
LAPTOP GSM
System
User Manual
TLC SOLUTIONS INC.
SUITCASE GSM USER MANUAL
(SEPARATE COMPONENT PACKAGE)
UPDATED SEPTEMBER 9, 2009

ALL RIGHTS RESERVED!
This product and related documentation are protected by copyright and are distributed un der
license restricting its use, copying, distributing and decompilation. No part of this product or
related documentation may be reproduced in any form by any means without prior written
authorization from TLC Solutions, Inc. or its licensors, if any.
SPECIFICATIONS ARE SUBJECT TO CHANGE!
While all reasonable efforts have been made to assure the accuracy of this document, TLC
Solutions, Inc. assumes no liability resulting from any errors or omissions in this document or
from the use of the information obtained herein. The information contained in this document has
been carefully reviewed and is believed to be reliable. However, no responsibility is assumed for
inaccuracies. TLC Solutions, Inc. re serves the right to make changes to any equipment
described herein to improve reliability, function, or design, and reserves the right to revise this
document and to make changes in content hereof with no obligation to notify any person of
revisions or changes. TLC Solutions, Inc. does not assume any liability arising out of the use or
application of any equipment or circuit described herein.
SOFTWARE COPYRIGHT!
The equipment described in this manual includes computer program(s) (the “SOFTWARE”) which
are stored in semiconductor memories or other media. The SOFTWARE is licensed through TLC
Solutions, Inc. by its respective vendor and is protected by copyright, trade secret, patent and
other intellectual property laws. Accordingly, the use of the SOFTWARE described in this manual
requires a separate software license from the respective vendor and may not be copied or
reproduced in any manner inconsistent with that license. The purchase of equipment shall not be
deemed to grant either directly or implied, any license under copyrights, trade secrets, patents, or
patent applications of TLC Solutions Inc. or its vendors.
RADIO TRANSMISSION SYSTEM RESTRICTIONS OF USE!
The equipment described in this document generates Radio Frequency (RF ) waves and requires
proper Federal Communications Commission (FCC) frequency clearance before being used.
TLC Solutions, Inc. is not responsible for seeking the approval and assumes no liability from the
use of the equipment. It is solely the responsibility of the END USER to obtain proper approval
and frequency clearance prior to operations. While TLC Solutions, Inc. may assist the END
USER in obtaining proper clearance, at no time will any submission be submitted in the name of,
by or for TLC Solutions, Inc. All applications shall be submitted in the name of, by and for the
END USER only. TLC Solutions, Inc. does not assume any liability arising out of the improper
use of any equipment described herein.
TLC Solutions, Inc.
120 Cumberland Park Drive
Suite 101
St. Augustine, FL. 32095
(904) 829-0323
Product names mentioned in this manual are the trademarks of their respective manufacturers.
Printed in the U.S.A. © 2006 TLC Solutions, Inc
.

THIS PAGE INTENTIONALLY LEFT BLANK.

TABLE OF CONTENTS
Preface ....................................................................................................................................... 1
General Information ..................................................................................................................................... 1
Intended Users of this Guide ...................................................................................................................... 1
Conventions Used in this Guide ................................................................................................................. 1
Guide Organization ...................................................................................................................................... 1
Safety Precautions ....................................................................................................................................... 3
TLC’s Laptop GSM System ..................................................................................................... 5
Single Chassis MSC, BSC, GSN, and SMSC ............................................................................................. 5
External Connectivity................................................................................................................................... 5
Single Carrier BTS ........................................................................................................................................ 6
Small Portable Packaging ........................................................................................................................... 6
System Installation ................................................................................................................... 7
Unpacking the System ................................................................................................................................. 7
Deploying the system ‘without’ the use of an Ethernet HUB or Switch ................................................. 7
Deploying the system ‘with’ the use of an Ethernet HUB or Switch ....................................................... 7
Connecting a second BTS to the system .................................................................................................. 7
Connecting a Range Enhancement Package ............................................................................................ 7
System Configuration .............................................................................................................. 8
Previously Configured Parameters ............................................................................................................ 8
Hardware and Software Information .......................................................................................................... 8
Administration Procedures Using the Web Browser interface ............................................................... 9
Upgrades to the System .......................................................................................................... 9
Periodic Maintenance ............................................................................................................ 10
Technical Support .................................................................................................................. 10
Appendix A – Common Acronyms ....................................................................................... A1
Appendix B – Quick Deployment Guide .............................................................................. B1
Deploying the system ‘without’ the use of an Ethernet HUB or Switch .............................................. B3
Deploying the system ‘with’ the use of an Ethernet HUB or Switch .................................................. B10
CONNECTING A SECOND BTS .............................................................................................................. B18
CONNECTING THE RANGE ENHANCEMENT PACKAGE (REP) ......................................................... B21
APPENDIX C Configuration Guide ........................................................................................ C1
Introduction ............................................................................................................................................... C1
Starting your PMN system configuration ............................................................................................... C1
Provider Configuration ............................................................................................................................. C3
MSC Configuration .................................................................................................................................... C4

BSC Configuration .................................................................................................................................... C5
Cell Group Configuration ......................................................................................................................... C5
Cell Configuration ..................................................................................................................................... C6
LA Configuration ....................................................................................................................................... C6
PMX Administrator Password Change .................................................................................................... C7
Tenancy Configuration ............................................................................................................................. C8
General Tab .......................................................................................................................... C9
Ranges Tab .......................................................................................................................... C9
Authentication Tab .............................................................................................................. C10
Diverts Tab .......................................................................................................................... C11
SIM Card and Extension Number Configuration .................................................................................. C14
Provisioning Method 1 ............................................................................................................................ C14
General Tab ........................................................................................................................ C15
GPRS Tab ........................................................................................................................... C16
Advanced Tab ..................................................................................................................... C17
Diverts Tab ............................................................................................................................................... C18
Provisioning Method 2 ............................................................................................................................ C19
SMS Distribution Lists ............................................................................................................................ C21
Gateways .................................................................................................................................................. C23
Routes 26
General Tab ........................................................................................................................ C27
Destinations Tab .............................................................................................................. ....................... C27
Click on the ‘Destinations’ tab to see the list of destinations. ........................................................... C27
Patterns Tab ....................................................................................................................... C28
Click on the ‘Patterns’ tab to see the list of patterns. ......................................................................... C28
Translations Tab ................................................................................................................. C29
Click on the ‘Translations’ tab to see the list of translations. ............................................................ C29
CLI Transforms ................................................................................................................... C29
Destination Transform ......................................................................................................... C32
Tenancy Translations ............................................................................................................................. C34
Presence .................................................................................................................................................. C36
Appendix D - I/O Connector Pinouts .................................................................................... D1
Ethernet Port .............................................................................................................................................. D1
Ethernet Cable Pin Outs “Cross Over Cable” ........................................................................................ D1
Appendix E - dBm-to-Watts Conversion Table ................................................................... E1
Appendix F - ARFCN Frequencies ........................................................................................ E1
F-1. GSM-850 ARFCN Frequencies (in MHz) ..................................................................................... E1
F-2. E-GSM-900 ARFCN Frequencies (in MHz) ................................................................................. E3
F-3. GSM-1900 ARFCN Frequencies (in MHz) ................................................................................... E5
F-4. GSM-1800 ARFCN Frequencies (in MHz) ................................................................................... E9
Preface
General Information
The information in this document describes the connectivity and deployment of TLC
Solutions’ Laptop GSM (LTGSM) System (Separate Components).
Intended Users of this Guide
This guide is intended to be read by individuals responsible for the deployment and use
of the LTGSM System. It is assumed that the reader has a basic knowledge of Global
Systems for Mobile Communications (GSM) technology.
Conventions Used in this Guide
WARNING – Alerts the reader to a situation that
WARNING – Alerts the reader to a situation that
might affect personal safety.
might affect personal safety.
WARNING
WARNINGWARNING
!
!
!
CAUTION
CAUTION
CAUTION
NOTE
NOTENOTE
STOP
STOP
Guide Organization
CAUTION – Alerts the reader to a situation that
CAUTION – Alerts the reader to a situation that
might affect the integrity of equipment, software or
might affect the integrity of equipment, software or
data.
data.
NOTE – Provides the reader with important or
NOTE – Provides the reader with important or
supporting information.
supporting information.
STOP – Informs the reader that a procedure is
STOP – Informs the reader that a procedure is
finished.
finished.
The guide is organized as follows:
Section 1, “The TLC Laptop GSM System”, describes the subsystem and its
characteristics and provides a list of items provided with the package.
_____________________________________________________________________________________
LTGSM User Manual 1 Confidential

Section 2, “Installation”, covers the procedures to unpack and install the equipment.
Section 3, “System Configuration”, provides current system information as well as
screenshots and configuration commands for the MSC, BSC and BTS.
Section 4, “Upgrades to the MSC and BSC”, provides instructions for LTGSM
upgrades.
Section 5, “Periodic Maintenance”, describes the procedures that should be
performed periodically to ensure the LTGSM operates properly.
Section 6, “Technical Support”, provides information to obtain additional technical
assistance, if required.
Appendix A, “Acronyms”, provides a list of acronyms used in this manual.
Appendix B, “Quick Installation Guide”, provides step by step procedures on
installing the LTGSM.
Appendix C, “Configuration Guide”, provides information on the Web Browser
interface and how to proper administer the LTGSM
Appendix D, “I/O Connector Pinouts”, provides pinouts for all external connectors on
the LTGSM.
Appendix E, “dBm to Watts Conversion Table”, provides a dBm to Watts conversion
table.
Appendix F, “ARFCN Frequencies”, provides the ARFCN frequencies for the 850,
900, 1800, and 1900 MHz frequency bands.
_____________________________________________________________________________________
LTGSM User Manual 2 Confidential
Safety Precautions
The following general safety precautions must be observed during all phases of system
installation, service, and repair of this equipment. Failure to comply with these
precautions or specific warnings elsewhere in this manual violates safety standards of
design, manufacture, and intended use of this equipment. TLC Solutions, Inc. assumes
no liability for the customer’s failure to comply with these requirements.
The safety precautions listed below represent warnings of certain dangers that TLC
Solutions, Inc. is aware of. As the user of the product, you should follow these warnings
for the safe operation of the equipment in your operating environment.
Read this Guide Thoroughly
!
CAUTION
CAUTION - The technician must be completely familiar with the procedures
contained in this document before beginning the actual installation.
Complete all Steps
!
CAUTION
CAUTION - The technician must perform each procedure in its entirety.
Ground the Equipment
WARNING - To minimize shock hazard, the equipment should be connected to a
WARNING
properly grounded electrical outlet.
Only Qualified Personnel Should Service the Equipment
WARNING
WARNING - Only trained personnel may remove equipment covers to install and
service the internal assemblies of the LTGSM. The LTGSM contains highenergy equipment that can cause injury or death. Under certain conditions,
dangerous voltages and/or currents may exist even with the power supply
removed.
Do Not Service or Adjust Alone
WARNING - Do not attempt internal service or adjustment unless another person
capable of rendering first aid and resuscitation is present. Dangerous voltages
WARNING
and/or currents, capable of causing injury or death, are present in this
equipment.
_____________________________________________________________________________________
LTGSM User Manual 3 Confidential

Do Not Operate in an Explosive Atmosphere
WARNING - Do not operate the equipment in the presence of flammable gases
or fumes. Operation of electrical equipment in such an environment creates a
WARNING
definite safety hazard.
Do Not Substitute Parts or Modify Equipment
WARNING - Because of the danger of introducing additional hazards, do not
install substitute parts or perform any unauthorized modification of equipment.
WARNING
_____________________________________________________________________________________
LTGSM User Manual 4 Confidential

TLC’s Laptop GSM System
The LTGSM System is a complete GSM system in a suitcase. The package contains a
MSC, GSN*, SMSC, AUC*, MMSC*, BSC and BTS. This system is capable of providing
Voice, Circuit Switched Data (CSD) and High Speed Data. Due to the system type, the
area of coverage is limited to 500 feet indoors and approximately 100 yards outdoors
depending on the environment. Larger footprints can be achieved with the addition of
TLC’s Range Enhancement Pack (REP) and external antennas.
The main features of the LTGSM System are as follows:
• Single Chassis MSC, BSC, GSN*, AUC* and SMSC with single PCI slot
for external voice connectivity
• External connectivity is achieved via a SIP interface
• Single Carrier BTS with internal antenna (up to 20 supported)
• Small package consisting of all communications equipment and power
equipment
Note: * Indicates a non-standard feature and the purchase of a separate software
license is required.
Single Chassis MSC, BSC, GSN, and SMSC
A single Laptop computer running Windows XP with Linux Redhat on a virtual machine
is used to support the MSC, BSC, GSN, AUC and SMSC functionality of the network.
While this is a very small package it is capable of supporting up to 20 single carrier
BTSs.
External Connectivity
External connectivity is achieved with a single Ethernet interface. Both administration as
well as voice traffic is carried over this interface.
_____________________________________________________________________________________
LTGSM User Manual 5 Confidential

Single Carrier BTS
The single carrier BTS is offered in all four (4) standard GSM Bands. As with most
single carrier base stations this one offers 8 total timeslots (7 usable + 1 control). Voice,
CSD and General Packet Radio Service (GPRS) are supported. The LTGSM can
support up to 20 single carrier BTSs.
!
CAUTION
CAUTION – The single carrier BTS used in the LTGSM system was designed as
an indoor base station. As such, the receiver on the BTS is not as efficient as
those found in commercial grade outdoor base stations. This means that the
LTGSM system will be more susceptible to interference and may not provide a
balanced link to and from the GSM handset. TLC has taken steps to resolve
some of the complications associated with the BTS, but can not guarantee
optimal service during its use.
Note – The standard GSM bands are 850 MHz, 900 MHz, 1800 MHz and 1900
MHz.
Small Portable Packaging
The packaging is system dependant, but in most situations the major components are in
a single suitcase with additional base stations and peripheral equipment packaged in
additional cases. The typical packaging is as follows:
• Laptop PC consisting of the MSC, BSC, GSN, AUC and SMSC with associated
voice connectivity module (if any)
• USB Security Dongle for the MSC/BSC software
• Power Supply and cord for the Laptop
• Single Carrier BTS
• Range Enhancement Package
• One (1) Straight Through Ethernet cable
• One (1) Crossover Ethernet cable
• Two (2) standard AC power cords
If there are additional BTSs they will be supplied in a separate case so that they may be
deployed separately from the main set-up. The separate case will normally include the
following:
• Single Carrier BTS
• Range Enhancement Package
• One (1) Straight Through Ethernet cable
• One (1) Crossover Ethernet cable
• Two (2) standard AC power cord
_____________________________________________________________________________________
LTGSM User Manual 6 Confidential
System Installation
Completely read and understand this entire section as well as Appendix B of this
document before deploying and operating the LTGSM.
There are several ways to deploy the LTGSM. It may be deployed as a single carrier
system with no external connectivity or there could be multiple carriers connected across
the world via the internet using technology such as VPN connectivity. The following
sections will provide the user with instructions on how to unpack and connect the system
for the best results. The following scenarios will be covered:
• Unpacking the system
• Deploying the system without
• Deploying the system with
• Connecting a second BTS to the system
• Connecting to a Range Enhancement Package
Unpacking the System
1. Ensure that there is adequate space to operate the system.
2. Remove all equipment from the foam case.
3. Inventory the equipment in accordance with the packing slip.
4. Ensure that none of the components are damaged.
5. Proceed to system installation.
the use of an Ethernet HUB or Switch
the use of an Ethernet HUB or Switch
CAUTION – Do not operate the system while it is still in the foam. Doing so
could damage components due to overheating.
Deploying the system ‘without’ the use of an Ethernet HUB or Switch
See section 1 of the Quick Installation Guide in Appendix B of this document.
Deploying the system ‘with’ the use of an Ethernet HUB or Switch
See section 2 of the Quick Installation Guide in Appendix B of this document.
Connecting a second BTS to the system
See section 3 of the Quick Installation Guide in Appendix B of this document.
Connecting a Range Enhancement Package
See section 4 of the Quick Installation Guide in Appendix B of this document.
_____________________________________________________________________________________
LTGSM User Manual 7 Confidential
System Configuration
The software configuration is vitally important to how the LTGSM operates. No matter
how well the system is deployed and connected it will not work without the appropriate
software settings. Most systems are delivered to the end user ready to operate out of
the box with the exception of a couple of items. Those items are typically the subscriber
database and the routing tables. In some instances this information is provided to TLC
prior to shipment and has already been administered according to the contract and
instructions. If this is the case, the system should be ready to operate as soon as you
receive it, if not follow the instructions provided in this section as well as Appendix C of
this document to complete the database administration. This section provides the
following information:
• Previously configured parameters (System Dependant)
• Hardware and Software information
• Administration procedures using the Web Browser interface
Previously Configured Parameters
The following information is system dependant and was recorded from the LTGSM prior
to shipment. While this information may appear to be part of the master configuration
guide, it is changed for each individual customer.
• MSC IP Address contact support
• Web Access Address Local Host (127.0.0.1)
• BSC IP Address LAN #1 contact support
• User Name pmnowner
• Password admin
Note – IP Addresses may be different depending on the end user’s request.
Hardware and Software Information
With the exception of the operating system and software version the following
information is system dependant and was recorded from the LTGSM prior to shipment.
While this information may appear to be part of the master configuration guide, it is
changed for each individual customer.
• Operating System Windows XP
• MSC/BSC Software Version 2.0.0.14 / 3.0.64.38
• License # XXXXX
• Chassis Type Dell E6400 ATG
All other pertinent information can be found on the accompanying packing list.
_____________________________________________________________________________________
LTGSM User Manual 8 Confidential

