SECUTECH SOLUTIONS UNIMATETOKEN Users manual

UNIMATE & UNITOKEN
PRO MANUAL
V
ERSION
3.0

The data and information contained in this document cannot be altered without the express
written permission of SecuTech Solution Inc. No part of this document can be reproduced or
tr ans m itt e d f or a ny purpos e wh at s oev er , eit h er by e lec tron ic or mecha nic a l means.
The general terms of trade of SecuTech Solution Inc. apply. Diverging agreements must be
ma d e in writ in g.
Copyright © SecuTech Solution Inc. All r ights reserved.
WINDOWS is a registere d t ra demark of Microsoft Corporation.
(TM)
The W IN D OW S-logo is a registered trademark
Soft w ar e Lic e nse
The software and the enclosed documentation are copyright-protected. By installing the
softwa re, you agre e to the conditions of the licensing agre ement.
of Microsof t Corporation.
Licensing Agr ee ment
SecuTech Solution Inc. (SecuTech for short) gives the buyer the simple, exclusive and non transferable licensing right to use the software on one individual computer or networked
computer sy stem (LAN). Copying and any othe r form of reproduction of the software in full or
i n part as well as mixing and linking it with others is prohibited. The buyer is authorized to make
one single copy of the software as backup. SecuTech reserves the right to change or impro ve
the s oftwar e without notice or to repl ac e it with a n ew de ve l o pm e nt. S ec u T ec h is n ot ob li ge d t o
inform the buyer of changes, improvements or new developments or to make these available to
hi m . A legall y binding pr omi se of cer tain quali ti es is not given . SecuTe ch is not respon sible fo r
damage unles s it is t he res ult of deliberate ac tion or negligence on the part of SecuTech or its
aids and assistants. SecuTech accepts no responsibility of any kind for indirect, accompanying or
subsequent damage.
I
Contact Information
HTTP: www.eSecuTech.com
E-Mail: Sales@eSecuTech.com
Please Email any comments, suggestions or questions regarding this document or our products
to us at: Sales@eSecuTech.com
Version Date
II


Table of Contents
PART 1 AN OVERVIEW OF UNIMATE & UNITOKEN 2
CHAPTER 1: UNIMATE & UNITOKEN DEVICE 2
1.1 Features 2
1.2 Specifications 3
CHAPTER 2: UNIMATE & UNITOKEN SOFTWARE 3
2.1 UniMate & UniToken driver installation 3
2.2 The PKCS#11 and MS-CAPI Modules of UniToken 4
2.3 T oken API 4
2.4 S up por t e d Pl at f orms 4
CHAPTER 3: SECURITY 5
3.1 Key 5
3.2 Data transmission 7
3.3 Fac t or y Def a ult Sett i n gs 7
PART 2 UNIMATE & UNITOKEN SDK 7
CHAPTER 4: SDK OVERVIEW 7
4.1 Driver installation 8
4.2 Re di s tributi on Pa c k a g e 8
4.3 Console 12
4.4 Monitor 42
PART 3 APPLYING DIGITAL CERTIFICATES 55
CHAPTER 1: APPLYING DIGITAL CERTIFICATES 55
1.1 Applyin g VeriSi gn Cert ificates 55
1.2 Applying Micros oft Certificates 56
1.3 Using Digital Certificates 58
PART 4 DEVELOPER S GUIDE 59
1.1 Device Initializatio n 59
CHAPTER 1: PKCS11 APPLICATION 59
1.2 Introduction 59
1.3 S up por t e d PK CS#11 Algorithms and APIs 61
1.4 UniMate & UniToken PKCS#11 Function Libra ry 62
1.5 Samples 65
IV

CHAPTER 2: MS-CAPI APPLICATIONS 67
2.1 Introduction 67
2.2 S up por t e d A lg or it h ms a nd APIs 68
