

Notices
Specifications may be changed without notice. This document is provided for
informational purposes only. I/O Software, Inc. makes no warranties, either
express or implied, as to the accuracy of this document. The entire risk of the
use, or the results of the use, of this product remains with the user. This product
may have a small possibility of granting access to persons other than those who
have registered their security token. In no event shall I/O Software, Inc. or our
representatives be liable for any incidental, consequential or special loss arising
from granting an access to persons other than those who have registered their
security token. In no event shall I/O Software, Inc., or our representatives, be
liable for any incidental, consequential or special loss arising from any use,
defect, malfunction, or fault of this product.
Version 4.0
©1998-2002 I/O Software, Inc. All rights reserved.
SecureSuite, SecureLaunch, SecureLogon, SecureSession, and SecureFolder
are trademarks or registered trademarks of I/O Software, Inc.
Sony and Puppy are trademarks of Sony Corporation.
Microsoft, Windows, and the Windows logo are registered trademarks of
Microsoft Corporation. All other trademarks and registered trademarks are
trademarks or registered trademarks of their respective holders.
I/O Software, Inc.
http://www.iosoftware.com

Table of Contents
Chapter 1: Welcome to SecureSuite............................................... 8
ABOUT THE GUIDE .......................................................................................................................... 8
NAMING CONVENTIONS AND TYPEFACES .................................................................................... 10
SYSTEM REQUIREMENTS............................................................................................................... 11
ADDITIONAL INFORMATION.......................................................................................................... 11
Chapter 2: SecureSuite Overview................................................. 12
SECURESUITE HIGHLIGHTS........................................................................................................... 12
ARCHITECTURE ............................................................................................................................. 15
SecureSuite XS Workstation vs. SecureSuite XS Server ............................................... 15
SecureSuite User Roles................................................................................................. 15
Chapter 3: Installing SecureSuite XS Workstation...................... 16
INSTALLATION .............................................................................................................................. 16
INITIAL LOGON PROCEDURE ......................................................................................................... 18
THE SECURESUITE WELCOME SCREEN......................................................................................... 19
Chapter 4: SecureSuite Key Features .......................................... 20
SYSTEM INTEGRITY VERIFICATION .............................................................................................. 20
RAS SUPPORT ............................................................................................................................... 20
POLICY MANAGEMENT ................................................................................................................. 20
CREDENTIAL CACHING ................................................................................................................. 21
RANDOMIZE PASSWORD ............................................................................................................... 21
LOGON TIME.................................................................................................................................. 21
WINDOWS SYSTEM TRAY ............................................................................................................. 22
SecureSession for Applications Icon ............................................................................ 22
Authentication Method Icons........................................................................................ 22
Chapter 5: Using SecureSuite....................................................... 23
SECURESUITE LICENSE MANAGER ............................................................................................... 23
The License Manager Properties Dialog ..................................................................... 23
Product License Keys ................................................................................................... 24
User License Keys ........................................................................................................25
Duplicate License Keys ................................................................................................26
SECURESUITE USER AUTHENTICATION ........................................................................................ 27
Authentication Methods................................................................................................ 27
Verification vs. Identification ....................................................................................... 28
Multiple Authentication Methods ................................................................................. 28
The Authentication Dialog ........................................................................................... 29
SECURESUITE ICONS AND THE WELCOME SCREEN ...................................................................... 31
SecureSuite Icons.......................................................................................................... 31
The SecureSuite Welcome Screen................................................................................. 32
USING THE SECURESUITE HELP SYSTEM...................................................................................... 33
ONE-TOUCH LOGON ..................................................................................................................... 33
WORKSTATION SECURITY............................................................................................................. 34

Locking Your Workstation............................................................................................ 34
Unlocking Your Workstation ........................................................................................34
Chapter 6: Account Management ................................................. 35
MY SECURESUITE SETTINGS ........................................................................................................ 35
USER PROPERTIES – SECURESUITE POLICIES ............................................................................... 36
AUTHENTICATION METHODS........................................................................................................ 37
USER PROPERTIES – SECURESESSION POLICIES ........................................................................... 38
Changing User-Level Policy Settings........................................................................... 39
Modifying Individual SecureSession Account Information .......................................... 40
Changing policies for an individual application window or web site.......................... 42
USER PROPERTIES – SECUREFOLDER POLICIES............................................................................ 43
Chapter 7: System Administration................................................ 44
ADMINISTERING SECURESUITE ON WINDOWS 2000 AND XP PROFESSIONAL ............................. 44
SecureSuite User Manager........................................................................................... 44
Creating a New User Account...................................................................................... 45
ADMINISTERING SECURESUITE ON WINDOWS XP HOME ............................................................ 47
SecureSuite User Manager........................................................................................... 47
Creating a New User Account...................................................................................... 49
ADDING AUTHENTICATION METHODS TO A USER ACCOUNT....................................................... 54
User License Keys ........................................................................................................54
Chapter 8: SecureSuite System Settings..................................... 56
SYSTEM SETTINGS – POLICIES ...................................................................................................... 59
SYSTEM SETTINGS – AUTHENTICATION METHODS ...................................................................... 60
Managing Authentication Devices on Windows 2000 and XP Professional................ 61
SYSTEM SETTINGS – DATABASE................................................................................................... 62
Local Database Backup - Setup and Operation ...........................................................63
SYSTEM SETTINGS – SECUREFOLDER........................................................................................... 64
SYSTEM SETTINGS – SECURELAUNCH.......................................................................................... 64
SYSTEM SETTINGS – SECURESESSION FOR APPLICATIONS .......................................................... 65
SYSTEM SETTINGS – SECURESESSION FOR INTERNET EXPLORER ................................................ 65
SYSTEM SETTINGS – COMMUNICATION SETTINGS ....................................................................... 66
Port Settings .................................................................................................................67
Timeouts ....................................................................................................................... 67
Virtual IP ......................................................................................................................67
Chapter 9: SecureSession............................................................. 68
SECURESESSION FOR APPLICATIONS ............................................................................................ 69
Registering an Application ...........................................................................................70
Activating SecureSession for Applications................................................................... 74
Editing SecureSession Information ..............................................................................75
Removing Registered Application Information ............................................................ 76
SECURESESSION FOR INTERNET EXPLORER.................................................................................. 77
Registering a Web Site.................................................................................................. 78
Activating SecureSession for Internet Explorer ........................................................... 80
Editing SecureSession Information ..............................................................................81
Removing Registered Web Site Information................................................................. 82
Chapter 10: SecureFolder.............................................................. 83

SECURING A FILE OR FOLDER ....................................................................................................... 84
SECUREFOLDER EMERGENCY RECOVERY UTILITY...................................................................... 85
Choosing your Emergency Recovery Passphrase ........................................................ 85
Changing your Emergency Recovery Passphrase........................................................ 86
Disabling the Emergency Recovery Utility ..................................................................87
SECUREFOLDER SHARING............................................................................................................. 88
WORKING WITH SECURED FILES AND FOLDERS ........................................................................... 90
REMOVING SECURITY FROM A FILE OR FOLDER .......................................................................... 91
Chapter 11: SecureLaunch............................................................ 92
SETTING USER RESTRICTIONS ...................................................................................................... 92
Changing User Restrictions ......................................................................................... 97
REMOVING USER RESTRICTIONS .................................................................................................. 98
SECURELAUNCH ACCESS POLICY RULES ................................................................................... 100
Chapter 12: SecureSuite Program Maintenance ....................... 101
CHANGING YOUR CONFIGURATION ............................................................................................ 101
Installing OEM Device Modules ................................................................................ 102
Removing OEM Device Modules................................................................................ 104
UNINSTALLING SECURESUITE XS WORKSTATION ..................................................................... 106
Appendix 1: Troubleshooting...................................................... 107
COMMON USER PROBLEMS......................................................................................................... 107
Appendix 2: Glossary .................................................................. 109
Appendix 3: A Table of SecureSuite Policies ............................ 115
DOMAIN/SYSTEM-LEVEL SECURESUITE POLICIES ..................................................................... 115
POLICY ........................................................................................................................................ 115
AVAILABLE SETTINGS................................................................................................................. 115
LIMITS SETTINGS OF…................................................................................................................ 115
DEPENDS ON SETTING OF… ........................................................................................................ 115
USER-LEVEL SECURESUITE POLICIES......................................................................................... 116
POLICY ........................................................................................................................................ 116
AVAILABLE SETTINGS................................................................................................................. 116
LIMITS SETTINGS OF…................................................................................................................ 116
DEPENDS ON SETTING OF… ........................................................................................................ 116
USER-LEVEL SECUREFOLDER POLICIES ..................................................................................... 116
POLICY ........................................................................................................................................ 116
AVAILABLE SETTINGS................................................................................................................. 116
LIMITS SETTINGS OF…................................................................................................................ 116
DEPENDS ON SETTING OF… ........................................................................................................ 116
DOMAIN/SYSTEM-LEVEL SECUREFOLDER POLICIES.................................................................. 117
POLICY ........................................................................................................................................ 117
AVAILABLE SETTINGS................................................................................................................. 117
LIMITS SETTINGS OF…................................................................................................................ 117
DEPENDS ON SETTING OF… ........................................................................................................ 117
USER-LEVEL SECURESESSION FOR INTERNET EXPLORER POLICIES .......................................... 117
POLICY ........................................................................................................................................ 117
AVAILABLE SETTINGS................................................................................................................. 117
LIMITS SETTINGS OF…................................................................................................................ 117
DEPENDS ON SETTING OF… ........................................................................................................ 117
SITE-LEVEL SECURESESSION FOR INTERNET EXPLORER POLICIES............................................ 118

