Risco AGILITY Users Manual

User Manual

Important Notice
This guide is delivered subject to the following conditions and restrictions:
This guide contains proprietary information belonging to RISCO Group. Such
information is supplied solely for the purpose of assisting explicitly and properly
authorized users of the system.
No part of its contents may be used for any other purpose, disclosed to any person
or firm , or re pro duced by any me an s , ele c t roni c or me chani c al , without th e ex p r ess
prior written permission of RISCO Group.
The information contained herein is for the purpose of illustration and reference
only.
Information in this document is subject to change without notice.
Corpora t e and indiv idual name s an d da t a used in ex am pl e s here in belong to th eir
respective owners.
Agility User Manual
All rights reserved.
©
2008 RISCO Group August 2008
Page 2

Agility User Manual
Table of Contents
Chapter 1 Introduction......................................................................................... 5
NKN=j~áå=cÉ~íìêÉë
NKO=^Öáäáíó=^êÅÜбнЙЕнìêÉ
NKP=rëÉê=léÉê~íáåÖ=qççäë
NKQ=pí~íìë=fåÇáÅ~íáçåë
iba=fåÇáÅ~íçêë
pí~íìë=_ìííçå=L=pЙкобЕЙ=`~ää=EiáëíÉå=C=q~äâF
sçáÅÉ=jÉëë~ÖáåÖ
pjp=jÉëë~ÖáåÖ
bã~áä=jÉëë~ÖáåÖ
pçìåÇ=fåÇáÅ~íáçåë
Chapter 2 Local System Operation.................................................................... 11
OKN=^êãáåÖ=óçìê=лулнЙг KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NN
^ï~ó=EcìääF=~êãáåÖW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NN
pí~ó=EeçãÉF=~êãáåÖWKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NO
m~êíáíáçå=~êãáåÖWKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NO
cçêÅÉ=^êãáåÖWKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NP
^êãáåÖ=ïáíÜ=íêçìÄäÉë=áå=íÜÉ=póëíÉãKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NP
OKO=aáë~êãáåÖ=óçмк=лулнЙã KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NQ
pулнЙг=Çáë~êãáåÖW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NQ
m~êíáíáçå=Çáë~êãáåÖW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKNR
aмкЙлл=Зáë~êãáåÖW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKNR
aáë~êãáåÖ=~ÑíÉê=~å=^ä~êãW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKNR
oЙлЙннáåÖ=~ÑíÉê=~å=~ä~êãW KKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NS
^åíá=`çÇÉ=oÉëÉíKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKNS
fåëí~ääÉê=oÉëÉíKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKKK NS
OKP=pÉåÇáåÖ=~=m~åáÅ=^ä~êã
Chapter 3 Remote System Operation.................................................................18
PKN=oÉãçíÉ=mÜçåÉ=léÉê~íáçå
oÉãçíÉду=^ЕЕЙллбеÖ=íÜÉ=póëíÉã
sçáÅÉ=léÉê~íáçåë=jÉåì
oÉÅÉáîáåÖ=`~ääë=Ñêçã=íÜÉ=póëíÉã
^ÅâåçïäÉÇÖÉ=jÉåì
_áJÇáêÉÅíáçå~ä=`çããìåáÅ~íáçå
PKO=pjp=léÉê~íáçå
pjp=oÉãçíÉ=`çåíêçä
pjp=`çåÑáêã~íáçå=jÉëë~ÖÉ
Chapter 4 User Functions and Settings............................................................. 23
QKN=rëÉê=`çÇÉë
QKO=mêçñáãáíó=q~Öë
QKP=aÉÑáåáåÖ=cçääçï=jÉ=aÉëíáå~íáçåë
QKQ=pÅÜÉÇìäÉê
QKR=`çãéäÉíÉ=jÉåì=çÑ=rëÉê=cìåÅíáçåë
Chapter 5 System Specifications....................................................................... 32
Chapter 6 EN 50131 Compliance........................................................................ 33
....................................................................................................................................... 5
................................................................................................................................6
........................................................................................................................... 7
................................................................................................................................. 8
.................................................................................................................................... 8
................................................................................ 8
............................................................................................................................... 9
................................................................................................................................. 9
............................................................................................................................... 9
............................................................................................................................10
......................................................................................................................
.................................................................................................................18
.................................................................................................18
..................................................................................................................18
.................................................................................................19
.........................................................................................................................20
.......................................................................................................20
....................................................................................................................................21
......................................................................................................................21
.........................................................................................................22
..........................................................................................................................................23
.....................................................................................................................................25
.....................................................................................................26
.............................................................................................................................................28
.................................................................................................29
NT
=
=
=
=
=
=
=
=
=
=
=
=
=
=
Page 3

