Page 1

Preface
RUGGEDCOM ROS
v4.1
User Guide
Introduction
Using ROS
Device Management
System Administration
Setup and Configuration
Troubleshooting
1
2
3
4
5
6
For RSG2200, M2200
12/2014
RC1119-EN-02
Page 2

RUGGEDCOM ROS
User Guide
Copyright © 2014 Siemens Canada Ltd.
All rights reserved. Dissemination or reproduction of this document, or evaluation and communication of its contents, is not authorized
except where expressly permitted. Violations are liable for damages. All rights reserved, particularly for the purposes of patent application or
trademark registration.
This document contains proprietary information, which is protected by copyright. All rights are reserved. No part of this document may be
photocopied, reproduced or translated to another language without the prior written consent of Siemens Canada Ltd..
Disclaimer Of Liability
Siemens has verified the contents of this manual against the hardware and/or software described. However, deviations between the product
and the documentation may exist.
Siemens shall not be liable for any errors or omissions contained herein or for consequential damages in connection with the furnishing,
performance, or use of this material.
The information given in this document is reviewed regularly and any necessary corrections will be included in subsequent editions. We
appreciate any suggested improvements. We reserve the right to make technical improvements without notice.
Registered Trademarks
ROX™, Rugged Operating System On Linux™, CrossBow™ and ELAN™ are trademarks of Siemens Canada Ltd. . ROS® is a registered
trademark of Siemens Canada Ltd..
Other designations in this manual might be trademarks whose use by third parties for their own purposes would infringe the rights of the
owner.
Third Party Copyrights
Siemens recognizes the following third party copyrights:
• Copyright © 2004 GoAhead Software, Inc. All Rights Reserved.
Security Information
Siemens provides products and solutions with industrial security functions that support the secure operation of plants, machines, equipment
and/or networks. They are important components in a holistic industrial security concept. With this in mind, Siemens ’ products and solutions
undergo continuous development. Siemens recommends strongly that you regularly check for product updates.
For the secure operation of Siemens products and solutions, it is necessary to take suitable preventive action (e.g. cell protection concept)
and integrate each component into a holistic, state-of-the-art industrial security concept. Third-party products that may be in use should also
be considered. For more information about industrial security, visit http://www.siemens.com/industrialsecurity.
To stay informed about product updates as they occur, sign up for a product-specific newsletter. For more information, visit http://
support.automation.siemens.com.
Warranty
Refer to the License Agreement for the applicable warranty terms and conditions, if any.
For warranty details, visit www.siemens.com/ruggedcom or contact a Siemens customer service representative.
Contacting Siemens
Address
Siemens Canada Ltd.
Industry Sector
300 Applewood Crescent
Concord, Ontario
Canada, L4K 5C7
Telephone
Toll-free: 1 888 264 0006
Tel: +1 905 856 5288
Fax: +1 905 856 1995
E-mail
ruggedcom.info.i-ia@siemens.com
Web
www.siemens.com/ruggedcom
ii
Page 3

RUGGEDCOM ROS
User Guide
Table of Contents
Table of Contents
Preface ................................................................................................................ xi
Conventions ....................................................................................................................................... xi
Alerts ......................................................................................................................................... xi
CLI Command Syntax ................................................................................................................ xii
Related Documents ............................................................................................................................ xii
System Requirements ........................................................................................................................ xii
Accessing Documentation .................................................................................................................. xiii
Training ............................................................................................................................................ xiii
Customer Support ............................................................................................................................. xiii
Chapter 1
Introduction .......................................................................................................... 1
1.1 Overview ..................................................................................................................................... 1
1.2 Security Recommendations and Considerations ............................................................................. 2
1.2.1 Security Recommendations ................................................................................................ 2
1.2.2 Key Files .......................................................................................................................... 3
1.2.2.1 SSL Certificates ...................................................................................................... 4
1.2.2.2 SSH Key Pairs ....................................................................................................... 6
1.3 Port Numbering Scheme .............................................................................................................. 7
1.4 Available Services by Port ............................................................................................................ 7
1.5 SNMP Management Interface Base (MIB) Support ......................................................................... 9
1.5.1 Supported Standard MIBs .................................................................................................. 9
1.5.2 Supported Proprietary RUGGEDCOM MIBs ...................................................................... 10
1.5.3 Supported Agent Capabilities ........................................................................................... 10
1.6 SNMP Traps .............................................................................................................................. 11
1.7 ModBus Management Support .................................................................................................... 13
1.7.1 ModBus Function Codes .................................................................................................. 13
1.7.2 ModBus Memory Map ...................................................................................................... 14
1.7.3 ModBus Memory Formats ................................................................................................ 19
1.7.3.1 Text ...................................................................................................................... 19
1.7.3.2 Cmd ..................................................................................................................... 20
1.7.3.3 Uint16 .................................................................................................................. 20
1.7.3.4 Uint32 .................................................................................................................. 20
1.7.3.5 PortCmd ............................................................................................................... 20
1.7.3.6 Alarm ................................................................................................................... 21
iii
Page 4

Table of Contents
RUGGEDCOM ROS
1.7.3.7 PSStatusCmd ....................................................................................................... 21
1.7.3.8 TruthValues .......................................................................................................... 22
1.8 Certificate and Key Requirements ............................................................................................... 23
Chapter 2
Using ROS ......................................................................................................... 25
2.1 Connecting to ROS .................................................................................................................... 25
2.1.1 Connecting Directly .......................................................................................................... 25
2.1.2 Connecting via the Network ............................................................................................. 26
2.2 Logging In ................................................................................................................................. 27
2.3 Logging Out ............................................................................................................................... 28
2.4 Using the Web Interface ............................................................................................................. 28
2.5 Using the Console Interface ........................................................................................................ 30
2.6 Using the Command Line Interface ............................................................................................. 32
2.6.1 Available CLI Commands ................................................................................................. 32
2.6.2 Tracing Events ................................................................................................................ 35
2.6.3 Executing Commands Remotely via RSH .......................................................................... 36
2.6.4 Using SQL Commands .................................................................................................... 36
2.6.4.1 Finding the Correct Table ...................................................................................... 37
2.6.4.2 Retrieving Information ........................................................................................... 37
2.6.4.3 Changing Values in a Table ................................................................................... 39
2.6.4.4 Resetting a Table .................................................................................................. 39
2.6.4.5 Using RSH and SQL ............................................................................................. 39
2.7 Selecting Ports in ROS ............................................................................................................... 40
2.8 Managing the Flash File System ................................................................................................. 40
2.8.1 Viewing a List of Flash Files ............................................................................................ 40
2.8.2 Viewing Flash File Details ................................................................................................ 41
2.8.3 Defragmenting the Flash File System ............................................................................... 42
2.9 Accessing BIST Mode ................................................................................................................ 42
User Guide
Chapter 3
Device Management .......................................................................................... 43
3.1 Viewing Product Information ....................................................................................................... 43
3.2 Viewing CPU Diagnostics ........................................................................................................... 45
3.3 Restoring Factory Defaults .......................................................................................................... 46
3.4 Uploading/Downloading Files ...................................................................................................... 47
3.4.1 Uploading/Downloading Files Using XMODEM .................................................................. 48
3.4.2 Uploading/Downloading Files Using a TFTP Client ............................................................ 48
3.4.3 Uploading/Downloading Files Using a TFTP Server ........................................................... 49
3.4.4 Uploading/Downloading Files Using an SFTP Server ......................................................... 50
3.5 Managing Logs .......................................................................................................................... 50
iv
Page 5

RUGGEDCOM ROS
User Guide
3.6 Managing Ethernet Ports ............................................................................................................ 56
3.7 Managing IP Interfaces ............................................................................................................... 77
3.8 Managing IP Gateways .............................................................................................................. 81
3.9 Configuring IP Services .............................................................................................................. 84
3.10 Managing Remote Monitoring .................................................................................................... 85
Table of Contents
3.5.1 Viewing Local Logs ......................................................................................................... 51
3.5.2 Clearing Local Logs ......................................................................................................... 51
3.5.3 Configuring the Local System Log .................................................................................... 52
3.5.4 Managing Remote Logging .............................................................................................. 52
3.5.4.1 Configuring the Remote Syslog Client .................................................................... 53
3.5.4.2 Viewing a List of Remote Syslog Servers ............................................................... 53
3.5.4.3 Adding a Remote Syslog Server ............................................................................ 54
3.5.4.4 Deleting a Remote Syslog Server .......................................................................... 55
3.6.1 Controller Protection Through Link Fault Indication (LFI) .................................................... 57
3.6.2 Viewing the Status of Ethernet Ports ................................................................................ 58
3.6.3 Viewing Statistics for All Ethernet Ports ............................................................................ 59
3.6.4 Viewing Statistics for Specific Ethernet Ports ..................................................................... 60
3.6.5 Clearing Statistics for Specific Ethernet Ports .................................................................... 62
3.6.6 Managing SFP Transceivers ............................................................................................ 62
3.6.6.1 Configuring an SFP Port ....................................................................................... 63
3.6.6.2 Monitoring an SFP Port ......................................................................................... 63
3.6.6.3 Displaying Information for an SFP Port ................................................................... 64
3.6.7 Configuring an Ethernet Port ............................................................................................ 65
3.6.8 Configuring Port Rate Limiting .......................................................................................... 68
3.6.9 Configuring Port Mirroring ................................................................................................ 69
3.6.10 Configuring Link Detection ............................................................................................. 70
3.6.11 Detecting Cable Faults ................................................................................................... 72
3.6.11.1 Viewing Cable Diagnostics Results ....................................................................... 72
3.6.11.2 Performing Cable Diagnostics .............................................................................. 74
3.6.11.3 Clearing Cable Diagnostics .................................................................................. 75
3.6.11.4 Determining the Estimated Distance To Fault (DTF) ............................................... 76
3.6.12 Resetting Ethernet Ports ................................................................................................ 76
3.7.1 Viewing a List of IP Interfaces .......................................................................................... 77
3.7.2 Adding an IP Interface ..................................................................................................... 78
3.7.3 Deleting an IP Interface ................................................................................................... 80
3.8.1 Viewing a List of IP Gateways .......................................................................................... 81
3.8.2 Adding an IP Gateway ..................................................................................................... 82
3.8.3 Deleting an IP Gateway ................................................................................................... 83
3.10.1 Managing RMON History Controls .................................................................................. 86
3.10.1.1 Viewing a List of RMON History Controls .............................................................. 86
v
Page 6

Table of Contents
RUGGEDCOM ROS
3.10.1.2 Adding an RMON History Control ......................................................................... 86
3.10.1.3 Deleting an RMON History Control ....................................................................... 88
3.10.2 Managing RMON Alarms ............................................................................................... 89
3.10.2.1 Viewing a List of RMON Alarms ........................................................................... 90
3.10.2.2 Adding an RMON Alarm ...................................................................................... 91
3.10.2.3 Deleting an RMON Alarm .................................................................................... 93
3.10.3 Managing RMON Events ................................................................................................ 94
3.10.3.1 Viewing a List of RMON Events ........................................................................... 95
3.10.3.2 Adding an RMON Event ...................................................................................... 95
3.10.3.3 Deleting an RMON Event .................................................................................... 97
3.11 Upgrading/Downgrading Firmware ............................................................................................. 97
3.11.1 Upgrading Firmware ....................................................................................................... 98
3.11.2 Downgrading Firmware .................................................................................................. 98
3.12 Resetting the Device ................................................................................................................ 99
3.13 Decommissioning the Device .................................................................................................. 100
Chapter 4
System Administration ...................................................................................... 101
User Guide
4.1 Configuring the System Information ........................................................................................... 101
4.2 Customizing the Login Screen ................................................................................................... 102
4.3 Configuring Passwords ............................................................................................................. 102
4.4 Managing Alarms ..................................................................................................................... 105
4.4.1 Viewing a List of Pre-Configured Alarms ......................................................................... 105
4.4.2 Viewing and Clearing Latched Alarms ............................................................................. 106
4.4.3 Configuring an Alarm ..................................................................................................... 107
4.4.4 Authentication Related Security Alarms ........................................................................... 110
4.4.4.1 Security Alarms for Login Authentication ............................................................... 110
4.4.4.2 Security Messages for Port Authentication ............................................................ 112
4.5 Managing the Configuration File ................................................................................................ 113
4.5.1 Configuring Data Encryption ........................................................................................... 113
4.5.2 Updating the Configuration File ...................................................................................... 114
4.6 Managing an Authentication Server ........................................................................................... 115
4.6.1 Managing RADIUS Authentication ................................................................................... 115
4.6.1.1 Configuring the RADIUS Server ........................................................................... 116
4.6.1.2 Configuring the RADIUS Client ............................................................................ 116
4.6.2 Managing TACACS+ Authentication ................................................................................ 118
4.6.2.1 Configuring TACACS+ ......................................................................................... 118
4.6.2.2 Configuring User Priviliges ................................................................................... 119
vi
Page 7

RUGGEDCOM ROS
User Guide
Chapter 5
Table of Contents
Setup and Configuration .................................................................................. 121
5.1 Configuring the DHCP Relay Agent ........................................................................................... 121
5.2 Managing Virtual LANs ............................................................................................................. 122
5.2.1 VLAN Concepts ............................................................................................................. 123
5.2.1.1 Tagged vs. Untagged Frames .............................................................................. 123
5.2.1.2 Native VLAN ....................................................................................................... 123
5.2.1.3 The Management VLAN ...................................................................................... 124
5.2.1.4 Edge and Trunk Port Types ................................................................................. 124
5.2.1.5 Ingress and Egress Rules ................................................................................... 124
5.2.1.6 Forbidden Ports List ............................................................................................ 125
5.2.1.7 VLAN-Aware and VLAN-Unaware Modes ............................................................. 125
5.2.1.8 GARP VLAN Registration Protocol (GVRP) .......................................................... 126
5.2.1.9 PVLAN Edge ...................................................................................................... 127
5.2.1.10 QinQ ................................................................................................................ 127
5.2.1.11 VLAN Advantages ............................................................................................. 128
5.2.2 Viewing a List of VLANs ................................................................................................ 130
5.2.3 Configuring VLANs Globally ........................................................................................... 130
5.2.4 Configuring VLANs for Specific Ethernet Ports ................................................................. 131
5.2.5 Managing Static VLANs ................................................................................................. 133
5.2.5.1 Viewing a List of Static VLANs ............................................................................ 134
5.2.5.2 Adding a Static VLAN ......................................................................................... 134
5.2.5.3 Deleting a Static VLAN ........................................................................................ 136
5.3 Managing Spanning Tree Protocol ............................................................................................. 137
5.3.1 RSTP Operation ............................................................................................................ 137
5.3.1.1 RSTP States and Roles ...................................................................................... 138
5.3.1.2 Edge Ports ......................................................................................................... 139
5.3.1.3 Point-to-Point and Multipoint Links ....................................................................... 140
5.3.1.4 Path and Port Costs ............................................................................................ 140
5.3.1.5 Bridge Diameter .................................................................................................. 141
5.3.1.6 eRSTP ............................................................................................................... 141
5.3.1.7 Fast Root Failover .............................................................................................. 142
5.3.2 RSTP Applications ......................................................................................................... 142
5.3.2.1 RSTP in Structured Wiring Configurations ............................................................ 143
5.3.2.2 RSTP in Ring Backbone Configurations ............................................................... 144
5.3.2.3 RSTP Port Redundancy ...................................................................................... 146
5.3.3 MSTP Operation ............................................................................................................ 146
5.3.3.1 MSTP Regions and Interoperability ...................................................................... 147
5.3.3.2 MSTP Bridge and Port Roles ............................................................................... 148
5.3.3.3 Benefits of MSTP ................................................................................................ 149
vii
Page 8

Table of Contents
5.4 Managing Classes of Service .................................................................................................... 167
5.5 Managing MAC Addresses ........................................................................................................ 172
5.6 Managing Time Services ........................................................................................................... 179
5.7 Managing SNMP ...................................................................................................................... 182
RUGGEDCOM ROS
User Guide
5.3.3.4 Implementing MSTP on a Bridged Network ........................................................... 150
5.3.4 Configuring STP Globally ............................................................................................... 150
5.3.5 Configuring STP for Specific Ethernet Ports .................................................................... 152
5.3.6 Configuring eRSTP ........................................................................................................ 154
5.3.7 Viewing Global Statistics for STP .................................................................................... 156
5.3.8 Viewing STP Statistics for Ethernet Ports ........................................................................ 158
5.3.9 Managing Multiple Spanning Tree Instances .................................................................... 159
5.3.9.1 Viewing Statistics for Global MSTIs ...................................................................... 160
5.3.9.2 Viewing Statistics for Port MSTIs ......................................................................... 161
5.3.9.3 Configuring the MST Region Identifier .................................................................. 162
5.3.9.4 Configuring a Global MSTI .................................................................................. 163
5.3.9.5 Configuring an MSTI for an Ethernet Port ............................................................. 164
5.3.10 Clearing Spanning Tree Protocol Statistics .................................................................... 166
5.4.1 Configuring Classes of Service Globally .......................................................................... 168
5.4.2 Configuring Classes of Service for Specific Ethernet Ports ................................................ 168
5.4.3 Configuring Priority to CoS Mapping ............................................................................... 170
5.4.4 Configuring DSCP to CoS Mapping ................................................................................ 171
5.5.1 Viewing a List of MAC Addresses ................................................................................... 172
5.5.2 Configuring MAC Address Learning Options .................................................................... 173
5.5.3 Configuring MAC Address Flooding Options .................................................................... 174
5.5.4 Managing Static MAC Addresses .................................................................................... 176
5.5.4.1 Viewing a List of Static MAC Addresses ............................................................... 176
5.5.4.2 Adding a Static MAC Address .............................................................................. 176
5.5.4.3 Deleting a Static MAC Address ............................................................................ 178
5.5.5 Purging All Dynamic MAC Addresses ............................................................................. 179
5.6.1 Configuring the Time and Date ....................................................................................... 180
5.6.2 Configuring NTP ............................................................................................................ 181
5.7.1 Managing SNMP Users .................................................................................................. 183
5.7.1.1 Viewing a List of SNMP Users ............................................................................. 183
5.7.1.2 Adding an SNMP User ........................................................................................ 184
5.7.1.3 Deleting an SNMP User ...................................................................................... 186
5.7.2 Managing Security-to-Group Mapping ............................................................................. 187
5.7.2.1 Viewing a List of Security-to-Group Maps ............................................................. 188
5.7.2.2 Adding a Security-to-Group Map .......................................................................... 188
5.7.2.3 Deleting a Security-to-Group Map ........................................................................ 189
5.7.3 Managing SNMP Groups ............................................................................................... 190
viii
Page 9

RUGGEDCOM ROS
User Guide
5.8 Managing Network Discovery .................................................................................................... 193
5.9 Managing Multicast Filtering ...................................................................................................... 202
5.10 Managing Port Security ........................................................................................................... 215
5.11 Managing Link Aggregation ..................................................................................................... 223
Table of Contents
5.7.3.1 Viewing a List of SNMP Groups ........................................................................... 191
5.7.3.2 Adding an SNMP Group ...................................................................................... 191
5.7.3.3 Deleting an SNMP Group .................................................................................... 193
5.8.1 Network Discovery Concepts .......................................................................................... 194
5.8.1.1 Link Layer Discovery Protocol (LLDP) .................................................................. 194
5.8.1.2 RUGGEDCOM Discovery Protocol (RCDP) .......................................................... 194
5.8.2 Configuring LLDP Globally ............................................................................................. 195
5.8.3 Configuring LLDP for an Ethernet Port ............................................................................ 197
5.8.4 Enabling/Disabling RCDP ............................................................................................... 198
5.8.5 Viewing Global Statistics and Advertised System Information ............................................ 199
5.8.6 Viewing Statistics for LLDP Neighbors ............................................................................ 200
5.8.7 Viewing Statistics for LLDP Ports .................................................................................... 201
5.9.1 Multicast Filtering Concepts ............................................................................................ 202
5.9.1.1 IGMP ................................................................................................................. 202
5.9.1.2 GMRP (GARP Multicast Registration Protocol) ...................................................... 206
5.9.2 Viewing a List of IP Multicast Groups .............................................................................. 208
5.9.3 Viewing a Summary of Multicast Groups ......................................................................... 209
5.9.4 Configuring IGMP .......................................................................................................... 209
5.9.5 Configuring GMRP Globally ............................................................................................ 211
5.9.6 Configuring GMRP for Specific Ethernet Ports ................................................................. 211
5.9.7 Managing Static Multicast Groups ................................................................................... 213
5.9.7.1 Viewing a List of Static Multicast Groups .............................................................. 213
5.9.7.2 Adding a Static Multicast Group ........................................................................... 213
5.9.7.3 Deleting a Static Multicast Group ......................................................................... 215
5.10.1 Port Security Concepts ................................................................................................. 216
5.10.1.1 Static MAC Address-Based Authentication .......................................................... 216
5.10.1.2 IEEE 802.1x Authentication ............................................................................... 216
5.10.1.3 IEEE 802.1X Authentication with MAC Address-Based Authentication ................... 217
5.10.1.4 Assigning VLANS with Tunnel Attributes ............................................................. 218
5.10.2 Viewing a List of Authorized MAC Addresses ................................................................ 218
5.10.3 Configuring Port Security .............................................................................................. 219
5.10.4 Configuring IEEE 802.1X .............................................................................................. 221
5.11.1 Link Aggregation Concepts ........................................................................................... 224
5.11.1.1 Rules and Limitations ........................................................................................ 224
5.11.1.2 Link Aggregation and Layer 2 Features .............................................................. 225
5.11.1.3 Link Aggregation and Physical Layer Features .................................................... 225
ix
Page 10

Table of Contents
RUGGEDCOM ROS
5.11.2 Managing Port Trunks .................................................................................................. 225
5.11.2.1 Viewing a List of Port Trunks ............................................................................. 226
5.11.2.2 Adding a Port Trunk .......................................................................................... 226
5.11.2.3 Deleting a Port Trunk ........................................................................................ 228
Chapter 6
Troubleshooting ................................................................................................ 229
6.1 General .................................................................................................................................... 229
6.2 Ethernet Ports .......................................................................................................................... 230
6.3 Spanning Tree ......................................................................................................................... 230
6.4 VLANs ..................................................................................................................................... 231
User Guide
x
Page 11

RUGGEDCOM ROS
User Guide
Preface
This guide describes v4.1 of ROS (Rugged Operating System) running on the RUGGEDCOM RSG2200. It
contains instructions and guidelines on how to use the software, as well as some general theory.
It is intended for use by network technical support personnel who are familiar with the operation of networks. It is
also recommended for us by network and system planners, system programmers, and line technicians.
IMPORTANT!
Some of the parameters and options described may not be available depending on variations in the
device hardware. While every attempt is made to accurately describe the specific parameters and
options available, this Guide should be used as a companion to the Help text included in the software.
Conventions
This User Guide uses the following conventions to present information clearly and effectively.
Preface
Alerts
The following types of alerts are used when necessary to highlight important information.
DANGER!
DANGER alerts describe imminently hazardous situations that, if not avoided, will result in death or
serious injury.
WARNING!
WARNING alerts describe hazardous situations that, if not avoided, may result in serious injury and/or
equipment damage.
CAUTION!
CAUTION alerts describe hazardous situations that, if not avoided, may result in equipment damage.
IMPORTANT!
IMPORTANT alerts provide important information that should be known before performing a procedure
or step, or using a feature.
NOTE
NOTE alerts provide additional information, such as facts, tips and details.
Conventions xi
Page 12

