
Installation and Operations
Guide
AirLink Connection Manager
4119855
Rev 3

ACM Installation and Operations Guide
Important
Notice
Limitation of
Liability
Due to the nature of wireless communications, transmission and reception of data
can never be guaranteed. Data may be delayed, corrupted (i.e., have errors) or be
totally lost. Although significant delays or losses of data are rare when wireless
devices such as the Sierra Wireless modem are used in a normal manner with a
well-constructed network, the Sierra Wireless modem should not be used in
situations where failure to transmit or receive data could result in damage of any
kind to the user or any other party, including but not limited to personal injury,
death, or loss of property. Sierra Wireless accepts no responsibility for damages
of any kind resulting from delays or errors in data transmitted or received using
the Sierra Wireless modem, or for failure of the Sierra Wireless modem to
transmit or receive such data.
The information in this manual is subject to change without notice and does not
represent a commitment on the part of Sierra Wireless. SIERRA WIRELESS AND
ITS AFFILIATES SPECIFICALLY DISCLAIM LIABILITY FOR ANY AND ALL
DIRECT, INDIRECT, SPECIAL, GENERAL, INCIDENTAL, CONSEQUENTIAL,
PUNITIVE OR EXEMPLARY DAMAGES INCLUDING, BUT NOT LIMITED TO,
LOSS OF PROFITS OR REVENUE OR ANTICIPATED PROFITS OR REVENUE
ARISING OUT OF THE USE OR INABILITY TO USE ANY SIERRA WIRELESS
PRODUCT, EVEN IF SIERRA WIRELESS AND/OR ITS AFFILIATES HAS BEEN
ADVISED OF THE POSSIBILITY OF SUCH DAMAGES OR THEY ARE
FORESEEABLE OR FOR CLAIMS BY ANY THIRD PARTY.
Notwithstanding the foregoing, in no event shall Sierra Wireless and/or its
affiliates aggregate liability arising under or in connection with the Sierra Wireless
product, regardless of the number of events, occurrences, or claims giving rise to
liability, be in excess of the price paid by the purchaser for the Sierra Wireless
product.
Patents This product may contain technology developed by or for Sierra Wireless Inc. This
product includes technology licensed from QUALCOMM
manufactured or sold by Sierra Wireless Inc. or its affiliates under one or more
patents licensed from MMP Portfolio Licensing.
®
. This product is
Copyright © 2017 Sierra Wireless. All rights reserved.
Trademarks Sierra Wireless
are registered trademarks of Sierra Wireless.
Windows
Corporation.
QUALCOMM
under license.
Other trademarks are the property of their respective owners.
Rev 3 Nov 17 2 4119855
®
, AirPrime®, AirLink®, AirVantage® and the Sierra Wireless logo
®
and Windows Vista® are registered trademarks of Microsoft
®
is a registered trademark of QUALCOMM Incorporated. Used
Contact
Information
Revision
History
Sales information and technical
support, including warranty and returns
Corporate and product information Web: sierrawireless.com
Web: sierrawireless.com/company/contact-us/
Global toll-free number: 1-877-687-7795
6:00 am to 5:00 pm PST
Preface
Revision
number
1 September 2016 • Document created
2 May 2017 • Added FIPS content
3 November 2017 • Added important notice to change password
Release date Changes
Rev 3 Nov 17 3 4119855

Contents
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Who Should Read This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
What is the AirLink Connection Manager (ACM)? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
FIPS-Compliant ACM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8
NCP Client for Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8
Supported AirLink Gateways and Routers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Physical Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9
Environmental Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Mounting Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Connecting the ACM to Your Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .9
Ethernet Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .10
Connecting to the ACM from an Inside Device. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Configuration Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Logging In and Out. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Change to Configuration Mode. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
Configuration Tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Manage Configuration Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13
