
!
!
!
!
!
!
!
!
!
! !
!
!
!
!
USER!MANUAL!
Version!2.1!
October!2017!
WWW.SOLIDASYSTEMS.COM
SL-2000!/!SL-4000!/!SL-6000!!Security!Appliances!

2
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
"#$%&!'(!)'*+&*+,!
!
1.#Introduction#........................................................................................................................................#4!
1.1#Reputatio n #Based#Detection #a n d#Prevention#..................................................................................#4 !
1.2#Intrusion#Detection#and#Prevention#...................................................................................................#4!
1.3#Monitoring#and#Logging#..........................................................................................................................#4!
2.#Hardware#Installation#.....................................................................................................................#5!
2.1#Physical#Installation#.................................................................................................................................#5!
2.2#Port#Location#..............................................................................................................................................#6!
2.3#Management#Port#......................................................................................................................................#7!
2.4#Required#Open#Network#Ports#.............................................................................................................#8!
Threat!Intelligence!Updates!........................................................................................................................................!8!
Solida!Monitor!...................................................................................................................................................................!8!
Solida!Multi!.........................................................................................................................................................................!9!
Solida!Notify!and!Email!Notifications!.....................................................................................................................!9!
2.5#Powering#On#The#Appliance#..................................................................................................................#9!
2.6#Powering#Off#The#Appliance#..................................................................................................................#9!
3.#Accessing#The#Web#Applications#..............................................................................................#10!
3.1!Management!Ethernet!Port#....................................................................................................................#10!
3.2#Managing#Users#.......................................................................................................................................#11!
4.#Reputation#Based#Detection#.......................................................................................................#13!
4.1#Overview#...................................................................................................................................................#13!
4.2#DGA#List#................................................................ .....................................................................................#13!
4.3#List#Updates#..............................................................................................................................................#14!
5.#Reputation#Threat#List#Updates#................................................................................................#16!
5.1#About#Tor#Exit#Nodes#............................................................................................................................#17!
6.#Deep#Packet#Inspection#Configuration#...................................................................................#18!
7.#User#Black#and#White#Listing#.....................................................................................................#19!
7.1#Overview#...................................................................................................................................................#19!
7.2#Blacklisting#Domain#Names#................................................................................................................#19!
7.3#Blacklisting#IP#Addresses#....................................................................................................................#20!
7.4#Whitelisting#IP#Addresses#...................................................................................................................#20!
7.5#Uploading#a#Blacklist#File#....................................................................................................................#20!
8.#Intrusion#Detection#and#Prevention#Rules#............................................................................#21!
8.1#Rule#Overview#.........................................................................................................................................#21!
8.2#Rule#List#.....................................................................................................................................................#21!
8.3#Export#Rule#File#......................................................................................................................................#22!
8.4#Import#Rule#File#......................................................................................................................................#22!
8.5#Rule#Sets#....................................................................................................................................................#22!
8.6#Activating#a#Rule#Set#..............................................................................................................................#23!
8.7#Operating#Mode#......................................................................................................................................#23!
8.8#Creating#Custom#Rules#.........................................................................................................................#23!
8.9#Rule#Id#........................................................................................................................................................#24!
9.#Events#and#Event#Severity#...........................................................................................................#25!
9.1#Event#Overview#.......................................................................................................................................#25!
9.2#Event#Severity#..........................................................................................................................................#26!
9.2.1!Low!severity!(colored!green!in!the!GUI)!.................................................................................................!26!
9.2.2!Medium!severity!(colored!orange!in!the!GUI)!.......................................................................................!26!

3
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
9.2.3!Critical!severity!(colored!red!in!the!GUI)!................................................................................................!27!
9.3#Source#and#Destination#IP#Addresses#.............................................................................................#27!
10.#Responding#To#Critical#Events#................................................................................................#28!
11.#Remote#Monitoring#.....................................................................................................................#29!
11.1#Multi#Appliance#Remote#Mo nitoring#.............................................................................................#29!
11.2#Mobile#Phone#Application#Remote#Monitoring#.........................................................................#30!
11.3#Netflow#Logging#....................................................................................................................................#30!
11.3#Remote#Logging#To#Syslog#Server#..................................................................................................#30!
12.#Single#Appliance#High#Availability#........................................................................................#32!
12.1#Configuration#........................................................................................................................................#32!
13.#Multi#Appliance#High#Availability#..........................................................................................#33!
13.1.#Master#Slave#Configuration#.............................................................................................................#33!
14.#Email#Notification#........................................................................................................................#34!
14.1#Setting#Up#Email#Notification#...........................................................................................................#34!
14.1.1!Email!Notification!...........................................................................................................................................!34!
14.1.2!Instant!Critical!..................................................................................................................................................!34!
14.1.3!Current!Email!Address!.................................................................................................................................!34!
14.1.4!New!Email!Address!........................................................................................................................................!35!
14.2#Event#Notification#Emails#..................................................................................................................#35!
15.#Data#Logging#..................................................................................................................................#36!
15.1#Packet#Logging#......................................................................................................................................#36!
15.2#Dropped#Packet#Logging#...................................................................................................................#36!
15.3#Event#Logging#........................................................................................................................................#37!
15.4#IP#Address#Logging#..............................................................................................................................#37!
15.5#HTTP#Logging#........................................................................................................................................#37!
15.6#Downloading#Log#Files#.......................................................................................................................#38!
15.7#Deleting#Log#Files#................................................................................................................................#38!
16.#System#Software#Updates#.........................................................................................................#39!
17.#Support#Bundle#Generation#.....................................................................................................#41!
17.1#Generating#a#support#bundle#...........................................................................................................#41!
17.2#Downloading#a#support#bundle#......................................................................................................#41!
18.#Report#Generation#......................................................................................................................#43!
Appendix#A.#VoIP#Caller#Blocking#.................................................................................................#44!
A.1#Appliance#Setup#......................................................................................................................................#44!
A.2#Blocked#Numbers#List#..........................................................................................................................#44!
A.3#System#VoIP#Rules#.................................................................................................................................#45!
A.4#Event#Generation#...................................................................................................................................#46!
Appendix#B.#Direct#Access#of#Log#Files#........................................................................................#47!
B.1#Logging#In#To#The#Log#File#Directories#...........................................................................................#47!
B.2#Copying#Out#Log#Files#...........................................................................................................................#47!
B.3#Log#File#Formats#.....................................................................................................................................#47!
Appendix#C.#Solida#Multi#Remote#Monitoring#...........................................................................#48!
C.1#Setting#Up#The#Solida#Multi#Sever#.....................................................................................................#48!
C.2#Configuring#The#Appliance#for#Solida#Multi#..................................................................................#48!
C.3#Required#Network#Ports.#.....................................................................................................................#48!
C.4#Communication#.......................................................................................................................................#48!

4
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
-.!/*+0'123+4'*!
!
This!manual!contains!instructions!for!how!to!configure!and!use!the!following!Solida!Systems!
network!security!appliances:!
!
! SL-2000! Dual!1!Gigabit!Ethernet!ports!
! SL-4000! Quad!1!Gigabit!Ethernet!ports!
! SL-6000! Dual!10!Gigabit!Ethernet!ports!
!
The!SL-2000,!SL-4000!and!SL-6000!appliances!represent!the!latest!in!network!security!
technology.!They!combine!functionality!that!would!otherwise!require!several!different!devices.!
These!intrusion!detection!and!prevention!systems!offer!reputation!based!detection,!intrusion!
detection!and!prevention,!network!traffic!monitoring!and!packet!logging.!
!
The!next!sections!will!describe!what!some!of!these!features!mean!for!your!network.!
!
-.-!5&62+#+4'*!7#,&1!8&+&3+4'*!#*1!90&:&*+4'*!
!
Solida!Systems!provides!reputational!threat!intelligence!in!the!form!of!a!data!feed!hosted!in!the!
cloud.!This!threat!feed!is!updated!hourly!and!includes!malicious!URLs,!domain!names!and!IP!
addresses.!These!are!harvested!from!various!international!threat!intelligence!sources.!!
!
The!threat!feed!includes!information!about!current!threats!such!as!ransomware,!phishing!sites,!
trojans!and!many!other!threat!categories.!
!
-.;!/*+02,4'*!8&+&3+4'*!#*1!90&:&*+4'*!
!
Intrusion!detection!and!prevention!is!implemented!through!a!rule!engine!and!deep!packet!
inspection!(DPI).!Solida!Systems!provides!pre-defined!rules!and!rule!sets!through!the!cloud!
based!threat!feed.!A!simple!and!intuitive!configuration!page!is!provided!for!users!interested!in!
writing!custom!rules.!
!
-.<!='*4+'04*>!#*1!?'>>4*>!
!!!
Tools!are!available!to!facilitate!monitoring!and!evidence!collection.!Logs!and!evidence!files!are!
written!in!PCAP!format!and!are!compatible!with!most!industry!standard!analysis!tools.!
!
!
5
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
;.!@#01A#0&!/*,+#%%#+4'*!
!
;.-!9BC,43#%!/*,+#%%#+4'*!
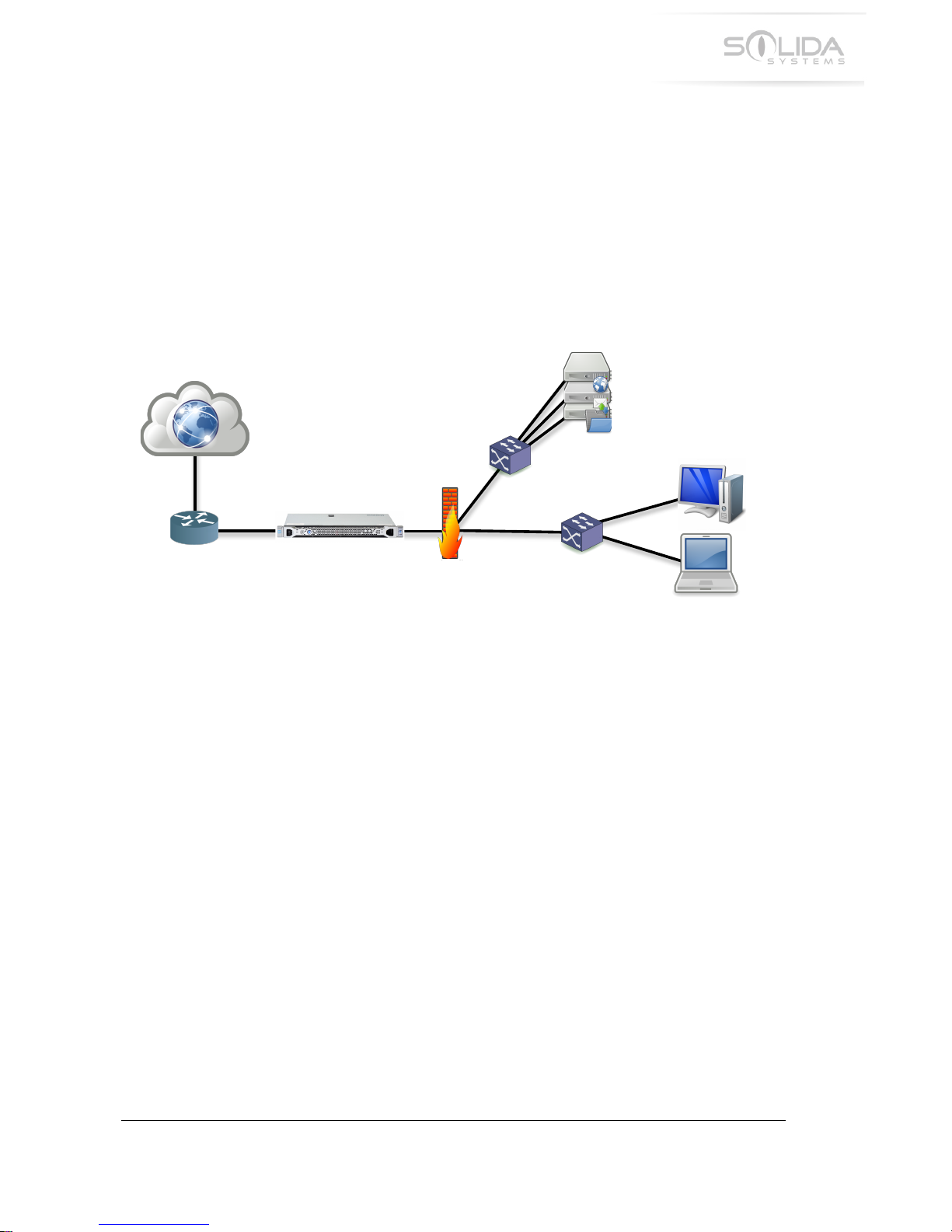
For the appliance to work as designed it must be installed immediately after the Internet router
and in front of any firewall. It is very important that the appliance is installed IN FRONT of any
firewall. This way the appliance will be able to see all incoming and outgoing packets on the
Internet and gain full exposure to the threat environment.
Figure 2.1 Typical Installation
For networks with high availability requirements it is possible to install two identical appliances
next to each other and configure them in a high availability mode. Please refer to the chapter
Multi Appliance High Availability for instructions on how to configure the appliances in this
mode.
In some rare cases the main switch in the network might use PPPoE for its communication with
the Internet router. All Solida System appliances have support for this type of configuration.
!
!
"B&!/*+&0*&+
DE+&0*#%!5'2+&0
F*'!(4%+&04*>G
H'%41#!8&:43&
I40&A#%%
HA4+3B
HA4+3B
J'0K,+#+4'*,
H&0:&0,
6
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
;.;!9'0+!?'3#+4'*!
!
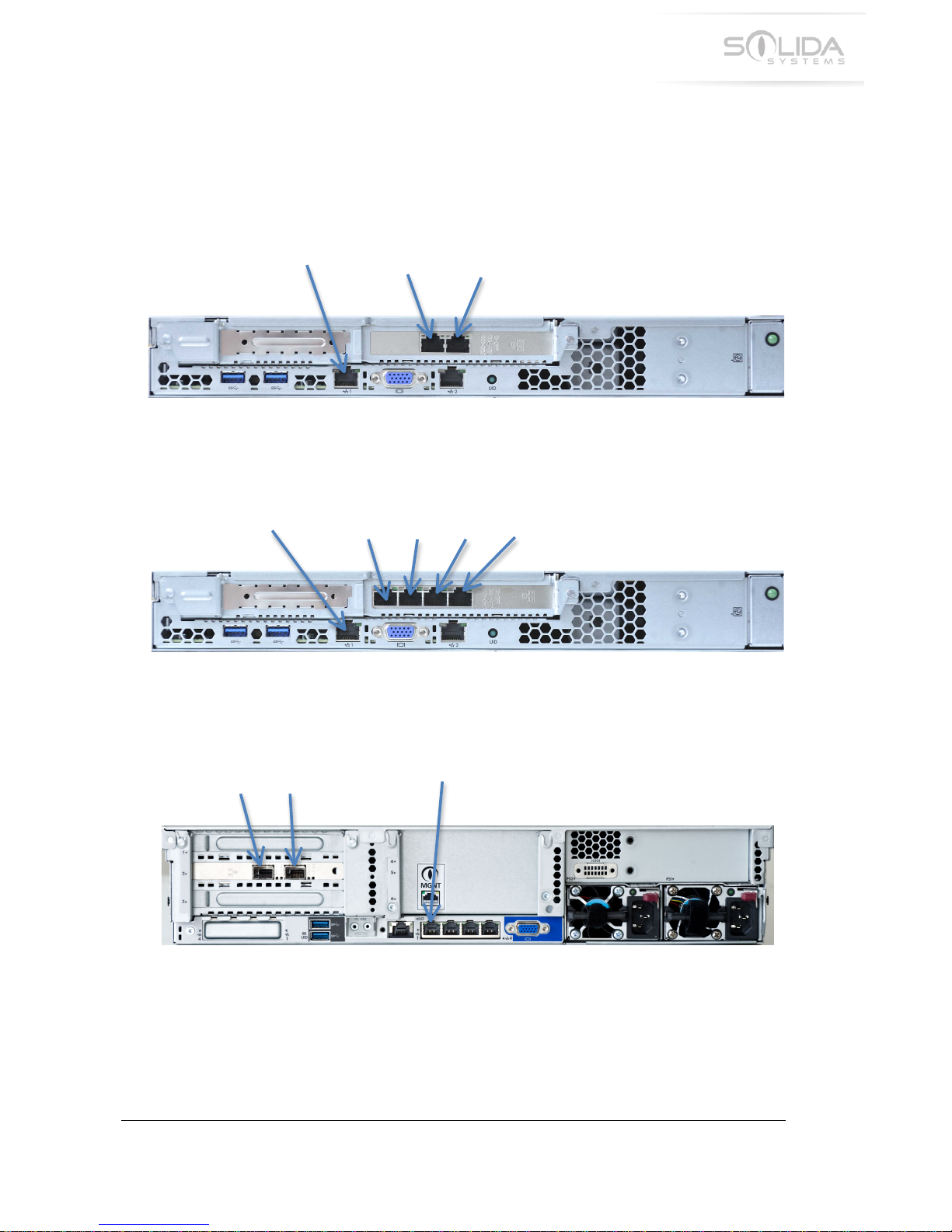
The!appliances!include!two!different!sets!of!Ethernet!ports.!One!set!is!located!on!the!server!
motherboard.!The!other!set!on!a!high-speed!network!interface!adapter.!
!
!
!
!
!
!
Figure 2.1 SL-2000 back view.
!
!
!
!
! !
Figure 2.2 SL-4000 back view.
!
!
!
!
!
!
!
!
!
Figure 2.3 SL-6000 back view.
!
Located!in!the!upper!row!of!the!Ethernet!ports!are!the!ports!used!for!high-speed!network!
traffic.!The!bottom!left!Ethernet!port!on!the!SL-2000!and!SL-4000!is!used!for!device!
management.!The!bottom!right!port!is!currently!unused.!The!bottom!left!port!on!the!SL-6000!
High-speed ports
Port1 Port0
High-speed ports
Port0 Port1
Management Port
Management Port
High-speed ports
Port3 Port2 Port1 Port0
Management Port

