the detection area in the center of the video image. Make sure no
obstructions are in the main crossing area. It is strongly recommended to make the obstructions (like
trees, bushes, flags, etc.) outside the detection area.
Here we take some improper application scenarios for instance.
There are so many trees
near the road and cars
running on the road,
which make the scene
too complex to detect the
crossing objects.
1.5.4 Intrusion
Intrusion: The relevant alarms will be triggered if someone or something intrudes into the alarm areas
or moves in the pre-defined alarm areas.
Go to Config
àEventàIntrusion interface as shown below.
Page 28

Transcendent IP Cameras v4: Operation Manual
27
1. Enable region intrusion detection alarm and set the alarm holding time.
2. Set alarm trigger options. The setting steps are the same with that of motion detection. Please refer
to motion detection chapter for details.
3. Click “Save” button to save the settings.
4. Set the alarm area of the intrusion detection. Click “Area” tab to go to the interface as shown below.
Set the alarm area number on the right side. You can add 4 alarm areas at most.
Click “Draw Area” button and then click around the area where you want to set as the alarm area in the
image on the left side (the alarm area should be a closed area). Click “Stop Draw” button to stop
drawing. Click “Clear” button to delete the alarm area. Click “Save” button to save the settings.
5. Set the schedule of the intrusion detection. The setting steps of the schedule are the same with that of
motion detection. Please refer to motion detection chapter for details.
※
Application Scenario Illustration
1. Auto-focusing function should not been enabled for intrusion detection. If enabled, the video image
Page 29

Transcendent IP Cameras v4: Operation Manual
28
will change so greatly that the algorithm will stop working temporarily.
2. Try not to enable intrusion detection when light changes dramatically in the scene.
3. Adequate light and clear scenery are very important to intrusion detection.
4. Adjust the camera to make the detection area in the center of the video image. The detected object
should be in the detection area for about two seconds at least. Make sure no obstructions are in the
main crossing area. It is strongly recommended to make the obstructions (like trees, bushes, flags, etc.)
outside the detection area.
Here we take some improper application scenarios for instance.
The camera’s angle of view
is not wide enough; there are
so many trees in the scene.
The above mentioned
environment is too com plex
to detect the intrusion.
1.6 Network Configuration
1.6.1 TCP/IP
Go to ConfigàNetworkàTCP/IP interface as shown below. There are two ways for network
connection.
Use IP address (take IPv4 for example)-There are two options for IP setup: obtain an IP address
automatically by DHCP protocol and use the following IP address. Please choose one of the options for
Page 30

Transcendent IP Cameras v4: Operation Manual
29
your requirements.
Use PPPoE-Click “PPPoE Config” tab to go to the interface as shown below. Enable PPPoE and then
enter the user name and password from your ISP.
You can choose either way for the network connection. If you use PPPoE to connect internet, you will
get a dynamic WAN IP address. This IP address will change frequently. You may use the function of
IP change notification.
Click “IP Change Notification Config” to go to the interface as shown below.
Trigger Email: when the IP address of the device is changed, a new IP address will be sent to the
appointed mailbox automatically
Trigger FTP: when the IP address of the device is changed, a new IP address will be sent to FTP
server.
1.6.2 Port
Go to ConfigàNetworkàPort interface as shown below. HTTP port, Data port and RTSP port can be
set.
HTTP Port: The default HTTP port is 80. It should be changed to any port which is not occupied.
Data Port: The default data port is 9008. Please change it as required.
RTSP Port: The default port is 554. Please change it as required.
Page 31

