Page 1

Red Hat Network 3.7
Reference Guide
Page 2

Red Hat Network 3.7: Reference Guide
Copyright © 2005 by Red Hat, Inc.
Red Hat, Inc.
1801 Varsity Drive
Raleigh NC 27606-2072 USA
Phone: +1 919 754 3700
Phone: 888 733 4281
Fax: +1 919 754 3701
PO Box 13588
Research Triangle Park NC 27709 USA
RHNref(EN)-3.7-RHI (2005-03-16T12:14)
Copyright © 2005 by Red Hat, Inc. This material may be distributedonly subject to the terms and conditions set forth in the
Open Publication License, V1.0 or later (the latest version is presentlyavailableat http://www.opencontent.org/openpub/).
Distribution of substantively modified versions of this document is prohibitedwithout the explicit permission of the copyright
holder.
Distribution of the work or derivative of the work in any standard (paper)book form for commercial purposes is prohibited
unless prior permission is obtained from the copyright holder.
Red Hat and the Red Hat "Shadow Man" logo are registered trademarks of Red Hat, Inc. in the United States and other
countries.
All other trademarks referencedherein are the property of their respective owners.
The GPG fingerprint of the security@redhat.comkey is:
CA 20 86 86 2B D6 9D FC 65 F6 EC C4 21 91 80 CD DB 42 A6 0E
Page 3

Table of Contents
Introduction to the Guide.................................................................................................................... i
1. Document Conventions..........................................................................................................i
2. More to Come ...................................................................................................................... iv
2.1. Send in Your Feedback ......................................................................................... iv
1. Red Hat Network Overview........................................................................................................... 1
1.1. Demo.................................................................................................................................. 2
1.2. Update................................................................................................................................ 2
1.3. Management....................................................................................................................... 2
1.4. Provisioning ....................................................................................................................... 3
1.5. Monitoring ......................................................................................................................... 4
1.6. Errata Notifications and Scheduled Package Installations ................................................. 4
1.7. Security, Quality Assurance, and Red Hat Network..........................................................4
1.8. Before You Begin............................................................................................................... 5
2. Red Hat Update Agent.................................................................................................................... 7
2.1. Starting the Red Hat Update Agent ................................................................................. 7
2.2. Registration........................................................................................................................ 9
2.2.1. Registering a User Account ..............................................................................11
2.2.2. Registering a System Profile ............................................................................. 14
2.3. Setup and Use ..................................................................................................................18
2.3.1. Choosing a Software Channel...........................................................................19
2.3.2. Choosing Packages to Update...........................................................................19
2.3.3. Installing Updated Packages ............................................................................. 24
2.3.4. Update Agent Finished ..................................................................................... 25
2.3.5. Command Line Version .................................................................................... 26
2.4. Configuration ...................................................................................................................30
2.4.1. Using the Red Hat Update Agent Configuration Tool..................................30
2.4.2. Command Line Version .................................................................................... 33
2.5. Registering with Activation Keys ....................................................................................34
3. Red Hat Network Daemon ...........................................................................................................37
3.1. Configuring ...................................................................................................................... 37
3.2. Viewing Status ................................................................................................................. 37
3.3. Disabling..........................................................................................................................37
3.4. Troubleshooting ............................................................................................................... 37
4. Red Hat Network Alert Notification Tool................................................................................... 39
4.1. Configuring the Applet ....................................................................................................39
4.2. Notification Icons............................................................................................................. 40
4.3. Viewing Updates ..............................................................................................................41
4.4. Applying Updates ............................................................................................................ 41
4.5. Launching the RHN Website ........................................................................................... 41
5. Red Hat Network Registration Client ......................................................................................... 43
5.1. Configuring the Red Hat Network Registration Client................................................ 43
5.2. Starting the Red Hat Network Registration Client ...................................................... 44
5.3. Registering a User Account .............................................................................................47
5.4. Registering a System Profile ............................................................................................ 49
5.4.1. Hardware System Profile .................................................................................. 49
5.4.2. Software System Profile....................................................................................50
5.5. Finishing Registration......................................................................................................52
5.6. Entitling Your System......................................................................................................54
5.7. Text Mode RHN Registration Client ...............................................................................54
Page 4

