Page 1

Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide
Sun Microsystems, Inc.
4150 Network Circle
Santa Clara, CA 95054
U.S.A.
Part No: 819–0994
March 2007
Sun Condential:Registered
Page 2

Copyright 2007 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved.
Sun Microsystems, Inc. has intellectual property rights relating to technology embodied in the product that is described in this document. In particular, and without
limitation, these intellectual property rights may include one or more U.S. patents or pending patent applications in the U.S. and in other countries.
U.S. Government Rights – Commercial software. Government users are subject to the Sun Microsystems, Inc. standard license agreement and applicable provisions
of the FAR and its supplements.
This distribution may include materials developed by third parties.
Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other
countries, exclusively licensed through X/Open Company, Ltd.
Sun, Sun Microsystems, the Sun logo, the Solaris logo, the Java Coee Cup logo, docs.sun.com, Java, and Solaris are trademarks or registered trademarks of Sun
Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC
International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc.
The OPEN LOOK and Sun
of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. Sun holds a non-exclusive license from Xerox to
the Xerox Graphical User Interface, which license also covers Sun's licensees who implement OPEN LOOK GUIs and otherwise comply with Sun's written license
agreements.
Products covered by and information contained in this publication are controlled by U.S. Export Control laws and may be subject to the export or import laws in
other countries. Nuclear, missile, chemical or biological weapons or nuclear maritime end uses or end users, whether direct or indirect, are strictly prohibited. Export
or reexport to countries subject to U.S. embargo or to entities identied on U.S. export exclusion lists, including, but not limited to, the denied persons and specially
designated nationals lists is strictly prohibited.
DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDINGANY
IMPLIED WARRANTY OF MERCHANTABILITY,FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO
THE EXTENT THATSUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID.
TM
Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering eorts
Copyright 2007 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. Tous droits réservés.
Sun Microsystems, Inc. détient les droits de propriété intellectuelle relatifs à la technologie incorporée dans le produit qui est décrit dans ce document. En particulier,
et ce sans limitation, ces droits de propriété intellectuelle peuvent inclure un ou plusieurs brevets américains ou des applications de brevet en attente aux Etats-Unis
et dans d'autres pays.
Cette distribution peut comprendre des composants développés par des tierces personnes.
Certaines composants de ce produit peuvent être dérivées du logiciel Berkeley BSD, licenciés par l'Université de Californie. UNIX est une marque déposée aux
Etats-Unis et dans d'autres pays; elle est licenciée exclusivement par X/Open Company, Ltd.
Sun, Sun Microsystems, le logo Sun, le logo Solaris, le logo Java Coee Cup, docs.sun.com, Java et Solaris sont des marques de fabrique ou des marques déposées de
Sun Microsystems, Inc. aux Etats-Unis et dans d'autres pays. Toutes les marques SPARC sont utilisées sous licence et sont des marques de fabrique ou des marques
déposées de SPARC International, Inc. aux Etats-Unis et dans d'autres pays. Les produits portant les marques SPARC sont basés sur une architecture développée par
Sun Microsystems, Inc.
L'interface d'utilisation graphique OPEN LOOK et Sun a été développée par Sun Microsystems, Inc. pour ses utilisateurs et licenciés. Sun reconnaît les eorts de
pionniers de Xerox pour la recherche et le développement du concept des interfaces d'utilisation visuelle ou graphique pour l'industrie de l'informatique. Sun détient
une licence non exclusive de Xerox sur l'interface d'utilisation graphique Xerox, cette licence couvrant également les licenciés de Sun qui mettent en place l'interface
d'utilisation graphique OPEN LOOK et qui, en outre, se conforment aux licences écrites de Sun.
Les produits qui font l'objet de cette publication et les informations qu'il contient sont régis par la legislation américaine en matière de contrôle des exportations et
peuvent être soumis au droit d'autres pays dans le domaine des exportations et importations. Les utilisations nales, ou utilisateurs naux, pour des armes nucléaires,
des missiles, des armes chimiques ou biologiques ou pour le nucléaire maritime, directement ou indirectement, sont strictement interdites. Les exportations ou
réexportations vers des pays sous embargo des Etats-Unis, ou vers des entités gurant sur les listes d'exclusion d'exportation américaines, y compris, mais de manière
non exclusive, la liste de personnes qui font objet d'un ordre de ne pas participer, d'une façon directe ou indirecte, aux exportations des produits ou des services qui
sont régis par la legislation américaine en matière de contrôle des exportations et la liste de ressortissants spéciquement designés, sont rigoureusement interdites.
LA DOCUMENTATIONEST FOURNIE "EN L'ETAT" ET TOUTES AUTRESCONDITIONS, DECLARATIONS ET GARANTIES EXPRESSES OU TACITES
SONT FORMELLEMENT EXCLUES, DANS LA MESURE AUTORISEE PAR LA LOI APPLICABLE, Y COMPRIS NOTAMMENT TOUTE GARANTIE
IMPLICITE RELATIVE A LA QUALITE MARCHANDE, A L'APTITUDE A UNE UTILISATIONPARTICULIEREOU A L'ABSENCE DE CONTREFACON.
070222@16599
Sun Condential: Registered
Page 3

Contents
Preface ...................................................................................................................................................15
1 Overview of the Migration Process for Directory Server .............................................................. 25
Before You Migrate ............................................................................................................................. 25
Prerequisites to Migrating a Single Directory Server Instance From 5.1 .............................. 26
Prerequisites to Migrating a Single Directory Server Instance From 5.2 .............................. 26
Deciding on the New Product Distribution ..................................................................................... 27
Outline of Migration Steps ................................................................................................................. 27
Deciding on Automatic or Manual Migration ................................................................................. 28
2 Automated Migration Using the dsmig Command ........................................................................ 29
About the Automatic Migration Tool ............................................................................................... 29
Prerequisites for Running dsmig ....................................................................................................... 30
Using dsmig to Migrate the Schema .................................................................................................. 30
Using dsmig to Migrate Security Data .............................................................................................. 31
Using dsmig to Migrate Conguration Data .................................................................................... 31
Plug-in Conguration Data ........................................................................................................ 32
Chained Sux Conguration Data ........................................................................................... 32
Conguration Data For Suxes With Multiple Backends ..................................................... 33
Replication Conguration Data ................................................................................................. 33
Conguration Data for o=netscapeRoot ................................................................................. 33
Conguration Attributes Not Migrated by dsmig .................................................................... 33
Using dsmig to Migrate User Data .................................................................................................... 35
Tasks to be Performed After Automatic Migration ......................................................................... 35
3 Migrating Directory Server Manually ..............................................................................................37
Before You Start a Manual Migration ............................................................................................... 37
Sun Condential: Registered
3
Page 4

Contents
Migrating the Schema Manually ........................................................................................................ 38
Migrating Conguration Data Manually ......................................................................................... 38
Migration of Specic Conguration Attributes ....................................................................... 38
Migrating Security Settings Manually ...............................................................................................48
Migrating User Data Manually .......................................................................................................... 49
Migrating User Plug-Ins Manually .................................................................................................... 50
Tasks to be Performed After Manual Migration .............................................................................. 50
4 Migrating a Replicated Topology...................................................................................................... 51
Overview of Migrating Replicated Servers ....................................................................................... 51
Issues Related to Migrating Replicated Servers ................................................................................ 52
Issues With the New Password Policy ....................................................................................... 52
Migration of Replication Agreements ....................................................................................... 52
Migration of Referrals ................................................................................................................. 52
Manual Reset of Replication Credentials .................................................................................. 53
Problems Related to Tombstone Purging ................................................................................. 53
New Replication Recommendations ................................................................................................. 53
Migration Scenarios ............................................................................................................................ 54
Migrating a Replicated Topology to an Identical Topology ................................................... 54
Migrating a Replicated Topology to a New Topology ............................................................. 63
Migrating Over Multiple Data Centers ..................................................................................... 67
5 Architectural Changes in Directory Server 6.0 ............................................................................... 69
Changes in the Administration Framework .................................................................................... 69
Removal of the ServerRoot Directory ........................................................................................ 69
Removal of the o=netscapeRoot Sux ..................................................................................... 70
Changes to ACIs .................................................................................................................................. 70
Changes in the ACI Scope ........................................................................................................... 70
Changes in Sux-Level ACIs ..................................................................................................... 70
Command Line Changes .................................................................................................................... 71
Deprecated Commands ..............................................................................................................73
Changes to the Console ...................................................................................................................... 74
New Password Policy .......................................................................................................................... 74
Password Policy Compatibility .................................................................................................. 75
Changes to Plug-Ins ............................................................................................................................ 77
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 20074
Sun Condential: Registered
Page 5

Contents
New Plug-Ins in Directory Server 6.0 ........................................................................................ 77
Plug-Ins Deprecated in Directory Server 6.0 ............................................................................ 78
Changes to the Plug-In API ........................................................................................................ 78
Changes to the Installed Product Layout .......................................................................................... 78
Administration Utilities Previously Under ServerRoot ........................................................... 79
Binaries Previously Under ServerRoot/bin ............................................................................... 79
Libraries and Plug-Ins Previously Under ServerRoot/lib ........................................................ 79
Online Help Previously Under ServerRoot/manual ................................................................. 79
Plug-Ins Previously Under ServerRoot/plugins ........................................................................ 80
Utilities Previously Under ServerRoot/shared/bin ................................................................ 80
Certicate and Key Files .............................................................................................................. 81
Silent Installation and Uninstallation Templates ..................................................................... 82
Server Instance Scripts Previously Under ServerRoot/slapd-ServerID ............................... 82
Server Instance Subdirectories ................................................................................................... 82
6 Migrating Directory Proxy Server .....................................................................................................83
Mapping the Global Conguration ................................................................................................... 83
Mapping the Global Security Conguration ............................................................................ 85
Mapping the Connection Pool Conguration ................................................................................. 87
Mapping the Groups Conguration ................................................................................................. 88
Mapping the Group Object ......................................................................................................... 88
Mapping the Network Group Object ......................................................................................... 89
Mapping Bind Forwarding ......................................................................................................... 90
Mapping Operation Forwarding ................................................................................................ 91
Mapping Subtree Hiding ............................................................................................................. 92
Mapping Search Request Controls ............................................................................................ 92
Mapping Compare Request Controls ........................................................................................ 93
Mapping Attributes Modifying Search Requests ..................................................................... 93
Mapping Attributes Restricting Search Responses .................................................................. 94
Mapping the Referral Conguration Attributes ...................................................................... 95
Mapping the Server Load Conguration .................................................................................. 96
Mapping the Properties Conguration ............................................................................................ 97
Attribute Renaming Property ..................................................................................................... 97
Forbidden Entry Property ........................................................................................................... 97
LDAP Server Property ................................................................................................................. 98
Sun Condential: Registered
5
Page 6

Contents
Load Balancing Property ............................................................................................................. 99
Search Size Limit Property ........................................................................................................ 101
Log Property ............................................................................................................................... 101
Mapping the Events Conguration ................................................................................................. 103
Mapping the Actions Conguration ............................................................................................... 104
Conguring Directory Proxy Server 6.0 as a Simple Connection-Based Router ....................... 104
7 Migrating Identity Synchronization for Windows .......................................................................105
Migration Overview .......................................................................................................................... 106
Before You Migrate Identity Synchronization for Windows ....................................................... 106
Preparing for Identity Synchronization for Windows Migration ............................................... 107
Exporting Version 1.1 Conguration ...................................................................................... 107
Checking for Undelivered Messages ........................................................................................ 114
▼ Using the checktopics Utility ............................................................................................ 114
▼ To Clear Messages .............................................................................................................. 115
Forcing Password Changes on Windows NT ......................................................................... 116
Migrating Your System ..................................................................................................................... 116
Preparing for Migration ............................................................................................................ 117
▼ Preparing to migrate from version 1.1, and 1.1 SP1, to version 6.0 .............................. 118
Uninstalling Identity Synchronization for Windows ............................................................ 120
▼ To Uninstall Identity Synchronization for Windows Version 1.1 ............................... 120
Installing or Upgrading the Dependent Products .................................................................. 122
Installing Identity Synchronization for Windows 6.0 ........................................................... 122
▼ To install the Identity Synchronization for Windows 6.0 components: ...................... 122
What to Do if the 1.1 Uninstallation Fails ...................................................................................... 125
Manually Uninstalling 1.1 Core and Instances from Solaris ................................................ 125
▼ To Manually Uninstall Core From a Solaris Machine: ................................................... 126
Manually Uninstalling 1.1 Core and Instances from Windows 2000 .................................. 130
▼ To uninstall Core from a Windows 2000 machine: ........................................................ 131
▼ Manually Uninstalling a 1.1 Instance from Windows NT .................................................... 135
Other Migration Scenarios ............................................................................................................... 139
Multi-Master Replication Deployment ................................................................................... 140
Multi-Host Deployment with Windows NT .......................................................................... 141
Checking the Logs ............................................................................................................................. 144
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 20076
Sun Condential: Registered
Page 7

Contents
Index ................................................................................................................................................... 145
Sun Condential: Registered
7
Page 8

8
Sun Condential: Registered
Page 9

Figures
FIGURE 4–1 Existing version 5 Topology ..................................................................................... 55
FIGURE 4–2 Isolating the Consumer From the Topology ..........................................................55
FIGURE 4–3 Migrating the version 5 Consumer ......................................................................... 56
FIGURE 4–4 Placing the 6.0 Consumer Into the Topology ........................................................57
FIGURE 4–5 Existing version 5 Topology With Migrated Consumers ..................................... 58
FIGURE 4–6 Isolating the HubFrom the Topology ..................................................................... 58
FIGURE 4–7 Migrating the version 5 Hub .................................................................................... 59
FIGURE 4–8 Placing the 6.0 Hub Into the Topology ...................................................................60
FIGURE 4–9 Existing version 5 Topology With Consumers and Hubs Migrated ................... 61
FIGURE 4–10 Isolating the Master From the Topology ................................................................ 62
FIGURE 4–11 Migrating the version 5 Master ................................................................................ 62
FIGURE 4–12 Placing the 6.0 Master Into the Topology ............................................................... 63
FIGURE 4–13 Existing version 5 Topology ..................................................................................... 64
FIGURE 4–14 Existing Topology With Migrated Servers ............................................................. 65
FIGURE 4–15 Migrated Topology With Promoted HubReplicas ............................................... 66
FIGURE 4–16 New Fully-Meshed All-Master Topology ............................................................... 67
FIGURE 7–1 Migrating a Single-HostDeployment ................................................................... 117
FIGURE 7–2 Migrating a Multi-Master Replication Deployment ...........................................141
FIGURE 7–3 Migrating a Multi-HostDeployment with Windows NT ...................................143
Sun Condential: Registered
9
Page 10

10
Sun Condential: Registered
Page 11

Tables
TABLE 1–1 Migration Matrix Showing Support for AutomatedMigration ........................... 28
TABLE 3–1 Change Log AttributeName Changes .................................................................... 41
TABLE 3–2 Fractional Replication Attribute Name Changes ................................................... 41
TABLE 3–3 Mapping Between 5 and 6.0 Password Policy Attributes ...................................... 43
TABLE 5–1 Directory Server 5 and 6 commands ....................................................................... 71
TABLE 5–2 Directory Server 5 and 6 Commands (Subcommands of the directoryserver
Command) ................................................................................................................. 73
TABLE 5–3 Version 5 Commands That Have Been Deprecated .............................................. 73
TABLE 5–4 Support for Plug-Ins .................................................................................................. 80
TABLE 5–5 Tools Previously Under ServerRoot/shared/bin .................................................... 80
TABLE 5–6 Location of Certicate and Key Files ....................................................................... 81
TABLE 5–7 Instance-SpecicSubdirectories ............................................................................. 82
TABLE 6–1 Mapping of Version 5 Global Conguration Attributes to 6.0 Properties ......... 84
TABLE 6–2 Mapping of Security Conguration ........................................................................ 86
TABLE 6–3 Mapping of Connection Pool Attributes ................................................................ 87
TABLE 6–4 Mapping Between Version 5 Group Attributes and Version 6 Connection
Handler Properties .................................................................................................... 88
TABLE 6–5 Mapping Between Version 5 Network Group Attributes and 6.0 Properties ..... 89
TABLE 6–6 Mapping of Directory Proxy Server 5 Bind Forwarding Attributes to Directory
Proxy Server 6 Connection Handler Property Settings ........................................ 90
TABLE 6–7 Mapping of Directory Proxy Server 5 Operation Forwarding Attributes to
Directory Proxy Server 6 Request Filtering Properties ......................................... 91
TABLE 6–8 Mapping Directory Proxy Server 5 Search Request Control Attributes to
Directory Proxy Server 6.0 Properties .................................................................... 93
TABLE 6–9 Mapping of Directory Proxy Server 5 Compare Request Control Attributes to
Directory Proxy Server 6 Properties ....................................................................... 93
TABLE 6–10 Mapping of Directory Proxy Server 5 Search Request Modifying Attributes to
Directory Proxy Server 6 Properties ....................................................................... 94
TABLE 6–11 Mapping of Directory Proxy Server 5 Search Response Restriction Attributesto
Directory Proxy Server 6.0 Properties .................................................................... 95
Sun Condential: Registered
11
Page 12

Tables
TABLE 6–12 Mapping of Directory Proxy Server 5 Referral Conguration Attributes to
Directory Proxy Server 6 resource limits Properties ............................................. 96
TABLE 6–13 Mapping of Directory Proxy Server 5 Server Load Conguration Attributes to
Directory Proxy Server 6.0 Resource Limits Properties ....................................... 96
TABLE 6–14 Mapping of Directory Proxy Server 5 Server Load Conguration Attributes to
Directory Proxy Server 6 Resource Limits Properties .......................................... 98
TABLE 6–15 Mapping of ids-proxy-sch-LDAPServer Attributes to Data Source Properties
...................................................................................................................................... 99
TABLE 6–16 Mapping of Version 5 Search Size Limit Attributes to 6.0 Properties ...............101
TABLE 6–17 Version 5 and Version 6 Log Functionality .......................................................... 102
TABLE 6–18 Mapping Between Version 5 Event Attributes and Version 6 Connection
Handler Properties .................................................................................................. 103
TABLE 7–1 Component Distribution in a Multi-Master Replication Deployment ............ 140
TABLE 7–2 Multi-Host Deployment .........................................................................................142
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200712
Sun Condential: Registered
Page 13

Examples
EXAMPLE 7–1 Sample Export Conguration File .........................................................................109
Sun Condential: Registered
13
Page 14

14
Sun Condential: Registered
Page 15

Preface
This Migration Guide describes how to migrate the components of Directory Server Enterprise
Edition to version 6.0. The guide provides migration instructions for Directory Server,
Directory Proxy Server, and Identity Synchronization for Windows.
Who Should Use This Book
This guide is intended for directory service administrators who are migrating to Directory
Server Enterprise Edition 6.0. The guide might also be useful to business planners who are
considering migrating to the new version.
BeforeYou Read This Book
If you are not yet familiar with this version of Directory Server Enterprise Edition, you might
want to start by evaluating the new features and capabilities of the product. For more
information, see the Sun Java System Directory Server Enterprise Edition 6.0 Evaluation Guide
and the Sun Java System Directory Server Enterprise Edition 6.0 Release Notes.
HowThis Book Is Organized
Chapter 1 describes the steps involved in migrating to Directory Server 6.0.
Chapter 2 explains how to use the migration tool provided with Directory Server 6.0.
Chapter 3 describes the process for manual migration of each part of Directory Server.
Chapter 4 describes the issues involved in migrating replicated servers.
Chapter 5 describes the architectural changes in Directory Server 6.0 that aect migration from
a previous version.
Chapter 6 describes how the conguration properties in Directory Proxy Server 6.0 can be used
to simulate a version 5 conguration.
Chapter 7 describes the steps involved in migrating to Identity Synchronization for Windows
6.0.
Sun Condential: Registered
15
Page 16

