safenet 600 User Manual

© 2005
-
2010 SafeNet, Inc. All rights reserved.
www.safenet
-
inc.com
002-010003
-
001
Revision
B
This document may be freely reproduced and distributed whole and intact including this copyright notice.
SafeNet
Encryptor
Model 600
FIPS 140
-2–
Level 3 Validation
Non
-
Proprietary Security Policy
Hardware
Part Numbers
155/622 MB (OC
-
3/12)
2 km (904
-
10001
-
00x)
904-30013
-
00x(RoHS)
155/622 MB (OC
-
3/12)
15 km (904
-
10002
-
00x)
904-10014
-
00x(Ro
HS)
155/622 MB (OC
-
3/12)
40 km (904
-
10003
-
00x)
904-10014
-
00x(RoHS)
1.0 GB
10km (904
-
10112
-
00x)
904-10113
-
00x(RoHS)
2.4 GB (OC
-
48)
2 km (904
-
20001
-
00x)
904-25005
-
00x(RoHS)
2.4 GB (OC
-
48)
15 km (904
-
20002
-
00x)
904-25005
-
00x(RoHS)
2.4 GB (OC
-
48)
40 km (904
-
20003
-
00x)
904-25005
-
00x(RoHS)
SafeNet
SONET Encryptor (SSE)
904-511i0-00xN/A
SafeNet
Ethernet Encryptor (SEE)
943-511i0-00xN/A
Note: See
Table
2.2-1
for
model numbering conventions.
with
3.5
Firmware
Security Policy Revision
B
January
2010

002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
iofi
i
TABLE OF CONTENTS
Section
Title
Page
1
Introduction
................................
................................
................................
................................
...........
1
1.1
Overview
................................
................................
................................
................................
..........
1
1.2
References
................................
................................
................................
................................
.......11.3
Terminology
................................
................................
................................
................................
......11.4
FIPS Requirements
................................
................................
................................
..........................
2
2
SafeNet Encryptor
................................
................................
................................
................................
3
2.1
Functional Overview
................................
................................
................................
.........................
3
2.2
Module Description
................................
................................
................................
...........................
4
2.2.1
Enclosure Indicators, Connectors and Controls
................................
................................
........
5
2.2.1.1
Front Panel Physical Interfaces
................................
................................
................................
....62.2.1.2
Rear Panel Physical Interfaces
................................
................................
................................
....
6
2.3
Security Functions
................................
................................
................................
............................
8
2.4
FIPS Approved Mode of Operation
................................
................................
................................
..92.4.1
FIPS Approved Mode
................................
................................
................................
..............
10
2.4.2
Non-FIPS Approved Mode
................................
................................
................................
.......102.5
Identi
fication and Authentication
................................
................................
................................
....102.5.1
Cryptographic Keys and CSPs
................................
................................
................................
13
2.5.2
Roles and Services
................................
................................
................................
..................
15
2.5.3
Access Control
................................
................................
................................
.........................
16
2.6
Physical Sec
urity
................................
................................
................................
............................
17
2.7
Self Tests
................................
................................
................................
................................
.......
19
3
Glossary of Acronyms, Terms and Abbreviations
................................
................................
..........
21
LIST OF TABLES
Table
Title
Page
Table
1.4-1-Cryptographic Module
Security Requirements
................................
................................
........
2
Table
2.2-1–Supported Models
................................
................................
................................
...................
4
Table
2.2-2–Cryptographic M
odule Logical Interfaces
................................
................................
................
7
Table
2.2-3–Mapping of Logical Interfaces to Physical Ports
................................
................................
.....8Table
2.3-1–Approved Module Algor
ithms
................................
................................
................................
..8Table
2.3-2–Module Security Functions
................................
................................
................................
......9Table
2.5-1–Roles with Required Identification and Authentication
................................
..........................
11
Table
2.5-2–Strength of Authentication
................................
................................
................................
.....12Table
2.5-3–Cryptographic Keys and CSPs
................................
................................
..............................
13
Table
2.5-4–Roles and Services
................................
................................
................................
...............
15
Table
2.5-5–Access Control
................................
................................
................................
......................
17
Table
2.6-1–Security Mechanism In
spection and Test
................................
................................
.............
18
Table
2.7-1–Self Tests
................................
................................
................................
..............................