6. Red Hat Network Website............................................................................................................ 57
6.1. Navigation........................................................................................................................ 57
6.1.1. Entitlement Views............................................................................................. 57
6.1.2. Categories and Pages ........................................................................................ 57
6.1.3. Errata Alert Icons .............................................................................................. 59
6.1.4. Quick Search.....................................................................................................59
6.1.5. Systems Selected............................................................................................... 59
6.1.6. Lists................................................................................................................... 59
6.2. Logging into the RHN Website........................................................................................ 60
6.3. Your RHN ........................................................................................................................ 60
6.3.1. Your Account .................................................................................................... 62
6.3.2. Your Preferences ............................................................................................... 63
6.3.3. Purchase History ............................................................................................... 63
6.3.4. Help................................................................................................................... 63
6.4. Systems ............................................................................................................................64
6.4.1. Overview —
6.4.2. Systems ............................................................................................................. 66
6.4.3. System Groups —
6.4.4. System Set Manager — ..............................................................................79
6.4.5. System Entitlements ......................................................................................... 84
6.4.6. Advanced Search —
6.4.7. Activation Keys — ..................................................................................... 85
6.4.8. Stored Profiles — ....................................................................................... 87
6.4.9. Custom System Info — ..............................................................................87
6.4.10. Kickstart — ..............................................................................................87
6.5. Errata................................................................................................................................94
6.5.1. Relevant Errata.................................................................................................. 95
6.5.2. All Errata...........................................................................................................95
6.5.3. Advanced Search............................................................................................... 97
6.6. Channels...........................................................................................................................97
6.6.1. Software Channels ............................................................................................97
6.6.2. Channel Entitlements ......................................................................................101
6.6.3. Easy ISOs........................................................................................................101
6.6.4. Package Search ...............................................................................................101
6.6.5. Software Packages ..........................................................................................101
6.6.6. Manage Config Channels — .................................................................... 103
6.7. Schedule......................................................................................................................... 109
6.7.1. Pending Actions .............................................................................................. 109
6.7.2. Failed Actions ................................................................................................. 110
6.7.3. Completed Actions.......................................................................................... 110
6.7.4. Archived Actions ............................................................................................110
6.7.5. Actions List..................................................................................................... 110
6.8. Users — ................................................................................................................... 111
6.8.1. User Roles....................................................................................................... 112
6.8.2. User List —
6.9. Monitoring — ..........................................................................................................115
6.9.1. Probe Status — .........................................................................................115
6.9.2. Notification — .......................................................................................... 118
6.9.3. Scout Config Push — ............................................................................... 118
6.9.4. General Config — ....................................................................................118
...............................................................................................65
...................................................................................... 76
................................................................................... 85
..............................................................................................112
Page 5

