Siemens SCALANCE W1750D UI Configuration Manual
SIMATIC NET
SCALANCE W1750D UI
Configuration Manual
C79000
About this guide
1
Security recommendations
2
About SCALANCE W
3
Setting up an AP
4
Automatic Retrieval of
Configuration
5
SCALANCE W User
Interface
6
Initial Configuration Tasks
7
Customizing AP Settings
8
VLAN Configuration
9
IPv6 Support
10
Wireless Network Profiles
11
Wired Profiles
12
Captive Portal for Guest
Access
13
Authentication and User
Management
14
Roles and Policies
15
DHCP Configuration
16
Configuring Time-Based
Services
17
Continued on next page
-G8976-C451-02

Siemens AG
Division Process Industries and Drives
Postfach 48 48
90026 NÜRNBERG
DEUTSCHLAND
C79000-G8976-C451-02
Ⓟ
Copyright © Siemens AG .2018
Alle Rechte vorbehalten
02/2018 Änderungen vorbehalten

SCALANCE W1750D UI
Configuration Manual
Continued
Dynamic DNS Registration
18
VPN Configuration
19
AP-VPN Deployment
20
Adaptive Radio Management
21
Deep Packet Inspection and
Application Visibility
22
Voice and Video
23
Services
24
AP Management and
Monitoring
25
Uplink Configuration
26
Intrusion Detection
27
Mesh AP Configuration
28
Mobility and Client
Management
29
Spectrum Monitor
30
AP Maintenance
31
Monitoring Devices and Logs
32
Hotspot Profiles
33
ClearPass Guest Setup
34
AP-VPN Deployment
Scenarios
35
Appendix
A

Siemens AG
Division Process Industries and Drives
Postfach 48 48
90026 NÜRNBERG
GERMANY
C79000-G8976-C451-02
Ⓟ
Copyright © Siemens AG .
All rights reserved
Legal information
Warning notice system
DANGER
indicates that death or severe personal injury will result if proper precautions are not taken.
WARNING
may
CAUTION
indicates that minor personal injury can result if proper precautions are not taken.
NOTICE
indicates that property damage can result if proper precautions are not taken.
Qualified Personnel
personnel qualified
Proper use of Siemens products
WARNING
Siemens products may only be used for the applications described in the catalog and in the relevant technical
ambient conditions must be complied with. The information in the relevant documentation must be observed.
Trademarks
Disclaimer of Liability
This manual contains notices you have to observe in order to ensure your personal safety, as well as to prevent
damage to property. The notices referring to your personal safety are highlighted in the manual by a safety alert
symbol, notices referring only to property damage have no safety alert symbol. These notices shown below are
graded according to the degree of danger.
indicates that death or severe personal injury
If more than one degree of danger is present, the warning notice representing the highest degree of danger will
be used. A notice warning of injury to persons with a safety alert symbol may also include a warning relating to
property damage.
result if proper precautions are not taken.
The product/system described in this documentation may be operated only by
task in accordance with the relevant documentation, in particular its warning notices and safety instructions.
Qualified personnel are those who, based on their training and experience, are capable of identifying risks and
avoiding potential hazards when working with these products/systems.
Note the following:
documentation. If products and components from other manufacturers are used, these must be recommended
or approved by Siemens. Proper transport, storage, installation, assembly, commissioning, operation and
maintenance are required to ensure that the products operate safely and without any problems. The permissible
All names identified by ® are registered trademarks of Siemens AG. The remaining trademarks in this publication
may be trademarks whose use by third parties for their own purposes could violate the rights of the owner.
We have reviewed the contents of this publication to ensure consistency with the hardware and software
described. Since variance cannot be precluded entirely, we cannot guarantee full consistency. However, the
information in this publication is reviewed regularly and any necessary corrections are included in subsequent
editions.
for the specific
021/2018 Subject to change

Table of contents
1 About this guide .................................................................................................................................... 19
2 Security recommendations .................................................................................................................... 21
3 About SCALANCE W ............................................................................................................................ 25
4 Setting up an AP ................................................................................................................................... 29
5 Automatic Retrieval of Configuration ..................................................................................................... 41
6 SCALANCE W User Interface ............................................................................................................... 45
3.1 Overview ................................................................................................................................. 25
3.2 SCALANCE W UI .................................................................................................................... 26
3.3 SCALANCE W CLI .................................................................................................................. 27
4.1 Setting up an SCALANCE W Network .................................................................................... 29
4.1.1 Connecting an AP ................................................................................................................... 29
4.1.2 Assigning an IP address to the AP ......................................................................................... 30
4.2 Provisioning an AP .................................................................................................................. 31
4.2.1 Zero Touch Provisioning of APs ............................................................................................. 31
4.2.2 Provisioning APs through Airwave .......................................................................................... 33
4.3 Logging in to the SCALANCE W UI ........................................................................................ 34
4.4 Accessing the SCALANCE W CLI .......................................................................................... 36
5.1 Managed Mode Operations .................................................................................................... 41
5.2 Configuration Managed Mode Parameters ............................................................................. 42
5.3 Verifying the Configuration ..................................................................................................... 44
6.1 Login Screen ........................................................................................................................... 45
6.2 Main Window .......................................................................................................................... 47
6.2.1 Tabs ........................................................................................................................................ 49
6.2.1.1 Network Tab ............................................................................................................................ 49
6.2.1.2 Access Points Tab .................................................................................................................. 50
6.2.1.3 Clients Tab .............................................................................................................................. 51
6.2.2 Links ........................................................................................................................................ 52
6.2.2.1 New Version Available ............................................................................................................ 52
6.2.2.2 System .................................................................................................................................... 53
6.2.2.3 RF ........................................................................................................................................... 54
6.2.2.4 Security ................................................................................................................................... 54
6.2.2.5 Maintenance ........................................................................................................................... 55
6.2.2.6 More ........................................................................................................................................ 56
6.2.2.7 Help ......................................................................................................................................... 61
6.2.2.8 Logout ..................................................................................................................................... 61
6.2.2.9 Monitoring ............................................................................................................................... 61
6.2.2.10 Client Match ............................................................................................................................ 72
6.2.2.11
AppRF ..................................................................................................................................... 73
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
5

