Page 1

EZ Connect N
Draft 11n Wireless USB2.0 Adapter
ADSL2 BARRICADE ™
4-Ports Wireless Annex B ADSL/ADSL2 Modem Router
SMC7904WBRB4
Page 2

54Mbps Wireless Router
with built-in ADSL Modem
From SMC’s line of award-winning connectivity solutions
March 2009
R.01 f/w 1.0
Page 3

Copyright
Information furnished is believed to be accurate and reliable. However, no responsibility is assumed
by our company for its use, nor for any infringements of patents or other rights of third parties which
may result from its use. No license is granted by implication or otherwise under any patent or patent
rights of our company. We reserve the right to change specifications at any time without notice.
Copyright © 2009 by
SMC Networks, Inc.
20 Mason
Irvine, CA 92618
All rights reserved.
Trademarks:
SMC is a registered trademark; and Barricade is a trademark of SMC Networks, Inc. Other product
and company names are trademarks or registered trademarks of their respective holders.
ii
Page 4

Warranty and
Product Registration
To register SMC products and to review the detailed warranty statement, please refer to
the Support Section of the SMC Website at http://www.smc.com
SMC Networks, Inc.
20 Mason
Irvine, CA 92618
SMC Networks Europe
C/Fructuós Gelabert 6-8 2o, 2a
Edificio Conata II
08970 Sant Joan Despí
Barcelona - Spain
iii
Page 5

Compliances
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant
to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates, uses and can radiate radio frequency
and, if not installed and used in accordance with the instructions, may cause harmful interference to radio
communications. However, there is no guarantee that interference will not occur in a particular installation.
If this equipment does cause harmful interference to radio or television reception, which can be determined
by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more
of the following measures:
• Reorient or relocate the receiving antenna.
• Increase the distance between the equipment and receiver.
• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.
• Consult the dealer or an experienced radio/TV technician for help.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions:
(1) This device may not cause harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation.
FCC Caution: To assure continued compliance, (example - use only shielded interface cables when
connecting to computer or peripheral devices) any changes or modifications not expressly approved by the
party responsible for compliance could void the user’s authority to operate this equipment.
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment.
This equipment should be installed and operated with a minimum distance of 20cm between the radiator
and your body. This transmitter must not be co-located or operating in conjunction with any other
antenna or transmitter..
FCC - Part 68
This equipment complies with Part 68 of the FCC rules. This equipment comes with a label attached to
it that contains, among other information, the FCC registration number and ringer equivalence number
(REN) for this equipment. If requested, this information must be provided to the telephone company.
This equipment uses the following jacks: RJ-11.
The REN is used to determine the quantity of devices that may be connected to the telephone line.
Excessive RENs on the telephone line may result in the devices not ringing in response to an incoming
call. In most, but not all areas, the sum of the RENs should not exceed five (5.0). To be certain of the
number of devices that may be connected to the line, as determined by the total RENs, contact the
telephone company to determine the maximum REN for the calling area
IMPORTANT NOTE:
IEEE 802.11b or 802.11g operation of this product in the U.S.A. is firmware-limited to channels 1 through 11.
iv
Page 6

Industry Canada Statement
Operation is subject to the following two conditions:
1. This device may not cause interference and
2. This device must accept any interference, including interference that may cause undesired operation of
the device
To prevent radio interference to the licensed service, this device is intended to be operated indoors and
away from windows to provide maximum shielding. Equipment (or its transmit antenna) that is installed
outdoors is subject to licensing.
This device has been designed to operate with an antenna having maximum gain of 1.5dBi.
Any antenna having a higher gain is strictly prohibited per regulations of Industry Canada. The required
antenna impedance is 50 ohms.
To reduce potential radio interference to other users, the antenna type and its gain should be so chosen
that the EIRP is not more than required for successful communication.
NCC Statement
依據 低功率電波幅射性電機管理辦法
第十二條 經型式認證合格之低功率射頻電機,非經許可,公司、商號或使用者不得擅自變更頻
率、加大功率或變更原設計之特性及功能
第十四條 低功率射頻電機之使用不得影響飛航安全及干擾合法通信;經發現有干擾現象時,
應立即使用,並改善至無干擾時方得繼續使用。
前項合法通信,指依電信規定作業之無線電信。低功率射頻電機須忍受合法通信或工業、科學
及醫療用電波幅射性電機設備之干擾。
Countries of Operation & Conditions of Use in the European Community
SMC contact for these products in Europe is:
SMC Networks Spain, S.L.
Edificio Conata II,
Group CTSG
Fructuos Gelabert 6-8 2o2a
08970 Sant Joan Despi, Barcolona,Spain
This device complies with the essential requirements of the R&TTE Directive 1999/5/EC. The
following test methods have been applied in order to prove presumption of conformity with the
essential requirements of the R&TTE Directive 1999/5/EC:
- EN 61000-3-2: 2000+A2:2005
- EN 61000-3-3:1995 + A1:2001+A2:2005
- EN 55024:1998 + A1:2001+A2:2003
- EN 55022:1998 + A1:2000 + A2:2003
v
Page 7
- EN 301 489-1 V1.6.1 (2004-12)
-
EN 301 489-17 V1.2.1 (2002-08)
-
EN 300 386 V1.3.3 (2005-04)
-
EN 60950-1:2006
-
EN 300 328 V1.7.1 (2006-10)
-
EN 50932:2004
This device is a 2.4 GHz wideband transmission system (transceiver), intended for use in all EU
member states and EFTA countries, except in France and Italy where restrictive use applies.
In Italy the end-user should apply for a license at the national spectrum authorities in order to obtain
authorization to use the device for setting up outdoor radio links and/or for supplying public access to
telecommunications and/or network services.
This device may not be used for setting up outdoor radio links in France and in some areas the RF
output power may be limited to 10 mW EIRP in the frequency range of 2454 – 2483.5 MHz. For
detailed information the end-user should contact the national spectrum authority in France.
The official CE certificate of conformity can be downloaded by selecting the relevant model/ part
number from www.smc.com -> support -> download"
Declaration of Conformity in Languages of the European Community
[Czech]
Společ
nost SMC Networks tímto prohlašuje, že toto rádiové
zařízení LAN je ve shodě se základními požadavky a dalšími
příslušnými ustanoveními směrnice 1999/5/ES. Oficiální ES
prohlášení o shodě je uvedeno v příslušné části k produktu na
webu
http://www.smc.com
[Danish]
SMC Networks erklærer herved, at følgende Radio
LAN-enhed overholder de
væsentlige krav og andre relevante
bestemmelser i direktiv 1999/5/EF. Den officielle
EU-overensstemmelseserklæring er tilgængelig under det
relevante produktafsnit på følgende webadresse:
http://www.smc.com
.
[German]
Hiermit erklärt SMC Networks, dass sich dieses Wireless LAN
Gerät in Übereinstimm
ung mit den grundlegenden
Anforderungen und den anderen relevanten Vorschriften der
Richtlinie 1999/5/EG befindet. Die offizielle EC-Declaration
of Conformity finden Sie im Internet unter
http://www.smc.com unter der entsprechenden
vi
Page 8