Preface
Directory Server Enterprise Edition Documentation Set
This Directory Server Enterprise Edition documentation set explains how to use Sun Java
System Directory Server Enterprise Edition to evaluate, design, deploy, and administer
directory services. In addition, it shows how to develop client applications for Directory Server
Enterprise Edition. The Directory Server Enterprise Edition documentation set is available at
http://docs.sun.com/coll/1224.1.
For an introduction to Directory Server Enterprise Edition, review the following documents in
the order in which they are listed.
TABLE P–1 Directory Server Enterprise Edition Documentation
Document Title Contents
Sun Java System Directory Server Enterprise
Edition 6.0 Release Notes
Sun Java System Directory Server Enterprise
Edition 6.0 Documentation Center
Sun Java System Directory Server Enterprise
Edition 6.0 Evaluation Guide
Sun Java System Directory Server Enterprise
Edition 6.0 Deployment Planning Guide
Sun Java System Directory Server Enterprise
Edition 6.0 Installation Guide
Sun Java System Directory Server Enterprise
Edition 6.0 Migration Guide
Contains the latest information about Directory Server Enterprise Edition,
including known problems.
Contains links to key areas of the documentation set.
Introduces the key features of this release. Demonstrates how these features
work and what they oer in the context of a ctional deployment that you can
implement on a single system.
Explains how to plan and design highly available, highly scalable directory
services based on Directory Server Enterprise Edition. Presents the basic
concepts and principles of deployment planning and design. Discusses the
solution life cycle, and provides high-level examples and strategies to use when
planning solutions based on Directory Server Enterprise Edition.
Explains how to install the Directory Server Enterprise Edition software. Shows
how to select which components to install, congure those components after
installation, and verify that the congured components function properly.
For instructions on installing Directory Editor, go to
http://docs.sun.com/coll/DirEdit_05q1.
Make sure you read the information in Sun Java System Directory Server
Enterprise Edition 6.0 Release Notes concerning Directory Editor before you
install Directory Editor.
Provides instructions for upgrading components from earlier versions of
Directory Server, Directory Proxy Server, and Identity Synchronization for
Windows.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200716
Sun Condential: Registered
Page 17

TABLE P–1 Directory Server Enterprise Edition Documentation (Continued)
Document Title Contents
Preface
Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide
Sun Java System Directory Server Enterprise
Edition 6.0 Developer’s Guide
Sun Java System Directory Server Enterprise
Edition 6.0 Reference
Sun Java System Directory Server Enterprise
Edition 6.0 Man Page Reference
Sun Java System Identity Synchronization for
Windows 6.0 Deployment Planning Guide
Related Reading
Provides command-line instructions for administering Directory Server
Enterprise Edition.
For hints and instructions on using the Directory Service Control Center,
DSCC, to administer Directory Server Enterprise Edition, see the online help
provided in DSCC.
For instructions on administering Directory Editor, go to
http://docs.sun.com/coll/DirEdit_05q1.
For instructions on installing and conguring Identity Synchronization for
Windows, see Part II, “Installing Identity Synchronization for Windows,”in
Sun Java System Directory Server Enterprise Edition 6.0 Installation Guide.
Shows how to develop server plug-ins with the APIs that are provided as part of
Directory Server Enterprise Edition.
Introduces the technical and conceptual foundations of Directory Server
Enterprise Edition. Describes its components, architecture, processes, and
features. Also provides a reference to the developer APIs.
Describes the command-line tools, schema objects, and other public interfaces
that are available through Directory Server Enterprise Edition. Individual
sections of this document can be installed as online manual pages.
Provides general guidelines and best practices for planning and deploying
Identity Synchronization for Windows
The SLAMD Distributed Load Generation Engine (SLAMD) is a JavaTMapplication that is
designed to stress test and analyze the performance of network-based applications. It was
originally developed by Sun Microsystems, Inc. to benchmark and analyze the performance of
LDAP directory servers. SLAMD is available as an open source application under the Sun
Public License, an OSI-approved open source license. To obtain information about SLAMD, go
http://www.slamd.com/. SLAMD is also available as a java.net project. See
to
https://slamd.dev.java.net/.
Java Naming and Directory Interface (JNDI) technology supports accessing the Directory
Server using LDAP and DSML v2 from Java applications. For information about JNDI, see
http://java.sun.com/products/jndi/. The JNDI Tutorial contains detailed descriptions and
examples of how to use JNDI. This tutorial is at
http://java.sun.com/products/jndi/tutorial/.
Directory Server Enterprise Edition can be licensed as a standalone product, as a component of
Sun Java Enterprise System, as part of a suite of Sun products, such as the Sun Java Identity
Management Suite, or as an add-on package to other software products from Sun. Java
Sun Condential: Registered
17
Page 18

Preface
Enterprise System is a software infrastructure that supports enterprise applications distributed
across a network or Internet environment. If Directory Server Enterprise Edition was licensed
as a component of Java Enterprise System, you should be familiar with the system
documentation at
http://docs.sun.com/coll/1286.2.
Identity Synchronization for Windows uses Message Queue with a restricted license. Message
Queue documentation is available at
http://docs.sun.com/coll/1307.2.
Identity Synchronization for Windows works with Microsoft Windows password policies.
■
Information about password policies for Windows 2003 is available in the Microsoft
documentation
■
Information about changing passwords, and about group policies in Windows 2003 is
available the
■
Information about the Microsoft Certicate Services Enterprise Root certicate authority is
available in the
■
Information about conguring LDAP over SSL on Microsoft systems is available in the
online.
Microsoft documentation online.
Microsoft support documentation online.
Microsoft support documentation online.
Redistributable Files
Directory Server Enterprise Edition does not provide any les that you can redistribute.
Default Paths and Command Locations
This section explains the default paths used in the documentation, and gives the locations of
commands on dierent operating systems and deployment types.
Default Paths
The table in this section describes the default paths that are used in this document. For full
descriptions of the les installed, see also Chapter 15, “Directory Server File Reference,” in Sun
Java System Directory Server Enterprise Edition 6.0 Reference, Chapter 26, “Directory Proxy
Server File Reference,” in Sun Java System Directory Server Enterprise Edition 6.0 Reference,or
Appendix A, “Directory Server Resource Kit File Reference,” in Sun Java System Directory
Server Enterprise Edition 6.0 Reference.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200718
Sun Condential: Registered
Page 19
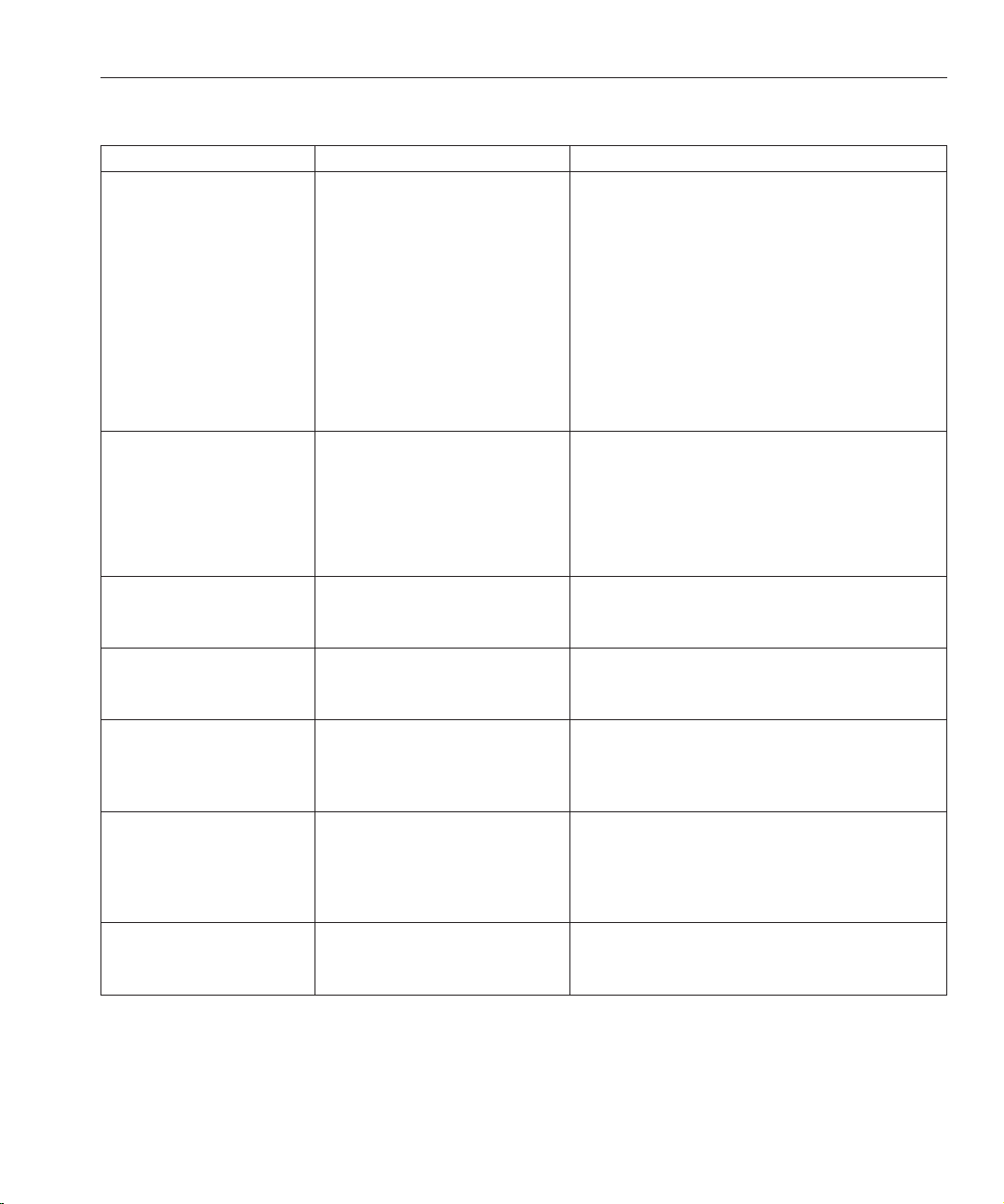
TABLE P–2 DefaultPaths
Placeholder Description Default Value
Preface
install-path Represents the base installation
directory for Directory Server
Enterprise Edition software.
The software is installed in directories
below this base install-path.For
example, Directory Server software is
installed in install-path/ds6/.
instance-path Represents the full path to an instance
of Directory Server or Directory Proxy
Server.
The documentation uses /local/ds/
for Directory Server and /local/dps/
for Directory Proxy Server.
serverroot Represents the parent directory of the
Identity Synchronization for Windows
installation location
isw-hostname Represents the Identity
Synchronization for Windows
instance directory
When you install from a zip distribution using
dsee_deploy(1M), the default install-path is the current
directory. You can set the install-path using the -i option
of the dsee_deploy command. When you install from a
native package distribution, such as you would using the
Java Enterprise System installer, the default install-path is
one of the following locations:
■
Solaris systems - /opt/SUNWdsee/.
■
HP-UX systems - /opt/sun/.
■
Red Hat systems - /opt/sun/.
■
Windows systems - C:\Program
Files\Sun\JavaES5\DSEE.
No default path exists. Instance paths must nevertheless
always be found on a local le system.
The following directories are recommended:
/var on Solaris systems
/global if you are using Sun Cluster
Depends on your installation. Note the concept of a
serverroot no longer exists for Directory Server.
Depends on your installation
/path/to/cert8.db Represents the default path and le
name of the client’s certicate database
for Identity Synchronization for
Windows
serverroot/isw-hostname/
logs/
Represents the default path to the
Identity Synchronization for Windows
local logs for the System Manager,
each connector, and the Central
Logger
serverroot/isw-hostname/
logs/central/
Represents the default path to the
Identity Synchronization for Windows
central logs
Sun Condential: Registered
current-working-dir/cert8.db
Depends on your installation
Depends on your installation
19
Page 20
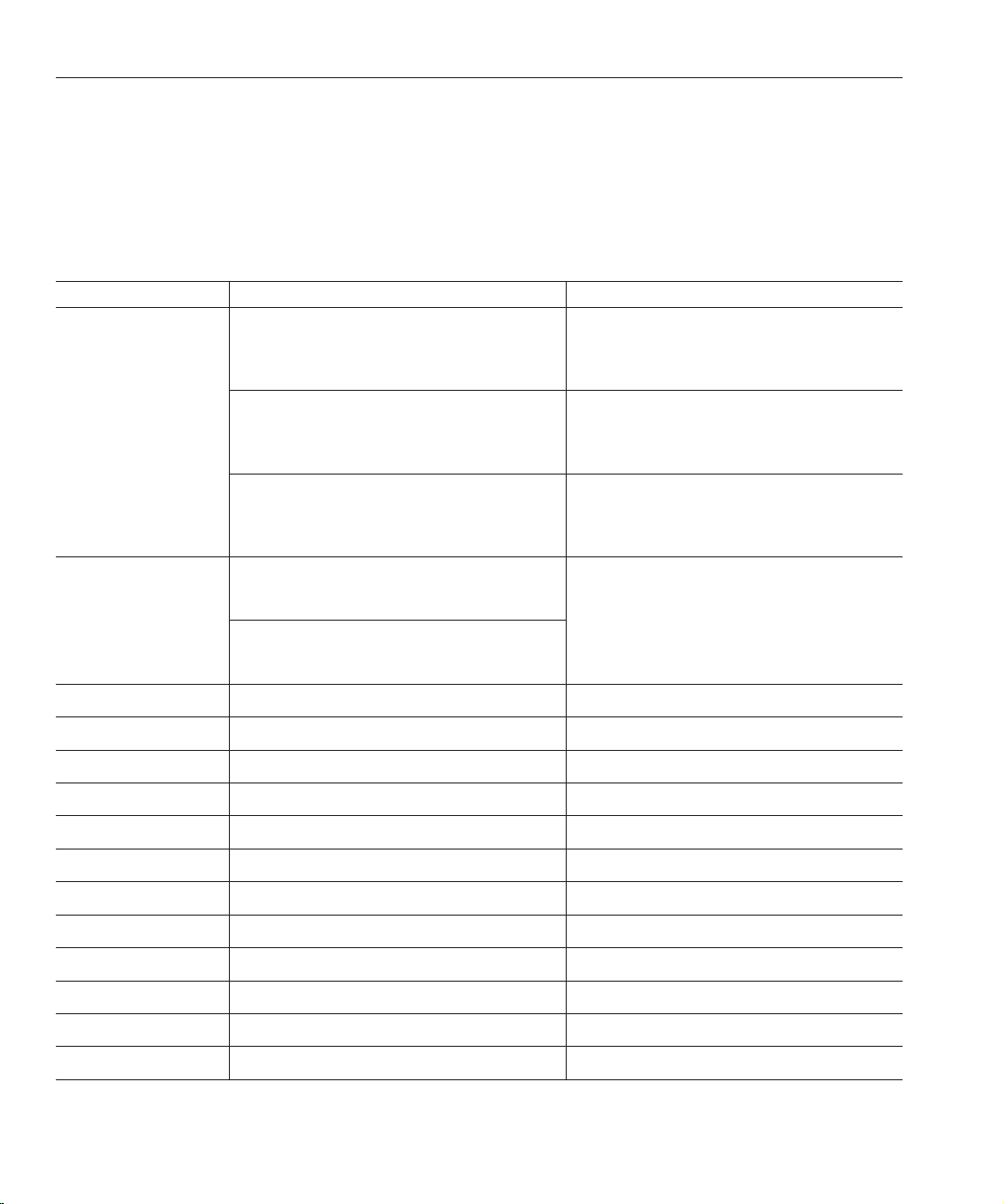
Preface
Command Locations
The table in this section provides locations for commands that are used in Directory Server
Enterprise Edition documentation. To learn more about each of the commands, see the relevant
man pages.
TABLE P–3 CommandLocations
Command Java ES, Native Package Distribution Zip Distribution
cacaoadm Solaris -
/usr/sbin/cacaoadm
Red Hat, HP-UX -
/opt/sun/cacao/bin/cacaoadm
Windows -
install-path\share\
cacao_2.0\bin\cacaoadm.bat
certutil Solaris -
/usr/sfw/bin/certutil
Red Hat, HP-UX -
/opt/sun/private/bin/certutil
dpadm(1M) install-path/dps6/bin/dpadm install-path/dps6/bin/dpadm
dpconf(1M) install-path/dps6/bin/dpconf install-path/dps6/bin/dpconf
dsadm(1M) install-path/ds6/bin/dsadm install-path/ds6/bin/dsadm
dsccmon(1M) install-path/dscc6/bin/dsccmon install-path/dscc6/bin/dsccmon
dsccreg(1M) install-path/dscc6/bin/dsccreg install-path/dscc6/bin/dsccreg
Solaris -
install-path/dsee6/
cacao_2.0/usr/lib/cacao/bin/cacaoadm
Red Hat, HP-UX -
install-path/dsee6/
cacao_2.0/cacao/bin/cacaoadm
Windows -
install-path\
dsee6\cacao_2.0\bin\cacaoadm.bat
install-path/dsee6/bin/certutil
dsccsetup(1M) install-path/dscc6/bin/dsccsetup install-path/dscc6/bin/dsccsetup
dsconf(1M) install-path/ds6/bin/dsconf install-path/ds6/bin/dsconf
dsee_deploy(1M) Not provided install-path/dsee6/bin/dsee_deploy
dsmig(1M) install-path/ds6/bin/dsmig install-path/ds6/bin/dsmig
entrycmp(1) install-path/ds6/bin/entrycmp install-path/ds6/bin/entrycmp
fildif(1) install-path/ds6/bin/fildif install-path/ds6/bin/fildif
idsktune(1M) install-path/dsrk6/bin/idsktune install-path/dsrk6/bin/idsktune
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200720
Sun Condential: Registered
Page 21
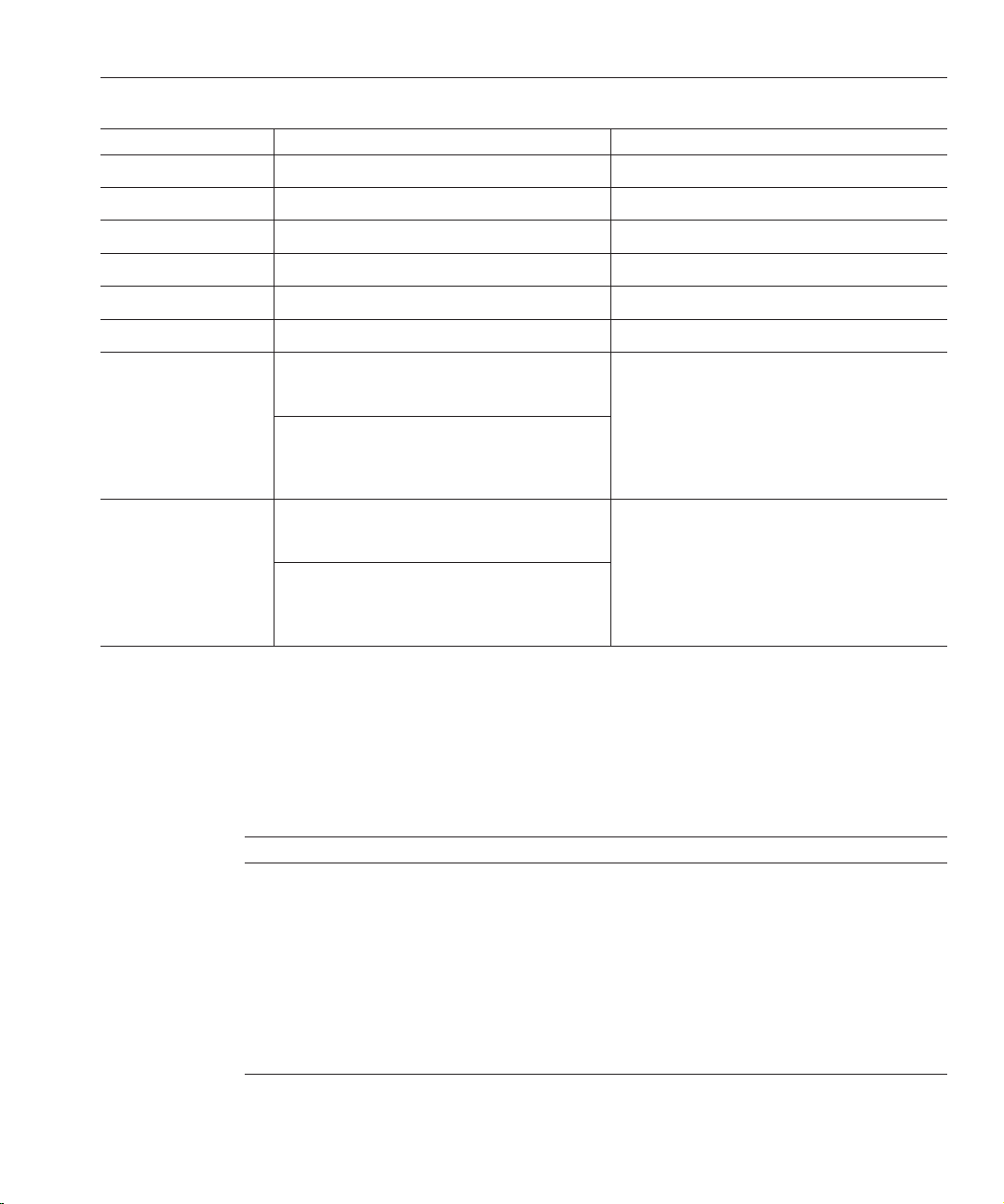
TABLE P–3 Command Locations (Continued)
Command Java ES, Native Package Distribution Zip Distribution
insync(1) install-path/ds6/bin/insync install-path/ds6/bin/insync
ns-accountstatus(1M) install-path/ds6/bin/ns-accountstatus install-path/ds6/bin/ns-accountstatus
ns-activate(1M) install-path/ds6/bin/ns-activate install-path/ds6/bin/ns-activate
ns-inactivate(1M) install-path/ds6/bin/ns-inactivate install-path/ds6/bin/ns-inactivate
repldisc(1) install-path/ds6/bin/repldisc install-path/ds6/bin/repldisc
schema_push(1M) install-path/ds6/bin/schema_push install-path/ds6/bin/schema_push
Preface
smcwebserver Solaris, Linux, HP-UX-
/usr/sbin/smcwebserver
Windows -
install-path\share\
webconsole\bin\smcwebserver
wcadmin Solaris, Linux, HP-UX -
/usr/sbin/wcadmin
Windows -
install-path\share\
webconsole\bin\wcadmin
Typographic Conventions
The following table describes the typographic changes that are used in this book.
TABLE P–4 TypographicConventions
Typeface Meaning Example
AaBbCc123 The names of commands, les, and
directories, and onscreen computer
output
This command pertains only to Directory Service
Control Center, which is not available in the zip
distribution.
This command pertains only to Directory Service
Control Center, which is not available in the zip
distribution.
Edit your .login le.
Use ls -a to list all les.
machine_name% you have mail.
AaBbCc123 What you type, contrasted with onscreen
computer output
AaBbCc123 A placeholder to be replaced with a real
name or value
Sun Condential: Registered
machine_name% su
Password:
The command to remove a le is rm lename.
21
Page 22