19

002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
iiofi
i
LIST OF FIGURES
Figure
Title
Page
Figure
2.1-1–E
ncryptor Operation
................................
................................
................................
................
3
Figure
2.1-2-Encryptor Usage in Path Encryption Mode
................................
................................
..............
3
Figure
2.1-3–Encryptor Usage in Line Encryption
Mode
................................
................................
..............
4
Figure
2.2-1–Front View of Model 600 Encryptor
................................
................................
........................
5
Figure
2.2-2–Rear View of Model 600 Encryptor
................................
................................
........................
5

002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
1of21
1
Introduction
1.1
Overview
This document is the Security Policy for the
SafeNet
Encryptor
, Model 600
manufactured by SafeNet, Inc.
This Security Policy specifies the security rules under which the module shall operate to meet the
requirements
of FIPS 140
-
2 Level 3.
It also
describes how the encryptor functions in order to meet the
FIPS requirements, and the actions that operators must take to maintain the security of the encryptor.
This Security Policy describes the features and design of the
e
ncryptor
using the terminology contained in
the FIPS 140
-
2 specification.
FIPS 140
-
2, Security Requirements for Cryptographic Modules
specifies the
security requirements that will be satisfied by a cryptographic module utilized within a securitysystem
pr
otecting sensitive but unclassified information. The NIST
/CSE
C
Cryptographic Module Validation
Program (CMVP) validates cryptographic modules to FIPS 140
-2.
Validated products are accepted by the
Federal agencies of both the USA and Canada for the protecti
on of sensitive or designated information.
The FIPS 140
-
2 standard, and information on the CMVP, can be found at
http://csrc.nist.gov/groups/STM/cmvp/index.html
. More information describing t
he SafeNet Encryptor can
be found at
http://safenet
-
inc.com
.
This Security Policy defines the
cryptographic module
for multiple interface variants from 155
MB to
2.4
GB. These variants are functionally identical.
Th
is Security Policy contains only non
-
proprietary information. All other documentation submitted for FIPS
140-2 conformance testing and validation is “SafeNet
-
Proprietary” and is releasable only under
appropriate non
-
disclosure agreements.
1.2
References
Docu
ment No.
Author
Title
FIPS PUB 140
-2NIST
FIPS PUB 140
-
2: Security Requirements for Cryptographic Modules
FIPS PUB 140
-2Annex A
NIST
FIPS 140
-
2 Annex A: Approved Security Functions
FIPS PUB 140
-2Annex B
NIST
FIPS 140
-
2 Annex B: Approved Protection Pro
files
FIPS PUB 140
-2Annex C
NIST
FIPS 140
-
2 Annex C: Approved Random Number Generators
FIPS PUB 140
-2Annex D
NIST
FIPS 140
-
2 Annex D: Approved Key Establishment Techniques
DTR for FIPS
PUB 140
-2NIST
Derived Test Requirements (DTR) for FIPS PUB 140
-2, Security
Requirements for Cryptographic Modules
FIPS PUB 46
-3NIST
Data Encryption Standard (DES)
FIPS PUB 81
NIST
DES Modes of Operation
FIPS PUB 186
-2NIST
Digital Signature Standard (DSS)
FIPS PUB 180
-1NIST
Secure Hash Standard (SHS)
All of the
above references are available at URL:
http://csrc.nist.gov/groups/STM/cmvp/index.html
.
1.3
Terminology
In this document, the
SafeNet
Encryptor
is also referred to as “the module” or “the encryptor”.

002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
2of21
1.4
FIPS Requirements
The encryptor
meets the overall requirements applicable
for FIPS 140
-
2 to Level 3 security
as shown in
Table
1.4-1
.
Table
1.4-1-Cryptographic Module
Security Requirements
Security Requirements Section
Level
Cryptographic Module Specification
3
Cryptographic Module Ports and Interfaces
3
Roles and Services and
Authentication
3
Finite State Machine Model
3
Physical Security
3
Operational Environment
N/A
Cryptographic Key Management
3
EMI/EMC
3
Self-Tests
3
Design Assurance
3
Mitigation of Other Attacks
N/A
Cryptographic Module Security Policy
3
002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
3of21
2
SafeN
et
Encryptor
2.1
Functional Overview
The
SafeNet
Encryptor
provides data privacy and access control for connections between vulnerable
public and private networks. It employs
FIPS approved
AES and Triple
-
DES algorithms and, with the
flexibility to choose the d
esired interface module, can be deployed in
155/622 MB (
OC-3/12),1.0 GB, and
2.4 GB (
OC-48)networks. The encryptor can be centrally controlled or managed across multiple remote
stations using SafeNet's Security Management Center (SMC), a SNMPv3
-
based sec
urity management
system.