Add or Modify Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .14
Delete Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Show Uncommitted Attribute Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .15
Discard Uncommitted Attribute Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16
Apply Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Save Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .17
Restore Default Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .18
Basic Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Admin Password. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Rev 3 Nov 17 4 4119855

Contents
Host Name. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Domain Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
OUTSIDE Interface IP Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Default Gateway . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
INSIDE Interface IP Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
INSIDE Routing Information IP Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
DNS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
ACM VPN Configuration. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
VPN Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
IPsec VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
ACM IKE/ESP Negotiation Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
IKE Group Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
ESP Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
VPN Peers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Certificate Management and Revocation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Configuring for NCP Client for Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Assigning a Virtual IP Address from the Pool . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
EAP Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
ACM Server Protocols. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Virtual Router Redundancy Protocol (VRRP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
AirLink oMG/MG90 Router Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
oMG/MG90 IKE/ESP Negotiation Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
AirLink Gateway/Router Support—LS, ES, GX, MP Series . . . . . . . . . . . . . . . . . . . . 38
ACM/AirLink (LS, ES, GX, MP Series) Setup Requirements . . . . . . . . . . . . . . . . . 39
‘Single Address’ Type for Host2LAN Connection . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Main/Aggressive Mode Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
NCP Client for Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
NCP Client/ACM Setup Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Upgrading to ACM 1.6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
Rev 3 Nov 17 5 4119855

ACM Installation and Operations Guide
View VPN Configuration Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
IKE Process Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44
IKE Security Associations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
IPsec Process Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45
IPsec Security Associations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
IPsec IP Pool Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
Debug Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
View VRRP Configuration Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
Dead Peer Detection is not Working . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
vpn ipsec ‘lifetime’ Command is Not Available . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
VPN Tunnel Establishes with Mismatched IKE Group. . . . . . . . . . . . . . . . . . . . . . . . . 50
NCP Certificate Authentication Failed—“No trusted RSA public key”. . . . . . . . . . . . . 51
Basic Configuration Requirements. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
RADIUS Server Settings. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Rev 3 Nov 17 6 4119855
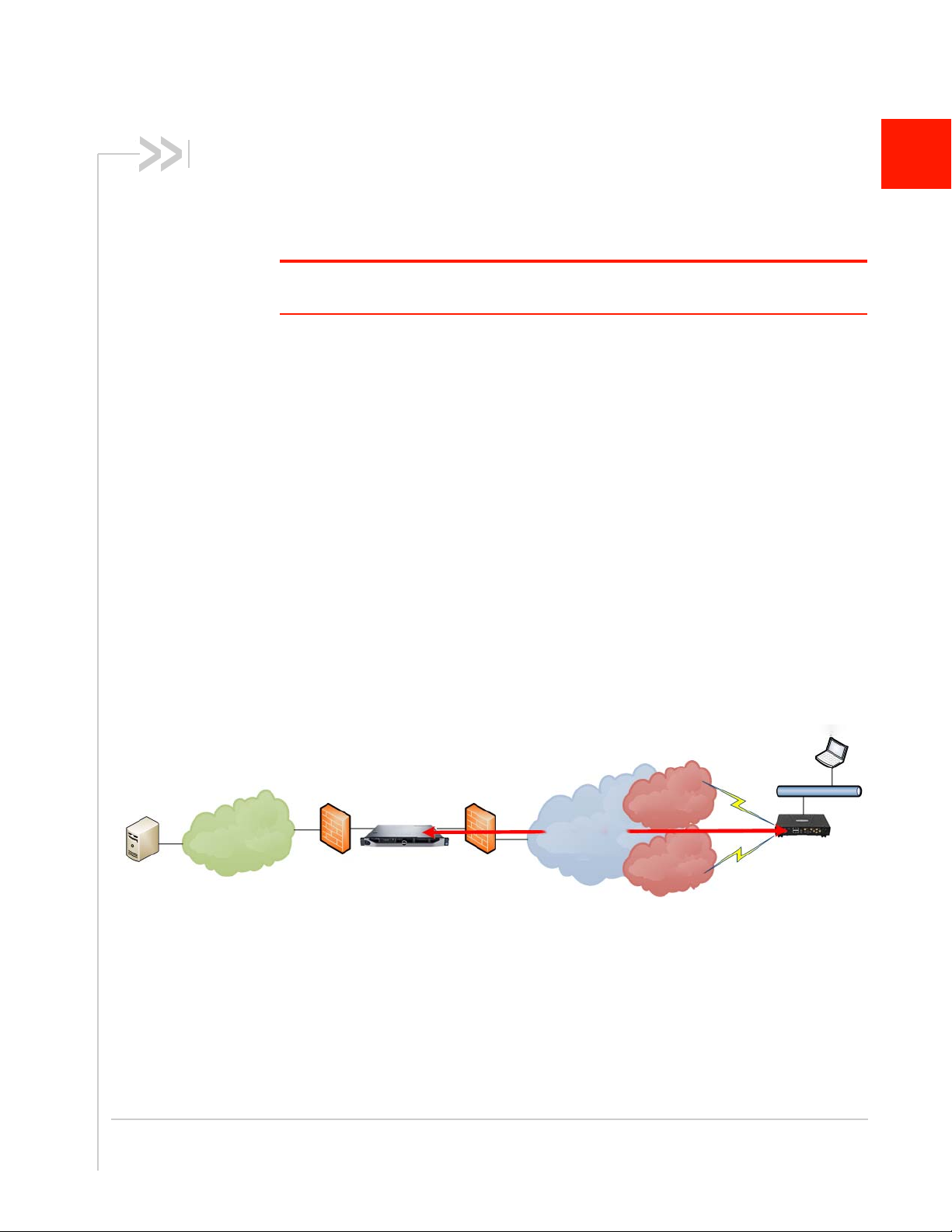
1: Introduction
Application
Servers
Enterprise
Network
Internal Firewall/
IPS/IDS/Router
ACM
External
Firewall
Internet Cellular
Wi-Fi/Public
Safety/Other
In Vehicle Laptop
IPsec VPN
Sierra Wireless
AirLink
Gateway / Router
This document provides configuration instructions for the AirLink Connection Manager
VPN (Virtual Private Network) server.