Produktkategorie.
[Estonian]
Käesolevaga kinnitab SMC Networks, et see Radio LAN seade
vastab direktiivi 1995/5/E
Ü põhinõuetele ja teistele
asjakohastele sätetele. Ametliku EÜ vastavusdeklaratsiooni
leiate vastavast tootejaotisest aadressil http://www.smc.com
.
[English]
Hereby, SMC Networks, declares that this Radio LAN device
is in com
pliance with the essential requirements and other
relevant provisions of Directive 1999/5/EC. The official
EC-Declaration of Conformity can be found under the
corresponding product section on the web
http://www.smc.com.
[Spanish]
Por medio de la presente SMC Networks declara que el Radio
LAN device
cumple con los requisitos esenciales y
cualesquiera otras disposiciones aplicables o exigibles de la
Directiva 1999/5/CE. The official EC-Declaration of
Conformity can be found under the corresponding product
section on the web
http://www.smc.com
[Greek]
Με την παρούσα,
η SMC Networks, δηλώνει ότι η συσκευή
ασύρματου τοπικού δικτύου συμμορφώνεται με τις ουσιώδεις
απαιτήσεις και τις λοιπές σχετικές διατάξεις της Οδηγίας
1999/5/EΚ. Η επίσημη δήλωση συμμόρφωσης EΚ παρέχεται
στην αντίστοιχη ενότητα προϊόντων, στην ιστοσελίδα
http://www.smc.com
.
[French]
Par la présente SMC Networks déclare
que l'appareil Radio
LAN device est conforme aux exigences essentielles et aux
autres dispositions pertinentes de la directive 1999/5/CE. La
déclaration de conformité officielle peut être trouvée sur notre
site internet http://www.smc.com dans la rubrique Produits.
[Italian]
Con la presente SMC Networks dichiara che questo Radio
LAN device
è conforme ai requisiti essenziali ed alle altre
disposizioni pertinenti stabilite dalla direttiva 1999/5/CE. La
Dichiarazione di conformità CE ufficiale è disponibile nella
sezione dedicata al rispettivo prodotto sul sito Web
http://www.smc.com
.
[Latvian]
Ar šo SMC Networks deklarē
, ka Radio LAN device atbilst
Direktīvas 1999/5/EK būtiskajām prasībām un citiem ar to
saistītiem noteikumiem. Oficiālā EK atbilstības deklarācija ir
atrodama attiecīgā produkta sadaļā tīmeklī
http://www.smc.com
.
[Lithuanian]
Šiuo „SMC Networks“ deklaruoja, kad šis radijo LAN
įrenginy
s atitinka esminius reikalavimus ir kitas 1999/5/EB
Direktyvos nuostatas. Oficialią jo EB atitikties deklaraciją
galima rasti atitinkamų gaminių skyriuje šiame tinklalapyje:
http://www.smc.com
.
[Dutch]
Hierbij verklaart SMC Networks dat het toestel Radio LAN
device in ove
reenstemming is met de essentiële eisen en de
andere relevante bepalingen van richtlijn 1999/5/EG. Het
vii
Page 9
officiële EC- gelijkvormigheidattest kan men vinden op de
internetsite http://www.smc.com onder de betrokken
productcategorie.
[Maltese]
B’dan, SMC Networks, tiddikjara li dan it-tagħmi
r LAN
tar-Radju huwa konformi mar-rekwiżiti essenzjali u
dispożizzjonijiet rilevanti oħra ta’ Direttiva 1999/5/KE.
Id-Dikjarazzjoni ta’ Konformità uffiċjali tal-KE tinsab
fit-taqsima korrispondenti fis-sit ta’ l-Internet
http://www.smc.com
.
[Hungarian]
Az SMC Networks kijelenti, hogy a Radio LAN eszköz
megfelel a vo
natkozó alapvető követelményeknek és az
1999/5/EC irányelv egyéb előírásainak. A hivatalos EC
megfelelőségi nyilatkozat megtalálható a vonatkozó termék
ismertetőjénél, a következő címen: http://www.smc.com
[Polish]
Firma SMC Networks niniejszym oświ
adcza, że urządzenie
Radio LAN jest zgodne z zasadniczymi wymaganiami oraz
pozostałymi stosownymi postanowieniami Dyrektywy
1999/5/EC. Oficjalna Deklaracja zgodności UE znajduje się w
odpowiedniej sekcji produktu w witrynie
http://www.smc.com
.
[Portuguese]
A SMC Networks declara que este dispositivo de LAN de
Rádio está e
m conformidade com os requisitos essenciais e
com outras provisões relevantes da Directiva 1999/5/CE. A
Declaração de Conformidade CE oficial encontra-se na secção
correspondente do produto na Web,
http://www.smc.com
.
[Slovenian]
Družba SMC Network izjavlja, da je naprava Radio LAN
skladna z bistvenim
i zahtevami in drugimi ustreznimi predpisi
direktive 1999/5/ES. Za uradno izjavo o skladnosti ES glejte
razdelek za ustrezni izdelek na spletni strani
http://www.smc.com
.
[Slovak]
Spoloč
nosť SMC Networks týmto vyhlasuje, že toto zariadenie
Radio LAN spĺňa základné požiadavky a ďalšie príslušné
ustanovenia smernice 1999/5/ES. Oficiálne prehlásenie ES o
zhode je uvedené v sekcii príslušného produktu v lokalite
http://www.smc.com
.
[Finnish]
SMC Networks vakuuttaa täten, että Radio LAN device
-tyyppi
nen laite on direktiivin 1999/5/EY oleellisten
vaatimusten ja sitä koskevien direktiivin muiden ehtojen
mukainen. EY:n virallinen vaatimustenmukaisuusvakuutus on
tuotteen kohdalla Web-sivustossa
http://www.smc.com
.
[Swedish]
Härmed intygar SMC Networks att denna Radio LAN-apparat
uppf
yller de väsentliga egenskapskrav och övriga relevanta
bestämmelser i direktiv 1999/5/EG. Den officiella
EG-försäkran om överensstämmelse finns under motsvarande
produktavsnitt på
http://www.smc.com
.
[Icelandic]
Hér með lýsir SMC Networks því yfir að þessi Radio LAN
búnaður er í s
amræmi við grunnkröfur og aðrar viðeigandi
kröfur, sem gerðar eru í tilskipun 1999/5/EB. Opinberu
viii
Page 10
EB-samræmisyfirlýsinguna er að finna í viðeigandi hluta um
þennan búnað á vefsetrinu http://www.smc.com
.
[Norwegian]
SMC Networks erklærer herved at Radio LAN-enheten er i
samsvar
med de grunnleggende kravene og øvrige relevante
krav i direktiv 1999/5/EF. Denne offisielle
EU-konformitetserklæringen finnes under korresponderende
produktseksjon på Internett:
http://www.smc.com
.
Countries of Operation & Conditions of Use in EC/ EFTA member states
[English]
This device is a 2.4 GHz wireless LAN transceiver, intended for
indoor
home and office use in all notified EC and EFTA
member states. In accordance with article 6.4 of the R&TTE
Directive 1999/5/EC the following EC/ EFTA member states
have been notified: Austria, Belgium, Denmark, Finland,
France, Germany, Italy, Luxembourg, Netherlands, Norway,
Spain, Sweden, Switzerland, United Kingdom, Portugal,
Greece, Ireland, Iceland. Requirements for outdoor operation,
like license requirements and allowed channels of operation
apply in some countries. Please contact your local regulation
authority or SMC Networks for details on current restrictions
for outdoor use.
[French]
Ce produit est un appareil radio LAN transceiver de 2.4 GHz
destiné aux PME et à l’utilisation dom
estique dans tous les pays
certifiés conformes aux conditions de l’EU et de l’EFTA. En
accord avec l’article 6.4 de la R&TTE directive 1999/5/EC, the
membres de la EU et de l’EFTA sont les suivants : Autriche,
Belgique, Danemark, finalnde, France, Allemagne, Italie,
Luxembourg, Pays-Bas, Norvège, Espagne, Suède, Suisse,
Royaume-Uni, Portugal, Grèce, Irelande, Icelande. Des
conditions sont appliquées à certains pays pour l’utilisation en
extérieur, tels que des licences spécífiques et des canaux
d’opération. Veuillez contacter votre autorité locale ou SMC
Networks pour plus de détails quant aux restrictions actuelles
concernant l’utilisation en extérieur.
[Dutch]
Dit toestel is een 2.4 Ghz draadloze Lan transceiver, bestemd
voor gebrui
k binnen huis en kantoor in alle geïnformeerde
lidstaten van de EC en de EFTA. In overeenstemming met
artikel 6.4 van de R&T TE Directive 1999/5/EC zijn de
volgende EC/EFTA lidstaten verwittigd: België, Denemarken,
Duitsland, Finland, Frankrijk,Griekenland, Ierland, IJsland,
Italië, Luxemburg, Nederland, Noorwegen,Oostenrijk, Portugal,
Spanje , Verenigd Koninkrijk, Zweden, Zwitserland.
Benodigdheden voor gebruik buiten, zoals
gebruiksvergunningen en toegelaten werkkanalen zijn van
toepassing in sommige landen. Gelieve uw lokale instantie of
SMC Networks te contacteren voor details op huidige
beperkingen voor gebruik in buitenlucht.
ix
Page 11
[Spanish]
Este aparato es un transmisor inalámbrico de 2.4 GHz, previsto
para el uso in
terior en domicilios y Pymes en todos los Estados
de la CE y la EFTA notificados. De acuerdo con el artículo 6.4
de la Directiva R&TTE 1999/5/EC los siguientes estados de la
CE y de la EFTA han sido notificados: Austria, Bélgica,
Dinamarca, Finlandia, Francia, Alemania, Italia, Luxemburgo,
Países Bajos, Noruega, España, Suecia, Suiza, Reino Unido,
Portugal, Grecia, Irlanda, Islandia. Los requisitos para su uso
exterior, como requerimiento de licencia y canales de operación
permitidos se aplican en algunos países. Por favor contacte la
autoridad reguladora local o SMC Networks para más detalles
en relación con las restricciones actuales para uso exterior.
[German]
Dieses Wireless LAN Gerät arbeitet im 2.4 GHz Frequenzband
und
ist für den Einsatz im Innenbereich in den benachrichtigten
EC/ EFTA Mitgliedstaaten geeignet. In Übereinstimmung mit
Artikel 6.4 der R&TTE Direktive 1999/5/EC wurden folgende
Mitgliedstaaten benachrichtigt: Österreich, Belgien, Dänemark,
Finland, Frankreich, Deutschland, Italien, Luxemburg,
Niederlande, Norwegen, Spanien, Schweden, Schweiz,
Großbritannien, Portugal, Griechenland, Irland, Island. Für den
Einsatz im Aussenbereich sind in einigen Ländern Lizenzen
erforderlich oder die Anzahl der Kanäle ist eingeschränkt. Bitte
kontaktieren Sie Ihre Regulierungsbehörde oder SMC Networks
für die aktuellen Einschränkungen beim Einsatz im
Aussenbereich.
[Czech]
Toto zař
ízení je přijímač a vysílač pro bezdrátové sítě LAN v
pásmu 2,4 GHz, určený pro použití v interiéru domácností a
kanceláří ve všech členských zemích ES a ESVO, kterým byl
oznámen záměr uvést zařízení na trh. V souladu s čl. 6 odst. 4
směrnice 1999/5/ES o rádiových zařízeních a
telekomunikačních koncových zařízeních byly uvědoměny tyto
členské země ES nebo ESVO: Belgie, Dánsko, Finsko, Francie,
Irsko, Island, Itálie, Lucembursko, Německo, Nizozemsko,
Norsko, Portugalsko, Rakousko, Řecko, Spojené království,
Španělsko, Švédsko, Švýcarsko. Na použití ve venkovním
prostředí se v některých zemích vztahují určité požadavky, např.
požadavky na licenci nebo provoz v povolených kanálech. O
omezení venkovního použití se informujte u místních regulátorů
nebo u společnosti SMC Networks.
[Danish]
Enheden er en 2,4 GHz trådløs LAN-transceiver, beregnet til
indendørs hj
emme- og kontorbrug i alle notificerede EU- og
EFTA-medlemslande. I henhold til afsnit 6.4 i
R&TTE-direktivet 1999/5/EF er følgende
EU-/EFTA-medlemslande notificeret: Østrig, Belgien,
Danmark, Finland, Frankrig, Tyskland, Grækenland, Island,
Irland, Italien, Luxembourg, Holland, Norge, Portugal, Spanien,
Sverige, Schweiz og Storbritannien. I visse lande gælder der
krav vedrørende udendørs betjening af enheden, f.eks.
licenskrav og tilladte betjeningskanaler. Kontakt de lokale
lovgivende myndigheder eller SMC Networks for at få
oplysninger om aktuelle begrænsninger vedrørende udendørs
betjening.
x
Page 12
[Estonian]
See seade on 2.4 GHz juhtmeta LAN vastuvõtu-saatejaam, mis
on m
õeldud kodus ja kontoris kasutamiseks kõikides teavitatud
EÜ ja Euroopa Vabakaubanduse Assotsiatsiooni (EFTA)
liikmesriikides. Vastavalt R&TTE direktiivi 1999/5/EÜ
paragrahvile 6.4 on teavitatud järgmisi EÜ/EFTA liikmesriike:
Austriat, Belgiat, Taanit, Soomet, Prantsusmaad, Saksamaad,
Itaaliat, Luksemburgi, Hollandit, Norrat, Hispaaniat, Rootsit,
Šveitsi, Ühendkuningriiki, Portugali, Kreekat, Iirimaad, Islandi.
Mõningates riikides kehtivad väljas kasutamiseks nõuded,
näiteks litsentsinõuded ja lubatud töökanalid. Palun teavitage
vastavat kohalikku ametkonda või ettevõtet SMC Networks’i,
kui soovite täpsemaid andmeid väljas kasutamisel kehtivate
piirangute kohta.
[Greek]
Αυτή η συσ
κευή είναι ένας ασύρματος πομποδέκτης τοπικού
δικτύου 2,4 GHz, που προορίζεται για οικιακή και
επαγγελματική χρήση σε εσωτερικό χώρο, σε όλα τα
κράτη-μέλη της ΕΚ και της ΕΖΕΣ. Σύμφωνα με το άρθρο 6.4
της Οδηγίας για ραδιοεξοπλισμό και τηλεπικοινωνιακό
τερματικό εξοπλισμό (R&TTE), 1999/5/ΕΚ, έχουν ανακοινωθεί
τα ακόλουθα κράτη-μέλη ΕΕ/ΕΖΕΣ: Αυστρία, Βέλγιο, Δανία,
Φιλανδία, Γαλλία, Γερμανία, Ιταλία, Λουξεμβούργο, Ολλανδία,
Νορβηγία, Ισπανία, Σουηδία, Ελβετία, Ηνωμένο Βασίλειο,
Πορτογαλία, Ελλάδα, Ιρλανδία, Ισλανδία. Σε ορισμένες χώρες
επιβάλλονται απαιτήσεις για χρήση σε εξωτερικό χώρο, όπως
απαιτήσεις παραχώρησης άδειας και επιτρεπόμενα κανάλια
λειτουργίας. Απευθυνθείτε στην τοπική αρμόδια αρχή ή στην
SMC Networks για λεπτομέρειες σχετικά με τους τρέχοντες
περιορισμούς για χρήση σε εξωτερικό χώρο.
[Italian]
Il presente device è un ricetrasmettitore LAN wireless da 2,4
GHz, previsto per l'uso in interni a
casa e in ufficio in tutti gli
Stati membri della CE e dell'EFTA notificati. Conformemente
all'articolo 6.4 della Direttiva 1999/5/CE R&TTE, sono stati
notificati i seguenti Stati membri della CE/dell'EFTA: Austria,
Belgio, Danimarca, Finlandia, Francia, Germania, Grecia,
Irlanda, Islanda, Italia, Lussemburgo, Norvegia, Paesi Bassi,
Portogallo, Regno Unito, Spagna, Svezia, Svizzera. In alcuni
Paesi si applicano i requisiti per il funzionamento in esterni,
quali requisiti di licenza e canali consentiti. Contattare
l'Autorità normativa locale del proprio Paese o SMC Networks
per informazioni dettagliate sulle limitazioni correnti per
l'utilizzo in esterni.
[Latvian]
Šī ier
īce ir 2,4 GHz bezvadu LAN raiduztvērējs, kas paredzēts
izmantošanai iekštelpās mājās un birojos visās paziņotajās EK
un EBTA (European Free Trade Association - Eiropas brīvās
tirdzniecības asociācija) dalībvalstīs. Atbilstoši radioiekārtu un
telekomunikāciju gala iekārtu direktīvas 1999/5/EK 6.4. pantam
paziņotās EK/EBTA valstis ir : Austrija, Beļģija, Dānija,
Somija, Francija, Vācija, Itālija, Luksemburga, Nīderlande,
Norvēģija, Spānija, Zviedrija, Šveice, Apvienotā Karaliste,
Portugāle, Grieķija, Īrija, Islande. Dažās valstīs ir spēkā
ierobežojumi lietošanai ārvidē, piemēram, licences prasības un
darbībai atļautie kanāli. Lūdzu, sazinieties ar vietējo
regulējošo instanci vai SMC Network, lai saņemtu informāciju
xi
Page 13
par pašreizējiem ierobežojumiem lietošanai ārvidē.
[Lithuanian]
Šis įrengin
ys yra 2,4 GHz belaidis LAN siųstuvas-imtuvas,
skirtas naudoti patalpose namie ar biure visose notifikuotose EB
ir ELPA šalyse narėse. Pagal RTTE Direktyvos 1999/5/EB 6.4
straipsnį, notifikuotos yra šios EB/ELPA šalys narės: Austrija,
Belgija, Danija, Suomija, Prancūzija, Vokietija, Italija,
Liuksemburgas, Nyderlandai, Norvegija, Ispanija, Švedija,
Šveicarija, Jungtinė Karalystė, Portugalija, Graikija, Airija,
Islandija. Kai kuriose šalyse galioja tam tikri reikalavimai
norint naudoti įrenginį lauke, pvz., licencijos ir suteikti ryšio
kanalai. Jei norite sužinoti, kokie apribojimai galioja norint
naudoti įrenginį lauke, kreipkitės į nacionalinę reguliavimo
instituciją arba „SMC Networks“.
[Maltese]
Dan it-tagħmir huwa LA
N transreciever mingħajr fili ta’ 2.4
GHz maħsub biex jintuża fuq ġewwa fi djar u uffiċċini
fil-pajjiżi notifikati tal-KE u
l-Istati Membri ta’ l-EFTA. B’mod konformi ma’ Artikolu 6.4
tad-Direttiva R&TTE 1999/5/KE l-Istati Membri tal-KE/EFTA
li ġejjin ġew notifikati: L-Awstrija, Il-Belġju, Id-Danimarka,
Il-Finlandja, Franza, Il-Ġermanja, L-Italja, Il-Lussemburgu,
L-Olanda, In-Norveġja, Spanja, L-Iżveżja, L-Iżvizzera, Ir-Renju
Unit, Il-Portugal, Il-Greċja, L-Irlanda, L-Islanda. Rekwiżiti għal
tħaddim fuq barra, bħal ħtiġijiet ta’ liċenzja u kanali permessi
għal tħaddim japplikaw f’ċertu pajjiżi. Jekk jogħġbok
ikkuntattja lill-awtorità regolarorja lokali jew SMC Networks
għal dettalji dwar restrizzjonijiet attwali dwar l-użu fuq barra.
[Hungarian]
Ez az eszköz egy 2,4 GHz-es vezeték nélküli LAN adó-vevő,
a
mely beltéri és irodai használatra készült, és az összes értesített
EC- és EFTA-tagországban használható. Az 1999/5/EC jelű
R&TTE előírás 6.4-es cikkének megfelelően a következő EC/
EFTA tagországok kaptak értesítést: Ausztria, Belgium, Dánia,
Finnország, Franciaország, Németország, Olaszország,
Luxemburg, Hollandia, Norvégia, Spanyolország, Svédország,
Svájc, Egyesült Királyság, Portugália, Görögország, Írország és
Izland. Egyes országokban külön előírások vonatkoznak a
kültéri használatra, például a licencre és az engedélyezett
csatornákra. A kültéri használatra vonatkozó aktuális
előírásokkal kapcsolatos részletekért forduljon a helyi
szabályozó hatósághoz vagy az SMC Networkshöz.
[Polish]
Niniejsze urzą
dzenie to urządzenie do odbierania i przesyłania
sygnału (transceiver) w bezprzewodowej sieci LAN o
częstotliwości 2,4 GHz, przeznaczone do użytku wewnątrz
pomieszczeń, w domach i biurach we wszystkich krajach
członkowskich UE i EFTA. Zgodnie z artykułem 6.4 dyrektywy
1999/5/EC dotyczącej norm dla urządzeń radiowych i
końcowych urządzeń teletransmisyjnych powiadomione zostały
następujące kraje członkowskie: Austria, Belgia, Dania,
Finlandia, Francja, Niemcy, Włochy, Luksemburg, Holandia,
Hiszpania, Szwecja, Szwajcaria, Wielka Brytania, Portugalia,
Grecja, Irlandia, Islandia. W niektórych krajach obowiązują
wymagania dotyczące działania na zewnątrz budynków, na
przykład wymagania licencyjne i dozwolone kanały pracy.
xii
Page 14
Szczegółowe informacje na temat obowiązujących ograniczeń
użytkowania zewnętrznego można uzyskać, kontaktując się z
lokalnym urzędem regulacji lub firmą SMC Networks.
[Portuguese]
Este dispositivo é um transreceptor de LAN sem fios de 2,4
GHz, destin
ado a uma utilização interior em casa e no
escritório, em todos os Estados membros notificados da CE e da
EFTA. De acordo com o artigo 6.4 da Directiva sobre R&TTE
1999/5/CE, foram notificados os seguintes Estados membros da
CE/EFTA: Áustria, Bélgica, Dinamarca, Finlândia, França,
Alemanha, Itália, Luxemburgo, Holanda, Noruega, Espanha,
Suécia, Suíça, Reino Unido, Portugal, Grécia, Irlanda, Islândia.
Os requisitos para uma utilização no exterior, tais como de
licença e de canais de funcionamento permitidos aplicam-se a
alguns países. Para obter informações sobre as restrições de
utilização no exterior, contacte a autoridade local competente ou
a SMC Networks.
[Slovenian]
Ta naprava je oddajno-sprejemna enota za brezžično lo
kalno
omrežje, namenjena uporabi na domu ali v pisarni v vseh
priglašenih državah članicah ES in EFTA. Skladno s členom 6.4
Direktive 1999/5/ES o radijski opremi in telekomunikacijski
terminalski opremi so bile obveščene naslednje države članice
ES/EFTA: Avstrija, Belgija, Danska, Finska, Francija, Nemčija,
Italija, Luksemburg, Nizozemska, Norveška, Španija, Švedska,
Švica, Velika Britanija, Portugalska, Grčija, Irska, Islandija. V
nekaterih državah veljajo zahteve za delovanje na prostem, kot
so zahteve za dovoljenje in dovoljeni kanali za delovanje. Če
potrebujete natančne informacije o trenutnih omejitvah uporabe
na prostem, se obrnite na lokalni regulativni organ ali družbo
SMC Networks.
[Slovak]
Toto zariadenie je prijímač
a vysielač pre bezdrôtové siete v
pásme 2,4 GHz a je určené na použitie v interiéroch domácností
a kancelárií vo všetkých členských štátoch ES a EZVO, ktorým
bol oznámený zámer uviesť zariadenie na trh. V súlade s čl. 6
odst. 4 smernice 1999/5/ES o rádiovom zariadení a koncových
telekomunikačných zariadeniach boli upovedomené nasledujúce
členské štáty ES/EZVO: Belgicko, Dánsko, Francúzsko, Fínsko,
Grécko, Holandsko, Island, Írsko, Luxembursko, Nemecko,
Nórsko, Portugalsko, Rakúsko, Španielsko, Švajčiarsko,
Švédsko, Taliansko, Veľká Británia. V niektorých štátoch sa na
prevádzku v exteriéroch vzťahujú určité požiadavky, napríklad
požiadavky na licenciu alebo požiadavky na prevádzkové
kanály. Podrobné informácie o aktuálnych obmedzeniach pri
prevádzke v exteriéroch vám poskytnú miestne regulačné
orgány alebo spoločnosť SMC Networks.
[Finnish]
Laite on 2,4 GHz:n langaton LAN-vastaanotin, joka on
tarkoitettu koti- ja toim
istokäyttöön kaikissa EY:n ja EFTAn
jäsenmaissa, joihin siitä on ilmoitettu. Radio- ja
telepäätelaitedirektiivin 1999/5/EY mukaisesti seuraaville
EY-/EFTA-maille on ilmoitettu: Itävalta, Belgia, Tanska, Suomi,
Ranska, Saksa, Italia, Luxemburg, Alankomaat, Norja, Espanja,
Ruotsi, Sveitsi, Iso-Britannia, Portugali, Kreikka, Irlanti ja
Islanti. Joissakin maissa ulkokäyttöä koskevat erilliset
xiii
Page 15
vaatimukset, kuten erikseen anottava lupa ja sallittujen kanavien
rajoittaminen. Ota yhteyttä paikalliseen käyttöä valvovaan
viranomaiseen tai SMC Networksiin, jos haluat lisätietoja
laitteen ulkokäytön rajoituksista.
[Swedish]
Apparaten är en 2,4 GHz trådlös LAN-mottagare för
inom
husbruk i hem och på kontor i alla underrättade EG- och
EFTA-medlemsstater. Enligt artikel 6.4 i R&TTE-direktivet
1999/5/EG är följande EG-/EFTA-stater underrättade:
Österrike, Belgien, Danmark, Finland, Frankrike, Tyskland,
Italien, Luxemburg, Nederländerna, Norge, Spanien, Sverige,
Schweiz, Storbritannien, Portugal, Grekland, Irland och Island.
I vissa länder tillkommer krav för utomhusbruk, t.ex. licenskrav
och tillåtna användarkanaler. Kontakta lokala
tillsynsmyndigheter eller SMC Networks för information om
aktuella bestämmelser för utomhusbruk.
[Icelandic]
Þessi búnaður er 2,4 GHz þráðlaust LAN sendiviðtæki til
notkunar innanhúss á hei
mili og skrifstofu í öllum tilkynntum
aðildarríkjum EB og EFTA. Í samræmi við grein 6.4 í R&TTE
tilskipuninni 1999/5/EB hefur eftirfarandi aðildarríkjum
EB/EFTA verið tilkynnt þar um: Austurríki, Belgía, Danmörk,
Finnland, Frakkland, Þýskaland, Ítalía, Lúxemborg, Holland,
Noregur, Spánn, Svíþjóð, Sviss, Bretland, Portúgal, Grikkland,
Írland, Ísland. Kröfur fyrir notkun utanhúss, svo sem kröfur um
leyfi og heimilaðar rásir eiga við í sumum löndum. Hafið
samband við reglugerðaryfirvöld á hverjum stað eða SMC
Networks til að fá upplýsingar um gildandi takmarkanir á
notkun utanhúss.
[Norwegian]
Denne enheten er en trådløs 2.4 GHz LAN-mottaker som er
beregnet for innendørs pri
vat- og kontorbruk i alle underrettede
EF- og EFTA-medlemsstater. I overensstemmelse med artikkel
6.4 i R&TTE-direktivet 1999/5/EF, har følgende EF-/
EFTA-medlemsstater blitt underrettet: Østerrike, Belgia,
Danmark, Finland, Frankrike, Tyskland, Italia, Luxembourg,
Nederland, Norge, Spania, Sverige, Sveits, Storbritannia,
Portugal, Hellas, Irland og Island. Krav for utendørsbruk, som
lisenskrav og tillatte brukskanaler, gjelder i noen land. Ta
kontakt med din lokale regulerende myndighet eller SMC
Networks for detaljert informasjon om gjeldende begrensninger
for utendørs bruk.
xiv
Page 16
Safety Compliance
Underwriters Laboratories Compliance Statement
Important! Before making connections, make sure you have the correct cord set. Check it (read the
label on the cable) against the followings:
Operating Voltage Cord Set Specifications
UL Listed/CSA certified Cord Set
Minimum 18AWG
Type SVT or SJT three conductor cord
Maximum length of 15 feet
120Volts
Parallel blade, grounding type attachment plug rated 15A, 125V
Cord Set with H05VV-F cord having three conductors with
minimum diameter of 0.75mm2
IEC-320 receptacle
240Volts(Europe only)
Male plug rated 10A,250V
The unit automatically matches the connected voltage. Therefore, no additional adjustments are
necessary when connecting it to any input voltage within the range marked on the power adapter.
xv
Page 17