POLICY ........................................................................................................................................ 118
AVAILABLE SETTINGS................................................................................................................. 118
LIMITS SETTINGS OF…................................................................................................................ 118
DEPENDS ON SETTING OF… ........................................................................................................ 118
DOMAIN/SYSTEM-LEVEL SECURESESSION FOR INTERNET EXPLORER POLICY ......................... 118
POLICY ........................................................................................................................................ 118
AVAILABLE SETTINGS................................................................................................................. 118
LIMITS SETTINGS OF…................................................................................................................ 118
DEPENDS ON SETTING OF… ........................................................................................................ 118
USER-LEVEL SECURESESSION FOR APPLICATIONS POLICIES..................................................... 118
POLICY ........................................................................................................................................ 118
AVAILABLE SETTINGS................................................................................................................. 118
LIMITS SETTINGS OF…................................................................................................................ 118
DEPENDS ON SETTING OF… ........................................................................................................ 118
APPLICATION-LEVEL SECURESESSION FOR APPLICATIONS POLICIES........................................ 119
POLICY ........................................................................................................................................ 119
AVAILABLE SETTINGS................................................................................................................. 119
LIMITS SETTINGS OF…................................................................................................................ 119
DEPENDS ON SETTING OF… ........................................................................................................ 119
DOMAIN/SYSTEM-LEVEL SECURESESSION FOR APPLICATIONS POLICY .................................... 119
POLICY ........................................................................................................................................ 119
AVAILABLE SETTINGS................................................................................................................. 119
LIMITS SETTINGS OF…................................................................................................................ 119
DEPENDS ON SETTING OF… ........................................................................................................ 119
SECURELAUNCH ACCESS POLICY............................................................................................... 119
POLICY ........................................................................................................................................ 119
AVAILABLE SETTINGS................................................................................................................. 119
LIMITS SETTINGS OF…................................................................................................................ 119
DEPENDS ON SETTING OF… ........................................................................................................ 119

Chapter 1: Welcome to SecureSuite
Chapter 1: Welcome to SecureSuite
About the Guide
The SecureSuite XS User’s Guide is designed to introduce and familiarize you
with SecureSuite’s many features and applications. It also provides the
information necessary for you to customize SecureSuite to meet your specific
needs and security requirements.
This manual has been divided into 12 chapters, providing an overview of
SecureSuite as well as operating instructions for the various SecureSuite
applications.
• Chapter 1: Welcome to SecureSuite introduces you to the SecureSuite XS
Workstation Guide. It also defines the minimum system requirements for a
SecureSuite XS installation, important naming conventions, and where to
look when you need more information.
• Chapter 2: SecureSuite Overview provides an overview of SecureSuite and
it’s features.
• Chapter 3: Installing SecureSuite XS Workstation explains the SecureSuite
installation process, including the initial logon procedure.
• Chapter 4: SecureSuite Key Features explains some important features of
SecureSuite, such as credential caching, RAS support, system binary
verification, and password randomization options.
• Chapter 5: Using SecureSuite describes the main functionality of
SecureSuite, including detailed instructions and tips.
• Chapter 6: Account Management explains how to set up and maintain your
own user account, including how to set your user-level policies and manage
your authentication methods.
• Chapter 7: System Administration explains how to set up the SecureSuite
SecureSuite XS Workstation Guide 8

Chapter 1: Welcome to SecureSuite
User Manager, add a new user account to SecureSuite, and make new
methods of authentication available.
• Chapter 8: SecureSuite System Settings describes the various system
properties, including system policies, device management, event logging,
database management, SecureFolder policies, SecureSession policies,
communication settings, and logon settings for identification devices. It also
covers the basics of how to secure applications with SecureLaunch.
• Chapter 9: SecureSession explains how to use the “password bank” and
account management functionality of SecureSession for Internet Explorer for
web sites and SecureSession for Applications for Windows applications.
• Chapter 10: SecureFolder explains how to use SecureFolder, a SecureSuite
application that provides security for files and folders.
• Chapter 11: SecureLaunch explains how to set and remove restrictions in
order to prevent unauthorized users from running Windows applications.
• Chapter 12: SecureSuite Program Maintenance explains how to modify,
repair, or uninstall SecureSuite.
• The Appendices include supplemental material that provides quick access to
important information. Appendix 1 lists common user problems and
troubleshooting techniques. Appendix 2 contains a glossary, which covers
important terms used in SecureSuite. Appendix 3 contains a table of
SecureSuite policies.
SecureSuite XS Workstation Guide 9

