Page 1

Getting Started Guide
Page 2

Page 3

Trend Micro Incorporated reserves the right to make changes to this document and to the
products described herein without notice. Before installing and using the software,
please review the Readme file, release notes, and the latest version of the Getting Started
Guide, available from Trend Micro’s website:
http://www.trendmicro.com/download
Trend Micro, the Trend Micro logo, Trend Micro Internet Security, Trend Micro
Internet Security Pro, HouseCall, TrendSecure, and TrendLabs are trademarks or
registered trademarks of Trend Micro Incorporated. All other product or company
names may be trademarks or registered trademarks of their owners. All other brand and
product names are trademarks or registered trademarks of their respective companies or
organizations.
Copyright© 2007 Trend Micro Incorporated. All rights reserved. No part of this
publication may be reproduced, photocopied, stored in a retrieval system, or transmitted
without the express prior written consent of Trend Micro Incorporated.
Document part number: PCEM63335/70828
Release date: September 2007
Page 4

The Getting Started Guide for Trend Micro™ Internet Security 2008 explains how
to set up and start using the software. Please read it before installing the software.
For technical support, please refer to Technical Support in this guide for contact
information. For detailed instructions, refer to the Product Help, accessible from the
main console of Trend Micro Internet Security 2008.
Page 5

Contents
Preface
Documentation ........................................................................ii
About this Getting Started Guide ............................................ii
Document Conventions ...........................................................ii
Chapter 1: Introduction
What’s New .............................................................................2
Protection Checklist ................................................................ 3
Automatic Protection ...............................................................3
Main Console ..........................................................................4
Action Buttons and System Tray Icons ...............................4
Chapter 2: Installation
Computer Requirements ..........................................................6
Before Installation ...................................................................7
Upgrading from a Previous Release ........................................8
Installing Trend Micro Internet Security 2008.........................9
Uninstalling Trend Micro Internet Security 2008 ..................15
Chapter 3: Getting Started
Verifying a Successful Installation .......................................20
Accessing the Main Console .................................................20
Checking Current Settings ....................................................20
Getting Updates .....................................................................21
Setting a Password ................................................................22
Getting More Help ................................................................22
Chapter 4: Troubleshooting
Installation and Activation Problems .....................................24
Update Problems ...................................................................25
Frequently Asked Questions .................................................26
i
Page 6

Chapter 5: Technical Support
Before Contacting Technical Support ...................................30
Contacting Technical Support ...............................................30
Submitting Samples of Infected Files ...................................30
Reporting Spam, Fraud, and Incorrectly Tagged Messages .. 31
TrendLabs ..............................................................................31
Other Resources ....................................................................31
ii Contents
Page 7

Preface
This guide explains how to install and begin using Trend Micro™ Internet
Security 2008.
This preface covers the following topics:
• Documentation on page ii
• About this Getting Started Guide on page ii
• Document Conventions on page ii
i
Page 8
Documentation
In addition to this guide, Trend Micro™ Internet Security 2008 also includes
Product Help, which explains key software features. Click the Help button to
get help with the window currently open, or find information on other topics.
Tip: Click Update Now on the main console to get the latest update for Trend
Micro Internet Security 2008
http://www.trendmicro.com/download .
. You can also download the updates from
About this Getting Started Guide
•The Introduction summarizes the main features of Trend Micro Internet
Security 2008.
• Installation explains how to install, upgrade, renew, or remove Trend
Micro Internet Security 2008.
• Getting Started tells how to start using the software.
• Troubleshooting suggests how to solve basic problems, and includes a list
of Frequently Asked Questions.
• Technical Support gives ways to contact Trend Micro if you cannot find
the answers you need in the Troubleshooting section.
Document Conventions
This guide adheres to the following conventions:
STYLE EXPLANATION
ALL CAPITALS Acronyms, abbreviations, and keys on your keyboard
Bold Menu, menu command, button, tab, and option names, as
Italics Documentation titles
Monospace Examples (including sample command lines), program
Note:
Tip:
WA RN I N G !
TABLE 1. Documentation conventions
ii Documentation
well as service and process names
code, Internet and World Wide Web addresses, file names,
folder names, and program output
Configuration notes
Recommendations
Things you should not do
Page 9

Introduction
This chapter gives an overview of Trend Micro Internet Security 2008, and
covers the following topics:
• What’s New on page 2
• Protection Checklist on page 3
• Automatic Protection on page 3
• Main Console on page 4
To start the installation procedure, refer to one of the following topics:
• Computer Requirements for memory, hard drive, and other specifications
• Before Installation for pre-installation tasks and other considerations
• Upgrading from a Previous Release if your computer has an older version
of Trend Micro Internet Security installed
• Installing Trend Micro Internet Security 2008 for installation instructions
• Getting Started for instructions on using Trend Micro Internet Security
2008
1
1
Page 10