Preface
CLI Command Syntax
The syntax of commands used in a Command Line Interface (CLI) is described according to the following
conventions:
Example Description
RUGGEDCOM ROS
User Guide
command
command parameter
command parameter1 parameter2
command parameter1 parameter2
command [parameter1 | parameter2]
command {parameter3 | parameter4}
command parameter1 parameter2 {parameter3 |
parameter4}
Related Documents
Other documents that may be of interest include:
• RUGGEDCOM RSG2200 Installation Guide
• RUGGEDCOM M2200 Installation Guide
• RUGGEDCOM RSG2200 Data Sheet
• RUGGEDCOM M2200 Data Sheet
• RUGGEDCOM Fiber Guide
• RUGGEDCOM Wireless Guide
• White Paper: Rapid Spanning Tree in Industrial Networks
Commands are in bold.
Parameters are in plain text.
Parameters are listed in the order they must be entered.
Parameters in italics must be replaced with a user-defined value.
Alternative parameters are separated by a vertical bar (|).
Square brackets indicate a required choice between two or more
parameters.
Curly brackets indicate an optional parameter(s).
All commands and parameters are presented in the order they must
be entered.
System Requirements
Each workstation used to connect to the ROS interface must meet the following system requirements:
• Must have one of the following Web browsers installed:
▪ Microsoft Internet Explorer 8.0 or higher
▪ Mozilla Firefox
▪ Google Chrome
▪ Iceweasel/IceCat (Linux Only)
• Must have a working Ethernet interface compatible with at least one of the port types on the RUGGEDCOM
device
• The ability to configure an IP address and netmask on the computer’s Ethernet interface
xii CLI Command Syntax
Page 13

RUGGEDCOM ROS
User Guide
Accessing Documentation
The latest Hardware Installation Guides and Software User Guides for most RUGGEDCOM products are
available online at www.siemens.com/ruggedcom.
For any questions about the documentation or for assistance finding a specific document, contact a Siemens
sales representative.
Training
Siemens offers a wide range of educational services ranging from in-house training of standard courses on
networking, Ethernet switches and routers, to on-site customized courses tailored to the customer's needs,
experience and application.
Siemens' Educational Services team thrives on providing our customers with the essential practical skills to make
sure users have the right knowledge and expertise to understand the various technologies associated with critical
communications network infrastructure technologies.
Siemens' unique mix of IT/Telecommunications expertise combined with domain knowledge in the utility,
transportation and industrial markets, allows Siemens to provide training specific to the customer's application.
For more information about training services and course availability, visit www.siemens.com/ruggedcom or
contact a Siemens sales representative.
Preface
Customer Support
Customer support is available 24 hours, 7 days a week for all Siemens customers. For technical support or
general information, contact Siemens Customer Support through any of the following methods:
• Online
Visit http://www.siemens.com/automation/support-request to submit a Support Request (SR) or check on the
status of an existing SR.
• Telephone
Call a local hotline center to submit a Support Request (SR). To locate a local hotline center, visit http://
www.automation.siemens.com/mcms/aspa-db/en/automation-technology/Pages/default.aspx.
• Mobile App
Install the Industry Online Support app by Siemens AG on any Android, Apple iOS or Windows mobile device
and be able to:
▪ Access Siemens' extensive library of support documentation, including FAQs, manuals, and much more
▪ Submit SRs or check on the status of an existing SR
▪ Find and contact a local contact person
▪ Ask questions or share knowledge with fellow Siemens customers and the support community
▪ And much more...
Accessing Documentation xiii
Page 14

RUGGEDCOM ROS
User Guide
Preface
Customer Support xiv
Page 15
RUGGEDCOM ROS
User Guide
Introduction
This chapter provides a basic overview of the ROS software. It describes the following topics:
• Section 1.1, “Overview”
• Section 1.2, “Security Recommendations and Considerations”
• Section 1.3, “Port Numbering Scheme”
• Section 1.4, “Available Services by Port”
• Section 1.5, “SNMP Management Interface Base (MIB) Support”
• Section 1.6, “SNMP Traps”
• Section 1.7, “ModBus Management Support”
• Section 1.8, “Certificate and Key Requirements”
Chapter 1
Introduction
Section 1.1
Overview
Welcome to the ROS Software User Guide for the RSG2200. This Guide describes the wide array of carrier
grade features made available by ROS (Rugged Operating System). These features include:
IMPORTANT!
The RSG2200/M2200 is not intended for use or resale as online control equipment in hazardous, highrisk environments that require fail-safe performance, such as nuclear facilities, aircraft navigation or
communication systems, air traffic control, direct life support machines or weapons systems, in which
the failure of the software could result in death, personal injury, or severe physical or environmental
damage.
Rugged Operating System (ROS) Features
• Simple plug and play operation - automatic learning,
negotiation and crossover detection
• MSTP 802.1Q-2005 (formerly 802.1s)
• RSTP (802.1w) and Enhanced Rapid Spanning Tree
(eRSTP™) network fault recovery (<5ms)
• Quality of Service (802.1p) for real-time traffic
• VLAN (802.1Q) with double tagging and GVRP
support
• Link aggregation (802.3ad)
• IGMP Snooping for multicast filtering
• Port rate limiting and broadcast storm limiting
• Port configuration, status, statistics, mirroring,
security
• SNTP time synchronization (client and server)
Cyber Security Features
• Muti-level user passwords
• SSH/SSL (128-bit encryption)
• Enable/disable ports, MAC based port security
• Port-based network access control (802.1X)
• VLAN (802.1Q) to segregate and secure network
traffic
• RADIUS centralized password management
• SNMPv3 authentication and 56-bit encryption
Management Features
• Web-based, Telnet, CLI management interfaces
• SNMP v1/v2/v3 (56-bit encryption)
• Remote Monitoring (RMON)
• Rich set of diagnostics with logging and alarms
Overview 1
Page 16

Chapter 1
Introduction
• Industrial automation features (eg. Modbus)
Section 1.2
RUGGEDCOM ROS
User Guide
Security Recommendations and Considerations
The following describes important security-related recommendations and suggestions that should be considered
before implementing the RSG2200 on any network:
• Section 1.2.1, “Security Recommendations”
• Section 1.2.2, “Key Files”
Section 1.2.1
Security Recommendations
To prevent unauthorized access to the device, note the following security recommendations:
• Do not connect the device to the Internet. Deploy the device only within a secure network perimeter.
• Replace the default passwords for all user accounts and processes (where applicable) before the device is
deployed.
• Use strong passwords. Avoid weak passwords such as password1, 123456789, abcdefgh, etc. For more
information about creating strong passwords, refer to the password requirements in Section 4.3, “Configuring
Passwords”.
• Make sure passwords are protected and not shared with unauthorized personnel.
• Passwords should not be re-used across different usernames and systems, or after they expire.
• When RADIUS authentication is done remotely, make sure all communications are within the security perimeter
or on a secure channel.
• SSL and SSH keys are accessible to users who connect to the device via the serial console. Make sure to take
appropriate precautions when shipping the device beyond the boundaries of the trusted environment:
▪ Replace the SSH and SSL keys with throwaway keys prior to shipping.
▪ Take the existing SSH and SSL keys out of service. When the device returns, create and program new keys
for the device.
• Restrict physical access to the device to only trusted personnel. A person with malicious intent could extract
critical information, such as certificates, keys, etc. (user passwords are protected by hash codes), or reprogram
the device.
• Control access to the serial console to the same degree as any physical access to the device. Access to the
serial console allows for potential access to the ROS boot loader, which includes tools that may be used to gain
complete access to the device.
• Only enable services that will be used on the device, including physical ports. Unused physical ports could
potentially be used to gain access to the network behind the device.
• If SNMP is enabled, limit the number of IP addresses that can connect to the device and change the
community names. Also configure SNMP to raise a trap upon authentication failures. For more information,
refer to Section 5.7, “Managing SNMP”.
• Avoid using insecure services such as Telnet and TFTP, or disable them completely if possible. These services
are available for historical reasons and are disabled by default.
2 Security Recommendations and Considerations
Page 17
RUGGEDCOM ROS
User Guide
• Limit the number of simultaneous Web Server, Telnet and SSH sessions allowed.
• Configure remote system logging to forward all logs to a central location. For more information, refer to
Section 3.5, “Managing Logs”.
• Configuration files are provided in the CSV (comma separated values) format for ease of use. Make sure
configuration files are properly protected when they exist outside of the device. For instance, encrypt the files,
store them in a secure place, and do not transfer them via insecure communication channels.
• Management of the configuration file, certificates and keys is the responsibility of the device owner. Before
returning the device to Siemens for repair, make sure encryption is disabled (to create a cleartext version of the
configuration file) and replace the current certificates and keys with temporary throwaway certificates and keys
that can be destroyed upon the device's return.
• Be aware of any non-secure protocols enabled on the device. While some protocols, such as HTTPS and
SSH, are secure, others, such as Telnet and RSH, were not designed for this purpose. Appropriate safeguards
against non-secure protocols should be taken to prevent unauthorized access to the device/network.
• Configure port security features on access ports to prevent a third-party from launching various attacks that can
harm the network or device. For more information, refer to Section 5.10, “Managing Port Security”.
• Periodically audit the device to make sure it complies with these recommendations and/or any internal security
policies.
Chapter 1
Introduction
Section 1.2.2
Key Files
ROS uses security keys to establish secure remote logins (SSH) and Web access (SSL).
It is strongly recommended that a unique SSL certificate and SSH keys be created and provisioned. New ROS based units from Siemens will be shipped with a unique certificate and keys preconfigured in the ssl.crt and
ssh.keys flash files.
The default and auto-generated SSL certificates are self-signed. It is recommended to use an SSL certificate that
is either signed by a trusted third-party Certificate Authority (CA) or by an organization's own CA. This technique
is described in the Siemens application note: Creating/Uploading SSH Keys and SSL Certificates to ROS Using
Windows, available from www.siemens.com/ruggedcom.
The sequence of events related to Key Management during an upgrade to ROS v4.1 or later is as follows:
NOTE
The auto-generation of SSH keys is not available for Non-Controlled (NC) versions of ROS.
• On first boot, ROS will start the SSH and SSL services using the default keys.
• Immediately after boot, ROS will start to generate a unique SSL certificate and SSH key pair, and save each
one to its corresponding flash file. This process may take several minutes to complete. As each one is created,
the corresponding service is immediately restarted with the new keys.
• At any time during the key generation process, custom keys can be uploaded. The custom keys will take
precedence over both the default and auto-generated keys.
• On subsequent boot, if there is a valid ssl.crt file, the default certificate will not be used for SSL. If there is a
valid ssh.keys file, the default SSH key will not be used.
• At any time, new keys may be uploaded or generated by ROS using the sslkeygen or sshkeygen CLI
commands.
The following sections describe SSL certificates and SSH key pairs in more detail:
Key Files 3
Page 18

Chapter 1
Introduction
RUGGEDCOM ROS
• Section 1.2.2.1, “SSL Certificates”
• Section 1.2.2.2, “SSH Key Pairs”
Section 1.2.2.1
SSL Certificates
ROS supports SSL certificates that conform to the following specifications:
• X.509 v3 digital certificate format
• PEM format
• RSA key pair, 512 to 2048 bits
The RSA key pair used in the default certificate and in those generated by ROS uses a public key of 1024 bits in
length.
NOTE
RSA keys smaller than 1024 bits in length are not recommended. Support is only included here for
compatibility with legacy equipment.
User Guide
NOTE
The default certificate and keys are common to all ROS versions without a certificate or key files. That
is why it is important to either allow the key auto-generation to complete or to provision custom keys. In
this way, one has at least unique, and at best, traceable and verifiable keys installed when establishing
secure communication with the unit.
NOTE
RSA key generation times increase depending on the key length. 1024 bit RSA keys may take several
minutes to generate, whereas 2048 bit keys may take significantly longer. A typical modern PC system,
however, can generate these keys in seconds.
The following (bash) shell script fragment uses the openssl command line utility to generate a self-signed
X.509 v3 SSL certificate with a 1024 bit RSA key suitable for use in ROS . Note that two standard PEM files are
required: the SSL certificate and the RSA private key file. These are concatenated into the resulting ssl.crt file,
which may then be uploaded to ROS:
# RSA key size:
BITS=1024
# 20 years validity:
DAYS=7305
# Values that will be stored in the Distinguished Name fields:
COUNTRY_NAME=CA # Two-letter country code
STATE_OR_PROVINCE_NAME=Ontario # State or Province
LOCALITY_NAME=Concord # City
ORGANIZATION=Ruggedcom.com # Your organization's name
ORGANIZATION_CA=${ORGANIZATION}_CA # Your Certificate Authority
COMMON_NAME=RC # The DNS or IP address of the ROS unit
ORGANIZATIONAL_UNIT=ROS # Organizational unit name
# Variables used in the construction of the certificate
REQ_SUBJ="/C=${COUNTRY_NAME}/ST=${STATE_OR_PROVINCE_NAME}/L=${LOCALITY_NAME}/O=${ORGANIZATION}/OU=
${ORGANIZATIONAL_UNIT}/CN=${COMMON_NAME}/"
REQ_SUBJ_CA="/C=${COUNTRY_NAME}/ST=${STATE_OR_PROVINCE_NAME}/L=${LOCALITY_NAME}/O=${ORGANIZATION_CA}/
OU=${ORGANIZATIONAL_UNIT}/"
4 SSL Certificates
Page 19

RUGGEDCOM ROS
User Guide
########################################################################
# Make the self-signed SSL certificate and RSA key pair:
openssl req -x509 -newkey rsa:${BITS} -nodes \
-days ${DAYS} -subj ${REQ_SUBJ} \
-keyout ros_ssl.key \
-out ros_ssl.crt
# Concatenate Cert and Key into a single file suitable for upload to ROS:
# Note that cert must precede the RSA key:
cat ros_ssl.crt ros_ssl.key > ssl.crt
For information on creating SSL certificates for use with ROS in a Microsoft Windows environment, refer to the
following Siemens application note: Creating/Uploading SSH Keys and SSL Certificates to ROS Using Windows.
The following is an example of a self-signed SSL certificate generated by ROS:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
ca:01:2d:c0:bf:f9:fd:f2
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=CA, ST=Ontario, L=Concord, O=RuggedCom.com, OU=RC, CN=ROS
Validity
Not Before: Dec 6 00:00:00 2012 GMT
Not After : Dec 7 00:00:00 2037 GMT
Subject: C=CA, ST=Ontario, L=Concord, O=RuggedCom.com, OU=RC, CN=ROS
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:83:e8:1f:02:6b:cd:34:1f:01:6d:3e:b6:d3:45:
b0:18:0a:17:ae:3d:b0:e9:c6:f2:0c:af:b1:3e:e7:
fd:f2:0e:75:8d:6a:49:ce:47:1d:70:e1:6b:1b:e2:
fa:5a:1b:10:ea:cc:51:41:aa:4e:85:7c:01:ea:c3:
1e:9e:98:2a:a9:62:48:d5:27:1e:d3:18:cc:27:7e:
a0:94:29:db:02:5a:e4:03:51:16:03:3a:be:57:7d:
3b:d1:75:47:84:af:b9:81:43:ab:90:fd:6d:08:d3:
e8:5b:80:c5:ca:29:d8:45:58:5f:e4:a3:ed:9f:67:
44:0f:1a:41:c9:d7:62:7f:3f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
EC:F3:09:E8:78:92:D6:41:5F:79:4D:4B:7A:73:AD:FD:8D:12:77:88
X509v3 Authority Key Identifier:
keyid:EC:F3:09:E8:78:92:D6:41:5F:79:4D:4B:7A:73:AD:FD:8D:12:77:88
DirName:/C=CA/ST=Ontario/L=Concord/O=RuggedCom.com/OU=RC/CN=ROS
serial:CA:01:2D:C0:BF:F9:FD:F2
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha1WithRSAEncryption
64:cf:68:6e:9f:19:63:0e:70:49:a6:b2:fd:09:15:6f:96:1d:
4a:7a:52:c3:46:51:06:83:7f:02:8e:42:b2:dd:21:d2:e9:07:
5c:c4:4c:ca:c5:a9:10:49:ba:d4:28:fd:fc:9d:a9:0b:3f:a7:
84:81:37:ca:57:aa:0c:18:3f:c1:b2:45:2a:ed:ad:dd:7f:ad:
00:04:76:1c:f8:d9:c9:5c:67:9e:dd:0e:4f:e5:e3:21:8b:0b:
37:39:8b:01:aa:ca:30:0c:f1:1e:55:7c:9c:1b:43:ae:4f:cd:
e4:69:78:25:5a:a5:f8:98:49:33:39:e3:15:79:44:37:52:da:
28:dd
Chapter 1
Introduction
SSL Certificates 5
Page 20

Chapter 1
RUGGEDCOM ROS
Introduction
Section 1.2.2.2
SSH Key Pairs
Controlled versions of ROS support SSH public/private key pairs that conform to the following specifications:
• PEM format
• DSA key pair, 512 to 2048 bits in length
The DSA key pair used in the default key pair and in those generated by ROS uses a public key of 1024 bits in
length.
NOTE
DSA keys smaller than 1024 bits in length are not recommended, and support is only included here for
compatibility with legacy equipment.
NOTE
DSA key generation times increase depending on the key length. 1024 bit RSA keys may take several
minutes to generate, whereas 2048 bit keys may take significantly longer. A typical modern PC system,
however, can generate these keys in seconds.
The following (bash) shell script fragment uses the ssh-keygen command line utility to generate a 1024 bit DSA
key suitable for use in ROS . The resulting ssh.keys file, which may then be uploaded to ROS:
User Guide
# DSA key size:
BITS=1024
# Make an SSH key pair:
ssh-keygen -t dsa -b 1024 -N '' -f ssh.keys
The following is an example of an SSH key generated by ROS:
Private-Key: (1024 bit)
priv:
00:b2:d3:9d:fa:56:99:a5:7a:ba:1e:91:c5:e1:35:
77:85:e8:c5:28:36
pub:
6f:f3:9e:af:e6:d6:fd:51:51:b9:fa:d5:f9:0a:b7:
ef:fc:d7:7c:14:59:52:48:52:a6:55:65:b7:cb:38:
2e:84:76:a3:83:62:d0:83:c5:14:b2:6d:7f:cc:f4:
b0:61:0d:12:6d:0f:5a:38:02:67:a4:b7:36:1d:49:
0a:d2:58:e2:ff:4a:0a:54:8e:f2:f4:c3:1c:e0:1f:
9b:1a:ee:16:e0:e9:eb:c8:fe:e8:16:99:e9:61:81:
ed:e4:f2:58:fb:3b:cb:c3:f5:9a:fa:ed:cd:39:51:
47:90:5d:6d:1b:27:d5:04:c5:de:57:7e:a7:a3:03:
e8:fb:0a:d5:32:89:40:12
P:
00:f4:81:c1:9b:5f:1f:eb:ac:43:2e:db:dd:77:51:
6e:1c:62:8d:4e:95:c6:e7:b9:4c:fb:39:9c:9d:da:
60:4b:0f:1f:c6:61:b0:fc:5f:94:e7:45:c3:2b:68:
9d:11:ba:e1:8a:f9:c8:6a:40:95:b9:93:7c:d0:99:
96:bf:05:2e:aa:f5:4e:f0:63:02:00:c7:c2:52:c7:
1a:70:7c:f7:e5:fe:dd:3d:57:02:86:ae:d4:89:20:
ca:4b:46:80:ea:de:a1:30:11:5c:91:e2:40:d4:a3:
82:c5:40:3b:25:8e:d8:b2:85:cc:f5:9f:a9:1d:ea:
0a:ac:77:95:ee:d6:f7:61:e3
Q:
00:d5:db:48:18:bd:ec:69:99:eb:ff:5f:e1:40:af:
20:80:6d:5c:b1:23
G:
01:f9:a1:91:c0:82:12:74:49:8a:d5:13:88:21:3e:
32:ea:f1:74:55:2b:de:61:6c:fd:dd:f5:e1:c5:03:
68:b4:ad:40:48:58:62:6c:79:75:b1:5d:42:e6:a9:
6 SSH Key Pairs
Page 21