7. Monitoring................................................................................................................................... 119
7.1. Prerequisites. ..................................................................................................................119
7.2. Red Hat Network Monitoring Daemon (rhnmd) ...........................................................119
7.2.1. Probes requiring the daemon .......................................................................... 120
7.2.2. Installing the Red Hat Network Monitoring Daemon..................................... 120
7.2.3. Configuring SSH.............................................................................................121
7.2.4. Installing the SSH key ....................................................................................121
7.3. Notifications. ..................................................................................................................122
7.3.1. Creating Notification Methods........................................................................ 122
7.3.2. Receiving Notifications................................................................................... 123
7.3.3. Redirecting Notifications ................................................................................123
7.3.4. Filtering Notifications ..................................................................................... 124
7.3.5. Deleting Notification Methods........................................................................ 124
7.4. Probes.............................................................................................................................124
7.4.1. Managing Probes ............................................................................................ 125
7.4.2. Establishing Thresholds ..................................................................................125
7.4.3. Monitoring the RHN Server............................................................................ 126
7.5. Troubleshooting ............................................................................................................. 126
7.5.1. Examining Probes with rhn-catalog .......................................................... 126
7.5.2. Viewing the output of rhn-runprobe...........................................................127
A. Command Line Config Management Tools.............................................................................129
A.1. Red Hat Network Configuration Client .................................................................... 129
A.1.1. Listing Config Files........................................................................................129
A.1.2. Getting a Config File...................................................................................... 129
A.1.3. Viewing Config Channels .............................................................................. 129
A.1.4. Differentiating between Config Files............................................................. 130
A.1.5. Verifying Config Files ....................................................................................130
A.2. Red Hat Network Configuration Manager ............................................................... 130
A.2.1. Creating a Config Channel ............................................................................. 131
A.2.2. Adding Files to a Config Channel .................................................................. 131
A.2.3. Differentiating between Latest Config Files .................................................. 132
A.2.4. Differentiating between Various Versions...................................................... 132
A.2.5. Downloading All Files in a Channel ..............................................................133
A.2.6. Getting the Contents of a File ........................................................................ 133
A.2.7. Listing All Files in a Channel ........................................................................133
A.2.8. Listing All Config Channels .......................................................................... 134
A.2.9. Removing a File from a Channel ...................................................................134
A.2.10. Deleting a Config Channel ........................................................................... 134
A.2.11. Determining the Number of File Revisions ................................................. 134
A.2.12. Updating a File in a Channel........................................................................135
A.2.13. Uploading Multiple Files at Once................................................................ 135
B. RHN API Access......................................................................................................................... 137
B.1. Using the auth Class and Getting the Session ...............................................................137
B.2. Obtaining the system_id................................................................................................137
B.3. Determining the sid ....................................................................................................... 137
B.4. Viewing the cid.............................................................................................................. 137
B.5. Getting the sgid ............................................................................................................. 138
B.6. Sample API Script......................................................................................................... 138
Page 6

C. Probes.......................................................................................................................................... 141
C.1. Probe guidelines ............................................................................................................141
C.2. Apache 1.3.x and 2.0.x ..................................................................................................141
C.2.1. Apache::Processes.......................................................................................... 142
C.2.2. Apache::Traffic............................................................................................... 142
C.2.3. Apache::Uptime ............................................................................................. 143
C.3. BEA WebLogic 6.x and higher .....................................................................................143
C.3.1. BEA WebLogic::Execute Queue ....................................................................144
C.3.2. BEA WebLogic::Heap Free ........................................................................... 144
C.3.3. BEA WebLogic::JDBC Connection Pool ......................................................145
C.3.4. BEA WebLogic::Server State ......................................................................... 146
C.3.5. BEA WebLogic::Servlet.................................................................................146
C.4. General .......................................................................................................................... 147
C.4.1. General::Remote Program ..............................................................................147
C.4.2. General::Remote Program with Data .............................................................147
C.4.3. General::SNMP Check ...................................................................................148
C.4.4. General::TCP Check ...................................................................................... 149
C.4.5. General::UDP Check...................................................................................... 149
C.4.6. General::Uptime (SNMP) ..............................................................................150
C.5. Linux .............................................................................................................................150
C.5.1. Linux::CPU Usage .........................................................................................150
C.5.2. Linux::Disk IO Throughput ...........................................................................151
C.5.3. Linux::Disk Usage.......................................................................................... 151
C.5.4. Linux::Inodes .................................................................................................152
C.5.5. Linux::Interface Traffic ..................................................................................152
C.5.6. Linux::Load.................................................................................................... 153
C.5.7. Linux::Memory Usage ................................................................................... 153
C.5.8. Linux::Process Counts by State ..................................................................... 154
C.5.9. Linux::Process Count Total............................................................................154
C.5.10. Linux::Process Health .................................................................................. 155
C.5.11. Linux::Process Running ............................................................................... 156
C.5.12. Linux::Swap Usage ......................................................................................156
C.5.13. Linux::TCP Connections by State ................................................................157
C.5.14. Linux::Users.................................................................................................158
C.5.15. Linux::Virtual Memory ................................................................................158
C.6. LogAgent.......................................................................................................................159
C.6.1. LogAgent::Log Pattern Match ....................................................................... 159
C.6.2. LogAgent::Log Size .......................................................................................160
C.7. MySQL 3.23 - 3.33 ....................................................................................................... 161
C.7.1. MySQL::Database Accessibility ....................................................................161
C.7.2. MySQL::Opened Tables.................................................................................161
C.7.3. MySQL::Open Tables ....................................................................................161
C.7.4. MySQL::Query Rate ......................................................................................162
C.7.5. MySQL::Threads Running.............................................................................162
C.8. Network Services .......................................................................................................... 163
C.8.1. Network Services::DNS Lookup....................................................................163
C.8.2. Network Services::FTP .................................................................................. 163
C.8.3. Network Services::IMAP Mail.......................................................................164
C.8.4. Network Services::Mail Transfer (SMTP) ..................................................... 164
C.8.5. Network Services::Ping. ................................................................................. 165
C.8.6. Network Services::POP Mail .........................................................................165
C.8.7. Network Services::Remote Ping .................................................................... 166
C.8.8. Network Services::RPCService......................................................................167
C.8.9. Network Services::Secure Web Server (HTTPS)...........................................167
C.8.10. Network Services::SSH................................................................................ 168
C.8.11. Network Services::Web Server (HTTP)....................................................... 168
Page 7

