SynOptics 3395, 3395A Management Manual

Software Management Guide
for the Model 3395/3395A
Terminal Server
Supplement 5.2
893-763-A July 1994
SynOptics Communications, Inc.
4401 Great America Parkway
Santa Clara, CA 95052-8185
(408) 988-2400

© 1994 by SynOptics Communications, Inc. All rights reserved.
Trademarks
SynOptics, SynOptics Communications, and LattisNet are registered trademarks of SynOptics
Communications, Inc. Lattis System 3000 and SynOptics Press are trademarks of SynOptics
Communications, Inc.
Other brand and product names are registered trademarks or trademarks of their respective holders.
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, SynOptics
Communications, Inc. reserves the right to make changes to the products described in this document
without notice.
SynOptics Communications, Inc. does not assume any liability that may occur due to the use or
application of the product(s) or circuit layout(s) described herein.
Federal Communications Commission (FCC) Statement
Note: This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable protection against
harmful interference when the equipment is operated in a commercial environment. This equipment
generates, uses, and can radiate radio frequency energy. If it is not installed and used in accordance with the
instruction manual, it may cause harmful interference to radio communications. Operation of this
equipment in a residential area is likely to cause harmful interference, in which case users will be required to
take whatever measures may be necessary to correct the interference at their own expense.
Electromagnetic Emissions
Meets requirements of
FCC Part 15, Subparts A and B, Class A
En 55 022 (CISPR 22:1985), Class A
General License VDE 0871, Class B (AmtsblVfg No. 243/1991 and Vfg 46/1992)
VCCI Class 1 ITE
This supplement contains new pages and replacement pages for the Software Management Guide for the
Model 3395/3395A Terminal Server, 893-158-C. Follow these instructions to add and replace pages in this
manual:
Replacement Pages
The following new pages: Replace these existing pages:
i through xiii i through xi
Chapter 5 Chapter 5
index-1 through index-6 index-1 through index-6
Addendum Pages
Add these pages: Following this page:
Chapter 20 Setting Up SecurID 19-9
Chapter 21 Setting Up ARAP 20-4
ii 893-763-A

Software Management Guide
for the Model 3395/3395A
Terminal Server
Version 5.2
893-763-A July 1994
SynOptics Communications, Inc.
4401 Great America Parkway
Santa Clara, CA 95052-8185
(408) 988-2400

© 1994 by SynOptics Communications, Inc. All rights reserved.
Trademarks
SynOptics, SynOptics Communications, and LattisNet are registered trademarks of SynOptics
Communications, Inc. Lattis System 3000 and SynOptics Press are trademarks of SynOptics
Communications, Inc.
Other brand and product names are registered trademarks or trademarks of their respective holders.
Statement of Conditions
In the interest of improving internal design, operational function, and/or reliability, SynOptics
Communications, Inc. reserves the right to make changes to the products described in this document
without notice.
SynOptics Communications, Inc. does not assume any liability that may occur due to the use or
application of the product(s) or circuit layout(s) described herein.
Federal Communications Commission (FCC) Statement
Note: This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC rules. These limits are designed to provide reasonable protection against
harmful interference when the equipment is operated in a commercial environment. This equipment
generates, uses, and can radiate radio frequency energy. If it is not installed and used in accordance with the
instruction manual, it may cause harmful interference to radio communications. Operation of this
equipment in a residential area is likely to cause harmful interference, in which case users will be required to
take whatever measures may be necessary to correct the interference at their own expense.
Electromagnetic Emissions
Meets requirements of
FCC Part 15, Subparts A and B, Class A
En 55 022 (CISPR 22:1985), Class A
General License VDE 0871, Class B (AmtsblVfg No. 243/1991 and Vfg 46/1992)
VCCI Class 1 ITE
ii 893-763-A

Table of Contents
Preface
Conventions xvi
Ordering SynOptics Publications..............................................................................................xvii
SynOptics Customer Support ..................................................................................................xvii
Chapter 1 - Introducing the Model 3395 Terminal Server
Obtaining Operating Software and Parameters.............................................................................1-2
Compatibility Issues..............................................................................................................1-2
Terminal Server Software Management Tools.............................................................................1-3
Software Management Tools .............................................................................................1-3
Standard DEC Software Installation and Management Tools ....................................................1-3
Chapter 2 - Setting Up the Terminal Server
Setting Up the Terminal Server................................................................................................2-1
Changing Operational Parameters.......................................................................................2-2
Assigning Basic Internet Characteristics.....................................................................................2-2
Assigning an Internet Address and Subnet Mask....................................................................2-2
Configuring Domain Name Server Support..........................................................................2-2
Related Commands and Server Characteristics.......................................................................2-3
Selecting Protocols and Features ..............................................................................................2-5
Chapter 3 - Setting Up Terminal Devices
Basic Procedures....................................................................................................................3-1
Preparing the Host for Local Access Connections........................................................................3-2
LAT Services .................................................................................................................3-2
TCP/IP Connections........................................................................................................3-2
Preparing Specific Types of Terminal and Ports ..........................................................................3-4
Setting Up Standard Terminals...........................................................................................3-4
Using Personal Computers as Terminals..............................................................................3-5
Setting Up Hard Copy (Printing) Terminals .........................................................................3-5
Setting Up Dedicated Services............................................................................................3-5
Setting Up Multisessions Terminals ...................................................................................3-6
Using the Menu Feature ...................................................................................................3-6
893-763-A iii

