Page 1

Network Cameras
User Manual
Manual Version: 1.00
Page 2

Thank you for purchasing our product. If there are any questions, or requests, please do not hesitate to
CAUTION!
The default password is used for your first login. To ensure account security, please change the password
after your first login. You are recommended to set a strong password (no less than eight characters).
contact the dealer.
Copyright
Copyright 2019 Zhejiang Uniview Technologies Co., Ltd. All rights reserved. No part of this manual may be
copied, reproduced, translated, or distributed in any form or by any means without prior consent in writing
from our company.
Trademark Acknowledgement
and other Uniview's trademarks and logos are the property of Zhejiang Uniview Technologies
Co., Ltd. Other trademarks, company names and product names contained in this manual are the property
of their respective owners.
Disclaimer
To the maximum extent permitted by applicable law, the product described, with its hardware, software,
firmware and documents, is provided on an “as is” basis.
Best effort has been made to verify the integrity and correctness of the contents in this manual, but no
statement, information, or recommendation in this manual shall constitute formal guarantee of any
kind, expressed or implied. We shall not be held responsible for any technical or typographical errors in
this manual. The contents of this manual are subject to change without prior notice. Update will be
added to the new version of this manual.
Use of this manual and the subsequent result shall be entirely on the user’s own responsibility. In no
event shall we be reliable to you for any special, consequential, incidental, or indirect damages,
including, among others, damages for loss of business profits, business interruption, or loss of data or
documentation in connection with the use of this product.
Video and audio surveillance can be regulated by laws that vary from country to country. Check the law
in your local region before using this product for surveillance purposes. We shall not be held responsible
for any consequences resulting from illegal operations of the device.
The illustrations in this manual are for reference only and may vary depending on the version or model.
The screenshots in this manual may have been customized to meet specific requirements and user
preferences. As a result, some of the examples and functions featured may differ from those displayed
on your monitor.
This manual is a guide for multiple product models and so it is not intended for any specific product.
Due to uncertainties such as physical environment, discrepancy may exist between the actual values
and reference values provided in this manual. The ultimate right to interpretation resides in our
company.
Page 3

Environmental Protection
Symbol
Description
WARNING!
Contains important safety instructions and indicates situations that could cause bodily
injury.
CAUTION!
Means reader be careful and improper operations may cause damage or malfunction
to product.
NOTE!
Means useful or supplemental information about the use of product.
This product has been designed to comply with the requirements on environmental protection. For the
proper storage, use and disposal of this product, national laws and regulations must be observed.
Symbols
The symbols in the following table may be found in this manual. Carefully follow the instructions indicated
by the symbols to avoid hazardous situations and use the product properly.
Page 4

Contents
1 Network Connection ························································································································· 1
2 Login ·················································································································································· 1
Preparation ················································································································································ 1
Logging In to the Web Interface ················································································································ 3
Introduction to the Web Interface············································································································· 4
Initial Configuration ··································································································································· 5
3 Configuring Parameters ···················································································································· 6
Local Parameters ········································································································································ 6
Network Configuration ······························································································································ 7
Ethernet ·············································································································································· 7
Port ····················································································································································· 8
Port Mapping ······································································································································ 9
DNS ····················································································································································· 9
DDNS ··················································································································································· 9
Uniarch ············································································································································· 10
FTP ···················································································································································· 10
E-Mail ················································································································································ 11
QoS ··················································································································································· 12
Image Configuration ································································································································ 12
Image Adjustment ·························································································································· 122
OSD Setting ······································································································································· 19
Privacy Mask ····································································································································· 20
Audio and Video Configuration ················································································································ 21
Video Configuration ························································································································· 21
Snapshot ··········································································································································· 22
ROI ···················································································································································· 23
Media Stream Configuration ············································································································ 24
Common Alarm Configuration ················································································································· 25
Configuring Motion Detection Alarm ······························································································· 25
Configuring Tampering Alarm ········································································································ 288
System Maintenance ······························································································································· 29
Security ············································································································································· 29
Setting the System Time ··················································································································· 32
Upgrading the Device ······················································································································· 33
Restarting the System ······················································································································ 33
Importing and Exporting System Configuration File ········································································ 34
Collecting Diagnosis Information ····································································································· 34
4 Live View ········································································································································· 35
Live View Toolbar ····································································································································· 35
Viewing Certain Area of Images ··············································································································· 36
Using Digital Zoom ··························································································································· 36
i
Page 5

Appendix B FAQ ································································································································· 37
ii
Page 6

1 Network Connection
Network cable
IPC PC
IPC
PC
Switch or Router
Network cable Network cable
Before accessing a network camera (also known as IP Camera or IPC) from a PC, you need to connect the
network camera to the PC directly with a network cable or via a switch or router.
Use a Shielded Twisted Pair (STP) cable to connect the network interfaces of the network camera and the PC.
Use Shielded Twisted Pair (STP) cables to connect the network interfaces of the camera and the switch or
router.
2 Login
Preparation
After you have completed the installation in accordance with the quick guide, connect the camera to power
to start it. After the camera is started, you can access the camera from a PC client installed with a web
browser or the client software EZStation. Internet Explorer (IE) is a recommended web browser. For more
information about EZStation, refer to the EZStation User Manual.
The following takes IE on a Microsoft Windows 7 operating system as an example.
Check before login
The camera is operating correctly.
The network connection between the PC and the camera is normal.
The PC is installed with Internet Explorer 10.0 or higher.
(Optional) The resolution is set to 1440 x 900.
1
Page 7

Add the IP address as a trusted site
1.13
1
2
2
Page 8

NOTE!
The IP address 192.168.1.13 in this example is the default IP address. Please replace it with the actual address
of your camera if it has been changed.
NOTE!
To manually load the ActiveX, type http://IP address/ActiveX/Setup.exe in the address bar and press
Enter.
The default password is used for your first login. To ensure account security, please change the
password after your first login. You are recommended to set a strong password (no less than eight
characters).
The camera protects itself from illegal access by limiting the number of failed login attempts. If login
fails six times consecutively, the camera locks automatically for ten minutes.
1
2
3
4
(Optional) Modify user access control settings
Before you access the camera, follow the steps to set User Account Control Settings to Never notify.
Logging In to the Web Interface
The default static IP address of the camera is 192.168.1.13, and the default subnet mask is 255.255.255.0.
DHCP is turned on by default. If a DHCP server is used in the network, the IP address of your camera may be
assigned dynamically, and you need to use the correct IP address to log in. Use the EZStation client to view
the dynamic IP address of your camera.
The following takes IE as an example to describe the login procedure.
1. Browse to the login page by entering the correct IP address of your camera in the address bar.
2. If you log in for the first time, follow system prompts and install the ActiveX. You need to close your
browser to complete the installation.
3
Page 9

3. Privacy policy is displayed on the screen when the user logs in for the first time (This function is not
supported by some models). After reading the privacy policy, you need to check in the 'I have read and
agree to the above policy' box, then click the 'OK' button to proceed to the next step.
4. Enter the username and password, and then click Login. For the first login, use the default username
“admin” and password “admin”or“123456”.
If you log in with Live View selected, live video will be displayed when you are logged in. Otherwise, you
need to start live video manually in the live view window.
To clear the Username and Password text boxes, click Reset.
Introduction to the Web Interface
By default the live view window is displayed when you are logged in to the Web interface. The following
shows an example.
4
Page 10

No.
Description
1
Menu
2
Live view window
3
Live view toolbar
Item
Description
1. Ethernet.
Reconfigure the device IP and network parameters based on
the actual networking.
2. Log out and log in again to the Web
using the new IP address.
-
3. Set the system time.
Set the system time based on the actual situation.
4. (Optional) Set the management
server.
Set the management server based on the actual networking.
5. (Optional) Set the server for storing
photos.
Set the server for storing photos based on the actual
networking.
6. Set OSD.
Set the information displayed on the screen as needed, for
example, time.
7. (Optional) Manage users.
Change the default password and add common users as
needed.
1
2
3
Initial Configuration
After you log in to the device, please perform the following initial configuration.
You can watch the live video after finishing the initial configuration. Please configure other parameters as
needed.
5
Page 11

NOTE!
The displayed live view interface, parameters displayed and value ranges may vary with models.
Please see the actual Web interface for details.
The parameters that are grayed out cannot be modified. For the actual settings, see the Web
interface.
It is recommended that you change the password when you are logged in the first time. For details
about how to change a password, see Security.
NOTE!
The local parameters may vary with models. Please see the actual Web interface for details.
Parameter
Description
Video
Processing Mode
Real-Time Priority: Recommended if the network is in good condition.
Fluency Priority: Recommended if you want short time lag for live video.
Ultra-low Latency: Recommended if you want the minimum time lag for
live video.
Protocol
Set the protocol used to transmit media streams to be decoded by the PC.
3 Configuring Parameters
Local Parameters
Set local parameters for your PC.
1. Select Setup > Common > Local Settings.
2. Modify the settings as required. The following table describes some major parameters.
6
Page 12