RUGGEDCOM ROS
2
1
4
3
6
5
8
7
10
9
12
11
User Guide
97:86:37:d8:1e:e5:65:09:28:86:2e:6a:d5:3d:62:
50:06:b8:d3:f9:d4:9c:9c:75:84:5b:db:96:46:13:
f0:32:f0:c5:cb:83:01:a8:ae:d1:5a:ac:68:fb:49:
f9:b6:8b:d9:d6:0d:a7:de:ad:16:2b:23:ff:8e:f9:
3c:41:16:04:66:cf:e8:64:9e:e6:42:9a:d5:97:60:
c2:e8:9e:f4:bc:8f:6f:e0
Section 1.3
Port Numbering Scheme
For quick identification, each port on an RSG2200/M2200 device is assigned a number. All port numbers are silkscreened on the device.
Chapter 1
Introduction
Figure 1: RSG2200/M2200 Port Numbering (Typical)
Use these numbers to configure applicable features on select ports.
Section 1.4
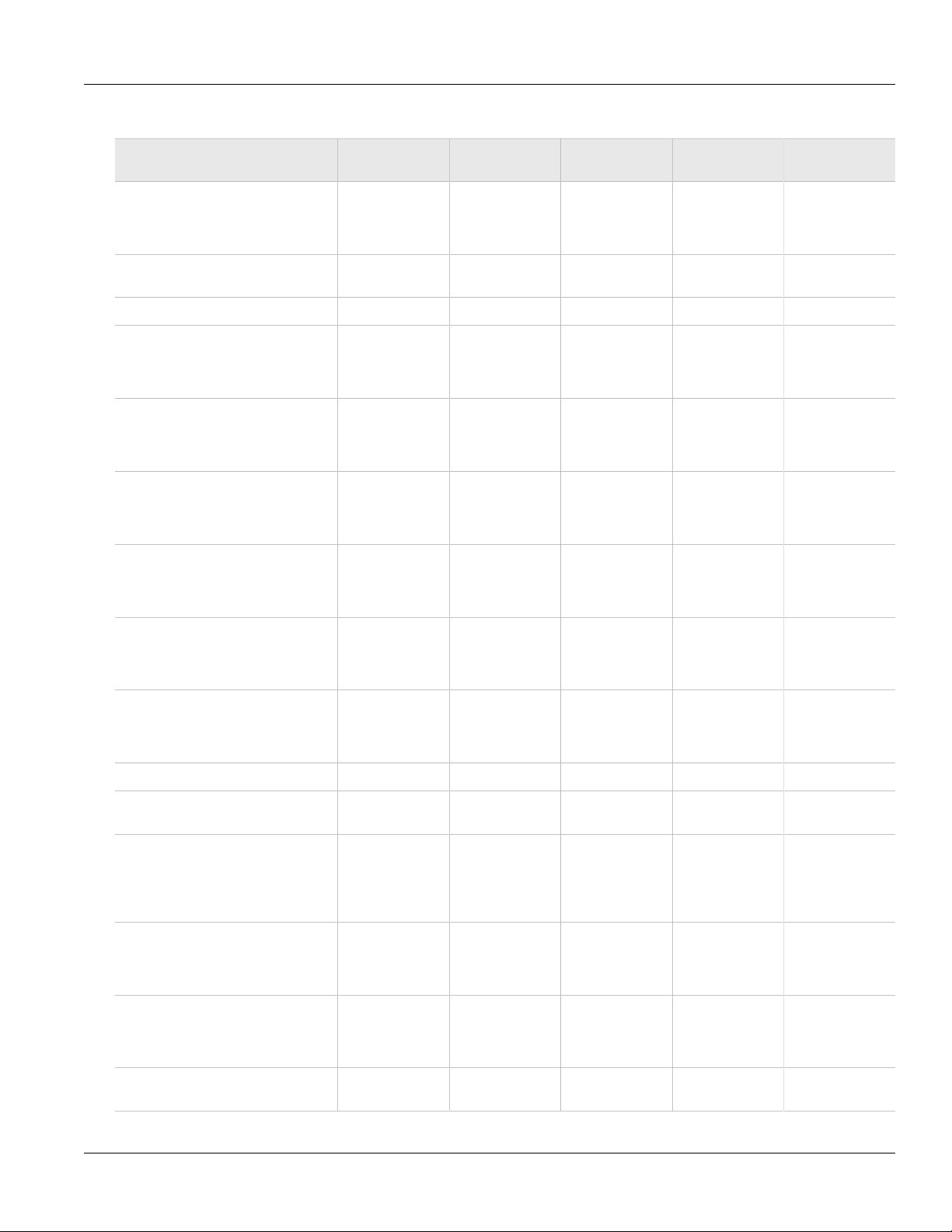
Available Services by Port
The following table lists the services available under ROS. This table includes the following information:
• Services
The service supported by the device.
• Port Number
The port number associated with the service.
• Port Open
The port state, whether it is always open and cannot be closed, or open only, but can be configured.
NOTE
In certain cases, the service might be disabled, but the port can still be open (e.g. TFTP).
• Port Default
• Access Authorized
The default state of the port (i.e. open or closed).
Port Numbering Scheme 7
Page 22
Chapter 1
Introduction
Denotes whether the ports/services are authenticated during access.
RUGGEDCOM ROS
User Guide
Services Port Number Port Open Port Default
Telnet TCP/23 Open
(configurable)
HTTP TCP/80 Open, redirects
to 443
HTTPS TCP/443 Open Open Yes
RSH TCP/512 Open
(configurable)
TFTP UDP/69 Open
(configurable)
SFTP TCP/22 Open Open Yes Only available
SNMP UDP/161 Open
(configurable)
Closed Yes Only available
Open —
Closed Yes Only available
Closed No Only available
Closed Yes Only available
Access
Authorized
Note
through two
management
interfaces.
through two
management
interfaces.
through two
management
interfaces.
through two
management
interfaces.
through two
management
interfaces.
SNTP UDP/123 Open - Always
SSH TCP/22 Open Open Yes Only available
ICMP — Open Open No
TACACS+ TCP/49
(configurable)
RADIUS UDP/1812
to send
(configurable),
opens random
port to listen to
Remote Syslog UDP/514
(configurable)
TCP Modbus (Server) TCP/502 Open Open No Only available
TCP Modbus (Switch) TCP/502 Open
might acts as
server
Open
(configurable)
Open
(configurable)
Open
(configurable)
(configurable)
Open No Only available
through two
management
interfaces.
through two
management
interfaces.
Closed Yes
Closed Yes Only available
through two
management
interfaces.
Closed No Only available
through two
management
interfaces.
through two
management
interfaces.
Closed No
8 Available Services by Port
Page 23
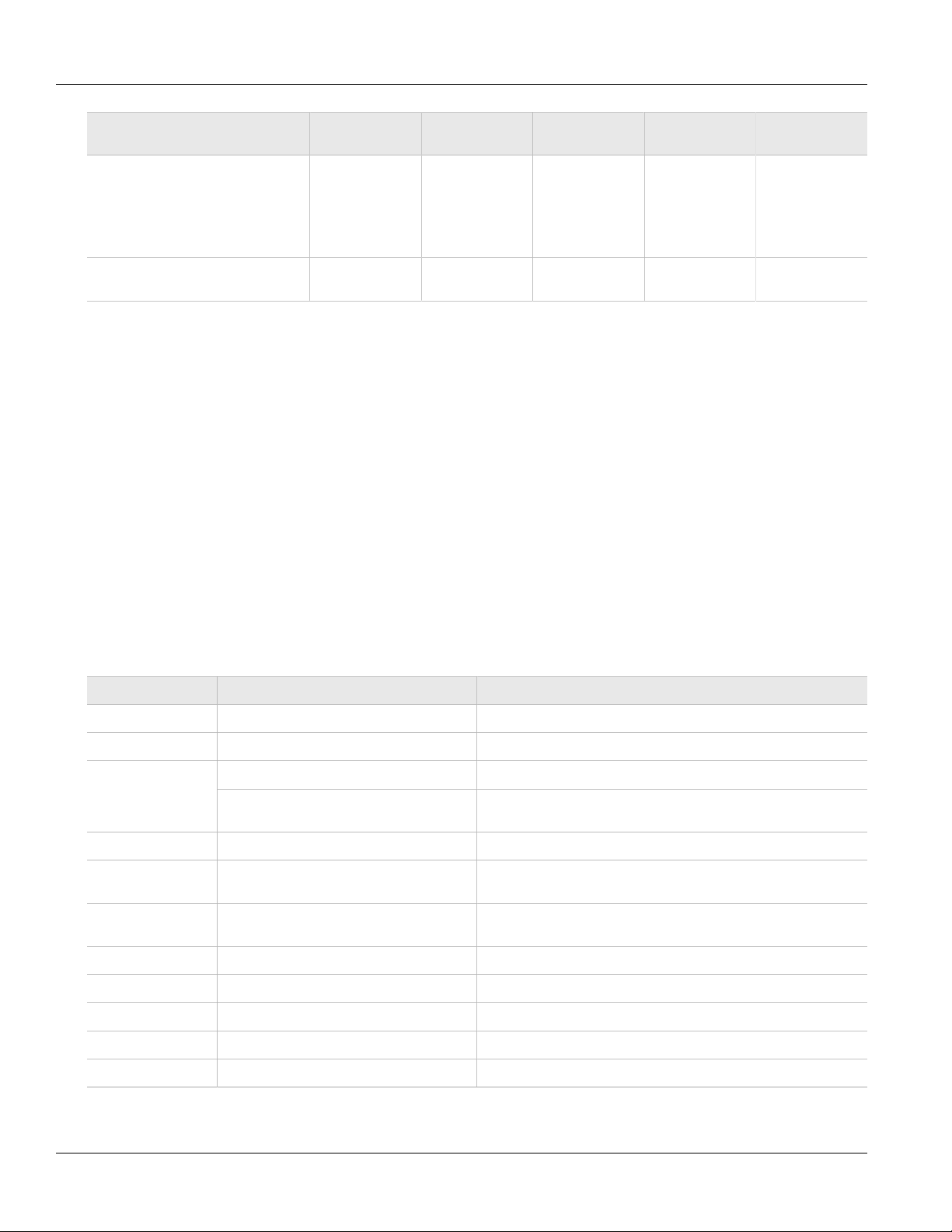
RUGGEDCOM ROS
User Guide
Chapter 1
Introduction
Services Port Number Port Open Port Default
DHCP, DHCP Agent UDP/67 sending
msg if enabled - if
received, always
come to CPU,
dropped if service
not configured
RCDP — Open
Open Open No
Closed Yes
(configurable)
Access
Authorized
Note
Section 1.5
SNMP Management Interface Base (MIB) Support
ROS supports a variety of standard MIBs, proprietary RUGGEDCOM MIBs and Agent Capabilities MIBs, all for
SNMP (Simple Network Management Protocol).
• Section 1.5.1, “Supported Standard MIBs”
• Section 1.5.2, “Supported Proprietary RUGGEDCOM MIBs”
• Section 1.5.3, “Supported Agent Capabilities”
Section 1.5.1
Supported Standard MIBs
ROS supports the following standard MIBs:
Standard MIB Name Title
RFC 2578 SNMPv2-SMI Structure of Management Information Version 2
RFC 2579 SNMPv2-TC Textual Convention s for SMIv2
SNMPv2-CONF Conformance Statements for SMIv2RFC 2580
IANAifType Enumerated Values of the ifType Object Defined ifTable defined in
RFC 1907 SNMPv2-MIB Management Information Base for SNMPv2
RFC 2011 IP-MIB SNMPv2 Mnagement Information Base for Internet Protocol using
RFC 2012 TCP-MIB SNMPv2 Management Information Base for the Transmission
RFC 2013 UDP-MIB Management Information Base for the UDP using SMIv2
RFC 1659 RS-232-MIB Definitions of Managed Objects for RS-232-like Hardware Devices
RFC 2863 IF-MIB The Interface Group MIB
IF-MIB
SMIv2
Control Protocol using SMIv2
RFC 2819 RMON-MIB Remote Network Monitoring (RMON) management Information base
RFC 4188 BRIDGE-MIB Definitions of Managed Objects for Bridges
SNMP Management Interface Base (MIB) Support 9
Page 24

Chapter 1
Introduction
Standard MIB Name Title
RUGGEDCOM ROS
User Guide
RFC 4318 RSTP-MIB Definitions of Managed Objects for Bridges with Rapid Spanning
RFC 3411 SNMP-FRAMEWORK-MIB An Architecture for Describing Simple Network Management
RFC 3414 SNMP-USER-BASED-SM-MIB User-based Security Model (USM) for Version 3 of the Simple
RFC 3415 SNMP-VIEW-BASED-ACM-MIB View-bsed Access Control Model (VACM) for the Simple
IEEE 802.3ad IEEE8023-LAG-MIB Management Information Base Module for Link Aggregation
IEEE 802.1AB-2005 LLDP-MIB Management Information Base Module for LLDP Configuration,
RFC 4363 Q-BRIDGE-MIB Definitions of Managed Objects for Bridges with Traffic Classes,
Tree Protocol
Protocol (SNMP) Management Framework
Network Management Protocol (SNMPv3)
Management Protocol (SNMP)
Statistics, Local System Data and Remote Systems Data
Components
Multicast Filtering, and Virtual LAN Extensions
Section 1.5.2
Supported Proprietary RUGGEDCOM MIBs
ROS supports the following proprietary RUGGEDCOM MIBs:
File Name MIB Name Description
ruggedcom.mib RUGGEDCOM-MIB RUGGEDCOM enterprise SMI
ruggedcomtraps.mib RUGGEDCOM-TRAPS-MIB RUGGEDCOM traps definition
rcsysinfo.mib RUGGEDCOM-SYS-INFO-MIB General system information about
rcDot11.mib RUGGEDCOM-DOT11-MIB Managemet for wireless interface on
rcPoe.mib RUGGEDCOM-POE-MIB Management for PoE ports on
rcSerial.mib RUGGEDCOM-SERIAL-MIB Managemet for seral ports on
rcRstp.mib RUGGEDCOM-STP-MIB Management for RSTP protocol
RUGGEDCOM device
RUGGEDCOM device
RUGGEDCOM device
RUGGEDCOM device
Section 1.5.3
Supported Agent Capabilities
ROS supports the following agent capabilities for the SNMP agent:
NOTE
For information about agent capabilities for SNMPv2, refer to RFC 2580 [http://tools.ietf.org/html/
rfc2580].
10 Supported Proprietary RUGGEDCOM MIBs
Page 25
RUGGEDCOM ROS
User Guide
File Name MIB Name Supported MIB
rcsnmpv2AC.mib RC-SNMPv2-MIB-AC SNMPv2-MIB
rcudpmibAC.mib RC-UDP-MIB-AC UDP-MIB
rctcpmibAC.mib RC-TCP-MIB-AC TCP-MIB
rcSnmpUserBasedSmMibAC.mib RC-SNMP-USER-BASED-SM-MIB-AC SNMP-USER-BASED-SM-MIB-AC
rcSnmpViewBasedAcmMibAC.mib RC-SNMP-VIEW-BASED-ACM-MIB-AC SNMP-VIEW-BASED-ACM-MIB-AC
rcifmibAC.mib RC-IF-MIB-AC IF-MIB
rcbridgemibAC.mib RC-BRIDGE-MIB-AC BRIDGE-MIB
rcrmonmibAC.mib RC-RMON-MIB-AC RMON-MIB
rcqbridgemibAC.mib RC-Q-BRIDGE-MIB-AC Q-BRIDGE-MIB
rcipmibAC.mib RC-IP-MIB-AC IP-MIB
rclldpmibAC.mib RC-LLDP-MIB-AC LLDP-MIB
rclagmibAC.mib RC-LAG-MIB-AC IEEE8023-LAG-MIB
rcrstpmibAC.mib RC_RSTP-MIB-AC RSTP-MIB
Chapter 1
Introduction
rcrcdot11AC.mib RC-RUGGEDCOM-DOT11-MIB-AC RUGGEDCOM-DOT11- MIB
rcrcpoeAC.mib RC-RUGGEDCOM-POE-MIB-AC RUGGEDCOM-POE-MIB
rcrcrstpmibAC.mib RC-RUGGEDCOM-STP-AC-MIB RUGGEDCOM-STP-MIB
rcrcsysinfomibAC.mib RC-RUGGEDCOM-SYS-INFO-MIB-AC RUGGEDCOM-SYS-INFO-MIB
rcrctrapsmibAC.mib RC-RUGGEDCOM-TRAPS-MIB-AC RUGGEDCOM-TRAPS-MIB
rcrs232mibAC.mib RUGGEDCOM_RS-232-MIB-AC RS-232-MIB
rcserialmibAC.mib RC-RUGGEDCOM-SERIAL-MIB-AC RUGGEDCOM-SERIAL-MIB
Section 1.6
SNMP Traps
The device generates the following standard traps:
Table: Standard Traps
Trap MIB
linkDown
linkUp
IF-MIB
authenticationFailure
coldStart
newRoot
topologyChage
risingAlarm RMON-MIB
SNMPv2-MIB
BRIDGE-MIB
SNMP Traps 11
Page 26
Chapter 1
Introduction
Trap MIB
fallingAlarm
lldpRemoteTablesChange LLDP-MIB
The device also generates the following proprietary traps:
Table: Proprietary Traps
Trap MIB
RUGGEDCOM ROS
User Guide
genericTrap
powerSupplyTrap
swUpgradeTrap
cfgChangeTrap
weakPasswordTrap
defaultKeysTrap
RUGGEDCOM-TRAPS-MIB
Generic traps carry information about events in their severity and description objects. They are sent at the same
time an alarm is generated for the device. The following are examples of RUGGEDCOM generic traps:
NOTE
Information about generic traps can be retrieved using the CLI command alarms. For more
information about the alarms command, refer to Section 2.6.1, “Available CLI Commands”.
Table: Generic Traps
Trap Severity
heap error Alert
NTP server failure notification
real time clock failure Error
failed password Warning
MAC address not learned by switch fabric Warning
BootP client: TFTP transfer failure Error
received looped back BPDU Error
received two consecutive confusing BPDUs on port, forcing down Error
GVRP failed to learn – too many VLANs Warning
The device generates the following traps when specific events occur:
Table: Event-Based Traps
Trap MIB Event
rcRstpNewTopology RUGGEDCOM-STP-MIB This trap is generated when the device
12 SNMP Traps
topology becomes stable after a topology
change occurs on a switch port.
Page 27

RUGGEDCOM ROS
User Guide
Section 1.7
ModBus Management Support
Modbus management support in RUGGEDCOM devices provides a simple interface for retrieving basic status
information. ModBus support simplifies the job of SCADA (Supervisory Control and Data Acquisition) system
integrators by providing familiar protocols for retrieving RUGGEDCOM device information. ModBus provides
mostly read-only status information, but there are some writable registers for operator commands.
The ModBus protocol PDU (Protocol Data Unit) format is as follows:
Function Code Data
The following sections describe the support for ModBus management:
• Section 1.7.1, “ModBus Function Codes”
• Section 1.7.2, “ModBus Memory Map”
• Section 1.7.3, “ModBus Memory Formats”
Section 1.7.1
Chapter 1
Introduction
ModBus Function Codes
RUGGEDCOM devices support the following ModBus function codes for device management through ModBus:
NOTE
While RUGGEDCOM devices have a variable number of ports, not all registers and bits apply to all
products.
Registers that are not applicable to a particular device return a zero (0) value. For example, registers
referring to serial ports are not applicable to RUGGEDCOM switch devices.
Read Input Registers or Read Holding Registers — 0x04 or 0x03
Example PDU Request
Function Code 1 Byte 0x04(0x03)
Starting Address 2 Bytes 0x0000 to 0xFFFF (Hexadecimal)
128 to 65535 (Decimal)
Number of Input Registers 2 Bytes Bytes 0x0001 to 0x007D
Example PDU Response
Function Code 1 Byte 0x04(0x03)
Byte Count 1 Byte 2 x N
Number of Input Registers Na x 2 Bytes
a
The number of input registers
a
Write Multiple Registers — 0x10
Example PDU Request
Function Code 1 Byte 0x10
Starting Address 2 Bytes 0x0000 to 0xFFFF
ModBus Management Support 13
Page 28
Chapter 1
Introduction
Number of Input Registers 2 Bytes Bytes 0x0001 to 0x0079
Byte Count 1 Byte 2 x N
Registers Value Nb x 2 Bytes Value of the register
b
The number of input registers
b
Example PDU Response
Function Code 1 Byte 0x10
Starting Address 2 Bytes 0x0000 to 0xFFFF
Number of Registers 2 Bytes 1 to 121 (0x79)
Section 1.7.2
ModBus Memory Map
The following details how ModBus process variable data is mapped.
Product Info
The following data is mapped to the Productinfo table:
RUGGEDCOM ROS
User Guide
Address #Registers Description (Reference Table in UI) R/W Format
0000 16 Product Identification R Text
0010 32 Firmware Identification R Text
0040 1 Number of Ethernet Ports R Uint16
0041 1 Number of Serial Ports R Uint16
0042 1 Number of Alarms R Uint16
0043 1 Power Supply Status R PSStatusCmd
0044 1 FailSafe Relay Status R TruthValue
0045 1 ErrorAlarm Status R TruthValue
Product Write Register
The following data is mapped to various tables:
Address #Registers Description (Reference Table in UI) R/W Format
0080 1 Clear Alarms W Cmd
0081 2 Reset Ethernet Ports W PortCmd
0083 2 Clear Ethernet Statistics W PortCmd
0085 2 Reset Serial Ports W PortCmd
0087 2 Clear Serial Port Statistics W PortCmd
Alarms
The following data is mapped to the alarms table:
14 ModBus Memory Map
Page 29
RUGGEDCOM ROS
User Guide
Address #Registers Description (Reference Table in UI) R/W Format
0100 64 Alarm 1 R Alarm
0140 64 Alarm 2 R Alarm
0180 64 Alarm 3 R Alarm
01C0 64 Alarm 4 R Alarm
0200 64 Alarm 5 R Alarm
0240 64 Alarm 6 R Alarm
0280 64 Alarm 7 R Alarm
02C0 64 Alarm 8 R Alarm
Ethernet Port Status
The following data is mapped to the ethPortStats table:
Address #Registers Description (Reference Table in UI) R/W Format
03FE 2 Port Link Status R PortCmd
Chapter 1
Introduction
Ethernet Statistics
The following data is mapped to the rmonStats table:
Address #Registers Description (Reference Table in UI) R/W Format
0400 2 Port s1/p1 Statistics - Ethernet In Packets R Uinst32
0402 2 Port s1/p2 Statistics - Ethernet In Packets R Uinst32
0404 2 Port s1/p3 Statistics - Ethernet In Packets R Uinst32
0406 2 Port s1/p4 Statistics - Ethernet In Packets R Uinst32
0408 2 Port s2/p1 Statistics - Ethernet In Packets R Uinst32
040A 2 Port s2/p2 Statistics - Ethernet In Packets R Uinst32
040C 2 Port s2/p3 Statistics - Ethernet In Packets R Uinst32
040E 2 Port s2/p4 Statistics - Ethernet In Packets R Uinst32
0410 2 Port s3/p1 Statistics - Ethernet In Packets R Uinst32
0412 2 Port s3/p2 Statistics - Ethernet In Packets R Uinst32
0414 2 Port s3/p3 Statistics - Ethernet In Packets R Uinst32
0416 2 Port s3/p4 Statistics - Ethernet In Packets R Uinst32
0418 2 Port s4/p1 Statistics - Ethernet In Packets R Uinst32
041A 2 Port s4/p2 Statistics - Ethernet In Packets R Uinst32
041C 2 Port s4/p3 Statistics - Ethernet In Packets R Uinst32
041E 2 Port s4/p4 Statistics - Ethernet In Packets R Uinst32
0420 2 Port s5/p1 Statistics - Ethernet In Packets R Uinst32
0422 2 Port s5/p2 Statistics - Ethernet In Packets R Uinst32
0424 2 Port s5/p3 Statistics - Ethernet In Packets R Uinst32
ModBus Memory Map 15
Page 30

Chapter 1
Introduction
RUGGEDCOM ROS
User Guide
Address #Registers Description (Reference Table in UI) R/W Format
0426 2 Port s5/p4 Statistics - Ethernet In Packets R Uinst32
0428 2 Port s6/p1 Statistics - Ethernet In Packets R Uinst32
042A 2 Port s6/p2 Statistics - Ethernet In Packets R Uinst32
042C 2 Port s6/p3 Statistics - Ethernet In Packets R Uinst32
042E 2 Port s6/p4 Statistics - Ethernet In Packets R Uinst32
0430 2 Port s7/p1 Statistics - Ethernet In Packets R Uinst32
0432 2 Port s7/p2 Statistics - Ethernet In Packets R Uinst32
0434 2 Port s8/p1 Statistics - Ethernet In Packets R Uinst32
0436 2 Port s8/p2 Statistics - Ethernet In Packets R Uinst32
0440 2 Port s1/p1 Statistics - Ethernet Out Packets R Uinst32
0442 2 Port s1/p2 Statistics - Ethernet Out Packets R Uinst32
0444 2 Port s1/p3 Statistics - Ethernet Out Packets R Uinst32
0446 2 Port s1/p4 Statistics - Ethernet Out Packets R Uinst32
0448 2 Port s2/p1 Statistics - Ethernet Out Packets R Uinst32
044A 2 Port s2/p2 Statistics - Ethernet Out Packets R Uinst32
044C 2 Port s2/p3 Statistics - Ethernet Out Packets R Uinst32
044E 2 Port s2/p4 Statistics - Ethernet Out Packets R Uinst32
0450 2 Port s3/p1 Statistics - Ethernet Out Packets R Uinst32
0452 2 Port s3/p2 Statistics - Ethernet Out Packets R Uinst32
0454 2 Port s3/p3 Statistics - Ethernet Out Packets R Uinst32
0456 2 Port s3/p4 Statistics - Ethernet Out Packets R Uinst32
0458 2 Port s4/p1 Statistics - Ethernet Out Packets R Uinst32
045A 2 Port s4/p2 Statistics - Ethernet Out Packets R Uinst32
045C 2 Port s4/p3 Statistics - Ethernet Out Packets R Uinst32
045E 2 Port s4/p4 Statistics - Ethernet Out Packets R Uinst32
0460 2 Port s5/p1 Statistics - Ethernet Out Packets R Uinst32
0462 2 Port s5/p2 Statistics - Ethernet Out Packets R Uinst32
0464 2 Port s5/p3 Statistics - Ethernet Out Packets R Uinst32
0466 2 Port s5/p4 Statistics - Ethernet Out Packets R Uinst32
0468 2 Port s6/p1 Statistics - Ethernet Out Packets R Uinst32
046A 2 Port s6/p2 Statistics - Ethernet Out Packets R Uinst32
046C 2 Port s6/p3 Statistics - Ethernet Out Packets R Uinst32
046E 2 Port s6/p4 Statistics - Ethernet Out Packets R Uinst32
0470 2 Port s7/p1 Statistics - Ethernet Out Packets R Uinst32
16 ModBus Memory Map
Page 31