Table of contents
7 Initial Configuration Tasks ..................................................................................................................... 81
8 Customizing AP Settings ....................................................................................................................... 89
9 VLAN Configuration ............................................................................................................................. 101
10 IPv6 Support ........................................................................................................................................ 103
11 Wireless Network Profiles .................................................................................................................... 109
6.2.2.12 Spectrum ................................................................................................................................ 73
6.2.2.13 Alerts ...................................................................................................................................... 74
6.2.2.14 IDS ......................................................................................................................................... 78
6.2.2.15 AirGroup ................................................................................................................................. 79
6.2.2.16 Configuration .......................................................................................................................... 79
6.2.2.17 Airwave Setup ........................................................................................................................ 80
6.2.2.18 Pause/Resume....................................................................................................................... 80
6.2.3 Views ...................................................................................................................................... 80
7.1 Configuring System Parameters ............................................................................................ 81
7.2 Changing Password ............................................................................................................... 87
8.1 Modifying the AP Host Name ................................................................................................. 89
8.2 Configuring Zone Settings on an AP ..................................................................................... 90
8.3 Specifying a Method for obtaining IP Address ....................................................................... 91
8.4 Configuring Radio Profiles for an AP ..................................................................................... 92
8.5 Configuring Uplink VLAN for an AP ....................................................................................... 94
8.6 Changing USB Port Status .................................................................................................... 95
8.7 Master Election and Virtual Controller ................................................................................... 96
8.8 Adding an AP to the Network ................................................................................................. 98
8.9 Removing an AP from the Network........................................................................................ 99
9.1 VLAN Pooling ....................................................................................................................... 101
9.2 Uplink VLAN Monitoring and Detection on Upstream Devices ............................................ 101
10.1 IPv6 Notation ........................................................................................................................ 103
10.2 Enabling IPv6 Support for AP Configuration ........................................................................ 104
10.3 Firewall Support for IPv6 ...................................................................................................... 106
10.4 Debugging Commands ........................................................................................................ 107
11.1 Configuring Wireless Network Profiles ................................................................................ 109
11.1.1 Configuring WLAN Settings for an SSID Profile .................................................................. 110
11.1.2 Configuring VLAN Settings for a WLAN SSID Profile .......................................................... 117
11.1.3 Configuring Security Settings for a WLAN SSID Profile ...................................................... 120
11.1.4 Configuring Access Rules for a WLAN SSID Profile ........................................................... 131
11.1.5 Configuring Per-AP SSID and Per-AP-VLAN Settings on a Wireless Profile ...................... 134
11.2 Configuring Fast Roaming for Wireless Clients ................................................................... 135
11.2.1 Opportunistic Key Caching .................................................................................................. 135
11.2.2 Fast BSS Transition (802.11r Roaming) .............................................................................. 137
11.2.3 Radio Resource Management (802.11k) ............................................................................. 138
SCALANCE W1750D UI
6 Configuration Manual, , C79000-G8976-C451-02

Table of contents
12 Wired Profiles ..................................................................................................................................... 147
13 Captive Portal for Guest Access .......................................................................................................... 161
11.2.4 BSS Transition Management (802.11v)................................................................................ 141
11.3 Configuring Modulation Rates on a WLAN SSID ................................................................. 142
11.4 Multi-User-MIMO ................................................................................................................... 143
11.5 Management Frame Protection ............................................................................................ 144
11.6 Disabling Short Preamble for Wireless Client ....................................................................... 144
11.7 Editing Status of a WLAN SSID Profile ................................................................................. 145
11.8 Deleting a WLAN SSID Profile .............................................................................................. 145
12.1 Configuring a Wired Profile ................................................................................................... 147
12.1.1 Configuring Wired Settings ................................................................................................... 147
12.1.2 Configuring VLAN for a Wired Profile ................................................................................... 149
12.1.3 Configuring Security Settings for a Wired Profile ................................................................. 151
12.1.4 Configuring Access Rules for a Wired Profile ....................................................................... 153
12.2 Assigning a Profile to Ethernet Ports .................................................................................... 155
12.3 Editing a Wired Profile .......................................................................................................... 156
12.4 Deleting a Wired Profile ........................................................................................................ 156
12.5 Link Aggregation Control Protocol ........................................................................................ 156
12.5.1 Enabling Port-Channel on a Switch ...................................................................................... 157
12.5.2 Enabling Static LACP Configuration ..................................................................................... 158
12.6 Understanding Hierarchical Deployment .............................................................................. 159
13.1 Understanding Captive Portal ............................................................................................... 161
13.1.1 Types of Captive Portal......................................................................................................... 161
13.1.2 Walled Garden ...................................................................................................................... 162
13.2 Configuring a WLAN SSID for Guest Access ....................................................................... 163
13.3 Configuring Wired Profile for Guest Access ......................................................................... 170
13.4 Configuring Internal Captive Portal for Guest Network ......................................................... 172
13.5 Configuring External Captive Portal for Guest Network ....................................................... 176
13.5.1 External Captive Portal Profiles ............................................................................................ 176
13.5.2 Creating a Captive Portal Profile .......................................................................................... 176
13.5.3 Configuring an SSID or Wired Profile to Use External Captive Portal Authentication .......... 178
13.5.4 External Captive Portal Redirect Parameters ....................................................................... 181
13.5.5 Configuring External Captive Portal Authentication Using ClearPass Guest ....................... 181
13.6 Configuring Facebook Login ................................................................................................. 184
13.6.1 Setting up a Facebook Page ................................................................................................ 184
13.6.2 Configuring an SSID ............................................................................................................. 184
13.6.3 Configuring the Facebook Portal Page ................................................................................. 185
13.6.4 Accessing the Portal Page .................................................................................................... 186
13.7 Configuring Guest Logon Role and Access Rules for Guest Users ..................................... 187
Configuring Captive Portal Roles for an SSID ...................................................................... 190
13.8
13.9 Configuring Walled Garden Access ...................................................................................... 194
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
7

Table of contents
14 Authentication and User Management .................................................................................................. 197
15 Roles and Policies ............................................................................................................................... 243
13.9.1 Disabling Captive Portal Authentication ............................................................................... 195
14.1 Managing AP Users ............................................................................................................. 197
14.1.1 Configuring AP Users .......................................................................................................... 198
14.1.2 Configuring Authentication Parameters for Management Users ......................................... 200
14.1.3 Adding Guest Users through the Guest Management Interface .......................................... 202
14.2 Supported Authentication Methods ...................................................................................... 203
14.3 Supported EAP Authentication Frameworks ....................................................................... 205
14.4 Configuring Authentication Servers ..................................................................................... 206
14.4.1 Supported Authentication Servers ....................................................................................... 206
14.4.2 TACACS Servers ................................................................................................................. 208
14.4.3 Configuring an External Server for Authentication ............................................................... 209
14.4.4 Enabling RADIUS Communication over TLS ....................................................................... 214
14.4.5 Configuring Dynamic RADIUS Proxy Parameters ............................................................... 216
14.4.6 Associate Server Profiles to a Network Profile .................................................................... 218
14.5 Understanding Encryption Types ......................................................................................... 220
14.6 Configuring Authentication Survivability .............................................................................. 222
14.7 Configuring 802.1X Authentication for a Network Profile .................................................... 224
14.8 Enabling 802.1X Supplicant Support ................................................................................... 227
14.9 Configuring MAC Authentication for a Network Profile ........................................................ 229
14.10
Configuring MAC Authentication with Captive Portal Authentication ................................... 231
14.11 Configuring WISPr Authentication ....................................................................................... 233
14.12 Blacklisting Clients ............................................................................................................... 235
14.13 Uploading Certificate ............................................................................................................ 238
15.1 Firewall Policies ................................................................................................................... 243
15.1.1 Access Control List Rules .................................................................................................... 243
15.1.2 Configuring ACL Rules for Network Services ...................................................................... 244
15.1.3 Configuring Network Address Translation Rules ................................................................. 247
15.1.4 Configuring ALG Protocols .................................................................................................. 250
15.1.5 Configuring Firewall Settings for Protection from ARP Attacks ........................................... 251
15.1.6 Configuring Firewall Settings to Disable Auto Topology Rules ........................................... 253
15.1.7 Managing Inbound Traffic .................................................................................................... 254
15.2 Content Filtering ................................................................................................................... 260
15.3 Configuring User Roles ........................................................................................................ 266
15.4 Configuring Derivation Rules ............................................................................................... 270
15.4.1 Understanding Role Assignment Rule ................................................................................. 270
15.4.2 Creating a Role Derivation Rule .......................................................................................... 271
15.4.3 Understanding VLAN Assignment ....................................................................................... 273
15.4.4 Configuring VLAN Derivation Rules ..................................................................................... 275
15.5 Using Advanced Expressions in Role and VLAN Derivation Rules ..................................... 277
15.6 Configuring a User Role for VLAN Derivation ...................................................................... 279
SCALANCE W1750D UI
8 Configuration Manual, , C79000-G8976-C451-02