2.3 Samples 69
2.4 UniMate & UniToken API 72
V
Part 1 An Overview of UniMate &
UniToken
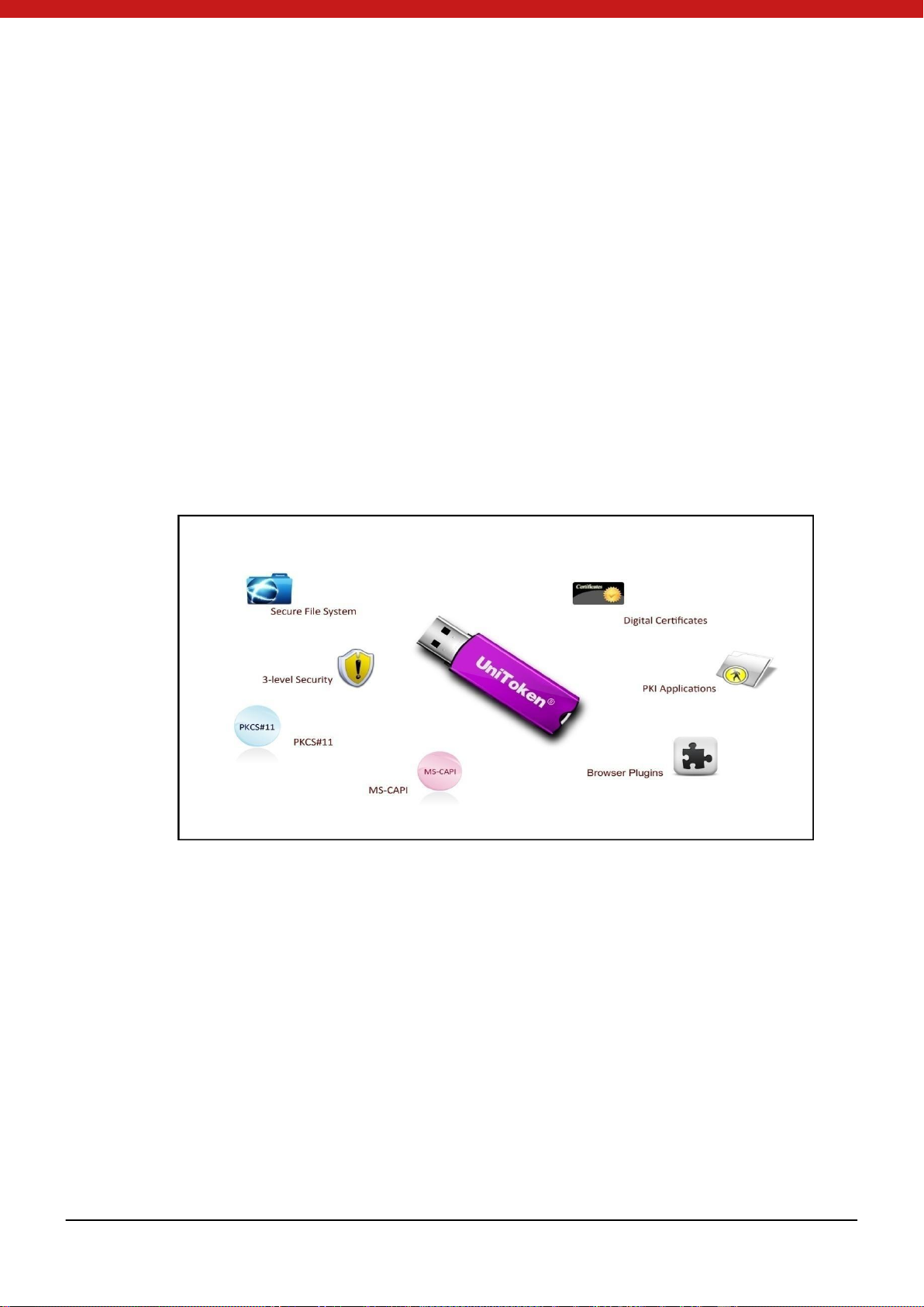
UniMate & UniToken, hereinafter referred to as Token, i s an information security
product based on CCID technology. It is a secure container for digital credentials.
Ad va nc e d proc es s or a n d secure m e mory ar e b uilt i n the Token device to guarantee the
security for exchanging, storing and handling electronic information.
Token has achieved an effect ive rights management and can provide a highly-secured
file system. A built-in compu ting eng ine a ccompli shes f ast and ef ficie nt info rm ation
processing.
Token supports PKI applic ations and provides Token API for s e conda ry development.
Abundant samples bring ease to integrations.
Chapter 1: UniMate & UniToken Device
1.1 Features
Key f e at ure s of UniMate & UniToken device:
Globally unique hardware ID
Custo mize d s oftware ID
Smartcard-based
2 of 72

On-b oar d e nc r y pt io n
Two levels of PIN management mechanism
A secure file system
Lar ge me m or y
Stylish and cute case
Lead free
1.2 Specifications
u p t o 64K
Dimensions
Weight 9g
Min. Ope ra t ing Voltage 5V
Current Consum pt ion <= 50 mA
Operation Temperature
Storage Temperature
Humidity Rate 0-70% without c ondens at ion
Casing Tamper-evident Metal
Memory Data Retention At least 10 years
Memory Cell Rewriters At least 100,000 times
57×16×8 mm
0℃ to 70℃
-10℃ t o 85℃
Chapter 2: UniMate & UniToken
2.1 UniM ate & UniToken driver installation
Software
3 of 72
2.2 The PKCS#11 and MS-CAPI Modules of
UniToken
PKCS#11 module of Token is implemented according to PKCS#11 standards V.2.20,
whi ch is a D LL file for C langu age running on Windows ope rating s ys tem . MS -CAPI
Module of UniToken is implemented in line wit h MS-CAPI s tandard.
These two modules can be used in cooperation with each other, i.e. the certificate
applied with PKC S#11 can be used by MS-C A PI m o du l e of Token, and vice ve rs a.
2.3 Token API
Token prov ide s a set of Token A PI, wh ic h al l ow s us er s t o m a na ge o ne or se v e ra l Token
hardware keys, i.e. operation of Token a ttribu tes , pe rmis sion, buil t -in a lgo ri thms and
secure file system. Please install Token API package or Token full pa ck ag e to en abl e
these features.
2.4 Supported Platforms
T ab le 1.3: S up p orted Pl at f orms
Components
OS
Windows 2000
Windows 2003
Windows XP
Wind ows Vi sta
Windows 7
UniMate Flex UniMate STD Un i T ok e n PRO
√ √ √
√ √ √
√ √ √
√ √ √
√ √ √
Windows 2008
Windows 2012
Windows 8
√ √ √
√ √ √
√ √ √
4 of 72
Ensure the security during the card
initialization, and provide encryption and
Directory level authentication. control
uses this key to authenticate the
iOS
Android
√
√
Chapter 3: Security
Se cu rity i s the most i mportant part in Token sys tem, whi ch in volv es in iden ti fica tion
and verification method, including not only the file access permission control
mechanism inside the token, but also the information confidential control inside the
token. The security attribute means the cu rrent state of the device when the card is
reset or after the token finis hed some commands .