What’s New
1
• A sophisticated monitoring system intercepts and blocks unauthorized
changes to your computer’s operating system and applications.
n
o
i
t
c
u
d
o
r
t
n
I
• A single integrated scan now checks for computer viruses, spyware, and
operating system security flaws.
• Security activity reports let you see at a glance how Trend Micro Internet
Security 2008 has protected you recently.
• New Trend Micro Data Network controls offer more protection.
• A streamlined installation process sets up the software quickly and easily.
• Image spam filtering catches unwanted messages containing only
advertising graphics used to bypass text-based scanning systems.
2 What’s New
Page 11

Protection Checklist
Trend Micro Internet Security 2008 protects you from these threats:
THREAT PROTECTION
Viruses, Trojan horse programs, and worms on
your computer or arriving in email messages
Spyware, Web browser tracking “cookies,”
rootkits
Unauthorized changes to your operating
system settings, registry or Hosts file
Unsolicited “spam” messages and email fraud
attempts (“Phishing”)
“Pharming” and other Web threats Protection Against Web Threats
Hackers Personal Firewall
Wireless network intruders Wireless Home Network Monitor
Theft of private information from instant
messages, email messages or websites
Microsoft
TABLE 1-1. Trend Micro Internet Security 2008 protection features
®
software security flaws Scheduled & Custom Scans
Protection Against Viruses & Spyware
Protection Against Viruses & Spyware
Unauthorized Change Prevention
Spam Email Filter
Data Theft Prevention
Automatic Protection
Once installed, Trend Micro Internet Security 2008 protects you by
automatically performing the following tasks:
• Checks for and downloads any new update every three hours
• Helps prevent spyware from monitoring your computer, as well as
unauthorized changes to your computer’s settings
• Searches for risks every time you open, copy, move, or save a file
• Stops you from downloading risky files, and blocks attempts to visit sites
that pose a security threat
• Helps protect your computer from hackers and network viruses
1
I
n
t
r
o
d
u
c
t
i
o
n
For greater protection, enable the optional Parental Controls, Spam Email
Filter, Data Theft Prevention, and Wireless Home Network Monitor features.
3Protection Checklist
Page 12
Main Console
Use the main console to see an overview of how Trend Micro Internet
1
Security 2008 protects you. Clicking the tabs on the left side of the window
reveals more detailed information and controls related to those features.
n
o
i
t
c
u
d
o
r
t
n
I
Tip: On the main console’s Overview tab, click the link next to Protection
status to see all of the features currently protecting you.
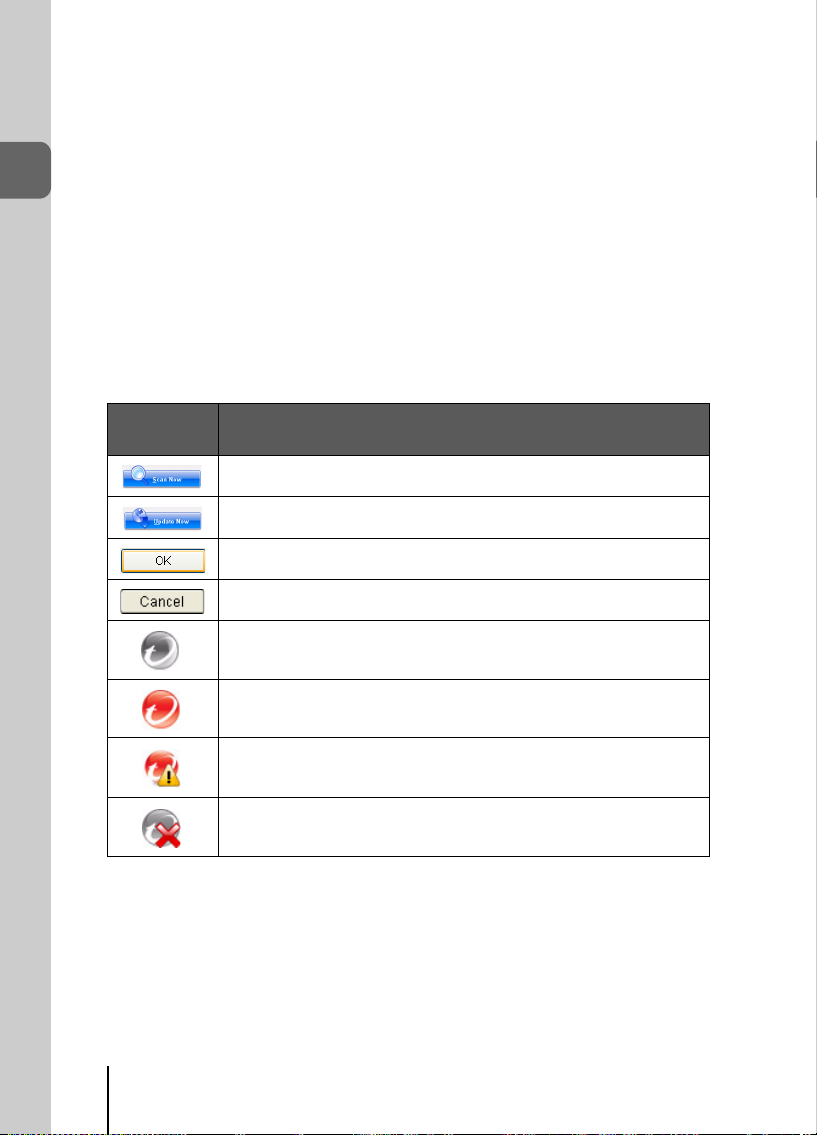
Action Buttons and System Tray Icons
The list below explains buttons and icons commonly used in Trend Micro
Internet Security 2008:
BUTTON /
I
CON
Scans your computer for security threats.
Downloads the latest update from Trend Micro.
Closes a window and saves any changes you made.
Closes the window without saving any changes.
Trend Micro Internet Security 2008 has started loading.
Trend Micro Internet Security 2008 currently protects you.
Trend Micro Internet Security 2008 needs your help to solve a
problem (double-click the icon to open the main console for more
information).
Trend Micro Internet Security 2008 has expired.
DESCRIPTION
TABLE 1-2. Common program buttons and icons
4 Main Console
Page 13