Table of contents
16 DHCP Configuration............................................................................................................................ 281
17 Configuring Time-Based Services ....................................................................................................... 295
18 Dynamic DNS Registration .................................................................................................................. 299
19 VPN Configuration .............................................................................................................................. 303
20 AP-VPN Deployment ........................................................................................................................... 327
21 Adaptive Radio Management .............................................................................................................. 341
22 Deep Packet Inspection and Application Visibility ................................................................................ 357
16.1 Configuring DHCP Scopes ................................................................................................... 281
16.1.1 Configuring Local DHCP Scopes .......................................................................................... 281
16.1.2 Configuring Distributed DHCP Scopes ................................................................................. 284
16.1.3 Configuring Centralized DHCP Scopes ................................................................................ 288
16.2 Configuring the Default DHCP Scope for Client IP Assignment ........................................... 291
17.1 Time Range Profiles ............................................................................................................. 295
17.2 Configuring a Time Range Profile ......................................................................................... 296
17.3 Applying a Time Range Profile to a WLAN SSID ................................................................. 297
17.4 Verifying the Configuration ................................................................................................... 298
18.1 Enabling Dynamic DNS ........................................................................................................ 299
18.2 Configuring Dynamic DNS Updates for Clients .................................................................... 301
18.3 Verifying the Configuration ................................................................................................... 302
19.1 Understanding VPN Features ............................................................................................... 303
19.2 Configuring a Tunnel from an AP to a Mobility Controller .................................................... 305
19.2.1 Configuring an IPsec Tunnel ................................................................................................ 305
19.2.2 Configuring an L2-GRE Tunnel ............................................................................................ 308
19.2.3 Configuring an L2TPv3 Tunnel ............................................................................................. 313
19.3 Configuring Routing Profiles ................................................................................................. 323
20.1 Understanding AP-VPN Architecture .................................................................................... 327
20.2 Configuring AP and Controller for AP-VPN Operations ........................................................ 331
20.2.1 Configuring an AP Network for AP-VPN Operations ............................................................ 331
20.2.2 Configuring a Controller for AP-VPN Operations ................................................................. 334
21.1 ARM Overview ...................................................................................................................... 341
21.2 Configuring ARM Features on an AP ................................................................................... 343
21.2.1 Band Steering ....................................................................................................................... 343
21.2.2 Airtime Fairness Mode .......................................................................................................... 343
21.2.3 Client Match .......................................................................................................................... 344
21.2.4 Access Point Control............................................................................................................. 347
21.2.5 Verifying ARM Configuration ................................................................................................ 348
21.3 Configuring Radio Settings ................................................................................................... 351
22.1 Deep Packet Inspection ........................................................................................................ 357
22.2 Enabling Application Visibility ............................................................................................... 358
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
9

Table of contents
23 Voice and Video ................................................................................................................................... 375
24 Services ............................................................................................................................................... 383
25 AP Management and Monitoring .......................................................................................................... 417
26 Uplink Configuration ............................................................................................................................. 425
27 Intrusion Detection ............................................................................................................................... 441
22.3 Application Visibility ............................................................................................................. 359
22.4 Enabling URL Visibility ......................................................................................................... 366
22.5 Configuring ACL Rules for Application and Application Categories .................................... 367
22.6 Configuring Web Policy Enforcement Service ..................................................................... 371
23.1 Wi-Fi Multimedia Traffic Management ................................................................................. 376
23.2 Media Classification for Voice and Video Calls ................................................................... 380
23.3 Enabling Enhanced Voice Call Tracking .............................................................................. 382
24.1 Configuring AirGroup ........................................................................................................... 383
24.1.1 Multicast DNS and Bonjour® Services ................................................................................ 384
24.1.2 DLNA UPnP Support ........................................................................................................... 385
24.1.3 AirGroup Features ............................................................................................................... 386
24.1.4 AirGroup Components ......................................................................................................... 388
24.1.5 Configuring AirGroup and AirGroup Services on an AP ...................................................... 389
24.1.6 Configuring AirGroup and ClearPass Policy Manager Interface in SCALANCE W ............. 393
24.2 Configuring an AP for RTLS Support ................................................................................... 395
24.3 Configuring an AP for Analytics and Location Engine Support ........................................... 397
24.4 Managing BLE Beacons ...................................................................................................... 400
24.5 Configuring OpenDNS Credentials ...................................................................................... 402
24.6 Integrating an AP with Palo Alto Networks Firewall ............................................................. 403
24.7 Integrating an AP with an XML API Interface ...................................................................... 406
24.8 CALEA Integration and Lawful Intercept Compliance.......................................................... 409
25.1 Managing an AP from AirWave ............................................................................................ 417
25.2 Configuring Organization String ........................................................................................... 421
25.3 Alternate Method for Defining Vendor Specific DHCP Options ........................................... 424
26.1 Uplink Interfaces .................................................................................................................. 425
26.2 Ethernet Uplink..................................................................................................................... 426
26.3 Cellular Uplink ...................................................................................................................... 429
26.4 Wi-Fi Uplink .......................................................................................................................... 431
26.5 Uplink Preferences and Switching ....................................................................................... 434
26.5.1 Enforcing Uplinks ................................................................................................................. 434
26.5.2 Setting an Uplink Priority ...................................................................................................... 435
26.5.3 Enabling Uplink Preemption ................................................................................................. 435
26.5.4 Switching Uplinks Based on VPN and Internet Availability .................................................. 436
26.5.5 Viewing Uplink Status and Configuration ............................................................................. 438
SCALANCE W1750D UI
10 Configuration Manual, , C79000-G8976-C451-02

