Page 1

RV ON-16
RTS Voice Over Network
F . 01U.193.291
Rev. 06
DECEMBER/2011
Page 2
ii RVON-16
PROPRIETARY NOTICE
The product information and design disclosed herein were originated by and are the property of Bosch Security Systems, Inc.
Bosch reserves all patent, proprietary design, manufacturing, reproduction, use and sales rights thereto, and to any article disclosed
therein, except to the extent rights are expressly granted to others.
COPYRIGHT NOTICE
Copyright 2011 by Bosch Security Systems, Inc. All rights
reserved. Reproduction, in whole or in part, without prior written
permission from Bosch is prohibited.
*All other trademarks are property of their respective owners.
WARRANTY AND SERVICE INFORMATION
For warranty and service information, refer to the appropriate web
site below:
RTS............................................... www.rtsintercoms.com/warranty
RTSTW..................................................... www.rtstw.com/warranty
AudioCom................................. www.telexaudiocom.com/warranty
RadioCom..................................www.telexradiocom.com/warranty
Headsets................................ www.intercomheadsets.com/warranty
CUSTOMER SUPPORT
Te chnical questions should be directed to:
Customer Service Department
Bosch Security Systems, Inc.
12000 Portland Avenue South
Burnsville, MN 55337 USA
Telephone: 877-863-4169
Fax: 800-323-0498
Info@rtsintercoms.com
THE LIGHTNING
FLASH AND
ARROWHEAD
WITHIN THE
TRIANGLE IS A
WARNING SIGN
ALERTING YOU OF
“DANGEROUS
VOLTAGE” INSIDE
THE PRODUCT.
SEE MARKING ON BOTTOM/BACK OF PRODUCT.
WARNING: APPARATUS SHALL NOT BE EXPOSED TO DRIPPING OR
SPLASHING AND NO OBJECTS FILLED WITH LIQUIDS, SUCH AS VASES,
SHALL BE PLACED ON THE APPARATUS.
WARNING: THE MAIN POWER PLUG MUST REMAIN READILY OPERABLE.
CAUTION: TO REDUCE THE RISK OF ELECTRIC SHOCK, GROUNDING OF
THE CENTER PIN OF THIS PLUG MUST BE MAINTAINED.
WARNING: TO REDUCE THE RISK OF FIRE OR ELECTRIC SHOCK, DO NOT
EXPOSE THIS APPRATUS TO RAIN OR MOISTURE.
WARNING: TO PREVENT INJURY, THIS APPARATUS MUST BE SECURELY
ATTACHED TO THE FLOOR/WALL/RACK IN ACCORDANCE WITH THE
INSTALLATION INSTRUCTIONS.
CAUTION: TO REDUCE
THE RISK OF ELECTRIC
SHOCK, DO NOT REMOVE
COVER. NO USERSERVICABLE PARTS
INSIDE. REFER
SERVICING TO
QUALIFIED SERVICE
PERSONNEL.
This product is AC only.
THE EXCLAMATION
POINT WITHIN THE
TRIANGLE IS A
WARNING SIGN
ALERTING YOU OF
IMPORTANT
INSTRUCTIONS
ACCOMPANYING
THE PRODUCT.
TECHNICAL QUESTIONS EMEA
Bosch Security Systems Technical Support EMEA
http://www.rtsintercoms.com/contact_main.php
DISCLAIMER
The manufacturer of the equipment described herein makes
no expressed or implied warranty with respect to anything
contained in this manual and shall not be held liable for any
implied warranties of fitness for a particular application or
for any indirect, special, or consequential damages. The
information contained herein is subject to change without
prior notice and shall not be construed as an expressed or
implied commitment on the part of the manufacturer.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 3

RVON-16 iii
Important Safety Instructions
1. Read these instructions.
2. Keep these instructions.
3. Heed all warnings.
4. Follow all instructions.
5. Do not use this apparatus near water.
6. Clean only with dry cloth.
7. Do not block any ventilation openings. Install in accordance with the
manufacturer’s instructions.
8. Do not install near any heat sources such as radiators, heat registers, stoves,
or other apparatus (including amplifiers) that produce heat.
9. Do not defeat the safety purpose of the polarized or grounding-type plug. A
polarized plug has two blades with one wider than the other. A grounding
type plug has two blades and a third grounding prong. The wide blade or the
third prong are provided for your safety. If the provided plug does not fit
into your outlet, consult an electrician for replacement of the obsolete outlet.
10. Protect the power cord from being walked on or pinched particularly at
plugs, convenience receptacles, and the point where they exit from the
apparatus.
11. Only use attachments/accessories specified by the manufacturer.
12. Use only with the cart, stand, tripod, bracket, or table specified by the
manufacturer, or sold with the apparatus. When a cart is used, use caution
when moving the cart/apparatus combination to avoid injury from tip-over.
13. Unplug this apparatus during lightning storms or when unused for long
periods of time.
14. Refer all servicing to qualified service personnel. Servicing is required
when the apparatus has been damaged in any way, such as power-supply
cord or plug is damaged, liquid has been spilled or objects have fallen into
the apparatus, the apparatus has been exposed to rain or moisture, does not
operate normally, or has been dropped.
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 4

iv RVON-16
Bosch Security Systems, Inc.
Technical Manual
F. 01U.193.291
Rev. 06
Page 5

Table
of
Contents
INTRODUCTION .........................................................................................................................3
Description of the RVON-16 Voice Over Network Card ........................................................................3
Requirements ...........................................................................................................................................3
Features ....................................................................................................................................................4
Specifications ...........................................................................................................................................4
Digital ..................................................................................................................................................................4
Connections .........................................................................................................................................................4
Default Ethernet IP Addresses .................................................................................................................5
RVON-16 CARD CHANNEL ASSIGNMENT ............................................................................7
RVON-16 Channels .................................................................................................................................7
Resize your ADAM frame to accommodate AIO-16 cards and RVON-16 cards ...................................8
INSTALLATION ..........................................................................................................................9
Installation of the RVON-16 Card into the ADAM System ....................................................................9
Color Key Code .................................................................................................................................................10
Addresses and the RVON-16 Card ....................................................................................................................10
Switches and Connections .....................................................................................................................11
Configuring the RVON-16 Card with AZedit .......................................................................................13
RVON Connection Status Screen ..........................................................................................................15
Download RVON-16 Firmware through AZedit ...................................................................................22
Configuring RVON-16 using RVONedit ..............................................................................................24
RVON-16 Backcard ...............................................................................................................................25
LED Explanation ....................................................................................................................................26
BASIC NETWORK CONFIGURATION ..................................................................................27
Basic Network Configuration ................................................................................................................27
LAN (Local Area Network) vs. WAN (Wide Area Network) ..........................................................................27
Local Area Network ....................................................................... ................................................................27
WIDE AREA NETWORK .................................................................................... .... ..... ................................28
ACCESSING THE WIDE AREA NETWORK (WAN) ...................................................................................29
NETWORK ADDRESS TRANSLATION (NAT) ............................................................................. ..............29
PORTS ...............................................................................................................................................................29
IP ADDRESSES ................................................................................................................................................31
Ping a Computer ................................................................................................................................................32
POSSIBLE PITFALL WITH ROUTERS, GATEWAYS, AND SWITCHES .................................................33
RVON Configuration .............................................................................................................................34
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.261
Rev. 06
Page 6

