Seagate 10K.3 - Savvio 300 GB Hard Drive,15K.2 - Savvio 146.8 GB Hard Drive,10K.3 300 Brochure
Technology Paper
Self-Encrypting Drives for
Servers, NAS and SAN Arrays
Overview
This paper discusses the challenge of securing data on hard
drives that will inevitably leave the owner’s control. It introduces
Self-Encrypting Drives (SED), which may be used in two ways: to
provide instant secure erase (cryptographic erase or making the
data no longer readable), and to enable auto-locking to secure
active data if a drive is misplaced or stolen from a system while in
use. Two appendices then follow: The first compares SEDs to other
encryption technologies used to secure drive data. The second
provides detailed analysis of instant secure erase and auto-lock
SED technology, explaining how SEDs are used in servers, NAS and
SAN arrays, virtualized environments, RAIDs, JBODs and discrete
drives.
Introduction
When hard drives are retired and moved outside the physically
protected data center into the hands of others, the data on those
drives is put at significant risk. IT departments routinely retire drives
for a variety of reasons, including:
•
Returning drives for warranty, repair or expired lease agreements
•
Removal and disposal of drives
•
Repurposing drives for other storage duties
Nearly all drives eventually leave the data center and their owners’
control; Seagate estimates that 50,000 drives are retired from data
centers daily. Corporate data resides on such drives, and when
most leave the data center, the data they contain is still readable.
Even data that has been striped across many drives in a RAID array
is vulnerable to data theft, because just a typical single stripe in
today’s high-capacity arrays is large enough to expose hundreds of
names and social security numbers.

Self-Encrypting Drives for
Servers, NAS and SAN Arrays
Drive Control Headaches and Disposal Costs
In an effort to avoid data breaches and the
ensuing customer notifications required by data
privacy laws, corporations have tried a myriad of
ways to erase the data on retired drives before
they leave the premises and potentially fall into
the wrong hands. Current retirement practices
designed to make data unreadable rely on
significant human involvement in the process,
and are thus subject to both technical and human
failure.
The drawbacks of today’s drive retirement
practices are both numerous and far-reaching:
•
Overwriting drive data is expensive, tying
up valuable system resources for days. No
notification of completion is generated by the
drive, and overwriting won’t cover reallocated
sectors, leaving that data exposed.
•
Degaussing or physically shredding a drive
are both costly. It’s difficult to ensure the
degauss strength is optimized for the drive
type, potentially leaving readable data on
the drive. Physically shredding the drive
is environmentally hazardous, and neither
practice allows the drive to be returned for
warranty or expired lease.
•
Some corporations have concluded the only
way to securely retire drives is to keep them
in their control, storing them indefinitely in
warehouses. But this is not truly secure, as
a large volume of drives coupled with human
involvement inevitably leads to some drives
being lost or stolen.
•
Other companies choose to hire professional
disposal services, an expensive option which
entails the cost of reconciling the services as
well as internal reports and auditing. More
troubling, transporting a drive to the service
puts the drive’s data at risk. Just one lost drive
could cost a company millions of dollars in
remedies for the breached data.
With these shortcomings in mind, it’s no surprise
that an IBM study found that 90 percent of the
drives returned to IBM were still readable. The key
lesson here? It’s not just the drive that’s exiting
the data center, it’s also the data stored within.
Encryption
Every day, thousands of terabytes of data leave
data centers as old systems are retired. But what
if all those hard drives had been automatically
and transparently encrypting that data, enabling
it to be instantly and securely erased? A majority
of U.S. states now have data privacy laws that
exempt encrypted data from mandatory reports
of data breaches. And make no mistake, the
cost of data exposure is high—US$6.6 million on
average1.
Challenges with performance, scalability and
complexity have led IT departments to push
back against security policies that require the
use of encryption. In addition, encryption has
been viewed as risky by those unfamiliar with key
management, a process for ensuring a company
can always decrypt its own data. Self-Encrypting
Drives comprehensively resolve these issues,
making encryption for drive retirement both easy
and affordable.