Table of contents
28 Mesh AP Configuration ....................................................................................................................... 451
29 Mobility and Client Management ......................................................................................................... 455
30 Spectrum Monitor ................................................................................................................................ 461
31 AP Maintenance.................................................................................................................................. 471
32 Monitoring Devices and Logs .............................................................................................................. 481
33 Hotspot Profiles .................................................................................................................................. 497
34 ClearPass Guest Setup ....................................................................................................................... 519
27.1 Detecting and Classifying Rouge APs .................................................................................. 441
27.2 OS Fingerprinting .................................................................................................................. 442
27.3 Configuring Wireless Intrusion Protection and Detection Levels .......................................... 443
27.4 Configuring IDS ..................................................................................................................... 448
28.1 Mesh Network Overview ....................................................................................................... 451
28.2 Setting up SCALANCE W Mesh Network ............................................................................. 453
28.3 Configuring Wired Bridging on Ethernet 0 for Mesh Point .................................................... 454
29.1 Layer-3 Mobility Overview .................................................................................................... 455
29.2 Configuring L3-Mobility ......................................................................................................... 457
30.1 Understanding Spectrum Data ............................................................................................. 461
30.2 Configuring Spectrum Monitors and Hybrid APs .................................................................. 467
31.1 Upgrading an AP ................................................................................................................... 471
31.2 Backing up and Restoring AP Configuration Data ................................................................ 473
31.3 Converting an AP to a Remote AP and Campus AP ............................................................ 474
31.4 Resetting a Remote AP or Campus AP to an AP ................................................................. 478
31.5 Rebooting the AP .................................................................................................................. 479
32.1 Configuring SNMP ................................................................................................................ 481
32.2 Configuring a Syslog Server ................................................................................................. 486
32.3 Configuring TFTP Dump Server ........................................................................................... 489
32.4 Running Debug Commands ................................................................................................. 490
32.5 Uplink Bandwidth Monitoring ................................................................................................ 495
33.1 Understanding Hotspot Profiles ............................................................................................ 497
33.2 Configuring Hotspot Profiles ................................................................................................. 500
33.2.1 Creating Advertisement Profiles for Hotspot Configuration .................................................. 500
33.2.2 Creating a Hotspot Profile ..................................................................................................... 509
33.2.3 Associating an Advertisement Profile to a Hotspot Profile ................................................... 511
33.2.4 Creating a WLAN SSID and Associating Hotspot Profile ..................................................... 512
33.3 Sample Configuration ........................................................................................................... 514
34.1 Configuring ClearPass Guest ............................................................................................... 519
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
11

Table of contents
35 AP-VPN Deployment Scenarios ........................................................................................................... 529
A Appendix ............................................................................................................................................. 553
Tables
34.2 Verifying ClearPass Guest Setup ........................................................................................ 526
34.3 Troubleshooting ................................................................................................................... 527
35.1 Scenario 1 - IPsec: Single Datacenter Deployment with No Redundancy .......................... 530
35.2 Scenario 2 - IPsec: Single Datacenter with Multiple controllers for Redundancy ................ 535
35.3 Scenario 3 - IPsec: Multiple Datacenter Deployment with Primary and Backup
Controllers for Redundancy ................................................................................................. 541
35.4 Scenario 4 - GRE: Single Datacenter Deployment with No Redundancy ........................... 547
A.1 Terms ................................................................................................................................... 553
A.2 Acronyms and Abbreviations ............................................................................................... 556
A.3 Glossary ............................................................................................................................... 566
Table 1- 1 Typographical Conventions.......................................................................................................... 19
Table 5- 1 Managed Mode Commands ......................................................................................................... 42
Table 6- 1 Types of Alerts ............................................................................................................................. 75
Table 6- 2 Types of Alerts ............................................................................................................................. 76
Table 7- 1 System Parameters ...................................................................................................................... 81
Table 13- 1 External Captive Portal Redirect Parameters ............................................................................ 181
Table 14- 1 User Privileges ........................................................................................................................... 197
Table 14- 2 WPA and WPA-2 Features ........................................................................................................ 220
Table 14- 3 Recommended Authentication and Encryption Combinations ................................................... 221
Table 15- 1 Regular Expressions .................................................................................................................. 277
Table 16- 1
DHCP Relay and Option 82 ...................................................................................................... 289
Table 19- 1 VPN Protocols ............................................................................................................................ 304
Table 20- 1 AP-VPN Scalability ..................................................................................................................... 327
Table 20- 2 DHCP Scope and VPN Forwarding Modes Matrix..................................................................... 330
Table 20- 3 Branch Details ............................................................................................................................ 339
Table 23- 1 WMM AC to 802.1p Priority Mapping ......................................................................................... 376
Table 23- 2
WMM AC-DSCP Mapping ......................................................................................................... 377
Table 23- 3 SNMP Trap Details for VoIP Calls ............................................................................................. 382
Table 24- 1 SCALANCE W, ClearPass Policy Manager, and ClearPass Guest Requirements ................... 388
Table 24- 2 AirGroup Filtering Options .......................................................................................................... 389
Table 24- 3 XML API Command ................................................................................................................... 407
Table 24- 4 XML API Command Options ...................................................................................................... 408
SCALANCE W1750D UI
12 Configuration Manual, , C79000-G8976-C451-02

Table of contents
Figures
Table 30- 1 Device Summary and Channel Information ............................................................................... 462
Table 30- 2 Non-Wi-Fi Interferer Types ........................................................................................................ 463
Table 30- 3 Channel Details Information ....................................................................................................... 464
Table 30- 4 Channel Metrics ......................................................................................................................... 466
Table 32- 1 SNMP Parameters for AP .......................................................................................................... 481
Table 33- 1
Table 33- 2 Venue Types .............................................................................................................................. 503
Table 33- 3
Table 33- 4 Advertisement Profile Association Parameters .......................................................................... 512
Table 34- 1 Troubleshooting ......................................................................................................................... 527
Table 35- 1 AP Configuration for Scenario 1—IPsec: Single Datacenter Deployment with No
Table 35- 2
Table 35- 3 AP Configuration for Scenario 3—IPsec: Multiple Datacenter Deployment .............................. 543
NAI Realm Profile Configuration Parameters ........................................................................... 502
Hotspot Profile Configuration Parameters ................................................................................ 510
Redundancy ............................................................................................................................... 532
AP Configuration for Scenario 2—IPsec: Single Datacenter with Multiple controllers for
Redundancy ............................................................................................................................... 537
Figure 4-1 Login Screen ................................................................................................................................ 34
Figure 6-1 Connectivity Summary ................................................................................................................. 45
Figure 6-2 SCALANCE W Main Window ....................................................................................................... 47
Figure 6-3
Figure 6-4
Figure 6-5
Figure 6-6
Figure 6-7
Figure 6-8
Figure 6-9
Figure 6-10
Figure 6-11
Figure 6-12
Figure 6-13
Figure 6-14 Channel Availability Map for Clients ............................................................................................ 72
Figure 6-15
Figure 6-16 Client Alerts .................................................................................................................................. 75
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
VPN Window for IPsec Configuration
IDS Window: Intrusion Detection
IDS Window: Intrusion Protection
Wired Window
.............................................................................................................................. 58
Services Window: Default View
DHCP Servers Window
................................................................................................................ 60
RF Dashboard in the Monitoring Pane
RF Trends for Access Point
RF Trends for Clients
......................................................................................................... 66
................................................................................................................... 66
.......................................................................................... 56
................................................................................................. 57
................................................................................................ 57
................................................................................................... 59
........................................................................................ 64
Usage Trends Graphs in the Default View
Client Distribution on AP Radio
Alerts Link
.................................................................................................................................... 74
.................................................................................................... 72
.................................................................................. 68
13

