Sonicwall AVENTAIL 10.5.1 INSTALLATION AND ADMINISTRATION GUIDE
10.5.1 Installation and Administration GuideSonicWALL / Aventail Secure Remote Access

SonicWALL Aventail E-Class SRA Installation and Administration Guide | i
Table of Contents
Chapter 1
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Features of Your SonicWALL Aventail Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
SonicWALL Aventail E-Class SRA Appliance Models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
Administrator Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2
User Access Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3
What’s New in This Release . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
System Requirements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
Server Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
Client Components. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
About the Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Document Conventions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Chapter 2
Installation and Initial Setup. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17
Network Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Preparing for the Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
Gathering Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Verifying Your Firewall Policies. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .19
Helpful Management Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
Installation and Deployment Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .21
Specifications and Rack Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
Front Panel Controls and Indicators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .23
Connecting the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .29
Powering Up and Configuring Basic Network Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
Web-Based Configuration Using Setup Wizard. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32
Configuring the Appliance Using the Management Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .33
Moving the Appliance into Production . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
Powering Down and Restarting the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35
Next Steps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .36
Chapter 3
Working with AMC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Accessing AMC. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
Logging In to AMC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .37
Logging Out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
AMC Basics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
A Quick Tour of the AMC Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .38
Adding, Editing, Copying, and Deleting Object s in AMC. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .43
Getting Help . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45
Administrator Accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
Managing Administrator Accounts and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .46
Avoiding Configuration File Conflicts with Multiple Administrators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .49
Managing Multiple SonicWALL Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .50
Configuring an Appliance for GMS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
Configuring an Appliance for ViewPoint. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51
Working with Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
Saving Configuration Changes to Disk . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
Applying Configuration Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .52
Discarding Pending Configuration Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53
Deleting Referenced Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .54
Chapter 4
Network and Authentication Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Configuring Basic Network Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
Specifying System Identity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56
Configuring Network Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57
Configuring ICMP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .57

ii | Table of Contents
Viewing Fully Qualified Domain Names and Custom Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Configuring Fallback Servers for Connect Tunnel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .58
Configuring Routing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59
Configuring Network Gateways . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
Choosing a Network Gateway Option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .60
Configuring Network Gateways in a Dual-H omed Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62
Configuring Network Gateways in a Single-Homed Environment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63
Enabling a Route to the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
Configuring Static Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .64
Configuring Name Resolution. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65
Configuring Domain Name Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .65
Configuring Windows Network Name Resolution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66
Server Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
CA Certificates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .74
Certificate FAQ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Managing User Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
About Intermediate Certificates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .80
Configuring Authentication Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .81
Configuring Microsoft Active Directory Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83
Configuring LDAP and LDAPS Authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .94
Configuring RADIUS Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .99
Configuring RSA Server Authentication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
Configuring a PKI Authentication Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Configuring a Single Sign-On Authentication Server. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .104
Using RSA ClearTrust Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .106
Configuring Local User Storage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
Testing LDAP and AD Authentication Configurations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .108
Configuring Chained Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Enabling Group Affinity Checking in a Realm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .112
Using One-Time Passwords for Added Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
Next Steps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .114
Chapter 5
Security Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Creating and Managing Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .115
Resource Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
Resources and Resource Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .117
Using Variables in Resource and WorkPlace Shortcut Definitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Creating and Managing Resource Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .137
Web Application Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Creating Forms-Based Single Sign-On Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Access Control Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .144
Configuring Access Control Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
Resolving Deny Rule Incompatibilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .157
Resolving Invalid Destination Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
Chapter 6
User Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
Overview: Users, Groups, Communities, and Realms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .159
Using Realms and Communities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .160
Viewing Realms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
Default, Visible, and Hidden Realms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Specifying the Default Realm. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .162
Enabling and Disabling Realms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Best Practices for Defining Realms. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Configuring Realms and Communities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Creating Realms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .163
Adding Communities to a Realm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Creating and Configuring Communities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .166
Network Tunnel Client Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .170
Using the Default Community . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
. . . . . . . . . . . 161

SonicWALL Aventail E-Class SRA Installation and Administration Guide | iii
Changing the Order of Communities Listed in a Realm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
Configuring RADIUS Accounting in a Realm. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Editing, Copying and Deleting Communities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .181
Managing Users and Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Viewing Users and Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
Managing Users and Groups Mapped to External R epositories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .182
Managing Local User Accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Chapter 7
System Administration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Optional Network Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Enabling SSH Access from Remote Hosts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .193
Enabling ICMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 194
Configuring Time Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .195
System Logging and Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Overview: System Logging and Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .196
Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Monitoring the Appliance. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .206
SNMP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .214
Managing Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .224
Exporting the Current Configuration to a Local Machine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .224
Saving the Current Configuration on the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .225
Importing Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226
Restoring or Exporting Configuration Data Stored on the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226
Replicating Configuration Data. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .227
Requirements for Replication. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .227
Getting Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Defining a Collection of Appliances to Receive Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Beginning Replication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
Viewing Configuration Data Recipients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .233
Upgrading, Rolling Back, or Resetting the System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
Updating the System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .234
Rolling Back to a Previous Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
Resetting the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .237
SSL Encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Configuring SSL Encryption. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
FIPS Certification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Requirements for FIPS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Managing FIPS-Compliant Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .241
FIPS Violations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
Enabling FIPS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .241
Exporting and Importing FIPS-Compliant Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .242
Disabling FIPS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .243
Zeroization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .243
Software Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
How Licenses Are Calculated . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Viewing License Details. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Managing Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 246
Chapter 8
End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
Overview: End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .249
How the Appliance Uses Zones and Device Profiles for End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
End Point Control Scenarios . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Managing EPC with Zones and Device Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .256
Enabling and Disabling End Point Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .257
Zones and Device Profiles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .257
Creating Zones for Special Situations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Using the Virtual Keyboard to Enter Credentials. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .280
Configuring Data Protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .281

iv | Table of Contents
Chapter 9
The Aventail WorkPlace Portal. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
A Quick Tour of Aventail WorkPlace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
Home Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .284
Intranet Address Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
Bookmarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .287
Network Explorer Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .288
Web Shortcut Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
Configuring WorkPlace General Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .289
Working with WorkPlace Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .290
Viewing Shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .290
Adding Web Shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
Creating a Group of Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 294
Adding Network Shortcuts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
Editing Shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295
WorkPlace Sites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 296
Adding WorkPlace Sites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .297
Modifying the Appearance of WorkPlace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .300
WorkPlace and Small Form Factor Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Fully Customizing WorkPlace Pages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3 08
WorkPlace Style Customization: Manual Edits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 308
Overview: Custom WorkPlace Templates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .309
How Template Files are Matched . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .309
Customizing WorkPlace Templates. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
Giving Users Access to Aventail WorkPlace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3 11
End Point Control and the User Experience . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
How OPSWAT Secure Desktop Emulator Works . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .312
How Aventail Cache Control Works. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313
Chapter 10
User Access Components and Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
User Access Agents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 315
Client and Agent Provisioning (Windows) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .317
Aventail WorkPlace. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .319
The Tunnel Clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .320
The Proxy Clients. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321
Web Access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .321
Client Installation Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 324
Downloading the SonicWALL Client Installation Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 324
Customizing the Configuration for the Connect Tunnel Client. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .326
Command Line Access to Connect Tunnel with NGDIAL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 328
Command Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .329
Customizing the Configuration for the Connect Mobile Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331
Running Connect as a Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .333
Distributing SonicWALL Client Setup Packages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 336
The OnDemand Proxy Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 337
Overview: OnDemand Proxy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 338
How OnDemand Redirects Network Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 339
Configuring OnDemand to Access Specific Applications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 340
Configuring Advanced OnDemand Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .342
Client Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 343
Managing the SonicWALL Access Services. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .344
Overview: Access Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 344
Stopping and Starting the SonicWALL Access Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 345
Configuring the Network Tunnel Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .346
Configuring IP Address Pools. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .347
Configuring Web Resource Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 353
Configuring Fallback Servers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 354
Configuring the Web Proxy Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 355