Preface
TABLE P–4 Typographic Conventions (Continued)
Typeface Meaning Example
AaBbCc123 Book titles, new terms, and terms to be
emphasized (note that some emphasized
items appear bold online)
Shell Prompts in Command Examples
The following table shows default system prompts and superuser prompts.
TABLE P–5 ShellPrompts
Shell Prompt
C shell on UNIX and Linux systems machine_name%
C shell superuser on UNIX and Linux systems machine_name#
Bourne shell and Korn shell on UNIX and Linux systems $
Bourne shell and Korn shell superuser on UNIX and Linux systems #
Microsoft Windows command line C:\
Symbol Conventions
Read Chapter 6 in the User's Guide.
A cache is a copy that is stored locally.
Do not save the le.
The following table explains symbols that might be used in this book.
TABLE P–6 SymbolConventions
Symbol Description Example Meaning
[] Contains optional arguments
and command options.
{|} Contains a set of choices for a
required command option.
${ } Indicates a variable
reference.
- Joins simultaneous multiple
keystrokes.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200722
Sun Condential: Registered
ls [-l] The -l option is not required.
-d {y|n} The -d option requires that you use
either the y argument or the n
argument.
${com.sun.javaRoot} References the value of the
com.sun.javaRoot variable.
Control-A Press the Control key while you press
the A key.
Page 23

TABLE P–6 Symbol Conventions (Continued)
Symbol Description Example Meaning
Preface
+ Joins consecutive multiple
keystrokes.
→ Indicates menu item
selection in a graphical user
interface.
Ctrl+A+N Press the Control key, release it, and
File → New → Templates From the File menu, choose New.
Documentation, Support, and Training
The Sun web site provides information about the following additional resources:
■
Documentation (http://www.sun.com/documentation/)
■
Support (http://www.sun.com/support/)
■
Training (http://www.sun.com/training/)
Third-PartyWeb Site References
Third-party URLs are referenced in this document and provide additional, related information.
Note – Sun is not responsible for the availability of third-party web sites mentioned in this
document. Sun does not endorse and is not responsible or liable for any content, advertising,
products, or other materials that are available on or through such sites or resources. Sun will not
be responsible or liable for any actual or alleged damage or loss caused or alleged to be caused by
or in connection with use of or reliance on any such content, goods, or services that are available
on or through such sites or resources.
then press the subsequent keys.
From the New submenu, choose
Templates.
Searching Sun Product Documentation
Besides searching for Sun product documentation from the docs.sun.com web site, you can use
a search engine of your choice by typing the following syntax in the search eld:
search-term site:docs.sun.com
For example, to search for Directory Server, type the following:
"Directory Server" site:docs.sun.com
To include other Sun web sites in your search, such as java.sun.com, www.sun.com, and
developers.sun.com, use sun.com in place of docs.sun.com in the search eld.
Sun Condential: Registered
23
Page 24

Preface
Sun WelcomesYour Comments
Sun is interested in improving its documentation and welcomes your comments and
suggestions. To share your comments, go to http://docs.sun.com and click Send Comments.
In the online form, provide the full document title and part number. The part number is a
7-digit or 9-digit number that can be found on the book's title page or in the document's URL.
For example, the part number of this book is 819-0994.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200724
Sun Condential: Registered
Page 25

CHAPTER 1
1
Overview of the Migration Process for Directory Server
This chapter describes the steps involved in migrating to Directory Server 6.0. Directory Server
6.0 provides a migration tool, dsmig, that automates aspects of the migration for certain
platform/version combinations. If servers within your topology fall outside of these
combinations, the same migration steps must be performed manually.
This chapter includes the following topics:
■
“Before You Migrate” on page 25
■
“Deciding on the New Product Distribution” on page 27
■
“Outline of Migration Steps” on page 27
■
“Deciding on Automatic or Manual Migration” on page 28
Before You Migrate
This chapter provides an overview of the upgrade and data migration process.
Before upgrading, familiarize yourself with the new features and xes available in the current
version. Take the opportunity to review design decisions made during implementation of
existing directory services. For a description of all new features and xes, see “What’s New at a
Glance” in Sun Java System Directory Server Enterprise Edition 6.0 Evaluation Guide.For
information about the new features that specically aect migration, see
Chapter 5.
25
Sun Condential: Registered
Page 26

Before You Migrate
Prerequisites to Migrating a Single Directory Server Instance From 5.1
Before migrating from a 5.1 server instance, ensure that the following prerequisites are met:
■
Directory Server 6.0 must be installed. The new server can be installed on the same machine
as the existing server or on a dierent machine.
■
Ensure that the new machine has sucient local disk space to house binaries and databases
for both the old and new servers, and also enough extra space to hold LDIF les containing
the entries in all existing suxes. You can estimate the local disk space required as
somewhat larger than the following calculation.
local space required=2*(space for existing server) + (space for LDIF files)
Prerequisites to Migrating a Single Directory Server Instance From 5.2
Before migrating from a 5.2 server instance, ensure that the following prerequisites are met:
■
Directory Server 6.0 must be installed. The new server can be installed on the same machine
as the existing server or on a dierent machine.
■
Ensure that the new machine has sucient local disk space to house binaries and databases
for both the old and new servers, and also enough extra space to hold LDIF les containing
the entries in all existing suxes. You can estimate the local disk space required as
somewhat larger than the following calculation.
local space required=2*(space for existing server) + (space for LDIF files)
■
If you are using the automatic migration tool, the following two prerequisites must be met:
■
The existing server instance must be stopped cleanly.
■
If the new server is located on a dierent machine, a complete image of the original
server instance must be created on the new machine. This includes all schema les,
conguration les, security les, and database les, in an identical layout to the original
server root.
To determine whether you should use automatic or manual migration, see
Automatic or Manual Migration” on page 28
■
If your Directory Server deployment includes Identity Synchronization for Windows, you
.
“Deciding on
must uninstall Identity Synchronization for Windows before migrating to Directory Server
6.0. For information about migrating Identity Synchronization for Windows, see
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200726
Sun Condential: Registered
Chapter 7.
Page 27

Deciding on the New Product Distribution
Directory Server 6.0 is provided in two distributions:
■
Java Enterprise System distribution. This distribution takes the form of operating
system-specic packages, such as pkg for Solaris and rpm for Linux.
■
Compressed archive (zip) distribution.
There are two major dierences between these two distributions:
1. Installation from zip can be done anywhere on the system and as a non-root user. The Java
Enterprise System distribution requires installation as a super user. It is also more dicult
from an automated deployment perspective to install the packages anywhere but in the
default location.
2. The zip distribution can be installed as many times as required and multiple distinct
versions of the same product can coexist on a single operating system instance. This is not
true for the Java Enterprise System distribution. The new version of certain shared
component packages required by Directory Server are incompatible with the previous
version of these packages. When you migrate to the new version of Directory Server using
the Java Enterprise System distribution, the old Directory Server version will no longer run
on that machine.
Outline of Migration Steps
Depending on your environment and the specic requirements of your organization, select the
appropriate packaging format. Note that the Sun Java Web Console is currently available only
in the Java Enterprise System distribution.
Outline of Migration Steps
Migration to Directory Server 6.0 can be broken down into the following distinct steps:
1. Migrating the Schema
2. Migrating the Security Settings
3. Migrating the Conguration
4. Migrating the Data
5. Migrating the Plug-Ins
6. Post-migration tasks
To avoid unforeseen problems with the migration, these steps should be performed in the order
listed above. In certain cases, you can automate some or all of these steps, using the dsmig
command. The following section indicates what can be automated and what must be done
manually, depending on your existing deployment.
Chapter 1 • Overview of the Migration Process for Directory Server 27
Sun Condential: Registered
Page 28
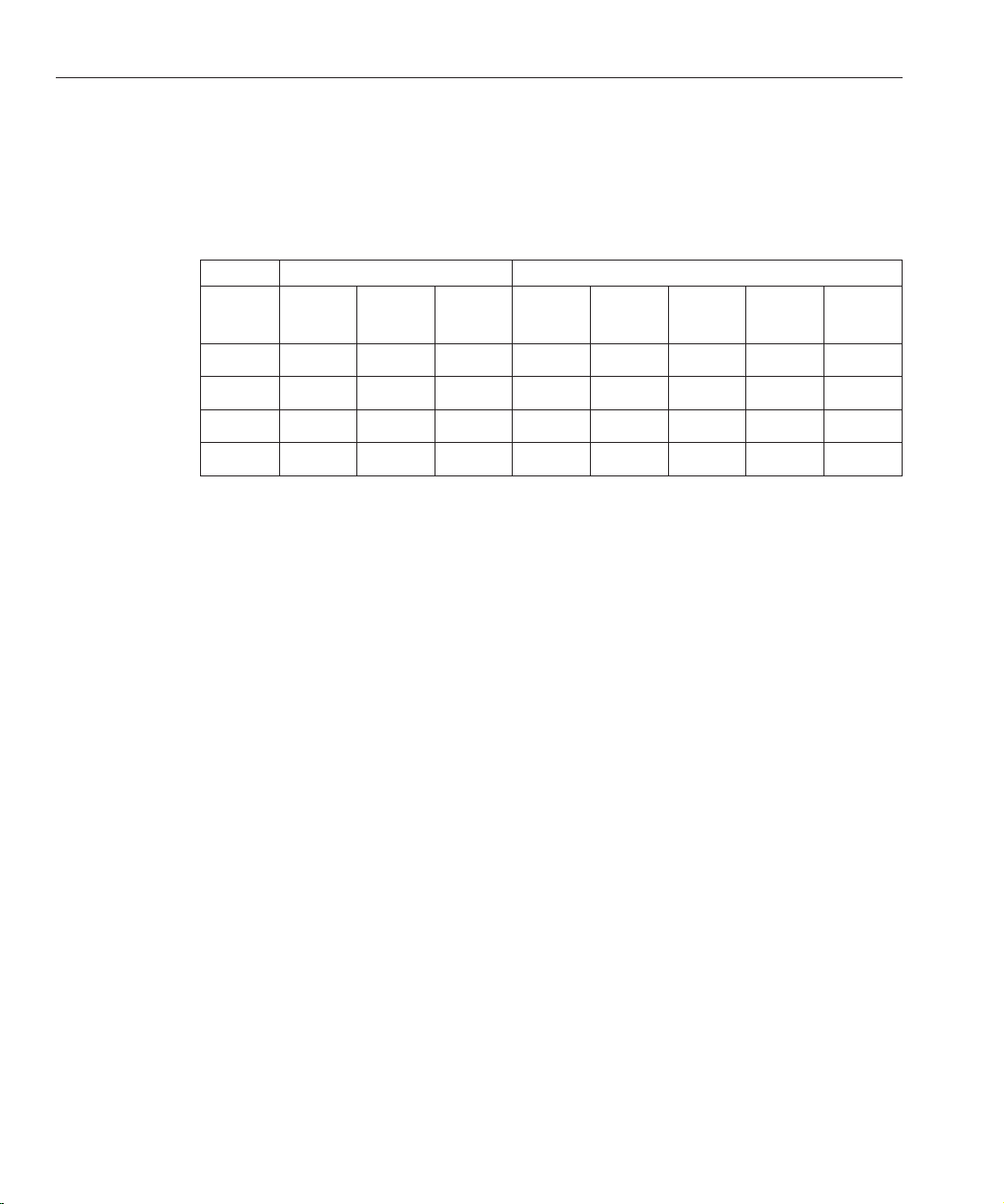
Deciding on Automatic or Manual Migration
Deciding on Automatic or Manual Migration
This section provides a table that shows when you can use dsmig and when you need to migrate
manually. It is based on the migration steps described in the previous section.
TABLE 1–1 Migration Matrix Showing Support for Automated Migration
From To Migration Step
Software
Version Version
5.1 6.0 Any Any Manual Manual Manual Manual Manual
5.2 6.0 Dierent Any dsmig dsmig dsmig Manual Manual
5.2 6.0 Same Dierent dsmig dsmig dsmig Manual Manual
5.2 6.0 Same Same dsmig dsmig dsmig dsmig Manual
The following two chapters explain how to perform each migration step outlined above, either
automatically, or manually. For information on automatic migration, see Chapter 2.For
information on manual migration, see Chapter 3.
(32/64–bit) OS Schema Cong Security Data Plug-Ins
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200728
Sun Condential: Registered
Page 29

CHAPTER 2
2
Automated Migration Using the dsmig Command
Directory Server 6.0 provides a command-line migration tool to help you migrate from a
Directory Server 5.2 instance to a Directory Server 6.0 instance. You can only use the migration
tool if your deployment satises the requirements for automatic migration described in
“Deciding on Automatic or Manual Migration” on page 28.
The migration tool provides migration per instance. If several instances exist within the same
server root, the migration tool must be run for each individual instance.
This chapter explains how to use the migration tool and covers the following topics:
■
“About the Automatic Migration Tool” on page 29
■
“Prerequisites for Running dsmig” on page 30
■
“Using dsmig to Migrate the Schema” on page 30
■
“Using dsmig to Migrate Security Data” on page 31
■
“Using dsmig to Migrate Conguration Data” on page 31
■
“Using dsmig to Migrate User Data” on page 35
■
“Tasks to be Performed After Automatic Migration” on page 35
About the Automatic Migration Tool
The migration tool, dsmig, is delivered with the Directory Server 6.0 packages. When these
packages have been installed, dsmig is located in install-path/ds6/bin.
dsmig must be run on the machine on which the new Directory Server instance will be located.
When the command is run, a migration directory is created within the new instance directory
(new-instance-path/migration). This directory is a repository for data produced by the
migration, including log les and migration status les.
dsmig includes a set of sub-commands and options, that map to the individual migration steps
described in
dsmig, see dsmig(1M).
“Outline of Migration Steps” on page 27. For information about the usage of
Sun Condential: Registered
29
Page 30

Prerequisitesfor Running dsmig
Prerequisites for Running dsmig
In this section, old instance refers to the 5.2 instance and new instance refers to the Directory
Server 6.0 instance.
Before you use dsmig to migrate an instance, ensure that the following tasks have been
performed:
■
The Directory Server 6.0 packages (either zip, or native packages) have been installed.
The Directory Server 6.0 packages can be installed on the same machine that holds the
Directory Server 5.2 instance, or on a dierent machine.
■
The old instance must have been stopped correctly.
A disorderly shutdown of the old instance will cause problems during the migration. Even if
the old and new instance are on dierent machines, the old instance must be stopped before
the migration is started.
■
dsmig has access to the old instance les.
■
If the old and new instances are on dierent machines, a complete image of the old instance
must be created on the machine that hosts the new instance.
The complete image includes all the les required for migration of the instance (schema,
conguration, security and database les). The complete image les must be located in the
same directories as they were under the original Server Root. You can run cp -r to achieve
this, provided none of the les have been relocated outside the Server Root.
You can create and start the new instance manually, but is not mandatory to create the new
instance before running dsmig. dsmig checks whether a new Directory Server instance exists in
the specied path. If a new instance exists, the commands are carried out on this instance. If a
new instance does exist, the instance is created automatically.
The new instance can be created anywhere except for the exact location of the old instance.
Using dsmig to Migrate the Schema
Directory Server 5.2 schema les are located in
serverRoot/slapd-instance-path/config/schema. Directory Server 6.0 schema les are located
in INSTANCE-PATH/config/schema.
Directory Server 6.0 provides a new schema le, 00ds6pwp.ldif, that contains new password
policy attributes. In addition, certain conguration attributes have been added to 00core.ldif.
Apart from these les, the standard schema les provided with Directory Server 6.0 are identical
to those provided in 5.2.
To migrate the schema automatically, run the following command:
$ dsmig migrate-schema old-instance-path new-instance-path
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200730
Sun Condential: Registered
Page 31

