Page 1

SonicWALL VPN Interoperability with Cisco IOS/PIX using IKE
Tech note prepared by SonicWALL, Inc.
SonicWALL, Inc.
1160 Bordeaux Drive
Sunnyvale, CA
94089
1-408-745-9600
Last updated by ah – October 30, 2000
Page 2
Introduction:
VPN standards are still evolving and interoperability between products is a continued effort.
SonicWALL has made progress in this area and is interoperable with Cisco IOS/PIX using IKE as
shown below. Advanced setups are possible but are not covered in this document.
This tech-note assumes the reader has a working knowledge of Cisco IOS/PIX management
tools and SonicWALL appliance configuration. This tech-note describes the required steps to setup a compatible Security Association on both Cisco IOS/PIX and SonicWALL products.
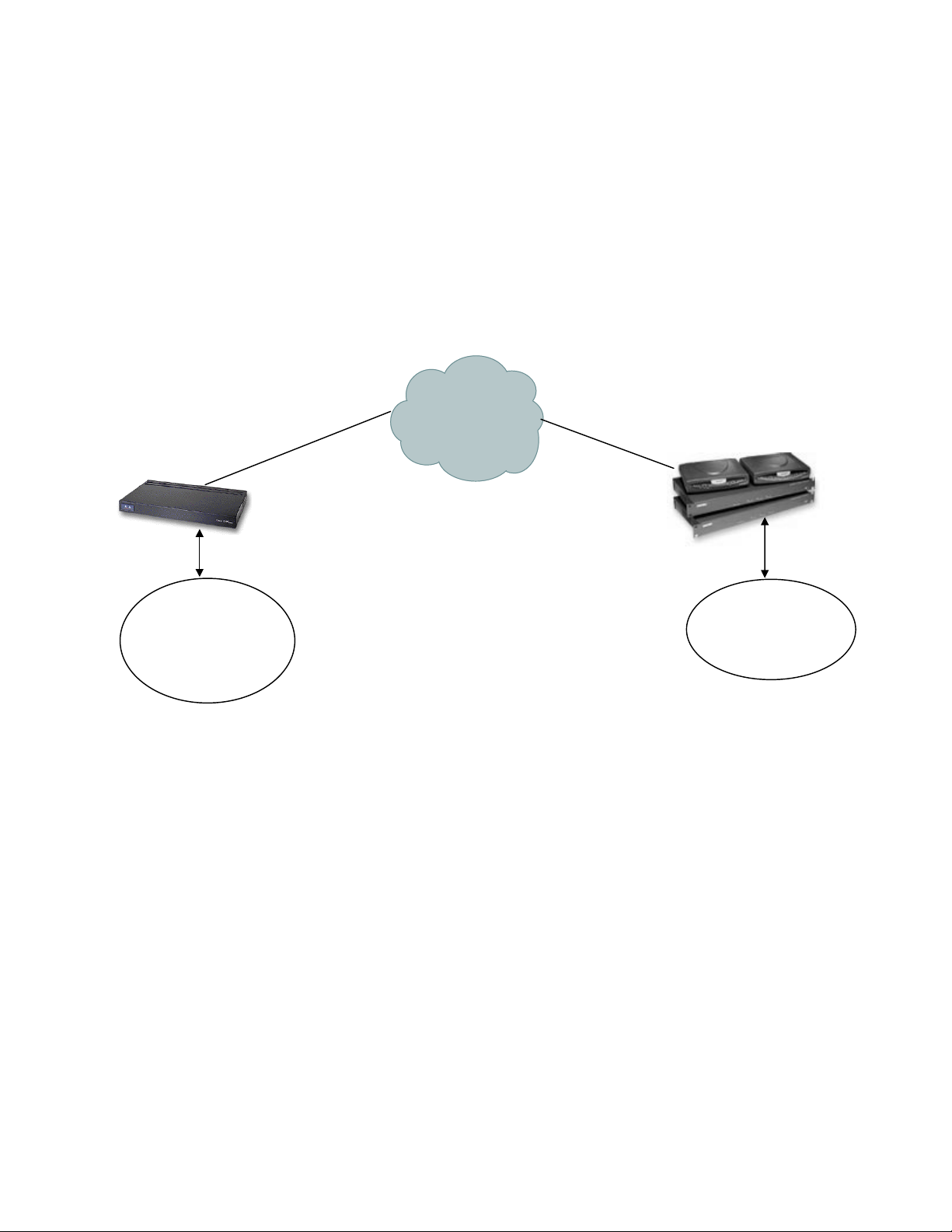
Sample Network:
The network configuration shown below is used an example for VPN configuration
CISCO IOS/PIX box
IP 216.5.31.42
Internet
IP 128.6.3.12
IP 10.0.0.1
Network 10.0.0.0
Mask 255.255.255.0
Network 192.0.0.0
Mask 255.0.0.0
Summary:
SonicWALL has tested VPN interoperability with Cisco IOS/PIX versions greater than 12.0 and
5.0 using the following VPN Security Association information:
Keying Mode: IKE
IKE Mode: Main Mode
No PFS (perfect forward secrecy)
SA Authentication Method: Pre-Shared key
Keying Group: DH (Diffie Hellman) – Group 1
ID_Type: IP subnet
Encryption and Data Integrity: ESP DES or ESP 3DES with MD5
Known Limitations:
When using this tech-note, both Gateway IP addresses must be known. Cisco IOS/PIX can
support gateway-to-gateway VPN with only one static IP address, however this is not discussed
here. For more information please see Cisco and SonicWALL product documentation.
If you have a gateway-to-gateway VPN requirement with only one static IP, you may consider
using SonicWALL gateways on both ends.
IP 192.0.0.1
Last updated by ah – October 30, 2000
Page 3

