Page 1

Symantec™ System Recovery 2011 User's Guide
Windows Edition
Page 2

Symantec System Recovery 2011 User's Guide
The softwaredescribed inthis bookis furnishedunder alicense agreementand maybe used
only in accordance with the terms of the agreement.
Documentation version: 9.0
Legal Notice
Copyright © 2011 Symantec Corporation. All rights reserved.
Symantec, the Symantec Logo, LiveUpdate, pcAnywhere, Symantec AntiVirus, NetBackup,
SmartSector, and Backup Exec are trademarks or registered trademarks of Symantec
Corporation orits affiliates in the U.S.and othercountries. Other namesmay betrademarks
of their respective owners.
Microsoft, Windows, Windows NT, Windows Vista, MS-DOS, Hyper-V, and the Windows
logo areregistered trademarks or trademarks of Microsoft Corporation in the United States
and other countries. VeriSign® is a registered trademark of Verisign, Inc.
VMware, the VMware "boxes" logo and design are registered trademarks or trademarks of
VMware, Inc..
Gear Software is a registered trademark of GlobalSpec, Inc.
Google and Google Desktop are trademarks of Google, Inc.
The product described in this document is distributed under licenses restricting its use,
copying, distribution, and decompilation/reverse engineering. No part of this document
may be reproduced in any form by any means without prior written authorization of
Symantec Corporation and its licensors, if any.
THE DOCUMENTATIONISPROVIDED "ASIS" AND ALLEXPRESS ORIMPLIED CONDITIONS,
REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF
MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT,
ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO
BE LEGALLYINVALID. SYMANTEC CORPORATIONSHALL NOT BELIABLE FOR INCIDENTAL
OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING,
PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED
IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE.
The LicensedSoftware andDocumentation aredeemed tobe commercialcomputer software
as definedin FAR 12.212 and subject to restricted rights asdefined inFAR Section52.227-19
"Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in
Commercial Computer Software or Commercial Computer Software Documentation", as
applicable, and any successor regulations. Any use, modification, reproduction release,
performance, displayor disclosure of the Licensed Software and Documentation bythe U.S.
Government shall be solely in accordance with the terms of this Agreement.
Page 3

Symantec Corporation
350 Ellis Street
Mountain View, CA 94043
http://www.symantec.com
Page 4

Technical Support
Symantec Technical Support maintains support centers globally. Technical
Support’s primary role is to respond to specific queries about product features
and functionality.The Technical Support group also creates contentfor our online
Knowledge Base. The Technical Support group works collaboratively with the
other functional areas within Symantec to answer your questions in a timely
fashion. Forexample, theTechnical Supportgroup works with Product Engineering
and SymantecSecurity Response to provide alerting services andvirus definition
updates.
Symantec’s maintenance offerings include the following:
■ A range of support options that give you the flexibility to select the right
amount of service for any size organization
■ Telephone and Web-based support that provides rapid response and
up-to-the-minute information
■ Upgrade assurance that delivers automatic software upgrade protection
■ Global support that is available 24 hours a day, 7 days a week
■ Advanced features, including Account Management Services
For information about Symantec’s Maintenance Programs, you can visitour Web
site at the following URL:
www.symantec.com/techsupp/
Contacting Technical Support
Customers with a current maintenanceagreement may access Technical Support
information at the following URL:
www.symantec.com/techsupp/
Before contacting Technical Support, make sure you have satisfied the system
requirements that are listed in your product documentation. Also, you should be
at thecomputer on which the problem occurred, incase itis necessaryto replicate
the problem.
When you contact Technical Support, please have the following information
available:
■ Product release level
■ Hardware information
■ Available memory, disk space, and NIC information
■ Operating system
Page 5

■ Version and patch level
■ Network topology
■ Router, gateway, and IP address information
■ Problem description:
■ Error messages and log files
■ Troubleshooting that was performed before contacting Symantec
■ Recent software configuration changes and network changes
Licensing and registration
If yourSymantec product requires registration or a licensekey, accessour technical
support Web page at the following URL:
www.symantec.com/techsupp/
Customer service
Customer service information is available at the following URL:
www.symantec.com/techsupp/
Customer Service is available to assist with the following types of issues:
■ Questions regarding product licensing or serialization
■ Product registration updates, such as address or name changes
■ General product information (features, language availability, local dealers)
■ Latest information about product updates and upgrades
■ Information about upgrade assurance and maintenance contracts
■ Information about the Symantec Buying Programs
■ Advice about Symantec's technical support options
■ Nontechnical presales questions
■ Issues that are related to CD-ROMs or manuals
Page 6

Maintenance agreement resources
If you want to contact Symantec regarding an existing maintenance agreement,
please contact the maintenance agreement administration team for your region
as follows:
Additional enterprise services
Symantec offers a comprehensive setof services that allow you to maximize your
investment in Symantec products and to develop your knowledge, expertise, and
global insight, which enable you to manage your business risks proactively.
Enterprise services that are available include the following:
customercare_apac@symantec.comAsia-Pacific and Japan
semea@symantec.comEurope, Middle-East, and Africa
supportsolutions@symantec.comNorth America and Latin America
Symantec EarlyWarning Solutions
Managed Security Services
Consulting Services
Educational Services
To access more information about Enterprise services, please visit our Web site
at the following URL:
www.symantec.com
Select your country or language from the site index.
These solutions provide early warning of cyber attacks, comprehensive threat
analysis, and countermeasures to prevent attacks before they occur.
These servicesremove theburden ofmanaging andmonitoring securitydevices
and events, ensuring rapid response to real threats.
Symantec Consulting Services provide on-site technical expertise from
Symantec andits trustedpartners. SymantecConsulting Servicesoffer avariety
of prepackaged and customizable options that include assessment, design,
implementation, monitoring,and managementcapabilities. Each is focused on
establishing andmaintaining the integrity and availability of your IT resources.
Educational Services provide a full array of technical training, security
education, security certification, and awareness communication programs.
Page 7

Contents
Technical Support ..... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ... 4
Chapter 1 Introducing Symantec™ System Recovery 2011 ... ..... .. 17
About Symantec System Recovery .... .... . .... . .... . .... ..... ..... .... . .... . .... .... 17
About the components of Symantec System Recovery . .... . .... . .... ..... ..... 18
What is new in Symantec System Recovery 2011 . .... ..... ..... .... . .... . .... . . 19
Accessing Help & Support for Symantec System Recovery . ..... .... . .... . ... 20
Sending your feedback regarding Symantec System Recovery
2011 .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 21
Chapter 2 Installing Symantec System Recovery .... . .... . .... . .... ..... .... 23
Before you install Symantec System Recovery . ..... .... . .... . .... . .... ..... ..... 23
System requirements for Symantec System Recovery ... ..... ..... .... . . 23
About supported file systems and removable media . .... . .... . .... ..... . 26
About the availability of features in Symantec System
Recovery . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... 26
About the trial version of Symantec System Recovery . . .... . .... ..... .. 28
Installing Symantec System Recovery . .... . .... . .... . .... ..... ..... .... . .... . .... . . 29
Custom Install options ... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... .... 30
Completing the installation of Symantec System Recovery . ..... ..... . 31
Activating Symantec System Recovery after the trial
period ... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... 33
Updating Symantec System Recovery with LiveUpdate ... . .... . .... ..... ..... 33
About uninstalling Symantec System Recovery ... . .... ..... ..... .... . .... . .... . 34
Chapter 3 Ensuring the recovery of your computer . ..... ..... .... . .... . ... 35
About ensuring the recovery of your computer . .... . .... ..... ..... .... . .... . .... 35
About testing Symantec System Recovery Disk . .... . .... . .... ..... ..... .... . .... 36
Testing Symantec System Recovery Disk ... . .... ..... ..... .... . .... . .... .... 36
Creating a custom Symantec System Recovery Disk ... . .... . .... . .... ..... ..... 37
About updating Symantec System Recovery Disk on USB . . .... . .... . .. 40
Symantec System Recovery Disk creation settings ... ..... .... . .... . .... . 40
Optional settings for Symantec System Recovery Disk ... ..... .... . .... . 41
Page 8

Contents8
Chapter 4 Getting Started ... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .. 43
How to use Symantec System Recovery ..... .... . .... . .... . .... ..... ..... .... . .... . 43
Starting Symantec System Recovery .... . .... . .... ..... ..... .... . .... . .... . .... ..... 45
Configuring Symantec System Recovery default options ... ..... .... . .... . ... 45
Setting up general backup options .... . .... . .... . .... ..... ..... .... . .... . .... .. 46
Adjusting the effect of a backup on computer performance .... ..... ... 48
About enabling network throttling ... ..... .... . .... . .... ..... ..... .... . .... . .. 48
Adjusting default tray icon settings . .... . .... . .... . .... ..... ..... .... . .... . ... 49
About managing file types and file extensions ... ..... .... . .... . .... ..... .. 50
About using unique names for external drives . .... . .... . .... ..... ..... .... 53
Configuring default FTP settings for use with Offsite Copy ... ..... .... 54
Logging Symantec System Recovery messages ... . .... . .... ..... ..... .... . 56
Enabling email notifications for product (event) messages .... . .... .... 58
Setting up your first backup using Easy Setup . .... . .... ..... ..... .... . .... . .... . 60
Hiding or showing the Advanced page .... . .... ..... ..... .... . .... . .... ..... ..... ... 60
Chapter 5 Best practices for backing up your data . .... . .... . .... . .... ..... 63
About backing up your data .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . . 63
About choosing a backup type . . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . . 64
What to do before you back up . ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 64
What to do during a backup .... ..... ..... .... . .... . .... . .... ..... .... . .... . .... . .... .. 66
What to do when a backup is finished . .... . .... ..... ..... .... . .... . .... . .... ..... .. 67
Tips for running defined backups . ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .. 68
Viewing the properties of a backup job . .... . .... . .... ..... ..... .... . .... . .... ..... . 69
About selecting a backup destination ..... .... . .... . .... . .... ..... ..... .... . .... . ... 69
About backing up dual-boot computers . ..... .... . .... . .... . .... ..... ..... .... . .... 71
Chapter 6 Backing up entire drives . .... ..... ..... .... . .... . .... . .... ..... ..... .... . ... 73
About defining a drive-based backup ... .... . .... . .... . .... ..... ..... .... . .... . .... . 73
Defining a drive-based backup ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... 74
Drives options . ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 75
Related drives options .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . ... 75
Recovery point type options ... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . . 76
Backup destination options ... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 77
Offsite Copy Settings options . . .... ..... ..... .... . .... . .... ..... ..... .... . .... . . 78
Recovery point options ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 79
Advanced Scheduling options . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .. 81
About files that are excluded from drive-based backups ... ..... ..... ... 82
About network credentials ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . ... 83
About running command files during a backup ... . .... . .... ..... ..... .... . 83
Command files options ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .. 84
Page 9

Advanced options for drive-based backups ... . .... . .... ..... ..... .... . .... . . 86
Backup time options ... ..... .... . .... . .... . .... ..... .... . .... . .... . .... ..... ..... .. 91
Compression levels for recovery points .... .... . .... . .... . .... ..... ..... .... . .... . . 92
Running a one-time backup from Symantec System Recovery . .... ..... .... 93
About running a one-time backup from Symantec System Recovery
Disk ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ... 94
Running a one-time backup from Symantec System Recovery
Disk ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 95
About Offsite Copy ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ... 100
How Offsite Copy works . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... 100
About using external drives as your offsite copy
destination .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 101
About using a network server as your offsite copy
destination .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 103
About using an FTP server as your offsite copy destination .... .... . . 104
Chapter 7 Backing up files and folders .... .... . .... . .... . .... ..... ..... .... . .... . . 107
About backing up files and folders . ..... ..... .... . .... . .... ..... ..... .... . .... . .... 107
Backing up files and folders . ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 107
9Contents
Chapter 8 Running and managing backup jobs . .... ..... .... . .... . .... . .... 117
Running an existing backup job immediately .... . .... . .... . .... ..... ..... .... . . 117
Running a backup with options . . .... . .... ..... ..... .... . .... . .... . .... ..... .. 118
Adjusting the speed of a backup . .... . .... ..... ..... .... . .... . .... . .... ..... ..... ... 120
Stopping a backup or a recovery task ... . .... . .... . .... ..... ..... .... . .... . .... . .. 120
Verifying that a backup is successful . .... ..... ..... .... . .... . .... . .... ..... ..... .. 121
Editing backup settings . .... . .... . .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... 122
Enabling event-triggered backups ... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 122
General Event Trigger options .... ..... .... . .... . .... . .... ..... ..... .... . .... . 123
Trigger Application options .... .... . .... . .... . .... ..... ..... .... . .... . .... . .... 123
About ThreatCon Response ... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . 124
Configuring ThreatCon Response for a backup job .... . .... . .... ..... ... 124
ThreatCon Response options .... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 125
Editing a backup schedule ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... .. 126
Turning off a backup job ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... .... 126
Deleting backup jobs . .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . ... 126
Adding users who can back up your computer .... ..... .... . .... . .... . .... ..... . 127
Configuring access rights for users or groups ... ..... ..... .... . .... . .... . .... .. 127
Page 10

Contents10
Chapter 9 Backing up remote computers from your
computer . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ... 129
About backing up other computers from your computer .... . .... ..... ..... . 129
Adding remote computers to the Computer List ... .... . .... . .... . .... ... 130
Adding local computers to the Computer List ... . .... ..... ..... .... . .... . . 131
Removing a computer from the Computer List . .... . .... . .... . .... ..... .. 131
About deploying the Symantec System Recovery Agent .... ..... .... . .... . .. 131
Preparing acomputer in a workgroup environment to deploythe
agent ... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 132
Deploying the Symantec System Recovery Agent ... ..... ..... .... . .... . 133
Manually installing the Symantec System Recovery Agent . . .... . .... 134
Granting rights to domain users on Windows 2003 SP1
servers ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 135
About the Symantec System Recovery Agent ..... .... . .... . .... . .... ..... ..... 135
Using the Symantec System Recovery Agent ..... ..... .... . .... . .... . .... 136
About managing the Symantec System Recovery Agent through
Windows Services ... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .. 136
Best practices for using services ... .... . .... . .... . .... ..... ..... .... . .... . .... . .... 137
Opening Windows services . .... ..... ..... .... . .... . .... . .... ..... ..... .... . ... 138
About startingor stoppingthe Symantec System Recovery Agent
service ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ... 139
Starting or stopping the Symantec System Recovery Agent
service ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ... 140
Setting uprecovery actionswhen the Symantec System Recovery
Agent does not start . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 140
About viewing Symantec System Recovery Agent dependencies .. ..... .. 141
Viewing Symantec System Recovery Agent dependencies ..... .... . .. 142
About controlling access to Symantec System Recovery . .... . .... ..... ..... 142
Adding users and groups ... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... 143
Changing permissions for a user or a group ... . .... . .... . .... ..... ..... ... 144
Removing a user or a group . ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .. 144
Running Symantec System Recovery using different user
rights ... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... 145
Chapter 10 Monitoring the status of your backups .... .... . .... . .... . .... .. 147
About monitoring backups . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . 147
Rescanning a computer’s hard disk . . .... . .... . .... ..... ..... .... . .... . .... . . 148
About the icons on the Home page .... . .... ..... ..... .... . .... . .... . .... ..... .... . . 148
About the icons on the Status page . ..... .... . .... . .... ..... ..... .... . .... . .... . ... 150
Configuring Symantec System Recovery to send SNMP traps . ..... .... . .. 155
About theSymantec SystemRecovery ManagementInformation
Base . ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . ... 156
Page 11

About customizing the status reporting of a drive (or file and folder
backups) .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 156
Customizing the status reporting of a drive (or file and folder
backups) .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... 157
Viewing drive details .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... 158
Improving the protection level of a drive ... . .... . .... . .... ..... ..... .... . .... . .. 158
About using event log information to troubleshoot problems . .... ..... .... 161
Chapter 11 Exploring the contents of a recovery point . . .... ..... ..... .. 163
About exploring recovery points ... ..... .... . .... . .... . .... ..... ..... .... . .... . .... 163
Exploring a recovery point through Windows Explorer ..... .... . .... . .... . .. 164
Mounting a recovery point from Windows Explorer . . .... . .... ..... .... 165
Opening and restoring files within a recovery point . .... . .... . .... . .... ..... . 165
About configuring a backup to create searchable recovery
points ... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . 167
Dismounting a recovery point drive ... .... . .... . .... . .... ..... ..... .... . .... . .... . 167
Viewing the drive properties of a recovery point .... . .... ..... ..... .... . .... . . 167
Recovery point drive properties . .... ..... ..... .... . .... . .... . .... ..... ..... .. 168
Chapter 12 Managing backup destinations . . .... . .... ..... ..... .... . .... . .... . .. 171
11Contents
About backup destinations ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... . 172
About backup methods . .... . .... . .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . 172
About drive-based backups .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . 172
About file and folder backups ... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 173
Cleaning up old recovery points . ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .. 174
Deleting a recovery point set . .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 175
Deleting recovery points within a set .... ..... .... . .... . .... ..... ..... .... . .... . .. 175
Making copies of recovery points .... . .... . .... . .... ..... ..... .... . .... . .... ..... .. 177
Source options .... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 178
Destination Location options .... . .... . .... . .... ..... ..... .... . .... . .... ..... .. 180
Copy recovery point options . ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 181
Defining a virtual conversion job . . .... . .... ..... ..... .... . .... . .... . .... ..... ..... . 183
Source options .... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 185
Virtual Disks Destination options . .... ..... ..... .... . .... . .... . .... ..... ..... 186
General Options properties . .... . .... . .... ..... ..... .... . .... . .... ..... ..... ... 188
Conversion Time options .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .. 190
Running an existing virtual conversion job immediately ... . .... . .... . .... .. 192
Viewing the properties of a virtual conversion job . .... . .... ..... ..... .... . ... 192
Viewing the progress of a virtual conversion job . .... . .... ..... ..... .... . .... . 192
Editing a virtual conversion job . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... 193
Deleting a virtual conversion job ... ..... .... . .... . .... . .... ..... .... . .... . .... . .... 193
Page 12