When you run this command, any custom schema dened in the 99user.ldif le are copied to
the new instance. If the new instance is already in production, and you have already modied
the 99user.ldif le of the new instance, dsmig performs a best eort merge of the two les.
Custom schema dened in any other les are also copied to the new instance.
During schema migration, all fractional replication information is moved from the schema les.
Fractional replication must be redened in the new instance.
For more information, see dsmig(1M).
Using dsmig to Migrate Security Data
To migrate the security settings automatically, run the following command:
$ dsmig migrate-security old-instance-path new-instance-path
During the migration of security settings, dsmig performs the following tasks:
■
Backs up the certicate and database les in the new instance.
■
Copies the certicate database and key database les from the old instance to the new
instance.
■
Copies the password le from the old instance to the new instance.
■
Copies the certicate mapping le from the old instance to the new instance.
■
If the old instance uses an external security token, copies the security module database and
the external token library to the new instance.
Using dsmig to Migrate Conguration Data
For more information, see dsmig(1M).
Using dsmig to Migrate Conguration Data
Directory Server 5.2 conguration is specied in the le
serverRoot/slapd-instance-path/config/dse.ldif. Directory Server 6.0 conguration is
specied in the le instance-path/config/dse.ldif.
To migrate the conguration automatically, run the following command:
$ dsmig migrate-config old-instance-path new-instance-path
In this step, dsmig reads each LDIF entry in the conguration le (dse.ldif) of the 5.2 instance.
If these entries exist in the corresponding Directory Server 6.0 conguration le, their values are
updated. If the entries do not exist, they are created.
Migration of the conguration is done over LDAP. By default, dsmig binds to the new instance
securely, issuing a StartTLS request.
Chapter 2 • AutomatedMigration Using the dsmig Command 31
Sun Condential: Registered
Page 32

Using dsmig to Migrate Conguration Data
Note – By default, StartTLS is not enabled on Windows. If you are running dsmig on Windows,
use the -e or -–unsecured option to specify an unsecure connection. Alternatively, use the -Z
or --use-secure-port option to specify a secure connection over SSL. If you do not use either
of these options on Windows, dsmig issues a warning and the migration process terminates
with an error.
For more information see dsmig(1M). For details of the specic conguration attributes that are
migrated, see
Plug-in Conguration Data
dsmig migrates conguration data for certain Directory Server plug-ins only. For most system
plug-ins, conguration data is not migrated automatically.
dsmig migrates all conguration data for the CoS plug-in. In addition, dsmig migrates the
enabled or disabled state for the following system plug-ins:
■
7–bit Check
■
DSML Frontend
■
Pass-Through Authentication
■
Referential Integrity
■
Retro Change Log
■
UID Uniqueness
“Migration of Specic Conguration Attributes” on page 38.
When you migrate the conguration in verbose mode, dsmig issues a warning indicating which
system plug-in congurations are not migrated.
Plug-ins that you have created are not migrated. However, during the migration process user
plug-in conguration data is dumped in the le
new-instance-path/migration/old_userplugins_conf.ldif. These plug-ins must be
recompiled when the migration is complete.
Chained Sux Conguration Data
Conguration data for chained suxes is not migrated. By default, the conguration data is
dumped in the le new-instance-path/migration/old_chaining_conf.ldif. You can import
the chaining conguration data from this le after migration, if required.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200732
Sun Condential: Registered
Page 33

Using dsmig to Migrate Conguration Data
Conguration Data For SuxesWith Multiple
Backends
Conguration data for suxes with multiple backends is not migrated. If dsmig detects that a
sux has more than one backend, it does not migrate any of the conguration entries that
belong to that sux. This includes conguration entries for the mapping tree, replicas,
replication agreements, LDBM instances, indexes, and encrypted attributes. Instead, all of these
entries are dumped in the le new-instance-path/migration/old_distribution_conf.ldif.
You can import the distribution conguration data from this le after migration, if required.
Replication Conguration Data
Conguration data for replication is not migrated by default. If you want this data to be
migrated, select the -R option. By default, the data is dumped in the le
new-instance-path/migration/old_replication_conf.ldif. You can import the replication
conguration data from this le after migration, if required.
Conguration Data for o=netscapeRoot
Conguration data for the o=NetscapeRoot sux is not migrated by default. If this information
is required, use the -N to migrate the conguration data. If you do not use the -N option, the data
is dumped in the le new-instance-path/migration/old_netscape_conf.ldif. You can
import the conguration data from this le after migration, if required.
Conguration Attributes Not Migrated by dsmig
The following common conguration attributes are not migrated automatically.
This is not an exhaustive list. You might have used additional conguration attributes that must
be migrated manually.
ds-hdsml-dsmlschemalocation
ds-hdsml-soapschemalocation
dsKeyedPassword
dsMappedDN
dsMatching-pattern
dsMatching-regexp
dsSaslPluginsEnable
dsSaslPluginsEnable
dsSaslPluginsPath
dsSearchBaseDN
dsSearchFilter
Chapter 2 • AutomatedMigration Using the dsmig Command 33
Sun Condential: Registered
Page 34

Using dsmig to Migrate Conguration Data
nsabandonedsearchcheckinterval
nsbindconnectionslimit
nsbindretrylimit
nsbindtimeout
nschecklocalaci
nsconcurrentbindlimit
nsconcurrentoperationslimit
nsconnectionlife
nshoplimit
nsMatchingRule
nsmaxresponsedelay
nsmaxtestresponsedelay
nsoperationconnectionslimit
nspossiblechainingcomponents
nspossiblechainingcomponents
nspossiblechainingcomponents
nspossiblechainingcomponents
nspossiblechainingcomponents
nspossiblechainingcomponents
nsproxiedauthorization
nsreferralonscopedsearch
nsslapd-db-durable-transaction
nsslapd-db-home-directory
nsslapd-db-logbuf-size
nsslapd-db-logdirectory
nsslapd-db-replication-batch-val
nsslapd-db-transaction-logging
nsslapd-directory
nsslapd-disk-full-threshold
nsslapd-disk-low-threshold
nsslapd-enquote-sup-oc
nsslapd-exclude-from-export
nsslapd-groupevalnestlevel
nsslapd-localhost
nsslapd-localuser
nsslapd-mode
nsslapd-port
nsslapd-return-exact-case
nsslapd-rewrite-rfc1274
nsslapd-secureport
nsslapd-security
nsSSL2
nsSSL3
nsSSLActivation
nsSSLServerAuth
nsSSLSessionTimeout
nsState
nstransmittedcontrols
plugin-order-preoperation-finish-entry-encode-result
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200734
Sun Condential: Registered
Page 35

Using dsmig to Migrate User Data
In Directory Server 5.2, data is stored in serverRoot/slapd-instance-name/db. Directory Server
6.0 stores user data in instance-path/db.
To migrate data automatically, run the following command:
$ dsmig migrate-data old-instance-path new-instance-path
All suxes are migrated by default, except the o=netscapeRoot sux. dsmig copies the data,
the indexes, and the transaction logs. The database context, that is, the state of the database, is
not migrated.
In the new Directory Server administration model, there is no Conguration Directory Server.
This means that the o=netscapeRoot sux is no longer relevant, unless your deployment
includes Identity Synchronization for Windows. By default, dsmig does not migrate the
o=netscapeRoot database, unless specically requested. To migrate the o=netscapeRoot
database, use the -N option with the migrate-data subcommand.
For more information, see dsmig(1M).
Note – During data migration, Directory Server checks whether nested group denitions exceed
30 levels. Deep nesting can signify a circular group denition, where a nested group contains a
group that is also its parent. When a group with more than 30 nesting levels is encountered,
Directory Server stops calculating the isMemberOf attributes for additional levels.
Tasksto be Performed After Automatic Migration
Each time this happens, Directory Server logs an error. You safely ignore these errors, although
you should examine the denition of the group mentioned in the error message for potential
circular denitions.
Tasks to be Performed After Automatic Migration
If you have used dsmig to migrate your server automatically, only the following two
post-migration tasks must be completed:
■
If you have customized user plug-ins, these need to be recompiled and added to the new
server manually.
■
If the migrated server was part of a replicated topology, see “Issues Related to Migrating
Replicated Servers” on page 52
Chapter 2 • AutomatedMigration Using the dsmig Command 35
Sun Condential: Registered
.
Page 36

36
Sun Condential: Registered
Page 37

CHAPTER 3
3
Migrating Directory Server Manually
If your deployment does not satisfy the requirements for automatic migration described in
“Deciding on Automatic or Manual Migration” on page 28, you must migrate the servers
manually. This chapter describes the process for manual migration of each part of the server.
The chapter covers the following topics:
■
“Before You Start a Manual Migration” on page 37
■
“Migrating the Schema Manually” on page 38
■
“Migrating Conguration Data Manually” on page 38
■
“Migrating Security Settings Manually” on page 48
■
“Migrating User Data Manually” on page 49
■
“Migrating User Plug-Ins Manually” on page 50
■
“Tasks to be Performed After Manual Migration” on page 50
BeforeYou Start a Manual Migration
Migrating an instance manually involves migrating each part of the server in the same order as
performed by the automatic migration tool (dsmig). In this section, old instance refers to the
version 5 instance and new instance refers to the 6.0 instance.
Before you start a manual migration, ensure that the following tasks have been performed:
■
Directory Server 6.0 software has been installed.
Directory Server 6.0 software can be installed on the same machine that holds the Directory
Server 5 instance, or on a dierent machine.
■
The new instance has been created.
The new instance can be created anywhere except for the exact location of the old instance.
The new instance can be installed on the same LDAP/LDAPS port or on a dierent port. If
you use dierent ports, any replication agreements to the new instance must be changed
accordingly.
Sun Condential: Registered
37
Page 38

Migrating the Schema Manually
■
The old instance has been stopped correctly.
A disorderly shutdown of the old instance will cause problems during migration. Even if the
old and new instances are on dierent machines, the old instance must be stopped before
migration is started.
Migrating the Schema Manually
Directory Server 5 schema les are located in serverRoot/slapd-serverID/config/schema.
Directory Server 6.0 schema les are located in instance-path/config/schema.
Directory Server 6.0 provides a new schema le, 00ds6pwp.ldif, that contains new password
policy attributes. In addition, certain conguration attributes have been added to 00core.ldif.
Apart from these les, the standard schema les provided with Directory Server 6.0 are identical
to those provided in version 5.
To migrate the schema, perform the following steps:
1. Copy the 99user.ldif le from the existing instance to the new instance. If you have
already added custom schema to the new instance, you will need to choose which version of
the custom schema to keep.
2. If you have dened custom schema in any other les, copy these les to the new instance.
3. Any fractional replication information must be redened in the new instance.
Migrating CongurationData Manually
Directory Server 5 conguration is specied in the le
serverRoot/slapd-serverID/config/dse.ldif. Directory Server 6.0 conguration is specied
in the le instance-path/config/dse.ldif.
If you are migrating from 5.1, you must migrate the conguration les manually. The easiest
way to do this is to run the migrateInstance5 migration script to produce a 5.2 conguration,
and then to migrate the 5.2 conguration using dsmig. For information on using
migrateInstance5, see the Directory Server 5.2 2005Q1 Installation and Migration Guide.For
information on using dsmig to migrate the conguration, see
Conguration Data” on page 31
The following section describes the specic conguration attributes that must be migrated from
the old instance to the new instance.
Migration of Specic Conguration Attributes
The values of the following attribute types must be migrated.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200738
.
Sun Condential: Registered
“Using dsmig to Migrate
Page 39

Migrating Conguration Data Manually
Global Conguration Attributes
The implementation of global scope ACIs requires all ACIs specic to the rootDSE to have a
targetscope eld, with a value of base (targetscope=”base”). ACIs held in the rootDSE are
specic to each Directory Server instance and are not replicated. Therefore there should be no
incompatibility problems when running a Directory Server 6.0 server in a topology containing
servers of previous versions. For more information about the changes made with regard to ACI
scope, see
In addition to the ACI change, the following attributes under cn=config must be migrated:
nsslapd-accesscontrol
nsslapd-accesslog-level
nsslapd-accesslog-logbuffering
nsslapd-accesslog-logexpirationtime
nsslapd-accesslog-logexpirationtimeunit
nsslapd-accesslog-logging-enabled
nsslapd-accesslog-logmaxdiskspace
nsslapd-accesslog-logminfreediskspace
nsslapd-accesslog-logrotationtime
nsslapd-accesslog-logrotattiontimeunit
nsslapd-accesslog-maxlogsize
nsslapd-accesslog-maxlogsperdir
nsslapd-attribute-name-exceptions
nsslapd-auditlog-logexpirationtime
nsslapd-auditlog-logexpirationtimeunit
nsslapd-auditlog-logging-enabled
nsslapd-auditlog-logmaxdiskspace
nsslapd-auditlog-logminfreediskspace
nsslapd-auditlog-logrotationtime
nsslapd-auditlog-logrotattiontimeunit
nsslapd-auditlog-maxlogsize
nsslapd-auditlog-maxlogsperdir
nsslapd-certmap-basedn
nsslapd-ds4-compatible-schema
nsslapd-enquote-sup-oc
nsslapd-errorlog-level
nsslapd-errorlog-logexpirationtime
nsslapd-errorlog-logexpirationtimeunit
nsslapd-errorlog-logging-enabled
nsslapd-errorlog-logmaxdiskspace
nsslapd-errorlog-logminfreediskspace
nsslapd-errorlog-logrotationtime
nsslapd-errorlog-logrotattiontimeunit
nsslapd-errorlog-maxlogsize
nsslapd-errorlog-maxlogsperdir
nsslapd-groupevalnestlevel
nsslapd-idletimeout
“Changes to ACIs” on page 70.
Chapter 3 • Migrating Directory Server Manually 39
Sun Condential: Registered
Page 40

Migrating Conguration Data Manually
nsslapd-infolog-area
nsslapd-infolog-level
nsslapd-ioblocktimeout
nsslapd-lastmod
nsslapd-listenhost
nsslapd-maxbersize
nsslapd-maxconnections
nsslapd-maxdescriptors
nsslapd-maxpsearch
nsslapd-maxthreadsperconn
nsslapd-nagle
nsslapd-readonly
nsslapd-referral
nsslapd-referralmode
nsslapd-reservedescriptors
nsslapd-return-exact-case
nsslapd-rootpwstoragescheme
nsslapd-schema-repl-useronly
nsslapd-schemacheck
nsslapd-search-tune
nsslapd-securelistenhost
nsslapd-security
nsslapd-sizelimit
nsslapd-threadnumber
nsslapd-timelimit
ds-start-tls-enabled
Security Conguration Attributes
All attributes under "cn=encryption,cn=config" must be migrated.
If you are using certicate authentication or the secure port, the key le path and certicate
database le path under "cn=encryption,cn=config" must be updated. The values of the
following attributes must be migrated:
nsKeyfile
nsCertfile
FeatureCongurationAttributes
The values of the aci attributes under "cn=features,cn=config" must be migrated.
In addition, the values of all identity mapping attributes must be migrated.
Mapping Tree Conguration Attributes
All entries under "cn=mapping tree,cn=config" must be migrated.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200740
Sun Condential: Registered
Page 41

Migrating Conguration Data Manually
The Netscape Root database has been deprecated in Directory Server 6.0. If your old instance
made specic use of the Netscape Root database, the attributes under o=netscaperoot must be
migrated. Otherwise, they can be ignored.
Replication Conguration Attributes
Before migrating replication conguration attributes, ensure that there are no pending changes
to be replicated. You can use the insync command to do this.
In addition to the conguration attributes, all entries under cn=replication,cn=config must
be migrated. You must manually update the host and port on all replication agreements to the
new instance, as well as the path to the change log database (nsslapd-changelogdir).
The following sections list the replication conguration attributes that must be migrated:
Change Log Attributes
TABLE 3–1 Change Log AttributeName Changes
Old Attribute Name Directory Server 6.0 Attribute Name
nsslapd-changelogmaxage dschangelogmaxage
nsslapd-changelogmaxentries dschangelogmaxentries
In addition, these attributes must be moved from cn=changelog5,cn=config to
cn=replica,cn=suffixname,cn=mapping tree,cn=config entries (for each sux name).
Fractional Replication Conguration Attributes
If your topology uses fractional replication, the following attribute names must be changed.
TABLE 3–2 Fractional Replication Attribute Name Changes
Old Attribute Name Directory Server 6.0Attribute Name
dsFilterSPType == fractional_include dsReplFractionalInclude
dsFilterSPType == fractional_exclude dsReplFractionalExclude
Replica Conguration Attributes
The values of the following replica conguration attributes must be migrated:
ds5ReferralDelayAfterInit
nsDS5Flags
nsDS5ReplicaBindDN
Chapter 3 • Migrating Directory Server Manually 41
Sun Condential: Registered
Page 42

Migrating Conguration Data Manually
nsDS5ReplicaId
nsDS5ReplicaLegacyConsumer
nsDS5ReplicaName
nsDS5ReplicaPurgeDelay
nsDS5ReplicaReferral
nsDS5ReplicaRoot
nsDS5ReplicaTombstonePurgeInterval
aci
The dschangelogmaxage and dschangelogmaaxentries attributes are added to the replica
entry.
Replication Agreement Conguration
The values of the following attributes must be migrated for each replication agreement:
description
ds5agreementEnable
ds5ReplicaTransportCompressionLevel
ds5ReplicaTransportGroupSize
ds5ReplicaTransportWindowSize
nsDS5ReplicaBindDN
nsDS5ReplicaBindMethod
nsDS5ReplicaCredentials
nsDS5ReplicaHost
nsDS5ReplicaPort
nsDS5ReplicaRoot
nsDS5ReplicaTimeout
nsDS5ReplicaTransportInfo
nsDS5ReplicaUpdateSchedule
aci
Issues can arise when you migrate the nsDS5ReplicaCredentials attribute. For more
information, see
“Manual Reset of Replication Credentials” on page 53.
There is no ds5PartialReplConfiguration attribute in Directory Server 6.0. This attribute
must be removed.
If you are using fractional replication, the dsReplFractionalInclude and
dsReplFractionalExclude attributes are added for each replication agreement.
All attributes under "cn=replication,cn=config" are migrated.
PasswordPolicy Conguration Attributes
Directory Server 6.0 implements a new password policy. For details on conguration of the new
password policy, see Chapter 7, “Directory Server Password Policy,” in Sun Java System
Directory Server Enterprise Edition 6.0 Administration Guide. The attributes that dene the
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200742
Sun Condential: Registered
Page 43

Migrating Conguration Data Manually
password policy are stored in the entry cn=Password Policy,cn=config. Note that in
Directory Server 5.1, password policy attributes were located directly under cn=config.
Directory Server 6.0 introduces the new pwdPolicy object class. The attributes of this object
class replace the old password policy attributes. For a description of these new attributes see the
pwdPolicy(5dsoc) man page.
By default, the new password policy is backward compatible with the old password policy.
However, because backward compatibility is not guaranteed indenitely, you should migrate to
the new password policy as soon as is convenient for your deployment. For information about
password policy compatibility, see
“Password Policy Compatibility” on page 75.
The following table provides a mapping of the new password policy attributes whose values
must be migrated from the legacy attributes.
TABLE 3–3 Mapping Between 5 and 6.0 Password Policy Attributes
Legacy Directory Server Attribute Directory Server 6.0 Attribute
- (password policy is applied to the userPassword
attribute only.)
passwordMinAge pwdMinAge
passwordMaxAge pwdMaxAge
passwordInHistory pwdInHistory
passwordSyntax pwdCheckQuality
passwordMinLength pwdMinLength
passwordWarning pwdExpireWarning
- pwdGraceLoginLimit
passwordMustChange pwdMustChange
passwordChange pwdAllowUserChange
- pwdSafeModify
passwordExp -
passwordStorageScheme -
passwordExpireWithoutWarning -
passwordLockout pwdLockout
passwordLockoutDuration pwdLockoutDuration
pwdAttribute
passwordMaxFailure pwdMaxFailure
Chapter 3 • Migrating Directory Server Manually 43
Sun Condential: Registered
Page 44