C.9. Oracle 8i and 9i .............................................................................................................169
C.9.1. Oracle::Active Sessions.................................................................................. 169
C.9.2. Oracle::Availability ........................................................................................170
C.9.3. Oracle::Blocking Sessions..............................................................................170
C.9.4. Oracle::Buffer Cache...................................................................................... 171
C.9.5. Oracle::Client Connectivity. ...........................................................................171
C.9.6. Oracle::Data Dictionary Cache ...................................................................... 172
C.9.7. Oracle::Disk Sort Ratio .................................................................................. 172
C.9.8. Oracle::Idle Sessions ......................................................................................173
C.9.9. Oracle::Index Extents .....................................................................................173
C.9.10. Oracle::Library Cache .................................................................................. 174
C.9.11. Oracle::Locks ............................................................................................... 175
C.9.12. Oracle::Redo Log .........................................................................................175
C.9.13. Oracle::Table Extents ...................................................................................176
C.9.14. Oracle::Tablespace Usage ............................................................................ 176
C.9.15. Oracle::TNS Ping ......................................................................................... 177
C.10. RHN Satellite Server ................................................................................................... 177
C.10.1. RHN Satellite Server::Disk Space................................................................177
C.10.2. RHN Satellite Server::Execution Time ........................................................ 178
C.10.3. RHN Satellite Server::Interface Traffic........................................................ 178
C.10.4. RHN Satellite Server::Latency ..................................................................... 179
C.10.5. RHN Satellite Server::Load ......................................................................... 179
C.10.6. RHN Satellite Server::Probe Count..............................................................179
C.10.7. RHN Satellite Server::Process Counts ......................................................... 180
C.10.8. RHN Satellite Server::Processes .................................................................. 180
C.10.9. RHN Satellite Server::Process Health.......................................................... 181
C.10.10. RHN Satellite Server::Process Running..................................................... 182
C.10.11. RHN Satellite Server::Swap....................................................................... 182
C.10.12. RHN Satellite Server::Users.......................................................................182
Glossary ........................................................................................................................................... 183
Index.................................................................................................................................................189
Page 8