Administration Procedures Using the Web Browser interface
It is extremely important that you read and understand the System Administrator
User Guide before attempting to make administrative changes to the system.
Please refer to Appendix C “System Administrator User Guide” for all administrative
procedures.
Note: For information on how to configure the BSC and BTS please refer to the
Configuration Manager user guide that is provided as a separate document.
Upgrades to the System
TLC provides software upgrades as they become available to customers with a Software
License Agreement (SLA). It should be noted that a SLA is not necessary to resolve
problems with the software. If a problem should arise it will be addressed on a case by
case basis. For the purposes of the guide TLC will address only those issues
surrounding the SLA.
If the end user has a SLA and a software upgrade becomes available TLC will contact
the user via telephone and email to inform him/her at the time of availability. The
customer will be provided an FTP site from which to download the patch/software
upgrade. The username and password will be provided in a separate email for security
purposes. Instructions on how to apply the upgrade will be provided at the time of the
download.
TLC does not provide hardware upgrades unless specified and agreed upon during the
contracting phase of the business transaction. All hardware is considered operational at
the time of acceptance. If a problem should arise with the hardware during the warranty
period it will be repaired or replaced at no charge to the customer. All other hardware
issues will be addressed on a case by case basis.
_____________________________________________________________________________________
LTGSM User Manual 9 Confidential

Periodic Maintenance
Due to the simplicity of the LTGSM very little maintenance is required. The following
items should be performed on a periodic basis:
• Back up the configuration database (after every major system change)
• Test the system monthly to ensure it operates correctly
• Clean all components of the system with a soft damp cloth and compressed air
as needed
• Test cables periodically and replace as needed.
CAUTION – Do not clean the system components when in operation. Never use
a wet cloth to clean the system as there are vent holes that may allow moisture
inside the chassis. If a damp cloth is used to clean the system components allow
24 hours of drying time before the next power up.
WARNING – Never use a damp cloth on the system while it is in operation.
Doing so may cause death or injury from electric shock! Always unplug any
WARNING
device before maintenance or cleaning.
Technical Support
TLC provides technical support to its customers based on contract requirements. The
technical support department can be reached at 904-829-0323 option #3 24 hours a day.
In addition each customer is provided with a user name and password to access user
documentation and other important information at TLC’s web site. The URL is
www.toplevelcom.com/support
documentation and software.
. You must have a username and password to access
_____________________________________________________________________________________
LTGSM User Manual 10 Confidential

Appendix A – Common Acronyms
Abis Refers to the BSC-BTS data link
ARFCN Absolute Radio Frequency Channel Number
BCCH Broadcast Control Channel
BSC Base Station Controller
BSS Base Station System
BTS Base Transceiver Station
CPU Central Processing Unit
CSD Circuit Switch Data
DSP Digital Signal Processor
EDGE Enhanced Data Rates for GSM Evolution
FTP File Transfer Protocol
GGSN Gateway GPRS Support Node
GPRS General Packet Radio Service
GSM Global Systems for Mobile Communications
GSN GPRS Support Node
HLR Home Location Registry
HPA High Power Amplifier
IP Internet Protocol
ISDN Integrated Services Digital Network
MCPA Multi-Carrier (High) Power Amplifier
MMS Multimedia Message Service
MMSC Multimedia Messaging Service Center
MS Mobile Station
MSC Mobile Switching Center
OMC-R Operations Maintenance Center – Radio
PBX Private Branch Exchange
PRI Primary Rate Interface
PSTN Public Switched Telephone Network
RF Radio Frequency
SCPA Single Carrier Power Amplifier
SGSN Serving GPRS Support Node
SMS Short Message Service
SMSC Short Messaging Service Center
_____________________________________________________________________________________
LTGSM User Manual A1 Confidential

TRAU Transcoder and Rate Adaptation Unit
VLR Visitor Location Registry
_____________________________________________________________________________________
LTGSM User Manual A2 Confidential

_________________________________________________________________________________________________________________________________
LTGSM User Manual B1 Confidential
Appendix B – Quick Deployment Guide
_________________________________________________________________________________________________________________________________
LTGSM User Manual B2 Confidential
!
CAUTION
NOTE
WARNING
STOP
WARNING – Alerts the reader to a situation that
might affect personal safety.
CAUTION – Alerts the reader to a situation that
might affect the integrity of equipment, software or
data.
NOTE – Provides the reader with important or
supporting information.
STOP – Informs the reader that a procedure is
finished.
STRAIGHT ETHERNET CABLE
CROSS OVER ETHERNET CABLE
CONVENTIONS USED
SMA MALE TO SMA MALE (TX)
SMA MALE TO SMA MALE (RX)
N-Type Male to 7/16 DIN Male (ANT)

_________________________________________________________________________________________________________________________________
LTGSM User Manual B3 Confidential
Deploying the system ‘without’ the use of an Ethernet HUB or Switch

_________________________________________________________________________________________________________________________________
LTGSM User Manual B4 Confidential
Set-Up Without Ethernet HUB or Switch
Step # 1:
Insert Security Dongle into any available USB port.
Security Dongle
_________________________________________________________________________________________________________________________________
LTGSM User Manual B5 Confidential
Set-Up Without Ethernet HUB or Switch
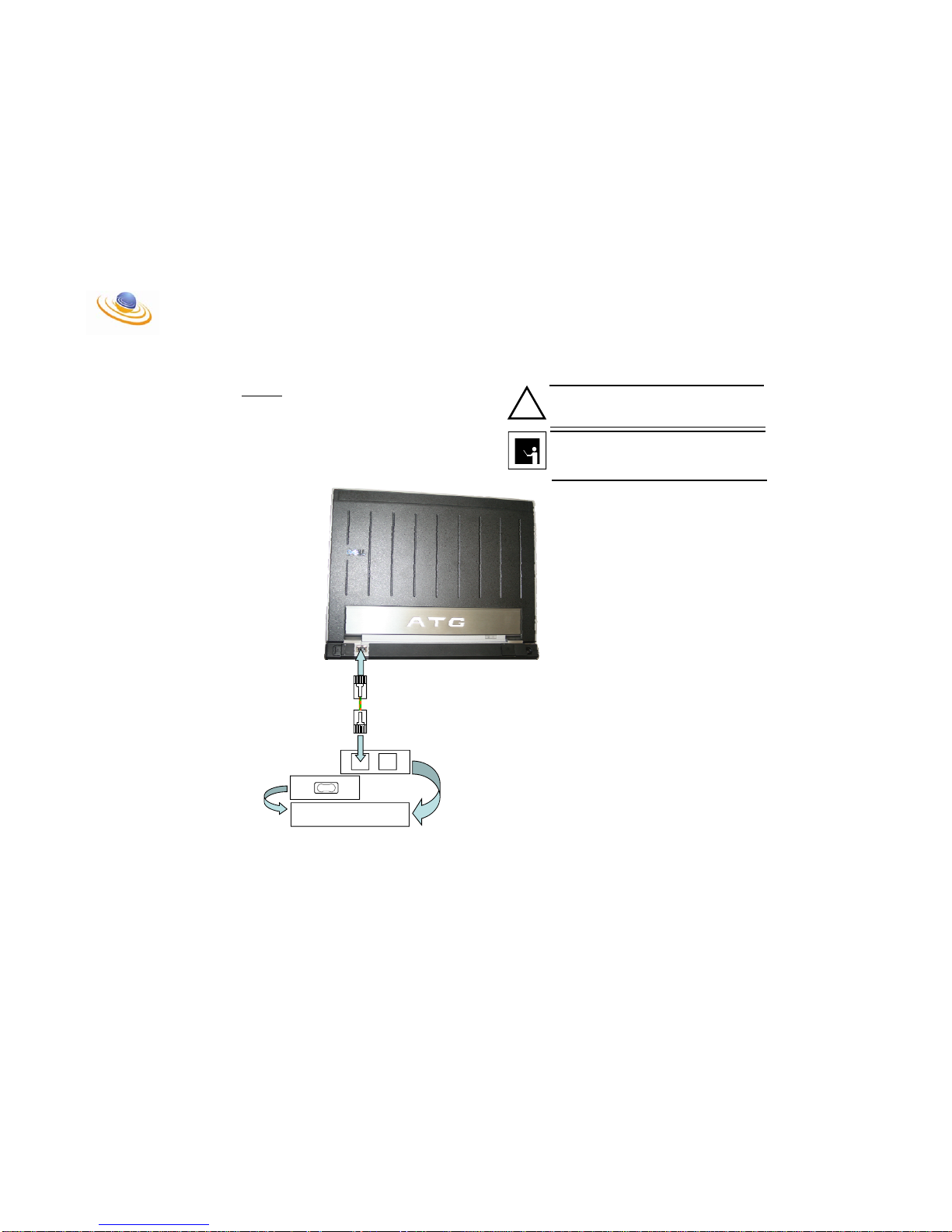
Step # 2:
Connect the LAN port on the Laptop to the LAN port on the
BTS Power Block using an Ethernet crossover cable.
AC to DC Power Block
!
CAUTION
DO NOT PLUG THE CABLE INTO THE BTS SIDE OF THE BTS
POWER BLOCK. THIS PORT PROV IDES PO E (P ower Over
Ethernet) [48 VDC] FOR THE BTS. IF THESE PORTS ARE
MISTAKEN THE LAPTOP COULD BE DAMAGED!!!
NOTE
ENSURE THAT A CROSSOVER CABLE IS USED BETWEEN
THE LAPTOP MSC AND THE POWER BLOCK. THIS IS
ONLY NECESSARY W HEN A HUB OR SWITCH IS NOT
USED.
LAN BTS
X
_________________________________________________________________________________________________________________________________
LTGSM User Manual B6 Confidential
Set-Up WithoutEthe rnet HUB or Switch
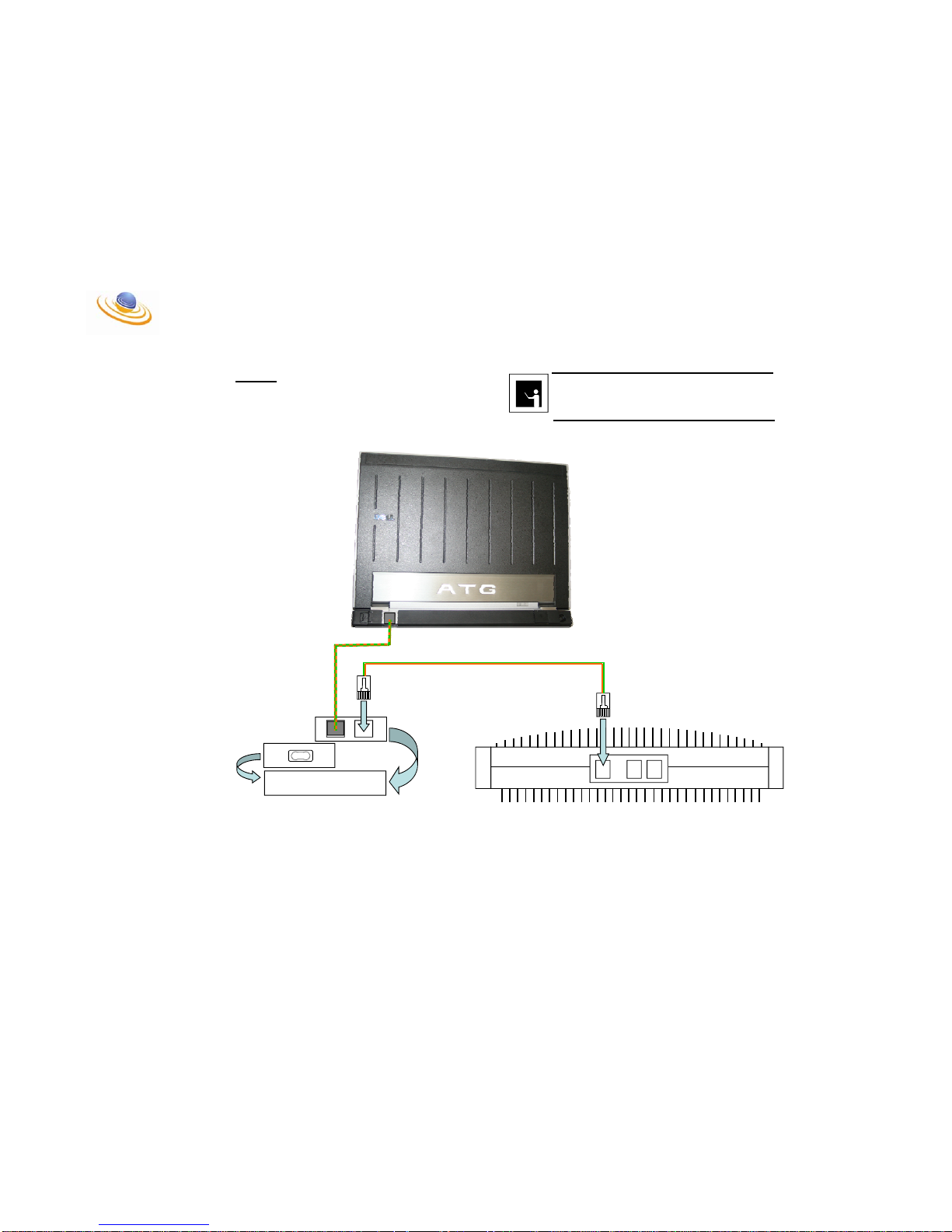
Step # 3:
Connect the BTS port on the BTS Power Block to the main
Ethernet Port on the BTS. This port can be identified by the 48
VDC marking above it. This connection will be accomplished
with a straight through Ethernet cable.
AC to DC Power Block
NOTE
ENSURE THAT A STRAIGHT THROUGH CABLE IS USED
BETWEEN THE POWER BLOCK AND THE BTS.
OTHERWISE THE SYSTEM WILL NOT WORK
48 VDC
BTS
_________________________________________________________________________________________________________________________________
LTGSM User Manual B7 Confidential
Set-Up Without Ethernet HUB or Switch
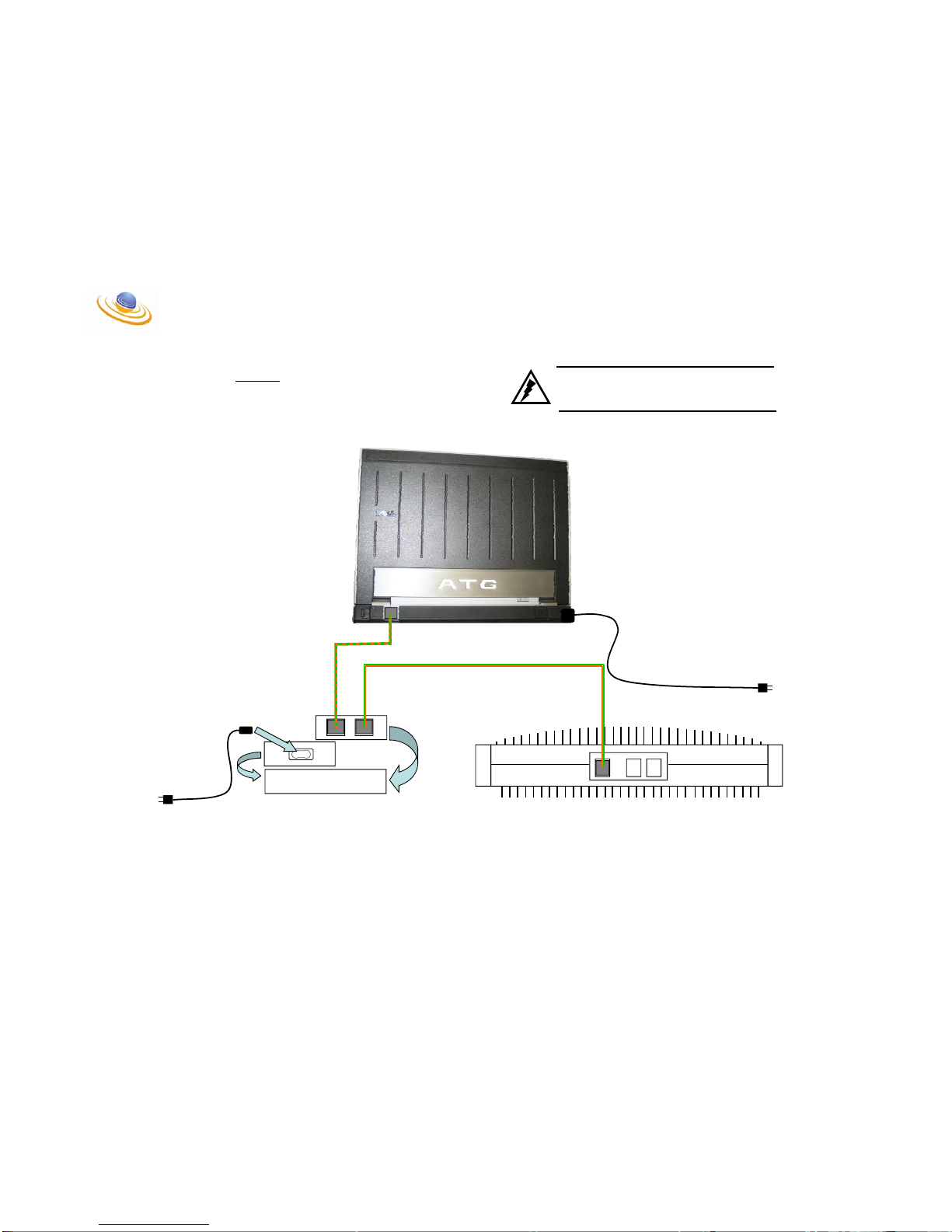
Step # 4:
Connect the AC Power to both the Laptop and the BTS Power
Block.
AC to DC Power Block
48 VDC
To AC Outlet
WARNING
ALWAYS USE CAUTION WHEN PLUGGING IN AC
ADAPTER. SERIOUS INJURY OR DEATH COULD BE
CAUSED BY ELECTRIC SHOCK!!!
To AC Outlet