Migrating Conguration Data Manually
TABLE 3–3 Mapping Between 5 and 6.0 Password Policy Attributes (Continued)
Legacy Directory Server Attribute Directory Server 6.0 Attribute
passwordResetFailureCount pwdFailureCountInterval
passwordUnlock -
SNMP Attributes
The entry cn=SNMP,cn=config does not exist in Directory Server 6.0. All attributes under this
entry are therefore deprecated. For information about setting up SNMP in Directory Server 6.0,
see “Setting Up SNMP for Directory Server” in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide.
UniqueID Generator Conguration Attributes
The nsState attribute under cn=uniqueid generator,cn=config must be migrated.
Database Conguration Attributes
General database conguration attributes are stored under cn=config,cn=ldbm
database,cn=plugins,cn=config. The following attributes must be migrated:
nsslapd-lookthroughlimit
nsslapd-allidsthreshold
nsslapd-cache-autosize
nsslapd-cache-autosize-split
nsslapd-cachesize
nsslapd-db-checkpoint-interval
nsslapd-db-circular-logging
nsslapd-db-durable-transactions
nsslapd-db-idl-divisor
nsslapd-db-locks
nsslapd-db-logbuf-size
nsslapd-db-logfile-size
nsslapd-db-page-size
nsslapd-db-transaction-batch-val
nsslapd-db-tx-max
nsslapd-dbncache
nsslapd-import-cachesize
nsslapd-exclude-from-export
nsslapd-disk-low-threshold
nsslapd-disk-full-threshold
Database-specic attributes are stored in entries of the form cn=database instance
name,cn=ldbm database,cn=plugins,cn=config. The following attributes must be migrated:
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200744
Sun Condential: Registered
Page 45

Migrating Conguration Data Manually
nsslapd-suffix
nsslapd-cachesize
nsslapd-cachememsize
nsslapd-readonly
nsslapd-require-index
If your deployment uses the NetscapeRoot sux, you must migrate the attributes under
cn=netscapeRoot,cn=ldbm database,cn=plugins,cn=config. You must also replace the
database location (nsslapd-directory) with the location of the new Directory Server 6
instance.
All default index conguration attributes must be migrated, except for system indexes. Default
index conguration attributes are stored in the entry cn=default indexes,cn=ldbm
database,cn=plugins,cn=config. Indexes for the NetscapeRoot database do not need to be
migrated.
All index conguration attributes must be migrated, except for system indexes. Index
conguration attributes are stored in entries of the sort cn=index name, cn=index,
cn=database instance name, cn=ldbm database, cn=plugins, cn=config.
All attribute encryption conguration attributes must be migrated.
Chained Sux Attributes
All chained sux conguration attributes must be migrated. The following conguration
attributes are common to all chained suxes. These attributes are stored in the entry
cn=config,cn=chaining database,cn=plugins,cn=config.
nsActivechainingComponents
nsTransmittedControls
The following conguration attributes apply to a default instance of a chained sux. These
attributes are stored in the entry cn=default instance config, cn=chaining
database,cn=plugins,cn=config.
nsAbandonedSearchCheckInterval
nsBindConnectionsLimit
nsBindRetryLimit
nsBindTimeout
nsCheckLocalACI
nsConcurrentBindLimit
nsConcurrentOperationsLimit
nsConnectionLife
nsHopLimit
nsmaxresponsedelay
nsmaxtestresponsedelay
nsOperationConnectionslimit
Chapter 3 • Migrating Directory Server Manually 45
Sun Condential: Registered
Page 46

Migrating Conguration Data Manually
nsProxiedAuthorization
nsReferralOnScopedSearch
nsslapd-sizelimit
nsslapd-timelimit
Plug-In Conguration Attributes
If you have changed the conguration of any standard plug-in, you must update that
conguration. You must also update the conguration of all custom plug-ins. At a minimum,
you must recompile all custom plug-ins and add their conguration to the directory. For a
detailed list of plug-in API changes, see Chapter 2, “Changes to the Plug-In API Since Directory
Server 5.2,” in Sun Java System Directory Server Enterprise Edition 6.0 Developer’s Guide.
The following sections describe the standard plug-ins whose conguration must be migrated if
you have changed it.
7–Bit Check Plug-In
The conguration of this plug-in is stored under cn=7-bit check,cn=plugins,cn=config.
The following attributes must be migrated:
nsslapd-pluginarg*
nsslapd-pluginenabled
Class of Service Plug-In
The conguration of this plug-in is stored under cn=Class of
Service,cn=plugins,cn=config. The following attributes must be migrated:
nsslapd-pluginarg0
nsslapd-pluginenabled
DSML Frontend Plug-In
The conguration of this plug-in is stored under
cn=DSMLv2-SOAP-HTTP,cn=frontends,cn=plugins,cn=config. The following attributes must
be migrated:
ds-hdsml-port
ds-hdsml-iobuffersize
ds-hdsml-requestmaxsize
ds-hdsml-responsemsgsize
ds-hdsml-poolsize
ds-hdsml-poolmaxsize
ds-hdsml-clientauthmethod
ds-hdsml-rooturl
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200746
Sun Condential: Registered
Page 47

Migrating Conguration Data Manually
ds-hdsml-soapschemalocation
ds-hdsml-dsmlschemalocation
nsslapd-pluginenabled
PassThrough Authentication Plug-In
The conguration of this plug-in is stored under cn=Pass Through
Authentication,cn=plugins,cn=config. The following attribute must be migrated:
nsslapd-pluginenabled
The nsslapd-pluginarg* attributes must be migrated only if you require the conguration for
o=netscapeRoot to be migrated.
PasswordSynchronization Plug-In
The conguration of this plug-in is stored under cn=pswsync,cn=plugins,cn=config. The
following attribute must migrated:
nsslapd-pluginenabled
Referential Integrity Plug-In
The conguration of this plug-in is stored under cn=Referential Integrity
Postoperation,cn=plugins,cn=config. The following attributes must be migrated:
nsslapd-pluginarg*
nsslapd-pluginenabled
Retro Change Log Plug-In
The conguration of this plug-in is stored under cn=Retro Changelog
PlugIn,cn=plugins,cn=config. The following attributes must be migrated:
nsslapd-changelogmaxage
nsslapd-changelogmaxentries
nsslapd-pluginarg*
nsslapd-pluginenabled
UID Uniqueness Plug-In
The conguration of this plug-in is stored under cn=UID Uniqueness,cn=plugins,cn=config.
The following attributes must be migrated:
nsslapd-pluginarg*
nsslapd-pluginenabled
Chapter 3 • Migrating Directory Server Manually 47
Sun Condential: Registered
Page 48

Migrating Security Settings Manually
Migrating Security Settings Manually
When you migrate an instance manually, the order in which you perform the migration of the
security and the migration of the conguration is dierent to when you migrate using dsmig.If
you migrate the security settings by replacing the default Directory Server 6.0 certicate and key
databases wit the old databases, as described in this section, you must migrate the conguration
rst.
To migrate the security settings manually, perform the following steps:
1. If you have already started using the new instance, stop the instance.
2. Back up the certicate database and key database les on the new instance.
3. Copy the certicate database and key database les from the existing instance to the new
instance.
$cpserverRoot/alias/slapd-serverID-cert8.db instance-path/alias/slapd-cert8db
$cpserverRoot/alias/slapd-serverID-key3.db instance-path/alias/slapd-key3.db
For 5.1 servers and earlier releases of 5.2 servers, the certicate database to be copied is
serverRoot/alias/slapd-serverID-cert7.db.
4. Copy the password le from the existing instance to the new instance.
$cpserverRoot/alias/slapd-serverID-pin.txt instance-path/alias/slapd-pin.txt
5. Update the certicate database password.
$ dsadm set-flags instance-path cert-pwd-prompt=on
6. Copy the certicate mapping le from the existing instance to the new instance.
$cpserverRoot/shared/config/certmap.conf instance-path/alias/certmap.conf
7. If the existing instance uses an external security token, copy the security module database
and the external token library to the new instance.
$cpserverRoot/alias/secmod.db instance-path/alias/secmod.db
8. Start the new instance.
The security conguration attributes are migrated when you migrate the rest of the
conguration attributes. In this sense, migration of the security settings is not complete until
you have migrated the conguration. Migration of the conguration is described in the
following section.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200748
Sun Condential: Registered
Page 49

Migrating User Data Manually
If your topology does not support automatic data migration, you must migrate the data
manually. This involves exporting the data from the existing instance and re-importing it to the
new instance.
To migrate data manually from an existing version 5 instance, perform the following steps:
1. If you already have data in the new instance, back up any conicting suxes in the new
instance.
2. If you are migrating a master server instance in a replicated topology, make sure that the
master is synchronized with all servers that are direct consumers of that master.
It is not possible to migrate the change log manually. A new change log is created in the 6.0
instance.
3. Export the required suxes to LDIF by using the db2ldif command. This command
exports all the sux contents to an LDIF le, when the server is either running or stopped.
The following example exports two suxes to a single LDIF le.
$ serverRoot/slapd-serverID/db2ldif -a example.ldif \
-r -s "ou=people,dc=example,dc=com" -s "ou=departments,dc=example,dc=com"
Migrating User Data Manually
In this example, -a species the resulting LDIF le, -r indicates that replication information
should be exported, and -s species the suxes to be included in the export.
4. On the new instance, import the LDIF les by using the dsadm import command. For
example, the following commands import the LDIF le created previously into the two
suxes that were exported.
$ dsadm import instance-path example.ldif ou=people,dc=example,dc=com
$ dsadm import instance-path example.ldif ou=departments,dc=example,dc=com
5. If the retro change log was congured on the 5.2 instance, export the retro change log to
LDIF by using the db2ldif command.
$ serverRoot/slapd-serverID/db2ldif -a changelog.ldif \
-s "cn=changelog"
In this example, -a species the resulting LDIF le, and -s species the changelog sux.
6. On the new instance, import the retro change log using the dsadm import command. For
example, the following command imports the change log LDIF le created previously.
$ dsadm import instance-path changelog.ldif cn=changelog
7. Start the new instance.
Chapter 3 • Migrating Directory Server Manually 49
Sun Condential: Registered
Page 50

Migrating User Plug-Ins Manually
Note – During data migration, Directory Server checks whether nested group denitions exceed
30 levels. Deep nesting can signify a circular group denition, where a nested group contains a
group that is also its parent. When a group with more than 30 nesting levels is encountered,
Directory Server stops calculating the isMemberOf attributes for additional levels.
Each time this happens, Directory Server logs an error. You safely ignore these errors, although
you should examine the denition of the group mentioned in the error message for potential
circular denitions.
Migrating User Plug-Ins Manually
User plug-ins cannot be migrated. If you have custom user plug-ins, recompile them and add
them to the Directory Server 6.0 instance manually. For a detailed list of plug-in API changes,
see Chapter 2, “Changes to the Plug-In API Since Directory Server 5.2,” in Sun Java System
Directory Server Enterprise Edition 6.0 Developer’s Guide.
Tasks to be Performed After Manual Migration
If you have migrated your server manually, the following post-migration tasks are required
before you can run the new server.
■
If you have customized user plug-ins, these need to be recompiled and added to the new
server manually.
■
If the migrated server was part of a replicated topology, see Chapter 4.
■
If you have customized backup, recovery, and installation scripts, you need to rewrite these
scripts to comply with the new version.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200750
Sun Condential: Registered
Page 51

CHAPTER 4
4
Migrating a Replicated Topology
Directory Server Enterprise Edition 6.0 does not provide a way to migrate an entire replicated
topology automatically. Migrating a replicated topology involves migrating each server
individually. Usually, however, you should be able to migrate your entire topology without any
interruption in service.
This chapter describes the issues involved in migrating replicated servers, and covers the
following topics:
■
“Overview of Migrating Replicated Servers” on page 51
■
“Issues Related to Migrating Replicated Servers” on page 52
■
“New Replication Recommendations” on page 53
■
“Migration Scenarios” on page 54
Overview of Migrating Replicated Servers
Directory Server 6.0 supports an unlimited number of masters in a multi-master topology. This
and other changes might mean that you redesign your topology rather than migrate to an
identical topology with new servers. See Part III, “Logical Design,” in Sun Java System Directory
Server Enterprise Edition 6.0 Deployment Planning Guide before continuing.
When migrating replicated version 5 servers, you typically start with the consumers, continue
with the hubs, and nish with the masters. This bottom-up approach involves interrupting only
one server at a time, rather than interrupting an entire branch of the replication topology. The
approach also helps you avoid potential custom schema synchronization issues between
masters and consumers.
Sun Condential: Registered
51
Page 52

Issues Related to Migrating Replicated Servers
Issues Related to Migrating Replicated Servers
Depending on your replication topology, and on your migration strategy, certain issues might
arise when you migrate replicated servers. These issues are described in the following sections.
Issues With the New Password Policy
If you are migrating a multi-master replicated topology, a situation will arise where a 6.0 master
is replicating to a version 5 server. In this situation, an object class violation will occur if changes
are made to the new password policy attributes on the 6.0 server, and replicated to the version 5
server. The password policy attributes are managed internally by the server but they might be
updated in the event of a bind, a user password modify, or the addition of an entry with the
userpassword attribute.
To avoid the object class violation, the 6.0 password policy schema le (00ds6pwp.ldif) must
be copied to every version 5 server that will be supplied by a 6.0 master. When the password
policy schema le has been copied, restart the version 5 server.
Migration of Replication Agreements
If possible, you should migrate replicated servers to the same host name and port number. If
you must change the host name or port number of a replicated server, all replication agreements
that point to that server must be updated manually to point to the new server. For example, if
you migrate a consumer server from red.example.com:1389 to blue.example.com:1389, the
replication agreements on all masters that point to red.example.com:1389 must be updated
manually to point to blue.example.com:1389.
Replication agreements from the migrated master to consumers in the topology are managed by
the dsmig migration tool. If your topology does not support automated migration, these
replication agreements must also be updated manually.
Migration of Referrals
Referrals are also aected if you migrate a master replica to a new host or port. The details of
each master in a topology are present in the Replica Update Vector (RUV) of all other servers in
the topology. The RUV of each server is used to determine the referrals. When you change the
host name or port number of a master server during migration, all referrals to that master from
other servers in the topology become invalid. The easiest way to correct this is to use the
following steps, in order, when performing the migration.
1. Before migrating a master server, verify that there are no pending changes to be replicated.
You can use the insync tool to do this.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200752
Sun Condential: Registered
Page 53

New Replication Recommendations
2. Demote the master server to a hub, as described in “Promoting or Demoting Replicas” in
Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide.
3. Migrate the hub server, either using dsmig or the manual migration progress.
4. Promote the hub server to a master, as described in “Promoting or Demoting Replicas” in
Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide. When you
promote the hub, you must assign a replicaID to the new migrated master. This new
replicaID must be dierent to the replicaID of the old server that is being migrated, and
must be unique within the replicated topology.
Manual Reset of Replication Credentials
dsmig does not migrate the password of the default replication manager entry (cn=replication
manager,cn=replication,cn=config). Instead, the replication manager password is deleted.
Therefore, whether you are using manual or automatic migration, you must reset the
replication manager password manually.
To reset the replication manager password, use the following command:
$ dsconf set-server-prop -h host -p port def-repl-manager-pwd-file:lename
In addition, dsmig does not migrate non-default replication manager entries. If a version 5
replica uses an entry other than the default replication manager, and if this entry is under
cn=config, you must add the default replication manager manually. Please refer to the
documentation to add a non-default replication manager entry manually. For information
about adding a non-default replication manager, see “Using a Non-Default Replication
Manager” in Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide.
Problems Related to Tombstone Purging
In some cases, after migrating a replicated topology you might experience problems related to
tombstone purging. In some cases, tombstone entries are not purged when they should be. This
problem can be resolved by re-indexing the objectclass attribute of the corresponding sux.
New Replication Recommendations
Directory Server 6.0 does not limit the number of masters in a multi-master topology. A
fully-meshed, multi-master topology with no hubs or consumers is recommended in most
cases.
Chapter 4 • Migrating a Replicated Topology 53
Sun Condential: Registered
Page 54

Migration Scenarios
Advantages of an all-master topology include the following:
■
Availability. Write trac is never disrupted if one of the servers goes down.
■
Simplicity. In an all-master topology, there is no need to set up referrals to route reads and
writes to dierent servers.
There may be reasons that an all-master topology is not viable in a specic deployment. For
example, fractional replication cannot be used in an all-master topology because fractional
replication is only supported from masters to consumers.
Migration Scenarios
This section provides sample migration scenarios for a variety of replicated topologies.
Migrating a ReplicatedTopology to an Identical Topology
Before you start migrating replicated servers, determine whether your deployment might not be
better served by changing the architecture of the topology. This section describes how to
migrate if you want to keep your existing topology. Migrating a replicated topology to an
identical topology, involves migrating the consumers, then the hubs, then the masters. The
following sections demonstrate a sample migration of a simple multi-master topology.
Migrating the Consumers
For each consumer in the replicated topology:
1. Reroute clients to another consumer in the topology.
2. Disable any replication agreements to the consumer you want to migrate.
3. Stop the consumer.
4. Migrate the consumer according to the instructions under
5. Start the consumer.
6. Enable the replication agreements from the hubs to that consumer.
7. If you have migrated the data, check that replication is in sync.
8. If you have not migrated the data, reinitialize the consumer.
9. Reroute clients back to the consumer.
The following sequence of diagrams illustrate the migration of a consumer, as described above.
The rst diagram shows the version 5 topology before the migration.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200754
Sun Condential: Registered
Chapter 1.
Page 55

Migration Scenarios
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
5.x Consumer A 5.x Consumer B
FIGURE 4–1 Existing version 5 Topology
The rst step involves rerouting clients and disabling replication agreements, eectively
isolating the consumer from the topology.
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
5.x Consumer A 5.x Consumer B
FIGURE 4–2 Isolating the Consumer From the Topology
Chapter 4 • Migrating a Replicated Topology 55
Sun Condential: Registered
Page 56

Migration Scenarios
The next step involves migrating the version 5 consumer.
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
5.x Consumer A 5.x Consumer B6.0 Consumer A
FIGURE 4–3 Migrating the version 5 Consumer
The next step involves enabling the replication agreements to the new consumer, initializing the
consumer if necessary, and rerouting client applications to the new consumer.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200756
Sun Condential: Registered
Page 57

5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
5.x Consumer B6.0 Consumer A
FIGURE 4–4 Placing the 6.0 Consumer Into the Topology
Migrating the Hubs
Migration Scenarios
For each hub in the replicated topology:
1. Disable replication agreements from the masters to the hub you want to migrate.
2. Disable replication agreements from the hub you want to migrate to the consumers.
3. Stop the hub.
4. Migrate the hub according to the instructions under
Chapter 1.
5. Start the hub.
6. Enable the replication agreements from the masters to that hub.
7. Enable the replication agreements from that hub to the consumers.
8. If you have migrated the data, check that replication is in sync.
9. If you have not migrated the data, reinitialize the hub.
The following sequence of diagrams illustrate the migration of a hub, as described above. The
rst diagram shows the topology before migrating the hubs.
Chapter 4 • Migrating a Replicated Topology 57
Sun Condential: Registered
Page 58

Migration Scenarios
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–5 Existing version 5 Topology With Migrated Consumers
The rst migration step involves disabling replication agreements, eectively isolating the hub
from the topology.
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–6 Isolating the HubFrom the Topology
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200758
Sun Condential: Registered
Page 59

The next step involves migrating the version 5 hub.
5.x Master A 5.x Master B
Migration Scenarios
6.0 Hub A
FIGURE 4–7 Migrating the version 5 Hub
5.x Hub A 5.x Hub B
6.0 Consumer A
6.0 Consumer B
The next step involves enabling the replication agreements to the new hub and initializing the
hub if necessary.
Chapter 4 • Migrating a Replicated Topology 59
Sun Condential: Registered
Page 60