RUGGEDCOM ROS
User Guide
Chapter 1
Introduction
Address #Registers Description (Reference Table in UI) R/W Format
0472 2 Port s7/p2 Statistics - Ethernet Out Packets R Uinst32
0474 2 Port s8/p1 Statistics - Ethernet Out Packets R Uinst32
0476 2 Port s8/p2 Statistics - Ethernet Out Packets R Uinst32
0480 2 Port s1/p1 Statistics - Ethernet In Packets R Uinst32
0482 2 Port s1/p2 Statistics - Ethernet In Packets R Uinst32
0484 2 Port s1/p3 Statistics - Ethernet In Packets R Uinst32
0486 2 Port s1/p4 Statistics - Ethernet In Packets R Uinst32
0488 2 Port s2/p1 Statistics - Ethernet In Packets R Uinst32
048A 2 Port s2/p2 Statistics - Ethernet In Packets R Uinst32
048C 2 Port s2/p3 Statistics - Ethernet In Packets R Uinst32
048E 2 Port s2/p4 Statistics - Ethernet In Packets R Uinst32
0490 2 Port s3/p1 Statistics - Ethernet In Packets R Uinst32
0492 2 Port s3/p2 Statistics - Ethernet In Packets R Uinst32
0494 2 Port s3/p3 Statistics - Ethernet In Packets R Uinst32
0496 2 Port s3/p4 Statistics - Ethernet In Packets R Uinst32
0498 2 Port s4/p1 Statistics - Ethernet In Packets R Uinst32
049A 2 Port s4/p2 Statistics - Ethernet In Packets R Uinst32
049C 2 Port s4/p3 Statistics - Ethernet In Packets R Uinst32
049E 2 Port s4/p4 Statistics - Ethernet In Packets R Uinst32
04A0 2 Port s5/p1 Statistics - Ethernet In Packets R Uinst32
04A2 2 Port s5/p2 Statistics - Ethernet In Packets R Uinst32
04A4 2 Port s5/p3 Statistics - Ethernet In Packets R Uinst32
04A6 2 Port s5/p4 Statistics - Ethernet In Packets R Uinst32
04A8 2 Port s6/p1 Statistics - Ethernet In Packets R Uinst32
04AA 2 Port s6/p2 Statistics - Ethernet In Packets R Uinst32
04AC 2 Port s6/p3 Statistics - Ethernet In Packets R Uinst32
04AE 2 Port s6/p4 Statistics - Ethernet In Packets R Uinst32
04B0 2 Port s7/p1 Statistics - Ethernet In Packets R Uinst32
04B2 2 Port s7/p2 Statistics - Ethernet In Packets R Uinst32
04B4 2 Port s8/p1 Statistics - Ethernet In Packets R Uinst32
04B6 2 Port s8/p2 Statistics - Ethernet In Packets R Uinst32
04C0 2 Port s1/p1 Statistics - Ethernet Out Packets R Uinst32
04C2 2 Port s1/p2 Statistics - Ethernet Out Packets R Uinst32
04C4 2 Port s1/p3 Statistics - Ethernet Out Packets R Uinst32
ModBus Memory Map 17
Page 32

Chapter 1
Introduction
RUGGEDCOM ROS
User Guide
Address #Registers Description (Reference Table in UI) R/W Format
04C6 2 Port s1/p4 Statistics - Ethernet Out Packets R Uinst32
04C8 2 Port s2/p1 Statistics - Ethernet Out Packets R Uinst32
04CA 2 Port s2/p2 Statistics - Ethernet Out Packets R Uinst32
04CC 2 Port s2/p3 Statistics - Ethernet Out Packets R Uinst32
04CE 2 Port s2/p4 Statistics - Ethernet Out Packets R Uinst32
04D0 2 Port s3/p1 Statistics - Ethernet Out Packets R Uinst32
04D2 2 Port s3/p2 Statistics - Ethernet Out Packets R Uinst32
04D4 2 Port s3/p3 Statistics - Ethernet Out Packets R Uinst32
04D6 2 Port s3/p4 Statistics - Ethernet Out Packets R Uinst32
04D8 2 Port s4/p1 Statistics - Ethernet Out Packets R Uinst32
04DA 2 Port s4/p2 Statistics - Ethernet Out Packets R Uinst32
04DC 2 Port s4/p3 Statistics - Ethernet Out Packets R Uinst32
04DE 2 Port s4/p4 Statistics - Ethernet Out Packets R Uinst32
04E0 2 Port s5/p1 Statistics - Ethernet Out Packets R Uinst32
04E2 2 Port s5/p2 Statistics - Ethernet Out Packets R Uinst32
04E4 2 Port s5/p3 Statistics - Ethernet Out Packets R Uinst32
04E6 2 Port s5/p4 Statistics - Ethernet Out Packets R Uinst32
04E8 2 Port s6/p1 Statistics - Ethernet Out Packets R Uinst32
04EA 2 Port s6/p2 Statistics - Ethernet Out Packets R Uinst32
04EC 2 Port s6/p3 Statistics - Ethernet Out Packets R Uinst32
04EE 2 Port s6/p4 Statistics - Ethernet Out Packets R Uinst32
04F0 2 Port s7/p1 Statistics - Ethernet Out Packets R Uinst32
04F2 2 Port s7/p2 Statistics - Ethernet Out Packets R Uinst32
04F4 2 Port s8/p1 Statistics - Ethernet Out Packets R Uinst32
04F6 2 Port s8/p2 Statistics - Ethernet Out Packets R Uinst32
Serial Statistics
The following data is mapped to the uartPortStatus table:
Address #Registers Description (Reference Table in UI) R/W Format
0600 2 Port 1 Statistics – Serial In characters R Uint32
0602 2 Port 2 Statistics – Serial In characters R Uint32
0604 2 Port 3 Statistics – Serial In characters R Uint32
0606 2 Port 4 Statistics – Serial In characters R Uint32
0640 2 Port 1 Statistics – Serial Out characters R Uint32
0642 2 Port 2 Statistics – Serial Out characters R Uint32
18 ModBus Memory Map
Page 33

RUGGEDCOM ROS
User Guide
Address #Registers Description (Reference Table in UI) R/W Format
0644 2 Port 3 Statistics – Serial Out characters R Uint32
0646 2 Port 4 Statistics – Serial Out characters R Uint32
0680 2 Port 1 Statistics – Serial In Packets R Uint32
0682 2 Port 2 Statistics – Serial In Packets R Uint32
0684 2 Port 3 Statistics – Serial In Packets R Uint32
0686 2 Port 4 Statistics – Serial In Packets R Uint32
06C0 2 Port 1 Statistics – Serial Out Packets R Uint32
06C2 2 Port 2 Statistics – Serial Out Packets R Uint32
06C4 2 Port 3 Statistics – Serial Out Packets R Uint32
06C6 2 Port 4 Statistics – Serial Out Packets R Uint32
Section 1.7.3
ModBus Memory Formats
Chapter 1
Introduction
The following ModBus memory formats are supported by Siemens:
• Section 1.7.3.1, “Text”
• Section 1.7.3.2, “Cmd”
• Section 1.7.3.3, “Uint16”
• Section 1.7.3.4, “Uint32”
• Section 1.7.3.5, “PortCmd”
• Section 1.7.3.6, “Alarm”
• Section 1.7.3.7, “PSStatusCmd”
• Section 1.7.3.8, “TruthValues”
Section 1.7.3.1
Text
The Text format provides a simple ASCII representation of the information related to the product. The most
significant register byte of an ASCII characters comes first.
For example, consider a Read Multiple Registers request to read Product Identification from location 0x0000.
0x04 0x00 0x00 0x00 0x08
The response may look like:
0x04 0x10 0x53 0x59 0x53 0x54 0x45 0x4D 0x20 0x4E 0x41 0x4D 0x45
0x00 0x00 0x00 0x00 0x00
ModBus Memory Formats 19
Page 34

Chapter 1
Introduction
RUGGEDCOM ROS
In this example, starting from byte 3 until the end, the response presents an ASCII representation of the
characters for the product identification, which reads as SYSTEM NAME. Since the length of this field is smaller
than eight registers, the rest of the field is filled with zeros (0).
Section 1.7.3.2
Cmd
The Cmd format instructs the device to set the output to either true or false. The most significant byte comes first.
• FF 00 hex requests output to be True
• 00 00 hex requests output to be False
• Any value other than the suggested values does not affect the requested operation
For example, consider a Write Multiple Registers request to clear alarms in the device.
0x10 0x00 0x80 0x00 0x01 2 0xFF 0x00
• FF 00 for register 00 80 clears the system alarms
• 00 00 does not clear any alarms
The response may look like:
User Guide
0x10 0x00 0x80 0x00 0x01
Section 1.7.3.3
Uint16
The Uint16 format describes a Standard ModBus 16 bit register.
Section 1.7.3.4
Uint32
The Uint32 format describes Standard 2 ModBus 16 bit registers. The first register holds the most significant 16
bits of a 32 bit value. The second register holds the least significant 16 bits of a 32 bit value.
Section 1.7.3.5
PortCmd
The PortCmd format describes a bit layout per port, where 1 indicates the requested action is true, and 0
indicates the requested action is false.
PortCmd provides a bit layout of a maximum of 32 ports. Therefore, it uses two ModBus regsiters:
• The first ModBus register corresponds to ports 1 – 16
• The second ModBus register corresponds to ports 17 – 32 for a particular action
Bits that do not apply to a particular product are always set to zero (0).
A bit value of 1 indicates that the requested action is true. For example, the port is up.
A bit value of 0 indicates that the requested action is false. For example, the port is down.
20 Cmd
Page 35

RUGGEDCOM ROS
User Guide
Reading Data Using PortCmd
To understand how to read data using PortCmd, consider a ModBus Request to read multiple registers from
locatoin 0x03FE.
0x04 0x03 0xFE 0x00 0x02
The response depends on how many parts are available on the device. For example, if the maximum number of
ports on a connected RUGGEDCOM device is 20, the response would be similar to the following:
0x04 0x04 0xF2 0x76 0x00 0x05
In this example, bytes 3 and 4 refer to register 1 at location 0x03FE, and represent the status of ports 1 – 16.
Bytes 5 and 6 refer to register 2 at location 0x03FF, and represent the status of ports 17 – 32. The device only
has 20 ports, so byte 6 contains the status for ports 17 – 20 starting from right to left. The rest of the bites in
register 2 corresponding to the non-existing ports 21 – 31 are zero (0).
Performing Write Actions Using PortCmd
To understand how data is written using PortCmd, consider a Write Multiple Register request to clear Ethernet
port statistics:
0x10 0x00 0x83 0x00 0x01 2 0x55 0x76 0x00 0x50
A bit value of 1 clears Ethernet statistics on the corresponding port. A bit value of 0 does not clear the Ethernet
statistics.
Chapter 1
Introduction
0x10 0x00 0x81 0x00 0x02
Section 1.7.3.6
Alarm
The Alarm format is another form of text description. Alarm text corresponds to the alarm description from the
table holding all of the alarms. Similar to the Text format, this format returns an ASCII representation of alarms.
NOTE
Alarms are stacked in the device in the sequence of their occurence (i.e. Alarm 1, Alarm 2, Alarm 3,
etc.).
The first eight alarms from the stack can be returned, if they exist. A zero (0) value is returned if an alarm does
not exist.
Section 1.7.3.7
PSStatusCmd
The PSStatusCmd format describes a bit layout for providing the status of available power supplies. Bits 0-4 of
the lower byte of the register are used for this purpose.
• Bits 0-1: Power Supply 1 Status
• Bits 2-3: Power Supply 2 Status
Other bits in the register do not provide any system status information.
Bit Value Description
01 Power Supply not present (01 = 1)
Alarm 21
Page 36

Chapter 1
Introduction
Bit Value Description
10 Power Supply is functional (10 = 2)
11 Power Supply is not functional (11 = 3)
RUGGEDCOM ROS
The values used for power supply status are derived from the RUGGEDCOM-specific SNMP MIB.
Reading the Power Supply Status from a Device Using PSStatusCmd
To understand how to read the power supply status from a device using PSStatusCmd, consider a ModBus
Request to read multiple registers from location 0x0043.
0x04 0x00 0x43 0x00 0x01
The response may look like:
0x04 0x02 0x00 0x0A
The lower byte of the register displays the power supply's status. In this example, both power supplies in the unit
are functional.
Section 1.7.3.8
TruthValues
User Guide
The Truthvalues format represents a true or false status in the device:
• 1 indicates the corresponding status for the device to be true
• 2 indicates the corresponding status for the device to be false
Reading the FailSafe Relay Status From a Device Using TruthValue
To understand how to use the TruthValue format to read the FailSafe Relay status from a device, consider a
ModBus request to read multiple registers from location 0x0044.
0x04 0x00 0x44 0x00 0x01
The response may look like:
0x04 0x02 0x00 0x01
The register's lower byte shows the FailSafe Relay status. In this example, the FailSafe Relay is energized.
Reading the ErrorAlarm Status From a Device Using TruthValue
To understand how to use the TruthValue format to read the ErrorAlarm status from a device, conside a ModBus
request to read mulitple registers from location 0x0045.
0x04 0x00 0x45 0x00 0x01
The response may look like:
0x04 0x02 0x00 0x01
The register's lower byte shows the ErrorAlarm status. In this example, there is no active ERROR, ALERT or
CRITICAL alarm in the device.
22 TruthValues
Page 37

RUGGEDCOM ROS
User Guide
Section 1.8
Certificate and Key Requirements
Users are able to load custom and unique SSL certificates and SSL/SSH keys in ROS or use the certificates and
keys provided by ROS.
There are three types of certificates and keys:
NOTE
Default and auto-generated SSH keys are not available for Non-Controlled (NC) versions of ROS.
• Default
Each ROS device is shipped with an SSL certificate and RSA key pair, and a DSA key pair for SSH that are
unique to software version. If a valid SSL certificate or SSL/SSH keys are not available on the device, the
default certificate and keys are used immediately so that SSH and SSL (https) sessions can be served.
• Auto-Generated
If a default SSL certificate and SSL/SSH keys are in use, ROS immediately begins to generate a unique
certificate and SSL/SSH keys for the device in the background. This process takes approximately 5 minutes
to complete (depending on how busy the device is at the time) following the startup of the device. If a custom
certificate and keys are loaded while auto-generated certificates and keys are being generated, the generator
will abort and the custom certificate and keys and will be used.
• User-Generated (Recommended)
Custom certificates and keys are the most secure option. They give the user complete control over certificate
and key management, allow for certificates signed by a public or local certificate authority, controlled
distribution of public SSH keys to network hosts that need them, and more.
Chapter 1
Introduction
NOTE
The RSA key pair must be added to the ssl.crt file after the SSL certificate.
For SSL, ROS requires an X.509 certificate in standard PEM format and an RSA key pair. The certificate may
be self-signed or signed by a separate authoriy. The RSA key must be between 512 and 2048 bits in length. The
certificate and keys must be combined in a single ssl.crt file and uploaded to the device.
The following is an example of a combined SSL certificate and key:
-----BEGIN CERTIFICATE----MIIC9jCCAl+gAwIBAgIJAJh6rrehMt3iMA0GCSqGSIb3DQEBBQUAMIGuMQswCQYD
VQQGEwJDQTEQMA4GA1UECBMHT250YXJpbzEQMA4GA1UEBxMHQ29uY29yZDESMBAG
A1UEChMJUnVnZ2VkY29tMRkwFwYDVQQLExBDdXN0b21lciBTdXBwb3J0MSYwJAYD
VQQDEx1XUy1NSUxBTkdPVkFOLlJVR0dFRENPTS5MT0NBTDEkMCIGCSqGSIb3DQEJ
ARYVc3VwcG9ydEBydWdnZWRjb20uY29tMB4XDTEyMTAyMzIxMTA1M1oXDTE3MTAy
MjIxMTA1M1owgZwxCzAJBgNVBAYTAlVTMRAwDgYDVQQIEwdPbnRhcmlvMRAwDgYD
VQQHEwdDb25jb3JkMRIwEAYDVQQKEwlSdWdnZWRDb20xGTAXBgNVBAsTEEN1c3Rv
bWVyIFN1cHBvcnQxFDASBgNVBAMTCzE5Mi4xNjguMS4yMSQwIgYJKoZIhvcNAQkB
FhVTdXBwb3J0QHJ1Z2dlZGNvbS5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJ
AoGBALfE4eh2aY+CE3W5a4Wz1Z1RGRP02COHt153wFFrU8/fFQXNhKlQirlAHbNT
RSwcTR8ZFapivwYDivn0ogOGFXknYP90gv2oIaSVY08FqZkJW77g3kzkv/8Zrw3m
W/cBsZJ8SyKLIDfy401HkHpDOle5NsQFSrziGUPjAOIvvx4rAgMBAAGjLDAqMAkG
A1UdEwQCMAAwHQYDVR0OBBYEFER0utgQOifnrflnDtsqNcnvRB0XMA0GCSqGSIb3
DQEBBQUAA4GBAHtBsNZuh8tB3kdqR7Pn+XidCsD70YnI7w0tiy9yiRRhARmVXH8h
5Q1rOeHceri3JFFIOxIxQt4KgCUYJLu+c9Esk/nXQQar3zR7IQCt0qOABPkviiY8
c3ibVbhJjLpR2vNW4xRAJ+HkNNtBOg1xUlp4vOmJ2syYZR+7XAy/OP/S
-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY----MIICXAIBAAKBgQC3xOHodmmPghN1uWuFs9WdURkT9Ngjh7ded8BRa1PP3xUFzYSp
Certificate and Key Requirements 23
Page 38

Chapter 1
Introduction
UIq5QB2zU0UsHE0fGRWqYr8GA4r59KIDhhV5J2D/dIL9qCGklWNPBamZCVu+4N5M
5L//Ga8N5lv3AbGSfEsiiyA38uNNR5B6QzpXuTbEBUq84hlD4wDiL78eKwIDAQAB
AoGBAI2CXHuHg23wuk9zAusoOhw0MN1/M1jYz0k9aajIvvdZT3Tyd29yCADy8GwA
eUmoWXLS/C4CcBqPa9til8ei3rDn/w8dveVHsi9FXjtVSYqN+ilKw+moMAjZy4kN
/kpdpHMohwv/909VWR1AZbr+YTxaG/++tKl5bqXnZl4wHF8xAkEA5vwut8USRg2/
TndOt1e8ILEQNHvHQdQr2et/xNH4ZEo7mqot6skkCD1xmxA6XG64hR3BfxFSZcew
Wr4SOFGCtQJBAMurr5FYPJRFGzPM3HwcpAaaMIUtPwNyTtTjywlYcUI7iZVVfbdx
4B7qOadPybTg7wqUrGVkPSzzQelz9YCSSV8CQFqpIsEYhbqfTLZEl83YjsuaE801
xBivaWLIT0b2TvM2O7zSDOG5fv4I990v+mgrQRtmeXshVmEChtKnBcm7HH0CQE6B
2WUfLArDMJ8hAoRczeU1nipXrIh5kWWCgQsTKmUrafdEQvdpT8ja5GpX2Rp98eaU
NHfI0cP36JpCdome2eUCQDZN9OrTgPfeDIXzyOiUUwFlzS1idkUGL9nH86iuPnd7
WVF3rV9Dse30sVEk63Yky8uKUy7yPUNWldG4U5vRKmY=
-----END RSA PRIVATE KEY-----
For SSH, ROS requires a DSA key pair in PEM format. The DSA key must be between 512 and 2048 bits in
length for Controlled versions. The key file is uploaded to the ssh.keys flash file on the device.
The following is an example of a PEM formatted SSH key:
-----BEGIN DSA PRIVATE KEY----MIIBuwIBAAKBgQD0gcGbXx/rrEMu2913UW4cYo1OlcbnuUz7OZyd2mBLDx/GYbD8
X5TnRcMraJ0RuuGK+chqQJW5k3zQmZa/BS6q9U7wYwIAx8JSxxpwfPfl/t09VwKG
rtSJIMpLRoDq3qEwEVyR4kDUo4LFQDsljtiyhcz1n6kd6gqsd5Xu1vdh4wIVANXb
SBi97GmZ6/9f4UCvIIBtXLEjAoGAAfmhkcCCEnRJitUTiCE+MurxdFUr3mFs/d31
4cUDaLStQEhYYmx5dbFdQuapl4Y32B7lZQkohi5q1T1iUAa40/nUnJx1hFvblkYT
8DLwxcuDAaiu0VqsaPtJ+baL2dYNp96tFisj/475PEEWBGbP6GSe5kKa1Zdgwuie
9LyPb+ACgYBv856v5tb9UVG5+tX5Crfv/Nd8FFlSSFKmVWW3yzguhHajg2LQg8UU
sm1/zPSwYQ0SbQ9aOAJnpLc2HUkK0lji/0oKVI7y9MMc4B+bGu4W4OnryP7oFpnp
YYHt5PJY+zvLw/Wa+u3NOVFHkF1tGyfVBMXeV36nowPo+wrVMolAEgIVALLTnfpW
maV6uh6RxeE1d4XoxSg2
-----END DSA PRIVATE KEY-----
RUGGEDCOM ROS
User Guide
For more information about encryption key management, refer to Section 1.2, “Security Recommendations and
Considerations”.
24 Certificate and Key Requirements
Page 39