2 RVON-16
Network Terminology 35
RVON TRUNKING CONNECTIONS .......................................................................................37
Notes 45
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.261
Rev. 06
Page 7
CHAPTER 1
Intr oduction
Description of the RVON-16 Voice Over Network Card
Like the RVON-8, the RVON-16 is installed into the ADAM intercom frame, the RVON-16 provid es vo ice over IP
communications for the RTS ADAM intercom family of products. Voice over IP technology sends voice (audio) information
in digital form using discrete packets rather than the traditional telephone network. The R VON-16 is an integrated solution for
connecting custom keypanels to the Intercom Matrix over standard IP networks by supporting 16 channels (ports) of Audio in
and out.
The RVON-16 supports all standard, hot-swappable and configurable options through Bosch’s RVONedit VoIP configuration
software, as well as support for remote keypanels and virtual keypanels via VoIP (voice over internet protocol).
RVON-16 also supports RTS Intelligent Trunking over IP. Trunking is a method of using minimal audio paths for a large
number of users. Because it is flexible, a trunked system can expand along with your business, to accommodate a growing
number of users. RTS’ Intelligent Trunking is a pro ven techn ology, which provides the same capabilities and ease of use for
intercoms and the seamless routing of communications between facilities, regardless of distance.
RVON-16 is fully compatible with internationally recognized standards and supports the following prot ocols: G.711, G.729A.
and G.723 (2 speeds).
Requirements
Application Version
RVON-Keyp anel v 2.1.0 or higher
RVON-8 v 2.1.0 or higher
RVON-C v 2.1.0 or higher
RVON-IO v 2.1.0 or higher
AZedit v 3.3.1 or higher
RVONed it v 2.0.0 or higher
VKP v 2.0.0 or higher
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 8
4 Introduction RVON-16
Features
Installation: The RVON-16 is hot-swappable and installs into any available slot in an ADAM intercom
system. It provides a single RJ-45 Ethernet connection for use with a 10 BASE-T or
100 BASE-TX network. It also has two DB-9 connections for RS-232 or RS-485
pass-thru port.
16 channels of Audio
IN and OUT: Expands the connectivity of the ADAM intercom by supporting 16 channels or ports of
audio in and out. Each channel has configurabl e network and bandwidth parameters that
can be tailored to individual network functions, as well as ancillary data for keypanels and
trunking control.
Ethernet Compatible: Fully Ethernet capable. The RVON-16 uses standard Ethernet protocols and is compatible
with 10 BASE-T or 100 BASE-TX Ethernet compliant devices and networks.
RVONedit Configuration: Users have the ability to adjust the audio parameters of each RVON-16 channel to
optimize the available bandwidth on the network.
Trunk Capable: The RVON-16 supports ancillary data control or use with RTS Intelligent Trunking.
Addressing: 16 individually addressable audio channels. The RVON-16 can simultaneously feed VoIP
capable keypanels, as well as various other matrix intercom systems.
Pass-Through Serial Port: Provides two (2) virtual serial connections via an IP connection. Which, if used while
trunking, may eliminate the need for multiple IP resources.
Specifications
Digital
COMPRESSION BIT RATE
G.711 64 K 125 s 20-60 ms 160-224 kbps 8k
G.729A 8 K 10 ms 20-120 ms 32 112 kbps 8k
G.723 5.3 K / 6.3 K 30 ms 60-120 ms 29-45 kbps 8k
*Data Rate depends on Codec Selection
NOTE: The Playout Delay and Bandwidth depends on the configured amount of audio per packet.
CODING
DELAY
Connections
1- RJ-45 Shielded Ethernet via backcard
2- DB-9 Serial Port via backcard
High-density keyed ADAM compatible backplane connector
Power..............................................................................................................................................................................10.2 Watts
Physical .......................................................................................................................................................5.687” W x 11.024” L
PLAYOUT
DELAY
BANDWIDTH
SAMPLE
RATE
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 9
RVON-16 Introduction 5
Default Ethernet IP Addresses
TABLE 1. Default Address for the RVON Product Line
Product Default IP Ad dress Default Subnet Mask
RVON-I/O 192.168.0.1 255.255.0.0
RVON-8 192.168.0.2 255.255.0.0
RVON-Keypanel 192.168.0.3 255.255.0.0
RVON-C 192.168.0.4 255.255.0.0
RVON-16 192.168.0.5 255.255.0.0
GPIO-16 192.168.0.6 255.255.0.0
MCII-e 192.168.0.7 255.255.0.0
Cronus 192.168.0.8 255.255.0.0
Zeus III 192.168.0.9 255.255.0.0
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 10

6 Introduction RVON-16
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 11
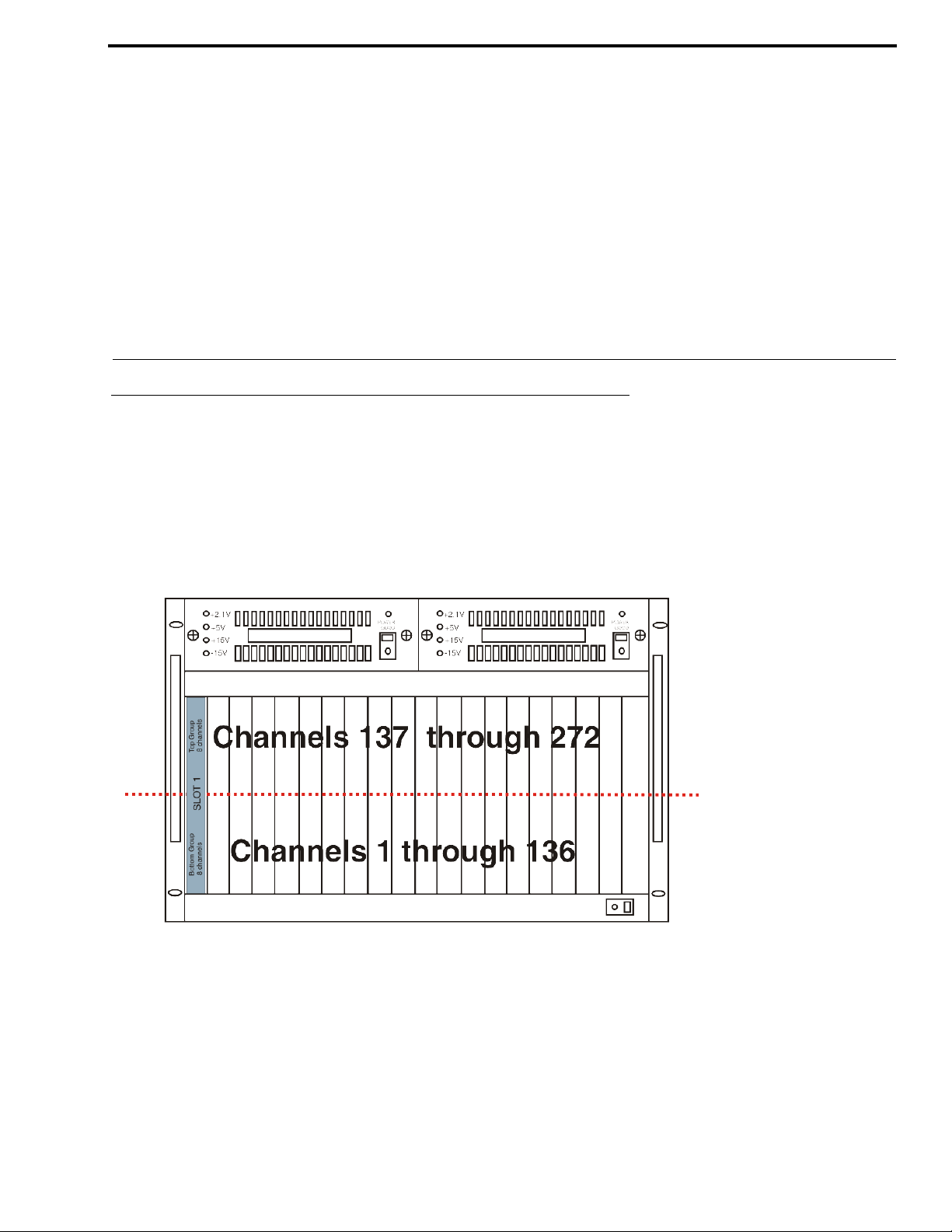
CHAPTER 2
RV ON-16 Car d Channel Assignment
RVON-16 Channels
With the introduction of RVON-16 cards into the ADAM system, the number of channels availabl e doubl es from 136 to 272
channels. This is because instead of the eight (8) channels of audio per R VON-8 card, you now have 16 channels of audio per
R VON-16 card. To be backwards compatible with the RVON-8, the RVON-16 channels have been split in to two (2) groups of
eight (8) channels; an upper group and a lower group. The channel numbering sequence follows the lower group channels
before numbering the upper group channels. For example, if you have an RVON-16 card in slot one (1) of an ADAM frame,
the bottom group of eight (8) channels has channels 1-8 assigned to them, while the top group of eight (8) channels has
channels 137 to 144 assigned to them (see Figure 1).
FIGURE 1. ADAM frame with RVON-16 cards only and the port numbering scheme
The ADAM Intercom System can run both the RVON-8 and RVON-16 card in the same frame. You can position your
RVON-8 and RVON-16 cards in any slot or in any sequence within the ADAM frame. However, when mixing the RVON
cards, it is important to consider that the channel numbering is consistent with the 2-tier channel systems. For example, in slots
1, 2, and 3, you have R VON-8 cards and in slot 4 you have a RVON-16 card. The channel numbering scheme assigns eight (8)
channels per card for the first four (4) slots. When assigning ports to slot four (4), the bottom group of channels are assigned in
sequence with the RVON-8 cards; however, the top group of ports associated with the RVON-16 card are assigned the
corresponding channels with the card position. This means channels 137 through 160 are not used and the top group of
channels used by the RV ON-16 card starts with channel 161 (see Figure 2 on page 8).
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 12