_________________________________________________________________________________________________________________________________
LTGSM User Manual B8 Confidential
Set-Up Without Ethernet HUB or Switch
Step # 5:
Press the power button above the keyboard on the laptop.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B9 Confidential
STOP
THIS COMPLETES THE SET-UP W HEN DEPLOYED
WITHOUT AN ETHERNET HUB OR SWITCH.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B10 Confidential
Deploying the system ‘with’ the use of an Ethernet HUB or Switch

_________________________________________________________________________________________________________________________________
LTGSM User Manual B11 Confidential
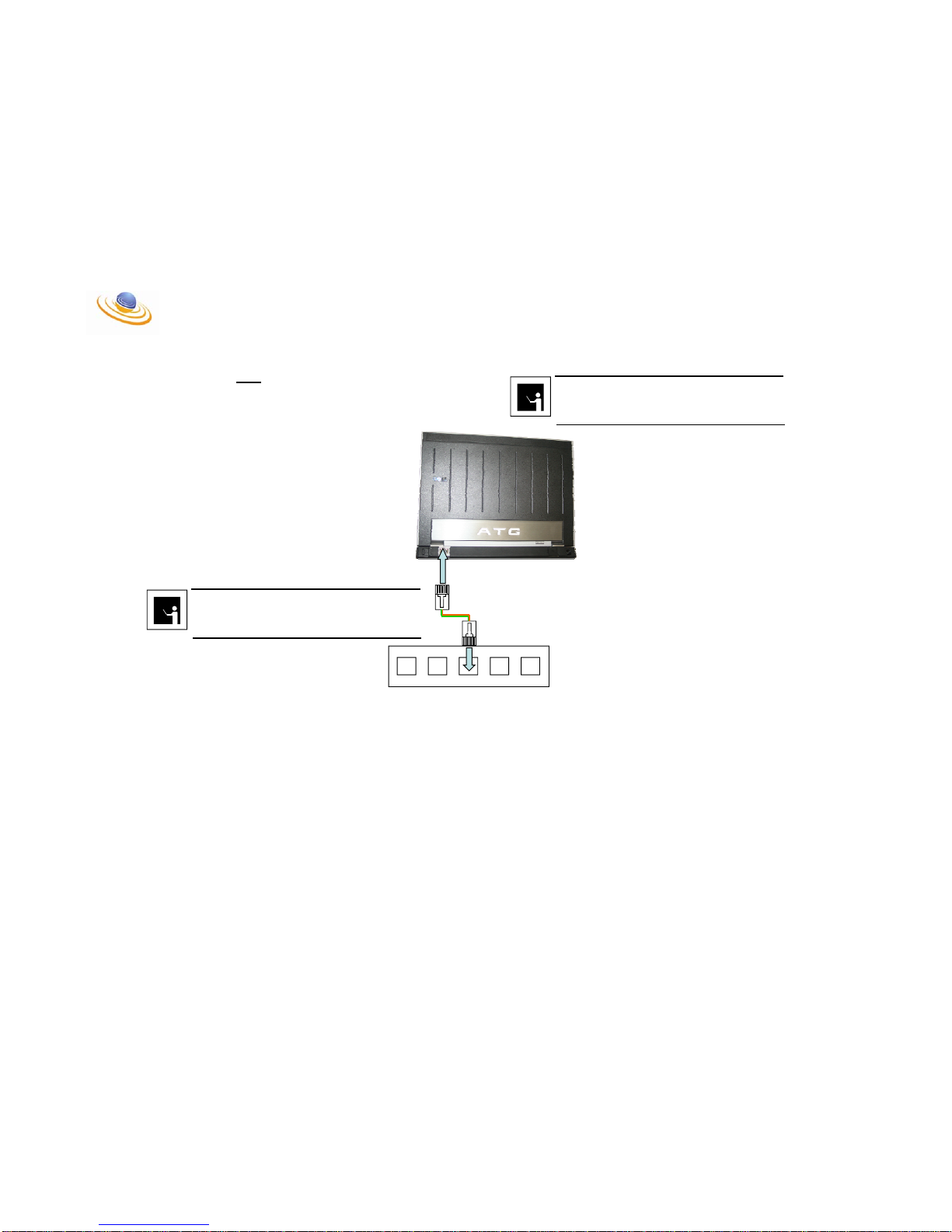
Set-Up With Ethernet HUB or Switch
Step # 1:
Insert Security Dongle into any available USB port.
Security Dongle
_________________________________________________________________________________________________________________________________
LTGSM User Manual B12 Confidential
Set-Up With Ethernet HUB or Switch
Step # 2:
Connect the LAN on the Laptop to any of the LAN ports on the
Ethernet Switch (except port 5).
NOTE
IT IS NOT NECESSARY TO USE CROSSOVER CABLES
WHEN CONNECTING DEVICES THROUGH A HUB OR
SWITCH.
NOTE
PORT 5 ON THE ETHERNET SWITCH IS AN UPLINK PORT.
DO NOT USE THIS PORT UNLESS IT NECESSARY. IF THE
PORT IS USED IT WILL REQUIRE A CROSSOVER CABLE.
1 2 3 4 5
Ethernet Switch

_________________________________________________________________________________________________________________________________
LTGSM User Manual B13 Confidential
1 2 3 4 5
Ethernet Switch
Set-Up With Ethernet HUB or Switch
Step # 3:
Connect any port on the Ethernet Hub (except port 5) to the
LAN port on the BTS Power Block.
AC to DC Power Block
NOTE
IT IS NOT NECESSARY TO USE CROSSOVER CABLES
WHEN CONNECTING DEVICES THROUGH A HUB OR
SWITCH.
!
CAUTION
DO NOT PLUG THE CABLE INTO THE BTS SIDE OF THE BTS
POWER BLOCK. THIS PORT PROVIDES POE (Power Over
Ethernet) [48 VDC] FOR THE BTS. IF THESE PORTS ARE
MISTAKEN THE ETHERNET SWITCH COULD BE
DAMAGED!!!
NOTE
PORT 5 ON THE ETHERNET SWITCH IS AN UPLINK PORT.
DO NOT USE THIS PORT UNLESS IT NECESSARY. IF THE
PORT IS USED IT WILL REQUIRE A CROSSOVER CABLE.
LAN BTS
X

_________________________________________________________________________________________________________________________________
LTGSM User Manual B14 Confidential
Set-Up With Ethernet HUB or Switch
Step # 4:
Connect the BTS port on the BTS Power Block to the Main
Ethernet port on the BTS labeled 48 VDC
AC to DC Power Block
NOTE
IT IS NOT NECESSARY TO USE CROSSOVER CABLES
WHEN CONNECTING DEVICES THROUGH A HUB OR
SWITCH.
NOTE
PORT 5 ON THE ETHERNET SWITCH IS AN UPLINK PORT.
DO NOT USE THIS PORT UNLESS IT NECESSARY. IF THE
PORT IS USED IT WILL REQUIRE A CROSSOVER CABLE.
48 VDC
BTS
1 2 3 4 5
Ethernet Switch

_________________________________________________________________________________________________________________________________
LTGSM User Manual B15 Confidential
1 2 3 4 5
Ethernet Switch
Set-Up With Ethernet HUB or Switch
Step # 5:
Connect the AC Power to both the Laptop and the BTS Power
Block.
AC to DC Power Block
NOTE
PORT 5 ON THE ETHERNET SWITCH IS AN UPLINK PORT.
DO NOT USE THIS PORT UNLESS IT NECESSARY. IF THE
PORT IS USED IT WILL REQUIRE A CROSSOVER CABLE.
48 VDC
To AC Outlet
To AC Outlet
WARNING
ALWAYS USE CAUTION WHEN PLUGGING IN AC
ADAPTER. SERIOUS INJURY OR DEATH COULD BE
CAUSED BY ELECTRIC SHOCK!!!
To AC Outlet

_________________________________________________________________________________________________________________________________
LTGSM User Manual B16 Confidential
Set-Up With Ethernet HUB or Switch
Step # 6:
Press the power button on the front of the MSC.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B17 Confidential
STOP
THIS COMPLETES THE SET-UP WHEN DEPLOYED
WITH AN ETHERNET HUB OR SWITCH.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B18 Confidential
CONNECTING A SECOND BTS

_________________________________________________________________________________________________________________________________
LTGSM User Manual B19 Confidential
1 2 3 4 5
Ethernet Switch
Adding a Second BTS to the Network
To connect a second base station to the Laptop MSC/BSC
simply add the second BTS Power Block and connect the LAN
port from the BTS Power Block to any open LAN ports on the
Ethernet switch. After connecting the Power Block to the
Ethernet switch, connect the BTS port of the BTS Power Block
to the main Ethernet port on the BTS (identified by the 48 VDC
indication above the port).
AC to DC Power Block
NOTE
PORT 5 ON THE ETHERNET SWITCH IS AN UPLINK PORT.
DO NOT USE THIS PORT UNLESS IT NECESSARY. IF THE
PORT IS USED IT WILL REQUIRE A CROSSOVER CABLE.
48 VDC
TO PC
48 VDC
AC to DC Power Block
NOTE
SEVERAL BTSs CAN BE ADDED TO THE LAPTOP
MSC/BSC BY FOLLOWING THESE SAME INSTRUCTIONS.
REMEMBER THE SITES MUST ALSO BE AD DED IN T HE
BSC ADMINISTRATION CONSOLE
!
CAUTION
ENSURE THAT THE BTS SIDE OF THE POWER BLOCK IS
ONLY PLUGGED INTO T HE BT S. THIS PORT PROVIDE S
POE (Power Over Ethernet) [48 VDC] FOR THE BTS. IF
THESE PORTS ARE MISTAKEN THE ETHERNET SWITCH
COULD BE DAMAGED!!!

_________________________________________________________________________________________________________________________________
LTGSM User Manual B20 Confidential
STOP
THIS COMPLETES THE SET-UP FOR CONNECTING
TWO OR MORE BTSs.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B21 Confidential
CONNECTING THE RANGE ENHANCEMENT PACKAGE (REP)

_________________________________________________________________________________________________________________________________
LTGSM User Manual B22 Confidential
Connecting the Range Enhancement Package
Step # 1:
Connect the BTS TX port to the REP TX Input port and then
connect the BTS RX port to the REP RX Input port using the
SMA Male to SMA Male cables provided.
48 VDC
TX
RX

_________________________________________________________________________________________________________________________________
LTGSM User Manual B23 Confidential
Connecti ng the Range Enhancement Package
Step # 2:
Connect the REP Antenna port to an appropriate antenna
using an N Type Male connector on the REP side of the cable.
!
CAUTION
DO NOT POWER ON THE REP WITHOUT AN ANTENNA OR
OTHER APPROPRIATE LOAD ON THE ANTENNA PORT.
RUNNING THE REP WITHOUT A LOAD MAY CAUSE
DAMAGE TO THE INTERNAL POWER AMPLIFIER.
NOTE
ALL CABLES, ANTENNAS AND LOADS SHOULD BE RATED
AT 50 OHMS.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B24 Confidential
Connecti ng the Rang e Enhancement Package
Step # 3:
Connect AC power to the REP.
To AC Outlet

_________________________________________________________________________________________________________________________________
LTGSM User Manual B25 Confidential
Connecting the Range Enhancement Package
Step # 4:
Toggle the power button next to the AC entry point to the on
position.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B26 Confidential
Connecting the Range Enhancement Package
Step # 5:
The blue LED on the from of the REP should illuminate and
the power meter should indicate an estimated power output
level.
NOTE
THE POWER METER IS SIMPLY AN INDICATOR OF OUPUT
POWER AND MAY NOT REFLECT THE ACTUAL RF
OUTPUT.