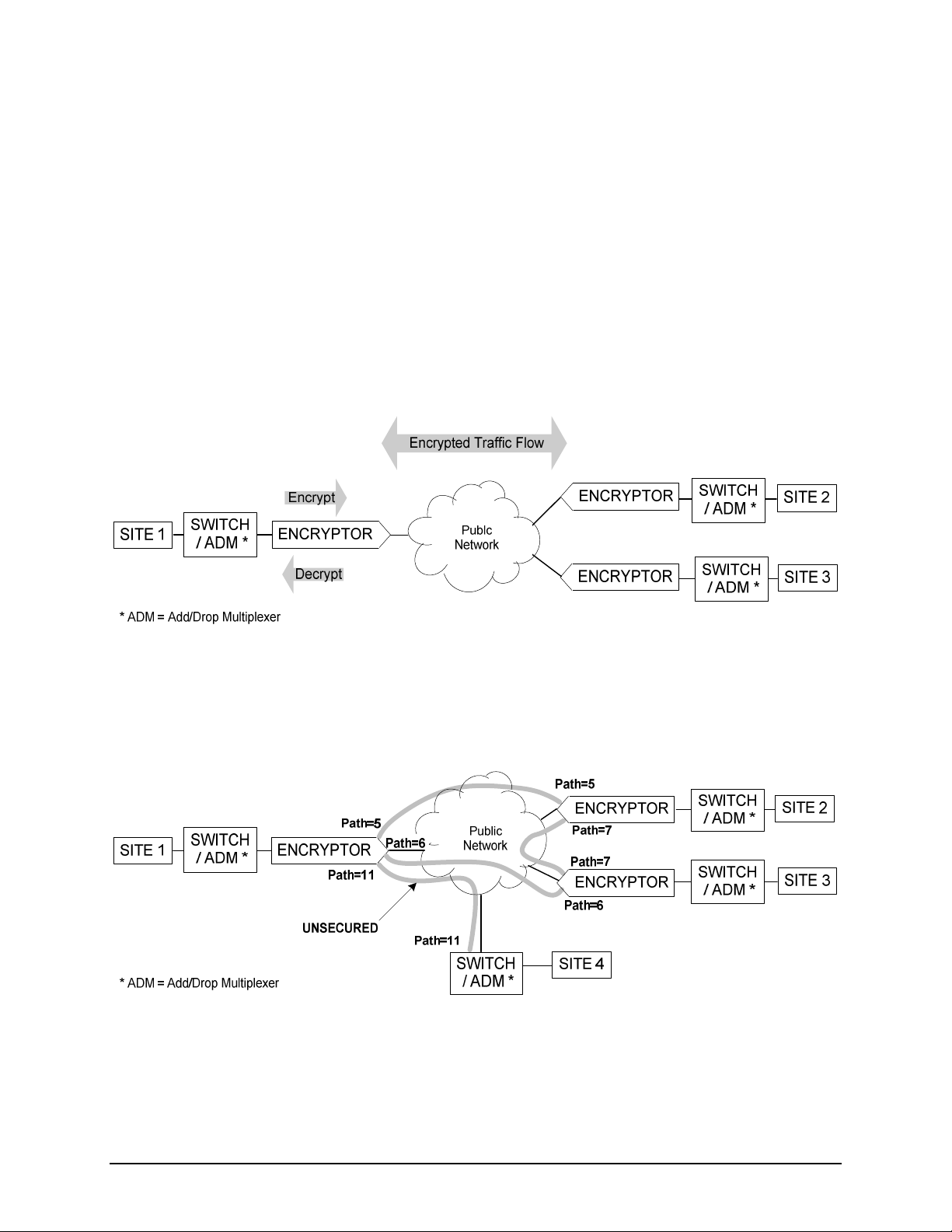
The role of the encryptor is illustrated in
Figure
2.1-1
. The encryptor is installed between
private
network
equipment
and
a public
network. An encryptor communicates with other encryptors in the network,
establishing secured connections between itself and the other modules. The encryptors selectively
en
crypt,
zeroize
, or pass in the clear, data flowing from the switch to the network. Conversely the
encryptors selectively decrypt, reject, or pass information flowing from the network to the switch.