Parameter
Description
Record
and
Snapshot
Recording
Subsection By Time: Duration of recorded video for each recording file on
the computer. For example, 2 minutes.
Subsection By Size: Size of each recording file stored on the computer. For
example, 10M.
When Storage
Full
Overwrite Recording: When the total capacity allocated to the local
recording is full, the oldest recording file will be deleted.
Stop Recording: When the total capacity allocated to the local recording
is full, the recording will stop.
Files Folder
The save path of snapshots and recordings. The max. Path length is 260
bytes. If the limit is exceeded, recording or snapshot during live view will
fail, and messages will appear on the screen.
NOTE!
After you have changed the IP address, you need to use the new IP address to log in.
The configurations of DNS (Domain Name System) server are applicable when the device is accessed
by domain name.
3. Click Save.
Network Configuration
Ethernet
Modify communication settings such as the IP address for the camera so that the camera can communicate
with other devices.
Static Address
1. Click Setup > Network > Network.
2. Select Static from the Obtain IP Address drop-down list.
3. Enter the IP address, subnet mask, and default gateway address. Make sure that the IP address of the
camera is unique in the network.
4. Click Save.
7
Page 13

DHCP
NOTE!
This function is not supported by some models. Please see the actual model for details.
The Dynamic Host Configuration Protocol (DHCP) is enabled by default when the camera is delivered. If a
DHCP server is deployed in the network, the camera can automatically obtain an IP address from the DHCP
server.
To manually configure DHCP, follow the steps below:
1. Click Setup > Network > Network.
2. Select DHCP from the Obtain IP Address drop-down list.
3. Click Save.
IPv6
1. Click Setup > Network > Network.
2. By default the IPv6 mode is set to Manual.
3. Enter the IPv6 address, set the prefix length and default gateway. The IP address must be unique on the
network.
4. Click Save.
Port
1. Click Setup > Network > Port.
2. Configure relevant port numbers.
3. Click Save.
8
Page 14

Port Mapping
NOTE!
This function is not supported by some models. Please see the actual model for details.
1. Click Setup > Network > Port. Go to Port Mapping tab.
2. Enable Port Mapping and select mapping type. If Manual is selected, then external ports must be
configured (external IP is obtained automatically by the camera). If the configured port is occupied, then
the Status will show Inactive.
3. Click Save.
DNS
1. Click Setup > Network > DNS.
2. Set DNS server addresses.
3. Click Save.
DDNS
1. Click Setup > Network > DDNS.
2. Enable DDNS Service.
3. Select a DDNS type: DynDNS, NO-IP, or EZDDNS.
4. Complete other settings including server address, domain name, username and password.
5. Click Save.
9
Page 15

Uniarch
NOTE!
This function is not available to all models.
Scan the QR code with your mobile phone (iOS or Android) to download the APP.
When installed, run the APP to add the camera. Please refer to the online help in the APP for detailed
steps.
1. Click Setup > Network > Uniarch.
2. Enable Uniarch. Select On to enable cloud service.
3. Enable Quick Add. When the device password is a strong password, you can add the device through
EZView without account scan code.
4. Click Save.
FTP
All snapshots (except face detection) are saved through the general FTP service. After the configuration of
FTP, you will be able to upload snapshots from network cameras to the specified FTP server.
General
1. Click Setup > Storage > FTP. Go to General tab.
10
Page 16

2. Set the IP address and port for the FTP server, username and password used to upload images to the
Parameter
Description
TLS/SSL
When enabled, the e-mail will be encrypted using TLS (Transport Layer Security) or
Secure Socket Layer (SSL) to protect privacy.
First it tries to send through an SSL connection. If the SMTP server supports SSL, the
e-mail will be sent through the SSL connection; otherwise, it tries to send using
STARTTLS.
Attach Image
When enabled, the e-mail will contain 3 instant snapshots as attachment according to
the Capture Interval.
Username/Password
Username and password of the registration email address.
FTP server, select Upload Images, Overwrite Storage and set Overwrite At (threshold for overwriting
images). Some camera models support FTP test. You may test FTP after completing FTP settings correctly.
3. Set the path for saving snapshots on the FTP server and the file name format. For example, set path as
Date-YYYY\\Date-MM\\Date-DD\\Hour(s), and set file name as Date-YYYY-Date-MM-Date-DD.jpg.
4. Click Save.
E-Mail
After the configuration of E-mail, when alarms are triggered, you will be able to send messages to the
specified E-mail address (This function is not supported by some models).
1. Click Setup > Network > E-mail.
2. Configure relevant parameters of the sender and the recipient. Some camera models support Email test.
You may test email after setting the recipient address. The following table describes some major
parameters.
3. Click Save.
11
Page 17

QoS
NOTE!
To use QoS, make sure that the switch support QoS mode.
NOTE!
The image parameters displayed and value ranges allowed may vary with camera model. For the
actual parameters and value ranges of your camera, see the Web interface. You may move the sliders
to adjust settings or enter values in the text boxes directly.
Clicking Default will restore all the default image settings.
QoS (Quality of Service) is the ability to provide better service for specified network communication. As a
network security mechanism, QoS is used to address problems like network delay and blocking. When the
network is overloaded or congested, QoS ensures that critical services are not delayed or discarded and that
the network runs efficiently (This function is not supported by some models).
1. Click Setup > Network > QoS.
2. Set a priority level (0~63) for each service. At present, QoS allows you to assign different priority to
audio and video, alarm report, configuration management and FTP transmission. The greater the value,
the higher the priority. For example, if the value of audio and video is set to 60, alarm report and
configuration management is set to 0, and FTP is set to 4, when network congestion occurs, the priority
is to ensure the smooth running of audio and video.
3. Click Save.
Image Configuration
Image Adjustment
Setting the Scene
Set image parameters to achieve the desired image effects based on live video in different scenes.
Click Setup > Image > Image.
The scene management page of some models is displayed as follows, you can take the following steps to
configure the scene.
12
Page 18