Contents
1 Introduction ............................................................................................................................................................. 1
1.1 Packing List.............................................................................................................................................
1
1.2 Safety Precautions ...................................................................................................................................
1
1.3 LED and Interface
................................................................................................................................... 1
1.4 System Require
ments.............................................................................................................................. 3
1.5 Features ...................................................................................................................................................
3
2 Hardware Installa
tion ..............................................................................................................................................5
3 About the Web Configuration..................................................................................................................................
7
3.1 How to Access the Router .......................................................................................................................
7
3.2 Setup W
izard ...........................................................................................................................................8
3.3 Status .....................................................................................................................................................
15
3.3.1 Syste
m ...........................................................................................................................................15
3.3.2 LAN...............................................................................................................................................
16
3.3.3 WLAN
........................................................................................................................................... 16
3.3.4 WAN..............................................................................................................................................
17
3.3.5 Port Ma
pping................................................................................................................................. 17
3.3.6 Statistics.........................................................................................................................................
18
3.3.7 ARP Table......................................................................................................................................
19
3.4 LAN.......................................................................................................................................................
19
3.4.1 LAN Settings
.................................................................................................................................19
3.4.2 DHCP Settings
............................................................................................................................... 20
3.5 WLAN...................................................................................................................................................
24
3.5.1 Basic Se
ttings ................................................................................................................................24
3.5.2 Security..........................................................................................................................................
26
3.5.3 Advance Se
ttings........................................................................................................................... 27
3.5.4 Access Contr
ol ..............................................................................................................................28
3.5.5 WDS Settings
................................................................................................................................29
3.6 WAN......................................................................................................................................................
30
3.6.1 WAN Interfac
e............................................................................................................................... 30
3.6.2 ADSL Settings
............................................................................................................................... 35
3.7 Advanced...............................................................................................................................................
35
3.7.1 DNS
............................................................................................................................................... 35
3.7.2 Firewall..........................................................................................................................................
37
3.7.3 Virtual Server
................................................................................................................................ 39
3.7.4 Routing ..........................................................................................................................................
41
3.7.5 IP QoS
........................................................................................................................................... 43
3.7.6 Anti-DoS .......................................................................................................................................
45
3.7.7 Port Ma
pping................................................................................................................................. 45
xvi
Page 18

3.7.8 Other.............................................................................................................................................. 46
3.8 Admin....................................................................................................................................................
49
3.8.1 Remote Access ..............................................................................................................................
49
3.8.2 Commit/Reboot .............................................................................................................................
49
3.8.3 Password
........................................................................................................................................ 50
3.8.4 Backup/Res
tore ............................................................................................................................. 51
3.8.5 Upgrade Firm
ware......................................................................................................................... 52
3.8.6 Time Zone .....................................................................................................................................
52
3.8.7 Syste
m Log.................................................................................................................................... 53
3.8.8 SNMP ............................................................................................................................................
54
3.8.9 TR069............................................................................................................................................
55
3.8.10 ACL
............................................................................................................................................... 56
3.9 Diagnostic..............................................................................................................................................
56
3.9.1 Ping................................................................................................................................................
57
3.9.2 ATM Loopback..............................................................................................................................
57
3.9.3 ADSL.............................................................................................................................................
58
3.9.4 Diagnostic
...................................................................................................................................... 58
Appendix A ...................................................................................................................................................................
59
Appendix B ...................................................................................................................................................................
61
Appendix C ...................................................................................................................................................................
63
xvii
Page 19

1 Introduction
The SMC7904WBRB4 supports multiple line modes. It provides four 10/100 base-T Ethernet interfaces at the user
end. The device provides high-speed ADSL broadband connection to the Internet or Intranet for high-end users,
such as net bars and office users. The device provides high performance access to the Internet, downlink up to 24
Mbps and uplink up to 1 Mbps.
The device supports WLAN access, as WLAN AP or WLAN router
, to the Internet. It complies with IEEE 802.11,
802.11b/g specifications, and WEP, WPA and WPA2 security specifications.
1.1 Packing List
1 x SMC7904WBRB4
1
x power adapter
2
x telephone cables (RJ-11)
1 x
Ethernet cable (RJ-45)
1 x
Quick Installation Guide (QIG)
1 x
driver and utility software CD
1.2 Safety Precautions
Follow the following instructions to protect the device from risks and damage caused by fire or electric power:
U
se volume labels to mark the type of power.
Use
the power adapter that is packed within the device package.
Pay
attention to the power load of the outlet or prolonged lines. An overburden power outlet or damaged lines
and plugs may cause electric shock or fire accident. Check the power cords regularly. If you find any damage,
replace it at once.
Proper spa
ce left for heat dissipation is necessary to avoid any damage caused by overheating to the device.
The long and thin holes on the device are designed for heat dissipation to make sure the device works normally.
Do not cover these heat radiant holes.
Do not
put this device close to a place where a heat source exits or high temperature occurs. Avoid the device
from direct sunshine.
D
o not put this device close to a place where is over damp or watery. Do not spill any fluid on this device.
Do
not connect this device to any PC or electronic product, unless our customer engineer or your broadband
provider instructs you to do this, because any wrong connection may cause any power or fire risk.
Do
not place this device on an unstable surface or support.
1.3 LED and Interface
Front Panel
1
Page 20
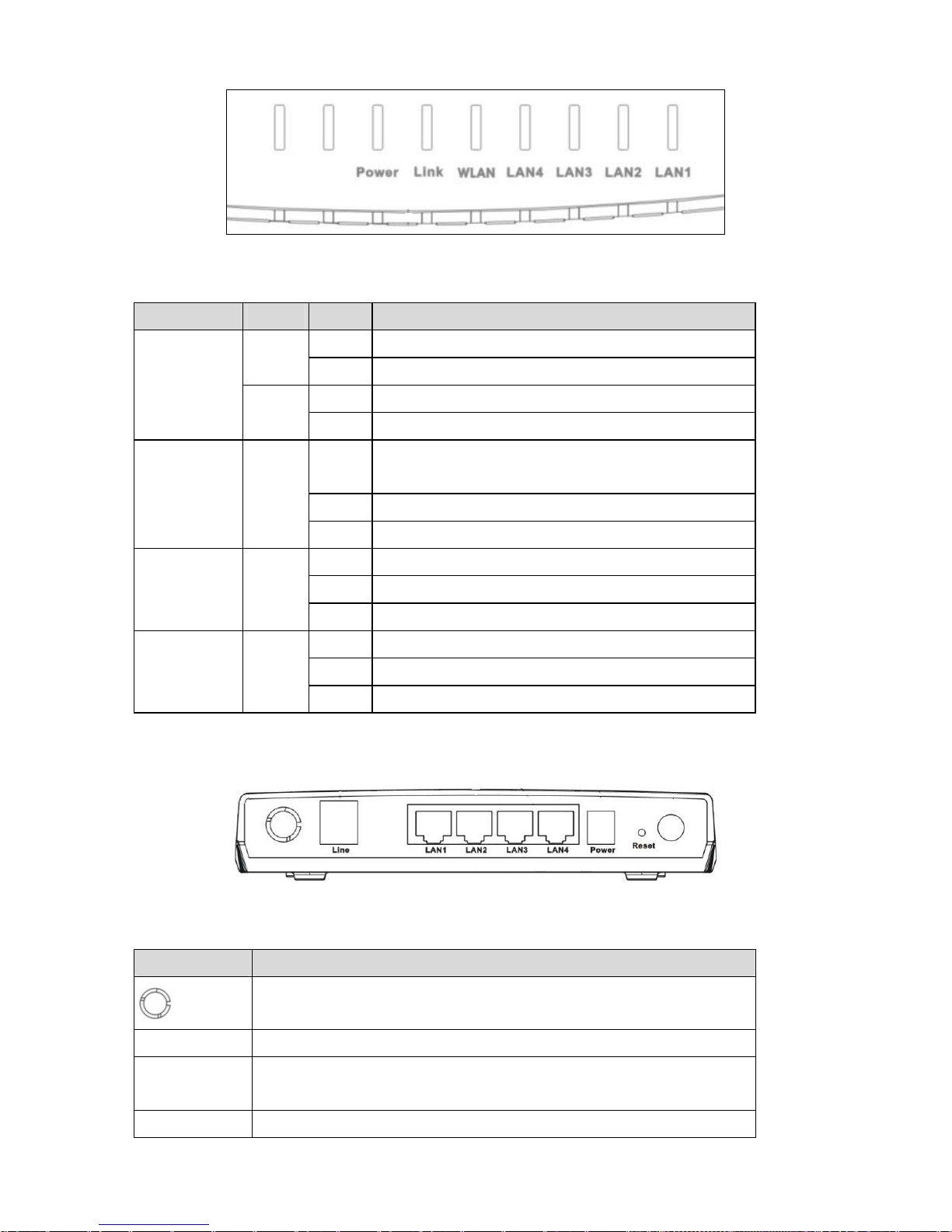
The following table describes the LEDs of the device:
LED Color Status Description
On The initialization of the device is successful. Green
Off The device is powered off.
On The device is self-testing or the self-testing is failed.
Power
Red
Blinks The software is upgrading.
On
Connection between the device and the physical layer of the office is
established.
Blinks The device is handshaking with the physical layer of the office.
Link
Blue
Off No signal is being detected.
On The WLAN connection is activated.
Blinks Data is being transmitted in the WLAN.
WLAN
Green
Off The WLAN connection is not activated.
On The LAN connection is established and activated.
Blinks Data is being transmitted in the LAN.
LAN4/LAN3/
LAN2/LAN1
Green
Off The LAN connection is not activated.
Rear Panel
The following table describes the interfaces of the device:
Interface Function
The wireless antenna interface.
Line RJ-11 interface, for connecting to the ADSL interface or a splitter through a telephone cable.
LAN1/LAN2/
LAN3/LAN4
RJ-45 interface, for connecting to the Ethernet interface of a PC or the Ethernet devices
through an Ethernet cable.
Power Power interface, for connecting to the power adapter of 12 V DC, 1 A.
2
Page 21
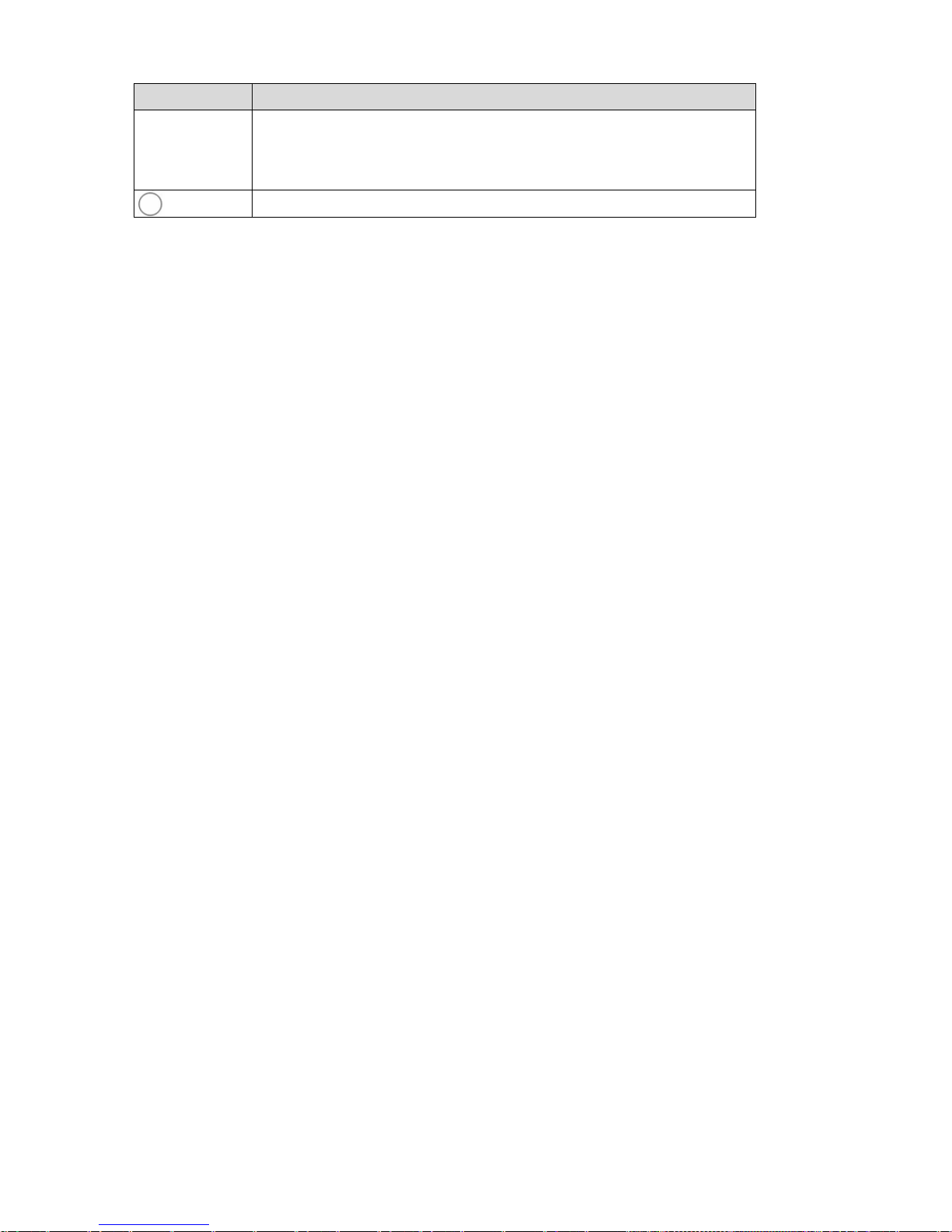
Interface Function
Reset
Reset to the factory default configuration. Keep the device powered on, and insert a needle
into the hole for 3 seconds, then release it. The deivce is reset to the factory default
configuration.
Power switch, power on or power off the device.
1.4 System Requirements
Recommended system requirements are as follows:
A
10/100 base-T Ethernet card is installed on your PC
A
hub or Switch (connected to several PCs through one of Ethernet interfaces on the device)
O
perating system: Windows Vista, Windows XP, Windows 2000, Windows ME, or Windows 98SE
Interne
t Explorer V5.0 or higher, Netscape V4.0 or higher, or Firefox 1.5 or higher
1.5 Features
The device supports the following features:
Com
patible with IEEE 802.11b/g standard
H
igh-speed wireless data transfer: up to 54 Mbps
Various line modes
Exter
nal PPPoE dial-up access
Internal PPPoE and PPPoA
dial-up access
Zero i
nstallation PPP bridge mode (ZIPB)
14
83 Briged, 1483 Routed, and MER access
Mul
tiple PVCs (up to eight) and these PVCs can be isolated from each other
A
single PVC with multiple sessions
Mul
tiple PVCs with multiple sessions
Bin
ding of ports with PVCs
80
2.1Q and 802.1P protocol
DHCP
server
NA
T and NAPT
S
tatic route
Firm
ware upgrade: Web, TFTP, and FTP
Reset
to factory defaults through the Reset button or Web
DNS relay
Vi
rtual server
DMZ
IP
address mapping
W
eb interface
3
Page 22