Chapter 1: Welcome to SecureSuite
Naming Conventions and Typefaces
Information within this guide is clearly structured with descriptive instructions as
well as many step-by-step examples on how to implement or configure a particular
feature. These are supplemented with graphics that make the instructions easy to
follow.
Note: Notes generally represent information that requires special
attention. Notes in the manual will be displayed in this typeface.
More Info: References to other books and sources of information are offered
throughout the manual.
Important: These notes contain important warnings about the subject at hand –
critical information about the security of your system.
Specific names and instructions (as they appear on your
computer screen) are displayed in this typeface.
SecureSuite XS Workstation Guide 10
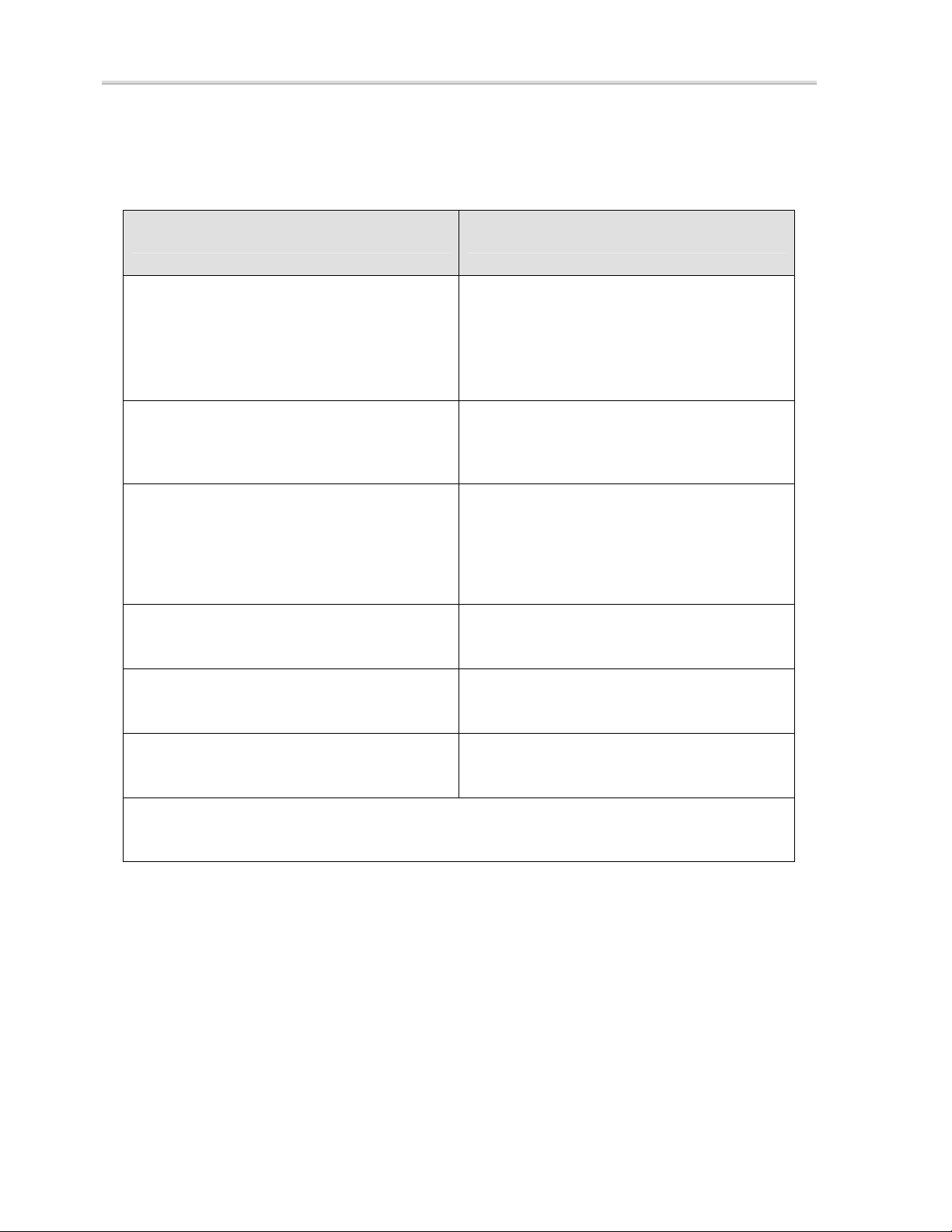
System Requirements
Requirements Recommendations
Chapter 1: Welcome to SecureSuite
Windows 2000 w/ SP1
Windows XP Professional or Windows XP
Home Edition
For SecureSession for Internet Explorer, IE
4.x or above
At least one network client service installed,
with TCP/IP available
Pentium II-350 or better Pentium III-700 or better
128 MB of RAM 256 MB of RAM
Windows 2000 w/ SP2
Windows XP Professional
Internet Explorer 6.0 or above
MS client for MS networks and TCP/IP
30 MB of free hard disk space 30 MB of free hard disk space
For client/server functionality, the domain must have DNS capability
Table 1: System Requirements
Additional Information
Refer to the SecureSuite Release Notes for the most current information and
general issues. The
the
Release Notes after installation, from the Start menu, select Programs,
SecureSuite and click SecureSuite Release Notes.
SecureSuite XS Workstation Guide 11
Release Notes are available during installation. To view

Chapter 2: SecureSuite Overview
Chapter 2: SecureSuite Overview
SecureSuite is an enhanced security software solution that seamlessly integrates
with the Windows 2000 and Windows XP operating systems to provide
biometrically enabled user authentication services and additional functionality.
SecureSuite supports stand-alone workstation installations, as well as full
client/server functionality. SecureSuite is the most comprehensive biometric
security solution available on the market today, supporting the largest number and
widest variety of biometric and non-biometric authentication devices.
Computer security has traditionally been based on two authentication methods:
Something you know (e.g., passwords) and something you have (e.g., smart
cards, tokens). In recent years, a third method of security has emerged:
Something you are, known as biometrics. With biometrics, users can verify their
identity via unique physical characteristics, such as their fingerprint, iris, retina,
hand, face, or voice.
SecureSuite XS is an integrated 4-in-1 software package that provides a suite of
security applications for Windows 2000 and Windows XP. SecureSuite’s scalable
authentication infrastructure improves security, enhances user convenience,
reduces costs and increases productivity. SecureSuite is unique in that it allows
users to utilize a wide range of powerful and secure authentication methods such
as passwords, biometrics, smart cards, token devices, and any combination of
these. These advanced authentication methods can be used to control access to
sensitive files and applications. In addition to enhancing standard logon
procedures, SecureSuite includes SecureSession, SecureLaunch, and
SecureFolder, providing powerful tools that are necessary for the security and
productivity of your PC.
SecureSuite Highlights
SecureSuite provides system administrators with a complete set of tools for
managing user accounts and controlling access to information via an intuitive and
easy-to-use software package. SecureSuite also addresses the need for a robust
and rich set of security services users once they are logged on to a domain.
SecureSuite’s functionality includes:
• SecureSuite enables deployment of a wide range of biometric and non-
biometric authentication technologies through single-factor and multi-factor
authentication.
• SecureSuite seamlessly supports the Windows 2000, Windows XP
Professional and Windows XP Home platforms.
• SecureSuite is highly scalable, supporting a single user in one location to
members of an enterprise scattered around the globe.
SecureSuite XS Workstation Guide 12

Chapter 2: SecureSuite Overview
• User-friendly wizards facilitate the installation and enrollment of
authentication methods including smart cards, tokens or biometric devices.
• SecureSuite provides efficient administrator tools, such as the SecureSuite
User Manager, which enables full user management, from system policies
to biometric enrollment.
• SecureSession captures and stores information for application windows and
web sites, and releases the information upon authentication.
• SecureFolder allows you to easily protect files with strong encryption. The
locking/unlocking of directories and the encryption/decryption of files can be
activated by a SecureSuite-compatible authentication device.
• With SecureLaunch, Windows-based applications can easily be secured to
prevent unauthorized use.
• Credential caching allows credentials from the last successful logon to a
remote domain to be stored on the client computer. This allows users to log
on to client computers in the event that they are disconnected from the
network or if all the domain controllers are down.
• SecureSuite supports Remote Access Service (RAS) connections. Using a
RAS connection via a modem, a client computer can operate as if it were
physically connected to a LAN.
• Administration is easy and powerful using the native MMC-style snap-ins for
system policy and user account management.
• Password randomization options allow system administrators to enable or
disable SecureSuite management of user passwords. This feature is
invisible to the user and, when enabled, enhances system security. Refer to
Chapter 4: SecureSuite Key Features for a detailed explanation of this
feature.
• SecureSuite administrators can quickly and easily view event-logging details.
An administrator can use
security and application event logs.
Event Viewer to view and manage system
• One-Touch Logon Support provides users with single sign-on capabilities
with all SecureSuite applications.
• SecureSuite is BAPI (Biometric Application Programming Interface)
compliant.
This sophisticated and empowering suite of security features and applications
offers advanced security via a wide range of authentication methods. Following is
a list of the security applications available with SecureSuite:
SecureSuite XS Workstation Guide 13

Chapter 2: SecureSuite Overview
SecureLogon: SecureLogon enhances the normal logon procedure for
Windows, enabling you to log on to your system securely and easily using one or
multiple authentication methods and devices supported by SecureSuite.
SecureSession: SecureSession is composed of two applications:
• SecureSession for Applications (SecureSession/Apps) stores passwords and
other text-based information for application windows, and enters the
information for you.
• SecureSession for Internet Explorer (SecureSession/IE) stores
authentication information, such as user names and passwords for web sites,
and enters it for you.
SecureFolder: SecureFolder is a powerful, fast and convenient way to protect
data. With a right-click you can secure folders, allowing only authorized users to
view the contents. SecureFolder also encrypts individual files. Secured folders
look and function like other Windows folders: You can "drag and drop" files into
and out of the secured folder. All of the security functions in SecureFolder take
place quickly and transparently. SecureFolder also includes an emergency data
recovery utility for use in the event that some or all data encryption/decryption
keys are lost.
SecureLaunch: SecureLaunch prevents unauthorized users from running
Windows applications. Administrators can secure most programs, and set access
permissions for individual users or groups of users. This application is very
convenient for accounting software and databases that contain sensitive or
confidential information, or for controlling usage of games and entertainment
software.
SecureSuite XS Workstation Guide 14