RUGGEDCOM ROS
User Guide
Using ROS
This chapter describes how to use the ROS interface. It describes the following tasks:
• Section 2.1, “Connecting to ROS”
• Section 2.2, “Logging In”
• Section 2.3, “Logging Out”
• Section 2.4, “Using the Web Interface”
• Section 2.5, “Using the Console Interface”
• Section 2.6, “Using the Command Line Interface”
• Section 2.7, “Selecting Ports in ROS”
• Section 2.8, “Managing the Flash File System”
• Section 2.9, “Accessing BIST Mode”
Chapter 2
Using ROS
Section 2.1
Connecting to ROS
The following describes the various methods for connecting the device:
• Section 2.1.1, “Connecting Directly”
• Section 2.1.2, “Connecting via the Network”
Section 2.1.1
Connecting Directly
ROS can be accessed through a direct serial console or Ethernet connection for management and
troubleshooting purposes. A console connection provides access to the console interface and CLI.
To establish a serial connection to the device, do the following:
1. Connect a workstation (either a terminal or computer running terminal emulation software) to the RS232
serial console port on the device. For more information about the RS232 serial console port, refer to the
RSG2200 Installation Guide.
NOTE
The baud rate for the device is printed on the chassis exterior near the RS232 serial console port.
2. Configure the workstation as follows:
• Speed (baud): 57600
• Data Bits: 8
• Parity: None
Connecting to ROS 25
Page 40

Chapter 2
Using ROS
• Flow Control: Off
• Terminal ID: VT100
• Stop Bit: 1
3. Connect to the device. Once the connection is established, the login form appears. For more information
about logging in to the device, refer to Section 2.2, “Logging In”.
Section 2.1.2
RUGGEDCOM ROS
Connecting via the Network
ROS can be accessed over the network either through a Web browser, terminal or a workstation running terminal
emulation software.
Using a Web Browser
Web browsers provide a secure connection to the Web interface for ROS using the SSL (Secure Socket Layer)
communication method. SSL encrypts traffic exchanged with its clients.
The ROS Web server guarantees that all communications with the client are private. If a client requests access
through an insecure HTTP port, the client is automatically rerouted to the secure port. Access to the Web server
through SSL will only be granted to clients that provide a valid user name and password.
To establish a connection through a Web browser, do the following:
1. On the workstation being used to access the device, configure an Ethernet port to use an IP address falling
within the subnet of the device. The default IP address is 192.168.0.1/24.
For example, to configure the device to connect to one of the available Ethernet ports, assign an IP address
to the Ethernet port on the workstation in the range of 192.168.0.3 to 192.168.0.254.
2. Open a Web browser. For a list of recommended Web browsers, refer to the section called “System
Requirements”.
User Guide
IMPORTANT!
Upon connecting to the device, some Web browsers may report the Web server's certificate
cannot be verified against any known certificates. This is expected behavior, and it is safe to
instruct the browser to accept the certificate. Once the certificate is accepted, all communications
with the Web server through that browser will be secure.
3. In the address bar, type the IP address for the port that is connected to the network. For example, to access
the device using its factory default IP address, type https://192.168.0.1 and press Enter. Once the
connection is established, the login screen for the Web interface appears.
For more information about logging in to the device, refer to Section 2.2, “Logging In”. For more information
about the Web interface, refer to Section 2.4, “Using the Web Interface”.
Using a Terminal or Terminal Emulation Software
A terminal or computer running terminal emulation software provides secure access to the console interface for
ROS through a Telnet, RSH (Remote Shell) or SSH (Secure Shell) service.
NOTE
IP services can be restricted to control access to the device. For more information, refer to Section 3.9,
“Configuring IP Services”.
To establish a connection through a terminal or terminal emulation software, do the following:
26 Connecting via the Network
Page 41

RUGGEDCOM ROS
1
2
1
3
2
User Guide
1. Select the service (i.e. Telnet, RSH or SSH).
2. Enter the IP address for the port that is connected to the network.
3. Connect to the device. Once the connection is established, the login form appears. For more information
about logging in to the device, refer to Section 2.2, “Logging In”.
Section 2.2
Logging In
To log in to the device, do the following:
1. Connect to the device either directly or through a Web browser. For more information about how to connect
to the device, refer to Section 2.1, “Connecting to ROS”.
Once the connection is established, the login form appears.
Chapter 2
Using ROS
Figure 2: SSH Login Screen (Console Interface)
1. User Name Box 2. Password Box
Figure 3: Login Screen (Web Interface)
1. Username Box 2. Password Box 3. Submit Button
NOTE
The following default usernames and passwords are set on the device for each user type:
Guest
Username: guest
Password: guest
Operator
Username: operator
Password: operator
Admin
Username: admin
Password: admin
Logging In 27
Page 42

Chapter 2
1
Using ROS
CAUTION!
To prevent unauthorized access to the device, make sure to change the default guest, operator,
and admin passwords before commissioning the device.
For more information about changing passwords, refer to Section 4.3, “Configuring Passwords”.
2. In the User Name field, type the username for an account setup on the device.
3. In the Password field, typ the password for the account.
4. Click Enter or click Submit (Web interface only).
Section 2.3
Logging Out
To log out of the device, navigate to the main screen and do the following:
• To log out of the Console or secure shell interfaces, press CTRL + X.
• To log out of the Web interface, click Logout.
RUGGEDCOM ROS
User Guide
Figure 4: Web Interface (Example)
1. Logout
NOTE
If any pending configuration changes have not been committed, ROS will request confirmation before
discarding the changes and logging out of the device.
Section 2.4
Using the Web Interface
The Web interface is a Web-based Graphical User Interface (GUI) for displaying important information and
controls in a Web browser. The interface is divided into three frames: the banner, the menu and the main frame.
28 Logging Out
Page 43

RUGGEDCOM ROS
2
1
3
User Guide
Figure 5: Web Interface Layout (Example)
1. Top Frame 2. Side Frame 3. Main Frame
Frame Description
Chapter 2
Using ROS
Top The top frame displays the system name for the device.
Side The side frame contains a logout option and a collapsible list of links that open various
Main The main frame displays the parameters and/or data related to the selected feature.
screens in the main frame. For information about logging out of ROS, refer to Section 2.3,
“Logging Out”.
Each screen consists of a title, the current user's access level, parameters and/or data (in form or table format),
and controls (e.g. add, delete, refresh, etc.). The title provides access to context-specific Help for the screen that
provides important information about the available parameters and/or data. Click on the link to open the Help
information in a new window.
When an alarm is generated, an alarm notification replaces the current user's access level on each screen until
the alarm is cleared. The notification indicates how many alarms are currently active. For more information about
alarms, refer to Section 4.4, “Managing Alarms”.
Using the Web Interface 29
Page 44

Chapter 2
3
1
2
4
Using ROS
Figure 6: Elements of a Typical Screen (Example)
1. Title 2. Parameters and/or Data 3. Access Level or Alarm Notification 4. Controls
RUGGEDCOM ROS
User Guide
Section 2.5
Using the Console Interface
The Console interface is a Graphical User Interface (GUI) organized as a series of menus. It is primarily
accessible through a serial console connection, but can also be accessed through IP services, such as a Telnet,
RSH (Remote Shell), or SSH (Secure Shell) session.
NOTE
IP services can be restricted to control access to the device. For more information, refer to Section 3.9,
“Configuring IP Services”.
Each screen consists of a system identifier, the name of the current menu, and a command bar. Alarms are also
indicated on each screen in the upper right corner.
30 Using the Console Interface
Page 45

RUGGEDCOM ROS
5
4
1
2
3
User Guide
Chapter 2
Using ROS
Figure 7: Console Interface (Example)
1. System Identification 2. Menus 3. Command Bar 4. Menu Name 5. Alarms Indicator
NOTE
They system identifier is user configurable. For more information about setting the system name, refer
to Section 4.1, “Configuring the System Information”.
Navigating the Interface
Use the following controls to navigate between screens in the Console interface:
Enter Select a menu item and press this Enter to enter the sub-menu or screen beneath.
Esc Press Esc to return to the previous screen.
Configuring Parameters
Use the following controls to select and configure parameters in the Console interface:
Up/Down Arrow Keys Use the up and down arrow keys to select parameters.
Enter Select a parameter and press Enter to start editing a parameter. Press Enter again to commit the change.
Esc When editing a parameter, press Esc to abort all changes.
Commands
The command bar lists the various commands that can be issued in the Console interface. Some commands are
specific to select screens. The standard commands include the following:
Ctrl + A Commits configuration changes made on the current screen.
Using the Console Interface 31
Page 46

Chapter 2
Using ROS
NOTE
Before exiting a screen, ROS will automatically prompt the user to save any changes that have
not been committed.
Ctrl + I Inserts a new record.
Ctrl + L Deletes a record.
Ctrl + S Opens the CLI interface.
Ctrl + X Terminates the current session. This command is only available from the main menu.
Ctrl + Z Displays important information about the current screen or selected parameter.
Section 2.6
Using the Command Line Interface
The Command Line Interface (CLI) offers a series of powerful commands for updating ROS, generating
certificates/keys, tracing events, troubleshooting and much more. It is accessed via the Console interface by
pressing Ctrl-S.
The following sections describe how to use the Command Line Interface (CLI):
• Section 2.6.1, “Available CLI Commands”
• Section 2.6.2, “Tracing Events”
• Section 2.6.3, “Executing Commands Remotely via RSH”
• Section 2.6.4, “Using SQL Commands”
RUGGEDCOM ROS
User Guide
Section 2.6.1
Available CLI Commands
The following commands are available at the command line:
Command Description
alarms all
arp Displays the IP to MAC address resolution table.
clearalarms Clears all alarms.
clearethstats [all | port]
clearlogs Clears the system and crash logs.
clrcblstats [all | port]
Displays a list of available alarms.
Optional and/or required parameters include:
• all displays all available alarms
Clears Ethernet statistics for one or more ports.
Optional and/or required parameters include:
• all clears statistics for all ports
• port is a comma separated list of port numbers (e.g. 1,3-5,7)
Clears cable diagnostics statistics for one or more ports.
Optional and/or required parameters include:
• all clears statistics for all ports
32 Using the Command Line Interface
Page 47

RUGGEDCOM ROS
User Guide
Command Description
• port is a comma separated list of port numbers (e.g. 1,3-5,7)
clrstpstats Clears all spanning tree statistics.
cls Clears the screen.
dir Prints the directory listing.
exit Terminates the session.
Chapter 2
Using ROS
factory Enables factory mode, which includes several factory-level commands used for testing and
troubleshooting. Only available to admin users.
CAUTION!
Misuse of the factory commands may corrupt the operational state of device
and/or may permanently damage the ability to recover the device without
manufacturer intervention.
flashfiles {info filename |
defrag}
flashleds timeout
fpgacmd
help command
A set of diagnostic commands to display information about the Flash filesystem and to
defragment Flash memory.
Optional and/or required parameters include:
• info filename displays information about the specified file in the Flash file system
• defrag defragments files in the Flash file system
For more information about the flashfiles command, refer to Section 2.8, “Managing the
Flash File System”.
Flashes the LED indicators on the device for a specified number of seconds.
Optional and/or required parameters include:
• timeout is the number of seconds to flash the LED indicators. To stop the LEDs from
flashing, set the timeout period to 0 (zero).
Provides access to the FPGA management tool for troubleshooting time synchronization.
Displays a brief description of the specified command. If no command is specified, it
displays a list of all available commands, including a description for each.
Optional and/or required parameters include:
• command is the command
ipconfig Displays the current IP address, subnet mask and default gateway. This command provides
loaddflts Loads the factory default configuration.
login Logs in to the shell.
logout Logs out of the shell.
ping address {count | timeout}
the only way of determining these values when DHCP is used.
Sends an ICMP echo request to a remotely connected device. For each reply received, the
round trip time is displayed. Use this command to verify connectivity to the next connected
device. It is a useful tool for testing commissioned links. This command also includes
the ability to send a specific number of pings with a specified time for which to wait for a
response.
Optional and/or required parameters include:
• address is the target IP address.
• count is the number of echo requests to send. The default is 4.
• timeout is the time in milliseconds to wait for each reply. The range is 2 to 5000
seconds. The default is 300 milliseconds.
NOTE
The device to be pinged must support ICMP echo. Upon commencing the ping,
an ARP request for the MAC address of the device is issued. If the device to be
Available CLI Commands 33
Page 48

Chapter 2
Using ROS
Command Description
pinged is not on the same network as the device pinging the other device, the
default gateway must be programmed.
purgemac Purges the MAC Addrtess table.
reset Perform a hard reset of the switch.
RUGGEDCOM ROS
User Guide
resetport {all | ports}
Resets one or more Ethernet ports, which may be useful for forcing re-negotiation of speed
and duplex, or in situations where the link partner has latched into an inappropriate state.
Optional and/or required parameters include:
• all resets all ports
• ports is a comma separated list of port numbers (e.g. 1,3-5,7)
rmon Displays the names of all RMON alarm eligible objects.
route Displays the gateway configuration.
sfp port {base | alarms | diag |
calibr | thr | all | no parameter
specified}
Displays SFP (Small Form Factor Pluggable) device information and diagnostics. If optional
or required parameters are not used, this command displays the base and extended
information.
Optional and/or required parameters include:
• port is the port number for which the data are required
• base displays the base information
• alarms displays alarms and warning flags
• diag displays measured data
• calibr displays calibration data for external calibration
• thr displays thresholds data
• all displays all diagnostic data
sql {default | delete | help |
info | insert | save | select |
update}
Provides an SQL-like interface for manipulating all system configuration and status
parameters. All commands, clauses, table, and column names are case insensitive.
Optional and/or required parameters include:
• default sets all records in a table(s) to factory defaults
• delete allows for records to be deleted from a table
• help provides a brief description for any SQL command or clause
• info displays a variety of information about the tables in the database
• insert enables new records to be inserted into a table
• save saves the database to non-volatile memory storage
• select queries the dtabase and displays selected records
• update enable existing records in a table to be updated
For more information about the sql command, refer to Section 2.6.4, “Using SQL
Commands”.
sshkeygen size
Generates new SSH keys in ssh.keys.
Optional and/or required parameters include:
• size is the number of bits in length between 512 and 2048. The default is 1024 bits.
sslkeygen size
Generates a new SSL certificate in ssl.crt.
Optional and/or required parameters include:
• size is the number of bits in length between 512 and 2048. The default is 1024 bits.
telnet dest
Opens a telnet session. Press Ctrl-C to close the session.
Optional and/or required parameters include:
• dest is the server's IP address
tftp {dest | cmd | fsource |
Opens a TFTP session. Press Ctrl-C to close the session.
fdest}
34 Available CLI Commands
Page 49

RUGGEDCOM ROS
User Guide
Command Description
Optional and/or required parameters include:
• dest is the remote TFTP server's IP address
• cmd is either put (upload) or get (download)
• fsource is the source filename
• fdest is the destination filename
trace Starts event tracing. Run trace ? for more help.
Chapter 2
Using ROS
type filename
version Prints the software version.
xmodem {send | receive} filename
Section 2.6.2
Displays the contents of a text file.
Optional and/or required parameters include:
• filename is the name of the file to be read
Opens an XModem session.
Optional and/or required parameters include:
• send sends the file to the client.
• receive receives the file from the client.
• filename is the name of the file to be read.
Tracing Events
The CLI trace command provides a means to trace the operation of various protocols supported by the device.
Trace provides detailed information, including STP packet decodes, IGMP activity and MAC address displays.
NOTE
Tracing has been designed to provide detailed information to expert users. Note that all tracing is
disabled upon device startup.
To trace an event, do the following:
1. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
2. Determine the protocols and associated options available by typing:
trace ?
If an option such as allon or alloff is required, determine which options are available for the desired
protocol by typing:
trace protocol ?
NOTE
If required, expand the trace scope by stringing protocols and their associated options together
using a vertical bar (|).
3. Select the type of trace to run by typing:
trace protocol option
Where:
• protocol is the protocol to trace
Tracing Events 35
Page 50

Chapter 2
Using ROS
RUGGEDCOM ROS
• option is the option to use during the trace
Example:
>trace transport allon
TRANSPORT: Logging is enabled
4. Start the trace by typing:
trace
Section 2.6.3
Executing Commands Remotely via RSH
The Remote Shell (RSH) facility can be used from a workstation to cause the product to act upon commands as if
they were entered at the CLI prompt. The syntax of the RSH command is usually of the form:
rsh ipaddr –l auth_token command_string
Where:
• ipaddr is the address or resolved name of the device.
• auth_token is the user name (i.e. guest, operator or admin) and corresponding password separated by a
comma. For example, admin,secret.
• command_string is the ROS CLI command to execute.
User Guide
NOTE
The access level (corresponding to the user name) selected must support the given command.
NOTE
Any output from the command will be returned to the workstation submitting the command. Commands
that start interactive dialogs (such as trace) cannot be used.
Section 2.6.4
Using SQL Commands
ROS provides an SQL-like command facility that allows expert users to perform several operations not possible
under the traditional Web or CLI interface. For instance:
• Restoring the contents of a specific table, but not the whole configuration, to their factory defaults.
• Search tables in the database for specific configurations.
• Make changes to tables predicated upon existing configurations.
When combined with RSH, SQL commands provide a means to query and configure large numbers of devices
from a central location.
NOTE
For a list of parameters available under the sql command, refer to Section 2.6.1, “Available CLI
Commands”.
36 Executing Commands Remotely via RSH
Page 51

RUGGEDCOM ROS
User Guide
The following sections describe in more detail how to use SQL commands:
• Section 2.6.4.1, “Finding the Correct Table”
• Section 2.6.4.2, “Retrieving Information”
• Section 2.6.4.3, “Changing Values in a Table”
• Section 2.6.4.4, “Resetting a Table”
• Section 2.6.4.5, “Using RSH and SQL”
Section 2.6.4.1
Finding the Correct Table
Many SQL commands operate upon specific tables in the database, and require the table name to be specified.
Navigating the menu system in the console interface to the desired menu and pressing Ctrl-Z displays the name
of the table. The menu name and the corresponding database table name will be cited.
Another way to find a table name is to type the following in the CLI:
sql info tables
This command also displays menu names and their corresponding database table names depending upon the
features supported by the device. For example:
Chapter 2
Using ROS
Table Description
------------------------------------------------------------------------------alarms Alarms
cpuDiags CPU Diagnostics
ethPortCfg Port Parameters
ethPortStats Ethernet Statistics
ethPortStatus Port Status
ipCfg IP Services
Section 2.6.4.2
Retrieving Information
The following describes various methods for retrieving information about tables and parameters.
Retrieving Information from a Table
Use the following command to display a summary of the parameters within a table, as well as their values:
sql select from table
Where:
• table is the name of the table
Example:
>sql select from ipAddrtable
IP Address Subnet IfIndex IfStats IfTime IfName
172.30.146.88 255.255.224.0 1001 17007888 2994 vlan1
1 records selected
Finding the Correct Table 37
Page 52

Chapter 2
Using ROS
Retrieving Information About a Parameter from a Table
Use the following command to retrieve information about a specific parameter from a table:
NOTE
The parameter name must be the same as it is displayed in the menu system, unless the name
contains spaces (e.g. ip address). Spaces must be replaced with underscores (e.g. ip_address) or the
parameter name must be wrapped in double quotes (e.g. "ip address").
sql select parameter from table
Where:
• parameter is the name of the parameter
• table is the name of the table
Example:
>sql select "ip address" from ipSwitchIfCfg
IP Address
192.168.0.1
1 records selected
RUGGEDCOM ROS
User Guide
Retrieving Information from a Table Using the Where Clause
Use the following command to display specific parameters from a table that have a specific value:
sql select from table where parameter = value
Where:
• table is the name of the table
• parameter is the name of the parameter
• value is the value of the parameter
Example:
>sql select from ethportcfg where media = 1000T
Port Name ifName Media State AutoN Speed Dupx FlowCtrl LFI Alarm
1 Port 1 1 1000T Enabled On Auto Auto Off Off On
2 Port 2 2 1000T Enabled On Auto Auto Off Off On
3 Port 3 3 1000T Enabled On Auto Auto Off Off On
4 Port 4 4 1000T Enabled On Auto Auto Off Off On
4 records selected
Further refine the results by using and or or operators:
sql select from table where parameter = value [{and | or} | parameter | = | value...]
Where:
• table is the name of the table
• parameter is the name of the parameter
• value is the value of the parameter
Example:
>sql select from ethportcfg where media = 1000T and State = enabled
38 Retrieving Information
Page 53

RUGGEDCOM ROS
User Guide
Port Name ifName Media State AutoN Speed Dupx FlowCtrl LFI Alarm
1 Port 1 1 1000T Enabled On Auto Auto Off Off on
2 Port 2 2 1000T Enabled On Auto Auto Off Off On
3 Port 3 3 1000T Enabled On Auto Auto Off Off On
4 Port 4 4 1000T Enabled On Auto Auto Off Off On
4 records selected
Section 2.6.4.3
Changing Values in a Table
Use the following command to change the value of parameters in a table:
sql update table set parameter = value
Where:
• table is the name of the table
• parameter is the name of the parameter
• value is the value of the parameter
Example:
Chapter 2
Using ROS
>sql update iplcfg set IP_Address_Type = static
1 records updated
Conditions can also be included in the command to apply changes only to parameters that meet specific criteria.
In the following example, flow control is enabled on ports that are operating in 100 Mbps full-duplex mode with
flow control disabled:
>sql update ethportcfg set FlowCtrl = Off where ( Media = 100TX and FlowCtrl = On )
2 records updated
Section 2.6.4.4
Resetting a Table
Use the following command to reset a table back to its factory defaults:
sql default into table
Where:
• table is the name of the table
Section 2.6.4.5
Using RSH and SQL
The combination of remote shell scripting and SQL commands offers a means to interrogate and maintain a
large number of devices. Consistency of configuration across sites may be verified by this method. The following
presents a simple example where the devices to interrogate are drawn from the file Devices:
Need a new example not related to VLANs
C:> type Devices
Changing Values in a Table 39
Page 54

Chapter 2
Using ROS
10.0.1.1
10.0.1.2
C:\> for /F %i in (devices) do rsh %i -l admin,admin sql select from ipAddrtable
C:\>rsh 10.0.1.1 -l admin,admin sql select from ipAddrtable
IP Address Subnet IfIndex IfStats IfTime IfName
192.168.0.31 255.255.255.0 1001 274409096 2218 vlan1
1 records selected
C:\>rsh 10.0.1.2 -l admin,admin sql select from ipAddrtable
0 records selected
C:\
Section 2.7
Selecting Ports in ROS
Many features in ROS can be configured for one or more ports on the device. The following describes how to
specify a single port, a range of ports, or all ports.
RUGGEDCOM ROS
User Guide
Select a single port by specifying the port number:
2
Select a range of ports using a dash (-) between the first port and the last port in the list:
1-4
Select multiple ports by defining a comma-separated list:
1,4,6,9
Use the All option to select all ports in the device, or, if available, use the None option to select none of the
ports.
Section 2.8
Managing the Flash File System
The following sections describe how to manage the flash file system:
• Section 2.8.1, “Viewing a List of Flash Files”
• Section 2.8.2, “Viewing Flash File Details”
• Section 2.8.3, “Defragmenting the Flash File System”
Section 2.8.1
Viewing a List of Flash Files
To view a list of files currently stored in Flash memory, do the following:
40 Selecting Ports in ROS
Page 55