Chapter 4 - Setting Up Printers
How to Set Up Shared Printers ................................................................................................4-2
Setting Up a UNIX Shared Printer Service .................................................................................4-3
Installing the Shared Printer Output Filter............................................................................4-3
Defining a Printer to the UNIX Printer Subsystem ................................................................4-5
Operating the Shared Printer..............................................................................................4-6
Error Conditions .............................................................................................................4-6
Restrictions....................................................................................................................4-8
UNIX Shared Printer Protocol Description ...........................................................................4-8
Setting Up a UNIX PostScript Printer Service ............................................................................4-10
Setting Up a VMS/Ultrix Printer Service...................................................................................4-12
VMS Hosts....................................................................................................................4-13
Ultrix Hosts ...................................................................................................................4-14
Setting Up Services and Queues for Remote Access Connections ...................................................4-15
The Server Connection Queue............................................................................................4-16
Chapter 5 - Setting Up Modems
Setting Up Dial-In Modems ....................................................................................................5-1
Setting Up Dial-Back Modems.................................................................................................5-3
Using Dial-Back Scripts on the Terminal Server....................................................................5-3
Configuring PORT Characteristics .....................................................................................5-4
Setting Up a Dial-Back Script Server ..................................................................................5-5
Script File Structure and Guidelines....................................................................................5-7
Setting Up a Dial-Out Modem.................................................................................................5-9
Basic Procedure...............................................................................................................5-9
Configuring a LAT Application Port at a VMS Host.............................................................5-11
Modem Control Operation ......................................................................................................5-12
Device Types..................................................................................................................5-12
Supported Modem Control Signals.....................................................................................5-13
Information About Model 3395 Cabling Methods..................................................................5-13
Modem-Related PORT Characteristics.................................................................................5-14
Server Modem Disconnect Sequence....................................................................................5-16
Modem Control Signal Interaction......................................................................................5-17
Using Signal Check...............................................................................................................5-26
Flow Control .......................................................................................................................5-27
Software Flow Control.....................................................................................................5-27
Hardware Flow Control ....................................................................................................5-28
Chapter 6 - Setting Up TN3270 Terminals
Enabling the TN3720 Protocol ................................................................................................6-1
Enabling Extended Attributes.............................................................................................6-2
Defining TN3270 Devices.......................................................................................................6-2
Creating a New Device Type .............................................................................................6-3
Defining a TN3270 Terminal Type.....................................................................................6-3
Defining the TN3278 Type ...............................................................................................6-4
Modifying the Keymap.....................................................................................................6-4
Modifying the Screenmap .................................................................................................6-5
Assigning a TN3270 Device to a Port.................................................................................6-9
Other Commands That Affect TN3270 Devices.....................................................................6-11
Defining TN3270 Translation Tables ........................................................................................6-11
Creating a New Translation Table.......................................................................................6-12
Entering New Values Into the Table....................................................................................6-13
Assigning a Translation Table to a Port...............................................................................6-15
Other Commands that Affect Translation Tables....................................................................6-16
iv 893-763-A

Local Printer Support.............................................................................................................6-17
Chapter 7 - Using TCP/IP Features
Configuring Internet Routes....................................................................................................7-1
Dynamic Routing ...........................................................................................................7-1
Static Routing ................................................................................................................7-2
Related Commands and Terminal Server Characteristics..........................................................7-2
Configuring Rotary Connections..............................................................................................7-3
Rotary Configuration Procedure .........................................................................................7-4
Domain Name Storage .....................................................................................................7-5
Associated Commands......................................................................................................7-5
Configuring RLOGIN Support ................................................................................................7-6
Associated Commands......................................................................................................7-7
Remote Network Management Support .....................................................................................7-7
Using SNMP .................................................................................................................7-7
Associated Commands......................................................................................................7-9
Using Telnet to Gain Access to Remote Console Ports ..........................................................7-10
Associated Commands......................................................................................................7-11
Loading With Internet Protocols...............................................................................................7-11
Loading Images and Parameter Files....................................................................................7-13
Configuring Protocols on Servers with NVR........................................................................7-13
Directed TFTP Request.....................................................................................................7-14
Merit Value of Responses.................................................................................................7-14
Filenames in NVR ..........................................................................................................7-14
Eliminating TFTP Broadcasts............................................................................................7-14
Saving Parameters in the Permanent Database.......................................................................7-15
Dump Transmission ........................................................................................................7-15
Associated Commands......................................................................................................7-16
Using the Terminal Server as a Domain Name Server...................................................................7-16
Associated Commands......................................................................................................7-17
Configuring the Terminal Server to Use SLIP ............................................................................7-18
Terminal Server and Port Configuration...............................................................................7-18
SLIP Sessions ................................................................................................................7-20
Associated Commands......................................................................................................7-20
Using IP Reassembly.............................................................................................................7-21
Associated Commands......................................................................................................7-21
Using TCP Resequencing .......................................................................................................7-21
Associated Commands......................................................................................................7-23
Chapter 8 - Managing Terminal Server Resources
How the Terminal Server Allocates Memory ..............................................................................8-1
Strategies for Managing Memory .............................................................................................8-2
Select Only Features and Protocols Necessary at Your Site......................................................8-2
Alter Operating Parameters for the Enabled Features or Protocols .............................................8-5
Use a Terminal Server With More Memory..........................................................................8-5
Accept Less Than Optimal Performance or Less Functionality.................................................8-6
Parameters that Directly Affect Memory Allocation .....................................................................8-6
Identifying Memory Problems ...........................................................................................8-7
Adjusting Parameters .......................................................................................................8-8
Server Node Limit...........................................................................................................8-8
Server Queue Limit .........................................................................................................8-9
Server Session Limit .......................................................................................................8-9
Server Service Groups......................................................................................................8-9
Server Textpool Size........................................................................................................8-9
Server Packet Buffers .......................................................................................................8-10
893-763-A v

Parameter Server Limit.....................................................................................................8-10
Port Typeahead Size.........................................................................................................8-10
Port Internet TCP Window Size.........................................................................................8-11
Helpful Displays...................................................................................................................8-11
The SHOW|MONITOR SERVER COUNTERS Display........................................................8-11
The SHOW|MONITOR SERVER STATUS Display.............................................................8-11
The SHOW|MONITOR SERVER ALTERNATE STATUS Display.........................................8-13
Chapter 9 - Using Terminal Server Security Features
Controlling Access to the Terminal Server.................................................................................9-1
Terminal Server Passwords................................................................................................9-1
Privilege Levels..............................................................................................................9-3
The Kerberos Security System...........................................................................................9-4
Controlling Access to Resources on the Network ........................................................................9-8
The Port Access Characteristic...........................................................................................9-8
Limited View Protection for Network Resources ...................................................................9-8
Authorized LAT Service Groups.........................................................................................9-9
Password Protection for LAT Services.................................................................................9-9
Using the Internet Security Table .......................................................................................9-9
Default Values for the Internet Security Table.......................................................................9-11
Using Scripts to Enhance Network Security ...............................................................................9-16
Dedicated Services ...........................................................................................................9-16
Dial-back Modem Scripts..................................................................................................9-17
vi 893-763-A