SonicWALL Aventail E-Class SRA Installation and Administration Guide | v
Terminal Server Access. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .356
Providing Access to Terminal Server Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .356
Citrix Server Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .357
Defining an Access Control Rule and Resource for Terminal Server Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
Managing Graphical Terminal Agents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
Graphical Terminal Shortcuts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Chapter 11
Virtual Assist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367
What is Virtual Assist? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 67
How Does Virtual Assist Work? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .367
Configuring Virtual Assist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .368
Enabling Virtual Assist Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .368
Configuring Virtual Assist Ticket Queue. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368
Configuring Virtual Assist Requests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .369
Enabling Virtual Assist on a Layout. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
Configuring Virtual Assist Invitations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .371
Using the Virtual Assist Ticket Queue . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .371
Using Virtual Assist from the Technician View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
Installing the Virtual Assist Technician Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
Managing the Virtual Assist Queue. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .374
Emailing an Invitation to a Client. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Assisting a Client . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Virtual Assist Technician Console Tools. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .375
Using Chat in Virtual Assist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .377
Using Virtual Assist from the Customer View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 378
Using Virtual Assist from the Customer View (W indows). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 378
Using Virtual Assist from the Customer View (Mac) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .380
Chapter 12
Administering a High-Availability Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 385
Overview: High-Availability Cluster. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .385
Cluster Architecture . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 385
The Load Balancing Service. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .386
Stateful Failover . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .387
Synchronized Cluster Administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 387
Installing and Configuring a Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 388
Step 1: Connect the Cluster Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 389
Step 2: Run Setup Tool on All Nodes of the Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .389
Step 3: Configure the Cluster’s External Virtual IP Address. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .390
Final Steps: Network Configuration and Licensing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .390
Managing the Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .391
Viewing and Configuring Network Information for Each Node . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391
Powering up a Cluster. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391
Starting and Stopping Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391
Monitoring a Cluster. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 392
Backing up a Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 93
Performing Maintenance on a Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393
Upgrading a Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393
Upgrading a Single Appliance to a Cluster Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393
Troubleshooting a Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .394
Cluster Scenarios. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Normal Flow of Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 394
Node Failure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 395
Appendix A
Appliance Command-Line Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 397
Configuring a New Appliance Using Setup Tool. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3 98
Tips for Working with Setup Tool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .398
Using Setup Tool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 398
. . . . . . . . . . . . . . . . . . 394

vi | Table of Contents
Saving and Restoring Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .399
Saving Configuration Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .399
Restoring Configuration Data. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 400
Upgrading or Rolling Back System Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 401
Installing System Upgrades (Command Line Tool). . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .402
Reverting to a Previous Version. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 402
Performing a Factory Reset . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 403
Validating Hosts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 403
Appendix B
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 405
General Networking Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 405
Verify a Downloaded Upgrade File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 407
Troubleshooting Agent Provisioning (Windows) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 08
AMC Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 409
Authentication Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .410
Using Personal Firewalls with Aventail Agents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 410
Aventail Services Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 411
Tunnel Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
OnDemand Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .417
General OnDemand Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 417
Specific OnDemand Issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
Client Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .419
Windows Client Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .419
Macintosh and Linux Tunnel Client Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .421
Troubleshooting Tools in AMC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .423
Ping Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 423
Traceroute Command. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
DNS Lookup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
Viewing the Current Routing Table. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .425
Capturing Network Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .425
Logging Tools for Network Tunnel Clients . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .427
Snapshot Tool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 428
Appendix C
Best Practices for Securing the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 429
Network Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .429
Appliance Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .430
Appliance Sessions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .430
Administrator Accounts. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 430
Access Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431
Set Up Zones of Trust. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431
SSL Ciphers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
Client Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
Appendix D
Log File Output Formats. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 433
File Locations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 433
System Message Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 434
Auditing Access Policy Decisions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 436
Viewing Client Certificate Errors in the Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 437
End Point Control Interrogation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438
Unregistered Device Log Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438
Network Tunnel Audit Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Auditing Connection Status Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .441
Web Proxy Audit Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 442
Management Console Audit Log . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .444
WorkPlace Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 444
WorkPlace Shortcut Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .444
. . . . . . . . . . . . . . .440

SonicWALL Aventail E-Class SRA Installation and Administration Guide | vii
Appendix E
Internationalization Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 447
Support for Native Character Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .447
RADIUS Policy Server Character Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .447
Selected RADIUS Character Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .448
Other Supported RADIUS Character Sets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 449
Appendix F
Configuring a High-Capacity Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 451
Overview of Clustering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .451
Cluster Management. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 451
Performing Initial Appliance Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .451
Configuring the Appliance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 452
Attaching the Appliance to the Switch. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 452
Configuring the Load Balancer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .452
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 453

viii | Table of Contents
Chapter 1
Introduction
The SonicWALL SSL VPN appliance provides secure access—including clientless acce ss to Web
applications, access to client/server applications, and file sharing—to employees, business
partners, and customers. All traffic is encrypted using Secure Sockets Layer (SSL) to protect it from
unauthorized users.
The appliance makes applications available from a range of acce ss meth ods—incl uding a s tandard
Web browser, a Windows client, or a mobile device—on a wide range of platforms including
Windows, Macintosh, and Linux.
SonicWALL Aventail E-Class SRA Installation and Administration Guide | 1
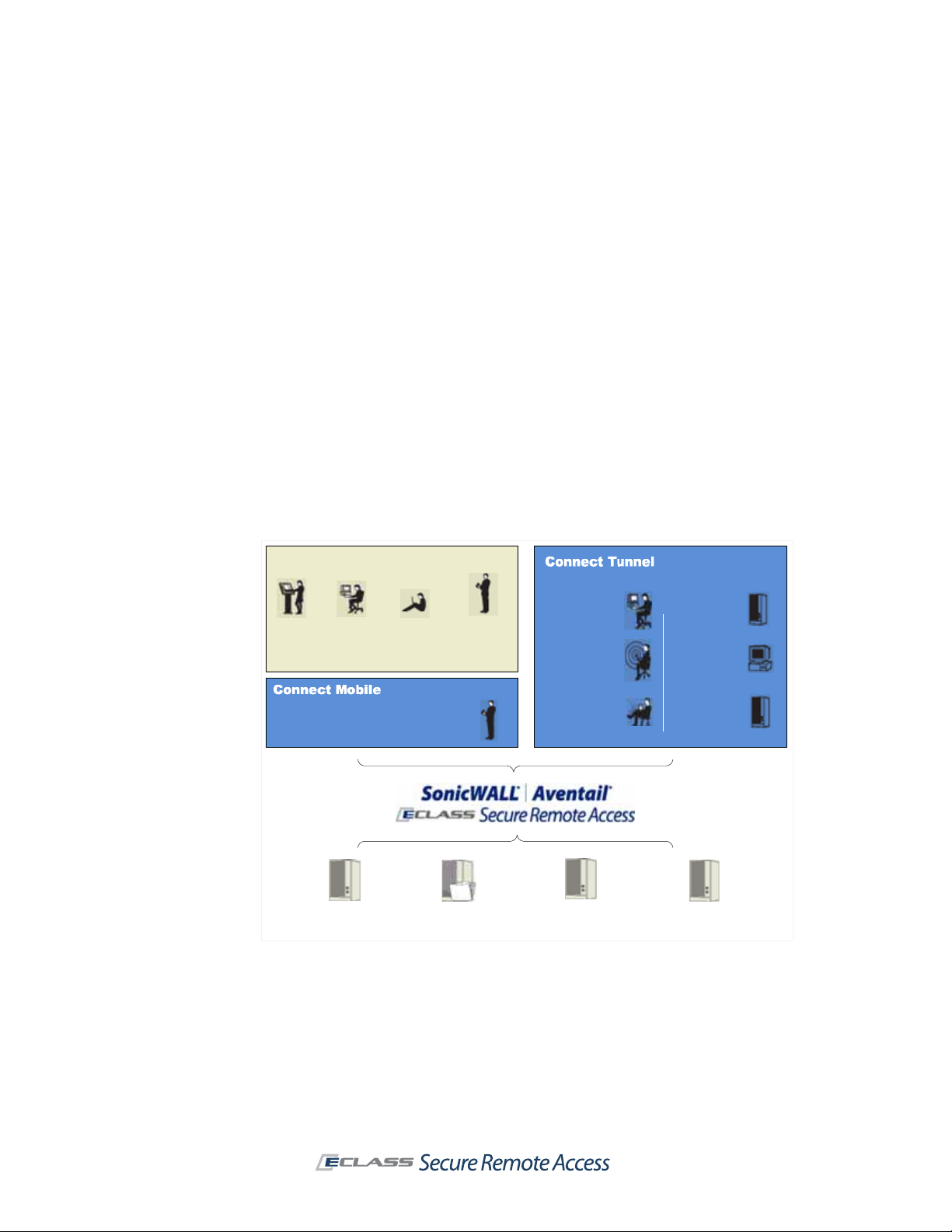
Aventail WorkPlace
Internal
Kiosk
users
Windows Mobile-powered devices
Business
partners
Teleworkers
Web-based
PDA
smartphone
users
File shares
applications
You might use the appliance to:
z
Create a remote access VPN that enables remote employees to securely access private company
applications such as email over the Internet.
z
Create a business partner VPN that provides designated suppliers with access to an internal
supply chain application over the Internet.
users
Wireless
LANs
IT-managed
devices
Thin client/server
applications
Windows
servers
Windows
desktops
Branch office
applications
Traditional client/
server applications