Figure
2.1-1–Encryptor Operation
Secured connections are established between the cryptographic module
s
using the RSA key exchange
process
(as specified in the
ATM Forum Security Specification version 1.1)
. This results in a separate
se
cure
session
and does not require any secret
session
keys to ever be displayed or manually transported
and installed.
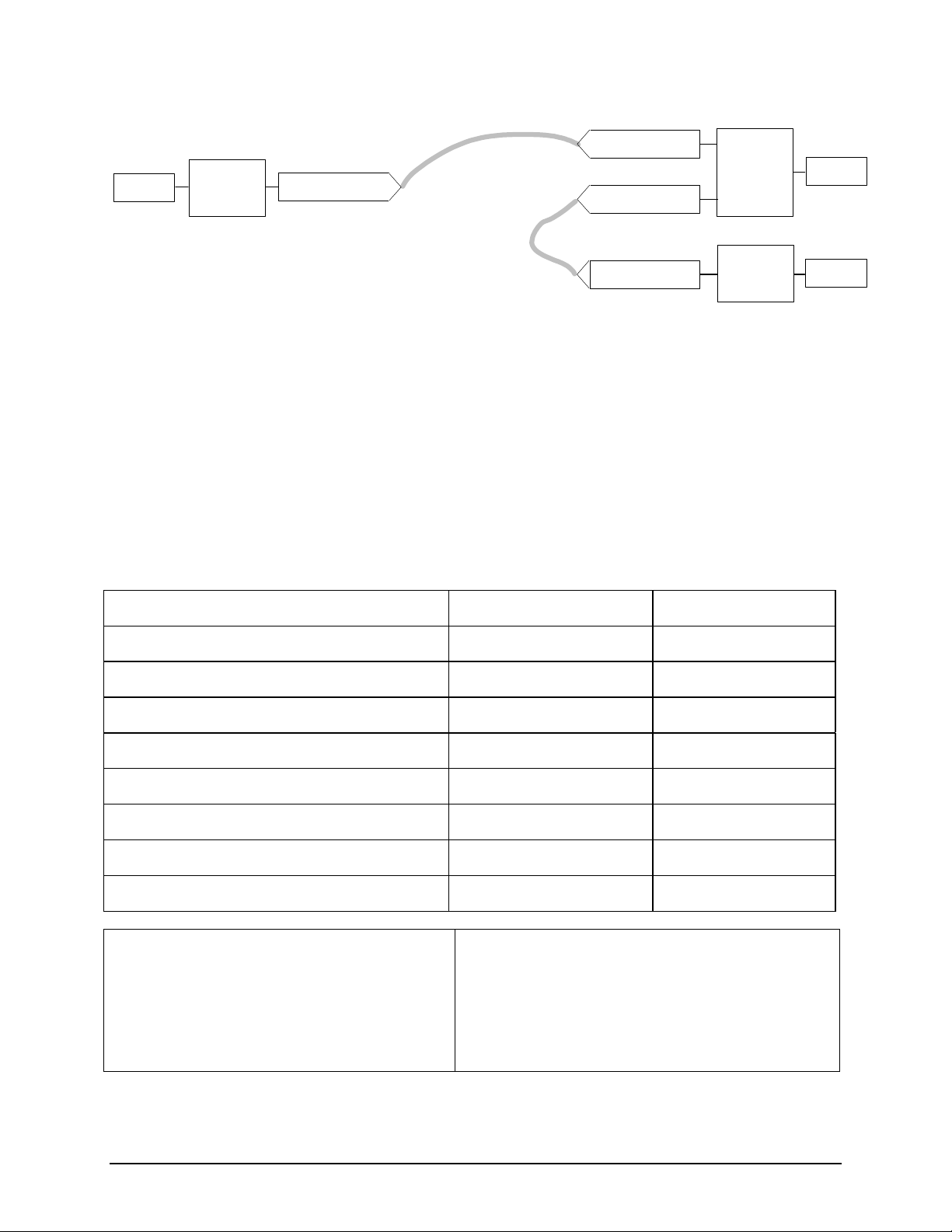
Figure
2.1-2-Encryptor Usage in Path Encryption Mode
Figure
2.1-2
shows an example of three secured paths and one unsecured path between sites.
