Page 1

Technaxx® * User Manual
WiFi Smart Alarm System Starter-Kit TX-84
WiFi Basis Station TX-91
PIR Detection Sensor TX-85
Door & Window Contact TX-86
Remote Control SOS Button TX-87
Alarm Siren TX-88
[ not enclosed in Kit TX-84]
The manufacturer Technaxx Deutschland GmbH & Co.KG hereby declares that this device,
to which this user manual belongs, complies with the essential requirements of the
standards referred to the Directive RED 2014/53/EU. The Declaration of Conformity you
find here: www.technaxx.de/ (in bar at the bottom “Konformitätserklärung”). Before using
the device the first time, read the user manual carefully.
Service phone No. for technical support: 01805 012643 (14 cent/minute from German
fixed-line and 42 cent/minute from mobile networks). Free Email: support@technaxx.de
If you drill a hole in the wall, please make sure that power cables, electrical cords and/or
pipelines are not damaged. When using the supplied mounting material, we do not take the
liability for a professional installation. You are entirely responsible to ensure that the
mounting material is suitable for the particular masonry, and that the installation is done
properly. When working at higher altitudes, there is danger of falling! Therefore, use
suitable safeguards.
Important Hint regarding the uer mnuals:
All languages of the user manual are on the CD enclosed.
Keep this user manual for future reference or product sharing carefully. Do the same with
the original accessories for this product. In case of warranty, please contact the dealer or
the store where you bought this product.
Warranty 2 years
1
Page 2

Table of Contents
1
Features.............................................................................................................................. 3
1.1 WiFi Basis Station TX-91...................................................................................................... 3
1.2 PIR Detection Sensor TX-85................................................................................................3
1.3 Door & Window Contact TX-86.............................................................................................4
1.4 Remote Control SOS Button TX-87...................................................................................... 4
1.5 Alarm Siren TX-88................................................................................................................ 4
2
Packaging list (1x User Manual for all 5 devices together)................................................... 4
3
Product Overview................................................................................................................4
3.1 WiFi Basis Station TX-91...................................................................................................... 5
3.2 PIR Detection Sensor TX-85................................................................................................5
3.3 Door & Window Contact TX-86.............................................................................................6
3.4 Remote Control SOS Button TX-87...................................................................................... 7
3.5 Alarm Siren TX-88................................................................................................................ 7
4
Product Mounting ................................................................................................................ 8
4.1 WiFi Basis Station TX-91...................................................................................................... 8
4.2 PIR Detection Sensor TX-85................................................................................................9
4.3 Door & Window Contact TX-86...........................................................................................11
4.4 Alarm Siren TX-88.............................................................................................................. 13
5
Start Use ........................................................................................................................... 14
5.1 WiFi Basis Station TX-91.................................................................................................... 14
5.1.1 Connect Basis Station TX-91 to WIFI and add detector and siren to the Basis Station...... 14
5.1.2 Add Detector & Siren (TX-85, 86, 88)................................................................................16
5.1.3 Clear Detector / Siren Matching Info.................................................................................. 17
5.1.4 Add Remote Control TX-87 ............................................................................................... 17
5.1.5 Delete Detector, Siren or Remote Control..........................................................................17
5.2 PIR Detection Sensor TX-85..............................................................................................18
5.3 TX-86 Door and Window Contact....................................................................................... 19
5.4 Remote Control SOS Button TX-87.................................................................................... 19
5.5 Alarm Siren TX-88.............................................................................................................. 19
2
Page 3

6
My Secure Pro APP........................................................................................................... 20
6.1 WiFi Basis Station Alarm.................................................................................................... 20
6.1.1 Select and set mode (Stay, Away, Custom & Disarm) .......................................................20
6.1.2 Setting of Detector & Siren................................................................................................21
6.1.3 Change view of detector & siren list...................................................................................22
6.2 Alarm Basis Station (Hub) Manager................................................................................... 23
6.3 Event List........................................................................................................................... 24
6.4 Local Files..........................................................................................................................25
7
Change batteries of devices..............................................................................................26
8
FAQ...................................................................................................................................26
9
Technical Specification...................................................................................................... 26
9.1 WiFi Basis Station TX-91.................................................................................................... 26
9.2 PIR Detection Sensor TX-85..............................................................................................27
9.3 Door and Window Contact TX-86....................................................................................... 27
9.4 Remote Control SOS Button TX-87.................................................................................... 27
9.5 Alarm-Siren TX-88.............................................................................................................. 28
1 Features
1.1 WiFi Basis Station TX-91
Modularly expandable, connect max. 32 detectors [max. 28 detectors (TX-85 & TX-86)],
max. 4 Siren (TX-88) Connection with up to 6 remote controls Push message at alarm
release & emergency call Two-way communication between detector & basis station
Transimission distance to sensors ~200m open areas Adjustable alarm tone volume
(mute, silent, loud) Easy installation & configuration via Smartphone with My Secure Pro
APP (iOS & Android) Activate & Deactivate of the alarm system via remote control or APP
5V/2A power supply via USB power adapter
1.2 PIR Detection Sensor TX-85
Alarm release at motion detection, ~12m distance Built-in vadalism alarm Two-way
communication between PIR & basis station Transimission distance ~200m open areas
Two levels of sensitivity adjustable Viewing angle 90° horizontal & 70° vertical Push
message at low battery level ~3 years battery life time at ~20 operations/day
3
Page 4