7
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
appliance!is!used!for!the!device!management.!The!right!side!ports!are!unused.!
!
The!high-speed!Ethernet!ports!are!named!Port!0!and!Port!1!on!the!SL-2000!and!SL-6000!and!
Port!0!to!Port!3!on!the!SL-4000.!
!
The!default!factory!configuration!for!the!high-speed!Ethernet!ports!is:!
!
! Port!0! ! WAN!side! Internet!connected!router!
! Port!1! ! LAN!side!
! Port!2! ! Unused! (for!the!SL-4000!only)!
! Port!3! ! Unused! (for!the!SL-4000!only)!
!
The!default!factory!settings!can!be!changed!through!the!web!configuration!utility!that!is!
accessed!through!a!browser.!
!
The!most!common!setup!is!using!the!Solida!appliance!as!an!endpoint!device.!This!allows!for!all!
incoming!and!outgoing!data!packets!to!be!inspected.!This!offers!the!best!protection!against!any!
type!of!malicious!traffic!
!
For!larger!networks!it!might!be!necessary!to!protect!multiple!sections!of!the!network!with!
dedicated!security!appliances.!For!those!installations!make!sure!that!the!WAN!port!is!connected!
upwards!(towards!the!Internet!router!side).!Conversely!make!sure!the!LAN!side!is!connected!to!
the!sub-partitioned!network.!!
!
!
;.<!=#*#>&L&*+!9'0+!
!
The!management!port!is!used!for!two!purposes:!Accessing!the!configuration!utility!and!the!
monitoring!utility!is!done!through!this!port.!The!management!port!is!also!used!for!updating!the!
threat!list!data!and!for!communicating!with!other!appliances!in!a!high!availability!configuration.!
!
/+!4,!:&0C!4L6'0+#*+!+B#+!+B&!L#*#>&L&*+!6'0+!#%A#C,!B#,!/*+&0*&+!#33&,,.!This!is!typically!
accomplished!by!connecting!the!management!port!to!a!switch!in!the!LAN!side!of!the!network!
being!protected.!The!default!IP!address!for!the!management!port!is!192.168.1.250.!Please!refer!
to!the!following!chapter!on!how!to!change!this!IP!address.!
!
The!management!port!IP!settings!configuration!window!includes!a!button!labeled!“Test!
Connection”.!Pressing!this!button!will!generate!a!ping!to!an!IP!address!on!the!Internet.!If!this!
ping!receives!a!response!it!can!be!assumed!the!management!port!has!proper!access!to!the!
Internet.!If!no!response!to!this!ping!is!detected,!the!management!port!does!not!have!the!
required!access!to!the!Internet.!!In!this!case!it!will!be!necessary!to!troubleshoot!the!installation!
and!retry!this!test!until!a!proper!connection!is!made.!
!

8
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
;.M!5&N240&1!O6&*!P&+A'0K!9'0+,!
!
The!appliance!needs!to!be!able!to!connect!with!Solida!Systems!cloud!server!to!retrieve!threat!
intelligence!updates!and!occasional!software!updates.!It!is!very!important!that!this!connection!
is!working!correctly.!Without!a!proper!connection,!the!appliance!will!still!function,!but!the!
threat!intelligence!will!not!be!updated!and!the!remote!monitoring!tools!will!not!be!functional.!
!
The!domain!name!for!this!cloud!server!is!3%'21B',+.,'%41#,C,+&L,.3'L.!The!server!is!set!up!
with!a!fixed!IP!address.!This!IP!address!can!be!obtained!by!using!nslookup!(windows)!or!the!dig!
tool!(Linux),!if!it!needs!to!be!provided!to!a!firewall.!!
!
In!case!a!firewall!is!deployed!in!the!network,!it!is!not!required!to!open!up!any!ports!for!incoming!
traffic!from!the!Internet.!All!communication!is!initiated!from!within!the!appliance.!The!only!
exception!to!this!would!be!if!the!user!elects!to!access!the!GUI!applications!from!outside!the!
network!over!the!Internet!without!the!use!of!a!VPN!connection.!This!is!possible!but!not!
recommended.!When!several!ports!are!opened!up!in!the!firewall!it!might!result!in!a!security!
weakness.!!
!
The!“reputation!threat!list!updates”!configuration!window!includes!a!button!labeled!“Test!
Connection”.!When!pressing!this!button,!the!appliance!will!try!to!connect!with!Solida’s!cloud!
server!the!exact!same!way!it!would!do!for!an!update!of!the!threat!intelligence.!If!this!test!fails,!
the!installation!must!be!checked!to!identify!the!cause!of!the!failure.!This!test!must!complete!
successfully!for!the!appliance!to!be!able!to!download!the!threat!intelligence!data!and!function!
as!designed.!
!
"B0&#+!/*+&%%4>&*3&!Q61#+&,!
The!threat!intelligence!updates!are!performed!as!follows:!
!
If!port!22!(SSH!port)!is!opened!in!the!network!for!outgoing!traffic!towards!the!Internet,!all!
threat!intelligence!data!will!be!downloaded!over!this!port.!
!
If!outgoing!traffic!over!port!22!is!blocked!by!a!firewall,!then!the!appliance!will!default!to!using!
port!443!(HTTPS)!port!for!its!threat!intelligence!download.!
!
It!is!VERY!IMPORTANT!that!one!of!these!two!paths!are!opened.!Otherwise!the!appliance!will!not!
be!able!to!perform!its!hourly!threat!feed!updates.!
!
H'%41#!='*4+'0!
Solida!Monitor!GUI!application!is!using!port!443!for!its!communication!with!the!appliance.!It!
supports!an!option!that!performs!a!WhoIs!lookup!of!a!selected!IP!address.!!These!WhoIs!
accesses!are!initiated!from!within!the!appliance!and!take!place!over!port!43.!Port!43!must!be!
opened!for!outgoing!requests!to!the!Internet!for!the!WhoIs!feature!to!work!properly.!
!

9
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
H'%41#!=2%+4!
The!multi!appliance!remote!monitoring!tool,!Solida!Multi,!also!requires!either!port!22!or!port!
443!to!be!opened!for!outgoing!communication!towards!the!Internet.!The!appliance!will!also!use!
one!of!these!ports!when!it!pushes!event!data!and!log!files!to!the!server!that!is!hosting!Solida!
Multi.!!
!
H'%41#!P'+4(C!#*1!DL#4%!P'+4(43#+4'*,!
The!mobile!phone!application,!Solida!Notify,!uses!either!outgoing!port!22!or!port!443!for!its!
event!data!push!needs.!If!email!notification!is!enabled,!this!communication!also!takes!place!on!
either!outgoing!port!22!or!port!443!towards!the!Internet.!
!
;.R!9'A&04*>!O*!"B&!S66%4#*3&!
!
The!appliance!is!powered!on!by!pushing!the!button!at!the!front!of!the!appliance.!To!do!this!it!is!
necessary!to!first!remove!the!security!bezel.!Once!powered!on!it!will!take!up!to!4!minutes!or!
more!for!the!appliance!to!become!fully!operational.!!
!
;.T!9'A&04*>!O((!"B&!S66%4#*3&!
!
To!power!off!the!appliance,!remove!the!security!bezel!and!push!the!power!button!once.!This!
will!initiate!the!shut-down!procedure!inside!the!appliance.!It!will!take!about!30!seconds!for!the!
appliance!to!properly!shut!itself!down.!It!is!not!advised!to!pull!out!the!power!cord!as!a!way!to!
shut!down!an!appliance.!This!could!result!in!log!data!loss.!
!
!
!
!
!

10
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
<.!S33&,,4*>!"B&!J&$!S66%43#+4'*,!
!
The!appliances!contain!two!different!software!applications.!One!application!is!used!for!system!
configuration!and!another!for!monitoring.!Both!applications!are!password!protected!to!prevent!
unauthorized!use.!These!applications!are!both!accessed!through!the!appliance!management!
port.!Both!applications!are!accessed!over!HTTPS.!This!makes!it!secure!in!case!a!user!wants!to!
monitor!an!application!from!outside!the!LAN!or!over!the!Internet.!!
!
3.1!Management!Ethernet!Port!
!
To!access!the!configuration!and!monitoring!applications,!connect!the!management!port!to!a!
switch!on!the!LAN!side!of!the!network.!Open!a!browser!on!a!computer!connected!to!the!same!
network.!Enter!the!MGNT!port!IP!address!in!the!browser!as!follows:!
!
! https://192.168.1.250/config! for!the!configuration!application!
! https://192.168.1.250! ! for!the!monitoring!application!
!
If!everything!is!configured!correctly,!a!login!page!will!appear!in!the!browser!window.!Enter!the!
supplied!user!name!and!password!to!log!in.!Some!networks!might!use!another!IP!address!range!
other!than!192.168.x.x,!for!example!10.32.x.x.!If!this!is!the!case!it!will!be!required!to!change!the!
management!port's!IP!address!before!the!appliance!is!connected!to!the!LAN!side!switch.!!
!
To!change!the!default!IP!address,!directly!connect!a!computer!with!the!appliance!through!an!
Ethernet!cable.!Make!sure!the!computer's!IP!address!is!set!manually!since!direct!connecting!
bypasses!any!DHCP!server.!Start!the!configuration!utility!by!entering!the!default!IP!address!into!
the!browser!followed!by!/config!(https://192.168.1.250/config).!
!
Log!into!the!application!and!then!navigate!to!the!page!named!“Configuration”.!Locate!the!box!
labeled!“Change!Management!Port!IP!Settings”.!Change!the!IP!address,!netmask!and!gateway!
fields!to!match!the!ones!used!in!the!network.!In!some!networks!it!might!be!required!to!use!a!
local!corporate!DNS!server!rather!than!a!public!one.!In!these!cases,!enter!the!IP!address!for!the!
local!DNS!server!in!the!DNS!server!field.!!The!appliance!will!use!this!IP!address!for!resolving!the!
domain!for!the!cloud!based!threat!intelligence!data!feed.!!
!
Once!the!“Activate”!button!is!pressed,!the!appliance!will!be!reconfigured!with!this!new!address!
information.!Note!that!it!will!take!up!to!a!minute!for!this!reconfiguration!to!complete.!A!
countdown!timer!pop-up!window!will!appear!and!show!a!60!second!countdown!after!a!change!
is!activated.!
!
An!example!is!shown!below:!
!
!
!
!

11
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
!
!
!
!
!
!
!
!
!
!
Figure 3.1 Change management port IP setting box.
!
!
Once!the!configuration!of!the!new!IP!addresses!is!complete,!remove!the!directly!connected!
computer!and!connect!the!appliance!to!the!LAN!side!switch.!
!
The!configuration!window!includes!a!button!labeled!“Test!Connection”.!Pressing!this!button!will!
generate!a!ping!to!an!IP!address!on!the!Internet.!If!this!ping!receives!a!response!it!can!be!
assumed!the!management!port!has!proper!access!to!the!Internet.!If!no!response!to!this!ping!is!
detected,!the!management!port!does!not!have!the!required!access!to!the!Internet.!!In!this!case!
it!will!be!necessary!to!troubleshoot!the!installation!and!retry!this!test!until!a!proper!connection!
is!made.!
!
<.;!=#*#>4*>!Q,&0,!
!
The!first!time!the!user!logs!into!either!Web!application,!a!default!factory!username!and!
password!will!be!used.!After!the!first!login!it!is!recommended!to!create!new!users!that!will!be!
allowed!to!log!in!to!the!applications.!Creating!and!managing!the!user!credentials!is!done!
through!the!configuration!application.!First!navigate!to!the!“Configuration”!page!and!then!
locate!the!box!named!“Manage!Users”..!!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure 3.2 Add new user box.

12
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
To!create!a!new!user,!press!the!button!labeled!“Add!User”!and!enter!the!new!credentials!in!the!
indicated!fields.!
!
The!drop!down!menu!at!the!top!of!the!“Add!New!User”!window!contains!two!options:!
“Monitoring!Only”!and!“Configuration!&!Monitoring”.!Select!“Monitoring!Only”!for!users!that!
are!only!allowed!to!log!into!the!monitoring!application.!The!monitoring!application!does!not!
allow!for!changing!any!configuration!parameters!or!modifying!the!detection!rules.!
!
!