Telnet CLI
Syste
m status display
PPP
session PAP and CHAP
IP
filter
IP
QoS
Re
mote access control
Line
connection status test
Rem
ote management (Telnet and HTTP)
Back
up and restore of configuration file
Ether
net interface supports crossover detection, auto-correction and polarity correction
UPn
P
Note:
When upgrading firmware by TFTP, you can not access the Web GUI temporarily until the upgrading
procedure has been finished and the device is rebooted.
4
Page 23

2 Hardware Installation
Step 1 Connect the Line interface of the device to the MODEM interface of the splitter through a telephone cable.
Connect the phone to the PHONE interface of the splitter through a telephone cable. Connect the
incoming line to the LINE interface of the splitter.
The splitter has three interfaces:
LINE: C
onnect to a wall phone jack (RJ-11 jack).
MODEM:
Connect to the ADSL jack of the device.
PHONE: Co
nnect to a telephone set.
Step 2 Connec
t the LAN interface of the device to the network interface card (NIC) of the computer through an
Ethernet cable (MDI/MDIX).
I Note:
Use twisted-pair cables to connect with the hub or switch.
Step 3 Plug
one end of the power adapter to the wall outlet and connect the other end to the Power interface of
the device.
Connection 1
Figure 1 displays the application diagram for the connection of the router, computer, splitter and the telephone sets,
when no telephone set is placed before the splitter.
Figure 1 Con
nection diagram (Without connecting telephone sets before the splitter)
Connection 2
Figure 2 displays the connection when the splitter is installed close to the router.
5
Page 24
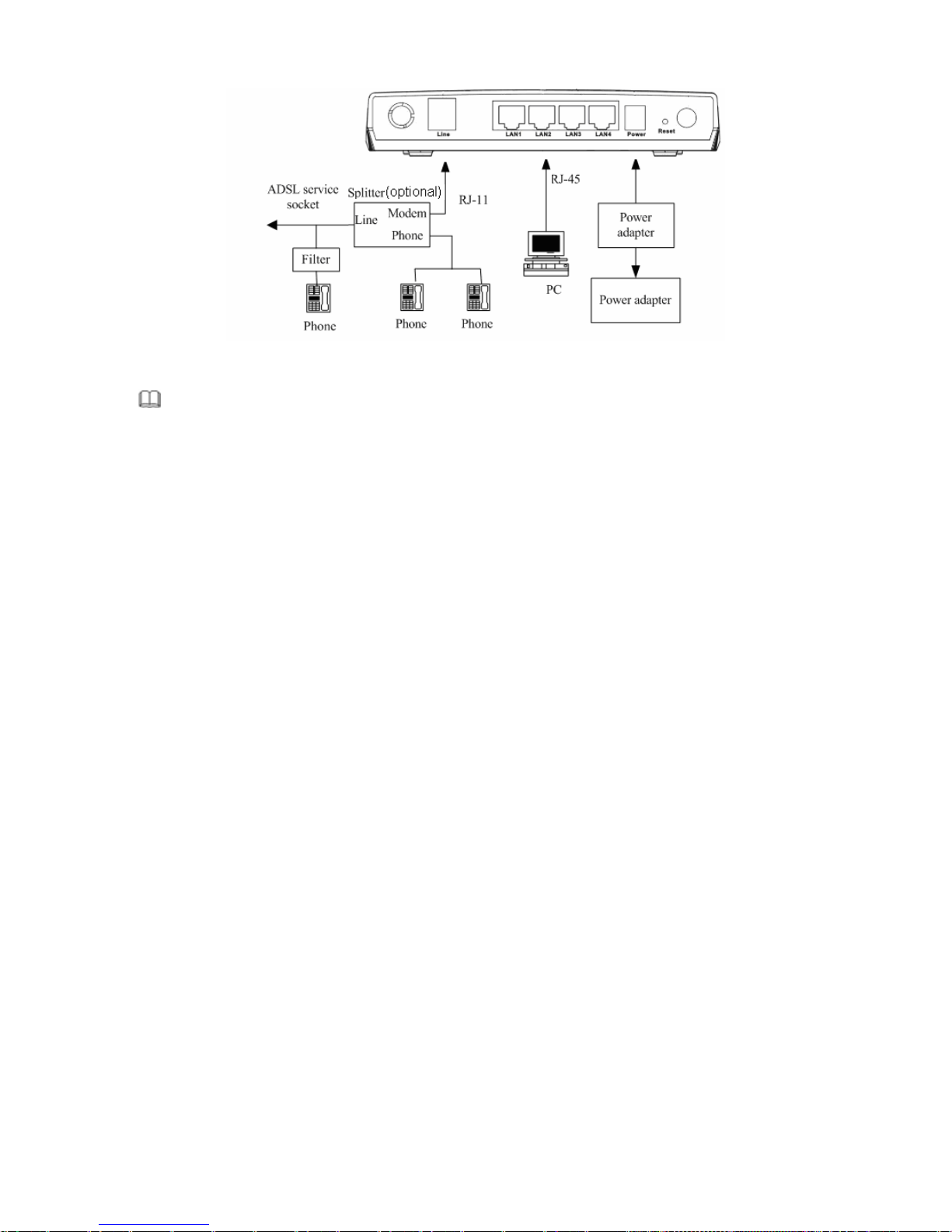
Figure 2 Con
nection diagram (Connecting a telephone set before the splitter)
Note:
When connection 2 is used, the filter must be installed close to the telephone cable. See Figure2. Do not use
the splitter to replace the filter.
Installing a telephone directly before the splitter may lead t
o failure of connection between the device and the
central office, or failure of Internet access, or slow connection speed. If you really need to add a telephone set
before the splitter, you must add a microfilter before a telephone set. Do not connect several telephones before the
splitter or connect several telephones with the microfilter.
6
Page 25
3 About the Web Configuration
This chapter describes how to configure the router by using the Web-based configuration utility.
3.1 How to Access the Router
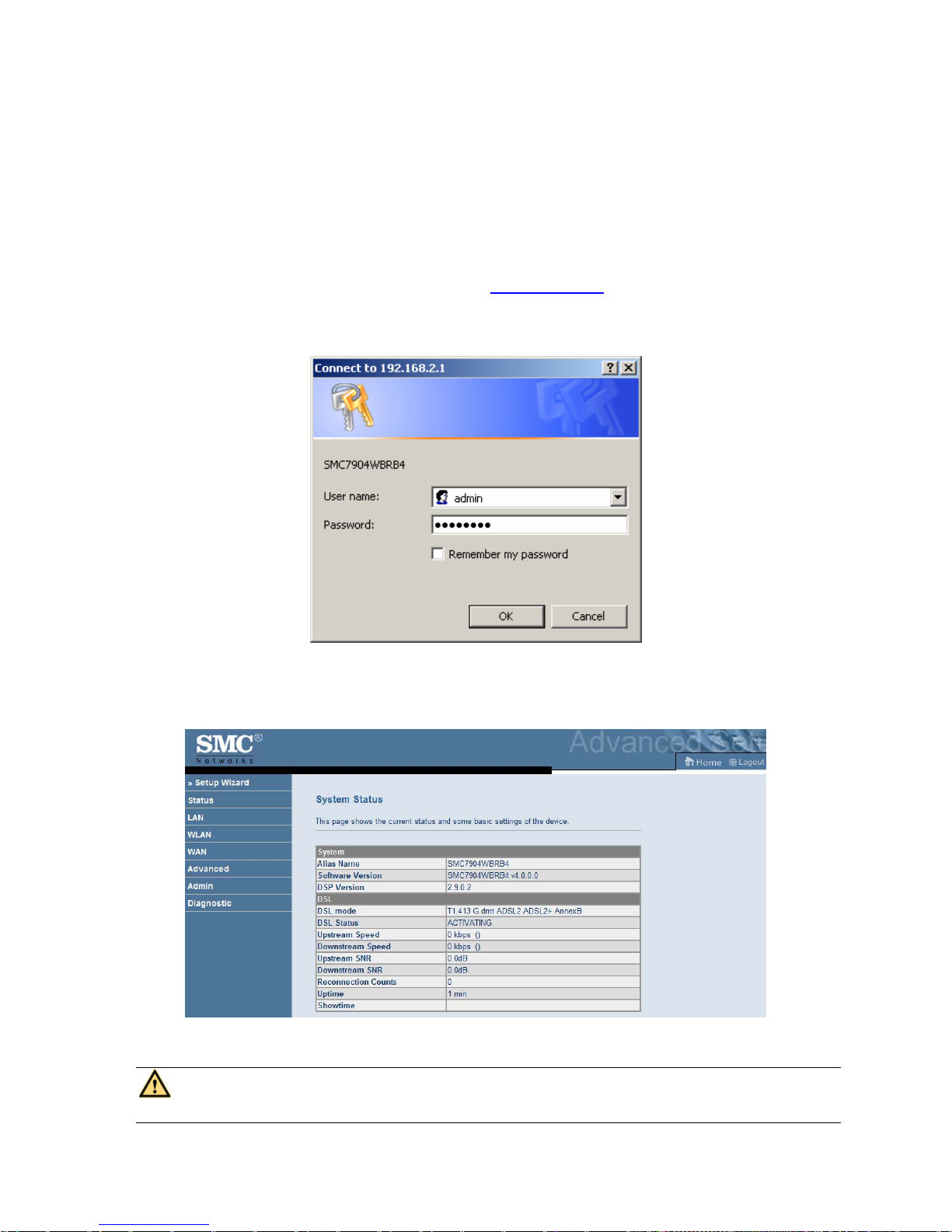
The following is the detailed description of accesing the router for the first time.
Step 1 Open the
Internet Explorer (IE) browser and enter http://192.168.2.1
.
Step 2 In the Lo
gin page that is displayed, enter the username and password.
The username and password of the super user are adm
in and smcadmin.
If you log in as the super user, the page as shown in the following figure appears. You can check, configure and
m
odify all the settings.
Caution:
If the device is not in use, power off the device.
7
Page 26
3.2 Setup Wizard
In the navigation bar, click Setup Wizard. In the Setup Wizard page, you can configure the VPI/VCI number.
The Setup Wizard page
guides fast and accurate configuration of the Internet connection and other important
parameters. The following sections describe these various configuration parameters. Whether you configure these
parameters or use the default ones, click NEXT to enable your Internet connection.
When subscribing to a broadband service, you should be aware of the method by which you are connected to the
Interne
t. Your physical WAN device can be either PPP, ADSL, or both. The technical information about the
properties of your Internet connection is provided by your Internet service provider (ISP). For example, your ISP
should inform you whether you are connected to the Internet using a static or dynamic IP address, and the protocol
that you use to communicate on the Internet.
Click NEX
T, and the page as shown in the following page appears. In this page, you can set the system time
manually or get the system time from the time server.
The following table describes the parameters in this page:
Field Description
Enable SNTP Client Update Select the checkbox to enable Simple Network Time Protocol (SNTP).
SNTP Server
After enabling SNTP, you can select the SNTP server from the drop-down
lis
t. You can also manually enter the server IP address.
Time Zone Select the time zone in which area you are from the drop-down list.
Click NEX
T, and the page as shown in the following page appears. In this page, you can configure the wireless
settings of the router.
8
Page 27
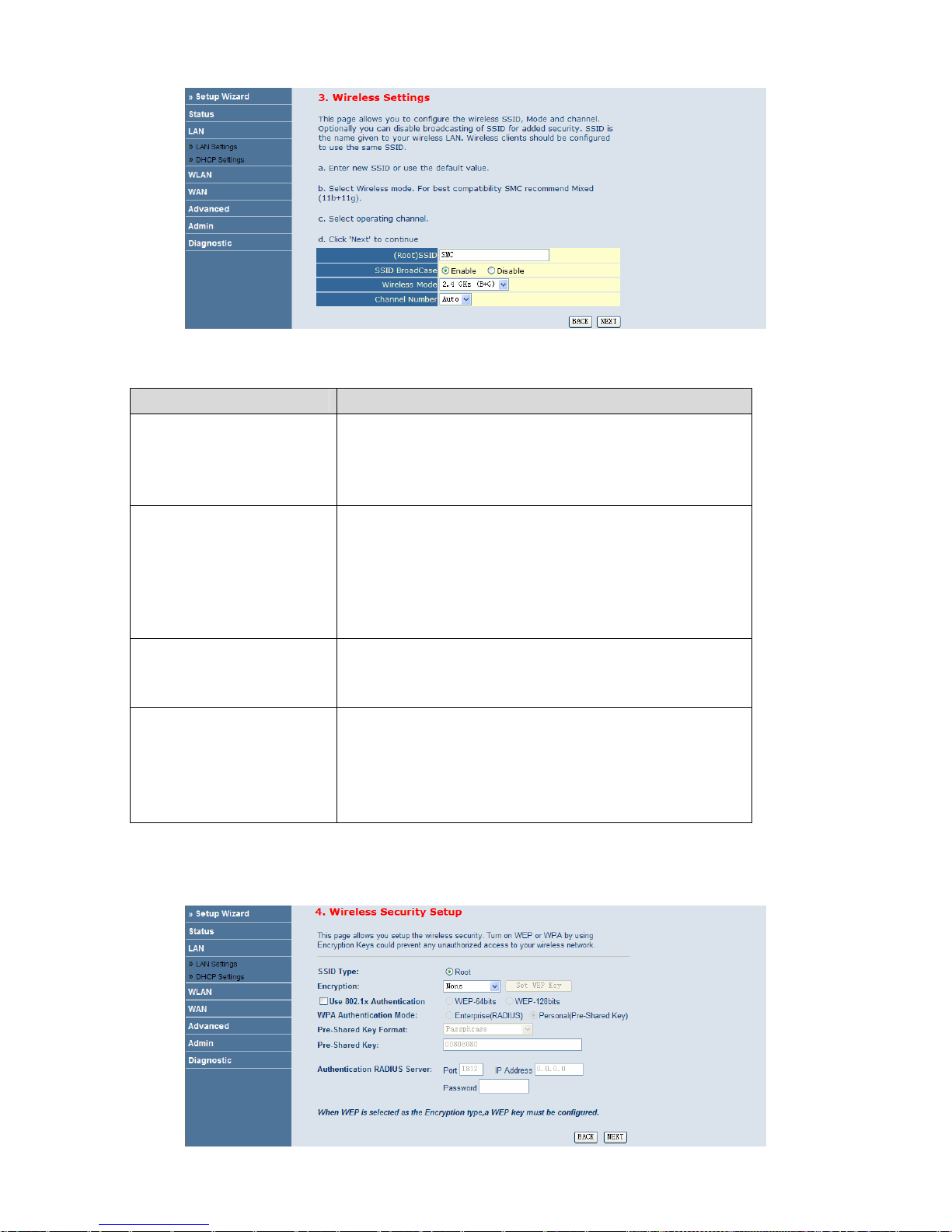
The following table describes the parameters in this page:
Field Description
(Root) SSID
The service set identification (SSID) is a unique name to identify the router
in the wireless LAN. Wireless stations associating to the router must have
the same SSID. Enter a descriptive name that is used when the wireless
client connecting to the router. By default, the SSID is SMC.
SSID BroadCase
Select whether the router broadcasts SSID or not. Y
ou can select Enable or
Disable.
Se
lect Enable, the wireless client searchs the router through
broadcasting SSID.
Se
lect Disable to hide SSID, the wireless clients can not search the
SSID.
Wireless Mode
Select the wireless working mode of the router
from the drop-down list.
You can select 2.4GHz (B), 2.4 GHz (G), 2.4 GHz (B+G). It is
recommended to select 2.4 GHz (B+G).
Channel Number
A channel is the radio frequency used b
y 802.11b/g wireless devices. There
are 11 channels (from 1 to 11) available, which depends on the
geographical area. You may have a choice of channels (for your region) and
you should use a different channel from an adjacent AP to reduce the
interference. Interference and degrading
After settings, click NEX
T. The page as shown in the following figure appears. In this page, you can configure the
wireless security parameters of the router.
9
Page 28