Installation
This chapter explains how to install Trend Micro Internet Security 2008.
The topics in this chapter include:
• Computer Requirements on page 6
• Before Installation on page 7
• Upgrading from a Previous Release on page 8
• Installing Trend Micro Internet Security 2008 on page 9
• Uninstalling Trend Micro Internet Security 2008 on page 15
2
5
Page 14

Computer Requirements
Table 2-1 lists the computer hardware and software specifications for
2
installing Trend Micro Internet Security 2008.
n
o
i
t
a
l
l
a
t
s
n
I
COMPUTER SPECIFICATIONS
Microsoft® Windows®
operating system
• Windows Vista
Business, or Ultimate (32-bit or 64-bit version)
• Windows
Edition 2005, or Tablet PC Edition 2005 with Service
Pack 2 (SP2)
Processor (CPU)
• Windows Vista
Intel® Pentium® 800MHz (1Ghz recommended), or
an equivalent processor
• Windows
Intel™ Pentium™ 350MHz, or equivalent processor
Minimum memory
• Windows Vista
1GB of RAM (Windows™ Vista® Home Basic
requires only 512MB minimum RAM)
• Windows
256MB minimum RAM (512MB recommended)
Disk space 300MB of available hard disk space for installation
Monitor Minimum of 1024 x 768 pixels and
High Color (65536 colors)
®
Home Basic, Home Premium,
®
XP Home, Professional, Media Center
®
®
XP
®
®
XP
TABLE 2-1. Trend Micro Internet Security 2008 computer requirements
Note: This version supports Intel Hyper-Threading and Dual-Core processors, as
well as RAID 0 (striping) or RAID 1 (mirroring or duplexing).
Internet Requirements
You need an Internet connection to activate the software, download updates,
obtain information about security threats, or visit the Trend Micro website.
Table 2-2 lists required and compatible Internet software.
Note: Some Internet Service Providers charge a fee every time you go online.
Others bill you based on how long you connect to the Internet, or how
much data you receive. If you must pay such fees, you might want to shut
down the Automatic Updates feature of Trend Micro Internet Security
2008. Also consider modifying your Internet connection software or router
to prevent the Automatic Updates feature from opening a connection (refer
to your software or router documentation for instructions).
6 Computer Requirements
Page 15