13
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
M.!5&62+#+4'*!7#,&1!8&+&3 +4'*!
!
M.-!O:&0:4&A!
!
The!most!basic!form!of!intrusion!and!malware!detection!goes!under!the!category!of!reputationbased!detection.!This!type!of!detection!is!performed!by!attempting!to!identify!communication!
with!unfriendly!hosts!on!the!Internet.!These!are!ones!that!are!believed!to!be!malicious,!based!
upon!a!reputation!for!previous!or!ongoing!malicious!activities.!
!
Reputation!based!detection!is!performed!by!comparing!requested!IP!addresses!or!domain!
names,!against!a!reputation!list!of!hosts!with!negative!reputations.!Solida!appliances!allow!for!
downloading!lists!based!on!domain!names!and!IP!addresses.!The!data!in!these!lists!are!
processed!and!stored!in!hash!tables,!so!that!fast!lookups!can!be!performed!against!them!in!real!
time.!These!lists!are!automatically!downloaded!from!a!cloud-based!service!provided!by!Solida!
Systems.!
!
Both!DNS!queries!and!HTTP!requests!are!monitored!and!compared!against!the!reputation!list.!If!
a!hit!is!detected,!the!request!can!be!either!flagged!as!suspicious!or!completely!dropped.!It!is!
important!to!recognize!that!a!hit!in!a!reputation!blacklist!doesn’t!always!mean!a!host!is!
malicious.!Hosts!that!were!previously!infected!might!have!been!cleaned!up,!and!the!maintainers!
of!the!reputation!lists!might!not!yet!have!registered!this.!
!
!
M.;!8US!?4,+!
!
The!most!important!data!in!the!threat!feed!is!the!list!of!Domain!Generation!Algorithm!(DGA)!
generated!domain!names.!Many!ransomware!and!other!serious!malware,!use!DGAs!to!generate!
a!large!number!of!domain!names.!These!domain!names!are!used!to!try!and!connect!with!their!
command!and!control!servers!(C2).!The!large!number!of!auto!generated!domain!names!makes!it!
difficult!to!track!and!shut!down!these!C2!servers.!
!
Most!DGA!engines!use!time!as!the!deciding!factor!for!what!domain!name!to!generate.!Using!
this!method,!a!hacker!will!be!able!to!predict!what!domain!names!their!malware!will!generate,!
so!they!can!be!ready!when!the!malware!attempts!to!connect!to!it!at!any!given!time.!When!the!
hacker!decides!it!is!time!to!provide!C2!access!to!his!malware,!the!hacker!simply!registers!a!
domain!name!with!a!commercial!DNS!service,!for!a!domain!that!the!malware!DGA!will!generate!
in!the!near!future.!When!the!malware!tries!this!specific!DGA!generated!domain,!a!connection!
will!suddenly!be!made.!At!that!point!the!malware!knows!it!has!found!its!C2!server.!
!
The!Solida!threat!list!contains!a!very!large!amount!of!DGA!domain!names.!These!domain!names!
are!generated!from!actual!DGA!engines,!harvested!from!malwares!collected!from!the!Internet.!
These!DGA!engines!are!running!in!a!server,!generating!their!time!based!domain!names.!This!

14
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
way!it!is!possible!to!know!in!advance!what!domain!names!similar!malwares!will!generate!in!the!
wild!at!any!given!point!in!time.!The!threat!feed!contains!on!average!750,000!domain!names,!
covering!a!time!window!of!UTC!–!48!hours!to!UTC!+!24!hours.!This!gives!a!72-hour!sliding!
window!that!covers!all!time!zones!worldwide.!These!domain!names!are!written!to!a!blacklist!in!
the!security!appliances.!All!outgoing!DNS!queries!and!URLs!are!verified!against!this!list!and!
dropped!if!a!match!is!found.!
!
M.<!?4,+!Q61#+&,!
!
The!reputation!lists!are!constantly!being!updated!through!a!cloud!based!threat!feed!offered!by!
Solida.!The!appliance!automatically!connects!with!this!cloud!service!once!every!hour,!to!
download!new!updated!versions!of!the!lists.!This!guarantees!that!the!appliance!always!contains!
information!about!the!latest!threats!seen!in!the!wild.!!
!
To!monitor!the!list!update!process!and!the!list!sizes,!start!the!configuration!application!and!
navigate!to!“Threat!Intelligence!–!Threat!Lists”.!A!similar!page!is!available!at!the!same!location!
in!the!monitoring!application.!The!page!looks!as!follows:!
Figure 4.1 Threat lists overview.
!
!
In!the!top!field!named!“Reputation!List!Control!Center”!the!following!information!is!provided:!
!
P&E+!3%'21!261#+&!–!Shows!the!time!at!which!the!next!list!update!will!be!performed.!
!
8US!5#*,'LA#0&!D*+04&,!–!The!number!of!DGA!generated!domain!names!in!this!list.!
!

15
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
8'L#4*!5&62+#+4'*!D*+04&,!–!The!number!of!domain!names!in!this!list.!
!
/9!5&62+#+4'*!D*+04&,!–!The!number!of!IP!addresses!(both!IPv4!and!IPv6)!in!this!list.!
!
"O5!&*16'4*+,!–!The!number!of!Tor!endpoints!provided!in!this!list!is!included.!
!
The!above!threat!lists!are!not!user!modifiable.!
!
The!window!titled!“My!Domain!Name!Blacklist!Entries”!contains!a!button!called!Q6%'#1!I4%&.!
This!button!allows!for!uploading!user!created!lists!to!the!blacklist!engine.!Currently!it!is!only!
possible!to!upload!a!file!containing!a!VoIP!style!telephone!number,!which!is!being!used!for!the!
VoIP!caller-blocking!feature.!Please!refer!to!the!appendix!in!this!document!for!further!
information!about!VoIP!caller!blocking.!
!
16
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
R.!5&62+#+4'*!"B0&#+!?4,+!Q61# +&,!
!
The!Solida!appliances!obtain!their!threat!information!by!downloading!proprietary!threat!lists!
from!a!cloud-based!server.!There!are!three!categories!of!lists,!which!are!domain!reputation!
blacklist,!IP!reputation!blacklist!and!Tor!exit!node!list.!The!factory!default!is!to!allow!for!all!these!
lists!to!be!included!in!the!cloud!updates.!Changing!this!factory!default!should!only!be!done!in!
very!special!cases.!Disabling!a!list!results!in!the!possibility!of!malicious!packets!being!able!to!
penetrate!the!network!and!cause!escalating!damage.!
!
To!change!the!factory!default!setting,!start!the!configuration!utility!and!navigate!to!
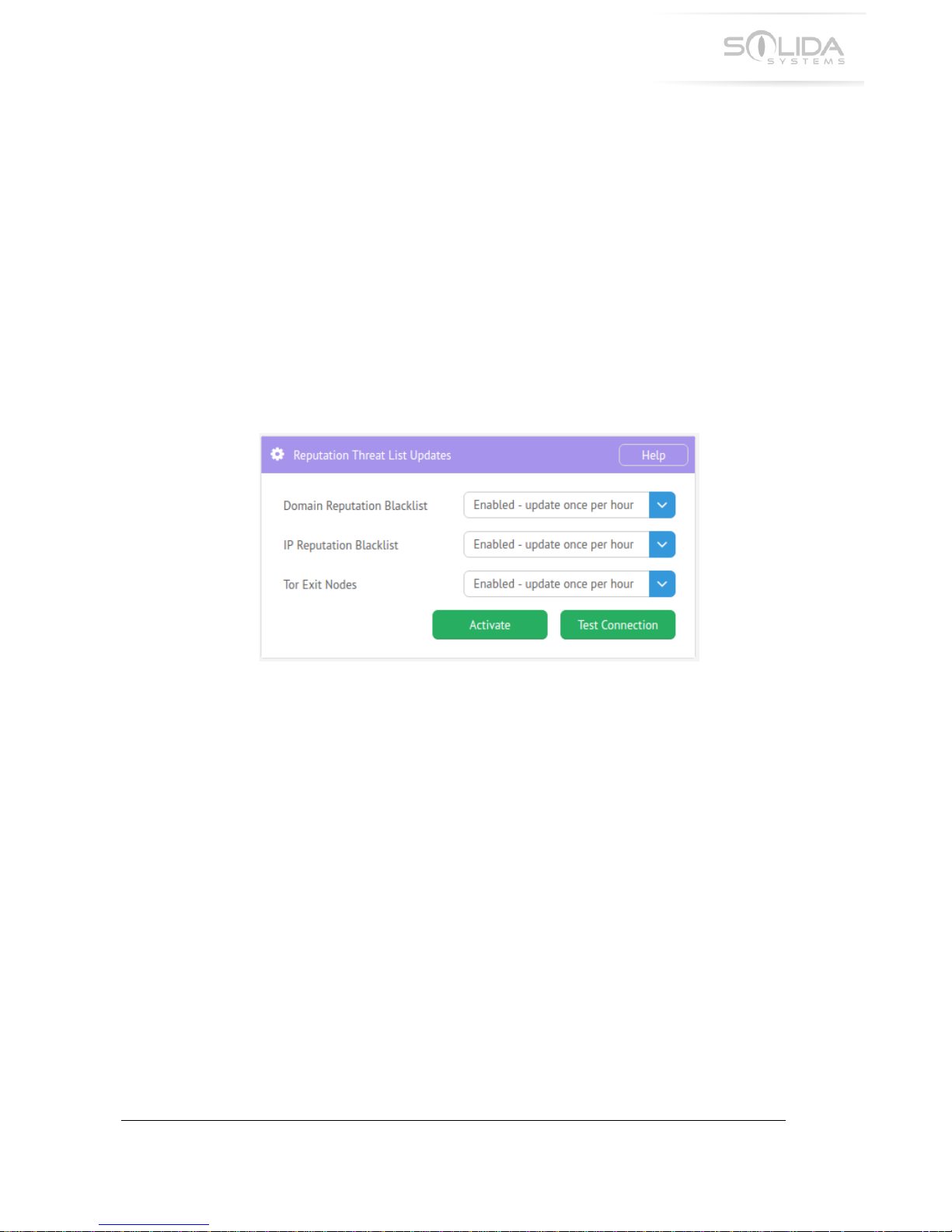
“Configuration”.!Locate!the!block!titled!“Reputation!Threat!List!Updates”.!It!will!look!as!shown!
in!the!picture!below.!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure 5.1 Reputation threat list updates window.
!
The!following!settings!are!available:!
!
! Domain!Reputation!Blacklist! !! -! Enabled!–!update!once!per!hour!(default)!
! ! ! ! ! ! -! Disabled!
!
! IP!Reputation!Blacklist! ! -! Enabled!–!update!once!per!hour!(default)!
! ! ! ! ! ! -! Disabled!
!
! Tor!Exit!Nodes!! ! ! -! Enabled!–!update!once!per!hour!(default)!
- Disabled!
!
The!“reputation!threat!list”!updates!configuration!window!includes!a!button!labeled!“Test!
Connection”.!When!pressing!this!button,!the!appliance!will!try!to!connect!with!Solida’s!cloud!
server!the!exact!same!way!it!would!do!for!an!update!of!the!threat!intelligence.!If!this!test!fails,!
the!installation!must!be!checked!to!identify!the!cause!of!the!failure.!This!test!must!complete!
successfully!for!the!appliance!to!be!able!to!download!the!threat!intelligence!data!and!function!
as!designed.!

17
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
!
R.-!S$'2+!"'0!DE4+!P'1&,!
The!Tor!exit!nodes!list!contains!IP!addresses!of!known!Tor!network!end!point!IP!addresses.!It!is!
common!for!hackers!to!use!Tor!exit!nodes!for!their!attack!traffic!to!mask!its!origin.!In!some!rare!
cases,!the!use!of!the!Tor!network!is!valid.!Examples!would!be!in!countries!that!censor!their!
citizens'!Internet!traffic.!In!those!circumstances!the!Tor!network!can!be!used!to!circumvent!such!
censorship.!Then!it!is!recommended!to!disable!the!inclusion!of!Tor!endpoints!in!the!IP!blacklist.!
!
18
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
T.!8&&6!9#3K&+!/*,6&3+4'* !) '*(4>20#+4'*!
!
Deep!packet!inspection!(DPI)!refers!to!the!process!that!inspects!all!incoming!and!outgoing!
network!packets.!The!factory!default!setting!applies!DPI!on!all!packets,!including!incoming!and!
outgoing!packets.!Only!under!very!special!circumstances!should!the!factory!default!be!changed.!
Changing!the!factory!default!will!prohibit!the!appliance!from!detecting!all!possible!malwares!
and!other!threats.!
!
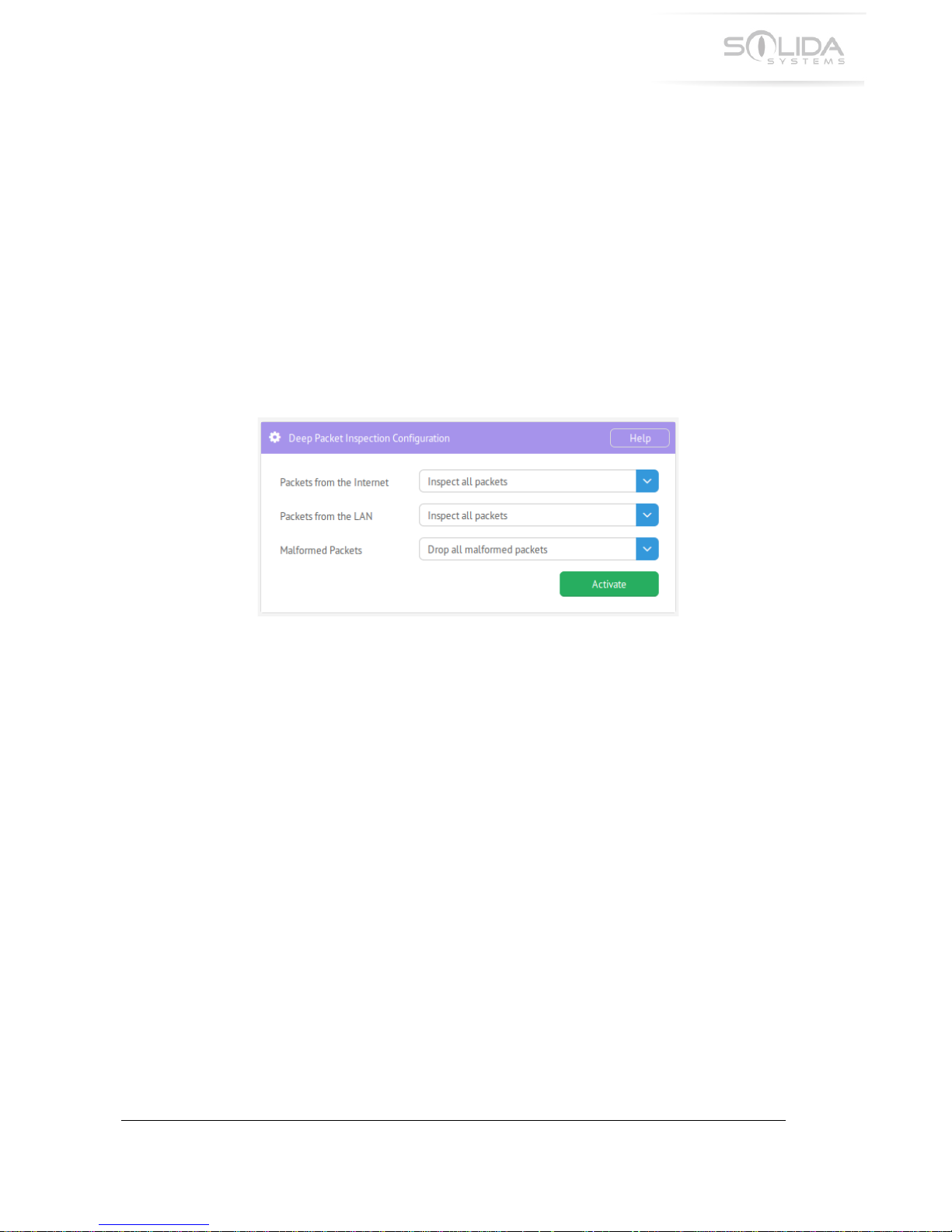
To!change!the!factory!default!setting,!start!the!configuration!utility!and!navigate!to!
“Configuration”.!Locate!the!block!titled!“Deep!Packet!Inspection!Configuration”.!It!will!look!as!
shown!in!the!picture!below.!
!
!
!
!
!
!
!
!
!
!
!
!
Figure 6.1 Deep packet inspection configuration window.
!
!
The!following!settings!are!available:!
!
! Packets!from!the!Internet! -! Inspect!all!packets!(Factory!default)!
- Disable!Inspection!
!
Packets!from!the!LAN!! -! Inspect!all!packets!(Factory!default)!
- Disable!Inspection!
!
Malformed!Packets! ! -! Drop!all!malformed!packets!(Factory!default)!
- Do!not!drop!malformed!packets!
!
Hackers!sometimes!intentionally!generate!network!packets!that!are!malformed.!The!reason!
might!be!to!try!and!confuse,!or!even!crash!the!system!stacks!in!the!computers!connected!to!the!
network.!Letting!the!appliances!drop!these!packets!guarantees!that!they!will!not!cause!any!
damage!in!the!protected!LAN.!
!

