2048-bit EEPROM tag IC at 13.56 MHz, with 64-bit UID and
Sawn Bumped Wafer
Password, ISO15693 and ISO18000-3 Mode 1 compliant
Features
■ ISO 15693 standard fully compliant
■ ISO 18000-3 Mode 1 standard fully compliant
■ 13.56 MHz ±7 kHz carrier frequency
■ To tag: 10% or 100% ASK modulation using
1/4 (26 Kbit/s) or 1/256 (1.6 Kbit/s) pulse
position coding
■ From tag: Load modulation using Manchester
coding with 423 kHz and 484 kHz subcarriers
in Low (6.6 Kbit/s) or High (26 Kbit/s) data rate
mode. Supports the 53 Kbit/s data rate with
Fast commands
■ Internal tuning capacitor 21 pF
■ 1 000 000 Erase/Write cycles (minimum)
■ 40 year data retention (minimum)
■ 2048-bits EEPROM with Block Lock feature
■ 64-bit unique identifier (UID)
■ Electrical article surveillance (EAS) capable
(software controlled)
■ Kill function
■ Multipassword protection
■ Read & Write (block of 32 bits)
■ 5 ms programming time
LRIS2K
September 2011 Doc ID 13888 Rev 9 1/98
www.st.com
1

Contents LRIS2K
Contents
1 Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
1.1 Memory mapping . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
1.2 Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
1.3 Initial dialogue for vicinity cards . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
1.3.1 Power transfer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
1.3.2 Frequency . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
1.3.3 Operating field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
2 LRIS2K block security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
3 Example of LRIS2K security protection . . . . . . . . . . . . . . . . . . . . . . . . 17
4 Communication signal from VCD to LRIS2K . . . . . . . . . . . . . . . . . . . . 18
5 Data rate and data coding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
5.1 Data coding mode: 1 out of 256 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
5.2 Data coding mode: 1 out of 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
5.3 VCD to LRIS2K frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
5.4 Start of frame (SOF) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
6 Communications signal from LRIS2K to VCD . . . . . . . . . . . . . . . . . . . 25
6.1 Load modulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
6.2 Subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
6.3 Data rates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
7 Bit representation and coding . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
7.1 Bit coding using one subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
7.1.1 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
7.1.2 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
7.2 Bit coding using two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
7.3 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
7.4 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
2/98 Doc ID 13888 Rev 9

LRIS2K Contents
8 LRIS2K to VCD frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
8.1 SOF when using one subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
8.2 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
8.3 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
8.4 SOF when using two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
8.5 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
8.6 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
8.7 EOF when using one subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
8.8 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
8.9 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
8.10 EOF when using two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
8.11 High data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
8.12 Low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
9 Unique identifier (UID) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
10 Application family identifier (AFI) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
11 Data storage format identifier (DSFID) . . . . . . . . . . . . . . . . . . . . . . . . . 36
11.1 CRC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
12 LRIS2K protocol description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
13 LRIS2K states . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
13.1 Power-off state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
13.2 Ready state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
13.3 Quiet state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
13.4 Selected state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
14 Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
14.1 Addressed mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
14.2 Non-addressed mode (general request) . . . . . . . . . . . . . . . . . . . . . . . . . 41
14.3 Select mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
15 Request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Doc ID 13888 Rev 9 3/98

Contents LRIS2K
15.1 Request_flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
16 Response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
16.1 Response_flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
16.2 Response error code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
17 Anticollision . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
17.1 Request parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
18 Request processing by the LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
19 Explanation of the possible cases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49
20 Inventory Initiated command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51
21 Timing definition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
21.1 t1: LRIS2K response delay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
21.2 t2: VCD new request delay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
21.3 t
: VCD new request delay in the absence of a response from
3
the LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
22 Commands codes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
23 Inventory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
24 Stay Quiet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
25 Read Single Block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
26 Write Single Block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
27 Lock Block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
28 Select . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
29 Reset to Ready . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
30 Write AFI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
4/98 Doc ID 13888 Rev 9

LRIS2K Contents
31 Lock AFI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
32 Write DSFID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
33 Lock DSFID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
34 Get System Info . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
35 Get Multiple Block Security Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
36 Kill . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
37 Write Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
38 Lock Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
39 Present Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
40 Fast Read Single Block . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
41 Fast Inventory Initiated . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
42 Fast Initiate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
43 Inventory Initiated . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
44 Initiate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
45 Maximum rating . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
46 DC and AC parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
47 Part numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Appendix A Anticollision algorithm (Informative) . . . . . . . . . . . . . . . . . . . . . . . . 92
A.1 Algorithm for pulsed slots . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
Appendix B CRC (informative) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
B.1 CRC error detection method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Doc ID 13888 Rev 9 5/98

Contents LRIS2K
B.2 CRC calculation example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Appendix C Application family identifier (AFI) (informative) . . . . . . . . . . . . . . . 95
Revision history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
6/98 Doc ID 13888 Rev 9

LRIS2K List of tables
List of tables
Table 1. Signal names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Table 2. Memory map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Table 3. Memory blocks with protect status area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Table 4. Protect status area organization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15
Table 5. Read / Write protection bit setting and block protection status . . . . . . . . . . . . . . . . . . . . . . 15
Table 6. Password system area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Table 7. LRIS2K block security protection after power-up . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Table 8. LRIS2K block security protection after a valid presentation of password 1 . . . . . . . . . . . . 17
Table 9. 10% modulation parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Table 10. Response data rates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Table 11. UID format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Table 12. CRC transmission rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36
Table 13. VCD request frame format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Table 14. LRIS2K response frame format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Table 15. LRIS2K response depending on Request_flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Table 16. General request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Table 17. Definition of request_flags 1 to 4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Table 18. Request_flags 5 to 8 when Bit 3 = 0 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Table 19. Request_flags 5 to 8 when Bit 3 = 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43
Table 20. General response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Table 21. Definitions of response_flags 1 to 8 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Table 22. Response error code definition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
Table 23. Inventory request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
Table 24. Example of the addition of 0-bits to an 11-bit mask value . . . . . . . . . . . . . . . . . . . . . . . . . 46
Table 25. Timing values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Table 26. Command codes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Table 27. Inventory request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Table 28. Inventory response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Table 29. Stay Quiet request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Table 30. Read Single Block request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Table 31. Read Single Block response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . 56
Table 32. Block Locking status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
Table 33. Read Single Block response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . 56
Table 34. Write Single Block request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Table 35. Write Single Block response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . 58
Table 36. Write Single Block response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . 58
Table 37. Lock Single Block request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Table 38. Lock Block response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Table 39. Lock Block response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Table 40. Select request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Table 41. Select Block response format when Error_flag is NOT set. . . . . . . . . . . . . . . . . . . . . . . . . 62
Table 42. Select response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Table 43. Reset to Ready request format. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Table 44. Reset to Ready response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . 63
Table 45. Reset to Ready request format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
Table 46. Write AFI request format. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Table 47. Write AFI response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Table 48. Write AFI response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Doc ID 13888 Rev 9 7/98

List of tables LRIS2K
Table 49. Lock AFI request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Table 50. Lock AFI response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Table 51. Lock AFI response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Table 52. Write DSFID request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Table 53. Write DSFID response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . 67
Table 54. Write DSFID response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
Table 55. Lock DSFID request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Table 56. Lock DSFID response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . . 69
Table 57. Lock DSFID response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Table 58. Get System Info request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Table 59. Get System Info response format when Error_flag is NOT set. . . . . . . . . . . . . . . . . . . . . . 70
Table 60. Get System Info response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Table 61. Get Multiple Block Security Status request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Table 62. Get Multiple Block Security Status response format when Error_flag is NOT set . . . . . . . 72
Table 63. Block Locking status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
Table 64. Get Multiple Block Security Status response format when Error_flag is set . . . . . . . . . . . . 72
Table 65. Kill request format. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Table 66. Kill response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Table 67. Kill response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
Table 68. Write Password request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Table 69. Write Password response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . 76
Table 70. Write Password response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . . . 76
Table 71. Lock Password request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Table 72. Protect status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Table 73. Lock Password response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . . . 78
Table 74. Lock Password response format when Error_flag is set. . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Table 75. Present Password request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Table 76. Present Password response format when Error_flag is NOT set . . . . . . . . . . . . . . . . . . . . 80
Table 77. Present Password response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . . . . . 80
Table 78. Fast Read Single Block request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Table 79. Fast Read Single Block response format when Error_flag is NOT set . . . . . . . . . . . . . . . . 82
Table 80. Block Locking status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Table 81. Fast Read Single Block response format when Error_flag is set . . . . . . . . . . . . . . . . . . . . 82
Table 82. Fast Inventory Initiated request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Table 83. Fast Inventory Initiated response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
Table 84. Fast Initiate request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Table 85. Fast Initiate response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Table 86. Inventory Initiated request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Table 87. Inventory Initiated response format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
Table 88. Initiate request format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Table 89. Initiate Initiated response format. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Table 90. Absolute maximum ratings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
Table 91. AC characteristics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Table 92. DC characteristics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Table 93. Operating conditions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
Table 94. Ordering information scheme . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Table 95. CRC definition. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Table 96. AFI coding. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
Table 97. Document revision history . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
8/98 Doc ID 13888 Rev 9

LRIS2K List of figures
List of figures
Figure 1. Pad connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Figure 2. 100% modulation waveform . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Figure 3. 10% modulation waveform . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Figure 4. 1 out of 256 coding mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Figure 5. Detail of a time period . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Figure 6. 1 out of 4 coding mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Figure 7. 1 out of 4 coding example. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22
Figure 8. SOF to select 1 out of 256 data coding mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Figure 9. SOF to select 1 out of 4 data coding mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Figure 10. EOF for either data coding mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Figure 11. Logic 0, high data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 12. Logic 0, high data rate x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 13. Logic 1, high data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 14. Logic 1, high data rate x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Figure 15. Logic 0, low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 16. Logic 0, low data rate x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 17. Logic 1, low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 18. Logic 1, low data rate x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Figure 19. Logic 0, high data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Figure 20. Logic 1, high data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Figure 21. Logic 0, low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Figure 22. Logic 1, low data rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Figure 23. Start of frame, high data rate, one subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Figure 24. Start of frame, high data rate, one subcarrier x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Figure 25. Start of frame, low data rate, one subcarrier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Figure 26. Start of frame, low data rate, one subcarrier x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Figure 27. Start of frame, high data rate, two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Figure 28. Start of frame, low data rate, two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Figure 29. End of frame, high data rate, one subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Figure 30. End of frame, high data rate, one subcarriers x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Figure 31. End of frame, low data rate, one subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Figure 32. End of frame, low data rate, one subcarriers x2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Figure 33. End of frame, high data rate, two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Figure 34. End of frame, low data rate, two subcarriers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Figure 35. LRIS2K decision tree for AFI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Figure 36. LRIS2K protocol timing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Figure 37. LRIS2K state transition diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Figure 38. Principle of comparison between the mask, the slot number and the UID . . . . . . . . . . . . . 47
Figure 39. Description of a possible anticollision sequence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
Figure 40. Stay Quiet frame exchange between VCD and LRIS2K. . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Figure 41. Read Single Block frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . 57
Figure 42. Write Single Block frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . 59
Figure 43. Lock Block frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . 61
Figure 44. Select frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62
Figure 45. Reset to Ready frame exchange between VCD and LRIS2K. . . . . . . . . . . . . . . . . . . . . . . 63
Figure 46. Write AFI frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
Figure 47. Lock AFI frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
Figure 48. Write DSFID frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . 68
Doc ID 13888 Rev 9 9/98

List of figures LRIS2K
Figure 49. Lock DSFID frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . 69
Figure 50. Get System Info frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . 71
Figure 51. Get Multiple Block Security Status frame exchange between VCD and LRIS2K . . . . . . . . 73
Figure 52. Kill frame exchange between VCD and LRIS2K. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
Figure 53. Write Password frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . 77
Figure 54. Lock Password frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . 79
Figure 55. Present Password frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . 81
Figure 56. Fast Read Single Block frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . 83
Figure 57. Fast Initiate frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Figure 58. Initiate frame exchange between VCD and LRIS2K . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Figure 59. LRIS2K synchronous timing, transmit and receive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
10/98 Doc ID 13888 Rev 9
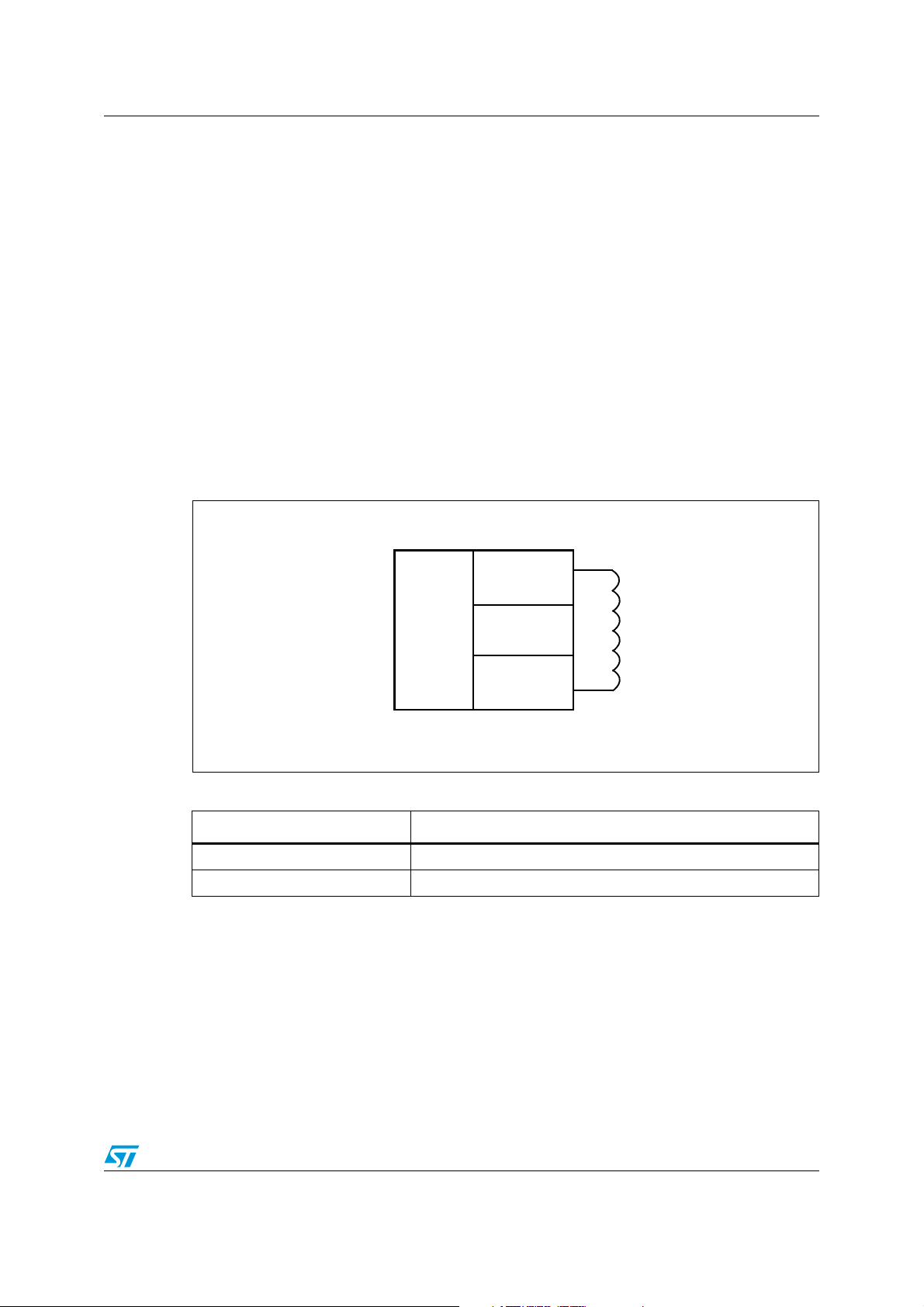
LRIS2K Description
AI12853
AC1
LRIS2K
AC0
Power
Supply
Regulator
Manchester
Load
Modulator
ASK
Demodulator
2048 bit
EEPROM
memory
1 Description
The LRIS2K is a contactless memory powered by the received carrier electromagnetic
wave, which follows the ISO 15693 recommendation for radio frequency power and signal
interface. It is a 2048-bit electrically erasable programmable memory (EEPROM). The
memory is organized as 64 blocks of 32 bits. The LRIS2K is accessed via the 13.56 MHz
carrier electromagnetic wave on which incoming data are demodulated from the received
signal amplitude modulation (ASK: amplitude shift keying). The received ASK wave is 10%
or 100% modulated with a data rate of 1.6 Kbit/s using the 1/256 pulse coding mode or a
Data rate of 26 Kbit/s using the 1/4 pulse coding mode.
Outgoing data are generated by the LRIS2K load variation using Manchester coding with
one or two subcarrier frequencies at 423 KHz and 484 kHz. Data are transferred from the
LRIS2K at 6.6 Kbit/s in low data rate mode and 26 Kbit/s high data rate mode. The LRIS2K
supports the 53 Kbit/s in high data rate mode in one subcarrier frequency at 423 kHz.
The LRIS2K also features a unique 32-bit multi-password protection scheme.
Figure 1. Pad connections
Table 1. Signal names
AC1 Antenna coil
AC0 Antenna coil
Signal name Function
Doc ID 13888 Rev 9 11/98
Description LRIS2K
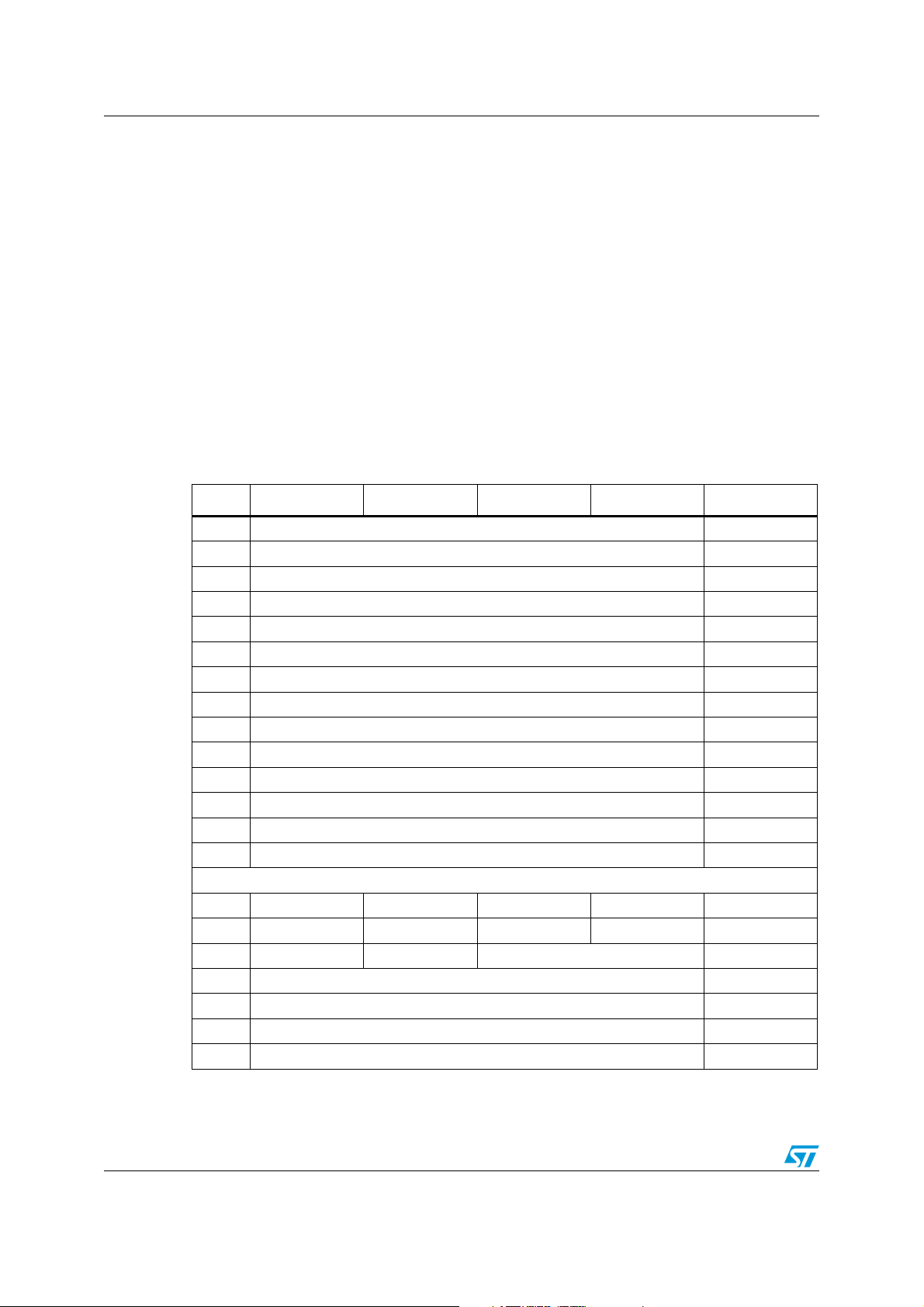
1.1 Memory mapping
The LRIS2K is divided into 64 blocks of 32 bits as shown in Ta bl e 2 . Each block can be
individually read- and/or write-protected using a specific lock or password command.
The user area consists of blocks that are always accessible. Read and Write operations are
possible if the addressed block is not protected. During a Write, the 32 bits of the block are
replaced by the new 32-bit value.
The LRIS2K also has a 64-bit block that is used to store the 64-bit unique identifier (UID).
The UID is compliant with the ISO 15963 description, and its value is used during the
anticollision sequence (Inventory). This block is not accessible by the user and its value is
written by ST on the production line.
The LRIS2K also includes an AFI register in which the application family identifier is stored,
and a DSFID register in which the data storage family identifier used in the anticollision
algorithm is stored. The LRIS2K has four additional 32-bit blocks in which the Kill code and
the password codes are stored.
Table 2. Memory map
Add 0 7 8 15 16 23 24 31 Protect status
0 User area 5 bits
1 User area 5 bits
2 User area 5 bits
3 User area 5 bits
4 User area 5 bits
5 User area 5 bits
6 User area 5 bits
7 User area 5 bits
8 User area 5 bits
... ... ...
60 User area 5 bits
61 User area 5 bits
62 User area 5 bits
63 User area 5 bits
UID 0 UID 1 UID 2 UID 3
UID 4 UID 5 UID 6 UID 7
AFI DSFID
(1)
0
(1)
1
(1)
2
(1)
3
1. RFU bit (b8) of Request_flag set to 1.
12/98 Doc ID 13888 Rev 9
Kill code 5 bits
Password code 1 5 bits
Password code 2 5 bits
Password code 3 5 bits