1.3 Door & Window Contact TX-86
Sensor alam triggering at ~2.5cm distance Built-in vadalism alarm Two-way
communication between contact & basis station Transimission distance ~200m open
areas Push message at low battery level ~3 years battery life time at ~20
operations/day
1.4 Remote Control SOS Button TX-87
SOS button for emergency calls with Push message 4 adjustments possible: activate,
stay at home, disarm, SOS
1.5 Alarm Siren TX-88
Acoustic and visual alarm for deterrence Sound intensity is 85dB (1m) Built-in
vadalism alarm Two-way communication between sirene & basis station Transimission
distance ~200m open areas Push message at low battery level ~1.5 years battery life
time at ~2 operations/day
2 Packaging list
WiFi Basis Station TX-91: 1x USB power adapter, 1x Micro USB cable, 3x screws, 3x
dowels, 1x adhesive tape # PIR Detection Sensor TX-85: 1x bracket (on the device), 4x
screws, 4x dowels, 1x CR123A battery # Door & Window Contact TX-86: 4x screws, 4x
dowels, 1x CR123A battery, 2x adhesive tape # Remote Control SOS Button TX-87: 1x
CR2032 battery 3V (installed in device) # Alarm Siren TX-88: 4x screws, 4x dowels, 4x
CR123A batteries
(User Manual for all 5 devices)
3 Product Overview
The alarm system with Basis Station (“The Brain”), PIR Sensor, Door & Window contact,
Remote and Alarm Siren is a basic kit for your home security (all sensors/detectors are
available separately). The Basis Station is installed and used with the free My Secure Pro
APP (only for Smartphone iOS & Android). You can connect max. 32 detector (max. 28
detector (TX-85 & TX-86), max. 4 Siren (TX-88). The Basis Station has to be connected to
your WiFi. Its sensors/detectors/sirens are connected with the radio frequency 868MHz to
the Basis Station. Over die APP the Basis Station informs you via push notification on your
Smartphone, when door/indow are opend or the PIR Sensor is triggered. As well the Basis
Station and the conncted siren will start to make noise and frighten the burglar.
Attention: The devices included in the TX-84 Kit (TX-85, 86, 87, 88 and 91) are all for
indoor use only. If you want to install and use the devices outside you have to install it on
your own risk of damage and warranty lose.
4
Page 5
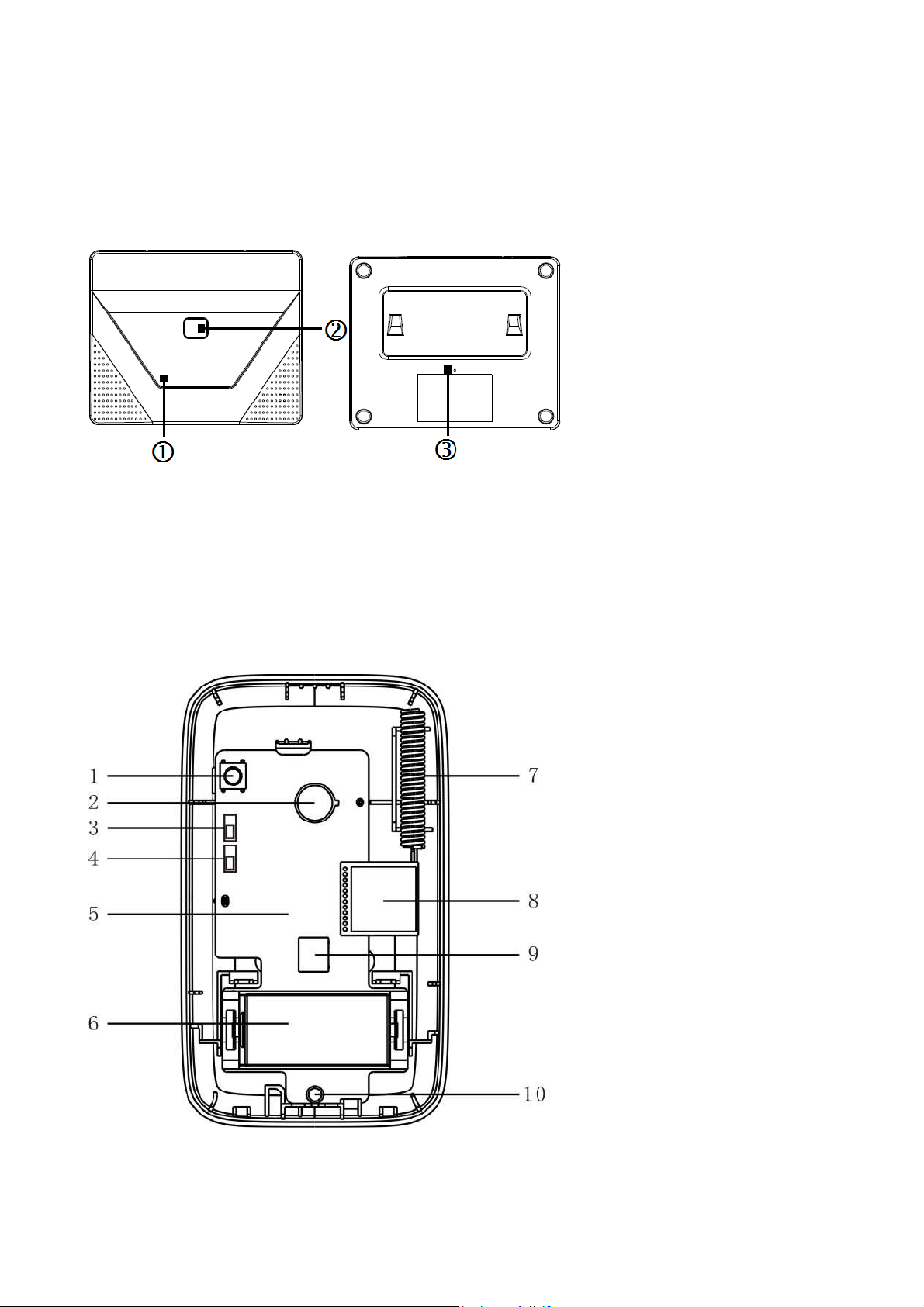
3.1 WiFi Basis Station TX-91
The Basis Station is the brain of your alarm system. It has to be connected to your WiFi
network. About this way it can send you push notifications on your Smartphone. With the
868MHz transmission it is able to connect to the detectors, sensors, remotes and sirens.
The technique allows spanning a transmission range up to ~200m open space (no
interference).
Figure 3-1
1 = Power indicator; 2 = Function key; 3 = Reset button
3.2 PIR Detection Sensor TX-85
This PIR TX-85 Detector is an indoor wireless passive infrared intrusion detector. When a
zone is intruded, the detector will output alarm signal via wireless module to upload to
wireless alarm Basis Station, thus alarm is generated and send as push notification to your
Smartphone.
Figure 3-2
5
Page 6
1
Case vandal-proof switch 6 Battery (Type CR123A)
2 Pyroelectric infrared detector 7 Antenna
3 Sensitivity adjustment 8 WiFi module
4 LED adjustment 9 Wall vandal-proof switch (backside)
5 Motherboard PCB (Printed Circuit Board) 10 LED
3.3 Door & Window Contact TX-86
This Door Detector is wireless intrusion detector. When arming zone is intruded, the
detector will output alarm signal via wireless module to upload to wireless alarm Basis
Station, thus alarm is generated.
Figure 3-3
1 = WiFi Module; 2 = Case vandal-proof switch; 3 = LED; 4 = Wall vandal-proof switch
(backside); 5 = Reed switch; 6 = Battery (Type CR123A); 7 = Magnet
6
Page 7
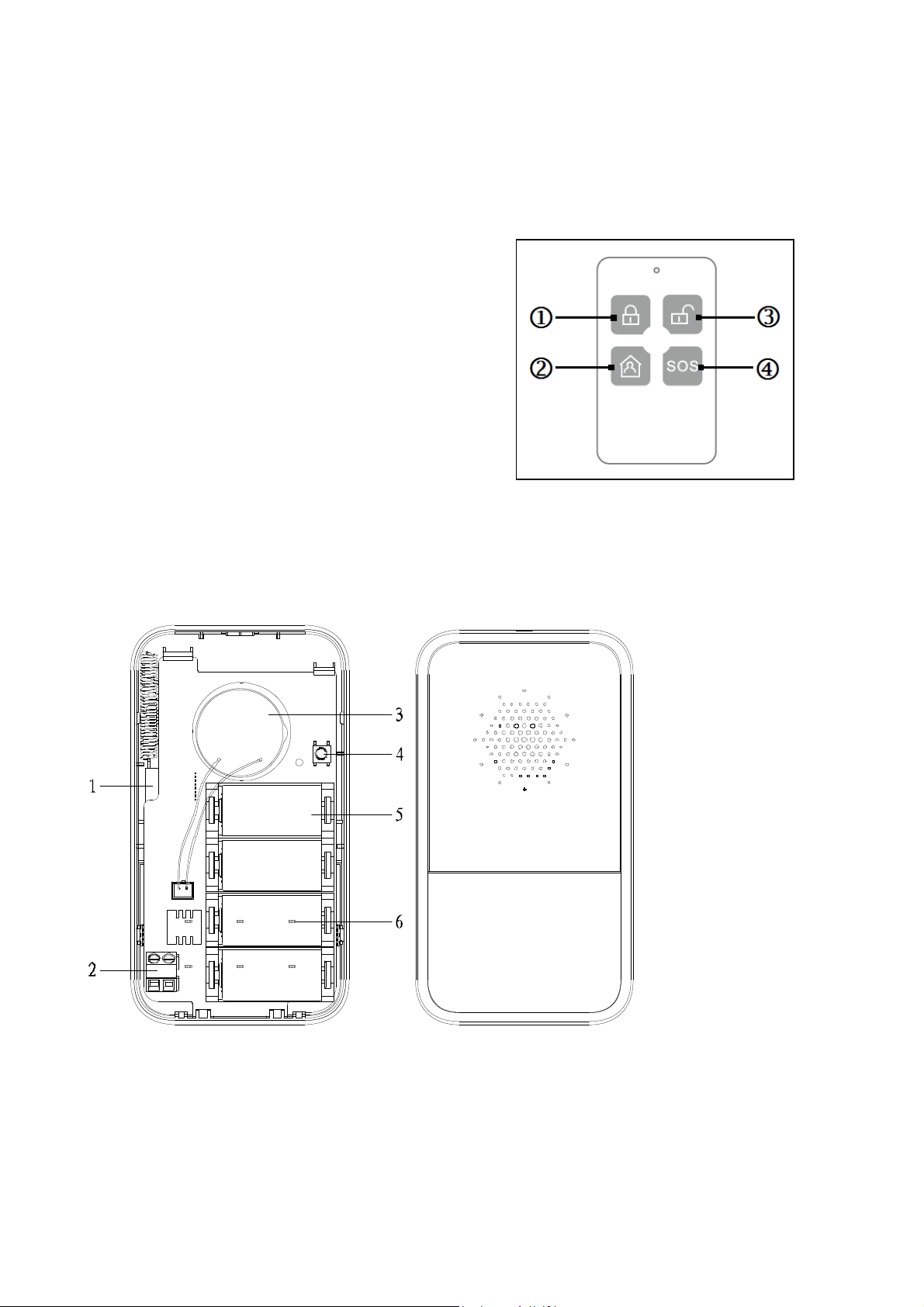