Table of contents
Figure 6-17 Active Faults ................................................................................................................................. 76
Figure 6-18 Fault History ................................................................................................................................. 76
Figure 6-19 Intrusion Detection ....................................................................................................................... 78
Figure 6-20 AirGroup Link ............................................................................................................................... 79
Figure 6-21 Configuration Link ........................................................................................................................ 79
Figure 8-1 AP Settings - Provisioning Master AP .......................................................................................... 97
Figure 9-1 Uplink VLAN Detection ............................................................................................................... 101
Figure 11-1 WLAN Settings Tab .................................................................................................................... 110
Figure 11-2 VLAN Tab ................................................................................................................................... 117
Figure 11-3 Security Tab: Enterprise ............................................................................................................. 121
Figure 11-4 Security Tab: Personal ............................................................................................................... 122
Figure 11-5 Security Tab: Open .................................................................................................................... 123
Figure 12-1 Hierarchical Deployment ............................................................................................................ 160
Figure 13-1 Captive Portal Rule for Internal Splash Page Type ................................................................... 191
Figure 13-2 Captive Portal Rule for External Splash Page Type .................................................................. 191
Figure 14-1 Adding a User ............................................................................................................................ 199
Figure 14-2 Configuring WISPr Authentication ............................................................................................. 233
Figure 14-3 Loading Certificate through AirWave ......................................................................................... 240
Figure 14-4 Server Certificate ....................................................................................................................... 240
Figure 14-5 Selecting the Group ................................................................................................................... 241
Figure 15-1 Firewall Settings - ALG Protocols .............................................................................................. 250
Figure 15-2 Firewall Settings - Protection Against Wired Attacks ................................................................. 251
Figure 15-3 Inbound Firewall Rules - New Rule Window .............................................................................. 255
Figure 15-4 Firewall Settings -Management Subnets .................................................................................. 258
Figure 15-5 Roles - New Rule ....................................................................................................................... 262
Figure 15-6 Configuring RADIUS Attributes on the RADIUS Server ............................................................ 274
Figure 15-7 VLAN Assignment Rule Window ................................................................................................ 275
Figure 16-1 New DHCP Scope: Distributed DHCP Mode ............................................................................. 285
Figure 16-2 DHCP Servers Window .............................................................................................................. 292
Figure 19-1 IPsec Configuration .................................................................................................................... 306
Figure 19-2 Manual GRE Configuration ........................................................................................................ 309
Figure 19-3 Aruba GRE Configuration .......................................................................................................... 312
Figure 19-4 L2TPv3 Tunneling ...................................................................................................................... 314
Figure 19-5 Tunnel Configuration .................................................................................................................. 315
Figure 19-6 Session Configuration ................................................................................................................ 316
Figure 19-7 Tunneling— Routing .................................................................................................................. 323
SCALANCE W1750D UI
14 Configuration Manual, , C79000-G8976-C451-02

Table of contents
Figure 22-1 AppRF Dashboard ..................................................................................................................... 359
Figure 22-2 Application Categories Chart: Client View ................................................................................. 360
Figure 22-3 Application Categories List: Client View .................................................................................... 360
Figure 22-4 Application Categories Chart: AP View ..................................................................................... 361
Figure 22-5 Applications Chart: Client View .................................................................................................. 361
Figure 22-6 Applications List: Client View ..................................................................................................... 362
Figure 22-7 Application Chart: Access Point View ........................................................................................ 362
Figure 22-8 Web Categories Chart: Client View ........................................................................................... 363
Figure 22-9 Web Categories List: Client View............................................................................................... 363
Figure 22-10 Web Categories Chart: Access Point View ................................................................................ 364
Figure 22-11 Web Reputation Chart: Client View ........................................................................................... 364
Figure 22-12 Web Reputation List: Client View.............................................................................................. 365
Figure 22-13 Web Reputation Chart: AP View ................................................................................................ 365
Figure 22-14 Web Policy Enforcement ........................................................................................................... 371
Figure 24-1 AirGroup Enables Personal Device Sharing .............................................................................. 384
Figure 24-2 Bonjour Services and AirGroup Architecture ............................................................................. 385
Figure 24-3 DLNA UPnP Services and AirGroup Architecture ..................................................................... 386
Figure 24-4 AirGroup in a Higher-Education Environment ............................................................................ 387
Figure 24-5 AirGroup Configuration .............................................................................................................. 390
Figure 24-6 RTLS Window ............................................................................................................................ 395
Figure 24-7 Services Window - ALE Integration ........................................................................................... 398
Figure 24-8 Services Window: Network Integration Tab ............................................................................... 404
Figure 24-9 AP to CALEA Server .................................................................................................................. 410
Figure 24-10 AP to CALEA Server through VPN ............................................................................................ 411
Figure 25-1 Adding an AP in VisualRF .......................................................................................................... 419
Figure 26-1 Uplink Types .............................................................................................................................. 425
Figure 26-2 Uplink Status .............................................................................................................................. 426
Figure 27-1 Intrusion Detection ..................................................................................................................... 441
Figure 27-2 Wireless Intrusion Detection ...................................................................................................... 443
Figure 27-3 Wireless Intrusion Protection ..................................................................................................... 445
Figure 27-4 Containment Methods ................................................................................................................ 447
Figure 29-1 Routing of traffic when the client is away from its home network .............................................. 455
Figure 29-2 L3 Mobility Window .................................................................................................................... 458
Figure 30-1 Device List .................................................................................................................................. 462
Figure 30-2 Channel Details .......................................................................................................................... 464
Figure 30-3 Channel Metrics for the 2.4 GHz Radio Channel ....................................................................... 465
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
15