Note: “ACM” and “AirLink Connection Manager“ identify Sierra Wireless’ VPN server, formerly
named “oCM”.
Who Should Read This Guide
ACM users typically include IT support staff and IT security staff.
What is the AirLink Connection Manager (ACM)?
The ACM is a Virtual Private Network (VPN) server available in both an appliance
format (supplied by Sierra Wireless in a Dell 1U form factor), and as a virtual machine
running in VMWare vSphere Hypervisor (ESXi) 6.0 or above.
ACM is designed to work with Sierra Wireless' AirLink Gateways and Routers. ACM
provides security for all connected devices and applications in the router/gateway's
"vehicle area network".
1
Figure 1-1 shows how the ACM fits into a standard enterprise deployment:
Figure 1-1: The ACM fits between firewalls in an enterprise deployment
The ACM eliminates session interruptions when secure IP traffic is switched from one
wireless network to another because it is based on IKEv2 Mobile Internet Key
Exchange (MOBIKE) standards. MOBIKE enables the AirLink gateway/router to
establish a secure tunnel over any available wireless network, and as the vehicle
moves and network access changes, the gateway/router can "move the tunnel" to the
next best available network. This happens automatically, transparently, and without
disruption to the end-user's applications.
Rev 3 Nov 17 7 4119855
ACM Installation and Operations Guide
Note: Not all AirLink gateways/routers support IKEv2 and MOBIKE. Please consult the
device’s datasheet and User Guide for details.
The ACM is based on proven Vyatta® technology and strongSwan (for more
information, go to http://www.vyos.net and https://www.strongswan.org/).
Note: The ACM supports a subset of the commands and attributes described in the Vyatta
VPN Reference Guide.
FIPS-Compliant ACM
ACM is available in a FIPS-compliant configuration (ACM 1.6-FIPS) that provides
improved encryption capabilities. ACM 1.6-FIPS meets the requirements of the
Federal Information Processing Standard 140-2, security level 1 (http://
csrc.nist.gov/groups/STM/cmvp/documents/140-1/140sp/140sp2164.pdf).
NCP Client for Windows
ACM 1.6 and above support connections from systems using NCP Client for
Windows. Refer to the AirLink Connection Manager Configuration Guide for NCP
Client for details.
Supported AirLink Gateways and Routers
This document applies to the device versions in the following table.
Table 1-1: Supported Device Versions
Software Versions Supported
AirLink Device ACM 1.6 (non-FIPS) ACM 1.6 FIPS
3.12.1
oMG2000/500 Series
MG90 4.0.3 4.1.0
MP70 4.6.1+ Not supported
RV50 4.5.2+ Not supported
GX440/GX450
3.14.3.2
3.14.4
4.4.4+
4.5.1+
3.14.5
a
Not supported
GX400 4.4.1+ Not supported
ES440/ES450
LS300 4.4.4+ Not supported
a. Pending release Q3 2017
4.4.4+
4.5.1+
Not supported
Rev 3 Nov 17 8 4119855

2: Installation
This chapter describes how to install an ACM server appliance, and how to connect
the ACM (server or software) to your network.
Physical Installation
The ACM dedicated server appliance is a Dell PowerEdge R230XL (subject to future
change).
