Siemens SCALANCE W788C-2 Series, SCALANCE W788C-2 RJ45, SCALANCE W788C-2 M12, SCALANCE W788C-2 M12 EEC Operating Instructions Manual

___________________
___________________
___________________
___________________
___________________
___________________
SIMATIC NET
Industrial Wireless LAN
SCALANCE W788C-2
Operating Instructions
01/2017
A5E03692120
Introduction
1
Security recommendations
2
Description
3
Mounting
4
Connection
5
Technical data
6
Dimension drawings
7
Approvals
8
-11

Siemens AG
Division Process Industries and Drives
Postfach 48 48
90026 NÜRNBERG
GERMANY
A5E03692120-11
Ⓟ
Copyright © Siemens AG 2011 - 2017.
All rights reserved
Legal information
Warning notice system
DANGER
indicates that death or severe personal injury will result if proper precautions are not taken.
WARNING
indicates that death or severe personal injury may result if proper precautions are not taken.
CAUTION
indicates that minor personal injury can result if proper precautions are not taken.
NOTICE
indicates that property damage can result if proper precautions are not taken.
Qualified Personnel
personnel qualified
Proper use of Siemens products
WARNING
Siemens products may only be used for the applications described in the catalog and in the relevant technical
maintenance are required to ensure that the products operate safely and without any problems. The permissible
ambient conditions must be complied with. The information in the relevant documentation must be observed.
Trademarks
Disclaimer of Liability
This manual contains notices you have to observe in order to ensure your personal safety, as well as to prevent
damage to property. The notices referring to your personal safety are highlighted in the manual by a safety alert
symbol, notices referring only to property damage have no safety alert symbol. These notices shown below are
graded according to the degree of danger.
If more than one degree of danger is present, the warning notice representing the highest degree of danger will
be used. A notice warning of injury to persons with a safety alert symbol may also include a warning relating to
property damage.
The product/system described in this documentation may be operated only by
task in accordance with the relevant documentation, in particular its warning notices and safety instructions.
Qualified personnel are those who, based on their training and experience, are capable of identifying risks and
avoiding potential hazards when working with these products/systems.
Note the following:
documentation. If products and components from other manufacturers are used, these must be recommended
or approved by Siemens. Proper transport, storage, installation, assembly, commissioning, operation and
All names identified by ® are registered trademarks of Siemens AG. The remaining trademarks in this publication
may be trademarks whose use by third parties for their own purposes could violate the rights of the owner.
We have reviewed the contents of this publication to ensure consistency with the hardware and software
described. Since variance cannot be precluded entirely, we cannot guarantee full consistency. However, the
information in this publication is reviewed regularly and any necessary corrections are included in subsequent
editions.
for the specific
01/2017 Subject to change

Table of contents
1 Introduction ............................................................................................................................................. 5
2 Security recommendations ...................................................................................................................... 7
3 Description ............................................................................................................................................ 11
4 Mounting ............................................................................................................................................... 23
5 Connection ........................................................................................................................................... 29
6 Technical data ...................................................................................................................................... 39
7 Dimension drawings .............................................................................................................................. 43
8 Approvals .............................................................................................................................................. 45
Index..................................................................................................................................................... 47
1.1 Information on the Operating Instructions ................................................................................ 5
3.1 Description of the device ........................................................................................................ 11
3.2 Structure of the type designations .......................................................................................... 13
3.3 Components of the product .................................................................................................... 14
3.4 Accessories ............................................................................................................................. 15
3.4.1 Installation ............................................................................................................................... 15
3.4.2 Flexible connecting cables and antennas ............................................................................... 18
3.4.2.1 Flexible connecting cables ...................................................................................................... 18
3.4.2.2 Antennas ................................................................................................................................. 19
3.5 LED display ............................................................................................................................. 22
4.1 Securing the housing .............................................................................................................. 24
4.2 Wall mounting ......................................................................................................................... 25
4.3 Installing on the S7-300 standard rail ..................................................................................... 26
4.4 Installing on a DIN rail ............................................................................................................. 27
5.1 Safety when connecting up ..................................................................................................... 29
5.2 Lightning protection, power supply and grounding ................................................................. 30
5.3 Power supply and Ethernet ..................................................................................................... 33
5.4 Antenna connectors ................................................................................................................ 35
6.1 Technical specifications of the SCALANCE W788C-2) .......................................................... 39
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
3

Table of contents
SCALANCE W788C-2
4 Operating Instructions, 01/2017, A5E03692120-11
1
1.1
Information on the Operating Instructions
Validity of the Operating Instructions
Product
Article number
SCALANCE W788C-2 RJ-45
6GK5 788-2FC00-1AA0
SCALANCE W788C-2 M12
6GK5 788-2GD00-1AA0
Purpose of the Operating Instructions
Documentation on the accompanying CD
GS_SCALANCE-WLC711_76 pdf
Note
Detection of the W788C-2 M12 EEC devices
When the W788C
WLC 711, they are shown as W788C
Note
Make sure that you read the explanations and instructions in the README.txt file
These operating instructions cover the following products:
SCALANCE W788C-2 M12 EEC 6GK5788-2GD00-1TA0
If information relates to all the named products, the term SCALANCE W7x8 will be used.
