Page 1

TrustedTM
PD-T8019
TM
Trusted
Process Control Algorithm
Software Package
Introduction
M
The system architecture of the Trusted
interlock applications as is possible. The control algorithms detailed in this Product Description are
primarily intended to support the limited process control capabilities required for Floating Production,
Storage and Offloading (FPSO) installations. The algorithms may also be used for other process
control applications as required.
Control functions require the use of floating point values. This ultimately limits the integrity that can be
attributed to these functions because of the introduction of an element of “loss of precision” and the
general inability to exhaustively verify floating-point capabilities.
T
is intended to cover as large a cross section of control and
The functions are integrated into the IEC1131 TOOLSET execution environment. This environment is
“Commercial-Off-The-Shelf (COTS)” and designed to commercial standards. The overall system
achieves higher levels of integrity by the use of additional on-line monitoring and internal state control.
The combination of the above factors indicate that the target integrity for the basic process control
functions should be SIL1 (AK3). These functions should therefore NOT be used within elements of
application programs intended for SIL3 (AK6) use.
TM
The control algorithms are executed within the Trusted
program and are divided into ‘functions’ and ‘function blocks’.
‘Functions’ are those algorithms with no internal state, or time dependent operation, i.e. they have no
storage element. The functions process the defined number of parameters and return a single
resultant state or value. Functions, therefore, have only a single operating mode, always performing
the same operation.
The ‘function blocks’ include retentive information and may return multiple values. Function blocks will
have an initial state or value for each of their outputs. The initial value may be maintained for a single
or multiple application iterations, depending on the detail of the algorithms.
Controller as part of the standard application
Issue 8 Sep 07 PD-T8019 1
Page 2
Trusted
Issue Record
Issue
Number Date Revised by Technical CheckAuthorised by Modification
6 Oct 05 J W Clark Format
7 Dec 06 N Owens I Vince P Stock Example PID loop
8 Sep 07 N Owens I Vince P Stock Corrections
TM
Process Control Algorithms T8019
Issue 8 Sep 07 PD-T8019 2
Page 3

Trusted
TM
Process Control Algorithms T8019
This page is intentionally blank
Issue 8 Sep 07 PD-T8019 3
Page 4

Trusted
TM
Process Control Algorithms T8019
Table of Contents
1. Description...................................................................................................................................7
1.1. Functions .....................................................................................................................................8
1.1.1. Square Root Extraction................................................................................................................8
1.2. BCD Translation...........................................................................................................................9
1.3. Analogue Select.........................................................................................................................10
1.4. Multiple Value Averaging ...........................................................................................................10
1.5. Drum Level Control....................................................................................................................11
1.6. Mass Flow Computation ............................................................................................................11
2. Function Blocks .........................................................................................................................12
2.1. Analogue Scaling .......................................................................................................................12
2.2. Analogue Value Clamping .........................................................................................................13
2.3. Low Value Select .......................................................................................................................13
2.4. High Value Select ......................................................................................................................14
2.5. Median Value Select ..................................................................................................................14
2.6. Proportional PID Function..........................................................................................................15
2.7. Incremental PID Function ..........................................................................................................17
2.8. Deviation Alarm..........................................................................................................................19
2.9. Manual Tracking ........................................................................................................................19
2.10. Time Averaged Value ................................................................................................................20
2.11. Rate of Change Detection..........................................................................................................22
2.12. Analogue Value Slew.................................................................................................................24
3. Other Functions .........................................................................................................................25
3.1. Lead/Lag Control .......................................................................................................................25
4. Sample Application Program .....................................................................................................26
Figures
Figure 1 PID Function.............................................................................................................................16
Figure 2 IPID Function............................................................................................................................18
Figure 3 Sample Application Program ....................................................................................................26
Tables
Table 1 Error Statistics .............................................................................................................................7
Table 2 BCD Translation ..........................................................................................................................9
Table 3 Example Time Average .............................................................................................................21
Issue 8 Sep 07 PD-T8019 4
Page 5

Trusted
TM
Process Control Algorithms T8019
Notice
The content of this document is confidential to ICS Triplex Technology Ltd. companies and their
partners. It may not be given away, lent, resold, hired out or made available to a third party for any
purpose without the written consent of ICS Triplex Technology Ltd.
his document contains proprietary information that is protected by copyright. All rights are reserved.
T
Microsoft, Windows, Windows 95, Windows NT, Windows 2000, and Windows XP are registered
trademarks of Microsoft Corporation.
The information contained in this document is subject to change without notice. The reader should, in
all cases, consult ICS Triplex Technology Ltd. to determine whether any such changes have been
made. From time to time, amendments to this document will be made as necessary and will be
distributed by ICS Triplex Technology Ltd.
Information in this documentation set may be subject to change without notice and does not represent
a commitment on the part of ICS Triplex Technology Ltd.
The contents of this document, which may also include the loan of software tools, are subject to the
confidentiality and other clause(s) within the Integrator Agreement and Software License Agreement.
No part of this documentation may be reproduced or transmitted in any form or by any means,
electronic or mechanical, including photocopying and recording, for any purpose, without the express
written permission of ICS Triplex Technology Ltd.
Disclaimer
The illustrations, figures, charts, and layout examples in this manual are intended solely to illustrate the
text of this manual.
The user of, and those responsible for applying this equipment, must satisfy themselves as to the
acceptability of each application and use of this equipment.
This document is based on information available at the time of its publication. While efforts have been
made to be accurate, the information contained herein does not purport to cover all details or variations
in hardware or software, nor to provide for every possible contingency in connection with installation,
operation, or maintenance. Features may be described herein which are present in all hardware or
software systems. ICS Triplex Technology Ltd. assumes no obligation of notice to holders of this
document with respect to changes subsequently made.
ICS Triplex Technology Ltd. makes no representation or warranty, expressed, implied, or statutory with
respect to, and assumes no responsibility for the accuracy, completeness, sufficiency, or usefulness of
the information contained herein. No warranties of merchantability or fitness for purpose shall apply.
Issue 8 Sep 07 PD-T8019 5
Page 6