Migration Scenarios
5.x Master A 5.x Master B
6.0 Hub A
6.0 Consumer A 6.0 Consumer B
FIGURE 4–8 Placing the 6.0 Hub Into the Topology
5.x Hub B
Check that the replication on the consumers is in sync with the rest of the topology before
migrating another hub. A server that has just been migrated does not have a change log, and can
therefore not update consumer servers that are out of sync. Allow the topology to stabilize and
all servers to synchronize before migrating the next supplier server.
Migrating the Masters
For each master in the replicated topology:
1. If you have client applications that write to the master you want to migrate, reroute these
applications to write to another master in the topology.
2. Ensure that the master is no longer receiving write requests. You can do this by enabling
read-only mode on the master.
3. Check that replication is synchronized between the master and all its consumers.
Migration of the change log is not supported if you are migrating manually, so the preceding
two steps are mandatory in this case. Although automatic migration does migrate the
change log, you should still perform the above steps to avoid the risk of losing changes.
4. Disable any replication agreements to and from the master you want to migrate.
5. Stop the master.
6. Migrate the master according to the instructions under
Chapter 1.
7. Start the master.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200760
Sun Condential: Registered
Page 61

Migration Scenarios
8. Enable the replication agreements from the master to the hubs and other masters in the
topology.
9. If you have migrated the data, check that replication is in sync.
10. If you have not migrated the data, reinitialize the master from another master in the
topology.
11. If you rerouted client applications (Step 2), you can now route the applications to write to
the migrated master.
The following sequence of diagrams illustrate the migration of a master, as described above.
The rst diagram shows the version 5 topology before the migration of the masters.
5.x Master A 5.x Master B
6.0 Hub A 6.0 Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–9 Existing version 5 Topology With Consumers and HubsMigrated
The rst step in migrating a master involves disabling replication agreements, eectively
isolating the master from the topology.
Chapter 4 • Migrating a Replicated Topology 61
Sun Condential: Registered
Page 62

Migration Scenarios
5.x Master A 5.x Master B
6.0 Hub A 6.0 Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–10 Isolating the Master From the Topology
The next step involves migrating the version 5 master.
6.0 Master A
5.x Master A 5.x Master B
6.0 Hub A
6.0 Consumer A 6.0 Consumer B
FIGURE 4–11 Migrating the version 5 Master
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200762
Sun Condential: Registered
6.0 Hub B
Page 63

Migration Scenarios
The next step involves enabling the replication agreements to and from the new master and
initializing the master if necessary.
6.0 Master A
6.0 Hub A 6.0 Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–12 Placing the 6.0 Master Into the Topology
5.x Master B
Check that the replication on all hubs and consumers is in sync with the rest of the topology
before migrating another master. A server that has just been migrated does not have a change
log, and can therefore not update servers that are out of sync. Allow the topology to stabilize and
all servers to synchronize before migrating the next supplier server.
Migrating a ReplicatedTopology to a NewTopology
Before you start migrating replicated servers, determine whether your deployment might not be
better served by changing the architecture of the topology. This section describes how to
migrate a basic version 5 topology to a new all-master topology. Migrating to an all-master
topology involves migrating the consumers, hubs, and masters, then promoting the hubs to
masters and the consumers to hubs, then to masters. The following sections demonstrate a
sample migration of a simple multi-master topology to a new all-master topology.
The following gure shows the existing version 5 topology.
Chapter 4 • Migrating a Replicated Topology 63
Sun Condential: Registered
Page 64

Migration Scenarios
5.x Master A 5.x Master B
5.x Hub A 5.x Hub B
5.x Consumer A 5.x Consumer B
FIGURE 4–13 Existing version 5 Topology
Migrating All the Servers
The rst step is to migrate all the servers individually, as described in “Migrating a Replicated
Topology to an Identical Topology” on page 54
. The resulting topology is illustrated in the
following gure.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200764
Sun Condential: Registered
Page 65

6.0 Master A 6.0 Master B
6.0 Hub A 6.0 Hub B
6.0 Consumer A 6.0 Consumer B
FIGURE 4–14 Existing Topology With Migrated Servers
Promoting the Hubs
Migration Scenarios
The next step involves promoting the hubs to masters, and creating a fully-meshed topology
between the masters. To promote the hubs, follow the instructions in “Promoting or Demoting
Replicas” in Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide.
The following diagram illustrates the topology when the hubs have been promoted.
Chapter 4 • Migrating a Replicated Topology 65
Sun Condential: Registered
Page 66

Migration Scenarios
6.0 Master A 6.0 Master B
6.0 Master C 6.0 Master D
6.0 Consumer A 6.0 Consumer B
FIGURE 4–15 Migrated Topology With Promoted Hub Replicas
Promoting the Consumers
The next step involves promoting the consumers to hubs, and then to masters, and creating a
fully-meshed topology between the masters. To promote the consumers, follow the instructions
in “Promoting or Demoting Replicas” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
The following diagram illustrates the topology when the consumers have been promoted.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200766
Sun Condential: Registered
Page 67

6.0 Master A 6.0 Master B
6.0 Master C 6.0 Master D
6.0 Master E 6.0 Master F
FIGURE 4–16 New Fully-MeshedAll-Master Topology
Migration Scenarios
Migrating Over Multiple Data Centers
Migrating servers over multiple data centers involves migrating each server in each data center
individually. Before you start migrating replicated servers, determine whether your deployment
might not be better served by changing the architecture of the topology. If you want to keep
your existing topology, follow the examples in
Topology” on page 54
for each data center. To migrate to a new topology, follow the examples
in “Migrating a Replicated Topology to a New Topology” on page 63 for each data center.
Chapter 4 • Migrating a Replicated Topology 67
Sun Condential: Registered
“Migrating a Replicated Topology to an Identical
Page 68

68
Sun Condential: Registered
Page 69

CHAPTER 5
5
Architectural Changes in Directory Server 6.0
This chapter describes the architectural changes in Directory Server 6.0 that aect migration
from a previous version. For information on all changes and bug xes in Directory Server 6.0,
see “What’s New at a Glance” in Sun Java System Directory Server Enterprise Edition 6.0
Evaluation Guide.
This chapter covers the following topics:
■
“Changes in the Administration Framework” on page 69
■
“Changes to ACIs” on page 70
■
“Command Line Changes” on page 71
■
“Changes to the Console” on page 74
■
“New Password Policy” on page 74
■
“Changes to Plug-Ins” on page 77
■
“Changes to the Installed Product Layout” on page 78
Changes in the Administration Framework
Directory Server 6.0 does not include an administration server, as in previous versions. Servers
are now registered in the Directory Service Control Center (DSCC) and can be administered
remotely by using the web-based GUI or the command-line tools.
To migrate to the new administration framework, you need to do the following:
■
Upgrade each server individually
■
Register each server in the DSCC
Removal of the ServerRoot Directory
In the new administration model, a Directory Server instance is no longer tied to a ServerRoot.
Each Directory Server instance is a standalone directory that can be manipulated in the same
manner as an ordinary standalone directory.
Sun Condential: Registered
69
Page 70

Changes to ACIs
Removal of the o=netscapeRoot Sux
In previous versions of Directory Server, centralized administration information was kept in
o=netscapeRoot. In the new administration model, the concept of a conguration directory
server no longer exists. The o=netscapeRoot sux is no longer required, and the netscapeRoot
database les are therefore not migrated. The conguration data for this sux can be migrated,
if it is specically required.
Changes to ACIs
The following changes have been made to ACIs in Directory Server 6.0.
Changes in the ACI Scope
In Directory Server 5.2 ACIs on the root DSE had base scope. In Directory Server 6.0, ACIs on
the root DSE have global scope by default, equivalent to targetscope="subtree".
To reproduce the same behavior as Directory Server 5.2, add targetscope="base" to ACIs on
the root DSE. If you use dsmig to migrate the conguration, this is done automatically.
Changes in Sux-Level ACIs
In Directory Server 5.2, the following ACI was provided, at the sux level:
aci: (targetattr != "nsroledn || aci || nsLookThroughLimit ||
nsSizeLimit || nsTimeLimit || nsIdleTimeout || passwordPolicySubentry ||
passwordExpirationTime || passwordExpWarned || passwordRetryCount ||
retryCountResetTime || acc ountUnlockTime || passwordHistory ||
passwordAllowChangeTime")(version 3.0; acl "Allow self entry modification
except for nsroledn, aci, resource limit attributes, passwordPolicySubentry
and password policy state attributes"; allow (write)userdn ="ldap:///self";)
This ACI allowed self-modication of user passwords, among other things. This ACI is no
longer provided in Directory Server 6.0. Instead, the following global ACIs are provided by
default:
aci: (targetattr != "aci") (targetscope = "base") (version 3.0;
aci "Enable read access to rootdse for anonymous users";
allow(read,search,compare) user dn="ldap:///anyone"; )
aci: (targetattr = "*") (version 3.0; acl "Enable full access
for Administrators group"; allow (all)(groupdn =
"ldap:///cn=Administrators,cn=config"); )
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200770
Sun Condential: Registered
Page 71

Command Line Changes
aci: (targetattr = "userPassword") ( version 3.0; acl "allow
userpassword self modification"; allow (write) userdn = "ldap:///self";)
In Directory Server 6.0, the default userPassword ACI at root DSE level provides equivalent
access control to the default 5.2 ACI at sux level. However, if you want to reproduce exactly
the same access control as in 5.2, add the following ACI to your sux. This ACI is the 5.2 ACI,
with the new password policy operational attributes for Directory Server 6.0.
aci: (targetattr != "nsroledn || aci || nsLookThroughLimit ||
nsSizeLimit || nsTimeLimit || nsIdleTimeout || passwordPolicySubentry ||
passwordExpirationTime || passwordExpWarned || passwordRetryCount ||
retryCountResetTime || accountUnlockTime || passwordHistory ||
passwordAllowChangeTime || pwdAccountLockedTime || pwdChangedTime ||
pwdFailureTime || pwdGraceUseTime || pwdHistory ||
pwdLastAuthTime || pwdPolicySubentry || pwdReset")(version 3.0; acl "Allow self entry modification
except for nsroledn, aci, resource limit attributes, passwordPolicySubentry
and password policy state attributes"; allow (write)userdn ="ldap:///self";)
Tip – Do not allow users write access to everything and then deny write access to specic
attributes. Instead, explicitly list the attributes to which you allow write access.
Command Line Changes
In Directory Server 6.0 the functionality of most command-line tools is replaced by only two
commands: dsadm and dsconf.
The following table shows commands used in Directory Server 5, and the corresponding
commands for Directory Server 6.0. The default path of these commands when installed from
native packages is /opt/SUNWdsee/ds6/bin. When installed from the zip installation, the
default path is install-path/ds6/bin.
TABLE 5–1 Directory Server 5 and 6 commands
Version 5 Command Version 6.0 Command Description
bak2db dsadm restore Restore a database from backup (locally,
bak2db-task dsconf restore Restore a database from backup (remotely,
db2bak dsadm backup Create a database backup archive (locally,
Chapter 5 • Architectural Changes in Directory Server 6.0 71
oine)
online)
oine)
Sun Condential: Registered
Page 72

Command Line Changes
TABLE 5–1 Directory Server 5 and 6 commands (Continued)
Version 5 Command Version 6.0 Command Description
db2bak-task dsconf backup Create a database backup archive
(remotely, online)
db2index dsadm reindex Create and generate indexes (locally,
oine)
db2index-task dsconf reindex Create and generate indexes (remotely,
online)
db2ldif dsadm export Export database contents to LDIF (locally,
oine)
db2ldif-task dsconf export Export database contents to LDIF
(remotely, online)
entrycmp No change Compare the same entry in multiple
replicas
fildif No change Create a ltered version of an LDIF le
idsktune No change Check patches and veries system tuning
insync No change Indicate synchronization between multiple
replicas
ldif2db dsadm import Import database contents from LDIF
(locally, oine)
ldif2db-task dsconf import Import database contents from LDIF
(remotely, online)
ldif2ldap ldapmodify -B Import data from LDIF over LDAP
(remotely, online)
MigrateInstance5 dsmig / manual migration
Migrate data from a previous version
procedure
mmldif No change Combine multiple LDIF les
monitor ldapsearch on cn=monitor Retrieve performance monitoring
information
pwdhash No change Print the encrypted form of a password
repldisc No change Discover a replication topology
restart-slapd dsadm restart Restart a Directory Server instance
schema_push No change Update schema modication time stamps
start-slapd dsadm start Start a Directory Server instance
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200772
Sun Condential: Registered
Page 73

Command Line Changes
TABLE 5–1 Directory Server 5 and 6 commands (Continued)
Version 5 Command Version 6.0 Command Description
stop-slapd dsadm stop Stop a Directory Server instance
suffix2instance dsconf get-suffix-prop See the backend name for a sux
vlvindex dsadm reindex Create virtual list view indexes
TABLE 5–2 Directory Server 5 and 6 Commands (Subcommands of the directoryserver Command)
Version 5 Command Version 6.0 Command Description
directoryserver
accountstatus
directoryserver activate ns-activate Activate an entry or group of entries
directoryserver configure Installation procedure Install Directory Server
directoryserver inactivate ns-inactivate Inactivate an entry or group of entries
directoryserver
unconfigure
ns-accountstatus Establish account status
Uninstallation procedure UninstallDirectory Server
Deprecated Commands
Some version 5 commands have been deprecated in Directory Server 6.0. The following table
provides a list of these commands.
TABLE 5–3 Version 5 Commands That HaveBeen Deprecated
Command Description
getpwenc Print encrypted password
ns-ldapagt Starts a Directory Server SNMP subagent. For information about how to do this in
Directory Server 6.0, see “To Set Up SNMP” in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide
restore-config Restore Administration Server conguration
saveconfig Save Administration Server conguration
Chapter 5 • Architectural Changes in Directory Server 6.0 73
Sun Condential: Registered
Page 74

Changes to the Console
Changes to the Console
The downloaded, Java Swing-based console has been replaced by Directory Service Control
Center (DSCC). DSCC is a graphical interface that enables you to manage an entire directory
service by using a web browser. The DSCC requires no migration. Migrated Directory Server
instances can be registered in the DSCC. For more information about the DSCC see Chapter 1,
“Directory Server Overview,” in Sun Java System Directory Server Enterprise Edition 6.0
Reference.
New Password Policy
Directory Server6.0 implements a new password policy that uses the standard object class and
attributes described in the “Password Policy for LDAP Directories” Internet-Draft.
The new password policy provides the following new features:
■
A grace login limit, specied by the pwdGraceAuthNLimit attribute. This attribute species
the number of times an expired password can be used to authenticate. If it is not present or if
it is set to 0, authentication will fail.
■
Safe password modication, specied by the pwdSafeModify attribute. This attribute
species whether the existing password must be sent when changing a password. If the
attribute is not present, the existing password does not need to be sent.
In addition, the new password policy provides the following new controls:
■
LDAP_CONTROL_PWP_[REQUEST|RESPONSE]
■
LDAP_CONTROL_ACCOUNT_USABLE_[REQUEST|RESPONSE]
These controls enable LDAP clients to obtain account status information.
The LDAP_CONTROL_PWP control provides account status information on LDAP bind, search,
modify, add, delete, modDN, and compare operations.
The following information is available, using the OID 1.3.6.1.4.1.42.2.27.8.5.1 in the
search:
■
Period of time before the password expires
■
Number of grace login attempts remaining
■
The password has expired
■
The account is locked
■
The password must be changed after being reset
■
Password modications are allowed
■
The user must supply his/her old password
■
The password quality (syntax) is insucient
■
The password is too short
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200774
Sun Condential: Registered
Page 75

New Password Policy
■
The password is too young
■
The password already exists in history
The LDAP_CONTROL_PWP control indicates warning and error conditions. The control value is a
BER octet string, with the format {tii}, which has the following meaning:
■
t is a tag dening which warning is set, if any. The value of t can be one of the following:
LDAP_PWP_WARNING_RESP_NONE (0x00L)
LDAP_PWP_WARNING_RESP_EXP (0x01L)
LDAP_PWP_WARNING_RESP_GRACE (0x02L)
■
The rst i indicates warning information.
The warning depends on the value set for t as follows:
■
If t is set to LDAP_PWP_WARNING_RESP_NONE, the warning is -1.
■
If t is set to LDAP_PWP_WARNING_RESP_EX, the warning is the number of seconds before
expiration.
■
If t is set to LDAP_PWP_WARNING_RESP_GRACE, the warning is the number of remaining
grace logins.
■
The second i indicates error information. If t is set to LDAP_PWP_WARNING_RESP_NONE, the
error contains one of the following values:
pwp_resp_no_error (-1)
pwp_resp_expired_error (0)
pwp_resp_locked_error (1)
pwp_resp_need_change_error (2)
pwp_resp_mod_not_allowed_error (3)
pwp_resp_give_old_error (4)
pwp_resp_bad_qa_error (5)
pwp_resp_too_short_error (6)
pwp_resp_too_young_error (7)
pwp_resp_in_hist_error (8)
The LDAP_CONTROL_ACCOUNT_USABLE control provides account status information on LDAP
search operations only.
PasswordPolicy Compatibility
For migration purposes, the new password policy maintains compatibility with previous
Directory Server versions by identifying a compatibility mode. The compatibility mode
determines whether password policy attributes are handled as old attributes or new attributes,
where old refers to Directory Server 5 password policy attributes.
The compatibility mode can be read using dsconf command as follows:
Chapter 5 • Architectural Changes in Directory Server 6.0 75
Sun Condential: Registered
Page 76

New Password Policy
$ dsconf get-server-prop pwd-compat-mode
The pwd-compat-mode property can have one of the following values:
DS5-compatible-mode If you install a Directory Server instance as part of a replicated
topology that includes a version 5 server, the compatibility state
should be set to DS5-compatible-mode. In this state both old and
new password policy attributes are recognized. Only version 5
password policy attributes are replicated, but both sets of attributes
are stored in the database.
If you upgrade an existing standalone server to Directory Server 6.0,
the compatibility state is set to DS5-compatible-mode. The server
generates the new equivalent password policy attributes.
If you upgrade an existing server as part of a replicated topology
that includes Directory Server 5 servers, the compatibility state
should also set to DS5-compatible-mode. The server accepts both
old and new password policy attributes. Both sets of attributes are
stored in the database. Only version 5 attributes can be replicated
(using fractional replication).
DS6-migration-mode As part of your migration, you can set the compatibility state to
DS6-migration-mode. In this mode, all servers in the topology are
version 6 servers, but there may be some existing Directory Server 5
password policy attributes in the database.
DS6-mode If you install a standalone Directory Server instance, set
compatibility mode to DS6-mode. In this case, only new password
policy attributes are recognized.
A server in DS6-mode can never be a supplier to or consumer of a
Directory Server 5 server. When all servers have been migrated to
version 6.0, DS6-mode should be the only compatibility mode.
The compatibility mode is set using the dsconf command as follows:
$ dsconf pwd-compat new-mode
The new-mode action takes one of the following values:
to-DS6-migration-mode Change to DS6-migration-mode from DS5-compatible-mode.
Once the change is made, only DS6-migration-mode and
DS6-mode are available.
to-DS6-mode Change to DS6-mode from DS6-migration-mode.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200776
Sun Condential: Registered
Page 77