Chapter 10 - Using the Accounting Feature
Enabling the Accounting Feature on the Terminal Server..............................................................10-1
Enabling the syslogd Daemon..................................................................................................10-2
About Information in the Account Log......................................................................................10-2
Enabling the Verbose Account Log —The Default Account Log ..............................................10-4
Specifying a Verbose Priority Number and Log File Location..................................................10-4
Clearing the Account Log.................................................................................................10-5
Commands Associated With the Accounting Feature....................................................................10-6
Chapter 11 - Using Scripts
How the Script Feature Works.................................................................................................11-1
Setting Up the Script Servers ..................................................................................................11-2
Developing a Script File...................................................................................................11-4
Directory Requirements ....................................................................................................11-5
Setting Up the Terminal Server to Use Scripts............................................................................11-6
Associated Commands......................................................................................................11-7
Script File Execution and Processing ..................................................................................11-7
Examples of Scripts...............................................................................................................11-9
Chapter 12 - Model 3395 Support for the Xremote Protocol
Terminal Server Support for Xremote Features............................................................................12-1
Starting Up the XDM Host .....................................................................................................12-3
Configuring the Terminal Server for Xremote Support.................................................................12-5
Enabling the Xremote Protocol on the Terminal Server ..........................................................12-5
Defining Remote Font Servers...........................................................................................12-5
TFTP Security on Font Servers .........................................................................................12-7
Defining Xremote Characteristics at Terminal Server Ports......................................................12-8
Establishing an Xremote Session .......................................................................................12-9
Using a Script to Configure the Terminal Server for Xremote Support......................................12-12
Enhancing Security for Xremote Users ................................................................................12-14
Notes on Memory Requirements for Xremote .............................................................................12-15
How Xremote Can Affect Terminal Server Performance..........................................................12-15
Memory Requirements for Sessions and Windows .................................................................12-15
Notes and Restrictions......................................................................................................12-16
Chapter 13 - Model 3395 Support for the Point-to-Point Protocol
About the Point-to-Point Protocol............................................................................................13-1
Enabling PPP on the Terminal Server.......................................................................................13-3
Setting Up Terminal Server Ports to Support PPP ......................................................................13-4
Specifying Optional PPP Port Characteristics.......................................................................13-5
Configuring a PPP Port for Modem Support ........................................................................13-6
Assigning Local and Remote PPP Addresses to PPP Ports......................................................13-6
893-763-A vii

Examples of Single-Node Configurations...................................................................................13-7
A PC With an Internet Address Within the LAN Subnet.........................................................13-8
A PC With an Internet Address Outside of the LAN Subnet.....................................................13-9
A PC With No Configured Internet Address..........................................................................13-11
Example of a Two-Node Configuration......................................................................................13-13
Chapter 14 - Configuring Print Services for Novell Users
Using Model 3395 Commands to Configure Novell Printing.........................................................14-2
Configuring a Port to Support Novell Printing .....................................................................14-2
Viewing Available Novell Printer Servers............................................................................14-3
Viewing Status of Xprinter Ports .......................................................................................14-3
Terminating Xprinter Operations........................................................................................14-3
Viewing IPX Protocol Packet Type Setting..........................................................................14-4
Novell Server Configuration....................................................................................................14-5
Adding a New NetWare Print Server....................................................................................14-7
Changing an Existing NetWare Print Server.........................................................................14-15
Chapter 15 - Managing Initialization Records
Viewing Initialization Parameters.............................................................................................15-1
Enabling and Disabling Protocols.............................................................................................15-2
Model 3395 Terminal Servers............................................................................................15-2
Changing Protocols from the Command Interface..................................................................15-2
Using the CARD, NVS, LattisNet, and MOP Protocols.........................................................15-3
Using the BOOTP and RARP Protocols..............................................................................15-4
Using the DTFTP Protocol ...............................................................................................15-4
Resetting Initialization Parameters to Default Values ...................................................................15-5
Chapter 16 - Setting Up Server Daemons
Enabling Daemons at the Server...............................................................................................16-2
Using the Finger Daemon (fingerd)...........................................................................................16-2
Using the Route Daemon (routd)..............................................................................................16-6
Using the Rwho Daemon (rwhod).............................................................................................16-7
Chapter 17 - Setting Printers Using the lpd Daemon
Setting Up lpd Shared Printers.................................................................................................17-1
Enable the lpd Daemon at the Terminal Server......................................................................17-1
Set Port Characteristics to Support Shared Printer Connections................................................17-2
Setting up queues for lpd
Setting up Berkeley (BSD) UNIX lpd printers
Configuring the lpd Printer at the UNIX Host.......................................................................17-3
Setting up AT&T System V UNIX lpd printers ....................................................................17-6
Setting up AIX lpd printer ................................................................................................17-7
Operating and Managing the lpd Printer and Print Queue...............................................................17-9
viii 893-763-A

Chapter 18 - Using Nested Menus
About the Nested Menus Feature..............................................................................................18-1
How the Terminal Server Obtains the Menu File...................................................................18-3
How the Port Obtains the Menus .......................................................................................18-3
Setting Up the Script Servers ..................................................................................................18-4
Creating the Nested Menus File ...............................................................................................18-5
Using Comment Lines in the Menu File .............................................................................18-8
Programming Guidelines ..................................................................................................18-8
Debugging the Menu File.................................................................................................18-8
Configuring the Terminal Server to Support Nested Menus...........................................................18-9
Terminal Server Characteristics..........................................................................................18-9
Port Characteristics..........................................................................................................18-10
Sample Nested Menu Files......................................................................................................18-11
Sample File 1.................................................................................................................18-11
Sample File 2.................................................................................................................18-14
Chapter 19 - Installing and Using the csportd Daemon
Running the Installation Script ................................................................................................19-2
csportd Command And Options................................................................................................19-4
Communication Server Port Setup Considerations.......................................................................19-4
Example Applications............................................................................................................19-4
Example csportd Installation Script...........................................................................................19-6
Chapter 20 - Setting Up SecurID
SecurID Client Features..........................................................................................................20-1
SecurID Client Setup.............................................................................................................20-2
Configuring the SecurID Client at the UNIX Host.................................................................20-2
Install the Model 3395 Load Image Which Contains the SecurID Client ....................................20-2
Enable The Server SecurID Feature.....................................................................................20-3
Specify Server-Related SecurID Characteristics......................................................................20-3
Configure Ports To Require SecurID Authentication ....................................................................20-4
Chapter 21 - Setting Up ARAP
ARAP Features.....................................................................................................................21-2
ARAP Setup 21-5
Overview.......................................................................................................................21-5
Install the Model 3395 Load Image for the Remote Access Server.............................................21-5
Verify Port Cabling.........................................................................................................21-6
Enable the server ARAP Protocol.......................................................................................21-8
Specify SERVER Characteristics .......................................................................................21-9
Specify PORT Characteristics............................................................................................21-10
Install CCL Cripts ..........................................................................................................21-12
893-763-A ix