Trusted
TM
Process Control Algorithms T8019
Revision and Updating Policy
All new and revised information pertinent to this document shall be issued by ICS Triplex Technology
Ltd. and shall be incorporated into this document in accordance with the enclosed instructions. The
change is to be recorded on the Amendment Record of this document.
Precautionary Information
WARNING
Warning notices call attention to the use of materials, processes, methods, procedures or limits which
must be followed precisely to avoid personal injury or death.
CAUTION
Caution notices call attention to methods and procedures which must be followed to avoid damage to
the equipment.
Notes:
Notes highlight procedures and contain information to assist the user in the understanding of the
information contained in this document
Warning
RADIO FREQUENCY INTERFERENCE
Most electronic equipment is influenced by Radio Frequency Interference (RFI). Caution should be
exercised with regard to the use of portable communications equipment around such equipment.
Signs should be posted in the vicinity of the equipment cautioning against the use of portable
communications equipment.
MAINTENANCE
Maintenance must be performed only by qualified personnel, otherwise personal injury or death, or
damage to the system may be caused.
Caution
HANDLING
Under no circumstances should the module housing be removed.
Associated Documents
Product Descriptions (PD) provide product specific information.
The Safety Manual contains the recommended safety requirements for the safety system design.
The PD8082B – Toolset Suite provides specific guidance on system configuration and application
generation.
The Operator and Maintenance Manual contains general guidelines on maintenance and diagnostic
procedures.
For technical support email: support@icstriplex.com
Issue 8 Sep 07 PD-T8019 6
Page 7
Trusted
TM
Process Control Algorithms T8019
1. Description
Several of the basic control algorithms may generate error conditions at run-time as all function
arameters are variable. This may result in reversed parameters, e.g. max < min, overflow and
p
underflow conditions, divide by zero errors, etc. For each function, the required output under these
conditions is defined and error counters are incremented. These error counters are available to the
application programmer using the error statistics function block.
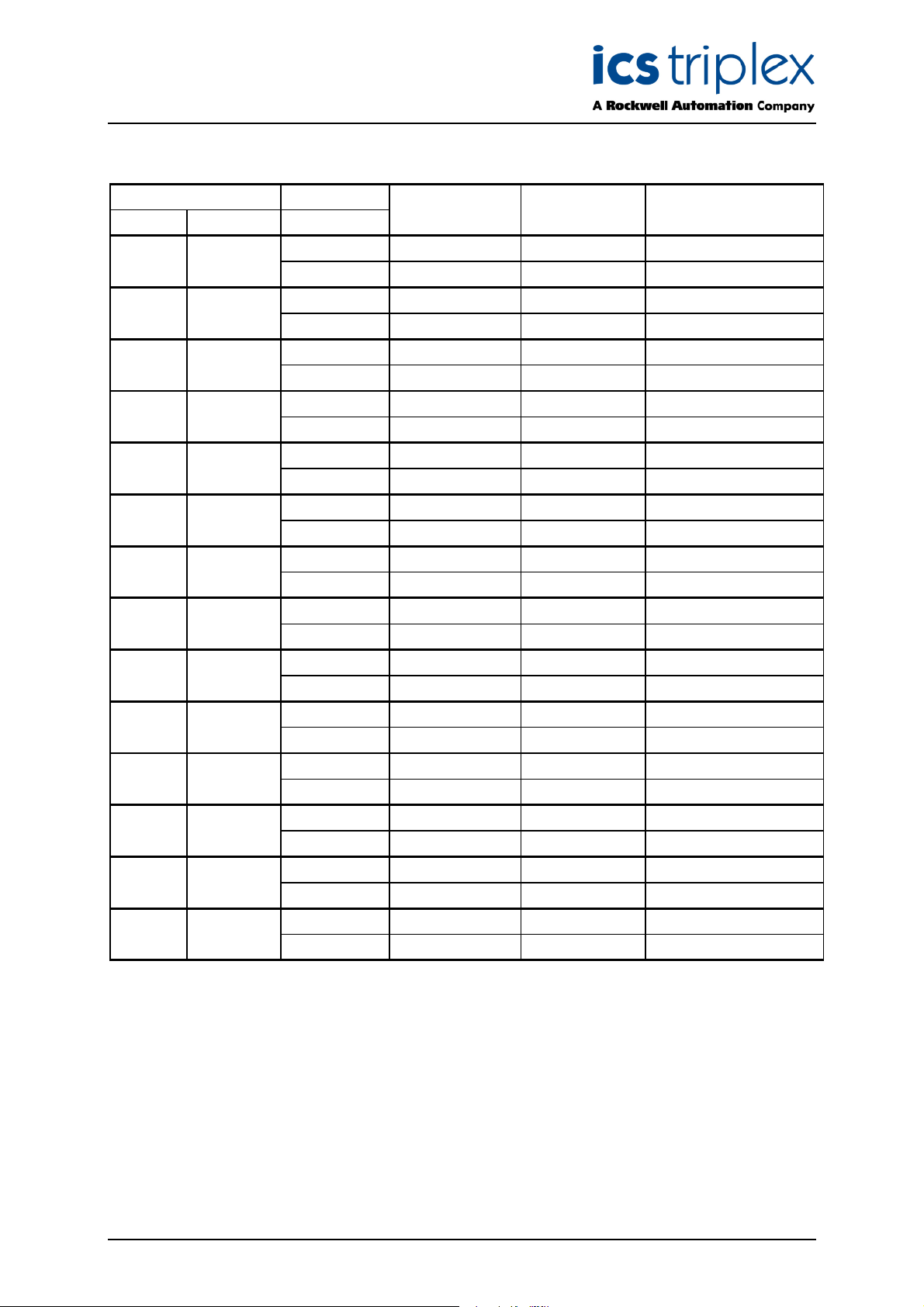
The function block has a single Boolean input that is used to reset the counters. Whilst this input is
true, the error counters will be reset to zero. The initial value of all error counters is zero.
eversed
RESET
ERRSTAT
R
Param
Overflow
Underflow
Data types are
1. RESET Boolean
2. All others Integer
Output Error condition
Reversed Pairs of function parameters are reversed, i.e. max<min.
Param A function parameter is incorrect, e.g. out of range or not
Overflow An overflow error occurred in the execution of the function.
Underflow An underflow error occurred in the execution of the function.
Zero Divide A divide by zero error occurred in the execution of the
Zero Divide
The associated function has reversed the two values in order
to obtain a valid result. The count is incremented on each
iteration of the function whilst the parameters are reversed.
consistent with the functions required operation. The count
is incremented on each iteration of the function whilst the
parameter is incorrect.
The count is incremented on each iteration of the function
whilst the overflow condition occurs.
The count is incremented on each iteration of the function
whilst the underflow condition occurs.
function. The count is incremented on each iteration of the
function whilst the divide by zero condition occurs.
Table 1 Error Statistics
Issue 8 Sep 07 PD-T8019 7
Page 8
Trusted
()(
)
TM
Process Control Algorithms T8019
1.1. Functions
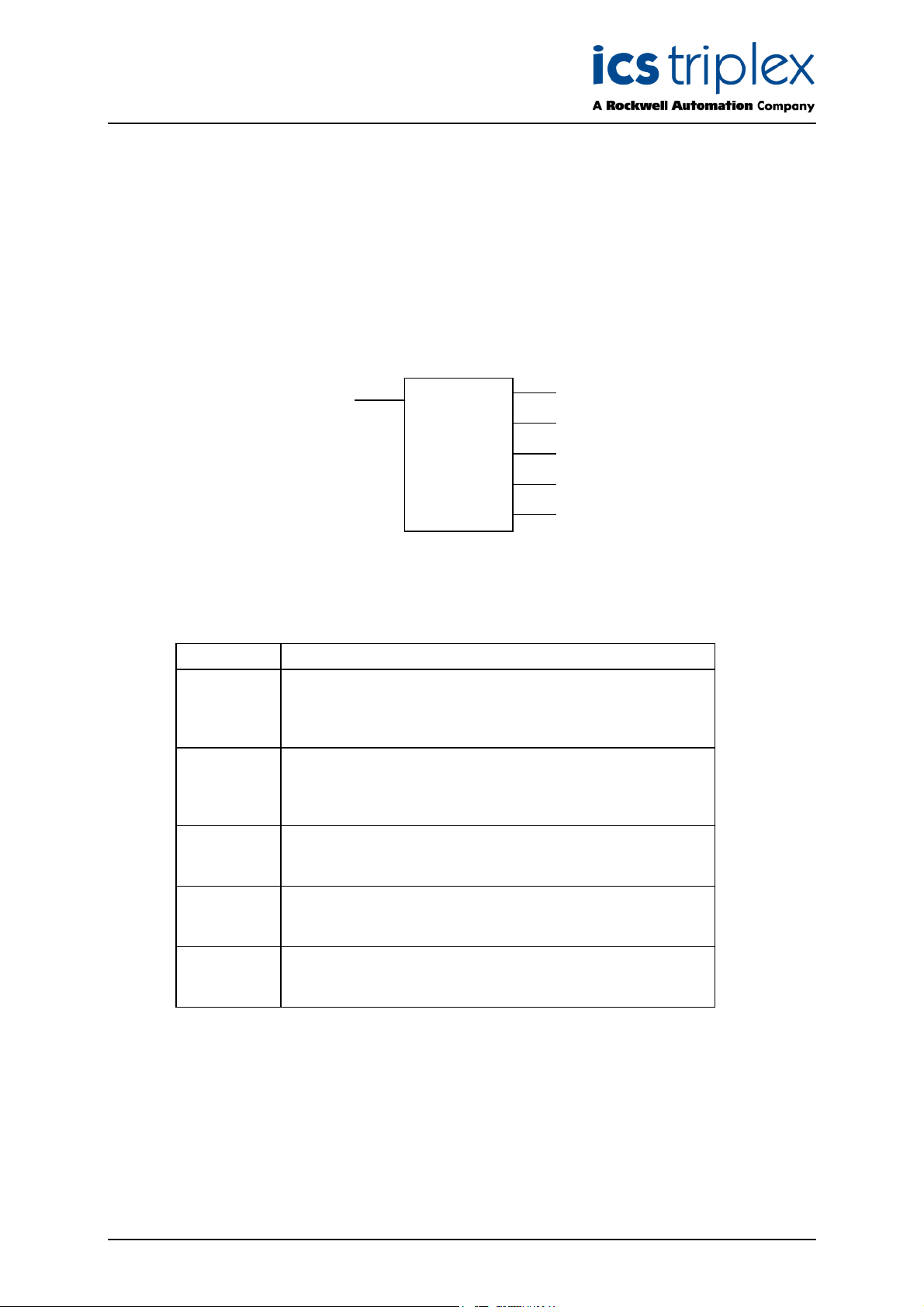
1.1.1. Square Root Extraction
SQRTX
OUT
IP
IP
PV
MAX
MIN
The Process Variable (PV) is scaled to a value 0…1 according to maximum input value (IP
minimum input value (IP
i.e. a value greater than maximum input will use the IP
will use the IP
value. The square root of the resulting value is then taken and is returned as a
MIN
). Out of range values will result in the value being clamped to the range,
MIN
value, similarly a value below the minimum
AX
M
MAX
) and
percentage.
i.e.
IPIP,IPPV,MaxMin
MINMAXMIN
100
×
Note: All inputs (PV, IP
If IP
MAX
< IP
, the function assumes that the values have been reversed and “swap” the values. The
MIN
MIN
OUT
=
and IP
IP -IP
MINMAX
) and the returned value OUT must be real.
MAX
“reversed” error counter is incremented each time the function has to swap the parameters.
If IP
MAX
= IP
, the function returns a value of zero and increments the “zero divide” error counter to
MIN
indicate that a divide by zero error would have occurred.
If PV is not a number (NaN), the function returns a value of zero and increments the “Param” error
counter.
All input range parameters (IP
MIN
and IP
) must be finite, i.e. not ±infinities or NaNs. Behaviour is not
MAX
defined for any other values.
If PV is not a NaN, and an overflow or underflow condition occurs the function returns zero and
increment the corresponding error counter.
Issue 8 Sep 07 PD-T8019 8
Page 9
Trusted
()(
)
TM
Process Control Algorithms T8019
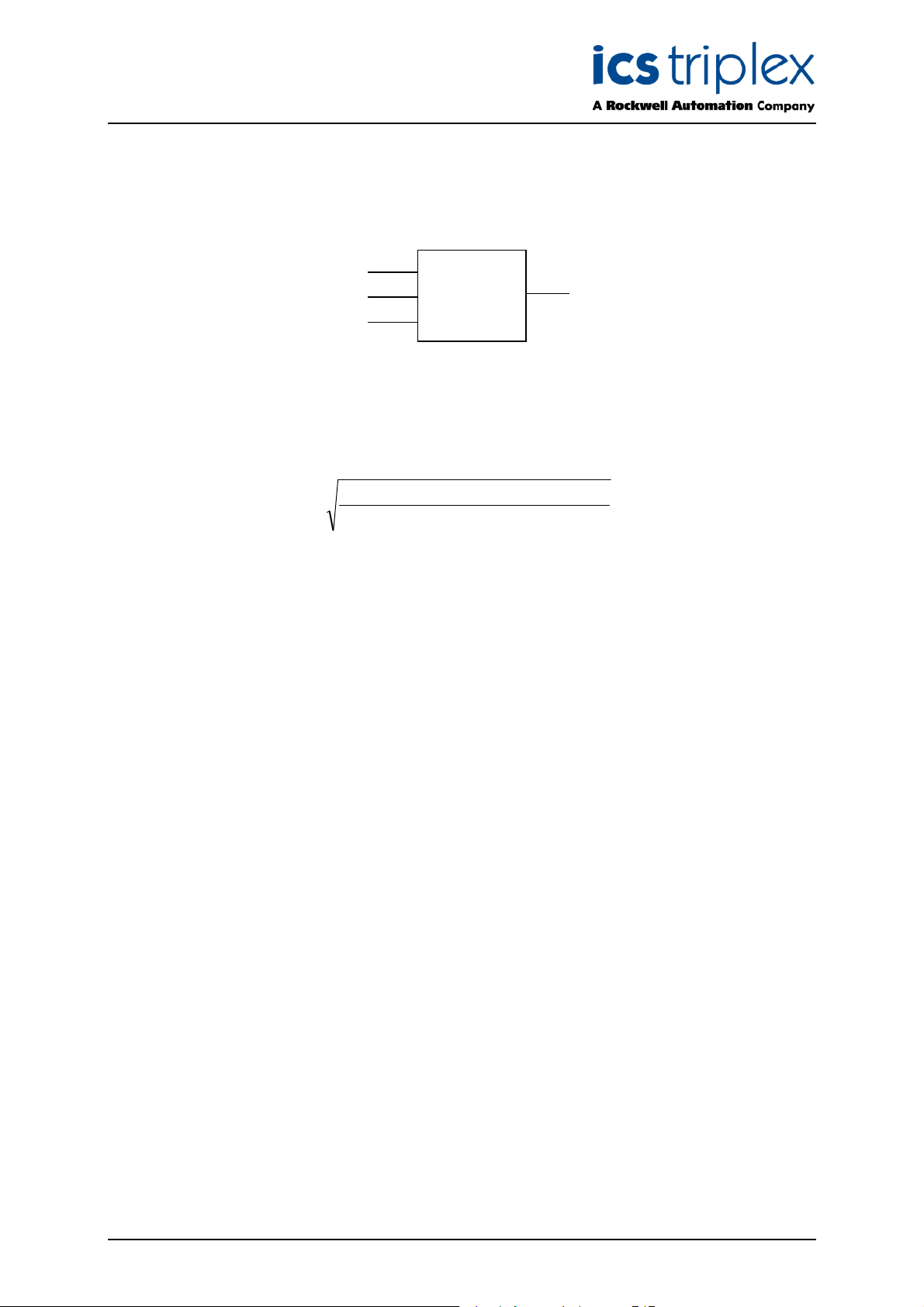
1.2. BCD Translation
IP0
I
P1
IP2
IP3
M
N
The BCD translation function requires the 4-bit BCD value represented as 4 Boolean parameters (IP0,
IP1, IP2, and IP3), IP0 being the least significant bit, IP3 the most significant bit. All four inputs must
be defined; inputs not required for specific application must be set to FALSE. M and N are of type
integer.
M specifies the value multiplier and must be a power of 10, i.e. 1, 10, 100, etc. N allows the BCD
functions to be cascade, by adding the value from a previous function. A value of -1 is assumed to be
the result of an up-stream conversion error and will result in all chained BCD functions generating
values of -1. The returned value OUT is an integer.
BCD
OUT
NMIP3IP2,IP1,IP0,BCDOUT +×=
Invalid BCD number (see table below) are to result in OUT = -1.
IP3
IP2
IP1
IP0
OUT
(with M=1 and N=0)
0 0 0 0 0
0 0 0 1 1
0 0 1 0 2
0 0 1 1 3
0 1 0 0 4
0 1 0 1 5
0 1 1 0 6
0 1 1 1 7
1 0 0 0 8
1 0 0 1 9
1 0 1 0 -1
1 0 1 1 -1
1 1 0 0 -1
1 1 0 1 -1
1 1 1 0 -1
1 1 1 1 -1
Table 2 BCD Translation
Multiple values (M) that are not powers of 10 are to result in a value of -1. If an overflow condition
occurs, the function is to return a value of -1 and increment the “Overflow”, error counter.
Issue 8 Sep 07 PD-T8019 9
Page 10

