Page 1

TELNET Command Line Interface
Quick Reference Syntax 1.0.10
1
Page 2
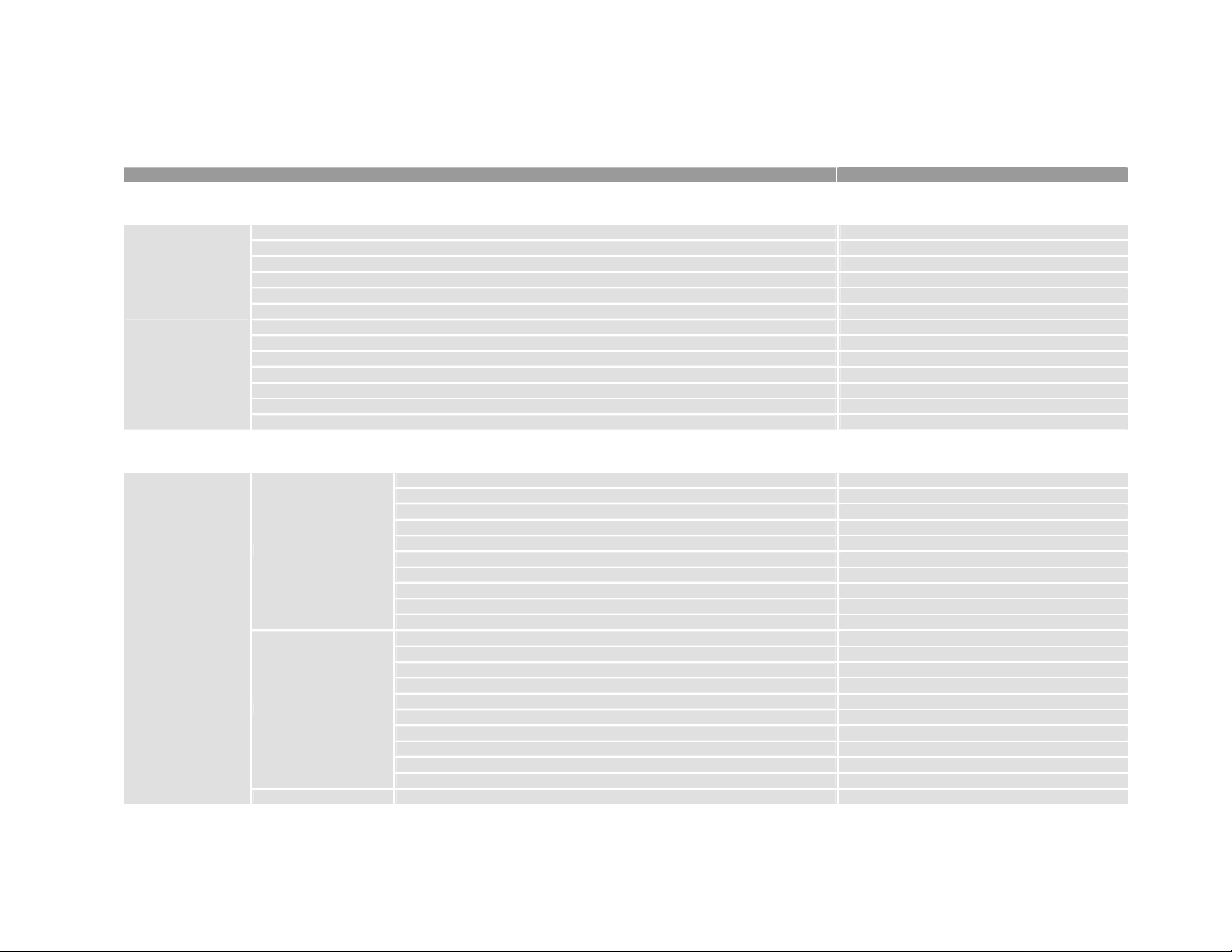
SYSTEM part level II
information <CR>
op_mode <Router|Bridging|Host>
hostname [name]
domain_name [domain]
group_name <name>
system
time_zone <0~62>
use_time_server <Disable|Enable> [time]
update_interval <1~72>
daylight_save <Disable|Enable>
time_server <ip> [ip] [ip]
adsl_mode <Auto|T1.413Full|T1.413Lite|G.DMT|G.Lite|ADSL2|ADSL2PLUS>
clone_mac <Default|PC's|mac>
response_mode <Normal|Brief>
INTERFACE part level II
interface
lan <1~4>
wireless <1~1>
atm <1~8>
Command syntax
address <ip> <netmask>
link_type <Disable|Ethernet>
nat_type <Public|Private>
bridge <Disable|Enable>
access-list <0~4> <0~4>
device-filter <0~4> <0~4>
access_ctrl <Disable|Enable>
inspect-rule <0~4> <0~4>
network_secure <Untrust|Trust>
vlan <0~4>
address <ip> <netmask>
link_type <Disable|Ethernet>
nat_type <Public|Private>
bridge <Disable|Enable>
access-list <0~4> <0~4>
device-filter <0~4> <0~4>
access_ctrl <Disable|Enable>
inspect-rule <0~4> <0~4>
network_secure <Untrust|Trust>
vlan <0~4>
address <ip> <netmask>
Short Description
Show system hardware information
Kernel operation mode
Config local hostname
Config local domain name
Config group name for NetBIOS resource share
Time zone ID
Using time server or base time
Update interval (hours)
Automatic daylight saving
Time servers
ADSL modem operation mode
Clone WAN port MAC address
Config response mode in CLI