Using ARAP with Authentication and Dial-Back Features.............................................................21-15
Modifying CCL Scripts for Macintosh Computers ......................................................................21-20
Basic Format of a CCL Script ...........................................................................................21-20
Modify a CCL Script.......................................................................................................21-22
Example Model 3395 CCL Extensions................................................................................21-23
Example of a Typical CCL Script ......................................................................................21-26
Modifying Dial-Back Scripts for ARAP Ports.............................................................................21-32
ARAP Planning Considerations...............................................................................................21-33
Appendix A - Shared Printer Source Code
Sample UNIX Output Filter File..............................................................................................A-1
Sample BSD UNIX Printcap File.............................................................................................A-19
Sample AT&T UNIX System V Interface File............................................................................A-20
Shared UNIX Printer Daemon File............................................................................................A-22
Appendix B - OPCOM Messages
Appendix C - DECserver Software Difference Data
Appendix D - Notes on Local and Remote Parameter Storage
Concurrent Local and Remote Parameter Storage.........................................................................D-1
Index
x 893-763-A

Figures
Figure 1-1. Network configuration with terminal servers..........................................................1-1
Figure 3-1. A sample terminal server menu...........................................................................3-6
Figure 4-1 Shared printer topology .....................................................................................4-1
Figure 4-2. Shared printer protocol overview.........................................................................4-8
Figure 4-3. Registration data ..............................................................................................4-9
Figure 4-4. Example VMS print queue command file..............................................................4-4
Figure 5-1. Example script server directory structure...............................................................5-6
Figure 5-2. State diagram for dial-in modems that support RNG................................................5-18
Figure 5-3. State diagram for dial-in modems that do not support RNG......................................5-20
Figure 5-4. State diagram for dial-out modems.......................................................................5-22
Figure 5-5. State diagram for dial-in/out modems that support RNG..........................................5-24
Figure 5-6. State diagram for dial-in/out modems that do not support RNG.................................5-26
Figure 7-1. Rotary connections...........................................................................................7-3
Figure 7-2. A connection to a host with RLOGIN..................................................................7-6
Figure 7-3. Sample SNMP application.................................................................................7-9
Figure 7-4. Telnet connection to remote console ports.............................................................7-10
Figure 7-5. Loading with an Internet router ...........................................................................7-12
Figure 7-6. SLIP connections to remote netowrk, remote PC...................................................7-19
Figure 9-1. A Kerberos realm .............................................................................................9-5
Figure 9-2. Kerberos password verification............................................................................9-6
Figure 9-3. An Internet network..........................................................................................9-12
Figure 10-1. A sample SHOW SERVER ACCOUNTING display ..............................................10-3
Figure 10-2. A sample verbose account log.............................................................................10-4
Figure 11-1. Example script server directory structure...............................................................11-3
Figure 12-1. Conventional Xremote implementation................................................................12-2
Figure 12-2. An Xterminal connected to a System 3000 with a Model 3395 Terminal Server ...........12-3
Figure 12-2. Font servers....................................................................................................12-6
Figure 13-1. PPP single-node configuration............................................................................13-2
Figure 13-2. A two-node configuration...................................................................................13-3
Figure 13-3. A PC with an Internet address within the LAN subnet.............................................13-8
Figure 13-4. A PC with an Internet address outside of the LAN subnet.........................................13-9
Figure 13-5. A PC with no configureed Internet address.............................................................13-11
Figure 13-6. Two terminal servers in a back-to-back gateway .....................................................13-12
893-763-A xi

Figure 14-1. Example SHOW XPRINTER display...................................................................14-3
Figure 14-2. Example SHOW|LIST XPRINTER PORTS display ...............................................14-3
Figure 14-3 Example LIST|MONITOR|SHOW SERVER CHARACTERISTICS display...............14-4
Figure 14-4. Network printing environments...........................................................................14-6
Figure 15-1. A SERVER LOADDUMP characteristics display of a Model 3395 Terminal Server......15-1
Figure 18-1. A three-level menu structure...............................................................................18-2
Figure 18-2. A sample menu................................................................................................18-3
Figure 18-3. Example of script server directory structure............................................................18-4
Figure 21-1. Standard remote access configuration....................................................................21-2
Figure 21-2. Remote access configuration using Model 3395 Terminal Servers..............................21-3
Figure 21-3. Modular cables for connecting a modem................................................................21-6
Figure 21-4. Modular cables for connecting a Macintosh computer..............................................21-7
Figure 21-5. Operation of authentication and security methods..................................................21-16
xii 893-763-A

Tables
Table 2-1. Memory usage for Model 3395 Terminal Server features and protocols.......................2-7
Table 3-1. Model 3395 Terminal Server commands and menu items .........................................3-8
Table 6-1. IBM display station functions.............................................................................6-4
Table 6-2. Screenmap actions............................................................................................6-6
Table 6-3. Special values for escape sequences......................................................................6-8
Table 6-4. EBCDICTOSASII portion of the USENGLISH translation table...............................6-14
Table 6-5. ASCIITOEBCDIC portion of the USENGLISH translation table...............................6-15
Table 7-1. Initial settings for PORT INTERNET SLIP characteristics.......................................7-21
Table 8-1. Memory usage for Model 3395 Teminal Server features and protocols........................8-3
Table 8-2. Memory usage for various sesstion types..............................................................8-5
Table 8-3. Value ranges for node limit, parameter server limit, queue limit, and identification
size for all products.....................................................................................8-6
Table 8-4. Value ranges for server session limit and server text pool size...................................8-7
Table 8-5. PORT characteristics that affect memory usage ......................................................8-8
Table 10-1. Priority numbers for messages from UNIX daemons ...............................................10-5
Table 12-1. Default files ....................................................................................................12-4
Table 12-2. Settings for port characteristics ...........................................................................12-11
Table 15-1. Default and available protocols for loading and dumping ..........................................15-2
Table 15-2. Default load image names ..................................................................................15-3
893-763-A xiii

