
R&S®ZNB/ZNBT/ZNC/ZND
Vector Network Analyzer
Instrument Security Procedures
(;ÙÎ32)
1175640302
Version 07
Instrument Security Procedures

R&S®ZNB/ZNBT/ZNC/ZND
Contents
1 Overview................................................................................................. 2
2 Instrument Models Covered..................................................................2
3 Security Terms and Definitions............................................................ 3
4 Types of Memory and Information Storage......................................... 4
5 Instrument Declassification.................................................................. 6
6 Special Considerations for USB Ports.................................................8
Contents
1 Overview
It is often imperative that R&S ZNB/ZNBT/ZNC/ZND Vector Network Analyzers are
used in a secured environment. Generally these highly secured environments do not
allow any test equipment to leave the area unless it can be proven that no user information leaves with the test equipment. Security concerns can arise when devices need
to leave a secured area, e.g. to be calibrated or serviced.
This document describes the types of memory and their usage in the R&S ZNB/
ZNBT/ZNC/ZND. It provides a statement regarding the volatility of all memory types
and specifies the steps required to declassify an instrument through memory clearing
or sanitization procedures. These sanitization procedures are designed for customers
who need to meet the requirements specified by the US Defense Security Service
(DSS).
2 Instrument Models Covered
Table 2-1: Vector Network Analyzer models
Vector Network Analyzer
R&S ZNB4 - 2 port 1311.6010.22
R&S ZNB4 - 4 port 1311.6010.24
R&S ZNB8 - 2 port 1311.6010.42
R&S ZNB8 - 4 port 1311.6010.44
R&S ZNB20 - 2 port 1311.6010.62
R&S ZNB20 - 4 port 1311.6010.64
2Instrument Security Procedures 1175.6403.02 ─ 07

R&S®ZNB/ZNBT/ZNC/ZND
Vector Network Analyzer
R&S ZNB40 - 2 port 1311.6010.72
R&S ZNB40 - 2 port 1311.6010.82
R&S ZNB40 - 4 port 1311.6010.84
R&S ZNBT8 - up to 24 ports 1318.7006.24
R&S ZNBT20 - up to 24 ports 1332.9002.24
R&S ZNBT26 - up to 24 ports 1332.9002.34
R&S ZNBT40 - up to 24 ports 1332.9002.44
R&S ZNC3 1311.6004.12
R&S ZND 1328.5170.92
Security Terms and Definitions
3 Security Terms and Definitions
Clearing
The term "clearing" is defined in Section 8-301a of DoD 5220.22-M, "National Industrial
Security Program Operating Manual (NISPOM)". Clearing is the process of eradicating
the data on media so that the data can no longer be retrieved using the standard interfaces on the instrument. Therefore, clearing is typically used when the instrument is to
remain in an environment with an acceptable level of protection.
Sanitization
The term "sanitization" is defined in Section 8-301b of DoD 5220.22-M, "National
Industrial Security Program Operating Manual (NISPOM)". Sanitization is the process
of removing or eradicating stored data so that the data cannot be recovered using any
known technology. Instrument sanitization is typically required when an instrument is
moved from a secure to a non-secure environment, such as when it is returned for service of calibration.
The memory sanitization procedures described in this document are designed for customers who need to meet the requirements specified by the US Defense Security Service (DSS). These requirements are specified in the "Clearing and Sanitization Matrix"
in Section 14.1.16 of the ISFO "Manual for the Certification and Accreditation of Classified Systems under the NISPOM".
Instrument declassification
The term "instrument declassification" refers to procedures that must be undertaken
before an instrument can be removed from a secure environment, for example when
the instrument is returned for calibration. Declassification procedures include memory
sanitization or memory removal, or both. The declassification procedures described in
this document are designed to meet the requirements specified in DoD 5220.22-M,
"National Industrial Security Program Operating Manual (NISPOM)", Chapter 8.
3Instrument Security Procedures 1175.6403.02 ─ 07

R&S®ZNB/ZNBT/ZNC/ZND
4 Types of Memory and Information Storage
Vector Network Analyzers R&S ZNB/ZNBT/ZNC/ZND contain various memory components.