_________________________________________________________________________________________________________________________________
LTGSM User Manual B27 Confidential
STOP
THIS COM PL E TES THE SET-UP WHEN
CONNECTING THE BTS TO THE REP

_________________________________________________________________________________________________________________________________
LTGSM User Manual B28 Confidential
THIS PAGE INTENTIONALLY LEFT BLANK.

APPENDIX C Configuration Guide
Introduction
This document introduces the Management System of the LTGSM solution and
should initially be read in conjunction with the Quick Start Guide for the LTGSM. The
Quick Start Guide details how to physically connect-up your LTGSM.
This System Administrator User Guide can be used as a training and/or reference
document by anyone who requires access to the Management System in order to
configure, administer, register handsets or support the LTGSM. Typically this is likely
to be a Network Manager, System Administrator, Telecoms Administrator or a
Support member of staff.
Anyone needing to use the LTGSM Management System should refer to the
following section of this document for further information on how to use the LTGSM
interface:
Starting your PMN system configuration
PMX Administrator must first be installed on a server (running IIS) on the PMX system. For
details of how to install PMX Administrator, please refer to the PMX Administrator installation
guide.
Launch PMX Administrator either from the Private Mobile Networks program group on the
start menu of the server where it was installed,
or from a desktop shortcut or browser from any other PC with access to the network.
You will be prompted to enter your user credentials.
Having logged into PMX Administrator, you will be presented with a screen as shown below:
__________________________________________________________________________________
LTGSM User Manual C1 Confidential

For a brand new system, there will be no existing tenancies.
You should first select ‘System Settings’ in order to add a new ‘provider’:
You will be presented with the ‘System Settings’ menu:
__________________________________________________________________________________
LTGSM User Manual C2 Confidential

Provider Configuration
‘Location Area’ coverage is provided by a variety of companies in many countries. The
provider giving coverage within an area is made known to and displayed on the handset.
Each country is assigned a 3-digit identifier code, or codes, and each company auth orized to
give GSM coverage is given a 2-digit identifier code. Therefore, the PMX system allows
‘providers’ to be added so they can be allocated to individual location areas (see section on
location areas).
In most cases PMX systems will use the 2-digit identifier allocated to PMN by Ofcom and this
will be the only provider configured on the system. As shown below, this will normally be set
to code 19 in country 234. In cases where PMN pro vide co verag e on be ha lf of anothe r mobile
operator, the other operator’s code may be entere d. For demonstration equipment, code 01
and country 001 may be used as these are development codes.
Click on the ‘Providers’ icon to be presented with the providers list, then click on ‘Add
Provider’ to enter details of the new provider.
Once added to the system, a provider may be edited but not deleted.
__________________________________________________________________________________
LTGSM User Manual C3 Confidential

MSC Configuration
Creating a Mobile Switching Cen tre (MSC) will set up the top level of your system hierarchy.
Having selected ‘MSCs’ from the ‘System Settings’ menu, you will be presented with the MSC
list:
Select ‘Add MSC’ to add details of the MSC:
Enter details as given on your network diagram and click ‘Accept’.
NOTE : The loop back IP address of 127.0.0.1 should never be used as the MSC will fail to start.
__________________________________________________________________________________
LTGSM User Manual C4 Confidential

BSC Configuration
This will create the second level of the hardware hierarchy.
Select ‘Add BSC’ to configure the BSC:
Enter details as given on your network diagram and click ‘Accept’. Repeat the p rocess as
required to create all BSC’s on the network.
N.B. The configuration of cell groups (and therefore cells) must b e done via th e BSC settin gs.
Please note that, whilst cell groups will be listed under Location Areas, they may only be
configured within the BSC, not the LA.
Cell Group Configuration
This will create the second layer of the virtual hierarchy.
Select the required BSC to edit an d select ‘Add Cell Group’ to cre at e t he cell g roup:
Define a suitable name and choose the required LA from th e list and click ‘Accept’. Repeat
the process as necessary to create all cell groups required on the network.
Reminder: Although cell groups may be viewed from within LA settings, they may only be
configured via the BSC.
___________________________________________________________________________________
LTGSM User Manual C5 Confidential

Cell Configuration
This will create the final layer of the hardware hierarchy.
Select your required cell group to edit and select ‘Add Cell’ to be presented with the ‘Add Cell’
screen:
Enter details as given on your network diagram and click ‘Accept’. (The ‘Cell Number’ can be
obtained from the BSC configuration softwa re). Repeat the process as required to cre ate all
cells in the cell group.
Hardware configuration is now complete and you can move on to the tenancy configuration.
LA Configuration
This will create the first layer within the virtual hierarchy.
Select ‘Add Location Area’ to configure the LA:
Enter details as given on your network diagram along with the appropriate provider and click
‘Accept’. The ‘LA Code’ number can be obtained from the BSC configuration software.
Normally, there will only be one provider given in the drop down list. Repeat process as
required to create all LA’s on the network.
Having now created an MSC, at least one BSC and at least o ne LA, you can n ow create new
cell groups to be assigned to your LA(s) and new cells to be assigned to your cell group(s).
___________________________________________________________________________________
LTGSM User Manual C6 Confidential

PMX Administrator Password Change
For security reasons, you may wish to change your PMX administrator’s password. This can
be done by selecting the password change option from the ‘System Settings’ menu:
From there, you will be prompted to enter the current password, followed by the new
password you wish to use, then to confirm that new password and accept the change.
___________________________________________________________________________________
LTGSM User Manual C7 Confidential

Tenancy Configuration
Having configured the hardware, browse to the ‘Tenanc ies’ scree n by us in g the ‘Tenanc y L ist’
link from any page:
You will be presented with the list of tenancies:
For a brand new system, there will be no existing tenancies.
Select ‘Add Tenancy’ and yo u will be presented with the ‘Add Tenan cy ’ screen:
___________________________________________________________________________________
LTGSM User Manual C8 Confidential

General Tab
Enter a name which will be displayed in the tenancy list and add a description if required.
The length of your PMX extension numbers should be defined from the drop down list.
Location Areas will be listed in ‘Available LAs’ and can be moved into the ‘Selected LAs’ list.
The PMX system may be installed and run in one country but used by people in several
different countries. Therefore, you may set which time zone the tenancy uses so that
information relevant to the tenancy’s local time ma y be used. The local time will relate to the
sending of SMS messages and to call logging / billing.
The ‘Open Timeout’ setting defines the maximum number of minutes you expect users to
remain on a single call. Mobile handsets attempt to re-re gister periodically with their network,
the norm being every 90 minutes. This process cannot take place whils t the handset is on a
call. Therefore, the re-registration may be delayed. The open timeout will cater for this
scenario by keeping the registration alive for the set time if PMX thinks the extension is on a
call. After this time, PMX will deem that the call should have terminated and the extension will
be un-registered from the system. If the call is still in progress, it will be allowed to continue
but PMX will treat the extension as being “off net”.
The ‘Closed Timeout’ setting defines the number of minutes PMX will keep the extension
registered when not on a call. As stated above, the handset should attempt to re-register
periodically. If it fails to do so within the closed timeout period, PMX will deem that the
handset has been switched off, has roamed out of the PMX network range or switched to
another network.
Ranges Tab
From the Tenancy List, select the tenancy you have just created and, in the ‘Tenancy Menu’,
click on the ‘Tenancy Settings’ icon:
This will take you back to the details in order to create a number range:
___________________________________________________________________________________
LTGSM User Manual C9 Confidential

Click ‘Add Range’ in order to create a range of extension numbers to which SIM cards may be
allocated.
Enter the required range then click ‘Accept’ to accept the defined numbers.
Once the Tenancy has at least one number range defined, you can start associating SIM
cards with the telephone network extension numbers within the range(s).
No tenancy may use a numbering range which overlaps with that of another tenancy.
A tenancy may have multiple ranges but they must share a common number length as
defined in the ‘Tenancy Conf iguration’ screen.
Authentication Tab
The required levels of security offered by the PMX system should be determined for the
tenancy. By default, all options are selected.
___________________________________________________________________________________
LTGSM User Manual C10 Confidential

Normal External
When ticked, authentication will be required upon the handset roaming from an ‘external’ cell
(i.e. macro network), to a PMX cell.
Normal Internal
If ticked, authentication will be required when a handset roams from one PMX cell to another.
Attach
When this option is ticked, PMX will attempt to authenticate the SIM when the extension
attempts to register back on the network.
Calls
When selected, this option sets PMX to authenticate the SIM whenever the extension
attempts to make a call.
Periodic
Each mobile handset will attempt to re-register regular intervals – the norm being 90 minutes.
The frequency is set in the IP Access configuration. This setting determines whether or not
PMX attempts to authenticate th e SIM with eac h re- registr a tion . If un - tick ed , the mobile w ill be
allowed to re-register without authenticating again.
Ciphering
Allows the radio traffic between handsets and cells to be scrambled. The encryption
algorithms are set on each cell in th e IP Access configuration.
For further information about authentication, please refer to the authentication settings for
extensions.
Diverts Tab
There may be a requirement to forward / divert calls to other destinations under certain
conditions. For example, you may wish to divert calls to a voicemail sys tem or a switchboard
if an extension is busy. These diverts may either be set at tenancy level, i.e . all extensions
within the tenancy will follow the same diverts (unless overridden by an extension-specific
divert) or on individual extensions. The diver ts tab within the ‘Tenanc y Settings’ will apply the
rules for all extensions within the tenancy.
___________________________________________________________________________________
LTGSM User Manual C11 Confidential

Active?
Against each divert type is a tick box labelled ‘Active?’. Wh en ticked, the divert will become
active and, when un-ticked, the divert destination will remain but the divert will no longer be
active.
All Calls
Otherwise known as an ‘unconditional’ or ‘immedi ate’ divert, the number defined in this field
will be called under all circumstances. Caution should be exercised when activating this
divert, especially at tenancy level, as calls will no longer route to handsets. This divert, once
activated, will take precedence over all other divert types.
Busy
Allows an alternative point of answer to be defined when extens ions are busy on another call
and no second line is enabled on th e extension / handset.
No Answer
Sets an alternative point of answer when calls give no reply with in the ringing duration set in
‘Timeout’.
Timeout
Defines the number of seconds the system will wait for an answer from the extension before
following the ‘No Answer’ divert to the defined number.
Not Reachable
In circumstances where it can no longer be estab lished th at the e xtension is register ed on the
system i.e. the handset is switched off, is no longer within range of an access point or has
roamed to another network, the system will divert calls to the number defined here.
Allow Users to Alter Diverts
The diverts set on this tab may be defined exclusively by the administrator, in which case this
box should remain un-ticked, or you may wish to tick the box in order to allow divert
commands from handsets to up date the divert destination s.
Should you need to remove a tenancy from the system, this can be done by selecting
‘Remove Tenancies’ from the ‘Associated Links’ options in the ‘Tenancy Settings’ section.
___________________________________________________________________________________
LTGSM User Manual C12 Confidential

From the list of Tenancies offered, select those to be deleted by ticking the box for the
tenancy then click ‘Continue’ at the bottom of the screen.
You will be prompted to ‘Accept’ or ‘Cancel’ the deletion. Pleas e exercise caution when using
this facility as tenancy settings cannot be restored once deleted.
___________________________________________________________________________________
LTGSM User Manual C13 Confidential

SIM Card and Extension Number Configuration
There are two different ways to provision a SIM card against a particular extension number.
The method used will depend upon whether or not you know the unique ID (IMSI) of the SIM
card to be provisioned. If the IMSI is known to you, method 1 is the simpler method of
provisioning the SIM card.
Provisioning Method 1
Browse to the ‘Tenancy Menu’ and se le ct ‘Extensions’. This will take you to th e list of
extensions.
Select ‘Add Extension’.
___________________________________________________________________________________
LTGSM User Manual C14 Confidential

General Tab
Enter the IMSI number and give an appropriate description (normally the user’s name). The
extension number to be associated with the IMSI may be manually selected from the
remaining unassigned numbers so th at a specific extension can be used or it may be autoassigned whereby the lowest available number is used.
PMX Administrator gives the opportunity to associate two external numbers with the PMX
extension. The ‘DDI Number’ should normally be a public number which points to the gateway
connected to the PMX system. The ‘External Mobile Netwo rk Number’ should normally be the
mobile number provided by a macro network provider for any SIM c ard already owned by the
user. The user should set a divert on their macro network so that when their phone is not
using that network, calls will be forwarded to PMN via the ‘DDI Number’. By knowing that
these two numbers are associated with the PMX extension, any user on the PMX system
dialling either of those two numbers instead of the internal PMX extension number may be
routed internally within PMX, thus avoiding call charges on the public network. If the user is
not currently on the PMX network, the system can then dial the ‘External Mobile Network
Number’ via the gateway to try to contact the user on the macro networ k. This also app lies to
SMS messages so that, when the mobile is not present on the PMX netw ork, any texts can be
forwarded to the external mobile number.
Select the user class of service from the profile drop down list:
‘Normal Subscriber’ is for users who expect to be registered primarily on the PMX network.
Such users would issue their external landline number to the ir c allers. PMX w ill accept calls in
from this number and route calls to the PMX extension. If the PMX exte nsion is not regis tered
at the time, the call will be routed to the external mobile number.
‘Internal Only’ is intended for users who expect to use their macro network mobile number
most of the time. Such users would issue the ir normal mobile number to callers and forward
calls to the ‘DDI Number’ when not present on the macro network. Their normal mobile
number would be the primary point of contact with calls routed to PMX if not on the macro
network. Calls for these users are then kept ‘internal only’ on the PMX network i.e. PMX will
not dial back out to ‘External Mobile Network Number’ at any point, either for voice calls or
text messages.
‘Emergency Privilege’ – the PMX system or individual tenancies may be switched into
‘emergency mode’ which means that calls on the s ystem are restricted. Whilst in emergency
mode, only those users with emergency privilege are allowed to make calls.
Where you are not using the ‘Auto -assign Number’, the number of extensions listed in the
drop-down may be restricted so that, for example, only the first 10 unassigned extension
numbers are listed. The value is defined in the web.config file found in [x]:\Program
Files\Private Mobile Networks\iMobileNetwork
<!-- The max no of entries in a list box -->
<add key="MaxListCount" value="10" />
___________________________________________________________________________________
LTGSM User Manual C15 Confidential

GPRS Tab
The PMX system can allow GPRS-enabled handsets to access data services. As part of the
provisioning process, the rele vant settings can be configure d o n e a ch individual extension.
Enable GPRS
To allow the extension to access GPRS services this box must be ticked. All other settings
will be disabled until this is enabled.
Enable VPLMN
Allows an IP address assign ed by another network to b e us ed.
Dynamic IP
If ticked, an IP address will automatically assigned to the device. This may change from one
registration to the next. When enabled, the ‘IP Address’ setting which follows will be disabled.
IP Address
Allows a static IP address to be assigned to the extension.
APN
Sets the access point name to be used by the extension. This may be defin ed as a specific
name or, more usually, be set to a value of ‘*’ to allow the device to carry on using their
access point settings for macro network GPRS on the PMX network.
Reliability Class
Sets the required level of reliability when sending & receiving GPRS data. The values
determine whether sent data should be acknow ledged and whether or not the transmission
deals with data loss. There is a trade-off between speed and reliability i.e. the faster the
transmission, the less the qu alit y of the data can be guaranteed.
Delay Class
Sets the level of artificial latency on data transmission. If set to ‘Best Effort’, data will be
transmitted as quickly as current network conditions allow.
Precedence Class
Allows the GPRS data for this extension to be given a lower, eq ual or greater priority than the
data of other users.
___________________________________________________________________________________
LTGSM User Manual C16 Confidential