RUGGEDCOM ROS
User Guide
1. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
2. Type flashfiles. A list of files currently in Flash memory is displayed, along with their locations and the
amount of memory they consume. For example:
>flashfiles
----------------------------------------------------------------Filename Base Size Sectors Used
----------------------------------------------------------------boot.bin 00000000 110000 0-16 1095790
main.bin 00110000 140000 17-36 1258403
fpga.xsvf 00250000 010000 37-37 55882
syslog.txt 00260000 140000 38-57 19222
ssh.keys 003A0000 010000 58-58 915
ssl.crt 003B0000 010000 59-59 1970
banner.txt 003C0000 010000 60-60 256
crashlog.txt 003D0000 010000 61-61 256
config.bak 003E0000 010000 62-62 15529
config.csv 003F0000 008000 63-63 15529
factory.txt 003FC000 004000 66-66 407
-----------------------------------------------------------------
Section 2.8.2
Chapter 2
Using ROS
Viewing Flash File Details
To view the details of a file currently stored in Flash memory, do the following:
1. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
2. Display information about a file by typing:
flashfiles info filename
Where:
• filename is the name of the file stored in Flash memory
Details, similar to the following, are displayed.
Updated for RP110
>flashfiles info main.bin
Flash file information for main.bin:
Header version : 4
Platform : ROS-CF52
File name : main.bin
Firmware version : v4.1.0
Build date : Sep 27 2014 15:50
File length : 2624659
Board IDs : 3d
Header CRC : 73b4
Header CRC Calc : 73b4
Body CRC : b441
Body CRC Calc : b441
Viewing Flash File Details 41
Page 56

Chapter 2
Using ROS
Section 2.8.3
RUGGEDCOM ROS
Defragmenting the Flash File System
The flash memory is defragmented automatically whenever there is not enough memory available for a binary
upgrade. However, fragmentation can occur whenever a new file is uploaded to the unit. Fragmentation causes
sectors of available memory to become separated by ones allocated to files. In some cases, the total available
memory might be sufficient for a binary upgrade, but that memory may not be available in one contiguous region.
To defragment the flash memory, do the following:
1. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
2. Defragment the flash memory by typing:
flashfiles defrag
Section 2.9
Accessing BIST Mode
User Guide
BIST (Built-In-Self-Test) mode is used by service technicians to test and configure internal functions of the device.
It should only be accessed for troubleshooting purposes.
CAUTION!
Mechanical hazard – risk of damage to the device. Excessive use of BIST functions may cause
increase wear on the device, which may void the warranty. Avoid using BIST functions unless
instructed by a Siemens Customer Support representative.
To access BIST mode, do the following:
IMPORTANT!
Do not connect the device to the network when it is in BIST mode. The device will generate excess
multicast traffic in this mode.
1. Disconnect the device from the network.
2. Connect to ROS through the RS232 console connection and a terminal application. For more information,
refer to Section 2.1.1, “Connecting Directly”.
3. Reset the device. For more information, refer to Section 3.12, “Resetting the Device”.
4. During the boot up sequence, press Ctrl-C when prompted. The command prompt for BIST appears.
>
5. Type help to view a list of all available options under BIST.
42 Defragmenting the Flash File System
Page 57

RUGGEDCOM ROS
User Guide
Device Management
Device Management
This chapter describes how to configure and manage the device and its components, such as module interfaces,
logs and files. It describes the following tasks:
NOTE
For information about how to configure the device to work with a network, refer to Chapter 5, Setup and
Configuration.
• Section 3.1, “Viewing Product Information”
• Section 3.2, “Viewing CPU Diagnostics”
• Section 3.3, “Restoring Factory Defaults”
• Section 3.4, “Uploading/Downloading Files”
• Section 3.5, “Managing Logs”
• Section 3.6, “Managing Ethernet Ports”
Chapter 3
• Section 3.7, “Managing IP Interfaces”
• Section 3.8, “Managing IP Gateways”
• Section 3.9, “Configuring IP Services”
• Section 3.10, “Managing Remote Monitoring”
• Section 3.11, “Upgrading/Downgrading Firmware”
• Section 3.12, “Resetting the Device”
• Section 3.13, “Decommissioning the Device”
Section 3.1
Viewing Product Information
During troubleshooting or when ordering new devices, Siemens personnel may request specific information about
the device, such as the model, order code or serial number.
To view information about the device, navigate to Diagnostics » View Product Information. The Product
Information form appears.
Viewing Product Information 43
Page 58

Chapter 3
9
5
4
3
2
1
6
7
8
Device Management
Figure 8: Product Information Form (Example)
1. MAC Address Box 2. Order Code Box 3. Classification Box 4. Serial Number Box 5. Boot Version Box 6. Main Version Box
7. Required Boot Box 8. Hardware ID Box 9. Reload Button
RUGGEDCOM ROS
User Guide
This screen displays the following information:
Parameter Description
MAC Address Synopsis: ##-##-##-##-##-## where ## ranges 0 to FF
Shows the unique MAC address of the device.
Order Code Synopsis: Any 57 characters
Shows the order code of the device.
Classification Synopsis: Any 15 characters
Provides system classification.
The value Controlled indicates the main firmware is a Controlled release. The value Non-
Controlled indicates the main firmware is a Non-Controlled release. The Controlled main
firmware can run on Controlled units, but it can not run on Non-Controlled units. The Non-
Controlled main firmware can run on both Controlled and Non-Controlled units.
Serial Number Synopsis: Any 31 characters
Shows the serial number of the device.
Boot Version Synopsis: Any 47 characters
Shows the version and the build date of the boot loader software.
Main Version Synopsis: Any 47 characters
Shows the version and build date of the main operating system software.
Required Boot Synopsis: Any 15 characters
Shows the minimum boot software loader version required by running main.
Hardware ID Synopsis: { RSMCPU (40-00-0008 Rev B1), RSMCPU2 (40-00-0026 Rev A1), RS400
(40-00-0010 Rev B2), RMC30, RS900 (40-00-0025 Rev B1), RS900 (40-00-0032 Rev
B1), RS1600M, RS400 (40-00-0010 Rev C1), RSG2100, RS900G, RSG2200, RS969,
RS900 (v2, 40-00-0066), RS900 (v2, 40-00-0067), , RS416 (40-00-0078), RMC30 (v2),
RS930 (40-00-0089), RS969 (v2, 40-00-0090), RS910 (40-00-0091-001 Rev A), RS920L
(40-00-0102-001 Rev A), RS940G (40-00-0097-000 Rev A), RSi80X series CPU board,
RSG2300, RS416v2, ... }
44 Viewing Product Information
Page 59

RUGGEDCOM ROS
2
11
1
3
4
5
6
7
8
9
User Guide
Parameter Description
Shows the type, part number, and revision level of the hardware.
Device Management
Section 3.2
Viewing CPU Diagnostics
To view CPU diagnostic information useful for troubleshooting hardware and software performance, navigate to
Diagnostics » View CPU Diagnostics. The CPU Diagnostics form appears.
Chapter 3
Figure 9: CPU Diagnostics Form
1. Running Time Box 2. Total Powered Time Box 3. CPU Usage Box 4. RAM Total Box 5. RAM Free Box 6. RAM Low Watermark
Box 7. Temperature Box 8. Free Rx Bufs Box 9. Free Tx Bufs Box 10. Reload Button
This screen displays the following information:
Parameter Description
Running Time Synopsis: DDDD days, HH:MM:SS
The amount of time since the device was last powered on.
Total Powered time Synopsis: DDDD days, HH:MM:SS
The cumulative powered up time of the device.
CPU Usage Synopsis: 0.0 to 100.0%
The percentage of available CPU cycles used for device operation as measured over the
last second.
RAM Total Synopsis: 0 to 4294967295
The total size of RAM in the system.
RAM Free Synopsis: 0 to 4294967295
The total size of RAM still available.
RAM Low Watermark Synopsis: 0 to 4294967295
Viewing CPU Diagnostics 45
Page 60

Chapter 3
3
2
1
Device Management
Parameter Description
The size of RAM that have never been used during the system runtime.
Temperature Synopsis: -32768 to 32767 C
The temperature on CPU board.
Free Rx Bufs Synopsis: 0 to 4294967295
Free Rx Buffers.
Free Tx Bufs Synopsis: 0 to 4294967295
Free Tx Buffers.
Section 3.3
RUGGEDCOM ROS
Restoring Factory Defaults
The device can be completely or partially restored to its original factory default settings. Excluding groups of
parameters from the factory reset, such as those that affect basic connectivity and SNMP management, is useful
when communication with the device is still required during the reset.
The following categories are not affected by a selective configuration reset:
• IP Interfaces
• IP Gateways
• SNMP Users
• SNMP Security to Group Maps
• SNMP Access
• RUGGEDCOM Discovery Protocol™ (RCDP)
In addition, the following categories are not affected by a full or selective configuration reset:
• Time Zone
• DST Offset
• DST Rule
To restore factory defaults, do the following:
1. Navigate to Diagnostics » Load Factory Defaults. The Load Factory Defaults form appears.
User Guide
Figure 10: Load Factory Defaults Form
1. Defaults Choice List 2. Apply Button 3. Reload
2. Configure the following parameter(s) as required:
46 Restoring Factory Defaults
Page 61

RUGGEDCOM ROS
User Guide
NOTE
If the VLAN ID for the Management IP interface is not 1, setting Defaults Choice to Selected
will automatically set it to 1.
Parameter Description
Defaults Choice Synopsis: { None, Selected, All }
Setting some records like IP Interfaces management interface, default gateway, SNMP
settings to default value would cause switch not to be accessible with management
applications. This parameter allows user to choose to load defaults to Selected tables,
which would preserve configuration for tables that are critical for switch management
applications, or to force All tables to default settings.
3. Click Apply.
Section 3.4
Uploading/Downloading Files
Files can be transferred between the device and a host computer using any of the following methods:
• Xmodem using the CLI shell over a Telnet or RS232 console session
• TFTP client using the CLI shell in a console session and a remote TFTP server
• TFTP server from a remote TFTP client
• SFTP (secure FTP over SSH) from a remote SFTP client
Device Management
Chapter 3
NOTE
The contents of the internal file system are fixed. New files and directories cannot be created, and
existing files cannot be deleted. Only the files that can be uploaded to the device can be overwritten.
Files that may need to be uploaded or downloaded include:
• main.bin – the main ROS application firmware image
• boot.bin – the boot loader firmware image
• fpga.xsvf – the FPGA firmware binary image
• config.csv – the complete configuration database, in the form of a comma-delimited ASCII text file
• banner.txt – contains text that appears on the login screen
The following sections describe how to upload and download files:
• Section 3.4.1, “Uploading/Downloading Files Using XMODEM”
• Section 3.4.2, “Uploading/Downloading Files Using a TFTP Client”
• Section 3.4.3, “Uploading/Downloading Files Using a TFTP Server”
• Section 3.4.4, “Uploading/Downloading Files Using an SFTP Server”
Uploading/Downloading Files 47
Page 62

Chapter 3
Device Management
Section 3.4.1
Uploading/Downloading Files Using XMODEM
To updload or download a file using XMODEM, do the following:
NOTE
This method requires a host computer that has terminal emulation or Telnet software installed and the
ability to perform XMODEM transfers.
NOTE
Xmodem transfers can only be performed through the serial console, which is authenticated during
login.
1. Establish a direct connection between the device and the host computer. For more information, refer to
Section 2.1.1, “Connecting Directly”.
2. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
NOTE
The send option sends files to the host computer, while the receive option pulls files from the
host computer.
RUGGEDCOM ROS
User Guide
3. At the CLI prompt, type:
xmodem [send | receive] filename
Where:
• filename is the name of the file (i.e. main.bin)
NOTE
If available in the terminal emulation or Telnet software, select the XModem 1K protocol for
transmission over the standard XModem option.
4. When the device responds with
Press Ctrl-X to cancel
, launch the XMODEM transfer from the host computer. The device will indicate when the transfer is
complete.
The following is an example from the CLI shell of a successful XMODEM file transfer:
>xmodem receive main.bin
Press Ctrl-X to cancel
Receiving data now ...C
Received 1428480 bytes. Closing file main.bin ...
main.bin transferred successfully
Section 3.4.2
Uploading/Downloading Files Using a TFTP Client
To updload or download a file using a TFTP client, do the following:
48 Uploading/Downloading Files Using XMODEM
Page 63

RUGGEDCOM ROS
User Guide
Device Management
IMPORTANT!
TFTP does not define an authentication scheme. Any use of the TFTP client or server is considered
highly insecure.
NOTE
This method requires a TFTP server that is accessible over the network.
1. Identify the IP address of the computer running the TFTP server.
2. Establish a direct connection between the device and a host computer. For more information, refer to
Section 2.1.1, “Connecting Directly”.
3. Log in to the device as an admin user and access the CLI shell. For more information about accessing the
CLI shell, refer to Section 2.6, “Using the Command Line Interface”.
4. At the CLI prompt, type:
tftp address [get | put] source-filename destination-filename
Where:
• get copies files from the host computer to the device
Chapter 3
• put copies files from the device to the host computer
• address is the IP address of the computer running the TFTP server
• source-filename is the name of the file to be transferred
• destination-filename is the name of the file (on the device or the TFTP server) that will be replaced
during the transfer
The following is an example of a successful TFTP client file transfer:
>tftp 10.0.0.1 get ROS-CF52_Main_v3.7.0.bin main.bin
TFTP CMD: main.bin transfer ok. Please wait, closing file ...
TFTP CMD: main.bin loading succesful.
Section 3.4.3
Uploading/Downloading Files Using a TFTP Server
To updload or download a file using a TFTP server, do the following:
IMPORTANT!
TFTP does not define an authentication scheme. Any use of the TFTP client or server is considered
highly insecure.
NOTE
This method requires a host computer that has TFTP server software installed.
IMPORTANT!
Interaction with TFTP servers is strictly controlled within the device to prevent unauthorized access.
Make sure the device is configured to accept the TFTP connection. For more information, refer to
Section 3.9, “Configuring IP Services”.
Uploading/Downloading Files Using a TFTP Server 49
Page 64

Chapter 3
Device Management
1. Establish a direct connection between the device and the host computer. For more information, refer to
Section 2.1.1, “Connecting Directly”.
2. Initialize the TFTP server on the host computer and launch the TFTP transfer. The server will indicate when
the transfer is complete.
The following is an example of a successful TFTP server exchange:
C:\>tftp -i 10.1.0.1 put C:\files\ROD-CF52_Main_v3.7.0.bin main.bin
Transfer successful: 1428480 bytes in 4 seconds, 375617 bytes/s
Section 3.4.4
Uploading/Downloading Files Using an SFTP Server
SFTP (Secure File Transfer Protocol) is a file transfer mechanism that uses SSH to encrypt every aspect of file
transfer between a networked client and server.
NOTE
The device does not have an SFTP client and, therefore, can only receive SFTP files from an external
source. SFTP requires authentication for the file transfer.
RUGGEDCOM ROS
User Guide
To updload or download a file using an SFTP server, do the following:
NOTE
This method requires a host computer that has SFTP client software installed.
1. Establish an SFTP connection between the device and the host computer.
2. Launch the SFTP transfer. The client will indicate when the transfer is complete.
The following is an example of a successful SFTP server exchange:
user@host$ sftp admin@ros_ip
Connecting to ros_ip...
admin@ros_ip's password:
sftp> put ROS-CF52_Main_v3-7-0.bin main.bin
Uploading ROS-CF52_Main_v3-7-0.bin to /main.bin
ROS-CF52_Main_v3-7-0.bin 100% 2139KB 48.6KB/s 00:44
sftp>
Section 3.5
Managing Logs
The crash (crashlog.txt) and system (syslog.txt) log files contain historical information about events that
have occurred during the operation of the device.
The crash log contains debugging information related to problems that might have resulted in unplanned restarts
of the device or which may effect the operation of the device. A file size of 0 bytes indicates that no unexpected
events have occurred.
The system log contains a record of significant events including startups, configuration changes, firmware
upgrades and database re-initializations due to feature additions. The system log will accumulate information until
it is full, holding approximately 2 MB of data.
50 Uploading/Downloading Files Using an SFTP Server
Page 65

RUGGEDCOM ROS
1
User Guide
Device Management
The following sections describe how to configure and manage logs:
• Section 3.5.1, “Viewing Local Logs”
• Section 3.5.2, “Clearing Local Logs”
• Section 3.5.3, “Configuring the Local System Log”
• Section 3.5.4, “Managing Remote Logging”
Section 3.5.1
Viewing Local Logs
The local crash and system logs can both be downloaded from the device and viewed in a text editor. For more
information about downloading log files, refer to Section 3.4, “Uploading/Downloading Files”.
To view the system log through the Web interface, navigate to Diagnostics » View System Log. The syslog.txt
form appears.
Chapter 3
Figure 11: syslog.txt Form
Section 3.5.2
Clearing Local Logs
To clear both the local crash and system logs, log in to the CLI shell and type:
clearlogs
To clear only the local system log, log in to the Web interface and do the following:
1. Navigate to Diagnostics » Clear System Log. The Clear System Log form appears.
Figure 12: Clear System Log Form
1. Confirm Button
2. Click Confirm.
Viewing Local Logs 51
Page 66

Chapter 3
32
1
Device Management
Section 3.5.3
Configuring the Local System Log
To configure the severity level for the local system log, do the following:
NOTE
For maximum reliability, use remote logging. For more information, refer to Section 3.5.4, “Managing
Remote Logging”.
1. Navigate to Administration » Configure Syslog » Configure Local Syslog. The Local Syslog form
appears.
RUGGEDCOM ROS
User Guide
Figure 13: Local Syslog Form
1. Local Syslog Level 2. Apply Button 3. Reload Button
2. Configure the following parameter(s) as required:
Parameter Description
Local Syslog Level Synopsis: { EMERGENCY, ALERT, CRITICAL, ERROR, WARNING, NOTICE,
INFORMATIONAL, DEBUGGING }
Default: INFORMATIONAL
The severity of the message that has been generated. Note that the severity level
selected is considered the minimum severity level for the system. For example, if
ERROR is selected, the system sends any syslog messages generated by Error,
Critical, Alert and Emergency.
3. Click Apply.
Section 3.5.4
Managing Remote Logging
In addition to the local system log maintained on the device, a remote system log can be configured as well to
collect important event messages. The syslog client resides on the device and supports up to 5 collectors (or
syslog servers).
The remote syslog protocol, defined in RFC 3164, is a UDP/IP-based transport that enables the device to send
event notification messages across IP networks to event message collectors, also known as syslog servers. The
protocol is designed to simply transport these event messages from the generating device to the collector(s).
The following sections describe how to configure a remote syslog client and server:
• Section 3.5.4.1, “Configuring the Remote Syslog Client”
• Section 3.5.4.2, “Viewing a List of Remote Syslog Servers”
52 Configuring the Local System Log
Page 67

RUGGEDCOM ROS
32
1
User Guide
Device Management
• Section 3.5.4.3, “Adding a Remote Syslog Server”
• Section 3.5.4.4, “Deleting a Remote Syslog Server”
Section 3.5.4.1
Configuring the Remote Syslog Client
To configure the remote syslog client, do the following:
1. Navigate to Administration » Configure Syslog » Configure Remote Syslog Client. The Remote Syslog
Client form appears.
Chapter 3
Figure 14: Remote Syslog Client Form
1. UDP Port 2. Apply Button 3. Reload Button
2. Configure the following parameter(s) as required:
Parameter Description
UDP Port Synopsis: 1025 to 65535 or { 514 }
Default: 514
The local UDP port through which the client sends information to the server(s).
3. Click Apply.
Section 3.5.4.2
Viewing a List of Remote Syslog Servers
To view a list of known remote syslog servers, navigate to Administration » Configure Syslog » Configure
Remote Syslog Server. The Remote Syslog Server table appears.
Configuring the Remote Syslog Client 53
Page 68

Chapter 3
1
Device Management
Figure 15: Remote Syslog Server Table
If remote syslog servers have not been configured, add the servers as needed. For more information, refer to
Section 3.5.4.3, “Adding a Remote Syslog Server”.
Section 3.5.4.3
Adding a Remote Syslog Server
RUGGEDCOM ROS
User Guide
ROS supports up to 5 remote syslog servers (or collectors). Similar to the local system log, a remote system log
server can be configured to log information at a specific severity level. Only messages of a severity level equal to
or greater than the specified severity level are written to the log.
To add a remote syslog server to the list of known servers, do the following:
1. Navigate to Administration » Configure Syslog » Configure Remote Syslog Server. The Remote
Syslog Server table appears.
Figure 16: Remote Syslog Server Table
1. InsertRecord
2. Click InsertRecord. The Remote Syslog Server form appears.
54 Adding a Remote Syslog Server
Page 69

RUGGEDCOM ROS
75
6
4
3
2
1
User Guide
Figure 17: Remote Syslog Server Form
1. IP Address Box 2. UDP Port Box 3. Facility Box 4. Severity Box 5. Apply Button 6. Delete Button 7. Reload Button
3. Configure the following parameter(s) as required:
Parameter Description
Device Management
Chapter 3
IP Address Synopsis: ###.###.###.### where ### ranges from 0 to 255
Syslog server IP Address.
UDP Port Synopsis: 1025 to 65535 or { 514 }
Facility Synopsis: { USER, LOCAL0, LOCAL1, LOCAL2, LOCAL3, LOCAL4, LOCAL5,
Severity Synopsis: { EMERGENCY, ALERT, CRITICAL, ERROR, WARNING, NOTICE,
Default: 514
The UDP port number on which the remote server listens.
LOCAL6, LOCAL7 }
Default: LOCAL7
Syslog Facility is one information field associated with a syslog message. The syslog
facility is the application or operating system component that generates a log message.
ROS map all syslog logging information onto a single facility which is configurable by
user to facilitate remote syslog server.
INFORMATIONAL, DEBUGGING }
Default: DEBUGGING
The severity level is the severity of the message that has been generated. Please note
that the severity level user select is accepted as the minimum severity level for the
system. For example, if user selects the severity level as 'Error' then the system send
any syslog message originated by Error, Critical, Alert and Emergency.
4. Click Apply.
Section 3.5.4.4
Deleting a Remote Syslog Server
To delete a remote syslog server from the list of known servers, do the following:
1. Navigate to Administration » Configure Syslog » Configure Remote Syslog Server. The Remote
Syslog Server table appears.
Deleting a Remote Syslog Server 55
Page 70

Chapter 3
75
6
4
3
2
1
Device Management
Figure 18: Remote Syslog Server Table
2. Select the server from the table. The Remote Syslog Server form appears.
RUGGEDCOM ROS
User Guide
Figure 19: Remote Syslog Server Form
1. IP Address Box 2. UDP Port Box 3. Facility Box 4. Severity Box 5. Apply Button 6. Delete Button 7. Reload Button
3. Click Delete.
Section 3.6
Managing Ethernet Ports
The following sections describe how to set up and manage Ethernet ports:
NOTE
For information about configuring remote monitoring for Ethernet ports, refer to Section 3.10,
“Managing Remote Monitoring”.
• Section 3.6.1, “Controller Protection Through Link Fault Indication (LFI)”
• Section 3.6.2, “Viewing the Status of Ethernet Ports”
• Section 3.6.3, “Viewing Statistics for All Ethernet Ports”
• Section 3.6.4, “Viewing Statistics for Specific Ethernet Ports”
• Section 3.6.5, “Clearing Statistics for Specific Ethernet Ports”
56 Managing Ethernet Ports
Page 71