Trusted
TM
Process Control Algorithms T8019
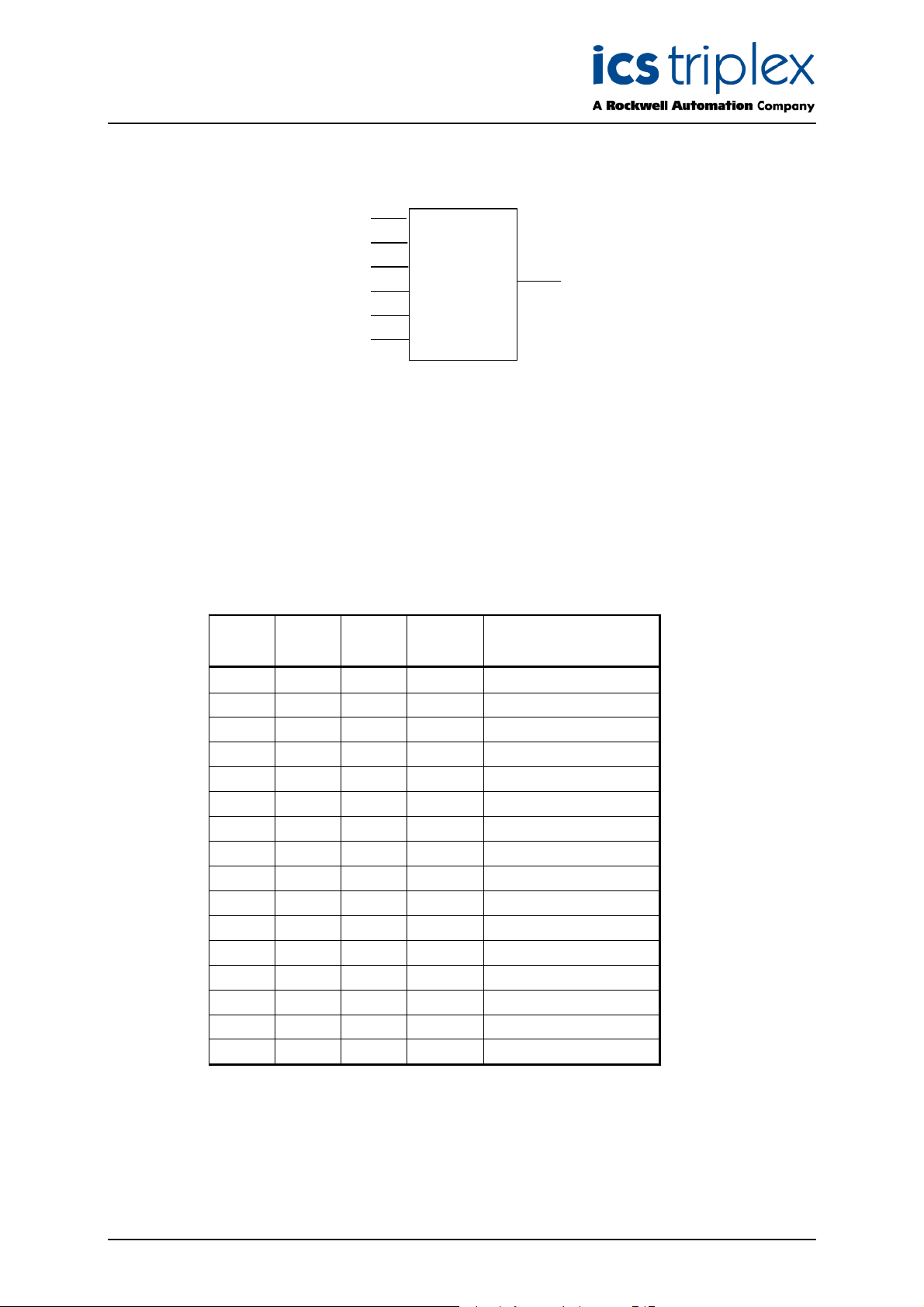
1.3. Analogue Select
SEL
PV1
PV2
R_SEL
OUT
The process variables (PV1 and PV2) and the output (OUT) must all be of type REAL
1
. The select
signal (SEL) is of type BOOLEAN. When SEL is FALSE, PV1 is copied to the output; when SEL is
TRUE, PV2 is copied to the output.
if SEL
Set OUT = PV2
else
Set OUT = PV1
end if
Out is finite if, and only if, the selected PV1 or PV2 is finite.
1.4. Multiple Value Averaging
N
PV1
PV2
PV3
PV4
PV5
PV6
PV7
PV8
PV9
PV10
AVG
OUT
The multiple value averaging calculates the average of between 1 and 10 values (PV1 to PV10). N
specifies the number of values averaged; the first N values are averaged. E.g. if N=3, the average of
PV1, PV2 and PV3 is returned. N is of type INTEGER, PV1 to PV10 and OUT are of type REAL. All
input values must be connected; unused inputs should be tied to either one of the other used inputs or
a constant value.
If the value of N is out of range, i.e. 1>N>10, the average of all ten input values is to be returned and
the “param” error count incremented. Overflow errors occurring whilst calculating the average are to
result in a value of PV1 being returned and the “overflow” error count incremented. If an “underflow”
condition occurs, the function is to set OUT to zero and increment the “underflow” error counter.
1
Issue 8 Sep 07 PD-T8019 10
The standard ISaGRAF SEL function provides the equivalent operation for integer values.
Page 11