19
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
V.!Q,&0!7%#3K!#*1!JB4+&!?4,+4*>!
!
V.-!O:&0:4&A!
The!configuration!application!allows!for!a!user!to!enter!additional!blacklist!and!whitelist!IP!
addresses!and!domain!names.!These!addresses!will!be!appended!to!the!internal!threat!lists!and!
all!network!packets!will!be!checked!against!these!user-entered!addresses.!
!
PO"DW!NEVER!whitelist!an!IP!address!for!a!Domain!Name!Server!(DNS!server).!Doing!so!will!
cause!the!blacklist!engine!to!skip!checking!DNS!lookup!packets.!Checking!DNS!queries!against!
the!blacklists!is!an!essential!part!of!the!scanning!process.!Bypassing!this!will!allow!malicious!
packets!to!flow!freely!in!and!out!of!the!appliance!without!being!noticed!or!blocked.!
!
V.;!7%#3K%4,+4*>!8'L#4*!P#L&,!
!
The!user!can!enter!any!domain!name!into!the!user!managed!blacklist!entry!table.!The!picture!
below!shows!three!different!domain!names!having!been!blacklisted!by!a!user.!
!
!
Figure'7.1'User'managed'black'and'white'lists.'
!
To!blacklist!a!domain,!press!the!button!labeled!“+!Add!Domain!Name”.!Enter!the!domain!name!
and!select!the!action!and!severity!level.!!
!
!

20
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
Testing!that!the!new!entry!is!blacklisted!can!be!done!by!entering!the!domain!in!a!web!browser!
and!confirming!that!an!event!is!generated!for!the!domain.!
!
V.<!7%#3K%4,+4*>!/9!S110&,,&,!
IP!addresses!can!be!entered!into!an!IP!address!blacklist!in!a!similar!way!a!domain!name!is!
blacklisted.!To!add!an!IP!address!to!the!user!blacklist,!press!the!button!labeled!“+!Add!IP!
Address”.!Enter!the!IP!address,!IPv4!or!IPv6.!Select!the!desired!action!and!severity!level!and!
press!the!“Save”!button.!The!new!IP!address!will!be!added!to!the!user!blacklist.!
!
V.M!JB4+&%4,+4*>!/9!S110&,,&,!
!
It!is!possible!to!add!an!IP!address!to!a!whitelist.!If!this!is!done,!the!security!engine!will!ignore!all!
packets!containing!this!IP!address.!!
!
PO"DW!NEVER!whitelist!an!IP!address!for!a!Domain!Name!Server!(DNS!server).!Doing!so!will!
cause!the!blacklist!engine!to!skip!checking!DNS!lookup!packets.!Checking!DNS!queries!against!
the!blacklists!is!an!essential!part!of!the!scanning!process.!Bypassing!this!will!allow!malicious!
packets!to!flow!freely!in!and!out!of!the!appliance!without!being!noticed!or!blocked.!
!
Whitelisting!of!IP!addresses!should!only!be!done!in!very!specific!situations.!Solida!Systems!
strongly!suggests!never!whitelisting!any!IP!addresses.!The!unwanted!side!effect!might!be!that!
the!LAN!side!is!left!unprotected!or!only!performs!a!limited!amount!of!protection.!
!
V.R!Q6%'#14*>!#!7%#3K%4,+!I4%&!
The!window!titled!“My!Domain!Name!Blacklist!Entries”!contains!a!button!called!Q6%'#1!I4%&.!
This!button!allows!for!uploading!user!created!lists!to!the!blacklist!engine.!Currently!it!is!only!
possible!to!upload!a!file!containing!a!VoIP!style!telephone!number,!which!is!being!used!for!the!
VoIP!caller-blocking!feature.!Please!refer!to!the!appendix!in!this!document!for!further!
information!about!VoIP!caller!blocking.!
!
!
21
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
X.!/*+02,4'*!8&+&3+4'*!#*1!90 &: & *+4' *!5 2 %&,!
!
X.-!52%&!O:&0:4&A!
!
To!protect!against!intrusion!attacks,!Solida!appliances!rely!on!a!rule!engine!that!can!perform!
deep!packet!inspection!(DPI)!of!Ethernet!packets!flowing!through!the!appliance.!The!DPI!engine!
can!inspect!all!packets!and!look!for!signatures!and!any!combination!of!data!patterns,!such!as!
port!scans,!OS!finger!printing!and!vulnerability!scans.!
!
The!DPI!engine!is!controlled!by!detection!rules.!These!rules!instruct!the!DPI!engine!what!to!look!
for!in!the!packets!and!what!action!to!take!if!a!pattern!match!is!detected.!!
!
Solida!provides!a!set!of!system!rules!that!includes!protection!from!many!types!of!penetration!
attempts.!An!expert!user!can!also!create!custom!rules.!Writing!custom!rules!requires!detailed!
knowledge!of!rule!writing,!and!the!different!types!of!packets!flowing!over!a!network.!Such!
custom!rules!can!be!created!using!the!rule!editor!in!the!Solida!configuration!application.!In!most!
cases!it!is!recommended!to!use!the!system!rules!provided!by!Solida!through!the!threat!feed.!
!
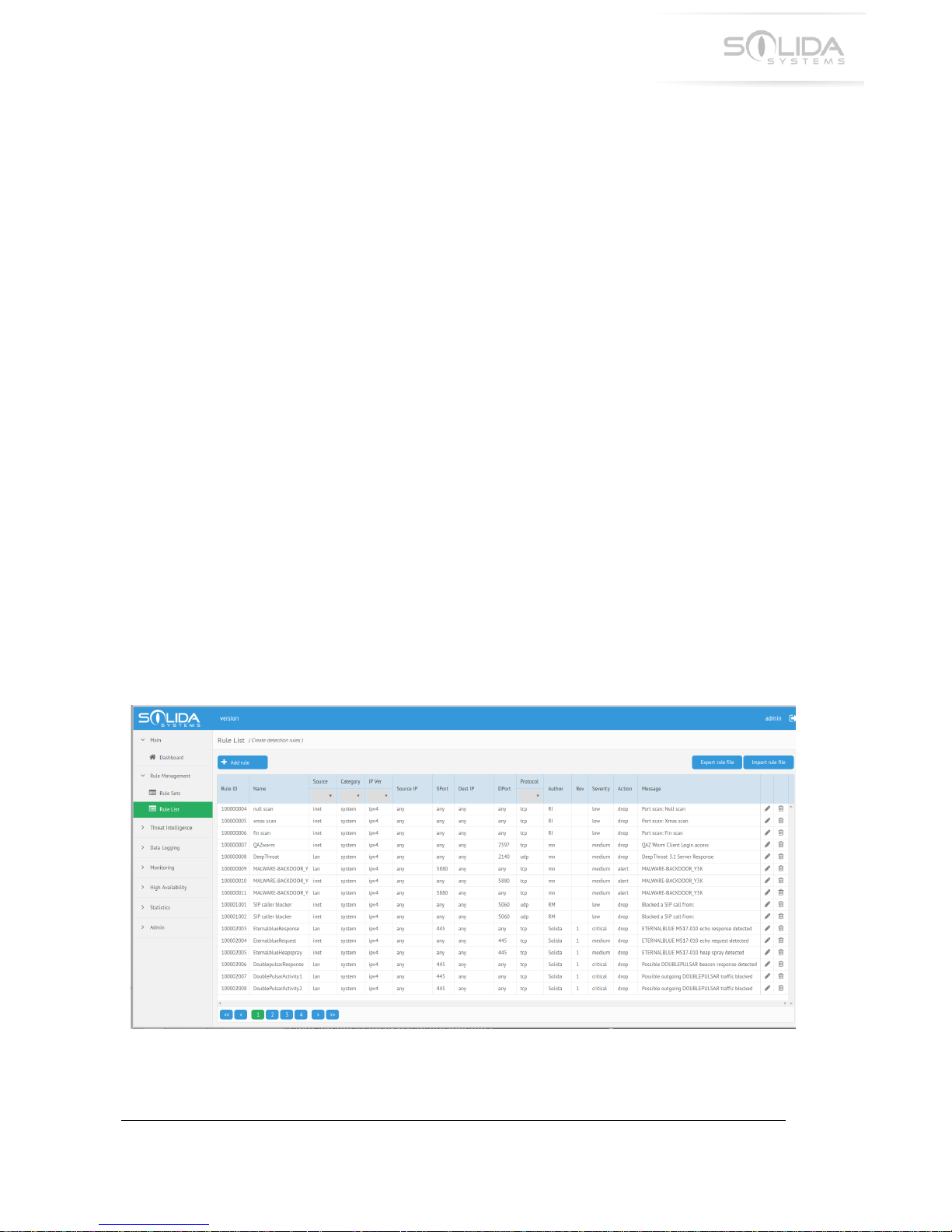
X.;!52%&!?4,+!
!
Detection!rules!can!be!created!and!edited!trough!the!configuration!application.!Start!the!
application!and!navigate!to!“Rule!List”.!This!will!show!a!list!over!all!available!rules!in!the!
appliance.!
Figure 8.1 Rule list in the configuration utility.
!