COMPATIBLE INTERNET SOFTWARE AND SERVICES
Compatible Web browsers • Microsoft Internet Explorer® 6.0 with Service Pack
Compatible email software
2, or 7.0 (required)
• Mozilla
• Microsoft Outlook
• Microsoft Outlook Express 6.0 with Service Pack 2
• Mozilla
®
Firefox® 2.0
®
2000, 2002, 2003, or 2007
®
Thunderbird™ 1.5 or 2.0
• Windows Mail™ (Windows Vista™ only)
®
• AOL
Compatible Web-based mail
services
Compatible instant messaging
services
Mail
• Microsoft Hotmail
• Windows Live™ Mail
• Yahoo!
• AOL
• ICQ
• MSN
• Windows Live™ Messenger 8.0
• Yahoo!
®
Mail
®
Instant Messenger™ (AIM®) 5.9
®
5.1 and ICQ® Lite
®
Messenger 7.5 (Windows® XP only)
®
Messenger 8.0
®
TABLE 2-2. Compatible Internet software and services
Before Installation
A few simple preparations can help make installing Trend Micro Internet
Security 2008 much easier.
2
I
n
s
t
a
l
l
a
t
i
o
n
• Make sure that the computer where you plan to install the program meets
the requirements listed in Tabl e 2 -1 on page 6. You cannot install Trend
Micro Internet Security 2008 if your computer does not meet the
requirements, including a working Internet connection.
• You must have administrator privileges on your computer to install Trend
Micro Internet Security 2008. If you have installed other software on your
computer before, then you probably have these privileges.
Note: If you downloaded Trend Micro Internet Security 2008 onto a
computer running Windows Vista, right-click the installation program
and select Run as Administrator.
7Before Installation
Page 16

• If a firewall like the Windows Firewall already protects your computer,
please disable or remove the other firewall before installing Trend Micro
Internet Security 2008, which includes a Personal Firewall.
2
• Many businesses and schools offer Internet connections through a “proxy
server,” a computer that accelerates or filters communications with the
n
o
i
t
a
l
l
a
t
s
n
I
Internet. Your home computer probably does not use a proxy server.
If necessary, Trend Micro Internet Security 2008 will import your proxy
server settings from Internet Explorer. If Internet Explorer does not have
the correct proxy server settings, then you must will need to enter the
proxy server’s name or IP address and port number yourself.
Note: Trend Micro Internet Security 2008 uses proxy server information
when connecting to the Internet to activate your software, set up your
Personal Firewall, and receive updates from Trend Micro.
• Close all windows except the installation program window.
• Make sure to keep your serial number handy. Where you find the serial
number depends on whether you downloaded Trend Micro Internet
Security 2008 or bought the software on a disk.
Upgrading from a Previous Release
You can start installing Trend Micro Internet Security 2008 on your computer
without making an effort to remove older Trend Micro software first. The
installation program will automatically detect and uninstall these versions:
• Trend Micro Internet Security 2007
• Trend Micro Internet Security 2006
• Trend Micro AntiVirus plus AntiSpyware 2007
• Trend Micro AntiVirus 11
Note: An upgrade will delete all files quarantined by older Trend Micro security
software and all entries in the Approved and Blocked Lists.
Quarantined files may contain viruses or include spyware that should not
remain on your computer. If you must preserve them, restore the files, then
transfer them to an isolated location like a USB memory stick before removing the program. For instructions on how to restore quarantined files, please
refer to the Product Help.
8 Upgrading from a Previous Release
Page 17

Installing Trend Micro Internet Security 2008
Before installing Trend Micro Internet Security 2008, make sure to go
through the checklist on page 7.
2
To install Trend Micro Internet Security 2008:
1. Start the installation program by placing the CD into your CD-ROM
drive, or by running the installation program downloaded from Trend
Micro (http://www.trendmicro.com/download).
After the screen shown below disappears, click Install Program.
FIGURE 2-1. Installation program launch screen
Note: If the CD-ROM menu window does not open
automatically, double-click the My Computer icon on the
Windows desktop, open the CD-ROM drive, and then
double-click the setup.exe file.
2. If a User Account Control window asks for your permission to install the
program, click Continue.
I
n
s
t
a
l
l
a
t
i
o
n
FIGURE 2-2. User Account Control warning
9Installing Trend Micro Internet Security 2008
Page 18

2
3. Read the terms and conditions in the Trend Micro End User License
Agreement carefully. To install the software, you must select I accept the
Agreement, and then click Next.
n
o
i
t
a
l
l
a
t
s
n
I
FIGURE 2-3. License Agreement screen
4. Type the serial number in the Serial Number screen and click Next. Click
the Not sure where to find the Serial Number? link if you need help.
FIGURE 2-4. Serial Number screen
5. On the Ready to Install screen, click Install.
FIGURE 2-5. Ready to Install screen
10 Installing Trend Micro Internet Security 2008
Page 19

Note: Click Customize on the Ready to Install screen to change the
installation folder, or skip installing the Personal Firewall included
with Trend Micro Internet Security 2008.
• To install Trend Micro Internet Security 2008 in a different
folder, click Change... Click Next after choosing a location.
FIGURE 2-6. Installation Location screen
• If you would prefer to use the Windows Firewall, remove the
mark from the Install the Trend Micro Personal Firewall
checkbox. After making your choice, click Install.
2
I
n
s
t
a
l
l
a
t
i
o
n
FIGURE 2-7. Firewall screen
6. Installation of Trend Micro Internet Security 2008 now begins.
FIGURE 2-8. Installing Trend Micro Internet Security screen
11Installing Trend Micro Internet Security 2008
Page 20