LRIS2K Description
1.2 Commands
The LRIS2K supports the following commands:
● Inventory, used to perform the anticollision sequence.
● Stay Quiet, used to put the LRIS2K in quiet mode, where it does not respond to any
inventory command.
● Select, used to select the LRIS2K. After this command, the LRIS2K processes all
Read/Write commands with Select_flag set.
● Reset To Ready, used to put the LRIS2K in the ready state.
● Read Block, used to output the 32 bits of the selected block and its locking status.
● Write Block, used to write the 32-bit value in the selected block, provided that it is not
locked.
● Lock Block, used to lock the selected block. After this command, the block cannot be
modified.
● Write AFI, used to write the 8-bit value in the AFI register.
● Lock AFI, used to lock the AFI register.
● Write DSFID, used to write the 8-bit value in the DSFID register.
● Lock DSFID, used to lock the DSFID register.
● Get System Info, used to provide the system information value
● Get Multiple Block Security Status, used to send the security status of the selected
block.
● Initiate, used to trigger the tag response to the Inventory Initiated sequence.
● Inventory Initiated, used to perform the anticollision sequence triggered by the Initiate
command.
● Kill, used to definitively deactivate the tag.
● Write Password, used to write the 32 bits of the selected password.
● Lock Password, used to write the Protect Status bits of the selected block.
● Present Password, enables the user to present a password to unprotect the user
blocks linked to this password.
● Fast Initiate, used to trigger the tag response to the Inventory Initiated sequence.
● Fast Inventory Initiated, used to perform the anticollision sequence triggered by the
Initiate command.
● Fast Read Single Block, used to output the 32 bits of the selected block and its
locking status.
Doc ID 13888 Rev 9 13/98