8 RVON-16 Card Channel Assignment RVON-16
FIGURE 2. ADAM frame with both RVON-8 and RVON-16 cards
Essentially, the channel numbering is static, in that the channel numbers used do not change whether you are using an
RVON-8 or an RVON-16 card. Rather, it is a question of whether the channels shall or shall not exist.
NOTE: You can only hot-swap similar cards in a slot to achieve proper connection. If you swap different types of RVON
cards (RVON-8 and RVON-16), connection at the destination does not occur. You must reconfigure the
destination device to point to the newly swapped RVON device.
Resize your ADAM frame to accommodate AIO-16 cards and RVON-16 cards
For information on how to upgrade your ADAM frame to high density, go to http://www.rtsintercoms.com, search Upgrading
your ADAM to High Density.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 13

CHAPTER 3
Installation
Installation of the RVON-16 Card into the ADAM System
CAUTION: The RVON-16 front card works with either an RVON-16 backcard or an RVON-8 backcard. However, if the
RVON-16 is used with an RVON-8 backcard, the second of the two RS-232 ports on the RVO N-16 is
unavailable. Similarly, an RVON-8 card works with an RVON-16 backcard, but the second RS-232 port is
unavailable. The second serial port is only available when an RVON-16 front card is used with an RVON-16
backcard.
The following firmware versions are the minimum required for RVON-16 support:
• MC V9.28.0
• MCII-e V1.6.0
• DBX V1.19.0 (w/PC V10.19.0 or w/PCII-e V1.19.0)
When inserting the RVON-16 in the ADAM system, the following considerations need to be made:
• Gently insert the RVON-16 into the correct slot. If the card is forced or twisted while inserting, a pin on the
backplane could short or break causing the card to become inoperable.
• When inserting the RVON-16 into the ADAM system, make sure to insert it into a compatible backcard. If
the card is inserted into an incompatible backcard, undesirable results can occur.
• DO NOT FORCE MATING CARDS
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 14

10 Installation RVON-16
Color Key Code
FIGURE 3. The RVON-16 Col or Key Code. This Key Code allows only the RVON-8 or RVON-16 to plug into a blue
coded, compatible backcard.
On the RVON-16 card, Telex has provided a color key code and knock-outs for digits 1-8 to ensure a compatible connection
between cards. The RVON-16 card color is blue, and inserts into a blue coded backcard only.
Addresses and the RVON-16 Card
Because the RVON-16 has an Ethernet interface, it is required to have a MAC (Media Access Control) address. This is a low
level address that contains 48 bits. Do not confuse this address with an IP (Internet Protocol) Address. In order to be IP
compliant, all cards must have a unique MAC ID when shipped from the manufacturer. Typically, the MAC ID of a piece of
hardware, such as the RVON-16 card, has a fixed or static address. Whereas, the RVON-16 card’s IP Address can change over
time.
The MAC Address uniquely identifies each node of a network and interfaces directly with the network media. The RVON-16
has a small 8-pin serial device on the board that the processor can read the unique MAC Address from. For more information,
on MAC IDs, contact technical support.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 15

RVON-16 Installation 11
Switches and Connections
IMPORTANT: You must remove the card from the frame in order to change any DIP switch settings.
The RVON-16 card, unlike the RVON-8 card has two banks of eight DIP Switches.
DIP Switch 1 AZedit Configuration Disable
Closed: Configuration via AZedit is disabled.
Open (Default): Configuration via AZedit is enabled.
Description: Disables configuration changes via AZedit. AZedit is still able to view the RVON
configuration and status. The configuration can be changed via the serial and Telnet connections.
DIP Switch 2 Configuration File Save Location
Closed: The RV ON card holds the definitive configuration file.
Open (Default): The Master Controller holds the definitive configuration file.
Description: Assigns where the configuration file for the RVON products is to be stored, either on the
Master Controller or on the RVON card.
DIP Switch 3 Not Used.
Keep in Open position.
DIP Switch 4 Inhibit Reset
Closed: When enabled, the card is prevented from resetting after 30 seconds of no communication
with the system controller.
Open (Default): When disabled, the card resets after 30 seconds of no communication with the
system controller.
Description: Allows pass-through serial data to continue when the intercom is otherw ise down (i.e.,
upgrades). Mainly used to keep trunking connections open when disruptions in comm unication on
the card occur.
DIP Switch 5 Password Reset
Closed: Resets the Telnet user name and password to their default values. The password is case
sensitive:
User: telex
Password: password
Also, this setting disables RVONedit and resets the authentication table in RVONedit.
Open (Default): Uses current username and password.
Description: Enables the user to reset the Telnet username and password.
DIP Switch 6 Serial Monitor Enable
Closed: Enables a serial monitor on back card DB9 via Serial Port 1.
Open (Default): Enables pass-through serial port via the back card DB9 on both serial port 1 and
serial port 2.
NOTE: Serial Port 2 is always seen as the pass-through port.
Description: Selects DB9 serial configuration.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 16

12 Installation RVON-16
DIP Switch 7 Boot Download Enable
Closed: Runs the boot download
Open (Default): Runs the native flash program.
Description: Switches to the boot download flash program. This program is sent with the RVON-16
card in case the native flash program becomes corrupt.
DIP Switch 8 DEBUG ONLY!
Closed: Debug mode.
Open (Default): Normal operation mode.
WARNING: DIP Switch 8 must be left in the Open position. It is reserved for debugging and can
have unintended consequences.
DIP Switch 9 Serial Port Select A
Closed: Select RS-485 (for serial port 1)
Open (Default): Select RS-232 (for serial port 1)
Description: Selects either RS-485 or RS-232 operation on the debug/serial pass through port.
DIP Switch 10 Serial Port Select B
Closed: Select RS-485 (for serial port 2)
Open (Default): Select RS-232 (for serial port 2)
Description: Selects either RS-485 or RS-232 on the second debu g/seri al pass through port.
DIP Switches
11-15
Not Used.
Keep in Open position.
DIP Switch 16 Not Available
Closed: Not Connected
Open (Default): Not Connected
FIGURE 4. RVON-16 Switch Panels
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 17