Chapter 2: SecureSuite Overview
Architecture
This section provides an overview of product operation, including details about
SecureSuite XS Server, SecureSuite XS Workstation, and SecureSuite user roles.
SecureSuite XS Workstation vs. SecureSuite XS Server
SecureSuite XS Workstation: SecureSuite XS Workstation is a complete
package that can operate with or without SecureSuite XS Server installed.
SecureSuite XS Workstation provides all the user applications and authentication
software for a stand-alone workstation. It automatically detects the SecureSuite
XS Server (if installed) and then acts as a client.
SecureSuite XS Server: SecureSuite XS Server is a server application designed
to support an Active Directory domain. As in the Windows domain model,
SecureSuite XS Server provides centralized user management and authentication
services. Many of these services are also accessible from domain clients. In
addition, the standard functionality of the domain model is also supported including
user roaming and server fail-over protection.
SecureSuite User Roles
SecureSuite defines two distinct user roles that are equivalent to the
corresponding Windows user groups:
• Administrator – Installs and maintains software on systems, manages user
accounts, manages authentication methods and associated devices, and
manages security and related policies.
• User – A standard resource user. No special privileges or abilities.
Refer to Microsoft Windows documentation for more information on group
memberships.
SecureSuite XS Workstation Guide 15
Chapter 3: Installing SecureSuite XS Workstation
Chapter 3: Installing SecureSuite XS Workstation
Prior to running the installer, please verify that you have at least one network client
installed on the target system. This can be verified by viewing the properties of
any available connection in
by right-clicking the connection icon and selecting
Microsoft Networks (or something similar) is not listed, click the Install or
Add button, then select Client and press OK. The list of available clients will then
be available. We highly recommend that you select
Networks. If no connection is available or established, please contact your
system administrator.
Installation
Important: Software installation requires local administrator privileges in the case
of a workstation-only setup, or domain administrator privileges for domain
installations. Before installing SecureSuite, close all applications and disable your
virus detection software.
Network Neighborhood or My Network Places
Properties. If Client for
Client for Microsoft
Important: Please refer to the Sony® Puppy® installation guide (“Training Your
Puppy Unit”) included in your package or on the CD-ROM for specific instructions
on the installation and use of your fingerprint identity device.
To install SecureSuite:
1. Insert the SecureSuite CD into your CD-ROM drive. Wait
for the installation to start automatically.
2. If the software does not auto-initiate, select
taskbar and then click
Run. In the Run dialog, type
Start from the
D:\Setup.exe (where D is the drive letter for your CD-
ROM drive or other source media).
3. Follow the onscreen instructions, which are outlined below.
Welcome: Click
Next to continue.
License Agreement: You must accept the terms of this license
agreement by checking the
license agreement
installation. Click
SecureSuite XS Workstation Guide 16
Next to continue.
I accept the terms in the
check box to proceed with the

Chapter 3: Installing SecureSuite XS Workstation
Product License Key: Enter the product license key provided
on a label on the SecureSuite CD envelope. Click Next to
continue. If the product license key entered is invalid or already
in use, you will be prompted to enter a new one after restarting
your system.
Release Notes: Select the
Yes check box to review the
Release Notes for important information about installing and
using SecureSuite. If you deselect this check box, you may
view the Release Notes at a later time. Click Next to
continue.
Customer Information: Enter your name and company
information. Click
Complete or Custom Setup: Choose the type of setup that
best suits your needs. If you select Custom Setup, you can
select the program features that you want installed. You can
accept the default destination, or click the
select an alternate path, to which SecureSuite files will be
installed. Complete Setup will not allow for any modifications.
Next to continue.
Click
Shortcut Icon
Next to continue.
Change button to
: Select the Create a SecureSuite desktop
icon check box to have a SecureSuite shortcut group icon
placed on your desktop, from which you can access all
SecureSuite functionality. Click
Next to continue.
Install: Click
Device Setup: If you are installing an authentication device
module at this time, you will be instructed to connect your
authentication device. Refer to the Installing OEM Device
Modules section in Chapter 12 of this manual for more
information.
Restart: Click
You have completed your software installation. Once your
machine restarts, any user who previously existed on the
system will have now become “SecureSuite enabled”. To log
on to your system, supply your Windows password, which
existed before installing SecureSuite.
SecureSuite XS Workstation Guide 17
Install to initiate the installation process.
Yes to restart your machine.