Contents12
Running a one-time conversion of a physical recovery point to a
virtual disk .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... .. 194
Source options .... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 195
Virtual Disks Destination options . .... ..... ..... .... . .... . .... . .... ..... ..... 198
General Options properties . .... . .... . .... ..... ..... .... . .... . .... ..... ..... ... 200
About managing file and folder backup data ..... ..... .... . .... . .... . .... ..... .. 202
Viewing how much file and folder backup data is stored .... ..... .... . 203
Limiting the number of file versions to keep .... . .... . .... ..... ..... .... . . 203
Manually deleting files from your backups of files and
folders .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 203
Finding versions of a file or folder . . .... ..... ..... .... . .... . .... ..... ..... ... 204
Automating the management of backup data .... .... . .... . .... . .... ..... .... . .. 204
Moving your backup destination . . .... . .... . .... ..... .... . .... . .... . .... ..... ..... . 205
Chapter 13 Recovering files, folders, or entire drives .... .... . .... . .... . .. 207
About recovering lost data . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 207
Recovering files and folders by using file and folder backup data .... ..... 208
Recovering files and folders by using a recovery point ..... ..... .... . .... . ... 209
Select Recovery Point options .... ..... .... . .... . .... ..... ..... .... . .... . .... . . 210
Recover My Files options . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . . 212
About opening files and folders stored in a recovery point .... . .... . .... ... 213
About finding the files or folders you want ... ..... ..... .... . .... . .... . .... ..... . 213
Recovering a secondary drive . . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 213
Recover My Computer options .... ..... .... . .... . .... . .... ..... ..... .... . .... . 214
Customizing the recovery of a drive . .... . .... . .... . .... ..... ..... .... . .... . .... . .. 216
Recovery Point to Restore options ..... .... . .... . .... . .... ..... ..... .... . .... 217
Recovery options . .... ..... ..... .... . .... . .... . .... ..... .... . .... . .... . .... ..... ... 218
About restoringa computerfrom a remote location by using LightsOut
Restore ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . . 220
About setting up and using LightsOut Restore .... ..... .... . .... . .... . ... 220
Configuring LightsOut Restore ... . .... . .... . .... ..... .... . .... . .... . .... ..... . 222
Chapter 14 Recovering a computer ... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . . 227
About recovering a computer .... . .... ..... ..... .... . .... . .... . .... ..... .... . .... . ... 227
Booting a computer by using the Symantec System Recovery
Disk .... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 228
Configuring a computer to start from a CD/DVD or a USB
device ... ..... ..... .... . .... . .... . .... ..... .... . .... . .... . .... ..... ..... .... . .... 229
Preparing to recover a computer by checking the hard disk for
errors ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . ... 230
Recovering a computer ... . .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ... 231
Select a Recovery Point to Restore options ... . .... . .... . .... ..... ..... .... 233
Page 13

Drives to Recover options ... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ... 235
Recovering a computer from a virtual disk file . .... . .... ..... ..... .... . .... . ... 238
Recovery Options ... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... 240
About recovering to a computer with different hardware . . .... ..... ..... ... 243
How to use Restore Anyware ... .... . .... . .... . .... ..... ..... .... . .... . .... . ... 243
Recovering a computer through Restore Anyware ..... ..... .... . .... . .. 244
Recovering files and folders by using Symantec System Recovery
Disk ... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 246
Select Recovery Point options .... ..... .... . .... . .... ..... ..... .... . .... . .... . . 247
Exploring files and folders on your computer by using Symantec
System Recovery Disk ... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 249
About using the networking tools in Symantec System Recovery
Disk .... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 249
Starting networking services . .... . .... . .... ..... ..... .... . .... . .... . .... ..... . 249
Using the pcAnywhere thin host for a remote recovery . .... ..... ..... 250
Mapping anetwork drivefrom withinSymantec SystemRecovery
Disk .... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... . 252
Configuring network connection settings .... . .... . .... . .... ..... ..... .... . 253
Viewing the properties of a recovery point ... . .... . .... . .... ..... ..... .... . .... . 255
Recovery Point Properties . . .... . .... . .... ..... ..... .... . .... . .... . .... ..... .... 255
Viewing the properties of a drive within a recovery point .... . .... . .... . .... 256
Driver properties within a recovery point .... . .... . .... . .... ..... ..... .... 257
About the Support Utilities ... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 258
13Contents
Chapter 15 Copying a hard drive . ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ... 259
About copying a hard drive .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . 259
Preparing to copy a hard drive ... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .. 259
Copying one hard drive to another hard drive . . .... ..... ..... .... . .... . .... .... 261
Advanced options ... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... .... 262
Chapter 16 Using the Symantec System Recovery Granular
Restore Option . . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . . 265
About the Symantec System Recovery Granular Restore Option . .... . .... 266
Best practices when you create recovery points for use with the
Granular Restore Option . .... . .... . .... ..... .... . .... . .... . .... ..... ..... .... . .. 266
How to identify drives for backup . .... . .... ..... ..... .... . .... . .... . .... ..... 267
Starting the Granular Restore Option . .... . .... . .... . .... ..... ..... .... . .... . .... . 268
What you can do with the Granular Restore Option . .... . .... ..... ..... .... . . 268
Opening a specific recovery point .... . .... . .... ..... ..... .... . .... . .... . .... ..... .. 269
Open Recovery Points options ... . .... ..... ..... .... . .... . .... ..... ..... .... . .. 270
Restoring a mailbox . .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... 270
Restoring an email folder ... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... 271
Page 14

Contents14
Restoring an email message ... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... .... . 272
Restoring SharePoint documents ... ..... .... . .... . .... ..... ..... .... . .... . .... . ... 273
Restoring files and folders .... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... .. 274
Appendix A Using a search engine to search recovery
points ... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... .. 277
About using a search engine to search recovery points .... . .... . .... ..... ... 277
Enabling search engine support . .... . .... . .... . .... ..... ..... .... . .... . .... ..... ... 277
Installing Google Desktop ... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 278
Enabling Google Desktop support .... ..... ..... .... . .... . .... . .... ..... ..... . 279
Enabling search engine support for a backup job ... . .... . .... . .... ..... . 279
Recovering files using Google Desktop's Search Desktop feature . . .... . .. 280
Tips for finding a file using Google Desktop ... ..... .... . .... . .... . .... .... 280
Appendix B Backing up databases using Symantec System
Recovery . ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... ... 283
About backing up databases using Symantec System Recovery . . .... . .... 283
About backing up VSS-aware databases using Symantec System
Recovery ... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... . 283
About backing up non-VSS-aware databases using SymantecSystem
Recovery ... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... . 284
About creating a cold backup manually using Symantec System
Recovery or Symantec System Recovery Disk . .... . .... ..... ..... .. 285
About creating a warm backup automatically using Symantec
System Recovery ... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... ... 286
Creating a hot backup using Symantec System Recovery .... . .... . ... 287
Appendix C Backing up Active Directory ... . .... . .... ..... ..... .... . .... . .... ..... .. 289
About the role of Active Directory ... ..... ..... .... . .... . .... . .... ..... ..... .... . .. 289
Appendix D Backing up Microsoft virtual environments ..... ..... .... . .. 291
About backing up Microsoft virtual hard disks . . .... ..... .... . .... . .... . .... ... 291
About backing up and restoring Microsoft Hyper-V virtual
machines .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... 292
Page 15

Appendix E Using Symantec System Recovery 2011 and
Windows Server 2008 Core ... . .... . .... . .... ..... ..... .... . .... . . 295
About Symantec System Recovery 2011 and Windows Server 2008
Core . ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... 295
Installing SymantecSystem Recovery2011 onWindows Server2008
Core using commands ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... . 296
Running a full install with GUI support . .... ..... ..... .... . .... . .... . .... .. 296
Running a full silent install with logging ... . .... . .... ..... ..... .... . .... . .. 297
Running an agent-only silent install with logging ... ..... ..... .... . .... . 297
Index . . .... ..... ..... .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .... ..... ..... .... . .... . .... . .. 299
15Contents
Page 16

Contents16
Page 17

Chapter
Introducing Symantec™ System Recovery 2011
This chapter includes the following topics:
■ About Symantec System Recovery
■ About the components of Symantec System Recovery
■ What is new in Symantec System Recovery 2011
■ Accessing Help & Support for Symantec System Recovery
1
■ Sending your feedback regarding Symantec System Recovery 2011
About Symantec System Recovery
Symantec System Recovery is the gold standard in Windows® system recovery.
It allowsbusinesses to recover from systemloss or disasters in minutes, not hours,
or days.Symantec System Recovery provides fast, easy-to-use systemrestoration
to help IT administrators meet recovery time objectives. You can even perform
full bare metal recovery to dissimilar hardware and virtual environments for
servers, desktops, or laptops. It also provides the ability to recover systems in
remote, unattended locations.
Symantec System Recovery captures a recovery point of the entire live Windows
system. The backup includes theoperating system, applications, system settings,
files, and other items. The recovery point can be conveniently saved to various
media ordisk storage devices including SAN, NAS, DirectAttached Storage, RAID,
Blu-ray/DVD/CD, and so forth. When systems fail, you can quickly restore them
without the need for manual, lengthy, and error-prone processes.
You can manage Symantec System Recovery remotely using one of thefollowing:
Page 18
Introducing Symantec™ System Recovery 2011
18
About the components of Symantec System Recovery
■ Another licensed copy of Symantec System Recovery
■ Symantec System Recovery Management Solution (sold separately)
Symantec System Recovery Management Solution is a centralized management
application. It provides IT administrators an at-a-glance view of system recovery
jobs across your entire organization. You can centrally deploy, modify, and
maintain recovery activities, jobs, and policies for local and remote systems. You
can also monitor real-time status and quickly resolve any problems that are
identified.
Symantec System Recovery integrates with Google™ Desktop and Backup Exec
Retrieve to enable recovery of your files without IT intervention.
Using theintegrated GranularRestoreOption, youcan quickly restore individual
Microsoft® Exchange emails, folders, and mailboxes.
See “About the components of Symantec System Recovery” on page 18.
See “What is new in Symantec System Recovery 2011 ” on page 19.
About the components of Symantec System Recovery
Symantec System Recovery includes two key components:the programitself, and
the Symantec System Recovery Disk.
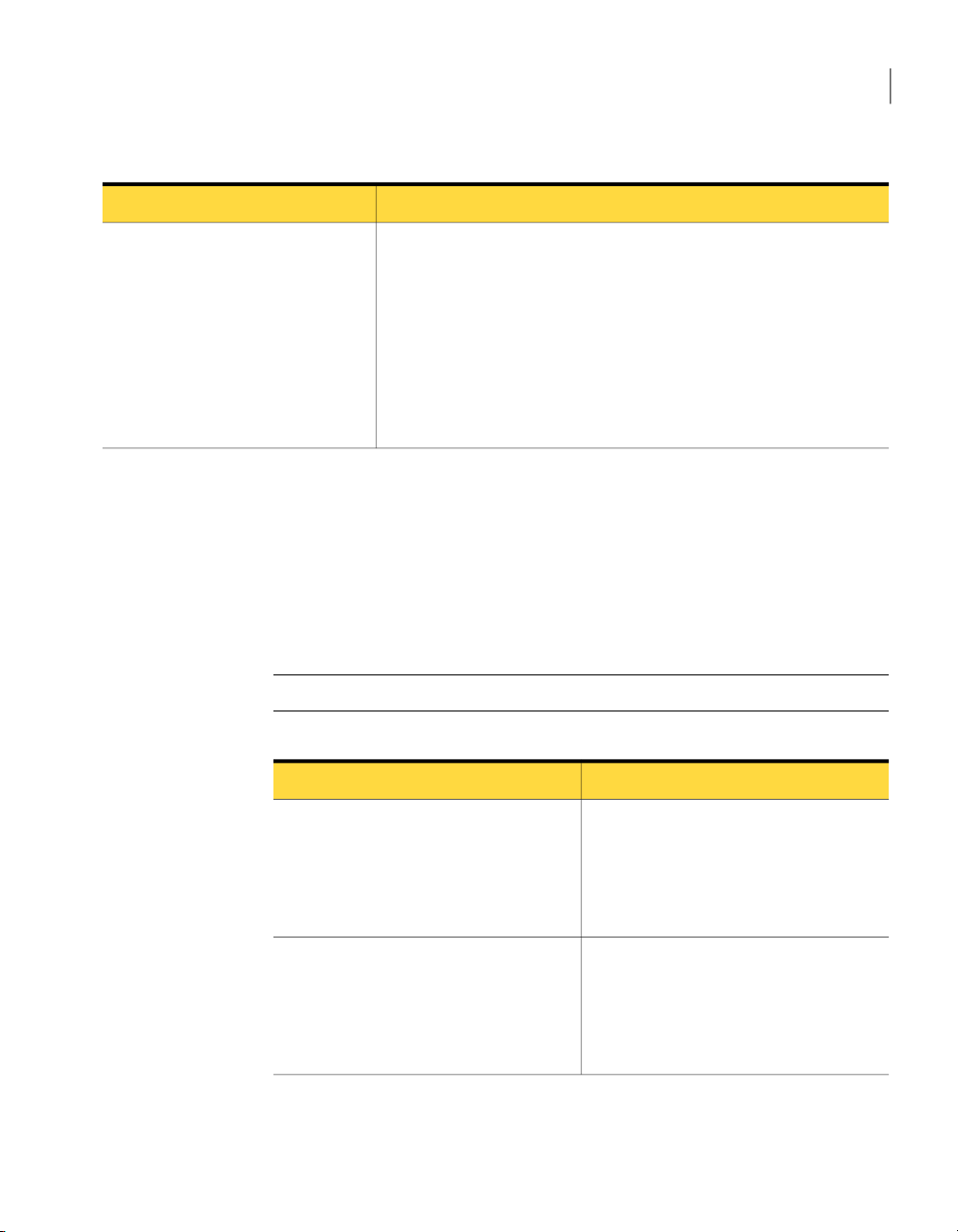
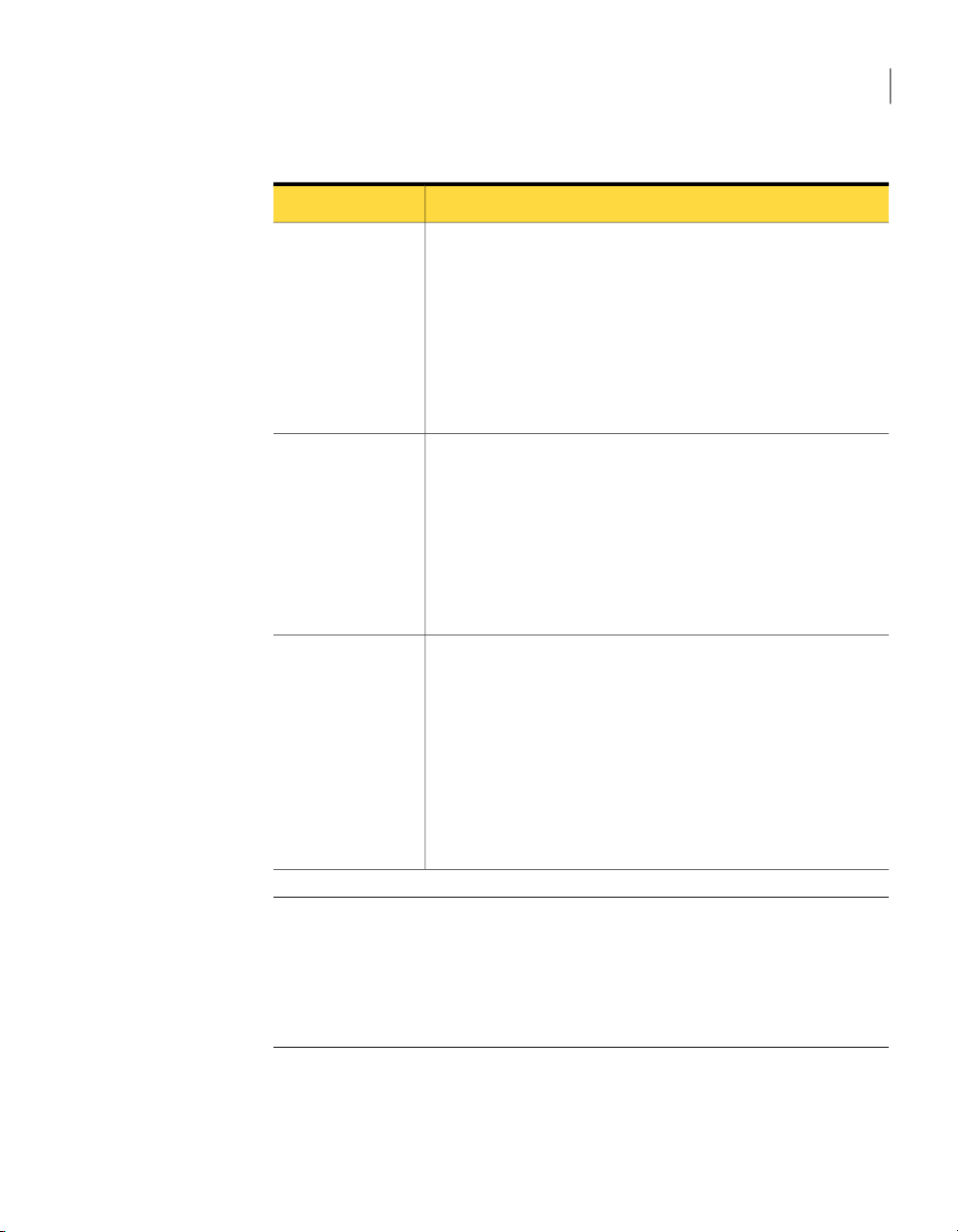
Table 1-1
Symantec System Recovery program
(user interface)
Key product components
DescriptionKey component
The Symantec System Recovery program lets you define, schedule, and
run backups of your computer. When you run a backup,recovery points of
your computerare created. Youcan thenuse the recoverypoints to recover
your entire computer, or individual drives, files, and folders.
The Symantec System Recovery also lets you do the following:
■ Manage the size of the recovery point storage (backup destination) so
that youcan useyour computer'svaluable diskspace for other purposes.
■ Monitor the backup status of your computer to make sure that your
valuable data is backed up on a regular basis.
Page 19
What is new in Symantec System Recovery 2011
19Introducing Symantec™ System Recovery 2011
Table 1-1
Key product components (continued)
DescriptionKey component
Symantec System Recovery Disk
The Symantec System Recovery Disk is used to start your computer in the
recovery environment. If your computer's operating system fails, use
Symantec System Recovery Disk to recover your system drive (the drive
where your operating system is installed).
Note: Depending on which version of the product you have purchased,
Symantec System Recovery Disk is either included on your product CD, or
as a separate CD. You should place the CD that contains Symantec System
Recovery Disk in a safe place.
See “About recovering a computer” on page 227.
See “About Symantec System Recovery” on page 17.
See “What is new in Symantec System Recovery 2011 ” on page 19.
What is new in Symantec System Recovery 2011
Symantec SystemRecovery includesmany enhancementsand new features. Refer
to thefollowing table for information about the latestfeatures and enhancements:
Note: Not all listed features are available in all versions of this product.
Table 1-2
Improved support for virtual formats
Improved platform support
What is new in Symantec System Recovery 2011
DescriptionFeature
Symantec System Recovery now includes
support for the following virtual platforms:
■ VMware ESX 4.1i
■ VMware ESX 4.1
■ Citrix XenServer 5.5 and 5.6
Symantec System Recovery now includes
support for the following platforms:
■ Microsoft Exchange Server 2010 SP1
■ Microsoft SharePoint 2010
■ Microsoft SQL Server 2008 R2
Page 20
Introducing Symantec™ System Recovery 2011
20
Accessing Help & Support for Symantec System Recovery
Table 1-2
Create custom Symantec System Recovery
Disk on a USB device.
Use ISO image file for creating custom
Symantec System Recovery Disk.
Add 64-bit drivers to the custom Symantec
System Recovery Disk.
What is new in Symantec System Recovery 2011 (continued)
DescriptionFeature
Symantec SystemRecovery nowenables you
to create a custom Symantec System
Recovery Disk on a USB device.
Symantec SystemRecovery nowlets youuse
an Symantec System Recovery Disk ISO
image file directly for creating a custom
Symantec System Recovery Disk. Until now
you were required to extract the ISO image
file for creating a custom Symantec System
Recovery Disk.
You cannow add64-bit driversto thecustom
Symantec SystemRecovery Disk.The 64-bit
drivers areused onlyfor restoringa recovery
point of a 64-bit operating system on a
computer with different hardware.
Note: SymantecSystem RecoveryDisk does
not use 64-bit drivers for starting a
computer. To start a computer having a
64-bit operating system using Symantec
System Recovery Disk the equivalent 32-bit
drivers are required.
See “About Symantec System Recovery” on page 17.
See “About the components of Symantec System Recovery” on page 18.
Accessing Help & Support for Symantec System
Recovery
To learnmore about Symantec System Recovery, visit the Helpand Support page.
The Helpand Support page provides access to the product'sHelp system and the
User's Guide. It also includes access to the Symantec Knowledge Base where you
can find troubleshooting information.
To access Help & Support
Start Symantec System Recovery.
1
On the Help menu, click Help and Support.
2
See “About Symantec System Recovery” on page 17.
Page 21