Preface
This manual describes the configuration, setup, and management of a terminal server software
communication package, supplied by SynOptics Communications®. It is intended that this manual will be
read by network, terminal server, and UNIX and VAX system managers.
This manual is organized as follows:
Chapter 1 Introduces the Model 3395 software package, and describes some basic terminal server
management options.
Chapter 2 Describes how to configure the server to operate on the Internet, operate with a Domain
Name Server, and select the protocols and features that will be available on the server.
Chapter 3 Describes how to configure ports to operate with basic terminal devices.
Chapter 4 Describes how to configure UNIX and VMS shared printers, and UNIX shared PostScript
printers.
Chapter 5 Describes how to configure and troubleshoot dial-in, dial-back, and dial-out modems.
Chapter 6 Describes how you set up a port so that the terminal connected to the port emulates a
TN3270 device.
Chapter 7 Describes how to set up and manage terminal server TCP/IP Telnet features, configure the
server to operate with a Domain Name Server, establish Internet routes, manage Internet
security entries, create an Internet rotary group, and use the Serial Line Internet Protocol
(SLIP).
Chapter 8 Describes how you can allocate some portions of the memory in a server. This chapter also
describes how to identify problems with how this memory is allocated and how to adjust
parameters to correct these problems.
Chapter 9 Describes terminal server security features, and some of the issues you may want to consider
before you implement them at your site.
Chapter 10 Describes how to set up and use the session accounting feature. This feature records
information about successful and attempted connections made to or from the unit, as well as
information about sessions that are disconnected.
Chapter 11 Describes the Network Command Script feature, which provides the server manager with the
ability to create a script file which contains one or more Model 3395 commands to be
executed when the user logs in at a port.
Chapter 12 Describes Model 3395 support for the Xremote protocol.
Chapter 13 Describes Model 3395 support for the Point-to-Point protocol.
Chapter 14 Describes how to configure print services for Novell users.
Chapter 15 Describes how to manage initialization records from the command interface on terminal
servers that support the commands.
Chapter 16 Explains how to enable certain UNIX daemons on the terminal server and describes the
function of each daemon.
893-763-A xv

Preface
Chapter 17 Describes how to set up shared printers using the lpd daemon.
Chapter 18 Describes the Nested Menu feature and how to create nested menu files. This chapter
includes two sample nested menu files.
Chapter 19 Describes how to set up connections between a UNIX host and a communication server port
using the csportd daemon.
Chapter 20 Describes how to set up the server to use the SecurID authentication system.
Chapter 21 Describes how to set up the server to support connections using the AppleTalk Remote
Access Protocol (ARAP).
Appendix A Provides listings of “template” C language shared printer filter programs, a BSD UNIX
printcap file, and an AT&T UNIX System V interface file.
Appendix B Lists OPCOM messages that may be displayed by the Model 3395 software, and describes
the cause of the condition.
Appendix C Summarizes the differences between Model 3395 software and the LAT software for a
DECserver 200 terminal server unit.
Appendix D Notes on Local and Remote Parameter Storage.
Conventions
This manual uses the following conventions:
1. Keys that you press on the keyboard are represented using left and right angle bracket characters (< and
>, respectively). For example, the notation <CTRL> means that you press the CTRL key on the
keyboard, <A> means that you press the letter A key, and <Return> means that you press the
RETURN key on the keyboard.
2. The <CTRL> key on the keyboard provides alternate functions when used with some keyboard keys.
Notation such as <CTRL>/<A> indicates that you press both the <CTRL> key and the letter A key at
same time. The terminal server will echo this control character as ^A.
3. Unless otherwise specified, commands are executed when you press the <RETURN> key on the
keyboard.
4. The manual uses the following typographical conventions:
Monospace Typeface indicates text displayed at a terminal (displays, messages,
system responses, etc.).
italics indicates variables in commands and procedures.
5. The following typeface indicates user input in response to system prompts:
TS3395> connect
6. The server prompt for secure users is this:
TS3395>
The server prompt for non-privileged and privileged users is this:
TS3395>>
This is the default terminal server user interface prompt; the server manager can specify a different
prompt, so the prompt in use at your site may be different.
xvi 893-763-A

Preface
7. The following default user prompts will be shown (different prompt may be in use at your site):
VMS $
UNIX/ULTRIX %
UNIX/Ultrix Superuser #
DOS C:\
Ordering SynOptics Publications
To purchase additional copies of this document or other SynOptics® product publications, order by part
number from SynOptics Press™ at the following numbers. You may also request a free catalog of
SynOptics Press product publications.
• Phone: 1-800-845-9523
• FAX: U.S./Canada: 1-800-582-8000, International: 1-916-939-1010
SynOptics Customer Support
For assistance with installing and configuring your SynOpticssystems or for post-installation questions or
problems, contact your local reseller. If you cannot contact your local reseller, call the SynOptics Technical
Response Center (TRC) Contract Hotline.
To contact the TRC Contract Hotline, call:
• U.S. and Canada: 1-800-473-4911
• Europe: 011-31-3480-31616
• Rest of the world: 408-764-1000
893-763-A xvii

Preface
Technical information is available from the SynOptics InfoFACTS fax-on-demand system by calling:
• U.S. and Canada: 1-800-786-3228
• International: 408-764-1002
You can also access technical information in the SynOptics forum on CompuServe.
For information about our education services, contact the SynOptics Training Coordinator at 1-800-473-
4911 or 408-764-1018.
xviii 893-763-A