Column
Description
Current
Indicates the scene that is being used.
Note:
Select an option button to switch to the scene and display the corresponding image
parameters for the scene.
The camera switches the current scene automatically when Enable Auto Switching is
selected.
Scene Name
Name of the current scene. The device provides several preset scene modes. When you
select a scene, the corresponding image parameters are displayed. You can adjust image
settings according to actual needs.
Common: recommended for outdoor scenes.
Indoor: recommended for indoor scenes.
Road/Park Highlight Compensation (HLC): Can suppress glare and obtain clear images,
such as suitable for roads/parks to suppress lights to capture license plates.
Custom: set a scene name as needed.
Auto Switching
Indicates whether to add a scene to the auto-switching list.
Note:
If Auto Switching is selected, the system switches to a scene automatically when the
condition for switching to the scene is met. By default the auto-switching list includes the
default scene.
Setup
Click to set conditions for auto-switching, including schedule, illumination, and current
elevation. It means that auto-switching is triggered only when illumination and the current
elevation during the set time period meet the set conditions. A condition is invalid if both
the start and end values are set to 0.
1. Click Scenes.
2. Select a scene, and then set scene switching parameters. The following table describes some major
parameters.
3. Select a scene and then click to set it as the default scene.
4. If auto-switching is enabled, the camera can switch to the scene automatically when the condition for
switching to a non-default scene is met. Otherwise, the camera remains in the default scene. When autoswitching is not enabled, the camera remains in the current scene.
13
Page 19
NOTE!
If Auto Switching is enabled (scene settings will be unavailable), the device will switch between the
set scenes. If not, the device will stay at the current scene. The device will stay at default scenes
unless the non-default scenes are triggered.
If multiple non-default scenes are triggered, then the device will switch to the scene with the
minimum number (starts from 1 to 5).
NOTE!
This function may vary with models. Please see actual Web interface for details.
Item
Description
Brightness
Set the degree of brightness of images.
Low brightness
High brightness
Saturation
The amount of a hue contained in a color.
Low saturation
High saturation
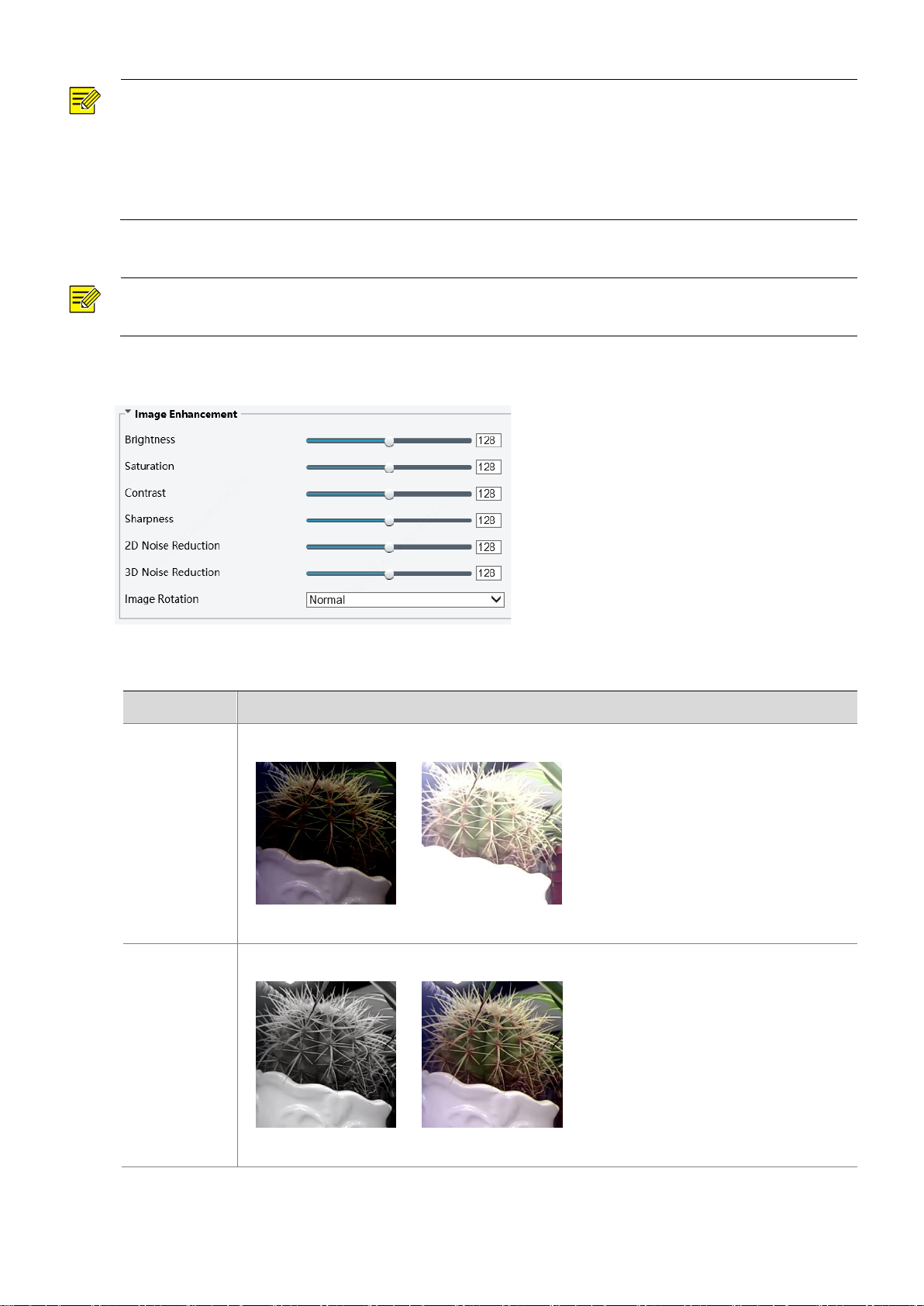
Image Enhancement
1. Click Setup > Image > Image and then click Image Enhancement.
2. Use the sliders to change the settings. You may also enter values directly. The following table describes
some major parameters.
14
Page 20

Item
Description
Contrast
Set the degree of difference between the blackest pixel and the whitest pixel.
Low contrast
High contrast
Sharpness
Contrast of boundaries of objects in an image.
Low sharpness
High sharpness
2D Noise
Reduction
Reduce the noise of images. The function may cause image blurring.
3D Noise
Reduction
Reduce the noise of images. The function may cause motion blur (or ghosting in some
applications).
Image
Rotation
Rotation of the image.
Normal
Flip Vertical
Flip Horizontal
180°
3. To restore default settings in this area, click Default.
15
Page 21
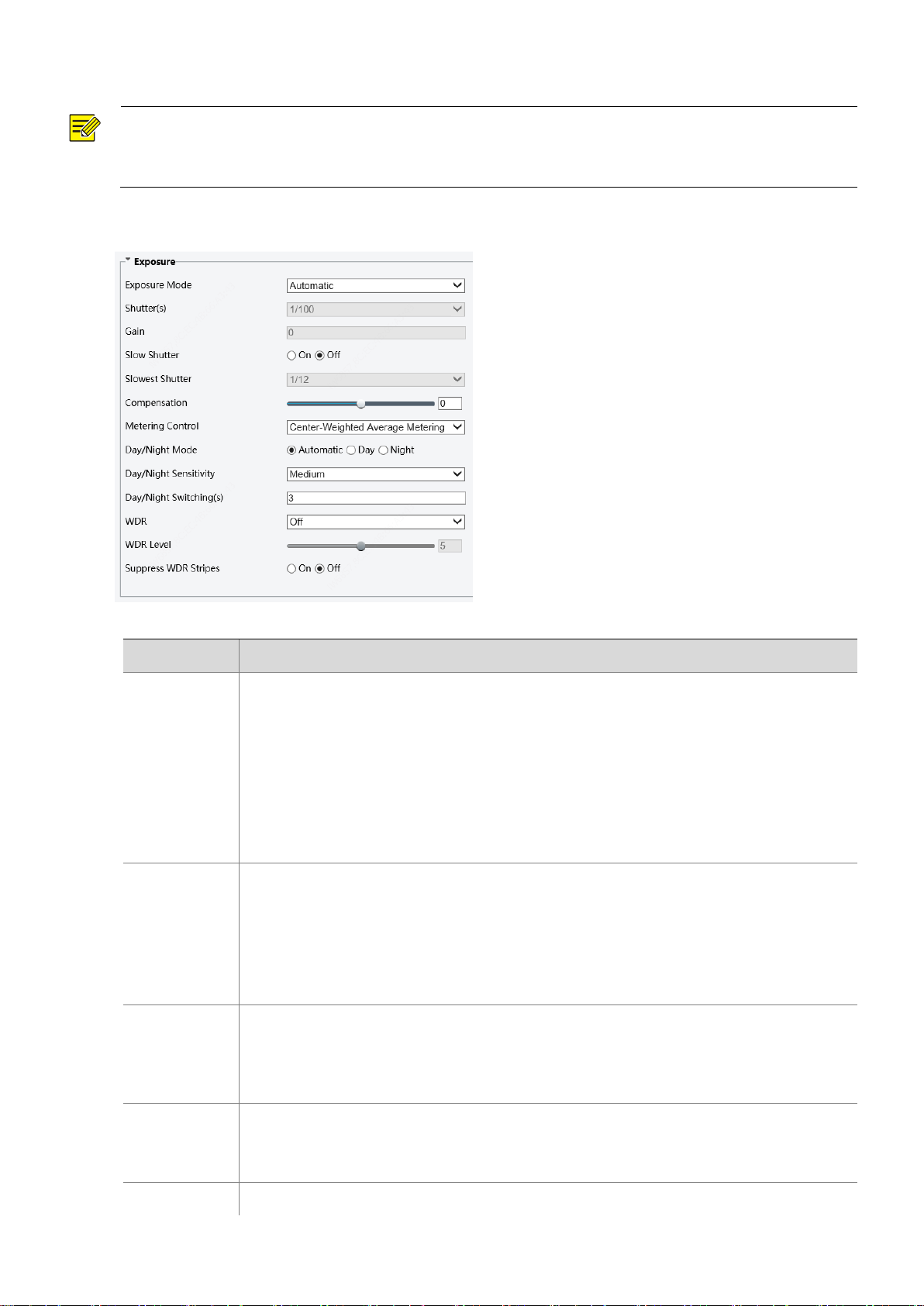
Exposure
NOTE!
This function may vary with models. Please see actual Web interface for details.
The default settings are scene-adaptive. Use default settings unless modification is necessary.
Parameter
Description
Exposure
Mode
Select the correct exposure mode to achieve the desired exposure effect.
Automatic: The camera automatically adjusts exposure according to the environment.
Custom: The user sets exposure as needed.
Indoor 50Hz: Reduce stripes by limiting shutter frequency.
Indoor 60Hz: Reduce stripes by limiting shutter frequency.
Manual: Fine tune image quality by setting shutter, gain and iris manually.
Low Motion Blur: Control the minimum shutter to reduce motion blur in faces captured
in motion.
Shutter(s)
Shutter is used to control the light that comes into the lens. A fast shutter speed is ideal for
scenes in quick motion. A slow shutter speed is ideal for scenes that change slowly.
Note:
You can set a shutter speed when Exposure Mode is set to Manual.
If Slow Shutter is set to Off, the reciprocal of the shutter speed must be greater than the
frame rate.
Gain
Control image signals so that the camera outputs standard video signals according to the
light condition.
Note:
You can set this parameter only when Exposure Mode is set to Manual.
Slow Shutter
Improves image brightness in low light conditions.
Note:
You can set this parameter only when Image Stabilizer is disabled.
Slowest
Set the slowest shutter speed that the camera can use during exposure.
1. Click Setup > Image > Image and then click Exposure.
2. Set the parameters as required. The following table describes some major parameters.
16
Page 22