The following table provides an overview of the memory components that are part of
your instrument. For a detailed description regarding type, size, usage and location,
refer to the subsequent sections.
Types of Memory and Information Storage
Volatile Memory
Memory type Size Content Volatility User
Data
●
SDRAM (CPU
board)
EEPROM
(board assembly)
or
Flash (board
assembly)
HDD or SSD
(removable
system drive)
R&S ZNB:
2 Gbyte or
8 Gbyte
●
R&S ZNBT:
8 Gbyte
●
R&S ZNC:
2 Gbyte or
4 Gbyte
●
R&S ZND:
4 Gbyte
Up to 32 Mbyte
128 to 500 Gbyte
Temporary information storage for operating system
and instrument firmware
●
Hardware information:
– Serial number
– Product options
– Calibration cor-
●
FPGA configuration data
●
●
●
●
●
●
●
rection data
BIOS
Operating system
Instrument firmware
Instrument states and
setups
Limit lines
User calculation data
Trace data
Measurement results
and screen images
Volatile Yes Turn off
Non-volatile
Non-volatile
No None
Yes Remove sys-
Sanitization
procedure
instrument
power
required (no
user data)
tem drive
from instrument
4.1 Volatile Memory
The volatile memory in the instrument does not have battery backup. It loses its contents as soon as power is removed from the instrument. The volatile memory is not a
security concern.
Removing power from this memory meets the memory sanitization requirements specified in the "Clearing and Sanitization Matrix" in Section 5.2.5.5.5 of the ISFO Process
Manual for the Certification and Accreditation of Classified Systems under the NISPOM.
4Instrument Security Procedures 1175.6403.02 ─ 07

R&S®ZNB/ZNBT/ZNC/ZND
SDRAM
The size of the SDRAM on the CPU board depends on the Vector Network Analyzer
model:
●
The R&S ZNB is equipped with 2 Gbyte or 8 Gbyte of SDRAM.
●
The R&S ZNBT is equipped with 8 Gbyte of SDRAM.
●
The R&S ZNC is equipped with 2 Gbyte or 4 Gbyte of SDRAM.
●
The R&S ZND is equipped with 4 Gbyte of SDRAM.
It contains temporary information storage for operating system and instrument firmware. The SDRAM loses its memory as soon as power is removed.
Sanitization procedure: Turn off instrument power
4.2 Non-Volatile Memory
The R&S ZNB/ZNBT/ZNC/ZND contains various non-volatile memories. Out of these,
only the removable system drive (HDD or SSD) contains user data. The system drive
can be physically removed from the R&S ZNB/ZNBT/ZNC/ZND and left in the secure
area.
Types of Memory and Information Storage
Non-Volatile Memory
All non-volatile memories of the R&S ZNB/ZNBT/ZNC/ZND are not a security concern.
EEPROM/Flash
Each board assembly in the R&S ZNB/ZNBT/ZNC/ZND Vector Network Analyzer has
either a serial EEPROM device or a Flash memory device. The EEPROM/Flash has a
size of 32 Mbyte.
The EEPROM contains the BIOS and information related to the installed hardware,
such as board serial number, product options and calibration correction data.
The Flash memory devices hold the FPGA configuration data.
The EEPROM/Flash does not hold user data nor can the user access the storage.
Sanitization procedure: None required (no user data)
HDD/SDD
The R&S ZNB/ZNBT/ZNC/ZND Vector Network Analyzer is equipped with a removable
system drive (HDD or SDD).
The system drive is used to store:
●
Instrument operating system
●
Instrument firmware and firmware options (measurement personalities) with option
license keys
●
Instrument states and setups
●
Limit lines
●
Trace data
5Instrument Security Procedures 1175.6403.02 ─ 07

R&S®ZNB/ZNBT/ZNC/ZND
●
User calculation data
●
Screen images
The system drive can hold user data and is non-volatile. Hence, user data is not
erased when power is removed from the instrument.