Page 9

Introduction to the Guide
Welcome to the Red Hat Network 3.7 Reference Guide. The RHN Reference Guide will guide you
through registering your system with Red Hat Network and using its many features.
Since Red Hat Network offers a variety of service levels, from the most basic Update module to the
most advanced Monitoring package, some content of this guide may be inapplicable to you. This is
particularly true of the RHN website, which displays selected categories, pages, and tabs depending
on the entitlement level of the account used to log in. Refer to Chapter 6 Red Hat Network Website to
determine what is available to you.
Depending on which version of Red Hat Enterprise Linux you have installed, the Red Hat Network
Registration Client and the Red Hat Update Agent might be different than the ones described in
this manual as new features are added. Once you use Red Hat Network to update these applications,
you can use the latest version of this manual.
All versions of this manual are available in HTML and PDF formats at
http://www.redhat.com/docs/manuals/RHNetwork/.
This version of the manual covers version 4.2.38 of the Red Hat Enterprise Linux 3 Red Hat Update
Agent and versions 2.9.14 and 2.9.12 of the Red Hat Enterprise Linux 2.1 Red Hat Update Agent
and Red Hat Network Registration Client, respectively.
Warning
Systems running Red Hat Enterprise Linux 2.1 will need to use the separate Red Hat Network
Registration Client before starting the Red Hat Update Agent. Refer to Chapter 5 Red Hat Network
Registration Client for instructions. Systems running Red Hat Enterprise Linux 3 can go directly to
the Red Hat Update Agent, which has registration functionality built in. Refer to Chapter 2 Red Hat
Update Agent for instructions.
For an overview of Red Hat Network offerings, please review the descriptions available at
http://www.redhat.com/software/rhn/ .
1. Document Conventions
When you read this manual, certain words are represented in different fonts, typefaces, sizes, and
weights. This highlighting is systematic; different words are represented in the same style to indicate
their inclusion in a specific category. The types of words that are represented this way include the
following:
command
Linux commands (and other operating system commands, when used) are represented this way.
This style should indicate to you that you can type the word or phrase on the command line
and press [Enter] to invoke a command. Sometimes a command contains words that would be
displayed in a different style on their own (such as file names). In these cases, they are considered
to be part of the command, so the entire phrase is displayed as a command. For example:
Use the cat testfile command to view the contents of a file, named testfile, in the current
working directory.
file name
File names, directory names, paths, and RPM package names are represented this way. This style
should indicate that a particular file or directory exists by that name on your system. Examples:
Page 10

ii Introduction to the Guide
The .bashrc file in your home directory contains bash shell definitions and aliases for your own
use.
The /etc/fstab file contains information about different system devices and file systems.
Install the webalizer RPM if you want to use a Web server log file analysis program.
application
This style indicates that the program is an end-user application (as opposed to system software).
For example:
Use Mozilla to browse the Web.
[key]
A key on the keyboard is shown in this style. For example:
To use [Tab] completion, type in a character and then press the [Tab] key. Your terminal displays
the list of files in the directory that start with that letter.
[key]-[combination]
A combination of keystrokes is represented in this way. For example:
The [Ctrl]-[Alt]-[Backspace] key combination exits your graphical session and returns you to the
graphical login screen or the console.
text found on a GUI interface
A title, word, or phrase found on a GUI interface screen or window is shown in this style. Text
shown in this style is being used to identify a particular GUI screen or an element on a GUI
screen (such as text associated with a checkbox or field). Example:
Select the Require Password checkbox if you would like your screensaver to require a password
before stopping.
top level of a menu on a GUI screen or window
A word in this style indicates that the word is the top level of a pulldown menu. If you click on
the word on the GUI screen, the rest of the menu should appear. For example:
Under File on a GNOME terminal, the New Tab option allows you to open multiple shell
prompts in the same window.
If you need to type in a sequence of commands from a GUI menu, they are shown like the
following example:
Go to Applications (the main menu on the panel) => Programming => Emacs Text Editor to
start the Emacs text editor.
button on a GUI screen or window
This style indicates that the text can be found on a clickable button on a GUI screen. For example:
Click on the Back button to return to the webpage you last viewed.
computer output
Text in this style indicates text displayed to a shell prompt such as error messages and responses
to commands. For example:
The ls command displays the contents of a directory. For example:
Desktop about.html logs paulwesterberg.png
Mail backupfiles mail reports
Page 11