Parameter
Description
Shutter
Note:
You can set this parameter only when Slow Shutter is set to On.
Compensation
Adjust the compensation value as required to achieve the desired effects.
Note:
You can set this parameter only when Exposure Mode is not set to Manual.
Metering
Control
Set the way the camera measures the intensity of light.
Center-Weighted Average Metering: Measure light mainly in the central part of images.
Evaluative Metering (BLC): Measure light in the customized area of images.
Spot Metering: Similar to the “area metering” effect, but it cannot improve the
brightness of the screen.
Note:
You can set this parameter only when Exposure Mode is not set to Manual.
Day/Night
Mode
Automatic: The camera outputs the optimum images according to the light condition. In
this mode, the camera can switch between night mode and day mode automatically.
Night: The camera provides high-quality black and white images using the existing light
Day: The camera provides high-quality color images using the existing light.
Day/Night
Sensitivity
Light threshold for switching between day mode and night mode. A higher sensitivity means
that the camera is more sensitive to the change of light and becomes more easily to switch
between day mode and night mode.
Note:
You can set this parameter only when Day/Night Mode is set to Automatic.
Day/Night
Switching(s)
Set the length of time before the camera switches between day mode and night mode after
the conditions for switching are met.
Note:
You can set this parameter only when Day/Night Mode is set to Automatic.
WDR
Enable WDR to distinguish the bright and dark areas in the same image.
Note:
You can set this parameter only when Exposure Mode is not set to Manual and when Image
Stabilizer is disabled.
Suppress WDR
Stripes
When enabled, the camera can automatically adjust slow shutter frequency according to
the frequency of light to minimize stripes that may appear in images.
NOTE!
This function may vary with models. Please see actual Web interface for details.
3. To restore the default settings, click Default.
Smart Illumination
1. Click Setup > Image > Image and then click Smart Illumination.
17
Page 23

Parameter
Description
Lighting Type
Infrared: The camera uses infrared light illumination.
Note:
When Control Mode is set to Manual, camera can set illumination level from 0~1000.
Control Mode
Global Mode: The camera adjusts IR illumination and exposure to achieve balanced
image effects. Some areas might be overexposed if you select this option. This option is
recommended if monitored range and image brightness are your first priority.
Overexposure Restrain: The camera adjusts IR illumination and exposure to avoid
regional overexposure. Some areas might be dark if you select this option. This option is
recommended if clarity of the central part of the image and overexposure control are
your first priority.
Manual: This mode allows you to manually control the intensity of IR illumination.
NOTE!
This function may vary with models. Please see the actual Web interface for details.
Parameter
Description
White Balance
Adjust the red or blue offset of the image:
Auto/Auto2: The camera adjusts the red and blue offset automatically according to the
light condition (the color tends to be blue). If the images are still unnaturally red or blue
in Auto mode, please try Auto2.
Outdoor: Suitable for outdoor environment with a relatively greater color temperature
range.
Fine Tune: Allow you to adjust the red and blue offset manually.
Sodium Lamp: The camera adjusts red and blue offset automatically according to the
2. Select the correct IR control mode and set the parameters. The following table describes some major
parameters.
3. To restore the default settings, click Default.
White Balance
White balance is the process of offsetting unnatural color cast in images under different color temperatures
so as to output images that best suit human eyes.
1. Click Setup > Image > Image and then click White Balance.
2. Select a white balance mode as required. The following table describes some major parameters.
18
Page 24

light condition (the color tends to be red).
Locked: Lock the current color temperature without change.
Red Offset
Adjust the red offset manually.
Note:
You can set this parameter only when White Balance is set to Fine Tune.
Blue Offset
Adjust the blue offset manually.
Note:
You can set this parameter only when White Balance is set to Fine Tune.
NOTE!
You can set this parameter only when WDR is turned off.
Only some camera models support optical defog. When Defog is set to On, defog intensity level 6-9
represent optical defog, and images change from color to black/white when defog intensity is set
from level 5 to 6; if Defog is set to Auto and defog intensity level is somewhere between 6-9, images
do not automatically change to black/white in light fog conditions; the camera automatically
switches to optical defog only in heavy fog conditions.
Defog Off
Defog On
3. To restore the default settings, click Default.
Advanced
Use the defog function to adjust the clarity of images captured in fog or haze conditions.
1. Click Setup > Image > Image and then click Advanced.
2. Enable the defog function and then select a level for the scene. Level 9 achieves the maximum defog
effects, and level 1 achieves the minimum.
3. To restore the default settings, click Default.
OSD Setting
On Screen Display (OSD) is the text displayed on the screen with video images and may include time and
other customized contents.
19
Page 25

NOTE!
This function may vary with models. Please see the actual Web interface for details.
1. Click Setup > Image > OSD.
2. Select the position and content of the OSD.
Position: Click the desired box in the Live View area. After the cursor shape is changed, click and hold
the button to move the box to the desired position. To set the position precisely, use the X and Y
coordinates under Overlay Area.
Overlay OSD Content: The drop-down list provides Time, Preset and Serial Info. You may also select
Custom and enter the content you want.
After you have set the position and OSD content, the symbol appears in the Status column, which
means that the OSD is set successfully.
3. After you have completed the settings, a message appears to indicate the successful settings.
You may right-click in the preview window and then choose to view in full screen mode or at an aspect ratio.
You may also double-click the preview window to enter or exit full screen mode.
To cancel OSD for an area, clear the OSD content in the Overlay OSD Content column or select None in the
Position column.
The following shows an example time OSD.
Privacy Mask
On certain occasions, you may need to set a mask area on the camera image to protect privacy, for example,
the keyboard of an ATM machine.
20
Page 26

NOTE!
This function may vary with models. Please see the actual Web interface for details.
The same picture shows up to only 4 privacy masks.
NOTE!
Mask mode is only available to certain models.
1. Click Setup > Image > Privacy Mask.
2. Click Add to add a privacy mask, and click Delete to delete a mask.
To mask a position: Click the box (with Mask displayed on it) to activate the mask. After the cursor shape
has changed, drag the box to the intended position.
To mask an area: Use the mouse to draw a box on the area you want to mask.
When privacy mask is configured, the intended area is blocked. The following shows an example.
3. Set mask mode. You may select regular or irregular mode as needed.
Audio and Video Configuration
Video Configuration
You can set video parameters that your camera supports and view the current status of BNC output. If
available, you may also enable sub-stream as required.
21
Page 27

NOTE!
After enabling the sub stream, modify the parameters as required. The parameters for the sub stream have
the same meanings as that for the main stream.
Parameter
Description
Video
Compression
Three options: H.265, H.264 and MJPEG (This function is not supported by some models).
Note:
Image Quality cannot be set when Video Compression is set to H.265 or H.264. When
set to MJPEG, only three frame rates are available: 1, 3 and 5; and Bit Rate, I Frame
Interval, Smoothing and U-Code cannot be set.
The bit rate changes to the default when you change the setting between H.264 and
H.265. The default bit rate for H.265 is half of that for H.264.
Frame Rate
Frame rate for encoding images. Unit: FPS (frame per second).
Note:
To ensure image quality, note that the frame rate should not be greater than the
reciprocal of shutter speed.
Bitrate Type
CBR: Constant Bit Rate, which means that the camera transmits data at a constant
data rate.
VBR: Variable Bit Rate, which means that the camera adjusts the bit rate dynamically
according to image quality.
Image Quality
When Encoding Mode is VBR, you can move the slider to adjust quality level for images.
Moving the slider toward Bit Rate decreases the bit rate and may affect image quality.
Moving the slider toward Quality increases the bit rate and improves image quality.
1. Click Setup > Video > Video.
Modify the settings as required. The following table describes some major parameters.
2. Click Save.
22
Page 28

