Time domain Ultra wideband User Manual
Draft
October 23, 2014
TIME DOMAIN
®
Cummings Research Park
4955 Corporate Drive Suite 101
Huntsville, AL 35805 USA
http://www.timedomain.com
Tel: +1 256.922.9229
+1 888.826.8378
Fax: +1.256.922.0387
User’s Manual
Ultra wideband
Perimeter Surveillance Pole

2 Ultra Wideband Perimeter Surveillance Pole / User’s Manual
Copyright
All rights reserved. Time Domain
®
2001-2014. All rights reserved.
Trademarks
Time Domain®, PulsON®, and “PulsON Triangle” logo are registered trademarks of Time Domain. Microsoft® and
Windows XP®, Windows Vista®, and Windows 7® are registered trademarks of Microsoft Corporation. Any trademarks,
trade names, service marks or service names owned or registered by any other company and used in this manual are the
property of its respective company.
Rights
Rights to use this documentation are set forth in the PulsON Products Terms and Conditions of Sale.
Notice to Users
Operation of this device is restricted to law enforcement, fire and rescue officials, public
utilities, and industrial entities. Operation by any other part is a violation of 47 U.S.C 301
and could subject the operator to serious legal penalties.
Per Title 47, Part 15, Subpart F, paragraph 15.511(2), the operation of imaging systems
requires coordination as detailed in paragraph 15.525.
Parties operating under the provisions of Title 47, Part 15, Subpart F, paragraph 15.511 must
be eligible for licensing under the provisions of part 90.
Changes or modifications not expressly approved by the manufacturer could void the user’s
authority to operate the equipment
Time Domain as manufacturer is in charge of all marketing. Any purchasers (nongovernment) by commercial clients will be informed of their responsibility under FCC rules
by receiving a copy of Section 15.525 which requires them to co-ordinate their activities and
inform the FCC at the following address preferable via certified mail.
Frequency Coordination Branch, OET
Federal Communications Commission
445 12th Street, SW
Washington, D.C. 20554
Attn: UWB Coordination

Ultra Wideband Perimeter Surveillance Pole / User’s Manual 3
Overview
This document is a User’s Manual for the Time Domain Ultra Wideband (UWB) Perimeter
Surveillance Pole (PSP400). The document is divided into the following sections.
Section 1 System Introduction & Theory of Operation
Section 2 Pole Overview
Section 3 P400 Radar
Section 4 Broadspec Antenna
Section 5 FCC Compliance
The user will note we have not included a Section on installation and system bringup. After
reviewing Section 1 the reader will appreciate that the PSP400 is one element of an overall
system that will be integrated with existing elements of an installations fixed infrastructure.
For this reason each installation is unique; system turn-on and setup instructions will be
developed in conjunction the receiving facility.
1 System Introduction & Theory of Operation
This document addresses the Ultra Wideband (UWB) surveillance radar pole which is the
sensor component of an integrated surveillance system. In order to introduce and provide
operational context for the pole the overall system is discussed in this Section.
1.1 System Overview
The UWB Surveillance System (USS) creates a virtual fence along or around the perimeter
of an area to be protected. It consists of a staggered fence line of distributed short range
radars contained in poles. These poles work together to detect, track, and distinguish
between people and animals moving along or through the perimeter area. The ability to
distinguish between different types of targets also known as Items Of Interest (IOIs) is often
referred to as classification. Because the USS does not create a physical barrier it can be
deployed in areas where an actual fence would be detrimental to the environment such as
along a shore line or across a wildlife migratory path.
UWB is the enabling technology that allows the USSUSS to offer the following capabilities:
All weather, day/night operation
High Probability of Detection coupled with a Low Probability of False Alarms
Deployment in cluttered RF environments (near fences, buildings, moderate foliage)
Classification/Identification
Numerous agencies eligible for licensing under the provisions of part 90 have identified an
unmet need for a security system with the above characteristics.
4 Ultra Wideband Perimeter Surveillance Pole / User’s Manual
USS
• Array
• Network
• Server
Tracks/Classifications/Notifications
Pole
Array
Server
Ethernet
Hub
Radar (3)
AC/DC
Converter
Terminal
Keyboard
Monitor
RAID
Storage
Software
Ethernet Hubs
CAT-5e/CAT-6 Cables
Power
Cables
Software
Pole
Ethernet
Hub
Radar (3)
AC/DC
Converter
Software
Pole
Ethernet
Hub
Radar (3)
AC/DC
Converter
Software
…
Network
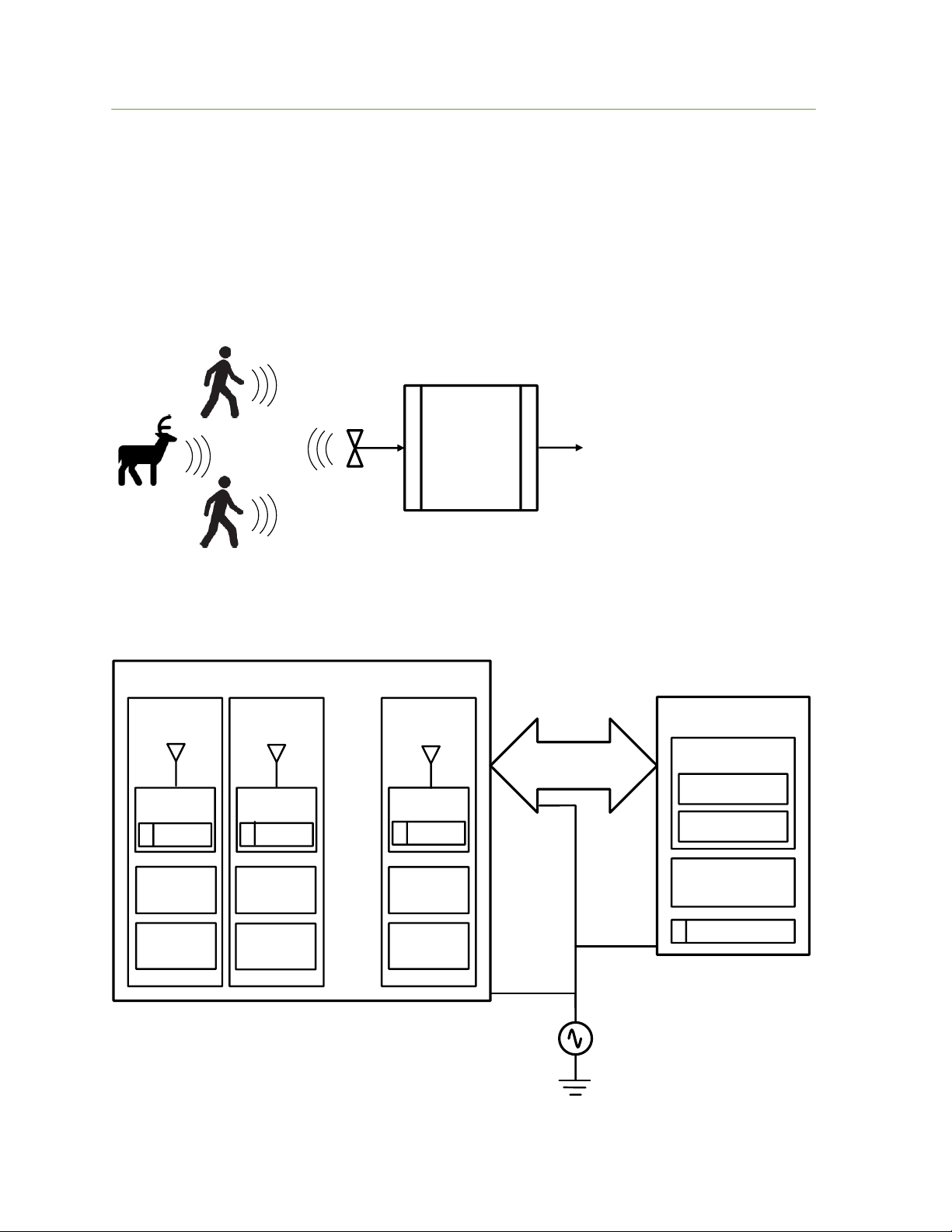
Figure 1 is a conceptual depiction of the USS. As suggested in the figure the USS can track
and independently classify multiple people and animals using its system of radars. A server
processes data from the radars and provides outputs to external users of the data. A network
connects the radars to each other and the server. The lower level components that make up
the poles, server, and network and the USS interfaces will be described in subsequent
paragraphs.
USS requires supporting infrastructure including power, a wired network, pole footings, and
a central server. The cost of this infrastructure suggests USS will be deployed around high
value assets or infrastructure typically found at many Government installations.
Figure 1 USS System Concept
As illustrated in Figure 2 USS consists of a staggered line of poles, a wired network and a
server. The server processes data from the poles and controls radar operation through the
network.
Figure 2 USS Hardware Components