Trusted
LV
(
)
(
)
(
)
(
)
TM
Process Control Algorithms T8019
1.5. Drum Level Control
PP
This function is to provide the pressure compensated drum level. PP is the differential pressure, and
LV is the level in percentage of full-scale, the output (OUT) is return as a value 0 to 100%. PP, LV and
OUT are all of type REAL. The function additionally to compensates for the reverse acting output of the
level input (increasing PP value of decreasing differential pressure).
OUT
=
Underflow, overflow and divide by zero error conditions are to result in value of zero being returned and
the corresponding error counter incremented.
PC_DRUM
OUT
3
LV P105.43101
××
3
P100.1730.88
××
1.6. Mass Flow Computation
Error! Objects cannot be created from editing field codes.
The mass-flow computation block provides the mass flow corrected for the current operating
conditions.
hemZCOUT
+
××××××=
()
+
14.7P
273T
PP is the differential pressure, P is pressure and T is temperature. C, Z, m, e and h are intended to be
constant values. All parameters are of type REAL.
0
PP and P are in psi, T is in
If T=-273, a divide by zero error condition is generated, this is to increment the associated error
counter and the mass flow function is to return a value of -1. Over and underflow conditions are to
result in an output value of -1 and increment the associated error counter.
C.
Issue 8 Sep 07 PD-T8019 11
Page 12