Sending your feedback regarding Symantec System Recovery 2011
See “What is new in Symantec System Recovery 2011 ” on page 19.
Sending your feedback regarding Symantec System
Recovery 2011
Please take a moment to share your feedback and ideas with Symantec regarding
Symantec System Recovery 2011.
To send feedback
Do one of the following:
◆
■ Click ShareYourIdeas in the upper-right cornerof the Symantec System
Recovery 2011 window.
■ On the Help menu, click Share Your Ideas.
See “About Symantec System Recovery” on page 17.
See “What is new in Symantec System Recovery 2011 ” on page 19.
21Introducing Symantec™ System Recovery 2011
Page 22

Introducing Symantec™ System Recovery 2011
22
Sending your feedback regarding Symantec System Recovery 2011
Page 23

Chapter
Installing Symantec System Recovery
This chapter includes the following topics:
■ Before you install Symantec System Recovery
■ Installing Symantec System Recovery
■ Updating Symantec System Recovery with LiveUpdate
■ About uninstalling Symantec System Recovery
2
Before you install Symantec System Recovery
Installation procedures might vary, depending on your work environment and
which installation options you choose. This chapter focuses on installing the full
version of Symantec System Recovery from the installation CD.
Before you install Symantec System Recovery, ensure that your computer meets
the system requirements. Review the Readme file on the installation CD for any
known issues.
See “System requirements for Symantec System Recovery” on page 23.
System requirements for Symantec System Recovery
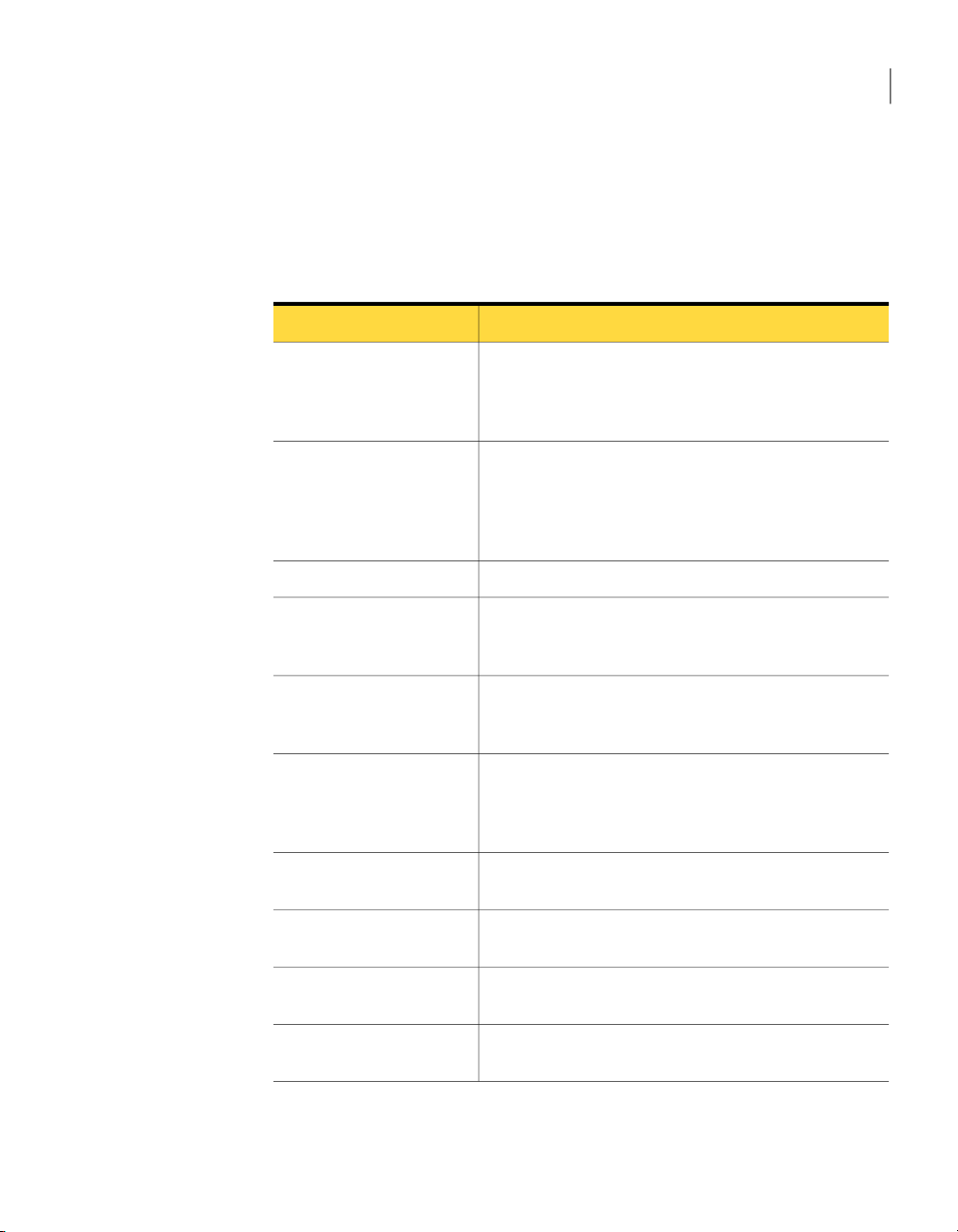
The following table lists the system requirementsfor Symantec System Recovery
to function properly.
Page 24
Installing Symantec System Recovery
24
Before you install Symantec System Recovery
Table 2-1
Operating system
RAM
Minimum system requirements
Minimum requirementsComponent
The following Windows 32-bit or 64-bit operating systems are
supported:
■ Windows 7 (all editions)
■ Windows Vista Home Basic
■ Windows Vista Home Premium
■ Windows Vista Ultimate
■ Windows Vista Business
■ Windows Vista Enterprise
■ Windows XP Professional/Home (SP2 or later)
■ Windows XP Media Center (SP2 or later)
■ Windows Server 2003
■ Windows Small Business Server 2003
■ Windows Server 2008, including SP1
■ Windows Server 2008 R2
■ Windows Essential Business Server 2008
■ Windows Small Business Server 2008
The following list indicates the memory requirements for each
component of Symantec System Recovery:
■ Symantec System Recovery Agent: 512 MB
■ Symantec System Recovery user interface and Recovery Point
Browser: 512 MB
■ Symantec System Recovery Disk: 1 GB (dedicated)
■ LightsOut Restore: 1 GB
Available hard disk
space
The following list indicates the hard disk space requirements for
Symantec System Recovery and other items:
■ When you install the entire product: Up to 430 MB is required
for a full install, depending on the language of the product you
select.
■ Microsoft .NET Framework 2.0: 280 MB of hard disk space is
required for 32-bit computers, and 610 MB is requiredfor 64-bit
computers.
■ Recovery points: Sufficient hard disk space on a local hard disk
or network server for storing recovery points.
The size of recovery points depends on the amount of data you
have backed up and the type of recovery point that is stored.
■ LightsOut Restore: 2 GB
Page 25
Before you install Symantec System Recovery
25Installing Symantec System Recovery
Table 2-1
CD-ROM or
DVD-ROM drive
Software
Virtual platforms
(for converted
recovery points)
Minimum system requirements (continued)
Minimum requirementsComponent
The drive can be any speed, but it must be capable of being used as
the startup drive from the BIOS.
Symantec System Recovery uses Gear Software technology. To
verify that your CD writer or DVD writer is compatible, visit the
Gear Software Web site.
http://www.gearsoftware.com
You canlook upinformation aboutyour writerif youknow thename
of the manufacturer and model number of your writer.
The Microsoft .NET Framework 2.0 or later is required to run
Symantec System Recovery.
If .NET Framework is not already installed, you are prompted to
install it after Symantec System Recovery is installed and your
computer is restarted.
If you want to be able to restore email using the Granular Restore
Option, you must have Microsoft Outlook 2003, 2007, or 2010
installed.
The following virtual platforms are supported:
■ VMware Workstation 4, 5, 6, and 6.5
■ VMware ESX 3.0, 3.5, 4.0, and 4.1
■ VMware ESX 3.5i , 4.0i, and 4.1i
■ VMware Server 1
■ VMware GSX Server 3.x (replaced by VMware Server)
■ Microsoft Virtual Server 2005 R2 and later
■ Microsoft Hyper-V 1.0 and 2.0
■ Citrix XenServer 5.5
Note: Windows 2000 Server/AdvancedServer, andWindows SmallBusiness Server
2000 are not supported in Symantec System Recovery 2011. You can still use
Backup Exec System Recovery 8.5 on these versions of Windows 2000. You can
also perform backup and restorefunctions remotelyon Windows 2000 computers
using Symantec System Recovery 2011 or Symantec System Recovery 2011
Management Solution.
See “About supported file systems and removable media ” on page 26.
Page 26

Installing Symantec System Recovery
26
Before you install Symantec System Recovery
About supported file systems and removable media
Symantec System Recovery supports the following file systems and removable
media:
Supported file
systems
Symantec System Recovery supports the following file systems:
■ FAT16, FAT16X
■ FAT32, FAT32X
■ NTFS
■ GUID partition table (GPT)
■ Dynamic disks
■ Linux Ext2, Linux Ext3
■ Linux swap partitions
Note: You must decrypt encrypted NTFS drives before you attempt to
restore them. You cannot view the files that are in a recovery point for an
encrypted NTFS drive.
Removable
media
You cansave recovery points locally (that is, on the same computer where
Symantec System Recovery is installed). Or, you can save recovery points
to most Blu-ray, DVD-R(W), DVD+RW, CD-R, and CD-RW recorders. You
can find an updated list of supported drives on the Gear Software Web
site.
http://www.gearsoftware.com
Symantec System Recovery also lets you save recovery points to most
USB devices, 1394 FireWire devices, REV, Jaz, Zip drives, and
magneto-optical devices.
See “System requirements for Symantec System Recovery” on page 23.
About the availability of features in Symantec System Recovery
Symantec System Recovery is packaged to meet various markets. Some features
might not be available, depending on the product you have purchased. However,
all features are documented. You should be aware of which features are included
with the version of the product you have purchased. If a feature is not accessible
in the product user interface, it is likely not included with your version of the
product.
Refer tothe Symantec Web site for information about the featuresthat areincluded
with your version of Symantec System Recovery.
See “About Symantec System Recovery Basic Edition” on page 27.
Page 27
Before you install Symantec System Recovery
About Symantec System Recovery Basic Edition
The following features are not available in Symantec System Recovery Basic
Edition. If you want to use these features,upgrade to the full version of Symantec
System Recovery.
27Installing Symantec System Recovery
Table 2-2
Centralized manageability
Recovery point sets
Blu-ray/DVD/CD support
LightsOut Restore
Recovery point indexing
Disabled features
DescriptionDisabled feature
Allows Symantec System Recovery Management Solution
to remotely monitor and manage installations of Symantec
System Recovery that are found on a network. It also
includes the ability to remotely back up and recover data.
Captures aninitial, fullbackup ofa drive. Additional backups
only capture the changes that were made to data on the
drive since the full backup was performed. Without this
feature, you can create only independent recovery points
(full backups) of a drive.
Copies allcontents of one hard drive to a second harddrive.Copy My Hard Drive Wizard
Backs up your computer directly to Blu-ray, DVD, or CD
media. Or, copy recovery points to Blu-ray, DVD, or CD
media.
Restores a computer from a remote location, regardless of
the state of the computer, provided that its file system is
intact.
Lets a search engine index all of the file names that are
contained ineach recoverypoint. Byindexing thefile names,
you can then use your search engine to locate the files to
restore.
Google Desktop™ support
Backup Exec Retrieve
support
File and folder backup
Offsite Copy
Searches for and recovers the files that are stored in
recovery points by using Google Desktop.
Searches for and recovers the files that are stored in
recovery points by using Backup Exec Retrieve.
Limits your backup to include a selected set of files or
folders.
Copies your recovery points and stores them at one or two
locations.
You canenable these features by purchasing an upgradelicense for the full version
of Symantec System Recovery.
Page 28

Installing Symantec System Recovery
28
Before you install Symantec System Recovery
Symantec System Recovery Basic Edition may not be available in all regions. For
more information, or to purchase an upgrade license, contact your local reseller.
http://www.symantec.com/backupexec/
See “Aboutthe availability of features inSymantec System Recovery” on page 26.
See “About the trial version of Symantec System Recovery ” on page 28.
About the trial version of Symantec System Recovery
If you choose to delay installation of the license key, all features in Symantec
System Recovery remain enabled during the 60-day trial period.
However, you cannot use Symantec System Recovery Disk, a component of
Symantec System Recovery, during the trial period.
You needa valid license key to use thefollowing key features of Symantec System
Recovery Disk:
■ Back Up My Computer wizard
See “Aboutrunning a one-time backup from Symantec SystemRecovery Disk”
on page 94.
■ Recover My Computer wizard, which lets you useRestore Anyware to restore
a virtual disk (.vmdk or .vhd) back to a physical computer that has different
hardware.
See “About recovering to a computer with different hardware” on page 243.
The trial period of Symantec SystemRecovery begins when you do any one of the
following in the software:
■ Define a drive-based or file and folder backup.
■ Recover a computer.
■ Copy a drive.
■ Consolidate incremental recovery points.
■ Run a drive-based backup or file and folder backup.
■ Define a scheduled convert to virtual disk job.
■ Run a scheduled convert to virtual disk job.
■ Define a one time convert to virtual disk job.
■ Define a drive-based or file and folder backup.
■ Recover a computer.
■ Consolidate incremental recovery points.
Page 29