Snapshot
NOTE!
This function is not supported by some models. Please see the actual model for details.
Parameter
Description
Snapshot Interval
Interval between two snapshots. For example, with Snapshot Interval set to 1 and
Number of Snapshot set to 2, the camera will take 2 snapshots (take one first and
then take another after 1 second).
Number to Snapshot
Currently 1, 2, and 3 snapshots are allowed.
Snapshot Mode
Schedule: You need to set a snapshot time, e.g., 19:12:00, which means the camera
takes a snapshot at 19:12:00.
Repeat: Allows you to set an interval (unit: sec). For example, according to the
settings shown in the figure above, 60 seconds must elapse before the camera takes
another two snapshots.
1. Click Setup > Video > Snapshot.
2. Select On, and then set resolution, most large and schedule as needed. Some parameters are described
in the table below.
3. Click Save.
ROI
When Region of Interest (ROI) is enabled, the system ensures image quality for ROI first if the bit rate is
insufficient.
23
Page 29
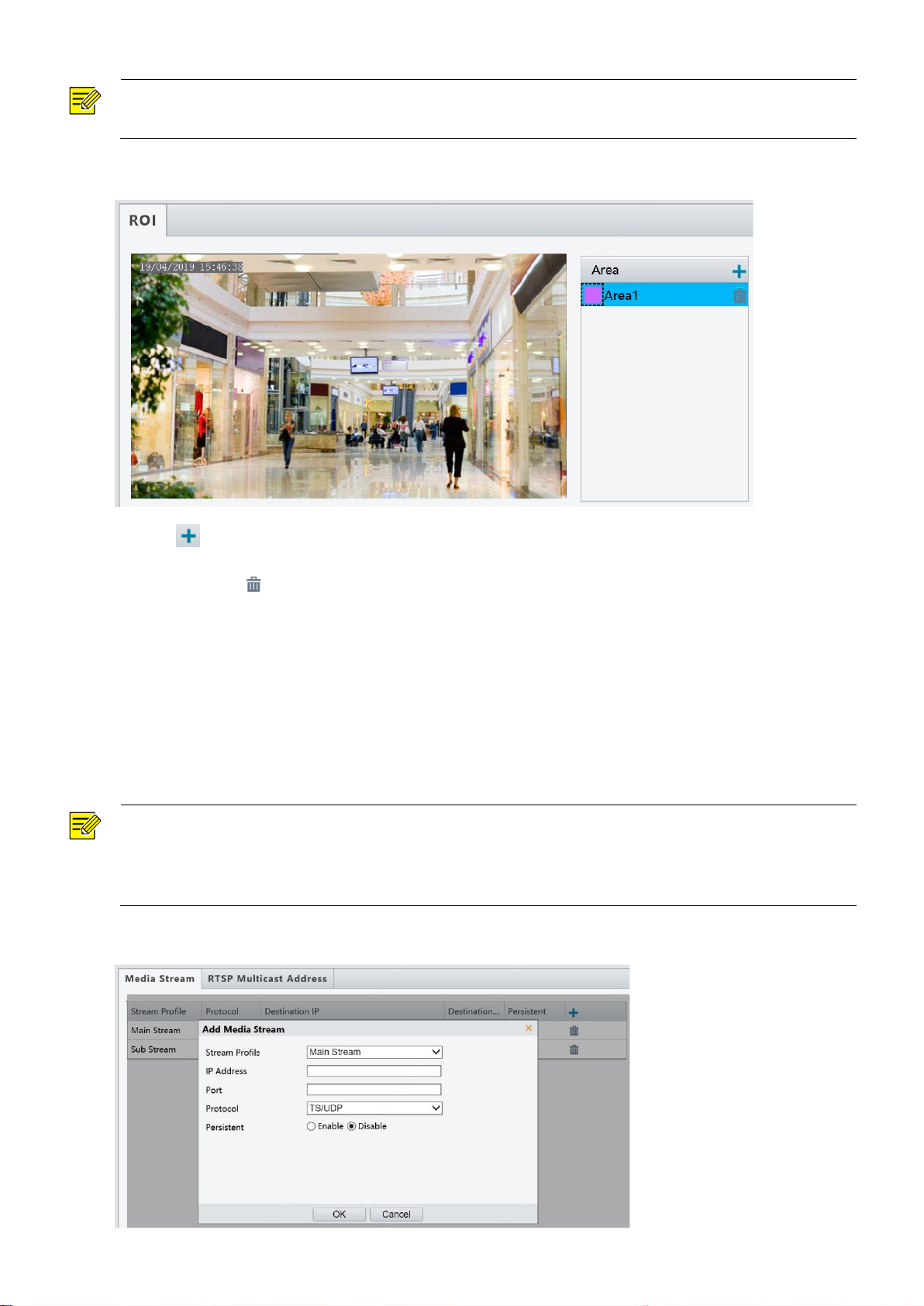
NOTE!
This function is not supported by some models. Please see the actual model for details.
NOTE!
This function is not supported by some models. Please see the actual model for details.
Choosing a transport protocol based on your actual needs and network performance. Generally
speaking, TCP enables better image quality than UDP but also causes higher latency.
1. Click Setup > Video > ROI.
2. Click , and then drag the mouse to cover the intended part of the images. To delete, select the area
and then click .
Media Stream Configuration
Media Stream
You can display the established media streams from a camera. You may also set the camera so it transmits
code streams by the UDP or TCP protocol to a specified IP address and port number. The settings can be
saved and take effect after the camera is restarted.
1. Click Setup > Video > Media Stream.
24
Page 30
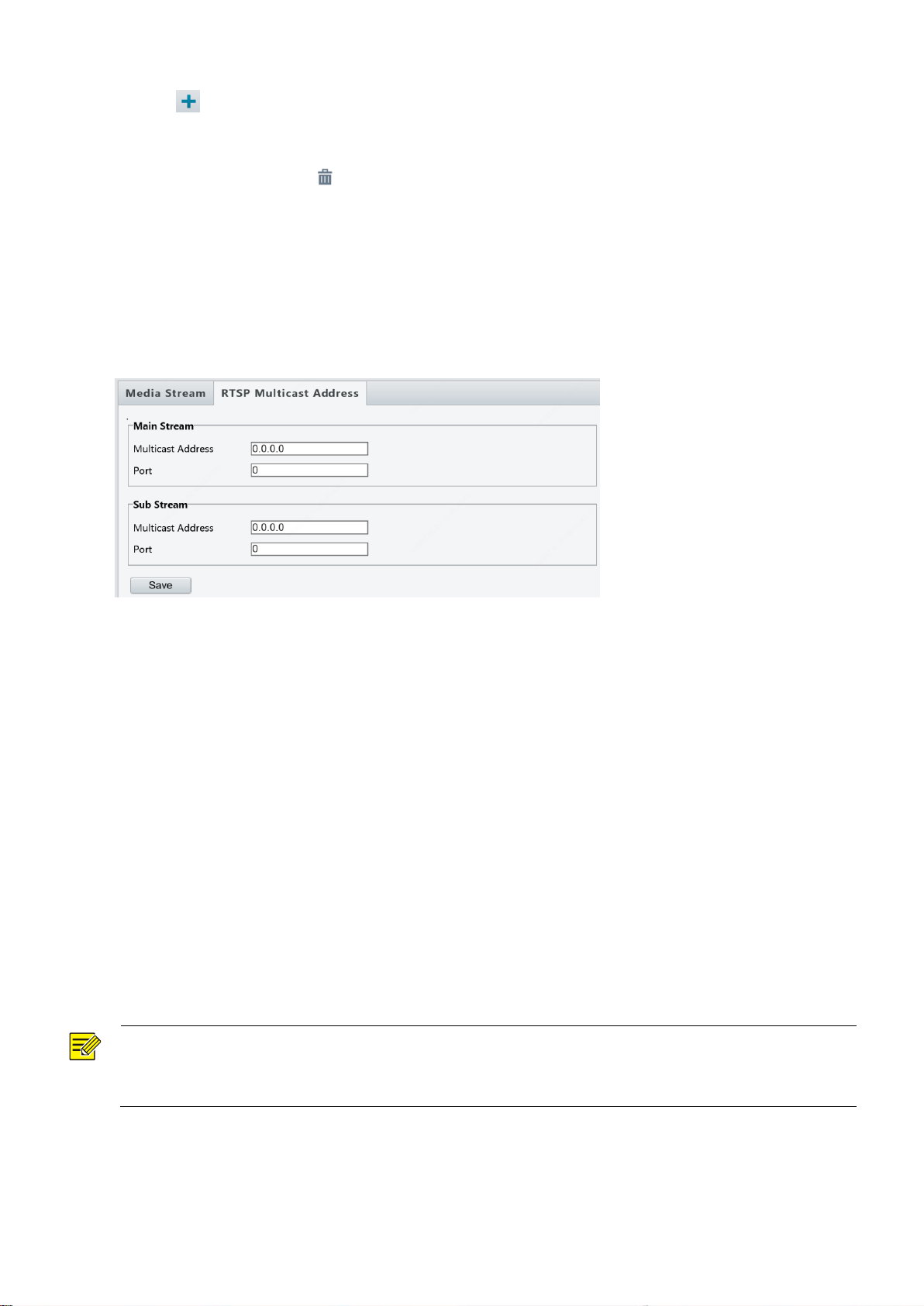
2. Click , select a stream type, and then set the IP address and port number of the unicast or multicast
NOTE!
This function is not supported by some models. Please see the actual model for details.
The alarm triggered actions may vary with models. Please see the actual Web interface for details.
group for the decoding device that receives audio and video streams from the camera.
3. To delete a stream, click .
4. Click OK to complete the operations.
RTSP Multicast Address
After an RTSP multicast address is configured, the third-party player can request the RTSP multicast media
stream from the camera through the RTP protocol.
1. Click Setup > Video > Media Stream > RTSP Multicast Address.
2. Set the multicast address (224.0.1.0 to 239.255.255.255) and port number (0 to 65535).
3. Click Save.
Common Alarm Configuration
You can schedule alarm reporting and set actions that can be triggered by other devices so that alarms and
the triggered actions can be handled in time.
Alarm reporting can be scheduled for motion detection alarm, alarm input, alarm output, tampering
detection alarm, and audio detection alarm. The supported alarms may vary with device model. For the
alarm types that your camera supports, see the Web interface.
Configuring Motion Detection Alarm
Motion detection detects the object motion in a specified rectangular area during a period. You need to set
a detection area, sensitivity of detection, object size, and history for the camera to decide whether to report
a motion detection alarm when it detects motion.
Area Detection
1. Click Setup > Events > Common Alarm > Motion Detection. Set Detection Mode to Area.
25
Page 31
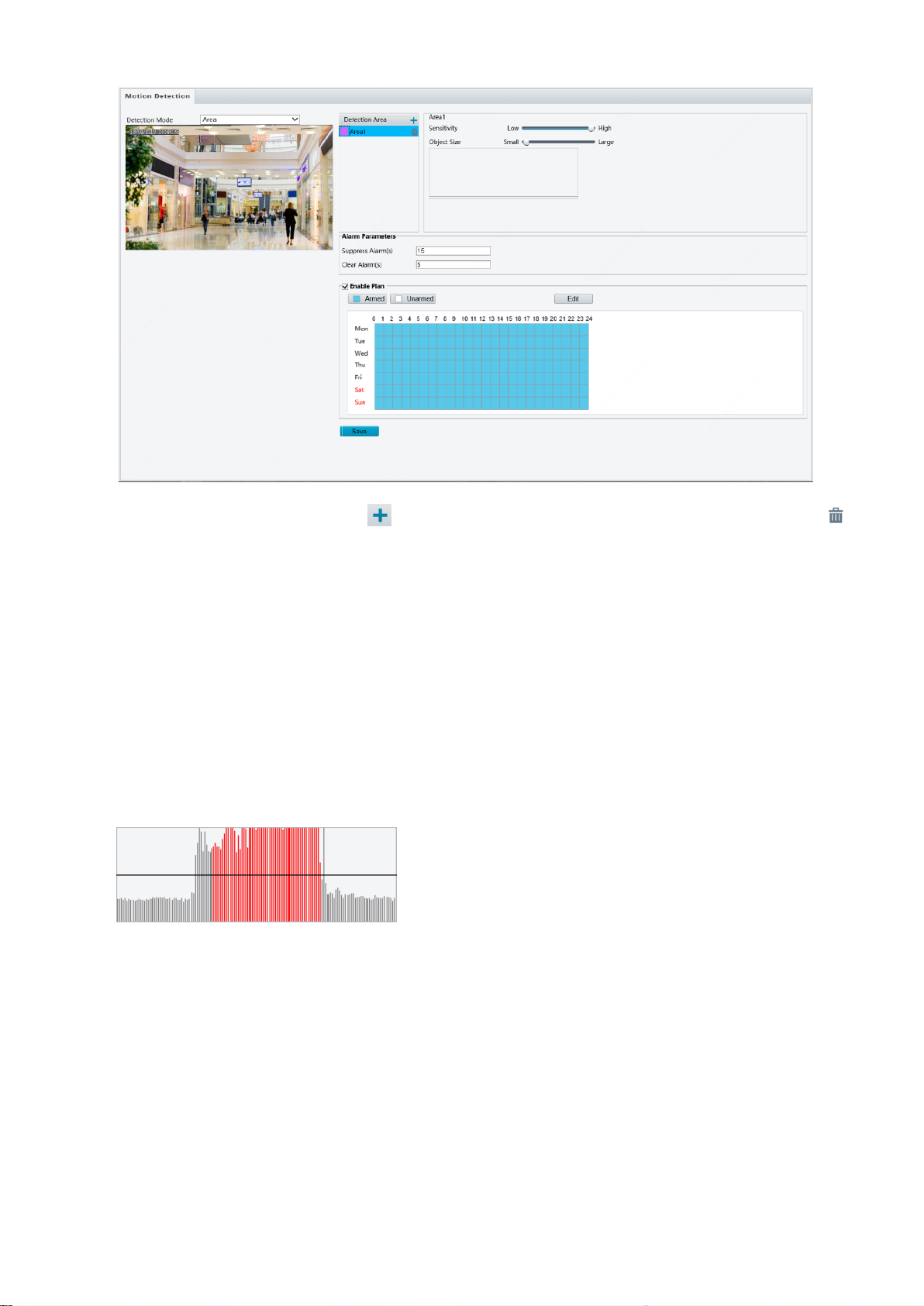
2. In the Detection Area area, click to add a new detection area. To delete a detection area, click .
3. Click and drag the mouse to set a detection area.
4. Set the detection sensitivity, object size, and history for the camera to decide whether to report a motion
detection alarm.
Moving the slider to the right increases detection sensitivity. When the extent of motion within the
detection area exceeds the set object size, the camera reports an alarm.
Object size specifies the minimum ratio of the object's size to the size of the total detection area before
an alarm will be reported. That is to say, to detect motion of tiny objects, you need to draw a small box
(detection area) in the actual motion area accordingly.
Motion detection results are shown in real time. The red lines represent the raised motion detection
alarms. The longer a line, the greater the extent of motion. The denser the lines, the greater the
frequency of motion.
5. Set the alarm parameters.
Suppress Alarm(s): After an alarm is triggered, the same alarm will not be reported within the set time.
Clear Alarm(s): After an alarm is triggered,
a. If the same alarm is not triggered within the set time, the alarm will be cleared and the same alarm
can be reported again.
b. If the same alarm is triggered within the set time, the alarm will not be cleared until the suppress
alarm time expires. Then the same alarm can be reported again.
6. Set actions to be triggered by motion detection alarm and the plan.
The following table describes the triggered actions and how to set a plan.
26
Page 32