SonicWALL Configuration
On the SonicWALL, create an SA.
1. Change the IPSec Keying Mode to IKE.
2. Fill in the IPSec gateway (in this example 216.5.31.42)
3. Fill in the appropriate Destination Network (in this example 10.0.0.0) and Subnet Mask (in
this example 255.255.255.0)
4. Select ESP DES HMAC MD5 or ESP 3DES HMAC MD5
A Sample Screen shot from SonicWALL firmware version 5.0 is displayed below
CISCO IOS/PIX Configuration
The Cisco IOS/PIX system has a very rich and complex instruction set. Before you proceed to
enter commands on the Cisco Product, you must be logged into the enable/configure terminal
mode. For more details on logging into your Cisco Product and configuring settings, please refer
to the Cisco documentation available online at http://www.cisco.com
Once you are logged into the enable/configure terminal, use the commands below to setup a SA
complimentary to the SA setup on the SonicWALL as shown above in the screen shot.
The commands below are not a complete guide to configuring a Cisco IOS/PIX product, but are
intended only to guide existing Cisco users. Refer to the Cisco documentation (www.cisco.com
)
for more information regarding the commands below.
Last updated by ah – October 30, 2000
Page 4

COMMANDS FOR CISCO IOS
Command Description
Set ACCESS LIST
Access-list 120 permit ip
To specify the inside and destination networks
10.0.0.0 0.255.255.255 host
192.0.0.0 0.0.0.255
Define IKE parameters
crypto isakmp policy 20
To define an IKE policy, use the
crypto isakmp policy
global
configuration command. IKE policies define a set of parameters
to be used during the IKE negotiation. Use the no form of this
command to delete an IKE policy.
encr 3des To specify the encryption algorithm within an IKE policy
hash md5 To specify the hash algorithm within an IKE policy
authentication pre-share To specify the authentication method within an IKE policy, use
authentication
the
(IKE policy) ISAKMP policy configuration
command.
exit To exit and enter a new command
crypto isakmp key SonicWALL
address 128.6.3.12
To configure a pre-shared authentication key, use the
isakmp key
global configuration command. In this case the
crypto
pre-shared secret is “SonicWALL”
Define IPSEC parameters
crypto ipsec transform-set
sonic esp-des esp-md5-hmac
To define a transform set---an acceptable combination of
security protocols and algorithms---use the
transform-set
global configuration command. Here you can
crypto ipsec
specify if you want to use ESP with authentication and DES or
3DES.
crypto map sonic-map20 localaddress Ethernet0/1
crypto map sonic-map20 5
ipsec-isakmp
To specify and name an identifying interface to be used by the
crypto map for IPSec traffic
Indicates that IKE will be used to establish the IPSec security
associations for protecting the traffic specified by this crypto
map entry. 5 is a number assigned to the crypto map entry
set peer 128.6.3.12 To specify an IPSec peer in a crypto map entry,