Installing Symantec System Recovery
■ Run a drive-based or file and folder backup.
If you use the product in trial mode,it expires after 60 days. However, all features
are enabled until the end of the trial period, at which time you must purchase the
product or uninstall it. You can purchase a license at any time (even after the trial
period expires) without reinstalling the software.
Note: If this product came already installed from a computer manufacturer, your
trial period could be as long as 90 days. The product licensing or activation page
in the installation wizard indicates the duration of your trial period.
See “Activating Symantec System Recovery after the trial period” on page 33.
Installing Symantec System Recovery
Before you begin, you should review the system requirements for installing
Symantec System Recovery.
See “System requirements for Symantec System Recovery” on page 23.
29Installing Symantec System Recovery
Note: During the installation process, you might be required to restart the
computer. Youshould ensure proper functionality of the computerafter it restarts.
To do so, log on again using the same user credentials that you used to log on
when you installed Symantec System Recovery.
Warning: The Symantec System Recovery Disk provides the tools that you need
to recover your computer. The Symantec System Recovery Disk may be included
on yourproduct CD or on a separate CD,depending on your version of the product.
Store the CD in a safe place.
To install Symantec System Recovery
Log onto your computer using either the Administrator account oran account
1
with administrator privileges.
Insert the Symantec System Recoveryproduct CD into the media drive of the
2
computer.
The installation program should start automatically.
Page 30

Installing Symantec System Recovery
30
Installing Symantec System Recovery
3
4
5
6
If the installation program does not run, type the following command at a
command prompt:.
<drive>:\browser.exe
where <drive> is the drive letter of your media drive.
In the CD browser panel, click Install Symantec System Recovery.
In the License Agreement panel, read the license agreement, and then click
I accept the terms in the license agreement.
Do one of the following:
■ In theLicense Agreement panel, click InstallNow to begin theinstallation.
■ In the License Agreement panel, click Custom Install, select the options
you want installed, and then click Install Now.
Note: Deselect any of the options you do not want to install at this time.
You can install them later by modifying the Symantec System Recovery
program using the Windows Add or Remove Programs tool.
See “Custom Install options” on page 30.
Click Finish to complete the installation.
7
Remove the product CD from the media drive, and then click Yes to exit the
8
installation wizard and restart the computer.
If you click No, you cannot run Symantec System Recovery until after you
restart your computer.
See “Completing the installation of Symantec System Recovery” on page 31.
Custom Install options
The following table describes the options that are available on the CustomSetup
panel.
Table 2-3
Backup and Recovery Service
Recovery Point Browser
Custom Install options
DescriptionOptions
Installs the primary service that is required
to back up or recover your computer.
Enables you to browse, mount, copy, verify,
and restore files and folders using recovery
points.
Page 31

Installing Symantec System Recovery
31Installing Symantec System Recovery
Table 2-3
User Interface
Agent Deployment
Granular Restore Option
CD/DVD Support
Custom Install options (continued)
DescriptionOptions
Installs the product user interface that is
required for interacting with the Symantec
System Recovery Service.
This option appears when you expand the
User Interface option.
Allows the computer on which you have
installed Symantec System Recovery to
deploy theSymantec SystemRecovery Agent
to other computers. The Symantec System
Recovery Agent is required for remote
recovery management.
This option appears when you expand the
User Interface option.
Lets you open recovery points and restore
Microsoft Exchange mailboxes, folders, and
individual messages. You can also restore
Microsoft SharePoint documents and
unstructured files and folders.
Lets you back up directly to a CD or a DVD
and create a custom Symantec System
Recovery Disk. A CD or a DVD writer is
required to use this feature.
LiveUpdate
Keeps your Symantec software up to date
with the latest product updates.
See “Installing Symantec System Recovery” on page 29.
Completing the installation of Symantec System Recovery
After you complete Symantec System Recovery installation and restart your
computer, the Symantec System Recovery setup wizard starts automatically.
Using the setup wizard you can license or activate your product. You can then
run LiveUpdateto check for product updates, and thenconfigure yourfirst backup.
Note: If this product came already installed from a computer manufacturer, your
trial period could be as long as 90 days. Refer to the Activate later label on the
Product Activation panel in the setup wizard.
Page 32

Installing Symantec System Recovery
32
Installing Symantec System Recovery
To complete the installation of Symantec System Recovery
1
2
In the Welcome panel, click Next.
If your computer manufacturer installed the product, the Welcome page
might appear the first time that you run Symantec System Recovery.
Do one of the following:
■ Click I've already purchased the product and have a license key.
Note: You can find the license key on the back of your product CD jacket.
Do not lose the license key. You must use it when you install Symantec
System Recovery.
■ Click Activate later to delay the activation of your license. After the trial
period ends, the product will no longer work.
See “About the trial version of Symantec System Recovery ” on page 28.
■ If Symantec System Recovery is a trial version and you want to purchase
a license key, click Symantec Global Store.
■ If you have a Volume Incentive Program (VIP) Activation key, enter it in
the appropriate spaces as it appears on your certificate.
Click Next.
3
Do any of the following:
4
■ Click RunLiveUpdate to check forany product updates since theproduct
shipped.
■ Click Launch Easy Setup to open the Easy Setup window when you
complete the install process. (This option is not available in the server
versions of Symantec System Recovery.)
■ Click EnableGoogle DesktopFile andFolderRecovery if you wantGoogle
Desktop to search your recovery points for the files and folders that you
want to recover.
If youselect thisoption, Symantec System Recovery automatically catalogs
each file as it creates a recovery point. Google Desktop can then use this
catalog to search for files by name. It does not index the contents of the
files.
Note: This option is available only if Google Desktop is already installed
on your computer. If you plan to install Google Desktop, you can enable
search engine support later.
Page 33

Updating Symantec System Recovery with LiveUpdate
See “Enabling search engine support” on page 277.
Click Finish.
5
See “Activating Symantec System Recovery after the trial period” on page 33.
Activating Symantec System Recovery after the trial period
If you do not activateSymantec System Recovery before the trial period ends, the
software stops working. However, you can activate the product at any time after
the trial period expires.
To activate Symantec System Recovery after the trial period
On the Help menu, click Enter License Key.
1
Click I've already purchased the product and have a license key.
2
Note: You can find the license key on the back of your product CD jacket.
Enter the license key in the appropriate spaces.
3
Click Next, and then click Finish.
4
See “About the trial version of Symantec System Recovery ” on page 28.
33Installing Symantec System Recovery
Updating Symantec System Recovery with LiveUpdate
You canreceive software updates for yourversion of the product over an Internet
connection. LiveUpdate connects to the Symantec LiveUpdate server and
automatically downloads and installs updates for each Symantec product that
you own.
You run LiveUpdate as soon as you install the product. You should continue to
run LiveUpdate periodically to obtain program updates.
To update Symantec System Recovery with LiveUpdate
On the Help menu, click Run LiveUpdate.
1
In the LiveUpdate window, click Start to install the updates.
2
When the installation is complete, click Close.
3
Some program updates might require that you restart your computer before
the changes take effect.
See “Installing Symantec System Recovery” on page 29.
Page 34

Installing Symantec System Recovery
34
About uninstalling Symantec System Recovery
About uninstalling Symantec System Recovery
When you upgrade Symantec System Recovery from a previous version of the
product, the install program automatically uninstalls the previous versions. If
required, you can manually uninstall the product.
Follow your operating system's instructions on how to uninstall software.
See “Activating Symantec System Recovery after the trial period” on page 33.
Page 35

Chapter
Ensuring the recovery of your computer
This chapter includes the following topics:
■ About ensuring the recovery of your computer
■ About testing Symantec System Recovery Disk
■ Creating a custom Symantec System Recovery Disk
3
About ensuring the recovery of your computer
If Windowsfails to start or it does notrun normally,you can recover your computer
by using the Symantec System Recovery Disk. The drivers that are included on
the recoverydisk must match the drivers that arerequired to run your computer's
network cards and hard disks.
To ensure that you have the drivers required to recover your computer, you can
use the RunDriver Validation tool. The driver validation tool is available on the
Symantec System Recovery Disk. It compares hardware drivers on the Symantec
System Recovery Disk with the drivers required to run your computer's network
cards and hard disks.
You should run the driver validation test any time you make changes to the
network interface cards or storage controllers on a computer.
Note: The driver validation tool on Symantec System Recovery Disk does not
support wireless network adapter drivers.
See “About testing Symantec System Recovery Disk” on page 36.
See “Testing Symantec System Recovery Disk” on page 36.
Page 36

Ensuring the recovery of your computer
36
About testing Symantec System Recovery Disk
About testing Symantec System Recovery Disk
You should test the Symantec System Recovery Disk to ensure that the recovery
environment runs properly on your computer.
Note: Depending on the product version you have purchased, Symantec System
Recovery Disk is either included on your product CD, or as a separate CD. You
should place the CD containing Symantec System Recovery Disk in a safe place.
Testing the Symantec System Recovery Disk lets you identify and solve the
following types of problems:
■ You cannot start Symantec System Recovery Disk.
See “Configuring a computer to start from a CD/DVD or a USB device”
on page 229.
■ You do not have the necessary storage drivers to access recovery points on
the computer.
■ You need information about your system to help you run Symantec System
Recovery Disk.
See “Testing Symantec System Recovery Disk” on page 36.
Testing Symantec System Recovery Disk
The following table summarizes the steps for testing Symantec System Recovery
Disk.
Page 37

Creating a custom Symantec System Recovery Disk
37Ensuring the recovery of your computer
Table 3-1
Step 1
Step 2
Testing Symantec System Recovery Disk.
Run drivervalidation
tool
Boot your computer
using Symantec
System Recovery
Disk
Test the connectionStep 3
DescriptionActionStep
Run the driver validation tool to test whether Symantec
System Recovery Disk works with the network cards and
storage devices on the computer. If any drivers are not
included on the recovery disk, the Driver Validation
Results dialog box appears.
Without access to the correct drivers, a device cannot be
used while you run Symantec System Recovery Disk.
Therefore, if the recovery points are stored on a network
or a local hard drive, you might not have access to them.
You can find the drivers and copy them to a CD or a floppy
disk. You can also create a custom Symantec System
Recovery Disk.
See “Creating a custom Symantec System Recovery Disk”
on page 37.
Boot your computer using the Symantec System Recovery
Disk.
See “Booting a computer by using the Symantec System
Recovery Disk” on page 228.
Run amock restoreof a recovery point that is storedeither
on a network or locally on a computer. Running a mock
restore helps you to test if you can connect to the network
or the local hard drive.
See “About testing Symantec System Recovery Disk” on page 36.
Creating a custom Symantec System Recovery Disk
Symantec recommendsthat youcreate acustom Symantec System Recovery Disk,
even if driver validation succeeds, and your Symantec System Recovery Disk
appears to work. You can create a custom Symantec System Recovery Disk on a
CD/DVD or on a USB device. A custom Symantec System Recovery Disk contains
your computer's current network and storage device drivers. It helps to ensure
that inan emergency you can get to therecovery points that are required to restore
your computer.
After creatinga custom Symantec System Recovery Disk, youcan useit as a source
for creating another custom Symantec System Recovery Disk.
Page 38

Ensuring the recovery of your computer
38
Creating a custom Symantec System Recovery Disk
Note: You must have a writeable Blu-ray/DVD/CD-RW drive to create a custom
Symantec System Recovery Disk CD/DVD.
To create a custom Symantec System Recovery Disk
Attach and turn on all storage devices and network devices that you want to
1
make available.
Start Symantec System Recovery.
2
Insert the Symantec System Recovery Disk CD into your media drive.
3
On the Tasks menu, click Create Custom Recovery Disk.
4
Click Next.
5
Do one of the following:
6
If you know the path to the source
Symantec System Recovery Disk
If you do not know the path to the source
Symantec System Recovery Disk
Click Next.
7
In the Symantec System Recovery Disk Creation panel, select the settings
8
Type the path in the Symantec System
Recovery Disk media location field.
Do the following in the order listed:
■ Click Browse.
■ Click SymantecSystem Recovery Disk
ISO File to locate the path for the ISO
image file, or click Symantec System
Recovery Disk Folder to locate the
path for the disk on other media.
■ On the Open dialog box, navigate to
the location of the appropriate ISO
image file, media drive, or folder.
■ Click Open.
for creating the Symantec System Recovery Disk.
See “Symantec System Recovery Disk creation settings” on page 40.
Click Next.
9
Page 39

Creating a custom Symantec System Recovery Disk
Review the list of storage and network drivers to be included, and add
10
additional drivers or remove the drivers you do not need.
You can add 64-bit drivers to the custom Symantec System Recovery Disk.
The 64-bit drivers are used only for restoring a recovery point of a 64-bit
operating system on a computer with different hardware.
Note: SymantecSystem Recovery Disk does not use 64-bitdrivers for starting
a computer. To start a computer that has a 64-bit operating system using
Symantec System Recovery Disk, the equivalent 32-bit drivers are required.
Click Next.
11
In the Startup Options panel, select the default keyboard layout, display
12
language, and time zone from the respective lists.
Click Next.
13
In the Options panel, select the optional settings for the custom Symantec
14
System Recovery Disk.
See “Optional settings for Symantec System Recovery Disk” on page 41.
Click Next.
15
In the License Setup panel, specify how you want to enable licensed features
16
in the customized Symantec System Recovery Disk. For example, the cold
imaging feature called Back Up My Computer.
Click Next.
17
Review the summary of theoptions youhave selected for creating thecustom
18
Symantec System Recovery Disk.
Click Finish.
19
39Ensuring the recovery of your computer
Warning: Be certain to test your new custom SymantecSystem RecoveryDisk.
It ensures that you can use the Symantec System Recovery Disk to start your
computer and can access the drive that contains your recovery points.
See “Testing Symantec System Recovery Disk” on page 36.
See “Creating a custom Symantec System Recovery Disk” on page 37.
See “About testing Symantec System Recovery Disk” on page 36.
See “About updating Symantec System Recovery Disk on USB” on page 40.
Page 40

Ensuring the recovery of your computer
40
Creating a custom Symantec System Recovery Disk
About updating Symantec System Recovery Disk on USB
Whenever new drivers or driver versions are added to your computers, you must
add them to the Symantec System Recovery Disk. If your Symantec System
Recovery Disk is on a CD/DVD, you need to create a new custom recovery disk to
include the new drivers. However, if your Symantec System Recovery Disk is on
a USB device, you can update it rather than creating a new one.
To update an existing Symantec System Recovery Disk on a USB device, run the
CreateCustomSymantecRecoveryDisk wizard.Ensure that you use theexisting
Symantec System Recovery Disk on the USB device as the source as well as the
destination. DuringSymantec System Recovery Disk creation, the existingdrivers
are retained and only the new drivers are added to the recovery disk.
Note: You can add drivers from multiple computers to a single Symantec System
Recovery Disk on a USB device.
See “Creating a custom Symantec System Recovery Disk” on page 37.
Symantec System Recovery Disk creation settings
The followingtable describes the options on the SymantecSystem Recovery Disk
Creation panel in the Create Custom Symantec System Recovery Disk wizard.
Table 3-2
Symantec System Recovery Disk creation settings
DescriptionOption
Disk label
Create Symantec System
RecoveryDiskonCD/DVDorUSB
device
Lets you specifythe name that you want to use for the
Symantec System Recovery Disk label.
Lets you save your customized Symantec System
Recovery Disk to a CD/DVD or a USB device. Select
this option and then select the media drive in which
you have placed the CD/DVD or plugged in the USB
device.
Note: The existing data on the USB device is not
formatted during Symantec System Recovery Disk
creation.
Save a copy of the custom
Symantec System Recovery Disk
(ISO file)
Lets you save your customized Symantec System
Recovery Disk as a CD/DVD image (.iso) file. To save
the Symantec System Recovery Disk as an .iso file,
select this option. Then specify the path where you
want to save the resulting file.
Page 41

Creating a custom Symantec System Recovery Disk
41Ensuring the recovery of your computer
Table 3-2
Symantec System Recovery Disk creation settings (continued)
DescriptionOption
Skip Symantec SystemRecovery
Disk Customization
Lets you skip the remaining panels of the Create
Custom Symantec System Recovery Disk wizard. If
you donot wantto changeany ofthe defaultSymantec
System Recovery Disk options, select this option.
See “Creating a custom Symantec System Recovery Disk” on page 37.
Optional settings for Symantec System Recovery Disk
The following table describes the options on the Options panel in the Create
Custom Symantec System Recovery Disk wizard.
Table 3-3
Automatically start network
services
Dynamic IP
Optional settings for Symantec System Recovery Disk
DescriptionOption
Starts networkingautomatically whenyou recoverthe
computer through LightsOut Restore.
Connects to a network withoutthe need for additional
network configuration.You can click this option if you
know there is a DHCP server available on the network
at the time you restore.
Static IP
Automatically start Symantec
pcAnywhere
Configure
Use Windows firewall settings
Connects to a network with a particular network
adapter andspecific address settings. You should click
this optionif youknow thereis noDHCP server(or the
DHCP server is unavailable) when you recover.
Starts the Symantec pcAnywhere thin host
automatically when you start Symantec System
Recovery Disk.
Lets you configure log on credentials and other
optional parameters for pcAnywhere.
See “Optionsfor configuringpcAnywhere” on page 42.
Saves the current Windows firewall settings to the
Symantec System Recovery Disk.
See “Creating a custom Symantec System Recovery Disk” on page 37.
Page 42