Table of contents
Figure 30-4 Channel Metrics for the 5 GHz Radio Channel .......................................................................... 466
Figure 31-1 Maintenance—Convert Tab ....................................................................................................... 475
Figure 31-2 Converting an AP to Campus AP ............................................................................................... 476
Figure 31-3 Stand-Alone AP Conversion ...................................................................................................... 477
Figure 31-4 Rebooting the AP ....................................................................................................................... 479
Figure 32-1 Monitoring Tab: SNMP Configuration Parameters .................................................................... 482
Figure 32-2 SNMPv3 User ............................................................................................................................ 483
Figure 32-3 Syslog Server ............................................................................................................................. 486
Figure 34-1 Configure AirGroup Services ..................................................................................................... 519
Figure 34-2 Add a New Controller for AirGroup Services ............................................................................. 520
Figure 34-3 Configure AirGroup Services: Controller Settings ..................................................................... 521
Figure 34-4 Configuration > Identity > Local Users Selection ....................................................................... 522
Figure 34-5 Create an AirGroup Administrator .............................................................................................. 523
Figure 34-6 Create an AirGroup Operator ..................................................................................................... 524
Figure 34-7 Local Users UI Screen ............................................................................................................... 524
Figure 34-8 Create a Device ......................................................................................................................... 525
Figure 34-9 ClearPass Guest- Register Shared Device ................................................................................ 525
Figure 35-1 Scenario 1 - IPsec: Single datacenter Deployment with No Redundancy ................................. 531
Figure 35-2 Scenario 2 - IPsec: Single Datacenter with Multiple controllers for Redundancy ...................... 536
Figure 35-3 Scenario 3 - IPsec: Multiple Datacenter Deployment with Primary and Backup Controllers
for Redundancy .......................................................................................................................... 542
Figure 35-4 Scenario 4 - GRE: Single Datacenter Deployment with No Redundancy ................................. 548
SCALANCE W1750D UI
16 Configuration Manual, , C79000-G8976-C451-02
Security information
Siemens provides products and solutions with industrial security functions that support the
secure operation of plants, systems, machines and networks.
In order to protect plants, systems, machines and networks against cyber threats, it is
necessary to implement – and continuously maintain – a holistic, state-of-the-art industrial
security concept. Siemens’ products and solutions constitute one element of such a concept.
Customers are responsible for preventing unauthorized access to their plants, systems,
machines and networks. Such systems, machines and components should only be
connected to an enterprise network or the internet if and to the extent such a connection is
necessary and only when appropriate security measures (e.g. firewalls and/or network
segmentation) are in place.
For additional information on industrial security measures that may be implemented, please
visit: https://www.siemens.com/industrialsecurity
Siemens’ products and solutions undergo continuous development to make them more
secure. Siemens strongly recommends that product updates are applied as soon as they are
available and that the latest product versions are used. Use of product versions that are no
longer supported, and failure to apply the latest updates may increase customer’s exposure
to cyber threats.
To stay informed about product updates, subscribe to the Siemens Industrial Security RSS
Feed under https://www.siemens.com/industrialsecurity
SCALANCE W1750D UI
Configuration Manual, 02/2018 , C79000-G8976-C451-02
17

About this guide
SCALANCE W1750D UI
18 Configuration Manual, 02/2018, C79000-G8976-C451-02

1
Intended Audience
Related Documents
Conventions
Style Type
Description
books.
System items
Commands
typed exactly as shown.
This User Guide describes the features supported by SCALANCE W and provides detailed
instructions for setting up and configuring the SCALANCE W network
This guide is intended for administrators who configure and use APs.
In addition to this document, the SCALANCE W product documentation includes the
following:
● Access Point Installation Guides
● Quick Start Guide
● CLI Function Manual
The following conventions are used throughout this manual to emphasize important
concepts:
Table 1- 1 Typographical Conventions
Italics
This style is used to emphasize important terms and to mark the titles of
This fixed-width font depicts the following:
• Sample screen output
• System prompts
• Filenames, software devices, and specific commands when mentioned in
the text.
In the command examples, this style depicts the keywords that must be
<Arguments>
In the command examples, italicized text within angle brackets represents
items that you should replace with information appropriate to your specific
situation. For example:
# send
In this example, you would type “send” at the system prompt exactly as
shown, followed by the text of the message you wish to send. Do not type the
angle brackets.
<text message>
SCALANCE W1750D UI
Configuration Manual, 02/2018, C79000-G8976-C451-02
19

About this guide
Style Type
Description
[Optional]
brackets.
{Item A | Item B}
type the braces or bars.
Service & Support
Command examples enclosed in brackets are optional. Do not type the
In the command examples, items within curled braces and separated by a
vertical bar represent the available choices. Enter only one choice. Do not
In addition to the product documentation, also check out the comprehensive online
information platform of Siemens Industry Online Support at the following Internet address:
(https://support.industry.siemens.com/cs/de/en/
Apart from news, there you will also find:
● Project information: Manuals, FAQs, downloads, application examples etc.
● Contacts, Technical Forum
● The option to submit a support query
(https://support.industry.siemens.com/My/ww/en/requests
)
):
● Our service offer:
Right across our products and systems, we provide numerous services that support you
in every phase of the life of your machine or system - from planning and implementation
to commissioning, through to maintenance and modernization.
You will find contact data on the Internet at the following address:
https://www.automation.siemens.com/aspa_app/?ci=yes&lang=en
SCALANCE W1750D UI
20 Configuration Manual, 02/2018, C79000-G8976-C451-02
2
General
Physical access
Software (security functions)
To prevent unauthorized access, note the following security recommendations.
● You should make regular checks to make sure that the device meets these
recommendations and/or other security guidelines.
● Evaluate your plant as a whole in terms of security. Use a cell protection concept with
suitable products (
security/pages/default.aspx).
● When the internal and external network are disconnected, an attacker cannot access
internal data from the outside. Therefore operate the device only within a protected
network area.
● For communication via non-secure networks use additional devices with VPN
functionality to encrypt and authenticate the communication.
https://www.industry.siemens.com/topics/global/en/industrial-
● Terminate management connections correctly (WBM. Telnet, SSH etc.).
● Restrict physical access to the device to qualified personnel.
● Keep the software up to date. Check regularly for security updates of the product. You
will find information on this on the Internet pages "Industrial Security
(https://www.siemens.com/industrialsecurity
● Inform yourself regularly about security advisories and bulletins published by Siemens
ProductCERT (https://www.siemens.com/cert/en/cert-security-advisories.htm
● Only activate protocols that you really require to use the device.
● Use the security functions such as address translation with NAT (Network Address
Translation) or NAPT (Network Address Port Translation) to protect receiving ports from
access by third parties.
● Restrict access to the device with a firewall or rules in an access control list (ACL -
Access Control List).
● If RADIUS authentication is via remote access, make sure that the communication is
within the secured network area or is via a secure channel.
)"
).
● The option of VLAN structuring provides good protection against DoS attacks and
unauthorized access. Check whether this is practical or useful in your environment.
● Enable logging functions. Use the central logging function to log changes and access
attempts centrally. Check the logging information regularly.
SCALANCE W1750D UI
Configuration Manual, 02/2018, C79000-G8976-C451-02
21