Transcendent IP Cameras v4: Operation Manual
30
1.6.3 Server Configuration
This function is mainly used for connecting network video management system.
1. Check “Enable”.
2. Check the IP address and port of the transfer media server in the Transcendent VMS. Then enable
the auto report in the Transcendent VMS when adding a new device. Next, input the remaining
information of the device in the Transcendent VMS. After that, the system will auto allot a device ID.
Please check it in the Transcendent VMS.
3. Input the above-mentioned server address, server port and device ID in the responding boxes. Click
“Save” button to save the settings.
1.6.4 DDNS
If your camera is set to use PPPoE as its default network connection, DDNS should be set for network
access. Before you set the DDNS, please make sure you have registered a domain name on the DDNS
server.
1. Go to ConfigàNetworkà DDNS.
2. Apply for a domain name. Take www.dvrdyndns.com for example.
Input www.dvrdydns.com in the IE address bar to visit its website. Then click “Registration” button.
Page 32

Transcendent IP Cameras v4: Operation Manual
31
Create domain name.
After you successfully request your domain name, you will see your domain in the list.
3. Input the username, password, domain you apply for in the DDNS configuration interface.
4. Click “Save” button to save the settings.
1.6.5 SNMP
To get camera status, parameters and alarm information and remotely manage the camera, you can set
the SNMP function. Before using the SNMP, please download the SNMP software and set the
parameters of the SNMP, such as SNMP port, trap address.
1. Go to ConfigàNetworkàSNMP.
Page 33

Transcendent IP Cameras v4: Operation Manual
32
2. Check the corresponding version checkbox (Enable SNMPv1, Enable SNMPv2, Enable SNMPv3)
according to the version of the SNMP software you download.
3. Set the “Read SNMP Community”, “Write SNMP Community”, “Trap Address”, “Trap Port” and
so on. Please make sure the settings are the same as that of your SNMP software.
Note: Please use the different version in accordance with the security level you required. The higher
the version is, the higher the level of the security is.
1.6.6 RTSP
Go to ConfigàNetworkàRTSP.
Page 34

Transcendent IP Cameras v4: Operation Manual
33
1. Select “Enable”.
2. RTSP Port: Access port of the streaming media. The default number is 554.
3. RTSP Address: The RTSP address you need to input in the media player.
4. Check “Allow anonymous login…”.
1.6.7 UPNP
If you enable this function, you can quickly access the camera via LAN and you don’t need to
configure the port mapping when the camera is connected to the WAN via the router.
Go to ConfigàNetworkàUPnP. Enable UPNP and then input UPnP name.
After you enable it and set the UPnP name, you will see the UPnP name by clicking “Network” on the
desktop of your computer which is in the same local area network. Then double click this name to
access the camera quickly.
1.6.8 Email
If you need to trigger Email when an alarm happens or IP address is changed, please set the Email here
first.
Go to ConfigàNetwork àEmail.
Page 35

Transcendent IP Cameras v4: Operation Manual
34
Sender Address: Sender’s e-mail address.
User name and password: Sender’s user name and password.
Server Address: The SMTP IP address or host name.
Select the secure connection type at the “Secure Connection” pull-down list according to actual needs.
SMTP Port: The SMTP port.
Send Interval(S): Set it as needed.
Click “Test” button to test the effectiveness of the account.
Recipient Address: Receiver’s e-mail address.
1.6.9 FTP
After you set the FTP server, the captured pictures on an alarm will be uploaded to the FTP server.
Go to ConfigàNetwork àFTP.
Page 36

Transcendent IP Cameras v4: Operation Manual
35
To Add FTP:
Server Name: The name of the FTP.
Server Address: The IP address or domain name of the FTP.
Upload Path: The path of uploading the files.
Port: The port of the FTP.
Use Name and Password: The username and password are used to login the FTP.
4.1 Security Configuration
1.6.10 User Configuration
Go to ConfigàSecurityàUser interface as shown below.
Add user:
1. Click “Add” button to pop up the following textbox.
Page 37