3.4 Remote Control SOS Button TX-87
With the Remote Control you can change the modus arm, disarm, stay at home or you can
activate the siren by pressing SOS. It is for home use. To easily disarm your alarm system
when you coming home or arming the alarm system when you leave (see Figure 3-4
below).
1 = Activate the alarm system (on the road)
2 = Home Mode (at home)
3 = Deaktivate the alarm system
4 = Manuel Alarm (emergency alarm)
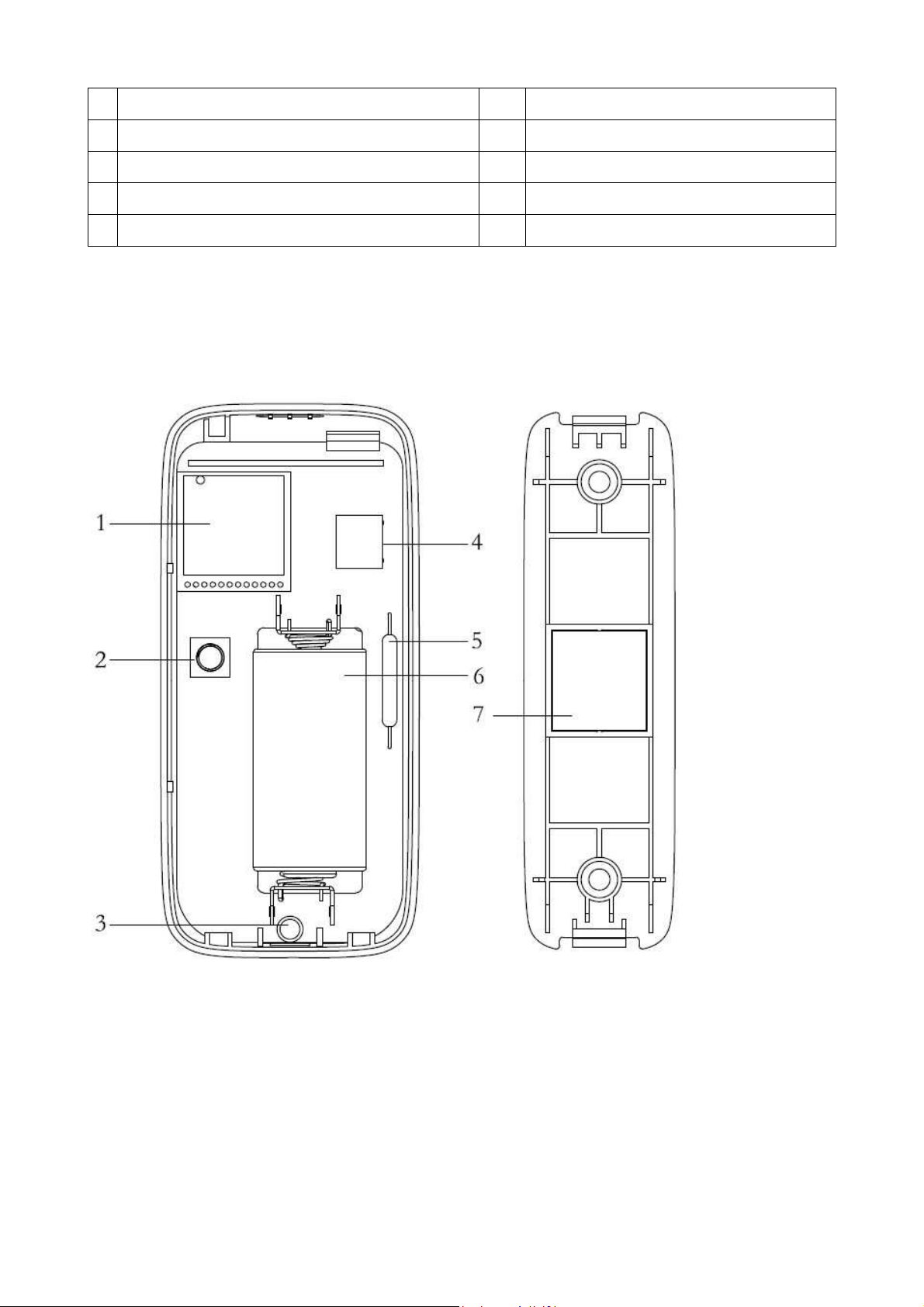
3.5 Alarm Siren TX-88
This wireless Siren is a device which can generate warning signal via sound and flash,
when activated. When someone enter the armed zone, detector outputs alarm signal to
wireless alarm Basis Station, and the Basis Station outputs control signal to the siren
wirelessly. It generates sound/flash signal for warning purpose.
Figure 3-5
1 = WiFi Module; 2 = DC 12V Power Adapter; 3 = Loudspeaker (Buzzer); 4 = Case
vandal-proof switch; 5 = Battery (Type CR123A); 6 = LED
7
Page 8
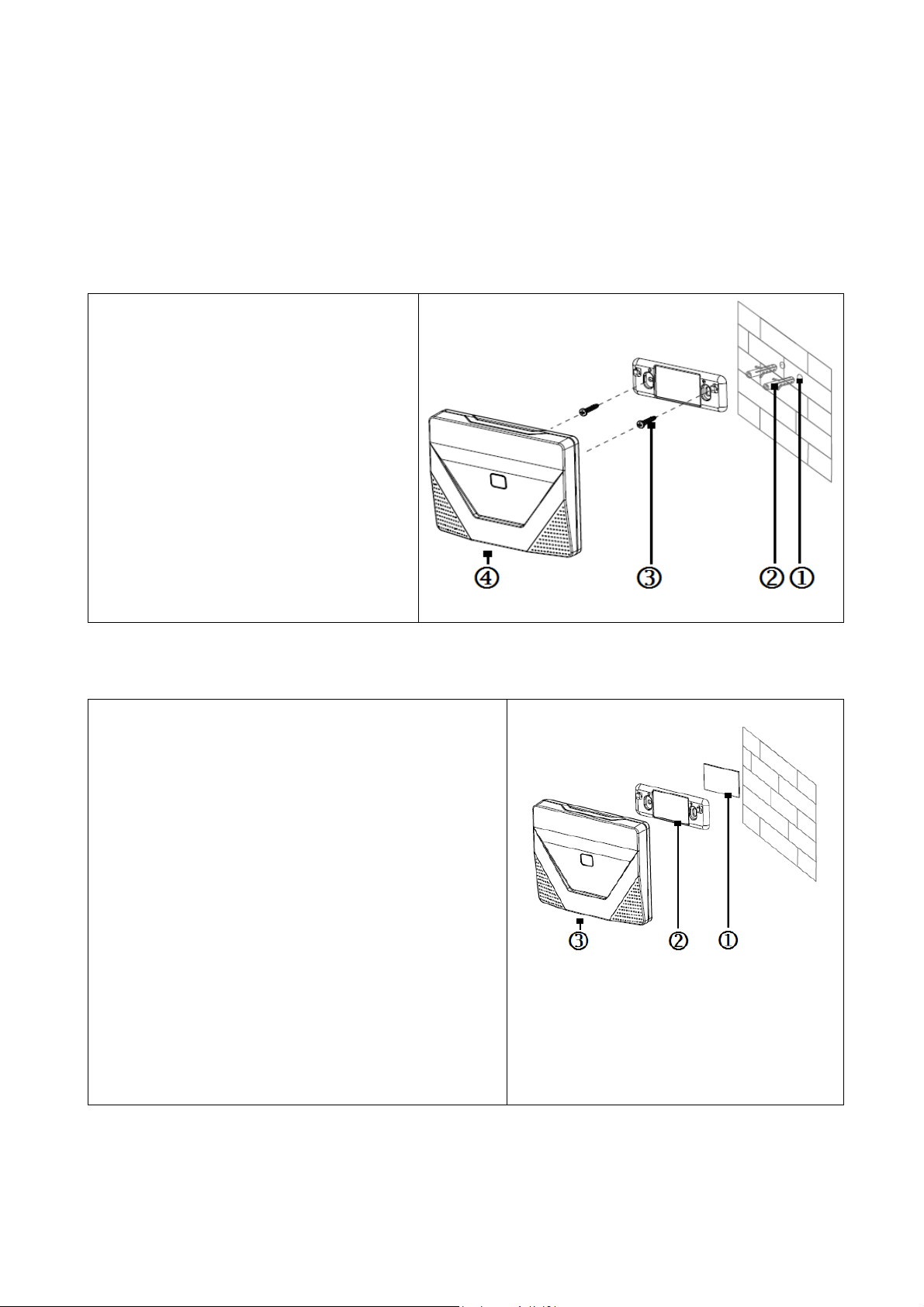
4 Product Mounting
Before fix mounting insert batteries, configure the device first and try it out. See
chapter 5.
4.1 WiFi Basis Station TX-91
Screw installation: If you want to mount the device make sure there is a power socket
nearby and the WiFi signal is good constantly.
Step 1. Dig holes according to
bracket position.
Step 2. Insert a dowel (=expansion
bolt) into the hole.
Step 3. Fix bracket via screw.
Step 4. Buckle the Basis Station into
bracket from top to bottom.
Double-sided adhesive tape Installation: If you want to mount the device make sure
there is a power socket nearby and the WiFi signal is good constantly.
Step 1. Before using the double-sided adhesive
tape* (*included), clean the flat surface you want
to stuck it on with nail polish remover or alcohol.
Attention: This can maybe cause damage to the
surface, but will increase the strength of the
connection
Step 2. Stick double-sided adhesive tape (not
included)r on the bracket.
Step 3. Stick the bracket on appropriate position
on wall (That you have cleaned before).
Step 4. Buckle Basis Station into bracket from
top to bottom.
Device is for indoor use only
Figure 4-1
Figure 4-2
8
Page 9
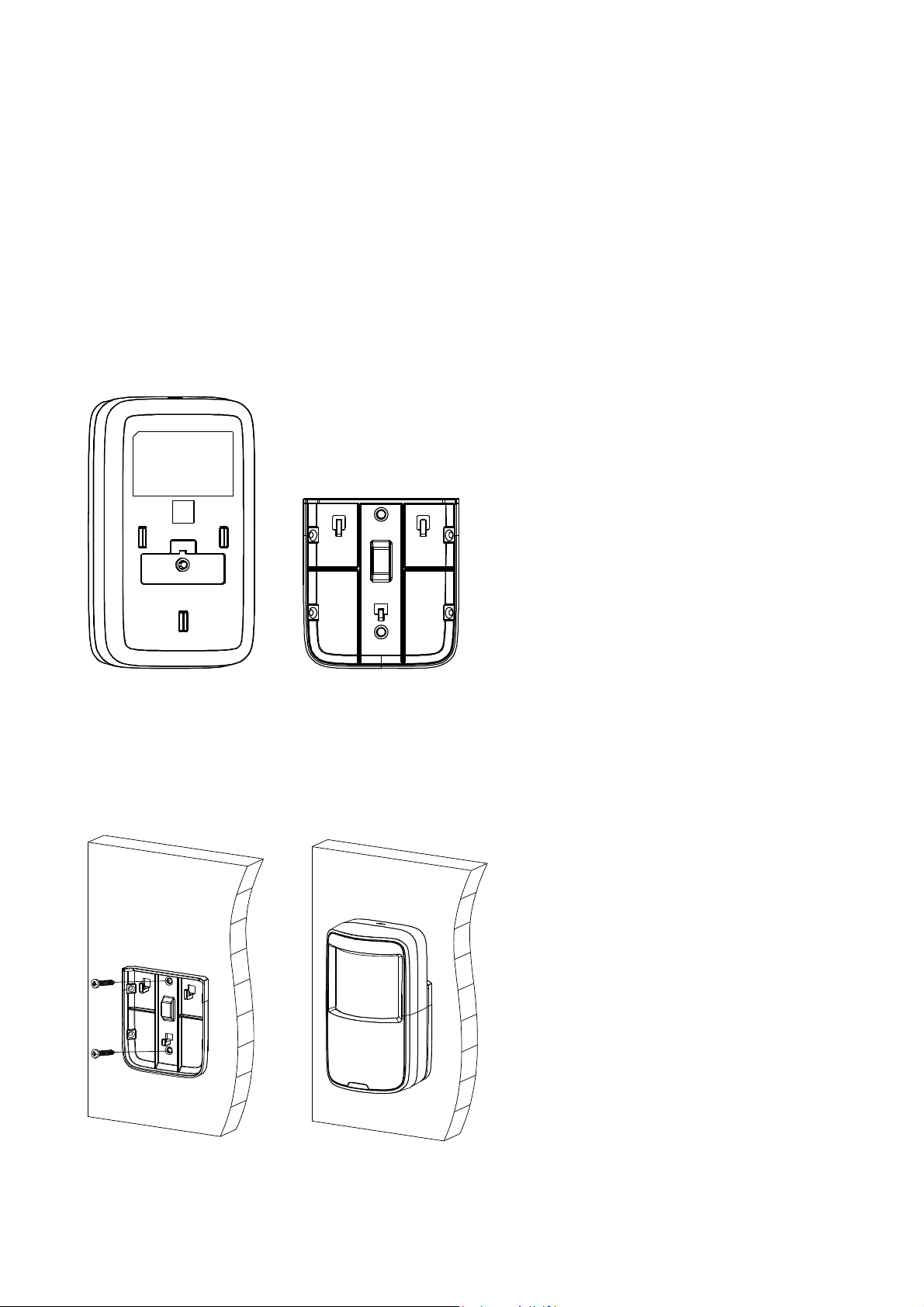
4.2 PIR Detection Sensor TX-85
Warnings: Installation and debugging must be executed by professional staff. If you
encounter device failure, please do not open and repair the device, you shall contact its
after-sales department. Avoid installation under direct sunlight. Avoid installation in
environment of rapid change in wind speed. Avoid installation in places where the
temperature is too high. Avoid installation in places with obstruction in the detection
range of the device. Avoid installation in places with a large amount of metal objects.
Device is for indoor use only
Steps of installation:
Step 1. The sensor should be mounted in about 2.1~2.5m height. Take down installation
bracket at the bottom back of detector; see Figure 4-3 below. (Left: PIR Sensor, Right:
Installation bracket)
Figure 4-3
Step 2. Drill through the fixing hole on installation bracket (for wall mount figure 4-4 or
corner mount figure 4-5).
Step 3. For wall mount, installation bracket bottom is parallel to the wall. Fix it on wall with 2
screws via the hole on installation bracket, and hang device on hanger on installation
bracket. See Figure 4-4.
Figure 4-4
9
Page 10
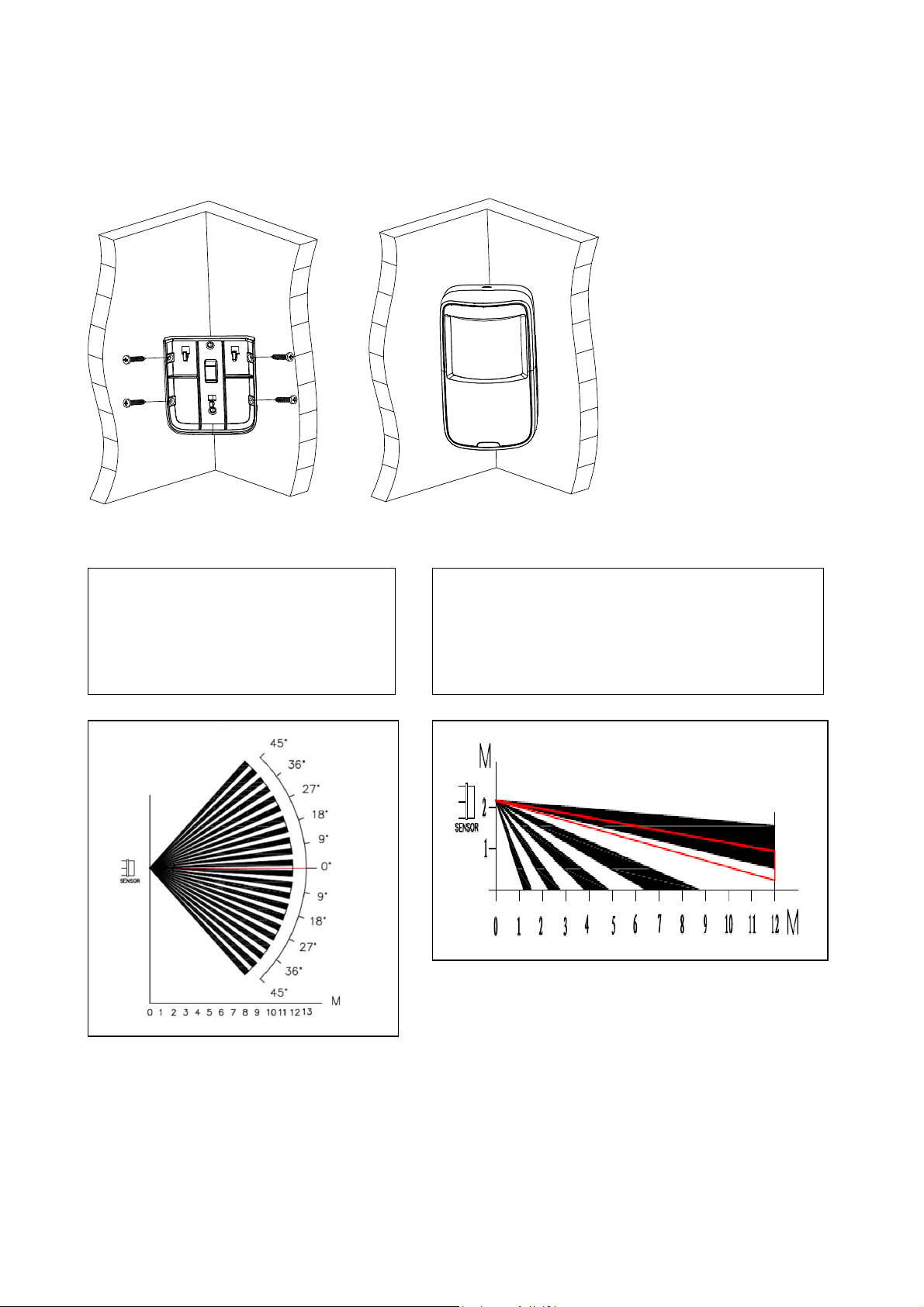
Step 4. For corner mount, form a triangle with installation bracket and two walls. Fix it on
wall with screws via the hole on installation bracket. Hang device on hanger on installation
bracket. See Figure 4-5.
Figure 4-5
Horizontal angle (range) of
detection 90°
(see Figure 4-6 below)
Detection distance is ~1m up to ~12m
( see Figure 4-7 below)
10
Page 11