We’ll discuss two security scenarios:
•
SEDs that provide instant secure erase without
the need to manage keys
•
Auto-locking SEDs that help secure active data
against theft with key lifecycle management
2 1 2008 Annual Study: Co st of a Data Breach, Ponemon Institute, Februar y 2009

Self-Encrypting Drives for
Servers, NAS and SAN Arrays
Instant Secure Erase Without Managing Keys
The Self-Encrypting Drive provides instant data
destruction via cryptographic erase. When
the SED is in normal use, its owner need not
maintain authentication keys (otherwise known
as credentials or passwords) in order to access
the drive’s data. The SED will encrypt data being
written to the drive and decrypt data being read
from it, all without requiring an authentication key
from the owner.
When it’s time to retire or repurpose the drive,
the owner sends a command to the drive to
perform a cryptographic erase. Cryptographic
erase simply replaces the encryption key inside
the encrypted drive, making it impossible to ever
decrypt the data encrypted with the deleted key.
(A more detailed explanation of how secure erase
works appears in Appendix A.)
Self-Encrypting Drives reduce IT operating
expenses by freeing IT from both drive control
headaches and disposal costs. The SED’s
government-grade data security helps ensure
Safe Harbor for data privacy compliance without
hindering IT efficiency. Furthermore, SEDs
simplify decommissioning and preserve hardware
value for returns and repurposing by:
•
Eliminating the need to overwrite or destroy the
drive
•
Securing warranty and expired lease returns
•
Enabling drives to be repurposed securely
Auto-Locking Self-Encrypting Drives With
Key Lifecycle Management
Beyond using a Self-Encrypting Drive for instant
secure erase at retirement, the drive owner
may also choose to employ that same SED in
the auto-lock mode to help secure active data
against theft. Insider theft or misplacement is a
growing concern for businesses of all sizes; in
addition, managers of branch offices and small
businesses without strong physical security face
greater vulnerability to external theft.
Utilizing the SED in auto-lock mode simply
requires securing the drive during its normal use
with an authentication key. When secured in this
manner, the drive’s data encryption key is locked
whenever the drive is powered down. In other
words, the moment the SED is switched off or
unplugged, it automatically locks down the drive’s
data.
When the SED is then powered back on, the
SED requires authentication before being able to
unlock its encryption key and read any data on
the drive, thus protecting against misplacement
and insider or external theft.
The lifecycle of authentication keys can be
managed by the IBM Tivoli Key Lifecycle
Manager (formerly Encryption Key Manager),
which is a Java-based software program
that centrally generates, protects, stores and
backs up authentication keys. It is a unified
key management service that will support the
key management requirements for all forms of
storage (as well as other security applications).
IBM, LSI and Seagate will support the Key
Management Interoperability Protocol submitted
to OASIS for advancement through their open
standards process. With its platform neutrality,
IBM Tivoli Key Lifecycle Manager offers a simple
and effective method for managing the growing
number of encryption keys across the enterprise.
The auto-lock mode of Self-Encrypting Drives and
IBM Tivoli Key Lifecycle Manager is discussed in
detail in Appendix A.
The owner of a Self-Encrypting Drive is able to
use the SED first in secure erase-only mode, and
then later change that SED to auto-lock mode.
Later, after performing an instant secure erase
and repurposing the drive, the drive may then go
back to being used in secure erase-only mode.
So, initially, the drive owner may choose to leave
the SED in secure erase only mode during normal
operation, intending to just perform an instant
secure erase when needed. Later, perhaps
due to growing concerns over theft, the owner
may elect to use the SED in auto-lock mode for
the remainder of the owner’s use of the drive,
by simply creating an authentication key that
wraps the existing encryption key. Subsequently,
once the SED has been securely erased and
repurposed, its new owner may decide to not put
the drive in auto-lock mode and use the drive in
secure erase-only mode to securely erase the
drive at the end of its useful life.
3

Self-Encrypting Drives for
Servers, NAS and SAN Arrays
Using Self-Encrypting Drives merely for instant
secure erase provides an extremely efficient and
effective means to help securely retire a drive.
But using SEDs in auto-lock mode provides even
more advantages. In short, from the moment the
drive or system is removed from the data center
(with or without authorization), the drive is locked.
No advance thought or action is required from
the data center administrator to protect this data.
This helps prevent a breach should the drive be
mishandled and helps secure the data against the
threat of insider or outside theft.