These operating instructions apply to the following software version:
● SCALANCE W7x8C with firmware as of version 8.31
Using the Operating Instructions, you will be able to install and connect the SCALANCE
W7x8 correctly. The configuration and the integration of the device in a WLAN are not
described in these instructions.
You will find introductory information about configuration in the document "Getting Started
SCALANCE WLC711" on the accompanying SIMATIC NET IWLAN CD under the file name:
-2 M12 EEC devices are detected by the configuration software of the
-2 M12.
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
5
Introduction
Security information
Trademarks
1.1 Information on the Operating Instructions
Siemens provides products and solutions with industrial security functions that support the
secure operation of plants, systems, machines and networks.
In order to protect plants, systems, machines and networks against cyber threats, it is
necessary to implement – and continuously maintain – a holistic, state-of-the-art industrial
security concept. Siemens’ products and solutions only form one element of such a concept.
Customer is responsible to prevent unauthorized access to its plants, systems, machines
and networks. Systems, machines and components should only be connected to the
enterprise network or the internet if and to the extent necessary and with appropriate security
measures (e.g. use of firewalls and network segmentation) in place.
Additionally, Siemens’ guidance on appropriate security measures should be taken into
account. For more information about industrial security, please visit
http://www.siemens.com/industrialsecurity (http://www.siemens.com/industrialsecurity)
Siemens’ products and solutions undergo continuous development to make them more
secure. Siemens strongly recommends to apply product updates as soon as available and to
always use the latest product versions. Use of product versions that are no longer supported,
and failure to apply latest updates may increase customer’s exposure to cyber threats.
To stay informed about product updates, subscribe to the Siemens Industrial Security RSS
Feed under
http://www.siemens.com/industrialsecurity (http://www.siemens.com/industrialsecurity)
The following and possibly other names not identified by the registered trademark sign ® are
registered trademarks of Siemens AG:
SIMATIC NET, SCALANCE, C-PLUG, RCOAX
SCALANCE W788C-2
6 Operating Instructions, 01/2017, A5E03692120-11

2
General
Physical access
Software (security functions)
To prevent unauthorized access, note the following security recommendations.
● You should make regular checks to make sure that the device meets these
recommendations and/or other security guidelines.
● Evaluate your plant as a whole in terms of security. Use a cell protection concept with
suitable products.
● When the internal and external network are disconnected, an attacker cannot access
internal data from the outside. Therefore operate the device only within a protected
network area.
● For communication via non-secure networks use additional devices with VPN functionality
to encrypt and authenticate the communication.
● Terminate management connections correctly (WBM. Telnet, SSH etc.).
● Restrict physical access to the device to qualified personnel.
● The memory card or the PLUG (C-PLUG, KEY-PLUG, security PLUG) contains sensitive
data such as certificates, keys etc. that can be read out and modified.
● Keep the software up to date. Check regularly for security updates of the product.
You will find information on this on the Internet pages "Industrial Security
(http://www.siemens.com/industrialsecurity)".
● Inform yourself regularly about security advisories and bulletins published by Siemens
ProductCERT (http://www.siemens.com/cert/en/cert-security-advisories.htm).
● Only activate protocols that you really require to use the device.