RUGGEDCOM ROS
2
1
5
3
4
User Guide
Device Management
• Section 3.6.6, “Managing SFP Transceivers”
• Section 3.6.7, “Configuring an Ethernet Port”
• Section 3.6.8, “Configuring Port Rate Limiting”
• Section 3.6.9, “Configuring Port Mirroring”
• Section 3.6.10, “Configuring Link Detection”
• Section 3.6.11, “Detecting Cable Faults”
• Section 3.6.12, “Resetting Ethernet Ports”
Section 3.6.1
Controller Protection Through Link Fault Indication (LFI)
Modern industrial controllers often feature backup Ethernet ports used in the event of a link failure. When these
interfaces are supported by media (such as fiber) that employ separate transmit and receive paths, the interface
can be vulnerable to failures that occur in only one of the two paths.
Consider for instance two switches (A and B) connected to a controller. Switch A is connected to the main port on
the controller, while Switch B is connected to the backup port, which is shut down by the controller while the link
with Switch A is active. Switch B must forward frames to the controller through Switch A.
Chapter 3
Figure 20: Example
1. Switch A 2. Switch B 3. Main Transmit Path 4. Backup Transmit Path 5. Controller
If the transmit path from the controller to Switch A fails, Switch A still generates a link signal to the controller
through the receive path. The controller still detects the link with Switch A and does not failover to the backup
port.
This situation illustrates the need for a notification method that tells a link partner when the link integrity signal
has stopped. Such a method natively exists in some link media, but not all.
100Base-TX, 1000Base-T, 1000Base-X Includes a built-in auto-negotiation feature (i.e. a special flag called Remote Fault Indication
100Base-FX Links Includes a standard Far-End-Fault-Indication (FEFI) feature defined by the IEEE 802.3
10Base-FL LInks No standard support.
Controller Protection Through Link Fault Indication (LFI) 57
is set in the transmitted auto-negotation signal).
standard for this link type. This feature includes:
• Transmitting FEFI
Transmits a modified link integrity signal in case a link failure is detected (i.e. no link
signal is received from the link partner)
• Detecting FEFI
Indicates link loss in case an FEFI signal is received from the link partner
Page 72

Chapter 3
Device Management
RUGGEDCOM ROS
10Base-FL links do not have a native link partner notification mechanism and FEFI support in 100Base-FX links
is optional according to the IEEE 802.3 standard, which means that some links partners may not support it.
Siemens offers an advanced Link-Fault-Indication (LFI) feature for the links that do not have a native link partner
notification mechanism. With LFI enabled, the device bases the generation of a link integrity signal upon its
reception of a link signal. In the example described previously, if switch A fails to receive a link signal from the
controller, it will stop generating a link signal. The controller will detect the link failure and failover to the backkup
port.
IMPORTANT!
If both link partners have the LFI feature, it must not be enabled on both sides of the link. If it is enabled
on both sides, the link will never be established, as each link partner will be waiting for the other to
transmit a link signal.
The switch can also be configured to flush the MAC address table for the controller port. Frames destined for the
controller will be flooded to Switch B where they will be forwarded to the controller (after the controller transmits
its first frame).
Section 3.6.2
Viewing the Status of Ethernet Ports
User Guide
To view the current status of each Ethernet port, navigate to Ethernet Ports » View Port Status. The Port
Status table appears.
Figure 21: Port Status Table
This table displays the following information:
Parameter Description
Port Synopsis: 1 to maximum port number
The port number as seen on the front plate silkscreen of the switch.
Name Synopsis: Any 15 characters
A descriptive name that may be used to identify the device conected on that port.
Link Synopsis: { ----, ----, Down, Up }
The port's link status.
Speed Synopsis: { ---, 10M, 100M, 1G, 10G }
58 Viewing the Status of Ethernet Ports
Page 73

RUGGEDCOM ROS
User Guide
Parameter Description
The port's current speed.
Duplex Synopsis: { ----, Half, Full }
The port's current duplex status.
Device Management
Section 3.6.3
Viewing Statistics for All Ethernet Ports
To view statistics collected for all Ethernet ports, navigate to Ethernet Stats » View Ethernet Statistics. The
Ethernet Statistics table appears.
Chapter 3
Figure 22: Ethernet Statistics Table
This table displays the following information:
Parameter Description
Port Synopsis: 1 to maximum port number
The port number as seen on the front plate silkscreen of the switch.
State Synopsis: { ----, ----, Down, Up }
InOctets Synopsis: 0 to 4294967295
The number of octets in received good packets (Unicast+Multicast+Broadcast) and dropped
packets.
OutOctets Synopsis: 0 to 4294967295
The number of octets in transmitted good packets.
InPkts Synopsis: 0 to 4294967295
The number of received good packets (Unicast+Multicast+Broadcast) and dropped packets.
OutPkts Synopsis: 0 to 4294967295
The number of transmitted good packets.
ErrorPkts Synopsis: 0 to 4294967295
The number of any type of erroneous packet.
Viewing Statistics for All Ethernet Ports 59
Page 74

Chapter 3
Device Management
Section 3.6.4
Viewing Statistics for Specific Ethernet Ports
To view statistics collected for specific Ethernet ports, navigate to Ethernet Stats » View Ethernet Port
Statistics. The Ethernet Port Statistics table appears.
Figure 23: Ethernet Port Statistics Table
RUGGEDCOM ROS
User Guide
This table displays the following information:
Parameter Description
Port Synopsis: 1 to maximum port number
The port number as seen on the front plate silkscreen of the switch.
InOctets Synopsis: 0 to 18446744073709551615
The number of octets in received good packets (Unicast+Multicast+Broadcast) and dropped
packets.
OutOctets Synopsis: 0 to 18446744073709551615
The number of octets in transmitted good packets.
InPkts Synopsis: 0 to 18446744073709551615
The number of received good packets (Unicast+Multicast+Broadcast) and dropped packets.
OutPkts Synopsis: 0 to 18446744073709551615
The number of transmitted good packets.
TotalInOctets Synopsis: 0 to 18446744073709551615
The total number of octets of all received packets. This includes data octets of rejected and
local packets which are not forwarded to the switching core for transmission. It should reflect
all the data octets received on the line.
TotalInPkts Synopsis: 0 to 18446744073709551615
The number of received packets. This includes rejected, dropped local, and packets
which are not forwarded to the switching core for transmission. It should reflect all packets
received ont the line.
InBroadcasts Synopsis: 0 to 18446744073709551615
The number of good Broadcast packets received.
InMulticasts Synopsis: 0 to 18446744073709551615
The number of good Multicast packets received.
60 Viewing Statistics for Specific Ethernet Ports
Page 75

RUGGEDCOM ROS
User Guide
Parameter Description
CRCAlignErrors Synopsis: 0 to 4294967295
The number of packets received which meet all the following conditions:
• Packet data length is between 64 and 1536 octets inclusive.
• Packet has invalid CRC.
• Collision Event has not been detected.
• Late Collision Event has not been detected.
OversizePkts Synopsis: 0 to 4294967295
The number of packets received with data length greater than 1536 octets and valid CRC.
Fragments Synopsis: 0 to 4294967295
The number of packets received which meet all the following conditions:
• Packet data length is less than 64 octets, or packet without SFD and is less than 64
octets in length.
• Collision Event has not been detected.
• Late Collision Event has not been detected.
• Packet has invalid CRC.
Jabbers Synopsis: 0 to 4294967295
The number of packets which meet all the following conditions:
• Packet data length is greater that 1536 octets.
• Packet has invalid CRC.
Device Management
Chapter 3
Collisions Synopsis: 0 to 4294967295
The number of received packets for which Collision Event has been detected.
LateCollisions Synopsis: 0 to 4294967295
The number of received packets for which Late Collision Event has been detected.
Pkt64Octets Synopsis: 0 to 4294967295
The number of received and transmitted packets with size of 64 octets. This includes
received and transmitted packets as well as dropped and local received packets. This does
not include rejected received packets.
Pkt65to127Octets Synopsis: 0 to 4294967295
The number of received and transmitted packets with size of 65 to 127 octets. This includes
received and transmitted packets as well as dropped and local received packets. This does
not include rejected received packets.
Pkt128to255Octets Synopsis: 0 to 4294967295
The number of received and transmitted packets with size of 128 to 257 octets. This
includes received and transmitted packets as well as dropped and local received packets.
This does not include rejected received packets.
Pkt256to511Octets Synopsis: 0 to 4294967295
The number of received and transmitted packets with size of 256 to 511 octets. This
includes received and transmitted packets as well as dropped and local received packets.
This does not include rejected received packets.
Pkt512to1023Octets Synopsis: 0 to 4294967295
The number of received and transmitted packets with size of 512 to 1023 octets. This
includes received and transmitted packets as well as dropped and local received packets.
This does not include rejected received packets.
Pkt1024to1536Octets Synopsis: 0 to 4294967295
Viewing Statistics for Specific Ethernet Ports 61
Page 76

Chapter 3
1
2
Device Management
Parameter Description
The number of received and transmitted packets with size of 1024 to 1536 octets. This
includes received and transmitted packets as well as dropped and local received packets.
This does not include rejected received packets.
DropEvents Synopsis: 0 to 4294967295
The number of received packets that are droped due to lack of receive buffers.
OutMulticasts Synopsis: 0 to 18446744073709551615
The number of transmitted Multicast packets. This does not include Broadcast packets.
OutBroadcasts Synopsis: 0 to 18446744073709551615
The number of transmitted Broadcast packets.
UndersizePkts Synopsis: 0 to 4294967295
The number of received packets which meet all the following conditions:
• Packet data length is less than 64 octets.
• Collision Event has not been detected.
• Late Collision Event has not been detected.
• Packet has valid CRC.
RUGGEDCOM ROS
User Guide
Section 3.6.5
Clearing Statistics for Specific Ethernet Ports
To clear the statistics collected for one or more Ethernet ports, do the following:
1. Navigate to Ethernet Stats » Clear Ethernet Port Statistics. The Clear Ethernet Port Statistics form
appears.
Figure 24: Clear Ethernet Port Statistics Form (Typical)
1. Port Check Boxes 2. Confirm Button
2. Select one or more Ethernet ports.
3. Click Confirm.
Section 3.6.6
Managing SFP Transceivers
ROS supports Small Form Factor Pluggable (SFP) transceivers to provide a 1000Base-X, 100Base-FX,
1000Base-T or 100Base-TX link.
62 Clearing Statistics for Specific Ethernet Ports
Page 77

RUGGEDCOM ROS
User Guide
NOTE
Since 1000Base-X fiber SFP transceivers are standardized, ROS supports any model of this type. It
is strongly recommended to use SFP transceiver models offered by Siemens only. Siemens performs
extensive testing on the transceivers in harsh conditions. If a different SFP transceiver model is used, it
is the user’s responsibility to verify it meets environmental and usage requirements.
1000Base-T copper SFP transceivers are not standardized. ROS supports only selected models of this
type.
NOTE
SFP transceivers are hot swappable.
When an SFP transceiver is inserted in to the SFP cage, the speed and auto-negotiation settings for
the port are automatically adjusted to the appropriate values. For example, if a 1 G SFP transceiver is
installed, the speed of the port is automatically changed to 1 G and auto-negotiation is set to On.
The following sections describe how to configure and manage SFP transceivers:
• Section 3.6.6.1, “Configuring an SFP Port”
• Section 3.6.6.2, “Monitoring an SFP Port”
• Section 3.6.6.3, “Displaying Information for an SFP Port”
Device Management
Chapter 3
Section 3.6.6.1
Configuring an SFP Port
Depending on the required link media type, an SFP port may require some explicit configuration:
• For 1000Base-X or 1000Base-T links, the speed of the SFP port must be set to 1 Gbps.
• For 100Base-FX or 100Base-TX links, the speed must be set to 100 Mbps.
• Auto-negotiation can be configured to On when the port speed is set to 1 Gbps, or to Off when the port speed
is set to 100 Mbps.
• Duplex mode cannot be configured on an SFP port and is always forced to full duplex.
For more information about configuring SFP transceiver ports and other Ethernet ports on the device, refer to
Section 3.6.7, “Configuring an Ethernet Port”.
Section 3.6.6.2
Monitoring an SFP Port
ROS supports hot-swapping of SFP transceivers on SFP ports and will automatically detect when an SFP
transceiver is removed or installed.
When ROS detects that an SFP transceiver is plugged into an SFP port, it reads the transceiver information and
determines the transceiver type. This decision results in ROS either accepting, accepting and reconfiguring, or
rejecting the SFP port.
The following table shows in which cases an SFP transceiver is accepted or accepted and reconfigured.
Configuring an SFP Port 63
Page 78

Chapter 3
Device Management
RUGGEDCOM ROS
User Guide
Configured Speed
1 Gbps Accept
100 Mbps
Accept and automatically
set the speed to 1 Gbps and
set auto-negotiation to On
Detected SFP
Type: 1000Base-X
Detected SFP
Type: 100Base-FX
Accept and automatically set
the speed to 100 Mbps and
set auto-negotiation to Off
Accept
Detected SFP
Type: 1000Base-T
Accept
Compare the transceiver model
against a list of supported
models. Accept if it is in the
list. Otherwise, automatically
set the speed to 1 Gbps and
set auto-negotiation to On.
If the transceiver is accepted, the Media parameter under Ethernet Ports » Configure Port Parameters shows
detailed information about the SFP transceiver, including Gigabit Ethernet Compliance Code, transmission media,
connector type, and link length. For example:
SFP 1000LX SM LC 10 km
SFP 1000T 100 m
If the transceiver is not recognized, it is rejected. An alarm is also generated and the port is blocked so that
no link can be established until the transceiver is replaced. The Media parameter shows the rejected SFP
transceiver is unidentified. For example:
SFP Unidentified
If no transceiver is installed on an SFP port, the Media parameter shows the SFP transceiver is unplugged:
SFP Unplugged
Section 3.6.6.3
Displaying Information for an SFP Port
To display detailed information about an SFP port, do the following:
1. Log in to the device and access the CLI shell. For more information about accessing the CLI shell, refer to
Section 2.6, “Using the Command Line Interface”.
2. Type the following command:
sfp port
Where:
• port is the port number
Information about the SFP port is displayed. For example:
>sfp 11/1
ID: SFP
Extended ID: GBIC/SFP function is defined by serial ID only
Connector: LC
Transceiver:
Gigabit Ethernet Compliance Codes:
1000LX
Fibre Channel link length:
Long Distance (L)
Fibre Channel transmitter technology:
Longwave laser (LC)
Fibre Channel transmission media:
Single Mode (SM)
64 Displaying Information for an SFP Port
Page 79

RUGGEDCOM ROS
User Guide
Fibre Channel speed:
100 MBytes/Sec
Baud Rate, nominal: 1300 MBits/sec
Encoding type: 8B10B
Length(9um): 10 km
Length(9um): 10000 m
Length(50um): 550 m
Length(62.5um): 550 m
Length(Copper): Not specified
Vendor: xxxxxxx
IEEE company ID: xxxxxxx
Part number: xxxxxxxxxx
Revision: 0000
Laser wavelength: 1310 nm
>
Section 3.6.7
Configuring an Ethernet Port
To configure an Ethernet port, do the following:
NOTE
Depending on the required link media type, an SFP port may require some explicit configuration.
Before configuring an SFP port, refer to Section 3.6.6.1, “Configuring an SFP Port”.
Device Management
Chapter 3
1. Navigate to Ethernet Ports » Configure Port Parameters. The Port Parameters table appears.
Figure 25: Port Parameters Table
2. Select an Ethernet port. The Port Parameters form appears.
Configuring an Ethernet Port 65
Page 80

Chapter 3
7
11
6
5
4
3
2
1
8
12
9
10
Device Management
Figure 26: Port Parameters Form
1. Port Box 2. Name Box 3. Media Box 4. State Box 5. AutoN Box 6. Speed Box 7. Dupx Box 8. FlowCtrl Box 9. LFI
Box 10. Alarm Box 11. Apply Button 12. Reload Button
RUGGEDCOM ROS
User Guide
3. Configure the following parameter(s) as required:
Parameter Description
Port Synopsis: 1 to maximum port number
Name Synopsis: Any 15 characters
Media Synopsis: { 100TX, 10FL, 100FX, 1000X, 1000T, 802.11g, EoVDSL, 100TX Only,
State Synopsis: { Disabled, Enabled }
AutoN Synopsis: { Off, On }
Default: 1
The port number as seen on the front plate silkscreen of the switch.
Default: Port x
A descriptive name that may be used to identify the device connected on that port.
10FL/100SX, 10GX }
Default: 100TX
The type of the port media.
Default: Enabled
Disabling a port will prevent all frames from being sent and received on that port. Also,
when disabled link integrity signal is not sent so that the link/activity LED will never be
lit. You may want to disable a port for troubleshooting or to secure it from unauthorized
connections.
NOTE
Disabling a port whose media type is set to 802.11g disables the
corresponding wireless module.
Default: On
Enable or disable IEEE 802.3 auto-negotiation. Enabling auto-negotiation results in
speed and duplex being negotiated upon link detection; both end devices must be autonegotiation compliant for the best possible results. 10Mbps and 100Mbps fiber optic
66 Configuring an Ethernet Port
Page 81

RUGGEDCOM ROS
User Guide
Parameter Description
Device Management
Chapter 3
media do not support auto-negotiation so these media must be explicitly configured to
either half or full duplex. Full duplex operation requires that both ends are configured as
such or else severe frame loss will occur during heavy network traffic.
Speed Synopsis: { Auto, 10M, 100M, 1G }
Dupx Synopsis: { Auto, Half, Full }
Flow Control Synopsis: { Off, On }
LFI Synopsis: { Off, On }
Default: Auto
Speed (in Megabit-per-second or Gigabit-per-second). If auto-negotiation is enabled,
this is the speed capability advertised by the auto-negotiation process. If autonegotiation is disabled, the port is explicitly forced to this speed mode.
AUTO means advertise all supported speed modes.
Default: Auto
Duplex mode. If auto-negotiation is enabled, this is the duplex capability advertised by
the auto-negotiation process. If auto-negotiation is disabled, the port is explicitly forced
to this duplex mode.
AUTO means advertise all supported duplex modes.
Default: On
Flow Control is useful for preventing frame loss during times of severe network traffic.
Examples of this include multiple source ports sending to a single destination port or a
higher speed port bursting to a lower speed port.
When the port is half-duplex it is accomplished using 'backpressure' where the switch
simulates collisions causing the sending device to retry transmissions according to the
Ethernet backoff algorithm.
When the port is full-duplex it is accomplished using PAUSE frames which causes the
sending device to stop transmitting for a certain period of time.
Default: Off
Enabling Link-Fault-Indication (LFI) inhibits transmitting link integrity signal when the
receive link has failed. This allows the device at far end to detect link failure under all
circumstances.
Alarm Synopsis: { On, Off }
Default: On
Disabling link state alarms will prevent alarms and LinkUp and LinkDown SNMP traps
from being sent for that port.
NOTE
If one end of the link is fixed to a specific speed and duplex type and the peer auto-negotiates,
there is a strong possibility that the link will either fail to raise, or raise with the wrong settings on
the auto-negotiating side. The auto-negotiating peer will fall back to half-duplex operation, even
when the fixed side is full duplex. Full-duplex operation requires that both ends are configured
as such or else severe frame loss will occur during heavy network traffic. At lower traffic volumes
the link may display few, if any, errors. As the traffic volume rises, the fixed negotiation side will
begin to experience dropped packets, while the auto-negotiating side will experience excessive
collisions. Ultimately, as traffic load approaches 100%, the link will become entirely unusable.
These problems can be avoided by always configuring ports to the appropriate fixed values.
4. Click Apply.
NOTE
This feature must not be enabled at both ends of a fiber link.
Configuring an Ethernet Port 67
Page 82

Chapter 3
65
4
3
2
1
Device Management
Section 3.6.8
Configuring Port Rate Limiting
To configure port rate limiting, do the following:
1. Navigate to Ethernet Ports » Configure Port Rate Limiting. The Port Rate Limiting table appears.
Figure 27: Port Rate Limiting Table
RUGGEDCOM ROS
User Guide
2. Select an Ethernet port. The Port Rate Limiting form appears.
Figure 28: Port Rate Limiting Form
1. Port Box 2. Ingress Limit Box 3. Ingress Frames List 4. Egress Limit Box 5. Apply Button 6. Reload Button
3. Configure the following parameter(s) as required:
Parameter Description
Port Synopsis: 1 to maximum port number
Default: 1
The port number as seen on the front plate silkscreen of the switch.
Ingress Limit Synopsis: 62 to 256000 Kbps or { Disabled }
Ingress Frames Synopsis: { Broadcast, Bcast&Mcast, Bcast&Mcast&FloodUcast, Bcast&FloodUcast,
68 Configuring Port Rate Limiting
Default: 1000 Kbps
The rate after which received frames (of the type described by the ingress frames
parameter) will be discarded by the switch.
FloodUcast, All }
Page 83

RUGGEDCOM ROS
User Guide
Parameter Description
Device Management
Chapter 3
Default: Broadcast
This parameter specifies the types of frames to be rate-limited on this port. It applies
only to received frames:
• Broadcast - only broadcast frames
• Bcast&Mcast - broadcast and multicast frames
• Bcast&FloodUcast - broadcast and flooded unicast frames
• Bcast&Mcast&FloodUcast - broadcast, multicast and flooded unicast frames
• FloodUcast - only flooded unicast frames
• All - all (multicast, broadcast and unicast) frames
Egress Limit Synopsis: { Broadcast, Multicast, Mcast&FloodUcast, All }">62 to 256000 Kbps or
{ Disabled }
Default: Disabled
The maximum rate at which the switch will transmit (multicast, broadcast and unicast)
frames on this port. The switch will discard frames in order to meet this rate if required.
4. Click Apply.
Section 3.6.9
Configuring Port Mirroring
Port mirroring is a troubleshooting tool that copies, or mirrors, all traffic received or transmitted on a designated
port to specified mirror port. If a protocol analyzer is attached to the target port, the traffic stream of valid frames
on any source port is made available for analysis.
Select a target port that has a higher speed than the source port. Mirroring a 100 Mbps port onto a 10 Mbps port
may result in an improperly mirrored stream.
Frames will be dropped if the full-duplex rate of frames on the source port exceeds the transmission speed of the
target port. Since both transmitted and received frames on the source port are mirrored to the target port, frames
will be discarded if the sum traffic exceeds the target port’s transmission rate. This problem reaches its extreme in
the case where traffic on a 100 Mbps full-duplex port is mirrored onto a 10 Mbps half-duplex port.
NOTE
Invalid frames received on the source port will not be mirrored. These include CRC errors, oversize
and undersize packets, fragments, jabbers, collisions, late collisions and dropped events.
IMPORTANT!
Before configuring port mirroring, note the following limitations:
• Traffic will be mirrored onto the target port irrespective of its VLAN membership. It could be the same
as or different from the source port's membership
• Network management frames (such as RSTP, GVRP etc.) may not be mirrored
• Switch management frames generated by the switch (such as Telnet, HTTP, SNMP, etc.) may not be
mirrored
To configure port mirroring, do the following:
1. Navigate to Ethernet Ports » Configure Port Mirroring. The Port Mirroring form appears.
Configuring Port Mirroring 69
Page 84