2
7. When the window confirming a successful installation opens after a few
minutes, click Next to activate the software (normally you should not
remove the mark from the checkbox).
n
o
i
t
a
l
l
a
t
s
n
I
FIGURE 2-9. Trend Micro Internet Security installed successfully
8. The installation program now begins setting up the security software.
FIGURE 2-10. Setting Up Trend Micro Internet Security screen
9. Please provide an account password, your full name, and an email address
that you check regularly to activate the software. Select your current
location from the list beside Country/region and then click Next.
FIGURE 2-11. Activate Trend Micro Internet Security screen
12 Installing Trend Micro Internet Security 2008
Page 21

10. After confirming that you entered the correct information, please print
this page for future reference, and then click Next.
FIGURE 2-12. Need to make any changes?
11. To help set up your Personal Firewall, select how your computer currently
connects to the Internet and click Next.
2
I
n
s
t
a
l
l
a
t
i
o
n
FIGURE 2-13. How do you normally connect to the Internet?
13Installing Trend Micro Internet Security 2008
Page 22

2
12. Mark the Open the main console now checkbox and click Finish.
n
o
i
t
a
l
l
a
t
s
n
I
FIGURE 2-14. Trend Micro Internet Security now protects you
Tip: To install Trend Micro Internet Security 2008 on another computer
connected to your home network, just launch the installation program on
that computer and follow the same steps.
When activating a new installation of Trend Micro Internet Security 2008,
select a name (or description) to distinguish the new one from the
previous one. Since you can use Trend Micro Internet Security 2008 to
manage the security of other computers by remote control, these different
names will help you keep track of multiple installations.
14 Installing Trend Micro Internet Security 2008
Page 23

Uninstalling Trend Micro Internet Security 2008
Before removing Trend Micro Internet Security 2008, make sure you have
logged onto the computer with
removal process), and close any other open programs.
WA RN I N G ! Removing the program deletes all quarantined files, which may
contain viruses or include spyware that should not remain on your
computer. If you must preserve them, restore the files, then transfer
them to an isolated location like a USB memory stick before removing
Trend Micro Internet Security 2008.
1. You have two ways to start removing Trend Micro Internet Security 2008:
• Click the Windows Star t button and select All Programs > Trend
Micro Internet Security > Uninstall Trend Micro Internet
Security.
FIGURE 2-15. Windows Vista Start menu uninstall option
administrator privileges (needed during the
2
I
n
s
t
a
l
l
a
t
i
o
n
• Open the Control Panel and then double-click Add or Remove
Programs (Windows XP) or Uninstall a program (Windows Vista).
From the list of programs, select Trend Micro Internet Security,
and then click Remove (Windows XP) or Uninstall (Windows
Vista).
FIGURE 2-16. Windows Vista Control Panel uninstall option
15Uninstalling Trend Micro Internet Security 2008
Page 24

2
2. Click Next after reading the warning.
n
o
i
t
a
l
l
a
t
s
n
I
FIGURE 2-17. Warning screen
3. Click Remove to confirm that you want to uninstall the program.
FIGURE 2-18. Ready to Uninstall Trend Micro Internet Security
4. If you have enabled password protection, submit the correct password.
16 Uninstalling Trend Micro Internet Security 2008
Page 25

5. The Uninstalling Trend Micro Internet Security window names all of the
files removed.
FIGURE 2-19. Uninstalling Trend Micro Internet Security screen
6. Click Finish to restart your computer once the program has been
successfully removed.
2
I
n
s
t
a
l
l
a
t
i
o
n
FIGURE 2-20. Trend Micro Internet Security Successfully Uninstalled
Uninstalling with the Trend Micro Diagnostic Toolkit
If you ran into problems during installation, configuration, or uninstallation,
use the Trend Micro Diagnostic Toolkit to remove the program.
To uninstall the program using the Trend Micro Diagnostic Toolkit:
1. Open the folder where you installed the program (usually
C:\Program Files\Trend Micro\Internet Security).
17Uninstalling Trend Micro Internet Security 2008
Page 26

2
2. Double-click TISSuprt.exe to open the diagnostic toolkit.
n
o
i
t
a
l
l
a
t
s
n
I
FIGURE 2-21. Tab A of the Trend Micro Diagnostic Toolkit
3. On the [E] Uninstall tab, click the 4. Uninstall button.
FIGURE 2-22. Tab E of the Trend Micro Diagnostic Toolkit
4. In the small window that opens, click Uninstall to remove the program.
WA RN I N G! You cannot cancel after clicking Uninstall. The Trend Micro
Diagnostic Toolkit will delete the program files, registry entries,
and other components of Trend Micro Internet Security 2008.
18 Uninstalling Trend Micro Internet Security 2008
Page 27