Description LRIS2K
1.3 Initial dialogue for vicinity cards
The dialog between the vicinity coupling device (VCD) and the vicinity integrated circuit
Card or VICC (LRIS2K) takes place as follows:
● activation of the LRIS2K by the RF operating field of the VCD.
● transmission of a command by the VCD.
● transmission of a response by the LRIS2K.
These operations use the RF power transfer and communication signal interface described
below (see Power transfer, Frequency and Operating field). This technique is called RTF
(Reader Talk First).
1.3.1 Power transfer
Power is transferred to the LRIS2K by radio frequency at 13.56 MHz via coupling antennas
in the LRIS2K and the VCD. The RF operating field of the VCD is transformed on the
LRIS2K antenna to an AC Voltage which is rectified, filtered and internally regulated. The
amplitude modulation (ASK) on this received signal is demodulated by the ASK
demodulator.
1.3.2 Frequency
The ISO 15693 standard defines the carrier frequency (fC) of the operating field as
13.56 MHz ±7 kHz.
1.3.3 Operating field
The LRIS2K operates continuously between H
● The minimum operating field is H
● The maximum operating field is H
A VCD shall generate a field of at least H
volume.
and H
min
and has a value of 150 mA/m rms.
min
and has a value of 5 A/m rms.
max
and not exceeding H
min
max
.
max
in the operating
14/98 Doc ID 13888 Rev 9
LRIS2K LRIS2K block security
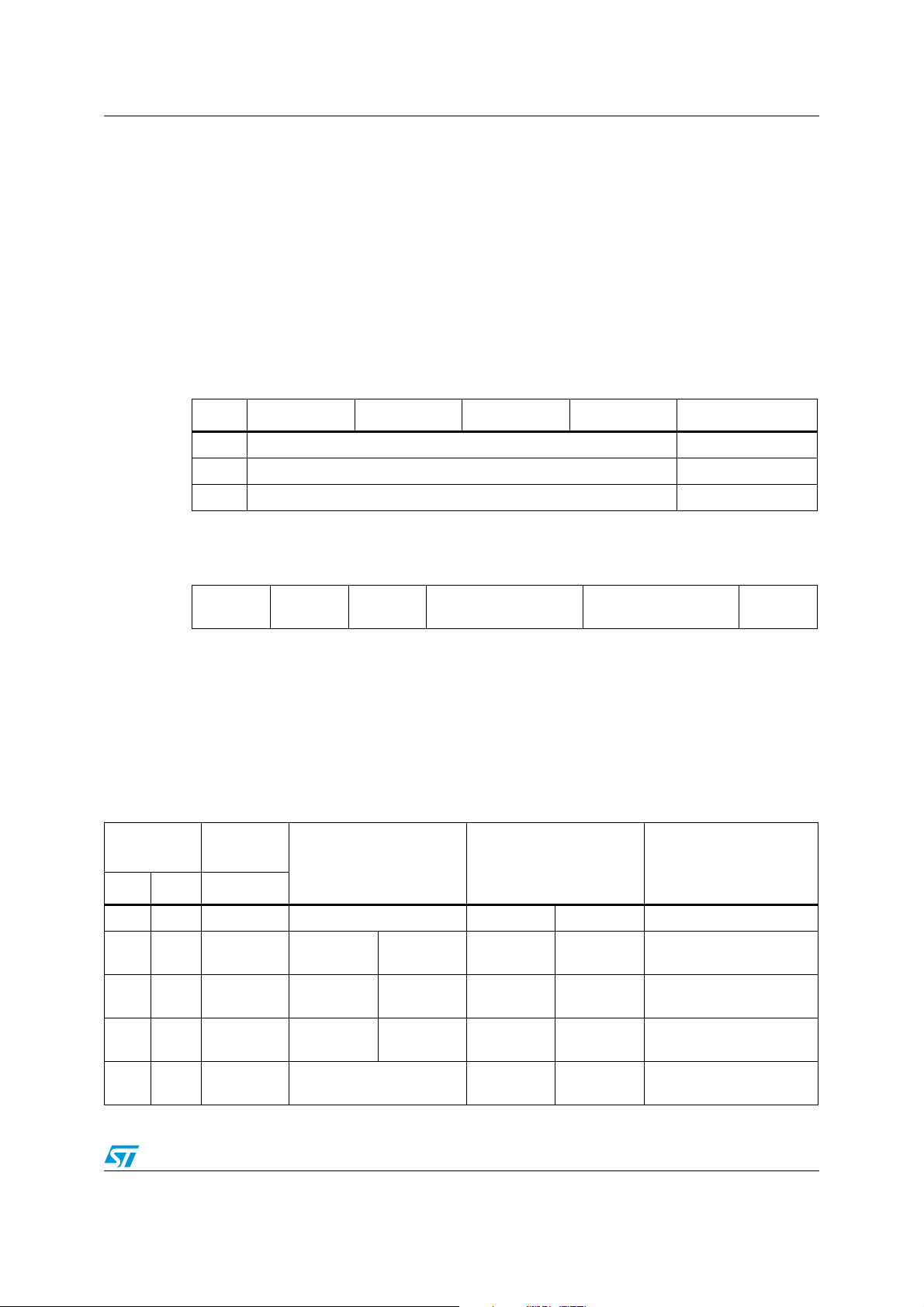
2 LRIS2K block security
The LRIS2K provides a special protection mechanism based on passwords. Each memory
block of the LRIS2K can be individually protected by one out of three available passwords,
and each block can also have Read/Write access conditions set.
Each memory block of the LRIS2K is assigned with a Protect Status area including a Block
Lock bit, two Password Control bits and two Read/Write protection bits as shown in Ta bl e 4 .
Ta bl e 4 describes the organization of the Protect status area which can be read using the
Read Single Block command with the Option_flag set to ‘1’, and the Get Multiple Block
Security status command.
Table 3. Memory blocks with protect status area
Add 0 7 8 15 16 23 24 31 Protect status
0 User area 5 bits
1 User area 5 bits
... User area 5 bits
Table 4. Protect status area organization
b
7
0 0 0 Password Control bits
b
6
b
5
b
4
b
3
b
2
b
1
Read / Write protection
bits
b
0
Block Lock
When the Block Lock bit is set to ‘1’, for instance by issuing a Block Lock command, the 2
Read/Write protection bits (b
, b2) are used to set the Read/Write access of the block as
1
described in Ta b le 5 .
The next 2 bits of the Protect Status area (b
, b4) are the Password Control bits. The value
3
of these two bits is used to link a password to the block as defined in Ta bl e 5 .
Combinations not described in Ta bl e 5 are reserved.
, b
1
Password
Control bits
b4, b
3
Block access when
password presented
Block access when
password not presented
Block protection status
the block is protected by
password 1
the block is protected by
password 2
the block is protected by
password 3
the block is not protected
by a password
Table 5. Read / Write protection bit setting and block protection status
Block lock
function
b
0b2
0 00 00 Not applicable READ WRITE the block is not protected
1 11 01 READ NO WRITE NO READ NO WRITE
1 11 10 READ NO WRITE NO READ NO WRITE
1 11 11 READ NO WRITE NO READ NO WRITE
1 00 00 Not applicable READ NO WRITE
Doc ID 13888 Rev 9 15/98
LRIS2K block security LRIS2K
The LRIS2K password protection is organized around a dedicated set of commands plus a
system area of four password blocks where the password values and the Kill code are
stored. Each password block also has a Protect Status area, making it possible to set the
Read / Write access right of each individual block. This system area is described in Ta bl e 6 .
Table 6. Password system area
Add 0 7 8 15 16 23 24 31 Protect status
0 Kill code 5 bits
1 Password 1 5 bits
2 Password 2 5 bits
3 Password 3 5 bits
The dedicated password commands are:
● Write Password:
The Write Password command is used to write a 32-bit block into the password system
area. This command must be used to write or update password values and to set the
kill code. Depending on the Read/Write access set in the Protect Status area, it is
possible to modify a password value after issuing a valid Present Password command.
● Lock Password:
The Lock Password command is used to set the Protect Status area of the selected
block. Bits b
The Block Lock bit, b
to b1 of the Protect Status are affected by the Lock Password command.
4
, is set to ‘1’ automatically. After issuing a Lock Password
0
command, the protection settings of the selected block are activated. The protection of
a locked block cannot be changed. A Lock Password command sent to a locked block
returns an error code.
The Lock Password command is also used to set the Protect Status areas of the
password blocks. RFU bit 8 of the Request_flag is used to select either the memory
area (bit 8 = ‘0’) or the password area (bit 8 = ‘1’).
● Present Password:
The Present Password command is used to present one of the three passwords to the
LRIS2K in order to modify the access rights of all the memory blocks linked to that
password (Ta bl e 5 ) including the password itself. If the presented password is correct,
the access rights remain activated until the tag is powered off or until a new Present
Password command is issued.
16/98 Doc ID 13888 Rev 9
LRIS2K Example of LRIS2K security protection
3 Example of LRIS2K security protection
Ta bl e 7 and Ta bl e 8 show the block security protections before and after a valid Present
Password command. The Ta bl e 7 shows blocks access rights of an LRIS2K after power-up.
After a valid Present Password command with password 1, the memory block access is
changed as given in Tab le 8 .
Table 7. LRIS2K block security protection after power-up
Protect status
Add
0781516232431b
0 Protection: Standard, Read - No Write xxx 00001
4Protection: Pswd 1, No Read - No Write xxx 01111
Table 8. LRIS2K block security protection after a valid presentation of password 1
Add
0781516232431b
0 Protection: Standard, Read - No Write xxx 00001
4 Protection: Pswd 1, Read - No Write xxx 01111
7b6b5b4b3b2b1b0
Protect status
7b6b5b4b3b2b1b0
Doc ID 13888 Rev 9 17/98
Communication signal from VCD to LRIS2K LRIS2K
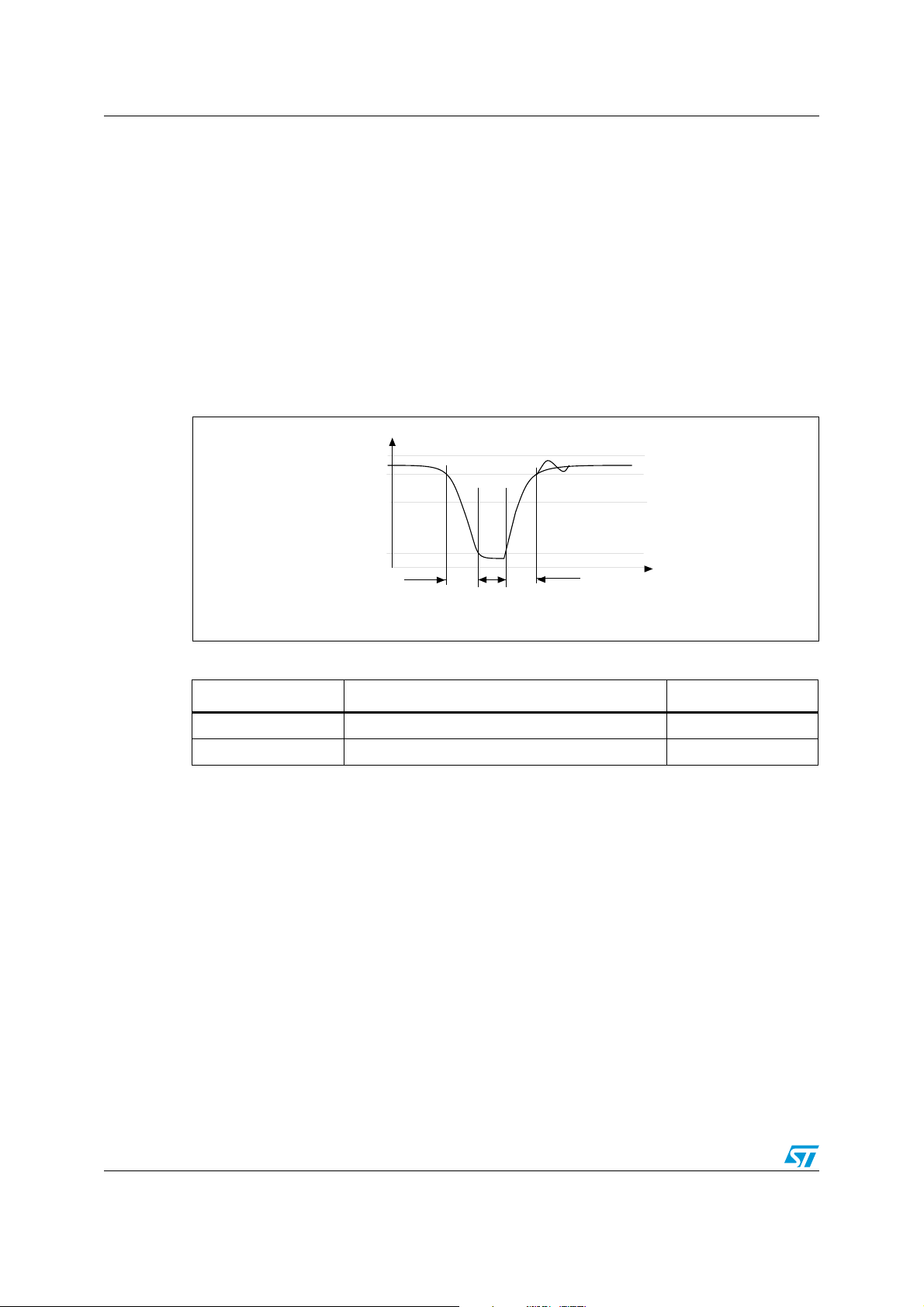
AI06683
tRFF
tRFSBL
tRFR
105%
a
t
100%
95%
60%
5%
4 Communication signal from VCD to LRIS2K
Communications between the VCD and the LRIS2K takes place using the modulation
principle of ASK (Amplitude Shift Keying). Two modulation indexes are used, 10% and
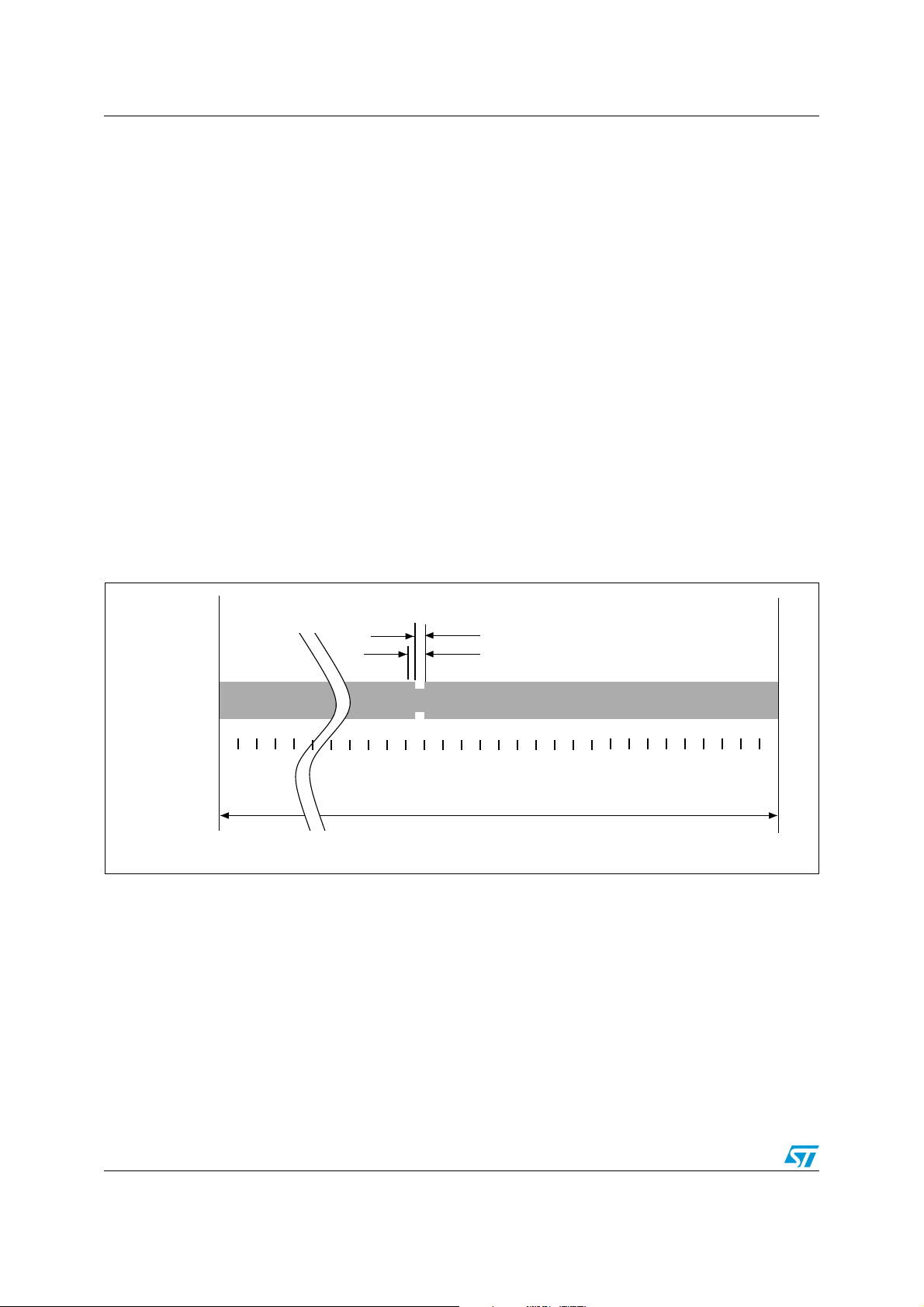
100%. The LRIS2K decodes both. The VCD determines which index is used.
The modulation index is defined as [a – b]/[a + b] where a is the peak signal amplitude and
b, the minimum signal amplitude of the carrier frequency.
Depending on the choice made by the VCD, a “pause” will be created as described in
Figure 2 and Figure 3.
The LRIS2K is operational for any degree of modulation index from between 10% and 30%.
Figure 2. 100% modulation waveform
Table 9. 10% modulation parameters
Symbol Parameter definition Value
hr 0.1 x (a – b) max
hf 0.1 x (a – b) max
18/98 Doc ID 13888 Rev 9
LRIS2K Communication signal from VCD to LRIS2K
AI06655
tRFF tRFSFL tRFR
hr
hf
ab t
Figure 3. 10% modulation waveform
Doc ID 13888 Rev 9 19/98
Data rate and data coding LRIS2K
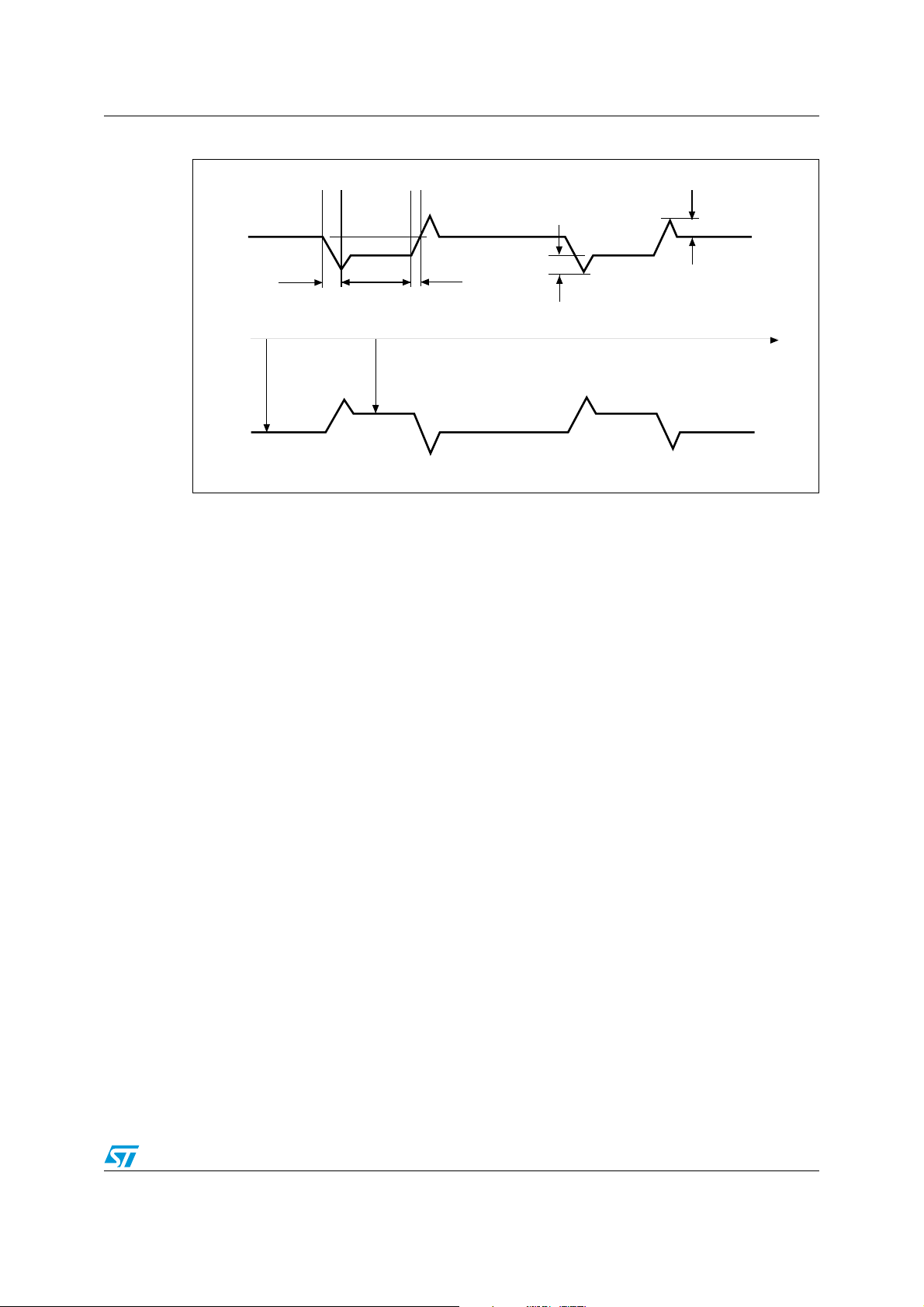
AI06656
0 1 2 3 . . . . . . . . 2 . . . . . . . . . . . . . . . . . . . . . 2 2 2 2
. . . . . . . . . 2 . . . . . . . . . . . . . . . . . . . . . 5 5 5 5
. . . . . . . . . 5 . . . . . . . . . . . . . . . . . . . . . 2 3 4 5
4.833 ms
18.88 µs
9.44 µs
Pulse
Modulated
Carrier
5 Data rate and data coding
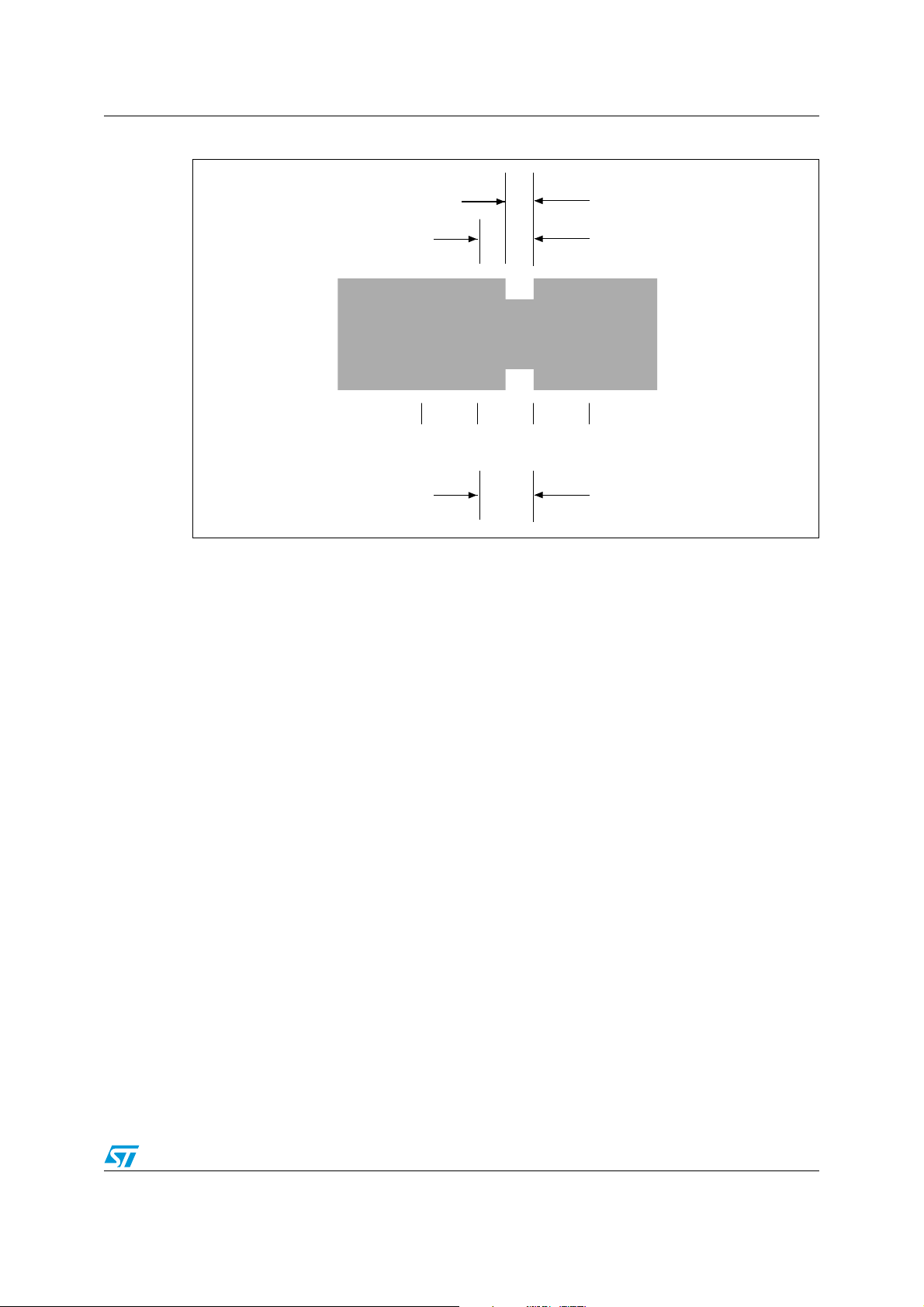
The data coding implemented in the LRIS2K uses pulse position modulation. Both data
coding modes that are described in the ISO15693 are supported by the LRIS2K. The
selection is made by the VCD and indicated to the LRIS2K within the start of frame (SOF).
5.1 Data coding mode: 1 out of 256
The value of one single byte is represented by the position of one pause. The position of the
pause on 1 of 256 successive time periods of 18.88 µs (256/f
byte. In this case the transmission of one byte takes 4.833 ms and the resulting data rate is
1.65 kbits/s (f
/8192).
C
Figure 4 illustrates this pulse position modulation technique. In this figure, data E1h (225
decimal) is sent by the VCD to the LRIS2K.
The pause occurs during the second half of the position of the time period that determines
the value, as shown in Figure 5.
A pause during the first period transmits the data value 00h. A pause during the last period
transmit the data value FFh (255 decimal).
), determines the value of the
C
Figure 4. 1 out of 256 coding mode
20/98 Doc ID 13888 Rev 9
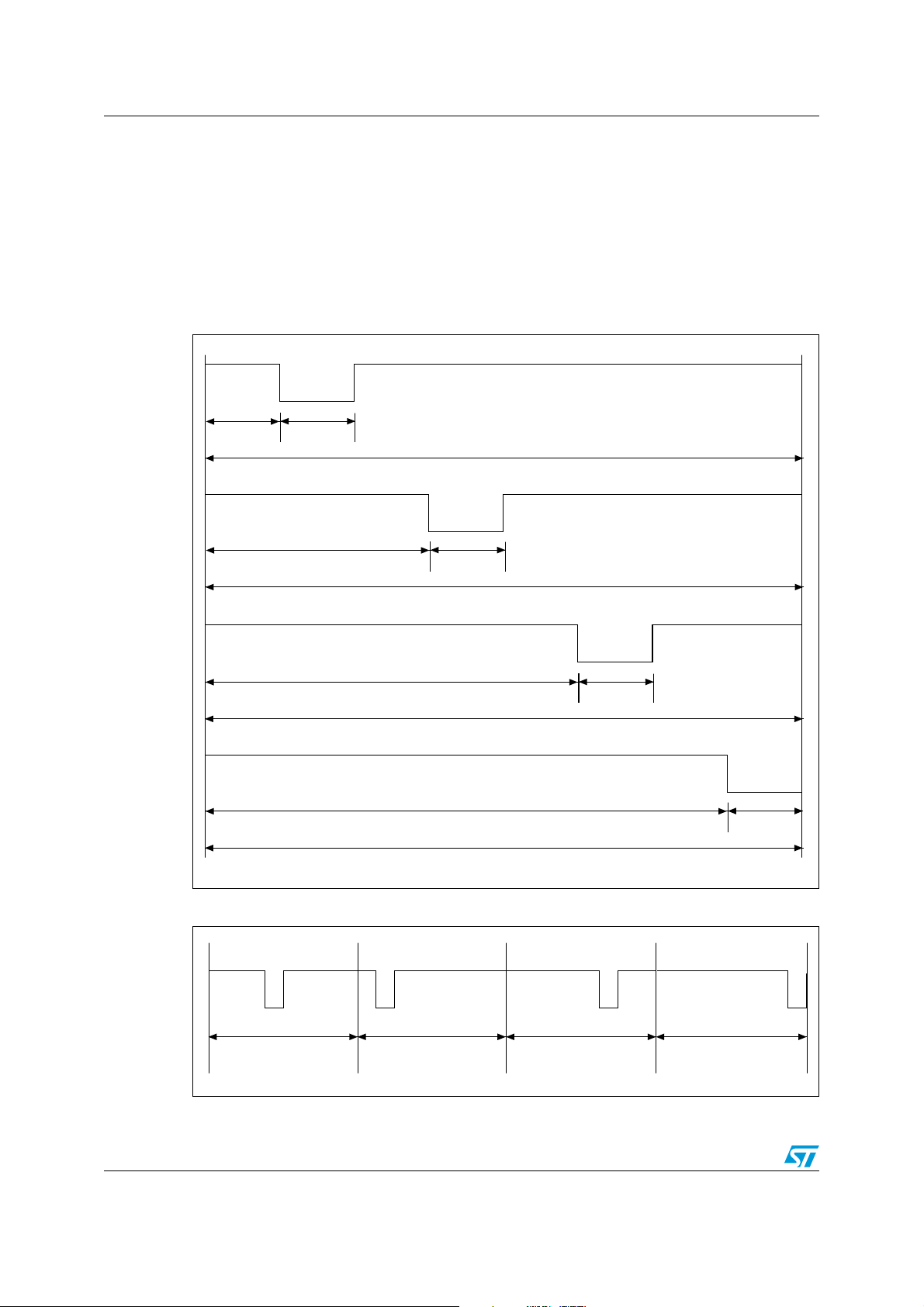
LRIS2K Data rate and data coding
AI06657
2
2
5
18.88 µs
9.44 µs
Pulse
Modulated
Carrier
2
2
6
2
2
4
. . . . . . .. . . . . . .
Time Period
one of 256
Figure 5. Detail of a time period
Doc ID 13888 Rev 9 21/98
Data rate and data coding LRIS2K
AI06658
9.44 µs 9.44 µs
75.52 µs
28.32 µs 9.44 µs