3.1 Key
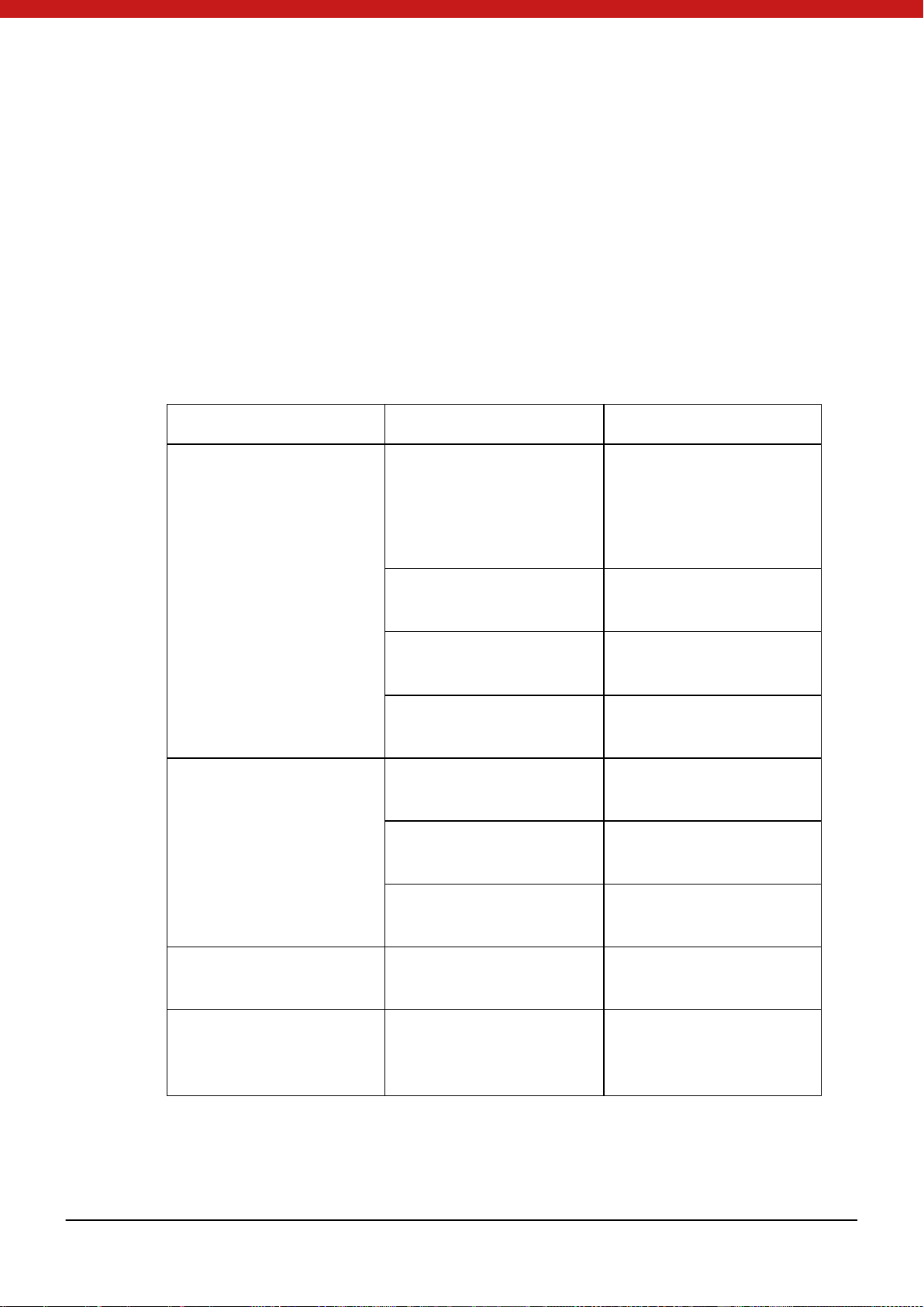
The following table describes different key types and use
Key Type
Trans m issi on Key
PIN
PIN unl oc k k ey
PIN reload key
External authentication key
Internal authentication key
Master key
Block encrypti on/ dec ryption ke y
Transmission key: a 16-byte key that every device must have only one transmission
key
PIN: a personal identification number based on directory. The PIN is firstly hashed and
th en s t or e d in t he d ev ic e
Use
decryption.
different users’ read and write permission
Used to unlock PIN
used to reload PIN
Token
ex ternal en t i ty
External entity uses this key to authenticate
the token device.
Used to secure transmission
Provide encryption/decryption for e xt e rn al
enti ty.
PIN unl ock key: a 16-byte key is used in unlock function. Its function is that encrypts
PIN and calculates MAC of the ci pher text as a key.
5 of 72
Access permission
External authentication
External authentication
Provide encryption
operation for external
Depending on
implemented encryption
PIN reload key: not used in this version and will add this function in the following
version.
External authentication key: a 16-byte key th at used for external authentication. The
first 8-b yt e is the ke y 1 an d key 3.
Internal authen tication key: a 16-byte key that used for internal authentication. The
first 8-b yt e is the ke y 1 an d key 3.
The block encryption/decryption key: used to specified algorithm, length is from 8byte to 16-byte. Currently the supported algorithms are DES (ECB, CBC), TDES (ECB,
CBC), AE S (EBC, CBC).