4.3 Door & Window Contact TX-86
Warnings: Installation and debugging must be executed by professional staff. If you
encounter device failure, please do not open and repair the device, you shall contact its
after-sales department. Avoid installation in environment with large magnetic field around.
Avoid installation in places with a large amount of metal objects. Be careful with
direction of installation, and install the magnet on the rear side with arrow (back) of the
sensor. See Figure 4-8 (Right: Sensor; Left: Magnet).
Tip: We recommend double-sided adhesive tape (not included) form for installation.
Device is for indoor use only
Figure 4-8
1. Mounting by fixing with screw:
Step 1. Open device housing, follow Figure 4-9. Use straight screwdriver to take down
device rear cover. Remove the circuit board before you go one with step 2 or use 3M rubber
form as mounting option.
Step 2. Drill carefully the marked markings on the drill holes on thr rear side of the unit.
Draw the holes with a pencil. Make sure that the sensor and magnet are at a maximum of
2.5cm. If possible, the sensor and magnet should not have any misalignment, and they
should be as close as possible to one another without touching.
Figure 4-9
11
Page 12

Step 3. Follow Figure 4-10, pre-drill two holes on fixed part of door/window frame, and
pre-drill two holes on mobile part of door/window.
Step 4. Face device rear cover with bolt, insert and fasten the screws to fix the front covers.
Figure 4-10
2. Mounting by fixing with double-sided adhesive tape* (*included):
Step 1. Paste adhesive at back of the device, see Figure 4-11.
Step 2. Paste the sensor on the unmovable part of the door or the window, and the
magnetic contact on the movable part of the door or the window. Between sensor and
magnetic contact should only be 2.5cm distance. When device installation is complete. See
Figure 4-12
Figure 4-11 Figure 4-12
12
Page 13