75.52 µs
47.20µs 9.44 µs
75.52 µs
66.08 µs 9.44 µs
75.52 µs
Pulse position for "00"
Pulse position for "11"
Pulse position for "10" (0=LSB)
Pulse position for "01" (1=LSB)
AI06659
75.52µs75.52µs 75.52µs 75.52µs
00
10
01 11
5.2 Data coding mode: 1 out of 4
The value of 2 bits is represented by the position of one pause. The position of the pause on
1 of 4 successive time periods of 18.88 µs (256/f
successive pairs of bits form a byte, where the least significant pair of bits is transmitted first.
In this case the transmission of one byte takes 302.08 µs and the resulting data rate is 26.48
Kbits/s (f
/512). Figure 6 illustrates the 1 out of 4 pulse position technique and coding.
C
Figure 7 shows the transmission of E1h (225d - 1110 0001b) by the VCD.
Figure 6. 1 out of 4 coding mode
), determines the value of the 2 bits. Four
C
22/98 Doc ID 13888 Rev 9
Figure 7. 1 out of 4 coding example
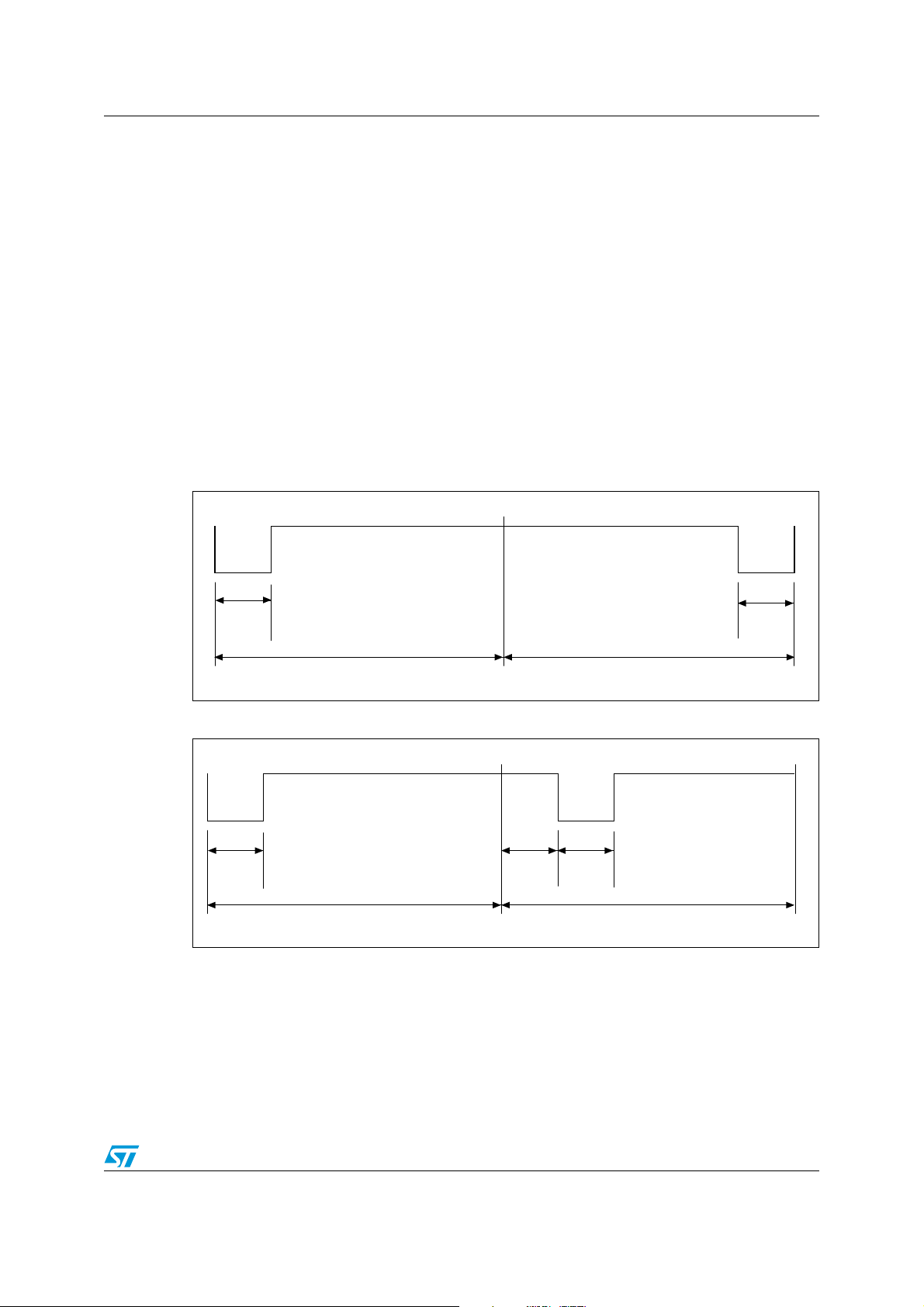
LRIS2K Data rate and data coding
AI06661
37.76µs
9.44µs
9.44µs
37.76µs
AI06660
37.76µs
9.44µs
9.44µs
37.76µs
9.44µs
5.3 VCD to LRIS2K frames
Frames are delimited by a start of frame (SOF) and an end of frame (EOF). They are
implemented using code violation. Unused options are reserved for future use.
The LRIS2K is ready to receive a new command frame from the VCD 311.5 µs (t
sending a response frame to the VCD.
The LRIS2K takes a power-up time of 0.1 ms after being activated by the powering field.
After this delay, the LRIS2K is ready to receive a command frame from the VCD.
5.4 Start of frame (SOF)
The SOF defines the data coding mode the VCD is to use for the following command frame.
The SOF sequence described in Figure 8 selects the 1 out of 256 data coding mode. The
SOF sequence described in Figure 9 selects the 1 out of 4 data coding mode. The EOF
sequence for either coding mode is described in Figure 10.
Figure 8. SOF to select 1 out of 256 data coding mode
) after
2
Figure 9. SOF to select 1 out of 4 data coding mode
Doc ID 13888 Rev 9 23/98
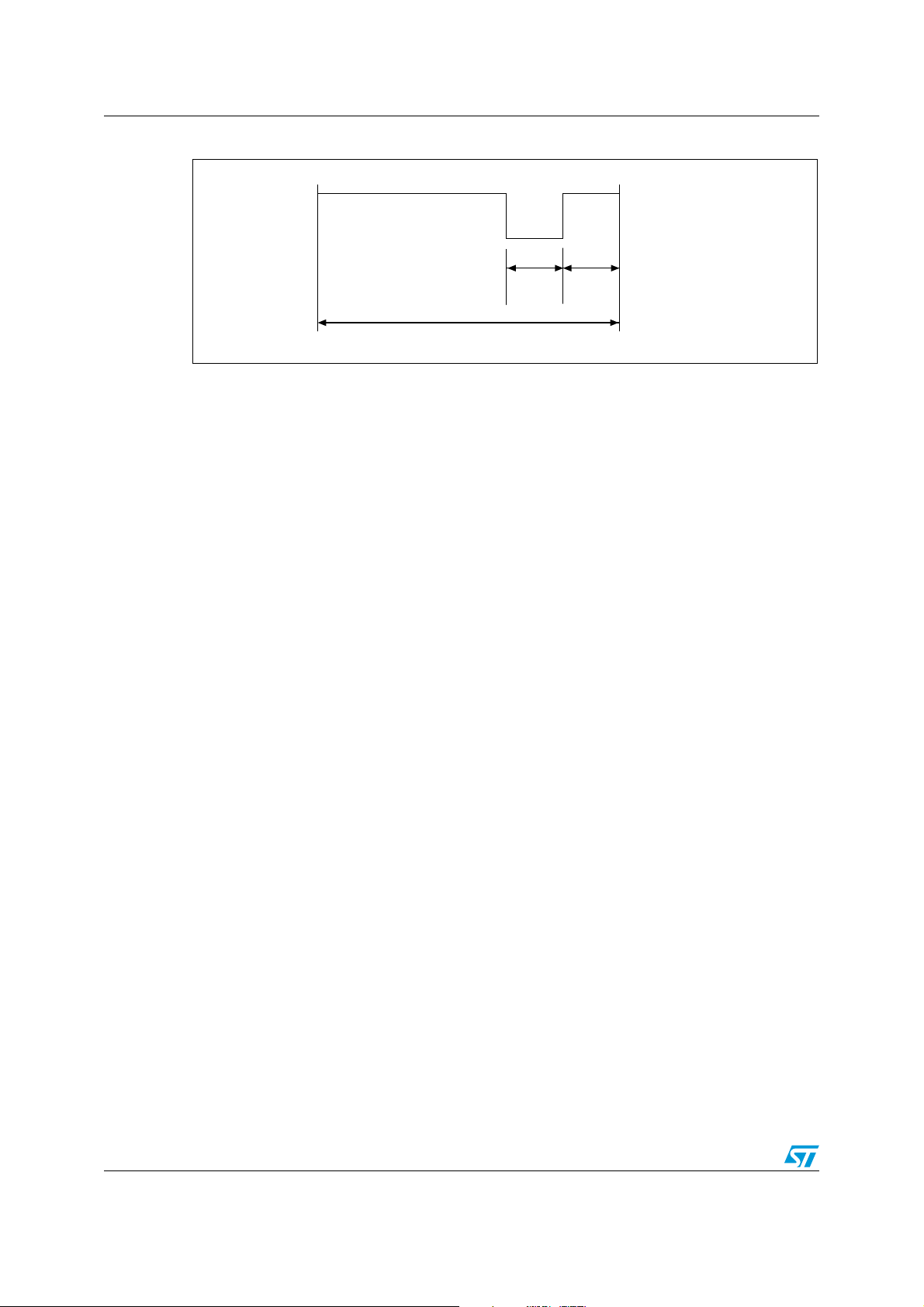
Data rate and data coding LRIS2K
AI06662
9.44µs
37.76µs
9.44µs
Figure 10. EOF for either data coding mode
24/98 Doc ID 13888 Rev 9
LRIS2K Communications signal from LRIS2K to VCD
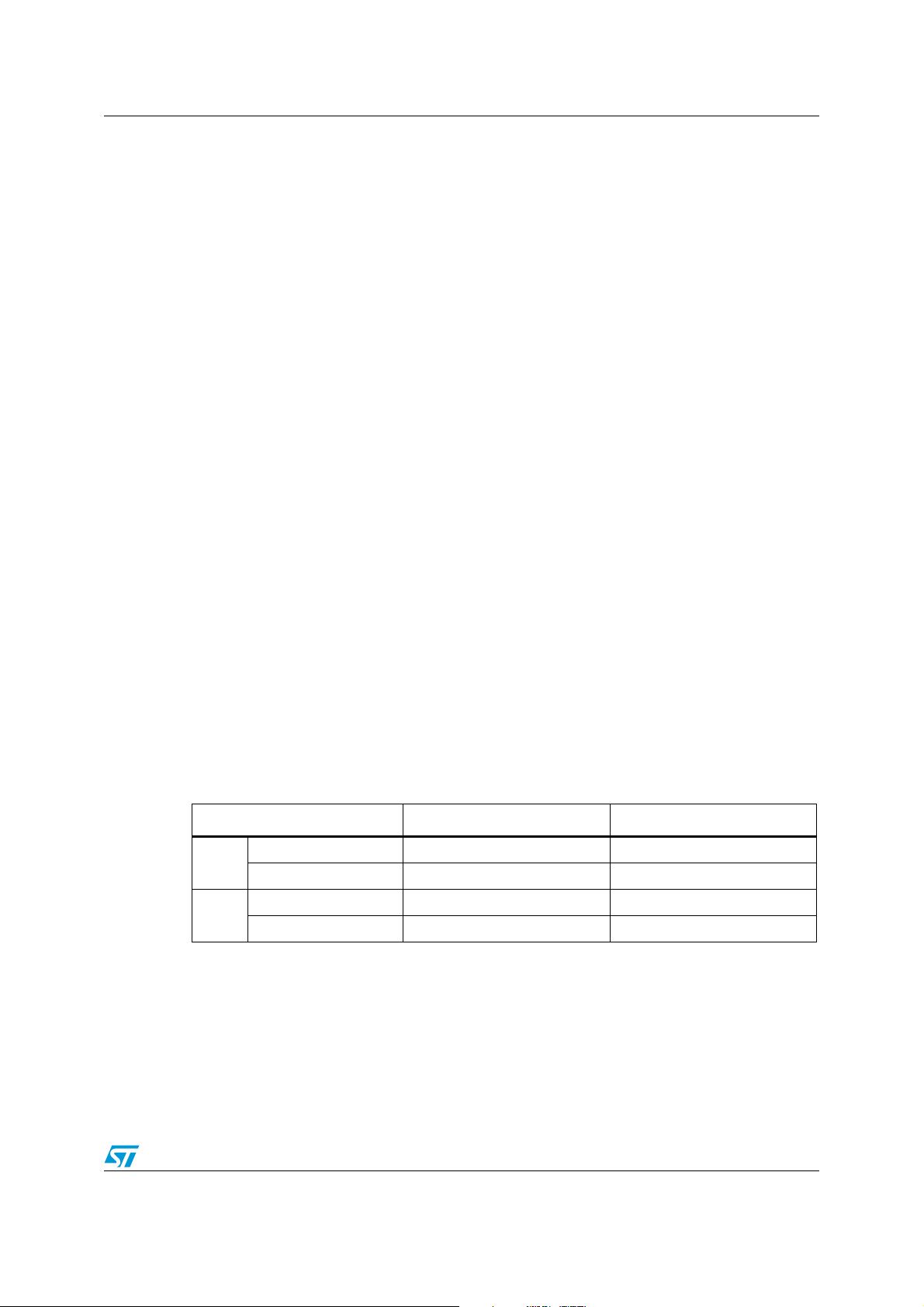
6 Communications signal from LRIS2K to VCD
The LRIS2K has several modes defined for some parameters, owing to which it can operate
in different noise environments and meet different application requirements.
6.1 Load modulation
The LRIS2K is capable of communication to the VCD via an inductive coupling area
whereby the carrier is loaded to generate a subcarrier with frequency f
generated by switching a load in the LRIS2K.
The load-modulated amplitude received on the VCD antenna must be of at least 10mV
when measured as described in the test methods defined in International Standard
ISO10373-7.
6.2 Subcarrier
The LRIS2K supports the one-subcarrier and two-subcarrier response formats. These
formats are selected by the VCD using the first bit in the protocol header. When one
subcarrier is used, the frequency f
When two subcarriers are used, the frequency f
is 484.28 kHz (f
continuous phase relationship between f
of the subcarrier load modulation is 423.75 kHz (fC/32).
S1
/28). When using the two-subcarrier mode, the LRIS2K generates a
C
and fS2.
S1
is 423.75 kHz (fC/32), and frequency fS2
S1
. The subcarrier is
S
6.3 Data rates
The LRIS2K can respond using the low or the high data rate format. The selection of the
data rate is made by the VCD using the second bit in the protocol header. It also supports
the x2 mode available on all the Fast commands. Tab le 1 0 shows the different data rates
produced by the LRIS2K using the different response format combinations.
Table 10. Response data rates
Data rate One subcarrier Two subcarriers
Standard commands 6.62 Kbits/s (f
Low
Fast commands 13.24 Kbits/s (f
Standard commands 26.48 Kbits/s (f
High
Fast commands 52.97 Kbits/s (f
/2048) 6.67 Kbits/s (fc/2032)
c
/1024) not applicable
c
/512) 26.69 Kbits/s (fc/508)
c
/256) not applicable
c
Doc ID 13888 Rev 9 25/98
Bit representation and coding LRIS2K
37.76µs
ai12076
18.88µs
ai12066
37.76µs
ai12077
18.88µs
ai12067
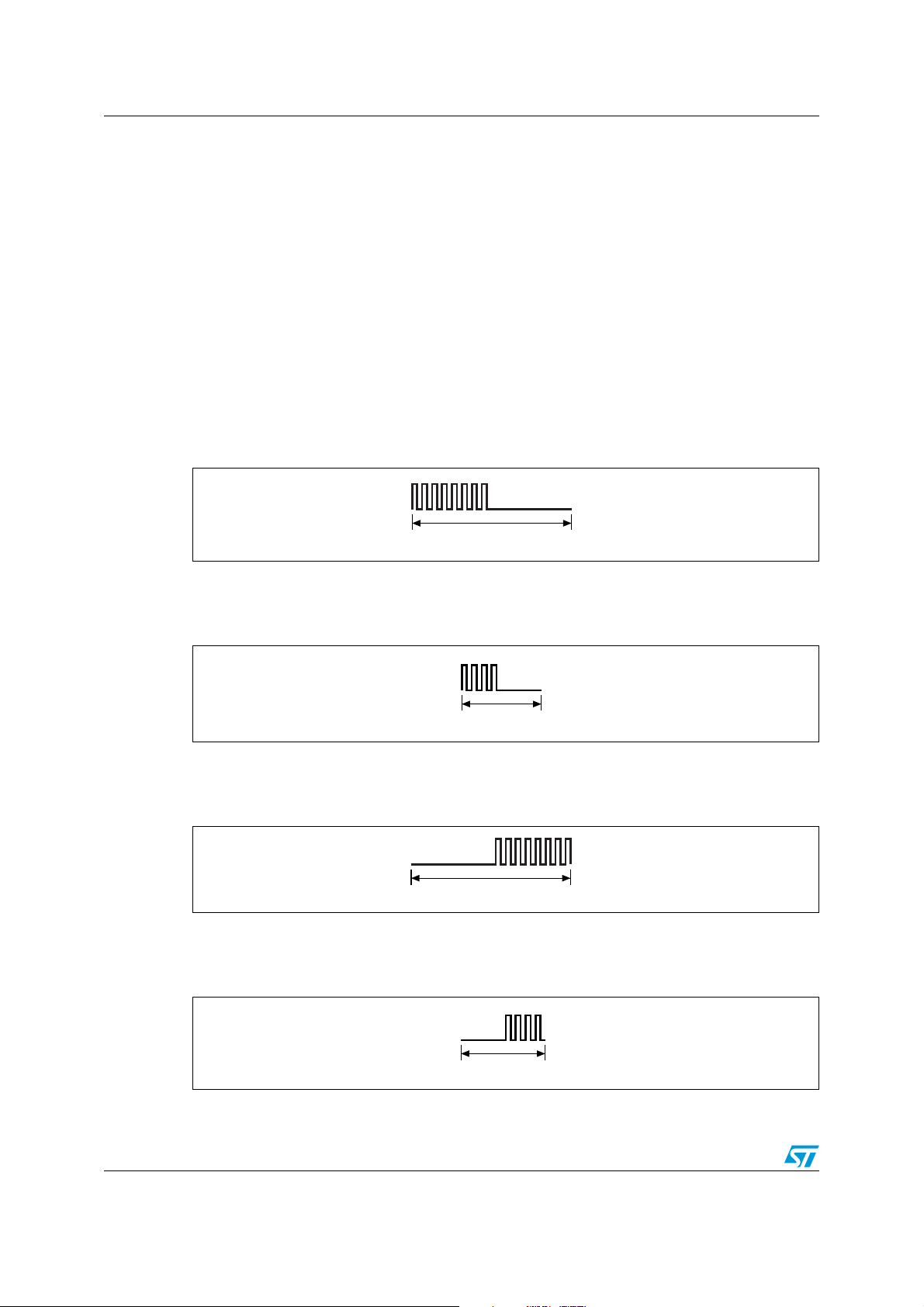
7 Bit representation and coding
Data bits are encoded using Manchester coding, according to the following schemes. For
the low data rate, same subcarrier frequency or frequencies is/are used, in this case the
number of pulses is multiplied by 4 and all times will increase by this factor. For the Fast
commands using one subcarrier, all pulse numbers and times are divided by 2.
7.1 Bit coding using one subcarrier
7.1.1 High data rate
A logic 0 starts with 8 pulses at 423.75 kHz (fC/32) followed by an unmodulated time of
18.88 µs as shown in Figure 11.
Figure 11. Logic 0, high data rate
For the fast commands, a logic 0 starts with 4 pulses at 423.75 kHz (f
/32) followed by an
C
unmodulated time of 9.44 µs as shown in Figure 12.
Figure 12. Logic 0, high data rate x2
A logic 1 starts with an unmodulated time of 18.88 µs followed by 8 pulses at 423.75 kHz
/32) as shown in Figure 13.
(f
C
Figure 13. Logic 1, high data rate
For the Fast commands, a logic 1 starts with an unmodulated time of 9.44 µs followed by 4
pulses of 423.75 kHz (f
/32) as shown in Figure 14.
C
Figure 14. Logic 1, high data rate x2
26/98 Doc ID 13888 Rev 9
LRIS2K Bit representation and coding
151.04µs
ai12068
75.52µs
ai12069
151.04µs
ai12070
75.52µs
ai12071
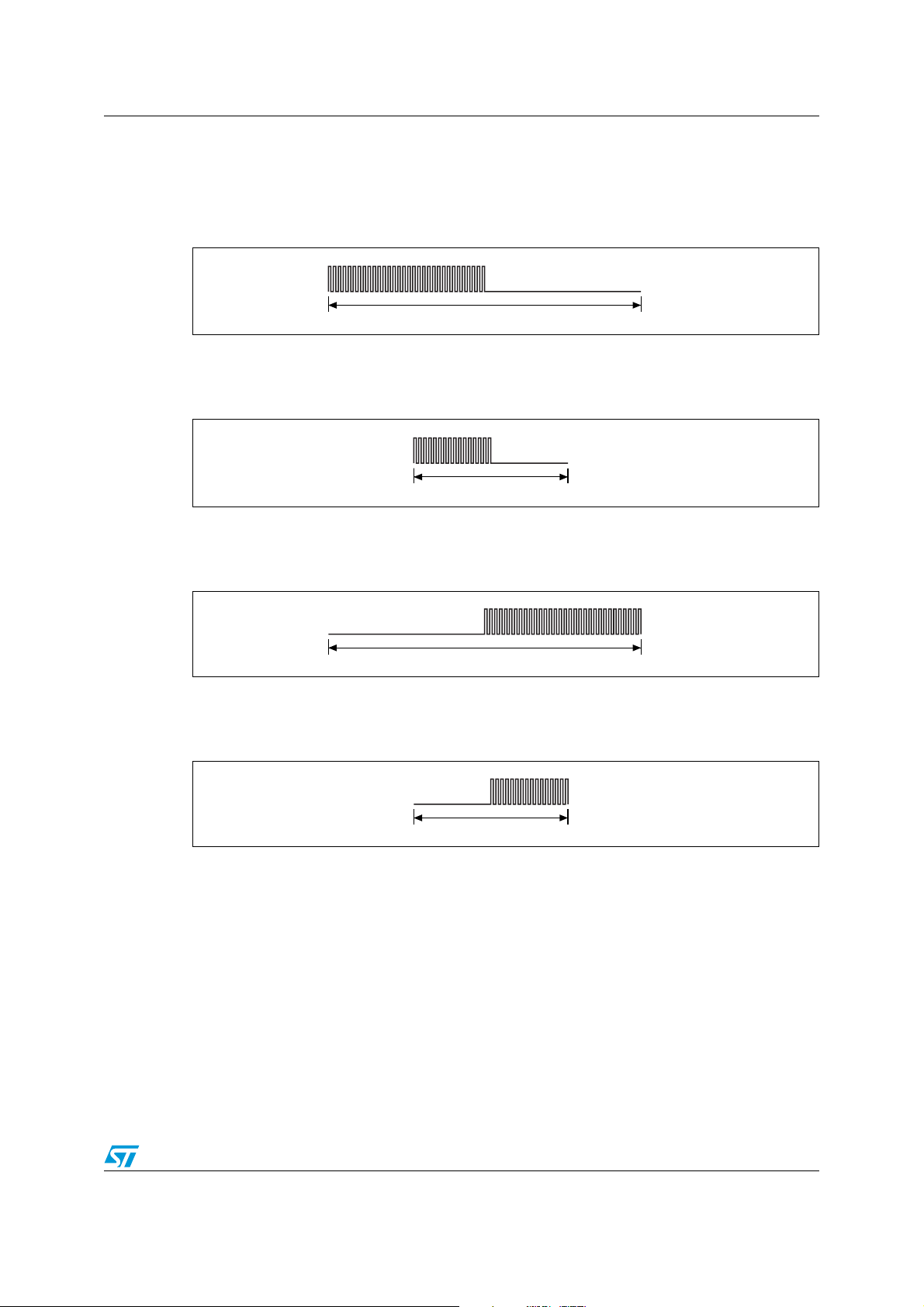
7.1.2 Low data rate
A logic 0 starts with 32 pulses at 423.75 kHz (fC/32) followed by an unmodulated time of
75.52 µs as shown in Figure 15.
Figure 15. Logic 0, low data rate
For the Fast commands, a logic 0 starts with 16 pulses at 423.75 kHz (f
/32) followed by an
C
unmodulated time of 37.76 µs as shown in Figure 16.
Figure 16. Logic 0, low data rate x2
A logic 1 starts with an unmodulated time of 75.52 µs followed by 32 pulses at 423.75 kHz
/32) as shown in Figure 17.
(f
C
Figure 17. Logic 1, low data rate
For the Fast commands, a logic 1 starts with an unmodulated time of 37.76 µs followed by
16 pulses at 423.75 kHz (f
/32) as shown in Figure 17.
C
Figure 18. Logic 1, low data rate x2
Doc ID 13888 Rev 9 27/98
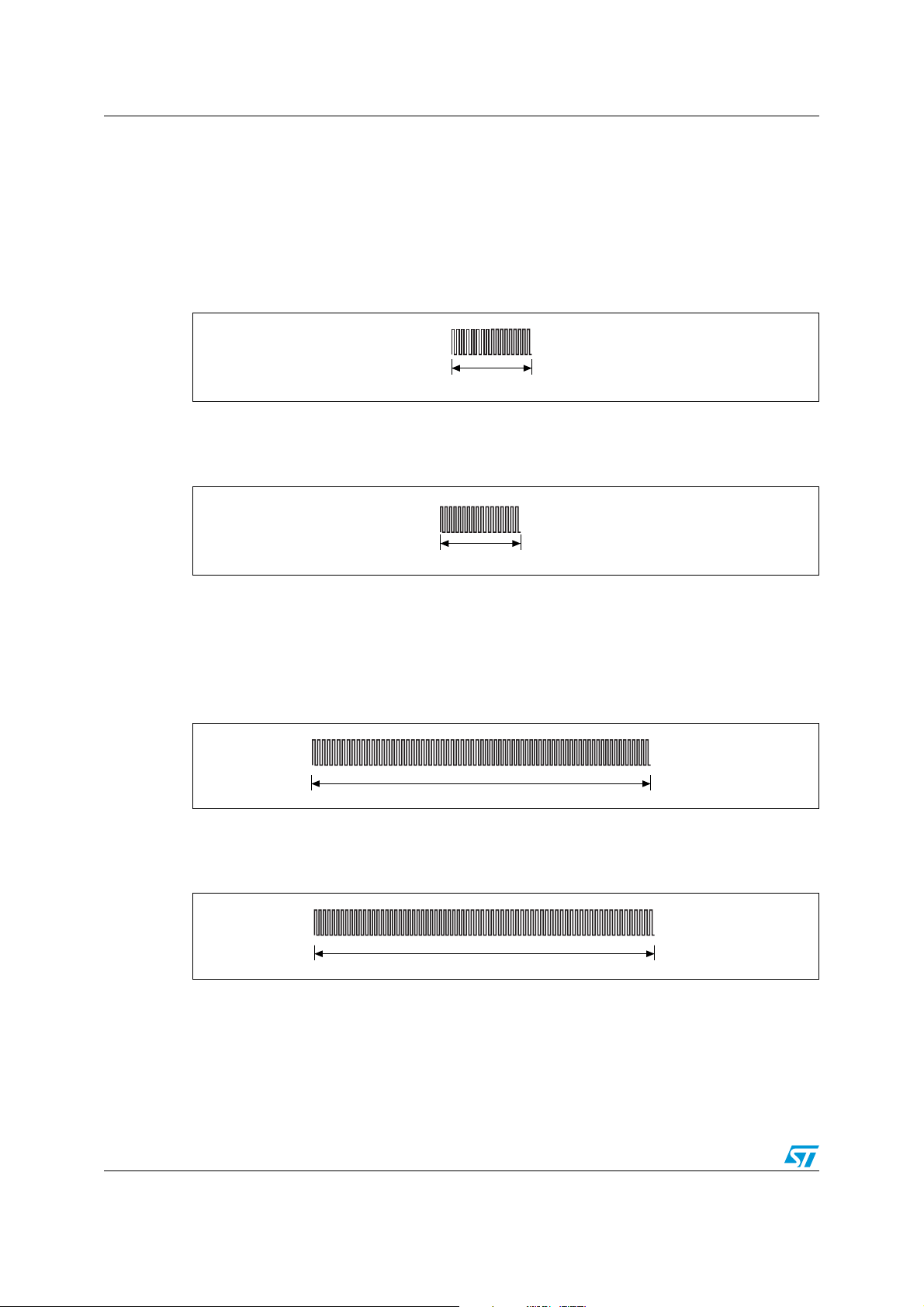
Bit representation and coding LRIS2K
37.46µs
ai12074
37.46µs
ai12073
149.84µs
ai12072
149.84µs
ai12075
7.2 Bit coding using two subcarriers
7.3 High data rate
A logic 0 starts with 8 pulses at 423.75 kHz (fC/32) followed by 9 pulses at 484.28 kHz
/28) as shown in Figure 19. For the Fast commands, the x2 mode is not available.
(f
C
Figure 19. Logic 0, high data rate
A logic 1 starts with 9 pulses at 484.28 kHz (f
/32) as shown in Figure 20. For the Fast commands, the x2 mode is not available.
(f
C
Figure 20. Logic 1, high data rate
7.4 Low data rate
A logic 0 starts with 32 pulses at 423.75 kHz (fC/32) followed by 36 pulses at 484.28 kHz
/28) as shown in Figure 21. For the Fast commands, the x2 mode is not available.
(f
C
Figure 21. Logic 0, low data rate
A logic 1 starts with 36 pulses at 484.28 kHz (f
/32) as shown in Figure 22. For the Fast commands, the x2 mode is not available.
(f
C
/28) followed by 8 pulses at 423.75 kHz
C
/28) followed by 32 pulses at 423.75 kHz
C
Figure 22. Logic 1, low data rate
28/98 Doc ID 13888 Rev 9
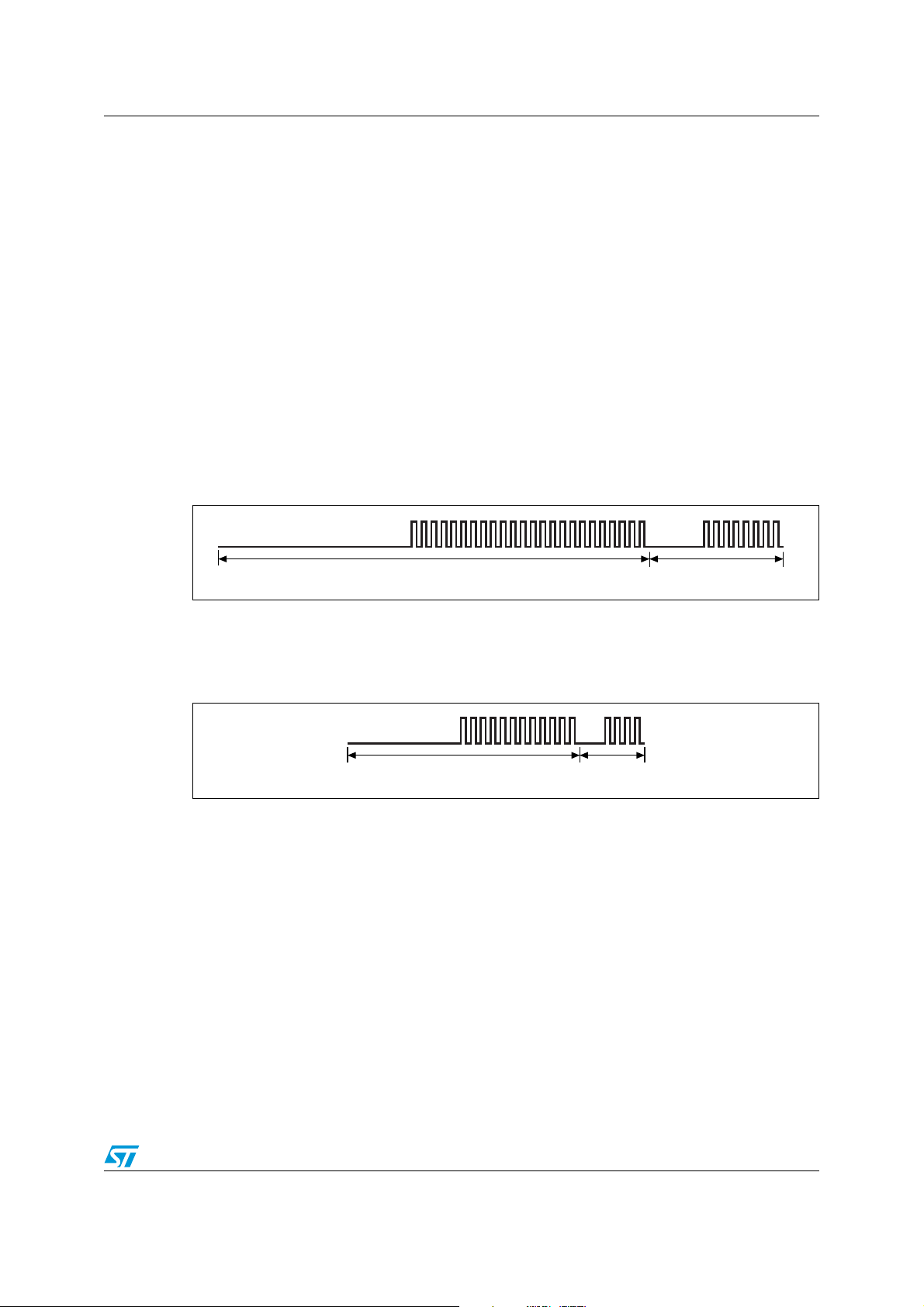
LRIS2K LRIS2K to VCD frames
113.28µs
ai12078
37.76µs
56.64µs
ai12079
18.88µs
8 LRIS2K to VCD frames
Frames are delimited by an SOF and an EOF. They are implemented using code violation.
Unused options are reserved for future use. For the low data rate, the same subcarrier
frequency or frequencies is/are used. In this case the number of pulses is multiplied by 4.
For the Fast commands using one subcarrier, all pulse numbers and times are divided by 2.
8.1 SOF when using one subcarrier
8.2 High data rate
The SOF includes an unmodulated time of 56.64 µs, followed by 24 pulses at 423.75 kHz
/32), and a logic 1 that consists of an unmodulated time of 18.88 µs followed by 8 pulses
(f
C
at 423.75 kHz as shown in Figure 23.
Figure 23. Start of frame, high data rate, one subcarrier
For the Fast commands, the SOF comprises an unmodulated time of 28.32 µs, followed by
12 pulses at 423.75 kHz (f
/32), and a logic 1 that consists of an unmodulated time of
C
9.44µs followed by 4 pulses at 423.75 kHz as shown in Figure 24.
Figure 24. Start of frame, high data rate, one subcarrier x2
Doc ID 13888 Rev 9 29/98
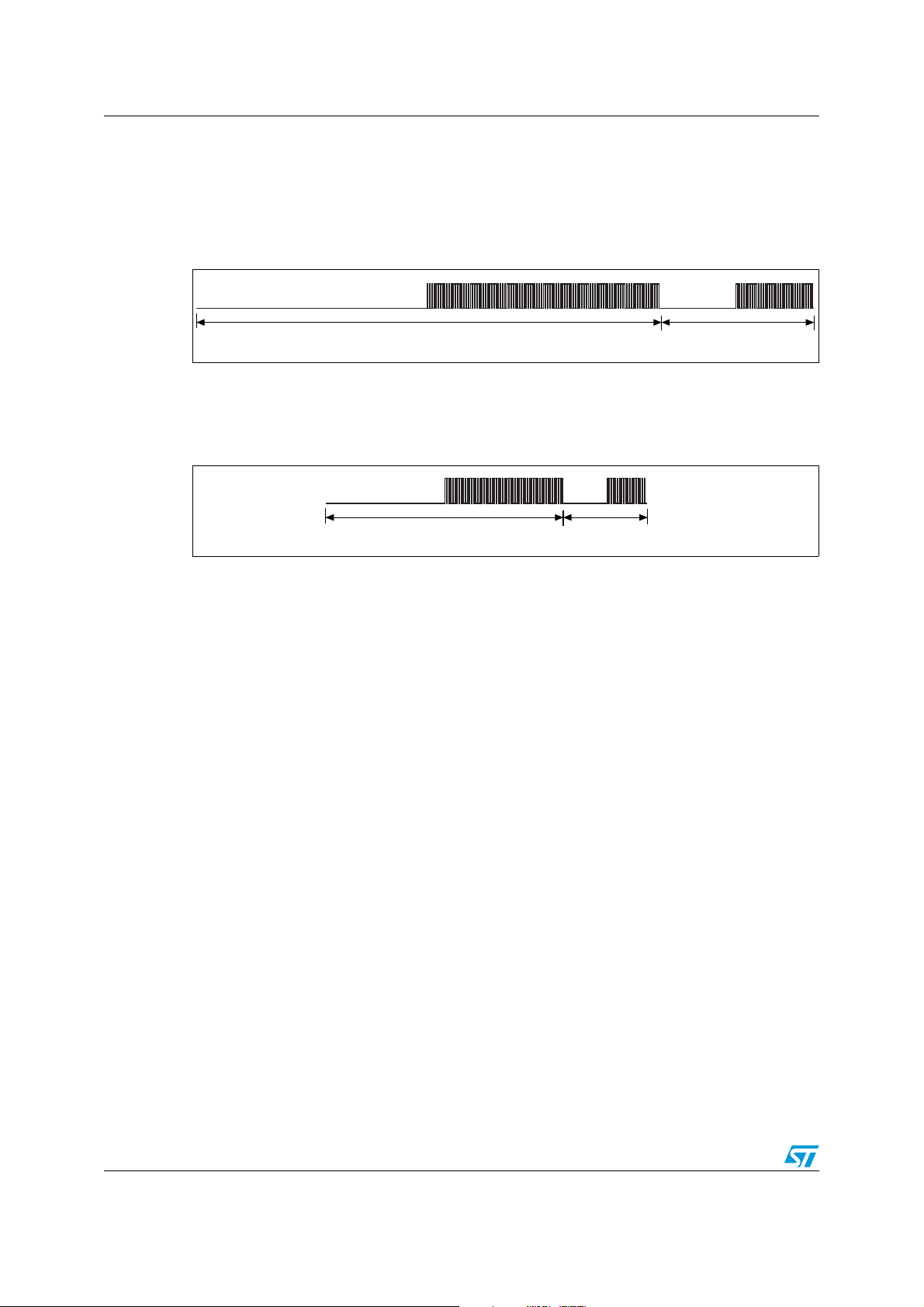
LRIS2K to VCD frames LRIS2K
453.12µs
ai12080
151.04µs
226.56µs
ai12081
75.52µs
8.3 Low data rate
The SOF comprises an unmodulated time of 226.56 µs, followed by 96 pulses at 423.75 kHz
/32), and a logic 1 that consists of an unmodulated time of 75.52 µs followed by 32 pulses
(f
C
at 423.75 kHz as shown in Figure 25.
Figure 25. Start of frame, low data rate, one subcarrier
For the Fast commands, the SOF comprises an unmodulated time of 113.28 µs, followed by
48 pulses at 423.75 kHz (f
followed by 16 pulses at 423.75 kHz as shown in Figure 26.
Figure 26. Start of frame, low data rate, one subcarrier x2
/32), and a logic 1 that includes an unmodulated time of 37.76 µs
C
30/98 Doc ID 13888 Rev 9