Interface IP address & netmask
Config interface link type
NAT network type
Config interface bridging function state
Binding interface access-list
Binding interface device-filter rules
Enable or disable access control
Binding interface inspection rule
Config interface security type
Config VLAN profile index
Interface IP address & netmask
Config interface link type
NAT network type
Config interface bridging function state
Binding interface access-list
Binding interface device-filter rules
Enable or disable access control
Binding interface inspection rule
Config interface security type
Config VLAN profile index
Interface IP address & netmask
2
Page 3
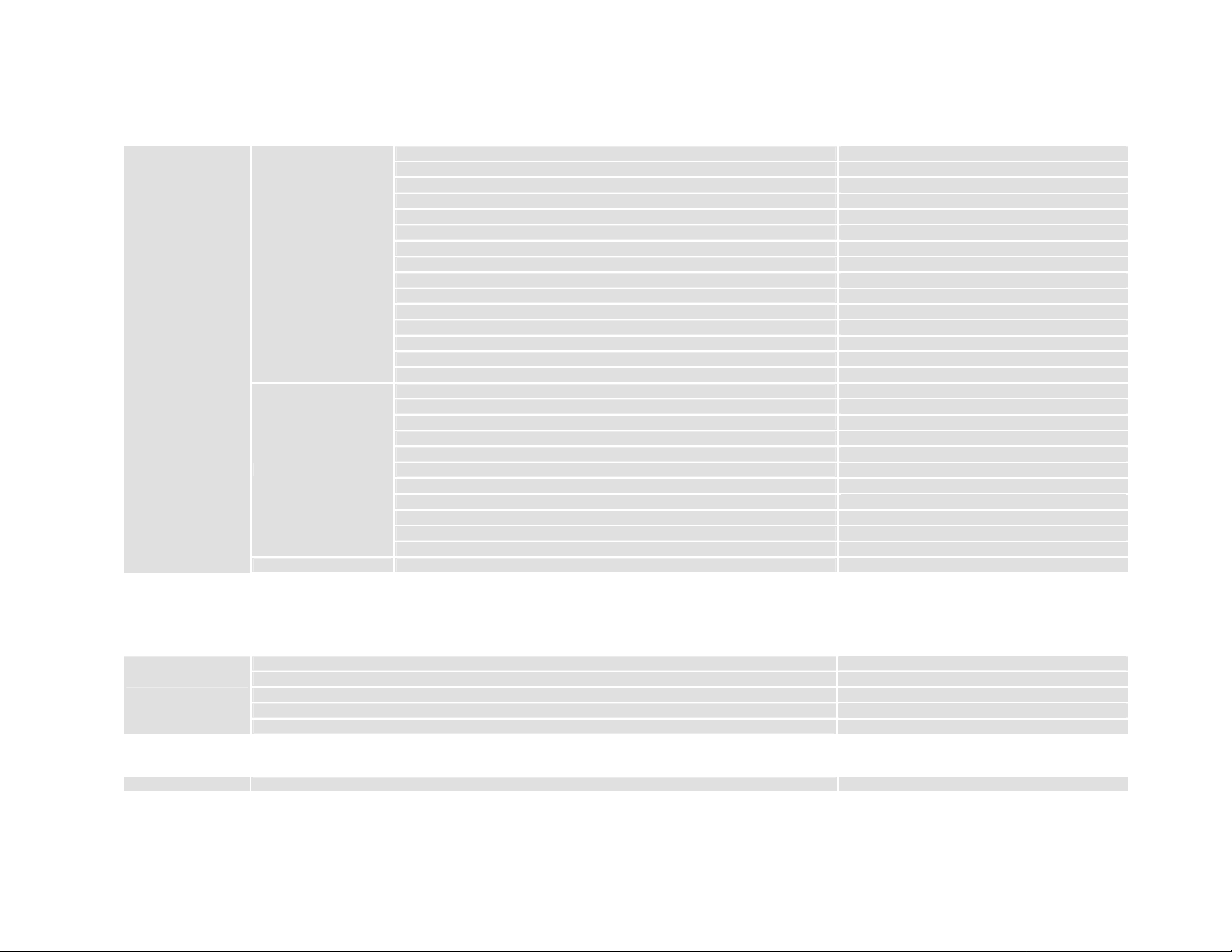
link_type <Disable|Ethernet|PPP|IPoA>
nat_type <Public|Private>
bridge <Disable|Enable>
dial <1~20> <0~32767> <-1~30>
vc <1~8>
access-list <0~4> <0~4>
device-filter <0~4> <0~4>
access_ctrl <Disable|Enable>
inspect-rule <0~4> <0~4>
network_secure <Untrust|Trust>
remote_route <ip> [Disable|Enable]
dns <ip> [ip]
ip_assign <Dynamic|Fixed>
vlan <0~4>
dhcp_clt <Disable|Enable>
address <ip> <netmask>
link_type <Disable|PPPoE>
ether_interface <interface>
dial <1~20> <0~32767> <-1~30>
pppoe <1~8>
lan_sec <1~1> address <ip> <netmask>
access-list <0~4> <0~4>
device-filter <0~4> <0~4>
access_ctrl <Disable|Enable>
inspect-rule <0~4> <0~4>
network_secure <Untrust|Trust>
ip_assign <Dynamic|Fixed>
vlan <0~4>
ps. The command `lan_sec` is for telefonica vendor.