4.4 Alarm Siren TX-88
Warnings: Installation and debugging must be executed by professional staff. If you
encounter device failure, please do not open and repair the device, you shall contact its
after-sales department. Avoid installation in environment with large magnetic field around.
Avoid installation in places with a large amount of metal objects. Device only for indoor
use.
Mounting by fixing with screw:
Step 1. Please open device package, follow Figure 4-13. Use straight screwdriver to take
down device rear cover.
Step 2. Follow Figure 4-14. Line the drill holes as shown in the figure or by attaching the
housing. Dig three holes on wall and insert one dowel in one hole each.
Device is for indoor use only
Figure 4-13
Figure 4-14
Step 3. Face device rear cover to expansion with bolts, install the screws at fasten the
coover to the positions (1) and (2) on wall. If you want to have leaving-wall vandal-proof
function for the device, insert a screw also at (3).
Step 4. Close device front cover component to complete.
13
Page 14

5 Start Use
5.1 WiFi Basis Station TX-91
Connect Power: Use the included power adapter and Micro USB cable to connect the
Basis Station with the AC socket.
Figure 5-1
Download the APP
Search for My Secure Pro APP, then download and start the APP.
Tips: Android user go to Google Play Store and search for My Secure Pro. Apple user goes
to Apple Store and search for My Secure Pro.
5.1.1 Connect Basis Station TX-91 to WIFI and add detector and siren to the Basis
Station
Step 1. Make sure the mobile phone is connected to WIFI (2.4GHz) and it has strong
signal.
Figure 5-2
Step 2. See figure 5-2. Open APP, click “Alarm” (1). Press + (2) to add new Alarm hub and
choose WiFi configuration (3).
14
Page 15

Step 3. Input Basis Station name (4), click the icon of QR code (5), and scan the QR code
on the back of the Basis Station. Username (6) and Password (7) are admin. Also enable
subscribe for getting Push Notifications (8). Click “Next” (9) after it is successfully
recognized, input WIFI password (10) (WiFi key of the router). See figure 5-4. STOP! Go on
with Step 4.
Step 4. (11) Long press the function key (No.2) of Basis Station for 6 seconds and the blue
LED flashes slowly. 1 = Power indicator; 2 = Function key
Figure 5-3
Figure 5-4
Step 5. Click “Next” (12) and the Basis Station begins to acquire WIFI info. The blue LED is
normally on and begins WIFI matching after it is successfully acquired. If APP says “added
successfully” (13), it means WIFI connection is successful, otherwise matching failed,
please repeat the above step. Tip: The longest duration for Basis Station to acquire WiFi
info can be 120 seconds.
15
Page 16

Step 6. To connect Detector & Siren with the Basis Station press function key of Basis
Station to enter the matching mode. Blue LED starts flashing. Now insert the battery into the
detector/siren you want to add. The Basis Station informs you with a beep that the
detector/siren is connected with the Basis Station. Same way for other detectors and sirens.
Matching mode will last for max. 120s or you turn it off by pressing function key of the Basis
Station again. To add. For adding remote control, see chapter 5.4. If you have any issues
follow the chapters below. Tip: For the first configuration of the Basis Station you use WiFi
configuration. After that you can use P2P connection and QR-code to add the Basis Station
of alarm system to other Smartphones.
5.1.2 Add Detector & Siren (TX-85, 86, 88)
In matching mode, it can add several detector and sirens in sequence. It is to realize
monitoring alarm when it is binded with Basis Station.
Step 1. Short press the function key of Basis Station to enter matching mode, then the blue
LED flashes quickly.
Step 2. Power on the detector/siren (by inserting battery or power input), auto enter
matching mode, it means it is successfully matched when the Basis Station gives off the
prompt tone of “beep”; otherwise the matching fails.
If matching fails, you can repeat the second step until it successfully matches, or you can
press the tamperproof switch by taking of the detector case and match manually.
Take wireless passive IR intrusion detector as an example, the location of tamperproof
switch is shown as follows: 1 = Case tamper proof switch
Figure 5-5
Tip: The matching process will last 120 seconds, after that it will auto exit matching mode,
the indicator light of the Basis Station becomes normally blue. You can press the function
key of the Basis Station to manually stop matching during the process.
16
Page 17

5.1.3 Clear Detector / Siren Matching Info
If the detector needs to be used with new Basis Station or restored factory default, you can
operate according to the following steps. Quickly press the tamperproof switch of the case
for 5 times, clear the config info of the detector/siren, restore to the initial status. The
indicator light will be normally on for 6s and then flash if it clears successfully.
Tip: The operation above can be used to fix malfunctions.
5.1.4 Add Remote Control TX-87
It is to arm/disarm and enable emergency alarm after binding remote controller and Basis
Station via matching mode.
Step 1. Short press the function key of Basis Station to enter matching mode, and then the
blue LED light flashes quickly.
Step 2. Long press any key of the wireless remote control for 2s, and then the Basis Station
gives off the prompt tone of “beep”, which means it is successfully matched, otherwise,
matching failed, please match again. See Figure 5-6 below.
1 = Activate the alarm system (on the road)
2 = Home Mode (if you are at home)
3 = Deaktivate the alarm system
4 = Manuel Alarm (Emergency alarm)
Tip: Enter match mode, you can add several wireless remote controllers. This process will
take 120 seconds, and then auto exit matching mode, the blue LED light is normally on.
During the matching process, press function key on the Basis Station to manually end
matching. Emergency Alarm is a manual alarm that activates the Basis Station and siren
alarm only.
5.1.5 Delete Detector, Siren or Remote Control
Method 1 (delete individually): In APP check accessory
details and press on delete disconnect the connection to the
Basis Station.
Method 2 (delete all in one): Press the RESET button of the
Basis Station for 6 seconds, when the device is powered on.
The Basis Station restarts and is restored to factory default
settings (see Figure 5-7 right hand side) 3 = RESET
17
Page 18