● Use the security functions such as address translation with NAT (Network Address
Translation) or NAPT (Network Address Port Translation) to protect receiving ports from
access by third parties.
● Restrict access to the device with a firewall or rules in an access control list (ACL -
Access Control List).
● If RADIUS authentication is via remote access, make sure that the communication is
within the secured network area or is via a secure channel.
● The option of VLAN structuring provides good protection against DoS attacks and
unauthorized access. Check whether this is practical or useful in your environment.
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
7

Security recommendations
Passwords
Keys and certificates
Secure/non-secure protocols
● Enable logging functions. Use the central logging function to log changes and access
attempts centrally. Check the logging information regularly.
● Configure a Syslog server to forward all logs to a central location.
● Use WPA2/ WPA2-PSK with AES to protect the WLAN. If iPCF or iPCF-MC is used, use
the AES encryption.
● Define rules for the use of devices and assignment of passwords.
● Regularly update passwords and keys to increase security.
● Change all default passwords for users before you operate the device.
● Only use passwords with a high password strength. Avoid weak passwords for example
password1, 123456789, abcdefgh.
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
● Do not use the same password for different users and systems or after it has expired.
This section deals with the security keys and certificates you require to set up HTTPS (
HyperText Transfer Protocol Secured Socket Layer).
● We strongly recommend that you create your own HTTPS certificates and make them
● Handle user-defined private keys with great caution if you use user-defined SSH or SSL
● Use the certification authority including key revocation and management to sign the
● Verify certificates and fingerprints on the server and client to avoid "man in the middle"
● We recommend that you use certificates with a key length of 2048 bits.
● Change keys and certificates immediately, if there is a suspicion of compromise.
available.
There are preset certificates and keys on the device. The preset and automatically
created HTTPS certificates are self-signed.
We recommend that you use HTTPS certificates signed either by a reliable external or by
an internal certification authority. The HTTPS certificate checks the identity of the device
and controls the encrypted data exchange. You can install the HTTPS certificate via the
WBM (System > Load and Save).
keys.
certificates.
attacks.
● For the DCP function, enable the "DCP read-only" mode after commissioning.
● Avoid and disable non-secure protocols, for example Telnet and TFTP. For historical
reasons, these protocols are still available, however not intended for secure applications.
Use non-secure protocols on the device with caution.
SCALANCE W788C-2
8 Operating Instructions, 01/2017, A5E03692120-11

Security recommendations
● The following protocols provide secure alternatives:
– SNMPv1/v2 → SNMPv3
Check whether use of SNMPv1 is necessary. SNMPv1 is classified as non-secure.
Use the option of preventing write access. The product provides you with suitable
setting options.
If SNMP is enabled, change the community names. If no unrestricted access is
necessary, restrict access with SNMP.
Use SNMPv3 in conjunction with passwords.
– HTTP → HTTPS
– Telnet → SSH
– SNTP → NTP
● Use secure protocols when access to the device is not prevented by physical protection
measures.
● To prevent unauthorized access to the device or network, take suitable protective
measures against non-secure protocols.
● If you require non-secure protocols and services, operate the device only within a
protected network area.
● Restrict the services and protocols available to the outside to a minimum.
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
9
Security recommendations
Available protocols per port
Protocol
Port number
Port status
Factory setting
Authentication
Protocol
Port number
Port status
Factory setting
of the port
Authentication
SSH
TCP/22
Open (when configured)
Open
Yes
TELNET
HTTP
TCP/80
Open (when configured)
Open
Yes
HTTPS
SNTP
NTP
SNMP
UDP/161
Open (when configured)
Open
Yes
PROFINET
49155
Syslog
UDP/514
Open (when configured)
Open
No
EtherNet/IP
8
DHCP
UDP/67,68
Open (when configured)
Closed
No
RADIUS
UDP/1812,1813
Open (when configured)
Closed
No
TFTP
UDP/69
Open (when configured)
Closed
No
The following list provides you with an overview of the open ports on this device.
The table includes the following columns:
●
All protocols that the device supports
●
Port number assigned to the protocol
●
– Open
– Open (when configured)
●
– Open
The port is always open and cannot be closed.
The port is open if it has been configured.