The removable system drive can be removed from the Vector Network Analyzer to
make sure that no user data is stored within the Vector Network Analyzer.
With its removable system drive the R&S ZNB/ZNBT/ZNC/ZND Vector Network Analyzer addresses the needs of customers working in secured areas.
Sanitization procedure: Remove system drive from instrument
5 Instrument Declassification
Instrument Declassification
Before you can remove the Vector Network Analyzer from a secured area (for example
to perform service or calibration), all classified user data needs to be removed. You can
declassify the Vector Network Analyzer as follows:
1. Turn off the Vector Network Analyzer and disconnect the power plug. This will sanitize the volatile memory.
2. To remove the classified system drive (HDD or SSD containing user data), perform
the following steps:
6Instrument Security Procedures 1175.6403.02 ─ 07
R&S®ZNB/ZNBT/ZNC/ZND
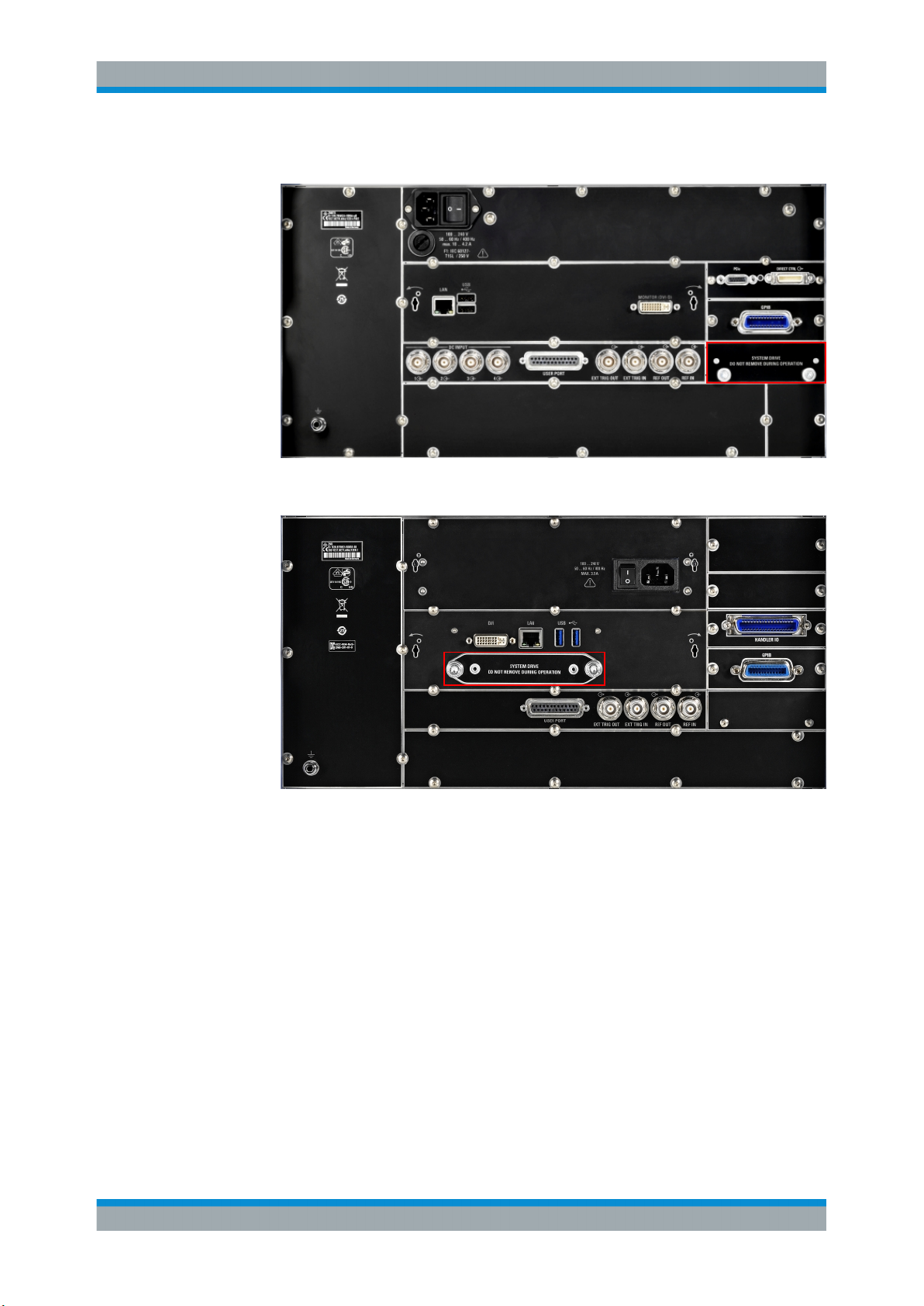
a) Locate the system drive at the rear of the instrument.