22
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
The!column!named!“Category”!shows!what!rules!are!Solida!system!rules!and!which!rules!have!
been!created!by!the!user.!!
!
X.<!DE6'0+!52%&!I4%&!
!
(This!feature!is!for!advanced!users!only)!
The!button!labeled!“Export!rule!file”!allows!for!exporting!a!text!file!containing!all!the!rules!in!the!
appliance.!This!text!file!is!written!in!JSON!format!and!can!be!opened!and!reviewed!in!a!text!
editor.!!
!
X.M!/L6'0+!52%&!I4%&!
!
(This!feature!is!for!advanced!users!only)!
The!button!labeled!“Import!rule!file”!allows!for!importing!a!JSON!formatted!text!file!containing!
one!or!more!rules.!Note!that!it!is!not!possible!to!import!system!rules.!System!rules!are!those!
rules!with!the!category!field!showing!“system”!and!the!rule!id!in!the!1xxyyyzzz!range.!If!system!
rules!are!part!of!the!imported!rules!they!will!be!overwritten!by!the!current!system!rules!
received!by!the!regular!threat!intelligence!downloads!from!the!cloud!host.
!
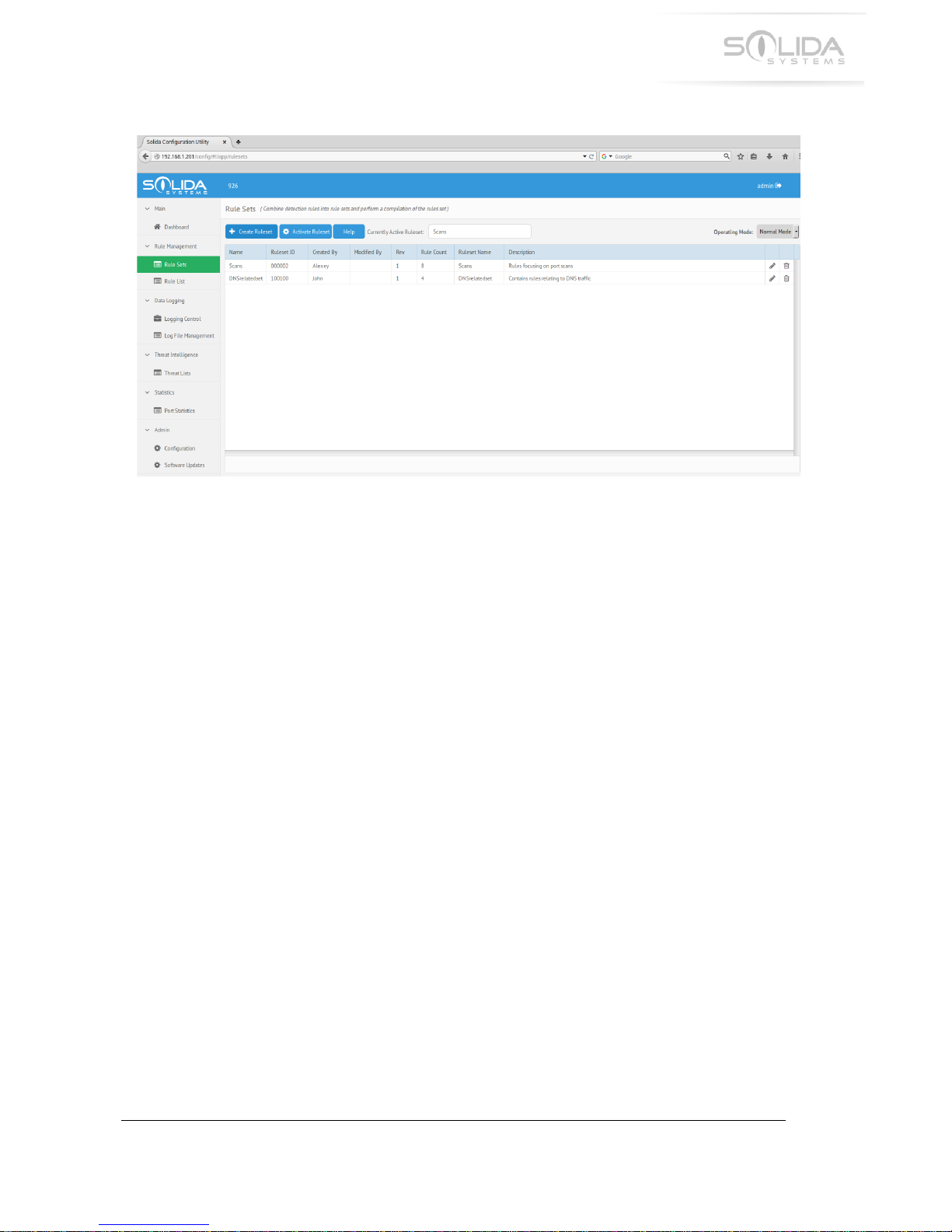
X.R!52%&!H&+,!
!
A!rule!set!is!a!collection!of!rules.!Multiple!rule!sets!can!be!created,!each!containing!a!different!
set!of!rules.!The!appliance!can!be!activated!with!one!single!rule!set.!Once!a!rule!set!has!been!
activated,!the!appliance!will!start!its!packet!scanning!using!all!the!rules!included!in!the!rule!set.!
!
To!display!and!create!rule!sets,!start!the!configuration!utility!and!navigate!to!“Rule!Sets”.!This!
will!show!a!list!of!all!available!rule!sets.!
23
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
!
Figure 8.2 Rule set list in the GUI configuration utility.
!
X.T!S3+4:#+4*>!#!52%&!H&+!
!
To!activate!a!rule!set,!select!the!rule!set!by!clicking!on!its!row!in!the!GUI.!Then!click!the!
“Activate!Rule!Set”!button.!This!will!perform!an!implicit!sanity!check!of!all!the!included!rules,!
and!then!upload!these!rules!to!the!appliance.!
!
Once!this!activation!completes,!the!appliance!will!start!using!the!new!rules!immediately.!
!
!
X.V!O6&0#+4*>!='1&!
!
When!trialing!a!new!rule!set,!it!is!possible!to!set!the!appliance!to!“monitor!mode”.!The!rule!set!
page!contains!a!drop!down!menu!where!the!desired!operating!mode!can!be!selected.!In!
monitor!mode!all!network!packets!are!scanned!using!the!rules!as!well!as!the!reputation!
detection!lists,!but!no!packets!will!be!dropped.!Alerts!will!still!be!generated!the!same!way!as!in!
normal!operation!mode.!This!allows!the!user!to!check!a!new!rule!set!to!make!sure!it!behaves!as!
expected.!Once!the!user!is!satisfied!with!the!new!rule!set,!set!the!operating!mode!back!to!
“Normal!Mode”.!
!
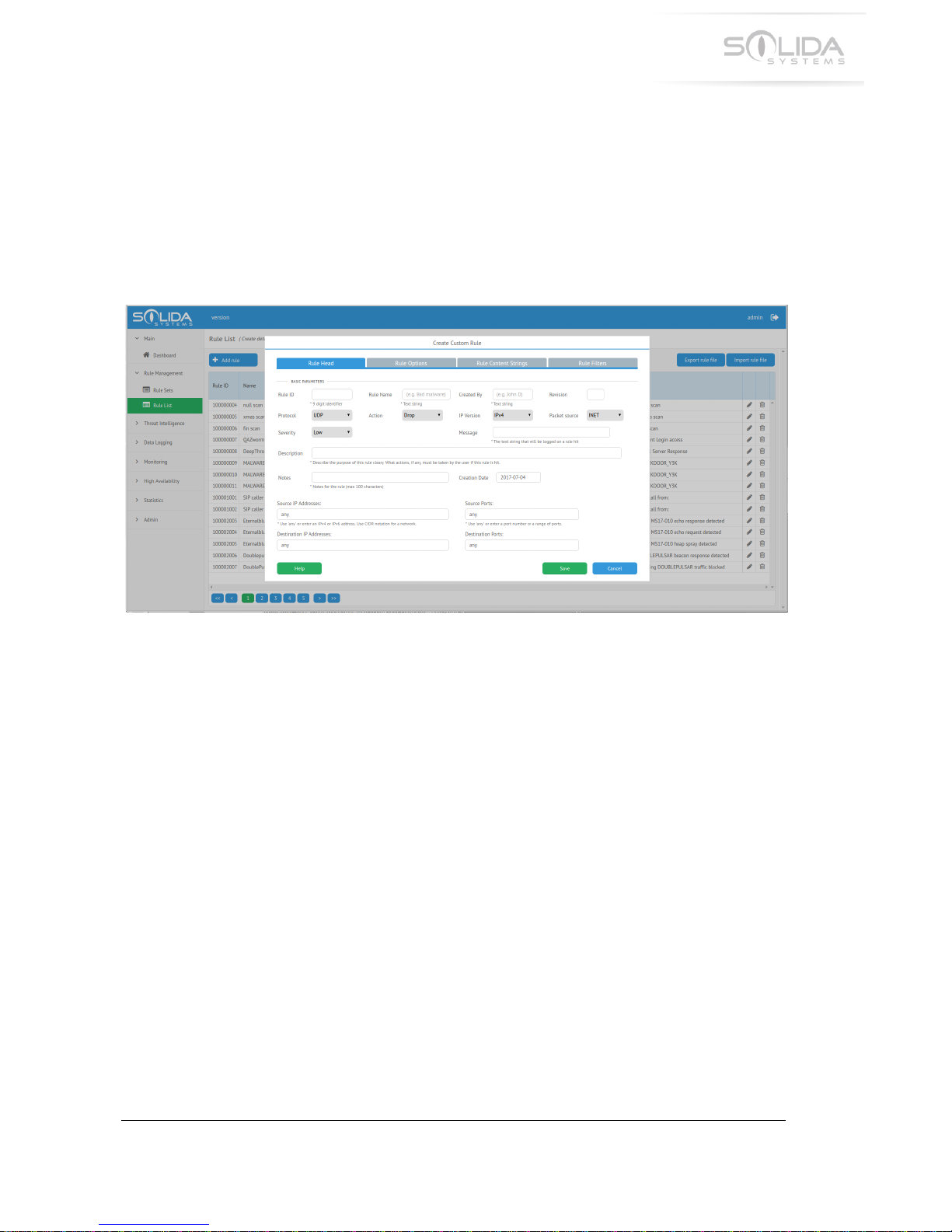
X.X!)0&#+4*>!)2,+'L!52%&,!
!
It!is!beyond!this!manual!to!explain!in!detail!how!to!write!custom!rules.!Please!refer!to!the!many!
24
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
tutorials!and!documentation!available!on!the!Internet!on!how!to!write!detection!rules.!
!
A!rule!is!created!using!the!configuration!application.!Start!the!application!and!navigate!to!the!
“Rule!List”!page.!This!page!will!display!a!list!of!all!rules!currently!available!in!the!appliance.!
!
At!the!top!left!side!of!this!page!a!blue!button!labeled!“+!Add!rule”!is!located.!To!create!a!new!
custom!rule,!simply!click!this!button.!A!new!window!will!pop!up!called!“Create!Custom!Rule”.!
!
Figure 8.3 Create a custom rule pop-up window.
!
This!window!contains!five!tabs.!Each!tab!contains!different!optional!rule!parameters.!These!
parameters!can!be!filled!in!to!define!the!new!rules!behavior.!For!a!detailed!description!of!each!
rule!option,!please!press!the!help!button!located!in!the!lower!left!corner!of!the!pop-up!window.!
!
!
X.Y!52%&!/1!
!
The!most!important!parameter!of!each!rule!is!the!“Rule!Id”.!Each!rule!must!have!a!unique!rule!
id!that!identifies!the!rule.!The!rule!id!consists!of!9!numbers.!It!is!common!practice!to!group!rules!
into!categories.!As!an!example,!the!first!three!numbers!identify!the!general!type!of!rule.!For!
example!UDP!rules,!TCP!rules,!ICMP!rules.!The!next!three!digits!identify!the!type!of!threat!the!
rule!concerns.!The!last!three!digits!could!be!a!general!identifier!that!is!incremented!by!one!for!
each!rule!in!the!category.!!A!rule!id!starting!with!a!1,!for!example!100001002,!is!reserved!for!
system!rules.!All!system!rules!have!a!rule!id!starting!with!a!1.!It!is!not!possible!to!make!
modifications!to!the!system!rules.!They!can!however!be!copied!and!turned!into!a!new!custom!
rule.!
!

25
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
!
Y.!D:&*+,!#*1!D:&*+!H&:&04+C!
!
Y.-!D:&*+!O:&0:4&A!
!
Each!time!a!network!packet!registers!a!hit!with!a!blacklist!entry!or!a!detection!rule,!an!“event”!is!
generated.!An!event!contains!information!that!describes!what!caused!the!event!to!be!
generated.!The!IP!address!of!the!offending!packet!is!included,!as!well!as!a!short!description!of!
the!meaning!of!the!event!and!a!timestamp.!
!
Events!are!stored!in!a!database!in!the!appliance!to!allow!for!tracking!and!statistics!gathering.!
Events!are!also!written!to!log!files!that!can!easily!be!downloaded!from!the!appliance!through!
the!GUI.!These!event!files!can!then!be!correlated!with!other!downloadable!packet!log!files,!so!
that!a!security!analyst!can!investigate!the!root!cause!of!the!event.!
!
Events!can!be!monitored!using!the!built-in!monitoring!application.!
!
Figure 9.1 Event summary view in the GUI monitoring application.
!
Located!in!the!right!side!of!the!Packet!Events!bar!is!a!drop!down!list.!This!list!shows!available!
event!files!in!the!appliance.!Events!are!written!into!files!that!are!rotated!to!avoid!them!growing!
too!large.!Event!files!are!rotated!on!a!daily!basis!(at!midnight)!or!once!an!event!file!reaches!10!
Mbytes!in!size.!A!rotated!event!file!will!have!a!time!stamp!appended!to!its!file!name.!
!
!An!example!would!look!as!follows:!

26
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure'9.2'List'of'event'files.'
!
!
In!this!example,!the!file!named!rune14.log!is!the!current!active!event!log!file.!The!remaining!
files!are!files!that!have!been!rotated.!The!appended!time!stamp!indicates!the!time!at!which!the!
event!file!was!rotated.!
!
Y.;!D:&*+!H&:&04+C!
!
Events!are!grouped!into!three!categories!depending!on!their!severity,!which!are!low,!medium!
and!critical.!Clicking!on!an!event!in!the!table!will!pop!up!a!new!window!containing!a!further!
explanation!of!the!cause!of!the!event.!
!
Y.;.-!?'A!,&:&04+C!F3'%'0&1!>0&&*!4*!+B&!UQ/G!
!
These!events!are!typically!generated!by!trying!to!visit!known!phishing!sites,!or!sites!containing!
various!types!of!malware.!The!appliance!will!automatically!drop!these!network!packets.!This!will!
prevent!malware!from!infecting!the!protected!network.!
!
These!events!require!no!further!action!from!the!user.!
!
Y.;.;!=&142L!,&:&04+C!F3'%'0&1!'0#*>&!4*!+B&!UQ/G!
!
Events!with!a!medium!severity!rating!include!known!C2!domains,!domains!with!severe!drive-by!
malware,!Trojans!and!more.!Network!packets!destined!to!these!domains!will!be!automatically!
dropped,!in!an!effort!to!maintain!network!integrity.!!
!
These!events!require!no!further!action!from!the!user.!!
!

27
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
Y.;.<!)04+43#%!,&:&04+C!F3'%'0&1!0&1!4*!+B&!UQ/G!
!
Critical!events!will!be!generated!if!the!appliance!detects!malicious!activities!occurring!inside!the!
network.!This!would!indicate!the!network!has!been!compromised.!Where!malware!is!already!
present,!it!requires!user!intervention!to!remove!it.!Examples!of!such!events!are!DNS!queries!
generated!by!a!ransomware!DGA!engine,!or!malwares!trying!to!connect!with!a!C2!server.!!
!
All!network!packets!resulting!in!critical!events!will!be!automatically!dropped!to!mitigate!further!
infection!to!the!network.!The!event!includes!the!source!and!destination!IP!addresses!of!the!
offending!packets,!which!allows!for!prompt!identification!of!the!infected!computer!on!the!
network.!The!user!will!be!required!to!remove!the!malware!from!the!infected!computer!using!a!
suitable!removal!tool.!
!
All!events!can!be!viewed!using!the!monitor!application!included!with!the!appliances.!Optionally,!
emails!containing!the!event!count!and!severity!can!be!automatically!generated!and!sent!out.!A!
mobile!phone!application!is!also!available!that!allows!the!user!to!monitor!events!in!real!time.!!
!
!
!
Y.<!H'203&!#*1!8&,+4*#+4'*!/9!S110&,,&,!
!
Each!rule!event!includes!the!source!and!destination!IP!addresses!of!the!packet!that!generated!
the!rule!hit.!Logging!these!IP!addresses!allows!for!a!more!detailed!examination!of!the!source!of!
the!threat.!The!Internet!offers!many!“WhoIs”!services!where!an!IP!address!can!be!entered!for!
analysis.!This!information!also!includes!geographical!information!regarding!an!IP!address.!!
!
!
!
!

28
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
-Z.!5&,6'*14*>!"'!)04+43#%!D:&*+,!
!
A!majority!of!all!events!will!require!no!further!action!by!the!user.!These!events!are!marked!with!
a!low!or!medium!severity.!
!
Critical!events!require!immediate!user!intervention.!Examples!of!such!events!are!DGA!events.!
They!will!be!generated!if!ransomware!infects!a!computer!in!the!network.!In!this!case!it!is!
extremely!important!to!remove!the!infected!computer!from!the!rest!of!the!network.!Some!
advanced!ransomware!are!capable!of!propagating!through!the!network!and!infecting!additional!
computers.!
!
The!critical!events!will!be!listed!with!the!source!and!destination!IP!addresses!visible.!Use!the!
destination!IP!address!from!the!event!and!match!it!with!a!computer!in!the!LAN!that!uses!this!IP!
address.!This!is!the!computer!that!has!become!infected.!Disconnect!this!computer!from!the!rest!
of!the!network.!
!
Once!the!infected!computer!has!been!removed!from!the!network,!use!Google!to!search!for!any!
available!removal!tools.!!
!
!
!

29
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
--.!5&L'+&!='*4+'04*>!
!
All!Solida!appliances!support!remote!monitoring.!There!are!three!categories!of!remote!
monitoring!supported.!The!picture!below!shows!the!setup!options!in!the!Remote!Monitoring!
window.!
!
!
Figure'11.1'Remote'Monitoring'Window.'
!
--.-!=2%+4!S66%4#*3&!5&L'+&!='*4+'04*>!
!
Solida!Systems!offers!a!software!tool!called!Solida!Multi.!This!tool!can!be!installed!in!the!cloud!
or!on!a!physical!server!in!the!user's!office.!Solida!Multi!allows!for!the!security!appliances!to!
connect!with!it!and!share!security!events!and!log!files.!!
!
For!an!appliance!to!connect!with!a!Solida!Multi!server,!enter!the!domain!name!(or!IP!address)!of!
the!server!followed!by!a!login!name!and!password.!Once!the!monitoring!is!activated,!the!
appliance!will!automatically!connect!with!the!Solida!Multi!server!and!start!sharing!its!security!
events!and!log!files.!!
!
The!button!labeled!“Test!Connection”!will!make!a!connection!attempt!with!the!Solida!Multi!
server.!Use!this!test!to!confirm!the!appliance!is!able!to!connect!with!Solida!Multi.!If!this!test!
fails,!check!any!firewall!setting!and!make!sure!it!is!possible!to!connect!with!Solida!Multi!over!
port!22!or!443.!

30
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
--.;!='$4%&!9B'*&!S66%43#+4'*!5&L'+&!='*4+'04*>!
The!appliances!can!be!remotely!monitored!by!a!mobile!phone!application!called!Solida!Notify.!
Two!versions!are!available:!one!for!iPhones!and!another!for!Android!phones.!The!Solida!Notify!
application!is!supported!on!the!following!phone!models:!
!
1. Apple!–!iPhone!5,!iPhone!5S!or!later.!
!
2. Android!–!Most!Android!based!mobile!phones.!
!
Solida!Notify!is!not!supported!on!Apple’s!iPad.!
!
The!Solida!Notify!application!connects!to!the!cloud!server!where!it!downloads!security!event!
data.!This!data!is!continuously!uploaded!to!the!cloud!server!by!the!appliance!once!this!feature!is!
enabled.!!
!
!
--.<!P&+(%'A!?'>>4*>!
!
Some!of!Solida’s!appliances!have!support!for!Netflow!9.!Netflow!is!a!standard!that!describes!
how!to!track!packet!flow!data!and!how!to!send!this!data!out!to!a!logging!server.!The!logging!
server!would!run!software,!typically!some!type!of!SIEM!tool!that!collects!Netflow!data!from!the!
appliances!and!presents!it!in!a!graphical!way.!
!
The!Netflow!collector!server!expects!UDP!packets!to!be!passed!to!it.!To!enable!the!Solida!
appliance!to!perform!Netflow!logging,!enter!the!connection!information!for!the!collector!server!
and!activate!the!feature.!
!
)'%%&3+'0!/9!#110&,,!–!This!is!the!IP!address!of!the!computer!that!runs!the!collector!software.!
!
)'%%&3+'0!6'0+!–!This!is!the!port!number!to!use!when!sending!out!the!Netflow!UDP!packets!to!
the!collector!computer.!The!default!port!number!to!use!for!Netflow!packets!is!2055.!!
!
I%'A!I'0L#+!–!This!selects!the!version!of!the!Netflow!data.!Currently!only!Netflow!version!9!is!
supported.!
!
H&*,'0!/8!–!Multiple!appliances!can!send!Netflow!data!to!a!single!collector.!Each!one!of!these!
appliances!must!be!set!up!with!a!unique!ID!number!to!allow!the!collector!to!differentiate!
between!the!appliances.!
!
--.<!5&L'+&!?'>>4*>!"'!HC,%'>!H&0:&0!
!
This!feature,!when!activated,!will!send!the!appliance!syslog!file!to!a!syslog!server!on!the!