The factory setting of the port is "Open".
– Closed
The factory setting of the port is "Closed".
●
Specifies whether or not the protocol is authenticated.
TCP/23 Open (when configured) Open Yes
TCP/443 Open (when configured) Open Yes
UDP/123 Open (when configured) Closed No
UDP/34964,
UDP/49154,
TCP/44818,
UDP/2222,4481
Open Open No
Open (when configured) Open No
SCALANCE W788C-2
10 Operating Instructions, 01/2017, A5E03692120-11
3
3.1
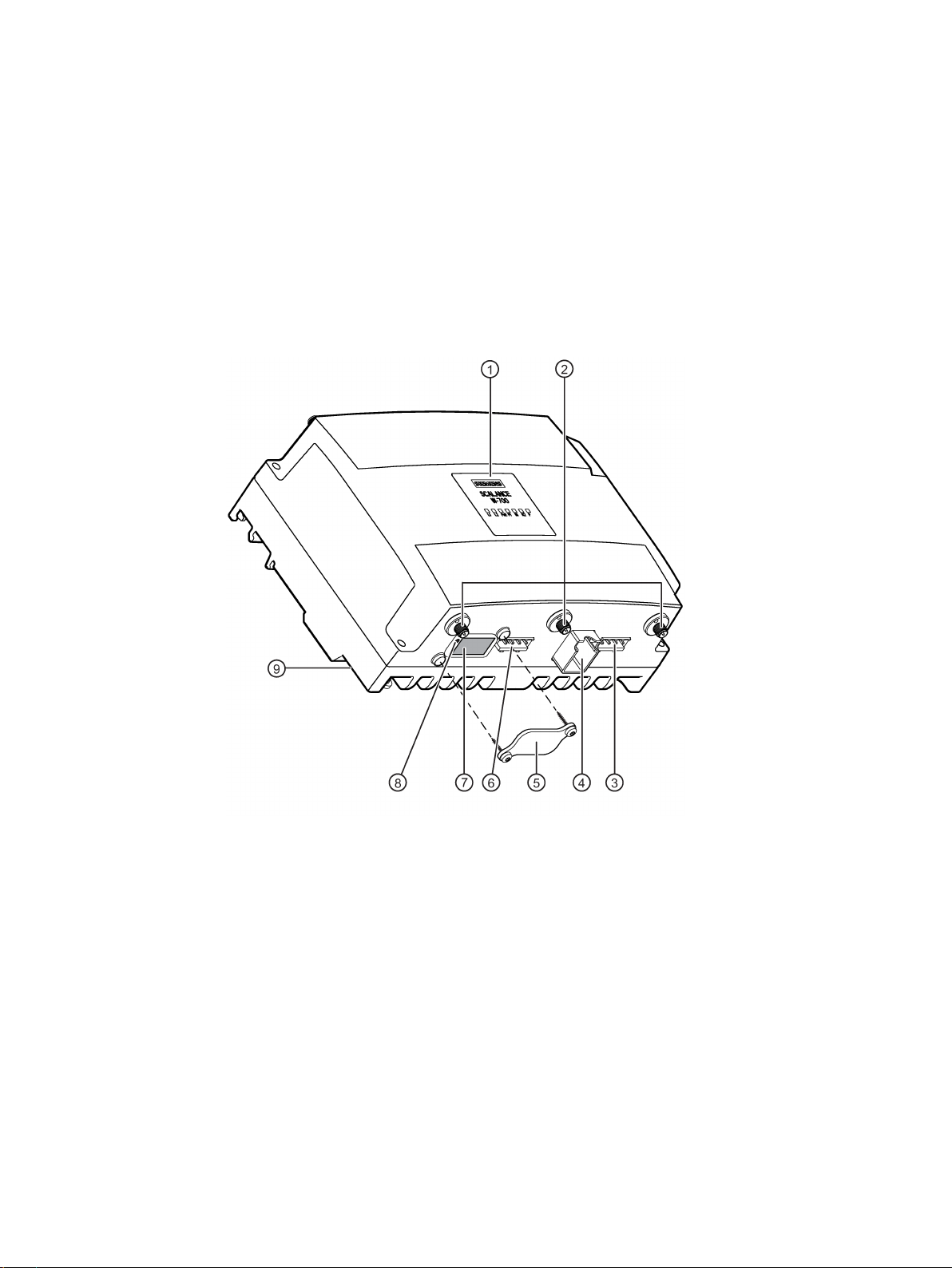