Environmental Requirements
The server must be installed in a temperature-controlled, computer data center
environment. An external UPS power source is recommended. The unit's power
supply is rated at 250W and a power cord is supplied.
Mounting Requirements
The server is shipped with Dell-supplied rails that can be used to mount the unit in
compatible 19" racks, or set onto securely mounted rack shelving.
2
Connecting the ACM to Your Network
The ACM is dedicated to providing secure mobile connections for AirLink gateways/
routers. It is not to be used as a replacement or substitute general purpose enterprise
firewall/router.
Sierra Wireless recommends that the ACM be installed behind the enterprise firewall
so that policies and procedures relating to enterprise security are not significantly
affected by the introduction of the ACM. When used in this mode, the ACM security
footprint is limited to:
• AirLink devices must be able to access the ACM from the WAN. Typically, this
requires that the ACM be assigned a public IP address. If the IP address is not
publicly routable, it should be network address translated (NAT) (see next point)
to a private address on the ACM physical network interface.
• TCP/IP port 2222 must be enabled to allow access to the ACM.
• The traffic between AirLink devices and the ACM consists of IPsec traffic on UDP
protocol port 500 and ESP encapsulated on UDP port 4500. Only these items
need to be taken into consideration for port and protocol translation from the
public to the private address.
To connect the ACM to your network, the following steps must be performed:
1. Assign a public IP address. If network address translation is required, translate
assigned IP addresses to the outside address of the ACM (see Table 1-1 on
page 52).
Rev 3 Nov 17 9 4119855
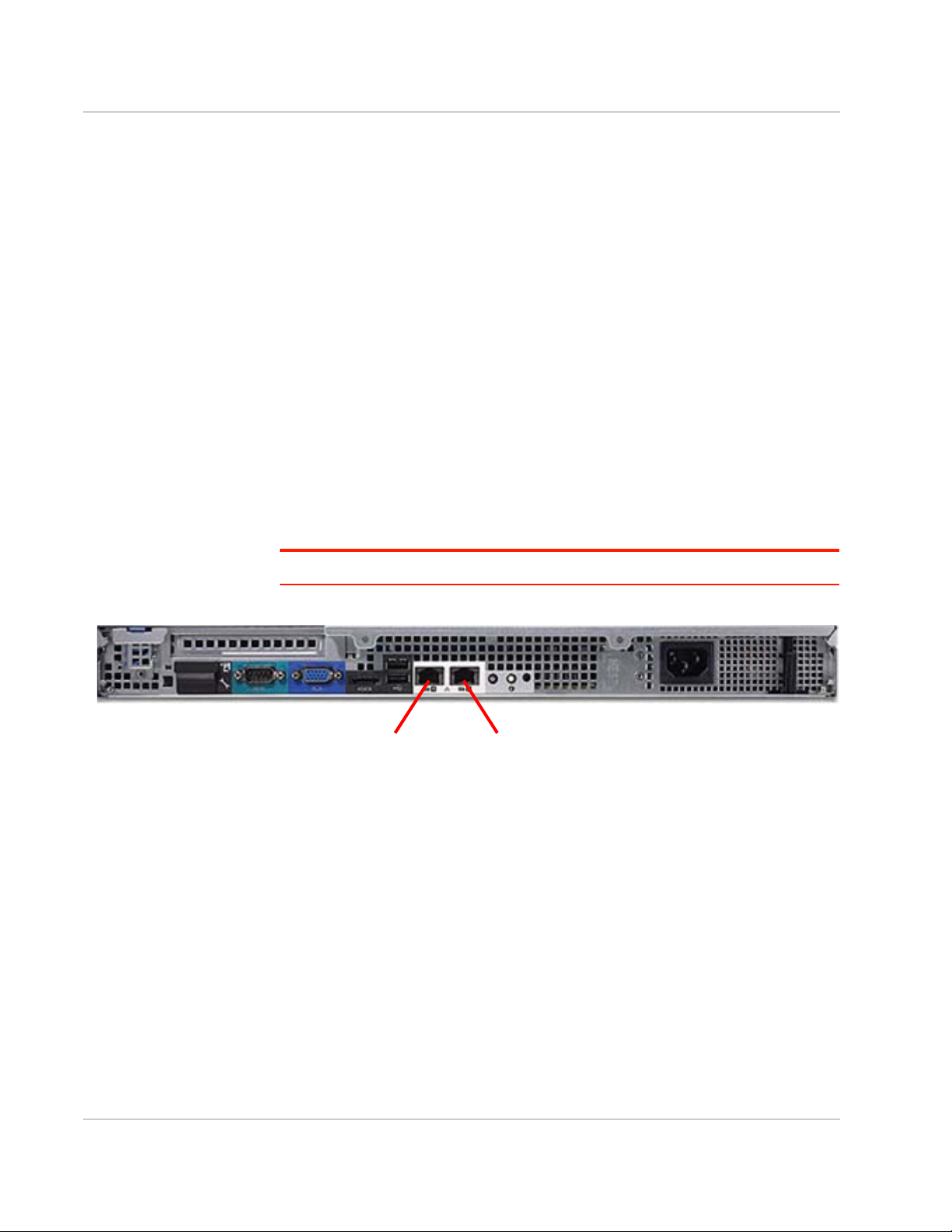
ACM Installation and Operations Guide
Port 1 Port 2
2. At a minimum, enable the following protocols and ports for the translated
address:
· IP Protocol ESP
· TCP/IP Port 2222
· UDP/IP 500
· UDP/IP 4500
If required by a customer security policy, the VPN between the AirLink gateway/
router and the ACM can be specified to route ALL traffic through the secure
connection. While there are some consequences with this approach, it does
provide the advantage of lock down so that all content is delivered to the
enterprise security environment where additional equipment can provide deeppacket inspection, anti-virus, and content filtering among other security services.
Ethernet Connections
Use Cat 5e Ethernet cabling with RJ45 connectors (not supplied) to connect the
ACM Ethernet ports to the network infrastructure.
• Connect Port 1 (GB1), the outside interface, to the network connected to the
enterprise firewall.