2 | Chapter 1 - Introduction
The appliance’s granular access control lets you define policy and control access down to the user
and resource level. Managing policy and configuring the appliance is quick and easy with the Webbased management console.
For an overview of planning your SonicWALL SSL VPN appliance configuration and deployment, see
the Getting Started Guide.
Features of Your SonicWALL Aventail Appliance
This section highlights the key components provided with your appliance.
SonicWALL Aventail E-Class SRA Appliance Models
SonicWALL offers the following SSL VPN appliance mod els, all of which are documented in this
manual. Most of them can be clustered: a cluster of two appliances with internal load balancing is
intended for high availability (it provides system redundancy in case one of the nodes fails), and
clusters of up to eight can be used to increase capacity:
z
SonicWALL Aventail SRA E-Class EX7000 and EX-2500: Supports up to 2,000 concurrent
users, and provides for clustering two identical appliances behind one virtual IP address with
internal load balancing, or up to eight appliances using an external load balancer.
z
SonicWALL Aventail SRA E-Class EX6000 and EX-1600: Supports up to 250 concurrent
users and provides for clustering two identical appliances behind one virtual IP address with
internal load balancing, or up to eight appliances using an external load balancer.
z
SonicWALL Aventail SRA E-Class EX-750: Supports up to 50 concurrent users.
Administrator Components
These are the key components for managing the SonicWALL appliance and services:
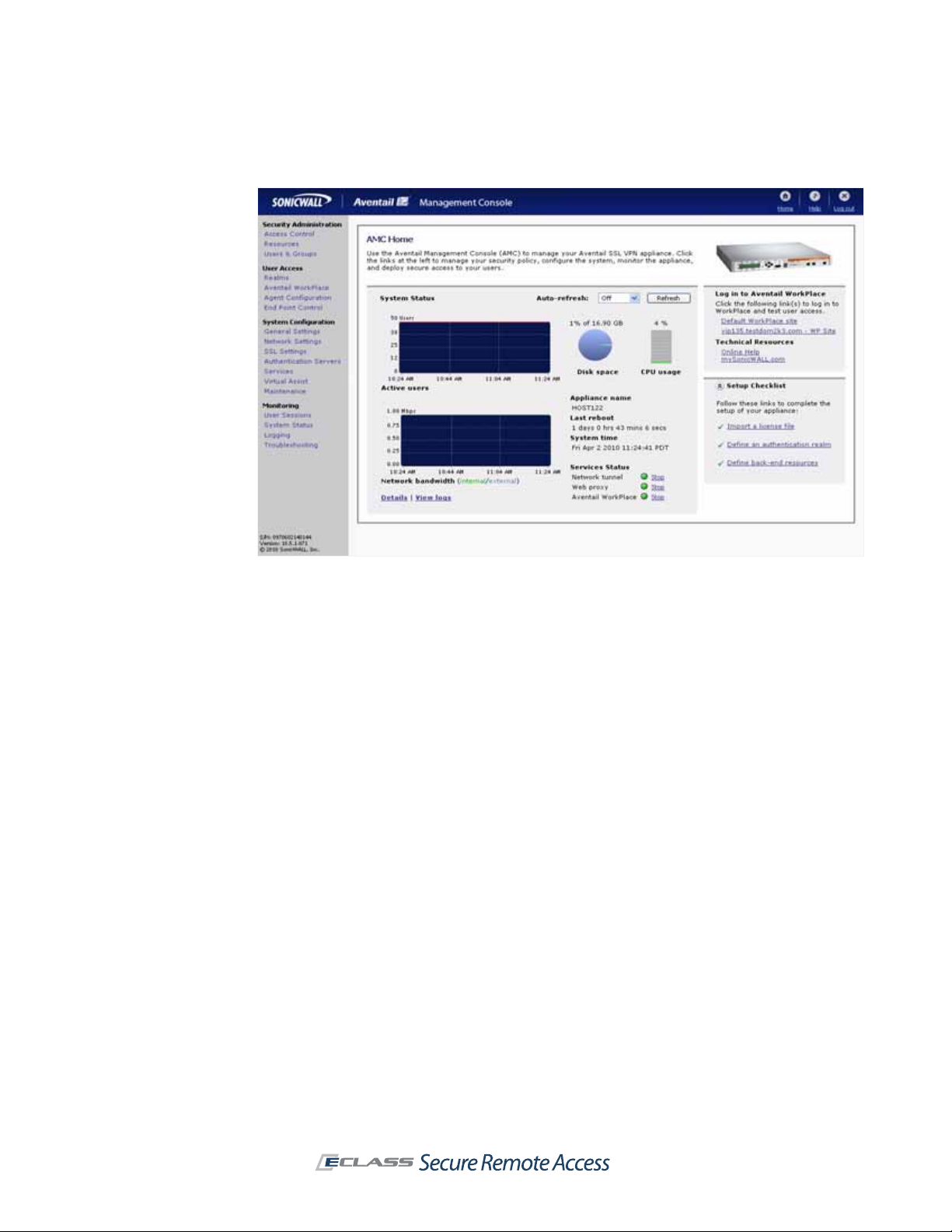
z
Aventail Management Console (AMC) is a Web-based administrative tool used to manage
the appliance. It provides centralized access for managing security policies, configuring the
system (including networking and certificate configuration), and monitoring. AMC is accessible
from a Web browser.
z
The Web proxy service provides users with secure access to Web-based applications, Web
servers, and network file servers from a W eb brow ser. The Web proxy service is a secure HT TP
reverse proxy that brokers and encrypts access to Web-based resources. It also manages
TCP/IP connections for the Connect Mobile client.
z
The network tunnel service is a network routing technology that provides secure network
tunnel access to a wide range of applications, including those that use non-TCP protocols such
as Voice Over IP (VoIP) and ICMP, reverse-connection protocols, and bi-directional protocols
SonicWALL Aventail E-Class SRA Installation and Administration Guide | 3
such as FTP. It works in conjunction with the Connect Tunnel client and t he OnD em and Tunnel
agent to provide authenticated and encrypted access. The network tunnel service can traverse
firewalls, NAT devices, and other proxy servers that can interfere with traditional VPN devices.
User Access Components
The appliance includes several components that provide users with access to resources on your
network.
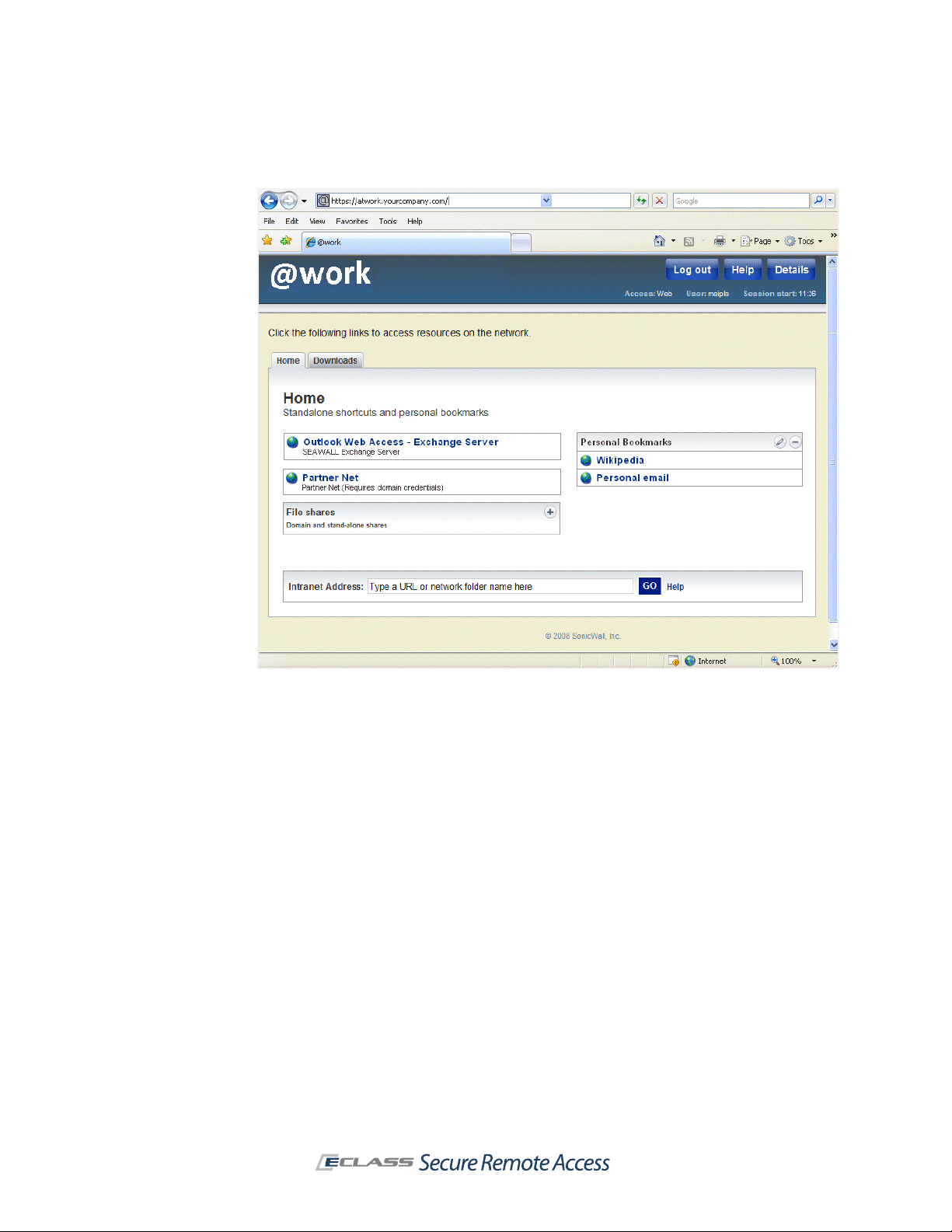
Aventail WorkPlace
The WorkPlace portal provides users with quick access to resources on your network. It is accessible
from any Web browser that supports SSL and has Jav aScript enabled. WorkPlace provides a range
of access methods for you to choose from:
z
Basic Web (HTTP) resources are accessible using the Web translation engine, a reverse proxy
that provides single sign-on and fine-grained access control.
z
Web resources are also ac cessible through custom port mapped and custom FQDN mapped Web
access. This type of proxy handles Web programming technologies such as AJAX without the
limitations of URL rewriting used in translatio n.
z
File system resources are accessible from the Web-based Network Explorer that is integrated
in WorkPlace.
z
Client/server traffic (TCP/IP) is accessible using one of the network redirection clients,
OnDemand Tunnel. The client is automatically provisioned or activated when the user logs in to
WorkPlace.
4 | Chapter 1 - Introduction
The access method you choose will be based on several factors, including the network protocols
used by your applications, your security requirements, end-user convenience, and the target
platforms. Here’s what your company’s WorkPlace portal might look like:
Connect and OnDemand Tunnel clients
T unnel clients provide network -level access to all resources, effectively making each user device a
virtual node on your network.
z
The Connect Tunnel client provides full network and application access from a Web-deployed
Windows client for computers running a Windows 7, Windows Vista, Windows XP, Macintosh, or
Linux operating system. The cl ient can be provisioned either transparently using a link from the
WorkPlace portal or through an executable installation package. The Connect Tunnel client
provides split-tunneling control, granular access controls, and automatic proxy detection and
authentication.
z
The OnDemand Tunnel agent provides the same features as the Connect T unnel, except that it
can’t be used as a dial-up adapter for domain logins, and is integrated into WorkPlace.
OnDemand can operate in either split-tunnel mode or redirect all traffic mode.
Connect Mobile client
Connect Mobile provides remote TCP/IP access to Windows Mobile-powered devices. The Connect
Mobile client is installed by a stand-alone installer package, and is managed by the Web proxy
service.
End Point Control (EPC)
EPC components ensure that your network is not compromised when accessed from PCs in
untrusted environments by enabling you to “interrogate” devices and determine whether they are
running the programs that you require. Advanced EPC simplifies granular end point protection by
allowing you to set up device profiles (for clients running on Microsoft Windows) using a
comprehensive predefined checklist that includes security solutions from leading vendors like
OPSWAT, McAfee, Computer Associates, Sophos, and Kaspersky. Advanced EPC is included with the
EX7000 and EX-2500 appliances and licensed separately for the other appliances in the EX-series.