LRIS2K LRIS2K to VCD frames
112.39µs
ai12082
37.46µs
449.56µs
ai12083
149.84µs
8.4 SOF when using two subcarriers
8.5 High data rate
The SOF comprises 27 pulses at 484.28 kHz (fC/28), followed by 24 pulses at 423.75 kHz
/32), and a logic 1 that includes 9 pulses at 484.28 kHz followed by 8 pulses at
(f
C
423.75 kHz as shown in Figure 27.
For the Fast commands, the x2 mode is not available.
Figure 27. Start of frame, high data rate, two subcarriers
8.6 Low data rate
The SOF comprises 108 pulses at 484.28 kHz (fC/28), followed by 96 pulses at 423.75 kHz
/32), and a logic 1 that includes 36 pulses at 484.28 kHz followed by 32 pulses at
(f
C
423.75 kHz as shown in Figure 28.
For the Fast commands, the x2 mode is not available.
Figure 28. Start of frame, low data rate, two subcarriers
Doc ID 13888 Rev 9 31/98

LRIS2K to VCD frames LRIS2K
113.28µs
ai12084
37.76µs
56.64µs
ai12085
18.88µs
453.12µs
ai12086
151.04µs
226.56µs
ai12087
75.52µs
8.7 EOF when using one subcarrier
8.8 High data rate
The EOF comprises a logic 0 that includes 8 pulses at 423.75 kHz and an unmodulated time
of 18.88 µs, followed by 24 pulses at 423.75 kHz (f
56.64 µs as shown in Figure 29.
Figure 29. End of frame, high data rate, one subcarriers
For the Fast commands, the EOF comprises a logic 0 that includes 4 pulses at 423.75 kHz
and an unmodulated time of 9.44 µs, followed by 12 pulses at 423.75 kHz (f
unmodulated time of 37.76 µs as shown in Figure 30.
Figure 30. End of frame, high data rate, one subcarriers x2
/32), and by an unmodulated time of
C
/32) and an
C
8.9 Low data rate
The EOF comprises a logic 0 that includes 32 pulses at 423.75 kHz and an unmodulated
time of 75.52 µs, followed by 96 pulses at 423.75 kHz (f
226.56 µs as shown in Figure 31.
Figure 31. End of frame, low data rate, one subcarriers
For the Fast commands, the EOF comprises a logic 0 that includes 16 pulses at 423.75 kHz
and an unmodulated time of 37.76 µs, followed by 48 pulses at 423.75 kHz (f
unmodulated time of 113.28 µs as shown in Figure 32.
Figure 32. End of frame, low data rate, one subcarriers x2
/32) and an unmodulated time of
C
/32) and an
C
32/98 Doc ID 13888 Rev 9

LRIS2K LRIS2K to VCD frames
112.39µs
ai12088
37.46µs
449.56µs
ai12089
149.84µs
8.10 EOF when using two subcarriers
8.11 High data rate
The EOF comprises a logic 0 that includes 8 pulses at 423.75 kHz and 9 pulses at
484.28 kHz, followed by 24 pulses at 423.75 kHz (f
/28) as shown in Figure 33.
(f
C
/32) and 27 pulses at 484.28 kHz
C
For the Fast commands, the x2 mode is not available.
Figure 33. End of frame, high data rate, two subcarriers
8.12 Low data rate
The EOF comprises a logic 0 that includes 32 pulses at 423.75 kHz and 36 pulses at
484.28 kHz, followed by 96 pulses at 423.75 kHz (f
/28) as shown in Figure 34.
(f
C
For the Fast commands, the x2 mode is not available.
/32) and 108 pulses at 484.28 kHz
C
Figure 34. End of frame, low data rate, two subcarriers
Doc ID 13888 Rev 9 33/98

Unique identifier (UID) LRIS2K
9 Unique identifier (UID)
The LRIS2Ks are uniquely identified by a 64-bit Unique Identifier (UID). This UID complies
with ISO/IEC 15963 and ISO/IEC 7816-6. The UID is a read-only code and comprises:
● 8 MSBs with a value of E0h
● The IC Manufacturer code of ST 02h, on 8 bits (ISO/IEC 7816-6/AM1)
● a Unique Serial Number on 48 bits
Table 11. UID format
MSB LSB
63 56 55 48 47 0
0xE0 0x02 Unique serial number
With the UID each LRIS2K can be addressed uniquely and individually during the
anticollision loop and for one-to-one exchanges between a VCD and an LRIS2K.
34/98 Doc ID 13888 Rev 9

LRIS2K Application family identifier (AFI)
AI13238
Inventory Request
Received
No
No Answer
Yes
No
AFI value
= 0 ?
Yes
No
AFI Flag
Set ?
Yes
Answer given by the LRIS2K
to the Inventory Request
AFI value
= Internal
value ?
10 Application family identifier (AFI)
The AFI (application family identifier) represents the type of application targeted by the VCD
and is used to identify, among all the LRIS2Ks present, only the LRIS2Ks that meet the
required application criteria.
Figure 35. LRIS2K decision tree for AFI
The AFI is programmed by the LRIS2K issuer (or purchaser) in the AFI register. Once
programmed and Locked, it can no longer be modified.
The most significant nibble of the AFI is used to code one specific or all application families.
The least significant nibble of the AFI is used to code one specific or all application
subfamilies. Subfamily codes different from 0 are proprietary.
(See ISO 15693-3 documentation)
Doc ID 13888 Rev 9 35/98

Data storage format identifier (DSFID) LRIS2K
11 Data storage format identifier (DSFID)
The data storage format identifier indicates how the data is structured in the LRIS2K
memory. The logical organization of data can be known instantly using the DSFID.
It can be programmed and locked using the Write DSFID and Lock DSFID commands.
11.1 CRC
The CRC used in the LRIS2K is calculated as per the definition in ISO/IEC 13239.
The initial register contents are all ones: FFFFh.
The two-byte CRC are appended to each request and response, within each frame, before
the EOF. The CRC is calculated on all the bytes after the SOF up to the CRC field.
Upon reception of a request from the VCD, the LRIS2K verifies that the CRC value is valid.
If it is invalid, the LRIS2K discards the frame and does not answer to the VCD.
Upon reception of a request from the LRIS2K, it is recommended that the VCD verifies
whether the CRC value is valid. If it is invalid, actions to be performed are left to the
discretion of the VCD designer.
The CRC is transmitted least significant byte first.
Each byte is transmitted least significant bit first.
Table 12. CRC transmission rules
LSByte MSByte
LSBit MSBit LSBit MSBit
CRC 16 (8 bits) CRC 16 (8 bits)
36/98 Doc ID 13888 Rev 9

LRIS2K LRIS2K protocol description
12 LRIS2K protocol description
The Transmission protocol (or simply protocol) defines the mechanism used to exchange
instructions and data between the VCD and the LRIS2K, in both directions. It is based on
the concept of “VCD talks first”.
This means that an LRIS2K will not start transmitting unless it has received and properly
decoded an instruction sent by the VCD. The protocol is based on an exchange of:
● a request from the VCD to the LRIS2K
● a response from the LRIS2K to the VCD
Each request and each request are contained in a frame. The frame delimiters (SOF, EOF)
are described in Section 8: LRIS2K to VCD frames.
Each request consists of:
● a request SOF (see Figure 8 and Figure 9)
● flags
● a command code
● parameters, depending on the command
● application data
● a 2-byte CRC
● a request EOF (see Figure 10)
Each request consists of:
● an Answer SOF (see Figure 23 to Figure 28)
● flags
● parameters, depending on the command
● application data
● a 2-byte CRC
● an Answer EOF (see Figure 29 to Figure 34)
The protocol is bit-oriented. The number of bits transmitted in a frame is a multiple of eight
(8), i.e. an integer number of bytes.
A single-byte field is transmitted least significant bit (LSBit) first. A multiple-byte field is
transmitted least significant byte (LSByte) first, each byte is transmitted least significant bit
(LSBit) first.
The setting of the flags indicates the presence of the optional fields. When the flag is set (to
one), the field is present. When the flag is reset (to zero), the field is absent.
Table 13. VCD request frame format
Request SOF Request_flags
Table 14. LRIS2K response frame format
Response
SOF
Response
_flags
Command
code
Parameters Data 2-byte CRC
Parameters Data 2-byte CRC
Request
EOF
Response
EOF
Doc ID 13888 Rev 9 37/98

LRIS2K protocol description LRIS2K
Figure 36. LRIS2K protocol timing
Request
VCD
frame
(Ta bl e 1 3 )
LRIS2K
Timing t
1
Response
frame
(Ta bl e 1 4 )
t
2
Request
frame
(Ta bl e 1 3 )
t
1
Response
frame
(Ta bl e 1 4)
t
2
38/98 Doc ID 13888 Rev 9

LRIS2K LRIS2K states
13 LRIS2K states
An LRIS2K can be in one of 4 states:
● Power-off
● Ready
● Quiet
● Selected
Transitions between these states are specified in Figure 37: LRIS2K state transition diagram
and Table 15: LRIS2K response depending on Request_flags.
13.1 Power-off state
The LRIS2K is in the Power-off state when it does not receive enough energy from the VCD.
13.2 Ready state
The LRIS2K is in the Ready state when it receives enough energy from the VCD. When in
the Ready state, the LRIS2K answers any request where the Select_flag is not set.
13.3 Quiet state
When in the Quiet state, the LRIS2K answers any request except for Inventory requests with
the Address_flag set.
13.4 Selected state
In the Selected state, the LRIS2K answers any request in all modes (see Section 14:
Modes):
● request in Select mode with the Select_flag set
● request in Addressed mode if the UID matches
● request in Non-Addressed mode as it is the mode for general requests
Doc ID 13888 Rev 9 39/98

LRIS2K states LRIS2K
AI06681
Power Off
In field
Out of field
Ready
Quiet
Selected
Any other Command
where Select_Flag
is not set
Out of field
Out of field
Stay quiet(UID)
Select (UID)
Any other command
Any other command where the
Address_Flag is set AND
where Inventory_Flag is not set
Stay quiet(UID)
Select (UID)
Reset to ready where
Select_Flag is set or
Select(different UID)
Reset to ready
Table 15. LRIS2K response depending on Request_flags
Address_flag Select_flag
Flags
1
Addressed0Non addressed
1
Selected0Non selected
LRIS2K in Ready or Selected state
(Devices in Quiet state do not
XX
answer)
LRIS2K in Selected state X X
LRIS2K in Ready, Quiet or
Selected state (the device which
XX
matches the UID)
Error (03h) X X
Figure 37. LRIS2K state transition diagram
40/98 Doc ID 13888 Rev 9
1. The intention of the state transition method is that only one LRIS2K should be in the selected state at a
time.