VLAN part level II
name <string>
vlan <1~4>
ipnet <ip> <netmask>
igmp-snooping <Disable|Enable>
igmp-querier <Disable|Enable>
func <Disable|Enable>
WLAN part level II
wlan
country <1~76>
Config interface link type
NAT network type
Config interface bridging function state
Config dial profile index and attributes
Specify VC profile index
Binding interface access-list
Binding interface device-filter rules
Enable or disable access control
Binding interface inspection rule
Config interface security type
Remote IP address and add route
ISP provides DNS IP addresses
Dynamic get IP address or use fixed IP
Config VLAN profile index
Enable or disable DHCP clie nt
Interface IP address & netmask
Config interface link type
Config PPP over ehternet interface number
Config dial profile index and attributes
Binding interface access-list
Binding interface device-filter rules
Enable or disable access control
Binding interface inspection rule
Config interface security type
Dynamic get IP address or use fixed IP
Config VLAN profile index
Interface IP address & netmask
VLAN profile description
VLAN subnet value
Config IGMP-Snooping function
Config IGMP-Querier function
Enable or disable this VLAN port
Country selection
3
Page 4
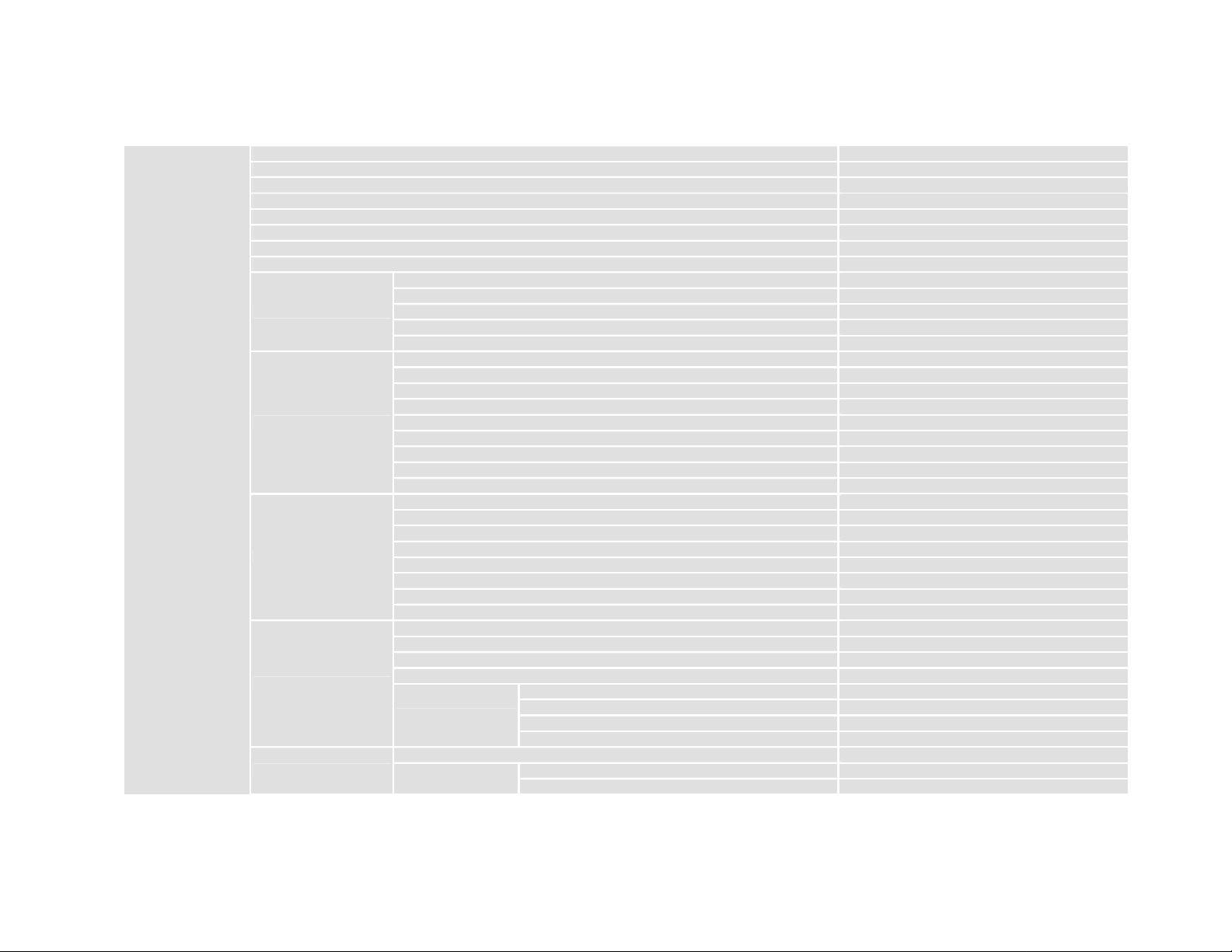
SSID <string>
hide_ssid <Disable|Enable>
channel <0~13>
tx_rate <Auto|54|48|36|24|18|12|11|9|6|5.5|2|1>
mode <mixed|long_range|g_only|b_only>
stationName <string>
rtsThreshold <0~3000>
fragThreshold <256^2346>
func <Disable|Enable>
mac_filter
wep
wpa
802.1x
wds
access_rule <Deny|Allow>
add <mac>
delete <1~32>
modify <1~32> <mac>
mode <Disable|Enable> [64|128]
dyna_key_prov <Disable|Enable>
defaultKeyId <1~4>
defaultKeys64 <1~4> <hex>
defaultKeys128 <1~4> <hex>
key64ascii <1~4> <string>
key128ascii <1~4> <string>
passphrase64 <string>
passphrase128 <string>
mode <Disable|Enable> [802.1X|PSK]
psk_type <Passphrase|Hex>
psk_hex <hex>
psk_passphrase <string>
obscure_psk <Disable|Enable>
rekey_period <Disable|Seconds|Packets>
rekey_second <number>
rekey_packet <number>
func <Disable|Enable>
session_timeout <number>
re_auth_period <number>
quiet_period <number>
server_ip <ip>
radius
func <Disable|Enable>
connect
server_port <1~65534>
secret_key <string>
nas_id <string>
func <1~4> <Disable|Enable>
mac <1~4> <mac>
SSID
Hide SSID
Current operating frequency channel
Transmission rate (Mbit)
Wireless mode
Station name
RTS threshold
Fragmentation threshold (even numbers only)
Enable MAC filter
Access rule for registered MAC address
Add MAC address
Delete MAC address
Modify MAC address
WEP mode
Key provisioning, static or dynamic
WEP default key ID
64 bits WEP key table (Hex)
128 bits WEP key table (Hex)
64 bits WEP key table (ASCII)
128 bits WEP key table (ASCII)
Passphrase for 64 bits WEP key
Passphrase for 128 bits WEP key
WPA mode
Pre-shared key type
256 bits PSK
Passphrase for PSK
Obscure PSK
Rekey period
Rekey second
Rekey packet
Enable/Disable 802.1X
Session idle timeout (milli seconds)
Re-authentication period (milli seconds)
Quiet period (milli seconds)
Server IP
Server port
Secret key
NAS-ID
WDS functionality
MAC of LAN mode to be use
MAC of LAN mode
4
Page 5
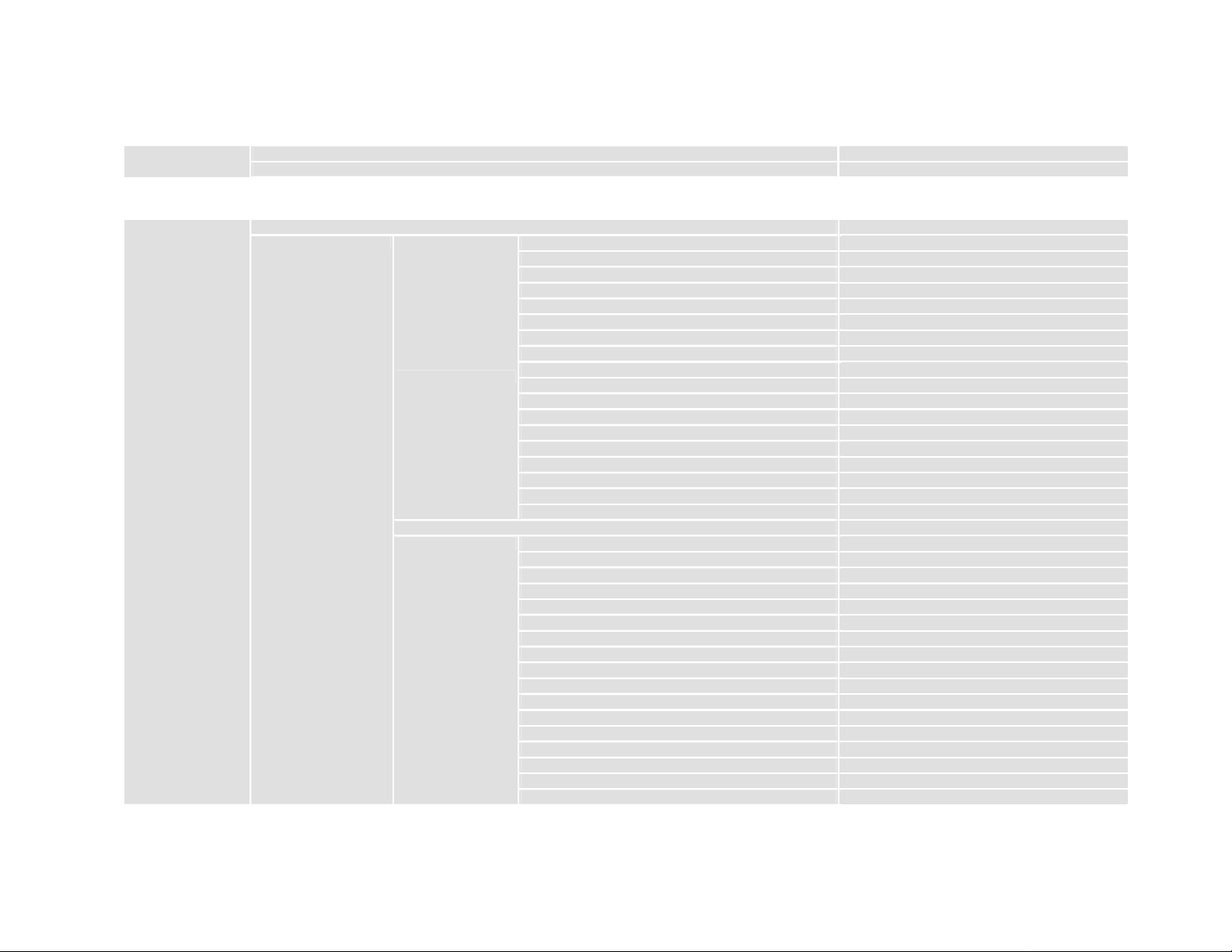
func <Disable|Enable>
security_mode <disable|wep|wpa2_only|wpa_wpa2>
BRIDGE part level II
bridge
generic <Disable|Enable> <ip> <netmask>
static
add
delete <1~20>
modify <1~20>
mac_address <mac>
LAN1_port <Filter|Forward|Dynamic>
WLAN1_port <Filter|Forward|Dynamic>
ATM1_port <Filter|Forward|Dynamic>
ATM2_port <Filter|Forward|Dynamic>
ATM3_port <Filter|Forward|Dynamic>
ATM4_port <Filter|Forward|Dynamic>
ATM5_port <Filter|Forward|Dynamic>
ATM6_port <Filter|Forward|Dynamic>
ATM7_port <Filter|Forward|Dynamic>
ATM8_port <Filter|Forward|Dynamic>
LAN2_port <Filter|Forward|Dynamic>
LAN3_port <Filter|Forward|Dynamic>
LAN4_port <Filter|Forward|Dynamic>
WDS1_port <Filter|Forward|Dynamic>
WDS2_port <Filter|Forward|Dynamic>
WDS3_port <Filter|Forward|Dynamic>
WDS4_port <Filter|Forward|Dynamic>
mac_address <mac>
LAN1_port <Filter|Forward|Dynamic>
WLAN1_port <Filter|Forward|Dynamic>
ATM1_port <Filter|Forward|Dynamic>
ATM2_port <Filter|Forward|Dynamic>
ATM3_port <Filter|Forward|Dynamic>
ATM4_port <Filter|Forward|Dynamic>
ATM5_port <Filter|Forward|Dynamic>
ATM6_port <Filter|Forward|Dynamic>