Introduction to the Guide iii
The output returned in response to the command (in this case, the contents of the directory) is
shown in this style.
prompt
A prompt, which is a computer’s way of signifying that it is ready for you to input something, is
shown in this style. Examples:
$
#
[stephen@maturin stephen]$
leopard login:
user input
Text that the user has to type, either on the command line, or into a text box on a GUI screen, is
displayed in this style. In the following example, text is displayed in this style:
To boot your system into the text based installation program, you must type in the text command at the boot: prompt.
replaceable
Text used for examples, which is meant to be replaced with data provided by the user, is displayed
in this style. In the following example,
The directory for the kernel source is /usr/src/kernels/
version-numberis the version and type of kernel installed on this system.
version-numberis displayed in this style:
version-number/, where
Additionally, we use several different strategies to draw your attention to certain pieces of information.
In order of how critical the information is to your system, these items are marked as a note, tip,
important, caution, or warning. For example:
Note
Remember that Linux is case sensitive. In other words, a rose is not a ROSE is not a rOsE.
Tip
The directory /usr/share/doc/ contains additional documentation for packages installed on your
system.
Important
If you modify the DHCP configuration file, the changes do not take effect until you restart the DHCP
daemon.
Page 12

iv Introduction to the Guide
Caution
Do not perform routine tasks as root — use a regular user account unless you need to use the root
account for system administration tasks.
Warning
Be careful to remove only the necessary partitions. Removing other partitions could result in data
loss or a corrupted system environment.
2. More to Come
The Red Hat Network Reference Guide is constantly expanding as new Red Hat Network features and
service plans are launched. HTML and PDF versions of this and other manuals are available within
the Help section of the RHN website and at http://www.redhat.com/docs/.
Note
Although this manual reflects the most current information possible, read the RHN Release Notes for
information that may not have been available prior to our documentation being finalized. The notes
can be found on the RHN website and at http://www.redhat.com/docs/.
2.1. Send in Your Feedback
If you would like to make suggestions about the Red Hat Network Reference Guide, please submit a
report in Bugzilla: http://bugzilla.redhat.com/bugzilla/
Be sure to select the Red Hat Network product and the Documentation component. To easily associate
the problem with this guide, mention its identifier:
RHNref(EN)-3.7-RHI (2005-03-16T12:14)
Page 13

Chapter 1.
Red Hat Network Overview
Have you ever read about a new version of a software package and wanted to install it but could not
find it?
Have you ever tried to find an RPM through an Internet search engine or an RPM repository and been
linked to a site that you have never heard of?
Have you ever tried to find an RPM but instead found only the source files that you had to compile
yourself?
Have you ever spent hours or even days visiting different websites to see if you have the latest packages
installed on your system, only to have to do it again in a few months?
Those days are over with Red Hat Network (RHN). RHN provides the solution to all your system
software management needs.
Red Hat Network is an Internet solution for managing a Red Hat Enterprise Linux system or a network
of Red Hat Enterprise Linux systems. All Security Alerts, Bug Fix Alerts, and Enhancement Alerts
(collectively known as Errata Alerts) can be downloaded directly from Red Hat or your own custom
collection. You can even have updates scheduled to be delivered directly to your system as soon as
they are released.
The main components of Red Hat Network are as follows:
• the Red Hat Update Agent
• the Red Hat Network website, whether this is hosted by the central RHN Servers, an RHN Satellite
Server or fed through an RHN Proxy Server
• Red Hat Network Daemon
• the Red Hat Network Registration Client - for systems running Red Hat Enterprise Linux 2.1
only.
The Red Hat Update Agent (up2date) provides your initial connection to Red Hat Network. Once
registered, it enables channel subscription, package installs, and management of System Profiles. Red
Hat Enterprise Linux 3 and newer systems will even use the Red Hat Update Agent to register with
RHN. See Chapter 2 Red Hat Update Agent for further information.
Although both the RHN website and the Red Hat Update Agent allow you to view Errata Alerts
from the Red Hat Errata list and apply updates, the website offers a much more granular view of your
account and provides added functionality required for management and provisioning of systems. For
enterprise deployments of Red Hat Network, the website is a must.
The Red Hat Network Daemon (rhnsd) runs in the background as a service and probes the Red Hat
Network for notifications and updates at set time intervals (see Chapter 3 Red Hat Network Daemon
for further information). This daemon is necessary if you want to schedule updates or other actions
through the website.
The Red Hat Network Registration Client allows you to register your Red Hat Enterprise Linux
2.1 systems with RHN. (Newer versions of Red Hat Enterprise Linux have registration functionality
built into the Red Hat Update Agent.) Registration involves creating a unique RHN username and
password, probing the hardware on your system to create a Hardware Profile, and probing the software
packages installed on your system to create a Package Profile. This information is sent to RHN, and
RHN returns a unique System ID to your system. See Chapter 5 Red Hat Network Registration Client
for more information.
Page 14