Ultra Wideband Perimeter Surveillance Pole / User’s Manual 5
100 meters
20 meters
20 meter grid
Pole location
The number of poles deployed at a given site depends on the length of the perimeter that
requires monitoring. The poles are organized into groups of six poles referrred to as
networking cells. As shown in Figure 3 the physical footprint of a networking cell is a
rectangle that is 100 meters long by 20 meters wide (note the radar coverage area extends up
to 20 meters beyond the cells footprint in all directions).
As described in Section 1.2.2 a key feature of the networking cell concept is that only a
single UWB radar (P400) within each cell is transmitting at any given time while the other
radars within the same networking cell attempt to receive that transmission thus making very
efficient use of the transmitted energy (air time). This has the benefit of reducing emissions
from the overall system (1 transmitter within the space of a football field) thus reducing (and
pratically speaking, eliminating) the system’s interference potential.
Figure 3: Footprint of six pole networking cell

6 Ultra Wideband Perimeter Surveillance Pole / User’s Manual
The end user provided server should feature multicore processors and an operator terminal
consisting of a keyboard and monitor. Such a server is needed to support the system’s
processing and interface operations. The operator terminal is for the purpose of configuring,
controlling, and maintaining the system. Figure 4 illustrates a typical server.
Figure 4: Typical end user provided server
The network consists of a number of Ethernet hubs and cables to provide data
communication between the UWB Modules within the poles and the server.
1.2 System Theory of Operation
1.2.1 Software Architecture & Data Flow
Figure 5 shows the data flow on the network between the poles and the server, internal to the
server, and external to the server. The P400s send TCP/IP packets containing radar scan data
to the server where they are processed to detect, track, and classify targets. The server also
sends TCP/IP packets to the poles as needed. Within the server, the outputs of the processing
are TCP/IP packets containing tracks, classifications, configuration, status, notifications, and
alarms. These are provided to the interface, which generates data and signals for
consumption by an external user of the data. The TCP/IP packets allow this data to be
processed or converted by another application, even one running at a separate location,
without the need to modify the processing application itself.
 Loading...
Loading...