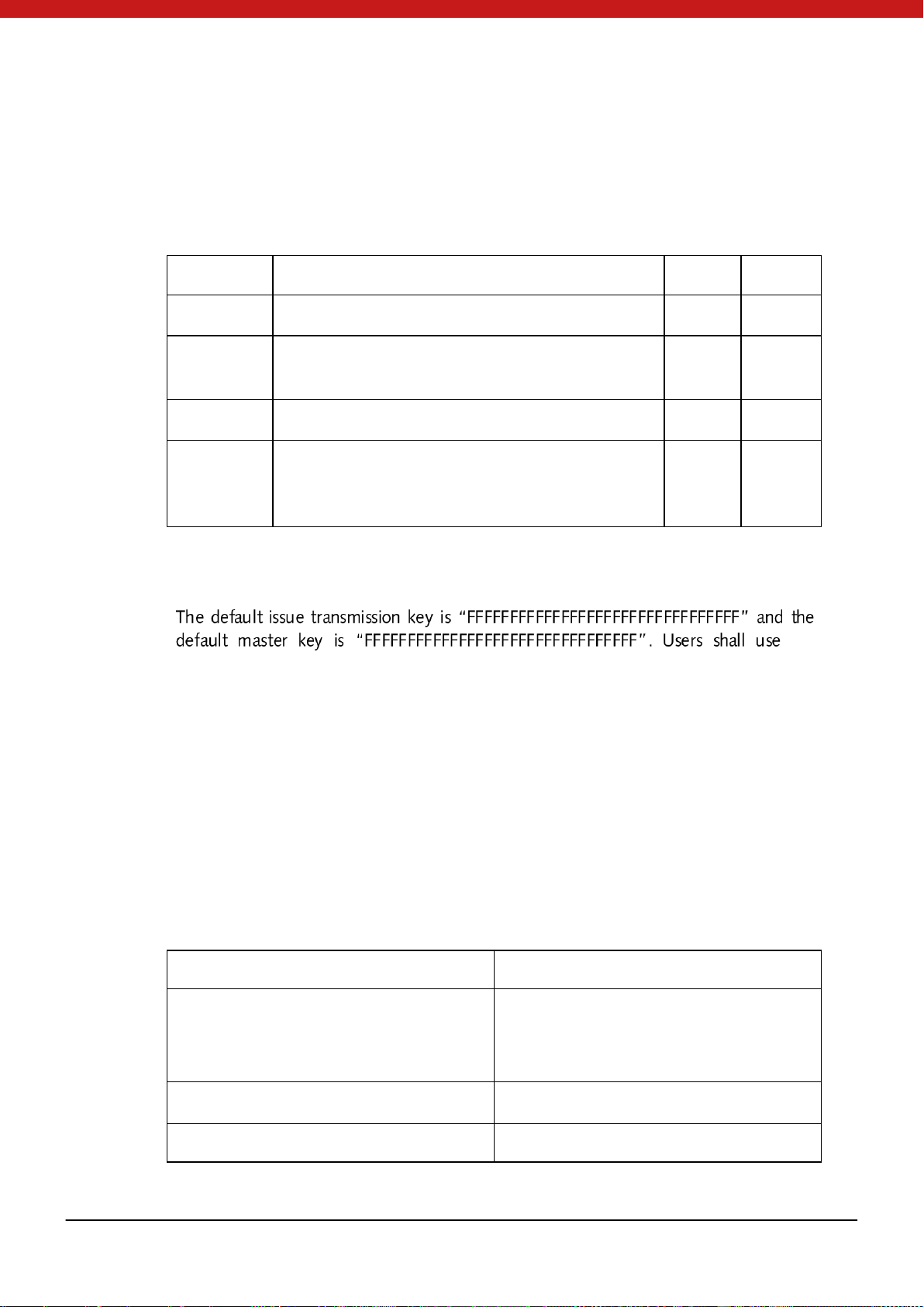
Authentication type Key type Use method and algorithm
Tran s mi ss io n k ey Comparison in plaintext
authentication
E xte rn al a uthe nticatio n ( for
example, format device in
user s tate)
Cipher te xt tra ns mission Tr an s mis s ion k ey TDES encryption (use DES
PIN reload key TDES en cryption (use DES
PIN
(TDES)
Ext er n au th e nt ic at i on key
(TDES)
Internal authentication key Internal authentication
(TDES)
in MAC)
Mas t er ke y TDES en cryption (use DES
in MAC)
PIN unlock key TDES en cryption (use DES
in MAC)
in MAC)
Encryption key
entity
algorithms.
6 of 72
Plaintext and MAC of the plaintext are transferred
encrypted data, and then transferred the cipher
3.2 Data transmission
Dat a tr an s mi ss io n mea ns d at a tra ns m itt e d betw e e n h ost machin e an d dev ic e, inc lu di n g
4 transmission modes.
Mode Definition Security Integrity
Plaintext Data is transferred directly without any process
Plaintext
with MAC
Cipher Plaintext is encrypt ed befor e transferre d
Cipher with
MAC
together
Data is encrypted and calculate the M AC o f th e
text and MAC
3.3 Factory Default Settings
ma ster key to create and delete file.
Part 2 UniMate & UniToken SDK
× ×
× √
√ ×
√ √
the
Table1.6 Token S DK Contents
Components Description
Include
Libraries
Documents
Chapter 4: SDK Overview
Declaration of t he standar dized
identifiers a nd inter f ac e of PKCS #11,
CSP and Token API.
Token libraries
Manual for Token PRO and API
7 of 72

reference
Integration Guides
Inst r uction about integr a t ion Token
with other software
Redists
Redistribut ion packages f or developer s
and end user s
Samples
Samples for CSP, PKCS and Token
API
Windows CCID Driver
Token Drivers
4.1 Driver installation
driver to make Token work . For some ol d versions , su ch like Windows V IST A and XP,
dr iv er m ust be i nst a l led t o mak e th e s yst e m rec o g nis e t h e dev ic e.
After inserting Token to a computer, from Control Panel → Hard war e and Sound →
Device Manager, open the Devic e manager.
From the hardware list find the unknown device, update the driver, the driver is in the
SDK\wi ndows CCI D Driver.
4.2 Redistribution Package
Token provides two different redistribution packages for developers and end users
respect ivel y. Both the package provide Token PKI installation package . If you want to
use t he PKI applicat ion, you must i nstall it .
Installation
Token PKI package c an be f ound in the redist folder of Token PR O SDK .
For devel opers package
Doubl e cli ck the icon to run the in stall shield wi za rd, and fol lo w the illu stra tion
below:
8 of 72
In this secti on, us er name and company n ame are re quired. And cl
9 of 72
10 of 72
Uninstallation
To uninstall the software, there are two ways: start menu and control panel.
Start Men u:
-All Programs-SecuTech-Token-Uninstall Token
11 of 72
4.3 Console
Token Console is used to manage devices, set user permi ssion as well as control file
system and certificates.