The following table describes the parameters in this page:
Field Description
Encryption
Select the wireless encryption mode. You can select None, WEP, WPA
(TKIP), WP A2 (AES) or WPA2 Mixed.
W
ired equivalent privacy (WEP) encrypts data frames before transmitting
over the wireless network.
W
i-Fi protected access (WPA) is a subset of the IEEE802.11i security
specification draft.
WP
A2 Mixed is the collection of WPA and WPA2 encryption modes. The
wireless client establishes the connection between the router through
WPA or WPA2.
Key differences between WPA and WEP are us
er authentication and improved
data encryption.
Set WEP Key
It is available when you set the encryption mode to WEP. Click it, the
Wireless WEP Key Setup page appears.
WPA Authentication Mode
Se
lect Personal (Pre-Shared Key), enter the pre-shared key in the
Pre-Shared Key field.
Se
lect Enterprise (RADIUS), enter the port, IP address, and password of
the Radius server. You need to enter the user name and password
provided by the Radius server when the wireless client connects to the
router.
If the encrypton is set to WEP,
the router uses 802.1 X authentication, which
is Radius authentication.
After settings, click NEXT. The page as shown in the following figure appears. In this page, you can configure the
ADSL settings.
The following table describes the parameters and buttons in this page:
Field
Description
Country Select the country in which you are in from the drop-down list.
Internet Service Provider Select your ISP from the drop-down list.
Protocol
Select the protocol. You can select PPPoE, PPPoA, 1483MER: DHCP,
1483MER: Static IP, 1483Bridge, or 1483 Routed.
10
Page 29

Connection Type
Select the connection type provided by your ISP from the drop-down list box.
Y
ou can choose LLC or VC-Mux.
VPI
VPI is the virtual path between two points in an
ATM network. Its valid value is
in the range of 0 to 255.
VCI
VCI is the virtual channel between two points
in an ATM network. Its valid value
is in the range of 32 to 65535. (0 to 31 is reserved for local management of ATM
traffic)
The procedure for configuring the ADSL settings of the router is as follows:
Step 1 Select the country where you are from the drop-down list.
Step 2 Sel
ect the corresponding ISP from the drop-down list.
After the selection, the protocol, connection type, VPI, VCI are displayed.
Step 3 Enter
the correction information for dial-up.
There are six protocols available: PPPoE, PPPoA, 14
83 MER: DHCP, 1483 MER: Static IP, 1483 Bridg ed, and
1483 Routed.
Select Be
lgium and Belgacom ISDN from the corresponding drop-down lists, and the page as shown in the
following figure appears.
PPPoE
In this example, select PPPoE as the protocol.
The following table describes the parameters in this page:
Field
Description
Protocol
There are six protocols available. In this example, PPPoE is th
e protocol for dial-up.
Connection Type
There are two connection types available: VC-Mux and LLC. In this example, LLC is
the connection type.
VPI
Virtual path identifier (VPI) is the virtual path
between two points in an ATM network.
Its valid value is in the range of 0 to 255. In this example, VPI is set to 0.
VCI Virtual channel identifier (VCI) is the virtual channel between two points in an ATM
11
Page 30

Description
Field
network. Its valid value is in the range of 32 to 65535 (0 to 31 is reserved for local
management of ATM traffic). In this example, VCI is set to 35.
User Name Enter the user name for PPPoE dial-up, which is provided by your ISP.
Password Enter the password for PPPoE dial-up, which is provided by your ISP.
Confirm Password Enter the password again.
PPPoA
Select PPPoA as the protocol, and the page as shown in the following figure appears.
For the parameters in this page, refer to the parameter description of PPPoE protocol.
1483 MER: DHCP
Select 1483 MER: DHCP as the protocol, and the page as shown in the following page appears.
12
Page 31

After entering correct VPI and VCI, DHCP automatically assigns the WAN IP address, gateway and DNS.
1483 MER: Static IP
Select 1483 MER: Static IP as the protocol, and the page as shown in the following page appears.
The following table describes the parameters in this page:
Field
Description
Protocol
There are six protocols available. In this example, 1483 MER: Static IP is the protocol
for dial-up.
Connection Type
There are two connection types available: VC-Mux and LLC. In this example, LLC is
the connection type.
VPI
Virtual path identifier (VPI) is the virtual path
between two points in an ATM network.
Its valid value is in the range of 0 to 255. In this example, VPI is set to 8.
VCI
Virtual channel identifier (VCI) is the virtu
al channel between two points in an ATM
network. Its valid value is in the range of 32 to 65535 (0 to 31 is reserved for local
management of ATM traffic). In this example, VCI is set to 35.
IP Address Enter the IP address for WAN connection, which is provided by your ISP.
Subnet Mask Enter the subnet mask of the WAN IP address, which is provided by your ISP.
Default Gateway Enter the default gateway, which is provided by your ISP.
Primary DNS Server Enter the DNS server, which is provided by your ISP.
1483 Bridged
Select 1483 Bridged as the protocol, and the page as shown in the following figure appears.
13
Page 32

1483 Routed
Select 1483 Routed as the protocol, and the page as shown in the following figure appears.
In this page, you need to enter the IP address of WAN connection, subnet mask, default gateway, and DNS server
w
hich are provided by your ISP.
For parameters in this page, refer to
the parameter description of 1483 MER: Static IP.
After setting, click NEXT, the page as shown in the following page appears.
14
Page 33

Click BACK t
o modify the settings.
Click FINISH to
take the settings into effect. Then you can check the configuration in the WAN page.
I Note:
After you select the country in which you are in and the correct ISP, the ADSL settings, such as protocol,
connection type, VPI, and VCI appear. It is recommended to keep the default values.
3.3 Status
In the navigation bar, click Status. In the Status page that is displayed contains: System, LAN, WLAN, WAN,
Port Mapping, Statistics, and ARP Table.
3.3.1 System
Choose Status > System. The page that is displayed shows the current status and some basic settings of the router,
including software version, DSL version, upstream speed, downstream speed, and uptime.
15
Page 34

3.3.2 LAN
Choose Status > LAN. The page that is displayed shows some basic LAN settings of the router. In the LAN page,
you can view the LAN IP address, DHCP server status, MAC address, and DHCP client table. If you want to
configure the LAN network, refer to Chapter 3.4.1 LAN Settings.
3.3.3 WLAN
Choose Status > WLAN. The page that is displayed shows some basic wireless LAN (WLAN) settings of the
router. In this page, you can view basic status of WLAN. If you want to configure the WAN network, refer to
chapter 3.5 WLAN.
16
Page 35

3.3.4 WAN
Choose Status > WAN. In the WAN page, you can view basic status of WAN, default gateway, DNS server. If you
want to configure the WAN network, refer to the chapter 3.6.1 WAN Interface.
3.3.5 Port Mapping
Choose Status > Port Mapping. In the Port Mapping page, you can view the mapping relation and the status of
port mapping.
17
Page 36

3.3.6 Statistics
Choose Status > Statistics. The Statistics page that is displayed contains Traffic Statistics and DSL Statistics.
3.3.6.1 Traffic Statistics
Click T raffic S t atistics, and the page as shown in the following figure appears. In this page, you can view statistics
of transmitted packets and received packets at each network interface.
3.3.6.2 DSL Statistics
Click DSL Statistics, and the page as shown in the following figure appears. In this page, you can view the ADSL
line statistics, downstream rate, upstream rate, and other information.
18
Page 37

3.3.7 ARP Table
Choose Status > ARP Table. In the ARP Table page, you can view MAC addresses of the router and the connected
devices.
3.4 LAN
In the navigation bar, click LAN. The LAN page that is displayed contains LAN Settings and DHCP Settings. In
this page, you can use the LAN configuration to define an IP address for the router and configure the DHCP server.
3.4.1 LAN Settings
Choose LAN > LAN Settings, and the page as shown in the following figure appears. In this page you can change
IP address of the router. The default IP address is 192.168.2.1, which is the private IP address of the router.
19
Page 38

By default, secondary IP is disabled. Enable secondary IP, and the page as shown in the following figure appears.
The following table describes the parameters in this page:
Field Description
IP Address
Enter the IP address of LAN interface. Its valid value is in the range of
192.168.2
.2 to 192.168.2.254. The default IP address is 192.168.2.1.
Subnet Mask
Enter the subnet mask of LAN interface. Its valid value is in the range of
255.255.0
.0 to 255.255.255.254.
Secondary IP
Select the checkbox to enable the secondary LAN IP. The two LAN IP address
must be in
the different network.
IGMP Snooping Enable or disable IGMP snooping.
3.4.2 DHCP Settings
Dynamic Host Configuration Protocol (DHCP) allows the individual computer to obain the TCP/IP configuration
from the centralized DHCP server. You can configure this router as a DHCP server or disable it. The DHCP server
can assign IP address, IP default gateway, and DNS server to DHCP clients. This router can also act as a surrogate
20
Page 39

DHCP server (DHCP proxy) where it relays IP address assignment from an actual real DHCP server to clients. You
can enable or disable DHCP server or DHCP proxy.
Chooose LA
N > DHCP Settings, and the page as shown in the following figure appears. There are three DHCP
modes available: Disable, DHCP Proxy, and DHCP Server. The following describes them respectively.
Disable
Select Disable in the DHCP Server Setup page, and the page as shown in the following figure appears.
DHCP Proxy
Select DHCP Proxy in the DHCP Server Setup page, and the page as shown in the following figure appears.
The following table describes the parameters in this page:
Field Description
DHCP Proxy
If set to DHCP Proxy, the router acts a surrogate DHCP server and relays the DHCP
requests and reponses between the remote server and the client.
DHCP Server Address Enter the DHCP server address provided by your ISP.
DHCP Server
Select DHCP Server in the DHCP Server Setup page, and the page as shown in the following figure appears.
21
Page 40