LRIS2K Modes
14 Modes
The term “mode” refers to the mechanism used in a request to specify the set of LRIS2Ks
that will answer the request.
14.1 Addressed mode
When the Address_flag is set to 1 (Addressed mode), the request contains the Unique ID
(UID) of the addressed LRIS2K.
Any LRIS2K that receives a request with the Address_flag set to 1 compares the received
Unique ID to its own. If it matches, then the LRIS2K executes the request (if possible) and
returns a request to the VCD as specified in the command description.
If the UID does not match, then it remains silent.
14.2 Non-addressed mode (general request)
When the Address_flag is cleared to 0 (Non-Addressed mode), the request does not contain
a Unique ID. Any LRIS2K receiving a request with the Address_flag cleared to 0 executes it
and returns a request to the VCD as specified in the command description.
14.3 Select mode
When the Select_flag is set to 1 (Select mode), the request does not contain an LRIS2K
Unique ID. The LRIS2K in the Selected state that receives a request with the Select_flag set
to 1 executes it and returns a request to the VCD as specified in the command description.
Only LRIS2Ks in the Selected state answer a request where the Select_flag set to 1.
The system design ensures in theory that only one LRIS2K can be in the Select state at a
time.
Doc ID 13888 Rev 9 41/98

Request format LRIS2K
15 Request format
The request consists of:
● an SOF
● flags
● a command code
● parameters and data
● a CRC
● an EOF
Table 16. General request format
S
OFRequest_flags Command code Parameters Data CRCEO
F
15.1 Request_flags
In a request, the “flags” field specifies the actions to be performed by the LRIS2K and
whether corresponding fields are present or not.
The flag field consists of eight bits.
The bit 3 (Inventory_flag) of the request_flag defines the contents of the 4 MSBs (bits 5 to
8).
When bit 3 is reset (0), bits 5 to 8 define the LRIS2K selection criteria.
When bit 3 is set (1), bits 5 to 8 define the LRIS2K Inventory parameters.
Table 17. Definition of request_flags 1 to 4
Bit No Flag Level Description
Bit 1 Subcarrier_flag
Bit 2 Data_rate_flag
(1)
(2)
Bit 3 Inventory_flag
Bit 4 Protocol Extension_flag 0 No Protocol format extension
1. Subcarrier_flag refers to the LRIS2K-to-VCD communication.
2. Data_rate_flag refers to the LRIS2K-to-VCD communication
0 A single subcarrier frequency is used by the LRIS2K
1 Two subcarrier are used by the LRIS2K
0 Low data rate is used
1 High data rate is used
0 The meaning of flags 5 to 8 is described in Ta bl e 1 8
1 The meaning of flags 5 to 8 is described in Ta bl e 1 9
42/98 Doc ID 13888 Rev 9

LRIS2K Request format
.
Table 18. Request_flags 5 to 8 when Bit 3 = 0
Bit No Flag Level Description
Request is executed by any LRIS2K according to the setting of
0
Bit 5 Select_flag
Bit 6 Address_flag
(1)
(1)
Bit 7 Option_flag 0
Bit 8 RFU 0
1. If the Select_flag is set to 1, the Address_flag is set to 0 and the UID field is not present in the request.
Table 19. Request_flags 5 to 8 when Bit 3 = 1
Bit No Flag Level Description
Address_flag
1 Request is executed only by the LRIS2K in Selected state
Request is not addressed. UID field is not present. The request is
0
executed by all LRIS2Ks.
Request is addressed. UID field is present. The request is
1
executed only by the LRIS2K whose UID matches the UID
specified in the request.
Bit 5 AFI_flag
Bit 6 Nb_slots_flag
Bit 7 Option_flag 0
Bit 8 RFU 0
0 AFI field is not present
1 AFI field is present
0 16 slots
11 slot
Doc ID 13888 Rev 9 43/98

Response format LRIS2K
16 Response format
The request consists of:
● an SOF
● flags
● parameters and data
● a CRC
● an EOF
Table 20. General response format
S
O
F
16.1 Response_flags
In a request, the flags indicate how actions have been performed by the LRIS2K and
whether corresponding fields are present or not. The request_flags consist of eight bits.
Table 21. Definitions of response_flags 1 to 8
Response_flags Parameters Data CRCEO
F
Bit No Flag Level Description
0 No error
Bit 1 Error_flag
1 Error detected. Error code is in the "Error" field.
Bit 2 RFU 0
Bit 3 RFU 0
Bit 4 Extension_flag 0 No extension
Bit 5 RFU 0
Bit 6 RFU 0
Bit 7 RFU 0
Bit 8 RFU 0
44/98 Doc ID 13888 Rev 9

LRIS2K Response format
16.2 Response error code
If the Error_flag is set by the LRIS2K in the request, the Error code field is present and
provides information about the error that occurred.
Error codes not specified in Ta bl e 2 2 are reserved for future use.
Table 22. Response error code definition
Error code Meaning
03h The option is not supported
0Fh Error with no information given
10h The specified block is not available
11h The specified block is already locked and thus cannot be locked again
12h The specified block is locked and its contents cannot be changed.
13h The specified block was not successfully programmed
14h The specified block was not successfully locked
Doc ID 13888 Rev 9 45/98

Anticollision LRIS2K
17 Anticollision
The purpose of the anticollision sequence is to inventory the LRIS2Ks present in the VCD
field using their unique ID (UID).
The VCD is the master of communications with one or several LRIS2Ks. It initiates LRIS2K
communication by issuing the Inventory request.
The LRIS2K sends its request in the determined slot or does not respond.
17.1 Request parameters
When issuing the Inventory command, the VCD:
● sets the Nb_slots_flag as desired
● adds the mask length and the mask value after the command field
● The mask length is the number of significant bits of the mask value.
● The mask value is contained in an integer number of bytes. The mask length indicates
the number of significant bits. LSB is transmitted first
● If the mask length is not a multiple of 8 (bits), as many 0-bits as required will be added
to the mask value MSB so that the mask value is contained in an integer number of
bytes
● The next field starts at the next byte boundary.
Table 23. Inventory request format
MSB LSB
SOF
Request_
flags
Command
Optional
AFI
Mask
length
Mask value CRC EOF
8 bits 8 bits 8 bits 8 bits 0 to 8 bytes 16 bits
In the example of the Ta bl e 2 4 and Figure 38, the mask length is 11 bits. Five 0-bits are
added to the mask value MSB. The 11-bit Mask and the current slot number are compared
to the UID.
Table 24. Example of the addition of 0-bits to an 11-bit mask value
(b15) MSB LSB (b0)
0000 0 100 1100 1111
0-bits added 11-bit mask value
46/98 Doc ID 13888 Rev 9

LRIS2K Anticollision
AI06682
Mask value received in the Inventory command 0000 0100 1100 1111b16 bits
The Mask value less the padding 0s is loaded
into the Tag comparator
100 1100 1111b11 bits
The Slot counter is calculated
xxxxNb_slots_flags = 0 (16 slots), Slot Counter is 4 bits
The Slot counter is concatened to the Mask value
xxxx 100 1100 1111
b
Nb_slots_flags = 0 15 bits
The concatenated result is compared with
the least significant bits of the Tag UID.
xxxx xxxx ..... xxxx xxxx x xxx xxxx xxxx xxxx 64 bits
LSBMSB
b
LSBMSB
LSBMSB
LSBMSB
b0b63
CompareBits ignored
UID
4 bits
Figure 38. Principle of comparison between the mask, the slot number and the UID
The AFI field is present if the AFI_flag is set.
The pulse is generated according to the definition of the EOF in ISO/IEC 15693-2.
The first slot starts immediately after the reception of the request EOF. To switch to the next
slot, the VCD sends an EOF.
The following rules and restrictions apply:
● if no LRIS2K answer is detected, the VCD may switch to the next slot by sending an
EOF,
● if one or more LRIS2K answers are detected, the VCD waits until the complete frame
has been received before sending an EOF for switching to the next slot.
Doc ID 13888 Rev 9 47/98

Request processing by the LRIS2K LRIS2K
18 Request processing by the LRIS2K
Upon reception of a valid request, the LRIS2K performs the following algorithm:
● NbS is the total number of slots (1 or 16)
● SN is the current slot number (0 to 15)
● LSB (value, n) function returns the n Less Significant Bits of value
● MSB (value, n) function returns the n Most Significant Bits of value
● “&” is the concatenation operator
● Slot_frame is either an SOF or an EOF
SN = 0
if (Nb_slots_flag)
then NbS = 1
SN_length = 0
endif
else NbS = 16
SN_length = 4
endif
label1:
if LSB(UID, SN_length + Mask_length) =
LSB(SN,SN_length)&LSB(Mask,Mask_length)
then answer to inventory request
endif
wait (Slot_frame)
if Slot_frame = SOF
then Stop Anticollision
decode/process request
exit
endif
if Slot_frame = EOF
if SN < NbS-1
then SN = SN + 1
goto label1
exit
endif
endif
48/98 Doc ID 13888 Rev 9

LRIS2K Explanation of the possible cases
19 Explanation of the possible cases
Figure 39 summarizes the main possible cases that can occur during an anticollision
sequence when the slot number is 16.
The different steps are:
● The VCD sends an Inventory request, in a frame terminated by an EOF. The number of
slots is 16.
● LRIS2K 1 transmits its request in Slot 0. It is the only one to do so, therefore no collision
occurs and its UID is received and registered by the VCD;
● The VCD sends an EOF in order to switch to the next slot.
● In slot 1, two LRIS2Ks, LRIS2K 2 and LRIS2K 3 transmit a request, thus generating a
collision. The VCD records the event and remembers that a collision was detected in
Slot 1.
● The VCD sends an EOF in order to switch to the next slot.
● In Slot 2, no LRIS2K transmits a request. Therefore the VCD does not detect any
LRIS2K SOF and decides to switch to the next slot by sending an EOF.
● In slot 3, there is another collision caused by requests from LRIS2K 4 and LRIS2K 5
● The VCD then decides to send a request (for instance a Read Block) to LRIS2K 1
whose UID has already been correctly received.
● All LRIS2Ks detect an SOF and exit the anticollision sequence. They process this
request and since the request is addressed to LRIS2K 1, only LRIS2K 1 transmits a
request.
● All LRIS2Ks are ready to receive another request. If it is an Inventory command, the
slot numbering sequence restarts from 0.
Note: The decision to interrupt the anticollision sequence is made by the VCD. It could have
continued to send EOFs until Slot 16 and only then sent the request to LRIS2K 1.
Doc ID 13888 Rev 9 49/98

Explanation of the possible cases LRIS2K
AI12885
Slot 0 Slot 1 Slot 2 Slot 3
VCD SOF
Inventory
Request
EOF EOF EOF EOF SOF
Request to
LRIS2K 1
EOF
Response
2
Response
4
LRIS2Ks
Response
from
LRIS2K 1
Response
1
Response
3
Response
5
Timing t1 t2 t1 t2 t3 t1 t2 t1
Comment
No
collision
Collision
No
Response
Collision
Time
Figure 39. Description of a possible anticollision sequence
50/98 Doc ID 13888 Rev 9

LRIS2K Inventory Initiated command
20 Inventory Initiated command
The LRIS2K provides a special feature to improve the inventory time response of moving
tags using the Initiate_flag value. This flag, controlled by the Initiate command, allows tags
to answer to Inventory Initiated commands.
For applications in which multiple tags are moving in front of a reader, it is possible to miss
tags using the standard inventory command. The reason is that the inventory sequence has
to be performed on a global tree search. For example, a tag with a particular UID value may
have to wait the run of a long tree search before being inventoried. If the delay is too long,
the tag may be out of the field before it has been detected.
Using the Initiate command, the inventory sequence is optimized. When multiple tags are
moving in front of a reader, the ones which are within the reader field will be initiated by the
Initiate command. In this case, a small batch of tags will answer to the Inventory Initiated
command which will optimize the time necessary to identify all the tags. When finished, the
reader has to issue a new Initiate command in order to initiate a new small batch of tags
which are new inside the reader field.
It is also possible to reduce the inventory sequence time using the Fast Initiate and Fast
Inventory Initiated commands. These commands allow the LRIS2Ks to increase their
response data rate by a factor of 2, up to 53kbit/s.
Doc ID 13888 Rev 9 51/98

Timing definition LRIS2K
21 Timing definition
21.1 t1: LRIS2K response delay
Upon detection of the rising edge of the EOF received from the VCD, the LRIS2K waits for a
time t
slot during an inventory process. Values of t
Figure 10 on page 24.
21.2 t2: VCD new request delay
t2 is the time after which the VCD may send an EOF to switch to the next slot when one or
more LRIS2K responses have been received during an Inventory command. It starts from
the reception of the EOF from the LRIS2Ks.
The EOF sent by the VCD may be either 10% or 100% modulated regardless of the
modulation index used for transmitting the VCD request to the LRIS2K.
is also the time after which the VCD may send a new request to the LRIS2K as described
t
2
in Figure 36: LRIS2K protocol timing.
before transmitting its response to a VCD request or before switching to the next
1nom
are given in Ta bl e 2 5 . The EOF is defined in
1
Values of t
are given in Ta bl e 2 5 .
2
21.3 t3: VCD new request delay in the absence of a response from the LRIS2K
t3 is the time after which the VCD may send an EOF to switch to the next slot when no
LRIS2K response has been received.
The EOF sent by the VCD may be either 10% or 100% modulated regardless of the
modulation index used for transmitting the VCD request to the LRIS2K.
From the time the VCD has generated the rising edge of an EOF:
● If this EOF is 100% modulated, the VCD waits a time at least equal to t
sending a new EOF.
● If this EOF is 10% modulated, the VCD waits a time at least equal to the sum of t
the LRIS2K nominal response time (which depends on the LRIS2K data rate and
subcarrier modulation mode) before sending a new EOF.
Table 25. Timing values
Minimum (min) values Nominal (nom) values Maximum (max) values
t
1
t
2
t
3
1. The tolerance of specific timings is ± 32/f
2. t
does not apply for write alike requests. Timing conditions for write alike requests are defined in the
1max
command description.
3. t
is the time taken by the LRIS2K to transmit an SOF to the VCD. t
SOF
rate: High data rate or Low data rate.
318.6 µs 320.9 µs 323.3 µs
309.2 µs No t
(2)
t
1max
+ t
SOF
(1)
(3)
nom
No t
nom
.
C
depends on the current data
SOF
3min
No t
No t
before
max
max
3min
+
52/98 Doc ID 13888 Rev 9

LRIS2K Commands codes
22 Commands codes
The LRIS2K supports the commands described in this section. Their codes are given in
Ta bl e 2 6 .
Table 26. Command codes
Command code
standard
01h Inventory A6h Kill
02h Stay Quiet B1h Write password
20h Read Single Block B2h Lock Password
21h Write Single Block B3h Present Password
22h Lock Block C0h Fast Read Single Block
25h Select C1h Fast Inventory Initiated
26h Reset to Ready C2h Fast Initiate
27h Write AFI D1h Inventory Initiated
28h Lock AFI D2h Initiate
29h Write DSFID
2Ah Lock DSFID
2Bh Get System Info
2Ch
Get Multiple Block Security
Status
Function
Command code
custom
Function
Doc ID 13888 Rev 9 53/98

Inventory LRIS2K
23 Inventory
When receiving the Inventory request, the LRIS2K runs the anticollision sequence. The
Inventory_flag is set to 1. The meaning of flags 5 to 8 is shown in Table 19: Request_flags 5
to 8 when Bit 3 = 1.
The request contains the:
● flags
● Inventory command code (see Table 26: Command codes)
● AFI if the AFI flag is set
● mask length
● mask value
● CRC
The LRIS2K does not generate any answer in case of error.
Table 27. Inventory request format
Request
SOF
Request_flags Inventory
Optional
AFI
Mask
length
Mask
value
CRC16
Request
EOF
8 bits 01h 8 bits 8 bits 0 - 64 bits 16 bits
The response contains the:
● flags
● unique ID
Table 28. Inventory response format
Response
SOF
Response_
flags
DSFID UID CRC16
Response
EOF
8 bits 8 bits 64 bits 16 bits
During an Inventory process, if the VCD does not receive an RF LRIS2K response, it waits a
before sending an EOF to switch to the next slot. t3 starts from the rising edge of the
time t
3
request EOF sent by the VCD.
● If the VCD sends a 100% modulated EOF, the minimum value of t
min = 4384/fC (323.3µs) + t
t
3
●
If the VCD sends a 10% modulated EOF, the minimum value of t3 is:
min = 4384/fC (323.3µs) + t
t
3
SOF
NRT
is:
3
where:
● t
● t
t
NRT
is the time required by the LRIS2K to transmit an SOF to the VCD
SOF
is the nominal response time of the LRIS2K
NRT
and t
are dependent on the LRIS2K-to-VCD data rate and subcarrier modulation
SOF
mode.
54/98 Doc ID 13888 Rev 9

LRIS2K Stay Quiet
24 Stay Quiet
Command code = 0x02
On receiving the Stay Quiet command, the LRIS2K enters the Quiet state and does NOT
send back a request. There is NO response to the Stay Quiet command even if an error
occurs.
When in the Quiet state:
● the LRIS2K does not process any request if the Inventory_flag is set,
● the LRIS2K processes any Addressed request
The LRIS2K exits the Quiet state when:
● it is reset (power off),
● receiving a Select request. It then goes to the Selected state,
● receiving a Reset to Ready request. It then goes to the Ready state.
Table 29. Stay Quiet request format
Request
SOF
Request_flags Stay Quiet UID CRC16
Request
EOF
8 bits 02h 64 bits 16 bits
The Stay Quiet command must always be executed in Addressed mode (Select_flag is reset
to 0 and Address_flag is set to 1).
Figure 40. Stay Quiet frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K
Timing
Stay Quiet
request
EOF
Doc ID 13888 Rev 9 55/98

Read Single Block LRIS2K
25 Read Single Block
On receiving the Read Single Block command, the LRIS2K reads the requested block and
sends back its 32 bits value in the request. The Option_flag is supported and gives access
to the protect status.
Table 30. Read Single Block request format
Request
SOF
Request_flags
8 bits 20h
Read Single
Block
UID
64 bits 8 bits 16 bits
Block
number
CRC16
Request parameters:
● Option_flag
● UID (optional)
● Block number
Table 31. Read Single Block response format when Error_flag is NOT set
Response
SOF
Response_flags
8 bits
Block locking
status
Data CRC16
8 bits 32 bits 16 bits
Response
Response parameters:
● Block Locking Status if Option_flag is set (see Table 32: Block Locking status)
● 4 bytes of block data
Table 32. Block Locking status
b
Reserved for future
b
7
use. All at 0
b
6
5
b
b
4
password
control bits
3
b
2
Read / Write
protection bits
b
1
0: Current Block not locked
1: Current Block locked
b
0
Request
EOF
EOF
Table 33. Read Single Block response format when Error_flag is set
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set
– 0Fh: other error
– 10h: block address not available
56/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Read Single Block
Figure 41. Read Single Block frame exchange between VCD and LRIS2K
VCD SOF
Read Single Block
request
EOF
LRIS2K <-t
-> SOF
1
Read Single Block
response
EOF
Doc ID 13888 Rev 9 57/98

Write Single Block LRIS2K
26 Write Single Block
On receiving the Write Single Block command, the LRIS2K writes the data contained in the
request to the requested block and reports whether the write operation was successful in
the request. The Option_flag is supported.
During the write cycle t
Otherwise, the LRIS2K may not program correctly the data into the memory. The t
equal to t
Table 34. Write Single Block request format
Request
SOF
+ 18 × 302 µs.
1nom
Request_
flags
8 bits 21h
, there should be no modulation (neither 100% nor 10%).
W
Write
Single
Block
UID
Block
number
Data CRC16
64 bits 8 bits 32 bits 16 bits
time is
W
Request
Request parameters:
● UID (optional)
● Block number
● Data
Table 35. Write Single Block response format when Error_flag is NOT set
Response SOF Response_flags CRC16 Response EOF
8 bits 16 bits
Response parameter:
● No parameter. The response is send back after the writing cycle.
Table 36. Write Single Block response format when Error_flag is set
EOF
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 10h: block address not available
– 12h: block is locked
– 13h: block not programmed
58/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Write Single Block
Figure 42. Write Single Block frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
Write Single
Block request
EOF
-> SOF
1
Write Single Block
response
EOF
LRIS2K <------------ tW ------------><- t1 -> SOF
Write sequence when
error
Write Single
Block response
EOF
Doc ID 13888 Rev 9 59/98