Peak Throughput
Provides a throttle for the extens ion’s data by setting the fastest rate at which data may be
transmitted (measured in b y tes per second).
Mean Throughput
Set the maximum amount of data which may be transmitted by the extens ion (measured in
bytes per hour). If set to ‘Best Effort’, as much data as cur rent ne twork con ditions a llow will be
transmitted.
Advanced Tab
Authentication Type
Sets the algorithm to be used to decrypt the Ki value e.g. ‘Milenage’ or ‘GSM- A’. Such types
would be used where the Ki’s are held on the PMX system itself. If your system uses SIM’s
issued by PMN, it is likely that the Ki values will not be divulged to you or held on your
system. They will be held centrally by PMN and authentication would take place by means of
‘authentication triplets’ sent via HTTP. Under this authentication method, your PMX system
will request authentication via one of 10 possible HTTP connections whereby a randomly
generated number is run through an algorithm and the resultant response from the SIM
checked against the result given by the central database. If the values are different,
authentication will fail. Where HTTP is used, a Ki value cannot be entered.
Ki
This is a code programmed on the SIM in addition to the IMSI. The Ki can only be determined
by means of an algorithm used during a call. The Ki cannot be determined by a card reader
and ensures that a ghosted SIM is not being used. For 3
supplied by a macro network provider, the Ki will be unknown to PMX and auth entication will
___________________________________________________________________________________
LTGSM User Manual C17 Confidential
rd
party SIM’s such as those already

not be possible. Where the SIM has been supplied by PMN, the Ki will be known and usable
as it is programmed by PMN.
Enable ODB
This sets whether or not Operator-Determined Barring will be used. ODB allows PMX to bar
calls from the extension to certain number types such as international or premium rate
numbers.
Operator-Determined Barring
The value set in this field is a combined value of the various number types that are either
allowed or disallowed. Eac h com bination will give a unique value, which may be entered here.
In most situations, ODB will not be applicable. Barring of calls may be achieved by the PMX
routes or by restrictions on the network beyond the PMX gateway. It may be required where
the PMX system links up with other network providers under roaming arrangements.
Diverts Tab
As described previously in this document, there may be a requirement to forward / divert calls
to other destinations under certain conditions. For example, you may wish to divert calls to a
voicemail system or a switchboard if an extension is busy. These diverts may either be set at
tenancy level, i.e. all extensions within the tenancy will follow the same diverts or they may be
set on individual extensions as described below. Extens ion diverts will take precedence over
tenancy diverts.
Active?
Against each divert type is a tick box labelled ‘Active?’. Wh en ticked, the divert will become
active and, when un-ticked, the divert destination will remain but the divert will no longer be
active.
All Calls
Otherwise known as an ‘unconditional’ or ‘immedi ate’ divert, the number defined in this field
will be called under all circumstances. This divert, once activated, will take precedence over
all other divert types.
Busy
Allows an alternative point of answer to be defined when the e xtension is bus y on an other call
and no second line is enabled on th e extension / handset.
No Answer
Sets an alternative point of answer when calls give no reply with in the ringing duration set in
‘Timeout’.
___________________________________________________________________________________
LTGSM User Manual C18 Confidential

Timeout
Defines the number of seconds the system will wait for an answer from the extension before
following the ‘No Answer’ divert to the defined number.
Not Reachable
In circumstances where it can no longer be estab lished th at the e xtension is register ed on the
system i.e. the handset is switched off, is no longer within range of an access point or has
roamed to another network, the system will divert calls to the number defined he re.
Allow User to Alter Diverts
The diverts set on this tab may be defined exclusively by the administrator, in which case this
box should remain un-ticked, or you may wish to tick the box in order to allow divert
commands from the handset to update the divert destinations.
Provisioning Method 2
Firstly, you must set up at least one ‘device’ which is allowed to extension SIM cards onto the
network. From the tenancy list, select the tenancy by using either the link on the tenancy ID or
name. This will bring you to the ‘T en an c y Menu’:
Click on the ‘Devices’ icon and you will be presented with the list of devices. Select ‘Add
Device’.
Add the IMEI number for the handset you wish to use in orde r to provision your SIM cards.
The IMEI number is the unique device number for that handset and can be obtained by
keying *#06# on the handset itself. A number of 15 or more digits in length will be presented
on screen. Enter this number in the IMEI field and give the handset a me aningful description.
Click ‘Accept’ to save the details.
Having added a device capable of provisioning extens ions, go back to the ‘Tenancy Menu’
and click on the ‘Pending Provisions’ icon.
___________________________________________________________________________________
LTGSM User Manual C19 Confidential

This will bring you to the list of extension waiting to be provisioned onto the system. Select
‘Add Pending Provision’ to be taken to the ‘Add Pending Provision’ screen:
From the device drop-down list, select the device you wish to use, then fill in the rest of the
details as per ‘Provisioning Method 1’. Repeat this pro cess as many times as necessary to
add the extensions required into the pending provisions list.
Once your pending provisions list is complete, place a SIM c ard into the handset and switch
on. If the phone does not automatically find the PMX network, use the handset’s menus
(consult the handset manual for details) to locate the network provider selection feature and
select the network detailed in your network diagram. The SIM card will be provisioned against
the first entry in the ‘Pending Pro v isio ns’ list.
Once provisioned, the SIM card will appear in the extensions list and may be removed from
the provisioning device and used in any mobile handset.
This process should be repeated until all pending provisio ns are completed and shown in the
extensions list. A careful note should be made of whic h order the SIM cards were registered
so that you know which extension number will have been allocated to each card.
Once configured, a provisioning device may be edited or deleted (once th e las t extension d ue
to be provisioned by that device has been successfully added).
Once you have created provisions in this ma nner, you may use the exten sions icon to further
edit the details of the provision and create GPRS, advanced and divert settings.
___________________________________________________________________________________
LTGSM User Manual C20 Confidential

SMS Distribution Lists
As a PMX system administrator, you may create SMS distribution lists in or der to send text
messages simultaneously to multiple recipients.
From the tenancy menu, select ‘Distribution Lists’.
You will be presented with a list of existing Distribution Lists. To create a new list, select ‘Add
Distribution List’.
Give the list a suitable name and add the required PMX extensions by highlighting them in the
‘Available Extensions’ list and clicking the right arrow to move them to the ‘Selected
Extensions’ list. Click ‘Accept’ to save the list.
Once a list has been configured, you may select the ‘Send SMS’ icon in the ‘Tenancy Menu’.
___________________________________________________________________________________
LTGSM User Manual C21 Confidential

Enter a value in the ‘SMS From’ field so recipients of the message will know who the
originator is. Please note that recipients will not be able to reply to messages sent with a
textual value or a number which does not exist. If you do wish recipients to reply to the
message, please ensure that you enter a valid PMX extension or macro network mobile
number.
Enter the text in the ‘Message’ field, up to a maximum of 160 characters.
Select the appropriate distribution list from the drop-down menu and click ‘Send SMS’.
NOTE: It is not possible to add external mobile numbers to distribution lists. Only PMX
extensions may be selected, although if a selected handset is “off net” and is on the ‘Normal
Subscriber’ profile, the system will attempt to deliver messages to the ‘External Mobile
Network Number’ defined against the extension.
___________________________________________________________________________________
LTGSM User Manual C22 Confidential

Gateways
Although a PMX system may act as a completely self-contained network, most will almost
certainly need to receive calls from and ma ke calls to a w ider netwo rk and th e PSTN. In order
to achieve this, the system must have a connection to at le ast one gateway. The gate way will
take the SIP messaging used by PMX and relay it to o ther SIP-enabled devices or convert it
to traditional TDM (Time Division Multiplex) protocols such as DPNSS or DASS. The details
of any gateway can be added using PMX Administrator and routes assigned to determine
which numbers will be placed out via each gateway.
Gateways may be allocated to the system i.e. made available for use by all tenancies , or be
assigned for use by one specific tenancy only.
In order to configure a gateway, browse to ‘System Settin gs’ and follow the ‘Gateways’ link
from the ‘System Settings’ menu.
You will be presented with the list of gateways:
___________________________________________________________________________________
LTGSM User Manual C23 Confidential

Select ‘Add Gateway’ to be pr es ented with the gateway config uration screen:
The ‘Type’ drop down list offers a choice of SIP and SMSC. Choose SIP for voice calls or
SMSC to set the gateway as an SMS Controller. The port number should be set to 5 060 for
SIP and 5080 for SMSC. These defaults may be changed if required.
The tenancy drop-down list offers a choice between ‘System’ and any existing tenancy
names. Select ‘System’ if the gateway is to be used by all ten ancies or the appropriate n ame
if only to be available to one tenancy.
___________________________________________________________________________________
LTGSM User Manual C24 Confidential

If you choose SMSC, you will be presented with a slightly different screen:
On many systems, the fields which are blank in the above screenshot may be left blank as
they will not be required. Only where the SMSC needs to register with a call server will the
SMS Centre Number (normally 8980449), SIP Password, Registrar and Proxy need to be
used in order to register onto the call server.
An IDD field may be seen in some versions of PMX Administrator. Its function is to set the
International Dialling Digits for the country where the gateway is located. For example, to dial
an international number from the UK, a prefix of 00 is required. The IDD will be used to
replace a plus symbol (+) at the front of any dialled numb er. Later versions do not inc lude the
setting as it is automatically handled by the MSC.
The PMX Administrator installation process creates two Microsoft Message Queues:
to_mms is used to deliver text messages to numbers not on PMX.
gsmregistrations is used to store text messages for extensions which are not currently
registered on PMX e.g. when the handset is switched off or out of the PMX coverage area.
When the handset re-registers with PMX, the queue d me ssages are delivered.
These two queues would normally be defined as shown in the scre enshot as these are the
standard naming convention. They may b e altered if requ ired. If the system is s et up to used
private instead of public queues, this screen offers the ability to defined the queue names as
.\private$\to_mms
and
.\private$\gsmregistrations
___________________________________________________________________________________
LTGSM User Manual C25 Confidential

Routes
Having created a gateway, you then need to decide w hich dialled numbers to send to that
gateway. When a SIM card is provisioned, you are asked to ente r an extension number to be
associated with that SIM along with any external number which may also be used in a dual
SIM handset. The purpose of the ‘External Mobile Network Number’ field is twofold. Firstly,
PMX will recognise the number and, if dialled by another extension on the PMX system, calls
can be routed to the associated handset without breaking out to the PSTN, thus saving on call
costs. Secondly, if the associated handset is “off net” we have a secondary means of
attempting to contact the user. In order to dial the number on the PSTN, there must be a
gateway which provides that connection.
To create a route, browse to the ‘Tenancy Menu’ and select ‘Routes’.
You will be presented with the list of routes:
Click on ‘Add Route’.
When creating a route, you will be presented with four main configuration sections. Changes
made in any tab may be saved at any time by clicking ‘Accept’. You will be returned to th e list
of routes. Further changes to routes may b e made by selecting the one you require from the
list.
___________________________________________________________________________________
LTGSM User Manual C26 Confidential

General Tab
Description
Allows a meaningful description for the function of the route to be given.
Emergency Route
If ticked, this box will indicate to the system that this route is to be used for r outin g em ergency
traffic. Every PMX system is pre-configured with a partially-built ‘SOS Route’ as described
earlier in this document so normally there is no need to add further routes for emergency
traffic. In most case, the box will remain un-ticked so that the route will handle ‘ordinary’
traffic.
Transmission Types
Simply tick the box for each type of transmission you wish to send along this route.
Predominantly, ‘Voice call’ will be the preferred option.
Destinations Tab
This allows you to decide where calls following this route will be sent. You may add a single
or multiple gateways (or extensions if required). Where multiple gateways are selected, PMX
will evenly load balance calls between all destinations. It may be appropriate to send calls to
particular numbers out via a certain gateway. For example, if one gateway has a connection
to an LCR (Least Cost Router) d evice, you may wish to send calls to 07 numbers via this
gateway to take advantage of lower ca ll co sts to the PSTN.
Click on the ‘Destinations’ tab to see the list of destinations.
Click on ‘Add Destination’ to sele ct from the list of available gatewa ys / extensions.
___________________________________________________________________________________
LTGSM User Manual C27 Confidential

Patterns Tab
Patterns are the numbers or number prefixes PMX will try to match in order to determine that
this route should be followed. The pattern with the closest match to the dialled number will be
used. Patterns may be built up using wild card characters and numbers in brackets. Some
examples are given below :
01845521000 This being a fully-defined number, PMX will look for an exact match.
07$ Any number beginning 07, regardless of the number of digits following this prefix.
0[12]XXXXXXXXX Any number beginning 01 or 02 followed by 9 digits of any value
(each X represents one digit of any value).
0[7-9]XXXXXXXXX Any number beginning 07, 08 or 09 followed by nine digits of any
value.
90$ Any number beginning 90. You may wish to incl ude patterns which cater for anyone
who puts a standard outside line prefix of 9 on the number. However, it is unlikely that this will
be required as mobile phone users never need to use an outside line prefix in any other
mobile environment.
D Any single character from 0 t o 9 in clu siv e .
N Any single character from 1 t o 9 in clu siv e .
Click on the ‘Patterns’ tab t o se e th e list of patterns.
Click on ‘Add Pattern’ to define the dialled numbers which are to follow this route. Repeat as
required.
___________________________________________________________________________________
LTGSM User Manual C28 Confidential

Translations Tab
Translations are made up of two component parts, each referred to as a ‘transform’. These
are the ‘CLI Transform’ and the ‘Destination Transform’.
Click on the ‘Translations’ tab to see the list of translations.
Click on ‘Add Translation’ to be presented with the ‘General’ tab for the translation where you
may give the translation a meaningful description and state whether the translation is to be
applied as part of an emergency route.
CLI Transforms
When passing out calls to a gateway, it may be necessary to modify the CLI of the calling
extension to a number more appropr iate to the recipient of the ca ll. Ordinarily, calls betw een
PMX extensions would display the extension number. When dialling to a number on the
PSTN, the extension number is not appropriate so the CLI may be modified so that the ‘DDI
Number’ for the calling extension is delivered. The CLI trans form can be given a meaningful
description and an ‘output mask’. The output mask uses the same construction method as
patterns.
To take a practical example, an internal number of 78002 has a DDI of 01845528002
associated with it. The output mask would be 0184552XXXX . The four X’ s tell PMX to ou tput
a CLI of 0184552 followed by the last four digits of the extension number.
Click on the ‘CLI Transforms’ tab so see the list of CLI transforms.
___________________________________________________________________________________
LTGSM User Manual C29 Confidential