Agility User Manual
Page 4

Agility User Manual
Chapter 1 - Introduction
Congratulations on your purchase of
System. The
and home automation needs for many residential and commercial applications.
Agility
of any protected door, window, hallway, room, or area. Status information is presented
visually or verbally. It supports the capabilities of communicating with a Central
Monitoring Station or to your mobile phone using friendly and easy to understand verbal
messages as well as SMS or E-mail messages.
This manual describes how to operate your system. It will guide you through
programming instructions for main system features as well as basic arming and disarming
commands for the system.
Agility
has been specifically designed to meet a wide range of security, safety
is designed to recognize abnormal conditions and inform the system of the status
Agility
- RISCO Group's Flexible Wireless Security
1.1 Main Features
Up to 32 wireless zones (1 way or 2 way
wireless detectors) + 4 optional wired
zones (only with I/O expander)
32 User codes + Grand Master code
4 fixed authority levels for user
Proximity tag for each user
3 partitions
3 wireless keypads (1 way or 2 way)
3 wireless sirens (internal or external)
8 Remote controls (1 way or 2 way)
250 Events Log
16 Follow Me destinations
4 outputs ( I/ O e x p and er )
X-10 support
Page 5

Agility User Manual
1.2 Agility Architecture
Your
Agility
throughout the premises, which provide external, perimeter and internal burglary
protection. The system is supervised, meaning that the panel checks the status of each
sensor to detect problems. If the panel detects trouble it will notify you with beeps and
indicator lights on the panel itself.
The following diagram shows the components that make up the system:
controls and monitors a variety of sensors, detectors, and contacts placed
Page 6

Agility User Manual
1.3 User Operating Tools
The
Agility
system can be operated using several devices, some of which have been
designed as bi-directional. If you have purchased a bi-directional device your system is
capable of sending a return reply status indication from the panel to the device for each
command that is sent to it.
Depending on your purchase you can operate your system via the following:
2-Way 8 Button Remote Control:
Using the bi-directional 8 button remote control you can arm, disarm,
send a panic alarm, activate outputs and more. Being bi-directional
the remote control receives a reply status indication, via its 3 colored
LEDs and internal buzzer siren, from the panel for each command
that it has sent to the panel. For higher security, commands can be
defined to be activated with a 4 digit PIN code.
Agility 2-Way Wireless Keypad:
Using the bi-directional wireless keypad you can program and
operate your system according to your needs. Being bi-directional the
keypad receives a reply status indication from the panel for each
command that it has sent to the panel. To use functions of the
keypad you can use a code or a proximity tag.
4 Button Key fob:
Using the 4 button key fob you can arm, disarm, send a panic alarm
and activate outputs.
Remote Phone Operation:
Using any remote, touch-tone phone you can perform remote
operations such as arming, disarming, listening in and talking to the
premises and more. The system can also provide audible information
such as event occurrences and the status of your system
.
SMS:
If your system is equipped with a GSM/GPRS module it can provide
information about the system such as event occurrences by SMS. You
can also operate the system using SMS commands for arming and
disarming the system and more
.
Configuration Software:
RISCO Group's Configuration Software enables the installer to
program the system and operate the system locally or remotely
.
Web Browser:
Using the web you can perform a variety of operations on your
system such as arming, disarming, output activation, receive status
information and viewing event logs
.
Page 7

Agility User Manual
1.4 Status Indications
LED Indicators
The LED indicators provide typical system indications, as discussed below. Some
indicators have additional functions, which are explained later on.
Power LED
The Power LED indicates system operation.
Condition Description
On
Power OK
Rapid flash
Slow flash
Arm/Alarm LED (Red)
Condition Description
On
System armed
Rapid flash
Slow flash
Stay LED
Condition Description
On
System armed at STAY
Off
System disarmed
Ready LED (Green)
Condition Description
On
System ready
Off
Open zones
Slow Flash
Trouble LED
Condition Description
Rapid Flash
Off
No trouble
Indicates AC trouble
Indicates low battery trouble
Alarm
System in Exit delay
System is ready to be armed while a specially
designated entry/exit door remains open
Trouble
Note:
When all LEDs flash one after another in sequence the system is in Installation mode.
Page 8