31
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
selected!IP!address.!Any!new!entries!in!the!syslog!file!will!immediately!show!up!in!the!syslog!
server!to!make!sure!the!two!sides!are!in!sync.!For!more!information!about!this!feature,!please!
contact!Solida!Systems!for!further!information.!
32
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
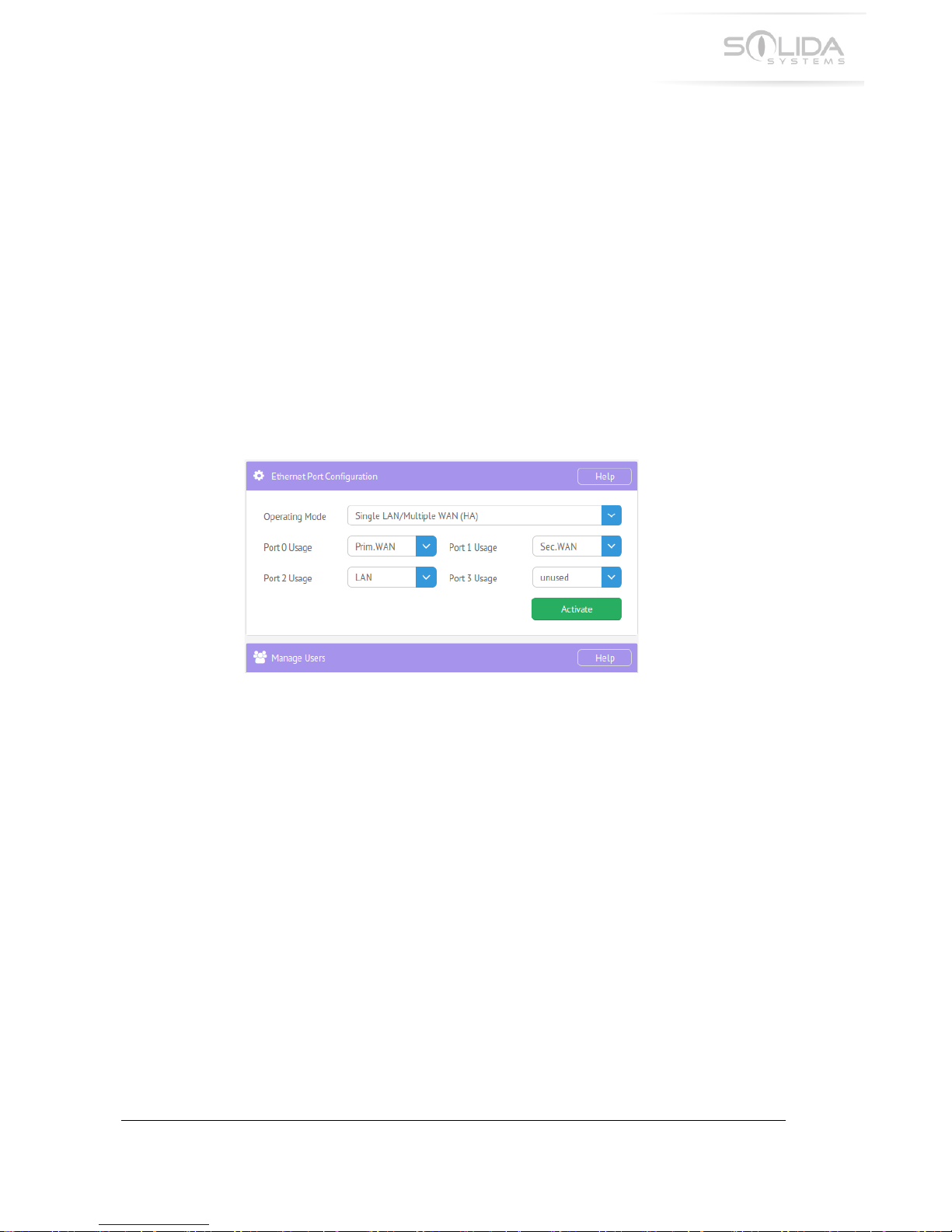
-;.!H4*>%&!S66%4#*3&!@4>B!S:#4%#$4%4+C!
!
Single!Appliance!High!Availability!is!an!option!that!allows!for!pairing!two!Internet!connections!
together!as!a!fault!tolerant!pair.!!One!Internet!connection!is!considered!the!primary!or!master!
connection.!The!other!Internet!connection!is!a!standby,!or!slave!connection.!
!
-;.-!)'*(4>20#+4'*!
!
To!configure!the!appliance!to!operate!in!this!high!availability!mode,!navigate!to!the!
Configuration!window.!This!window!includes!a!configuration!area!named!Ethernet!Port!
Configuration.!!This!area!looks!as!follows:!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure'12.1'High'Availability'Port'Configuration.'
!
!
The!top!pull-down!menu!labeled!Operating!Mode!contains!three!options.!To!enable!this!HA!
mode!select!the!option!labeled!H4*>%&!?SP[=2%+46%&!JSP!F@SG.!!
!
The!second!step!is!to!select!the!WAN!ports!that!will!connect!to!the!two!Internet!routers.!A!WAN!
port!is!assigned!to!be!either!the!primary!or!the!secondary!WAN!port.!The!primary!WAN!port!will!
become!the!master!WAN!port!and!will!handle!all!Internet!traffic!as!long!as!its!Internet!
connection!is!up!and!fully!functional.!!
!
Select!one!port!to!be!904L.JSP!and!another!port!to!be!H&3.JSP.!
!
Select!one!port!to!be!the!single!?SP!port.!
!
At!this!point!the!configuration!window!should!look!similar!to!the!picture!above.!Press!the!
Activate!button.!The!appliance!will!now!start!operating!in!this!mode.!

33
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
-<.!=2%+4!S66%4#*3&!@4>B!S:#4%#$4%4+C!
!
Multi!appliance!high!availability!is!an!option!where!two!security!appliances!are!configured!as!a!
fault!tolerant!pair.!One!appliance!is!configured!to!be!the!master!appliance!and!the!second!to!be!
the!slave!appliance.!!
!
-<.-.!=#,+&0!H%#:&!)'*(4>20#+4'*!
!
To!configure!multi!appliance!high!availability,!navigate!to!the!window!named!High!Availability.!
This!window!will!present!the!following!configuration!view:!
!
!
Figure'13.1'High'availability'configuration'window.'
!
!
@S!='1&! ! -!Primary!Unit.!Handles!network!traffic!in!a!normal!fault!free!situation.!
! ! ! -!Backup!Unit.!Standby!unit!activated!only!if!the!primary!unit!fails.!
!
9#40!/9!S110&,,! -!The!IP!address!of!the!other!unit’s!management!port.!Both!appliances!
must!be!able!to!communicate!with!the!other!appliance!management!port!
to!determine!the!status!of!the!unit.!
!
@S!9'%%!I0&N! !-!How!often!a!unit!checks!the!other!unit’s!functional!status.!Three!seconds!
is!the!default!value!and!should!be!appropriate!for!most!installs.!
!
S3+4:#+4'*!8&%#C! -!Determines!the!wait!period!after!a!power-on!until!HA!is!activated.!This!is!
needed!to!avoid!incorrect!failovers!after!a!system!start.!
!
I#4%':&0!"B0&,B'%1! -!Number!of!required!consecutive!missed!heartbeats!the!master!must!
experience!before!a!failover!to!the!passive!device!occurs.!
!
I#4%$#3K!"B0&,B'%1! -!Number!of!required!good!heartbeats!the!secondary!appliance!must!
receive!before!it!fails!back!to!normal!operation!mode.!
!
34
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
-M.!DL#4%!P'+4(43#+4'*!
!
The!appliances!have!support!for!sending!regular!emails!containing!information!about!the!
number!of!events!in!the!system!and!their!severity.!This!is!a!useful!feature!since!it!will!not!be!
required!to!constantly!monitor!the!appliance!through!the!monitoring!application.!
!
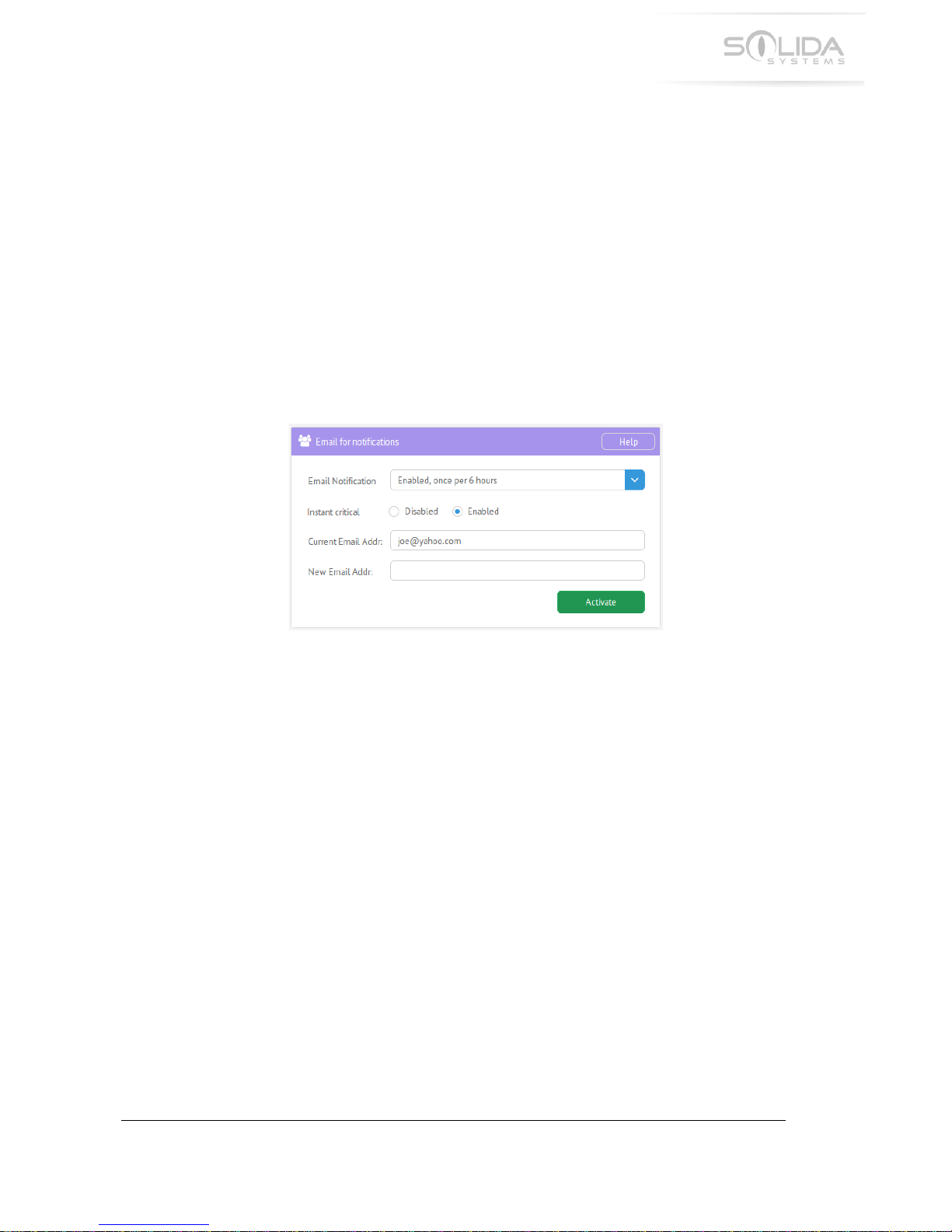
-M.-!H&++4*>!Q6!DL#4%!P'+4(43#+4'*!
!
To!set!up!email!notification,!login!to!the!configuration!application!and!navigate!to!Admin!–!
Configuration.!Locate!the!box!called!“Email!Notifications”.!The!box!will!look!as!follows:!
!
!
!
!
!
!
!
!
!
!
!
!
Figure 14.1 Email notification setup box.
!
-M.-.-!DL#4%!P'+4(43#+4'*!
This!dropdown!box!contains!four!options:!
!
84,#$%&1!!! ! ! -!Email!notification!disabled.!
D*#$%&1\!'*3&!6&0!1#C! -!Generates!one!email!per!day!with!event!information.!
D*#$%&1\!'*3&!6&0!T!B'20,!! -!Generates!four!emails!per!day!with!event!information.!
D*#$%&1\!'*3&!6&0!B'20! -!Generates!one!email!per!hour!with!event!information.!
!
-M.-.;!/*,+#*+!)04+43#%!
!
This!option,!if!enabled,!will!send!out!one!email!each!time!a!critical!event!is!generated.!These!
critical!events!require!user!intervention.!Therefore!it!is!important!that!such!events!are!
forwarded!to!the!user!with!minimum!delay.!
!
-M.-.<!)200&*+!DL#4%!S110&,,!
!
35
©!SOLIDA!SYSTEMS!INTERNATIONAL!2017!
This!text!box!shows!the!current!email!address!in!use,!assuming!this!feature!is!enabled.!This!
address!will!be!the!recipient!for!the!event!status!emails.!
!
-M.-.M!P&A!DL#4%!S110&,,!
!
Enter!a!valid!email!address!into!this!box.!This!is!the!new!address!that!will!be!used!to!receive!
these!emails.!
!
Once!the!above!fields!have!been!filled!in,!press!the!“Activate”!button.!This!will!activate!the!new!
configuration.!
!
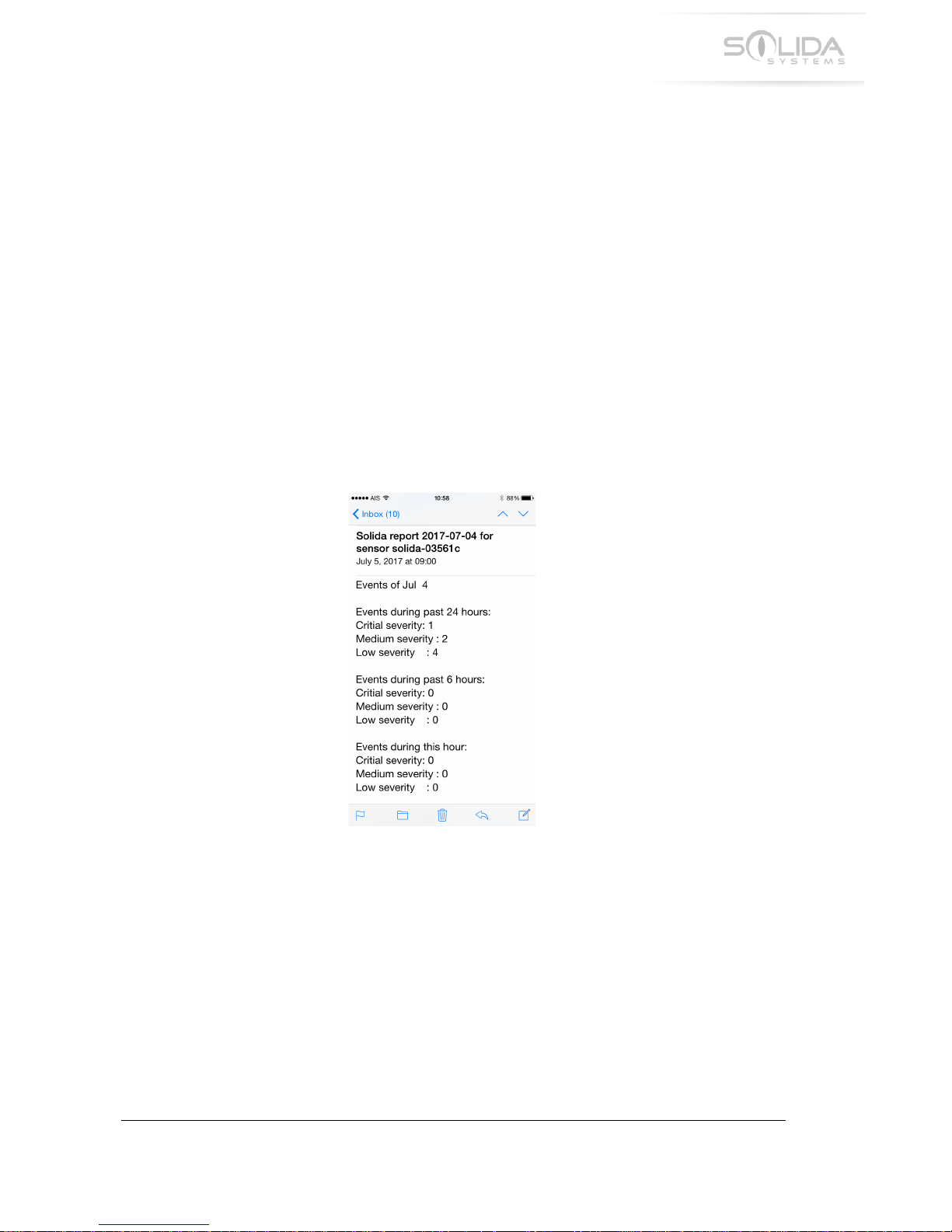
-M.;!D:&*+!P'+4(43#+4'*!DL#4%,!
!
The!event!notification!emails!are!short!but!contain!vital!information!a!user!will!need.!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure 14.2 Example of an event notification email.
!
The!most!recent!events!for!the!past!hour!and!the!past!6!hours!are!shown!separately!to!give!a!
clearer!overview!of!the!current!status.!Critical!events!require!immediate!user!intervention!and!are!
therefore!marked!clearly!as!critical!for!easy!identification.!
!
36
© SOLIDA SYSTEMS INTERNATIONAL 2017
-R.!8#+#!?'>>4*>!
!
The!appliances!have!a!wide!selection!of!logging!options.!The!factory!default!is!to!log!all!rule!events!
as!well!as!all!dropped!network!packets!but!the!user!has!the!option!to!enable!further!logging,!
including!full!packet!capture.!
!
Network!packet!data!is!written!to!the!log!files!in!the!industry!standard!PCAP!format.!This!makes!it!
possible!to!use!tools!such!as!Wireshark!to!open!these!files,!and!perform!analysis!on!the!packet!
content.!
!
All!log!files!can!be!downloaded!by!clicking!on!them!in!the!Log!File!management!window.!
!
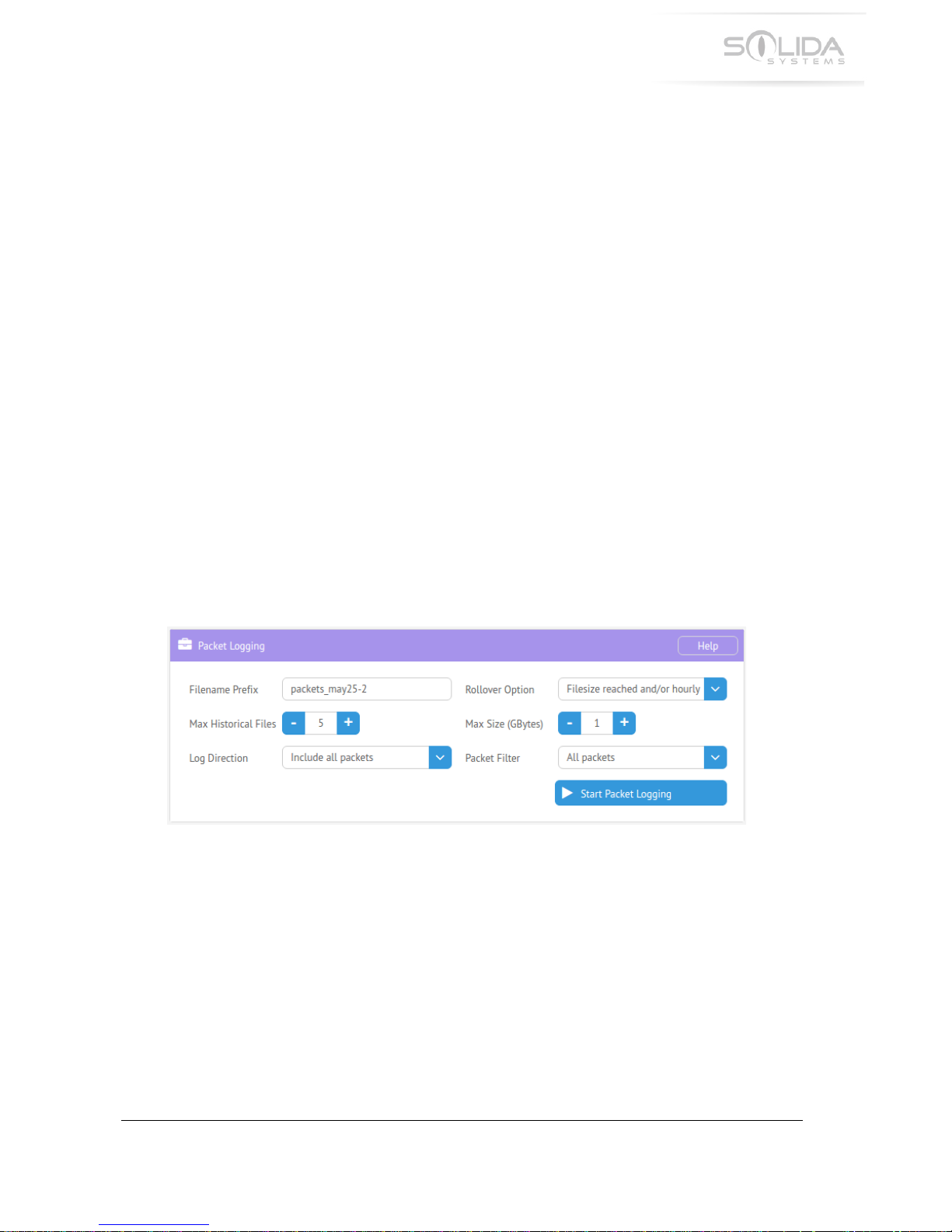
-R.-!9#3K&+!?'>>4*>!
!
Packet!logging!will!log!every!single!packet!passing!through!the!appliance.!This!mode!is!typically!
only!used!during!troubleshooting!of!the!network.!The!resulting!log!files!can!become!very!large!so!
it!is!important!to!select!an!appropriate!rollover!option!to!avoid!filling!up!the!disk!space!in!the!
appliance.!Packet!logging!should!be!disabled!during!normal!usage.!The!configuration!window!for!
packet!logging!looks!as!follows:!
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure'15.1'Packet'Logging'Configuration'Window'
!
-R.;!80'66&1!9#3K&+!?'>>4*>!
!
This!option!will!log!all!network!packets!that!are!dropped!by!the!appliance.!Packets!will!be!dropped!
by!the!rule!engine!as!well!as!by!the!reputation!detection!engine.!This!logging!option!is!enabled!by!
default.!These!log!files!can!be!used!during!forensic!analysis!to!determine!the!exact!reason!a!packet!
was!dropped.!
! !
!