Lock Block LRIS2K
27 Lock Block
On receiving the Lock Block command, the LRIS2K permanently locks the selected block.
During the write cycle t
Otherwise, the LRIS2K may not lock correctly the memory block. The t
+ 18 × 302µs.
t
1nom
Table 37. Lock Single Block request format
Request
SOF
Request_
flags
8 bits 22h
, there should be no modulation (neither 100% nor 10%).
W
W
Lock
Block
UID
Block
number
64 bits 8 bits 16 bits
Request parameters:
● (Optional) UID
● Block number
Table 38. Lock Block response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter.
Table 39. Lock Block response format when Error_flag is set
time is equal to
CRC16
Request
EOF
Response
EOF
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 10h: block address not available
– 11h: block is locked
– 14h: block not locked
60/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Lock Block
Figure 43. Lock Block frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
Lock Block
request
EOF
-> SOF
1
LRIS2K <------------ t
Lock Block
response
------------><- t1 -> SOF
W
Lock sequence when
EOF
Lock Block
response
error
EOF
Doc ID 13888 Rev 9 61/98

Select LRIS2K
28 Select
When receiving the Select command:
● if the UID is equal to its own UID, the LRIS2K enters or stays in the Selected state and
sends a request.
● if the UID does not match its own, the selected LRIS2K returns to the Ready state and
does not send a request.
The LRIS2K answers an error code only if the UID is equal to its own UID. If not, no
response is generated.
Table 40. Select request format
Request
SOF
Request_
flags
Select UID CRC16
8 bits 25h 64 bits 16 bits
Request parameter:
● UID
Table 41. Select Block response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter.
Table 42. Select response format when Error_flag is set
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Request
EOF
Response
EOF
Response
EOF
Response parameter:
● Error code as Error_flag is set:
– 0Fh: other error
Figure 44. Select frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
62/98 Doc ID 13888 Rev 9
Select
request
EOF
-> SOF
1
Select
response
EOF

LRIS2K Reset to Ready
29 Reset to Ready
On receiving a Reset to Ready command, the LRIS2K returns to the Ready state. In the
Addressed mode, the LRIS2K answers an error code only if the UID is equal to its own UID.
If not, no response is generated.
Table 43. Reset to Ready request format
Request
SOF
Request_
flags
8 bits 26h
Reset to
Ready
UID CRC16
64 bits 16 bits
Request parameter:
● UID (Optional)
Table 44. Reset to Ready response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter
Table 45. Reset to Ready request format when Error_flag is set
Response
SOF
Response_
flags
Error code CRC16
8 bits 8 bits 16 bits
Request
EOF
Response
EOF
Response
EOF
Response parameter:
● Error code as Error_flag is set:
– 0Fh: other error
Figure 45. Reset to Ready frame exchange between VCD and LRIS2K
Reset to
VCD SOF
LRIS2K <-t
Ready
request
EOF
Reset to
-> SOF
1
Ready
EOF
response
Doc ID 13888 Rev 9 63/98

Write AFI LRIS2K
30 Write AFI
On receiving the Write AFI request, the LRIS2K writes the AFI byte value into its memory.
During the write cycle t
, there should be no modulation (neither 100% nor 10%).
W
Otherwise, the LRIS2K may not write correctly the AFI value into the memory. The t
equal to t
Table 46. Write AFI request format
Request
SOF
+ 18 × 302 µs.
1nom
Request
_flags
8 bits 27h
Write
AFI
UID AFI CRC16
64 bits 8 bits 16 bits
Request parameters:
● UID (Optional)
● AFI
Table 47. Write AFI response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter.
Table 48. Write AFI response format when Error_flag is set
time is
W
Request
EOF
Response
EOF
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set
– 12h: block is locked
– 13h: block not programmed
64/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Write AFI
Figure 46. Write AFI frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
Write AFI
request
EOF
-> SOF
1
LRIS2K <------------ t
Write AFI
response
------------><- t1 -> SOF
W
EOF
Write sequence
when error
Write AFI
response
EOF
Doc ID 13888 Rev 9 65/98

Lock AFI LRIS2K
31 Lock AFI
On receiving the Lock AFI request, the LRIS2K locks the AFI value permanently.
During the write cycle t
, there should be no modulation (neither 100% nor 10%).
W
Otherwise, the LRIS2K may not Lock correctly the AFI value in memory. The t
equal to t
Table 49. Lock AFI request format
Request
SOF
+ 18 × 302 µs.
1nom
Request_
flags
8 bits 28h
Lock
AFI
UID CRC16
64 bits 16 bits
Request parameter:
● UID (optional)
Table 50. Lock AFI response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter
Table 51. Lock AFI response format when Error_flag is set
time is
W
Request
Response
EOF
EOF
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set
– 11h: block is locked
– 14h: block not locked
Figure 47. Lock AFI frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
LRIS2K <------------ t
Lock AFI
request
EOF
-> SOF
1
Lock AFI
response
------------><- t1 -> SOF
W
EOF
Response
EOF
Lock sequence when
error
Lock AFI
response
EOF
66/98 Doc ID 13888 Rev 9

LRIS2K Write DSFID
32 Write DSFID
On receiving the Write DSFID request, the LRIS2K writes the DSFID byte value into its
memory.
During the write cycle t
, there should be no modulation (neither 100% nor 10%).
W
Otherwise, the LRIS2K may not write correctly the DSFID value in memory. The t
equal to t
Table 52. Write DSFID request format
Request
SOF
+ 18 × 302 µs.
1nom
Request_
flags
8 bits 29h
Write
DSFID
UID DSFID CRC16
64 bits 8 bits 16 bits
Request parameters:
● UID (optional)
● DSFID
Table 53. Write DSFID response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter
Table 54. Write DSFID response format when Error_flag is set
time is
W
Request
EOF
Response
EOF
Response
SOF
Response_flags Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set
– 12h: block is locked
– 13h: block not programmed
Doc ID 13888 Rev 9 67/98
Response
EOF

Write DSFID LRIS2K
Figure 48. Write DSFID frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
Write DSFID
request
EOF
-> SOF
1
LRIS2K <------------ t
Write DSFID
response
------------><- t1 -> SOF
W
Write sequence when
EOF
Write DSFID
response
error
EOF
68/98 Doc ID 13888 Rev 9

LRIS2K Lock DSFID
33 Lock DSFID
On receiving the Lock DSFID request, the LRIS2K locks the DSFID value permanently.
During the write cycle t
, there should be no modulation (neither 100% nor 10%).
W
Otherwise, the LRIS2K may not lock correctly the DSFID value in memory. The t
equal to t
Table 55. Lock DSFID request format
Request
SOF
+ 18 × 302 µs.
1nom
Request_
flags
8 bits 2Ah
Lock
DSFID
UID CRC16
64 bits 16 bits
Request parameter:
● UID (optional)
Table 56. Lock DSFID response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter.
Table 57. Lock DSFID response format when Error_flag is set
time is
W
Request
EOF
Response
EOF
Response
SOF
Response_flags Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 11h: block is locked
– 14h: block not locked
Figure 49. Lock DSFID frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
LRIS2K <------------ t
Lock DSFID
request
EOF
-> SOF
1
Lock DSFID
response
------------><- t1 -> SOF
W
EOF
Response
Lock sequence
when error
Lock DSFID
response
EOF
EOF
Doc ID 13888 Rev 9 69/98

Get System Info LRIS2K
34 Get System Info
When receiving the Get System Info command, the LRIS2K sends back its information data
in the request.The Option_flag is supported and must be reset to 0. The Get System Info
can be issued in both Addressed and Non Addressed modes.
Table 58. Get System Info request format
Request
SOF
Request
_flags
Get System
Info
UID CRC16
Request
EOF
8 bits 2Bh 64 bits 16 bits
Request parameter:
● UID (optional)
Table 59. Get System Info response format when Error_flag is NOT set
Response
SOF
Response
_flags
Information
_flags
UID DSFID AFI
Memory
Size
reference
00h 0Fh 64 bits 8 bits 8 bits 033Fh 001010xx
IC
CRC16
16 bits
b
Response
EOF
Response parameters:
● Information flags set to 0Fh. DSFID, AFI, memory size and IC reference fields are
present
● UID code on 64 bits
● DSFID value
● AFI value
● Memory size. The LRIS2K provides 64 blocks (3Fh) of 4 byte (03h)
● IC Reference. Only the 6 MSB are significant. The product code of the LRIS2K is
00 1010
Table 60. Get System Info response format when Error_flag is set
b
=10
d
Response SOF
Response_
flags
Error code CRC16 Response EOF
01h 0Fh 16 bits
Response parameter:
● Error code as Error_flag is set:
– 03h: Option not supported
– 0Fh: other error
70/98 Doc ID 13888 Rev 9

LRIS2K Get System Info
Figure 50. Get System Info frame exchange between VCD and LRIS2K
VCD SOF
Get System Info
request
EOF
LRIS2K <-t
-> SOF Get System Info response EOF
1
Doc ID 13888 Rev 9 71/98

Get Multiple Block Security Status LRIS2K
35 Get Multiple Block Security Status
When receiving the Get Multiple Block Security Status command, the LRIS2K sends back
the block security status. The blocks are numbered from '00 to '3F' in the request and the
value is minus one (–1) in the field. For example, a value of '06' in the “Number of blocks”
field requests to return the security status of 7 blocks. In request, option flag must be set to
0.
Table 61. Get Multiple Block Security Status request format
Get
Request
SOF
Request
_flags
Multiple
Block
Security
Status
UID
First
block
number
Number
of
blocks
CRC16
Request
EOF
8 bits 2Ch
64 bits 8 bits 8 bits 16 bits
Request parameters:
● UID (optional)
● First block number
● Number of blocks
NOT set
Table 62. Get Multiple Block Security Status response format when Error_flag is
NOT set
Response
SOF
1. Repeated as needed.
Response_
Flags
8 bits
Block locking
status
(1)
8 bits
CRC16
16 bits
Response
EOF
Response parameters:
● Block Locking Status (see Table 63: Block Locking status)
● N blocks of data
Table 63. Block Locking status
b
7
Reserved for future use. All
b
at 0
6
b
5
b
4
b
3
password control
bits
b
2
b
Read / Write
protection bits
1
0: Current Block not locked
1: Current Block locked
b
0
Table 64. Get Multiple Block Security Status response format when Error_flag is
set
Response
SOF
72/98 Doc ID 13888 Rev 9
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response
EOF

LRIS2K Get Multiple Block Security Status
Response parameter:
● Error code as Error_flag is set:
– 03h: Option not supported
– 0Fh: other error
Figure 51. Get Multiple Block Security Status frame exchange between VCD and
LRIS2K
VCD SOF
Get Multiple Block
Security Status
EOF
LRIS2K <-t
-> SOF
1
Get Multiple Block
Security Status
EOF
Doc ID 13888 Rev 9 73/98

Kill LRIS2K
36 Kill
On receiving the Kill command, in the Addressed mode only, the LRIS2K compares the kill
code with the data contained in the request and reports whether the operation was
successful in the request. If the command is received in the Non Addressed or the Selected
mode, the LRIS2K returns an error response.
During the comparison cycle equal to t
10%). Otherwise, the LRIS2K may not match the kill code correctly. The t
+ 18 × 302 µs. After a successful Kill command, the LRIS2K is deactivated and does
t
1nom
, there should be no modulation (neither 100% nor
W
time is equal to
W
not interpret any other command.
Table 65. Kill request format
Request
SOF
Request
_flags
Kill
IC
MFG
Code
UID
Kill
access
Kill code CRC16
8 bits A6h 0x02 64 bits 00h 32 bits 16bits
Request parameters:
● UID
● Kill code
Table 66. Kill response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter. The response is send back after the writing cycle
Table 67. Kill response format when Error_flag is set
Request
EOF
Response
EOF
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 0Fh: other error
– 14h: LRIS2K not killed
74/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Kill
Figure 52. Kill frame exchange between VCD and LRIS2K
VCD SOF Kill request EOF
LRIS2K <-t
-> SOF Kill response EOF
1
LRIS2K <------------ tW ------------><- t1 -> SOF
Kill sequence when
error
Kill
response
EOF
Doc ID 13888 Rev 9 75/98

Write Password LRIS2K
37 Write Password
On receiving the Write Password command, the LRIS2K uses the data contained in the
request to write the password and reports whether the operation was successful in the
request. The Option_flag is supported.
During the write cycle time, t
Otherwise, the LRIS2K may not correctly program the data into the memory. The t
equal to t
+ 18 × 302 µs. After a successful write, the selected password must be locked
1nom
, there must be no modulation at all (neither 100% nor 10%).
W
time is
W
again by issuing a Lock Password command to re-activate the block protection.
Prior to writing the password for a block, the Write Password command erases the Protect
Status area of the block.
Table 68. Write Password request format
Request
SOF
Request
_flags
Write
Password
8 bits B1h 02h
IC
MFG
code
UID
Password
number
Data CRC16
64 bits 8 bits 32 bits 16 bits
Request
EOF
Request parameters:
● UID (optional)
● Password number (00h = Kill, 01h = Pswd1, 02h = Pswd2, 03h = Pswd3, other = Error)
● Data
Table 69. Write Password response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
Response
EOF
8 bits 16 bits
Response parameter:
● 32-bit password value. The response is sent back after the write cycle.
Table 70. Write Password response format when Error_flag is set
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 10h: block address not available
– 12h: block is locked
– 13h: block not programmed
76/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Write Password
Figure 53. Write Password frame exchange between VCD and LRIS2K
Write
VCD SOF
Password
request
EOF
LRIS2K <-t1-> SOF
Write Password
response
EOF
LRIS2K <------------ tW ------------><- t1 -> SOF
Write sequence when
error
Write
Password
EOF
response
Doc ID 13888 Rev 9 77/98

Lock Password LRIS2K
38 Lock Password
On receiving the Lock Password command, the LRIS2K sets the access rights and
permanently locks the selected block. The Option_flag is supported.
RFU bit 8 of the request_flag is used to select either the memory area (bit 8 = ‘0’) or the
password area (bit 8 = ‘1’).
During the write cycle t
, there should be no modulation (neither 100% nor 10%) otherwise,
W
the LRIS2K may not correctly lock the memory block.
time is equal to t
The t
W
Table 71. Lock Password request format
Request
SOF
Request
_flags
Password
8 bits B2h 02h
+ 18 × 302 µs.
1nom
Lock
IC
MFG
code
UID
Block
number
Protect
Status
CRC16
64 bits 8 bits 8 bits 16 bits
Request
EOF
Request parameters:
● (Optional) UID
● Block number (bit 8 = ‘1’: 00h = Kill, 01h = Pswd1, 02h = Pswd2, 03h = Pswd3, other =
Error)
● Protect status (refer to Ta bl e 7 2 )
Table 72. Protect status
b
7
0 0 0 password control bits
1. b1b2 is 00 or 11. Other combinations are reserved but will behave as 11 in terms of protection settings.
b
6
b
5
b
4
b
3
b
2
Read / Write protection
bits
(1)
b
1
b
0
1
Table 73. Lock Password response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
8 bits 16 bits
Response parameter:
● No parameter.
Table 74. Lock Password response format when Error_flag is set
Response
SOF
78/98 Doc ID 13888 Rev 9
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response
EOF
Response
EOF

LRIS2K Lock Password
Response parameter:
● Error code as Error_flag is set:
– 10h: block address not available
– 11h: block is locked
– 14: block not locked
Figure 54. Lock Password frame exchange between VCD and LRIS2K
Lock
VCD SOF
Password
request
EOF
LRIS2K <-t1-> SOF
LRIS2K <------------ t
Lock Password
response
------------><- t1 -> SOF
W
Lock sequence when
EOF
Lock
Password
response
error
EOF
Doc ID 13888 Rev 9 79/98

Present Password LRIS2K
39 Present Password
On receiving the Present Password command, the LRIS2K compares the requested
password with the data contained in the request and reports whether the operation has
been successful in the request. The Option_flag is supported.
During the comparison cycle equal to t
10%) otherwise, the LRIS2K the Password value may not be correctly compared.
time is equal to t
The t
W
+ 18 × 302 µs.
1nom
After a successful command, the access to all the memory blocks linked to the password is
changed as described in Section 2: LRIS2K block security.
Table 75. Present Password request format
, there should be no modulation (neither 100% nor
W
Request
SOF
Request
_flags
Present
Password
8 bits B3h 02h
IC
MFG
code
UID
Password
number
Data CRC16
64 bits 8 bits 32 bits 16 bits
Request parameters:
● UID (optional)
● Password number (0x01 = Pswd1, 0x02 = Pswd2, 0x03 = Pswd3, other = Error)
● Data
Table 76. Present Password response format when Error_flag is NOT set
Response
SOF
Response_flags CRC16
Response
EOF
8 bits 16 bits
Response parameter:
● No parameter. The response is send back after the writing cycle
Table 77. Present Password response format when Error_flag is set
Response
SOF
Response_
Flags
Error code CRC16
Response
Request
EOF
EOF
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 0Fh: other error
80/98 Doc ID 13888 Rev 9

LRIS2K Present Password
Figure 55. Present Password frame exchange between VCD and LRIS2K
Present
VCD SOF
LRIS2K <-t
LRIS2K <------------ t
Password
request
EOF
-> SOF
1
Present
Password
response
------------><- t1 -> SOF
W
EOF sequence when error
Present
Password
EOF
response
Doc ID 13888 Rev 9 81/98

Fast Read Single Block LRIS2K
40 Fast Read Single Block
On receiving the Fast Read Single Block command, the LRIS2K reads the requested block
and sends back its 32-bit value in the request. The Option_flag is supported. The data rate
of the response is multiplied by 2.
Table 78. Fast Read Single Block request format
Request
SOF
Request_
flags
Fast Read
Single
Block
8 bits C0h 02h
IC
MFG
code
UID
Block
number
CRC16
64 bits 8 bits 16 bits
Request
Request parameters:
● Option_flag
● UID (optional)
● Block number
Table 79. Fast Read Single Block response format when Error_flag is NOT set
Response
SOF
Response
_flags
8 bits
Block
Locking
Data CRC16
Status
8 bits 32 bits 16 bits
Response
EOF
Response parameters:
● Block Locking Status if Option_flag is set (see Ta bl e 8 0 )
● 4 bytes of block data
Table 80. Block Locking status
b
7
Reserved for future used. All
b
at 0
6
b
5
b
4
b
3
password control
bits
b
2
b
1
Read / Write
protection bits
b
0
0: Current Block not locked
1: Current Block locked
EOF
Table 81. Fast Read Single Block response format when Error_flag is set
Response
SOF
Response_
Flags
Error code CRC16
8 bits 8 bits 16 bits
Response parameter:
● Error code as Error_flag is set:
– 0Fh: other error
– 10h: block address not available
82/98 Doc ID 13888 Rev 9
Response
EOF

LRIS2K Fast Read Single Block
Figure 56. Fast Read Single Block frame exchange between VCD and LRIS2K
VCD SOF
Fast Read Single
Block request
EOF
LRIS2K <-t
-> SOF
1
Fast Read Single
Block response
EOF
Doc ID 13888 Rev 9 83/98

Fast Inventory Initiated LRIS2K
41 Fast Inventory Initiated
Before receiving the Fast Inventory Initiated command, the LRIS2K must have received an
Initiate or a Fast Initiate command in order to set the Initiate_ flag. If not, the LRIS2K does
not answer to the Fast Inventory Initiated command.
On receiving the Fast Inventory Initiated request, the LRIS2K runs the anticollision
sequence. The Inventory_flag must be set to 1. The meaning of flags 5 to 8 is shown in
Table 19: Request_flags 5 to 8 when Bit 3 = 1. The data rate of the response is multiplied by
2.
The request contains the:
● flags
● Inventory command code
● AFI option not supported, AFI_flag must be set to 0
● mask length
● mask value
● CRC
The LRIS2K does not generate any answer in case of error.
Table 82. Fast Inventory Initiated request format
Request
SOF
Request
Flags
Fast Inventory
Initiated
IC MFG
code
Optional
AFI
Mask
length
Mask value CRC16
Request
EOF
8 bits C1h 02h 8 bits 8 bits 0 - 64 bits 16 bits
The response contains:
● the flags
● the Unique ID
Table 83. Fast Inventory Initiated response format
Response SOF Response_flags DSFID UID CRC16 Response EOF
8 bits 00h 64 bits 16 bits
During an Inventory process, if the VCD does not receive an RF LRIS2K response, it waits a
before sending an EOF to switch to the next slot. t3 starts from the rising edge of the
time t
3
request EOF sent by the VCD.
● If the VCD sends a 100% modulated EOF, the minimum value of t
min = 4384/fC (323.3µs) + t
t
3
If the VCD sends a 10% modulated EOF, the minimum value of t3 is:
●
min = 4384/fC (323.3µs) + t
t
3
SOF
NRT
is:
3
where:
● t
● t
t
NRT
is the time required by the LRIS2K to transmit an SOF to the VCD
SOF
is the nominal response time of the LRIS2K
NRT
and t
are dependent on the LRIS2K-to-VCD data rate and subcarrier modulation
SOF
mode.
84/98 Doc ID 13888 Rev 9