5.2 PIR Detection Sensor TX-85
1. Network: Before you can normally use PIR detector, you must match device with Basis
Station. Connection with Basis Station: Activate the paring mode at the Basis Station with
the function key and power on the detector. When red LED is blinking, dial the vandal-proof
switch and indicator is flashing. Wait about 10 sekonds. If the red LED turns OFF, the
matching is successful. If the indicator flashes for three times, the matching is failed. You
shall follow these steps and try again.
Note: If the detector has been matched to another alarm host, you cancel previous
matching by quickly dialing vandal-proof switch. (5 times within 1 second)
2. PIR Setup for advanced user
You can set the PIR sensitivity according to product usage environment or distance
requirement for sensor. For the PIN setting you can set two levels for position of plunger pin:
1&2 or 2&3; select 1&2 (1P) as level 1 pulse; select 2&3 (2P) as level 2 pulse. Default setup
is 1P. 1P sensor sensitivity is high while 2P sensor sensitivity is low. See Figure 5-8 below.
3. LED Setup for advanced user
The red ON/OFF LED shows the operating status.
See Figure 5-8 left hand side.
You can set two plans at the plunger pin: 1&2 or 2&3,
select 1&2 as LED OFF, select 2&3 as LED ON, default
setup is LED ON. See Figure 5-6.
Note: This operation does not influence normal
operation of detector
4. Installation Test
You can test working status of detector: Within detection range of the detector, walk at the
rate about step speed to trigger the detector. The red indicator shines ON for 2 seconds,
which means the PIR sensor is triggered, and detector enters alarm status. It outputs alarm
signal and a PUSH notification is send to the Smartphone.
Note: If you have deactivated LED via the PIN configuration, the LED does not (!) shine for
2 seconds red.
18
Page 19

5.3 TX-86 Door and Window Contact
Before you can normally use Door/Window Contact you must match device with Basis
Station.
Connection with Basis Station: Activate the paring mode at the Basis Station with the
function key and power on the detector. When red LED is blinking, dial vandal-proof switch
and indicator is flashing. Wait about 10 seconds. If the red LED is OFF, the matching is
successful. If the indicator flashes for three times, the matching is failed. You shall follow
these steps and try again.
Note: If the detector has been matched to other alarm host, you cancel previous matching
by quickly dialing vandal-proof switch. (5 times within 1 second)
5.4 Remote Control SOS Button TX-87
For adding the remote and button configuration see chapter 5.1.4 Add Remote Control
TX-87.
5.5 Alarm Siren TX-88
Before you can normally use Siren, you must match device with Basis Station.
Connection with Basis Station:
Activate the paring mode at the Basis Station with the function key and power on the
detector.
When red LED is blinking, dial vandal-proof switch and indicator is flashing. Wait about 10
seconds. If the red LED is OFF, the matching is successful. If the indicator flashes for three
times, the matching is failed. You shall follow these steps and try again.
Note: If the detector has been matched to other alarm host, you cancel previous matching
by quickly dialing vandal-proof switch. (5 times within 1 second).
19
Page 20

6 My Secure Pro APP
On the main menu choose Alarm. After you have added the Basis Station TX-91 like in
chapter 5.1.1 Connect the Basis Station TX-91 to WIFI and add detector and siren to the
Basis Station you have the following options.
6.1 Basis Station Alarm
6.1.1 Select and set mode (Stay, Away, Custom & Disarm)
Figure 6-1
Stay When you are at home, press “Stay” than the alarm system is disarmed. A
short beep of the Basis Station shows that the mode is activated/ changed.
Away When you leave home, press “Away” the Basis Station starts to beep. After
the last beep the countdown is over and the Alarm system is armed. Now
door contact and PIR-sensor will activate the Basis Station and the Siren.
Custom When you activate “Custom” it is possible to set selected detector as
activated.
You stay e.g. at home and still want to activate all Door/Window contacts.
Then under „Custom“ activate all Door/Window contacts. In this case the
PIR sensors will not trip, and you can move freely in the house/flat, as long
as you do not open any door or window.
Disarm When the alarm system is triggered while you are away or at home and
want to stop the buzzer of Basis Station and siren, press “Disarm”. Now
the alarm system is deactivated.
20
Page 21

Setting
(Gear)
Audio Setting
(loudspeaker)
Tip: The alarm tone (buzzer) of Basis Station and siren can temporarily deactivated by
pressing on the function key of the Basis Station. Attention: After pressing the function key
is flashing blue. While the functions key is flashing blue no detector trigger is recognized.
Press functions key again to stop function key flashing blue. The function key must remain
permanently blue to ensure the detection of the detectors.
6.1.2 Setting of Detector & Siren
Press on the symbol of detector or siren you want to set. See Figure 6-2. below
Select for the different mode (Stay, Away, Custom and Disarm) which
detector should be activated.
Set the volume of the base station’s alarm tone. Set the volume of the
base station beteween mute, silent or loud. Note: this setting does not
affect the volume of the siren.
Siren
Door
contact
Name: Set name of the device.
Save: Press the disk on the top right corner on display.
Delete: The siren is disconnected from the Basis Station, until you
reconnect the device. See chapter 5.1.2 Add Detector & Siren.
Name: Set name of the device.
Link Device: Select a device (camera or door phone). The live view of
the selected device will be shown when you open the push
notification.
Enable Siren: When the door contact is triggered the siren will be
activated. If you disable that function siren will not buzz or flash, when
the device is triggered.
Preview Link Device Video: Pressing this button shows you the live
view of the selected device that was chosen under “Link Device”.
Save: Press the disk on the top right corner on display.
Delete: The siren is disconnected from the Basis Station, until you
reconnect the device. See chapter 5.1.2 Add Detector & Siren.
21
Page 22

PIR
Remote
Name: Set name of the device.
Link Device: Select a device (camera or door phone). The live view of
the selected device will be shown when you open the push
notification.
Enable Siren: When the PIR Sensor is triggered the siren will be
activated. If you disable that function siren will not buzz or flash, when
the device is triggered.
Preview Link Device Video: Pressing this button shows you the live
view of the selected device that was chosen under “Link Device”.
Save: Press the disk on the top right corner on display.
Delete: The siren is disconnected from the Basis Station, until you
reconnect the device. See chapter 5.1.2 Add Detector & Siren.
Name: Set name of the device.
Link Device: Select a device (camera or door phone). The live view of
the selected device will be shown when you open the push
notification.
Enable Siren: When you press SOS button the siren will be activated.
If you disable that function siren will not buzz or flash, when the device
is triggered.
Preview Link Device Video: Pressing this button shows you the live
view of the selected device that was chosen under “Link Device”.
Save: Press the disk on the top right corner on display.
Delete: The siren is disconnected from the Basis Station, until you
reconnect the device. See chapter 5.1.2 Add Detector & Siren.
6.1.3 Change view of detector & siren list
By swiping down at the alarm Basis Station interface beneath the selected mode (Stay,
Away, Custom or Disarm) you can choose between two modes. 1. option is to display the
detector with their symbols. 2. option is to display the detector in a list (Figure 6-3 below)
22
Page 23

Tip: When you want to refresh the detector list or the mode, just swipe to the bottom. The
following symbols can be shown in front of the device name:
the battery status of that device is low. Need to change the battery (CR123A 3V). If the
battery gets low you will receive a push notification.
the device is offline. Reasons can be that the distance between Basis Station and
detector/sensor is too big, there are interferences that interrupt the signal or battery is
empty. If the device is offline you will receive a push notification
6.1.4 Alarm Basis Station (Hub) Manager
By clicking on a connected device there are two options (see Figure 6-4).
Figure 6-4
Modify (pencil)
Delete (trashcan) Delete the device from the APP. To reconnect see chapter 5.1.1
Name: Set name of the device.
Username: Enter Username of device. Default is admin.
Password: Enter password of device. Default is admin.
Subscribe: Enable this option to get push notifications when alarm is
triggered.
Save: Press the disk on the top right corner.
View Alarm Basis Station: Go to back to the device, with saving
settings.
Connect Basis Station.
23
Page 24

6.2 Event List
See the push notifications in the event list that alarmed you of motion in your home (see
Figure 6-5 below).
Alarm Device / Function
Tamper alarm Door contact, PIR motion detector, Siren: When the detector is
removed from the wall or its bracket, or when the chassis is opened,
the base station sends a push notification to the Smartphone. If you
set under chapter 6.1.2 for Link device a camera or a door phone you
will get through pressing on the event to the live view of the selected
device.
Intrusion Door contact, PIR sensor: When the detector is triggered, the base
station sends a push notification to the Smartphone If you set under
chapter 6.1.2 for Link device a camera or a door phone you will get
through pressing on the event to the live view of the selected device.
Offline Door contact, PIR sensor, Siren / Indicates that the device has lost
connection to Basis Station. Reason: Distance between Basis Station
& Sensor too long or the interference is too strong. Solution: Install
device closer to the Basis Station or reposition the Basis Station so
that all devices (sensor, detector, siren) have nearly same distance to
the Basis Station. Do not forget that the Basis Stationo still has to be
in the WiFi range of your router.
24
Page 25

Low battery
status
Emergency alarm SOS button of the remote was triggered. / If you set under chapter
Door contact, PIR sensor, Siren / Indicates that a battery change of
the device is needed.
6.1.2 for Link device a camera or a door phone you will get through
pressing on the event to the live view of the selected device.
6.3 Local Files
Under local flies you see manual taken snapshots and records of the camera or door phone
you connected with the PIR sensor or the Door contact. See chapter 6.1.2 Setting of
Detector & Siren (see Figure 6-6).
Figure 6-6
Tip: With the pencil on to top right corner on display you can modify snapshot or record.
The options depend on the Smartphone you are using. Also you can delete the selected
snapshot or record here.
25
Page 26