Agility User Manual
Status Button / Se rvice Cal l (Li sten & Talk )
The button on the main unit can be defined as a system status indicator or as a S.O.S
button. Once pressed, a service call will be established to the monitoring station,
which then enables 2-way communication with the premises.
Voice Messaging
Three types of spoken messages are heard when using the
or remotely to your mobile:
Event messages:
Upon selected event occurrence, the
remote Follow Me (FM) telephone number, informing you of a security situation by
playing a pre-recorded Event announcement message.
Status messages:
Upon remote access of the system by initiating a call from a
remote telephone or receiving a call from the system, the
current system status by playing a pre-recorded Status message.
Local Announcement messages:
operations, the
Agility
can announce various local messages to residents.
Upon event occurrence or user’s keypad
Agility,
Agility
locally in the premises
initiates a call to a
Agility
announces the
SMS Messaging
Using the GSM/GPRS Module the system can send predefined SMS event messages to a
remote Follow Me (FM) telephone number, informing you of the status of the security
system and certain events that occurred in the system.
For example:
Email Messaging
Using the Agility IP Module the system can send event messages by Email to predefined e-
mail addresses informing you of the status of the security system and certain events that
occurred in the system.
For example:
Subject: Alarm Security Message: Intruder Alarm
System Name: John's Residence
Event: Fire Alarm, Zone 5, Entrance door
Time: 01 April 2008; 16:12
Partition: Partition 1, First floor
Service Contact: Monitoring Station 01, 03-5676778
Page 9
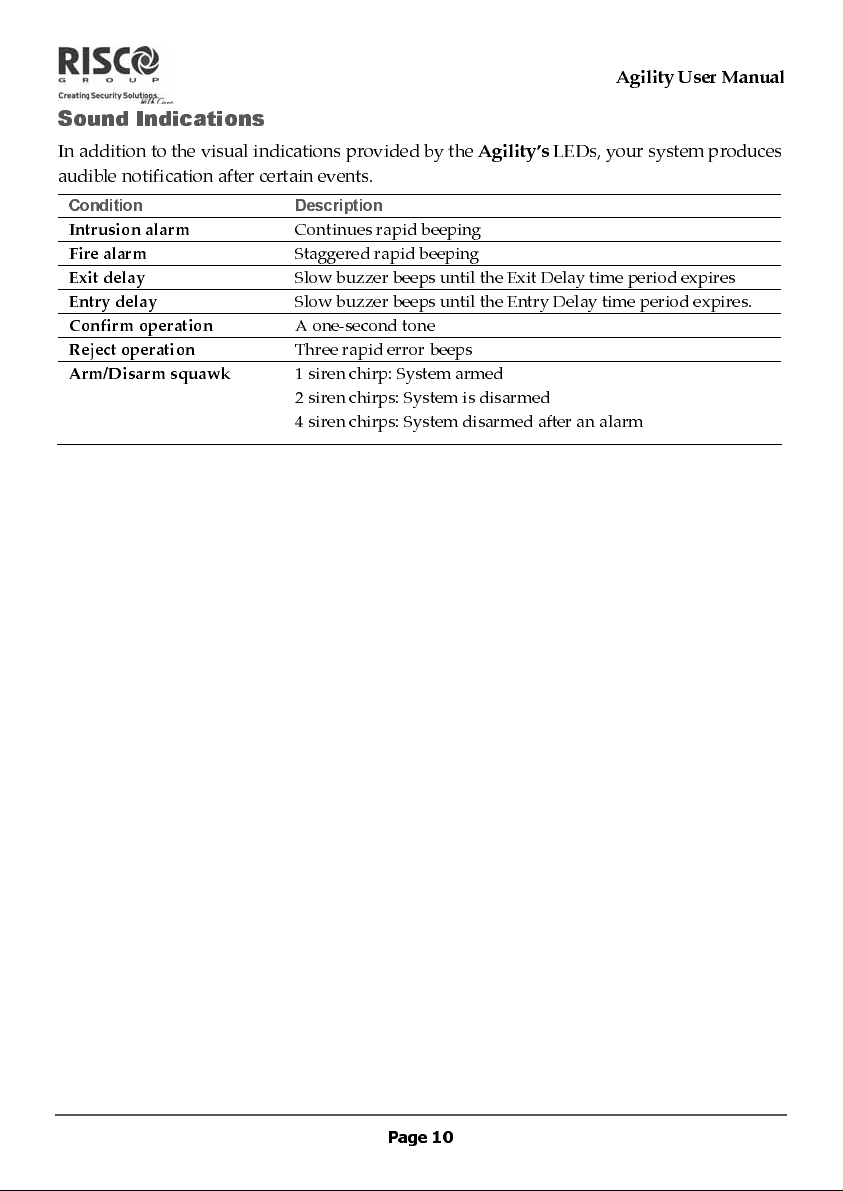
Sound Indications
In addition to the visual indications provided by the
audible notification after certain events.
Condition Description
Intrusion alarm
Fire alarm
Exit delay
Entry delay
Confirm operation
Reject operation
Arm/Disarm squawk
Continues rapid beeping
Staggered rapid beeping
Slow buzzer beeps until the Exit Delay time period expires
Slow buzzer beeps until the Entry Delay time period expires.
A one-second tone
Three rapid error beeps
1 siren chirp: System armed
2 siren chirps: System is disarmed
4 siren chirps: System disarmed after an alarm
Agility’s
Agility User Manual
LEDs, your system produces
Page 10

Agility User Manual
Chapter 2 - Local System Operation
2.1 Arming your system
Arming your system causes the intrusion detectors to trigger an alarm when violated. The
arming operation will be followed by a local message announcement (if defined).
Before arming the system check the
to be armed. If the system is NOT ready to be armed secure or bypass the violated zone(s),
and then proceed.
Failing to arm the system will be indicated by the system
Your
Agility
offers the following kinds of arming:
Note
: If you are unable to arm the system, press the status key to view system messages.
Away (Full) arming:
Away arming prepares all of the system's intrusion detectors to activate an alarm if
violated, and is used when leaving the premises. The system will arm after the
designated countdown time (Exit delay) and a local message will sound. Once you have
armed the system, exit via the designated final exit door.
Ready LED and make sure that the system is ready
To arm using=Away (Full) arming=procedure
Quick mode:
=
High security mode: Press + code
Quick mode:
High security mode
Press
=
Send SMS : [Code][A], example,
=
+ code or proximity tag
:
Page 11
=
1234A
 Loading...
Loading...