Security recommendations
Passwords
Keys and certificates
● Configure a Syslog server to forward all logs to a central location.
● Use WPA2/ WPA2-PSK with AES to protect the WLAN.
● Define rules for the use of devices and assignment of passwords.
● Regularly update passwords and keys to increase security.
● Change all default passwords for users before you operate the device.
● Only use passwords with a high password strength. Avoid weak passwords for example
password1, 123456789, abcdefgh.
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
● Do not use the same password for different users and systems or after it has expired.
● This section deals with the security keys and certificates you require to set up HTTPS (
HyperText Transfer Protocol Secured Socket Layer).
● We strongly recommend that you create your own HTTPS certificates and make them
available. There are preset certificates and keys on the device. The preset and
automatically created HTTPS certificates are self-signed. We recommend that you use
HTTPS certificates signed either by a reliable external or by an internal certification
authority. The HTTPS certificate checks the identity of the device and controls the
encrypted data exchange. You can install the HTTPS certificate via the SCALANCE W
UI, see "Uploading Certificate".
● Handle user-defined private keys with great caution if you use user-defined SSH or SSL
keys.
● Use the certification authority including key revocation and management to sign the
certificates.
● Verify certificates and fingerprints on the server and client to avoid "man in the middle"
attacks.
● We recommend that you use certificates with a key length of 2048 bits.
● Change keys and certificates immediately, if there is a suspicion of compromise
SCALANCE W1750D UI
22 Configuration Manual, 02/2018, C79000-G8976-C451-02

Security recommendations
Secure/non-secure protocols
● Avoid and disable non-secure protocols, for example Telnet and TFTP. For historical
reasons, these protocols are still available, however not intended for secure applications.
Use non-secure protocols on the device with caution.
● The following protocols provide secure alternatives:
– SNMPv1/v2 → SNMPv3
Check whether use of SNMPv1 is necessary. SNMPv1 is classified as non-secure.
Use the option of preventing write access. The product provides you with suitable
setting options. If SNMP is enabled, change the community names. If no unrestricted
access is necessary, restrict access with SNMP. Use SNMPv3 in conjunction with
passwords.
– HTTP → HTTPS
– Telnet → SSH
– SNTP → NTP
● Use secure protocols when access to the device is not prevented by physical protection
measures.
● To prevent unauthorized access to the device or network, take suitable protective
measures against non-secure protocols.
● If you require non-secure protocols and services, operate the device only within a
protected network area.
● Restrict the services and protocols available to the outside to a minimum.
SCALANCE W1750D UI
Configuration Manual, , C79000-G8976-C451-02
23
Security recommendations
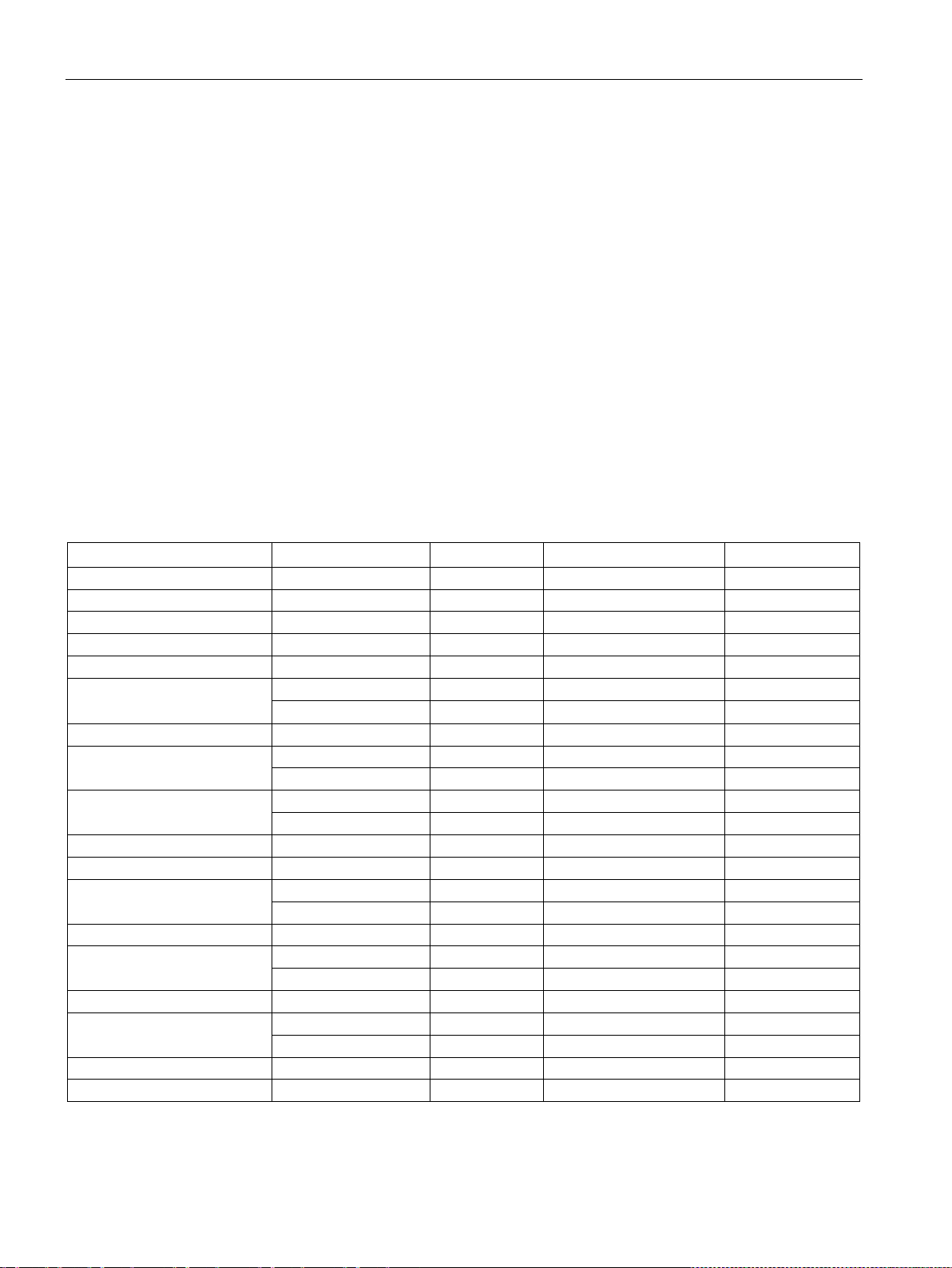
Available protocols per port
Protocol
Port number
Port status
Factory setting of the port
Authentication
Air Monitor
UDP/1144
Open
Open
Yes
Airgroup
UDP/53536
Open
Open
Yes
Airgroup Master to slave
UDP/53535
Open
Open
No
Bootps
UDP/67
Open
Open
No
Captive portal
TCP/8080
Open
Open
Yes
UDP/1067
Open
Open
No
UDP/4011
Open
Open
No
DTLS
UDP/4433
Open
Open
Yes
HTTP
TCP/80
Open
Open
Yes
TCP/4343
Open
Open
Yes
HTTPS
TCP/43430
Open
Open
Yes
TCP/443
Open
Open
Yes
mDNS
UDP/5353
Open
Open
No
NTP
UDP/123
Open
Open
No
UDP/8209
Open
Open
No
UDP/8211
Open
Open
No
Proprietary (dTable)
UDP/8612
Open
Open
No
RADIUS
UDP/1616
Open
Open
No
UDP/1892
Open
Open
No
SNMP
UDP/161
Open
Open
Yes
SSH
TCP/22
Open
Open
Yes
TCP/2322
Open
Open
Yes
Syslog
UDP/514
Open
Open
No
Telnet
TCP/23
Open
Open
Yes
The following list provides you with an overview of the open ports on this device. The table
includes the following columns:
● Protocol
All protocols that the device supports
● Port number
Port number assigned to the protocol
● Port status
– Open: The port is always open and cannot be closed.
● Factory setting
– Open: The factory setting of the port is "Open".
– Closed: The factory setting of the port is "Closed".
● Authentication
Specifies whether or not the protocol is authenticated.
DHCP
Proprietary
SCALANCE W1750D UI
24 Configuration Manual, 02/2018, C79000-G8976-C451-02