Trusted
PV
MAX
MAX
()(
)
TM
Process Control Algorithms T8019
2. Function Blocks
2.1. Analogue Scaling
SCALE
IP
OUT
OUT
IP
MIN
M
IN
OUT
LIMIT
The scale function linearly scales the input value (PV) according to the low input (IP
), low output (OUT
(IP
AX
M
to IP
IP
MIN
greater than IP
between OUT
. I.e. a PV value less than IP
MAX
results in the IP
MAX
and OUT
MIN
indicate that the input value (PV) is out of range, i.e LIMIT = IP
) and high output (OUT
IN
M
MIN
value being used). The output (OUT) value varies linearly
as the input (PV) varies between IP
MAX
MAX
) values. The input value is clamped to the range
AX
M
results in the IP
value being used, similarly a value
MIN
min
>PV>IP
MIN
and IP
. The LIMIT output is to
MAX
, LIMIT is set TRUE if PV
MAX
), high input
MIN
is out of range.
, IP
IP
MAX
MIN
, OUT
and OUT
MAX
are typically constants but may, in practise, use any analogue or
MIN
register value.
OUTOUTOUT
MINMINMAX
Note: PV, IP
OUT +
=
MAX
, IP
, OUT
MIN
MAX
IP-IP
and OUT
MINMAX
have to be of type REAL, the result (OUT) is returned as
MIN
IPIP,IPPV,MaxMin
MINMAXMIN
()
×
type REAL and LIMIT is of type BOOLEAN.
MAX
< IP
If IP
Similarly, if OUT
, the function is to assume that the values have been reversed and “swap” the values.
MIN
MAX
< OUT
the two values are to be swapped. In both cases, the “reversed” error
MIN
counter is to be incremented each time the function has to swap the parameters. All range parameters
, IP
(IP
MAX
MIN
, OUT
MAX
, OUT
) must be finite, i.e. not ±infinities or NaNs. Behaviour is not defined for
MIN
any other values.
If IP
MAX
= IP
, the function is to set OUT to OUT
MIN
, LIMIT to FALSE and increment the “Zero Divide”
MIN
error counter to indicate that a divide by zero error would have occurred.
If PV is a NaN, the function is to set OUT to OUT
, LIMIT to FALSE and increment the “Param” error
MIN
counter. If PV is not a NaN and overflow or underflow conditions occur during the execution of the
function, the function is to set OUT to OUT
or OUT
MAX
respectively, LIMIT to FALSE and increment
MIN
the corresponding error counter. If both overflow and underflow conditions occur, the function is to set
OUT to OUT
Issue 8 Sep 07 PD-T8019 12
, LIMIT to FALSE and increment both corresponding error counters.
MIN
Page 13

Trusted
()(
)
(
)
TM
Process Control Algorithms T8019
2.2. Analogue Value Clamping
CLAMP
OUT
LIMIT
IP
IP
MIN
PV
MAX
The process variable (PV), IP
(OUT) is clamped to the range specified by IP
Boolean, is set to TRUE if the clamp is in operation, i.e. LIMIT = IP
If IP
MAX
<IP
, the parameters are to be “swapped” and the reversed error count incremented.
MIN
Input range parameters (IP
M
IP,IPPV,MaxMin OUT =
and IP
IN
M
AX
MAXMIN
, IP
and OUT values are all of type REAL2. The output value
IN
M
) must be finite, i.e. not ±infinities or NaNs. Behaviour is
AX
M
and IP
MIN
. The LIMIT output, which is of the type
MAX
>PV>IP
MIN
MAX
.
undefined for any other values. If PV is a NaN, the function is to set OUT to OUT
“Param” error counter.
2.3. Low Value Select
PV1
PV2
The process variables (PV1 and PV2) and the output (OUT) are all REAL values
is set to the lower of the two process variable values.
LVS
OUT
SEL
and increment the
MIN
3
. The output (OUT)
PV2PV1,MINOUT =
The SEL output indicates which of the process variables is being used to generate OUT. SEL is of
type BOOLEAN, and is FALSE if using PV1 and TRUE if using PV2.
If PV1 or PV2 is a NaN, the function is to set OUT to PV1, SEL to FALSE and increment the “Param”
error counter. OUT is not a NaN if, and only if, PV1 is not a NaN and finite if, and only if, the lower of
PV1 and PV2 is finite.
2
integer values (without the limit output).
3
(without the SEL output).
The standard ISaGRAF LIMIT function provides the equivalent of the CLAMP operation for
The standard ISaGRAF MIN function provides the equivalent functionality for integer values
Issue 8 Sep 07 PD-T8019 13
Page 14