4.3.1 Check Token information
1. Start Console.exe and insert your device
12 of 72
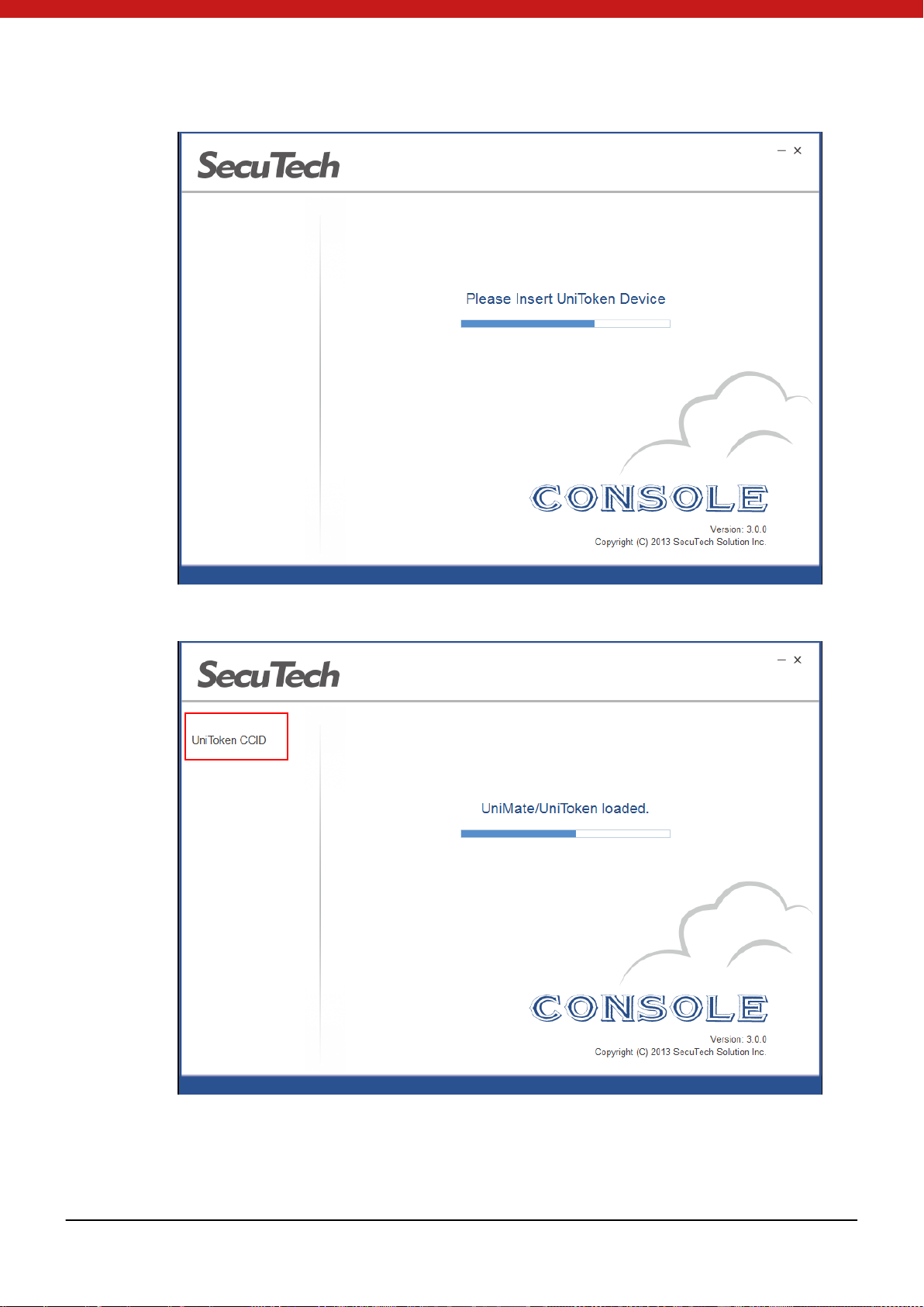
The devide name will appear on the left sid e of t he pa ge.