3
3.1
Overview
SCALANCE W is a simple, easy to deploy turn-key WLAN solution consisting of one or more
APs. An Ethernet port with routable connectivity to the Internet or a self-enclosed network is
used for deploying an SCALANCE W Wireless Network. An SCALANCE W Access Point
(AP) can be installed at a single site or deployed across multiple geographically-dispersed
locations. Designed specifically for easy deployment, and proactive management of
networks, SCALANCE W is ideal for small customers or remote locations without any on-site
IT administrator.
SCALANCE W consists of an AP and a Virtual Controller. The Virtual Controller resides
within one of the APs. In an SCALANCE W deployment scenario, only the first AP needs to
be configured. After the first AP is configured, the other APs inherit all the required
configuration information from the Virtual Controller. SCALANCE W continually monitors the
network to determine the AP that should function as the Virtual Controller at any time, and
the Virtual Controller will move from one AP to another as necessary without impacting
network performance.
SCALANCE W1750D UI
Configuration Manual, 02/2018, C79000-G8976-C451-02
25

About SCALANCE W
3.2
SCALANCE W UI
Continue login
Login
Note
To view the SCALANCE W UI, ensure that JavaScript is enabled on the web browser.
Note
The SCALANCE W UI logs out automatically if the window is inactive for
3.2 SCALANCE W UI
The SCALANCE W User Interface (UI) provides a standard web-based interface that allows
you to configure and monitor a Wi-Fi network. SCALANCE W is accessible through a
standard web browser from a remote management console or workstation and can be
launched using the following browsers:
● Microsoft Internet Explorer 11 or earlier
● Apple Safari 6.0 or later
● Google Chrome 23.0.1271.95 or later
● Mozilla Firefox 17.0 or later
If the SCALANCE W UI is launched through an unsupported browser, a warning message is
displayed along with a list of recommended browsers. However, the users are allowed to
login using the
link on the
page.
15 minutes.
SCALANCE W1750D UI
26 Configuration Manual, 02/2018, C79000-G8976-C451-02

About SCALANCE W
3.3
SCALANCE W CLI
3.3 SCALANCE W CLI
The SCALANCE W Command Line Interface (CLI) is a text-based interface that is
accessible through a Secure Shell (SSH) session.
SSH access requires that you configure an IP address and a default gateway on the AP and
connect the AP to your network. This is typically performed when the SCALANCE W network
on an AP is set up.
SCALANCE W1750D UI
Configuration Manual, 02/2018, C79000-G8976-C451-02
27

About SCALANCE W
3.3 SCALANCE W CLI
SCALANCE W1750D UI
28 Configuration Manual, 02/2018, C79000-G8976-C451-02

4
4.1
Setting up an SCALANCE W Network
4.1.1
Connecting an AP
Before installing an AP:
● Ensure that you have an Ethernet cable of the required length to connect an AP to the
home router.
● Ensure that you have one of the following power sources:
– IEEE 802.3af/at-compliant Power over Ethernet (PoE) source. The PoE source can be
any power source equipment (PSE) switch or a midspan PSE device.
– AP power adapter kit.
Perform the following procedures to set up the SCALANCE W network:
1. Connecting an AP (Page 29)
2. Assigning an IP address to the AP (Page 30)
Based on the type of the power source used, perform one of the following steps to connect
an AP to the power source:
● PoE switch—Connect the Ethernet 0 (Enet0) port of the AP to the appropriate port on the
PoE switch.
● PoE midspan—Connect the Enet0 port of the AP to the appropriate port on the PoE
midspan.
● AC to DC power adapter—Connect the 12V DC power jack socket to the AC to DC power
adapter.
SCALANCE W1750D UI
Configuration Manual, 02/2018, C79000-G8976-C451-02
29

Setting up an AP
4.1.2
Assigning an IP address to the AP
Note
If there is no DHCP service on the network,
static IP is not assigned, the AP obtains an IP automatically within the 169.254 subnet.
Assigning a Static IP
Console
apboot
Enter
apboot
apboot
printenv
4.1 Setting up an SCALANCE W Network
The AP needs an IP address for network connectivity. When you connect an AP to a
network, it receives an IP address from a DHCP server.
To obtain an IP address for an AP:
1. Ensure that the DHCP service is enabled on the network.
2. Connect the Enet0 port of AP to a switch or router using an Ethernet cable.
3. Connect the AP to a power source. The AP receives an IP address provided by the
switch or router.
the AP can be assigned a static IP address. If a
To assign a static IP to an AP:
1. Connect a terminal, PC, or workstation running a terminal emulation program to the
port on the AP.
2. Turn on the AP. An autoboot countdown prompt that allows you to interrupt the normal
startup process and access
3. Press
4. In the
5. Use the
key before the timer expires. The AP goes into the
Hit <Enter> to stop autoboot: 0
apboot>
apboot> setenv ipaddr 192.0.2.0
apboot> setenv netmask 255.255.255.0
apboot> setenv gatewayip 192.0.2.2
apboot> save
Saving Environment to Flash... Un-Protected 1 sectors
.done
Erased 1 sectors
Writing
apboot> printenv
mode, execute the following commands to assign a static IP to the AP.
command to view the configuration.
is displayed.
mode.
SCALANCE W1750D UI
30 Configuration Manual, 02/2018, C79000-G8976-C451-02
 Loading...
Loading...