37
© SOLIDA SYSTEMS INTERNATIONAL 2017
!
!
!
!
!
!
!
!
!
!
!
!
!
Figure'15.2'Dropped'Packets'Logging'
!
-R.<!D:&*+!?'>>4*>!
!
Event!logging!is!enabled!by!default!and!it!is!strongly!recommended!to!always!keep!it!enabled.!The!
resulting!log!files!contain!information!about!all!events!occurring!in!the!appliance.!The!default!
settings!are!as!shown!in!the!picture!below:!
!
!
!
'
Figure'15.3'Event'logging'configuration'window.'
-R.M!/9!S110&,,!?'>>4*>!
!
This!option!is!currently!not!supported.!
!
-R.R!@""9!?'>>4*>!
!
This!option!allows!for!logging!all!domain!names!that!are!being!accessed!through!browsers!in!the!
network.!Each!domain!entry!is!tagged!with!a!time!stamp!and!the!IP!address!that!requested!the!
domain!name.!
!

38
© SOLIDA SYSTEMS INTERNATIONAL 2017
-R.T!8'A*%'#14*>!?'>!I4%&,!
!
Log!files!can!be!downloaded!using!either!the!configuration!application!or!the!monitoring!
application.!To!download!a!log!file,!navigate!to!the!“Log!File!Management”!menu!option.!This!will!
open!up!a!file!management!interface!as!shown!in!the!picture!below:!
!
Figure 15.4 Log file management window.
!
Each!category!of!log!file!will!be!stored!in!its!own!dedicated!directory.!Open!the!directory!
containing!the!desired!log!file!to!download.!Double!click!on!the!log!file.!A!popup!window!will!ask!
for!a!final!confirmation!before!the!file!download!starts.!
!
-R.V!8&%&+4*>!?'>!I4%&,!
!
The!log!files!can!easily!be!deleted!if!needed.!Navigate!into!a!log!file!directory.!To!delete!a!file!
within!the!directory,!right-click!on!the!file!and!select!‘Delete’.!The!file!will!be!permanently!deleted!
from!the!appliance.!
!
It!is!also!possible!to!rename!a!log!file.!Right-click!on!the!file!to!rename!it.!
!
Even!though!possible,!never!delete!a!log!file!directory.!
!
Please!note!that!some!log!files!become!very!large.!The!appliance!has!limited!space!for!log!files,!
therefore!always!download!important!log!files!and!save!them!outside!the!appliance.!The!appliance!
performs!log!rotation,!which!means!older!log!files!will!be!deleted!if!needed!by!the!appliance.!
39
© SOLIDA SYSTEMS INTERNATIONAL 2017
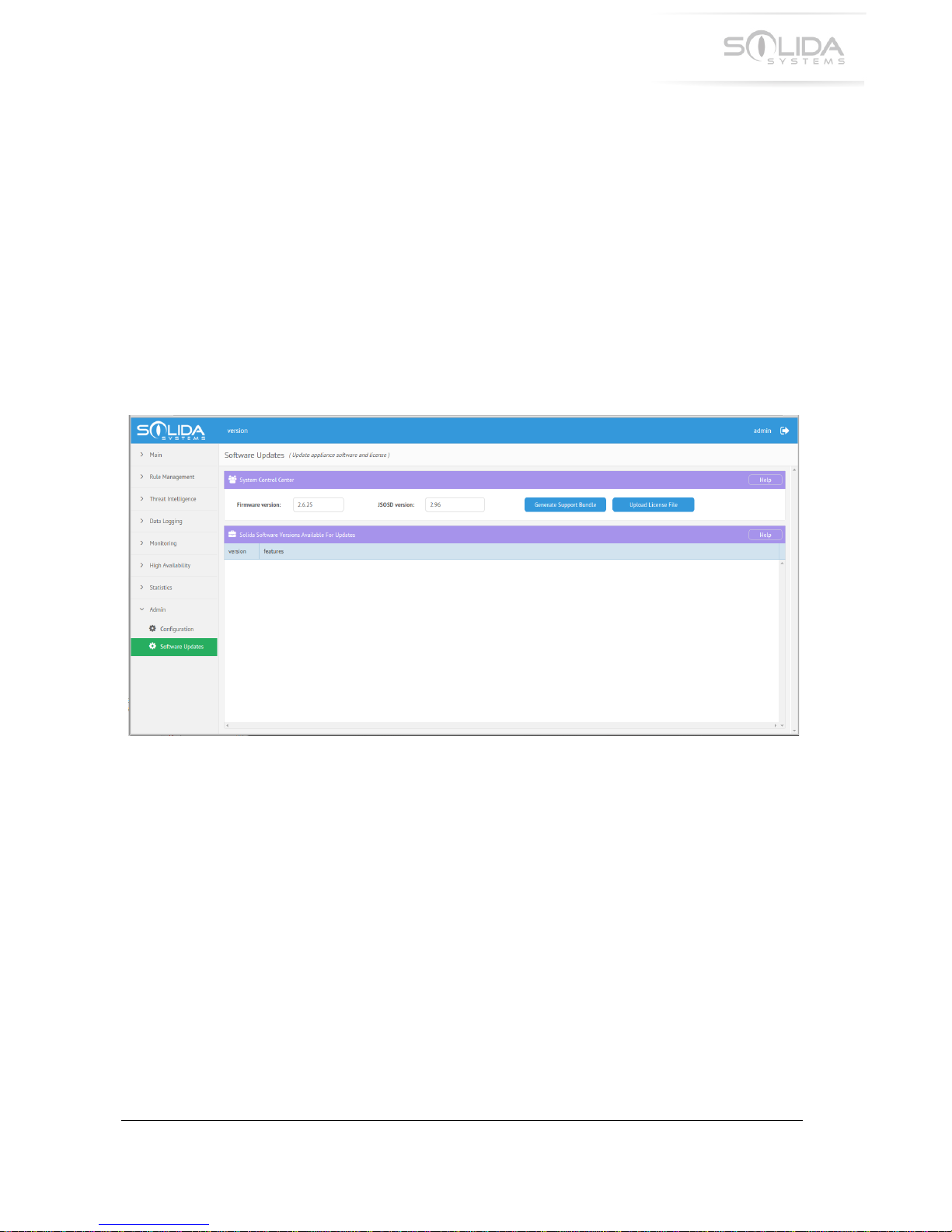
-T.!HC,+&L!H'(+A#0&!Q61#+&,!
!
Solida!Systems!will!occasionally!release!updated!system!software!for!the!appliances.!These!
releases!might!contain!bug!fixes!as!well!as!new!features.!New!releases!are!published!to!the!cloud!
for!distribution.!The!appliances!will!automatically!check!with!the!cloud!server!to!see!if!any!new!
updates!are!available.!The!user!can!decide!if!the!appliance!should!be!updated!or!not.!It!is!not!
required!to!perform!any!updates,!unless!it!is!specifically!advised!to!do!so!in!the!features!text!for!
the!release.!
!
To!check!for!a!new!software!release!or!to!perform!an!update,!start!the!configuration!application!
and!navigate!to!“Software!Updates”!in!the!menu!side!bar.!This!will!present!the!following!window:!
!
!
Figure 16.1 Software update GUI window.
!
The!upper!System!Control!Center!box!contains!the!following:!
!
! Firmware!version! -!Displays!the!currently!active!internal!firmware!version!number.!
! JSOSD!version!! -!Displays!the!version!of!the!current!security!OS!daemon.!
! !
!
The!button!named!“Generate!Support!Bundle”!starts!a!support!feature!that!collects!useful!
information!from!the!appliance.!See!the!“Support!Bundle!Generation”!chapter!for!further!
information!regarding!this.!
!
The!lower!box!titled!“Solida!Software!Versions!Available!For!Updates”!contains!a!list!of!available!
software!updates.!The!list!will!only!include!versions!that!are!later!than!the!version!currently!
running!in!the!appliance.!!
!