Getting Started
After installing Trend Micro Internet Security 2008, complete the tasks
explained on the following pages to start protecting your computer.
• Verifying a Successful Installation on page 20
• Opening the Main Console on page 20
• Checking Current Settings on page 20
• Controlling Your Updates on page 21
• Setting a Password on page 22
• Getting More Help on page 22
3
19
Page 28

Verifying a Successful Installation
Use the European Institute for Computer Antivirus Research (EICAR) test
3
d
e
t
r
a
t
S
g
n
i
t
t
e
G
file to confirm that Trend Micro Internet Security 2008 protects you.
Note: The EICAR test file is not a virus. This harmless text file with a *.com
extension does not replicate and contains no harmful payload.
1. Open http://us.trendmicro.com/us/support/virus-
primer/eicar-test-files/ .
2. Download the EICAR test file by clicking one of the eicar.com links,
such as eicar.com (HTTP).
After showing an “eicar_virus” warning, Trend Micro Internet Security 2008
will quarantine eicar_test.com and record what happened in the Virus
Scan log.
Opening the Main Console
Using the main console of Trend Micro Internet Security 2008, you can easily
check or customize your security settings, download updates, and run scans.
You have three ways to open the main console:
• Click the Windows Start button, and then select All Programs > Trend
Micro Internet Security > Trend Micro Internet Security.
• In the system tray at the bottom of your screen, right-click the Trend
Micro Internet Security 2008 icon and select Open Main Console.
• Double-click the Trend Micro Internet Security 2008 desktop icon.
Checking Current Settings
After opening the main console, you can see an overview of your protection.
• Protection status shows either “Good,” “At risk,” or “Incomplete.” “At
risk” appears if you disable recommended security features. “Incomplete”
appears if you neglect to activate the software.
• Expiration date shows when you will stop receiving updates (if
Subscription appears here instead, click the Not activated yet link).
20 Verifying a Successful Installation
Page 29

• Last update shows when you last downloaded an update. No date
appears here until you have downloaded an update for the first time. By
default, Trend Micro Internet Security 2008 checks for new updates every
three hours.
• Last scan shows the date of the last scan for security threats. No date
appears here until you have scanned your computer for the first time.
• Security activity provides a link to a report of recent security events.
Two large blue buttons also appear at the bottom of the window.
• Click Scan Now to detect and eliminate spyware, rootkits, viruses, Trojan
horse programs, worms, and other security threats.
• Click Update Now to download any new update available.
Controlling Your Updates
To download the latest update immediately:
1. Open the main console (see page 20).
2. On the Overview screen, click Update Now.
To check when you have received previous updates:
1. Open the main console (see page 20).
2. Click Other Settings, then expand the Logs header.
3. Choose Update from the dropdown list.
4. Click the View Logs button.
3
G
e
t
t
i
n
g
S
t
a
r
t
e
d
To check or change the update schedule:
1. Open the main console (see page 20).
2. Click Other Settings, then expand the Automatic Updates header.
3. Click the Settings... button.
4. Mark the Automatically check for updates checkbox. Trend Micro
Internet Security 2008 checks for updates every three hours by default.
5. To see the progress of each update, select Notify you before the update
starts.
21Controlling Your Updates
Page 30

Setting a Password
Set a password to prevent others from changing your settings. To manage the
3
security of other computers on a home network, you must set a password.
1. On the main console, select Other Settings, and then click Password.
d
e
t
r
a
t
S
g
n
i
t
t
e
G
2. Under Password, click Settings...
3. Mark the Enable password protection checkbox, and then type the same
password in both the Password and Confirm password fields.
Tip: The password must contain at least six characters, and can include
only letters of the alphabet (upper or lower case) and numbers (0
through 9). Refer to the Product Help > Tips > Establishing Strong
Passwords topic for more recommendations.
4. In the Password hint field, type a short phrase that will remind you of
your password in case you forget it later. Choose a hint that would not
allow someone else to guess your password easily.
5. Click OK to save your password.
Getting More Help
Trend Micro Internet Security 2008 offers several types of help:
HELP OPTION DESCRIPTION
Help & Support Click this button on the left side of the main console for links
Context-Sensitive Help Click the Help button to learn more about a given window.
Mouseover Help Stop your mouse cursor over an icon without clicking to
to the Product Help and Knowledge Base.
display a short description.
TABLE 3-1. Help options
22 Setting a Password
Page 31

Troubleshooting
This chapter explains how to solve basic problems you may encounter while
using Trend Micro Internet Security 2008.
The topics explained in this chapter include:
• Installation and Activation Problems on page 24
• Update Problems on page 25
• Frequently Asked Questions on page 26
4
23
Page 32