set transform-set sonic To specify which transform sets can be used with the crypto
map entry
match address 120 To specify an extended access list for a crypto map entry
exit To exit and enter a new command
crypto map combined localaddress Ethernet0/1
To specify and name an identifying interface to be used by the
crypto map for IPSec traffic,
Last updated by ah – October 30, 2000
Page 5

COMMANDS FOR CISCO PIX
Command Description
Set ACCESS LIST
Access-list 120 permit ip host 10.0.0.0
To specify the inside and destination networks
255.255 255.0 host 192.0.0.0 255.0.0.0
Access-list nonat permit ip host 10.0.0.0
255.255 255.0 host 192.0.0.0 255.0.0.0
This turns NAT off for packets coming from the VPN
tunnel
Sysopt connection permit-ipsec
Sysopt ipsec pl-compatible Required for PIX version before 5.0
Define IKE parameters
isakmp enable outside
isakmp key SonicWALL address
128.6.3.12 netmask 255.255.255.255
To configure a pre-shared authentication key, use the
isakmp key
global configuration command. In this case
the pre-shared secret is “SonicWALL”
isakmp identity address
isakmp policy 20 encryption des To specify the encryption algorithm within an IKE policy
isakmp policy 20 hash md5 To specify the hash algorithm within an IKE policy
isakmp policy 20 group 1 This specifies DH group 1
isakmp policy 20 authentication preshare
To specify the authentication method within an IKE
policy, use the
authentication
(IKE policy) ISAKMP
policy configuration command.
isakmp policy 20 lifetime 3600 This commands sets the life time intervals before IKE is
renegotiated. The value 3600 can be changed.
Define IPSEC parameters
Crypto ipsec transform-set sonic esp-des
esp-md5-hmac
To define a transform set---an acceptable combination of
security protocols and algorithms---use the
transform-set
global configuration command. Here you
crypto ipsec
can specify if you want to use ESP with authentication
and DES or 3DES.
crypto map sonic-map 20 ipsec-isakmp Indicates that IKE will be used to establish the IPSec
security associations for protecting the traffic specified by
this crypto map entry. 5 is a number assigned to the
crypto map entry
crypto map sonic-map 20 match address
To specify an extended access list for a crypto map entry
120
crypto map sonic-map 20 set peer
To specify an IPSec peer in a crypto map entry,
128.6.3.12
crypto map sonic-map 20 set transformset sonic
crypto map sonic-map 20 interface
To specify which transform sets can be used with the
crypto map entry
outside
Last updated by ah – October 30, 2000
Page 6

To Test the VPN tunnel:
From the PC behind the Cisco IOS/PIX firewall, try to ping 192.0.0.1
From the PC behind the SonicWALL, try to ping 10.0.0.1
Trouble Shooting Tips
:
Use the Log Viewer on the Cisco IOS/PIX and the SonicWALL to determine if IKE negotiation has
started.
If IKE negotiation is complete but pings timeout, the Cisco IOS/PIX host computer may need
route configuration.
Last updated by ah – October 30, 2000
 Loading...
Loading...