The server state can move only towards stricter compliance with the new password policy
specications. Compatibility with the old password policy will not be supported indenitely.
You should therefore migrate to the new password policy as soon as is feasible for your
deployment.
When you consider migrating to the new password policy, note that the pwdChangedTime
attribute did not exist in Directory Server 5.2. This attribute is required by the new password
policy. When the attribute is not present in the user entry, its value is calculated from the entry's
passwordExpirationTime attribute. However, writing the calculated pwdChangedTime attribute
to the user entry would have a large performance impact directly after migration, because the
rst bind for every entry would require a write to the directory.
The calculated pwdChangedTime is therefore not written to the user entry during the
DS5-compatible mode. You should leave your topology in DS5-compatible-mode until you
have been through an entire password expiration cycle (90 days, for example, depending on the
value of passwordMaxAge). In this way, the pwdChangedTime is added gradually across the
directory (at the password change of each user entry).
Changes to Plug-Ins
Changes to Plug-Ins
Once the change is made, only DS6-mode is available.
This section lists the new and deprecated plug-ins in Directory Server 6.0. The section also
describes what you need to do if you have custom plug-ins created with the old plug-in API.
New Plug-Ins in Directory Server 6.0
The following plug-ins have been added in Directory Server 6.0:
cn=example,cn=ldbm database,cn=plugins,cn=config
cn=gle,cn=plugins,cn=config
cn=MemberOf Plugin,cn=plugins,cn=config
cn=Monitoring Plugin,cn=plugins,cn=config
cn=ObjectDeletionMatch,cn=plugins,cn=config
cn=pswsync,cn=plugins,cn=config
cn=Replication Repair,cn=plugins,cn=config
cn=RMCE,cn=Password Storage Schemes,cn=plugins,cn=config
cn=Strong Password Check,cn=plugins,cn=config
For information about these plug-ins see the plugin(5dsconf) man page.
Chapter 5 • Architectural Changes in Directory Server 6.0 77
Sun Condential: Registered
Page 78

Changes to the Installed Product Layout
Plug-Ins Deprecated in Directory Server 6.0
The following plug-ins have been deprecated in Directory Server 6.0:
cn=aci,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=cn,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=encrypted attributes,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=entrydn,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=givenName,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=mail,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=mailHost,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=member,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=monitor,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=nsCalXItemId,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=nscpEntryDN,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=nsRoleDN,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=nsUniqueId,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=nswcalCALID,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=objectclass,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=owner,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=parentid,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=pipstatus,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=pipuid,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=seeAlso,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=sn,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=uid,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=uniquemember,cn=index,cn=userRoot,cn=ldbm database,cn=plugins,cn=config
cn=userRoot,cn=ldbm database,cn=plugins,cn=config
Changes to the Plug-In API
If you have developed your own custom plug-ins, you need to recompile these to work with
Directory Server 6.0. For a complete list of the changes made to the plug-in API, see Chapter 2,
“Changes to the Plug-In API Since Directory Server 5.2,” in Sun Java System Directory Server
Enterprise Edition 6.0 Developer’s Guide.
Changes to the Installed Product Layout
This section summarizes the changes to the installed product layout from Directory Server 5.2.
Several les and utilities have been deprecated since Directory Server 5.2, as described in the
following sections.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200778
Sun Condential: Registered
Page 79

Changes to the Installed Product Layout
Administration Utilities Previously Under ServerRoot
In Directory Server 6.0 the Administration Server is no longer used to manage server instances.
The following system administration utilities previously located under ServerRoot have
therefore been deprecated:
■
restart-admin
■
start-admin
■
startconsole
■
stop-admin
■
uninstall
Binaries Previously Under ServerRoot/bin
The following utilities under ServerRoot/bin have been deprecated:
■
ServerRoot/bin/admin/admconfig
■
ServerRoot/bin/https/bin/ns-httpd
■
ServerRoot/bin/https/bin/uxwdog
■
ServerRoot/bin/slapd/server/ns-ldapagt
On Solaris Sparc, the ns-slapd daemon is located in
install-path/ds6/bin/lib/sparcvSolaris-Version. On platforms other than Solaris Sparc, the
ns-slapd daemon is located in install-path/ds6/bin/lib.
Libraries and Plug-Ins Previously Under ServerRoot/lib
Product libraries and plug-ins in Directory Server 5.2 were located under ServerRoot/lib.In
Directory Server 6.0, on Solaris Sparc, these libraries and plug-ins are located in
install-path/ds6/lib/sparcvSolaris-Version. On platforms other than Solaris Sparc, they are
located directly under install-path/ds6/lib.
Online Help Previously Under ServerRoot/manual
Console online help les were previously located under ServerRoot/manual. The console online
help les for Directory Server 6.0 are located under opt/SUNWdsee/ds6/dccapp/html.
Chapter 5 • Architectural Changes in Directory Server 6.0 79
Sun Condential: Registered
Page 80

Changes to the Installed Product Layout
Plug-Ins Previously Under ServerRoot/plugins
The following tables describes the new location of sample server plug-ins, and header les for
plug-in development.
TABLE 5–4 Support for Plug-Ins
Directory Server 5.2 Plug-In Directory Directory Server 6.0 Plug-In Directory Remarks
ServerRoot/plugins/slapd/slapi/examplesinstall-path/ds6/examples Sample plug-ins
ServerRoot/plugins/slapd/slapi/include install-path/ds6/include Plug-in header les
SNMP support is no longer handled within Directory Server. SNMP monitoring is now
handled by the Java Enterprise System Management Framework (Java ES MF). All plug-ins and
binaries related to SNMP have therefore been deprecated within Directory Server.
These plug-ins include the following:
■
ServerRoot/plugins/snmp/magt/magt
■
ServerRoot/plugins/snmp/mibs/
■
ServerRoot/plugins/snmp/sagt/sagt
For information about enabling monitoring Java ES MF monitoring, see “Enabling Java ES MF
Monitoring” in Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide.
Utilities Previously Under ServerRoot/shared/bin
The following tables describes the new location of the administrative tools previously under
ServerRoot/shared/bin. Note that as a result of the change to the administrative framework,
some of these tools have been deprecated.
TABLE 5–5 Tools Previously Under ServerRoot/shared/bin
5.2 File 6.0 File Purpose
ServerRoot/shared/bin/admin_ip.pl Deprecated Change IP address
ServerRoot/shared/bin/entrycmp install-path/ds6/bin/entrycmp Compare entries for replication
ServerRoot/shared/bin/fildif install-path/ds6/bin/fildif Dump ltered LDIF
ServerRoot/shared/bin/insync install-path/ds6/bin/insync Check replication
synchronization
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200780
Sun Condential: Registered
Page 81

Changes to the Installed Product Layout
TABLE 5–5 Tools Previously Under ServerRoot/shared/bin (Continued)
5.2 File 6.0 File Purpose
ServerRoot/shared/bin/ldapcompare /usr/sfw/bin/ldapcompare Compare attribute value
In Directory Server 6.0 you must
install the SUN-LDAPCSDK-TOOLS
package to get this utility
ServerRoot/shared/bin/ldapdelete /usr/sfw/bin/ldapdelete Delete directory entry
In Directory Server 6.0 you must
install the SUN-LDAPCSDK-TOOLS
package to get this utility
ServerRoot/shared/bin/ldapmodify /usr/sfw/bin/ldapmodify Modify directory entry
In Directory Server 6.0 you must
install the SUN-LDAPCSDK-TOOLS
package to get this utility
ServerRoot/shared/bin/ldapsearch /usr/sfw/bin/ldapsearch Find directory entries
In Directory Server 6.0 you must
install the SUN-LDAPCSDK-TOOLS
package to get this utility
ServerRoot/shared/bin/modutil Deprecated Manage PKCS #11 modules
ServerRoot/shared/bin/uconv Deprecated Convert from ISO to UTF-8
ServerRoot/shared/bin/repldisc install-path/ds6/bin/repldisc Discover replication topology
Certicate and Key Files
The following table shows the new locations of the certicate and key les in Directory Server
6.0.
TABLE 5–6 Location of Certicate and Key Files
5.2 File 6.0 File Remarks
ServerRoot/shared/config/certmap.confinstance-path/alias/certmap.confConguration le for mapping certicates
to directory entries
ServerRoot/alias/cert8.db instance-path/alias/cert8.db Trusted certicate database le
ServerRoot/alias/key3.db instance-path/alias/key3.db Database le containing client keys
ServerRoot/alias/secmod.db instance-path/alias/secmod.dbDatabase le containing security modules
such as PKCS#11
Chapter 5 • Architectural Changes in Directory Server 6.0 81
Sun Condential: Registered
Page 82

Changes to the Installed Product Layout
Silent Installation and Uninstallation Templates
In Directory Server 5.2, the ServerRoot/setup5 directory contained sample templates for silent
installation and uninstallation. Silent installation and uninstallation are no longer needed for
Directory Server 6.0 and these les have therefore been deprecated.
Server Instance Scripts Previously Under
ServerRoot/slapd-ServerID
The command-line administration scripts previously under ServerRoot/slapd-ServerID have
been replaced in the new administration framework and deprecated. These commands and
their Directory Server 6.0 equivalents are described in
Server Instance Subdirectories
The following table describes the new locations for the conguration, log and backup data
previously located under ServerRoot/slapd-instance-name
TABLE 5–7 Instance-Specic Subdirectories
“Command Line Changes” on page 71.
Version 5 Directory Version 6 Directory Remarks
ServerRoot/slapd-ServerID/bak instance-path/bak Directory instance database
backup
ServerRoot/slapd-ServerID/confbak Deprecated Administration Server
conguration backup
ServerRoot/slapd-ServerID/conf_bk instance-path/conf_bk Directory instance conguration
backup
ServerRoot/slapd-ServerID/config instance-path/config Directory instance conguration
ServerRoot/slapd-ServerID/config/schemainstance-path/config/schema Directory instance schema
ServerRoot/slapd-ServerID/db instance-path/db Directory instance databases
ServerRoot/slapd-ServerID/ldif instance-path/ds6/bin/ldif Sample LDIF les
ServerRoot/slapd-ServerID/locks instance-path/locks Run time process locks
ServerRoot/slapd-ServerID/logs instance-path/logs Server instance log les
ServerRoot/slapd-ServerID/tmp instance-path/tmp Run time temporary les
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200782
Sun Condential: Registered
Page 83

CHAPTER 6
6
Migrating Directory Proxy Server
There is no automatic migration path to move from a previous version to Directory Proxy
Server 6.0. Directory Proxy Server 6.0 provides much more functionality than previous
versions. While a one to one mapping of conguration information is therefore not possible in
most instances, it is possible to congure Directory Proxy Server 6.0 to behave like a version 5
server for compatibility.
This chapter describes how the conguration properties in Directory Proxy Server 6.0 can be
used to simulate a version 5 conguration.
The chapter covers the following topics:
■
“Mapping the Global Conguration” on page 83
■
“Mapping the Connection Pool Conguration” on page 87
■
“Mapping the Groups Conguration” on page 88
■
“Mapping the Properties Conguration” on page 97
■
“Mapping the Events Conguration” on page 103
■
“Mapping the Actions Conguration” on page 104
■
“Conguring Directory Proxy Server 6.0 as a Simple Connection-Based Router” on page 104
Mapping the Global Conguration
Before you change the Directory Proxy Server 6.0 conguration, back up the conguration by
using the dpadm backup command. For more information, see dpadm(1M).
You can congure Directory Proxy Server 6.0 by using the Directory Service Control Center
(DSCC) or the dpconf command-line utility. For more information, see dpconf(1M).
Directory Proxy Server 6.0 conguration can be retrieved as a set of properties. For example,
information about the port is returned in the listen-port property. This section describes how
to map the version 5 global conguration attributes to the corresponding properties in
Directory Proxy Server 6.0, where applicable. Not all functionality can be mapped directly.
Sun Condential: Registered
83
Page 84

Mapping the Global Conguration
The global Directory Proxy Server 5 conguration is specied by two object classes:
■
ids-proxy-sch-LDAPProxy.Contains the name of the Directory Proxy Server server and
the DN of the global conguration object.
■
ids-proxy-sch-GlobalConguration. Contains various global conguration attributes.
Because of the way in which Directory Proxy Server 6.0 is congured, Directory Proxy Server
6.0 has no equivalent for the ids-proxy-sch-LDAPProxy object class or its attributes.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Config-Name=name,ou=global,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ids-proxy-con-Config-Name=user-dened-name,ou=system,ou=dar-config,o=netscaperoot.
The functionality of the ids-proxy-sch-GlobalConfiguration is provided as properties of
various elements in Directory Proxy Server 6.0. The following table maps the attributes of the
ids-proxy-sch-GlobalConfiguration object class to the corresponding properties in
Directory Proxy Server 6.0.
TABLE 6–1 Mapping of Version 5 Global Conguration Attributes to 6.0 Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-Config-Name No equivalent
Directory Proxy Server 6.0 has two listeners, a non-secure listener and a
secure listener. The version 5 listen conguration attributes can be mapped
to the following four listener properties. To congure listener properties,
use the dpconf command as follows:
$ dpconf set-ldap-listener-prop PROPERTY
$ dpconf set-ldaps-listener-prop PROPERTY
For more information, see “Conguring Listeners Between Clients and
Directory Proxy Server” in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide.
ids-proxy-con-listen-port listen-port
ids-proxy-con-listen-host listen-address
ids-proxy-con-listen-backlog max-connection-queue-size
ids-proxy-con-ldaps-port listen-port (property of the ldaps-listener)
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200784
Sun Condential: Registered
Page 85

Mapping the Global Conguration
TABLE 6–1 Mapping of Version 5 Global Conguration Attributesto 6.0 Properties (Continued)
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-max-conns This attribute can be mapped to the max-client-connections property of
a connection handler resource limit. To congure this property, use the
dpconf command as follows:
$ dpconf set-resource-limit-policy-prop POLICY-NAME
max-client-connections:VALUE
For more information, see “Creating and Conguring a Resource Limits
Policy” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
ids-proxy-con-userid This attribute can be mapped to the user and group names specied when
an instance is created by using the following command:
$ dpadm create [-u NAME -g NAME] INSTANCE-PATH
For more information, see “Creating and Deleting a Directory Proxy Server
Instance” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
ids-proxy-con-working-dir This attribute can be mapped to the INSTANCE-PATH specied when an
instance is created by using the following command:
$ dpadm create INSTANCE-PATH
For more information, see “Creating and Deleting a Directory Proxy Server
Instance” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
ids-proxy-con-include-logpropertyNo equivalent. For information on conguring logging in Directory Proxy
Server 6.0, see Chapter 27, “Directory Proxy Server Logging,” in Sun Java
System Directory Server Enterprise Edition 6.0 Administration Guide.
Mapping the Global Security Conguration
In Directory Proxy Server 5, security is congured by using attributes of the global
conguration object. In Directory Proxy Server 6.0, you can congure security when you create
the server instance by using the dpadm command. For more information, see Chapter 19,
“Directory Proxy Server Certicates,” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Config-Name=name,ou=global,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ids-proxy-con-Config-Name=user-dened-name,ou=system,ou=dar-config,o=netscaperoot.
The following table maps the version 5 security attributes to the corresponding properties in
Directory Proxy Server 6.
Chapter 6 • Migrating Directory Proxy Server 85
Sun Condential: Registered
Page 86

Mapping the Global Conguration
TABLE 6–2 Mapping of Security Conguration
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-ssl-key ssl-key-pin
ids-proxy-con-ssl-cert ssl-certificate-directory
ssl-server-cert-alias
ids-proxy-con-send-cert-as-client
This attribute enables the proxy server to send its
certicate to the LDAP server to allow the LDAP
server to authenticate the proxy server as an SSL
client.
ids-proxy-con-server-ssl-version
ids-proxy-con-client-ssl-version
ids-proxy-con-ssl-cert-required This feature can be achieved by setting the following
ids-proxy-con-ssl-cafile No equivalent
ssl-client-cert-alias
This property enables the proxy server to send a dierent
certicate to the LDAP server, depending on whether it is
acting as an SSL Server or an SSL Client.
No equivalent
server property:
$ dpconf set-server-prop
allow-cert-based-auth:require
Managing Certicates
Directory Proxy Server 5, certicates were managed by using the certreq utility, or by using the
console. In Directory Proxy Server 6.0, certicates are managed by using the dpadm command,
or by using the DSCC.
Certicates must be installed on each individual data source in Directory Proxy Server 6.0.
For information about managing certicates in Directory Proxy Server 6.0, see Chapter 19,
“Directory Proxy Server Certicates,” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
Access Control on the Proxy Conguration
In Directory Proxy Server 5, access control on the proxy conguration is managed by ACIs in
the conguration directory server. In Directory Proxy Server 6.0, access to the conguration le
is restricted to the person who created the proxy instance, or to the proxy manager if the
conguration is accessed through Directory Proxy Server. Editing the conguration le directly
is not supported.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200786
Sun Condential: Registered
Page 87

Mapping the Connection Pool Conguration
Directory Proxy Server 5 can be congured to reuse existing connections to the backend LDAP
servers. This can provide a signicant performance gain if the backend servers are on a Wide
Area Network (WAN). In Directory Proxy Server 6.0, this functionality is provided with
connection pools that are congured in the backend server itself. For more information, see
Chapter 20, “LDAP Data Sources and Data Source Pools,” in Sun Java System Directory Server
Enterprise Edition 6.0 Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Config-Name=name,ou=global,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ids-proxy-con-Config-Name=user-dened-name,ou=system,ou=dar-config,o=netscaperoot.
The following table provides a mapping between Directory Proxy Server 5 connection
conguration attributes and the corresponding Directory Proxy Server 6.0 properties.
TABLE 6–3 Mapping of Connection Pool Attributes
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-connection-pool No equivalent
Mapping the Connection PoolConguration
ids-proxy-con-connection-pool-interval The connection pool grows automatically to a
congured maximum. The maximum is congured
by setting the following properties of an LDAP data
source:
num-bind-init
num-bin-incr
num-bind-limit
num-read-init
num-read-incr
num-read-limit
num-write-init
num-write-incr
num-write-limit
For information about setting LDAP data source
properties, see “To Congure an LDAP Data Source”
in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide.
ids-proxy-con-connection-pool-timeout backendMaxReadWaitTimeInMilliSec
Chapter 6 • Migrating Directory Proxy Server 87
Sun Condential: Registered
Page 88

Mapping the Groups Conguration
Mapping the Groups Conguration
Directory Proxy Server 5 uses groups to dene how client connections are identied and what
restrictions are placed on the client connections. In Directory Proxy Server 6.0, this
functionality is achieved using connection handlers, data views and listeners.
Connection handlers, data views and listeners can be congured by using the Directory Service
Control Center or by using the dpconf command. For more information, see Chapter 25,
“Directory Proxy Server Connection Handlers,” in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide and Chapter 23, “Directory Proxy Server Data Views,” in Sun
Java System Directory Server Enterprise Edition 6.0 Administration Guide.
Mapping the Group Object
In Directory Proxy Server 5, a group is dened by setting the attributes of the
ids-proxy-sch-Group object class. Certain attributes of this object class can be mapped to
Directory Proxy Server 6.0 connection handler properties. For a list of all the
connection-handler properties, run the following command:
$ dpconf help-properties | grep connection-handler
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory Proxy
Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps version 5 group attributes to the corresponding connection handler
properties.
TABLE 6–4 Mapping Between Version 5 Group Attributesand Version 6 Connection Handler Properties
Directory Proxy Server 5 Group Attribute Directory Proxy Server 6.0 Connection Handler Property
ids-proxy-con-Name cn
ids-proxy-con-Priority priority
ids-proxy-sch-Enable is-enabled
ids-proxy-sch-belongs-to No equivalent
ids-proxy-con-permit-auth-none:TRUE
ids-proxy-con-permit-auth-sasl:TRUE
ids-proxy-con-permit-auth-simple:TRUE
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200788
Sun Condential: Registered
allowed-auth-methods:anonymous
allowed-auth-methods:sasl
allowed-auth-methods:simple
Page 89