Installation and Activation Problems
You may encounter one of the following problems during the installation and
4
g
n
i
t
o
o
h
s
e
l
b
u
o
r
T
activation of Trend Micro Internet Security 2008:
• The installation program stops responding.
• Trend Micro Internet Security 2008 will not start after a successful
installation.
• You lost your serial number or have an invalid serial number.
• You cannot activate Trend Micro Internet Security 2008 during
installation or through the main console after installation.
To solve an installation problem:
• Make sure you have administrator privileges on the computer where you
tried to install Trend Micro Internet Security 2008.
a. Press the CTRL - ALT - DELETE keys simultaneously to open a
small window showing the name of the account you have used to log
into the computer (look under Logon Information), write down the
account name, and then click Cancel.
b. Open the Control Panel.
• If your computer runs Windows XP, click User Accounts to find
out if the account you wrote down has administrator privileges.
• If your computer runs Windows Vista, click User Accounts and
Family Safety, then click User Account to see if the account
you wrote down has administrator privileges.
c. If you have not logged onto the computer with administrator
privileges, switch to an account that has those privileges.
• Make sure the computer meets all installation requirements on page 6.
• Make sure that you followed all of the instructions in the Installing Trend
Micro Internet Security 2008 section of this Getting Started Guide.
If these suggestions do not help solve the problem, contact Trend Micro
Technical Support for help. See page 30 for details.
24 Installation and Activation Problems
Page 33

To solve an activation problem:
• Make sure you entered the serial number correctly. You must provide this
information in the following format:
XXXX-XXXX-XXXX-XXXX-XXXX
Note: Each X corresponds to a number or letter. You can type the letters in
upper or lower case.
• Select a unique name or description for each installation after the first.
• To recover a lost password, try visiting this website:
http://www.trendsecure.com/my_account/
• Look for any warning messages or log information related to activation.
You can search for a solution based on this information.
• You can use the trial version of Trend Micro Internet Security 2008 for a
limited time only. Purchase Trend Micro Internet Security 2008 before
your trial expires to maintain your security.
If the suggestions above do not help solve the problem, please contact Trend
Micro Technical Support. See page 30 for details.
Update Problems
First, make sure that your computer can reach the Internet, then check your
network and computer for any obvious hardware or software failures. If Trend
Micro Internet Security 2008 still cannot download updates, check your
connection with the update server.
To check your connection with the update server:
• Open the Windows command prompt.
4
T
r
o
u
b
l
e
s
h
o
o
t
i
n
g
Note: For Windows XP, click the Start button, select Run..., and type cmd
in the window that opens. For Windows Vista, click the Start button
and type cmd in the Start Search field.
• Type the following commands to make sure your computer can resolve
the update server’s Fully Qualified Domain Name (FQDN).
nslookup
ping tis16-p.activeupdate.trendmicro.com
If your computer cannot contact the update server, please contact Trend Micro
Technical Support. See page 30 for details.
25Update Problems
Page 34

Frequently Asked Questions
How do I recover a lost serial number?
4
To recover a lost serial number, try visiting this website:
g
n
i
t
o
o
h
s
e
l
b
u
o
r
T
http://www.trendsecure.com/my_account/
If you cannot retrieve your serial number using the website above, please
send email to support@support.trendmicro.com to request a copy
of the original number. You can also submit a request for help to the following
support Web site:
http://esupport.trendmicro.com/support/consumer/submitonline.do
Why does uninstalling and then reinstalling Trend Micro
Internet Security 2008 on the same computer use up two of my
allowed installations?
Trend Micro cannot distinguish a new installation on a different computer
from a new installation on the same computer. When you reach the maximum
number of installations allowed, Trend Micro Internet Security 2008 will
automatically help you to deactivate the unused installation.
Why does Not activated yet appear on the main console after
successfully activating the program?
In some cases, depending on your network connection, you might not receive
a response from Trend Micro immediately. In this case, try clicking Update
Now. If Trend Micro Internet Security 2008 can successfully check for
updates, your correct expiration date should appear.
Can Trend Micro Internet Security 2008 filter instant
messages?
Trend Micro Internet Security 2008 cannot filter chat sessions, but can check
for and eliminate viruses, Trojan horse programs, worms, spyware, and other
threats sent through instant messaging software.
26 Frequently Asked Questions
Page 35