Initial Logon Procedure
To log on to your system after installation:
Chapter 3: Installing SecureSuite XS Workstation
1. Press
Ctrl + Alt + Delete as prompted by the
SecureSuite Authentication dialog.
2. Enter your user name and password.
3. Click
4. Click
Note: On some systems running Windows 2000 and XP, it is not
necessary to press Ctrl+Alt+Delete as it may be disabled. Consult
your Windows documentation for more information.
Options to change the target domain on which to
authenticate. Select the
check box to view instructions specific to your account.
Authentication Details
OK or press Enter when finished.
SecureSuite XS Workstation Guide 18
Chapter 3: Installing SecureSuite XS Workstation
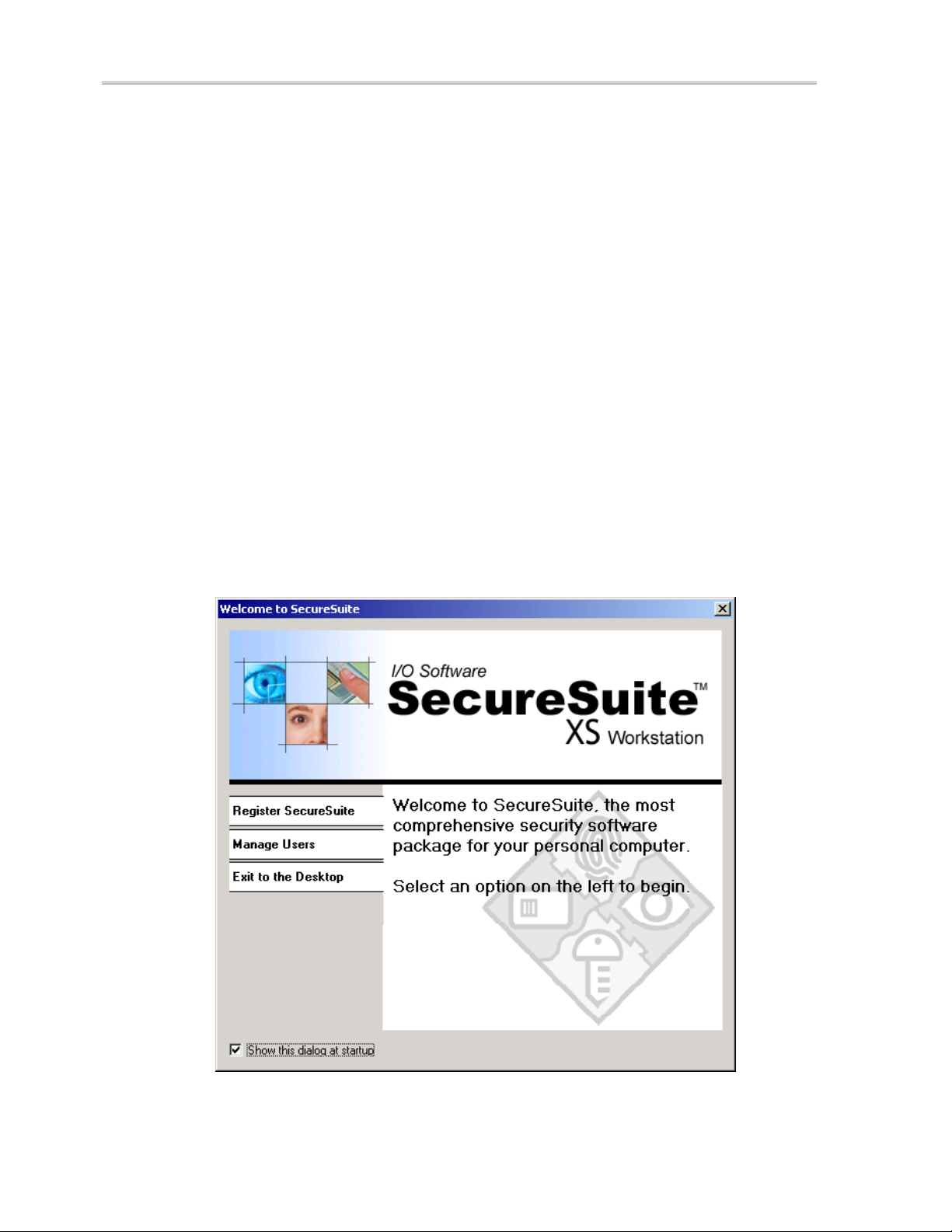
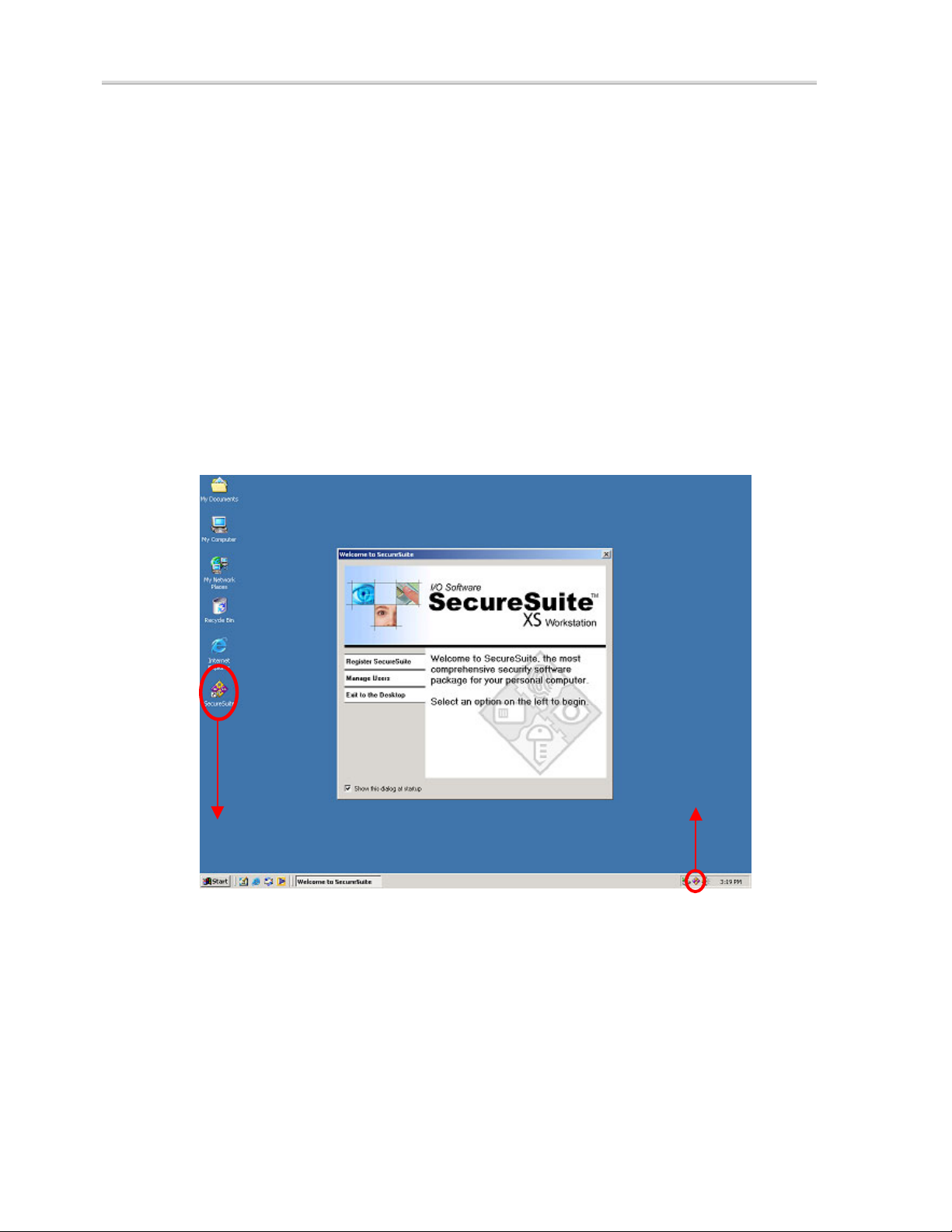
The SecureSuite Welcome Screen
Upon successful authentication, your desktop will appear and you will see the
SecureSuite Welcome Screen. From this screen, you can register your
SecureSuite software, create a new user account, or exit to the desktop.
Register SecureSuite: Click this tab to register SecureSuite and take
advantage of product update notifications and technical support. Your Internet
connection must be active in order to register SecureSuite.
Manage Users: Click this tab to create a new user account. You will be taken
directly to the
SecureSuite users.
Exit to the Desktop: Click this tab to close the Welcome Screen.
Deselect the Show this dialog at startup check box if you do not want
the
Welcome Screen to appear each time you log on.
Local Users and Groups dialog, from which you can enroll new
Figure 1: SecureSuite Welcome Screen
SecureSuite XS Workstation Guide 19

Chapter 5: Using SecureSuite
Chapter 4: SecureSuite Key Features
System Integrity Verification
On every system restart, SecureSuite makes sure all installed SecureSuite
binaries have not been tampered with, replaced, etc. If any corrupt or missing files
are detected, SecureSuite will display a message alerting you of the problem. At
this point, only an administrator will be able to log on to the computer and either
repair or uninstall SecureSuite via the Windows
Control Panel, or by re-running the SecureSuite installation program
(
Setup.exe).
Add/Remove application in the
RAS Support
SecureSuite supports Remote Access Service (RAS) connections. Using a RAS
connection, a client computer can operate as if it were physically connected to a
LAN. RAS makes it possible to connect a remote client workstation to a network
server. This can be accomplished over a Wide Area Network (WAN) link or a
Virtual Private Network (VPN) using a dial-up connection. The user authentication
required in order to establish RAS and/or VPN connections are not controlled by
SecureSuite.
The user may notice a delay corresponding to certain activities. The initial logon
will take longer. Use of some SecureSuite features may also take longer as the
bandwidth available over RAS is limited compared to that available over Ethernet
or other network topology.
Policy Management
A computer’s configuration is defined in terms of policies. A policy is a permission
or attribute for a particular item, action, or object. The ability to consistently
manage policies is an essential feature in SecureSuite. All administrator tools are
centralized and easy to use. This will lead to lower administration overhead and
an enhanced network/server security system. SecureSuite defines four levels of
policies: system-level policies, user-level policies, application policies, and userlevel application policies. For the two SecureSession applications, there is a
another level of policies called “site-level” or “application-level” policies, which are
only relevant for and applied to the website or application for which they are set.
The settings of some policies affect (and are affected by) the settings of others.
See Appendix 3: A Table of SecureSuite Policies for an overview of the policies
and the dependencies they have on each other.
SecureSuite XS Workstation Guide 20