• Connect Port 2 (GB2), the inside interface, to the internal network.
Note: Any additional ports that may be present are unused.
Figure 2-1: Rear panel of ACM
Connecting to the ACM from an Inside Device
The ACM may be pre-configured with an inside network address and other
information as specified in Basic Configuration Requirements on page 52.
1. Establish a 10/100/1000 Mbps Ethernet connection between the inside
interface on Ethernet Port 2 of the ACM server and either an Ethernet switch
or a direct connection on a PC.
The default address and netmask of the Inside interface is 10.99.0.1/
255.255.255.0.
2. Use an SSH client tool (such as putty.exe) running on a test PC to open an
SSH session to port 2222 to the inside address.
Rev 3 Nov 17 10 4119855

Installation
Note: Sierra Wireless can only provide remote technical support for the ACM if access to
Port 2222 is enabled on the public or private interface. If only private interface access is
available, an independent VPN access method must be provided.
Rev 3 Nov 17 11 4119855

3: Configuration Overview
This chapter describes some common tasks performed by the ACM Administrator.
Logging In and Out
To log in to the ACM, use the default username (admin) and password (inmotion). For
example:
login as: admin
UNAUTHORIZED USE OF THIS SYSTEM IS PROHIBITED!
password:
WELCOME TO ACM!
This system is open-source software.
The exact distribution terms for each module
comprising the full system are described in the
individual files in /usr/share/doc/*/copyright.
Last login: Fri Apr 20 11:29:35 2016 from
xyz.com
3
admin@ACM:~$
Important: Sierra Wireless strongly recommends that you immediately change the Admin
password from the default value (“inmotion”) to prevent unauthorized use of the system. See
Admin Password on page 19 for details.
To log out of the ACM use the exit command:
admin@ACM:~$exit
Change to Configuration Mode
By default, the system will be in operational mode after logging in to the ACM, as
indicated by the ":~$" prompt.
To modify the ACM configuration, the system must first be changed to configuration
mode. To change to configuration mode, enter the configure command:
admin@ACM:~$ configure
The prompt for configuration mode will change to "#" as shown here:
admin@ACM#
Note: To change back to operational mode from configuration mode, use the “exit” command.
Rev 3 Nov 17 12 4119855
Configuration Overview
Configuration Tree
The ACM configuration is stored in attributes and nodes:
• Attribute— Includes a name and a data value.
• Node—A container for one or more attributes. A node can also contain sub-
nodes to form a hierarchy of nodes.
Attributes and nodes are referred to as ‘statements’ when they are viewed from
the command line using the ‘show’ command.