Comparing Technologies for Securing Data
on Hard Drives
No single encryption technology can effectively
and efficiently secure all data against all threats.
Different technologies are used to protect against
different threats. For example, Self-Encrypting
Drives help secure data against threats when the
drive eventually leaves the owner’s control, but
it cannot protect data from certain threats that
take place within the data center. For example, if
an attacker gains access to a server that can in
turn access an unlocked drive, the attacker can
read the clear text coming from the drive. Thus
it’s important to remember that SED encryption
technology does not replace the data center’s
access controls, rather it complements them.
Securing data at rest also should be
complementary, rather than a replacement, to
securing data in motion. The vast majority of data
in motion moving over the wire downstream of
the file system, whether moving over Ethernet
on the NAS or at the block level on a SAN, is
physically under the IT storage administrator’s
control, and therefore is not considered a
security risk. For the data in motion that is not
physically under the administrator’s control, the
most widely accepted and established practice
for encrypting this data is to use IPSec or FC
over IP, which use ephemeral session encryption
keys to encrypt small amounts of data. It may
seem that, instead of using this session security
technique, encrypting in the fabric to secure the
data on the hard drive is a better solution: the
data is encrypted not only on the hard drive,
but also as it travels through the fabric. But this
4
approach has an a fundamental flaw: Rather than
increasing security, it actually decreases security
and increases complexity by exposing encryption
keys that are long-lived keys, while exposing large
amounts of cipher text that were all encrypted
with only a single encryption key. If encryption is
needed for data in motion, it should be provided
by IPSec or FC over IP. Encrypting data on the
drive is best performed by the drive itself, for all of
the reasons provided below.
Application, database, OS and file system
encryption (see Figure 1) are all techniques
that cover threats to drive data (whether from
database, file or system administrators or from
hackers) that arise within the data center. But due
to the significant performance degradation and
non-scalable changes required to the application,
database, OS or file system that such encryption
entails, it’s impractical to encrypt more than just a
limited portion of data. Administrators cope with
this restriction by reserving encryption for only the
most sensitive data.
This forces administrators to rely on data
classification in order to identify and locate
sensitive data; unfortunately, it’s widely
acknowledged that this process fails to identify
all instances of sensitive data. Data classification
is difficult, labor-intensive and challenging to