Chapter 5: Using SecureSuite
Credential Caching
Credential caching is a feature that allows the credentials of the last successful
logon to a remote domain to be securely cached (stored) on a client computer.
This policy can be enabled at the system level, or set per user via the
SecureSuite User Manager. If the client computer should become
disconnected from the network or if no authentication servers are available, the
last 10 users who successfully authenticated to the remote domain can perform
the same logon procedure and have the standard user desktop available (the user
will not be able to access the network). This is a convenient feature for those who
plan to travel with their workstation. Credentials uniquely identify a user within the
scope of a domain. Credential-cached logon compares submitted credentials
against the credentials that have been stored on the computer. You can configure
credential-caching policies through the
dialog, discussed later in this manual. By default, the credential caching policies
are enabled. These policies will be available to remote domain users only. They
will not appear on local machines (stand-alone workstations).
SecureSuite System Properties
Randomize Password
Password randomization is a powerful security feature that provides maximum
protection against password-based security attacks. This feature will automatically
change a user’s Windows password to a secure random password every time the
user authenticates. This prevents users from accessing SecureSuite protected
network resources from workstations that do not have SecureSuite installed. The
randomization process takes place without user knowledge or participation.
You can configure password randomization policies for all users and for
through the
manual. If password randomization is set as
then you can also enable or disable password randomization for each individual
user via the
is disabled (user defined) for all users, enabled for
each individual user.
SecureSuite System Settings dialog discussed later in this
User Defined at the system level,
SecureSuite User Manager. By default, password randomization
AND users, and disabled for
AND users
Logon time
Placing your cursor over the SecureSuite icon in the system tray will display how
long the current user has been logged on to the system.
Figure 2: SecureSuite Logon Time
SecureSuite XS Workstation Guide 21
Chapter 5: Using SecureSuite
App
Windows System Tray
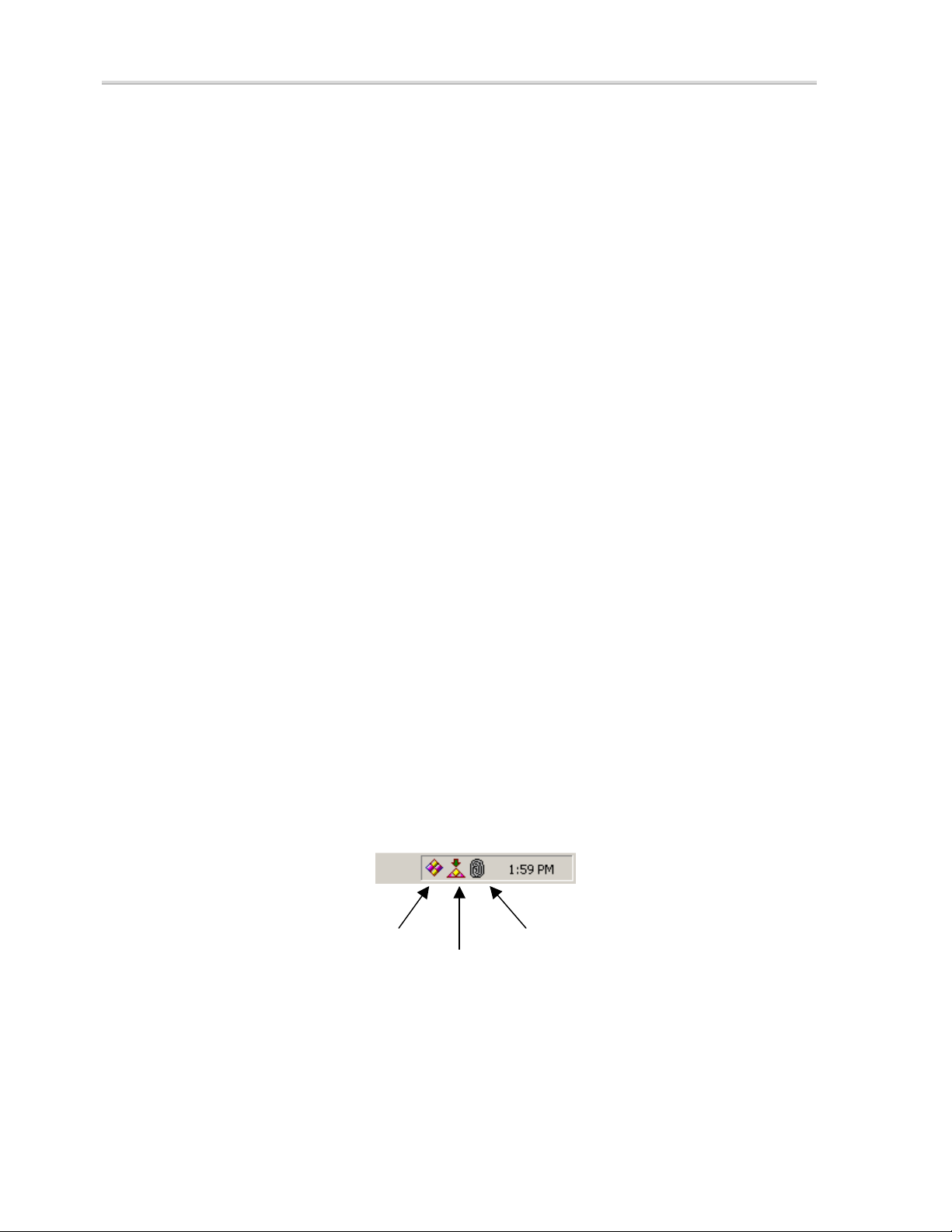
SecureSuite adds a SecureSuite shortcut icon to the Windows system tray. The
SecureSuite system tray icon allows you to access most SecureSuite functionality
quickly and conveniently. If enabled, the SecureSession for Applications icon and
any method icons will also appear in the system tray.
SecureSession for Applications Icon
The SecureSession for Applications icon allows users to register and manage
SecureSession data. See the SecureSession for Applications section in Chapter 9
of this manual.
Authentication Method Icons
If the logged-on user is associated with a biometric authentication method that fully
supports the concept of multiple sources (e.g., two or more fingerprints, each one
being a source), the method’s system tray icon may be displayed in the system
tray. From the SecureSuite shortcut icon (represented by the SecureSuite logo), a
user can choose to show or hide method icon(s) by checking or unchecking the
Show SecureSuite Method Icons option (which will only be available if the
user is enrolled with at least one method that supports this feature).
When a user clicks the method icon, a dialog appears that allows the user to
select their current and/or default source during the authentication process. In the
case of the fingerprint method, the dialog will typically contain a graphic of two
hands with all 10 fingers represented. These method-specific source dialogs
indicate all sources that have been enrolled for that authentication method. For
example, a red dot on the tip of a finger signifies that the fingerprint is currently
selected for authentication. To select a different fingerprint, click the
corresponding finger.
SecureSuite Icon
SecureSession for
lications icon
Figure 3: Fingerprint Icon, Windows System Tray
Fingerprint Icon
SecureSuite XS Workstation Guide 22

Chapter 5: Using SecureSuite
Chapter 5: Using SecureSuite
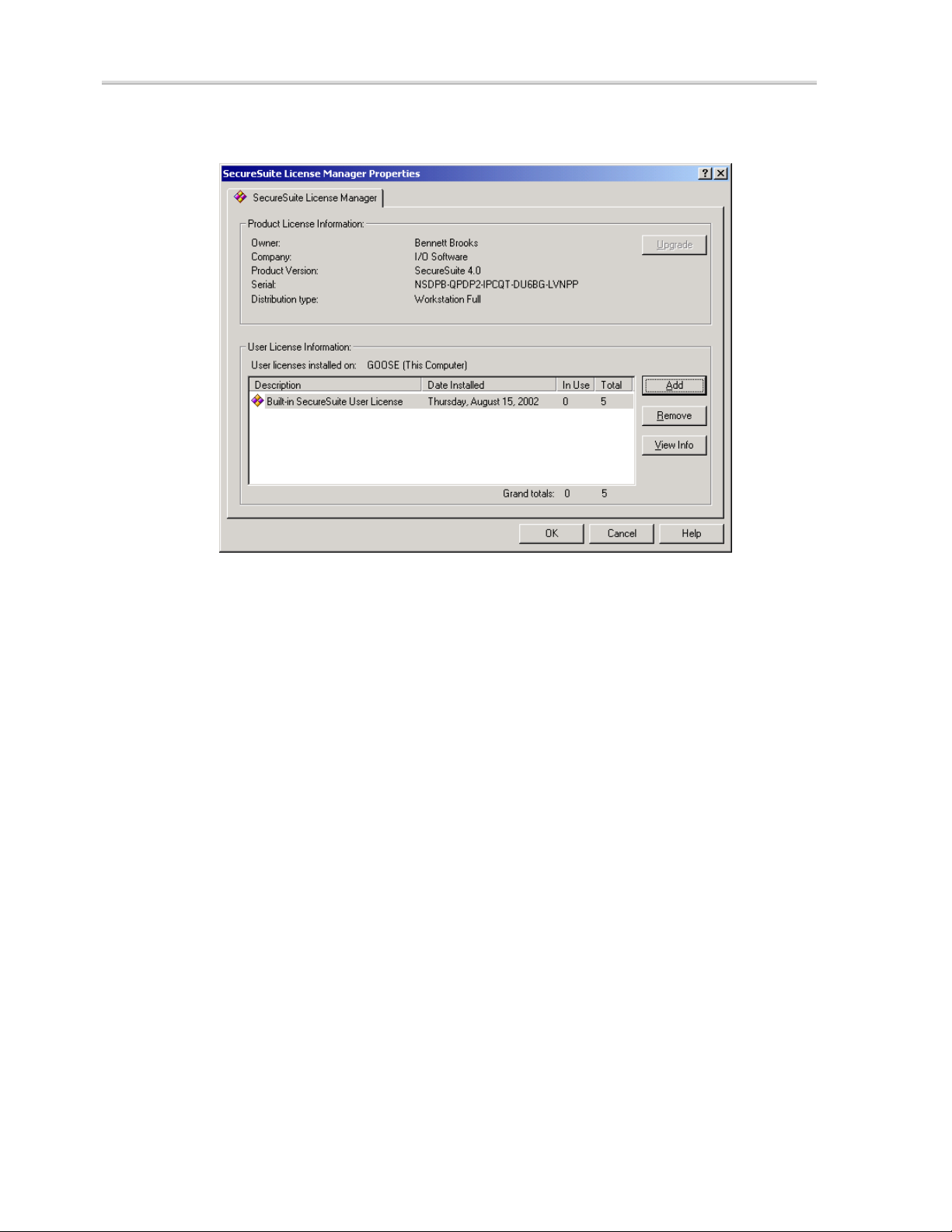
SecureSuite License Manager
The SecureSuite License Manager is an easy-to-use tool for managing your
Product License Key and User License Keys.
The License Manager Properties Dialog
From the SecureSuite License Manager Properties dialog, administrators
can enter a new Product License Key in order to upgrade SecureSuite and utilize
features that may be disabled in a demo or evaluation version, or add new User
License Keys.
To access the
SecureSuite License Manager
Properties dialog:
1. From the Start menu, select Programs, SecureSuite,
and click
2. Double-click SecureSuite
pane. The
SecureSuite License Manager.
License Manager in the right
SecureSuite License Manager
Properties dialog appears.
SecureSuite XS Workstation Guide 23
Chapter 5: Using SecureSuite
Figure 4: SecureSuite License Manager
Product License Keys
Your SecureSuite Product License Key, which you received with your SecureSuite
software for use during the installation process, is synonymous with a serial
number. You must have a valid, unique Product License Key in order to install
and use SecureSuite. This Product License Key determines the version of your
SecureSuite installation.
To enter a new Product License Key in order to upgrade your
version of SecureSuite:
1. In the
dialog, click the
SecureSuite License Manager Properties
Upgrade button. The Upgrade Product
License dialog appears.
2. Enter your new Product License Key, and click
3. Click
Yes when prompted to reboot your computer. When
your system restarts, SecureSuite will be upgraded
according to the Product License Key entered.
OK.
SecureSuite XS Workstation Guide 24