Item
Description
Upload to
FTP
With Upload to FTP selected, the camera will automatically upload snapshots to the specified FTP
server when an alarm is triggered.
Note:
Make sure you have completed FTP and Snapshot before using this function (This function is not
supported by some models).
Trigger Email
With Trigger E-mail selected, the camera will automatically send snapshots to the specified E-mail
address when an alarm is triggered.
Note:
Make sure you have completed E-Mail before using this function (This function is not supported
by some models).
Enable Plan
Select the check box and set the start and end times during which motion detection alarm is
effective. You can directly drag the mouse to draw a plan and click Edit to edit time periods in the
table. The time periods cannot overlap. The camera reports alarms during the specified period(s)
only.
You can select from Monday to Sunday and set four periods for each day.
Drag the mouse to draw a plan
Edit time periods in the table
Note:
Plan drawing using a mouse is only supported by IE versions later than 8.0. After setting the plan
for one day, you can apply the same settings to other days by clicking Copy and Paste.
7. Click Save.
Grid Detection
1. Click Setup > Events > Motion Detection. Set Detection Mode to Grid.
27
Page 33
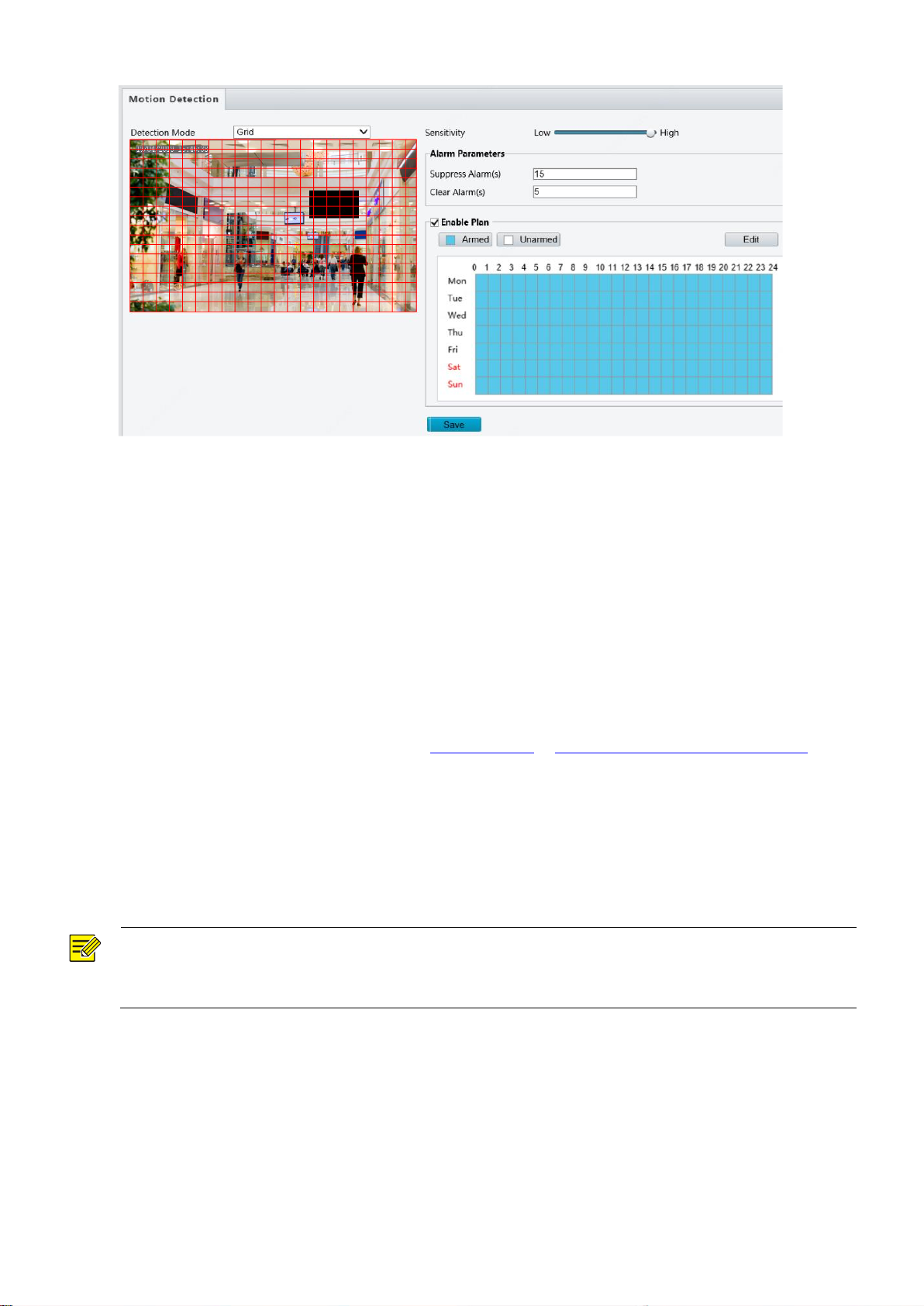
NOTE!
This function is not supported by some models. Please see the actual model for details.
The alarm triggered actions may vary with models. Please see the actual Web interface for details.
2. Detection area(s) can be irregular on the grid.
3. Set detection sensitivity for the camera to decide whether to report a motion detection alarm (alarm
visible on compatible NVR).
4. Set alarm parameters.
Suppress Alarm(s): After an alarm is triggered, the same alarm will not be reported within the set time.
Clear Alarm(s): After an alarm is triggered,
a. If the same alarm is not triggered within the set time, the alarm will be cleared and the same alarm
can be reported again.
b. If the same alarm is triggered within the set time, the alarm will not be cleared until the suppress
alarm time expires. Then the same alarm can be reported again.
5. Set actions to be triggered by motion detection alarm and the plan. For the detailed steps, see the
descriptions of alarm-triggered actions in Area Detection in Configuring Motion Detection Alarm.
6. Click Save.
Configuring Tampering Alarm
Configure tampering alarm so that the camera reports a tampering alarm when the lens is blocked for a
certain length of time.
1. Click Setup > Events > Common Alarm >Tampering Alarm.
28
Page 34