7 Change batteries of devices
The Basis Station will send you a Push message when the battery status of a device is low.
You will see a low battery status notification in the event list of your Smartphone. On the
main screen you will see a small battery sign next to the device.
For TX-85, TX-86 and TX-88 it is necessary to use CR123A 3V batteries. Open the device
with a flat cross-screwdriver and switch the old battery with the new one. Normally device
should reconnect automatically. If not activate the pairing mode of the Basis station and
then insert a new battery. If this does not work, the device has to be added again according
to chapter 5.1.2.
For TX-87 it is necessary to use CR2032 3V button cell battery. Change the battery by
using a screwdriver to remove the little screw on the back. Take a flat screwdriver carefully
into the gap of the housing to open it.
8 FAQ
Q: I cannot boot up intelligent alarm Basis Station? A: Please check device input power.
Q: After alarm is triggered, my mobile phone client did not receive push? A1: Please check
if network connection of Basis Station or router is normal. A2: Check to see whether the
Alarm Alert Manager is enabled in the APP “Subscribe Alert”.
Q: I failed to match accessory. A: The accessory may have the following problems: low
battery, other device has been connected, distance is too far (exceeding valid range).
Q: Accessory is triggered without any response. A: The accessory may have the following
problems: low battery, detector offline, exceed accessory detection range.
9 Technical Specification
9.1 WiFi Basis Station TX-91
Main process & OS Embedded Micro controller & Linux OS
Encryption basis station Sensor: 128bit-AES Encryption Algorithm
up to 32 detectors (868MHz)
Wireless connections
Audio output Built-in loudspeaker (alarm tone only)
WiFi protocol IEEE802.11b/g/n, distance ~25m
Power supply (Micro USB) DC 5V/ 2A, max 10W
Working temperature –10°C up to +50°C
Installation Wall mounting, indoor only
Weight & Dimensions 96g / (L) 9.4x (W) 11.4 x (H) 1.8cm
up to 6 remote controls
transmission distance ~10m (open areas)
26
Page 27

9.2 PIR Detection Sensor TX-85
,
Transmission frequency / power / distance 868MHz / 10dBm / ~200m (open areas)
Detection range / Method
Viewing angle horizontal 90° & vertical 70°
Alarm prompt Red LED (LED can be set off)
Sensitivity Two level (jumper cap) high or low
Power input DC 3V/50mA
Power supply 1x CR123A battery 3V
Vandal-proof Case and Wall
Installation
Working conditions –10°C ~ +50°C / < 95% RH
Weight / Dimensions 76g (without battery) / (L) 10.5 x (W) 6.2 x (H) 4.2cm
~12m / passive infrared
(not visible 6500 LUX illumination)
(H) ~2.1–2.5m, Wall or corner (indoor only), with bracket
screws or adhesive tape
9.3 WiFi Door and Window Contact TX-86
Transmission frequency / power / distance 868MHz / 10dBm / ~200m (open areas)
Distance sensor to magnet 1mm – 25mm
Alarm prompt Red LED
Power input DC 3V/50mA
Power supply 1x CR123A battery 3V
Vandal-proof Case and Wall
Installation Fixed with screws or adhesive tape, indoor only
Working conditions –10°C ~ +50°C / < 95% RH
Weight / Dimensions Sensor 33g (without battery) / (L) 8.3 x (W) 3.8 x (H) 2.0cm
Weight / Dimensions Magnet 34g / (L) 8.3 x (W) 2.5 x (H) 2.0cm
9.4 Remote Control SOS Button TX-87
Transmission frequency 3.15MHz min. / 868MHz regular / 915MHz max.
Transmission power 9.2dBm min. / 9.6dBm regular / 10dBm max.
Transmission distance ~10m open areas
Power supply 1x CR2032 battery 3V
Low consumption, current under standby <10nA
Working voltage 1.8V min. / 3.0V regular / 3.6V max.
Data transmission rate 100Kbps max.
Transmission current +10dBm 3.0V / 18.9mA min. / 19.8mA regular / 21mA max.
Data rate (FSK modulation) Min. 0.1Kbps / Regular 4.8Kbps / Max. 100Kbps
Working temperature –10° ~ +50°C
Protection class IP20 (protection against small parts from Ø 12.5mm, not waterproof)
Dimension 20g (with battery) / (L) 6.2 x (W) 3.0 x (H) 1.4cm
27
Page 28

9.5 WiFi Alarm Siren TX-88
Transmission frequency / power / distance 868MHz / 10dBm / ~200m (open areas)
Sound Intensity 85dB (within 1m distance)
Power input batteries DC 12V/200mA
Power supply 4x CR123A battery 3V
Vandal-proof Case and Wall
Working conditions –10°C ~ +50°C / < 95% RH
Installation Wall mounting (indoor only)
Weight & Dimensions 140g (without batteries) / (L) 11.3 x (W) 7.2 x (H) 3.0cm
Important Safeguards and Warnings
Do not expose the device to lampblack, steam or dust. Otherwise it may cause fire or
electric shock. Do not install the device at position exposed to sunlight or in high
temperature. Temperature rise in device may cause fire. Do not expose the device to
humid environment. Otherwise it may cause fire. The device must be installed on solid
and flat surface in order to guarantee safety under load and earthquake. Otherwise, it may
cause device to fall off or turnover. Do not place the device on carpet or quilt. Do not
block air vent of the device or ventilation around the device. Otherwise, temperature in
device will rise and may cause fire. Do not place any object on the device. Do not
disassemble the device without professional instruction. Use battery properly to avoid fire,
explosion and other dangers. Replace used battery with battery of the same type. Do not
use power line other than the one specified. Use it properly. Otherwise, it may cause fire or
electric shock.
Security and Disposal Hints for Batteries: Hold children off batteries.
When a child swallowed a battery go to a doctors place or bring the child
into a hospital promptly! Look for the right polarity (+) and (–) of batteries!
Always change all batteries. Never use old and new batteries or batteries of
different types together. Never short, open, deform or load up batteries!
Risk of injury! Never throw batteries into fire! Risk of explosion!
Hints for Environment Protection: Packages materials are raw materials
and can be recycled. Do not disposal old devices or batteries into the
domestic waste. Cleaning: Protect the device from contamination and
pollution (use a clean drapery). Avoid using rough, coarse-grained
materials or solvents/aggressive cleaner. Wipe the cleaned device
accurately. Distributor: Technaxx Deutschland GmbH & Co.KG, Kruppstr.
105, 60388 Frankfurt a.M., Germany
28
Page 29

This product includes software developed by third parties, including software which
is released under the GNU General Public License Version 2 (GPL v2). This program
is free software; you can redistribute it and/or modify it under the terms of the GNU
General Public License as published by the Free Software Foundation; either version
2 of the License, or (at your option) any later version. You may obtain a complete
machine-readable copy of the source code for the above mentioned software under
the terms of GPL v2 without charge except for the cost of media, shipping, and
handling, upon written request to Technaxx GmbH & Co. KG, Kruppstraße 105, 60388
Frankfurt am Main, Germany.
This program is distributed in the hope that it will be useful, but WITHOUT
ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or
FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for
more details. You should have received a copy of the GNU General Public License
along with this program; if not, write to the Free Software Foundation, Inc., 51
Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA. (Notice from Technaxx: A
copy of the GPL is included below).
GNU GENERAL PUBLIC LICENSE: Version 2, June 1991 / Copyright (C) 1989, 1991
Free Software Foundation, Inc. / 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301,
USA. Everyone is permitted to copy and distribute verbatim copies of this license document,
but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and
change it. By contrast, the GNU General Public License is intended to guarantee your
freedom to share and change free software--to make sure the software is free for all its
users. This General Public License applies to most of the Free Software Foundation's
software and to any other program whose authors commit to using it. (Some other Free
Software Foundation software is covered by the GNU Lesser General Public License
instead.) You can apply it to your programs, too. When we speak of free software, we are
referring to freedom, not price. Our General Public Licenses are designed to make sure that
you have the freedom to distribute copies of free software (and charge for this service if you
wish), that you receive source code or can get it if you want it, that you can change the
software or use pieces of it in new free programs; and that you know you can do these
things. To protect your rights, we need to make restrictions that forbid anyone to deny you
these rights or to ask you to surrender the rights. These restrictions translate to certain
responsibilities for you if you distribute copies of the software, or if you modify it. For
example, if you distribute copies of such a program, whether gratis or for a fee, you must
give the recipients all the rights that you have. You must make sure that they, too, receive or
can get the source code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this
license which gives you legal permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone
understands that there is no warranty for this free software. If the software is modified by
someone else and passed on, we want its recipients to know that what they have is not the
original, so that any problems introduced by others will not reflect on the original authors'
reputations.
avoid the danger that redistributors of a free program will individually obtain patent licenses,
in effect making the program proprietary. To prevent this, we have made it clear that any
Any free program is threatened constantly by software patents. We wish to
29
Page 30