2. Click on the name of the device to check the device information.
13 of 72
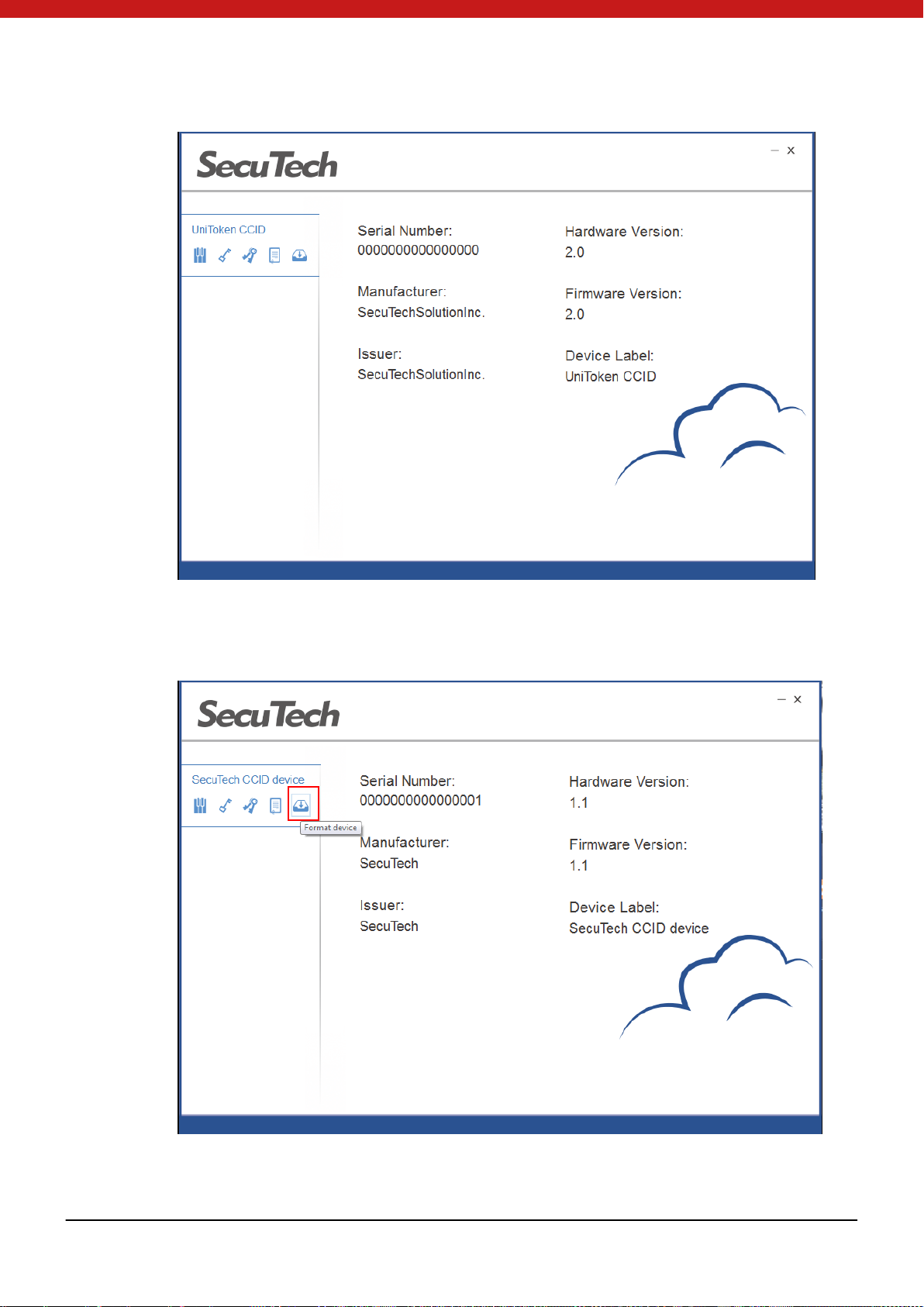
4.3.2 I nitialize Token
1. On the main page, select the To ken from the l is t.
14 of 72
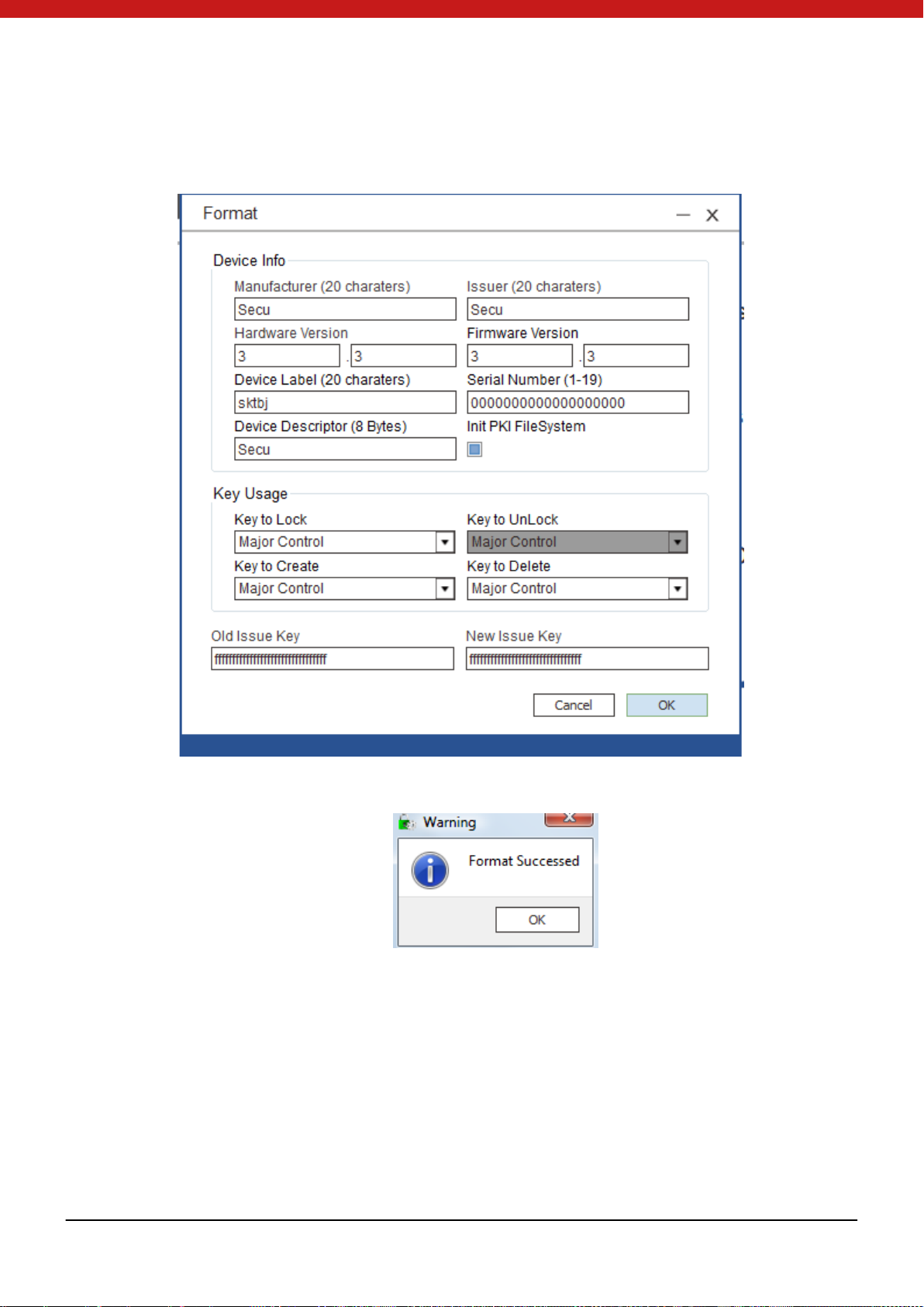
2. On the left side, click on the initialization icon. In the pop up page, fill the
information, configure the key usage and input old issue key and set new issue key.
3. Click on OK to start initialization.
Aft e r the to ken is initi ali zed su cces s fully , a me s sage pag e wi ll pop up . Cli ck on OK to
ret urn t he mai n p age.