The following table describes the parameters in this page:
Field Description
DHCP Server
If set to DHC
P Server, the router can assign IP addresses, IP default gateway and
DNS servers to the hosts that are in Windows95, Windows NT and other systems that
support the DHCP client.
IP Pool Range It specifies the first and the last of contiguous IP address of the IP address pool.
Show Client
Click it, the Active DHCP Client Table page appears. It shows the assigned IP
address of the clients.
Max Lease Time
The lease time determines the period that the PC retains the assigned IP addresses
before
the IP addresses change.
Domain Name
Enter the domain name if you know. If you leave it blank, the domain name obtained
by DHCP from the ISP is used. You must enter host name (system name) on each
individual PC. The domain name can be assigned from the router through the DHCP
server.
Gateway Address Enter the IP default gateway of the IP address pool.
MAC-based Assignment
Click it, the Static IP Assignment Table page appears. You can assign the IP
addresses in the LAN to specific PCs based on their MAC address.
Click Show Client in the DHCP Server Setup page, and the page as shown in the following figure appears. In this
page, you can view the IP address assigned to each DHCP client.
22
Page 41

The following table describes the parameters and buttons in this page.
Field
Description
IP Address It displays the IP address of the DHCP leased client.
MAC Address
It displays the MAC address of the DHCP client (for example, computer).
Each Ethernet device has a unique MAC a
ddress. The MAC address is assigned
at the factory and it consists of six pairs of hexadecimal character. For example,
00-14-78-0c-f2-ce.
Time Expired (s)
It shows the lease time. The lease time determines the period that the PCs retain
the
assigned IP addresses before the IP addresses change.
Refresh Click it to refresh this page.
Close Click it to close this page.
Click MAC-based Assignment in the DHCP Server Setup page. The page as shown in the following figure
appears. In this page, you can assign the IP addresses in the LAN to the specific individual PCs based on their
MAC address.
The following table describes the parameters and buttons in this page:
Field Description
Host MAC Address Enter the MAC address of a PC in the LAN.
Assigned IP Address It specifies the IP address of the IP address pool.
Assign IP After entering the host MAC address and assigned IP address, click it. A row will
be added into the MAC-base Assignment Table.
23
Page 42

Field Description
Modify Assigned IP
Select a row in the M
AC-base Assignment Ta ble. The MAC address and IP
address appear. After modifying the MAC address and IP address, click it to save
the settings.
Delete Assigned IP
Select a row in the M
AC-base Assignment Ta ble, and click it. Then this row is
deleted.
Close Click it to close this page.
MAC-based Assignment Table It shows the assigned IP address based on the MAC address.
3.5 WLAN
In the navigation bar, click WLAN. The WLAN page that is displayed contains Basic Settings, Security, Advance
Settings, Access Control, and WDS Settings.
3.5.1 Basic Settings
Choose WLAN > Basic Settings, and the page as shown in the following figure appears. In this page, you can
configure the parameters for wireless LAN clients that may connect to your access point.
The following table describes the parameters and buttons in this page:
Field Description
Disable Wireless LAN
Interface
Select the checkbox, you can not configure the parameters in this page. Normally.
It is not selected.
Band
Select the working mode of the router. You can select 2.4 GHz (B), 2.4 GHz (G),
or 2.4 GHz (B+G). By defaut, the band is 2.4 GHz (B+G).
Mode
Select the WLAN mode of the router, which is varied according to the software.
Y
ou can select AP or AP+WDS. By defaut, the WLAN mode of the router is AP.
(Root) SSID
The service set identification (SSID) is a unique name to identify the router in the
wire
less LAN. Wireless stations associating to the router must have the same
SSID. Enter a desciptive name. By default, the SSID is SMC.
Set VSSID
Click it, the V
irtual SSID Setting page appears. In this page, you can enable up to
24
Page 43

Field Description
4 VSSIDs.
SSID Enable or disnable SSID.
Country/Area Select the country in which area you are from the drop-down list.
Channel Number
A channel is the radio frequency used b
y 802.11b/g wireless device. Channels
available depend on your geographical area. You may have a choice of channels
(for your region) and you should use a different channel from an adjacent AP to
reduce the interference. Interference and degrading performance occurs when
radio signal from diffirent APs overlap.
Select a channel from the drop-down list box.
Send Rate
Select the transmission rate of the wireless data.
You can select Auto
, 1 M, 2 M, 5.5 M, 11 M , 6 M, 9 M, 12 M, 18 M, 24 M, 36
M, 48 M, or 54 M.
Radio Power (mW)
Select the transmission power of the radio signal from the drop-down list. It is
recommended to
select the default value 100%.
Click Set VSSID, and the page as shown in the following figure appears.
The following table describes the parameters in this page:
Field Description
Enable Select the checkbox to enable virtual access point (VAP). You need to enable
VAP, if you want to configure the parameters in this page.
SSID The service set identification (SSID) is a unique name to identify the router in
the wireless LAN
Auth Type Select the authentication mode of the router from the drop-down list. You can
select Open System, Shared Key, or Auto.
In the open
system, the wireless client can directly connect to the router.
In th
e encryption authentication, the wireless client connects to the router
through the shared key.
25
Page 44

3.5.2 Security
Choose WLAN > Security, and the page as shown in the following figure appears. Wireless security is vital to
your network. It protects the wireless communication among the wireless stations, access points and the wireless
network.
The following table describes the parameters and button in this page:
Field Description
Encryption
Select the wireless encryption mode. You can select None, WEP, WPA (TKIP),
WPA2 (AES) or WPA2 Mixed.
W
ired equivalent privacy (WEP) encrypts data frames before transmitting
over the wireless network.
W
i-Fi protected access (WPA) is a subset of the IEEE802.11i security
specification draft.
WP
A2 Mixed is the collection of WPA and WPA2 encryption modes. The
wireless client establishes the connection between the router through WPA
or WPA2.
Key differences between WPA and WEP are user au
thentication and improved
data encryption.
Set WEP Key
It is available when you set the encryption mode to WEP. Click it, the Wireless
WEP Key Setup page appears.
Authentication RADIUS
Server
RADIUS is based on a client-server model that supports authentication,
authorization and accounting. The access point is client and the server is
RADIUS server. RADIUS is a simple package exchange in which your router
acts as a message relay between the wireless station and the network RADIUS
server.
Port
The default port of the RADIUS server for authentication is 1812. You need not
change
this value unless your network administrator instructs you to do so with
additional information.
IP Address Enter the IP address of the RADIUS server.
Password
Enter a password as the key to be shared between the external authentication
s
erver and the access point. The key is not send over the network. This key must
26
Page 45

Field Description
be the same on the external authentication server and your router.
Set the encryption mode to WEP
, and click Set WEP Key. The page as shown in the following figure appears.
The following table describes the parameters in this page:
Field Description
Key Length
Select the WEP key length. You can select 64-bit or 128-bit.
Key Format
If the
key length is set to 64-bit, you can select ASCII (5 characters) or
Hex (10 characters).
If the
key length is set to 128-bit, you can select ASCII (13 characters) or
Hex (26 characters).
Default Tx Key
Select the index of WEP Key. You can select Key 1
, Key 2, Key 3, or Key 4.
Encryption Key 1 to Key 4
The encryption keys are used to encrypt the data. Both the router and wireless
s
tations must use the same encryption key for data transmission.
If you select 64-bit and ASCII (5 characters), enter any 5 ASCII characters.
If y
ou select 64-bit and Hex (10 characters), enter any 10 hexadecimal
characters.
If y
ou select 128-bit and ASCII (13 characters), enter any 13 ASCII
characters.
If y
ou select 128-bit and Hex (26 characters), enter any 26 hexadecimal
characters.
3.5.3 Advance Settings
Choose WLAN > Advance Settings, and the page as shown in the following figure appears. In this page, you can
configure the wireless advanced parameters. It is recommended to keep the default values.
Note:
The parameters in the Wireless Advance Settings page are modified by the professional engineer, it is
recommended to keep the default values.
27
Page 46

The following table describes the parameters in this page:
Field Description
Fragment Threshold
This is the maximum data fragment size (between 256 and 2346bytes) that can be sent
in th
e wireless network before the router fragments the packet into smaller data frames.
RTS Threshold
Request to send (RTS) is designed to prev
ent collisions due to hidden node. A RTS
defines the biggest size data frame you can send before a RTS handshake invoked. The
RTS threshold value is between 0 and 2347.
If the RTS threshold value is greater than the fragment threshold value, the RTS
hankshake do no
t occur. Because the data frames are fragmented before they reach the
RTS size.
3.5.4 Access Control
Choose WLAN > Access Control, and the page as shown in the following figure appears. In this page, you can
configure the wireless access control of the wireless clients.
28
Page 47

The following table describes the parameters and buttons in this page:
Field Description
Select Access Control
Mode
You can select Disable,
Allow Listed, or Deny Listed from the drop-down list.
Select Allow Listed to enable the white list function. Only the clients whose
MAC address is listed in the Current Access Control List can access the router.
Se
lect Deny Listed to enable the black list function. The clients whose MAC
address is listed in the Current Access Control List are blocked to access the
router.
Apply Changes Click it to save the settings of selecting the access control mode.
MAC Addr
Enter the MAC address of the wireless station that are allowed or denied access to
y
our router in this address field.
Apply Changes Click it to save the settings of MAC address.
Reset Click it to refresh the MAC address.
Current Access Control
List
The MAC addresses in this table are allowed or denied to access to the router.
Delete
Click it to delete the row you select in the Cu
rrent Access Control List.
Delete All
Click it to delete all rows in the
Current Access Control List .
Reset
Click it to refresh the Cu
rrent Access Control List.
3.5.5 WDS Settings
Choose WLAN > WDS Settings, and the page as shown in the following figure appears.
29
Page 48

The following table describes the parameters and buttons in this page:
Field Description
Enable WDS Select the checkbox to enable WDS. You need to enable WDS, if you want to
configure the parameters in this page.
MAC Addr Enter the MAC address of the AP.
Comment Enter the comment to describe the AP of the MAC address.
Apply Change
Click it to add the MAC address and the comment into the Curr
ent WDS AP
List.
Reset Click it to refresh the MAC address and the comment.
Current WDS AP List This table shows all APs of the WDS.
Delete
Click it to delete the row you select in the Curr
ent WDS AP List.
Delete All
Click it to delete all rows in the Cu
rrent WDS AP List.
3.6 WAN
In the navigation bar, click WAN. The WAN page that is displayed contains WAN Interface and ADSL Settings.
3.6.1 WAN Interface
Choose WAN > WAN Interface, and the page as shown in the following figure appears. In this page, you can
configure WAN interface of your router.
30
Page 49

The following table describes the parameters in this page:
Field Description
Current ATM VC Table
This table shows the existed PVCs. It shows the
interface name, channel mode,
VPI/VCI, encapsulation mode, local IP address, remote IP address, and other
information. The maximum item of this table is eight.
Click it, the PP
P/Briged/IP Interface-Modify page appears. You can modify
the PVCs’ parameters.
VPI
VPI is the virtual path between two points in an ATM network. Its valid value
is in
the range of 0 to 255.
VCI
VCI is the virtual channel between two points in an ATM network. Its valid
value is
in the range of 32 to 65535. (0 to 31 is reserved for local management
of ATM traffic)
Encapsulation
You can select LL
C and VC-Mux.
Channel Mode
You can select 1
483 Bridged, 1483 MER, PPPoE, PPPoA, or 1483 Routed.
Admin Status
Select Disable, and then
this PVC is unusable.
Enable NAPT
Select the checkbox to enable the Network Address Port Translation (NAPT)
function of the router. If you do not select it and you want to access the
Internet normally, you must add a route on the uplink equipment. Otherwise,
the access to the Internet fails. Normally, it is required to enable NAPT.
PPP Settings
Login Name Enter the correct user name for PPP dial-up, which is provided by your ISP.
Password Enter the correct password for PPP dial-up, which is provided by your ISP.
Connection Type
You can select Continuou
s, Connect on Demand, or Manual.
Continuous: After dial-up is successful, PPP connection is always on-line,
no matter whether the data is being transmitted or not.
It is
recommended to select it.
Conne
ct on Demand: After dial-up is successful, within the preset idle
31
Page 50

Field Description
time, no data is being transmitted, the router automatically disconnects the
PPP connection.
In this case, you need to
enter the idle time.
M
anual: Select it, you need to dial up and disconnect the connection
mannually.
WAN IP Settings
Type
You can select Fi
xed IP or Use DHCP.
If you select Fixed IP, you need to enter the local IP address, remote IP
address and subnet mask.
If y
ou select Use DHCP, the router is a DHCP client, the WAN IP address
is assigned by the remote DHCP server.
Local IP Address Enter the IP address of WAN interface that is provided by your ISP.
Remote IP Address Enter the gateway IP address that is provided by your ISP.
Subnet Mask Enter the subnet mask of the local IP address.
Unnumbered Select this checkbox to enable the IP unnumbered function.
Default Route
Set the PVC for dail-up in the routing mode. You can select Disable or
Enable.
If you select En
able, only one PVC in the routing mode can dial up. Other
PVCs can not dial up.
By default, in the routing mode, it is enabled. In the bridged mode, it is
disabled.
Add
After configuring the parameters in this page, click it to add a new PVC into
the
Current ATM VC Tab le.
Modify
Select a PVC in the Current ATM VC Table, then modify the parameters of
this PVC. After setting, click it to apply the change of this PVC.
Delete
Select a PVC in the Current ATM VC Table, and then click it to delete this
PVC.
Undo Click it to refresh the page.
ATM Settings
Click it, the ATM Settngs page appears. You can configure the parameters of
the ATM for the router, including Qos type, PCR, CDVT, SCR and MBS.
Click
in the PPPoE mode, and the page as shown in the following figure appears. In this page, you can
configure parameters of this PPPoE PVC.
32
Page 51

The following table describes the parameters and buttons in this page:
Field Description
Protocol It displays the protocol type used for this WAN connection. In this
example, it is PPPoE.
ATM VCC It displays the ATM virtual circuit connection assigned for this PPP
interface (VPI/VCI).
Login Name The login name provided by your ISP.
Password The password provided by your ISP.
Authentication Method
You can select AUT
O, CHAP, or PAP.
Connection Type
You can select Continuou
s, Connect on Demand, or Manual.
Continuous: After dial-up is successful, PPP connection is always
on-line, no matter whether the data is being transmitted or not.
It is
recommended to select it.
Conne
ct on Demand: After dial-up is successful, within the preset
idle time, no data is being transmitted, the router automatically
disconnects the PPP connection.
In this case, you need to
enter the idle time.
M
anual: Select it, you need to dial up and disconnect the connection
mannually.
MTU Maximum transmission unit (MTU) is the largest size packet or frame,
specified in octets (eight-bit bytes), that can be sent in a packet- or
frame-based network such as the Internet. Transmission Control Protocol
of the Internet uses the MTU to determine the maximum size of each
packet in any transmission.
IP Address
You can select Dy
namic IP or Static IP.
If you select Dynamic IP, the IP address for PPPoE dail-up is
33
Page 52

Field Description
assaigned by DHCP.
If you select St a t i c I P, you need to manually enter the IP address for
PPPoE dail-up.
Bridge
You can select B
ridged Ethernet, Bridged PPPoE, or Disable Bridge.
AC-Name Enter the accessed equipment type.
Service-Name Enter the service name.
Apply Changes Click it to save the settings in this page.
Return
Click it to return to the W
AN Interface page.
Undo Click it to refresh this page.
Click A
TM Settings in the WAN Interface page, and the page as shown in the following figure appears. In this
page, you can configure the parameters of ATM, including QoS type, PCR, CDVT, SCR and MBS.
The following table describes the parameters in this page:
Field Description
VPI The virtual path identifier of the ATM PVC.
VCI The virtual channel identifier of the ATM PVC.
QoS
The QoS category of the PVC. You can select UBR, CBR
, rt-VBR, or
nrt-VBR.
PCR Peak cell rate (PCR) is the maximum rate at which cells can be transmitted
along a connection in the ATM network. Its value ranges from 0 to 6000.
CDVT Cell delay variation tolerance (CDVT) is the amount of delay permitted
between ATM cells (in microseconds). Its value ranges from 0 to
4294967295.
SCR Subtain cell rate (SCR) is the maximum rate that traffic can pass over a PVC
without the risk of cell loss. Its value ranges from 1 to 6000.
MBS Maximum burst size (MBS) is the maximum number of cells that can be
transmitted at the PCR. Its value ranges from 0 to 65535.
34
Page 53

