Page 1

DEFCON
Notebook Computer Key Lock
™
KL
Page 2

Targus DEFCON™ KL
Thank you for purchasing the Targus DEFCON KL
Notebook Computer Key Lock. The cut and tamperresistant DEFCON KL helps protect your valuable notebook
computer from theft.
In addition to this user’s guide, this package contains:
• DEFCON KL Notebook Computer Key Lock
• Two keys
If you are missing any parts, contact Technical
Support immediately. For more information, refer to
“Technical Support” on page 7.
Registering the DEFCON KL
Registering the DEFCON KL enables you to order
extra or replacement keys more efficiently by
recording all of the information necessary to order
keys, including the DEFCON KL key code.
To register, go to:
http://www.targususa.com/accessories/DefconKL.htm
You will need to provide your name, email address,
phone number, DEFCON KL key code, and a
password.
Once you register, you can order keys at any time by
contacting Technical Support. For more information,
refer to “Ordering Replacement Keys” on page 7.
2
Locating the Key Code
The DEFCON KL key code is located on the key,
under the cover. For your convenience, record the key
code in the space provided at the end of this guide.
Page 3
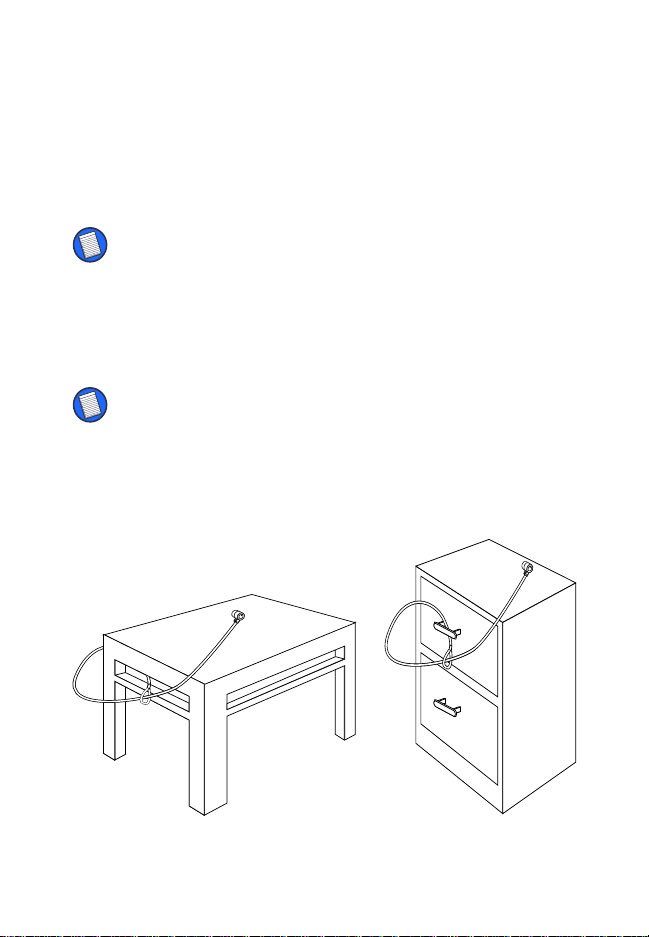
Using the DEFCON KL
Securing the DEFCON KL
Select an object in the room to which you will secure
your notebook computer with the DEFCON KL.
NOTE: Choose a large, heavy piece of furniture such as a
table or desk, or an immovable fixture such as a closet
hanging bar.
1 Take the looped end of the cable and wrap it
around the selected object.
NOTE: Wrap the cable around a part of the object that will
deter an intruder from slipping the cable off (for example, a
table or desk leg with a cross bar or a drawer handle).
2 Feed the locking device through the looped end
of the cable as shown.
3
Securing the DEFCON KL to an object
Page 4

Locking the DEFCON KL to your Notebook Computer
1 Check that the locking teeth are aligned in the
unlocked position and then insert the key using
slight pressure to depress the tumbler pins inside
the locking device.
Locking
teeth
DEFCON KL unlocked
NOTE: If the locking teeth are in the locked position, unlock
the DEFCON KL using the key. For more information, refer
to “Unlocking the DEFCON KL” on page 5.
4
2 Insert the locking device into your notebook
computer’s lock slot.
3 Turn the key counterclockwise, about 90
degrees, to activate the locking device.
Page 5

Unlocking the DEFCON KL
WARNING: Do not attempt to remove the DEFCON KL
without using the key. To do so will physically damage
your notebook computer.
1 Line up the guide bar on your key with the guide
notch on the locking device and insert the key
using slight pressure to depress the tumbler pins
inside the locking device.
NOTE: Hold the DEFCON KL with one hand while inserting
the key for additional stability.
Guide notch
Guide bar
5
Inserting the key into the DEFCON KL
2 Turn the key clockwise, about 90 degrees, to
align the locking teeth.
NOTE: You will hear a click when the locking teeth are
aligned.
3 Remove the DEFCON KL from your notebook
computer’s lock slot.
Page 6

Specifications
General
Weight: 5.5 ounces (157 g) overall
Locking Device
Dimension: 0.95 x 0.88 inches
24.3 x 22.5 mm
Diameter: 0.84 inches (21.4 mm)
Color: Black Nickel
Material: Steel alloy
Cable
Length: 6 foot (1.83 m)
Diameter: 0.16 inches (4 mm)
Material: Vinyl coated steel
Warranty
Targus warrants Targus accessories to be free from defects
in material and workmanship for one year. If your Targus
accessory is found to be defective within that time, we will
promptly repair or replace it. This warranty does not cover
accidental damage, wear and tear, or consequential or
incidental loss. Under no conditions is Targus liable for loss
of, or damage to, a computer; nor loss of, or damage to,
programs, records, or data; nor any consequential or
incidental damages, even if Targus has been informed of
their possibility. This warranty does not affect your statutory
rights.
Warranty Registration at:
http://www.targus.com/product_registration.asp
6
Page 7

Technical Support
In the unlikely event that you encounter a problem with your
Targus accessory, or to order missing parts or replacement
keys, please contact Technical Support at:
Email: techsupport@targus.com
Internet: http://www.targus.com/support.asp
Our knowledgeable staff is also available to answer your
questions through one of the following telephone numbers.
North America
Monday through Friday, 8:00 a.m. (08:00) to 6:00 p.m.
(18:00) Eastern time:
US & Canada: 800-283-6325
Ordering Replacement Keys
To order replacement keys for your DEFCON KL, contact
Technical Support at one of the numbers listed in the
previous section.
If your DEFCON KL is registered, provide Technical Support
with your name, the password you choose when you
registered, and your credit card number.
If your DEFCON KL is not registered, provide Technical
Support with the following:
• Your name
• Address
• Phone number
• Credit card number
• DEFCON KL key code
Targus assumes no responsibility for lost, stolen or
damaged keys.
7
Page 8

For your convenience, record your Key Lock serial number
in the space provided.
Key Lock serial number
8
DEFCON is a trademark of Targus Group International.
Page 9

400-0042-001A
 Loading...
Loading...