Click on ‘Add CLI Transform’ to create a description and output mask:
The output mask may take values from the configured patterns based on two wild card
character types:
X or _ - by entering an X or an underscore, the ou tput mask (as shown in the screenshot
above) will use any literal value and suffix it with digits taken from the pattern. In this example,
a prefix of 0184552 will be used and the last four digits of the output number will be the last
four digits derived from the number on the pattern. So, if the CLI is 78123 the output will be
01845528123.
$ - entering the dollar wild card in the output mask brings the “Truncate Characters” fu nction
into play. Instead of taking the set number of characters fro m the end of the pattern (as in the
example above), truncating the pattern means that a set number of characters from the
beginning of a pattern will be dropped. So, if this transform were to allow patterns of differing
lengths but where the prefix was th e same, the prefix could be removed without the need to
define separate transforms. For example, patterns of 78XXXXXX and 78XXXXXXX may be
allowed on the transform and you wish to output the n umber minus the “ 78” prefix, regar dless
of how many digits follow. Defining an output mask of 0845$ with a value of “2” in Truncate
Characters will cause the “78” to be dropped and the output will be 0845 followed by a 6 or 7digit number.
Entering a dollar in the output mask without a value in ‘Truncate Charac ters’ (or vice versa)
will generate an error message.
N.B. The dollar wild card only has this function in an output mask. On a pattern, the dollar will
still denote any number of characters of any value.
Click ‘Accept’ to save the transform and return to the list of CLI transforms . From the lis t, click
the ‘Configure’ icon to continue entering details.
___________________________________________________________________________________
LTGSM User Manual C30 Confidential

Click the ‘Patterns’ tab to see the list of patterns for the CLI transform.
Click on ‘Add Pattern’ to determine which extension CLI’s need to be modified:
Once configured, the CLI transform must be enabled to take effect:
NOTE : Telecoms regulation s in the c ountr y or countr ies wher e the s ystem is to opera te may res trict the CLI you a re
able to deliver to the PSTN. Only ‘trusted’ E1 or T1 links may be allowed to deliver any chosen CLI.
___________________________________________________________________________________
LTGSM User Manual C31 Confidential

Destination Transform
The purpose of this transform is to modify the dialled number into any alternative form as
required by the gateway. For example, the gateway may be required to dial external numbers
using international number format e.g. 441845528002 when the user has dialled
01845528002. As with the CLI transform, an output mask is req uired. In the example above,
the mask would be 44XXXXXXXXXX (10 X’s) so that the number dialled by the gateway
would be ‘44’ followed by the last 10 digits of the nu mber entered by the ca ller . PMX th erefore
adds ‘44’ and drops the leading zero. Not only is an output mask required but we need to
know when to apply that mask. Therefore, at least one pattern is also required. In th is case,
the pattern applies to the calling extension numbers i.e. when PMX sees a call from
extensions matching the pattern, the destination transform will be applied. Where PMX
extensions are in the range 78000 to 78999, a pattern of 78XXX (3 X’s) could be applied so
that calls from any extension in the 78xxx range would u se th e transform.
Click on the ‘Dest Transforms’ tab to see the list of destination transforms.
Click on ‘Add Destination Transform’ to create a description and output mask (including
‘Truncate Characters’ rule if required):
The output mask may take values from the configured patterns based on two wild card
character types:
X or _ - by entering an X or an underscore, th e output mask (as shown in the screenshot
above) will use any literal value and suffix it with digits taken from the pattern. In this example,
a prefix of “44” will be used and the last ten digits of the output number will be the last ten
digits derived from the number on the pattern. So, if the destination is “01845528100” the
output will be “441845528100”.
$ - entering the dollar wild card in the output mask brings the “Truncate Characters” fu nction
into play. Instead of taking the set number of characters fro m the end of the pattern (as in the
example above), truncating the pattern means that a set number of characters from the
beginning of a pattern will be dropped. So, if this transform were to allow patterns of differing
lengths but where the prefix was th e same, the prefix could be removed without the need to
define separate transforms. For example, patterns of “0XXXXXXXXX” and “0XXXXXXXXXX”
___________________________________________________________________________________
LTGSM User Manual C32 Confidential

may be allowed on the transform and you wish to output “44” plus the dialed number minus
the “0” prefix, regardless of how many digits follow. Defining an output mask of 0$ with a
value of “1” in Truncate Characters will cause the “0” to be dropped and the output will be “44”
followed by a 9 or 10-digit num ber.
Entering a dollar in the output mask without a value in ‘Truncate Charac ters’ (or vice versa)
will generate an error message.
N.B. The dollar wild card only has this function in an output mask. On a pattern, the dollar will
still denote any number of characters of any value.
Click ‘Accept’ to save the transform and return to the list of CLI transforms. From the list, click
the ‘Configure’ icon to continue entering details.
Click the ‘Patterns’ tab to see the list of patterns for the destination transform.
Click on ‘Add Pattern’ to define the dialled numbers which will be transformed:
Once configured, each transform must be enabled for it to take effect.
The route itself must then also be enabled for all its components to come into effect.
___________________________________________________________________________________
LTGSM User Manual C33 Confidential

Tenancy Translations
In addition to the translations applied against a route, PMX allows translations to be configured against
internal numbers. In this case, the destination is assumed be an extension number not a gateway, so no
destination can be specified. A practical example of a tenancy translation is where the gateway presents
calls to PMX with the destination digits in a format not matching the extension number scheme e.g. with a
network node prefix. A translation would be required to remove the prefix from the received digits to match
them to a number in the tenancy’s ranges.
Another example would be where you wish to use a long number for your extensions but allow users to
dial a shortened version of that number for ease of use.
To create a tenancy translation, browse to the ‘Tenancy Menu’ and select ‘Translations’.
You will be presented with the list of translations:
Click on ‘Add Translation’ to create a description and flag as an emergency translation if required:
Click ‘Accept’ to create the translation and drop back to the list of extensions.
Select the translation from the list to continue configuring details.
___________________________________________________________________________________
LTGSM User Manual C34 Confidential

In this example, no CLI transform is required because calls will be routed within PMX. Therefore, the
internal extension number is valid as the CLI to present.
Click on ‘Add Destination Transform’ to add a description and output mask (with a ‘Truncate Characters
rule defined, if required):
Click on ‘Add a Pattern’ to determine which dialled numbers should be modified by the transform:
The transform must then be enabled to take effect:
___________________________________________________________________________________
LTGSM User Manual C35 Confidential

Presence
Each extension will appear in a list of provisioned numbers within the selected tenancy. The list is
accessible via the ‘Tenancy Menu’ by clicking on the ‘Presence’ icon.
You will be presented with the following screen:
The list may be sorted by any of the column headings or may be filtered by searching on the selected
column heading (indicated by two asterisks).
The LA column will show which Location Area the user is currently in.
The first icon
not currently on the network. When on the PMX network, the icon will be green.
The second icon
on the network and therefore not on a call. When the user is on the network but not in call, the icon will be
blue. When on a call, the icon will be pink.
Please note that this screen does not update in real time. To get the most up-to-date view, click the
refresh button.
indicates the extension’s current subscription status. A grey icon means that the user is
indicates the extension’s current call status. A grey icon means that the user is not
___________________________________________________________________________________
LTGSM User Manual C36 Confidential

Appendix D - I/O Connector Pinouts
Ethernet Port
There is one (1) Ethernet port on the Laptop and one on each of the BTSs.
Pin Wire Color Signal
1 White Orange TX+
2 Orange TX3 White Green RX+
4 Blue POE
5 White Blue POE
6 Green RX7 White Brown POE
8 Brown POE
Ethernet Cable Pin Outs “Cross Over Cable”
Below is a pin for an Ethernet cross over cable. No Pin Out is provided for a straight
through cable, because it is simply straight through.
Connector 1 Connector 2
Pin 1
Pin 2
Pin 3
Pin 4
Pin 5
Pin 6
Pin 7
Pin 8
Æ
Æ
Æ
Æ
Æ
Æ
Æ
Æ
Pin 3
Pin 6
Pin 1
Pin 4
Pin 5
Pin 2
Pin 7
Pin 8
______________________________________________________________________________________
LTGSM User Guide D1 Confidential

Appendix E - dBm-to-Watts Conversion Table
dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts
20.0 0.100 25.0 0.316 30.0 1.00 35.0 3.16 40.0 10.00 45.0 31.62 50.0 100.00 55.0 316.23 60.0 1000.00
20.1 0.102 25.1 0.324 30.1 1.02 35.1 3.24 40.1 10.23 45.1 32.36 50.1 102.33 55.1 323.59 60.1 1023.29
20.2 0.105 25.2 0.331 30.2 1.05 35.2 3.31 40.2 10.47 45.2 33.11 50.2 104.71 55.2 331.13 60.2 1047.13
20.3 0.107 25.3 0.339 30.3 1.07 35.3 3.39 40.3 10.72 45.3 33.88 50.3 107.15 55.3 338.84 60.3 1071.52
20.4 0.110 25.4 0.347 30.4 1.10 35.4 3.47 40.4 10.96 45.4 34.67 50.4 109.65 55.4 346.74 60.4 1096.48
20.5 0.112 25.5 0.355 30.5 1.12 35.5 3.55 40.5 11.22 45.5 35.48 50.5 112.20 55.5 354.81 60.5 1122.02
20.6 0.115 25.6 0.363 30.6 1.15 35.6 3.63 40.6 11.48 45.6 36.31 50.6 114.82 55.6 363.08 60.6 1148.15
20.7 0.117 25.7 0.372 30.7 1.17 35.7 3.72 40.7 11.75 45.7 37.15 50.7 117.49 55.7 371.54 60.7 1174.90
20.8 0.120 25.8 0.380 30.8 1.20 35.8 3.80 40.8 12.02 45.8 38.02 50.8 120.23 55.8 380.19 60.8 1202.26
20.9 0.123 25.9 0.389 30.9 1.23 35.9 3.89 40.9 12.30 45.9 38.90 50.9 123.03 55.9 389.05 60.9 1230.27
21.0 0.126 26.0 0.398 31.0 1.26 36.0 3.98 41.0 12.59 46.0 39.81 51.0 125.89 56.0 398.11 61.0 1258.93
21.1 0.129 26.1 0.407 31.1 1.29 36.1 4.07 41.1 12.88 46.1 40.74 51.1 128.82 56.1 407.38 61.1 1288.25
21.2 0.132 26.2 0.417 31.2 1.32 36.2 4.17 41.2 13.18 46.2 41.69 51.2 131.83 56.2 416.87 61.2 1318.26
21.3 0.135 26.3 0.427 31.3 1.35 36.3 4.27 41.3 13.49 46.3 42.66 51.3 134.90 56.3 426.58 61.3 1348.96
21.4 0.138 26.4 0.437 31.4 1.38 36.4 4.37 41.4 13.80 46.4 43.65 51.4 138.04 56.4 436.52 61.4 1380.38
21.5 0.141 26.5 0.447 31.5 1.41 36.5 4.47 41.5 14.13 46.5 44.67 51.5 141.25 56.5 446.68 61.5 1412.54
21.6 0.145 26.6 0.457 31.6 1.45 36.6 4.57 41.6 14.45 46.6 45.71 51.6 144.54 56.6 457.09 61.6 1445.44
21.7 0.148 26.7 0.468 31.7 1.48 36.7 4.68 41.7 14.79 46.7 46.77 51.7 147.91 56.7 467.74 61.7 1479.11
21.8 0.151 26.8 0.479 31.8 1.51 36.8 4.79 41.8 15.14 46.8 47.86 51.8 151.36 56.8 478.63 61.8 1513.56
21.9 0.155 26.9 0.490 31.9 1.55 36.9 4.90 41.9 15.49 46.9 48.98 51.9 154.88 56.9 489.78 61.9 1548.82
22.0 0.158 27.0 0.501 32.0 1.58 37.0 5.01 42.0 15.85 47.0 50.12 52.0 158.49 57.0 501.19 62.0 1584.89
22.1 0.162 27.1 0.513 32.1 1.62 37.1 5.13 42.1 16.22 47.1 51.29 52.1 162.18 57.1 512.86 62.1 1621.81
22.2 0.166 27.2 0.525 32.2 1.66 37.2 5.25 42.2 16.60 47.2 52.48 52.2 165.96 57.2 524.81 62.2 1659.59
22.3 0.170 27.3 0.537 32.3 1.70 37.3 5.37 42.3 16.98 47.3 53.70 52.3 169.82 57.3 537.03 62.3 1698.24
22.4 0.174 27.4 0.550 32.4 1.74 37.4 5.50 42.4 17.38 47.4 54.95 52.4 173.78 57.4 549.54 62.4 1737.80
22.5 0.178 27.5 0.562 32.5 1.78 37.5 5.62 42.5 17.78 47.5 56.23 52.5 177.83 57.5 562.34 62.5 1778.28
22.6 0.182 27.6 0.575 32.6 1.82 37.6 5.75 42.6 18.20 47.6 57.54 52.6 181.97 57.6 575.44 62.6 1819.70
22.7 0.186 27.7 0.589 32.7 1.86 37.7 5.89 42.7 18.62 47.7 58.88 52.7 186.21 57.7 588.84 62.7 1862.09
22.8 0.191 27.8 0.603 32.8 1.91 37.8 6.03 42.8 19.05 47.8 60.26 52.8 190.55 57.8 602.56 62.8 1905.46
22.9 0.195 27.9 0.617 32.9 1.95 37.9 6.17 42.9 19.50 47.9 61.66 52.9 194.98 57.9 616.60 62.9 1949.84
23.0 0.200 28.0 0.631 33.0 2.00 38.0 6.31 43.0 19.95 48.0 63.10 53.0 199.53 58.0 630.96 63.0 1995.26
23.1 0.204 28.1 0.646 33.1 2.04 38.1 6.46 43.1 20.42 48.1 64.57 53.1 204.17 58.1 645.65 63.1 2041.74
23.2 0.209 28.2 0.661 33.2 2.09 38.2 6.61 43.2 20.89 48.2 66.07 53.2 208.93 58.2 660.69 63.2 2089.30
23.3 0.214 28.3 0.676 33.3 2.14 38.3 6.76 43.3 21.38 48.3 67.61 53.3 213.80 58.3 676.08 63.3 2137.96
23.4 0.219 28.4 0.692 33.4 2.19 38.4 6.92 43.4 21.88 48.4 69.18 53.4 218.78 58.4 691.83 63.4 2187.76
23.5 0.224 28.5 0.708 33.5 2.24 38.5 7.08 43.5 22.39 48.5 70.79 53.5 223.87 58.5 707.95 63.5 2238.72
23.6 0.229 28.6 0.724 33.6 2.29 38.6 7.24 43.6 22.91 48.6 72.44 53.6 229.09 58.6 724.44 63.6 2290.87
23.7 0.234 28.7 0.741 33.7 2.34 38.7 7.41 43.7 23.44 48.7 74.13 53.7 234.42 58.7 741.31 63.7 2344.23
23.8 0.240 28.8 0.759 33.8 2.40 38.8 7.59 43.8 23.99 48.8 75.86 53.8 239.88 58.8 758.58 63.8 2398.83
23.9 0.245 28.9 0.776 33.9 2.45 38.9 7.76 43.9 24.55 48.9 77.62 53.9 245.47 58.9 776.25 63.9 2454.71
24.0 0.251 29.0 0.794 34.0 2.51 39.0 7.94 44.0 25.12 49.0 79.43 54.0 251.19 59.0 794.33 64.0 2511.89
______________________________________________________________________________________
LTGSM User Guide E1 Confidential

dBm Watts
24.1 0.257 29.1 0.813 34.1 2.57 39.1 8.13 44.1 25.70 49.1 81.28 54.1 257.04 59.1 812.83 64.1 2570.40
24.2 0.263 29.2 0.832 34.2 2.63 39.2 8.32 44.2 26.30 49.2 83.18 54.2 263.03 59.2 831.76 64.2 2630.27
24.3 0.269 29.3 0.851 34.3 2.69 39.3 8.51 44.3 26.92 49.3 85.11 54.3 269.15 59.3 851.14 64.3 2691.53
24.4 0.275 29.4 0.871 34.4 2.75 39.4 8.71 44.4 27.54 49.4 87.10 54.4 275.42 59.4 870.96 64.4 2754.23
24.5 0.282 29.5 0.891 34.5 2.82 39.5 8.91 44.5 28.18 49.5 89.13 54.5 281.84 59.5 891.25 64.5 2818.38
24.6 0.288 29.6 0.912 34.6 2.88 39.6 9.12 44.6 28.84 49.6 91.20 54.6 288.40 59.6 912.01 64.6 2884.03
24.7 0.295 29.7 0.933 34.7 2.95 39.7 9.33 44.7 29.51 49.7 93.33 54.7 295.12 59.7 933.25 64.7 2951.21
24.8 0.302 29.8 0.955 34.8 3.02 39.8 9.55 44.8 30.20 49.8 95.50 54.8 302.00 59.8 954.99 64.8 3019.95
24.9 0.309 29.9 0.977 34.9 3.09 39.9 9.77 44.9 30.90 49.9 97.72 54.9 309.03 59.9 977.24 64.9 3090.30
dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts dBm Watts
______________________________________________________________________________________
LTGSM User Guide E2 Confidential