ATM7_port <Filter|Forward|Dynamic>
ATM8_port <Filter|Forward|Dynamic>
LAN2_port <Filter|Forward|Dynamic>
LAN3_port <Filter|Forward|Dynamic>
LAN4_port <Filter|Forward|Dynamic>
WDS1_port <Filter|Forward|Dynamic>
WDS2_port <Filter|Forward|Dynamic>
WDS3_port <Filter|Forward|Dynamic>
Wireless disable or enable
Config wireless security mode
Config bridging function, IP and subnet mask
Config mac address
Config LAN1 bridging type
Config WLAN1 bridging type
Config ATM1 bridging type
Config ATM2 bridging type
Config ATM3 bridging type
Config ATM4 bridging type
Config ATM5 bridging type
Config ATM6 bridging type
Config ATM7 bridging type
Config ATM8 bridging type
Config LAN2 bridging type
Config LAN3 bridging type
Config LAN4 bridging type
Config WDS1 bridging type
Config WDS2 bridging type
Config WDS3 bridging type
Config WDS4 bridging type
Delete static MAC entry
Config mac address
Config LAN1 bridging type
Config WLAN1 bridging type
Config ATM1 bridging type
Config ATM2 bridging type
Config ATM3 bridging type
Config ATM4 bridging type
Config ATM5 bridging type
Config ATM6 bridging type
Config ATM7 bridging type
Config ATM8 bridging type
Config LAN2 bridging type
Config LAN3 bridging type
Config LAN4 bridging type
Config WDS1 bridging type
Config WDS2 bridging type
Config WDS3 bridging type
5
Page 6
VC part level II
vpi_vci <0~255> <0~65535>
encapsulate <VC-Mux|LLC>
vc <1~8>
state <Disable|Enable>
qos <CBR|VBR|UBR>
pcr <0~9999>
scr <0~9999>
mbs <0~9999>
PPP part level II
users_edit
ppp
address_pool ip_pool <ip> <1~127>
authenticate <User_Pool|RADIUS> <User_Pool|RADIUS>
assign_address <Address_Pool|RADIUS> <Address_Pool|RADIUS>
wan_pppoe <Disable|PPPoE>
DIAL part level II
isp_profile <string> [string]
account_profile <account> <pass_set1>
dial <1~20>
on_demand <Disable|Enable>
auto_reconnect <Disable|Enable>
startup <Disconnected|Connected|Last>
mtu <512~1500>
IP_SHARE part level II
ip_share address_mapping
WDS4_port <Filter|Forward|Dynamic>
modify <1~25> profile <name> <pass_set0>
delete <1~25>
interface <interface>
add
delete <1~20>
func <Disable|Enable>
virtual_ip <ip> <1~254>
global_ip <ip>
Config WDS4 bridging type
Config VPI/VCI value
Config encapsulation type
Config ATM virtual circuit state
QoS class
Peak cell rate
Sustain cell rate
Maximum brust size
User account and password
Delete user profile
Edit IP pool. Based IP address & range number
User authentication policy
Peer address assignment policy
WAN port PPPoE function
Config dial-out ISP name and destination string
Config access account and password
Continuous or dial on demand
Automatic reconnect
Connection state while system startup
Config MTU
Activate interface
Enable or disable this entry
Local address pool
Global address
Delete address mapping
6
Page 7

virtual_server
special_ap
nat
FIREWALL-FUNC part level II
all <Disable|Enable>
DMZ <Disable|Enable>
schedule_rule <Disable|Enable>
inspect <Disable|Enable>
firewall-func
DoS <Disable|Enable>
WAN_ping <Disable|Enable>
rip_defect <Disable|Enable>
virtual_DMZ
maillog <DoS|Ping|RIP> <Disable|Enable>
interface <interface>
modify <1~20>
add
delete <1~20>
modify <1~20>
add
delete <1~10>
modify <1~10>
local
global
modify <1~20> <ip> <ip|WAN_IP>
interface <1~20> <interface>
delete <1~20>
func <Disable|Enable>
virtual_ip <ip> <1~254>
global_ip <ip>
name <name>
interface <interface>
server <ip>
port_map <wan_ports> <lan_ports>
func <Disable|Enable>
name <name>
interface <interface>
server <ip>
port_map <wan_ports> <lan_ports>
func <Disable|Enable>
incoming <port_range> <TCP|UDP>
func <Disable|Enable>
trigger <1~65534> <TCP|UDP>
incoming <port_range> <TCP|UDP>
func <Disable|Enable>
trigger <1~65534> <TCP|UDP>
range <1~5> <ip> <1~253>
delete <1~5>
range <1~5> <ip> <1~253>
interface <1~5> <interface>
delete <1~5>
Activate interface
Enable or disable this entry
Local address pool
Global address
Service name
Activate interface
LAN Host IP address
public to private protocol/ports mapping
Enable or disable this virtual server
Delete virtual server mapping
Service name
Activate interface
LAN Host IP address
public to private protocol/ports mapping
Enable or disable this virtual server
Incoming protocol & ports number
Enable or disable this applicat ion
Trigger port and protocol
Delete special application mapping