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 5
Note
z
Prior to version 10 of the SonicWALL Aventail E-Class SRA EX-Series firmware, there was an
OnDemand proxy agent that provided access to resources protected by the Web proxy service.
This agent and its settings are still available to you if you are upgrading from a previous version
of the firmware; new customers will not hav e this agent and will use OnDemand Tunnel instead.
What’s New in This Release
Version 10.5 of the Sonic W ALL E-Clas s Secure Remote Access software inclu des the fo llowing new
and enhanced features:
z
Firefox 3.5 Support—Full support for Mozilla Firefox 3.5.
z
Internet Explorer 8 Support—Full support for Microsoft Internet Explorer 8.
z
Safari 4.0 Support—Full support for Apple Safari 4.0.
z
Mac OS X Snow Leopard Support—Full support for Mac OS X Snow Leopard (10.6).
z
Windows 7 Support—Full support for Microsoft Windows 7.
z
Vista SP2 Support—Full support for Microsoft Vista SP2.
z
Vista 64-bit Support—Full support for Microsoft Vista 64-bit.
z
Virtual Assist Remote Helpdesk Support—Allows remote helpdesk technicians to see and
configure user’s desktops. SonicWALL Virtual Assist is a remote support tool that enables an
administrator or help desk technician to assume control of a user’s PC or laptop in order to
provide remote technical assistance. With the user’s permission, the technician gains instant
access to the computer using a Web browser and can then diagnose and fix a problem remotely .
See “Virtual Assist” on page 367 for more information.
z
Tunnel URL Filtering for Web Policy and SSO Tunnel Support—Enforces the URL-based
rules that administrators define for ExtraW eb within VPN tunnel sessions. This feature not only
provides more effective security, but also leverages single sign-on logic for Web applications.
See “Configuring Web Resource Filtering” on page 353
z
OPSWAT Cache Cleaner (Aventail Cache Control)—Provides VPN administrators with an
end-point data protection tool to ensure data downloaded or accessed during a session is
functionally wiped from the user’s system. This feature removes Web browser information, such
as cookies, browsing history, and stored passwords upon termination of the session. The
OPSWAT Cache Cleaner is supported on Windows and Mac platforms.
z
OPSWAT Secure Desktop Emulator—Provides VPN administrators with an additional endpoint data protection tool that prevents end users from copying or moving data from an endpoint system to other locations that hav e not been qualified for security clear ance. When a client
device is classified into a zone that requires the desktop emulator, the emulator will
automatically deploy for the user. The secure desktop emulator is available for Windows
platforms.
See “How OPSWAT Secure Desktop Emulator Works” on page 312 and “Zones and Device
Profiles” on page 257.
z
Apple iPhone and Symbian Support with ActiveSync for Exchange—Extends SonicWALL ’s
clientless ActiveSync support for Exchange email to Apple iPhones, iPads, Google Android
mobile operating system, and devices running the popular Symbian operating system. Symbian
runs on many Nokia and Samsung devices that are popular choices for corporate mail. This
feature also leverages the device’s ID capability to link the device to a single user, providing a
first layer of end-point control.
See “Integration with Third-Party Components” on page 14 for support information, “Exchange
ActiveSync Web Access” on page 322 for general information, and “Example: Supporting
Exchange on iPhones” on page 126 for an example configuration.
z
Password Management for Sun and Novell Directory Servers—Provides support to Novell
and Sun LDAP servers for improved password management. This new feature calls upon the
Policy server to probe and predetermine the directory server and the applicable version. End
users will be able to enter LDAP credentials and be notified through the appliance when their
password needs to be changed due to expiration or backend policies, and will then allow users
to change the password.