15 of 72
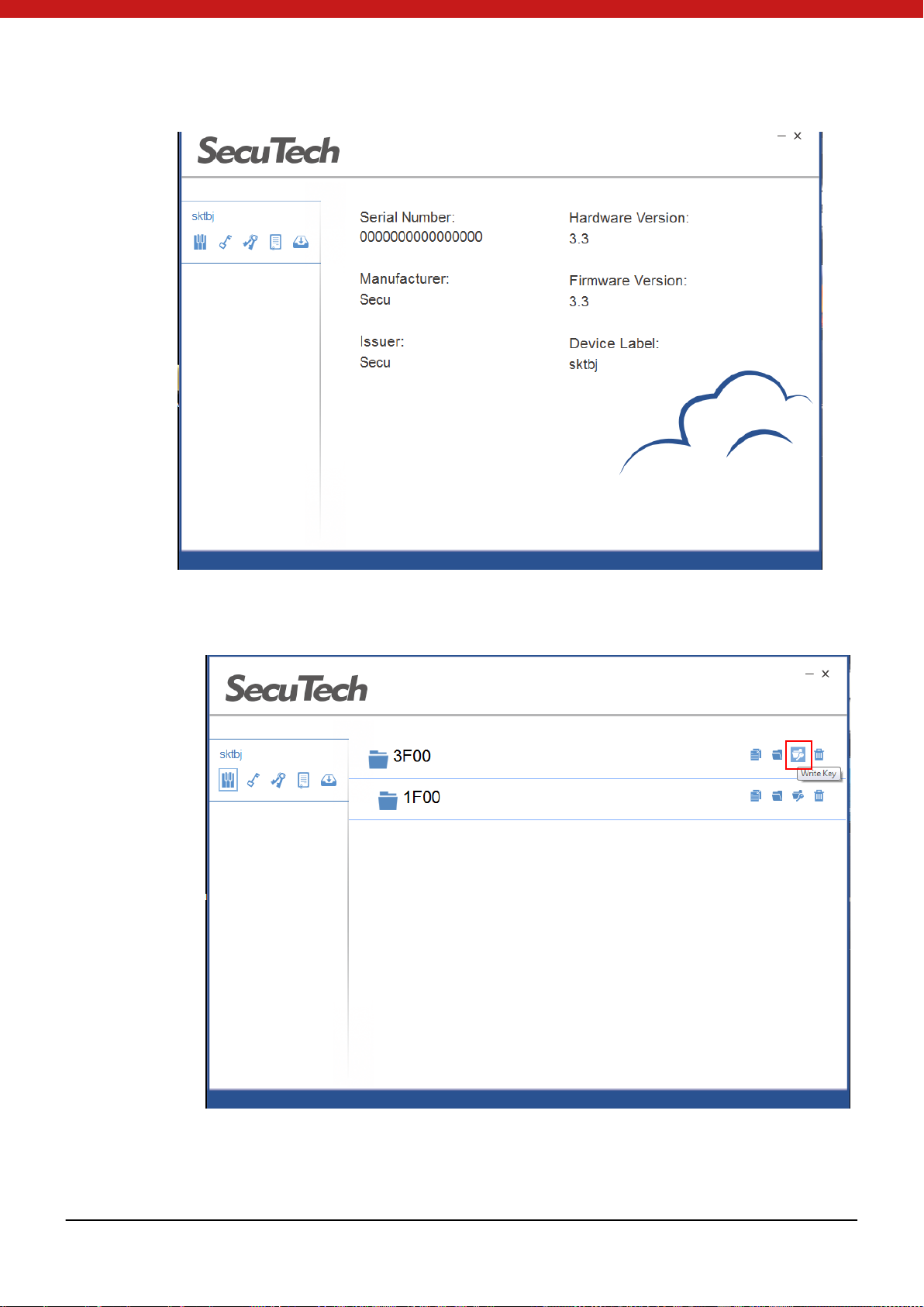
4.3.3 Change Key
1. Write a key for t h e fo ld er b y c lic ki n g on the writ he key ic o n.
2. In t he pop up pag e, select the key u sage, in put the key value , the maxi mum
attempts and input the master key of the fo lder.
16 of 72
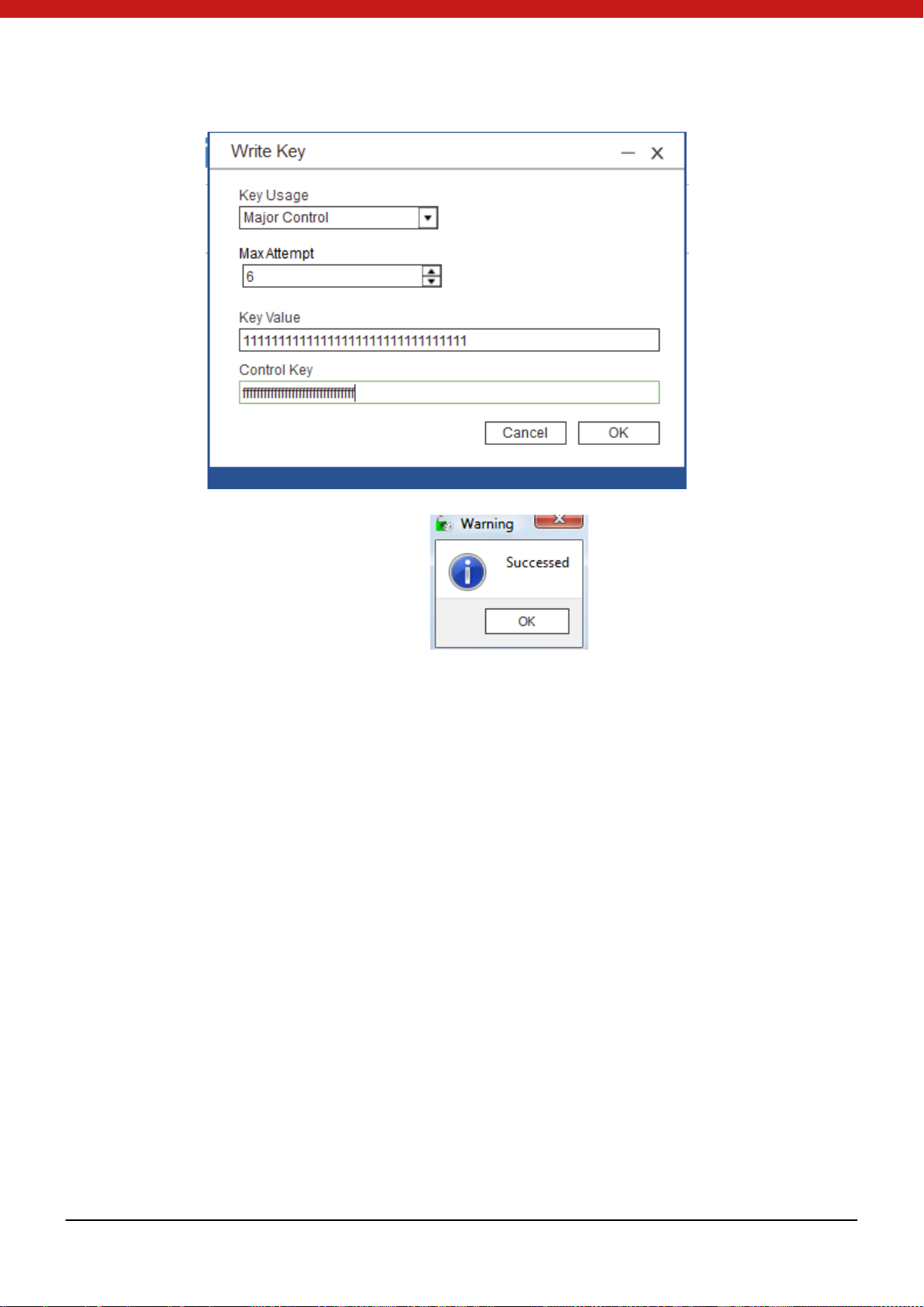
3. Cl ic k on OK
4.3.4 Create folder (max 3 level)