The following snippet (from ‘show config’ output) is an example of an attribute,
node, and subnode:
local-ip 192.168.12.242 Attribute (name = ‘local-ip’, value = IP
address 192.168.12.242)
tunnel 1 { Node
esp-group 1 Attribute (name = ‘esp-group’, value = 1)
local { Sub-node
subnet 0.0.0.0/0 Attribute (name = ‘subnet’, value =
0.0.0.0/0)
}
}
Note: Nodes always have an enclosing pair of { } braces.
Manage Configuration Attributes
When the ACM server boots, its boot configuration is loaded into its running
configuration. While the server is running, configuration attributes are managed
using the commands shown in Table 3-1.
Table 3-1: Configuration Attribute Management Commands
Command Purpose Details
set Add or modify an attribute. See Add or Modify Attributes on page 14.
delete Delete an attribute. See Delete Attributes on page 15.
show
discard Remove all pending attribute changes.
commit
save
Display all pending attribute changes (add,
modify , delete).
Apply all pending attribute changes to the
currently running configuration.
Save the running configuration as the boot
configuration.
See Show Uncommitted Attribute Changes on
page 15.
See Discard Uncommitted Attribute Changes on
page 16.
See Apply Configuration on page 17
See Save Configuration on page 17
load
Load the ACM’s default configuration
attributes.
See Restore Default Configuration on page 18
Rev 3 Nov 17 13 4119855

ACM Installation and Operations Guide
Note: Attribute changes (adding, modifying, deleting, lo ading defaults) do not take effect
on the ACM until they are first committed to the running configuration. After committing the
changes, they stay in effect until the server reboots. To keep them in effect across reboots,
they must be saved before the server reboots.
Add or Modify Attributes
To add a new attribute statement or modify an existing statement, use the set
command.
The following example demonstrates the set command being used to make the
following changes, and a snippet from the show command which displays the ‘+’
and ‘>’ symbols:
· change the hash method for an esp group’s “proposal 1” from “sha1” to
“md5”
· add a new “proposal 2” to the esp group
· add the encryption method for the new “proposal 2”
user@ACM1-Pro....duction# set vpn ipsec esp-group
espgroup1 proposal 1 hash md5
user@ACM1-Production# set vpn ipsec esp-group espgroup1
proposal 2 encryption aes256
user@ACM1-Production# show
...
esp-group espgroup1 {
compression enable
mode tunnel
pfs enable
proposal 1 {
encryption aes256
hash md5
}
+ proposal 2 {
+ encryption aes256
+ }
}
Rev 3 Nov 17 14 4119855

Configuration Overview
Delete Attributes
To delete an attribute statement, use the delete command.
The following example demonstrates the delete command being used to make
the following change, and a snippet from the show command that displays the ‘-’
symbol:
· delete the hash method for an esp group’s “proposal 1”
user@ACM1-Production# delete vpn ipsec esp-group
espgroup1 proposal 1 hash
user@ACM1-Production# show
...
esp-group espgroup1 {
compression enable
mode tunnel
pfs enable
proposal 1 {
encryption aes256
- hash md5
}
}
....
Show Uncommitted Attribute Changes
To view pending attribute changes, use the show command.
When the command is used:
• the plus (+) symbol appears next to new attributes
• the greater than (>) symbol appears next to modified attributes
• the minus (-) symbol appears next to deleted attributes
The following example demonstrates a snippet from the show command which
displays:
· ‘>’ for an encryption method being modified
· ‘–’ for a hash method being deleted
· ‘+’ for a proposal being added
Rev 3 Nov 17 15 4119855

ACM Installation and Operations Guide
user@ACM1-Production# show
...
esp-group espgroup1 {
compression enable
mode tunnel
pfs enable
proposal 1 {
> encryption aes256
- hash md5
}
+ proposal 2 {
+ encryption aes256
+ }
}
....
Discard Uncommitted Attribute Changes
To remove pending attribute changes so they cannot be committed to the running
configuration, use the discard command.
After discarding the configuration changes, the configuration reverts to the state it
was in prior to the changes and the symbol(s) (+, -, or >) located beside the
changed attribute statement(s) disappear.
The following example shows the discard command being used and a snippet
from the show command which displays:
· the original attribute values for proposal 1
· no proposal 2 (it is no longer being added)
user@ACM1-Production# show
...
esp-group espgroup1 {
compression enable
mode tunnel
pfs enable
proposal 1 {
encryption aes128
hash md5
}
}
....
Rev 3 Nov 17 16 4119855
 Loading...
Loading...