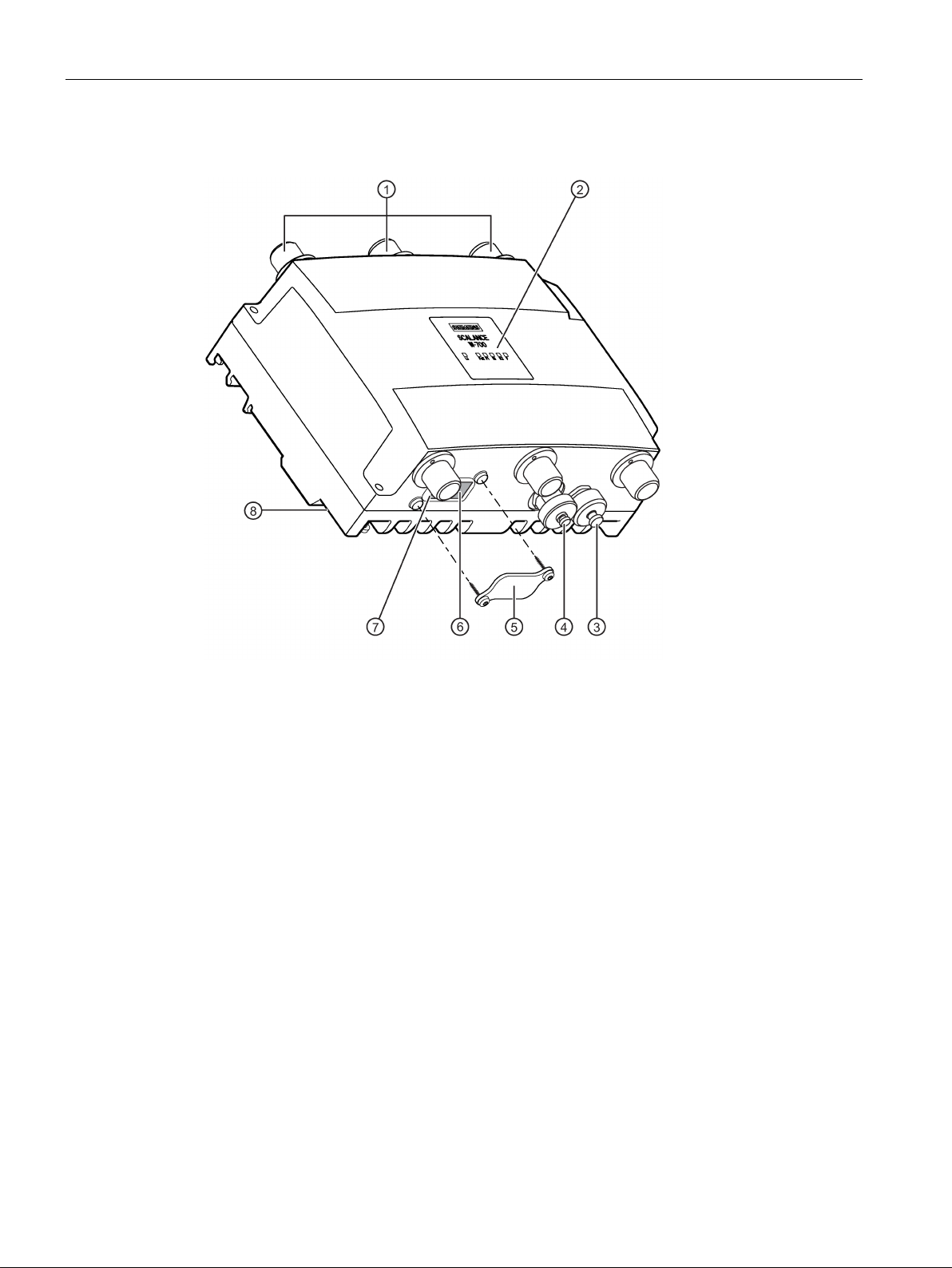
Description of the device
W7x8x-x RJ-45 - degree of protection IP30
①
LEDs
②
③
Connector for power supply
④
Connector for Ethernet, RJ-45 type
⑤
- PLUG compartment (not with W788C)
⑥
Connector for the digital input/output (not with W788C)
⑦
PLUG compartment (not with W788C)
⑧
Reset button
⑨
Grounding connector (thread M4) on the back of the device
Connecting connectors, R-SMA type female
• Devices with one IWLAN interface: 3 connectors on the top (covered in the figure).