Transcendent IP Cameras v4: Operation Manual
36
2. Input user name in “User Name” textbox.
3. Input letters or numbers in “Password” and “Confirm Password” textbox.
4. Choose the use type.
5. Input the MAC address of the PC in “Bind MAC” textbox.
After binding physical address to the IP-CAM, you can access the device on this PC only. If the MAC
address was “00:00:00:00:00:00” which means it can be connected to any computers.
6. Click “OK” button and then the new added user will display in the user list.
Modify user:
1. Select the user you need to modify password and physical address in the user configuration list box.
2. The “Edit user” dialog box pops up by clicking “Modify” button.
3. Input old password of this user in the “Old Password” text box.
4. Input new password in the “New password” and “Confirm Password” text box.
5. Input computer’s MAC address as required.
6. Click “OK” button to save the settings.
Delete user:
1. Select the user you want to delete in the user configuration list box.
2. Click “Delete” button to delete the user.
Note: The default super administrator cannot be deleted.
Page 38

Transcendent IP Cameras v4: Operation Manual
37
1.6.11 Online User
Go to ConfigàSecurityàOnline User. You can view the user who is viewing the camera.
1.6.12 Block and Allow Lists
Go to ConfigàSecurityàBlock and Allow Lists interface as shown below.
Setting steps are as follows:
Check “Enable IP address filtering” check box.
Select “Block the following IP address”, input IP address in the IP address list box and click “Add”
button. The operation step of “Allow the following IP address” and MAC address filter settings are the
same with “Block the following IP address”.
After you set the IP address or MAC address, the system will block or allow the user using the added
IP address or MAC address to access the camera.
4.2 Maintenance Configuration
1.6.13 Backup and Restore
Go to ConfigàMaintenanceàBackup & Restore.
Page 39

Transcendent IP Cameras v4: Operation Manual
38
Import & Export Settings
l
You can import or export the setting information from PC or to PC.
1. Click “Browse” to select save path for import or export information on PC.
2. Click “Import Setting” or “Export Setting” button.
Default Settings
l
Click “Load Default” button to restore all system settings to default status.
1.6.14 Reboot
Go to ConfigàMaintenanceàReboot.
Click “Reboot” button to reboot the device.
Timed Reboot Setting:
Enable “Time Settings”, set the date and time and then click “Save” button to save the settings.
1.6.15 Upgrade
Go to ConfigàMaintenanceàUpgrade. In this interface, you can upgrade the system.
1. Click “Browse” button to select the save path of the upgrade file
2. Click “Upgrade” button to start upgrading the application program.
3. The device will restart automatically
4. After you successfully update the software, click “OK” button to close IE and then re-open IE to
connect IP-Cam.
Caution! You can’t disconnect the PC or close the IP-CAM during upgrade.
Page 40

Transcendent IP Cameras v4: Operation Manual
39
1.6.16 Operation Log
To query and export log:
1. Go to ConfigàMaintenanceàOperation Log.
2. Select the main type, sub type, start and end time.
3. Click “Search” to view the operation log.
4. Click “Export” to export the operation log.
Page 41

Transcendent IP Cameras v4: Operation Manual
40
Close all: Click this button to
5 Record Search
5.1 Photo Search
Click SearchàPhoto to go to the interface as shown below. You can search the images saved in the SD
card. This feature is camera dependent; some cameras do not have an SD card slot.
5.2 Photo Search
Click SearchàPhoto to go to the interface as shown below. You can search the images saved in the SD
card.
1. Set time: Select date and choose the start and end time in the top left corner.
2. Chose events.
3. Click “Search” button to search the photos.
4. Click a file name in the list to view captured photos as shown above.
The descriptions of the buttons are shown as follows.
Icon Description Icon Description
Close: Select a picture and click
this button to close this picture.
close all pictures viewing.
Page 42

Transcendent IP Cameras v4: Operation Manual
41
Save all: Click this button to
Actual size: Click this button to
display the actual size of the
Zoom out: Click this button to
Slide show play: Click this
show mode.
Stop: Click this button to stop
Icon Description Icon Description
Save: Click this button to select
the save path of the picture on
the PC for saving the current
picture.
Fit size: The picture will fit on
screen by clicking this button.
Zoom in: Click this button to
zoom in to the picture.
select the save path of the pictures
to the PC for saving all pictures.
picture.
zoom out of the picture.
button to play the picture in slide
Play speed: Play speed of the slide show.
slide show.
5.3 Video Search
1.6.17 Local Video Search
Click SearchàVideoàLocal Video to go to the interface as shown below. You can play the local
video recording. Before playing, please set the storage path of the video recording in the local
configuration interface and make sure there are record files.
Choose the date and the start time and end time and then click “Search” button to search the recorded
files. Double click the recorded file to play the recording. The descriptions of the buttons on the
playback interface are as follows.
Page 43