Chapter 3
5
6
4
3
2
1
Device Management
Figure 29: Port Mirroring Form
1. Port Mirroring Box 2. Source Port Box 3. Target Port Box 4. Apply Button 5. Reload Button
2. Configure the following parameter(s) as required:
Parameter Description
RUGGEDCOM ROS
User Guide
Port Mirroring Synopsis: { Disabled, Enabled }
Source Port Synopsis: Any combination of numbers valid for this parameter
Source Direction Synopsis: Egress and Ingress, Egress Only
Target Port Synopsis: 1 to maximum port number
Default: Disabled
Enabling port mirroring causes all frames received and transmitted by the source port(s)
to be transmitted out of the target port.
The port(s) being monitored.
Default: Egress and Ingress
Specifies monitoring whether both egress and ingress traffics or only egress traffic of the
source port.
Default: 1
The port where a monitoring device should be connected.
3. Click Apply.
Section 3.6.10
Configuring Link Detection
To configure link detection, do the following:
1. Navigate to Ethernet Ports » Configure Link Detection. The Link Detection form appears.
70 Configuring Link Detection
Page 85

RUGGEDCOM ROS
4
3
2
1
User Guide
Figure 30: Link Detection Form
1. Fast Link Detection Box 2. Link Detection Time Box 3. Apply Button 4. Reload Button
2. Configure the following parameter(s) as required:
NOTE
When Fast Link Detection is enabled, the system prevents link state change processing from
consuming all available CPU resources. However, if Port Guard is not used, it is possible for
almost all available CPU time to be consumed by frequent link state changes, which could have a
negative impact on overall system responsiveness.
Device Management
Chapter 3
Parameter Description
Fast Link Detection Synopsis: { Off, On, On_withPortGuard }
Default: On_withPortGuard
This parameter provides protection against faulty end devices generating an improper
link integrity signal. When a faulty end device or a mis-matching fiber port is connected
to the unit, a large number of continuous link state changes could be reported in a short
period of time. These large number of bogus link state changes could render the system
unresponsive as most, if not all, of the system resources are used to process the link
state changes. This could in turn cause a serious network problem as the unit's RSTP
process may not be able to run, thus allowing network loop to form.
Three different settings are available for this parameter:
• ON_withPortGuard - This is the recommended setting. With this setting, an extended
period (~2 minutes) of excessive link state changes reported by a port will prompt Port
Guard feature to disable FAST LINK DETECTION on that port and raise an alarm.
By disabling FAST LINK DETECTION on the problematic port, excessive link state
changes can no longer consume substantial amount of system resources. However if
FAST LINK DETECTION is disabled, the port will need a longer time to detect a link
failure. This may result in a longer network recovery time of up to 2s. Once Port Guard
disables FAST LINK DETECTION of a particular port, user can re-enable FAST LINK
DETECTION on the port by clearing the alarm.
• ON - In certain special cases where a prolonged excessive link state changes
constitute a legitimate link operation, using this setting can prevent Port Guard from
disabling FAST LINK DETECTION on the port in question. If excessive link state
changes persist for more than 2 minutes, an alarm will be generated to warn user
about the observed bouncing link. If the excessive link state changes condition is
resolved later on, the alarm will be cleared automatically. Since this option does not
disable FAST LINK DETECTION, a persistent bouncing link could continue affect the
system in terms of response time. This setting should be used with caution.
• OFF - Turning this parameter OFF will disable FAST LINK DETECTION completely.
The switch will need a longer time to detect a link failure. This will result in a longer
network recovery time of up to 2s.
Link Detection Time Synopsis: 100 ms to 1000 ms
Configuring Link Detection 71
Default: 100 ms
Page 86

Chapter 3
Device Management
Parameter Description
The time that the link has to continuously stay up before the "link up" decision is made
by the device.
(The device performs de-bouncing of Ethernet link detection to avoid multiple responses
to an occasional link bouncing event, e.g. when a cable is shaking while being pluggedin or unplugged).
3. Click Apply.
Section 3.6.11
Detecting Cable Faults
Connectivity issues can sometimes be attributed to faults in Ethernet cables. To help detect cable faults, short
circuits, open cables or cables that are too long, ROS includes a built-in cable diagnostics utility.
The following sections describe how to run diagnostics on Ethernet cables:
• Section 3.6.11.1, “Viewing Cable Diagnostics Results”
• Section 3.6.11.2, “Performing Cable Diagnostics”
• Section 3.6.11.3, “Clearing Cable Diagnostics”
• Section 3.6.11.4, “Determining the Estimated Distance To Fault (DTF)”
RUGGEDCOM ROS
User Guide
Section 3.6.11.1
Viewing Cable Diagnostics Results
To view the results of previous diagnostic tests, navigate to Ethernet Ports » Configure/View Cable
Diagnostics Parameters. The Cable Diagnostics Parameters table appears.
NOTE
For information about how to start a diagnostic test, refer to Section 3.6.11.2, “Performing Cable
Diagnostics”.
Figure 31: Cable Diagnostics Parameters Table
This table displays the following information:
72 Detecting Cable Faults
Page 87

RUGGEDCOM ROS
User Guide
Parameter Description
Port Synopsis: 1 to maximum port number
The port number as seen on the front plate silkscreen of the switch.
State Synopsis: { Stopped, Started }
Control the start/stop of the cable diagnostics on the selected port. If a port does not support
cable diagnostics, State will be reported as N/A.
Runs Synopsis: 0 to 65535
The total number of times cable diagnostics to be performed on the selected port. If this
number is set to 0, cable diagnostics will be performed forever on the selected port.
Calib. Synopsis: -100.0 to 100.0 m
This calibration value can be used to adjust or calibrate the estimated distance to fault. User
can take following steps to calibrate the cable diagnostics estimated distance to fault:
• Pick a particular port which calibration is needed
• Connect an Ethernet cable with a known length (e.g. 50m) to the port
• DO NOT connect the other end of the cable to any link partner
• Run cable diagnostics a few times on the port. OPEN fault should be detected
• Find the average distance to the OPEN fault recorded in the log and compare it to the
known length of the cable. The difference can be used as the calibration value
• Enter the calibration value and run cable diagnostics a few more times
• The distance to OPEN fault should now be at similar distance as the cable length
• Distance to fault for the selected port is now calibrated
Device Management
Chapter 3
Good Synopsis: 0 to 65535
The number of times GOOD TERMINATION (no fault) is detected on the cable pairs of the
selected port.
Open Synopsis: 0 to 65535
The number of times OPEN is detected on the cable pairs of the selected port.
Short Synopsis: 0 to 65535
The number of times SHORT is detected on the cable pairs of the selected port.
Imped Synopsis: 0 to 65535
The number of times IMPEDANCE MISMATCH is detected on the cable pairs of the
selected port.
Pass /Fail /Total Synopsis: Any 19 characters
This field summarizes the results of the cable diagnostics performed so far.
Pass - number of times cable diagnostics successfully completed on the selected port.
Fail - number of times cable diagnostics failed to complete on the selected port.
Total - total number of times cable diagnostics have been attempted on the selected port.
>
NOTE
For each successful diagnostic test, the values for Good, Open, Short or Imped will increment based
on the number of cable pairs connected to the port. For a 100Base-T port, which has two cable pairs,
the number will increase by two. For a 1000Base-T port, which has four cable pairs, the number will
increase by four.
Viewing Cable Diagnostics Results 73
Page 88

Chapter 3
Device Management
NOTE
When a cable fault is detected, an estimated distance-to-fault is calculated and recorded in the system
log. The log lists the cable pair, the fault that was detected, and the distance-to-fault value. For more
information about the system log, refer to Section 3.5.1, “Viewing Local Logs”.
Section 3.6.11.2
Performing Cable Diagnostics
To perform a cable diagnostic test on one or more Ethernet ports, do the following:
1. Connect a CAT-5 (or better quality) Ethernet cable to the selected Ethernet port.
IMPORTANT!
Both the selected Ethernet port and its partner port can be configured to run in Enabled mode with
auto-negotiation, or in Disabled mode. Other modes are not recommended, as they may interfere
with the cable diagnostics procedure.
2. Connect the other end of the cable to a similar network port. For example, connect a 100Base-T port to a
100Base-T port, or a 1000Base-T port to a 1000Base-T port.
3. In ROS, navigate to Ethernet Ports » Configure/View Cable Diagnostics Parameters. The Cable
Diagnostics Parameters table appears.
RUGGEDCOM ROS
User Guide
Figure 32: Cable Diagnostics Parameters Table
4. Select an Ethernet port. The Cable Diagnostics Parameters form appears.
74 Performing Cable Diagnostics
Page 89

RUGGEDCOM ROS
11
10
9
8
7
6
5
4
3
2
1
User Guide
Figure 33: Cable Diagnostics Parameters Form
1. Port Box 2. State Options 3. Runs Box 4. Calib. Box 5. Good Box 6. Open Box 7. Short Box 8. Imped Box 9. Pass /
Fail /Total Box 10. Apply Button 11. Reload Button
Device Management
Chapter 3
5. Under Runs, enter the number of consecutive diagnostic tests to perform. A value of 0 indicates the test will
run continuously until stopped by the user.
6. Under Calib., enter the estimated Distance To Fault (DTF) value. For information about how to determine the
DTF value, refer to Section 3.6.11.4, “Determining the Estimated Distance To Fault (DTF)”.
7. Select Started.
IMPORTANT!
A diagnostic test can be stopped by selecting Stopped and clicking Apply. However, if the test is
stopped in the middle of a diagnostic run, the test will run to completion.
8. Click Apply. The state of the Ethernet port will automatically change to Stopped when the test is complete.
For information about how to monitor the test and view the results, refer to Section 3.6.11.1, “Viewing Cable
Diagnostics Results”.
Section 3.6.11.3
Clearing Cable Diagnostics
To clear the cable diagnostic results, do the following:
1. Navigate to Ethernet Ports » Clear Cable Diagnostics Statistics. The Clear Cable Diagnostics Statistics
form appears.
Clearing Cable Diagnostics 75
Page 90

Chapter 3
1
2
Device Management
Figure 34: Clear Cable Diagnostics Statistics Form
1. Port Check Boxes 2. Apply Button
2. Select one or more Ethernet ports.
3. Click Apply.
Section 3.6.11.4
Determining the Estimated Distance To Fault (DTF)
RUGGEDCOM ROS
User Guide
To determine the estimate Distance To Fault (DTF), do the following:
1. Connect a CAT-5 (or better quality) Ethernet cable with a known length to the device. Do not connect the
other end of the cable to another port.
2. Configure the cable diagnostic utility to run a few times on the selected Ethernet port and start the test. For
more information, refer to Section 3.6.11.2, “Performing Cable Diagnostics”. Open faults should be detected
and recorded in the system log.
3. Review the errors recorded in the system log and determine the average distance of the open faults. For
more information about the system log, refer to Section 3.5.1, “Viewing Local Logs”.
4. Subtract the average distance from the cable length to determine the calibration value.
5. Configure the cable diagnostic utility to run a few times with the new calibration value. The distance to the
open fault should now be the same as the actual length of the cable. The Distance To Fault (DTF) is now
calibrated for the selected Ethernet port.
Section 3.6.12
Resetting Ethernet Ports
At times, it may be necessary to reset a specific Ethernet port, such as when the link partner has latched into an
inappropriate state. This is also useful for forcing a re-negotiation of the speed and duplex modes.
To reset a specific Ethernet port(s), do the following:
1. Navigate to Ethernet Ports » Reset Port(s). The Reset Port(s) form appears.
76 Determining the Estimated Distance To Fault (DTF)
Page 91

RUGGEDCOM ROS
1
2
User Guide
Figure 35: Reset Port(s) Form
1. Ports 2. Apply Button
2. Select one or more Ethernet ports to reset.
3. Click Apply. The selected Ethernet ports are reset.
Section 3.7
Managing IP Interfaces
Device Management
Chapter 3
ROS allows one IP interface to be configured for each subnet (or VLAN), up to a maximum of 255 interfaces. One
of the interfaces must also be configured to be a management interface for certain IP services, such as DHCP
relay agent.
Each IP interface must be assigned an IP address. In the case of the management interface, the IP address type
can be either static, DHCP, BOOTP or dynamic. For all other interfaces, the IP address must be static.
CAUTION!
Configuration hazard – risk of communication disruption. Changing the ID for the management VLAN
will break any active Raw Socket TCP connections. If this occurs, reset all serial ports.
The following sections describe how to set up and manage IP interfaces:
• Section 3.7.1, “Viewing a List of IP Interfaces”
• Section 3.7.2, “Adding an IP Interface”
• Section 3.7.3, “Deleting an IP Interface”
Section 3.7.1
Viewing a List of IP Interfaces
To view a list of IP interfaces configured on the device, navigate to Administration » Configure IP Interfaces »
Configure IP Interfaces. The IP Interfaces table appears.
Managing IP Interfaces 77
Page 92

Chapter 3
1
Device Management
Figure 36: IP Interfaces Table
If IP interfaces have not been configured, add IP interfaces as needed. For more information, refer to
Section 3.7.2, “Adding an IP Interface”.
Section 3.7.2
Adding an IP Interface
RUGGEDCOM ROS
User Guide
To add an IP interface, do the following:
1. Navigate to Administration » Configure IP Interfaces. The IP Interfaces table appears.
Figure 37: IP Interfaces Table
1. InsertRecord
2. Click InsertRecord. The Switch IP Interfaces form appears.
78 Adding an IP Interface
Page 93

RUGGEDCOM ROS
7
8
1
2
3
4
5
6
9
User Guide
Figure 38: IP Interfaces Form
1. Type Options 2. ID Box 3. Mgmt Options 4. IP Address Type Box 5. IP Address Box 6. Subnet Box 7. Apply Button
8. Delete Button 9. Reload Button
Device Management
Chapter 3
3. Configure the following parameter(s) as required:
NOTE
The IP address and mask configured for the management VLAN are not changed when resetting
all configuration parameters to defaults and will be assigned a default VLAN ID of 1. Changes to
the IP address take effect immediately. All IP connections in place at the time of an IP address
change will be lost.
Parameter Description
Type Synopsis: { VLAN }
Default: VLAN
Specifies the type of the interface for which this IP interface is created.
ID Synopsis: 1 to 4094
Default: 1
Specifies the ID of the interface for which this IP interface is created. If the interface type
is VLAN, this represents the VLAN ID.
Mgmt Synopsis: { No, Yes }
Default: No
Specifies whether the IP interface is the device management interface.
IP Address Type Synopsis: { Static, Dynamic, DHCP, BOOTP }
Default: Static
Specifies whether the IP address is static or is dynamically assigned via DHCP or
BOOTP>. The Dynamic option automatically switches between BOOTP and DHCP until
it receives a response from the relevant server. The Static option must be used for nonmanagement interfaces.
IP Address Synopsis: ###.###.###.### where ### ranges from 0 to 255
Adding an IP Interface 79
Default: 192.168.0.1
Specifies the IP address of this device. An IP address is a 32-bit number that is notated
by using four numbers from 0 through 255, separated by periods. Only a unicast IP
address is allowed, which ranges from 1.0.0.0 to 233.255.255.255.
Page 94

Chapter 3
Device Management
Parameter Description
RUGGEDCOM ROS
User Guide
Subnet Synopsis: ###.###.###.### where ### ranges from 0 to 255
Default: 255.255.255.0
Specifies the IP subnet mask of this device. An IP subnet mask is a 32-bit number that
is notated by using four numbers from 0 through 255, separated by periods. Typically,
subnet mask numbers use either 0 or 255 as values (e.g. 255.255.255.0) but other
numbers can appear.
IMPORTANT!
Each IP interface must have a unique network address.
4. Click Apply.
Section 3.7.3
Deleting an IP Interface
To delete an IP interface configured on the device, do the following:
1. Navigate to Administration » Configure IP Interfaces. The IP Interfaces table appears.
Figure 39: IP Interfaces Table
2. Select the IP interface from the table. The IP Interfaces form appears.
80 Deleting an IP Interface
Page 95

RUGGEDCOM ROS
7
8
1
2
3
4
5
6
9
User Guide
Figure 40: IP Interfaces Form
1. IP Address Type Box 2. IP Address Box 3. Subnet Box 4. Apply Button 5. Delete Button 6. Reload Button
3. Click Delete.
Device Management
Chapter 3
Section 3.8
Managing IP Gateways
ROS allows up to ten IP gateways to be configured. When both the Destination and Subnet parameters are
blank, the gateway is considered to be a default gateway.
NOTE
The default gateway configuration will not be changed when resetting all configuration parameters to
their factory defaults.
The following sections describe how to set up and manage IP gateways:
• Section 3.8.1, “Viewing a List of IP Gateways”
• Section 3.8.2, “Adding an IP Gateway”
• Section 3.8.3, “Deleting an IP Gateway”
Section 3.8.1
Viewing a List of IP Gateways
To view a list of IP gateways configured on the device, navigate to Administration » Configure IP Gateways.
The IP Gateways table appears.
Managing IP Gateways 81
Page 96

Chapter 3
1
Device Management
Figure 41: IP Gateways Table
If IP gateways have not been configured, add IP gateways as needed. For more information, refer to
Section 3.8.2, “Adding an IP Gateway”.
Section 3.8.2
Adding an IP Gateway
To add an IP gateway, do the following:
1. Navigate to Administration » Configure IP Gateways. The IP Gateways table appears.
RUGGEDCOM ROS
User Guide
Figure 42: IP Gateways Table
1. InsertRecord
2. Click InsertRecord. The IP Gateways form appears.
82 Adding an IP Gateway
Page 97

RUGGEDCOM ROS
64
5
2
1
3
User Guide
Figure 43: IP Gateways
1. Destination Box 2. Subnet Box 3. Gateway Box 4. Apply Button 5. Delete Button 6. Reload Button
3. Configure the following parameter(s) as required:
Parameter Description
Destination Synopsis: ###.###.###.### where ### ranges from 0 to 255
Specifies the IP address of destination network or host. For default gateway, both the
destination and subnet are 0.
Device Management
Chapter 3
Subnet Synopsis: ###.###.###.### where ### ranges from 0 to 255
Specifies the destination IP subnet mask. For default gateway, both the destination and
subnet are 0.
Gateway Synopsis: ###.###.###.### where ### ranges from 0 to 255
Specifies the gateway to be used to reach the destination.
4. Click Apply.
Section 3.8.3
Deleting an IP Gateway
To delete an IP gateway configured on the device, do the following:
1. Navigate to Administration » Configure IP Gateways. The IP Gateways table appears.
Figure 44: IP Gateways Table
2. Select the IP gateway from the table. The IP Gateways form appears.
Deleting an IP Gateway 83
Page 98

Chapter 3
64
5
2
1
3
8 9
7
6
5
4
3
2
1
Device Management
Figure 45: IP Gateways Form
1. Destination Box 2. Subnet Box 3. Gateway Box 4. Apply Button 5. Delete Button 6. Reload Button
3. Click Delete.
Section 3.9
RUGGEDCOM ROS
User Guide
Configuring IP Services
To configure the IP services provided by the device, do the following:
1. Navigate to Administration » Configure IP Services. The IP Services form appears.
Figure 46: IP Services Form
1. Inactivity Timeout Box 2. Telnet Sessions Allowed Box 3. Web Server Users Allowed Box 4. TFTP Server Box 5. Modbus
Address Box 6. SSH Sessions Allowed Box 7. RSH Server Box 8. Apply Button 9. Reload Button
2. Configure the following parameter(s) as required:
Parameter Description
Inactivity Timeout Synopsis: 1 to 60 or { Disabled }
84 Configuring IP Services
Page 99

RUGGEDCOM ROS
User Guide
Parameter Description
Device Management
Chapter 3
Default: 5 min
Specifies when the console will timeout and display the login screen if there is no user
activity. A value of zero disables timeouts. For Web Server users maximum timeout
value is limited to 30 minutes.
Telnet Sessions Allowed Synopsis: 0 to 4
Web Server Users Allowed Synopsis: 1 to 4
TFTP Server Synopsis: { Disabled, Get Only, Enabled }
ModBus Address Synopsis: 1 to 255 or { Disabled }
SSH Sessions Allowed (Controlled
Version Only)
RSH Server Synopsis: { Disabled, Enabled }
Default: 0 (controlled version) or 4 (non-controlled version)
Limits the number of Telnet sessions. A value of zero prevents any Telnet access.
Default: 4
Limits the number of simultaneous web server users.
Default: Disabled
As TFTP is a very insecure protocol, this parameter allows user to limit or disable TFTP
Server access..
DISABLED - disables read and write access to TFTP Server
GET ONLY - only allows reading of files via TFTP Server
ENABLED - allows reading and writing of files via TFTP Server
Default: Disabled
Determines the Modbus address to be used for Management through Modbus.
Synopsis: 1 to 4
Default: 4
Limits the number of SSH sessions.
Default: Disabled (controlled version) or Enabled (non-controlled version)
Disables/enables Remote Shell access.
3. Click Apply.
Section 3.10
Managing Remote Monitoring
Remote Monitoring (RMON) is used to collect and view historical statistics related to the performance and
operation of Ethernet ports. It can also record a log entry and/or generate an SNMP trap when the rate of
occurrence of a specified event is exceeded.
The following sections describe how to configure and manage Remote Monitoring:
• Section 3.10.1, “Managing RMON History Controls”
• Section 3.10.2, “Managing RMON Alarms”
• Section 3.10.3, “Managing RMON Events”
Managing Remote Monitoring 85
Page 100

Chapter 3
Device Management
Section 3.10.1
Managing RMON History Controls
The history controls for Remote Monitoring take samples of the RMON-MIB history statistics of an Ethernet port
at regular intervals.
The following sections describe how to configure and manage RMON history controls:
• Section 3.10.1.1, “Viewing a List of RMON History Controls”
• Section 3.10.1.2, “Adding an RMON History Control”
• Section 3.10.1.3, “Deleting an RMON History Control”
Section 3.10.1.1
Viewing a List of RMON History Controls
To view a list of RMON history controls, navigate to Ethernet Stats » Configure RMON History Controls. The
RMON History Controls table appears.
RUGGEDCOM ROS
User Guide
Figure 47: RMON History Controls Table
If history controls have not been configured, add controls as needed. For more information, refer to
Section 3.10.1.2, “Adding an RMON History Control”.
Section 3.10.1.2
Adding an RMON History Control
To add an RMON history control, do the following:
1. Navigate to Ethernet Stats » Configure RMON History Controls. The RMON History Controls table
appears.
86 Managing RMON History Controls
 Loading...
Loading...