Figure 5-1: Location of the system drive for R&S ZNB/ZNBT/ZNC
Instrument Declassification
Figure 5-2: Location of the system drive for R&S ZND
b) Unscrew the two knurled screws.
c) Remove the system drive.
Following these steps removes all user data from the Vector Network Analyzer. The
Vector Network Analyzer can now leave the secured area.
These declassification procedures meet the needs of customers working in secured
areas.
Once the Vector Network Analyzer is outside the secured area, installing a second
non-classified removable system drive (without any user data) allows the Vector Network Analyzer to function properly for service or other needs (options R&S ZNB/
ZNBT/ZNC/ZND-B19).
Prior to re-entering the secured area, the non-classified removable system drive (without the user data), is removed. When the Vector Network Analyzer is back within the
secured area, the original classified removable system drive can be reinstalled.
7Instrument Security Procedures 1175.6403.02 ─ 07

R&S®ZNB/ZNBT/ZNC/ZND
●
To hold classified user data in secure areas, use the removable system drive which
comes with the instrument.
●
To hold non-classified user data in non-secure areas, use a second removable system drive (R&S ZNB/ZNBT/ZNC/ZND-B19).
Validity of instrument calibration after declassification
The calibration makes sure that measurements comply to government standards.
Rohde & Schwarz recommends that you follow the calibration cycle suggested for your
instrument.
The Flash/EEPROM is the only memory type used to hold permanent adjustment values required to maintain the validity of the R&S ZNB/ZNBT/ZNC/ZND's calibration.
Therefore, replacing one removable system drive (HDD or SSD) with another, does not
affect the validity of the instrument’s calibration.
Special Considerations for USB Ports
6 Special Considerations for USB Ports
USB ports can pose a security risk in high-security locations. Generally, this risk comes
from small USB pen drives, also known as memory sticks or key drives. They can be
easily concealed and can quickly read/write several Gbyte of data.
Disabling USB ports for writing user data
You can disable the write capability on the USB ports of the R&S ZNB/ZNBT/ZNC/ZND
via a utility software. This utility software is available on the R&S ZNB/ZNBT/ZNC/ZND
website https://www.rohde-schwarz.com/product/znb.html, https://www.rohde-
schwarz.com/product/znbt.html, https://www.rohde-schwarz.com/product/znc.html and
https://www.rohde-schwarz.com/product/znd.html.
To disable the write capability, copy the utility software to the R&S ZNB/
ZNBT/ZNC/ZND and run it once. After a reboot of the instrument, the write capability
on any USB memory device is disabled.
© 2019 Rohde & Schwarz GmbH & Co. KG
Mühldorfstr. 15, 81671 München, Germany
Phone: +49 89 41 29 - 0
Fax: +49 89 41 29 12 164
Email: info@rohde-schwarz.com
Internet: www.rohde-schwarz.com
Subject to change – Data without tolerance limits is not binding.
R&S® is a registered trademark of Rohde & Schwarz GmbH & Co. KG.
Trade names are trademarks of the owners.
Throughout this manual, products from Rohde & Schwarz are indicated without the ® symbol , e.g. R&S®ZNB
is indicated as R&S ZNB.
8Instrument Security Procedures 1175.6403.02 ─ 07
 Loading...
Loading...