Incoming protocol & ports number
Enable or disable this applicat ion
Trigger port and protocol
Edit address range
Delete address range
Edit address range
Bind address range to specific interface
Delete address range
Enable or disable overall firewall function
Enable or disable DMZ function
Enable or disable schedule rule function
Enable or disable inspection module
Enable or disable DoS pattern detect
Deny ping request from WAN
Deny RIP from WAN
Modify DMZ address mapping
Bind address pair to specific interface
Delete DMZ address mapping
Mail log functionality
7
Page 8

ACCESS-LIST part level II
access-list
standard <1~4>
extended <1~4>
device-filter
<1~4>
add <Deny|Permit|Count> <ip/mask|Any>
delete [1~1|All]
modify <1~1> <Deny|Permit|Count> <ip/mask|Any>
reset_counter [1~1]
default_action <Deny|Permit>
policy <1~1> <1~65535>
add <1~65534>
<Deny|Permit|
Count>
<TCP|UDP>
add <1~65534>
<Deny|Permit|
Count>
<ICMP>
add <1~65534>
<Deny|Permit|
Count>
<IP>
delete [1~250|All]
modify <1~250>
<Deny|Permit|
Count>
<TCP|UDP>
modify <1~250>
<Deny|Permit|
Count>
<ICMP>
modify <1~250>
<Deny|Permit|
Count>
<IP>
reset_counter [1~250]
default_action <Deny|Permit>
policy <1~250> <1~65535>
add <Deny|Permit> <hex>
delete [1~32|All]
modify <1~32> <Deny|Permit> <hex>
default_action <Deny|Permit>
from
<ip/mask|
Any>
<port_str
|Any>
from
<ip/mask|
Any>
from
<ip/mask|
Any>
from
<ip/mask|
Any>
<port_str
|Any>
from
<ip/mask|
Any>
from
<ip/mask|
Any>
to
<ip/mask|
Any>
<port_str
|Any>
to
<ip/mask|
Any>
to
<ip/mask|
Any>
to
<ip/mask|
Any>
<port_str
|Any>
to
<ip/mask|
Any>
to
<ip/mask|
Any>
<CR>
<CR>
type_code
<0~18|Don'tCare>
<0~15|Don'tCare>
<CR>
<CR>
<CR>
type_code
<0~18|Don'tCare>
<0~15|Don'tCare>
<CR>
Add new access control rule
Delete access control rule
Modify access control rule properties
Reset access control rule counter
Access-list default action
Assign policy number to access control rule
Access control rule
Access control rule
ICMP type, code
Access control rule
Delete access control rule
Modify access control rule
Modify access control rule
ICMP type, code
Modify access control rule
Reset access control rule counter
Access-list default action
Assign policy number to access control rule
Add new device-filter rule
Delete device-filter rule
Modify device-filter rule properties
Device-filter default action
8
Page 9

URL_list
schedule
policy <1~32> <1~65535>
add <keyword>
delete <1~30>
modify <1~30> <keyword>
everyday_start <0~23|Don'tCare> <0~59|Don'tCare>
everyday_end <0~23|Don'tCare> <0~59|Don'tCare>
sunday_start <0~23|Don'tCare> <0~59|Don'tCare>
sunday_end <0~23|Don'tCare> <0~59|Don'tCare>
monday_start <0~23|Don'tCare> <0~59|Don'tCare>
monday_end <0~23|Don'tCare> <0~59|Don'tCare>
tuesday_start <0~23|Don'tCare> <0~59|Don'tCare>
tuesday_end <0~23|Don'tCare> <0~59|Don'tCare>
add
delete <1~10>
modify
<1~10>
wednesday_start <0~23|Don'tCare> <0~59|Don'tCare>
wednesday_end <0~23|Don'tCare> <0~59|Don'tCare>
thursday_start <0~23|Don'tCare> <0~59|Don'tCare>
thursday_end <0~23|Don'tCare> <0~59|Don'tCare>
friday_start <0~23|Don'tCare> <0~59|Don'tCare>
friday_end <0~23|Don'tCare> <0~59|Don'tCare>
saturday_start <0~23|Don'tCare> <0~59|Don'tCare>
saturday_end <0~23|Don'tCare> <0~59|Don'tCare>
func <Disable|Enable>
name <name> [string]
everyday_start <0~23|Don'tCare> <0~59|Don'tCare>
everyday_end <0~23|Don'tCare> <0~59|Don'tCare>
sunday_start <0~23|Don'tCare> <0~59|Don'tCare>
sunday_end <0~23|Don'tCare> <0~59|Don'tCare>
monday_start <0~23|Don'tCare> <0~59|Don'tCare>
monday_end <0~23|Don'tCare> <0~59|Don'tCare>
tuesday_start <0~23|Don'tCare> <0~59|Don'tCare>
tuesday_end <0~23|Don'tCare> <0~59|Don'tCare>
wednesday_start <0~23|Don'tCare> <0~59|Don'tCare>
wednesday_end <0~23|Don'tCare> <0~59|Don'tCare>
thursday_start <0~23|Don'tCare> <0~59|Don'tCare>
thursday_end <0~23|Don'tCare> <0~59|Don'tCare>
friday_start <0~23|Don'tCare> <0~59|Don'tCare>
friday_end <0~23|Don'tCare> <0~59|Don'tCare>
saturday_start <0~23|Don'tCare> <0~59|Don'tCare>
saturday_end <0~23|Don'tCare> <0~59|Don'tCare>
func <Disable|Enable>
name <name> [string]
Assign policy number to access control rule
Add new blocking site or keyword
Delete blocking site or keyword
Modify blocking site or keyword
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Enable this schedule rule