maintain, especially when sensitive information
can be copied from a protected source to an
unprotected destination. Such problems result
in too much unencrypted sensitive data being
written to disk, data which will likely persist on
the hard drive long after the drive’s useful life has
ended.
As such, it falls to encryption technologies
downstream of the file system to provide full disk
encryption and close the gap created when data
classification fails to capture sensitive data. These
technologies relieve data custodians from the
responsibility of classifying the data’s sensitivity
upon leaving control of the data center, a task
fraught with management headaches and extra
cost. Encrypting in the fabric, RAID disk controller
(in a server or storage subsystem controller) or
hard drive are all possibilities. But where should
this encryption take place?
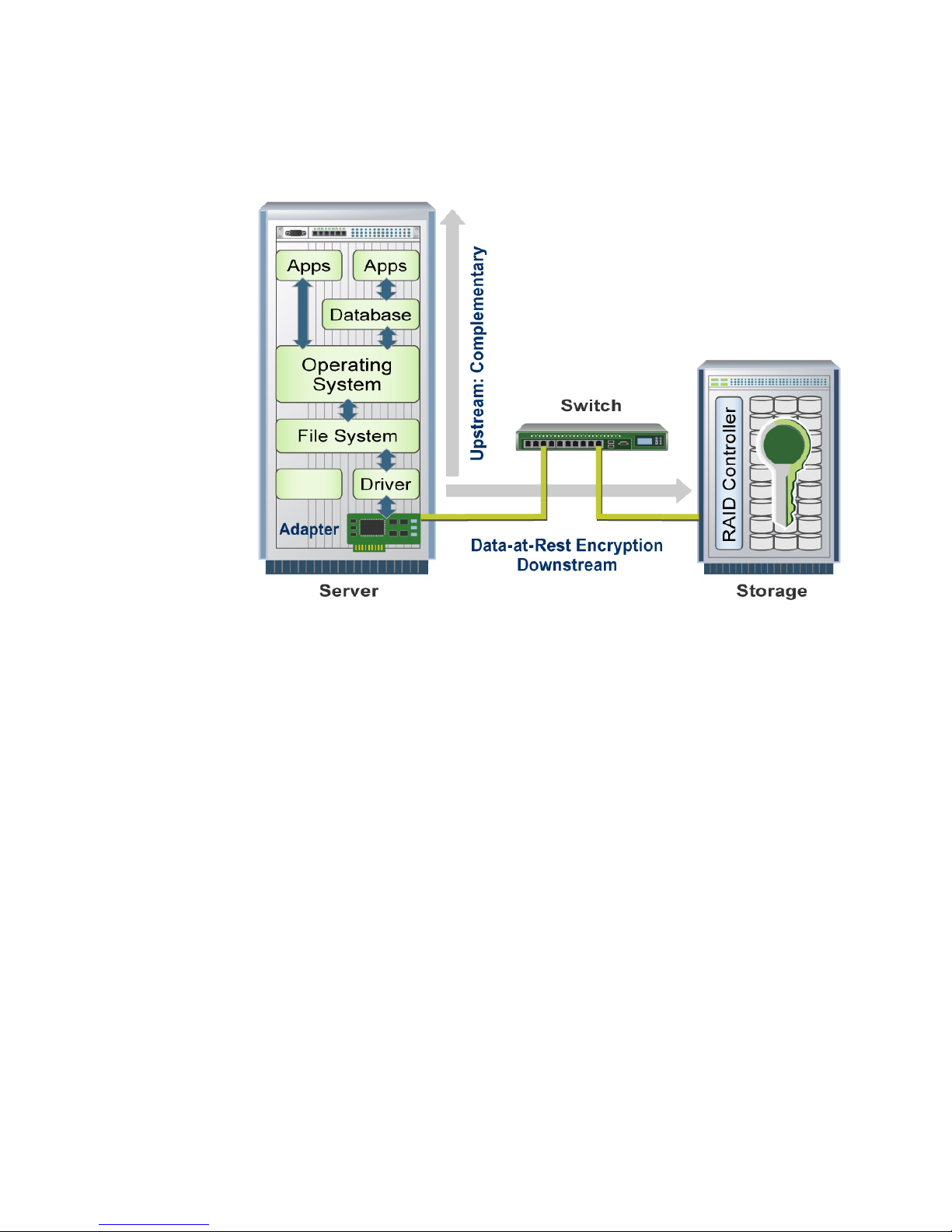
Self-Encrypting Drives for
Servers, NAS and SAN Arrays
Figure 1.
Several years ago, before Seagate began working
on drive encryption, the United States National
Security Agency (NSA) analyzed the problem of
data security and determined that the best place
to perform encryption is in the hard drive. It’s a
well-known security maxim that guards should
be placed as close to the jewels as possible.
Similarly, encrypting within the hard drive is
optimal because that’s precisely where the
data resides. SEDs boast superior technology
to provide full disk encryption, lowering total
cost of ownership for servers’ direct-attached
storage, SANs and NAS storage while delivering
compelling advantages:
•
Simplified Key Management: SED eliminates
the need to track or manage a data encryption
key; when used for secure erase only, there’s
no need to track or manage an authentication
key either.
•
Reduced Costs via Standardized
Technology: Employing industry-standardized
technology cuts costs and ensures common
technology is used across SAN, NAS, server,
desktop, notebook and portable storage
platforms.
•
Optimum Storage Efficiency: Unlike some
encryption technologies, SED enables data
compression and de-duplication to maximize
value of disk storage capacity.
•
Increased Data Integrity: SED enables
Protection Information, the future of data
integrity, and does not impact hard drive’s
reliability or warranty.
•
Maximum Performance and Scalability: SED
performs at full drive speed while also scaling
linearly and automatically.
•
No Data Classification : Expensive, time-
consuming data classification is not needed to
maintain peak performance.
•
Reduced Re-Encr yption : SED ensures there
is less need to re-key and re-encrypt, because
the data encryption key is never exposed.
•
Superior Security: NSA qualified the first
SED model. SED doesn’t weaken security by
needlessly encrypting the storage fabric, which
exposes long-lived cipher text and keys. SED
leaves over-the-wire encryption to technologies
designed for securing data in motion
5
 Loading...
Loading...