state-of-the-art security for peripheral authentication
SO8N
4 x 5 mm
Features
Key functions
■ Peripheral authentication
■ Secure data read/write from/to peripheral
■ Secure counters
■ Configurable key management
■ Customizable security architecture
■ Configurable memory partitioning
AuKey
AuKey for brand protection
Data brief
Hardware
Security
■ Latest generation of STMicroelectronics highly
secure ST23 MCUs
– Active shield
– Monitoring of environmental parameters
– Protection mechanism against faults
– Unique serial number on each die
■ Advanced cryptography
– AES (Advanced Encryption Standard) for
symmetric architecture
– RSA (Rivest, Shamir and Adleman) or ECC
(elliptic curve) for asymmetric architecture
■ Secure operating system
– Secure Aukey kernel for authentication and
data management
– Life cycle management and secure
personalization
– Protection against logical and physical
attacks
■ Highly secure ST23 MCU platform
■ 1 to 18 Kbyte configurable non-volatile memory
– Highly reliable CMOS EEPROM submicron
technology
– 10 years data retention
– 500,000 erase / program cycles endurance
typical at 25 °C
– 1 to 32 bytes erase / program in 1.5 ms
– 3 to 5 V supply voltage range
Protocol
■ I²C serial interface
– 100 kbit/s transmission speed
– Up to 128 peripherals on single bus
Package
■ ECOPACK
®
SO8N 8-lead plastic small outline
November 2009 Doc ID 16750 Rev 1 1/6
For further information contact your local STMicroelectronics sales office.
www.st.com
6
Description AuKey
!PPLICATION
PROCESSOR
!U+EY
COMPANION
CHIP
(OST
!U+EY
PERIPHERAL
CHIP
0ERIPHERAL
)£#"US
6
##
3
$!
3
#,
0ERIPHERAL
0AIRING
!UTHENTICATIONSEC UREREADWRITE
!U+EY
PERIPHERAL
CHIP
AI
1 Description
1.1 Architecture
AuKey is a highly advanced flexible security architecture supporting symmetric and
asymmetric cryptography. It is implemented as a secure operating system running on the
latest generation secure microcontrollers and providing authentication and secure data
management services to the host application processor.
Symmetric cryptographic architecture
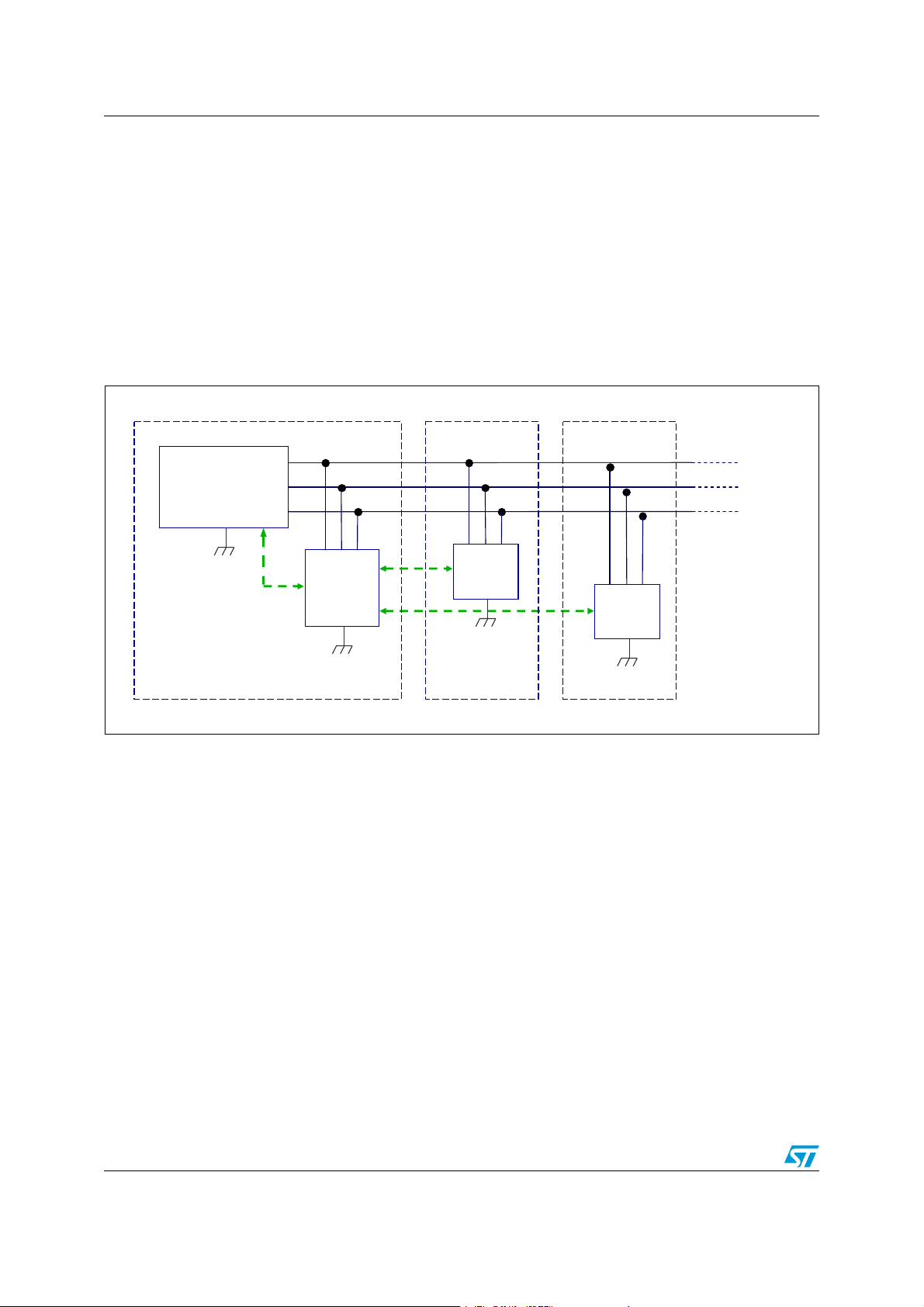
Figure 1. AuKey symmetric cryptographic architecture
The symmetric architecture (Figure 1) uses one AuKey secure microcontroller per
peripheral, and an AuKey secure microcontroller on the host main board. Symmetric
cryptography (AES) allows to authenticate and authorize access to AuKey peripheral chips.
It is also used for the secure channel between the host application processor and the AuKey
companion chip (optional pairing), and for an optional secure channel between the
equipment manufacturer remote server and the AuKey companion chip. This optional
channel may be used for application processor firmware upgrade.
The symmetric cryptographic architecture supports the following features:
● Authentication
Authentication serves to provide proof to a device application processor that a certain
peripheral is genuine. This allows an equipment manufacturer to ensure that only
authentic peripherals, accessories or consumables can be used in conjunction with the
original equipment. The application processor authenticates the AuKey peripheral chip
2/6 Doc ID 16750 Rev 1
 Loading...
Loading...