LRIS2K Fast Initiate
42 Fast Initiate
On receiving the Fast Initiate command, the LRIS2K sets the internal Initiate_flag and sends
back a request. The command has to be issued in the Non Addressed mode only
(Select_flag is reset to 0 and Address_flag is reset to 0). If an error occurs, the LRIS2K does
not generate any answer. The Initiate_flag is reset after a power off of the LRIS2K. The data
rate of the response is multiplied by 2.
The request contains:
● No data
Table 84. Fast Initiate request format
Request
SOF
Request_flags
Fast
Initiate
IC MFG
code
CRC16
8 bits C2h 02h 16 bits
The response contains:
● the flags
● the Unique ID
Table 85. Fast Initiate response format
Response
SOF
Figure 57. Fast Initiate frame exchange between VCD and LRIS2K
VCD SOF Fast Initiate request EOF
LRIS2K <-t
Response
_flags
DSFID UID CRC16
8 bits 00h 64 bits 16 bits
-> SOF Fast Initiate response EOF
1
Request
EOF
Response
EOF
Doc ID 13888 Rev 9 85/98

Inventory Initiated LRIS2K
43 Inventory Initiated
Before receiving the Inventory Initiated command, the LRIS2K must have received an
Initiate or a Fast Initiate command in order to set the Initiate_ flag. If not, the LRIS2K does
not answer to the Inventory Initiated command.
On receiving the Inventory Initiated request, the LRIS2K runs the anticollision sequence.
The Inventory_flag must be set to 1. The meaning of flags 5 to 8 is given in Tab le 1 9 :
Request_flags 5 to 8 when Bit 3 = 1.
The request contains the:
● flags
● Inventory command code
● AFI option not supported, AFI_flag must be set to 0
● mask length
● mask value
● CRC
The LRIS2K does not generate any answer in case of error.
Table 86. Inventory Initiated request format
Request
SOF
Request
_flags
Inventory
Initiated
IC MFG
code
Optional
AFI
Mask
length
Mask value CRC16
Request
EOF
8 bits D1h 02h 8 bits 8 bits 0 - 64 bits 16 bits
The response contains the:
● flags
● unique ID
Table 87. Inventory Initiated response format
Response SOF Response_flags DSFID UID CRC16 Response EOF
8 bits 0x00 64 bits 16 bits
During an Inventory process, if the VCD does not receive an RF LRIS2K response, it waits a
before sending an EOF to switch to the next slot. t3 starts from the rising edge of the
time t
3
request EOF sent by the VCD.
● If the VCD sends a 100% modulated EOF, the minimum value of t
min = 4384/fC (323.3µs) + t
t
3
If the VCD sends a 10% modulated EOF, the minimum value of t3 is:
●
min = 4384/fC (323.3µs) + t
t
3
SOF
NRT
is:
3
where:
● t
● t
t
NRT
is the time required by the LRIS2K to transmit an SOF to the VCD
SOF
is the nominal response time of the LRIS2K
NRT
and t
are dependent on the LRIS2K-to-VCD data rate and subcarrier modulation
SOF
mode.
86/98 Doc ID 13888 Rev 9

LRIS2K Initiate
44 Initiate
On receiving the Initiate command, the LRIS2K sets the internal Initiate_flag and sends
back a request. The command has to be issued in the Non Addressed mode only
(Select_flag is reset to 0 and Address_flag is reset to 0). If an error occurs, the LRIS2K does
not generate any answer. The Initiate_flag is reset after a power off of the LRIS2K.
The request contains:
● No data
Table 88. Initiate request format
Request
SOF
Request_flags Initiate
IC MFG
code
CRC16
8 bits D2h 02h 16 bits
The response contains the:
● flags
● unique ID
Table 89. Initiate Initiated response format
Response
SOF
Figure 58. Initiate frame exchange between VCD and LRIS2K
VCD SOF
LRIS2K <-t
Response
_flags
DSFID UID CRC16
8 bits 00h 64 bits 16 bits
Initiate
request
EOF
-> SOF
1
Initiate
response
EOF
Request
EOF
Response
EOF
Doc ID 13888 Rev 9 87/98

Maximum rating LRIS2K
45 Maximum rating
Stressing the device above the rating listed in the absolute maximum ratings table may
cause permanent damage to the device. These are stress ratings only and operation of the
device at these or any other conditions above those indicated in the operating sections of
this specification is not implied. Exposure to absolute maximum rating conditions for
extended periods may affect device reliability. Refer also to the STMicroelectronics SURE
Program and other relevant quality documents.
Table 90. Absolute maximum ratings
Symbol Parameter Min. Max. Unit
T
STG
t
STG
I
CC
V
MAX
V
ESD
1. AEC-Q100-002 (compliant with JEDEC Std JESD22-A114A, C1=100 pF, R1=1500 Ohm, R2=500 Ohm)
2. Human body model.
3. Machine model.
Storage conditions
Storage time 23 months
Wafer (kept in its
antistatic bag)
15 25 °C
Supply current on AC0 / AC1 –20 20 mA
Input voltage on AC0 / AC1 –7 7 V
(2)
–1000 1000 V
(3)
–100 100 V
Electrostatic discharge voltage
UFDFPN8 (HBM)
(1)
UFDFPN8 (MM)
88/98 Doc ID 13888 Rev 9

LRIS2K DC and AC parameters
46 DC and AC parameters
This section summarizes the operating and measurement conditions, and the DC and AC
characteristics of the device. The parameters in the DC and AC characteristic tables that
follow are derived from tests performed under the measurement conditions summarized in
the relevant tables. Designers should check that the operating conditions in their circuit
match the measurement conditions when relying on the quoted parameters.
Table 91. AC characteristics
Symbol Parameter Condition Min Typ Max Unit
(1) (2)
f
CC
MI
CARRIER
t
RFR,tRFF
t
RFSBL
MI
CARRIER
t
RFR,tRFF
t
RFSBL
t
JIT
t
MIN CD
f
SH
f
SL
t
1
t
2
t
W
1. T
= –20 to 85 °C.
A
2. All timing measurements were performed on a reference antenna with the following characteristics:
External size: 75 mm x 48 mm
Number of turns: 6
Width of conductor: 1 mm
Space between 2 conductors: 0.4 mm
Value of the tuning capacitor: 21 pF (LRIS2K-SBN18)
Value of the coil: 4.3 µH
Tuning frequency: 13.8 MHz.
External RF signal frequency 13.553 13.56 13.567 MHz
10% carrier modulation index MI=(A-B)/(A+B) 10 30 %
10% rise and fall time 0.5 3.0 µs
10% minimum pulse width for bit 7.1 9.44 µs
100% carrier modulation index MI=(A-B)/(A+B) 95 100 %
100% rise and fall time 0.5 3.5 µs
100% minimum pulse width for bit 7.1 9.44 µs
Bit pulse jitter -2 +2 µs
Minimum time from carrier
generation to first data
From H-field min 0.1 1 ms
Subcarrier frequency high FCC/32 423.75 KHz
Subcarrier frequency low FCC/28 484.28 KHz
Time for LRIS2K response 4224/F
Time between commands 4224/F
Programming time (including
internal verify time)
S
S
318.6 320.9 323.3 µs
309 311.5 314 µs
5.8 ms
Doc ID 13888 Rev 9 89/98

DC and AC parameters LRIS2K
AI06680
AB
t
RFF
t
RFR
t
RFSBL
t
MAX t
MIN CD
f
CC
Table 92. DC characteristics
(1)
Symbol Parameter Test conditions Min. Typ. Max. Unit
V
V
Regulated voltage 1.5 3.0 V
CC
Retromodulated induced
RET
voltage
ISO10373-7 10 mV
Read VCC= 3.0 V 50 µA
I
Supply current
CC
C
1. T
Table 93. Operating conditions
Internal tuning capacitor
TUN
= –20 to 85 °C.
A
Write V
= 3.0 V 150 µA
CC
f = 13.56 MHz for
SBN18/1
21 pF
Symbol Parameter Min. Max. Unit
T
A
Ambient operating temperature –20 85 °C
Figure 59 shows an ASK modulated signal, from the VCD to the LRIS2K. The test condition
for the AC/DC parameters are:
● Close coupling condition with tester antenna (1mm)
● LRIS2K performance measured at the tag antenna
Figure 59. LRIS2K synchronous timing, transmit and receive
90/98 Doc ID 13888 Rev 9

LRIS2K Part numbering
47 Part numbering
Table 94. Ordering information scheme
Example: LRIS2K - SBN18/ 1 GE
Device type
LRIS2K
Package
SBN18 = 180 µm ± 15 µm bumped and sawn wafer on 8-inch frame
Tuning capacitance
1 = 21 pF
Customer code given by ST
GE
For further information on any aspect of this device, please contact your nearest ST sales
office.
Doc ID 13888 Rev 9 91/98

Anticollision algorithm (Informative) LRIS2K
Appendix A Anticollision algorithm (Informative)
The following pseudocode describes how anticollision could be implemented on the VCD,
using recursivity.
A.1 Algorithm for pulsed slots
function push (mask, address); pushes on private stack
function pop (mask, address); pops from private stack
function pulse_next_pause; generates a power pulse
function store(LRIS2K_UID); stores LRIS2K_UID
function poll_loop (sub_address_size as integer)
pop (mask, address)
mask = address & mask; generates new mask
; send the request
mode = anticollision
send_Request (Request_cmd, mode, mask length, mask value)
for sub_address = 0 to (2^sub_address_size - 1)
pulse_next_pause
if no_collision_is_detected ; LRIS2K is inventoried
then
store (LRIS2K_UID)
else ; remember a collision was detected
push(mask,address)
endif
next sub_address
if stack_not_empty ; if some collisions have been detected and
then ; not yet processed, the function calls itself
poll_loop (sub_address_size); recursively to process the
last stored collision
endif
end poll_loop
main_cycle:
mask = null
address = null
push (mask, address)
poll_loop(sub_address_size)
end_main_cycle
92/98 Doc ID 13888 Rev 9

LRIS2K CRC (informative)
Appendix B CRC (informative)
B.1 CRC error detection method
The cyclic redundancy check (CRC) is calculated on all data contained in a message, from
the start of the flags through to the end of data. The CRC is used from VCD to LRIS2K and
from LRIS2K to VCD.
Table 95. CRC definition
CRC definition
CRC type Length Polynomial Direction Preset Residue
ISO/IEC 13239 16 bits X16 + X12 + X5 + 1 = 8408h Backward FFFFh F0B8h
To add extra protection against shifting errors, a further transformation on the calculated
CRC is made. The One’s Complement of the calculated CRC is the value attached to the
message for transmission.
To check received messages the 2 CRC bytes are often also included in the re-calculation,
for ease of use. In this case, the expected value for the generated CRC is the residue
F0B8h.
B.2 CRC calculation example
This example in C language illustrates one method of calculating the CRC on a given set of
bytes comprising a message.
C-example to calculate or check the CRC16 according to ISO/IEC 13239
#define POLYNOMIAL0x8408// x^16 + x^12 + x^5 + 1
#define PRESET_VALUE0xFFFF
#define CHECK_VALUE0xF0B8
#define NUMBER_OF_BYTES4// Example: 4 data bytes
#define CALC_CRC1
#define CHECK_CRC0
void main()
{
unsigned int current_crc_value;
unsigned char array_of_databytes[NUMBER_OF_BYTES + 2] = {1, 2, 3,
4, 0x91, 0x39};
int number_of_databytes = NUMBER_OF_BYTES;
int calculate_or_check_crc;
int i, j;
calculate_or_check_crc = CALC_CRC;
// calculate_or_check_crc = CHECK_CRC;// This could be an other
example
if (calculate_or_check_crc == CALC_CRC)
{
Doc ID 13888 Rev 9 93/98

CRC (informative) LRIS2K
number_of_databytes = NUMBER_OF_BYTES;
}
else // check CRC
{
number_of_databytes = NUMBER_OF_BYTES + 2;
}
current_crc_value = PRESET_VALUE;
for (i = 0; i < number_of_databytes; i++)
{
current_crc_value = current_crc_value ^ ((unsigned
int)array_of_databytes[i]);
for (j = 0; j < 8; j++)
{
if (current_crc_value & 0x0001)
{
current_crc_value = (current_crc_value >> 1) ^
POLYNOMIAL;
}
else
{
current_crc_value = (current_crc_value >> 1);
}
}
}
if (calculate_or_check_crc == CALC_CRC)
{
current_crc_value = ~current_crc_value;
printf ("Generated CRC is 0x%04X\n", current_crc_value);
// current_crc_value is now ready to be appended to the data
stream
// (first LSByte, then MSByte)
}
else // check CRC
{
if (current_crc_value == CHECK_VALUE)
{
printf ("Checked CRC is ok (0x%04X)\n",
current_crc_value);
}
else
{
printf ("Checked CRC is NOT ok (0x%04X)\n",
current_crc_value);
}
}
}
94/98 Doc ID 13888 Rev 9

LRIS2K Application family identifier (AFI) (informative)
Appendix C Application family identifier (AFI)
(informative)
The AFI (application family identifier) represents the type of application targeted by the VCD
and is used to extract from all the LRIS2K present only the LRIS2K meeting the required
application criteria.
It is programmed by the LRIS2K issuer (the purchaser of the LRIS2K). Once locked, it
cannot be modified.
The most significant nibble of the AFI is used to code one specific or all application families,
as defined in Ta b le 9 6 .
The least significant nibble of the AFI is used to code one specific or all application
subfamilies. Subfamily codes different from 0 are proprietary.
Table 96. AFI coding
(1)
AFI
Most
significant
nibble
‘0’ ‘0’ All families and subfamilies No applicative preselection
‘X’ '0 'All subfamilies of family X Wide applicative preselection
'X '‘Y’ Only the Yth subfamily of family X
‘0’ ‘Y’ Proprietary subfamily Y only
‘1 '‘0’, ‘Y’ Transport Mass transit, Bus, Airline,...
'2 '‘0’, ‘Y’ Financial IEP, Banking, Retail,...
'3 '‘0’, ‘Y’ Identification Access Control,...
'4 '‘0’, ‘Y’ Telecommunication Public Telephony, GSM,...
‘5’ ‘0’, ‘Y’ Medical
'6 '‘0’, ‘Y’ Multimedia Internet services....
'7 '‘0’, ‘Y’ Gaming
8 '‘0’, ‘Y’ Data Storage Portable Files,...
'9 '‘0’, ‘Y’ Item Management
'A '‘0’, ‘Y’ Express Parcels
AFI
Least
significant
nibble
Meaning
VICCs respond from
Examples / Note
'B '‘0’, ‘Y’ Postal Services
'C '‘0’, ‘Y’ Airline Bags
'D '‘0’, ‘Y’ RFU
'E '‘0’, ‘Y’ RFU
‘F’ ‘0’, ‘Y’ RFU
1. X = '1' to 'F', Y = '1' to 'F'
Doc ID 13888 Rev 9 95/98

Revision history LRIS2K
Revision history
Table 97. Document revision history
Date Revision Changes
13-Jun-2006 1 Initial release.
Figure 1.1: Memory mapping added.
Only bits set to ‘1’ are programmed to the AFI and DSFID Registers
19-Feb-2007 2
07-Sep-2007 3
08-Apr-2008 4
(see Section 30: Write AFI and Section 32: Write DSFID.
C
typical value for W4/3 modified in Table 92: DC characteristics.
TUN
Small text changes.
23.5 pF internal tuning capacitor (C
) value added (see Features
TUN
on page 1 and Table 92: DC characteristics.
modified for MLP in Table 90: Absolute maximum ratings.
V
ESD
Small text changes. Titles of Tab l e 6 2 and Ta b le 6 3 modified.
Response parameters modified in Section 35: Get Multiple Block
Security Status on page 72.
UFDFPN8 package mechanical data updated and dimensions in
inches rounded to four decimal digits instead of three in Ta bl e 9 4:
UFDFPN8 - 8-lead ultra thin fine pitch dual flat package no lead
(MLP) mechanical data
16-Sep-2008 5
24-Oct-2008 6
15-Dec-2009 7
LRIS2K products are no longer delivered in A1 inlays and A6 and A7
antennas.
Table 94: Ordering information scheme clarified.
Section 30: Write AFI and Section 32: Write DSFID: command
descriptions modified. Small changes in Table 90: Absolute
maximum ratings.
Note added to Table 2: Memory map.
Section 2: LRIS2K block security modified. Table 5: Read / Write
protection bit setting and block protection status modified to include
also the Password Control bits (Password Control bits table
removed), Write Password paragraph modified.
Addresses 1 and 2 removed from Table 7: LRIS2K block security
protection after power-up and Table 8: LRIS2K block security
protection after a valid presentation of password 1.
Option_flag specified in Section 25: Read Single Block.
Note added to Table 72: Protect status.
96/98 Doc ID 13888 Rev 9

LRIS2K Revision history
Table 97. Document revision history (continued)
Date Revision Changes
Removed unsawn wafer (W4) and MLP8 (MBTG).
Modified programming time to 5 ms.
Removed 23, 28.5, and 97 pF tuning capacitor.
Section 36: Kill: UID mandatory, and error code definition.
Removed Option_flag in Section 27: Lock Block, Section 30: Write
30-Sep-2010 8
AFI, Section 31: Lock AFI, Section 32: Write DSFID, Section 33:
Lock DSFID, Section 36: Kill. Specified Option_flag in Section 35:
Get Multiple Block Security Status.
Corrected IC reference in Table 59: Get System Info response format
when Error_flag is NOT set.
AFI_flag not supported by Fast Inventory and Inventory initiated
commands (see Section 41: Fast Inventory Initiated, Section 43:
Inventory Initiated).
19-Sep-2011 9
Updated Section 1: Description.
Updated disclaimer on last page.
Doc ID 13888 Rev 9 97/98

LRIS2K
Please Read Carefully:
Information in this document is provided solely in connection with ST products. STMicroelectronics NV and its subsidiaries (“ST”) reserve the
right to make changes, corrections, modifications or improvements, to this document, and the products and services described herein at any
time, without notice.
All ST products are sold pursuant to ST’s terms and conditions of sale.
Purchasers are solely responsible for the choice, selection and use of the ST products and services described herein, and ST assumes no
liability whatsoever relating to the choice, selection or use of the ST products and services described herein.
No license, express or implied, by estoppel or otherwise, to any intellectual property rights is granted under this document. If any part of this
document refers to any third party products or services it shall not be deemed a license grant by ST for the use of such third party products
or services, or any intellectual property contained therein or considered as a warranty covering the use in any manner whatsoever of such
third party products or services or any intellectual property contained therein.
UNLESS OTHERWISE SET FORTH IN ST’S TERMS AND CONDITIONS OF SALE ST DISCLAIMS ANY EXPRESS OR IMPLIED
WARRANTY WITH RESPECT TO THE USE AND/OR SALE OF ST PRODUCTS INCLUDING WITHOUT LIMITATION IMPLIED
WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE (AND THEIR EQUIVALENTS UNDER THE LAWS
OF ANY JURISDICTION), OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT.
UNLESS EXPRESSLY APPROVED IN WRITING BY TWO AUTHORIZED ST REPRESENTATIVES, ST PRODUCTS ARE NOT
RECOMMENDED, AUTHORIZED OR WARRANTED FOR USE IN MILITARY, AIR CRAFT, SPACE, LIFE SAVING, OR LIFE SUSTAINING
APPLICATIONS, NOR IN PRODUCTS OR SYSTEMS WHERE FAILURE OR MALFUNCTION MAY RESULT IN PERSONAL INJURY,
DEATH, OR SEVERE PROPERTY OR ENVIRONMENTAL DAMAGE. ST PRODUCTS WHICH ARE NOT SPECIFIED AS "AUTOMOTIVE
GRADE" MAY ONLY BE USED IN AUTOMOTIVE APPLICATIONS AT USER’S OWN RISK.
Resale of ST products with provisions different from the statements and/or technical features set forth in this document shall immediately void
any warranty granted by ST for the ST product or service described herein and shall not create or extend in any manner whatsoever, any
liability of ST.
ST and the ST logo are trademarks or registered trademarks of ST in various countries.
Information in this document supersedes and replaces all information previously supplied.
The ST logo is a registered trademark of STMicroelectronics. All other names are the property of their respective owners.
© 2011 STMicroelectronics - All rights reserved
STMicroelectronics group of companies
Australia - Belgium - Brazil - Canada - China - Czech Republic - Finland - France - Germany - Hong Kong - India - Israel - Italy - Japan -
Malaysia - Malta - Morocco - Philippines - Singapore - Spain - Sweden - Switzerland - United Kingdom - United States of America
www.st.com
98/98 Doc ID 13888 Rev 9
 Loading...
Loading...