• Devices with two IWLAN interfaces: 3 connectors on the top and 3 on the underside.
Screw-down cover for the
- reset button and the
Figure 3-1 Device description of the RJ-45 variant
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
11
Description
W7x8x-x M12 - degree of protection IP65
①
②
LEDs
③
Connector for the supply voltage, type M12 (with cover)
④
Connector for Ethernet, M12 type (with cover)
⑤
- PLUG compartment (not with W788C)
⑥
PLUG compartment (not with W788C)
⑦
Reset button (covered in the figure)
⑧
Grounding connector (thread M4) on the back of the device
3.1 Description of the device
Connecting connectors, N-Connect type female
• Devices with one IWLAN interface: 3 connectors on the top (covered in the figure).
• Devices with two IWLAN interfaces: 3 connectors on the top and 3 on the underside.
Screw-down cover for the
- reset button and the
Figure 3-2 Device description of the M12 variant
SCALANCE W788C-2
12 Operating Instructions, 01/2017, A5E03692120-11
Description
3.2
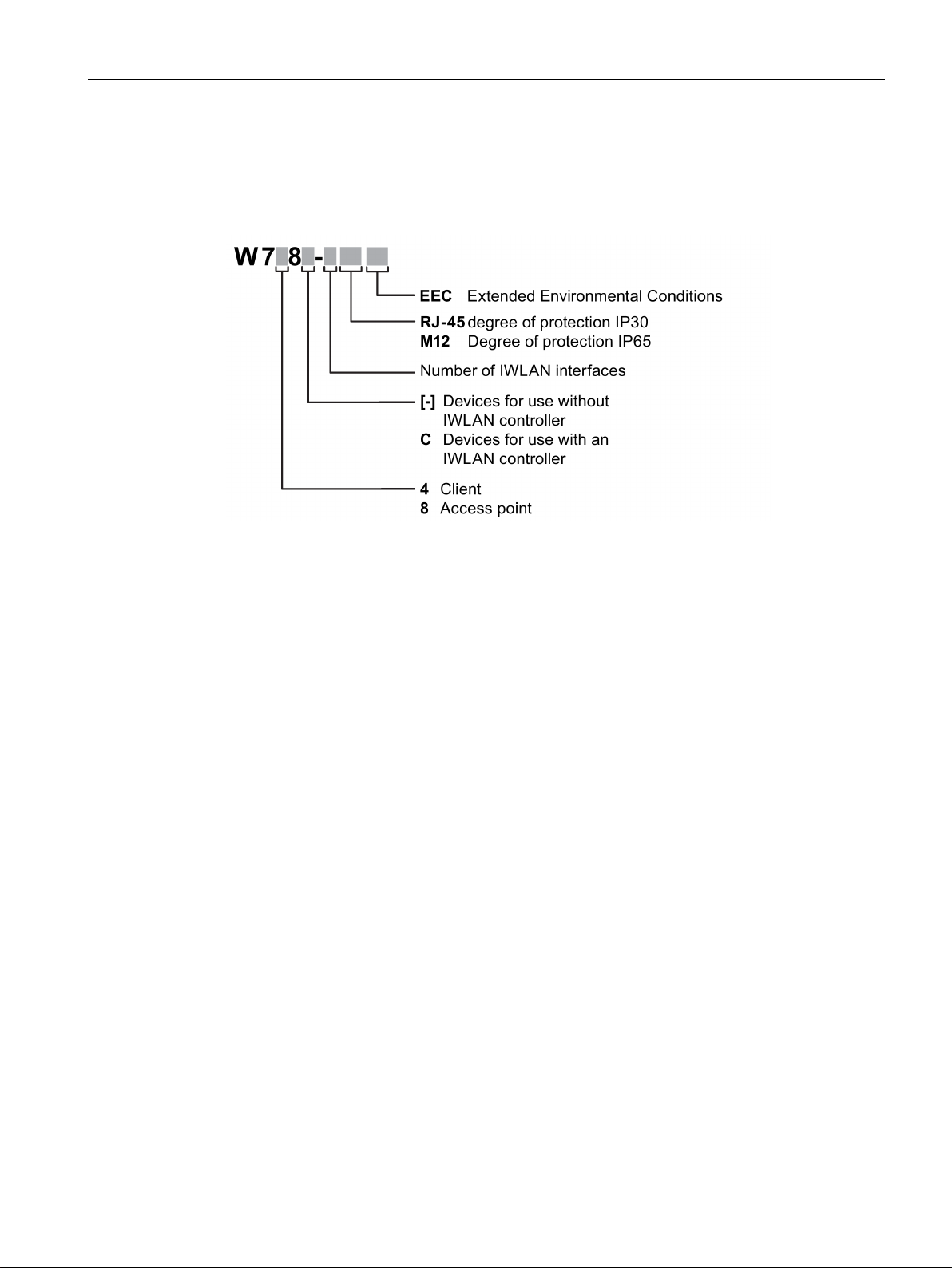
Structure of the type designations
3.2 Structure of the type designations
The type designation of a SCALANCE W7x8 is made up of several parts that have the
following meaning:
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
13

Description
3.3
Components of the product
Note
The mounting set with the holding plate does not ship with the device, see
(Page
3.3 Components of the product
The following components are supplied with the product:
● SCALANCE W7x8
● Only with device variant M12 / IP65:
– 2 protective caps for the M12 sockets
● Only with device variant RJ-45 / IP30:
– 4-pin terminal block for the supply voltage
– 4-pin terminal block for the digital input/output
● 2 screws for mounting on an S7-300 standard rail
● SIMATIC NET Industrial Wireless LAN CD
Accessories
15).