002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
4of21
Figure
2.1-3–Encryptor Usage in Line Encryption Mode
SITE 2
SITE 1
ENCRYPTOR
ENCRYPTOR
OC48
SITE 2
ENCRYPTOR
OC48
OC48
SWITCH
/ ADM *
SWITCH
/ ADM *
SWITCH
/ ADM *
* ADM = Add/Drop Multiplexer
OC48
ENCRYPTOR
Figure
2.1-3
shows an example using encryptors in line encryption mode.
2.2
Module Description
The
SafeNet
Encryptor
is a multip
le-chip standalone cryptographic module consisting of production
-
grade
components contained in a physically protected enclosure in accordance with FIPS 140
-
2 Level 3.
The
module outer casing defines the cryptographic boundary. The steel case completely enc
loses the
encryptor
to protect it from tampering. Any attempt to remove the cover will automatically erase all
sensitive information stored internally in the encryptor.
Table
2.2-1–Supported Models
155/622 MB (OC
-
3/12)
2 km (904
-
10001
-
00x)
904-30013
-
00x(RoHS)
155/622 MB (OC
-
3/12)
15 km (904
-
10002
-
00x)
904-10014
-
00x(RoHS)
155/622 MB (OC
-
3/12)
40 km (904
-
10003
-
00x)
904-10014
-
00x(RoHS)
1.0 GB
10km (904
-
10112
-
00x)
904-10113
-
00x(RoHS)
2.4 GB (OC
-
48)
2 km (904
-
20001
-
00x)
904-25005
-
00x(RoHS)
2.4 GB (OC
-
48)
15 km (904
-
20002
-
00x)
904-25005
-
00x(RoHS)
2.4 GB (OC
-
48)
40 km (904
-
20003
-
00x)
904-25005
-
00x(RoHS)
Safe
Net
SONET Encrypto
r (SSE)
904-511i0-00xN/A
Safe
Net
Ethernet Encryptor (SEE)
943-511i0-0
0xN/A
The’x’ in the model numbers represents the
power cord variants.
Power cords are accessory kit items that are
separate from the physical systems.
1 US power cord
2 UK power
cord4 European power cord
5 Swiss power cord
7-48V DC power

002-010003
-
001
Revision
B
SafeNet Encryptor Security Policy
Page
5of21
The ‘
i
’ in the model numbers represents the
licensed interface speed variants.
Licensing is a logical Right to Use that is
separate from the physical systems.
For SONET Encryptors (904
-
)
0
Lic
ense for OC3
2
License for OC12
4
License for OC48
For Ethernet Encryptors (943
-
)3
License for 100MBPS
5
License for 1GBPS
The models differ only in the enclosed line interface card containing the protocol specific cryptographic
accelerators. The line
interface card itself is not meant to be field serviceable. Any attempt to remove the
interface will tamper the encryptor, erasing all sensitive information stored internally. While the line
interface cards are not field serviceable, the pluggable transcei
vers are. The pluggable transceivers are
outside the cryptographic boundary and may be changed as needed for the specific requirements of the
network infrastructure.
Module management is provided in
-
band or out
-of-
band. In
-
band management uses management
c
hannels on the module’s interface ports. Out
-of-
band management is provided using the dedicated
Ethernet port or a console port.
2.2.1
Enclosure Indicators
,
Connectors and Controls
All
600 series
models share a common enclosure.
Figure
2.2-1
shows the front view, which is the same
for all the
600 series
models. The front panel provides a network management port, a console port, a USB
port, an LCD display and LEDs for status, and a keypad for control input.
Figure
2.2-1–Front View of Model 600 Encryptor
Figure
2.2-2–Rear View of Model 6
0
0 Encryptor
RJ45–
remote management
RS-232
local terminal
USB
-
reserved
LCD display
LEDs
–
system state
/
network traffic
Keypad
LEDs
–
system state
/
network traffic
Network port
(
public network
)
Local port
(
private network
)
Power
connector
Power
switch
Tamper evident
seal
 Loading...
Loading...