Schedule name and comment
Delete schedule rule
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Config schedule start time
Config schedule end time
Enable this schedule rule
Schedule name and comment
9
Page 10

INSPECT part level II
name <rule-name> <Frag|TCP|UDP|FTP|H323|TFTP|L2TP|SIP>
name_delete <1~4>
tcp
inspect
udp idle-time <1~120>
max-incomplete
one-minute
port_scan_defect <50~5000> <1~150>
fragment <10~60000> <1~150> <1~120>
block-time <0~30000>
h323-timeout <0~3600>
ROUTE part level II
static
route
rip
DHCP part level II
dhcp server_generic
<CR>
disable <CR>
synwait-time <1~120>
finwait-time <1~60>
idle-time <1800~7200>
high <1~300>
low <1~250>
high <1~250>
low <1~200>
add <network_ip> <netmask> <gateway_ip>
delete <1~20>
generic <Disable|Enable> <Disable|Enable>
version <None|RIP1|RIP2>
lan <1~4>
wlan <1~1>
atm <1~8>
interface <interface>
gateway <ip>
attrib <Disable|Enable|Silent>
<None|PASSWORD|MD5> <Disable|Enable>
authenticate <string>
version <None|RIP1|RIP2>
attrib <Disable|Enable|Silent>
<None|PASSWORD|MD5> <Disable|Enable>
authenticate <string>
version <None|RIP1|RIP2>
attrib <Disable|Enable|Silent>
<None|PASSWORD|MD5> <Disable|Enable>
authenticate <string>
Modify inspection rule
Disable specific protocol inspection function
Delete inspection rule
TCP session to be established waiting time
TCP session to be closed waiting time
TCP session idle timeout
UDP session idle timeout
Maximum existing half-open sessions
Minimum existing half-open sessions
Maximum rate of new half-open session
Minimum rate of new half-open session
'Port Scan/Flooding' defect sensitive criteria
Fragmention half-open entry threshold
Flood hacker blocking time
H.323 data channel idle timeout
Add static route entry
Delete static route entry
Config operation and auto summary mode
Config RIP protocol version
Config operation, authentication and Poison
reverse mode
Config authentication code
Config RIP protocol version
Config operation, authentication and Poison
reverse mode
Config authentication code
Config RIP protocol version
Config operation, authentication and Poison
reverse mode
Config authentication code
DHCP server activate interface
Default gateway for DHCP client
10
Page 11

fixed
client_release <ip>
client <Disable|Enable>
client_interface <interface>
DNS part level II
dns
proxy_func <Disable|Enable>
server <ip> [ip] [ip]
DDNS part level II
func <Disable|Enable>
ddns
provider <DynDNS.org|TZO.com>
domain_name <domain>
account <address>
password <password>
SNMP part level II
modify <Disable|Enable> <string>
<Read|Write|Read_Write|Deny>
delete <CR>
modify <Disable|1|2> <ip> <string>
delete <CR>
snmp
community
<1~5>
trap <1~5>
MAIL part level II
smtp <domain>
mail generic
pop3 <domain>
mail <address>
account <name>
password <pass_set0>
netmask <netmask>
ip_range <ip> <1~222>
name_server <ip> [ip] [ip]
lease_time <-1~1209600>
service <Disable|Enable>
add <mac> <ip>
delete <1~10>
Subnet mask for DHCP client
Dynamic assigned IP address range
Domain name servers
Lease time (seconds)
Trigger DHCPD service
Add a fixed host entry
Delete a fixed host entry
Release DHCP client(Ref.'monitor dhcp_client'
command)
DHCP client functionality
DHCP client activate interface number
Enable or disable DNS Proxy function
DNS servers
Dynamic DNS functionality
Dynamic DNS Provider
Dynamic Domain Name
Account (Email address)
Passowrd for Account
Edit community entry
Delete community entry
Edit trap host parameter
Delete trap host entry
Sharing account's SMTP server address
Sharing account's POP3 server address
Sharing account's E-mail address
POP3 server access account
POP3 server access password
11
Page 12

CHUSER part level III
max_user <1~5>
telnet_port <1~54999>
user_profile
chuser
address_control
login_timeout <0~1440>
remote_login <Disable|Enable|Disable_Lan>
UPNP part level II
upnp <Disable|Enable>
VOIP_SIP part level II
voip_sip
phone_config
<1~4>
sip_server
advanced_config
attrib <13~30> <Command|Menu>
<VT100|ANSI|Linux|XTerm>
add
delete <2~5>
modify
<1~5>
modify <1~16>
delete <1~16>
default_act <Deny|Permit>
remote_subnet <ip> <netmask>
phone_valid <Disable|Enable>
phone_number <string>
display_name <string>
sip_domain <ip|domain>
account <string> <sting> <pass_set1>
listen_port <1~65534>
call_waiting <Disable|Enable>