3.6.2 ADSL Settings
Choose WAN > ADSL Settings, and the page as shown in the following figure appears. In this pae, you can select
the DSL modulation. Mostly, you need to keep this factory default configuration. The router supports these
modulations: G.Lite, G.dmt, T1.413, ADSL2, ADSL2+, and Annex B. The router negotiates the modulation
modes with the DSLAM.
3.7 Advanced
In the navigation bar, click Advanced. The Advanced page that is displayed contains DNS, Firewall, Virtual
Server, Routing, IP QoS, Anti-DoS, Port Mapping, and Other.
3.7.1 DNS
Choose Advanced > DNS. The DNS page that is displayed contains DNS Server and DDNS.
3.7.1.1 DNS Server
Domain name system (DNS) is an Internet service that translates the domain name into IP address. Because the
domain name is alphabetic, it is easier to remember. The Internet, however, is based on IP addresses. Every time
you use a domain name, a DNS service translates the name into the corresponding IP address. For example, the
domain name www.example.com might translate to 198.105.232.4. The DNS system has its own network. If one
DNS server does not know how to translate a particular domain name, it asks another one, and so on, until the
correct IP address is returned.
Click DNS Server, a
nd the page as shown in the following figure appears.
35
Page 54

The following table describes the parameters in this page:
Field Description
Obtain DNS Automatically
Select it, the router accepts the first received DNS assignment from one of the
PPPo
A, PPPoE or MER enabled PVC (s) during the connection establishment.
Set DNS Manually Select it, enter the primary and optional secondary DNS server IP addresses.
3.7.1.2 DDNS
Click DDNS, and the page as shown in the following figure appears. This page is used to configure dynamic DNS
address (DDNS) from DDNS provider. The device supports two providers: DynDNS.org and TZO.
The following table describes the parameters in this page:
Field Description
Enable Enable or disable DDNS.
DDNS provider
Select the DDNS provider name from the drop-down list. You can select DynDNS.org
or TZO.
36
Page 55

Field Description
Hostname Enter the DDNS identifier.
Interface Select the WAN interface of the router.
DynDns Settings
Username Enter the user name provided by DDNS provider.
Password Enter the password provided by DDNS provider.
TZO Settings
Email Enter the email provided by DDNS provider.
Key Enter the key provided by DDNS provider.
3.7.2 Firewall
Choose Advanced > Firewall. The Firewall page that is displayed contains IP/Port Fileter, MAC Filter, and
URL Blocking.
3.7.2.1 IP/Port Filter
Click IP/Port Filter, and the page as shown in the following figure appears. Entries in the table are used to restrict
certain types of data packets from your local network to the Internet through the gateway. IP/Port filter is helpful in
keeping the local network secure.
Click Add Rule to
add a new rule of IP/port filter into the Current Filter Table.
37
Page 56

3.7.2.2 MAC Filter
Click MAC Filter, and the page as shown in the following figure appears. Entries in the table are used to restrict
certain types of data packets from your local network to the Internet through the gateway. These filters are helpful
in keeping the local network secure.
Click Add Rule to
add a new rule of the MAC filter into the Current Filter Table.
3.7.2.3 URL Blocking
Click URL Blocking, and the page as shown in the following figure appears. This page is used to block a fully
qualified domain name (FQDN), such as tw.yahoo.comand and filtered keyword. You can add or delete FQDN and
filtered keyword.
38
Page 57

The following table describes the parameters and buttons in this page:
Field Description
URL Blocking
You can select Disabled or Enabled.
Se
lect Disabled indicates turning off URL blocking and keyword filtering.
Se
lect Enabled indicates blocking access to the URLs and keywords specified
in the URL Blocking Table and Keyword Filtering Table.
URL Blocking Table A list of the URL (s) to which access is blocked.
Keyword Enter the keyword for blocking.
Add Keyword
Click it to add the keyword to the URL
Blocking Table.
Delete Keyword
Select a row in the URL
Blocking Table and click it to delete the row.
Keyword Filtering Table A list of the keyword to which access is blocked.
3.7.3 Virtual Server
Choose Advanced > Virtual Server. The Virtual Server page that is displayed contains Services and DMZ
Settings.
3.7.3.1 Services
Click Services, and the page as shown in the following figure appears. In this page, you can configure the virtual
server. Other devices that connect to a specified server can access the virtual server through the gateway.
39
Page 58

Click Add to add a virtual server, and the page as shown in the following figure appears.
The following table describes the parameters in this page:
Field Description
Service Type
You can select the common service type, such as AUTH, DNS
, or FTP. You can
also define a service name.
If
you select the common service type, the corresponding WAN
communication port/service host communication port has the default
settings.
If
you define service type, you need to enter the corresponding port.
Protocol
Select the transport layer protocol that the service type uses. You can select
TCP/UDP,
TCP, or UDP.
WAN Port Enter the access port in the WAN.
Server Host Port Enter the port number of the specified service type.
Server IP Address
Enter the IP address of the virtual server. It is in the same network segment with
LAN IP
address of the router.
3.7.3.2 DMZ Settings
De-militarized military zone (DMZ) is used to provide Internet services without sacrificing unauthorized access to
the local network. Typically, the DMZ host can be a device accessible to Internet traffic, such as a Web (HTTP)
server, a FTP server, a SMTP (e-mail) server or a DNS server.
Click DMZ Settings, a
nd the page as shown in the following figure appears.
40
Page 59

The procedure for configuring DMZ is as follows:
Step 1 Select
Enable DMZ to enable DMZ.
Step 2 Enter the IP address of the DMZ host.
Step 3 Clic
k Apply Changes to save the settings in this page.
3.7.4 Routing
Choose Advanced > Routing. The Routing page that is displayed contains Static Route and RIP.
3.7.4.1 Static Route
Click Static Route, and the page as shown in the following figure appears. In this page, you can configure the
routing information. You can add or delete IP routes.
The following table describes the parameters and buttons in this page:
Field Description
Enable Select the checkbox to use static IP routes.
Destination Enter the IP address of the destination device.
Subnet Mask Enter the subnet mask of the destination device.
Next Hop Enter the IP address of the next hop in the IP route to the destination device.
Metric The metric cost for the destination.
Interface Select the interface for the specified route.
Add Route
Click it to add the new static route to the S
tatic Route Table.
41
Page 60

Field Description
Update
Select a row in the Static Route Table and modify the parameters. Then click it to save
the settings in this page .
Delete Selected
Select a row in the S
tatic Route Table and click it to delete the row.
Show Routes
Click it, the IP Route Table appears. You can view a list of destination routes commonly
accessed by your network.
Static Route Table A list of the previously configured static IP routes.
Click Show Routes, the table as shown in the following figure appears. The table shows a list of destination routes
commonly accessed by your network.
3.7.4.2 RIP
Click RIP, and the page as shown in the following figure appears. If the device is used as a RIP-enabled router to
communicate with other devices by using Routing Information Protocol (RIP), you need to enbale RIP. In this page,
you can configure the parameters of RIP, including the interface, receiving version, transmitting version.
The following table describes the parameters and buttons in this page:
Field Description
RIP
Select Enable,
the router communicates with other RIP-enabled devices.
Apply Changes Click it to save the settings in this page.
interface Select the interface of the router that uses RIP.
Receive Mode
Select the interface version that receives RIP messages. You can select None,
RIP1,
RIP2, or Both.
42
Page 61

Field Description
None indicates that the router does not receive RIP message.
RIP1 indicates
that the router receives RIP V1 messages.
RIP2 indicates
that the router receives RIP V2 messages.
Both i
ndicates that the router receives RIP V1 and RIP V2 messages.
Send Mode
Select the working mode for sending RIP
messages. You can select None, RIP1
RIP2, or RIP1 COMPAT.
RIP1 indicates
that the router broadcasts RIP1 messages only.
RIP2 indic
ates that the router multicasts RIP2 messages only.
Add
Click it to add a specified RIP interface to the RI
P Configuration Table.
Delete Selected Entry
Select a row in the RIP
Configuration Table and click it to delete the row.
RIP Configuration Table A list of the router interfaces that enble RIP.
3.7.5 IP QoS
Choose Advanced > IP QOS, and the page as shown in the following figure appears. Entries in this table are used
to assign the precedence for each incoming packet according to physical LAN port, TCP/UDP port number, source
IP address, destination IP address, and other information.
The procedure for configuring quality of service (QoS) is as follows:
Step 1 Enable IP
QoS and click Apply to enable IP QoS.
Step 2 Clic
k add rule to add a new IP QoS rule.
The page as shown in the following figure appears.
43
Page 62

The following table describes the parameters and buttons in this page:
Field Description
IP QoS Disable or enable QoS. By default, IP QoS is disabled. You need to enable IP QoS,
and then you can configure the parameters in this page.
Source IP Enter the IP address of the source data packet.
Source Netmask Enter the subnet mask of the source IP address.
Destination IP Enter the IP address of the destination data packet.
Destination Netmask Enter the subnet mask of the destination IP address.
Source Port Enter the port of the source data packet.
Destination Port Enter the port of the destination data packet.
Protocol
The protocol responds to the IP QoS rules. You can select TCP, UDP, or ICM
P.
Physical Port The LAN interface responds to the IP QoS rules, including four LAN interfaces, one
AP interface, and four VAP interfaces.
Outbound Priority The priority of the IP QoS rules. P0 is the highest priority and P3 is the lowest.
QoS Tag Select the checkbox to enable QoS tag.
IP Precedence Set the priority in the ToS of the IP data packet. The priority is in the range of 0 to 7.
IP ToS The type of IP ToS for classifying the data package
You can select Normal Service, Minimize Cost, Maximize Reliability, Maximize
Throughput, or Minimize Delay.
802.1p The priority is in the range of 0 to 7.
Delete Selected
Select a row in the IP
QoS Rules and click it to delete the row.
Delete All
Select all the rows in the IP QoS
Rules and click it to delete the rows.
44
Page 63

3.7.6 Anti-DoS
A "denial-of-service" (DoS) attack is an explicit attempt by hackers to prevent legitimate users of a service from
using that service.
Choose Advanced >
Anti-DoS, and the page as shown in the following figure appears. In this page, you can
prevent DoS attack.
3.7.7 Port Mapping
Choose Advanced > Port Mapping, and the page as shown in the following figure appears. In this page, you can
bind the WAN interface and the LAN interface into the same group.
45
Page 64

The procedure for operating a mapping group is as follows:
Step 1 Enab
le port mapping.
Step 2 Select
a group from the table.
Step 3 Select
the interfaces from the WAN and LAN and bind the required interfaces into an interface group by
clicking the arrow button.
Step 4 Clic
k Apply Changes to take the settings into effect.
Note:
The selected interfaces are removed from the original groups and added to a new group.
3.7.8 Other
Choose Advanced > Other. In the Other page that is displayed contains IGMP Proxy, UPnP, Bridge, and IP
PassThrough.
3.7.8.1 IGMP Proxy
Click IGMP Proxy, and the page as shown in the following figure appears. IGMP proxy enables the system to
issue IGMP host messages on behalf of hosts that the system discovered through standard IGMP interfaces. The
system acts as a proxy for its hosts after you enable it.
46
Page 65

3.7.8.2 UPnP
Click UPnP, and the page as shown in the following figure appears. This page is used to configure universal
plug-n-play (UPnP). The system acts as a daemon after you enable it.
3.7.8.3 Bridge
Click Bridge, and the page as shown in the following figure appears. This page is used to configure the bridge
parameters. In this page, you can change the settings or view some information on the bridge and its attached ports.
47
Page 66

The following table describes the parameters and button in this page:
Field Description
Aging Time If the host is idle for 300 seconds (default value), its entry is deleted from the
bridge table.
802.1d Spanning Tree
Disable or Enable 802.1d Spanning T
ree Protocol (STP). Select Enable to provide
path redundancy while preventing undesirable loops in your network.
Show MACs Click it to show a list of the learned MAC addresses for the bridge.
Click Sho
w MACs, and the page as shown in the following figure appears. This table shows a list of learned MAC
addresses for this bridge.
3.7.8.4 IP PassThrough
Click IP Pass Through, and the page as shown in the following figure appears. IP passthrough is also known as
ZIPB or IP extension. In this page, you can enable and configure IP passthrough.
48
Page 67

3.8 Admin
In the navigation bar, click Admin. The Admin page that is displayed contains Remote Access, Commit/Reboot,
Password, Backup/Restore, Upgrade Firmware, Time Zone, System Log, SNMP, TR069, and ACL.
3.8.1 Remote Access
Choose Admin > Remote Access, and the page as shown in the following figure appears. In this page, you can
enable or disable the services which are used by the remote host. For example, if TELNET service is enabled and
the port is 23, the remote host can access this router by telnet through the port 23.
3.8.2 Commit/Reboot
Choose Admin > Commit/Reboot, the page as shown in the following figure appears. In this page, you can reset
the router to the factory default configuration or save the current configuration.
49
Page 68

The following table describes the parameters in this page:
Field Description
reset to default settings
Select the checkbox to reset the router
to the factory default
configuration.
commit current settings Select the checkbox to save the current configuration.
Reboot After selecting, click it to reboot the router.
3.8.3 Password
Choose Admin > Password, and the page as shown in the following figure appears. In this page, you can modify
the password of the user, including admin and user. By default, the super user name and password are admin and
smcadmin respectively.
The following table describes the parameters in this page:
50
Page 69

Field Description
User Name
Select the user name for accessing the router. You can select admin or user
from the drop-down list.
Old Password
After selecting the user name, enter
the corresponding old password of the
user.
New Password Enter the password to which you want to change the old password.
Confirmed Password Enter the new password again.
3.8.4 Backup/Restore
Choose Admin > Backup/Restore, and the page as shown in the following figure appears. In this page, you can
back up the current configuration to a file and restore the configuration from the file that was saved previously.
Caution:
Do not turn off the router or press the Reset button while the procedure is in progress. Otherwise, it may
crash the system.
The following table describes the parameters and buttons in this page:
Field Description
Save Settings to File
Click Save to select the path for backup. Then you can save the configuration file
of the router.
Load Settings from File
Click Br
owse to select the configuration file.
Upload
After selecting the configuration file of the router, click it to start uploading the
configuration file
of the router.
51
Page 70

3.8.5 Upgrade Firmware
Choose Admin > Upgrade Firmware, and the page as shown in the following figure appears. In this page, you can
upgrade the firmware of the router.
Caution:
Do not turn off the router or press the Reset button while the procedure is in progress. Otherwise, it may
crash the system.
The following table describes the parameters and buttons in this page:
Field Description
Select File
Click Br
owse to select the firmware file.
Upload After selecting the firmware file, click it to starting upgrading the firmware file.
Reset Click it to start selecting the firmware file again.
3.8.6 Time Zone
Choose Admin > Time Zone, and the page as shown in the following figure appears. In this page, you can
manually set the system time or get the system time from the time server.
52
Page 71