NOTE!
This function is not supported by some models. Please see the actual model for details.
2. Select On for Tampering Alarm.
3. Set detection sensitivity and duration for the camera to decide whether to report a tampering alarm.
Sensitivity is divided into three levels: high-level, mid-level and low-level. Compared with mid-level
sensitivity, the camera can detect blocking from a farther location when sensitivity is set to high. The
camera reports an alarm when the lens is blocked for a specified length of time.
Tampering alarm is effective to the whole screen. To disable tampering alarm, clear the Tampering
Alarm check box.
4. Set actions to be triggered by tampering alarms and the plan. For the detailed steps, see the descriptions
of alarm-triggered actions in Configuring Motion Detection Alarm.
5. Click Save.
System Maintenance
Security
User Management
There are two types of users in the system:
Administrator: referred to as “admin” in this manual. The default name of the administrator is admin,
which cannot be modified. Admin has full permission and can manage all users and devices. Only one
admin user is allowed in the system.
Common user: referred to as “user” in this manual. User only has permission to play live and recorded
video. Up to 32 common users are allowed in the system.
29
Page 35
You can add a user on the user management interface (under Setup > Security > User).
NOTE!
Only admin can change passwords. Changing the username or password for a user when the user is
still logged in will force the user to log out. The user must use the new username or password to log
in.
Only admin can add and delete users. Deleting a user when the user is still logged in will force the
user to log out. A deleted user cannot log in.
NOTE!
This function is not supported by some models. Please see the actual model for details.
After the user is added successfully, you can change the password by entering the new password or delete
the user by clearing the username.
Setting Secure Data Transmission
Set a secure channel for data transmission to ensure security.
1. Click Setup > Network > Port.
2. Enter the port number in the HTTPS Port text box.
3. Click Save.
4. Click Setup > Security > Network Security > HTTPS.
5. Select On for HTTPS. You may import a custom SSL certificate as needed.
6. Click Save.
Next time you log in, enter the address in https://IP:HTTPS port number format, for example,
https://192.168.1.13:443 to enter secure channel mode. If you use the default HTTPS port, enter https://IP.
Authentication
RTSP (Real Time Streaming Protocol) is an application layer protocol. To transmit and control the audio and
video, set RTSP authentication on the Web interface.
1. Click Setup > Security > Network Security > Authentication. HTTP authentication supports Basic mode,
which is compatible with Digest mode and displayed as Basic/Digest on the Web.
2. Select an authentication mode and then click Save.
30
Page 36

APR Protection
NOTE!
This function is not supported by some models. Please see the actual model for details.
NOTE!
This function is not supported by some models. Please see the actual model for details.
NOTE!
If Filtering Mode is set to Whitelist, then only the added IP address (es) are allowed to access the
camera. If Filtering Mode is set to Deny Access, then only the added IP address (es) are not allowed
to access the camera.
Up to 32 IP addresses are allowed. Each IP address can be added once only.
The first byte of each IP address must be 1-223, and the fourth cannot be 0. For example, the
following IP addresses are illegal and cannot be added: 0.0.0.0, 127.0.0.1, 255.255.255.255,
224.0.0.1.
This function protects a camera from ARP attacks. The gateway and the MAC address must be set properly
before a PC can access the camera from another network; if an incorrect MAC is set, only PCs on the same
LAN can access.
1. Click Setup > Security > Network Security > ARP Protection.
2. Select the check box to enable the ARP binding function and set the gateway MAC address.
3. Click Save.
IP Address Filtering
Use IP address filtering to allow or forbid access from specified IP address (es).
1. Click Setup > Security > Network Security > IP Address Filtering.
2. Select On to enable IP address filtering.
3. Select a filtering mode, and then add IP address (es).
4. Click Save.
31
Page 37

Access Policy
NOTE!
Enabling friendly password does not affect use. If you turn it off and log in with a weak password, a page
will pop up, prompting you to change the password. There is no Cancel or Close button on this page. The
default password is treated as weak. This function is not supported by some models. Please see the actual
model for details.
NOTE!
Only some camera models support this function.
1. Click Setup > Security > Network Security > Access Policy.
2. Select On to enable friendly password and MAC Authentication.
3. Click Save.
Watermark
Use watermark to encrypt custom information with video to prevent unauthorized delete or alteration.
1. Click Setup > Security > Watermark.
2. Select On to enable watermark, and then input watermark content.
3. Click Save.
Setting the System Time
You can use the following methods to adjust the system time of your device.
Manually Setting or Synchronizing the System Time
1. Click Setup > Common > Time, and then click the Time tab.
2. Select a synchronization mode.
3. Set the correct time zone and system time. You may also click Sync with Computer Time to synchronize
the time settings of your camera with that of your PC.
4. Click Save.
32
Page 38