Chapter 5
Setting Up Modems
This chapter describes how to configure the terminal server to support several different types of modems. It also
describes how modem control operates. You can use this information for trouble shooting.
This chapter includes information about the following topics:
• Setting up dial-in modems
• Setting up dial-back modems
• Setting up dial-out modem (also dial-in/dial-out modems)
• Modem control operation
• Using signal check
• Flow control
In the examples in this chapter, port options that are a matter of personal preference are not discussed. For
each device type, only the options that must be changed are listed.
Setting Up Dial-In Modems
Dial-in modems provide local access connections to services on the network. Most of the default values for
port characteristics support dial-in modems, but you do need to change the defaults for these characteristics:
• Specify the following modem-related characteristics:
TS3395>> define port 8-12 modem control enabled
TS3395>> define port 8-12 dsrlogout disabled
Some ports can also use concurrent hardware flow control. Refer to the section "Information about
Model 3395 Cabling Methods" for more information.
• Specify the type of access allowed to the port. If you want the port to originate connections only (local
access connections), but not accept connections that originate from a remote location on the network, use
LOCAL access, which is the default.
If you want the port to both originate connections and accept connections which originate on the network,
such as for a modem that can also dial-out, set the port access to DYNAMIC:
TS3395>> define port 8-12 access dynamic
• Specify a DTRWAIT value for the DTRWAIT. Specify the conditions in which the port should assert
the DTR modem control signal. Use the command:
TS3395>> DEFINE PORT n DTRWAIT
value
893-763-A 5-1

Setting Up Modems
For a modem which supports the Ring (RI) signal, set the value to FORRING if you want the port to assert
DTR only after the modem asserts RI, or to DISABLED if you want the port to always assert DTR. For a
modem which does not support the Ring (RI) signal, set the value to DISABLED.
Configure the port so that its characteristics match those of the modem connected to it. Port characteristics
are set with SET|DEFINE PORT commands. For most devices, the default settings for nearly all of the
PORT characteristics are appropriate, but you may need to alter the following:
Speed or Autobaud. The Autobaud characteristics is enabled by default at all serial ports. When enabled,
the port automatically matches the baud rate of the modem when the user presses the <Return> key a few
times at initialization time. For the terminal server to use the autobaud feature, however, the modem must
use 8-bit no parity or 7-bit even parity characters. If the characters cannot be set to 8-bit no parity or 7-bit
even parity, you must disable the PORT AUTOBAUD characteristic and individually set the PORT SPEED,
CHARACTER SIZE, and PARITY characteristics to the appropriate values. For smart modems, always set
the port speed to match the modem speed.
Flow Control. The default setting for the Port Flow Control characteristic at all serial ports is XON
(XON|OFF). If the modem attached to the port is using a form of hardware flow control (CTS|RTS or
DSR|DTR), or no flow control, you must set the Port Flow Control characteristic to the appropriate value.
These examples use port 6:
TS3395>> define port 6 autobaud enabled
TS3395>> define port 6 character size 8
TS3395>> define port 6 speed 9600
TS3395>> define port 6 parity none
TS3395>> define port 6 flow control xon
Dedicated Services. To ensure security, many dial-in modem ports limit connections to only one host
service (LAT or TELNET), called a dedicated service. The following are some examples of how to define a
dedicated service at one or more ports:
This command assigns a dedicated service named ACCOUNTING to port 5:
TS3395>> define port 5 dedicated service accounting
This command assigns a dedicated service with the Internet address 192.12.119.184 to ports 8-12:
TS3395>> define port 8-12 dedicated service 192.12.119.184
This command specifies that when a user logs in to ports 8-12, the port connects directly to the dedicated
service:
TS3395>> define port 8-12 autodedicated enabled
If you do this, you can also assign a permanent user-name for the port, so that you can identify the port more
easily:
TS3395>> define port 8-12 username "chris"
5-2 893-763-A

Setting Up Modems
Setting Up Dial-Back Modems
Dial-back modems combine the characteristics of a dial-in modem and a dial-out modem. Like dial-in
modems, they provide local access connections to services on the network. However, they provide this by
having the server port instruct the modem to dial the telephone of the user who wants to log in.
The Model 3395 Terminal Server software dial-back feature uses the network command script feature. The
commands are contained in a file, called a script file, which is stored at a host called a script server. The script
server can be a host system that supports the Trivial File Transfer Protocol (TFTP). See Chapter 11 for more
information about creating scripts.
For a dial-back modem port, you must create a dial-back script, which contains the information that tells the
modem which telephone number to dial when a specific user attempts to log on to the server through a
modem. If no script file for the user is found, the user will not be able to login. If a script file is found for
the user, the server will cause the modem to dial-back that user at a designated telephone number. You can
use the dial-back script in conjunction with a login script for dial-back ports.
This section describes how you set up a dial-back port. The following specific activities are involved:
• Using dial-back scripts on the terminal server
• Configuring PORT characteristics
• Setting up a dial-back script server
Using Dial-back Scripts on the Terminal Server
To use script files from the terminal server, you must specify the Internet destinations (Internet address or
domain-name) and directory locations where the server can request script files. You also specify which ports
will use or require a script file for login. The following procedure describes the steps to take at terminal
servers which use scripts.
• At the terminal server which will use script files, define one or more script servers, using the privileged
DEFINE SERVER SCRIPT SERVER command. For example, the following commands designate a
script server where all username directories and the common script are located in the directory path
/tftpboot/SCRIPTS. The /tftpboot directory is the TFTP home directory of the host which
has the domain name UNIXHOST.SynOptics.COM.
TS3395>> define server script server unixhost.synoptics.com
"/scripts"
TS3395>> set server script server unixhost.synoptics.com "/scripts"
You can specify up to four script servers for each server unit.
893-763-A 5-3