Transcendent IP Cameras v4: Operation Manual
42
Play button. After pausing
Click it to play the
audio; drag the slider to
adjust the volume after
display full screen.
Double click to exit
Icon Description Icon Description
the video, click this button
to continue playing.
Stop button.
Speed up.
Click it to play the next
recording.
Click it to enable / disable
enabling audio.
Pause button.
Speed down.
previous recording.
Open/close watermark.
Full screen. Click it to
full screen.
1.6.18 SD Card Video Search
1.6.19 This feature is camera dependent; some cameras do not have an SD card slot.
Click SearchàVideoàSD Card Recording to go to the interface as shown below. You can search the
recording saved in the SD card.
Before you search the SD record, you should trigger the SD recording in motion detection alarm (see
Motion Detection Trigger for detail information).
Set the date and the start and end time, select the recording type and then click “Search” button to
search the recordings. Double click the searched file name to play the recording.
Please refer to Local Video Search for the descriptions of the buttons on the playback interface.
Page 44

Transcendent IP Cameras v4: Operation Manual
43
VTD-TNMD4RFS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR
Compact IP Dome Camera with 10 IR LED Illumination
5. Set time: Select date and choose the start and end time in the top left corner.
6. Check events.
7. Click “Search” button to search the files.
8. Click a file name in the list to view captured video as shown above.
6 Specifications
VTD-TNMD4RFS Specifications
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Storage Card
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
0 Lux (IR LED ON)
2.8mm or 3.6mm Fixed Iris Lens Options
True Day/Night by ICR
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Max 8 detailed areas can be viewed
1 x IN & 1 x OUT (Two-Way Audio)
CMS / Web Browser / Mobile (iOS/Android)
IP66 Weather Resistance & IK10 Impact Rating
10
35’
H.265 / H.264 / MJPEG
G.711A / G.711U
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
Motion Alarm / Sensor Alarm
RJ45
1 x BNC (CVBS)
MicroSD up to 128GB
Microsoft Internet Explorer
ONVIF
12VDC / PoE
188mA (IR Off) / 292mA (IR On)
3.5W (IR’s off) / 4.5W (IR’s on)
-4~122 / 10%~90% Humidity
12.31 oz. / 0.77 lbs. / 349g
Page 45

44
VTC-TNB4RFS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR IP
Bullet Camera with 42 IR LED Illumination
VTC-TNB4RFS Specifications
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
Transcendent IP Cameras v4: Operation Manual
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
2.8mm or 3.6mm Fixed Iris Lens Options
True Day/Night by ICR
42
150’
H.265 / H.264 / MJPEG
G.711A / G.711U
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
Max 8 detailed areas can be viewed
CMS / Web Browser / Mobile (iOS/Android)
Microsoft Internet Explorer
210mA (IR Off) / 500mA (IR On)
4W (IR’s off) / 7.8W (IR’s on)
-4~122 / 10%~90% Humidity
21.87 oz. / 1.37 lbs. / 620g
3.43 x 8.62” (87mm x 219mm) Dia x L
Motion Alarm
RJ45
1 x BNC (CVBS)
1 x IN (One-way Audio)
ONVIF
IP66 Weather Resistance
12VDC / PoE
Page 46