Mapping the Groups Conguration
Mapping the Network Group Object
Directory Proxy Server 5 groups are congured by setting the attributes of the
ids-proxy-sch-NetworkGroup object class. These attributes can be mapped to properties of
Directory Proxy Server 6.0 connection handlers, data sources and listeners. For a list of all the
properties related to these objects, run the dpconf help-properties command, and search for
the object. For example, to locate all the properties of a connection handler, run the following
command:
$ dpconf help-properties | grep connection-handler
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps Directory Proxy Server 5 network group attributes to the
corresponding Directory Proxy Server 6.0 properties and describes how to set these properties
by using the command line.
TABLE 6–5 Mapping Between Version 5 Network Group Attributes and 6.0 Properties
Directory Proxy Server 5 Network Group Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-Client domain-name-filters and ip-address-filters
properties of a connection handler
ids-proxy-con-include-property No equivalent
ids-proxy-con-include-rule No equivalent
ids-proxy-con-ssl-policy:ssl_required Set this as a connection handler property by using the
following command:
$ dpconf set-connection-handler-prop
CONNECTION-HANDLER-NAME is-ssl-mandatory:true
ids-proxy-con-ssl-policy:ssl_optional Set this as an LDAP data source property by using the
following command:
$ dpconf set-ldap-data-source-prop ds1
ssl-policy:client
ids-proxy-con-ssl-policy:ssl_unavailable Set this as a connection handler property by using the
following command:
$ dpconf set-connection-handler-prop
CONNECTION-HANDLER-NAME is-ssl-mandatory:false
Chapter 6 • Migrating Directory Proxy Server 89
Sun Condential: Registered
Page 90

Mapping the Groups Conguration
TABLE 6–5 Mapping Between Version 5 Network Group Attributes and 6.0 Properties (Continued)
Directory Proxy Server 5 Network Group Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-tcp-no-delay Set this as a property for a specic listener port by using
ids-proxy-con-allow-multi-ldapv2–bind No equivalent
ids-proxy-con-reverse-dns-lookup No equivalent
ids-proxy-con-timeout This functionality exists but with less granularity than in
Mapping Bind Forwarding
Directory Proxy Server 5 bind forwarding is used to determine whether to pass a bind request
on to an LDAP server or to reject the bind request and close the client's connection. Directory
Proxy Server 6.0 forwards either all bind requests or no bind requests. However, by setting the
allowed-auth-methods connection handler property, successful binds can be classied into
connection handlers, according to the authentication criteria. Directory Proxy Server 6.0 can be
congured to reject all requests from a specic connection handler, providing the same
functionality as Directory Proxy Server 5 bind forwarding.
the following command:
$ dpconf set-ldap-listener-prop
use-tcp-no-delay:true
Directory Proxy Server 5. Set this limit as a property for a
specic listener port by using the following command:
$ dpconf set-ldap-listener-prop
connection-idle-timeout:value
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot
The following table maps the Directory Proxy Server 5 bind forwarding attributes to the
corresponding Directory Proxy Server 6 connection handler property settings.
TABLE 6–6 Mapping of Directory Proxy Server 5 Bind Forwarding Attributes to Directory Proxy Server 6
Connection Handler Property Settings
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-bind-name Noequivalent
ids-proxy-con-permit-auth-none allowed-auth-methods:anonymous
ids-proxy-con-permit-auth-simple allowed-auth-methods:simple
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200790
Sun Condential: Registered
Page 91

Mapping the Groups Conguration
TABLE 6–6 Mapping of Directory Proxy Server 5 Bind Forwarding Attributes to Directory Proxy Server 6
Connection Handler Property Settings (Continued)
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-permit-auth-sasl allowed-auth-methods:sasl
Mapping Operation Forwarding
Operation forwarding determines how Directory Proxy Server 5 handles requests after a
successful bind. In Directory Proxy Server 6.0, this functionality is provided by setting the
properties of a request ltering policy. For information on conguring a request ltering policy,
see “Creating and Conguring Request Filtering Policies and Search Data Hiding Rules” in Sun
Java System Directory Server Enterprise Edition 6.0 Administration Guide. For a list of all the
properties of a request ltering policy, run the following command:
$ dpconf help-properties | grep request-filtering-policy
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 operation forwarding attributes to the
corresponding Directory Proxy Server 6 request ltering properties.
TABLE 6–7 Mapping of Directory Proxy Server 5 Operation Forwarding Attributes to Directory Proxy
Server 6 Request Filtering Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-permit-op-search allow-search-operations
ids-proxy-con-permit-op-compare allow-compare-operations
ids-proxy-con-permit-op-add allow-add-operations
ids-proxy-con-permit-op-delete allow-delete-operations
ids-proxy-con-permit-op-modify allow-modify-operations
ids-proxy-con-permit-op-modrdn allow-rename-operations
ids-proxy-con-permit-op-extended allow-extended-operations
Chapter 6 • Migrating Directory Proxy Server 91
Sun Condential: Registered
Page 92

Mapping the Groups Conguration
Mapping Subtree Hiding
Directory Proxy Server 5 uses the ids-proxy-con-forbidden-subtree attribute to specify a
subtree of entries to be excluded in any client request. Directory Proxy Server 6.0 provides this
functionality with the allowed-subtrees and prohibited-subtrees properties of a request
ltering policy. For information on hiding subtrees in this way, see “Creating and Conguring a
Resource Limits Policy” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
If your subtrees are distributed across dierent backend servers, you can use the
excluded-subtrees property of a data view to hide subtrees. For more information on hiding
subtrees in this way, see “Excluding a Subtree From a Data View” in Sun Java System Directory
Server Enterprise Edition 6.0 Reference and “To Congure Data Views With Hierarchy and a
Distribution Algorithm” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
Mapping Search Request Controls
In Directory Proxy Server 5, search request controls are used to prevent certain kinds of
requests from reaching the LDAP server. In Directory Proxy Server 6.0, this functionality is
provided by setting properties of a request ltering policy and a resource limits policy.
For information on conguring a request ltering policy, see “Creating and Conguring
Request Filtering Policies and Search Data Hiding Rules” in Sun Java System Directory Server
Enterprise Edition 6.0 Administration Guide. For information on conguring a resource limits
policy, see “Creating and Conguring a Resource Limits Policy” in Sun Java System Directory
Server Enterprise Edition 6.0 Administration Guide. For a list of all the properties associated with
a request ltering policy, or a resource limits policy, run the dpadm help-properties
command and search for the object. For example, to locate all properties associated with a
resource limits policy, run the following command:
$ dpconf help-properties | grep resource-limits-policy
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 search request control attributes to the
corresponding Directory Proxy Server 6.0 properties.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200792
Sun Condential: Registered
Page 93

Mapping the Groups Conguration
TABLE 6–8 Mapping Directory Proxy Server 5 Search Request Control Attributes to Directory Proxy Server
6.0 Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-filter-inequality allow-inequality-search-operations property of
the request ltering policy
ids-proxy-con-min-substring-size minimum-search-filter-substring-length
property of the resource limits policy
Mapping Compare Request Controls
In Directory Proxy Server 5, compare request controls are used to prevent certain kinds of
search and compare operations from reaching the LDAP server. In Directory Proxy Server 6.0,
this functionality is provided by setting properties of a request ltering policy.
For information on conguring a request ltering policy, see “Creating and Conguring
Request Filtering Policies and Search Data Hiding Rules” in Sun Java System Directory Server
Enterprise Edition 6.0 Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 compare request control attributes to the
corresponding Directory Proxy Server 6 properties.
TABLE 6–9 Mapping of Directory Proxy Server 5 Compare Request Control Attributes to Directory Proxy
Server 6 Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-forbidden-compare prohibited-comparable-attrs
ids-proxy-con-permitted-compare allowed-comparable-attrs
Mapping Attributes Modifying Search Requests
In Directory Proxy Server 5, these attributes are used to modify the search request before it is
forwarded to the server. In Directory Proxy Server 6, this functionality is provided by setting
properties of a request ltering policy and a resource limits policy.
For information on conguring a request ltering policy, see “Creating and Conguring
Request Filtering Policies and Search Data Hiding Rules” in Sun Java System Directory Server
Chapter 6 • Migrating Directory Proxy Server 93
Sun Condential: Registered
Page 94

Mapping the Groups Conguration
Enterprise Edition 6.0 Administration Guide. For information on conguring a resource limits
policy, see “Creating and Conguring a Resource Limits Policy” in Sun Java System Directory
Server Enterprise Edition 6.0 Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 search request modifying attributes to
the corresponding Directory Proxy Server 6 properties.
TABLE 6–10 Mapping of Directory Proxy Server 5 Search Request Modifying Attributes to Directory Proxy
Server 6 Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-minimum-base allowed-subtrees property of the request ltering
ids-proxy-con-max-scope allowed-search-scopes property of the request
ids-proxy-con-max-timelimit search-time-limit property of the resource limits
policy
ltering policy
policy
Mapping Attributes Restricting Search Responses
In Directory Proxy Server 5, these attributes describe restrictions that are applied to search
results being returned by the server, before they are forwarded to the client. In Directory Proxy
Server 6, this functionality is provided by setting the properties of a resource limits policy and
by conguring search data hiding rules.
For information about conguring a resource limits policy, see “Creating and Conguring a
Resource Limits Policy” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide. For information about creating search data hiding rules, see “To Create
Search Data Hiding Rules” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide. For a list of properties associated with a search data hiding rule, run the
following command:
$ dpconf help-properties | grep search-data-hiding-rule
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200794
Sun Condential: Registered
Page 95

Mapping the Groups Conguration
The following table maps the Directory Proxy Server 5 search response restriction attributes to
the corresponding Directory Proxy Server 6.0 properties.
TABLE 6–11 Mapping of Directory Proxy Server 5 Search Response Restriction Attributes to Directory
Proxy Server 6.0 Properties
Directory Proxy Server 5 Attributes Directory Proxy Server 6.0 Properties
ids-proxy-con-max-result-size search-size-limit property of the resource limits
policy
ids-proxy-con-forbidden-return To hide a subset of attributes:
rule-action:hide-attributes
attributes:attribute-name
To hide an entire entry:
rule-action:hide-entry
ids-proxy-con-permitted-return rule-action:show-attributes
attributes:attribute-name
ids-proxy-con-search-reference No direct equivalent. Search continuation references
are governed by the referral-policy property of the
resource limits policy
Mapping the Referral Conguration Attributes
In Directory Proxy Server 5, these attributes determine what Directory Proxy Server should do
with referrals. In Directory Proxy Server 6.0, this functionality is provided by setting properties
of a resource limits policy.
For information on conguring a resource limits policy, see “Creating and Conguring a
Resource Limits Policy” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 referral conguration attributes to the
corresponding Directory Proxy Server 6 resource limits properties.
Chapter 6 • Migrating Directory Proxy Server 95
Sun Condential: Registered
Page 96

Mapping the Groups Conguration
TABLE 6–12 Mapping of Directory Proxy Server 5 Referral Conguration Attributes to Directory Proxy
Server 6 resource limits Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-reference referral-policy
ids-proxy-con-referral-ssl-policy referral-policy
ids-proxy-con-referral-bind-policy referral-bind-policy
ids-proxy-con-max-refcount referral-hop-limit
Mapping the Server Load Conguration
In Directory Proxy Server 5, these attributes are used to control the number of simultaneous
operations and total number of operations a client can request on one connection. In Directory
Proxy Server 6, this functionality is provided by setting properties of a resource limits policy.
For information on conguring a resource limits policy, see “Creating and Conguring a
Resource Limits Policy” in Sun Java System Directory Server Enterprise Edition 6.0
Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the Directory Proxy Server 5 server load conguration attributes to
the corresponding Directory Proxy Server 6.0 resource limits properties.
TABLE 6–13 Mapping of Directory Proxy Server 5 Server Load Conguration Attributes to Directory Proxy Server 6.0 Resource
Limits Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-max-simultaneous-operations-per-connectionmax-simultaneous-operations-per-connection
ids-proxy-con-operations-per-connection max-total-operations-per-connection
ids-proxy-con-max-conns max-connections
ids-proxy-con-max-simultaneous-conns-from-ip max-client-connections
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200796
Sun Condential: Registered
Page 97

Mapping the Properties Conguration
The Directory Proxy Server 5 property objects enable you to specify specialized restrictions that
LDAP clients must follow. Most of the functionality of property objects is available in Directory
Proxy Server 6, although it is supplied by various elements of the new architecture. The
following sections describe how to map the Directory Proxy Server 5 property objects to the
corresponding 6.0 functionality.
Attribute Renaming Property
In Directory Proxy Server 5, attribute renaming is dened by the
ids-proxy-sch-RenameAttribute object class. This object uses the
ids-proxy-con-server-attr-name and ids-proxy-con-client-attr-name attributes to
specify which attributes must be renamed by Directory Proxy Server.
The attribute renaming functionality is replaced in Directory Proxy Server 6 by the
attr-name-mappings property of an LDAP data source. This property is multi-valued, and
takes values of the form client-attribute-name#server-attribute-name. In a client request,
Directory Proxy Server renames the client-attribute-name to the server-attribute-name.
In a response, Directory Proxy Server renames the server-attribute-name to the
client-attribute-name.
Mapping the Properties Conguration
To congure this property, use the following command:
$ dpconf set-ldap-data-source-prop data-source-name \
attr-name-mappings:client-attribute-name#server-attribute-name
Forbidden Entry Property
In Directory Proxy Server 5, the ids-proxy-sch-ForbiddenEntryProperty object is used to
specify a list of entries or attributes that are hidden from client applications. In Directory Proxy
Server 6.0 this functionality is achieved by creating a search-data-hiding-rule for a request
ltering policy.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=group-name,ou=groups,ou=pd2,ou=iDAR,o=services. In Directory
Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the attributes of the ids-proxy-sch-ForbiddenEntryProperty
object to the corresponding properties of a search data hiding rule in Directory Proxy Server
6.0. For information about creating search data hiding rules, see “To Create Search Data Hiding
Rules” in Sun Java System Directory Server Enterprise Edition 6.0 Administration Guide.
Chapter 6 • Migrating Directory Proxy Server 97
Sun Condential: Registered
Page 98

Mapping the Properties Conguration
TABLE 6–14 Mapping of Directory Proxy Server 5 Server Load Conguration Attributes to Directory Proxy
Server 6 Resource Limits Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6 Property
ids-proxy-con-dn-exact target-dns
ids-proxy-con-dn-regexp target-dn-regular-expressions
ids-proxy-con-ava target-attr-value-assertions
ids-proxy-con-forbidden-return To hide a subset of attributes:
ids-proxy-con-permitted-return rule-action:show-attributes
LDAP Server Property
rule-action:hide-attributes
attrs:attribute-name
To hide an entire entry:
rule-action:hide-entry
attrs:attribute-name
In Directory Proxy Server 5, the ids-proxy-sch-LDAPServer property is used to dene the
backend LDAP servers to which Directory Proxy Server sends requests. In Directory Proxy
Server 6.0, this functionality is achieved by using LDAP data sources. You can set properties for
LDAP data sources by using the Directory Service Control Center or by using the command
line. For more information, see “Creating and Conguring LDAP Data Sources” in Sun Java
System Directory Server Enterprise Edition 6.0 Administration Guide.
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=server-name,ou=properties,ou=pd2,ou=iDAR,o=services.In
Directory Proxy Server 5.2, these conguration attributes are stored under
ou=groups,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
The following table maps the attributes of the ids-proxy-sch-LDAPServer object class to the
corresponding data source properties in Directory Proxy Server 6.0. Data sources provide
additional functionality that was not provided in Directory Proxy Server 5. Not all data source
properties are listed here. For a list of all the properties that can be congured for a data source,
run the following command:
$ dpconf help-properties | grep ldap-data-source
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 200798
Sun Condential: Registered
Page 99

Mapping the Properties Conguration
TABLE 6–15 Mapping of ids-proxy-sch-LDAPServer Attributesto Data Source Properties
Directory Proxy Server 5 Attribute Directory Proxy Server 6.0 Property
ids-proxy-con-host ldap-address
ids-proxy-con-port ldap-port
ids-proxy-con-sport ldaps-port
ids-proxy-con-supported-version No equivalent
Directory Proxy Server 6.0 supports LDAP v3
backends for both version 2 and version 3 clients.
Directory Proxy Server 6.0 supports the proxy
authorization control version 1 and version 2.
ids-proxy-con-use-version No equivalent
Directory Proxy Server 6.0 supports LDAP v3
backends for both v2 and v3 clients.
Directory Proxy Server 6.0 supports the proxy
authorization control version 1 and version 2.
ids-proxy-con-tcp-no-delay use-tcp-no-delay
ids-proxy-con-link-security-policy ssl-policy
ids-proxy-con-x509cert-subject No equivalent. Directory Proxy Server 6.0 does not
check the subject of the certicate provided by the
backend server.
ids-proxy-con-keepalive-interval This functionality is achieved by setting the
following properties of the LDAP data source:
monitoring-bind-timeout
monitoring-entry-timeout
monitoring-inactivity-timeout
monitoring-interval
For information about setting LDAP data source
properties, see “To Congure an LDAP Data
Source” in Sun Java System Directory Server
Enterprise Edition 6.0 Administration Guide.
Load Balancing Property
In Directory Proxy Server 5, the ids-proxy-sch-LoadBalanceProperty is used to congure
load balancing across multiple LDAP servers. Directory Proxy Server 5 supports proportional
Chapter 6 • Migrating Directory Proxy Server 99
Sun Condential: Registered
Page 100

Mapping the Properties Conguration
load balancing only, that is, each LDAP server is allotted a certain percentage of the total load.
The ids-proxy-sch-LoadBalanceProperty object class has one attribute,
ids-proxy-con-Server, whose value has the following syntax:
server-name[#percentage]
In Iplanet Directory Access Router 5.0 (IDAR) these conguration attributes are stored under
ids-proxy-con-Name=load-balance,ou=properties,ou=pd2,ou=iDAR,o=services.In
Directory Proxy Server 5.2, these conguration attributes are stored under
ids-proxy-con-name=load-balancing-1,ou=properties,cn=user-dened-name,ou=dar-config,o=NetscapeRoot.
In Directory Proxy Server 6.0, load balancing is congured as a property of a data source pool. A
data source pool is essentially a collection of LDAP servers to which Directory Proxy Server can
route requests. For information about setting up a data source pool, see “Creating and
Conguring LDAP Data Source Pools” in Sun Java System Directory Server Enterprise
Edition 6.0 Administration Guide. For a list of properties associated with a data source pool, run
the following command:
$ dpconf help-properties | grep ldap-data-source-pool
Directory Proxy Server 6.0 supports proportional load balancing but also supports additional
load balancing algorithms. To congure proportional load balancing, set the property of the
data source pool as follows:
$ dpconf set-ldap-data-source-pool-prop data-source-pool-name load-balancing-algorithm:proportional
The percentage of load allotted to each server is congured by setting various properties of an
attached data source. An attached data source is a data source that has been attached to a
specic data source pool. To congure proportional load, set the weight properties of the
attached data source for each operation type as follows:
$ dpconf set-attached-ldap-data-source-prop data-source-pool-name attached-data-source-name
add-weight:value
bind-weight:value
compare-weight:value
delete-weight:value
modify-dn-weight:value
modify-weight:value
search-weight:value
For more information, see “Conguring Load Balancing” in Sun Java System Directory Server
Enterprise Edition 6.0 Administration Guide.
Monitoring Backend Servers
To monitor the state of its backend LDAP servers, Directory Proxy Server 5 performs an
anonymous search operation on the RootDSE of each server every ten seconds. Directory Proxy
Sun Java System Directory Server Enterprise Edition 6.0 Migration Guide • March 2007100
Sun Condential: Registered
 Loading...
Loading...