Setting Up Modems
Configuring PORT Characteristics
Most of the default values for PORT characteristics are satisfactory. You need to make the following
changes to dial-back port and modem-related characteristics. These examples use port 12 as an example:
TS3395>> define port 12 modem control enabled
TS3395>> define port 12 dsrlogout disabled
TS3395>> define port 12 access dynamic
TS3395>> define port 12 dialback enabled
• Specify when the port should assert the DTR modem control signal with this command:
DEFINE PORT n DTRWAIT
If the modem supports the Ring (RI) signal, set the value to FORRING if you want the port to assert DTR
only after the modem asserts RI. Set it to DISABLED if you want the port to always assert DTR. For a
modem which does not support the Ring (RI) signal, set the value to DISABLED.
Configure the port so that its characteristics match those of the modem to which it is connected. The
SET|DEFINE PORT commands specify port characteristics. For most devices, nearly all of the PORT
characteristics can be left at their default settings, but you may wish to alter the following:
Speed or Autobaud. The AUTOBAUD characteristic is enabled by default at all serial ports. When
enabled, the port automatically matches the baud rate of the modem when the user presses the <Return> key a
few times at initialization. The modem must use 8-bit no parity or 7-bit even parity characters for the
terminal server to use this feature, however. If the characters cannot be set to 8-bit no parity or 7-bit even
parity, you must disable the port autobaud feature, and set the PORT SPEED, CHARACTER SIZE, and
PARITY characteristics to the appropriate values. Always set the port speed to match the modem speed on
smart modems.
Flow Control. The default setting for the PORT FLOW CONTROL characteristic at all serial ports is
XON (XON|OFF). If the modem attached to the port is using a form of hardware flow control (CTS|RTS or
DSR|DTR), or no flow control, you must set the PORT FLOW CONTROL characteristic to the appropriate
value. These examples use port 12 as an example.
TS3395>> define port 12 autobaud enabled
TS3395>> define port 12 character size 8
TS3395>> define port 12 speed 9600
TS3395>> define port 12 parity none
TS3395>> define port 12 flow control xon
value
To change the amount of time which the remote modem has in which to respond to a dial-back attempt, use
this command:
DEFINE PORT n DIALBACK TIMEOUT time
where time is between 0 and 60 seconds (default is 20 seconds).
5-4 893-763-A

Setting Up Modems
Setting Up a Dial-back Script Server
To use the network command script feature, you must specify information at the script server and the terminal
server. Complete the following steps to configure each script server:
a. Determine which UNIX host system or will be the script servers. You can use multiple hosts for
backup, which can be a combination of script server types. Each terminal server can have up to four
script servers.
Be sure that Telnet is enabled, as it is by default on most terminal servers. (If you need to enable Telnet,
be sure that you do not disable LAT unintentionally: include LAT in the command which enables the
protocol: DEFINE SERVER PROTOCOL LAT TELNET ENABLED.) Define an Internet-address and
optionally a domain name.
b. Set up directories to contain script files at each script server. For a UNIX host script server, you need to
consider the TFTP guidelines in the next section, as well.
Create a directory to contain the dial-back script file for each user who will have one. The directory name
must match the name that user will specify when logging on to the port at the Enter username>
prompt. At a given script server, all username directories must be located in the same top-level directory.
For ease of management, you can create a top-level directory just for script files, rather than use a
directory that already contains many files, such as /usr, /bin, /tftpboot, or /etc on a UNIX
host. The user name and the directory name cannot include space or tab characters.
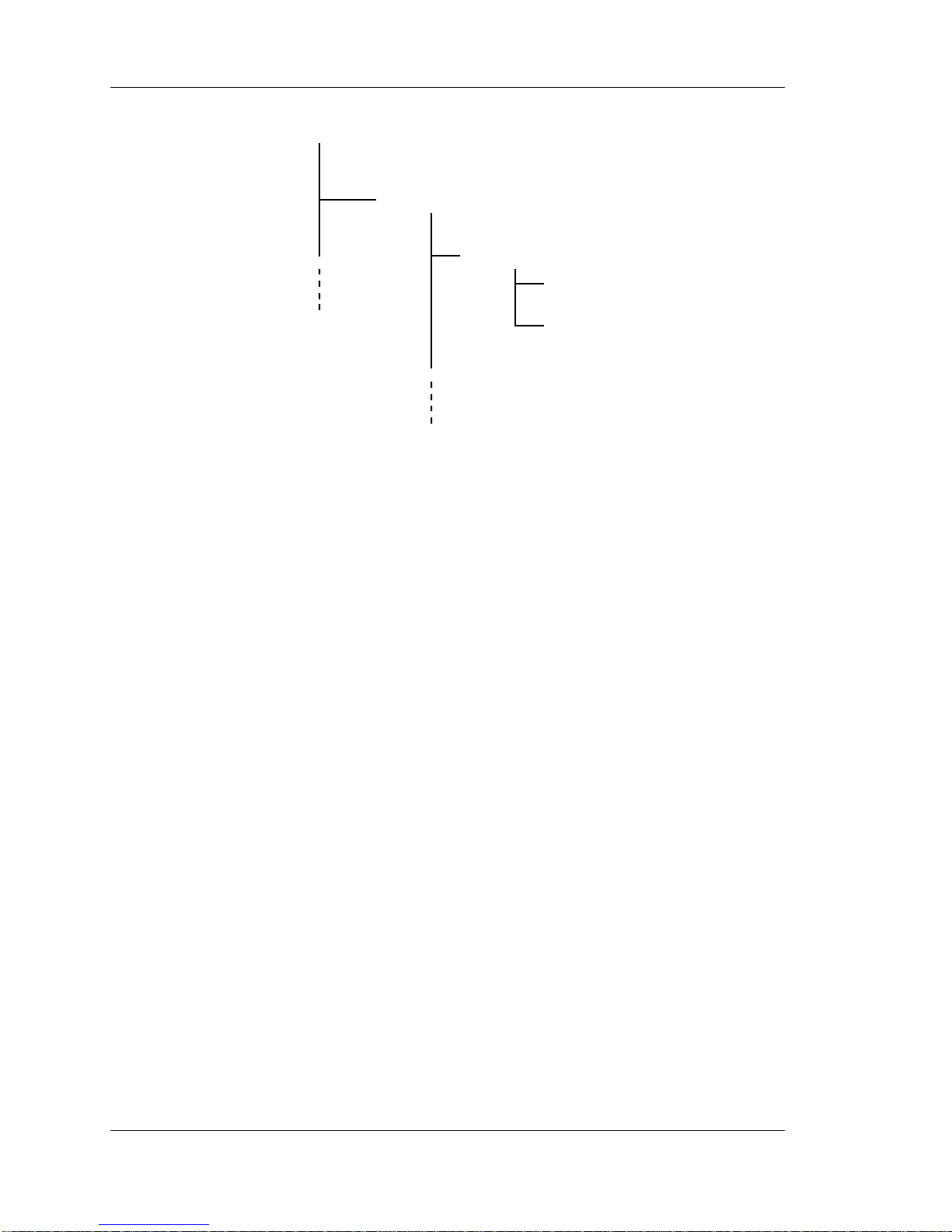
Figure 5-1 illustrates how to set up the directories to contain script files at a UNIX host. In the figure, the
user gjones has both a login script file and a dial-back script file which contains the information that tells the
modem which telephone number to dial when the user gjones attempts to log on to the server through a
modem. For example, when a user logs in as gjones, the terminal server request the file
/SCRIPTS/gjones/dialback from this script server (in this example, /tftpboot is the TFTP home
directory for this host). If the modem answers when dialed and gjones logs in, the connection is dropped, the
login script executes, and gjones is dialed back. Note that if a user logs in as gjones to a non-dial-back port
which is configured to use a login script, the script server will send the file /SCRIPTS/gjones/login to
be executed at the port.
The port user name must match the directory name at the host for the terminal server to locate a custom script
file for a user. Therefore, users need to type in the correct user name when they login to use their custom
login script file.
893-763-A 5-5
Setting Up Modems
/tftpboot
/SCRIPTS
/gjones
login
dialback
Figure 5-1. Example script server directory structure
The following examples creates a top-level directory named SCRIPTS, and a username directory for a user
whose login name will be jsmith on a UNIX host.
UNIX Host
% mkdir SCRIPTS
% cd SCRIPTS
% mkdir jsmith
% cd jsmith
For additional users, the directory for each username would be a sub-directory of the SCRIPTS directory.
c. At the UNIX host or PC, use a text editor to create the script file, which contain the instructions that
permit the server to dial-back to another modem. The name of file is dialback. At a UNIX host the file
name must consist of all lower-case letters (login or dialback). When creating the file, follow the
syntax rules listed in the next section. See also Chapter 11 for more information about Scripts.
5-6 893-763-A