Please check that the consignment you have received is complete. If the consignment is
incomplete, contact your supplier or your local Siemens office.
SCALANCE W788C-2
14 Operating Instructions, 01/2017, A5E03692120-11

Description
3.4
Accessories
3.4.1
Installation
Installation
Component
Description
Article number
ment to an S7-300 rail, a 35 mm DIN rail or a mast.
M12 data plug-in connector
Component
Description
Article number
package
package
Data line
Component
Description
Article number
Sold by the meter
Sold by the meter
(PROFINET type B)
Sold by the meter
3.4 Accessories
Technical data subject to change.
You will find further information on the accessories program in the Industry Mall.
(https://mall.industry.siemens.com)
Mounting set The mounting set with the holding plate for attach-
IE FC M12
PLUG PRO
2x2
IE FC TP STANDARD
CABLE GP2X2
(PROFINET type A)
IE FC TP ROBUST
STANDARD CABLE GP
2X2
(PROFINET type A)
M12 data plug-in connector for IE FC
TP cables 2x2, IP65/67, D-coded,
axial cable outlet
Standard bus cable, TP installation cable for connection to FC OUTLET RJ-45, for universal use, 4wire, shielded, CAT 5E
Standard bus cable, ATPE outer jacket for connection to FC RJ-45 PLUG and FC OUTLET RJ45, fixed installation, for universal use, 4-wire,
shielded, CAT 5
1 connector per
8 connectors per
6GK5798-8ML00-0AB3
6GK1 901-0DB20-6AA0
6GK1 901-0DB20-6AA8
6XV1 840-2AH10
6XV1 841-2A
IE FC TP ROBUST
FLEXIBLE CABLE GP
2X2
IE FC TP FLEXIBLE
CABLE GP 2X2
(PROFINET type B)
SCALANCE W788C-2
Operating Instructions, 01/2017, A5E03692120-11
Flexible bus cable, TPE outer jacket for connection to FC RJ-45 PLUG and FC OUTLET RJ-45,
flexible wires, 4-wire, shielded, CAT 5
Flexible bus cable, TP installation cable, flexible
wires, shielded, CAT 5
Sold by the meter
6XV1 841-2B
6XV1 870-2B
15
 Loading...
Loading...