Transcendent IP Cameras v4: Operation Manual
45
VTC-TNB4RMS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR IP
Bullet Camera with 48 IR LED Illumination & Motorized Varifocal Lens
VTC-TNB4RMS Specifications
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Storage Card
RS485
Alarm Input
Alarm Output
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
Motorized 3.3-12mm
True Day/Night by ICR
48
160”
H.265 / H.264 / MJPEG
G.711A / G.711U
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
Motion Alarm / Sensor Alarm
Max 8 detailed areas can be viewed
RJ45
1 x BNC (CVBS)
1 x IN & 1 x OUT (Two-Way Audio)
MicroSD up to 128GB
x 1
x 1
x 1
CMS / Web Browser / Mobile (iOS/Android)
Microsoft Internet Explorer
ONVIF
IP66 Weather Resistance
12VDC / PoE
210mA (IR Off) / 545mA (IR On)
4W (IR’s off) / 7.8W (IR’s on)
-4~122 / 10%~90% Humidity
21.87 oz. / 1.37 lbs. / 620g
4.25” x 10.25” (108mm x 267mm) Dia x L
Page 47

46
VTC-TNT4RFS Specifications
VTC-TNT4RFS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR IP Turret
Camera with 2 High Power IR LED Illumination
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
Transcendent IP Cameras v4: Operation Manual
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
2.8mm or 3.6mm Fixed Iris Lens Options
True Day/Night by ICR
2 x High Power
65’
H.265 / H.264 / MJPEG
G.711A / G.711U
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
CMS / Web Browser / Mobile (iOS/Android)
Motion Alarm
Max 8 detailed areas can be viewed
RJ45
1 x BNC (CVBS)
1 x IN (One-way Audio)
IE / Chrome / Firefox / Safari
ONVIF
IP66 Weather Resistance
12VDC / PoE
210mA (IR Off) / 420mA (IR On)
4W (IR’s off) / 6.7W (IR’s on)
-4~122 / 10%~90% Humidity
13.05 oz. / 0.82 lbs. / 370g
3.43” x 4.25” (87 × 108mm) Dia x H
Page 48

Transcendent IP Cameras v4: Operation Manual
47
VTC-TNT4RMS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR IP Turret
Camera with 2 High Power IR LED Illumination & Motorized Varifocal Lens
VTC-TNT4RMS Specifications
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
Motorized 3.3-12mm
True Day/Night by ICR
2 x High Power
100’
H.265 / H.264 / MJPEG
G.711A / G.711U
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
Motion Alarm / Sensor Alarm
Max 8 detailed areas can be viewed
RJ45
1 x BNC (CVBS)
1 x IN (One-way Audio)
CMS / Web Browser / Mobile (iOS/Android)
Microsoft Internet Explorer
ONVIF
IP66 Weather Resistance
12VDC / PoE
210mA (IR Off) / 460mA (IR On)
4W (IR’s off) / 6.7W (IR’s on)
-4~122 / 10%~90% Humidity
24.30 oz. / 1.52 lbs. / 689g
4.29” x 5.12” (109 × 130mm) Dia x H
Page 49

Transcendent IP Cameras v4: Operation Manual
48
VTD-TND4RFS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor
WDR IP Dome Camera with IR LED Illumination
Specifications VTD-TND4RFS-2 VTD-TND4RFS
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
2.8mm Fixed Iris Lens
10 x High Power
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
Max 8 detailed areas can be viewed
CMS / Web Browser / Mobile (iOS/Android)
IP66 Weather Resistance & IK10 Impact Rating
4.57” x 3.58” (150 x 114mm) Dia x H
True Day/Night by ICR
65’
H.265 / H.264 / MJPEG
G.711A / G.711U
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
Motion Alarm
RJ45
1 x BNC (CVBS)
1 x IN (One-way Audio)
Microsoft Internet Explorer
ONVIF
12VDC / PoE
210mA (IR Off) / 335mA (IR On)
4W (IR’s off) / 6.7W (IR’s on)
-4~122 / 10%~90% Humidity
21.34 oz. / 1.33 lbs. / 605g
3.6mm Fixed Iris Lens
24
Page 50