Setting Up Modems
Script File Structure and Guidelines
Observe the following rules when developing a dial-back script file:
• The first line in the script is always the following:
#control_script
• You can include commands which require user input, such as a command that requires a password. The
unit will prompt the user for the password or other input before continuing (the user prompt will be
displayed, regardless of the setting of the PORT SCRIPT ECHO characteristic).
• Each line of a script file can be up to 132 characters long. Each line of a script file must contain only
one command. Each command must be on only one line.
• Within command scripts, the server software recognizes the character (#) as a flag for special operations.
When the pound character is the first non-space character on a command line, the server attempts to treat
the contents of the line as control information that it must interpret. When followed by a space or tab,
the pound character indicates a comment; the server ignores the remainder of the line.
In a dial-back script, the pound character, when followed by the word modem and one or more spaces, specifies
a modem command that the server will pass on to a modem. The phrase "#modem" must be in lower case
letters.
Note: If you plan to use a dial-back script for a port that is configured to use AppleTalk Remote Access
Protocol (ARAP), refer to Chapter 21 for additional information.
Directory Requirements
Script files are downloaded to units through the TFTP protocol. UNIX systems usually require that you
locate all files that TFTP will transfer on the network in the TFTP "home directory." Most UNIX systems
provide a way for you to specify the TFTP home directory or use a default home directory. The default TFTP
home directory varies from system to system. Follow the configuration instructions for the TFTP daemon
(tftpd) in the system documentation (MAN pages, etc.) to determine how to locate the TFTP home directory.
On Sun workstations, for example, the MAN page for tftpd says that the home directory is specified in the
/etc./inetd.conf file, and that the factory default home directory is /tftpboot. Therefore, you
would examine the tftp entry in the /etc./inetd.conf file to see if the host is using the default home
directory or a user-specified home directory. Place the script files in the home directory.
For ease of configuration (for example, adding users) or to prevent the TFTP home directory from becoming
too cluttered, it may be desirable to locate script files in a directory other than the TFTP home directory. To
do this, you must create a link from the directory containing the script files to the TFTP home directory, so
that the TFTP daemon will know where to locate the files. Create this link and give it appropriate file
permissions using commands in the form (note, you must be superuser):
# cd tftp-home-directory
# ln -s tftp-home-directory script-directory
# chmod 777 script-directory
893-763-A 5-7

Setting Up Modems
For example, on Sun workstations, using the default TFTP home directory, /tftpboot, and a directory
named /SCRIPTS as the top-level directory in which script files are stored, you would use the commands:
# cd /tftpboot
# ln -s /tftpboot SCRIPTS
# chmod 777 SCRIPTS
Determine if any TFTP security mechanisms exist on your UNIX system. Some TFTP implementations do
not limit the directories that TFTP can access, which can present a security risk at some sites. Other
implementations do limit TFTP to certain directories. In this case, you must place all files in a particular
home directory, or in a subdirectory of the home directory. If the files are not located there, TFTP will not
find them. For example, SunOS, and some others, use a TFTP daemon -s ( secure) option, that restricts
TFTP to a particular directory and its subdirectories. Sun workstations are normally configured with this
option enabled. If you examine the /etc./inetd.conf file, you will see an entry similar to -s
/tftpboot in the tftpd entry. Other vendors may use a different method. Read the MAN page on tftp,
tftpd, and inetd.conf to determine the directory/security requirements on your UNIX system.
Script File Execution and Processing
The terminal server executes script files either when the user logs in to an appropriately configured port, or
when the user issues the SCRIPT command. The following steps describe what happens during script file
processing and execution:
1. The user attempts to log on to a dial-back port. The user specifies a username when the Enter
Username> prompt appears. The terminal server immediately disconnects the telephone connection.
The terminal server uses the port username to locate the script file and to reauthenticate the user and the
port speed.
2. The terminal server requests the TFTP process at each script server to download a specific script file. The
file to be downloaded is determined, as follows:
The terminal server requests a script file named "dialback" from a directory location which is based on two
items: the pathname specified in the DEFINE|SET SERVER SCRIPT SERVER command and the
username of the port, with blank spaces removed. The DEFINE|SET SERVER SCRIPT SERVER
command designates the top-level directories to be searched, the username designates the lowest directory
to be searched. For example, the following command to specifies a script server at address
192.12.119.184 and a top-level path name of /usr/SynOptics
TS3395>> define server script server 192.12.119.184
"/usr/SynOptics"
When a user named "John A. Smith" logged on to a port, the terminal server requests the script file
/usr/SynOptics/John A.Smith/dialback from the script server at address
192.12.119.184. If the script is not found in the first directory location, the TFTP process searches the
directory immediately above it.
5-8 893-763-A
 Loading...
Loading...