Can Trend Micro Internet Security 2008 scan all file types?
Yes, Trend Micro Internet Security 2008 can check every file on your
computer for threats, as well as email messages and your computer’s memory.
What Internet browsers work with Trend Micro Internet
Security 2008?
Data Theft Prevention and the Parental Controls in Trend Micro Internet
Security 2008 work with these browsers:
• Microsoft™ Internet Explorer™ 6.0 with Service Pack 2 (for Microsoft™
Windows™ XP only)
• Microsoft™ Internet Explorer™ 7.0
• Mozilla™ Firefox™ 2.0
What is phishing?
Phishing is a form of fraud meant to steal personal information. For example,
a fake website may carefully mimic a legitimate website to fool you into
divulging your name, credit card numbers, social security number, or other
confidential information. Criminals can then rob your financial accounts or
pose as you to make purchases online.
4
T
r
o
u
b
l
e
s
h
o
o
t
i
n
g
FIGURE 4-1. A sample phishing website
27Frequently Asked Questions
Page 36

4
Another common phishing fraud begins with an email message urging you to
solve a problem with a financial account immediately. The message looks
legitimate, but includes a link that opens a fraudulent website.
g
n
i
t
o
o
h
s
e
l
b
u
o
r
T
FIGURE 4-2. A sample phishing email message
Criminals also use Internet Relay Chat (IRC) and other instant messaging
programs to slip undesirable files and links to phishing websites into
“dynamic content” (such as graphics, website addresses, and media files) sent
directly to you through a chat window.
FIGURE 4-3. Sample phishing instant messages
28 Frequently Asked Questions
Page 37

Technical Support
Trend Micro seeks to provide technical support that exceeds your expectations. In this chapter, you can find out how to get technical support.
Remember, you cannot get support before activating Trend Micro Internet
Security 2008.
This chapter covers the following topics:
• Before Contacting Technical Support on page 30
• Submitting Samples of Infected Files on page 30
• Reporting Spam, Fraud, and Incorrectly Tagged Messages on page 31
• TrendLabs on page 31
• Other Resources on page 31
5
29
Page 38

Before Contacting Technical Support
Before contacting technical support, please consider a few other ways to find
5
t
r
o
p
p
u
S
l
a
c
i
n
h
c
e
T
a fast and easy answer to your question:
• Refer to the documentation. Check both the Troubleshooting chapter of
this Getting Started Guide and the Product Help for information about
Trend Micro Internet Security 2008.
• Visit the Trend Micro Technical Support site, which provides the very
latest information about all Trend Micro software, as well as answers to
questions submitted by others.
http://www.trendmicro.com/support/consumer/
Contacting Technical Support
Use this site to find the right Trend Micro telephone number:
http://esupport.trendmicro.com/support/consumer/callus.do
To help Trend Micro solve your problem as quickly as possible, please have
the following information ready before calling:
• Your Trend Micro Internet Security 2008 serial number
• Your Trend Micro Internet Security 2008 version number
• The exact text of the error message, if any
• A brief explanation of what you were doing when the problem occurred
(including ways to reproduce the problem)
Tip: Open the main console (page 20), select Help & Support, and click
Product Information to find your program version and serial numbers.
You can also open a technical support case online by visiting:
http://esupport.trendmicro.com/support/consumer/submitonline.do.
Submitting Samples of Infected Files
If a file seems unsafe but your security software fails to detect any problems,
please submit the suspicious file to this website:
http://subwiz.trendmicro.com
Include a brief description of any symptoms you have experienced. Trend
Micro specialists will “dissect” the file to identify any malicious code.
30 Before Contacting Technical Support
Page 39

Reporting Spam, Fraud, and Incorrectly Tagged Messages
Please forward spam email messages, as well as legitimate messages misidentified as spam, to the following address:
false@support.trendmicro.com
Please forward fraudulent (phishing) messages to the following address.
antifraud@support.trendmicro.com
Trend Micro Technical Support checks for patterns in these messages to
improve the software that detects spam and fraudulent email messages.
TrendLabs
TrendLabs, a global network of research and support centers, provides continuous information and updates to Trend Micro customers around the world.
Staffed by hundreds of highly-trained engineers and skilled support professionals, dedicated service centers in Paris, Munich, Manila, Taipei, Tokyo,
and California ensure a rapid response to new computer security threats.
For more information about TrendLabs, please visit this Web site:
http://us.trendmicro.com/us/about/company/trendlabs/
Other Resources
• Visit http://www.trendsecure.com/my_account/ to access
your Trend Micro account, or http://www.trendsecure.com for
access to more security tools and services.
• The Trend Micro site, http://www.trendmicro.com, offers free
trial downloads of award-winning security software, plus tools like the
Virus Map, which reports on virus infections found all over the world.
• You can download software updates and patches at any time from
http://www.trendmicro.com/download/ .
5
T
e
c
h
n
i
c
a
l
S
u
p
p
o
r
t
31Other Resources
Page 40

5
t
r
o
p
p
u
S
l
a
c
i
n
h
c
e
T
32 Other Resources
 Loading...
Loading...