Trusted
(
)
TM
Process Control Algorithms T8019
2.4. High Value Select
PV1
PV2
The process variables (PV1 and PV2) and the output (OUT) are all REAL
the higher process variable value.
HVS
OUT
SEL
4
. The output (OUT) is set to
PV2PV1,MAXOUT =
The selected output (SEL) indicates which of the process variables is being used to generate OUT.
SEL is of type Boolean, and is FALSE if using PV1 and TRUE if using PV2.
If PV1 or PV2 is a NaN, the function is to set OUT to PV1, SEL to FALSE and increment the “Param”
error counter. OUT is not a NaN if, and only if, PV1 is not a NaN and finite if, and only if, the higher of
PV1 and PV2 is finite.
2.5. Median Value Select
PV1
PV2
PV3
DEVIATION
The median value select sets OUT to the mean of the three process variables (PV1, PV2 and PV3) if
the deviation between their values is less than the maximum (DEVIATION). If the variation in inputs is
less than the allowed deviation the LIMIT output is set to FALSE. If the input values vary by more than
DEVIATION, OUT is set to the median value and LIMIT is set to TRUE.
MVS
OUT
LIMIT
If an overflow condition occurs during the execution of the function, e.g. if the deviation is huge, the
function is to set OUT to the median value, LIMIT to TRUE, and increment the “overflow” error counter.
All input parameters (PV1, PV2, PV3 and DEVIATION) must be finite, i.e. not ±infinities or NaNs.
4
(without the SEL output).
The standard ISaGRAF MAX function provides the equivalent functionality for integer values
Issue 8 Sep 07 PD-T8019 14
Page 15

Trusted
PV
X
TM
Process Control Algorithms T8019
2.6. Proportional PID Function
NOTE
The PID_II function block has been superseded by the IPID function block, which provides incremental
ID and enhanced functions. All new strategies should use IPID. PID_II is retained for compatibility,
P
but may be replaced in an application by IPID if desired.
A PID is a process regulator. Using the feedback concept, an output is regulated according to the
difference between its current value (PV) and its required value (SP).
PID-II
S
INC
DEC
Auto
XO
Kp
Td
Ts
X
MAX
X
MIN
STOP
STOP
P
Ti
OUT
LIMIT
LIMIT
HI
LO
Auto is the auto/manual mode select (type BOOLEAN). When set to TRUE the PID calculation is in
auto mode. XO is the manual set-point and is type REAL. Kp is the proportional constant (type
REAL). Ti is the integral time constant (type TIMER). If this is set to zero the function provides only the
P and D terms. Td is the derivative time constant (type TIMER). Ts is the sample time (type TIMER).
If the specified sample time is less than the application program scan time, then the effective Ts will be
the greater of the application scan time or PID function execution interval.
Issue 8 Sep 07 PD-T8019 15
Page 16

Trusted
S
TM
Process Control Algorithms T8019
The figure 1 below gives a simplified overview of the PID function:
SP
1
T
+
-
PV
e
Error
Kp
Proportional
TK
DP
d
dt
Integral
+
Xout
+
-
Derivative
Figure 1 PID Function
At entry the error
S is calculated as the difference between the set-point (SP) and the process variable
(PV). This error value is used in the calculation of the proportional and integral terms. The derivative
term is derived from PV as shown.
INC
prevents the output X
STOP
increasing when TRUE. When this input is TRUE and the PID is in
OUT
AUTO mode, the output is compared with the previous output and only values less than or equal to the
previous output will be returned and LIMIT
provide windup protection. Similarly, when DEC
or equal to the previous value, and LIMIT
will be set to TRUE. The integral term is also adjusted to
I
H
will be set to TRUE.
LO
is TRUE Xout will only return values greater than
STOP
In manual mode (AUTO = False), the output (Xout) follows the input XO. The function provides
manual to automatic bumpless transfer by adjusting the integral term. If set-point tracking is required
then the MANTRK function should be used in conjunction with the PID_II function.
The PID function provides reset windup protection by allowing high and low limits (Xmax and Xmin) to
be specified and anti-reset windup on the integral term. If the PID output would have exceeded the
specified high or low limits, the corresponding limit output (LIMIT
and LIMITLO) is generated. Note
HI
that the limit outputs are updated on each iteration of the PID function. The maximum and minimum
limits on Xout apply in both auto and manual modes.
In auto mode, the PID function will return only the proportional element on the first application scan,
and will the integral and derivative terms.
If Xmax < Xmin, the function assumes that the values have been reversed and “swaps” the values. On
each execution of the PID_II function with reversed parameters the ‘reversed’ error count will be
incremented. If an overflow condition occurs during the execution of the PID function the output Xout
will be set to Xmin in auto mode or XO in manual mode, and the integral term will be adjusted to
provide windup protection.
Issue 8 Sep 07 PD-T8019 16
Page 17

Trusted
PV
X
Tdf
TM
Process Control Algorithms T8019
2.7. Incremental PID Function
A PID is a process regulator. Using the feedback concept, an output is regulated according to the
difference between its current value (PV) and its required value (SP).
he IPID function block is an improved version of the PID_II block with incremental calculation,
T
derivative term switch for PV or error, and a derivative term filter. The IPID block is recommended for
all new applications. It is also a relatively simple retrofit for the PID_II to provide a more stable output.
IPID
S
P
Auto
XO
Kp
Ti
Td
Ts
X
MAX
X
MIN
INC
STOP
DEC
STOP
D
ERR
Fwd
Auto is the auto/manual mode select (type BOOLEAN). When set to TRUE the IPID calculation is in
auto mode. XO is the manual set-point and is type REAL. Kp is the proportional constant (type
REAL). Ti is the integral time constant (type TIMER). If this is set to zero the function provides only the
P and D terms. Td is the derivative time constant (type TIMER). Kp, Ti and Td may be dynamically
changed in Auto mode without process bump.
OUT
LIMIT
LIMIT
D
QP
D
QI
D
QD
D
XOUT
HI
LO
Fwd switches between Forward and Reverse action (type BOOLEAN). When Fwd is FALSE and Kp is
positive, an increasing PV causes a decreasing Xout (reverse action). When Fwd is TRUE and Kp is
positive, an increasing PV causes an increasing Xout (forward action). If Kp is negative, the action is
also inverted.
Ts is the sample time (type TIMER). If the specified sample time is less than the application program
scan time, then the effective Ts will be the greater of the application scan time or PID function
execution interval. Changing Ts when in Auto mode may cause a process bump due to recalculation of
dynamic variables.
Tdf is the derivative action filter time constant (type TIMER). This may be used to reduce reaction to
process noise, or to spread derivative action over time. Tdf sets the exponential time constant of a first
order lag. If set to zero, the derivative action will act on the process fluctuations immediately.
switches the derivative action input (type BOOLEAN). When set to TRUE, the derivative action is
D
ERR
calculated based on the change in error (SP – PV). When set to false, the derivative action is
calculated based on the change in PV. This allows a choice on whether setpoint changes demand a
derivative kick or not. Note that when D
is false, the proportional action will still react to setpoint
ERR
changes, but with less step than P + D action.
The IPID calculation is incremental; at each scan, the required change in output is calculated. This
means that the P,I and D settings may be dynamically tuned without significant change to the output.
The total change at each scan is output as D
are output as D
, DQI and DQD (all type REAL). These may be used for continuous incremental action
QP
(type REAL). The change due to the P,I and D terms
XOUT
or for commissioning data.
Issue 8 Sep 07 PD-T8019 17
Page 18