RVON-16 Installation 13
Configuring the RVON-16 Card with AZedit
NOTE: RVONedit version 2.0.0 has more extensive configuration options for the RVON-16 card. For more information
on purchasing RVONedit 2.0.0, contact customer service at 1-800-392-3497.
Once the RV ON-16 card is inserted into the intercom, AZedit automatically recognizes the card.
NOTE: Requires intercom firmware and AZedit software that supports RVON cards.
To configure the RVON-16 card, do the following:
1. From the Status menu, select I/O Cards.
The I/O Card Status screen appears showing a list of installed cards.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 18

14 Installation RVON-16
2. Right click an RVON-16 card, and select RVON Configuration.
The RVON Configuration screen appears.
3. From the RVON drop down list, select the slot in which the RVON-16 card resides, if it is not already selected.
4. In the IP Address field, enter the IP Address you have assigned to the RVON-16.
5. In the Network Mask field, enter the Network Mask of the network to which the RVON-16 is connected.
6. In the Default Gateway field, enter the Default Gateway Address, if applicable, of the network to which the RVON-
16 card is connected.
A Default Gateway is only required if the RVON-16 connection s are between LANs.
7. In the Target IP Addr field, enter the Target IP Address of the device you want to connect to over Ethernet.
8. From the First Serial Baud Rate drop down list, select the baud rate at which the data is transmitted for the first serial
port.
NOTE: Configuration of the 2nd pass-through port via AZedit is not supported.
NOTE: You must configure the channels settings on each end of a connection to ensure the same codec and packet
size are selected at each end. Remember, the RVON-16 card has more channels which can be configured.
9. From the R VON Channel drop down list, select the channel you want to use to communicate to another device across
the network.
10. In the Device IP Addr: field, enter the IP Address of the device to which you want to connect.
11. From the Device Type drop down list, select the type of device to which the RVON-16 card is connecting.
12. From the Device Channel drop down list, select the channel on the device to which the RVON-16 communicates.
13. From the CODEC type drop down list, select the CODEC type you want to use for this channel.
14. From the Packet Size drop down list, select the size of each audio packet.
NOTE: A CODEC is an algorithm used to compress audio. There are 5 Codices supported by Telex: G.711 s law,
G.711A, G.729AB, G.723 (5.3k), and G.723 (6.3k). The type of CODEC dictates the quality of audio you
hear and the network bandwidth used. The packet size determines how much audio is carried across the
network in each transmitted packet. The CODEC type and packet size chosen requires different amounts of
bandwidth from the network see “Specifications” on page 4. As with the CODEC type, the packet size you
choose for the audio transfer affects the audio you hear and the bandwidth you use over the network. The
larger the audio packet you choose to use, the lower the bandwidth used. However, the larger packet sized
can result in a higher delay and longer gaps if the packet is lost. On the other hand, smaller packet sizes
result in larger bandwidth use, but lower delays and smaller gaps if the packet is lost. The Intercom System
Engineer and the Network Administrator may want to work together in choosing the CODEC type and
packet size suitable for the size of the network, so degradation of the network resources does not happen.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 19

RVON-16 Installation 15
15. Select Enable VAD (Voice Activity Detection), if you want to conserve bandwidth when the audio level is below a
given threshold.
Voice activity detection saves network bandwidth by stopping the flow of audio packets when silence is detected. VAD
is similar to VOX.
NOTE: At this point you may choose another channel to configure or choose another card to configure.
16. Once you are completely finished, click Apply.
Apply sends all of the changes to all the cards in the intercom, or click Cancel to discard all changes you have made.
RV ON Connection Status Screen
The RVON-16 connection status screen di splays information pertaining to RVON channel connections. You can only show
statistics for one channel on a card at a time.
NOTE: To view the RVON Connection Status screens, make sure both AZedit and the RVON-16 card are on the same
Ethernet network. The reason this is important is because the statistics are updated once per second. At this rate
of dynamic update, a serial port could not pass the data effectively.
To view the RVON Connection Status screen, do the following:
1. From the Status menu, select I/O Cards.
The I/O Card Status screen appears showing the types of installed cards.
2. Right click the card with which you want to work.
A context menu appears.
3. Select RVON Con nection Status.
The RVON Connection Status screen appears. The connection screen contains five (5) pages of information about the
selected channel and are described in detail on the following pages.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 20

16 Installation RVON-16
Screen Item Description
Select Local Card and Channel
RVON Card The card for which you want to view the status
From the RVON drop do wn list, select the card you want to view.
IP Address Displays the IP (Internet Protocol) Address of the card you select
Local Channel One (1) of 16 channels supported by the RVON card.
From the Channel drop down list, select the channel for which you want to view
the status
Remote Connection Information
Device Type Displays the type of device the RVON card is connected to on the other end of
the channel.
IP Address Displays the IP Address of the device connected at the other end of the channel.
Remote Channel Displays the channel at the other end of the connection that the device is using.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 21

RVON-16 Installation 17
Screen Item Description
Attempts/Drops The number of times a call attempt has been made and dropped.
NOTE: The number of attempts should always be one greater than the
number of drops.
Current Call State The state of the connection. There are two connection states: Connected or Idle.
Origination/Termination Displays which end of the connection originated or terminated the call.
Local: RVON device
Remote: Device at the other end of the connection
Release Reason Displays why the connection was terminated, for example, congestion, network
error, local release, remote release.
Connection Duration Displays the duration of the connection. This is shown in hh/mm/ss.
Compression Algorithm Displays what type of configuration the connection is using. This can be
Audio Packet Size
Voice Activity Detect (VAD)
different than the original configuration if both ends of the channel are not
configured the same. If the configuration is different, these fields are red.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 22

18 Installation RVON-16
Screen Item Description
VOIP Playout Statistics
Playout Buffer Size Displays how much audio can be received from the network before packets are
lost. This is four times bigger than configured packet size. This is a static system
setting.
Nominal Playout Delay Displays how much audio is collected before playout begins. Playout begins at half
the Playout Buffer Size, which is two times the configured packet size. This is a
static system setting.
Average Playout Delay Displays the actual average audio collected before packets are played out. This is
measured over the length of the connection.
Voice Playout Buffer Underrun Displays the number of times that packets were not played because the Playout
Buffer was empty.
NOTE: If VAD is enabled, there are playout buffer runs because there are no
packets being received during silence.
Voice Playout Buffer Overrun Displays the number of packets that were discarded because the Playout Buffer
was full.
Missing Sequence Packet Displays how many audio packets were missed in the sequence.
Replaced Packets Displays how many audio packets were replayed.
Average Frame Jitter Displays the measure of consistency of packet arrival times. Lower jitter is better.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 23

RVON-16 Installation 19
Screen Item Description
Network Statistics
Voice Playout Packets (Tx/Rx) Displays the number of voice packets transmitted and received from the other side of
the connection.
DTMF Relay Packets (Tx/Rx) Displays the number of DTMF (dual tone multiple frequency) relay packets
transmitted and received. DTMF relay packets are a bandwidth and quality saving
feature within the RVON devices.
Silence Detection Packets (Tx/
Rx)
Displays the number of times a silence detection packet has been sent or received.
VAD (voice activity detection) must be enabled.
Silence Suppressed Packets (Tx) Displays the number of packets never sent because the packets contained silence.
Packet Interarrival Time (Min/
Displays the minimum and maximum time elapsed between packets being sent.
Max)
Recent Bandwidth Use (Tx/Rx) Displays the amount of bandwidth used in Kbytes/sec over the length of the call.
This is calculated by the number of voice packets transmitted and received over the
last 10 seconds.
Average Bandwidth Use (Tx/Rx) Displays the amount of bandwidth used in Kbytes/sec over the length of the call.
This is calculated by the number of voice packets transmitted and received and the
length of the connection.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 24