The following table describes the parameters in this page:
Field Description
Time Mode
You can select Time Server or Manual.
Select Time Ser ver, the router gets the system time from the time server.
Select Manual, you need to manually configure the system time.
Enable SNTP Client Update Select the checkbox to enable Simple Network Time Protocol (SNTP).
SNTP Server
After enabling SNTP, you can select the SNTP
server from the drop-down list.
You can also manually enter the server IP address.
Time Zone Select the time zone in which area you are from the drop-down list.
3.8.7 System Log
Choose Admin > System Log, and the page as shown in the following figure appears. In this page, you can enable
or disable the system log function. You can also view the system log.
53
Page 72

3.8.8 SNMP
Choose Admin > SNMP, and the page as shown in the following figure appears. In this page, you can configure
the parameters of Simple Network Management Protocol (SNMP).
The following table describes the parameters and buttons in this page:
Field Description
Trap IP Address Enter the IP address of trap host. The trap information is sent to the host.
Community name (read-only)
The network administrators must use this password to read
the information of
this router.
Community name (write-only)
The network administrators must use this password to configure the
information of
the router.
54
Page 73

3.8.9 TR069
Choose Admin > TR069, and the page as shown in the following page appears. This page is used to configure
TR-069 customer premises equipment (CPE). In this page, you can configure the parameters of auto-configuration
server (ACS).
The following table describes the parameters and buttons in this page:
Field Description
ACS
URL The URL of the ACS to connect to.
User Name The user name for logging in to the ACS.
Password The password for logging in to the ACS.
Periodic Inform Enable
Select Enabled to periodically connect to the ACS to check for
configuration updates.
Periodic Inform Interval (s) Specify the amount of time between connections to ACS.
Connection Request
User Name The username to connect the router from the ACS.
Password The password to connect the router from the ACS.
Debug
ACS Certificates CPE Specify whether to check the ACS certification of the router.
Show Message
Select Enabled to display ACS SOAP messages on the serial
console.
CPE Sends GetRPC
Select Enabled,
the CPE contact the ACS to obtain configuration
55
Page 74

Field Description
updates.
Skip MReboot
Specify whether to send an MReboot event code in the inform
me
ssage.
Delay Specify whether to start the TR-069 program after a short delay.
Auto-Execution
Specify whether to automatically start the TR-069 after the router is
powered on
.
Ceretificate Management
CPE Certificate Password The certificate password of the router.
CPE Certificate
Click Br
owse to browse and upload the certificate for the router.
CA Certificate
Click Browse to browse and upload the CA certificate for the
router.
3.8.10 ACL
Choose Admin > ACL, and the page as shown in the following figure appears. In this page, you can configure the
IP address in the access control list. If access control list (ACL) is enabled, only the effective IP adresses in ACL
can access the ADSL router.
The procedure for configure ACL is as follows:
Step 1 Select
Enable and click take effect.
Step 2 Select the interface from the drop-down list and enter the IP address in the LAN.
Step 3 Clic
k Add to add the interface and IP address into the ACL List.
Step 4 Clic
k take effect to take the settings into effect.
I Note:
If you select Enable in ACL Capability, ensure that your host IP address is in ACL list before it takes effect.
3.9 Diagnostic
56
Page 75

In the navigation bar, click Diagnostic. The Diagnostic page that is displayed contains Ping, ATM Loopback,
ADSL, and Diagnostic.
3.9.1 Ping
Choose Diagnostic > Ping, and the page as shown in the following figure appears.
The following table describes the parameters and buttons in this page.
Field Description
Host Address Enter the IP address.
Send Click it to start to ping the host address.
3.9.2 ATM Loopback
Choose Diagnostic > A TM Loopback, and the page as shown in the following figure appears. In this page, you can
use VCC loopback to check the connectivity of the VCC. The ATM loopback test is useful for troubleshooting
problems with the DSLAM and ATM network.
57
Page 76

3.9.3 ADSL
Choose Diagnostic > ADSL, and the page as shown in the following figure appears. In this page, you can diagnose
the ADSL tone.
Click Go! to start diagnosing ADSL tone.
3.9.4 Diagnostic
Choose Diagnostic > Diagnostic, and the page as shown in the following figure appears. In this page, you can test
the ADSL connection. You can also view the LAN connection, WLAN connection, ADSL connection, and Internet
connection.
Click R
un Diagnostic Test to start testing.
58
Page 77

Appendix A
Questions & Answers
This section describes common problems you may encounter and possible solutions to them. The
Barricade can be easily monitored through panel indicators to identify problems.
1. Question: Why all LED indicators are off?
Answer:
z Check the connection between the power adaptor and the power socket
z Check the power switch is on or not
2. Question: Why LAN LED is not lighting?
Answer:
z Check the connection between the ADSL modem and your computer or Hub/Switch
z Check your PC or Hub/Switch running status and make sure them are working normally.
3. Question: Why Link LED is not lighting?
Answer: Check the connection between the ADSL “Line” port and the wall jack.
4. Question: Why cannot visit Internet with Link LED is on?
Answer: Make sure following information has been input correctly:
VPI/VCI
User/password.
5. Question: Why cannot open the Modem configuring Web page?
Answer:
Follow below steps to check the communication between the computer and Modem:
59
Page 78

Click start -> run (input ping demands)-> Ping 192.168.2.1 (MODEM IP address).
If cannot reach the modem, please check following configuration:
z The type of the network cable
z The connection between the modem and computer
z You computer’s TCP/IP configuration
6. Question: How to load the default setting after incorrect configuration?
Answer:
Press “reset” button 5s-10s to load the default configuration. The modem’s default IP address:
192.168.2.1/255.255.255.0,
Username/password: admin/smcadmin
60
Page 79

Appendix B
Technical Specifications
External Connectors
z 1 push power switch
z 1 DC power jack
z 1 factory reset button
z 4 LAN 10/100M Auto MDI/MDIX RJ45 ports
z 1 WAN RJ11 DSL port
Protocol Feature
Bridging/Routing
z RFC 1483 Bridge
z IEEE 802.1D transparent bridging
z RFC 1483 Router
z RIP V1 and V2 supported
z DHCP (RFC1541) server, relay
z Network Address Translation (NAT)
z DNS relay
z IGMP V1 and V2
Encapsulation
z RFC 1483 router/bridge
z PPPoA
z PPPoE
z MER
ADSL Feature
z Support Annex B
z Support ANSI T1.413 Issue2
z Support ITU G.992.1(G.dmt)
z Support ITU G.992.2 (G.lite)
z Support ITU G.992.3 ADSL2(G.dmt.bis)
z Support ITU G.992.4 ADSL2(G.lite.bis)
z Support ITU G.992.5 ADSL2plus
61
Page 80

Ethernet Feature
z Fully compliant with IEEE802.3/802.3u auto-negotiation function
z Support 10base-T, 100base-TX
z Support half duplex, full duplex
z Support back pressure flow control for half duplex, IEEE802.3x flow control for full duplex
z Support MDI/MDIX auto cross
Management Support
z Support Web/TFTP mode which use as native and long-distance edition upgrade
z Support test estate of circuitry connect (Diagnostics)
z Support Web interface setting
z Support Telnet CLI command line
z Support user setting the reset fuction: hardware resert or Web interface mode
z Support configuration files backup and resume function
z Support LAN port IP address amend function
z Support System log function
z Support SNMP V1/V2 native and long-distance control (MIB RFC1213/ADSL line MIB RFC Ⅱ
2662 ATM MIB RFC 2515)
z Support SNTP enactment
Security Support
z Support firewall function
z Support and sign electronically the function (prevent the different kind of editions from upgrading
each other)
z Support DoS (Denial of service) which detect and protect a number of attacks (such as
SYN/FIN/RST Flood, Smurf, WinNuke, Echo Scan, Xmas Tree Scan)
z Packet filter based on IP and port
z Access control based on MAC
z PAP, CHAP authentication
Environment
z Operating temperature: 0℃ to 40℃(32ºF to104ºF)
z Storage temperature: -20℃ to 70℃(-13ºF to131ºF)
z Operating humidity: 10%~85% Non-Condensing
z Storage humidity: 5%~95% Non-Condensing
z External adapter spec: Input: AC220V, 50Hz. Output:12 V DC, 1000 mA(min)
z Dissipation: 7W (max)
62
Page 81

Appendix C
GPL Anouncement
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it
is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By
contrast, the GNU General Public License is intended to guarantee your freedom to share and change
free software--to make sure the software is free for all its users. This General Public License applies to
most of the Free Software Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by the GNU Lesser General Public
License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses
are designed to make sure that you have the freedom to distribute copies of free software (and charge
for this service if you wish), that you receive source code or can get it if you want it, that you can
change the software or use pieces of it in new free programs; and that you know you can do these
things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to
ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the
recipients all the rights that you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license which
gives you legal permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone understands that
there is no warranty for this free software. If the software is modified by someone else and passed on,
we want its recipients to know that what they have is not the original, so that any problems introduced
by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger
that redistributors of a free program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any patent must be licensed for
everyone's free use or not licensed at all.
63
Page 82

The precise terms and conditions for copying, distribution and modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work which contains a notice placed by the copyright
holder saying it may be distributed under the terms of this General Public License. The "Program",
below, refers to any such program or work, and a "work based on the Program" means either the
Program or any derivative work under copyright law: that is to say, a work containing the Program or a
portion of it, either verbatim or with modifications and/or translated into another language.
(Hereinafter, translation is included without limitation in the term "modification".) Each licensee is
addressed as "you".
Activities other than copying, distribution and modification are not covered by this License; they are
outside its scope. The act of running the Program is not restricted, and the output from the Program is
covered only if its contents constitute a work based on the Program (independent of having been made
by running the Program). Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any
medium, provided that you conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the notices that refer to this License and to
the absence of any warranty; and give any other recipients of the Program a copy of this License along
with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer
warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work based
on the Program, and copy and distribute such modifications or work under the terms of Section 1
above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files and
the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is
derived from the Program or any part thereof, to be licensed as a whole at no charge to all third parties
under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it, when
started running for such interactive use in the most ordinary way, to print or display an announcement
including an appropriate copyright notice and a notice that there is no warranty (or else, saying that
you provide a warranty) and that users may redistribute the program under these conditions, and telling
the user how to view a copy of this License. (Exception: if the Program itself is interactive but does not
normally print such an announcement, your work based on the Program is not required to print an
announcement.)
64
Page 83

These requirements apply to the modified work as a whole. If identifiable sections of that work are not
derived from the Program, and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those sections when you distribute them as
separate works. But when you distribute the same sections as part of a whole which is a work based on
the Program, the distribution of the whole must be on the terms of this License, whose permissions for
other licensees extend to the entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by
you; rather, the intent is to exercise the right to control the distribution of derivative or collective
works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with a
work based on the Program) on a volume of a storage or distribution medium does not bring the other
work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code or
executable form under the terms of Sections 1 and 2 above provided that you also do one of the
following:
a) Accompany it with the complete corresponding machine-readable source code, which must be
distributed under the terms of Sections 1 and 2 above on a medium customarily used for software
interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge
no more than your cost of physically performing source distribution, a complete machine-readable
copy of the corresponding source code, to be distributed under the terms of Sections 1 and 2 above on
a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding source
code. (This alternative is allowed only for noncommercial distribution and only if you received the
program in object code or executable form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it. For
an executable work, complete source code means all the source code for all modules it contains, plus
any associated interface definition files, plus the scripts used to control compilation and installation of
the executable. However, as a special exception, the source code distributed need not include anything
that is normally distributed (in either source or binary form) with the major components (compiler,
kernel, and so on) of the operating system on which the executable runs, unless that component itself
accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated place,
then offering equivalent access to copy the source code from the same place counts as distribution of
the source code, even though third parties are not compelled to copy the source along with the object
code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided under
65
Page 84

this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program is void, and
will automatically terminate your rights under this License. However, parties who have received
copies, or rights, from you under this License will not have their licenses terminated so long as such
parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else
grants you permission to modify or distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by modifying or distributing the
Program (or any work based on the Program), you indicate your acceptance of this License to do so,
and all its terms and conditions for copying, distributing or modifying the Program or works based on
it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient
automatically receives a license from the original licensor to copy, distribute or modify the Program
subject to these terms and conditions. You may not impose any further restrictions on the recipients'
exercise of the rights granted herein. You are not responsible for enforcing compliance by third parties
to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason
(not limited to patent issues), conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not excuse you from the conditions of
this License. If you cannot distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you may not distribute the Program
at all. For example, if a patent license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then the only way you could satisfy
both it and this License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the
balance of the section is intended to apply and the section as a whole is intended to apply in other
circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims
or to contest validity of any such claims; this section has the sole purpose of protecting the integrity of
the free software distribution system, which is implemented by public license practices. Many people
have made generous contributions to the wide range of software distributed through that system in
reliance on consistent application of that system; it is up to the author/donor to decide if he or she is
willing to distribute software through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of
this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or by
copyrighted interfaces, the original copyright holder who places the Program under this License may
add an explicit geographical distribution limitation excluding those countries, so that distribution is
permitted only in or among countries not thus excluded. In such case, this License incorporates the
limitation as if written in the body of this License.
66
Page 85

9. The Free Software Foundation may publish revised and/or new versions of the General Public
License from time to time. Such new versions will be similar in spirit to the present version, but may
differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of
this License which applies to it and "any later version", you have the option of following the terms and
conditions either of that version or of any later version published by the Free Software Foundation. If
the Program does not specify a version number of this License, you may choose any version ever
published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution
conditions are different, write to the author to ask for permission. For software which is copyrighted by
the Free Software Foundation, write to the Free Software Foundation; we sometimes make exceptions
for this. Our decision will be guided by the two goals of preserving the free status of all derivatives of
our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM "AS IS" WITHOUT
WARRANTY OF ANY KIND, EITHER EXPRESSED
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF
ALL NECESSARY SERVICING,
67
Page 86

REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR
DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES
ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING
BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the best
way to achieve this is to make it free software which everyone can redistribute and change under these
terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each
source file to most effectively convey the exclusion of warranty; and each file should have at least the
"copyright" line and a pointer to where the full notice is found.
<one line to give the program's name and a brief idea of what it does.> Copyright (C) <year> <name of
author>
This program is free software; you can redistribute it and/or modify it under the terms of the GNU
General Public License as published by the Free Software Foundation; either version 2 of the License,
or (at your option) any later version.
This program is distributed in the hope that it will be useful, but
WITHOUT ANY WARRANTY;
without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR
PURPOSE.
See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not, write
to the Free Software Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
This is free software, and you are welcome to redistribute it under certain conditions; type `show c' for
details.
68
Page 87

The hypothetical commands `show w' and `show c' should show the appropriate parts of the General
Public License. Of course, the commands you use may be called something other than `show w' and
`show c'; they could even be mouse-clicks or menu items--whatever suits your program.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a
"copyright disclaimer" for the program, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision' (which makes passes at compilers) written by James Hacker.
<signature of Ty Coon>, 1 April 1989 Ty Coon, President of Vice
This General Public License does not permit incorporating your program into proprietary programs. If
your program is a subroutine library, you may consider it more useful to permit linking proprietary
applications with the library. If this is what you want to do, use the GNU Lesser General Public
License instead of this License.
69
Page 88

SMC7904WBRB4
 Loading...
Loading...