sip_proxy <ip|domain> <1~65534>
sip_registrar <ip|domain> <1~65534>
expire_time <number>
call_waiting <Disable|Enable>
source <1~16|Pool|Unlimited|Subnet>
privilege <User|Conf>
<User|Conf|Root|Unlimited>
profile <name> <pass_conf>
attrib <13~30> <Command|Menu>
<VT100|ANSI|Linux|XTerm>
source <1~16|Pool|Unlimited|Subnet>
privilege <User|Conf>
<User|Conf|Root|Unlimited>
profile <name> <pass_conf>
entry_edit <network_ip> <netmask>
<Deny|Permit>
Maximum allow telnet access user number
Telnet TCP port config
Client attributes
Legal client IP address index or type
User login privilege and maximum allow privilege
Setting username and password
Delete user profile
Client attributes
Legal client IP address index or type
User login privilege and maximum allow privilege
Setting username and password
Modify adress control pool
Delete address control
Default access control action
Remote management address & netmask
Login timeout (minutes)
Remote management function disable or enable
Enable or disable Universal Plug and Play
Enable or disable Phone
Phone Number
Display Name
SIP Domain
Account : Realm Username Password
SIP listening port
Enable or disable Support Call Waiting
Proxy IP Address and Port
Registrar IP Address and Port
Expire Time
Enable or disable Support Call Waiting
12
Page 13

port_config
<1~4>
dial_plan
quick_dial
active <CR>
VOIP_QOS part level II
voip_qos
state <Disable|Enable>
bind <By_Routing|VC_1|VC_2|VC_3|VC_4|VC_5|VC_6|VC_7|VC_8>
caller_id <Disable|Enable>
user_agent <Disable|Enable>
dtmf <Disable|Enable>
call_hold_version <RFC2543|RFC3264>
tone_country <Japan|USA|France|Germany|Spain|Taiwan
|Canada|Italy|Belgium>
hook_flash_timer <number>
voip_tone <Disable|Enable>
add_codec <G7231|G711Ulaw|G711Alaw|G729>
codec
volume_gain <Off|Fixed|Adaptive>
gain_input <number>
gain_output <number>
gain_adapt <number>
jitter_buffer <Off|Fixed|Adaptive|Sequential>
delay <number>
echo_canceller <Off|08MS|16MS|32MS|48MS|64MS>
comfort_noise <Off|On>
voice_detect <Off|On>
packet_loss <Disable|Enable>
add_call_prefix <Disable|Enable>
call_prefix <number>
add <number> <connect_code>
modify <number> <connect_code>
delete <number>
delete_all <CR>
add <1~20> <string> <string>
modify <1~20> <string> <string>
delete <1~20>
delete_all <CR>
del_codec <G7231|G711Ulaw|G711Alaw|G729>
codec_pri <G7231|G711Ulaw|G711Alaw|G729>
<1~4>
Enable or disable Caller-ID Presentation
Enable or disable Support User-Agent Header
Enable or disable Support RFC 2833 (DTMF out of
band)
Config Call Hold Version
Config Telephony Tone Country
Config Telephony Hook Flash Timer
Enable or disable different dial tone for VoIP
Add Codec
Delete Codec
Modify Codec Priority
Config Volume Gain
Config Gain Input
Config Gain Output
Config Gain Adapt
Config Jitter Buffer
Config Fixed Delay
Config Echo Canceller
On or Off Comfort Noise Generation
On or Off Voice Activity Detector
Enable or disable Packet Loss Compensation
Enable or disable Automatically Ahead all
PSTN-number
Phone number of the call-by-call-provider
Add dial plan rule
Modify dial plan rule
Delete dial plan rule
Delete all dial plan rule
Add quick dial rule
Modify quick plan rule
Delete quick plan rule
Delete all quick plan rule
Active the changes
Disable or Enable VOIP QOS
Config VOIP QOS route parameter
13
Page 14

QOS part level II
outbound <Disable|Enable>
bandwidth <BE|AF1|AF2|AF3|AF4|EF> <0~100> <Disable|Enable>
add
<string>
qos
classify
modify
<1~16>
delete <string>
moveup <string>
movedown <string>
active <CR>
NETBIOS part level II
netbios
func <Disable|Enable>
remote_access <Disable|Enable>
src <mac_str|ip_range|thisrouter|any>
dst <ip_range|any>
tfc <FTP|VoIP|E-MAL|SNMP|TELNET|WWW|VPN|IP>
dscp <any|notany> <0x00~0xFF>
mapeto <BE|AF1|AF2|AF3|AF4|EF> <remark|notremark>
<0x00~0xFF>
outvc <0~8>
src <mac_str|ip_range|thisrouter|any>
dst <ip_range|any>
tfc <TCP|UDP>
localport <port_str>
remoteport <port_str>
dscp <any|notany> <0x00~0xFF>
mapeto <BE|AF1|AF2|AF3|AF4|EF> <remark|notremark>
<0x00~0xFF>
outvc <0~8>
rule_name <string>
src <mac_str|ip_range|thisrouter|any>
dst <ip_range|any>
tfc <FTP|VoIP|E-MAL|SNMP|TELNET|WWW|VPN|IP>
dscp <any|notany> <0x00~0xFF>
mapeto <BE|AF1|AF2|AF3|AF4|EF> <remark|notremark>
<0x00~0xFF>
outvc <0~8>
rule_name <string>
src <mac_str|ip_range|thisrouter|any>
dst <ip_range|any>