20 Installation RVON-16
Screen Item Description
Error Counts
Invalid Headers Displays how many IP packets could not be parsed.
Invalid MAC Address Displays how many invalid MAC addresses tried to connect.
Invalid SSRC Displays the number of packets with an invalid SSRC.
Invalid Payload Displays how many incorrectly formatted packets were received.
DSP to Micro Overrun Displays the number of packets that were lost because the Micro was too busy to
receive.
Invalid Destination Displays how many invalid destinations were received.
Lost Packets Displays how many packets were lost.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 25

RVON-16 Installation 21
Screen Item Description
SERIAL TO ETHERNET The Serial to Ethernet information shows the serial data that is received on the
serial connection and transferred to the Ethernet address of the card to which the
serial data is sent.
Bytes Transferred Displays the number of bytes transferred from the serial connection to Ethernet.
Bytes Lost Displays the number of bytes that could not be transferred.
Errors Displays the number of errors that occurred during transfer.
Tx IP Address Displays the IP Address of the card the serial data is sent.
Baud Rate Displays the baud rate of the serial connection.
ETHERNET TO SERIAL The Ethernet to Serial information shows the serial data that is received on the
Ethernet connection and transferred to the serial connection.
Bytes Transferred Displays the number of bytes that have been transferred to the serial port.
Bytes Lost Displays the number of bytes that could not be transferred.
Errors Displays the number of errors that occurred during transfer.
Rx IP Address Displays the IP Address from which data was last received via Ethernet (this
address should match the Tx IP Address).
Unexpected Bytes Displays the number of unexpected bytes of data.
Unexpected bytes is data that has come from any IP address that is not the Tx IP
Address. The bytes of data are considered unexpected bytes and are not
transferred.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 26

22 Installation RVON-16
Download RVON-16 Firmware through AZedit
NOTE: AZedit sends the program directly to the RVON-16 card over Ethernet. This is different from other I/O cards that
receive the firmware from the Master Controller. For this reason, verify the PC running AZedit is on the same
network as the RVON-16 card. If it is not, AZedit is not be able to find the card. To test the connection, ping the
RVON card from a command line. For more information on testing for a connection, see “Ping a Computer” on
page 32.
To download firmwa re to the RVON-16 card from AZedit, do the following:
1. Open AZedit.
2. From the Status menu, select Software Versions, then I/O Cards.
The I/O Card Version Information screen appears showing the occupied slots in the system.
3. Highlight the Version to be updated.
You may select more than one version at a time by holding the Ctrl key down while you select.
4. Right click the high-lighted selections and select Download Firmware.
The Firmware Download window appears.
5. Using the browse feature, browse to the file to be downloaded.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 27

RVON-16 Installation 23
6. Click Open.
The Download Device Firmware window appears.
7. Click Begin Download.
The download begins. Once the download shows 100% a message (shown below) appears.
8. Click OK.
The RVON-16 firmware download is complete. This takes a minute or two to occur.
9. Verify the version upgrade in the I/O Card Version Information Window.
CAUTION: Do not power down the frame or pull the RVON-16 card (s) from the frame until you have
verified the new version information from AZedit. If the card loses power while
reprogramming the onboard flash memory, the card may become unbootable, and may need to
have its flash chips replaced.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 28

24 Installation RVON-16
Configuring RVON-16 using RVONedit
NOTE: If you are using R VON-16 with RVONedit, you must use RVONedit version 2.0.0. Please contact your customer
service representative for ordering details.
R VONedit is a W indows-based, GUI (graphical user interface) application designed exclusively for Bosch RVON/V oIP-ba sed
products. It can be used to display or configure R VON (VoIP) options associated with the different devices. RVONedit is to the
VoIP products as AZedit is to ADAM, Cronus, and Zeus. There are five (5) RVON devices in the RVON family:
• RVON-8
• RVON-I/O
• RVON-Keypanel
• RVON-C
• RVON-16
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 29

RVON-16 Installation 25
RVON-16 Backcard
FIGURE 5. RVON-16 Backcard
RJ-45 PIN Function DB-9PIN Function
1 Ethernet TPO+ 1 N/A
2 Ethernet TPO- 2 RXD, RVON-16 Received Data
3 Ethernet TPI+ 3 TXD, RVON-16 Received Data
4TPO+ 4N/A
5 TPO- 5 GND
6 Ethernet TPO- 6 N/A
7TPI+ 7N/A
8TPI- 8N/A
9N/A
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 30
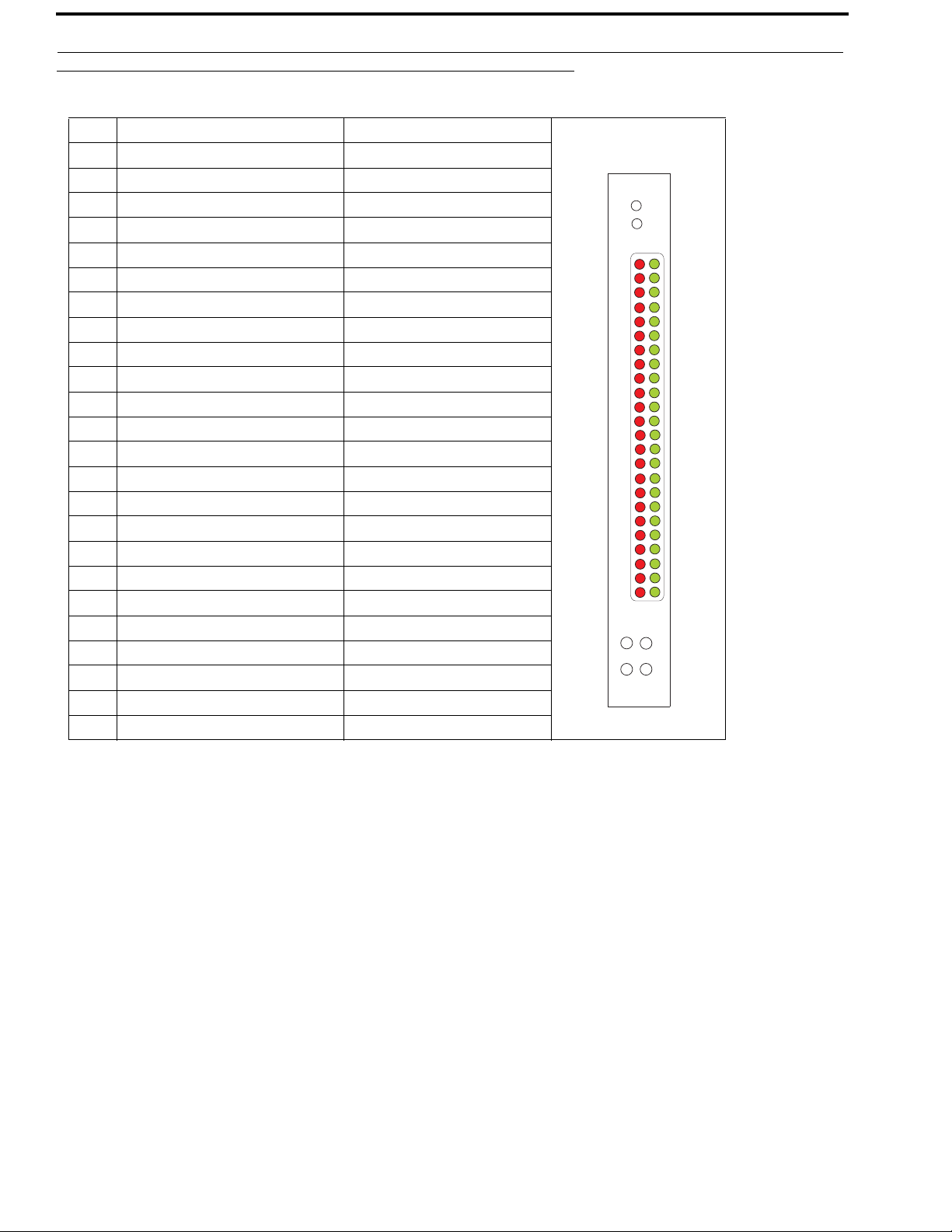
26 Installation RVON-16
LINK
ACT
RVON-16
1
0
2
3
4
6
5
7
8
9
10
11
22
23
20
21
18
19
16
17
14
15
12
13
1
2
LED Explanation
RED LED GREEN LED
23 VOIP not connected - Channel 1 VOIP connected - Channel 1
22 VOIP not connected - Channel 2 VOIP connected - Channel 2
21 VOIP not connected - Channel 3 VOIP connected - Channel 3
20 VOIP not connected - Channel 4 VOIP connected - Channel 4
19 VOIP not connected - Channel 5 VOIP connected - Channel 5
18 VOIP not connected - Channel 6 VOIP connected - Channel 6
17 VOIP not connected - Channel 7 VOIP connected - Channel 7
16 VOIP not connected - Channel 8 VOIP connected - Channel 8
15 VOIP not connected - Channel 9 VOIP connected - Channel 9
14 VOIP not connected - Channel 10 VOIP connected - Channel 10
13 VOIP not connected - Channel 11 VOIP connected - Channel 11
12 VOIP not connected - Channel 12 VOIP connected - Channel 12
11 VOIP not connected - Channel 13 VOIP connected - Channel 13
10 VOIP not connected - Channel 14 VOIP connected - Channel 14
9 VOIP not connected - Channel 15 VOIP connected - Channel 15
8 VOIP not connected - Channel 16 VOIP connected - Channel 16
7 Pass-Through Serial TX 1 Pass-Through Serial RX1
6 Pass-Through Serial TX 2 Pass-Through Serial RX2
5 RS-232 Enabled - Channel 1
4 Shell Log Message (TX) RS-232 Enabled - Channel 2
3 Ethernet Half Duplex Ethernet Full Duplex
2 Ethernet 10Mbps Ethernet 100Mbps
1 Ethernet Not ‘AUTO’ Ethernet Link Good
0 Control Bus TX Control Bus RX
The VOIP Red and Green LEDs 8-23 display different states of the VOIP connection:
Green LED on, Red LED off .................................................................................................................................VOIP Connection Connected
Green LED winks on and off; Red LED off...........................................................................................................VOIP Connected to keypanel
Green LED off; Red LED on...... .. .................................. .............................................................................VOIP Configured but not connected
Green LED off; Red LED off...................................... .................................. .................................................VOIP Connection Not Configured
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 31