Ensuring the recovery of your computer
42
Creating a custom Symantec System Recovery Disk
Options for configuring pcAnywhere
The followingtable describesthe options on the Configure Symantec pcAnywhere
panel. This panel is available from the Options panel in the Create Custom
Symantec System Recovery Disk wizard.
Table 3-4
User name
Password
Confirm password
Host name
Encryption level
Encryption level-None
Encrytion
level-pcAnywhere
Options for configuring pcAnywhere
DescriptionOption
Lets you type the user name for authenticating to
pcAnywhere.
Lets you type the password for authenticating to
pcAnywhere.
Lets you retype the password for authenticating to
pcAnywhere.
Lets you type the name that you want to use for the host.
You can leave this box blank to configure the host name to
be the same as the computer name.
Lets you encrypt the data stream between the host and
remote computer.
Lets youspecify thatno encryption of the data stream occurs
between the host and the remote computer.
Lets you scramble the data using a mathematical algorithm
so that a third party cannot easily interpret it.
This option is available on any operating system that
pcAnywhere supports.
Encryption
level-Symmetric
Lets you encode and decode data using a cryptographic key.
This option is available on any Windows operating system
that supports the Microsoft CryptoAPI.
See “Optional settings for Symantec System Recovery Disk” on page 41.
See “Creating a custom Symantec System Recovery Disk” on page 37.
Page 43

Getting Started
This chapter includes the following topics:
■ How to use Symantec System Recovery
■ Starting Symantec System Recovery
■ Configuring Symantec System Recovery default options
■ Setting up your first backup using Easy Setup
■ Hiding or showing the Advanced page
Chapter
4
How to use Symantec System Recovery
Symantec System Recovery helps you in backing up your files, folders, or entire
drives. Toback upyour data,you needto definea backup.A backupspecifies what
data to back up, when to back it up, and where to put the backed up data.
Using Symantec System Recovery includes the following key tasks:
■ Defining a backup
■ Running a backup
■ Recovering files, folders, or entire drives
Refer to the following figure to understand the relationship of these tasks.
Page 44

Getting Started
44
How to use Symantec System Recovery
Figure 4-1
Using Symantec System Recovery
See “Starting Symantec System Recovery” on page 45.
See “Configuring Symantec System Recovery default options” on page 45.
Page 45

Starting Symantec System Recovery
Symantec System Recovery is installed in the Windows program files folder by
default. During installation, a program icon is installed in the Windows system
tray from which you can open Symantec System Recovery. You can also open
Symantec System Recovery from the Windows Start menu.
To start Symantec System Recovery
Depending onthe Windows version you are running, use one ofthe following
◆
methods:
■ On the classic Windows taskbar, click Start > Programs > Symantec
System Recovery.
■ On the Windows taskbar, click Start> All Programs > Symantec System
Recovery.
■ In theWindows systemtray, double-click the SymantecSystemRecovery
tray icon.
■ In the Windows system tray, right-click the Symantec System Recovery
tray icon, and then click Open Symantec System Recovery.
See “Configuring Symantec System Recovery default options” on page 45.
Starting Symantec System Recovery
45Getting Started
Configuring Symantec System Recovery default options
The Options dialog box includes several views that let you configure Symantec
System Recovery default options.
To configure Symantec System Recovery default options
On the Tasks menu, click Options.
1
Select anoption you want to edit, make anynecessary changes, and then click
2
OK.
See “Setting up general backup options” on page 46.
See “Adjusting the effect of a backup on computer performance” on page 48.
See “Enabling network throttling” on page 49.
See “Adjusting default tray icon settings” on page 49.
See “Adding new file types and extensions” on page 51.
See “Renaming file types and extensions” on page 51.
See “Restoring default file types and extensions” on page 52.
Page 46

Getting Started
46
Configuring Symantec System Recovery default options
See “Deleting a file type and all of its extensions” on page 53.
See “Enabling search engine support” on page 277.
See “Removing or changing the unique name for an external drive” on page 54.
See “Configuring default FTP settings for use with Offsite Copy” on page 54.
See “Logging Symantec System Recovery messages” on page 56.
See “Enabling email notifications for product (event) messages” on page 58.
See “Configuring Symantec System Recovery to send SNMP traps” on page 155.
Setting up general backup options
You can specify the default destination for storing recovery points and file and
folder backup data that is created when you run a backup. This default location
is used if you do not specify a different location when you define a new backup.
You can also choose to prepend your computer's name to backup data file names
and save each backup file to a new subfolder.
To set up general backup options
On the Tasks menu, click Options.
1
Click General.
2
Set the appropriate options for your backups.
3
See “General options” on page 46.
Click OK.
4
See “Configuring Symantec System Recovery default options” on page 45.
General options
The following table describes the options on the General page. The options you
configure here are used as default backup options.
Page 47

Configuring Symantec System Recovery default options
47Getting Started
Table 4-1
Prepend computer name to backup
data file names
Save backup files to a unique subfolder
Default backup destination
General options
DescriptionOption
Adds thecomputer nameto thebeginning ofeach
backup data file name.
This option is useful if you back up more than
one computer to the same drive. For example,
you might back up a laptop and a desktop
computer to the same USB or network drive. By
prepending the computer name to each backup
data file name, you can more easily identify
which backup data files belong to which
computer.
Creates a new subfolder that serves as your
backup destination.
Note: The new subfolderis given thesame name
as yourcomputer. Forexample, ifyour computer
name is"My_Laptop", thenew subfolderis named
\My_Laptop.
Lets you specify a path to the folder where you
want to store recovery points and file and folder
backup data. If you do not know the path, you
can browse to the location.
If youentered thepath to a location on a network,
enter the user name and password that are
required for authentication.
Note: You cannot use an encrypted folder as your
backup destination. However, you can encrypt
your backup data to prevent other users from
accessing it. To encrypt your backup data, refer
to theAdvanced options when you define or edit
a backup.
See “Defining a drive-based backup” on page 74.
See “Editing advanced backup options”
on page 88.
See “Configuring Symantec System Recovery default options” on page 45.
Page 48

Getting Started
48
Configuring Symantec System Recovery default options
Adjusting the effect of a backup on computer performance
If a backup is running on your computer, your computer's performance might
slow down. The slow down in the computer's performance might be more
prominent ifit is the one creating an independent recovery point.The performance
slows down because Symantec System Recovery uses your computer's hard disk
and memory resources to perform the backup.
You canchange the speed of the backup to minimize theeffect ofSymantec System
Recovery on your computer while you work.
Note: During a backup or recovery, you have the option of overriding this default
setting to fit your needs at that moment.
To adjust the effect of a backup on computer performance
On the Tasks menu, click Options.
1
Click Performance.
2
Do one of the following:
3
■ To improve your computer's performance during backup jobs, move the
slider bar closer to Slow.
■ To enable backup jobs to run more quickly, move the slider bar closer to
Fast.
Click OK.
4
See “Adjusting the speed of a backup” on page 120.
See “Configuring Symantec System Recovery default options” on page 45.
About enabling network throttling
You canlimit the effect of a backup onnetwork performance by enabling network
throttling.
Many variables affect the network performance. Consider the following points
before you use this feature:
Network
cards
Network
backbone
Is your network wired or wireless? What are the speeds of your network
cards?
What is the size of your network pipeline? Does it support 10-MB transfer
rates, or 1-GB transfer rates?
Page 49

Configuring Symantec System Recovery default options
49Getting Started
Network
server
traffic
See “Enabling network throttling” on page 49.
See “Configuring Symantec System Recovery default options” on page 45.
How robust is your server hardware? How fast is its processor? How much
RAM does it have? Is it fast or slow?
How many computers are scheduled to back up at the same time?Backing up
Are backups scheduled to run when network traffic is heavy or light?Network
Enabling network throttling
Consider using this feature only when you know what your network can handle.
If you schedule your backups at staggered intervals and when network traffic is
low, you may not need to use this feature. Avoid backing up multiple computers
at the same time and to the same network destination.
Gather the required information about your network's performance and then
schedule backupsaccordingly. Enable this feature andset theMaximumnetwork
throttling to a setting that matches the circumstances.
To enable network throttling
On the Tasks menu, click Options.
1
Click Performance.
2
Select Enable network throttling.
3
In the Maximum network throttling field, enter the maximum amount (in
4
KB) of network throughput.
Click OK.
5
See “About enabling network throttling” on page 48.
See “Configuring Symantec System Recovery default options” on page 45.
Adjusting default tray icon settings
You can turn on the system tray icon or turn it off as required. You can choose to
show onlyerror messages,or toshow botherror messagesand otherinformation,
such as the completion of a backup.
Page 50

Getting Started
50
Configuring Symantec System Recovery default options
To adjust default tray icon settings
On the Tasks menu, click Options.
1
Click TrayIcon, and then select theoptions you wantto use for the tray icon.
2
See “Tray Icon options” on page 50.
Click OK.
3
See “Configuring Symantec System Recovery default options” on page 45.
Tray Icon options
The following table describes the options that you can select to adjust the default
tray icon settings.
Table 4-2
Tray Icon options
DescriptionOptions
Show system trayicon
Show missed backups
Show system tray
questions
Show status messages
Show error messages
Displays the Symantec System Recovery icon in the system tray.
You must select this option to enable or disable any of the
remaining options.
Notifies you when a backup was scheduled but did not run.
For example, it notifies you when your computer was turned off
at the time a backup was scheduled to run.
Offers youhelpful prompts inthe formof questions that can help
you keep your data backed up.
Displays themessages aboutthe status of backup operations.For
example, abackup hasstarted, oryour backupdestination isabout
to get full.
Displays the error messages when errors occur so that you can
resolve any issues that might hinder data protection.
See “Adjusting default tray icon settings” on page 49.
See “Configuring Symantec System Recovery default options” on page 45.
About managing file types and file extensions
When you define file and folder backups, file types are a quick way to include the
files thatyou usethe most.For example,if youkeep musicfiles on your computer,
you can configure a backup to include all music files. For example, .mp3, .wav.
Page 51

Configuring Symantec System Recovery default options
The most common file types and extensions are already defined for you. But you
can define additional file type categories as needed, and then edit them at any
time. For example, if you install a new program that requires the use of two new
file extensions (for example, .pft and .ptp,). You can define a new file type and
define the two file extensions for that category. Then when you define a backup,
you can select the new category. When the backup runs, all files that end with
.pft and .ptp are backed up.
See “Adding new file types and extensions” on page 51.
See “Renaming file types and extensions” on page 51.
See “Restoring default file types and extensions” on page 52.
See “Deleting a file type and all of its extensions” on page 53.
Adding new file types and extensions
The most common file types and extensionsare alreadydefined for you. However,
you can add additional file type categories as needed.
To add a new file type and extensions
On the Tasks menu, click Options.
1
Click File Types.
2
At the bottom of the File types list, click Add a file type (+).
3
Type a descriptive name of the new file type category, and then press Enter.
4
At the bottom of the Extensions for list, click Add an extension (+).
5
Type an asterisk (*) and a period, followed by the extension of the file type
6
you want to define, and then press Enter.
Click OK.
7
See “Renaming file types and extensions” on page 51.
See “Restoring default file types and extensions” on page 52.
See “Deleting a file type and all of its extensions” on page 53.
See “About managing file types and file extensions” on page 50.
See “Configuring Symantec System Recovery default options” on page 45.
51Getting Started
Renaming file types and extensions
You can rename existing file types and extensions as needed.
Page 52

Getting Started
52
Configuring Symantec System Recovery default options
To rename a file type and extensions
On the Tasks menu, click Options.
1
Click File Types.
2
Select a file type from the File types list, and then do one of the following:
3
■ Click Rename a file type to edit the name of the selected file type.
■ Select an extension from the Extensions for list and click Rename an
extension to edit the name of the extension.
Click OK.
4
See “Adding new file types and extensions” on page 51.
See “Restoring default file types and extensions” on page 52.
See “Deleting a file type and all of its extensions” on page 53.
See “About managing file types and file extensions” on page 50.
See “Configuring Symantec System Recovery default options” on page 45.
Restoring default file types and extensions
You can restore default file types and extensions as needed.
To restore default file types and extensions
On the Tasks menu, click Options.
1
Click File Types.
2
Select a file type from the File types list.
3
Click either Restoredefault file types list or Restore default extensions list
4
to restore all default file types or extensions.
Caution: Any file types and extensions you have setup are removed. You must
add them again manually.
Click OK.
5
See “Adding new file types and extensions” on page 51.
See “Renaming file types and extensions” on page 51.
See “Deleting a file type and all of its extensions” on page 53.
See “About managing file types and file extensions” on page 50.
See “Configuring Symantec System Recovery default options” on page 45.
Page 53

Configuring Symantec System Recovery default options
Deleting a file type and all of its extensions
You can delete a file type and all its extensions as needed.
To delete a file type and all of its extensions
On the Tasks menu, click Options.
1
Click File Types.
2
Select a file type from the File types list, and then do one of the following:
3
■ Click the Remove a file type to delete a file type and all its extensions.
■ Select an extension from the Extensions for list and click Remove an
extension to edit the name of the extension.
Note: You cannot delete a default filetype. You can delete all but oneextension
of a default file type, and you can add additional extensions to a default file
type.
Click OK.
4
See “Adding new file types and extensions” on page 51.
See “Renaming file types and extensions” on page 51.
See “Restoring default file types and extensions” on page 52.
See “About managing file types and file extensions” on page 50.
See “Configuring Symantec System Recovery default options” on page 45.
53Getting Started
About using unique names for external drives
Symantec SystemRecovery letsyou assign unique names to external drives when
you use them as a backup destination or an Offsite Copy destination. Assigning
unique names helps you to manage these destinations and avoid confusion if you
use more than one drive. It is especially helpful when the assigned drive letter
changes each time you plug in the drive.
Note: Using a unique name does not change the drive label. The unique name is
used only when you access a drive from within Symantec System Recovery.
For example, you might swap out two different external drives that are used as
Offsite Copy destinations during any given week. It would be difficult to identify
which drive your use at any given time basedon the drive labels. It becomes more
confusing if the previously assigned drive letter has changed.
Page 54

Getting Started
54
Configuring Symantec System Recovery default options
However, you can associate unique names with each drive when you use them
with Symantec System Recovery. Theunique name that is associatedwith a drive
is displayed in various locations in Symantec System Recovery.
Note: Placing physical labels on each external drive to help you manage the task
of swapping the drives is also a good idea.
For example, if you assigned the unique name, "Cathy Read" to one drive, and
"Thomas Read"to a second drive. Their unique names appear inSymantec System
Recovery whenever the drives are plugged in to your computer.
See “About Offsite Copy” on page 100.
To makeit eveneasier, theOptions dialogbox letsyou see all of your drive unique
names in one view. From this view, you can remove or edit existing names.
See “Removing or changing the unique name for an external drive” on page 54.
Removing or changing the unique name for an external drive
You can remove or change the unique name for the drive as needed.
Note: Symantec System Recovery lets you assign a unique name when you plug
in an external drive in to your computer for the first time.
To remove or change unique name for an external drive
On the Tasks menu, click Options.
1
Under Destinations, click External Drives.
2
Select an external drive from the list and then do one of the following:
3
■ Click Remove to delete the unique name that is associated with the
external drive.
■ Click Rename to edit the unique name.
Click OK.
4
See “About using unique names for external drives” on page 53.
Configuring default FTP settings for use with Offsite Copy
File transfer protocol , or FTP, is the simplest and most secure way to copy files
over theInternet. Symantec System Recovery serves as anFTP clientto copyyour
recovery points to a remote FTP server. You can copy your recovery points to an
FTP server as a secondary backup of your critical data.
Page 55

Configuring Symantec System Recovery default options
The Options dialog box lets you configure FTP settings to help ensure that your
recovery points are copied to your FTP server.
To configure default FTP settings for use with Offsite Copy
On the Tasks menu, click Options.
1
Under Destinations, click Configure FTP.
2
Select the appropriate options.
3
See “FTP configuration options” on page 55.
Click OK.
4
See “Configuring Symantec System Recovery default options” on page 45.
FTP configuration options
The following table describes the options that you can select to configure the
default FTP settings for use with Offsite Copy.
55Getting Started
Table 4-3
Connection mode: Passive
(Recommended)
Connection mode: Active
Limitconnectionattempts to
Stop trying to connect after
Default port
FTP configuration options
DescriptionOption
Helps prevent conflicts with security systems. This mode
is necessary for some firewalls and routers. When you use
passive mode, the FTP client opens the connection to an IP
address and port that the FTP server supplies.
Enables a server to open a connection to an IP address and
port that the FTP client supplies. Use active mode when
connections or transfer attempts fail in passive mode, or
when you receive data socket errors.
Indicates the number of times Symantec System Recovery
tries to connect to an FTP server before it gives up.
Symantec SystemRecovery canattempt amaximum of 100
times.
Indicates thenumber ofseconds Symantec SystemRecovery
tries toconnect toan FTPserver beforeit givesup. Youcan
specify up to 600 seconds (10 minutes).
Indicates the port of the FTP server that listens for a
connection.
You shouldconsult the FTP server administratorto besure
that the port you specify is configured to receive incoming
data.
Page 56

Getting Started
56
Configuring Symantec System Recovery default options
See “Configuring default FTP settings for use with Offsite Copy” on page 54.
Logging Symantec System Recovery messages
You can specify which product messages (errors, warnings, and information) are
logged asthey occur, and where the log fileis stored. Product messages can provide
useful information about the status of backups or related events. They can also
provide helpful information when you need to troubleshoot.
Two logging methods are available: Symantec System Recovery logging and the
Windows application log.
To log Symantec System Recovery messages
On the Tasks menu, click Options.
1
Under Notifications, click Log File.
2
Select the appropriate log file options.
3
See “Log File options” on page 56.
Click OK.
4
To configure which product events are written to a Windows event log
On the Tasks menu, click Options.
1
Under Notifications, click Event Log.
2
Select the appropriate event log options.
3
See “Event log options” on page 57.
Click OK.
4
See “Configuring Symantec System Recovery default options” on page 45.
Log File options
The following table describes the options to log Symantec System Recovery
messages.
Page 57