patent must be licensed for everyone's free use or not licensed at all.
and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the
copyright holder saying it may be distributed under the terms of this General Public License.
The "Program", below, refers to any such program or work, and a "work based on the
Program" means either the Program or any derivative work under copyright law: that is to
say, a work containing the Program or a portion of it, either verbatim or with modifications
and/or translated into another language. (Hereinafter, translation is included without
limitation in the term "modification".) Each licensee is addressed as "you". Activities other
than copying, distribution and modification are not covered by this License; they are outside
its scope. The act of running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the Program (independent of
having been made by running the Program). Whether that is true depends on what the
Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive
it, in any medium, provided that you conspicuously and appropriately publish on each copy
an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that
refer to this License and to the absence of any warranty; and give any other recipients of the
Program a copy of this License along with the Program. You may charge a fee for the
physical act of transferring a copy, and you may at your option offer warranty protection in
exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a
work based on the Program, and copy and distribute such modifications or work under the
terms of Section 1 above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the
files and the date of any change. b) You must cause any work that you distribute or publish,
that in whole or in part contains or is derived from the Program or any part thereof, to be
licensed as a whole at no charge to all third parties under the terms of this License. c) If the
modified program normally reads commands interactively when run, you must cause it,
when started running for such interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a notice that there is no
warranty (or else, saying that you provide a warranty) and that users may redistribute the
program under these conditions, and telling the user how to view a copy of this License.
(Exception: if the Program itself is interactive but does not normally print such an
announcement, your work based on the Program is not required to print an announcement).
These requirements apply to the modified work as a whole. If identifiable sections of that
work are not derived from the Program, and can be reasonably considered independent and
separate works in themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you distribute the same
sections as part of a whole which is a work based on the Program, the distribution of the
whole must be on the terms of this License, whose permissions for other licensees extend to
the entire whole, and thus to each and every part regardless of who wrote it. Thus, it is not
the intent of this section to claim rights or contest your rights to work written entirely by you;
rather, the intent is to exercise the right to control the distribution of derivative or collective
works based on the Program. In addition, mere aggregation of another work not based on
The precise terms
30
Page 31

the Program with the Program (or with a work based on the Program) on a volume of a
storage or distribution medium does not bring the other work under the scope of this
License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in
object code or executable form under the terms of Sections 1 and 2 above provided that you
also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which
must be distributed under the terms of Sections 1 and 2 above on a medium customarily
used for software interchange; or, b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your cost of physically performing
source distribution, a complete machine-readable copy of the corresponding source code, to
be distributed under the terms of Sections 1 and 2 above on a medium customarily used for
software interchange; or, c) Accompany it with the information you received as to the offer to
distribute corresponding source code. (This alternative is allowed only for noncommercial
distribution and only if you received the program in object code or executable form with such
an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to
it. For an executable work, complete source code means all the source code for all modules
it contains, plus any associated interface definition files, plus the scripts used to control
compilation and installation of the executable. However, as a special exception, the source
code distributed need not include anything that is normally distributed (in either source or
binary form) with the major components (compiler, kernel, and so on) of the operating
system on which the executable runs, unless that component itself accompanies the
executable. If distribution of executable or object code is made by offering access to copy
from a designated place, then offering equivalent access to copy the source code from the
same place counts as distribution of the source code, even though third parties are not
compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly
provided under this License. Any attempt otherwise to copy, modify, sublicense or distribute
the Program is void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under this License will not
have their licenses terminated so long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However,
nothing else grants you permission to modify or distribute the Program or its derivative
works. These actions are prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the Program), you indicate your
acceptance of this License to do so, and all its terms and conditions for copying,
distributing/modifying the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient
automatically receives a license from the original licensor to copy, distribute or modify the
Program subject to these terms and conditions. You may not impose any further restrictions
on the recipients' exercise of the rights granted herein. You are not responsible for enforcing
compliance by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any
other reason (not limited to patent issues), conditions are imposed on you (whether by court
order, agreement or otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot distribute so as to satisfy
simultaneously your obligations under this License and any other pertinent obligations, then
31
Page 32

as a consequence you may not distribute the Program at all. For example, if a patent license
would not permit royalty-free redistribution of the Program by all those who receive copies
directly or indirectly through you, then the only way you could satisfy both it and this License
would be to refrain entirely from distribution of the Program.
held invalid or unenforceable under any particular circumstance, the balance of the section
is intended to apply and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property
right claims or to contest validity of any such claims; this section has the sole purpose of
protecting the integrity of the free software distribution system, which is implemented by
public license practices. Many people have made generous contributions to the wide range
of software distributed through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing to distribute software
through any other system and a licensee cannot impose that choice. This section is intended
to make thoroughly clear what is believed to be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by
patents or by copyrighted interfaces, the original copyright holder who places the Program
under this License may add an explicit geographical distribution limitation excluding those
countries, so that distribution is permitted only in or among countries not thus excluded. In
such case, this License incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General
Public License from time to time. Such new versions will be similar in spirit to the present
version, but may differ in detail to address new problems or concerns. Each version is given
a distinguishing version number. If the Program specifies a version number of this License
which applies to it and "any later version", you have the option of following the terms and
conditions either of that version or of any later version published by the Free Software
Foundation. If the Program does not specify a version number of this License, you may
choose any version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose
distribution conditions are different, write to the author to ask for permission. For software
which is copyrighted by the Free Software Foundation, write to the Free Software
Foundation; we sometimes make exceptions for this. Our decision will be guided by the two
goals of preserving the free status of all derivatives of our free software and of promoting the
sharing and reuse of software generally.
NO WARRANTY
11. Because the program is licensed free of charge, there is no warranty for the program, to
the extent permitted by applicable law. Except when otherwise stated in writing the
Copyright holder and/or other parties provide the program "AS IS" without warranty of any
kind, either expressed or implied, including, but not limited to, the implied warranties of
merchantability and fitness for a particular purpose. The entire risk as to the quality and
performance of the program is with you. Should the program prove defective, you assume
the cost of all necessary servicing, repair or correction.
12. In no event unless required by applicable law or agreed to in writing will any Copyright
holder, or any other party who may modify and/or redistribute the program as permitted
above, be liable to you for damages, including any general, specia, incidental or
consequential. Damages arising out of the use or inability to use the program (including but
not limited to loss of data or data being rendered inaccurate or losses sustained by you or
If any portion of this section is
32
Page 33

third parties or a failure of the program to operate with any other programs), even if such
holder or other party has been advised of the possibility of such damages.
END OF TERMS AND CONDITIONS
HOW TO APPLY THESE TERMS TO YOUR NEW PROGRAMS
(1) If you develop a new program, and you want it to be of the greatest possible use to the
public, the best way to achieve this is to make it free software which everyone can
redistribute and change under these terms.
(2) To do so, attach the following notices to the program. It is safest to attach them to the
start of each source file to most effectively convey the exclusion of warranty; and each file
should have at least the "copyright" line and a pointer to where the full notice is found.
<one line to give the program's name and an idea of what it does.>
Copyright (C) <yyyy> <name of author>
(3) This program is free software; you can redistribute it and/or modify it under the terms of
the GNU General Public License as published by the Free Software Foundation; either
version 2 of the License, or (at your option) any later version.
(4) This program is distributed in the hope that it will be useful, but WITHOUT ANY
WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A
PARTICULAR PURPOSE. See the GNU General Public License for more details.
(5) You should have received a copy of the GNU General Public License along with this
program; if not, write to the Free Software Foundation Inc; 51 Franklin Street, Fifth Floor,
Boston, MA 02110-1301, USA.
(6) Also add information on how to contact you by electronic and paper mail.
(7) If the program is interactive, make it output a short notice like this when it starts in an
interactive mode: Gnomovision version 69, Copyright (C) year name of author Gnomovision
comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
(8) This is free software, and you are welcome to redistribute it under certain conditions; type
`show c' for details.
(9) The hypothetical commands `show w' and `show c' should show the appropriate parts of
the General Public License. Of course, the commands you use may be called something
other than `show w' and `show c'; they could even be mouse-clicks or menu items--whatever
suits your program.
(10) You should also get your employer (if you work as a programmer) or your school, if any,
to sign a "copyright disclaimer" for the program, if necessary. Here is a sample; alter the
names:
(11) Yoyodyne, Inc., hereby disclaims all copyright interest in the program `Gnomovision'
(which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989 [Ty Coon, President of Vice]
33
 Loading...
Loading...