APPENDIX A
Basic Network Configuration
Basic Network Configuration
This section covers basic network configuration set-up and testing. Also covered are basic concepts and operations, including
the difference between LAN and WAN networks and how IP Addressing is used.
In a networked environment, such as a company, typically there are many computers connected together using a router or a
switch. In larger companies, there may be several different routers distributed in buildings and plant locations. A router allows
any LAN-side computer to communicate with other computers and devices outside the LAN (local area network). Routers
send data packets from one place to another place on a network. routers use network addresses to route packets to the correct
destination. For example, in a TCP/IP network, the IP (internet protocol) address of the network interface is used to direct
router destinations.
Because routers help computers inside the LAN talk with computers outside of the LAN, the security of a company’s LAN
may be compromised by gaps of open ports in the router. Security measures may have been instituted to compensate for these
vulnerabilities. Consult you network administrator to learn about the security measures taken to protect your network. VPN, or
virtual private network, is one such security measure to protect the intelligence of the LAN. A computer outside the LAN must
have an address or key known by the VPN to allow access to the LAN. Many companies use a VPN to connect two different
LANs, thus allowing the transfer of data between two networks.
LAN (Local Area Network) vs. WAN (Wide Area Network)
Local Area Network
Simply put, a LAN is a computer network that connects a relatively small area (a single building or group of buildings). Most
LANs connect workstations and computers to each other. Each computer (also known as a “node”), has its own processing unit
and executes its own programs; however, it can also access data and devices anywhere on the LAN. This means many users
can access and share the same information and devices. A good example of a LAN device is a network printer. Most
companies cannot afford the budgetary or hardware expense of providing printers for each of its users; therefore, one printer
(or device) is placed on the LAN where every user can access the same printer.
The LAN uses IP Addresses to route data to different destinations on the network. An IP Address is a 32-bit numeric address
consisting of four numbers separated by periods (for example, 1.160.10.240).
NOTE: For more information on IP Addresses, see you local network administrator.
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 32

28 RVON-16
FIGURE 6. Local Area Network Diagram
WIDE AREA NETWORK
A wide area network (WAN) connects two or more LANs and can span a relatively large geographical area. For example,
Telex Headquarters in Burnsville, MN is connected to several branch offices in Nebraska and Arkansas over a WAN. The
largest WAN in existence is the Internet.
FIGURE 7. Wide Area Network Diagram
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 33

RVON-16 29
ACCESSING THE WIDE AREA NETWORK (WAN)
Figure 3 shows LAN IP Addresses using a common IP Address, 10.2.100.X (192.168.X.X is another common address). Most
devices are shipped with these addresses as its default. It is recommended to use these addresses for LANs.
FIGURE 8. Network Address Translation
NETWORK ADDRESS TRANSLATION (NAT)
Using the initial IP Address, then converting it to a valid WAN IP Address is how the network address translation works, in
theory . Once the IP address is changed, it is up to the network interface device (such as a router, gateway, switch, etc.) to keep
track of which computers are talking on which ports. For example, if two local devices (PC1 and PC2 in Figure 3) both wanted
to talk via port 1031, then the network interface device would have to change one of the port requests to the next available port,
1032.
PORTS
In general, a network port is an endpoint to a logical connection. The port number identifies what type of port it is. For
example, port 80 is used for HTTP traffic. When you type an address into the address bar of a web browser, your computer
goes to find an IP Address for the url you are requesting (http://www.telex.com). To obtain this address, the computer contacts
a DNS server (Domain Name Server). Once the IP Address is found, it tries to connect to the http port of the network device
(port 80). See Ta ble 1 for a list of the more well-known port numbers.
Each network device can be set-up to respond or not respond to the various ports. The function of responding or “hosting a
service” is called “serving”.
TABLE 2. Packet Translation
Packet before Translation Packet after Tr anslation
Source Destination Source Destination
To
Internet
From
Internet
IP Address
10.2.100.2 1031 192.156.136.22 80 99.5.1.30 1031 192.156.136.22 80
192.156.136.22 80 99.5.1.30 1031 192.156.136.22 80 10.2.100.2 1031
Port
Number
IP Address
Port
Number
IP Address
Port
Number
IP Address
Port
Number
If a second workstation on the LAN wants to communicate to the same server, and happens to use the same source port
number, then the LAN Modem translates the source port number as well as the source IP address. In Table, 2, a second LAN
computer wants to access a web page. The NAT device now uses port 1032 for this connection where it used port 1031 in
Table 1.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 34