Appendix F - ARFCN Frequencies
F-1. GSM-850 ARFCN Frequencies (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
242
243
824.200 869.200
824.400 869.400
824.600 869.600
824.800 869.800
825.000 870.000
825.200 870.200
825.400 870.400
825.600 870.600
825.800 870.800
826.000 871.000
826.200 871.200
826.400 871.400
826.600 871.600
826.800 871.800
827.000 872.000
827.200 872.200
827.400 872.400
827.600 872.600
827.800 872.800
828.000 873.000
828.200 873.200
828.400 873.400
828.600 873.600
828.800 873.800
829.000 874.000
829.200 874.200
829.400 874.400
829.600 874.600
829.800 874.800
830.000 875.000
830.200 875.200
830.400 875.400
830.600 875.600
830.800 875.800
831.000 876.000
831.200 876.200
831.400 876.400
831.600 876.600
847.000 892.000
847.200 892.200
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
246
247
831.800 876.800
832.000 877.000
832.200 877.200
832.400 877.400
832.600 877.600
832.800 877.800
833.000 878.000
833.200 878.200
833.400 878.400
833.600 878.600
833.800 878.800
834.000 879.000
834.200 879.200
834.400 879.400
834.600 879.600
834.800 879.800
835.000 880.000
835.200 880.200
835.400 880.400
835.600 880.600
835.800 880.800
836.000 881.000
836.200 881.200
836.400 881.400
836.600 881.600
836.800 881.800
837.000 882.000
837.200 882.200
837.400 882.400
837.600 882.600
837.800 882.800
838.000 883.000
838.200 883.200
838.400 883.400
838.600 883.600
838.800 883.800
839.000 884.000
839.200 884.200
847.800 892.800
848.000 893.000
204
205
206
207
208
208
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
250
251
839.400 884.400
839.600 884.600
839.800 884.800
840.000 885.000
840.200 885.200
840.400 885.400
840.600 885.600
840.800 885.800
841.000 886.000
841.200 886.200
841.400 886.400
841.600 886.600
841.800 886.800
842.000 887.000
842.200 887.200
842.400 887.400
842.600 887.600
842.800 887.800
843.000 888.000
843.200 888.200
843.400 888.400
843.600 888.600
843.800 888.800
844.000 889.000
844.200 889.200
844.400 889.400
844.600 889.600
844.800 889.800
845.000 890.000
845.200 890.200
845.400 890.400
845.600 890.600
845.800 890.800
846.000 891.000
846.200 891.200
846.400 891.400
846.600 891.600
846.800 891.800
848.600 893.600
848.800 893.800
______________________________________________________________________________________
LTGSM User Guide F1 Confidential

ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
244
245
847.400 892.400
847.600 892.600
248
249
848.200 893.200
848.400 893.400
251
847.000 892.000
--- --- ---
______________________________________________________________________________________
LTGSM User Guide F2 Confidential

F-2. E-GSM-900 ARFCN Frequencies (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
0 890.000 935.000 30 896.000 941.000 60 902.000 947.000
1 890.200 935.200 31 896.200 941.200 61 902.200 947.200
2 890.400 935.400 32 896.400 941.400 62 902.400 947.400
3 890.600 935.600 33 896.600 941.600 63 902.600 947.600
4 890.800 935.800 34 896.800 941.800 64 902.800 947.800
5 891.000 936.000 35 897.000 942.000 65 903.000 948.000
6 891.200 936.200 36 897.200 942.200 66 903.200 948.200
7 891.400 936.400 37 897.400 942.400 67 903.400 948.400
8 891.600 936.600 38 897.600 942.600 68 903.600 948.600
9 891.800 936.800 39 897.800 942.800 69 903.800 948.800
10 892.000 937.000 40 898.000 943.000 70 904.000 949.000
11 892.200 937.200 41 898.200 943.200 71 904.200 949.200
12 892.400 937.400 42 898.400 943.400 72 904.400 949.400
13 892.600 937.600 43 898.600 943.600 73 904.600 949.600
14 892.800 937.800 44 898.800 943.800 74 904.800 949.800
15 893.000 938.000 45 899.000 944.000 75 905.000 950.000
16 893.200 938.200 46 899.200 944.200 76 905.200 950.200
17 893.400 938.400 47 899.400 944.400 77 905.400 950.400
18 893.600 938.600 48 899.600 944.600 78 905.600 950.600
19 893.800 938.800 49 899.800 944.800 79 905.800 950.800
20 894.000 939.000 50 900.000 945.000 80 906.000 951.000
21 894.200 939.200 51 900.200 945.200 81 906.200 951.200
22 894.400 939.400 52 900.400 945.400 82 906.400 951.400
23 894.600 939.600 53 900.600 945.600 83 906.600 951.600
24 894.800 939.800 54 900.800 945.800 84 906.800 951.800
25 895.000 940.000 55 901.000 946.000 85 907.000 952.000
26 895.200 940.200 56 901.200 946.200 86 907.200 952.200
27 895.400 940.400 57 901.400 946.400 87 907.400 952.400
28 895.600 940.600 58 901.600 946.600 88 907.600 952.600
29 895.800 940.800 59 901.800 946.800 89 907.800 952.800
90 908.000 953.000
______________________________________________________________________________________
LTGSM User Guide F3 Confidential

ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
91 908.200 953.200 103 910.600 955.600 115 913.000 958.000
92 908.400 953.400 104 910.800 955.800 116 913.200 958.200
93 908.600 953.600 105 911.000 956.000 117 913.400 958.400
94 908.800 953.800 106 911.200 956.200 118 913.600 958.600
95 909.000 954.000 107 911.400 956.400 119 913.800 958.800
96 909.200 954.200 108 911.600 956.600 120 914.000 959.000
97 909.400 954.400 109 911.800 956.800 121 914.200 959.200
98 909.600 954.600 110 912.000 957.000 122 914.400 959.400
99 909.800 954.800 111 912.200 957.200 123 914.600 959.600
100 910.000 955.000 112 912.400 957.400 124 914.800 959.800
101 910.200 955.200 113 912.600 957.600
102 910.400 955.400 114 912.800 957.800
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
975 880.200 925.200 992 883.600 928.600 1009 887.000 932.000
976 880.400 925.400 993 883.800 928.800 1010 887.200 932.200
977 880.600 925.600 994 884.000 929.000 1011 887.400 932.400
978 880.800 925.800 995 884.200 929.200 1012 887.600 932.600
979 881.000 926.000 996 884.400 929.400 1013 887.800 932.800
980 881.200 926.200 997 884.600 929.600 1014 888.000 933.000
981 881.400 926.400 998 884.800 929.800 1015 888.200 933.200
982 881.600 926.600 999 885.000 930.000 1016 888.400 933.400
983 881.800 926.800 1000 885.200 930.200 1017 888.600 933.600
984 882.000 927.000 1001 885.400 930.400 1018 888.800 933.800
985 882.200 927.200 1002 885.600 930.600 1019 889.000 934.000
986 882.400 927.400 1003 885.800 930.800 1020 889.200 934.200
987 882.600 927.600 1004 886.000 931.000 1021 889.400 934.400
988 882.800 927.800 1005 886.200 931.200 1022 889.600 934.600
989 883.000 928.000 1006 886.400 931.400 1023 889.800 934.800
990 883.200 928.200 1007 886.600 931.600
991 883.400 928.400 1008 886.800 931.800
______________________________________________________________________________________
LTGSM User Guide F4 Confidential

F-3. GSM-1900 ARFCN Frequencies (in MHz)
This subsection includes the following GSM-1900 ARFCN tables:
GSM-1900 A-Band ARFCN - Frequency (in MHz) Table F-1
GSM-1900 B-Band ARFCN - Frequency (in MHz) Table F-2
GSM-1900 C-Band ARFCN - Frequency (in MHz) Table F-3
GSM-1900 D-Band ARFCN - Frequency (in MHz) Table F-4
GSM-1900 E-Band ARFCN - Frequency (in MHz) Table F-5
GSM-1900 F-Band ARFCN - Frequency (in MHz) Table F-6
GSM-1900 A-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
512 1850.2000 1930.2000 537 1855.2000 1935.2000 562 1860.2000 1940.2000
513 1850.4000 1930.4000 538 1855.4000 1935.4000 563 1860.4000 1940.4000
514 1850.6000 1930.6000 539 1855.6000 1935.6000 564 1860.6000 1940.6000
515 1850.8000 1930.8000 540 1855.8000 1935.8000 565 1860.8000 1940.8000
516 1851.0000 1931.0000 541 1856.0000 1936.0000 566 1861.0000 1941.0000
517 1851.2000 1931.2000 542 1856.2000 1936.2000 567 1861.2000 1941.2000
518 1851.4000 1931.4000 543 1856.4000 1936.4000 568 1861.4000 1941.4000
519 1851.6000 1931.6000 544 1856.6000 1936.6000 569 1861.6000 1941.6000
520 1851.8000 1931.8000 545 1856.8000 1936.8000 570 1861.8000 1941.8000
521 1852.0000 1932.0000 546 1857.0000 1937.0000 571 1862.0000 1942.0000
522 1852.2000 1932.2000 547 1857.2000 1937.2000 572 1862.2000 1942.2000
523 1852.4000 1932.4000 548 1857.4000 1937.4000 573 1862.4000 1942.4000
524 1852.6000 1932.6000 549 1857.6000 1937.6000 574 1862.6000 1942.6000
525 1852.8000 1932.8000 550 1857.8000 1937.8000 575 1862.8000 1942.8000
526 1853.0000 1933.0000 551 1858.0000 1938.0000 576 1863.0000 1943.0000
527 1853.2000 1933.2000 552 1858.2000 1938.2000 577 1863.2000 1943.2000
528 1853.4000 1933.4000 553 1858.4000 1938.4000 578 1863.4000 1943.4000
529 1853.6000 1933.6000 554 1858.6000 1938.6000 579 1863.6000 1943.6000
530 1853.8000 1933.8000 555 1858.8000 1938.8000 580 1863.8000 1943.8000
531 1854.0000 1934.0000 556 1859.0000 1939.0000 581 1864.0000 1944.0000
532 1854.2000 1934.2000 557 1859.2000 1939.2000 582 1864.2000 1944.2000
533 1854.4000 1934.4000 558 1859.4000 1939.4000 583 1864.4000 1944.4000
534 1854.6000 1934.6000 559 1859.6000 1939.6000 584 1864.6000 1944.6000
535 1854.8000 1934.8000 560 1859.8000 1939.8000 585 1864.8000 1944.8000
536 1855.0000 1935.0000 561 1860.0000 1940.0000 586 1865.0000 1945.0000
______________________________________________________________________________________
LTGSM User Guide F5 Confidential

GSM-1900 D-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
587 1865.2000 1945.2000 596 1867.0000 1947.0000 605 1868.8000 1948.8000
588 1865.4000 1945.4000 597 1867.2000 1947.2000 606 1869.0000 1949.0000
589 1865.6000 1945.6000 598 1867.4000 1947.4000 607 1869.2000 1949.2000
590 1865.8000 1945.8000 599 1867.6000 1947.6000 608 1869.4000 1949.4000
591 1866.0000 1946.0000 600 1867.8000 1947.8000 609 1869.6000 1949.6000
592 1866.2000 1946.2000 601 1868.0000 1948.0000 610 1869.8000 1949.8000
593 1866.4000 1946.4000 602 1868.2000 1948.2000 611 1870.0000 1950.0000
594 1866.6000 1946.6000 603 1868.4000 1948.4000
595 1866.8000 1946.8000 604 1868.6000 1948.6000
GSM-1900 B-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
612 1870.2000 1950.2000 637 1875.2000 1955.2000 662 1880.2000 1960.2000
613 1870.4000 1950.4000 638 1875.4000 1955.4000 663 1880.4000 1960.4000
614 1870.6000 1950.6000 639 1875.6000 1955.6000 664 1880.6000 1960.6000
615 1870.8000 1950.8000 640 1875.8000 1955.8000 665 1880.8000 1960.8000
616 1871.0000 1951.0000 641 1876.0000 1956.0000 666 1881.0000 1961.0000
617 1871.2000 1951.2000 642 1876.2000 1956.2000 667 1881.2000 1961.2000
618 1871.4000 1951.4000 643 1876.4000 1956.4000 668 1881.4000 1961.4000
619 1871.6000 1951.6000 644 1876.6000 1956.6000 669 1881.6000 1961.6000
620 1871.8000 1951.8000 645 1876.8000 1956.8000 670 1881.8000 1961.8000
621 1872.0000 1952.0000 646 1877.0000 1957.0000 671 1882.0000 1962.0000
622 1872.2000 1952.2000 647 1877.2000 1957.2000 672 1882.2000 1962.2000
623 1872.4000 1952.4000 648 1877.4000 1957.4000 673 1882.4000 1962.4000
624 1872.6000 1952.6000 649 1877.6000 1957.6000 674 1882.6000 1962.6000
625 1872.8000 1952.8000 650 1877.8000 1957.8000 675 1882.8000 1962.8000
626 1873.0000 1953.0000 651 1878.0000 1958.0000 676 1883.0000 1963.0000
627 1873.2000 1953.2000 652 1878.2000 1958.2000 677 1883.2000 1963.2000
628 1873.4000 1953.4000 653 1878.4000 1958.4000 678 1883.4000 1963.4000
629 1873.6000 1953.6000 654 1878.6000 1958.6000 679 1883.6000 1963.6000
630 1873.8000 1953.8000 655 1878.8000 1958.8000 680 1883.8000 1963.8000
631 1874.0000 1954.0000 656 1879.0000 1959.0000 681 1884.0000 1964.0000
632 1874.2000 1954.2000 657 1879.2000 1959.2000 682 1884.2000 1964.2000
633 1874.4000 1954.4000 658 1879.4000 1959.4000 683 1884.4000 1964.4000
634 1874.6000 1954.6000 659 1879.6000 1959.6000 684 1884.6000 1964.6000
635 1874.8000 1954.8000 660 1879.8000 1959.8000 685 1884.8000 1964.8000
636 1875.0000 1955.0000 661 1880.0000 1960.0000 686 1885.0000 1965.0000
______________________________________________________________________________________
LTGSM User Guide F6 Confidential