tfc <TCP|UDP>
localport <port_str>
remoteport <port_str>
dscp <any|notany> <0x00~0xFF>
mapeto <BE|AF1|AF2|AF3|AF4|EF> <remark|notremark>
<0x00~0xFF>
outvc <0~8>
Disable or Enable outbound control
Config bandwidth allocation
Add classify rule
Modify classify rule
Delete classify rule
Move classify rule up
Move classify rule down
Active the changes
NetBIOS file server function
Allow remote access to NetBIOS file server
14
Page 15

name <name>
group_name <name>
description <string>
share_profile
<1~10>
usb_disk1 <1~7>
usb_disk2 <1~7>
paper_out_wait <0~150>
spooler
STORAGE part level II
storage
usb_disk1
usb_disk2 volume mount <1~32> <Disable|Enable>
SHOW part level I
show
run <CR>
configuration <CR>
system <CR>
vc <CR>
interface [LAN|WAN]
mail <CR>
ppp [Generic|Users|Pool|IP_Pool]
ip_share [AddressMapping|VirtualServer|SpecialAP|NAT]
dhcp [Server|Fixed|Client]
ddns <CR>
route [Static|RIP]
bridge [Generic|Static|STP]
dial <CR>
wLAN [Generic|WEP|MAC|WPA|802.1x|status|WDS]
firewall_func [Generic|DMZ]
access-list [1~4]
inspect [Generic|Rule]
name <name>
description <string>
volume <0~32>
path <path>
secure <Disable|Enable> <RO|FUL|DEP>
read_pass [pass_set0]
full_pass [pass_set0]
func <Disable|Enable>
type <Printer|Disk>
volume mount <1~32> <Disable|Enable>
unplug <CR>
Device name for NetBIOS server
Workgroup name for NetBIOS server
Device description
Share name string
Description of share resource
Volume ID of sharing path
Root sharing path
Enable or disable password protect
Read-only password (Empty for don't check)
Full access password (Empty for don't check)
Share resource function disable or enable
Share resource type, printer or disk
Volume bind share profile index
Volume bind share profile index
Paper out waiting time (sec.)
Print job spooling configuration
mount <1~32> <Disable|Enable>
Unplug USB disk 1 device
USB disk volume mount
Show all configuration
Show all configuration in command script
Show common system configuration
Show ATM virtual circuit configuration
Show inter face configu ra tion
Show mail configuration
Show PPP configuration
Show IP address sharing configuration
Show DHCP configuration
Show Dynamic DNS configuration
Show routing configuration
Show bridging configuration
Show Dial configuration
Show wireless LAN configuration
Show firewall function configuration
Show access control rules pool
Show access control rules pool
15
Page 16

user [Generic|Profile|Pool]
voip_sip [phone|server|advanced|port|dial_plan|quick_dial]
qos [traffic_ctrl|classify|statistics]
netbios [Generic|usb1_binding|usb2_binding|share_profile]
storage [usbdisk1|usbdisk2]
MONITOR part level I
route <CR>
netbios_pool <Basic|Advance>
adsl [Status|Statistics]
interface [Status|ATM|Ethernet]
monitor
user <CR>
access-list <1~4>
inspect [Frag|TCP|UDP]
syslog [Alert|Log]
dhcp_client <CR>
socket [TCP|UDP|ICMP]
dns <CR>
UPGRADE part level III
all <ip|Xmodem> [file]
upgrade
kernel <ip|Xmodem> [file]
web_image <ip|Xmodem> [file]
conf_file <ip|Xmodem> [file]
boot_code <ip|Xmodem> [file]
BACKUP part level III
backup conf_file <ip|Xmodem> [file]
level I
passwd [username] [old_pass] [new_pass]
level II
default_reset <CR>
level II
write [reboot|exit]
Show configuration parameters and users profile
Show VOIP SIP profile
Show QoS profile
Show NetBIOS file server configuration
Show storage device info
Monitor routing table
Monitor NetBIOS name database
Monitor ADSL router running status or statistics
Monitor interface status or statistics
Monitor login user information
Monitor access control rules pool
Monitor inspection run-time pool
Monitor firewall alert or system log
Monitor DHCP client request address pool
Monitor socket run-time information
Monitor DNS cache table
Upgrade firmware image
Upgrade kernal run-time code image
Upgrade web image file
Upgrade configuration file
Upgrade boot code
Backup configuration file
Change user password
Reset system configuration to default status
Write configuration and restart system
16
Page 17

level II
reboot <CR>
level I
enable <CR>
level I
su <password>
level I
ping <ip|domain> [1~65534|-t] [1~1999]
level I
tracert <ip|domain> [option1] [option2]
level I
exit <CR>
Restart system
Enable configuration mode
Change to super user(root) mode
Ping test
Trace route utility
exit <CR>
17
 Loading...
Loading...