Chapter 5: Using SecureSuite
User License Keys
With SecureSuite installed on your system, all users may use the password
method for authentication. However, in order for a user to employ any other
authentication method supported by SecureSuite, a user license must be
available. Each user license enables a single user to have any SecureSuiterelated authentication method (or combination of methods) assigned to their
account. Enrolling a single user with multiple methods does not use multiple user
licenses. That is, once a SecureSuite user is assigned one user license, they can
have any number of authentication methods and devices assigned to their
account.
To enter a new User License Key:
1. In the
dialog, click the
dialog appears.
2. Enter your new User License Key, and click
3. Click Yes when prompted to reboot your computer. When
your system restarts, your new User License Key will be
available.
To remove a User License Key from your system:
1. In the
dialog, select the User License Key that you want to delete
from your system, and click the
2. The User License Key will no longer appear in the
SecureSuite License Manager Properties
Add button. The Add User License Key
OK.
SecureSuite License Manager Properties
Remove button.
SecureSuite License Manager Properties dialog.
Note: If any user licenses from the User License Key that you are
trying to remove are still in use, SecureSuite will search for
available user licenses from other User License Keys, and assign them
to the users. If there are no other available user licenses, a
message will appear informing you that there are not enough user
licenses to transfer to these user accounts. You will not be able to
delete this user license key until another user license is available
or until none of the licenses from this User License Key are assigned
to users.
To view a description of a User License Key, and the license
number itself, select the User License Key and click the
View
Info button.
SecureSuite XS Workstation Guide 25

Chapter 5: Using SecureSuite
Duplicate License Keys
If SecureSuite detects that you have entered a Product License Key or User
License Key that is already in use, you will receive a message asking if you would
like to enter a new License Key. Click
continue using SecureSuite. If you click
time you restart your machine. You will have to log on to your system using your
Windows password, at which time you will again be prompted to enter a new
License Key. SecureSuite will be disabled and you will continue to receive this
message until a unique License Key is provided, or until SecureSuite is uninstalled
from this machine.
Yes to enter a new License Key and
No, SecureSuite will be disabled the next
SecureSuite XS Workstation Guide 26
Chapter 5: Using SecureSuite
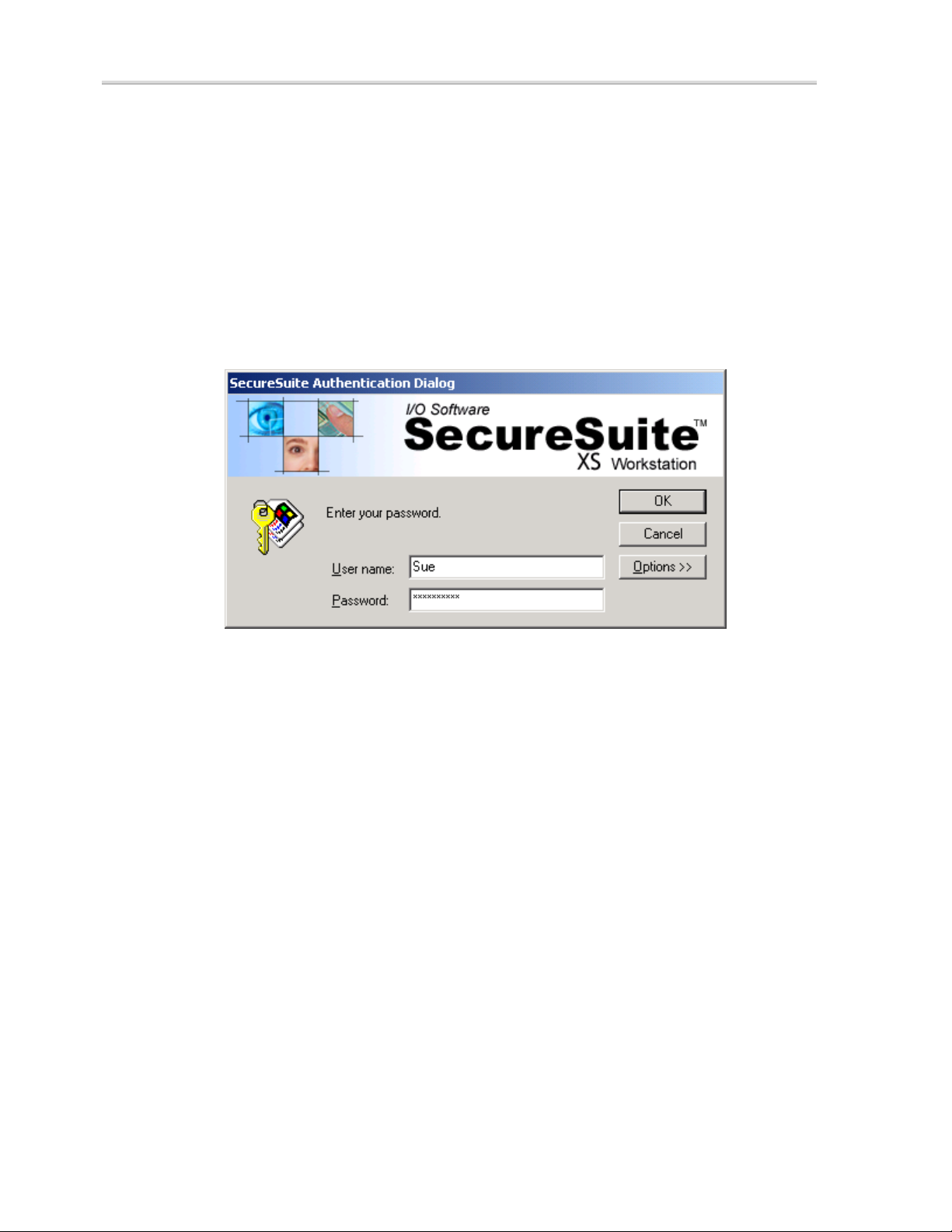
SecureSuite User Authentication
SecureSuite is an advanced authentication infrastructure designed to provide
secure and convenient forms of authentication. Before allowing users to access a
protected computer, application, web site, file or folder, SecureSuite will prompt
them to authenticate (prove who they are) via an authentication dialog. Depending
on what authentication method(s) have been installed and enrolled with, users
may authenticate using a single method or a combination of password, fingerprint,
smart card, iris scan, USB token, and other advanced authentication technologies.
Figure 5: SecureSuite Authentication Dialog
Authentication Methods
An authentication method is a way of proving your identity. Typing a password is
a common, but relatively insecure and inconvenient authentication method.
Biometric methods, such as scanning your fingerprint, are more secure and
convenient (it is hard to forget your finger!). Other methods, such as smart cards
and USB tokens, are also more secure than passwords and offer other
advantages, such as the ability to store data.
With SecureSuite installed on your system, you may have one or more
authentication methods associated with your account. For example, Sue might
use fingerprint authentication, while Bob uses only a password, and Carl has the
option to use either one. The system administrator is responsible for deciding
what authentication methods are assigned you.
SecureSuite XS Workstation Guide 27