6 | Chapter 1 - Introduction
z
Extension Configurations in Management UI—A new page has been added to the
Maintenance section of the AMC management interface to allow simple configurations to be
completed for extensions. This new feature assists administrators in making configuration
adjustments that appear in maintenance releases or hotfixe s, a nd a l low s for th e configuration
of arbitrary key-value pairs.
z
Zero-client Web Access Capabilities Extended—Custom port mapped and custom FQDN
mapped Web access support for modern Web applications such as AJAX without installation of
a client agent.
See “Web Access” on page 321 for more information.
z
Persistent Desktop Device Identity—Limits the set of devices that an y given user ma y use
to access protected resources.
See “Collecting Equipment IDs from Unregistered Devices” on page 276 for more information.
z
UDP Tunnel Mode—Use of Encapsulating Security Payload (ESP) improves the performance of
UDP streaming applications like VoIP.
See “UDP Tunnel Mode” on page 172 for more information.
z
FIPS Certification—EX-Series 6000 and 7000 appliances are being certified as FIPScompliant.
See “FIPS Certification” on page 240 for more information.
z
Control Session Termination for Tunnel Clients—Improves security and license usage by
providing an option to terminate OnDemand Tunnel or Connect Tunnel sessions when the
credentials for the community expire.
See “Session Termination” on page 174.
z
Intermediate CA Support—Certificate authority management is now more flexible with
support for wildcard server and client certificates signed by intermediate certificate authorities.
z
Option to Disable Authorization Checks—Prevents authorization check errors by providing
an option not to query directory servers for group information. Typically used for secondary
authentication servers, this option can also increase the speed of the authentication process for
users.
See “Disabling Authorization Checks” on page 83 for more information.
z
Enforce Single User Name in Chained Authentication—Improves security. The
administrator has the option of requiring that the same user identifier is used for each step of
chained authentication.
See “Configuring Chained Authentication” on page 109 for more information.
z
Enhance Terminal Services and Citrix Shortcut Configuration Options—New Web client
options for administrator include the ability to choose whether to allow copy and paste, user
screen size control, and other options during shortcut creation. A new check box for terminal
services shortcuts allows the option of automatically reconnecting when the session is
interrupted. Workplace users can control screen resolution when accessing shortcuts.
See “Adding Graphical Terminal Shortcuts to Individual Hosts” on page 361 for more
information.
z
AMC Navigation Improvements for Resources and Rules—Filtering drop boxes have been
added on a number of AMC pages to provide for more efficient searching.
See “Filters” on page 40 for more information.
z
Simplified OPSWAT Configuration in AMC—A new Any product from this vendor check
box is available for antivirus, antispyware, and personal firewall program vendors in Windows
device profiles during End Point Control configuration. Selecting this option allows the
administrator to create a profil e that do es not requi re updating ev eryti me th e v endor re lease s
a new version. When this option is selected, the administrator can still specify additional
criteria, such as signatures updated, file system scanned, and real-time protection enabled, as
long as all the versions of all the products in the list support that functionality.
See “Advanced EPC: Extended Lists of Security Programs” on page 271 for configuration
information.
z
Deployment of EPC Using Browser on Windows Mobile—End Point Control can be
performed on mobile devices without requiring Connect Mobile installation. The device must be
running Windows Mobile 6.5 or 6.1 with the corresponding version of Pocket Internet Explorer.
No configuration or separate device profile is necessary in the AMC. When logging into a
community that requires EPC, the user is prompted to install or upgrade the Aventail
Interrogator client. Interrogator communicates the EPC classification of the device to the
appliance.

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 7
z
Suspend and Resume a Spike License—Instead of having a fixed ex piration date once it is
activated, a Spike License can now be suspended and later resumed. Once it is activated, you
will see the total number of allowed users, the activation date, and the number of days
remaining on the license. A Spike License enables you to t emporarily increase the number of
remote users you can support.
See “Managing a Spike License” on page 248 for more information.
System Requirements
This section describes the system requirements for the administrator (server) and client
components for the SonicWALL SSL VPN.
Server Components
The system requirements for the administ rator components and authen tication servers are listed in
the following tables.
System Administration
Operating system Browser
Aventail Management Console (AMC)
z
Windows Vista SP2
z
Windows Vista x64
z
Windows XP Professional SP3
z
Linux kernel 2.4.20 or later
z
Internet Explorer 8.0
z
Internet Explorer 7.0
z
Mozilla Firefox 3.0
z
Mozilla Firefox 3.0

8 | Chapter 1 - Introduction
Authentication Servers
Operating system/Version Notes
Active Directory
Windows Server platform:
z
Windows 2008 Server
z
Windows 2003 Server
LDAP servers
z
LDAP version 3 compatible servers
z
IBM Directory Server, versions 5 and 6
RADIUS
z
Version 5.2
RSA
z
RSA Authentication Manager, version 7.1
z
RSA Authentication Manager, version 6.1
Single sign-on
z
RSA ClearTrust, version 4.6
z
General support, including password change
z
No LDAP password change support
z
LDAP password change supported on IDS
z
Supports IP address assignment
Citrix Server Farms
Servers Notes
z
Citrix XenApp 5.0
z
Citrix XenApp 4.5
z
Citrix Presentation Server 4
z
EOL has been announced for Citrix MetaFrame XP and
Citrix MetaFrame 1.8
Compatible Server Components
Server platforms, browsers, and third-party applications that are compatible with the appliance are
shown in the following table. There are no known issues with compatible configurations, and we
continue to offer technical support for them, but they have not been specifically tested in the
current release and future product changes will not take them into account.
The following platforms and browsers remain compatible with this release, but will be deprecated
in a future release:
Operating Systems Authentication and Citrix Se rvers
z
Windows XP Professional SP2
z
Windows Vista (32-bit/64-bit) No
Service Pack
z
Windows Vista (32-bit/64-bit)
SP1
z
Windows 2000 Server
z
Active Directory on Windows 2000 Server
z
RADIUS v5.0
z
RSA Authentication Manager v5.2
z
Citrix MetaFrame XP
Citrix XML service must be running on the
MetaFrame server.
z
Citrix MetaFrame v1.8
MetaFrame 1.8 must have a license for Service Pack
2 and Feature Release 1 (SP2/FR1)

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 9
Client Components
The system requirements for client components are listed in the following tables:
z
“Tunnel Clients” on page 10
z
“Web-Based Clients” on page 10
z
“Proxy Clients” on page 12
z
“Virtual Assist Clients” on page 11
z
“End Point Control” on page 12
z
“Integration with Third-Party Components” on page 14
z
“Compatible Client Components” on page 14

10 | Chapter 1 - Introduction
Tunnel Clients
Operating system Browser Notes
Connect Tunnel Client
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
Windows Server platform:
z
Windows 2003 Server
z
Mac OS X 10.6
(32-bit/64-bit)
z
Mac OS X 10.5
z
Linux kernel 2.4.20 or later
(32-bit)
z
Linux kernel 2.6.0 or later
(64-bit)
Connect Tunnel Service
Windows Server platform:
z
Windows Server 2008 SP1
(32-bit/64-bit)
z
Windows Server 2003 SP2
OnDemand Tunnel Agent
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Mac OS X 10.6
z
Mac OS X 10.5
z
Linux kernel 2.4.20 or later
z
Linux kernel 2.6.0 or later
(64-bit)
z
n/a
z
n/a
z
Mozilla Firefox 3.5
z
n/a
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
Safari 4.0
z
Safari 3.0
z
Mozilla Firefox 3.5
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
z
Administrator rights
required for installation
z
Administrator rights
required for installation
z
Administrator rights
required for installation
z
Browser required only for
proxy detection
z
No support for End Point
Control
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
z
Administrator rights
required for installation
z
JRE 1.6.0 update 14 or
later
z
Administrator rights
required for installation
z
JRE 1.6.0 update 14 or
later
z
Administrator rights
required for installation
Web-Based Clients
Operating system Browser
WorkPlace Portal, Translated/Custom Port Mapped/Custom FQDN Mapped Web access
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Mac OS X 10.6
z
Mac OS X 10.5
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
Safari 4.0
z
Safari 3.0