30 RVON-16
TABLE 3. Packet Translation
Packet before Translation Packet After T ranslation
Source Destination Source Destination
To
Internet
From
Internet
IP Address
10.2.100.1 1031 192.156.136.22 80 99.5.1.30 1032 192.156.136.22 80
192.156.136.22 80 99.5.1.30 1032 192.156.136.22 80 10.2.100.1 1031
Port
Number
IP Address
Port
Number
IP Address
Port
Number
IP Address
Port
Number
Amazingly , all the address translation that occurs takes place
automatically in order to make web browsing and other
functions easier. This is also a way for large web hosting
services to speed up the network by having different devices
perform different functions.
TABLE 4. Well-known TCP Port Numbers
Port Number Description
1
TCP Port Service Multiplexer
(TCPMUX)
5 Remote Job Entry (RJE)
7ECHO
18 Message Send Protocol (MSP)
20 FTP-Data
21 FTP- Control
23 Telnet
25 Simple Mail Transfer Protocol (SMTP)
29 MSG ICP
37 Time
42 Host Name Server (Nameserv)
43 Whols
49 Login Host Protocol (Login)
53 Domain Name Server (DNS)
69 Trivial File Transfer Protocol (TFTP)
70 Gopher Service
79 Finger
80 HTTP
103 X.400 Standard
108 SNA Gateway Access Server
109 POP2
110 POP3
115 Simple File Transfer Protocol
118 SQL Services
TABLE 4. Well-known TCP Port Numbers
Port Number Description
119 Newsgroup (NNTP)
137 NetBIOS Name Service
139 NetBIOS Datagram Service
143 Interim Mail Access Protocol (IMAP)
150 NetBIOS Session Service
156 SQL Server
161 SNMP
179 Border Gateway Protocol (BGP)
190
Gateway Access Control Protocol
(GACP)
194 Internet Relay Chat (IRC)
197 Directory Location Services (DLS)
389
Lightweight Directory Access Protocol
(LDAP)
396 Novell Netware over IP
443 HTTPS
444
Simple Network Paging Protocol
(SNPP)
445 Microsoft-DS
458 Apple Quick Time
546 DHCP Client
547 DHCP Server
563 SNEWS
569 MSN
1080 Socks
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 35

RVON-16 31
IP ADDRESSES
If you do not know your IP Address, you can open a DOS screen in a Windows- based environment and bring up the ipconfig
screen.
To find your IP Address using ipconfig, do the following:
1. From the Start Menu, open a Command Prompt screen.
2. At the prompt, type ipconfig, then press Enter.
The IP configurations appear for your machine, such as the DNS suffix, IP Address, Subnet Mask, and Default
Gateway.
3. At the prompt, type Exit to close the screen.
NOTE: If you want more detailed parameters for your machine, type ipconfig/All. This screen shows the computers
network configuration settings.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 36

32 RVON-16
Ping a Computer
Pinging a computer on the network makes sure it is able to be “seen” and receive messages on the network.
NOTE: You can also ping your RVON-8 card to verify that it is responding over the network by putting the cards IP
Address in place of the computer IP Address.
To Ping a computer on the network, do the following:
1. From the Start menu, select Run....
2. At the Run command, type CMD to open a Command Prompt screen.
3. At the prompt, type the IP Address of the computer you wish to ping (for example, 10.2.100.130).
4. Press Enter.
NOTE: If the computer you are pinging is not responding to the ping, you receive a time-out message in the
command prompt screen.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 37

RVON-16 33
POSSIBLE PITFALL WITH ROUTERS, GATEWAYS, AND SWITCHES
Anytime computers communicate through routers, gateways, and switches, they may be allowed or denied th e connection.
Network interface devices can be configured to block specific outgoing requests, as well as incoming requests, based on the IP
Address and/or port. This is one of the security mechanisms of a router. This also happens when broadcast messages are sent
and received.
To view the path an IP Address takes to retrieve information, do the following:
1. From the Start Menu, open a Command Prompt screen.
2. At the prompt, type tracert and type the url or IP Address you want to trace.
3. Press Enter.
The details of the tracer route are displayed.
NOTE: The message request timed out appears if the IP Address port in or out is denied to the incoming or outgoing
message.
4. When you are finished, type exit to close the Command Prompt window.
Bosch Security Systems, Inc.
Technical Manual
F.01U.193.291
Rev. 06
Page 38

34 RVON-16
RVON Configuration
RVON cards use ports for communication of audio and control packets. Because routers can be configured to block certain
incoming and outgoing requests, you need to open the following ports in your network to allow WAN connections to and from
a Network Interface Device. See Table X for the ports that need to be opened for the RVON cards to operate properly.
TABLE 5. Ports necessary for RVON card functionality.
Port Port Description
2076 UDP Call Control Signalling
2077 UDP Audio Packets
2079
2080 TCP Telex Keypanel Protocol
2081 UDP Pass Through Serial
2082 TCP Firmware Download
2100 Remote Administration
2102 Authentication Server
UDP Telex Proprietary
Signalling
Below, is an example of a router configuration screen. Not all routers are configured the same way and may not look exactly
like this screen.
Figure 6. Linksys Port Range Window
NOTE: Linksys supports up to 253 nodes on a router. This is why it is called a Router/Switch because there are WAN
functions like a router as well as having a 4-port LAN switch. It also does not support simultaneous forward and
DHCP.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 39

RVON-16 35
Network Terminology
Bridge A bridge is a device that connects two LANs, or two segments of the same LAN that use the
same protocol. Sometimes called “transparent bridges” they work at the OSI model layer 2.
Simply put, they are not concerned with protocols. Their main job is to pass data to a
destination address that is predetermined in the data packet.
With a bridge, all of your computers are on the same network subnet (s ee Subnet). This means
your computers can communicate with each other an have their own internet connection. If
you assign your own IP addresses be sure to use the same first three (3) octets of the IP
address (for example, 192.168.0.X).
Domain Name Server
(DNS)
A DNS Server is an internet service that translates domain names (for example, in the URL
http//www.telex.com, the domain name is telex.com) into IP addresses. The internet is based
on IP address which are numeric, and since domain names are alphabetic, they are easier to
remember. Every time a domain name is used it must go through the DNS server to be
translated.
Gateway A gateway is a node on a network that serves as an entrance to another network. The gateway
routes traffic from a computer to an outside network that is serving the web pages. For
example, the gateway for a home computer is the ISP provider that connects the user to the
Internet.
In a corporate environment, the gateway often acts as a proxy server and a firewall. Gateways
are similar to routers and switches, in that they forward data to the destination and provide the
path for which the data travels to the destination.
Hub A hub is a common connection point for devices in a network. A hub has multiple ports.
When a data packet arrives at a hub, it is copied and distributed to all of its ports so that all
nodes on the LAN can see the packets.
There are three types of hubs:
passive hub - this hub serves as a conduit for the data, enabling it to go from one
device to another.
intelligent hub - (also known as manageable hubs) this hub includes additional
features that enable administrators to monitor traffic through the hub.
switching hub - this hub reads the destination address of each packet and then
forwards the data pack to the appropriate port.
IP Address
(Internet Protocol
Address)
Bosch Security Systems, Inc.
An IP Address is an identifier or numerical name for a computer or device on a network. Data
between computers are routed over the network using these addresses to identify the
computer the message being sent to and the computer the message is being set from.
The format of an IP Address is a 32-bit numeric address written as four numbers separated by
periods. For example, an IP Address looks like 10.100.1.1.
When working within an isolated network (meaning there is no Internet access), IP Addresses
can be assigned at random just as long as they are unique to each computer and device. When
the isolated network is connected to the INternet, registered Internet Addresses must be
obtained. This is to prevent duplication of addresses.
The four numbers in an IP Address are used in different ways to identify a particular network
and host on the network. There are three (3) classes of Internet Addresses:
CLASS A: supports 16 million hosts on each of 127 networks.
CLASS B: supports 65,000 hosts on each of 16,000 networks.
CLASS C: supports 254 hosts on each of 2 million networks.
Technical Manual
F.01U.193.291
Rev. 06
Page 40