Configuring Symantec System Recovery default options
57Getting Started
Table 4-4
Select the priority and type of
messages
Log file location
Maximum file size
Log File options
DescriptionOption
Lets you select the priority level at which messages
should be logged. You can choose to log all or no
messages regardless of priority levels.
Select one of the following options:
■ All messages
■ Medium and high priority messages
■ High priority messages
■ No messages
Logs the error messages as they occur.Errors
Logs the warning messages as they occur.Warnings
Logs the information messages as they occur.Information
Lets you specify a path where you want to create and
store the log file.
If you do not know the path, you can browse to the
location.
Lets you specify the maximum size (in kilobytes) that
the log file is allowed to grow.
The file is kept within the limit you set by replacing the
oldest logged items in the file with new items as they
occur.
See “Logging Symantec System Recovery messages” on page 56.
Event log options
The following table describes the options to configure which product events are
written to a Windows event log.
Page 58

Getting Started
58
Configuring Symantec System Recovery default options
Table 4-5
Event log options
DescriptionOption
Select the priority and type of
messages
Lets you select the priority level at which messages
should be logged. You can choose to log all or no
messages regardless of priority levels.
Select one of the following options:
■ All messages
■ Medium and high priority messages
■ High priority messages
■ No messages
Logs the error messages as they occur.Errors
Logs the warning messages as they occur.Warning
Logs the information messages as they occur.Information
See “Logging Symantec System Recovery messages” on page 56.
Enabling email notifications for product (event) messages
Email notifications can be sent to a specified email address if there are any errors
or warnings that occurred when a backup is run.
Note: If you do not have an SMTP server, this feature is unavailable to you.
Notifications can also be sent to the system event log and a custom log file. The
custom log file is located in the Agent folder of the product installation.
If notifications are not delivered, check the setup of your SMTP server to ensure
that it functions properly.
To enable email notifications for product (event) messages
On the Tasks menu, click Options.
1
Under Notifications, click SMTP Email.
2
Select the appropriate options.
3
See “SMTP Email options” on page 59.
Click OK.
4
See “Configuring Symantec System Recovery default options” on page 45.
Page 59

Configuring Symantec System Recovery default options
SMTP Email options
The followingtable describes the options toenable email notifications for product
(event) messages.
59Getting Started
Table 4-6
Select the priority and type of
messages
To address
(admin@domain.com)
From address
SMTP server
(smtp.domain.com)
SMTP Email options
DescriptionOption
Lets you select the priority level at which messages
should be logged. You can choose to log all or no
messages regardless of priority levels.
Select one of the following options:
■ All messages
■ Medium and high priority messages
■ High priority messages
■ No messages
Logs the error messages as they occur.Errors
Logs the warning messages as they occur.Warnings
Logs the information messages as they occur.Information
Lets you specify the email address (for example,
admin@domain.com) where notifications are to be sent.
Lets you specify the email address of the sender.
The Fromaddress isnot mandatory. If you do not specify
a From address, the name of the product is used.
Lets you specify the path to the SMTP server that sends
the email notification (for example,
smtpserver.domain.com).
SMTP Authentication
Lets you specify the method to authenticate to the
specified SMTP server.
Lets you specify the SMTP user name.User name
Lets you specify the SMTP password.Password
Note: If you are not sure what your SMTP user name and password are, contact
a system administrator.
See “Enabling email notifications for product (event) messages” on page 58.
Page 60

Getting Started
60
Setting up your first backup using Easy Setup
Setting up your first backup using Easy Setup
If you had selected the Launch Easy Setup check box during the setup wizard,
the Easy Setup window appears the first time you open the Run or Manage
Backups window.
Note: The Easy Setup window is not available in server versions of Symantec
System Recovery.
To set up your first backup using Easy Setup
On the Tasks menu, click Run or Manage Backups.
1
In the Easy Setup window, either accept the default drive and file and folder
2
backup settings, or click any of the settings to edit them.
Click OK.
3
In the First Backup window, do one of the following:
4
■ Select Run first backup according to schedule to run the backup as per
the schedule that you specified.
■ Select Run backup now to run the backup immediately.
Click OK.
5
See “Configuring Symantec System Recovery default options” on page 45.
Hiding or showing the Advanced page
The Advancedpage offersexperienced SymantecSystem Recoveryusers asingle
view of the most common product features. If you have a good understanding of
Symantec System Recovery, you might prefer to perform most tasks from the
Advanced view.
Note: When you refer to the documentation while you use the Advanced page,
the first one or two steps do not apply. The first one or two steps merely indicate
where toaccess eachfeature from the other pages of the user interface. From that
point on, follow the remaining steps of each procedure.
The Advanced page can be hidden from view if you do not plan to use it.
Page 61

Hiding or showing the Advanced page
To hide or show the Advanced page
Start Symantec System Recovery.
1
On the View menu, click Advanced to hide or show the Advanced page.
2
See “Configuring Symantec System Recovery default options” on page 45.
61Getting Started
Page 62

Getting Started
62
Hiding or showing the Advanced page
Page 63

Chapter
Best practices for backing up your data
This chapter includes the following topics:
■ About backing up your data
■ About choosing a backup type
■ What to do before you back up
■ What to do during a backup
5
■ What to do when a backup is finished
■ Tips for running defined backups
■ Viewing the properties of a backup job
■ About selecting a backup destination
■ About backing up dual-boot computers
About backing up your data
To backup your computer or your individual filesand folders, you do the following:
■ Define a backup.
■ Run the backup.
See “How to use Symantec System Recovery” on page 43.
When you define a backup, you decide on the following:
■ What to back up (files and folders, or an entire drive).
■ Where to store the backup data (backup destination).
Page 64

Best practices for backing up your data
64
About choosing a backup type
■ Whether or not to use Offsite Copy to copy backup data to remote locations.
■ When to run the backup (automatically or manually).
■ What compressionlevels tospecify forrecovery points,and whetherto enable
security settings (encryption and password protection).
■ Which of the many other options you want to use. You can customize each
backup according to your backup needs.
See “About choosing a backup type” on page 64.
See “About selecting a backup destination” on page 69.
See “About backing up dual-boot computers” on page 71.
About choosing a backup type
You canuse the following guidelines to determine whichtype of backup to choose:
Drive-based backup
File and folder backup
Use this backup type to do the following:
■ Back up and recover your computer's system drive.
Typically, itis the C drive, which includes your operating
system).
■ Back up and recover a specific hard drive. For example,
a secondary drive other than the system drive that
includes your operating system.
■ Recover lost or damaged files or folders from a specific
point in time.
Use this backup type to do the following:
■ Back up and recover specific files and folders. For
example, your personal files that are stored in the My
Documents folder.
■ Back upand recoverfiles ofa specifictype. Forexample,
music (.mp3 or .wav) or photographs (.jpg or .bmp).
■ Recover a specific version of a file from a specific point
in time.
See “About selecting a backup destination” on page 69.
See “About backing up your data” on page 63.
What to do before you back up
Consider these best practices before you define and run your first backup:
Page 65

What to do before you back up
65Best practices for backing up your data
Schedule backups at a time when
you know your computer is on.
Use a secondary hard disk as your
backup destination.
Consider using external drives as
your backup destination.
Give uniquenames toyour external
drives to help you easily identify
them.
Your computermust be turnedon andWindows must
be running at the time a backup occurs. If not, any
scheduled backups are skipped until the computer is
turned on again. You then are prompted to run the
missed backup.
See “About choosing a backup type” on page 64.
You shouldstore recoverypoints ona harddisk other
than your primary hard disk (C). It helps ensure that
you can recover your system in the event that your
primary hard disk fails.
See “Setting up general backup options” on page 46.
Using anexternal drivemakes yourbackup datamore
portable. Shouldyou needto removeyour criticaldata
from a particular location, you can quickly grab an
external drive on your way out the door.
See “About Offsite Copy” on page 100.
You can assign a unique name to each external drive.
A unique name helps you to keep a track of where
your backupdata isstored foreach computeryou back
up. It is more useful in situations when the drive
letters change each time you unplug and plug an
external drive into your computer. A unique name
ensures that you always know which drive is used
when you are running Symantec System Recovery.
Using a unique name does not change the volume
label of a drive. A unique name helps you to identify
the drive when you use Symantec System Recovery.
Once a unique name is assigned, it stays with the
drive. If you plug the drive into a second computer
running anothercopy of Symantec System Recovery,
the unique name appears.
Note: You might also consider placing a sticky label
on each drive that matchesthe unique name that you
have assigned.
See “About using unique names for external drives”
on page 53.
Page 66

Best practices for backing up your data
66
What to do during a backup
Use Offsite Copy
Run backups frequently on a
regular basis.
Keep personal data on a separate
drive than the drive on which
Windows and your software
programs are installed.
Verify the recovery point after you
create it to ensure that it is stable.
Use Offsite Copy to copy your latest recovery points
to eithera portable storage device or a remote server.
By copying recovery points to a portable hard disk,
you can then take a copy of your data with you when
you leave the office.
See “About Offsite Copy” on page 100.
When you define your backups,schedule themto run
frequently sothat you haverecovery points thatspan
at least the last two months.
See “Editing a backup schedule” on page 126.
See “Defining a drive-based backup” on page 74.
You should keep your operating system and software
programs separate from your own data. It speeds the
creation of recovery points and reduces the amount
of informationthat needsto be restored. For example,
use the C drive to run Windows and to install andrun
software programs. Use the D drive to create, edit,
and store personal files and folders.
For other drive management solutions, go to the
Symantec Web site at the following URL:
www.symantec.com/
While defining a backup, select the option to verify
that the recovery point is stable and can be used to
recover lost data.
See “About choosing a backup type” on page 64.
See “What to do during a backup” on page 66.
See “What to do when a backup is finished ” on page 67.
What to do during a backup
When a backup starts to run on your computer, you might notice that the
performance of your computer slows down. Symantec System Recovery requires
significant system resources to run a backup. If slowing occurs, you can reduce
the speed of the backup to improve computer performance until you are finished
working.
See “Adjusting the speed of a backup” on page 120.
See “What to do before you back up” on page 64.
Page 67

What to do when a backup is finished
See “What to do when a backup is finished ” on page 67.
What to do when a backup is finished
After a backup finishes, consider the following best practices:
67Best practices for backing up your data
Review the contents of recovery
points and file and folder backup
data.
Review the Status page to verify
that backups have happened and
to identify any potential problems.
Manage storage space by
eliminating old backup data.
Periodically review the contents of your recovery
points to ensure that you back up only your essential
data.
See “About opening files and folders stored in a
recovery point” on page 213.
See “Toopen fileswithin arecovery point”on page165.
Periodically review the Status page. You can also
review the events log on the Advanced page.
The event log records events when they occur,
backups, and any errors that might have occurred
during or after a backup.
Note: Backup status and other messages are also
conveyed in the system tray. So you do not need to
start the product to identify the status of your
backups.
See “Verifyingthat abackup issuccessful” on page 121.
See “To hideor show the Advanced page” on page 61.
Delete outdated recovery points to make more hard
disk space available.
Also, reduce the number of file versions that are
created when you back up your files and folders.
See “About managing file and folder backup data”
on page 202.
Review the level of protection that
is provided for each of your
computer's drives.
Maintain backup copies of your
recovery points.
Check the Status page on a regular basis to ensure
that each drive has a defined backup.
Store backup copies of your recovery points in a safe
place. For example you can store them elsewhere on
a network, or you can store them on CDs, DVDs, or
tapes for long-term, off-site storage.
See “Making copies of recovery points” on page 177.
Page 68

Best practices for backing up your data
68
Tips for running defined backups
See “What to do before you back up” on page 64.
See “What to do during a backup” on page 66.
Tips for running defined backups
Consider the following tips when you run a defined backup:
■ Symantec SystemRecovery doesnot need to be running for a scheduled backup
to start. After you define a backup, you can close Symantec System Recovery.
■ The computer that is backed up must be turned on and Windows must be
started.
See “Enabling search engine support” on page 277.
■ All defined backups are saved automatically so that you can edit them or run
them later.
See “Running an existing backup job immediately” on page 117.
See “Running a backup with options” on page 118.
See “Editing backup settings” on page 122.
■ Do not run a disk defragmentation program during a backup. Doing so
significantly increases the time that it takes to create the recovery point and
might cause unexpected system resource issues.
■ If you have two or more drives that are dependent on each other, you should
include both drives in the same backup. Including both the drives in the same
backup provides the safest protection.
■ Include multipledrives inthe same defined backup to reduce the total number
of backupsthat must be run. Doing so minimizesinterruptions whileyou work.
■ Use the Progress and Performance feature to reduce the effect of a backup on
your computer's performance. For example, say a scheduled backup starts
while you are in the middle of a presentation. You can slow down the backup
to give more processing resources back to your presentation program.
See “Adjusting the speed of a backup” on page 120.
■ The power management features on a computer can conflict with Symantec
System Recovery during a backup.
For example, your computer might be configured to go into hibernation mode
after a period of inactivity. You should consider turning off the power
management features during a scheduled backup.
■ If a backup is interrupted, consider running it again.
■ If you experience problems while creating a backup, you may need to restart
the computer.
Page 69

Viewing the properties of a backup job
See “What to do before you back up” on page 64.
See “What to do during a backup” on page 66.
See “What to do when a backup is finished ” on page 67.
Viewing the properties of a backup job
You canreview the settings and configuration of a defined backupwithout opening
the backup job.
To view the properties of a backup job
On the Home page, click Run or Manage Backups.
1
In the Run or Manage Backups window, select a backup job and then click
2
Tasks > Properties.
See “Running an existing backup job immediately” on page 117.
See “Running a backup with options” on page 118.
See “Editing backup settings” on page 122.
69Best practices for backing up your data
About selecting a backup destination
You should review the following information before you decide where to store
recovery points and file and folder backup data.
Note: If you choose to use CDs or DVDs as your backup destination (not
recommended), you cannot back up to a subfolder on the disk. Backup data must
be created at the root of CDs and DVDs.
The following table contains the information that you need to consider when
selecting a backup destination.
Page 70

Best practices for backing up your data
70
About selecting a backup destination
Table 5-1
Selecting a backup destination
Local hard drive, USB drive,
or FireWire drive
(recommended)
Information to considerBackup destination
The benefits of this option are as follows:
■ Provides for fast backup and recovery.
■ Lets you schedule unattended backups.
■ Reduces cost because drive space can be overwritten
repeatedly.
■ Allows for off-site storage.
■ Reserves hard drive space for other uses.
Although you can save therecovery point to the samedrive
that is backed up, it is not recommended for the following
reasons:
■ As the number or size of recovery points grows it
consumes moredisk space. As a result you have less disk
space for regular use.
■ The recovery point is included in subsequent recovery
points of the drive, which increases the size of those
recovery points.
■ If the computer suffers a catastrophic failure, you may
not be able to recover the recovery point. You may not
be able to recover the recovery point even if you save it
to a different drive on the same hard disk.
Network folder
If your computer is connected to a network, you can save
your recovery points and file and folder backup data to a
network folder.
Backing up to a network folder typically requires that you
authenticate to the computer that hosts the folder. If the
computer is part of a network domain, you must provide
the domain name, user name, and password. For example,
domain\username.
If you connect to a computer in a workgroup, you should
provide the remote computer name and user name. For
example: remote_computer_name\username.
Page 71

About backing up dual-boot computers
71Best practices for backing up your data
Table 5-1
Selecting a backup destination (continued)
Information to considerBackup destination
CD-RW/DVD-RW
When you save backup data to removable media, the data
is automatically split into the correct sizes if the backup
spans more than one media.
If more than one drive is backed up, the recoverypoints for
each drive are stored independently on the media. The
recovery pointsare storedindependently onthe mediaeven
if there is space to store them on same media.
The schedulingof backupsis notavailable whenthis option
is used.
Note: Using CD-RW or DVD-RW as your recovery point
storage locationis notthe bestoption. You might be required
to swap disks during the process.
See “About choosing a backup type” on page 64.
See “Running an existing backup job immediately” on page 117.
See “Running a backup with options” on page 118.
About backing up dual-boot computers
You can back up dual-boot computers, even if you have hidden drives (partitions)
in the operating system from which you run Symantec System Recovery.
When you run a drive backup, the entire contents of each drive is captured in a
recovery point. When you restore a drive, the recovered drive can be used to start
up your computer.
Consider the following points when backing up dual-boot computers:
■ To boot your computer from a restored system, you must back up, and then
restore every drive that includes operating system boot information.
■ Do not create incremental backups of shared data drives if both the following
conditions are true:
■ Symantec System Recovery is installed on both operating systems.
■ Both the operating systems are set to manage the shared drive.
You might encounter issues if you try to use the Symantec System Recovery
LightsOut Restore feature on dual-boot systems. It is not supported.
The same is true for the Symantec System Recovery Restore Anyware feature.
Page 72

Best practices for backing up your data
72
About backing up dual-boot computers
See “Defining a drive-based backup” on page 74.
See “About backing up your data” on page 63.
Page 73

Chapter
Backing up entire drives
This chapter includes the following topics:
■ About defining a drive-based backup
■ Defining a drive-based backup
■ Compression levels for recovery points
■ Running a one-time backup from Symantec System Recovery
■ About running a one-time backup from Symantec System Recovery Disk
■ About Offsite Copy
6
■ How Offsite Copy works
About defining a drive-based backup
A drive-based backup takes a snapshot of your entire hard drive, capturing every
bit of information that is stored on it for later retrieval. All of your files, folders,
desktop settings,programs, andyour operating system are captured into a recovery
point. You can then use that recovery point to restore individual files or folders,
or your entire computer.
For optimum protection, you should define a drive-based backup and run it on a
regular basis.
By default, scheduled independent recovery point file names and recovery point
set file names are appended with 001.v2i, 002.v2i, and so forth. Incremental
recovery point file names within a set are appended with _i001.iv2i, _i002.iv2i,
and soforth. For example, if your base recoverypoint is called CathyReadF001.v2i,
the first incremental recovery point is called CathyReadF001_i001.iv2i.
See “Defining a drive-based backup” on page 74.
Page 74