GSM-1900 E-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
687 1885.2000 1965.2000 696 1887.0000 1967.0000 705 1888.8000 1968.8000
688 1885.4000 1965.4000 697 1887.2000 1967.2000 706 1889.0000 1969.0000
689 1885.6000 1965.6000 698 1887.4000 1967.4000 707 1889.2000 1969.2000
690 1885.8000 1965.8000 699 1887.6000 1967.6000 708 1889.4000 1969.4000
691 1886.0000 1966.0000 700 1887.8000 1967.8000 709 1889.6000 1969.6000
692 1886.2000 1966.2000 701 1888.0000 1968.0000 710 1889.8000 1969.8000
693 1886.4000 1966.4000 702 1888.2000 1968.2000 711 1890.0000 1970.0000
694 1886.6000 1966.6000 703 1888.4000 1968.4000
695 1886.8000 1966.8000 704 1888.6000 1968.6000
GSM-1900 F-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
712 1890.2000 1970.2000 721 1892.0000 1972.0000 730 1893.8000 1973.8000
713 1890.4000 1970.4000 722 1892.2000 1972.2000 731 1894.0000 1974.0000
714 1890.6000 1970.6000 723 1892.4000 1972.4000 732 1894.2000 1974.2000
715 1890.8000 1970.8000 724 1892.6000 1972.6000 733 1894.4000 1974.4000
716 1891.0000 1971.0000 725 1892.8000 1972.8000 734 1894.6000 1974.6000
717 1891.2000 1971.2000 726 1893.0000 1973.0000 735 1894.8000 1974.8000
718 1891.4000 1971.4000 727 1893.2000 1973.2000 736 1895.0000 1975.0000
719 1891.6000 1971.6000 728 1893.4000 1973.4000
720 1891.8000 1971.8000 729 1893.6000 1973.6000
GSM-1900 C-Band ARFCN - Frequency (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
737 1895.2000 1975.2000 762 1900.2000 1980.2000 787 1905.2000 1985.2000
738 1895.4000 1975.4000 763 1900.4000 1980.4000 788 1905.4000 1985.4000
739 1895.6000 1975.6000 764 1900.6000 1980.6000 789 1905.6000 1985.6000
740 1895.8000 1975.8000 765 1900.8000 1980.8000 790 1905.8000 1985.8000
741 1896.0000 1976.0000 766 1901.0000 1981.0000 791 1906.0000 1986.0000
742 1896.2000 1976.2000 767 1901.2000 1981.2000 792 1906.2000 1986.2000
743 1896.4000 1976.4000 768 1901.4000 1981.4000 793 1906.4000 1986.4000
744 1896.6000 1976.6000 769 1901.6000 1981.6000 794 1906.6000 1986.6000
745 1896.8000 1976.8000 770 1901.8000 1981.8000 795 1906.8000 1986.8000
746 1897.0000 1977.0000 771 1902.0000 1982.0000 796 1907.0000 1987.0000
747 1897.2000 1977.2000 772 1902.2000 1982.2000 797 1907.2000 1987.2000
748 1897.4000 1977.4000 773 1902.4000 1982.4000 798 1907.4000 1987.4000
749 1897.6000 1977.6000 774 1902.6000 1982.6000 799 1907.6000 1987.6000
750 1897.8000 1977.8000 775 1902.8000 1982.8000 800 1907.8000 1987.8000
751 1898.0000 1978.0000 776 1903.0000 1983.0000 801 1908.0000 1988.0000
752 1898.2000 1978.2000 777 1903.2000 1983.2000 802 1908.2000 1988.2000
753 1898.4000 1978.4000 778 1903.4000 1983.4000 803 1908.4000 1988.4000
______________________________________________________________________________________
LTGSM User Guide F7 Confidential

ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
754 1898.6000 1978.6000 779 1903.6000 1983.6000 804 1908.6000 1988.6000
755 1898.8000 1978.8000 780 1903.8000 1983.8000 805 1908.8000 1988.8000
756 1899.0000 1979.0000 781 1904.0000 1984.0000 806 1909.0000 1989.0000
757 1899.2000 1979.2000 782 1904.2000 1984.2000 807 1909.2000 1989.2000
758 1899.4000 1979.4000 783 1904.4000 1984.4000 808 1909.4000 1989.4000
759 1899.6000 1979.6000 784 1904.6000 1984.6000 809 1909.6000 1989.6000
760 1899.8000 1979.8000 785 1904.8000 1984.8000 810 1909.8000 1989.8000
761 1900.0000 1980.0000 786 1905.0000 1985.0000
______________________________________________________________________________________
LTGSM User Guide F8 Confidential

F-4. GSM-1800 ARFCN Frequencies (in MHz)
ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
512 1710.200 1805.200 552 1718.200 1813.200 592 1726.200 1821.200
513 1710.400 1805.400 553 1718.400 1813.400 593 1726.400 1821.400
514 1710.600 1805.600 554 1718.600 1813.600 594 1726.600 1821.600
515 1710.800 1805.800 555 1718.800 1813.800 595 1726.800 1821.800
516 1711.000 1806.000 556 1719.000 1814.000 596 1727.000 1822.000
517 1711.200 1806.200 557 1719.200 1814.200 597 1727.200 1822.200
518 1711.400 1806.400 558 1719.400 1814.400 598 1727.400 1822.400
519 1711.600 1806.600 559 1719.600 1814.600 599 1727.600 1822.600
520 1711.800 1806.800 560 1719.800 1814.800 600 1727.800 1822.800
521 1712.000 1807.000 561 1720.000 1815.000 601 1728.000 1823.000
522 1712.200 1807.200 562 1720.200 1815.200 602 1728.200 1823.200
523 1712.400 1807.400 563 1720.400 1815.400 603 1728.400 1823.400
524 1712.600 1807.600 564 1720.600 1815.600 604 1728.600 1823.600
525 1712.800 1807.800 565 1720.800 1815.800 605 1728.800 1823.800
526 1713.000 1808.000 566 1721.000 1816.000 606 1729.000 1824.000
527 1713.200 1808.200 567 1721.200 1816.200 607 1729.200 1824.200
528 1713.400 1808.400 568 1721.400 1816.400 608 1729.400 1824.400
529 1713.600 1808.600 569 1721.600 1816.600 609 1729.600 1824.600
530 1713.800 1808.800 570 1721.800 1816.800 610 1729.800 1824.800
531 1714.000 1809.000 571 1722.000 1817.000 611 1730.000 1825.000
532 1714.200 1809.200 572 1722.200 1817.200 612 1730.200 1825.200
533 1714.400 1809.400 573 1722.400 1817.400 613 1730.400 1825.400
534 1714.600 1809.600 574 1722.600 1817.600 614 1730.600 1825.600
535 1714.800 1809.800 575 1722.800 1817.800 615 1730.800 1825.800
536 1715.000 1810.000 576 1723.000 1818.000 616 1731.000 1826.000
537 1715.200 1810.200 577 1723.200 1818.200 617 1731.200 1826.200
538 1715.400 1810.400 578 1723.400 1818.400 618 1731.400 1826.400
539 1715.600 1810.600 579 1723.600 1818.600 619 1731.600 1826.600
540 1715.800 1810.800 580 1723.800 1818.800 620 1731.800 1826.800
541 1716.000 1811.000 581 1724.000 1819.000 621 1732.000 1827.000
542 1716.200 1811.200 582 1724.200 1819.200 622 1732.200 1827.200
543 1716.400 1811.400 583 1724.400 1819.400 623 1732.400 1827.400
544 1716.600 1811.600 584 1724.600 1819.600 624 1732.600 1827.600
545 1716.800 1811.800 585 1724.800 1819.800 625 1732.800 1827.800
546 1717.000 1812.000 586 1725.000 1820.000 626 1733.000 1828.000
547 1717.200 1812.200 587 1725.200 1820.200 627 1733.200 1828.200
548 1717.400 1812.400 588 1725.400 1820.400 628 1733.400 1828.400
549 1717.600 1812.600 589 1725.600 1820.600 629 1733.600 1828.600
550 1717.800 1812.800 590 1725.800 1820.800 630 1733.800 1828.800
551 1718.000 1813.000 591 1726.000 1821.000 631 1734.000 1829.000
______________________________________________________________________________________
LTGSM User Guide F9 Confidential

ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
632 1734.200 1829.200 675 1742.800 1837.800 718 1751.400 1846.400
633 1734.400 1829.400 676 1743.000 1838.000 719 1751.600 1846.600
634 1734.600 1829.600 677 1743.200 1838.200 720 1751.800 1846.800
635 1734.800 1829.800 678 1743.400 1838.400 721 1752.000 1847.000
636 1735.000 1830.000 679 1743.600 1838.600 722 1752.200 1847.200
637 1735.200 1830.200 680 1743.800 1838.800 723 1752.400 1847.400
638 1735.400 1830.400 681 1744.000 1839.000 724 1752.600 1847.600
639 1735.600 1830.600 682 1744.200 1839.200 725 1752.800 1847.800
640 1735.800 1830.800 683 1744.400 1839.400 726 1753.000 1848.000
641 1736.000 1831.000 684 1744.600 1839.600 727 1753.200 1848.200
642 1736.200 1831.200 685 1744.800 1839.800 728 1753.400 1848.400
643 1736.400 1831.400 686 1745.000 1840.000 729 1753.600 1848.600
644 1736.600 1831.600 687 1745.200 1840.200 730 1753.800 1848.800
645 1736.800 1831.800 688 1745.400 1840.400 731 1754.000 1849.000
646 1737.000 1832.000 689 1745.600 1840.600 732 1754.200 1849.200
647 1737.200 1832.200 690 1745.800 1840.800 733 1754.400 1849.400
648 1737.400 1832.400 691 1746.000 1841.000 734 1754.600 1849.600
649 1737.600 1832.600 692 1746.200 1841.200 735 1754.800 1849.800
650 1737.800 1832.800 693 1746.400 1841.400 736 1755.000 1850.000
651 1738.000 1833.000 694 1746.600 1841.600 737 1755.200 1850.200
652 1738.200 1833.200 695 1746.800 1841.800 738 1755.400 1850.400
653 1738.400 1833.400 696 1747.000 1842.000 739 1755.600 1850.600
654 1738.600 1833.600 697 1747.200 1842.200 740 1755.800 1850.800
655 1738.800 1833.800 698 1747.400 1842.400 741 1756.000 1851.000
656 1739.000 1834.000 699 1747.600 1842.600 742 1756.200 1851.200
657 1739.200 1834.200 700 1747.800 1842.800 743 1756.400 1851.400
658 1739.400 1834.400 701 1748.000 1843.000 744 1756.600 1851.600
659 1739.600 1834.600 702 1748.200 1843.200 745 1756.800 1851.800
660 1739.800 1834.800 703 1748.400 1843.400 746 1757.000 1852.000
661 1740.000 1835.000 704 1748.600 1843.600 747 1757.200 1852.200
662 1740.200 1835.200 705 1748.800 1843.800 748 1757.400 1852.400
663 1740.400 1835.400 706 1749.000 1844.000 749 1757.600 1852.600
664 1740.600 1835.600 707 1749.200 1844.200 750 1757.800 1852.800
665 1740.800 1835.800 708 1749.400 1844.400 751 1758.000 1853.000
666 1741.000 1836.000 709 1749.600 1844.600 752 1758.200 1853.200
667 1741.200 1836.200 710 1749.800 1844.800 753 1758.400 1853.400
668 1741.400 1836.400 711 1750.000 1845.000 754 1758.600 1853.600
669 1741.600 1836.600 712 1750.200 1845.200 755 1758.800 1853.800
670 1741.800 1836.800 713 1750.400 1845.400 756 1759.000 1854.000
671 1742.000 1837.000 714 1750.600 1845.600 757 1759.200 1854.200
672 1742.200 1837.200 715 1750.800 1845.800 758 1759.400 1854.400
673 1742.400 1837.400 716 1751.000 1846.000 759 1759.600 1854.600
674 1742.600 1837.600 717 1751.200 1846.200 760 1759.800 1854.800
______________________________________________________________________________________
LTGSM User Guide F10 Confidential

ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK ARFCN UPLINK DOWNLINK
761 1760.000 1855.000 802 1768.200 1863.200 844 1776.600 1871.600
762 1760.200 1855.200 803 1768.400 1863.400 845 1776.800 1871.800
763 1760.400 1855.400 804 1768.600 1863.600 846 1777.000 1872.000
764 1760.600 1855.600 805 1768.800 1863.800 847 1777.200 1872.200
765 1760.800 1855.800 806 1769.000 1864.000 848 1777.400 1872.400
766 1761.000 1856.000 807 1769.200 1864.200 849 1777.600 1872.600
767 1761.200 1856.200 808 1769.400 1864.400 850 1777.800 1872.800
768 1761.400 1856.400 809 1769.600 1864.600 851 1778.000 1873.000
769 1761.600 1856.600 810 1769.800 1864.800 852 1778.200 1873.200
770 1761.800 1856.800 811 1770.000 1865.000 853 1778.400 1873.400
771 1762.000 1857.000 812 1770.200 1865.200 854 1778.600 1873.600
772 1762.200 1857.200 813 1770.400 1865.400 855 1778.800 1873.800
773 1762.400 1857.400 814 1770.600 1865.600 856 1779.000 1874.000
774 1762.600 1857.600 815 1770.800 1865.800 857 1779.200 1874.200
775 1762.800 1857.800 816 1771.000 1866.000 858 1779.400 1874.400
776 1763.000 1858.000 817 1771.200 1866.200 859 1779.600 1874.600
777 1763.200 1858.200 818 1771.400 1866.400 860 1779.800 1874.800
778 1763.400 1858.400 819 1771.600 1866.600 861 1780.000 1875.000
779 1763.600 1858.600 820 1771.800 1866.800 862 1780.200 1875.200
780 1763.800 1858.800 821 1772.000 1867.000 863 1780.400 1875.400
781 1764.000 1859.000 822 1772.200 1867.200 864 1780.600 1875.600
782 1764.200 1859.200 823 1772.400 1867.400 865 1780.800 1875.800
783 1764.400 1859.400 824 1772.600 1867.600 866 1781.000 1876.000
784 1764.600 1859.600 825 1772.800 1867.800 867 1781.200 1876.200
785 1764.800 1859.800 826 1773.000 1868.000 868 1781.400 1876.400
786 1765.000 1860.000 827 1773.200 1868.200 869 1781.600 1876.600
787 1765.200 1860.200 828 1773.400 1868.400 870 1781.800 1876.800
788 1765.400 1860.400 829 1773.600 1868.600 871 1782.000 1877.000
789 1765.600 1860.600 830 1773.800 1868.800 872 1782.200 1877.200
790 1765.800 1860.800 831 1774.000 1869.000 873 1782.400 1877.400
791 1766.000 1861.000 832 1774.200 1869.200 874 1782.600 1877.600
792 1766.200 1861.200 833 1774.400 1869.400 875 1782.800 1877.800
793 1766.400 1861.400 834 1774.600 1869.600 876 1783.000 1878.000
794 1766.600 1861.600 835 1774.800 1869.800 877 1783.200 1878.200
795 1766.800 1861.800 836 1775.000 1870.000 878 1783.400 1878.400
796 1767.000 1862.000 837 1775.200 1870.200 879 1783.600 1878.600
797 1767.200 1862.200 838 1775.400 1870.400 880 1783.800 1878.800
798 1767.400 1862.400 839 1775.600 1871.600 881 1784.000 1879.000
799 1767.600 1862.600 840 1775.800 1871.800 882 1784.200 1879.200
800 1767.800 1862.800 841 1776.000 1871.000 883 1784.400 1879.400
801 1768.000 1863.000 842 1776.200 1871.200 884 1784.600 1879.600
843 1776.400 1871.400 885 1784.800 1879.800
______________________________________________________________________________________
LTGSM User Guide F11 Confidential

NOTES:
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
_______________________________________________________
______________________________________________________________________________________
LTGSM User Guide NOTES Confidential
 Loading...
Loading...