Chapter 5: Using SecureSuite
Verification vs. Identification
In order to understand SecureSuite’s authentication dialog, you must first
understand the difference between verification and identification.
• Verification answers the question: “Are you who you say you are?”
• Identification answers the question: “Who are you?”
With Sony Puppy fingerprint identity devices, it is necessary to first identify
yourself to the system by typing in your user name. Then SecureSuite performs a
one-to-one verification process to check if you are you.
Multiple Authentication Methods
When more than one authentication method is associated with your user account,
a relationship between them must be defined. This relationship is categorized into
AND or OR:
either
• Method 1 AND method 2 (greater security)
• Method 1 OR method 2 (greater convenience)
In the case of
authenticate. The user may choose which method to use each time they log on.
For
AND users, all associated authentication method credentials must be supplied
for successful authentication. You supply credentials by entering a password
(secret), inserting a token (put the smart card into its reader), and/or using a
supplied biometric device (allow the device to scan part of you). Credentials are
automatically detected. If more credentials are required, SecureSuite will prompt
you for the next required authentication step. Credentials can generally be
supplied in any order. However, users may specify in what order they would like
to be prompted to use their enrolled authentication method.
OR, only one method’s credential is required in order to successfully
SecureSuite XS Workstation Guide 28

Chapter 5: Using SecureSuite
The Authentication Dialog
To authenticate using a password:
When accessing a secured resource on a SecureSuite-protected system, the
SecureSuite Authentication dialog will appear. To log on to your system
using a password, type your user name in the
password in the
(Optional) Click Options to change the Log on to location to something other
than the default local machine (this computer) or network domain server. You can
also select the
authentication instructions. Select the
check box to log on to your system or domain by using a RAS connection. (For
more information on RAS please consult your Windows Help system. For more
information on RAS support in SecureSuite, please consult the SecureSuite
Release Notes and SecureSuite Administrator’s Guide).
OK or press Enter when you are done. If your password is correct, you will
Click
be successfully authenticated and logged on to the system.
Password text box.
Authentication Details check box to view additional
Log on using dial-up connection
User name text box and your
To authenticate using a biometric device for verification (we use
the fingerprint method as an example):
1. Type your user name in the
2. (Optional) Select the domain you wish to log on to, via the
User name text box.
Options button.
3. Place your fingerprint on the fingerprint device’s scanning
mechanism. SecureSuite will automatically detect the
presence of your finger on the device, sample your
fingerprint, and submit it for verification against the stored
set of fingerprints created during user enrollment.
4. If your fingerprint sufficiently matches your stored fingerprint
template, you will automatically be logged on to the target
domain.
SecureSuite XS Workstation Guide 29
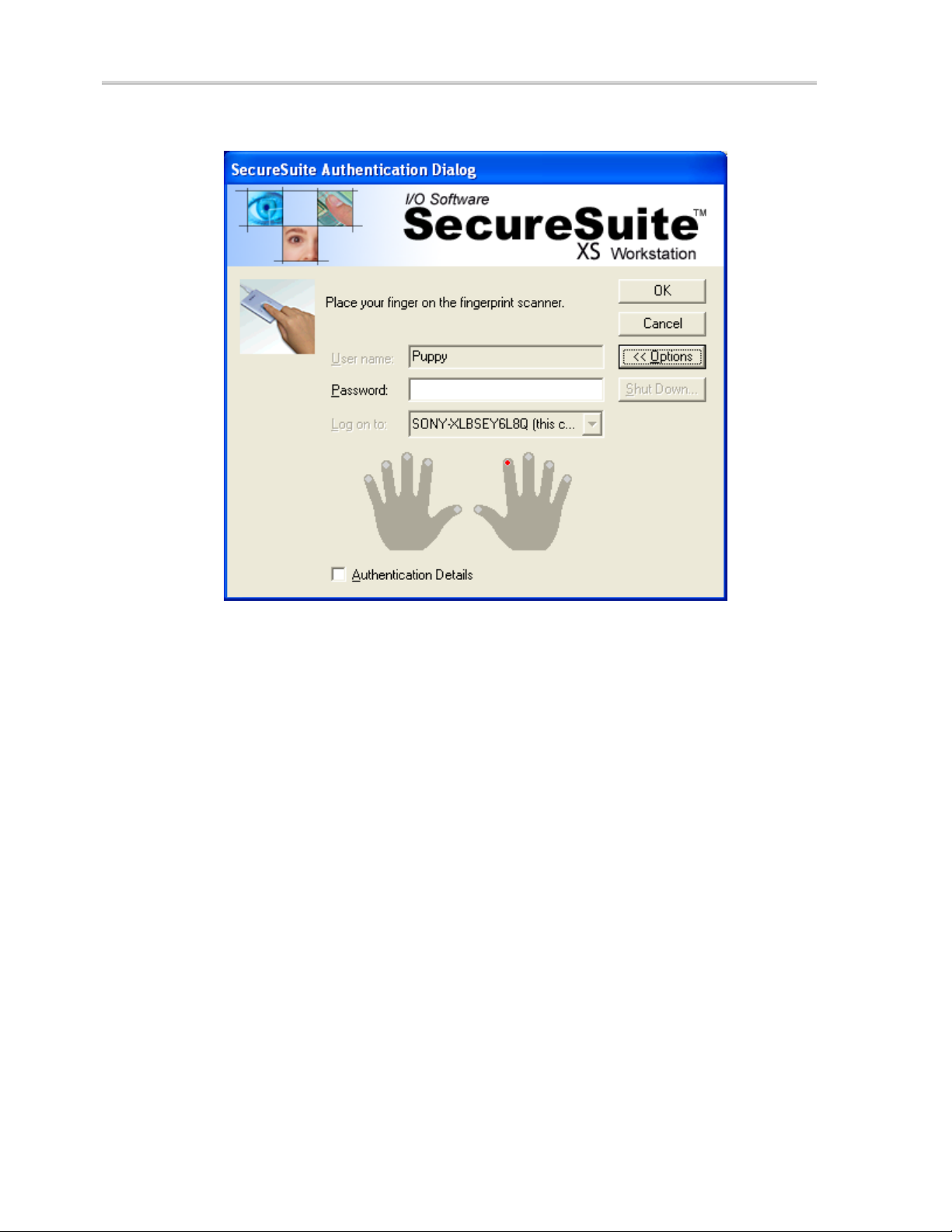
Chapter 5: Using SecureSuite
Figure 6: Multiple Authentication Methods, Password and Fingerprint
Like Windows, SecureSuite retains the last user name of the last user that logged
on, and the domain to which that user logged on. On subsequent system boots,
this information automatically appears in the
dialog.
SecureSuite Authentication
SecureSuite XS Workstation Guide 30
Chapter 5: Using SecureSuite
SecureSuite Icons and the Welcome Screen
SecureSuite Icons
Once you have logged on, SecureSuite will automatically place an icon in the
Windows system tray, from which you can quickly access product information,
help files, and your user settings. If you are an administrator, you will also be able
to access the
Settings dialog (on Windows 2000). If enabled when SecureSuite was
installed, a SecureSuite shortcut group icon will also appear on your desktop. This
icon will allow you to access SecureSuite tools and references including the
SecureSuite XS Workstation Guide and the
SecureSuite User Manager and the SecureSuite System
My SecureSuite Settings dialog.
SecureSuite
system tray icon
SecureSuite program group
shortcut
Figure 7: SecureSuite Icons and Welcome Screen
SecureSuite XS Workstation Guide 31
 Loading...
Loading...