Trusted
SP
PV+-
(Error)
d/dt
d/dt
dSd
S
d/dt
d/dt
d2PV
D
Tdf
W
S
Derivative
I
Integral
X++
+
X
Switch
TM
Process Control Algorithms T8019
The figure below gives an overview of the IPID function:
1
T
Proportional
K
KpTS/T
p
Y
S
2
-t/W
1 - e
KPTD/T
Figure 2 IPID Function
The calculation is performed one step into the derivative and is then integrated back for the real output.
At entry the error S is calculated as the difference between the set-point (SP) and the process variable
(PV). This error value is used directly for the integral action, after one differentiation for the proportional
action, and after two differentiations for the derivative action. The derivative action can be switched
using D
INC
STOP
to either use the second differential of error or PV, with a filter.
ERR
prevents the output X
increasing when TRUE. When this input is TRUE and the IPID is in
OUT
AUTO mode, the output is compared with the previous output and only values less than or equal to the
previous output will be returned and LIMIT
continue to update. Similarly, when DEC
D
XOUT
equal to the previous value, and LIMIT
will be set to TRUE. The delta outputs DQP, DQI, DQD and
HI
will be set to TRUE.
LO
is TRUE Xout will only return values greater than or
STOP
In manual mode (AUTO = False), the output (Xout) follows the input XO. Bumpless transfer to auto is
inherent because only the change in output is calculated. If set-point tracking is required then the
MANTRK function should be used in conjunction with the IPID function.
The IPID function provides high and low limits (Xmax and Xmin) to be specified. If the PID output
would have exceeded the specified high or low limits, the corresponding limit output (LIMIT
LIMIT
) is generated. Note that the limit outputs are updated on each iteration of the IPID function.
LO
and
HI
The maximum and minimum limits on Xout apply in both auto and manual modes. There is no need for
anti-windup protection because there is no stored integral term.
On the first application scan, the PID function will clear its registers and will not calculate an output.
If Xmax < Xmin, the function assumes that the values have been reversed and “swaps” the values. On
each execution of the IPID function with reversed parameters the ‘reversed’ error count will be
incremented. If an overflow condition occurs during the execution of the PID function the output Xout
will be set to Xmin in auto mode or XO in manual mode, and the stored registers are cleared.
Issue 8 Sep 07 PD-T8019 18
Page 19

Trusted
PV
OUT
XO
AUTO
TM
Process Control Algorithms T8019
2.8. Deviation Alarm
DEV_AL
DEV
EV
D
SP
US
S
D
DEV
EV
D
HI
LO
The deviation alarm function block takes the current process variable (PV) and set-point (SP), together
with the up-scale and down-scale deviation between the PV and SP (DEV
PV, SP, DEV
= ( (PV – SP) DEV
DEV
I
H
DEV
= ( (SP – PV) DEV
O
L
If an overflow condition occurs during the execution of the function, DEV
and DEVDS are of type REAL, both outputs (DEVHI and DEVLO) are of type Boolean.
US
)
S
U
)
S
D
HI
and DEV
S
U
is to be set to PV>0, DEVLO
respectively).
S
D
to PV<0 and the “overflow” error counter is to be incremented.
PV, SP, DEV
and DEV
S
U
must be finite, i.e. not ±infinities or NaNs.
S
D
2.9. Manual Tracking
X
MANTRK
XO
OUT
The manual tracking function requires the current PID function output (X
(XO) and auto/manual mode control (AUTO). Xout, XO and XO
OUT
), the manual set-point
OUT
are of type REAL, AUTO is
BOOLEAN.
Whilst AUTO is TRUE XO
will be set to the current value of X
OUT
i.e. AUTO changes to FALSE, the XO
value will remain at its previous value until the value of the
OUT
. On a transition to manual mode,
OUT
manual set-point input (XO) changes. Following a change to the manual set-point, the value of XO
will reflect the value of XO whilst AUTO is FALSE.
OUT
Issue 8 Sep 07 PD-T8019 19
Page 20

Trusted
Ts
Ts
TM
Process Control Algorithms T8019
2.10. Time Averaged Value
PV
Tp
Ts
EN
T_AVG
OUT
The average function calculates the average process variable (PV) value over the specified period
(Tp). The Ts specifies the minimum interval between samples. If the sample period is less than the
elapsed period between application program scans, Ts will be the application scan time. PV and OUT
are of type REAL; Tp and Ts are of type TIMER.
The enable input (EN) enables the use of the time averaged value; if this input is TRUE, OUT returns
the time averaged value, if this input is FALSE, out is set to the current process variable (PV) value.
The calculation of the time-averaged value continues irrespective of the EN state.
The function assumes that the input value (PV) changes linearly between samples, i.e. between
application program scans. The maximum number of samples taken must be less than 64, i.e.
Tp
64
. If the number of samples required to support
used and the time averaged value over these 64 samples returned
Tp
is greater than 64, then 64 samples will be
5
. The function is to include time
weighting of the sampled values to correct for variation in application scan times. If the sample period
(Tp) is less than the sample interval (Ts) the function will effectively average over a single sample, and
return OUT = PV.
The output value (OUT) will be updated only after a sample has been taken, i.e. after Ts.
If an underflow condition occurs during the execution of the function, the function is to set OUT to zero
and increment the “underflow” error counter.
Overflow conditions are to result in OUT = PV, and increment the “overflow” error counter.
On initialisation, i.e. first application program scan, the average value is set to the current input value,
and is assumed to have been stable at this value for greater than Tp.
Note: Tp and Ts are variable at run-time. Although the function should not normally be used in this
manner, it is important that the behaviour with varying values is predictable. Changes in Tp or
Ts are to result in OUT being held at its previous value until sufficient samples have been taken
to calculate the valid time weighted average, i.e. after Tp.
5
ISaGRAF does not support the verification of the values used for Tp and Ts within the
workbench. Also, note that these values are variables and may be changed at runtime, although this is
not recommended. Changing these values at runtime will result in the same behaviour as on
initialisation, i.e. the input will be assumed to have been stable for Tp and the output set to PV.
Issue 8 Sep 07 PD-T8019 20
Page 21

Trusted
TM
Process Control Algorithms T8019
Example:
PV
250ms
20ms
T_AVG
OUT
T (ms) 350 390 432 475 521 565 607 650 690 732 777 821
PV 23.5 15.46 10.01 56.03 58.61 90.17 85.68 84.56 18.09 95.94 75.66 49.38
Ts (ms) 46 40 42 43 46 44 42 43 40 42 45 44
% of Tp 103.2 102.4 101.6 102.8 102.8 104.4 102.8 104.0 103.2 102.8 102.4 102.4
OUT 23.5022.87 21.09 22.71 28.76 37.26 48.00 58.53 64.87 68.91 73.96 71.92
Table 3 Example Time Average
The example assumes that PV has been static at 23.5 for greater than 250 ms before the first sample
shown. The Ts row shows the actual interval between samples. The % of Tp row shows the figure
used for the overall output adjustment; e.g., the actual period between the 521ms and 777ms iterations
is 256ms, i.e. 102.4% of Tp.
Issue 8 Sep 07 PD-T8019 21
Page 22