Backing up entire drives
74
Defining a drive-based backup
See “About backing up files and folders” on page 107.
Defining a drive-based backup
Define a drive-based backup to take a snapshot of your entire hard drive.
See “About defining a drive-based backup” on page 73.
See “About backing up files and folders” on page 107.
To define a drive-based backup
On the Tasks menu, click Run or Manage Backups.
1
In the Run or Manage Backups window, click Define New.
2
If you have not yet defined a backup, the Easy Setup dialog box appears
instead.
Click Back up my computer, and then click Next.
3
In theDrives panel, select one or more drives to backup, andthen click Next.
4
See “Drives options” on page 75.
If the Related Drives panel appears, set the appropriate option, and then
5
click Next. Otherwise, skip to the next step.
See “Related drives options” on page 75.
On the Recovery point type panel, select the recovery point type that you
6
want the backup to create, and then click Next.
See “Recovery point type options” on page 76.
On the Backup Destination panel, select the appropriate options.
7
See “Backup destination options” on page 77.
You cannot use an encrypted folder as your backup destination. You can
choose to encrypt your backup data to prevent another user from accessing
it.
(Optional) If you want to make copies of your recovery points to store at a
8
remote locationfor added backup protection, click Add, selectthe appropriate
options, and then click OK.
See “Offsite Copy Settings options” on page 78.
Click Next.
9
Page 75

Defining a drive-based backup
On theOptions panel, set therecovery pointoptions youwant, andthen click
10
Next.
See “Recovery point options” on page 79.
See “Advanced options for drive-based backups” on page 86.
See “Command files options” on page 84.
On the Backup Time panel, select the appropriate optionsto specify the time
11
and frequency of the backup, and then click Next.
Note: Ensure that the time for running a base backup and an incremental
backup is not the same.
See “Backup time options” on page 91.
(Optional) If you want to run the new backup immediately, click Run backup
12
now.
This option is not available if you configured an independent recovery point
with the option to run it only once.
Review the options you have selected, then click Finish.
13
See “About backing up files and folders” on page 107.
75Backing up entire drives
Drives options
The following table describes the options on the Drives panel. This panel is
available in the Define Backup wizard.
Table 6-1
Show Hidden Drives
Drive selection table
See “Defining a drive-based backup” on page 74.
Related drives options
The following table describes the options on the Related Drives panel.
Drives options
DescriptionOption
Lets you seeany hidden drives on your hard
disk. The drives are displayed in the drive
selection table.
Lets youselect oneor moredrives toinclude
in the backup.
Page 76

Backing up entire drives
76
Defining a drive-based backup
Table 6-2
Related drives options
DescriptionOption
Add all related drives (recommended)
Edit the list of selected drives
Do not add related drives
Lets you select and include all related drives
in the backup definition.
Lets youselect or deselect related drives that
you want or do not want to include in the
backup definition.
Lets you deselect (not include) all related
drives in the backup definition.
The RelatedDrives wizard panel appears only if you initiallyselected a drive with
applications configured to use one or more of the drives that are listed in this
panel.
Such applications include the following:
■ Windows Server 2008 R2 with Hyper-V
■ Domain controllers
■ Boot configurationdatabases (asfound in Windows Vista and Windows 7) that
are on a separate drive from where the operating system is installed.
If you want to back up an attached Microsoft Virtual Hard Disk (VHD), you must
create a separate backup job for the host drive and for the attached VHD. For
example, if the VHD host is on the C: drive and the attached VHD is the D: drive,
you must create a backup job for C: and a backup job for D:. Also, you cannot back
up an attached VHD that is nested within another attached VHD.
See “About backing up Microsoft virtual hard disks” on page 291.
If you use Microsoft's BitLocker Drive Encryption to encrypt the data on a data
drive (any drive that does not have the operating system installed on it), be aware
that Symantec System Recovery does not work with locked data drives. Instead,
you must unlock the bitlocked drive before you can back it up.
Generally, you should accept the preselected option Add all related drives
(recommended). If you deselect certain related drives, you may experience an
incomplete recovery or an unsuccessful recovery.
See “Defining a drive-based backup” on page 74.
Recovery point type options
The following table describes the options on the Recovery Point Type panel.
Page 77

Defining a drive-based backup
77Backing up entire drives
Table 6-3
Recovery point set (recommended)
Independent recovery point
Recovery point type options
DescriptionOption
Schedules a base recovery point with
additional recoverypoints that contain only
incremental changesthat weremade toyour
computer sincethe previousrecovery point.
Incremental recovery points are created
faster than the base recovery point. They
also use less storage space than an
independent recovery point.
Note: You can only haveone recovery point
set defined for each drive. The Recovery
point set option is not available if you have
already assigned a selected drive to an
existing backup and specified Recovery
point set as the recovery point type. This
option also is unavailable if you select an
unmounted drive that cannot be part of a
recovery point set.
Creates acomplete, independentcopy ofthe
drives that you select. This backup type
typically requires more storage space,
especially if you run the backup multiple
times.
See “Defining a drive-based backup” on page 74.
Backup destination options
The following table describes the options on the Backup Destination panel.
Table 6-4
Folder
Backup destination options
DescriptionOption
Indicates the location where you want to
store the recovery points.
If Symantec System Recovery detects that
this locationdoes not haveenough available
space, it alerts you. You should choose
another location that has more space.
Page 78

Backing up entire drives
78
Defining a drive-based backup
Table 6-4
Browse
Destination Details
Edit
Customize recovery point file names
Add
Backup destination options (continued)
DescriptionOption
Lets you browse to locate a backup
destination that you want to use.
Displays the type of destination path. If you
add a network path it also displays the user
name.
Lets you enter the user name and password
for access to the network that is specified in
the Folderfield. This option is available only
if you selected a backup destination that is
on a network. This also applies if you want
to save the recovery point on a network
share.
See “Aboutnetwork credentials”on page83.
Lets you rename the recovery point.
Default file names include the name of the
computer followed by the drive letter.
You canalso saverecovery pointsto aunique
subfolder.
Lets you add up to two Offsite Copy
destinations.
Offsite Copyautomatically copiesyour latest
recovery points each time a backup
completes toeither aportable storagedevice,
such as an external drive, or to a remote
server either through a local area network
connection or to a remote FTP server.
See “About Offsite Copy” on page 100.
See “Defining a drive-based backup” on page 74.
Offsite Copy Settings options
The following table describes the options on the Offsite Copy Settings panel.
Page 79

Defining a drive-based backup
79Backing up entire drives
Table 6-5
Offsite Copy Settings options
DescriptionOptions
Turns on the Offsite Copy feature.Enable Offsite Copy
Prompt me tostart a copy when I attach an
external Offsite Copy destination drive
Folder, Network Path, or FTP address
Browse
Destination Details
Edit
Addan additional Offsite Copy destination
Indicates that you want to have recovery
points automatically copied to external
Offsite Copy destination drives whenever
you plug one in to your computer.
Lets you specify the destination path of the
offsite copy.
Lets you browse to locate an offsite copy
destination that you want to use.
Displays the type of destination path. If you
add a network path or an ftp path, it also
displays the user name.
Lets you edit the user name or password of
a specified network path or an ftp path.
Lets you add a second destination, and then
specify the path to that destination.
See “Defining a drive-based backup” on page 74.
Recovery point options
The following table describes the recovery point options on the Options panel.
Table 6-6
Name
Recovery point options
DescriptionOptions
Indicates a name for your backup.
Note: This option does not appear if you
create a recovery point using the Back Up
My Computer feature in Symantec System
Recovery Disk.
Page 80

Backing up entire drives
80
Defining a drive-based backup
Table 6-6
Recovery point options (continued)
Compression
Verify recovery point after creation
Limit the number of recovery point sets
saved for this backup
DescriptionOptions
Lets you set one of the following
compression levels for the recovery point:
■ None
■ Standard
■ Medium
■ High
See “Compressionlevels forrecovery points”
on page 92.
The resultscan vary depending on the types
of files that are saved in the drive.
Tests whethera recovery point or setof files
is valid or corrupt.
Limits thenumber ofrecovery pointsets that
can be saved for this backup. You can limit
the number of recovery point sets to reduce
the risk of filling up the hard drive with
recovery points. Each new recovery point
set replaces the oldest set on your backup
destination drive.
This option appears only if you are creating
a recovery point set.
Note: This option does not appear if you
create a recovery point using the Back Up
My Computer feature in Symantec System
Recovery Disk.
Page 81

Defining a drive-based backup
81Backing up entire drives
Table 6-6
Enable search engine support
Include system and temporary files
Advanced
Recovery point options (continued)
DescriptionOptions
Lets asearch engine,such asGoogle Desktop,
index allof the file names that are contained
in each recovery point. By indexing the file
names, you can then use your search engine
to locate files you want to restore.
This option is for NTFS file systems only.
See “About using a search engine to search
recovery points” on page 277.
Note: This option does not appear if you
create a recovery point using the Back Up
My Computer feature in Symantec System
Recovery Disk.
Includes indexing support for operating
system andtemporary files when a recovery
point is created on the client computer.
Note: This option does not appear if you
create a recovery point using the Back Up
My Computer feature in Symantec System
Recovery Disk.
Lets you add, among other things, security
options to the recovery point.
See “Advanced options for drive-based
backups” on page 86.
Command Files
Description
See “Defining a drive-based backup” on page 74.
Advanced Scheduling options
The following table describes the properties of the Advanced Scheduling panel.
Lets you use command files (.exe, .cmd,.bat)
during a backup.
See “About running command files during
a backup” on page 83.
Indicates a description for the recovery
point. The description can be anything that
helps you further identify the recovery
point's contents.
Page 82

Backing up entire drives
82
Defining a drive-based backup
Table 6-7
Schedule
Run more than once per day
Time between backups
Number of times
Automatically optimize
Start a new recovery point set
Custom
Event Triggers - General
Advanced Scheduling options
DescriptionOption
Lets you select the days and a start time for
when the backup should run.
Indicates that you can run the backup more
than once a day to protect data that you edit
or change frequently.
Specifies the maximum time that should
occur between backups.
Specifies the number of times per day that
the backup should run.
Lets you select how often optimization
should occur to help manage the disk space
that is used by your backup destination.
Indicates how frequently a new recovery
point set should be started.
Lets you customize the start time, and the
days ofthe weekor monthto runthe backup.
Lets you select the type of events that
automatically starts a backup.
See “Enabling event-triggered backups”
on page 122.
Event Triggers - ThreatCon Response
Lets you set the ThreatCon Response level
that automatically starts a backup.
See “ThreatCon Response options”
on page 125.
See “Defining a drive-based backup” on page 74.
About files that are excluded from drive-based backups
The following files are intentionally excluded from drive-based backups:
■ hiberfil.sys
■ pagefile.sys
Page 83

These files contain temporary data that can take up a large amount of disk space.
They are not needed, and there is no negative impact to your computer system
after a complete system recovery.
These file names do appear in recovery points, but they are placeholders. They
contain no data.
See “Defining a drive-based backup” on page 74.
About network credentials
If you connect to a computer on a network, you must provide the user name and
password fornetwork access, even if you previously authenticatedto the network.
The Symantec System Recovery service runs on the local system account.
When you enter network credentials, the following rules apply:
■ If the computer you want to connect to is on a domain, provide the domain
name, user name, and password. For example:
domain\username
■ If you connect to a computer in a workgroup, provide the remote computer
name and user name. For example:
remote_computer_name\username
■ If you have mapped a drive, you might be required to supply the user name
and passwordagain because the service runs in adifferent contextand cannot
recognize the mapped drive.
By going to the Tasks menu and selecting Options, you can set a default location.
If the default location is a computer on a network, you can also click the Edit
option and specify the necessary network credentials. Then when you create
future backup jobs, the dialog will default to the location you specified. Another
option would be to create a specific "backup" user account. Then configure the
Symantec System Recovery service to use this account.
See “Defining a drive-based backup” on page 74.
See “About files that are excluded from drive-based backups” on page 82.
Defining a drive-based backup
83Backing up entire drives
About running command files during a backup
You canuse commandfiles (.exe, .cmd, .bat) during a backup.You canuse command
files to integrate Symantec SystemRecovery with other backup routines that you
might be running on the computer. You can also use command files to integrate
with other applications that use a drive on the computer.
Page 84

Backing up entire drives
84
Defining a drive-based backup
Note: You cannot run command files that include a graphical user interface, such
as notepad.exe. Running such command files causes the backup job to fail.
You canrun a command file during any ofthe following stages during the creation
of a recovery point:
■ Run before snapshot creation
■ Run after snapshot creation
■ Run after recovery point creation
See “Command files options” on page 84.
The most common use for running command files is to stop and restart
non-VSS-aware databases that you want to back up.
To use a Visual Basic script file (.vbs) during a backup, you can create a batch file
(.bat) to run the script. For example, you can create a batch file called Stop.bat
that contains the following syntax:
Cscript script_filename.vbs
Make sure that Cscript precedes the file name of the Visual Basic script.
Warning: The command files cannot depend on any user interaction or have a
visible userinterface. You should test all command filesindependently ofSymantec
System Recovery before you use them during a backup.
When the backup begins, the command file is run during the specified stage. The
backup is stopped if an error occurs while a command file is running. Or, the
backup is stopped if the command file does not finish in the time you specified
(regardless of the stage). In either case, the command file is terminated (if
necessary), and the error information is logged and displayed.
See “Defining a drive-based backup” on page 74.
See “Running a one-time backup from Symantec System Recovery” on page 93.
Command files options
The following table describes the options that are available in the Command file
panel.
Page 85

Defining a drive-based backup
85Backing up entire drives
Table 6-8
Command files folder
Browse
User name
Password
Run before snapshot creation
Command files options
DescriptionOption
Specifies the location of command files if
you want them to be located in a place other
than the default location. You can also
specify a location on a per-job basis, as well
as specify a location that can be shared
among several computers. If you specify a
network location, you are prompted for
network credentials.
Lets you browse to locate a folder for any
command files that you want to use.
Specifies the user name to a command file
folder that is located in a network path.
Specifies the password to a command file
folder that is located in a network path.
Indicates that you can run a command file
after a backup has started and before a
recovery point is created. You can run a
command during this stage to prepare for
the recovery point creation process. For
example, youcan closeany openapplications
that are using the drive.
Note: If you use this option, be sure the
command file has an error recovery
mechanism built into it. Ifthe computer has
one or more services that must be stopped
at this stage (such as stopping a non-VSS
aware database or a resource-intensive
application), and the command file does not
contain any form of error recovery, one or
more of the stopped services may not be
restarted. An error in the command file can
cause the recovery point creation process to
stop immediately. No other command files
will run.
See “Howto useSymantec SystemRecovery”
on page 43.
Page 86

Backing up entire drives
86
Defining a drive-based backup
Table 6-8
Command files options (continued)
DescriptionOption
Run after snapshot creation
Run after recovery point creation
Timeout (applies to each stage)
Indicates that you can run a command file
after a snapshot is created. Running a
command duringthis stageis typicallya safe
point forallowing servicesto resumenormal
activity on the drive while continuing the
recovery point creation.
Because the snapshot takes only a few
seconds to create, the database is in the
backup state momentarily. A minimal
number of log files are created.
Indicates that you can run a command file
after the recovery point file is created. You
can run a command during this stage to act
on the recovery point itself. For example,
you can copy it to an offline location.
Lets you specify the amount of time (in
seconds) that a command file is allowed to
run.
See “About running command files during a backup” on page 83.
See “Defining a drive-based backup” on page 74.
See “Running a one-time backup from Symantec System Recovery” on page 93.
Advanced options for drive-based backups
The following table describes the Advanced options that are available when you
create a drive-based backup.
Table 6-9
Divide into smaller files to simplify
archiving
Advanced options for drive-based backups
DescriptionOption
Splits the recovery point into smaller files
and specifies the maximum size (in MB) for
each file.
Page 87

Defining a drive-based backup
87Backing up entire drives
Table 6-9
Disable SmartSector™ Copying
Ignore bad sectors during copy
Perform full VSS backup
Advanced options for drive-based backups (continued)
DescriptionOption
Copies used and unused hard-disk sectors.
This option increases process time and
usually results in a larger recovery point.
SmartSector technology speeds up the
copying process by copying only the
hard-disk sectors that contain data.
However, in some cases, you might want to
copy all sectors in their original layout,
whether or not they contain data.
Runs a backup even if there are bad sectors
on the hard disk. Although most drives do
not have bad sectors, the potential for
problems increases during the lifetime of
the hard disk.
Lets you perform a full backup on the VSS
storage andsend a request for VSSto review
its own transaction log. This option is used
for VSS applications, such as Microsoft
Exchange Server 2003 or Microsoft SQL.
VSS determines what transactions are
already committed to the databaseand then
truncates those transactions. Among other
things, truncatedtransaction logs help keep
the file size manageable and limits the
amount ofhard drive space that the file uses.
If you do not select this option, backups still
occur onthe VSSstorage. However,VSS does
not automatically truncate the transaction
logs following a backup.
Note: This option does not appear if you
create a recovery point using the Back Up
My Computer wizard feature in Symantec
System Recovery Disk.
Page 88