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 11
Operating system Browser
z
Linux kernel 2.4.20 or later
z
Web-enabled mobile devices
z
Mozilla Firefox 3.5
z
The browser appropriate for your device
The following table shows W eb-based applications that are supported and tested for different types
of custom access:
Custom Access Type Supported and Tested Web Applications
z
Translation
z
Custom Port Mapped
z
Custom FQDN Mapped
z
Outlook Web Access 2003
z
Outlook Web Access 2007
z
Sharepoint 2003
z
Sharepoint 2007
z
Outlook Web Access 2003
z
Outlook Web Access 2007
z
Sharepoint 2003
z
Sharepoint 2007
z
Domino Web Access 8.0
z
Domino Web Access 8.5.x
Virtual Assist Clients
Operating system Browser Notes
Customer Application
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Mac OS X 10.6 (32-bit/64-bit)
z
Mac OS X 10.5
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
Safari 4.0
z
Safari 3.0
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
z
JRE 1.6.0 update 14 or
later
Technician Application
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
z
Standalone application
(32-bit/64-bit)
z
Windows XP Pro, SP3
12 | Chapter 1 - Introduction
Proxy Clients
Operating system Browser Notes
OnDemand Proxy Agent
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Mac OS X 10.6
(32-bit/64-bit)
z
Mac OS X 10.5
z
Linux kernel 2.4.20 or later
z
Linux kernel 2.6.0 or later
(64-bit)
Web Proxy Agent
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
Connect Mobile Client
z
Windows Mobile 6.5
z
Windows Mobile 6.1
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
Safari 4.0
z
Safari 3.0
z
Mozilla Firefox 3.5
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
n/a
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
z
Port-mapped mode
requires ActiveX or Java;
for users who can’t run
ActiveX, JRE is used.
z
64-bit support on Windows
7 and Windows Vista is
only supported for
OnDemand Mapped Mode
z
JRE 1.6.0 update 14 or
later
z
JRE 1.6.0 update 14 or
later
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
z
Includes Mobile2Market
certification
z
Supports Pocket PC
devices and smartphones
z
Does not support some
legacy devices, such as
Audiovox SMT5600,
Motorola MPx200 and
MPx220, Sierra Wireless
Voq, Samsung i600, iMate
SP2, and so on.
End Point Control
Operating system Browser Notes
Interrogator and Installer
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
ActiveX, or JRE 1.6.0
update 14 or later is
required
SonicWALL Aventail E-Class SRA Installation and Administration Guide | 13
Operating system Browser Notes
z
Windows Mobile 6.5
z
Windows Mobile 6.1
z
Pocket Internet Explorer
6.1
z
Pocket Internet Explorer
6.0
z
Interrogator only; both
Windows Mobile
Workplace (with Pocket
IE) and Connect Mobile
are supported, and can
coexist on the device
z
Windows Mobile 2003
z
n/a
z
Interrogator only;
Connect Mobile is
required
z
Mac OS X 10.6 (32-bit/64bit)
z
Mac OS X 10.5
z
Linux kernel 2.4.20 or later
z
Linux kernel 2.6.0 or later
z
Safari 4.0
z
Safari 3.0
z
Mozilla Firefox 3.5
z
JRE 1.6.0 update 14 or
later
z
JRE 1.6.0 update 14 or
later
(64-bit)
Aventail Cache Control
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista (32-bit/64bit)
z
Windows XP (32-bit/64-bit)
z
Windows Server 2008
(32-bit/64-bit)
z
Windows Server 2003 R2
z
Internet Explorer 8.0
z
Internet Explorer 7.0
z
Internet Explorer 6.0
z
Mozilla Firefox 3.5
z
Mozilla Firefox 3.0
z
Mozilla Firefox 2.0
z
Safari 3.0
(32-bit/64-bit)
z
Windows Server 2003
z
Mac OS X 10.x
z
Safari 4.0
z
Safari 3.0
z
Mozilla Firefox 3.5
z
Mozilla Firefox 3.0
z
Mozilla Firefox 2.0
Advanced EPC / Secure Desktop Emulator
z
Windows 7 (32-bit/ 64-bit)
z
Windows Vista SP2
(32-bit/64-bit)
z
Windows XP Pro, SP3
z
Mac OS X 10.6 (32-bit/64bit)
z
Mac OS X 10.5
z
Linux kernel 2.4.20 or later
z
Linux kernel 2.6.0 or later
z
Internet Explorer 8.0
(32-bit only)
z
Internet Explorer 7.0
(32-bit only)
z
Mozilla Firefox 3.5
z
Safari 4.0
z
Safari 3.0
z
Mozilla Firefox 3.5
(64-bit)

14 | Chapter 1 - Introduction
Integration with Third-Party Components
ActiveSync
SonicWALL supports clientless ActiveSync support for Exchange email to Apple iPhones, iPads,
Google Android mobile operating system, and devices running the popular Symbian operating
system. Symbian runs on many Nokia and Samsung devices that are popular choices for corporate
mail. ActiveSync support also l everages the device’ s ID capability to link the device to a single user,
providing a first layer of end-point control.
ActiveSync - Certified With ActiveSync - Compatible With Mobile Operating System
Apple iPhone Google Android 2.x
Symbian Apple iPad (with valid
Terminal Services and Citrix
certificates)
z
Windows Mobile 6.1
Note: Window Mobile 6.5 is
not supported with ActiveSync
due to Microsoft proprietary
changes.
To access email when using
6.5, download and install
Connect Mobile to provide
secured communication with
the Exchange server.
The SonicWALL appliance integrates with several popular security programs. In some cases, the
files necessary for integration are already on the appliance, and in other cases they must be copied
to the appliance.
Description Notes
Windows Terminal Services agent
Windows (ActiveX control)
Cross-platform (Java applet)
Citrix agent
Windows (ActiveX control)
Cross-platform (Java applet)
z
Version 6.0
z
Version 5.2
z
Version 8.6
z
Requires JRE 1.5 or later
z
Versions 9.x and 10.x. Version 11 is also
supported, but only if the agent is
downloaded separately and installed using
Microsoft Windows Installer (MSI).
z
Version 9.x and later
z
Requires JRE 1.5 or later
Compatible Client Components
Client platforms, browsers, and Java versions that are compatible with the appliance are shown in
the following table. There are no known issues with compatible components, and we continue to
offer technical support for them, but they have not been specifically tested in the current release
and future product changes will not take them into account.

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 15
The following platforms and browsers remain compatible with this release, but will be deprecated
in a future release:
Operating Systems Browsers Java Versions
z
Windows XP Professional SP2
z
Windows Vista (32-bit/64-bit)
No Service Pack
z
Windows Vista (32-bit/64-bit)
z
Firefox 3.0 (Windows)
z
Firefox 3.0 (Linux)
z
Safari 2.0
z
JRE 1.6.0 updates previous
to 14
z
JRE 1.5.0
SP1
z
Windows 2000 Server, SP4
z
Mac OS X 10.4
z
Windows Mobile 6.0
z
Windows Mobile 5.0
The following browsers are deprecated in this release:
Browsers
z
Internet Explorer 6.0
z
Firefox 2.0 (Windows)
z
Firefox 2.0 (Linux)
About the Docu m en ta tio n
This document contains detailed information about installing, configuring, and maintaining the
appliance. Its contents are also available as context-sensitive Help from AMC; see “Getting Hel p ”
on page 45 for more information.
Your SonicW ALL appliance also comes with a printed Getting Starte d Guide that explains important
VPN concepts and components and will aid in planning to deploy your VPN. For access to electronic
copies of all of the product documentation, log in to your mySonicWALL.com account and register
your appliance. See “Registering Your SonicWALL E-Class SRA Appliance” on page 247 for more
information.
Document Conventions
Throughout this document, “external” refers to the network interface connected to the Internet.
“Internal” refers to the network interface connected to your internal corporate network. This
document uses the following typographical conventions:
Typographical convention Usage
Bold User interface components (such as text boxes or buttons on a
Monospace font Information you are supposed to type.
Italic File names and directories, examples, and selections from drop-
commandname -x [-y] In command-line syntax, square brackets indicate optional
Web page).
down lists.
parameters.