36 RVON-16
LAN A LAN is a computer network that connects a relatively small area (a single building or group
of buildings). Most LANs connect work stations and computers to each other. Each c omputer
(also known as a “node”) has its own processing unit and executes its own programs;
however, it can also access data and devices anywhere on the LAN. This means that many
users can access and share the same information and devices. A good example of a LAN
device is a network printer. Most companies cannot afford the budgetary or hardware expense
of providing printers for each of its users; therefore, one printer, (i.e., device) is placed on the
LAN where every user can access the same printer.
The LAN uses IP addresses to route data to different destinations on the network. An IP
address is a 32-bit numeric address written as four numbers separated by per i ods (for
example, 1.160.10.240).
Port A port, when referring to TCP and UDP networks, is an endpoint in a logical connection. The
port number identifies the type of port it is. For example, port 80 is used for HTTP traffic.
Routers A router is a device that forwards data packets over networks. Most commonly, a router is
connected to at least two (2) networks (normally LANs or WANs). Routers are located at
gateways, the place where two networks are connected. Routers do little data filtering, they
mainly deliver the data.
Subnet A subnet is a portion of a network that shares a common address component. On a TCP/IP
network, a subnet is described as all computers or devices wh ose IP Address have the same
prefix.
Subnetting a network is useful because it provides security for the network, as well as,
increases performance of the network. IP networks are divided using subnet masks.
Switches A switch is a device that filters and forwards data packets between networks. Switches
operate at the data layer, and sometimes at the network layer.
WAN A wide area network connects two or more LANs and can span a relatively large geographical
area. For example, Telex Headquarters in Burnsville, MN is connected to several branch
offices in Nebraska and Arkansas over the wide are a network. The largest WAN is the
Internet.
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 41

In this chapter, find the following drawings:
• AZedit Via RVON-8 RS-232 Mode
• CS9500 Trunking Via RVON-I/O To RVON-8
• ADAM Trunking Via RVON-8
• Zeus II Trunking Via RVON-I/O To RVON-C
• Cronus Trunking Via RVON-I/O To RVON-8
APPENDIX A
RV ON Trunking Connections
Bosch Security Systems, Inc.
Te chnical Manual
F . 01U.193.291
Rev. 06
Page 42

38 RVON-16
Bosch Security Systems, Inc.
Technical Manual
F . 01U.193.291
Rev. 06
Page 43

RVON-16 39
FIGURE 9. AZedit Via RVON-8 RS-232 Mode
Bosch Security Systems, Inc.
Technical Manual
F. 01U.193.291
Rev. 06
Page 44
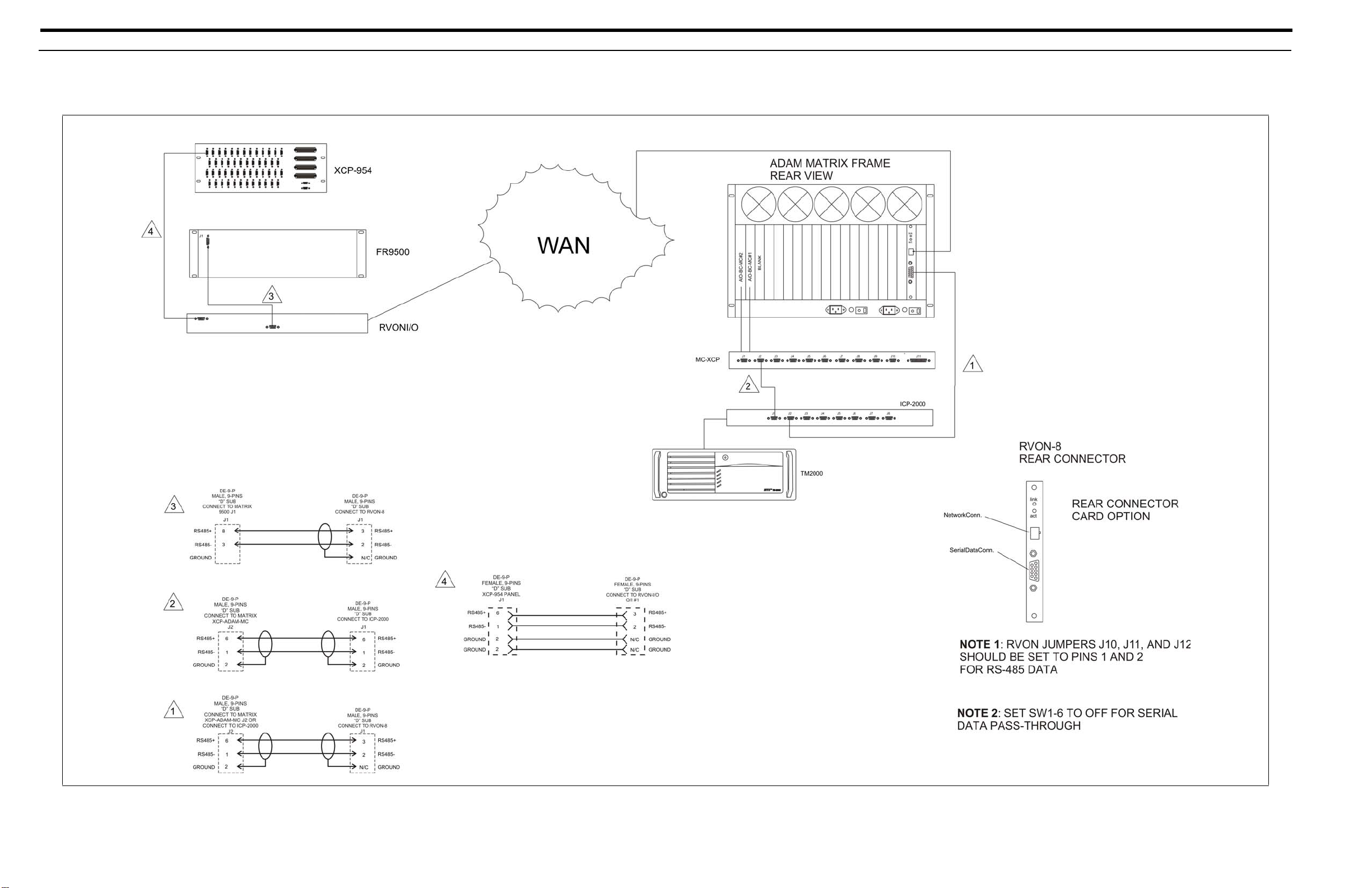
40 RVON-16
FIGURE 10.
CS9500 Trunking Via RVON-I/O To RVON-8
Rev. 06
F. 01U.193.291
Te chnical Manual
Bosch Security Systems, Inc.
Page 45

RVON-16 41
FIGURE 11. ADAM Trunking Via RVON-8
Bosch Security Systems, Inc.
Technical Manual
F. 01U.193.291
Rev. 06
Page 46

42 RVON-16
FIGURE 12.
Zeus II Trunking Via RVON-I/O to RVON-C
Rev. 06
F. 01U.193.291
Te chnical Manual
Bosch Security Systems, Inc.
Page 47

RVON-16 43
FIGURE 13. Cronus Trunking Via RVON-I/O To RVON-8
Bosch Security Systems, Inc.
Technical Manual
F. 01U.193.291
Rev. 06
Page 48

44 RVON-16
FIGURE 14.
RVON-16 Trunking
Rev. 06
F. 01U.193.291
Te chnical Manual
Bosch Security Systems, Inc.
Page 49

RVON-16 45
Notes
Bosch Security Systems, Inc.
Technical Manual
F. 01U.193.291
Rev. 06
Page 50

Bosch Security Systems, Inc.
12000 Portland Avenue South
Burnsville, MN 55337 U.S.A.
www.boschcommunications.com
 Loading...
Loading...