Transcendent IP Cameras v4: Operation Manual
49
VTD-TND4RMS
Transcendent Series 4 Megapixel H.265 Indoor/Outdoor WDR IP
Dome Camera with 30 IR LED Illumination & Motorized Varifocal Lens
VTD-TND4RMS Specifications
Image Sensor
Image Size
Resolution
Min. Illumination
Lens
Day/Night
IR LEDs
IR Distance
Video Compression
Audio Compression
Multi-Stream
WDR
DNR
Quality
Image Setting
Intelligent Analytics
Smart Alarm
ROI
Network
Video Output
Audio
Storage Card
RS485
Alarm Input
Alarm Output
Remote Viewing
Supported Browsers
Connection Protocol
Resistance
Power Input
Power Consumption (12VDC)
Power Consumption (PoE)
Working Environment
Weight
Dimensions
1/3” 4.0 Megapixel Progressive Scan CMOS
4 MegaPixel 2592x1520
4 MP (2592x1520) / 3 MP (2304x1296) / 1080P (1920x1080) / 720P (1280x720) / D1/CIF (480x240)
0 Lux (IR LED ON)
Motorized 3.3-12mm
True Day/Night by ICR
30
100’
H.265 / H.264 / MJPEG
G.711A / G.711U
1~30fps: 4 MP, 3 MP, 1080P, 720P, D1, CIF, 480x240
VBR (Five Levels of Adjustment) / CBR (Adjustable)
Saturation, Brightness, Contrast, WDR, Noise reduction
Object Removal/Museum Search, Line Crossing, and Area Intrusion Detection
120dB Super WDR
XD-DNR (2D-DNR & 3D-DNR)
Motion Alarm / Sensor Alarm
Max 8 detailed areas can be viewed
RJ45
1 x BNC (CVBS)
1 x IN & 1 x OUT (Two-Way Audio)
MicroSD up to 128GB
x 1
x 1
x 1
CMS / Web Browser / Mobile (iOS/Android)
Microsoft Internet Explorer
ONVIF
IP66 Weather Resistance & IK10 Impact Rating
12VDC / PoE
210mA (IR Off) / 420mA (IR On)
4W (IR’s off) / 6.7W (IR’s on)
-4~122 / 10%~90% Humidity
44.45 oz. / 2.78 lbs. / 1260g
5.91” x 4.49” (150 x 114mm) Dia x H
Page 51

OPTIONAL ACCESSORIES FOR
TRANSCENDENT IP CAMERAS
VT-TJB01
Junction Box for Cable
Management for use with all
Transcendent Bullet and Turret
Style Cameras
VT-TJB03
Junction Box for Cable
Management for use with
Transcendent 24 IR LED Vandal
Domes
VT-TJB02
Junction Box for Cable
Management for use with
Transcendent 30 IR LED Vandal
Domes
VT-TWM03
Wall Mount for Transcendent
30 IR LED Vandal Domes and
Varifocal Turret Cameras
VT-TWMT3
Optional Wall Mount for use
with Transcendent VTD-TND8RFS
Vandal Dome
Page 52

LIMITED PRODUCT WARRANTY
VITEK products carry a three (3) year limited warranty. VITEK
warrants to the purchaser that products manufactured by VITEK
are free of any rightful claim of infringement or the like, and when
used in the manner intended, will be free of defects in materials and
workmanship for a period of three (3) years, or as otherwise stated
above, from the date of purchase by the end user. This warranty is
nontransferable and extends only to the original buyer or end user
customer of a VITEK Authorized Reseller.
The product must have been used only for its intended purpose, and
not been subjected to damage by misuse, willful or accidental damage,
caused by excessive voltage or lightning.
The product must not have been tampered with in any way or the
guarantee will be considered null and void.
This guarantee does not affect your statutory rights.
Contact your local VITEK Reseller should servicing become
necessary.
VITEK makes no warranty or guarantee whatsoever with respect to
products sold or purchased through unauthorized sales channels.
Warranty support is available only if product is purchased through a
VITEK Authorized Reseller.
28492 CONSTELLATION ROAD VALENCIA, CA 91355
WWW.VITEKCCTV.COM
Version 2.0
July 2017
 Loading...
Loading...