16 | Chapter 1 - Introduction
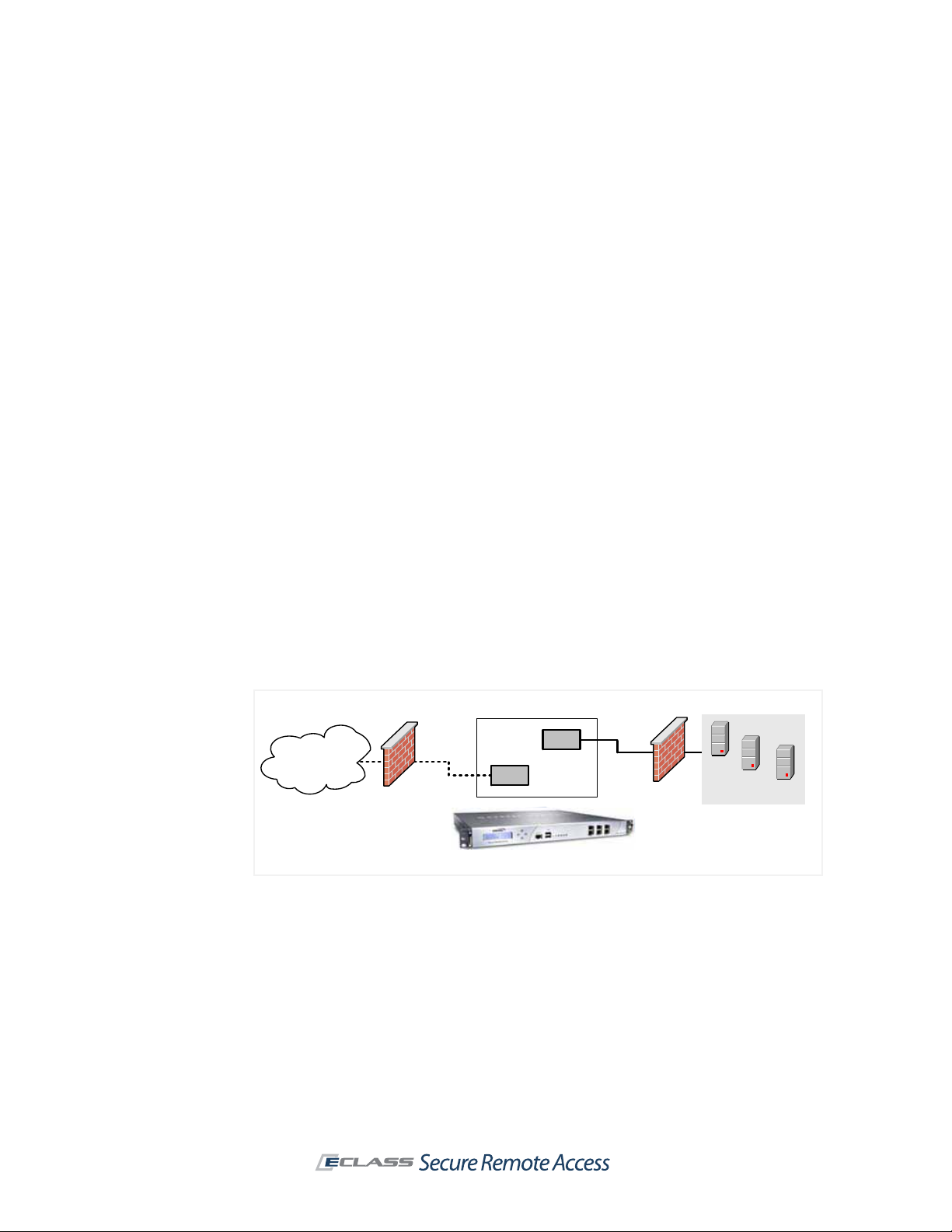
SonicWALL Aventail E-Class SRA Installation and Administration Guide | 17
Internal
interface
External
interface
SonicWALL Aventail Appliance
Firewall
Internet
Firewall
Corporate network
File
Server
Application
Server
Web
Server
Chapter 2
Installation and Initial Setup
This section shows where the appliance f its into your network environment, provides installation
and cabling instructions, and explains how to use the Web-based Setup Wizard (or alternatively use
the command-line Setup Tool) to perform basic network configuration.
Network Architecture
All of the SonicWALL appliances can be set up in either a dual interface or single interface
configuration, both of which are discussed in this section.
z
The EX7000, EX6000, EX-2500, and EX-1600 appliances include three physical network
interfaces and can be set up in a cluster for high availability (see “Installing and Configuring a
Cluster” on page 388 for more information), or one that uses an external load balancer (see
“Configuring a High-Capacity Cluster” on page 451).
z
The EX-750 appliance includes two physical network interfaces.
Dual-homed configuration (internal and external interfaces)
One network interface is used for external traffic (that is, to and from the Internet), and the other
interface is used for internal traffic (to and from your corporate network).
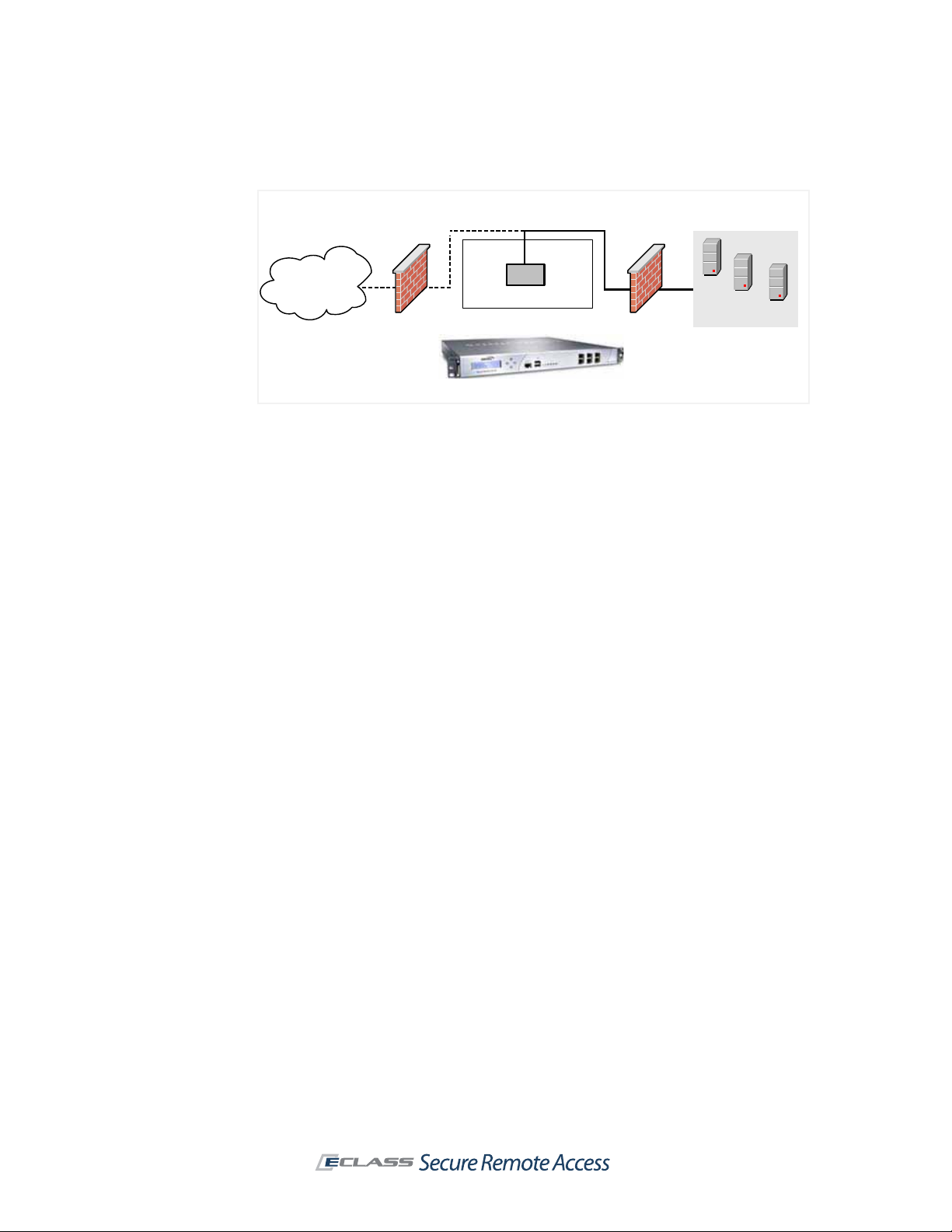
18 | Chapter 2 - Installation and Initial Setup
Single-homed interface configuration (internal interface)
A single network interface is used for both internal and external traffic. In this configuration, the
appliance is usually installed in the demili tarized zone (or DMZ, also known as a perimeter network).
Internet
Firewall
DMZ
Internal interface
Firewall
SonicWALL Aventail Appliance
Corporate network
File
Server
Application
Server
Web
Server
In both configurations, incoming requests to the SonicWALL services—including HTTP/S traffic for
the Web proxy service—are sent over port 80 (HTTP) and port 443 (HTTPS). Traffic from the
OnDemand agent is always sent over port 443. Because most networks are configured to enable
traffic over these ports, you shouldn’t need to reconfigure firewalls on your network.
You should install the appliance in a location where it can connect to resources on your network,
including:
z
Application servers and file servers, including Web servers, client/server applications, and
Windows file servers.
z
External authentication repositories (such as an LDAP, Microsoft Active Directory, or RADIUS
server).
z
One or more Domain Name System (DNS) servers.
z
Optionally, a Windows Internet Name Service (WINS) server. This is required for browsing
Windows networks using WorkPlace.
CAUTION The SonicWALL appliance does not provide full firewall capabilities and should be
!
secured behind a firewall. Running without a firewall makes the appliance vulnerable to
attacks that can compromise security and degrade performance.
Although not required, enabling the appliance to communicate with these additional resources
provides greater functionality and ease of use:
z
Network Time Protocol (NTP) server for synchronizing the time on the appliance.
z
External server for storing syslog output.
z
Administrator’s workstation for secure shell (SSH) access.
You can configure the appliance to use a self-signed server certificate, or, for enhanced security,
you can obtain a certificate from a commercial certificate authority (CA). For more information, see
“Obtaining a Certificate from a Commercial CA” on page 68.
Preparing for the Installation
Before beginning the installation, you need to gather information about your networking
environment and verify that your firewalls are properly configured to permit traffic to and from the
appliance.