1. Click on the cr eat e fol der icon
17 of 72
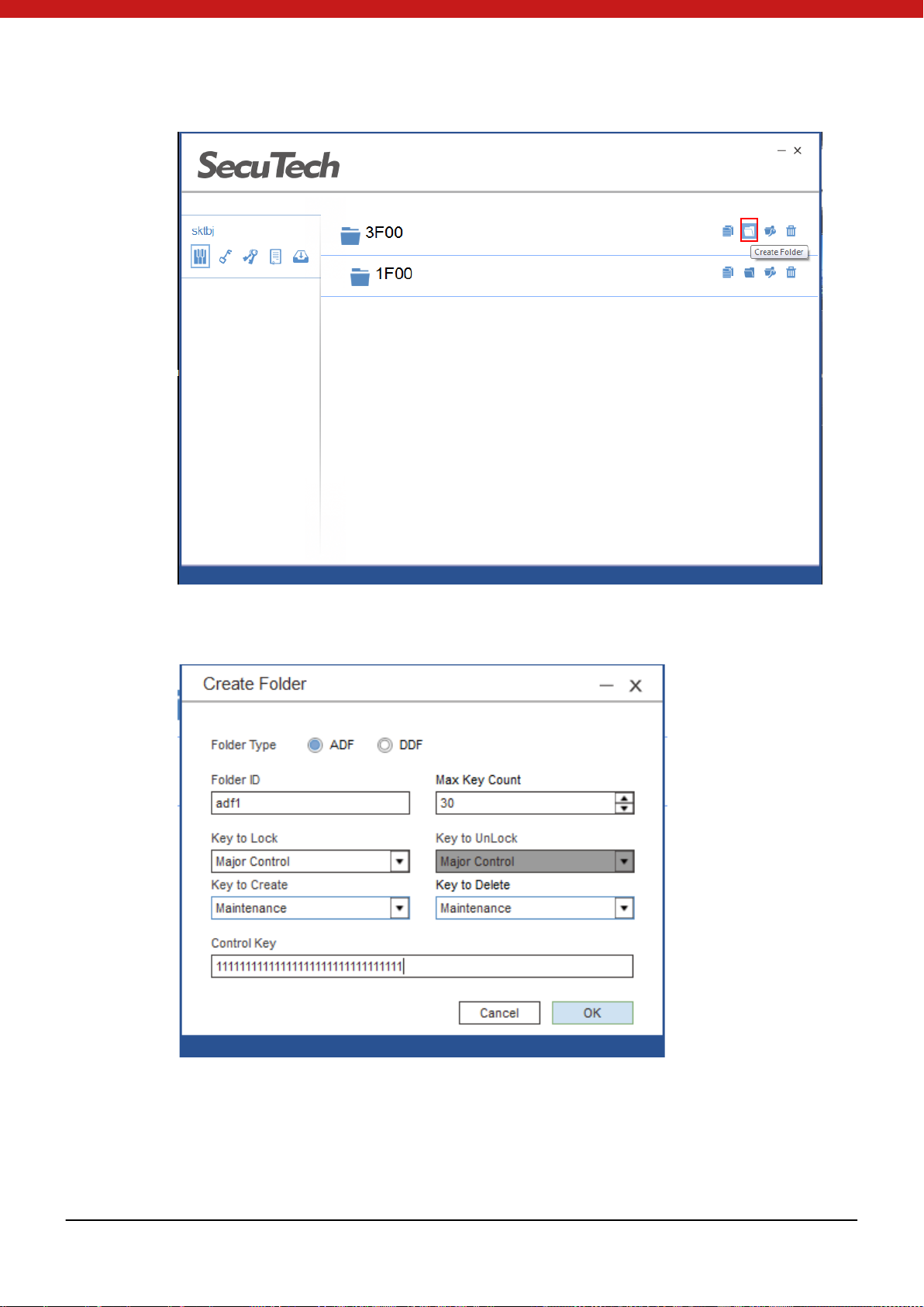
2. In the pop up p age, se lect folde r type, inpu t n ame, cre ate del ete key type , and
input the key of t he u p per folder.
3. Click on OK, and the new f older will appear in the selected folder.
18 of 72
4.3.5 Create file
Click on the create file icon under the s elect ed folder.
19 of 72
 Loading...
Loading...