Setting the DST
NOTE!
You must use the correct upgrade file for you camera. Otherwise, unexpected results may occur.
The upgrade file is a ZIP file and must include all the necessary files.
The boot program loads the operating system and then the system starts running. The upgrade boot
program function is disabled by default, and only the camera will be upgraded to the latest version.
If enabled, both the camera and the boot program are upgraded, and the operating system of the
following new versions can be booted properly and the camera can be upgraded conveniently.
Ensure that the power supply is normal during upgrade. The device will restart after the upgrade is
completed.
CAUTION!
Perform this operation with caution because restarting the system interrupts the ongoing service.
1. Click Setup > Common > Time, and then click the DST tab.
2. Select On for DST, set the start time, end time, and DST bias.
3. Click Save.
Upgrading the Device
If the device is managed by the central management server and you want to upgrade the devices in batch
mode, it is recommended to perform the upgrade operation on the central server. For detailed steps, see the
user manual for the central management server.
1. Click Setup > System > Maintenance.
2. Under Software Upgrade, click Browse and select the correct upgrade file.
3. Click Upgrade and then confirm to start. The camera will restart automatically after the upgrade is
completed. Some devices support boot program upgrade. To upgrade, select Upgrade Boot Program.
4. You may click Detect to check for new versions available to cloud upgrade.
Restarting the System
1. Click Setup > System > Maintenance.
2. Under Device Restart, click Restart. The device will restart after you confirm the operation.
33
Page 39

Importing and Exporting System Configuration File
CAUTION!
After you perform the Default operation, all settings are restored to factory defaults, except the
following: login password of the system administrator, network settings, and system time.
Make sure you import the correct configuration file for your camera. Otherwise, unexpected results
may occur.
The camera will restart when the configuration file is imported successfully.
Export the current configurations of the camera and save them to the PC or an external storage medium. You
can also quickly restore configurations by importing backup configurations stored on the PC or an external
storage medium back to the camera.
1. Click Setup > System > Maintenance.
2. To import configurations that you have backed up, click Browse next to the Import button and select
the configurations you want to import, and then click Import. The result will be displayed.
3. To export current system configurations, click Browse (next to the Exporting field), set the destination
and then click Export.
4. To restore default configurations, click Default and then confirm the operation. The device will restart
and restore the default configurations. Clicking Default with the check box selected will completely
restore the device to factory default settings.
Collecting Diagnosis Information
Diagnosis information includes logs and system configurations. You can export diagnosis information to your
PC.
1. Click Setup > System > Maintenance.
2. In the Diagnosis Info area, click Browse to set the destination and then click Export.
34
Page 40
NOTE!
Diagnosis information is exported to the local folder in form of a compressed file. You need to
decompress the file using a tool such as WinRAR and then open the file using a text editor.
By selecting Collect Image Debugging Info, you can display video with debugging information at the
same time, which makes troubleshooting easier (This function is not supported by some models).
4 Live View
NOTE!
The supported live view operations may vary with camera model. For the operations that your camera
supports, see the Web interface.
Button
Description
/
Play/stop live video.
Take a snapshot of the current image displayed on the PC.
Note:
The path for saving snapshots are set in System Configuration.
/
Start/stop local recording.
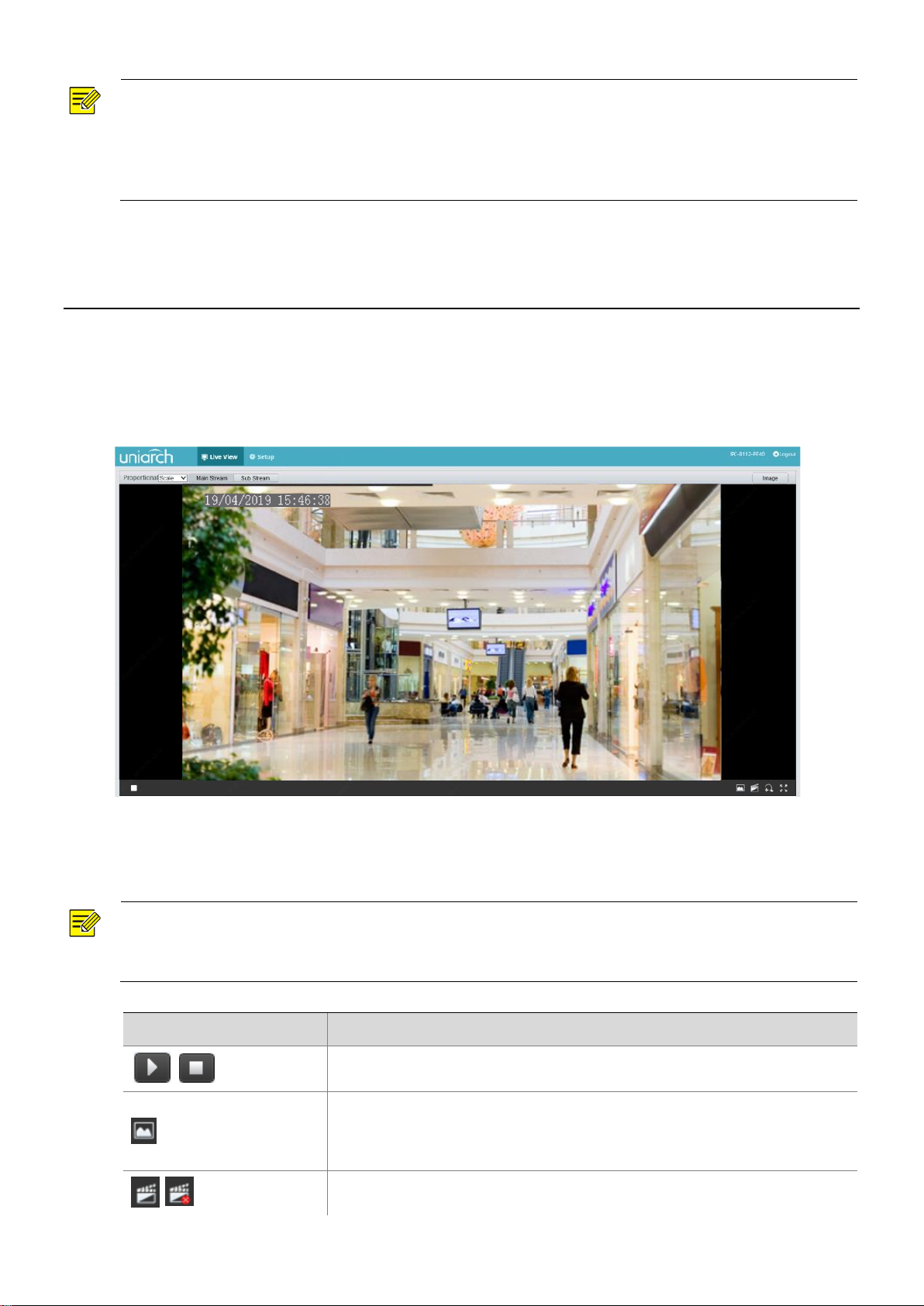
Live view means playing live video (real-time audio and video) received from a camera in a window through
the Web interface.
If you log in with the Live View check box selected, live video appears by default when you are logged in.
You may double-click the window to enter or exit full screen mode.
Live View Toolbar
35
Page 41

Button
Description
Note:
The path for saving local recordings is set in System Configuration.
/
Start/stop digital zoom. For more details, see Using Digital Zoom.
Set image display ratio in the window. For example, to display high-definition
images at original 16:9, select Scale; to display according to window size, select
Stretch; to display with the original image size, select Original.
Reset the packet loss rate to zero.
Note:
After you move the mouse cursor on a live view window, this button appears
on the floating toolbar.
Display packet loss rate and bit rate information at the bottom of the window.
Note:
After you move the mouse cursor on a live view window, this button appears
on the floating toolbar.
Click this button to always display the information. With another click, the
information appears only when you move the mouse cursor over the window
or place it at the bottom. If the mouse cursor rests on the window for around
3 seconds or leaves the window, the information disappears.
Click this button to open the image setting page.
Display in full screen mode.
Select a live video stream that the camera supports: main stream, sub stream.
NOTE!
The supported live view operations may vary with camera model. For the operations that your camera
supports, see the Web interface.
Viewing Certain Area of Images
Digital zoom, area focus and 3D positioning allow you to get more details of certain part of images. Digital
zoom enlarges an image with loss in image quality, while 3D positioning enlarges an image without.
Using Digital Zoom
1. On the Live View page, click on the toolbar.
36
Page 42

2. Click and hold the mouse button, and then drag from top down (draw a rectangle) to specify an area. To
restore the original image size and zoom in on other areas of the image, right-click the mouse.
3. To exit, click .
Appendix B FAQ
What to do if no message prompts me to install ActiveX when I log in on a Windows 7 PC the first time
Answer: Follow these steps to turn off UAC and then log in again:
1. Click the Start button, and then click Control Panel.
2. In the search box, type uac, and then click Change User Account Control Settings.
3. Move the slider to the Never Notify position, and then click OK.
4. After UAC is turned off, log in again.
What to do if the installation of ActiveX failed
Answer: If the installation failed, add the IP address of the camera as a trusted site: open Internet Option in
IE, click the Security tab, click Trusted sites, and then click Sites to add the website.
If you use Windows 7, you need to save the setup.exe to your PC first, right-click the file, select Run as
administrator, and then install it according to instructions.
What to do if live video fails when I log in for the first time
Answer: Close the firewall on your PC and then log in to the Web interface again.
37
 Loading...
Loading...