SonicWALL Aventail E-Class SRA Installation and Administration Guide | 19
Gathering Information
Before configuring the appliance, you need to gather the following information. You are prompted
for some of this information when running Setup Wizard (see “Web-Based Configuration Using
Setup Wizard” on page 32) or Setup Tool (see “Configuring a New Appliance Using Setup Tool” on
page 398), but most of it will be used when you configure the appliance in AMC (see “Network and
Authentication Configuration” on page 55).
If you are installing a cluster , you need some additional information. See “Installing and Configuring
a Cluster” on page 388 and “Configuring a High-Capacity Cluster” on page 451.
Settings required in order to start Aventail Management Console
z
The root password for administering the appliance
z
The name for the appliance (becaus e this n ame is used only in log files, you don’t need to add
it to DNS)
z
The internal IP address and, optionally, an external IP address
z
Select a routing mode and supply IP addresses for the network gateways to the Internet, and
your corporate network.
Certificate information
Several pieces of information are used to ge ne rate the server and AMC certificates:
z
A fully qualified domain name (FQDN) for the appliance and for any W orkPlace sites that use a
unique name. These names should be added to your public DNS; they are also visible to users
when they connect to Web-based resources.
z
A FQDN for the Aventail Management Console (AMC) server. The AMC server name is used to
access AMC, which is a Web-based tool for administering the appliance.
Name lookup information
z
Internal DNS domain name of the network to which the appliance is connected
z
Primary internal DNS server address (additional DNS servers are optional)
z
IP address for an internal WINS server and the name of your Windows domain (required to
browse files on a Windows network using WorkPlace, but are otherwise optional)
Authentication information
z
Server name and login information for your authentication servers (LDAP, Active Directory, or
RADIUS)
Virtual Address pool information
z
If you are planning to deploy either network tunnel client (Connect Tunnel or OnDemand
Tunnel), you must allocate IP addresses for on e or more address pools. F or m ore infor mation ,
see “Configuring IP Address Pools” on page 347.
Optional configuration information
z
To enable SSH access from a remote machine, you need to know the remote host’s IP address.
z
To synchronize with an NTP server, you need to know the IP addresses for one or more NTP
servers.
z
To send data to a syslog server, you need to know the IP address and port number for one or
more syslog servers.
Verifying Your Firewall Policies
For the appliance to function correctly, you must open ports on your external (Internet-facing) and
internal firewalls.

20 | Chapter 2 - Installation and Initial Setup
External firewall
For secure access to the appliance from a Web browser or OnDemand, you must make sure that
ports 80 and 443 are open on firewalls at your site. Opening your firewall to permit SSH access is
optional, but can be useful for performing administrative tasks from a remote system.
Traffic type Port/protocol Usage Required?
HTTP 80/tcp Unencrypted network access x
HTTPS 443/tcp Encrypted network access x
SSH 22/tcp Adm inistrative access to the appliance
Internal firewall
If you have a firewall on the internal network, you may need to adjust its policy to open ports for
back-end applications with which the appliance must communicate. In addition to opening ports for
standard network services such as DNS and email, you may need to modify your firewall policy in
order for the appliance to access the following services.
Traffic type Port/protocol Usage
Microsoft networking
z
z
z
z
z
LDAP (unencrypted) 389/tcp Communicate with an LDAP directory or
LDAP over SSL
636/tcp Communicate with an LDAP directory or
(encrypted)
RADIUS 1645/udp or 1812/udp Communicate with a RADIUS
NTP 123/udp Synchronize the appliance clock with an
Syslog 514/tcp Send system log information to a syslog
SNMP 161/udp Monitor the appliance from an SNMP
138/tcp and 138/udp
137/tcp and 137/udp
139/udp
162/snmp
445/smb
Used by WorkPlace to perform WINS name
resolution, browse requests, and access
file shares
Microsoft Active Directory
Microsoft Active Directory over SSL
authentication server
NTP server
server
management tool
Helpful Management Tools
To manage the appliance from a remote system running Microsoft Windows, you may find the
following management tools useful. Both of these tools use encryption to protect information from
eavesdropping, unlike standard FTP o r Telnet utilities:
z
A Secure Shell (SSH) client enables you to securely log in to the appliance and configure it
from the command line. This is useful for backing up the system, viewing log files, and
configuring advanced network settings. A popular SSH client for Windows is V anDyke Software’s
SecureCRT. A trial download is available at http://www.vandyke.com/products/securecrt/.
Another popular client is PuTTY, a free implementation of Telnet and SSH for Windows
platforms
To connect to the appliance using SSH, you type root as the username and type the password
you created using Setup Wizard.
z
A Secure Copy (scp) client makes it easy to securely transfer files from a PC running
Windows to the appliance. This is useful for copying certificates and other data to the appliance.
A popular Windows client is WinSCP, available at http://winscp.sourceforge.net/eng/.
. PuTTY is recommended by Cisco.
SonicWALL Aventail E-Class SRA Installation and Administration Guide | 21
Most of the configuration management tasks that you need to perform—backing up and restoring
your appliance configuration, applying upgrades, and so on—can be done on the Maintenance
page in AMC, as described in “Managing Configuration Data” on page 224. If you prefer to handle
these tasks on the command line, see “Appliance Command-Line Tools” on page 397.
Installation and Deployment Process
This section outlines the process of installing, configuring, and testing the appliance, and then
deploying it in a production environment. Here’s an overview of the steps:
Installation step Description
Make a note of your appliance serial
number and authentication code
Rack-mount the appliance and connect the
cables
Turn on the appliance and begin
configuration
Run Setup Wizard The wizard guides you through the process of initial
Register your appliance on MySonicWALL Register your appliance on MySonicWALL. Product
You’ll need this information when you register your
product on MySonicWALL. It is displayed in one or
two places, depending on your appliance model:
z
EX7000 and EX6000: The serial number and
authentication code are printed on your appliance
label; they are also displayed on the General
Settings page in AMC.
z
EX-2500, EX-1600 and EX-750: The serial
number is printed on your appliance label; the
General Settings page in AMC displays both the
serial number and authentication code.
See “Specifications and Rack Installation” on
page 22 and “Connecting the Appliance” on page 29.
To connect to your appliance on your internal
network you must specify an internal IP address, the
subnet mask, and indicate whether your appliance is
part of a cluster. How you do this depends on your
appliance model:
z
For all appliance models except the EX-750: Use
the controls on the front of the appliance. See
“Powering Up and Configuring Basic Network
Settings” on page 31.
z
EX-750: Use a command-line tool on the
appliance; see “Configuring a New Appliance
Using Setup Tool” on page 398.
setup for your SonicWALL SRA appliance. See “WebBased Configuration Using Setup Wizard” on
page 32.
registration gives you access to essential resources,
such as your license file and updates. In order to
register, you need both the serial number for your
appliance and its authentication code.
 Loading...
Loading...