Backing up entire drives
88
Defining a drive-based backup
Table 6-9
Advanced options for drive-based backups (continued)
DescriptionOption
Use password
Use AES encryption
Sets a password on the recovery point when
it iscreated. Passwordscan includestandard
characters. Passwords cannot include
extended characters, or symbols. (Use
characters with an ASCII value of 128 or
lower.)
A user must type this password before
restoring a backup or viewing the contents
of the recovery point.
Encrypts recoverypoint datato add another
level of protection to your recovery points.
Choose fromthe followingencryption levels:
■ Standard 128-bit (8+ character
password)
■ Medium 192-bit (16+ character
password)
■ High 256-bit (32+ character password)
See “Defining a drive-based backup” on page 74.
See “About files that are excluded from drive-based backups” on page 82.
Editing advanced backup options
After you define a backup, you can go back at any time and edit the advanced
options you chose when you first defined the backup.
To edit advanced backup options
On the Tasks menu, click Run or Manage Backups.
1
Select the backup you want to edit, and then click Edit Settings.
2
Click Next twice.
3
Click Advanced.
4
In the AdvancedOptions dialog box, make your changes, and then click OK.
5
See “Advanced options for drive-based backups” on page 86.
Click Next three times, and then click Finish.
6
See “Defining a drive-based backup” on page 74.
See “About files that are excluded from drive-based backups” on page 82.
Page 89

Defining a drive-based backup
About recovery point encryption
You can enhance the security of your data by using the Advanced Encryption
Standard (AES) to encrypt recovery points that you create or archive. You should
use encryptionif you store recovery points on anetwork and want to protect them
from unauthorized access and use.
You can also encrypt recovery points that were created with earlier versions of
Symantec LiveStateRecovery orSymantec SystemRecovery. However,encrypting
those files makes them readable with the current product only.
You can view the encryption strength of a recovery point at any time by viewing
the properties of the file from the Recovery Point Browser.
Encryption strengths are available in 128-bit, 192-bit, or 256-bit. While higher
bit strengthsrequire longer passwords, the resultis greater security for your data.
The following table explains the bit strength and required password length.
89Backing up entire drives
Table 6-10
Password length
Password lengthBit strength
8 characters or longer128 (Standard)
16 characters or longer192 (Medium)
32 characters or longer256 (High)
You must provide the correct password before you can access or restore an
encrypted recovery point.
Warning: Store the password in a secure place. Passwords are case-sensitive .
When youaccess or restore a recovery point thatis passwordencrypted, Symantec
System Recovery prompts you for the case-sensitive password. If you do not type
the correct password or you forget the password, you cannot open the recovery
point.
Symantec Technical Support cannot open an encrypted recovery point.
Besides bit strength, the format of the password can improve the security of your
data.
For better security, passwords should use the following general rules:
■ Do not use consecutive repeating characters (for example, BBB or 88).
■ Do not use common words you would find in a dictionary.
■ Use at least one number.
Page 90

Backing up entire drives
90
Defining a drive-based backup
■ Use both uppercase and lowercase alpha characters.
■ Use at least one special character such as ({}[],.<>;:’"?/|\`~!@#$%^&*()_-+=).
■ Change the password after a set period of time.
See “Defining a drive-based backup” on page 74.
See “Backing up files and folders” on page 107.
See “Verifying the integrity of a recovery point” on page 90.
Verifying the integrity of a recovery point
If you selected the Verify recovery point after creation option on the Options
panel of the Define Backup wizard, the following occurs:
■ Symantec System Recovery verifies that all of the files that make up the
recovery point are available for you to open.
■ Internal data structures in the recovery point are matched with the data that
is available.
Also, the recovery point can be uncompressed to create the expected amount of
data (if you selected a compression level at the time of creation).
Note: The time that isrequired to create a recovery point is doubledwhen you use
the Verify recovey point after creation option.
If you prefer, you can have recovery points automatically verified for integrity at
the time they are created.
See “Advanced options for drive-based backups” on page 86.
To verify the integrity of a recovery point
On the Tools page, click Run Recovery Point Browser.
1
Select a recovery point, and then click OK.
2
In the tree panel of the Recovery Point Browser, select the recovery point.
3
For example: C_Drive001.v2i.
On the File menu, click Verify Recovery Point.
4
If the Verify Recovery Point option is unavailable, you must first dismount
the recovery point. Right-click the recovery point and click Dismount
Recovery Point.
When the validation is complete, click OK.
5
See “About recovery point encryption” on page 89.
Page 91

Viewing the progress of a backup
You can view the progress of a backup while it runs to determine how much time
remains until the backup completes.
To view the progress of a backup
While a backup is running, on the View menu, click Progress and
◆
Performance.
See “Defining a drive-based backup” on page 74.
See “Backing up files and folders” on page 107.
Backup time options
The following tables describe the options on the BackupTime panel. The options
vary depending on the backup type you create.
Defining a drive-based backup
91Backing up entire drives
Table 6-11
Schedule
Advanced
Run more than once
per day
Start a new recovery
point set (base)
Custom
Select event triggers
Details
Backup time options for a recovery point set
DescriptionOption
Runs thebackup automaticallyaccording toa specifiedstart time
and the selected days of the week.
Lets you use the default backup time schedule.Default
Sets advanced scheduling options, such as setting up event
triggers that start the backup in response to specific events.
See “Advanced Scheduling options” on page 81.
Sets the time between backups and the number of times to back
up.
Starts anew recoverypoint set (base) weekly, monthly, quarterly,
or yearly.
(Optional) Indicates how frequently a new recovery point set
should be started.
For example, if you select Monthly, a new base recovery point
is createdthe firsttime thebackup runsduring each new month.
Lets you select events that will automatically create a recovery
point.
Shows you information about the backup time option you have
selected or specified.
Page 92

Backing up entire drives
92
Compression levels for recovery points
Table 6-12
Backup Time options for an independent recovery point
DescriptionOption
Runs the backup only when you run it yourself, manually.No Schedule
Weekly
Monthly
Only run once
Details
Runs the backup at the time and on the days of the week that
you specify.
When you select this option, the Select the days of the week to
protect dialog box appears.
Runs the backup at the time and on the days of the month that
you specify.
When you select this option, the Select the daysof the month to
protect dialog box appears.
Runs thebackup onetime on the date and at the time you specify.
When you select this option, the Createa single recovery point
dialog box appears.
Indicates information about the backup time option you have
selected or specified.
See “Defining a drive-based backup” on page 74.
See “Editing a backup schedule” on page 126.
Compression levels for recovery points
During thecreation orcopying of a recovery point, compression results may vary,
depending on the types of files that are saved to the drive you are backing up.
The following table describes the available compression levels.
Table 6-13
None
Standard
(recommended)
Compression level options
DescriptionOption
Indicates that no compression is applied to the recover point.
Use this option if storage space is not an issue. However, if the
backup isbeing savedto abusy networkdrive, highcompression
may be fasterthan no compressionbecause there is less data to
write across the network.
Uses lowcompression fora 40percent averagedata compression
ratio on recovery points. This setting is the default.
Page 93

Running a one-time backup from Symantec System Recovery
93Backing up entire drives
Table 6-13
Medium
High
See “Defining a drive-based backup” on page 74.
See “Making copies of recovery points” on page 177.
Compression level options (continued)
DescriptionOption
Uses medium compression for a 45 percent average data
compression ratio on recovery points.
Uses high compression for a 50 percent average data
compression ratio on recovery points. This setting is usually
the slowest method.
When a high compression recovery point is created, CPU usage
might be higherthan normal. Other processes on the computer
might also be slower. To compensate, you can adjust the
operation speed of Symantec System Recovery. This might
improve the performance of other resource-intensive
applications that you are running at the same time.
Running a one-time backup from Symantec System
Recovery
You can use One TimeBackup to quickly define and run a backup that creates an
independent recovery point. You use the One Time Backup wizard to define the
backup. The backup runs when you complete the wizard. The backup definition
is not saved for future use. You can use the independent recovery point later.
This feature is useful when you need to back up your computer or a particular
drive quickly before a significant event. For example, you can run a one-time
backup before you install new software. Or, you can run it when you learn about
a new computer security threat.
You canalso use Symantec System Recovery Disk to create one-timecold backups.
See “About running a one-time backup from Symantec System Recovery Disk”
on page 94.
To run a one-time backup from Symantec System Recovery
On the Tasks page, click One Time Backup.
1
Click Next.
2
Select one or more drives to back up, and then click Next.
3
Page 94

Backing up entire drives
94
About running a one-time backup from Symantec System Recovery Disk
If the RelatedDrives dialog box is displayed, set the appropriate option, and
4
then click Next. Otherwise, skip to the next step.
See “Related drives options” on page 75.
In the Backup Destinations panel, select the appropriate options.
5
See “Backup destination options” on page 77.
Click Next.
6
On the Options panel, select the appropriate options.
7
See “Recovery point options” on page 79.
Click Next.
8
If appropriate, in the lists, select the command files that you want to run
9
during aparticular stage in the recoverypoint creation process. Then, specify
the amount of time (in seconds) that you want the command to run before it
is stopped.
If you added the command file to the Command Files folder, you may need
to click Back, and then Next to see the files in each stage’s list.
See “Command files options” on page 84.
Click Next.
10
Click Finish to run the backup.
11
About running a one-time backup from Symantec
System Recovery Disk
Using a valid license key, you can create independent recovery points using the
BackUp My Computer feature inSymantec SystemRecovery Disk.You can create
recovery points of a partition without the need to install Symantec System
Recovery orits agent.This feature is sometimes known as a cold backupor offline
backup.
With a cold backup, all files are closed when the backup occurs. You do not copy
any data that may be in the middle of being updated or accessed on the desktop
or server. Cold backups are particularly useful for databases. They ensure that
no files are written to or accessed at any time during the backup so you have a
complete recovery point.
You can also use the Symantec System Recovery Disk to create recovery points
if you experience any of the following:
■ A level of corruption prevents you from starting Windows on the computer.
Page 95

About running a one-time backup from Symantec System Recovery Disk
■ Symantec System Recovery does not function properly while it runs on a
Windows operating system.
■ You want to back up the condition of a damaged system before you recover.
For example, if a computer is severely damaged, you can use the Symantec
System Recovery Disk. You can back up what remains of the system. Then,
you canrecover what you can later, after yourestore an independent recovery
point.
Note: Recovery points that you create using Symantec System Recovery Disk are
restored to dissimilar hardware using Restore Anyware.
When you want to createa backup fromSymantec System Recovery Disk , youare
prompted for a valid license key only for the following scenarios:
■ You use the original, shipping version of the Symantec System Recovery Disk
CD to create a backup of a computer. The computer does not have Symantec
System Recovery installed.
■ The computer that you intend to back up using the original, shipping version
of the Symantec System Recovery Disk CD has an unlicensed installation of
the software.
■ You create a custom Symantec System Recovery Disk on a computer that has
an unlicensed installation (60-day trial) of Symantec System Recovery. You
then use the custom Symantec System Recovery Disk to create a backup of a
computer. The computer does not have an installation of Symantec System
Recovery.
See “Creating a custom Symantec System Recovery Disk” on page 37.
■ You choose not to add a license key at the time you create the customized
Symantec System Recovery Disk.
See “Running a one-time backup from Symantec System Recovery Disk”
on page 95.
95Backing up entire drives
Running a one-time backup from Symantec System Recovery Disk
Using a valid license key, you can create independent recovery points using the
BackUp My Computer feature inSymantec SystemRecovery Disk.You can create
recovery points of a partition without the need to install Symantec System
Recovery orits agent.This feature is sometimes known as a cold backupor offline
backup.
Page 96

Backing up entire drives
96
About running a one-time backup from Symantec System Recovery Disk
To run a one-time backup from Symantec System Recovery Disk
If you intend to store the resulting recovery point on a USB device (for
1
example, an external hard drive), attach the device now.
Start the Symantec System Recovery Disk on the computer you want to back
2
up.
See “Booting a computer by using the Symantec System Recovery Disk”
on page 228.
On the Home panel, click Back Up My Computer, and then click Next.
3
On the Welcome panel, click Next.
4
If you are prompted, on the Specify License Key panel, enter a valid license
5
key, and then click Next.
On the Drives panel, select one or more drives that you want to back up, and
6
then click Next.
On the BackupDestination panel, set the options you want, then click Next.
7
See “Backup Destination options” on page 96.
On the Options panel, set the desired backup options and advanced options
8
for the recovery point.
See “Back Up My Computer options” on page 97.
On the Options panel, click Advanced.
9
On the Advanced options panel, set the advanced backup options you want
10
for the recovery point, and then click OK.
See “Advanced options” on page 98.
On the Options panel, click Next.
11
On the Completingthe Back Up My Computer Wizard panel, click Finish to
12
run the backup.
When the backup is finished, click Close to return to the main Symantec
13
System Recovery Disk window.
See “About running a one-time backup from Symantec System Recovery Disk”
on page 94.
Backup Destination options
The following table describes the options on the BackupDestination panel. This
panel is available from the Back Up My Computer wizard in Symantec System
Recovery Disk.
Page 97

About running a one-time backup from Symantec System Recovery Disk
97Backing up entire drives
Table 6-14
Folder
Map a network drive
Browse
Destination Details
Rename
Backup Destination options
DescriptionOption
Lets you browse to and specify the location
where you want to store the independent
recovery point.
Maps anetwork drive byusing the UNCpath
of the computer on which you want to store
the recovery point.
For example,\\computer_name\share_name
or \\IP_address\share_name.
Lets you browse to locate a backup
destination that you want to use.
Displays the type of destination path. If you
add a network path it also displays the user
name.
Lets you edit the recovery point file name.Recovery point file name
Lets you rename the recovery point file
name.
Default file names include the name of the
computer and then followed by the drive
letter.
See “Running a one-time backup from Symantec System Recovery Disk”
on page 95.
Back Up My Computer options
The following table describes the options on the Options panel. This panel is
available from the Back Up My Computer wizard in Symantec System Recovery
Disk.
Page 98

Backing up entire drives
98
About running a one-time backup from Symantec System Recovery Disk
Table 6-15
Compression
Verify recovery point after creation
Description
Advanced
Back Up My Computer options
DescriptionOptions
Lets you set one of the following
compression levels for the recovery point:
■ None
■ Standard
■ Medium
■ High
See “Compressionlevels forrecovery points”
on page 92.
The resultscan vary depending on the types
of files that are saved in the drive.
Tests whethera recovery point or setof files
is valid or corrupt.
Indicates a description for the recovery
point. The description can help you further
identify the recovery point's contents.
Lets you further add security options to the
recovery point.
See “Advanced options” on page 98.
See “Running a one-time backup from Symantec System Recovery Disk”
on page 95.
Advanced options
The following table describes the options on the Advanced options panel. This
panel is available from the Back Up My Computer wizard in Symantec System
Recovery Disk.
Table 6-16
Divide into smaller files to simplify
archiving
Advanced options for drive-based backups
DescriptionOption
Lets yousplit the recovery point into smaller
files and specify the maximum size (in MB)
for each file.
Page 99

About running a one-time backup from Symantec System Recovery Disk
99Backing up entire drives
Table 6-16
Disable SmartSector™ Copying
Ignore bad sectors during copy
Use password
Advanced options for drive-based backups (continued)
DescriptionOption
Lets you copy used and unused hard-disk
sectors. This option increases process time
and usuallyresults ina largerrecovery point.
SmartSector technology speeds up the
copying process by copying only the
hard-disk sectors that contain data.
However, in some cases, you might want to
copy all sectors in their original layout,
whether or not they contain data.
Lets you run a backup even if there are bad
sectors on the hard disk. Although most
drives do not have bad sectors, thepotential
for problems increases during the lifetime
of the hard disk.
Sets a password on the recovery point when
it iscreated. Passwordscan includestandard
characters. Passwords cannot include
extended characters, or symbols. (Use
characters with an ASCII value of 128 or
lower.)
A user must type this password before they
can restore abackup or viewthe contents of
the recovery point.
Use AES encryption
Encrypts recoverypoint datato add another
level of protection to your recovery points.
Choose fromthe followingencryption levels:
■ Standard 128-bit (8+ character
password)
■ Medium 192-bit (16+ character
password)
■ High 256-bit (32+ character password)
See “Back Up My Computer options” on page 97.
See “Running a one-time backup from Symantec System Recovery Disk”
on page 95.
Page 100

Backing up entire drives
100
About Offsite Copy
About Offsite Copy
Backing up your data to a secondary hard disk is a critical first step to protecting
your information assets. But to make certain your data is safe, use Offsite Copy.
This feature can copy your latest complete recovery points to the following:
■ A portable storage device.
■ A remote server in your network.
■ A remote FTP server.
Regardless of the method you use, storing copies of your recovery points at a
remote locationprovides a crucial level ofredundancy inthe event that your office
becomes inaccessible. Offsite Copy can double your data protection by ensuring
that you have a remote copy.
See “How Offsite Copy works” on page 100.
See “About using external drives as your offsite copy destination” on page 101.
See “About using a network server as your offsite copy destination” on page 103.
See “About using an FTP server as your offsite copy destination” on page 104.
How Offsite Copy works
You enableand configure OffsiteCopy when you define anew drive-basedbackup
job. Or you can edit an existing backup job to enable Offsite Copy.
When you enable Offsite Copy, you specify up to two offsite copy destinations.
After the backup job finishes creating recovery points, Offsite Copy verifies that
at least one of the offsite copy destinations is available. Offsite Copy then begins
copying the new recovery points to the offsite copy destination.
The most recent recovery points are copied first, followed by the next newest
recovery points. If you have set up two offsite copy destinations, Offsite Copy
copies recovery points to the destination that was added first. If an offsite copy
destination isunavailable, OffsiteCopy tries to copy recovery points to the second
destination, if it is available. If neither destination is available, then Offsite Copy
copies the recovery points the next time an offsite copy destination becomes
available.
For example, suppose you have configured a backup job to run at 6:00 p.m. and
configured an external drive as an offsite copy destination. However, when you
leave the office at 5:30 p.m., you take the drive with you for safekeeping. When
the backup job completes at 6:20 p.m., Symantec System Recovery detects that
the offsite copy destination drive is not available and the copy process is aborted.
 Loading...
Loading...