Trusted
TM
Process Control Algorithms T8019
2.11. Rate of Change Detection
Error! Objects cannot be created from editing field codes.
The Rate of Change Detection function requires 4 parameters: the process variable to be monitored
(PV), the sample interval (Ts), the maximum rate of change parameter (R), and rate of change
hysteresis (H). The function detects when the rate of increase or decrease of the process variable (PV)
has exceeded the defined limit R. When the rate of change has exceeded R, the output (Q) is set to
TRUE. Once the output is TRUE, it is set to FALSE as soon as the rate of increase or decrease has
fallen below R by at least the hysteresis value (H).
The process variable is sampled at the specified sample interval; the sample period used will be the
greater of Ts and the application scan time
samples is determined and used to establish the rate of change.
On initialisation, Q is set to FALSE and the previous PV value to the current PV value
PV, R and H must be of type REAL. Ts must be of type TIMER, the output (Q) is of type Boolean. The
rates of change parameters (R and H) are specified as rate of change per second.
i.e.
where:
()()
UP
Q
=
is the input value on the previous sample, on the first sample this value is set to
PV
t1
the current value of the input, i.e. PV
.is the current input value
PV
t2
.is the time the previous sample was taken.
T
t1
is the current time.
T
t2
R is the rate of change limit value
H is the rate of change hysteresis value
PVPV
12
tt
TT
12
tt
6
. The change in PV and the actual period between
>
R
.
t2
PVPV
12
tt
()
TT
12
tt
.
QHR
>
UP
1
t
is the previous value of Q
Q
1
6
maximum period between samples is T plus the application scan time.
Issue 8 Sep 07 PD-T8019 22
The actual sample interval will be NOT LESS THAN the specified sample interval. The
Page 23

Trusted
TM
Process Control Algorithms T8019
Parameters PV, R and H must be finite, i.e. not ±infinities or NaNs. Behaviour is not defined for any
other values. If negative values are specified for R or H, their ABS value will be used and the “param”
error counter will be incremented.
The function must record the sample time for the previous input value and calculate the rate of input
value change for the actual elapsed period.
In an overflow condition occurs, the function is to set Q
to PV>0, Q
P
U
to PV<0 and increment the
OWN
D
“overflow” error counter. In an underflow condition occurs, the function is to set Q
FALSE and increment the “underflow” error counter.
and Q
UP
DOWN
to
Issue 8 Sep 07 PD-T8019 23
Page 24

Trusted
TM
Process Control Algorithms T8019
2.12. Analogue Value Slew
PV
RATE
The analogue value slew function limits the rate of change of the output value (OUT) to the maximum
specified by the RATE input. On initialisation, OUT is set to PV. Changes in the input (PV) will be
tracked by the output with the maximum rate of change. If the rate of change of PV is less than the
maximum rate, the output will immediately follow the input. PV is assumed to be in units, RATE is then
in units per second.
OUT
PV
i.e.:
if PV > OUTt1 then
2 else
()
×+= RATE,
MinTTOUTOUT
t1t1
SLEW
OUT
()
OUTPVABS
TT
2
t1
t1
()
2
()
t1
Where:
is the current time (seconds)
T
2
is the time the algorithm was previously executed (seconds)
T
t1
PV is the current input value
is the output value the time the algorithm was previously executed
OUT
t1
RATE is the current RATE input value
All input parameters (PV and RATE) must be finite, i.e. not ±infinities or NaNs. Behaviour is not
defined for any other values. If RATE is negative, its ABS value will be used and the “param” error
counter incremented.
If an overflow condition occurs during the execution of the function, the function is to set OUT to its
previous value and increment the “overflow” error counter. If underflow occurs, the function is to set
OUT to its previous value and increment the “underflow” error counter.
t1
()
OUTPVABS
×= RATE,
MinTTOUTOUT
2
t1
TT
t1
()
end if
Issue 8 Sep 07 PD-T8019 24
Page 25

Trusted
TM
Process Control Algorithms T8019
3. Other Functions
3.1. Lead/Lag Control
The lead/lag facility will be provided using the high value select and low value select functions to select
the set-point values to be used for the fuel and airflow PID functions. The Lead/Lag is not a function or
function block in its own right; this paragraph illustrates the use of the previously defined high value
select and low value select functions to provide the required lead/lag control function.
Fuel Flow
Steam Demand
Air Flow
HVS
Fuel Flow PID Controller
Set Point
LVS
Air Flow PID Controller
Set Point
Issue 8 Sep 07 PD-T8019 25
Page 26

Trusted
TM
Process Control Algorithms T8019
4. Sample Application Program
A sample application program using selected Process Control Algorithms to implement a simple PID
oop is shown in Figure 3. Note that many of the input parameters to the ipid function block will usually
l
be program constants, and the extra outputs are not necessary for a single loop.
The mantrk blocks allow read/write control of setpoint and output. For the setpoint, the mantrk block
copies the measured variable to the setpoint input whilst the loop is in manual, to allow a bumpless
transfer to automatic mode. On entering automatic mode the setpoint will remain at this value until the
setpoint is changed. Note that since the ipid function block uses incremental action, this function is only
necessary if the output should not move on entering automatic mode until the setpoint is entered.
Without this function, the output will move to control to the setpoint but without a bump to the output.
The second mantrk block allows manual control of the output in manual mode, using the ‘operator
manual output’ tag. In automatic mode, the mantrk block follows the automatic output and writes to the
ipid’s XO input. On entering manual mode, the ipid block output follows XO, but the operator can now
change the output using ‘operator manual output’.
The slew function block limits the rate of change of the output, and is optional. Note that although this
will smooth the action to the control valve, it will also change the control response in a non-linear
fashion.
For cascade (master-slave) pairs of ipid blocks, wire the LIMIT outputs of the slave back to the
INCst/DECst inputs of the master. This will stop the master’s action if the slave output has hit its limit.
Wire the output of the master to the setpoint of the slave. If the slave is not in auto and reading its
setpoint from the master’s output (‘remote’ mode) then the master should be forced into manual mode
because its output is not being used. For any loop, if the measured variable is suspect, force the loop
into manual mode. If the remote setpoint is suspect, force the loop into local automatic mode with a
manually adjustable setpoint. Always wire intermediate signals like remote setpoints and master-slave
interactions through variables, so that their state can be monitored.
Figure 3 Sample Application Program
Issue 8 Sep 07 PD-T8019 26
Page 27

Trusted
TM
Process Control Algorithms T8019
This page is intentionally blank
Issue 8 Sep 07 PD-T8019 27
Page 28

 Loading...
Loading...