40
© SOLIDA SYSTEMS INTERNATIONAL 2017
To!perform!an!update,!simply!double!click!on!the!row!with!the!desired!new!version.!!
!
9%&#,&!*'+&!4+!A4%%!+#K&!#,!%'*>!#,!R!L4*2+&,!('0!#!,'(+A#0&!261#+&!+'!3'L6%&+&.!8204*>!+B4,!+4L&!
*'!*&+A'0K!+0#((43!A4%%!$&!#$%&!+'!(%'A!+B0'2>B!+B&!#66%4#*3&.!S(+&0!+B&!261#+&!B#,!3'L6%&+&1\!
6%&#,&!0&,&+!+B&!$0'A,&0!B4,+'0C!+'!>2#0#*+&&!+B&!$0'A,&0!A4%%!14,6%#C!+B&!%#+&,+!:&0,4'*!'(!+B&!
A&$!2+4%4+4&,.!
!
"B&!$2++'*!%#$&%&1!]Q6%'#1!?43&*,&!I4%&^!,+#0+,!#!(4%&!26%'#1!6'626!A4*1'A.!"B4,!4,!AB&0&!#!*&A!
+B0&#+!4*+&%%4>&*3&!%43&*,&!(4%&!,B'2%1!$&!26%'#1&1!+'!+B&!#66%4#*3&.!
41
© SOLIDA SYSTEMS INTERNATIONAL 2017
-V.!H266'0+!72*1%&!U&*&0#+4'*!
!
A!support!bundle!is!a!compressed!file!that!contains!critical!system!files!and!data.!A!support!bundle!
should!only!be!generated!after!a!request!from!Solida!Systems,!or!the!local!distributor.!A!support!
bundle!is!typically!only!generated!if!the!appliance!is!having!difficulties!performing!as!expected.!
The!files!in!the!support!bundle!will!help!a!support!engineer!to!determine!the!cause!of!a!problem.!
! !
-V.-!U&*&0#+4*>!#!,266'0+!$2*1%&!
!
To!generate!a!support!bundle,!start!the!configuration!application!on!the!appliance!experiencing!a!
problem.!Navigate!to!“Software!Updates”.!This!will!display!a!window!that!contains!a!blue!button!
with!the!text!“Generate!Support!Bundle”.!Pressing!this!button!and!answering!Yes!in!the!
confirmation!box!will!start!generating!a!support!bundle.!Note!that!it!might!take!up!to!5!minutes!or!
more!for!the!bundle!generation!to!complete.!
! !
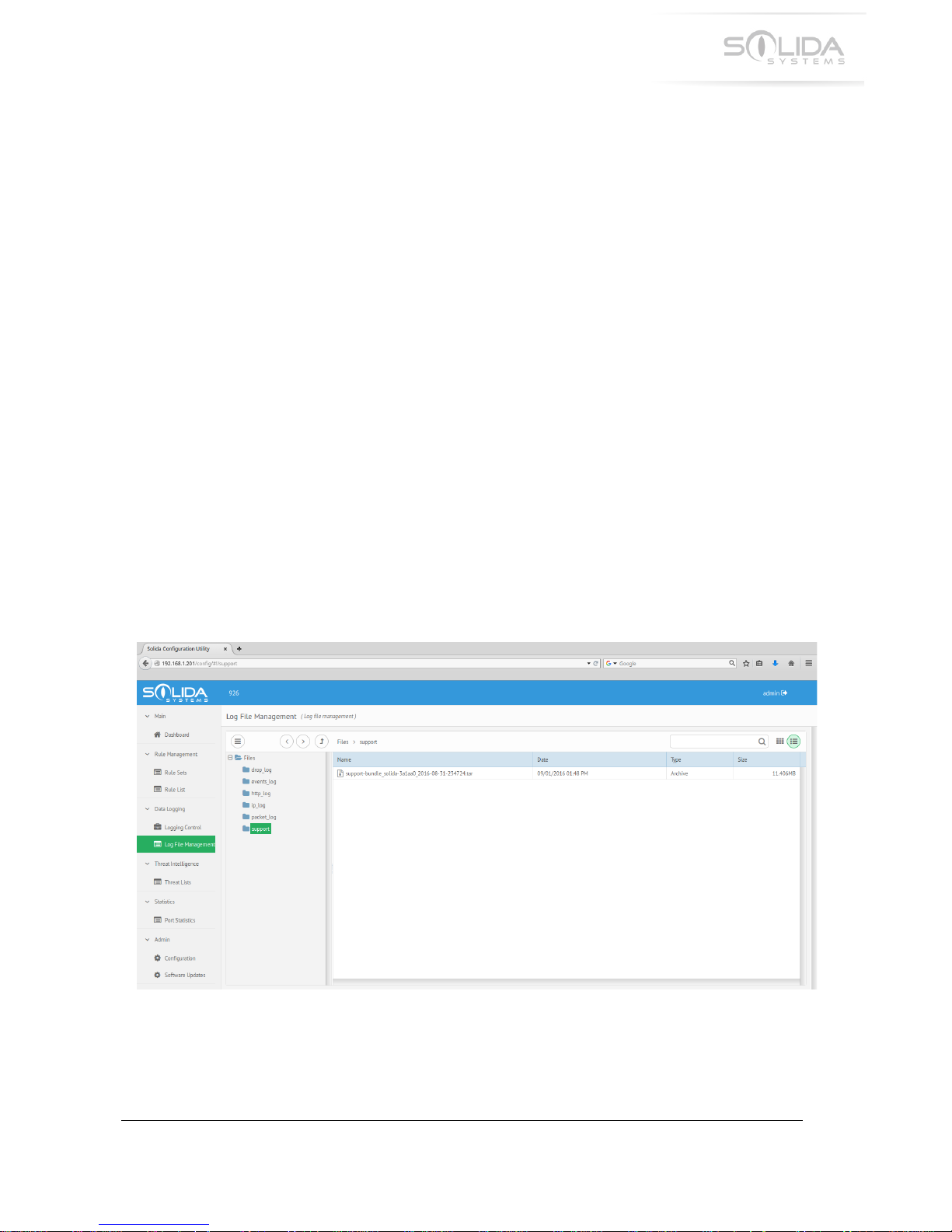
-V.;!8'A*%'#14*>!#!,266'0+!$2*1%&!
!
Once!a!support!bundle!has!been!generated,!it!will!be!placed!in!a!directory!called!“support”!in!the!
log!file!storage!area.!!
!
Figure 17.1 Log File Management window with support directory opened.
!
To!download!a!support!bundle!file,!start!the!configuration!application!and!navigate!to!“Log!File!
management”.!Then!click!on!the!“support”!directory!icon!in!the!file!viewer.!This!will!display!all!!

42
© SOLIDA SYSTEMS INTERNATIONAL 2017
available!support!bundles!that!are!ready!to!be!downloaded.!!!
!
Please!note!it!will!take!up!to!5!minutes!for!a!new!support!bundle!to!appear!in!this!directory.!
!
!
!
!
!

43
© SOLIDA SYSTEMS INTERNATIONAL 2017
-X.!5&6'0+!U&*&0#+4'*!
!
The!Solida!Monitor!utility!includes!a!tool!for!generating!security!reports.!A!security!report!is!a!
Microsoft!Excel!compatible!(xlsx)!file!containing!information!about!the!events!that!has!occurred!in!
the!appliance!over!the!past!30!days.!
!
To!generate!a!report,!navigate!to!Analysis!->!Reporting.!The!following!page!will!be!displayed:!
!
!
!
Figure'18.1'Report'generation'
!
!
A!report!file!will!be!generated!when!the!“Generate!Report”!button!is!pressed.!Generating!a!report!
can!take!up!to!several!minutes.!When!done,!the!report!can!be!downloaded!from!the!“report”!
directory!in!the!“Log!File!Management”!window.!
!
P'+&W!/+!4,!0&3'LL&*1&1!+B&!0&6'0+!(4%&!4,!'6&*&1!#*1!(20+B&0!60'3&,,&1!4*!#*!'04>4*#%!=430','(+!
DE3&%!#66%43#+4'*.!Q,&!'(!,4L4%#0!*'*_=430','(+!60'123+,!,23B!#,!?4$0&!O((43&!)#%3!L4>B+!*'+!
0&*1&0!+B&!0&6'0+!3'00&3+%C.!!!
!
The!report!is!formatted!so!that!it!will!print!in!a!pleasant!and!easily!readable!way!

44
© SOLIDA SYSTEMS INTERNATIONAL 2017
S66&*14E!S.!`'/9!)#%%&0!7%'3K4*>!
!
!
The!appliance!can!be!used!for!blocking!callers!in!a!VoIP!network.!Blocked!caller!phone!numbers!
are!provided!to!the!appliance!in!the!form!of!a!text!file.!
!
!
S.-!S66%4#*3&!H&+26!
!
The appliance is designed to be installed as an end-point device, installed between the Internet
router and the main VoIP network switch as the picture below illustrates.
Figure A.1 The appliance installed in a VoIP network.
If the network uses a firewall between the Internet router and main switch, install the appliance in
front of the firewall just behind the Internet router. The appliance will be invisible to the firewall
since it requires no IP or MAC addresses for its ports.
S.;!7%'3K&1!P2L$&0,!?4,+!
The user must provide a list containing the phone numbers that are to be blocked. The list must be a
simple ASCII text file created with a text editor tool. The name of this file must be “sip.txt”. The
appliance will accept no other name. It is also important that the list does not contain any
formatting characters like those used by advanced word processors such as MS Word. Each line in
the text file must contain only one phone number, or range of phone numbers. For example:

45
© SOLIDA SYSTEMS INTERNATIONAL 2017
8189124450
9921232131
123123310
It is the user's responsibility to maintain this list and to make sure it is a plain ASCII text file
containing no control characters. The appliance will reject lists that are not formatted properly or
named anything other than sip.txt.
Uploading a list is a simple process. Start the web configuration tool in the appliance and navigate
to the page called “Threat Lists”. This page has a file upload button marked “Upload file’.
Figure A.2 File upload button.
Press this button and upload the sip.txt text file. The list will immediately become active, and
replace the previous list if present, as soon as the upload completes.
!
S.<!HC,+&L!`'/9!52%&,!
!
The!VoIP!number!blocking!feature!also!requires!two!packet!inspection!rules!to!be!enabled.!These!
rules!contain!instructions!for!what!the!packet!inspection!engine!is!to!search!for.!The!rule!IDs!for!
these!two!rules!are:!
!
! 100!001!001!
100!001!002

To!activate!these!two!rules!it!will!be!required!to!create!a!new!rule!set.!This!rule!set!should!include!
these!two!VoIP!related!rules!as!well!as!any!other!rule!required!for!the!appliance.!Other!rules!will!
not!have!any!impact!on!the!VoIP!functionality.!
!
!
S.M!D:&*+!U&*&0#+4'*!
!
Each!time!an!incoming!call!has!been!blocked,!a!security!event!will!be!generated.!These!events!are!
readable!from!the!monitoring!utility!together!will!all!other!events!in!the!appliance.!All!VoIP!events!
will!be!written!to!the!event!log!file!and!the!corresponding!dropped!packets!will!be!written!to!the!
drop!log!file.!
!
!
!

47
© SOLIDA SYSTEMS INTERNATIONAL 2017
S66&*14E!7.!840&3+!S33&,,!'(!?'>!I4%&,!
!
The!appliance!allows!for!accessing!its!log!files!directly!over!the!management!Ethernet!port!without!
going!through!the!GUI!applications.!This!is!done!by!using!the!rsync!command!in!Linux!to!a!special!
user!account!in!the!appliance.!
!
7.-!?'>>4*>!/*!"'!"B&!?'>!I4%&!840&3+'04&,!
!
It!is!possible!to!log!in!to!the!special!user!account!and!inspect!the!contents!of!the!log!file!
directories.!Perform!an!SSH!login!to!the!special!log!file!user!account!on!the!management!port:!
!
!!solida-logs@192.168.1.250!
!
password:!The!serial!number!of!the!appliance!(case!sensitive)!
!
The!IP!address!is!the!same!address!as!used!in!general!for!logging!into!the!management!port.!This!
default!IP!address!can!be!changed.!If!so,!please!use!the!IP!current!active!IP!address!for!this!login.!
!
!
7.;!)'6C4*>!O2+!?'>!I4%&,!
!
Log!files!should!be!copied!out!from!the!appliance!using!the!rsync!command!from!a!Linux!
computer.!A!typical!command!sequence!for!copying!over!the!event!files!will!be:!
!
! rsync!–av solida-logs@192.168.1.250:/home/solida-logs/events_log .
!
Valid!log!file!directories!are!the!same!directories!as!seen!from!the!GUI!applications.!
!
7.<!?'>!I4%&!I'0L#+,!
!
Log!files!are!written!in!two!formats,!PCAP!and!JSON.!All!event!log!files!are!written!in!JSON!format!
and!all!packet!log!files!are!written!in!PCAP!format.!Any!text!editor!can!open!event!log!files!and!
packet!log!files!can!be!opened!with!for!example!Wireshark.!
!
!

48
© SOLIDA SYSTEMS INTERNATIONAL 2017
S66&*14E!).!H'%41#!=2%+4!5&L'+&!='*4+'04*>!
!
Solida!Multi!is!a!remote!monitoring!software!tool!that!allows!for!monitoring!multiple!appliances!
remotely!over!the!Internet.!
!
).-!H&++4*>!Q6!"B&!H'%41#!=2%+4!H&:&0!
!
Before!the!Solida!Multi!software!can!be!installed!the!user!must!decide!if!the!server!should!be!
hosted!in!the!cloud!or!be!installed!as!a!physical!server.!In!both!cases!it!is!required!that!the!server!
is!assigned!a!fixed!IP!address.!This!IP!address!is!then!passed!to!the!security!appliance!during!
configuration.!!The!server!needs!to!run!the!Linux!operating!system.!If!the!server!uses!Windows!
then!Solida!Multi!must!be!installed!as!a!virtual!instance!under!Windows.!!
!
).;!)'*(4>204*>!"B&!S66%4#*3&!('0!H'%41#!=2%+4!
It!is!straightforward!to!configure!the!appliance!so!that!it!starts!communication!with!the!remote!
computer!hosting!Solida!Multi.!The!IP!address!of!the!server!hosting!Solida!Multi!must!be!provided!
together!with!a!user!name!and!password!for!a!remote!login!connection.!
!
!
).<!5&N240&1!P&+A'0K!9'0+,.!
The!security!appliance!will!communicate!with!Solida!Multi!over!port!22!(ssh).!If!port!22!is!blocked!
by!a!firewall!then!the!appliance!require!port!443!(https)!to!be!opened!for!this!communication.!!
Port!53!must!also!be!open!for!DNS!lookups.!
!
).M!)'LL2*43#+4'*!
!
Once!the!security!appliance!has!been!set!up!to!communicate!with!a!Solida!Multi!server!it!will!start!
sharing!security!data.!!
!
!
!
!
! !

49
© SOLIDA SYSTEMS INTERNATIONAL 2017
!
!
!
!
!
!
!
!
!
!
SOLIDA!SYSTEMS!INTERNATIONAL!CO.,!LTD.!
1000/19-20!Liberty!Plaza!Building,!Floor!12A,!Thonglor,!Sukhumvit!
Soi!55,!Klongtan!Nua,!Wattana,!Bangkok,!Thailand,!10110!
"&%!!+66!2-714-8900!!!!!!!!DL#4%!!info@solidasystems.com!!!!!!!!J&$,4+&!!www.solidasystems.com!
 Loading...
Loading...