2 Chapter 1. Red Hat Network Overview
Many Red Hat Network terms are used throughout this manual. As you read the Red Hat Network
Reference Guide, refer to the Glossary as necessary for an explanation of common terms.
Tip
For a comparison chart of RHN service levels, refer to http://www.redhat.com/software/rhn/table/.
1.1. Demo
The RHN Demo service level is the complimentary service level. All users receive one free subscription to RHN Demo. All that is required is the completion of a brief survey once every 60 days.
With each Demo subscription, you receive:
• Errata Notifications — Be the first to know about Red Hat’s patches. Subscribe to email errata
notification through Red Hat Network.
• Errata Updates — Immediately bring individual systems up-to-date with the click of a button.
• Search Packages — Search through the full repository of RPMs available to Red Hat Network
users.
• Search Errata — Search through the collection of all errata ever released through Red Hat Network.
1.2. Update
The RHN Update service is ideal for a user with one Red Hat Enterprise Linux system or a small number of Red Hat Enterprise Linux systems to keep updated. Subscription to Update can be purchased
at http://rhn.redhat.com/purchase_info.pxt.
With each Update subscription, you receive the essential functionality provided to Demo users, plus:
• Easy ISOs — For customers who have purchased subscriptions to Red Hat Network, ISO images
are available for immediate download.
• Priority Access during periods of high load — When Red Hat releases a large errata, users with
Priority Access can be guaranteed that they will be able to access the updated packages immediately.
• RHN Support Access — All paying customers of Red Hat Network receive web based support for
their RHN questions.
• Errata Notification, Multiple Systems — Subscriptions for multiple systems means Errata notifi-
cation for Errata to all of those systems. Note that only one email is distributed per each Errata,
regardless of the number of systems affected.
• Errata Updates, Multiple Systems — Get quick updates for multiple systems with an easy button
click for each system.
1.3. Management
In addition to the features offered in the RHN Demo and Update subscription levels, the RHN Management subscription service allows you to manage your network of Red Hat Enterprise Linux systems,
users, and system groups through its System Set Manager interface.
RHN Management is based upon the concept of an organization. Each Management-level Red Hat
customer has the ability to establish users who have administration privileges to system groups. An
Page 15

Chapter 1. Red Hat Network Overview 3
Organization Administrator has overall control over each Red Hat Network organization with the
ability to add and remove systems and users. When users other than the Organization Administrator
log into the Red Hat Network website, they see only the systems they have permission to administer.
To create an account that can be used to entitle systems to RHN Management, go to
https://rhn.redhat.com/ and click on the Create Account link under the Sign In fields. On the Sign
Up for Red Hat Network page, click Create a new Corporate Login. After creating a corporate
account, you may add users within your organization to it.
The Red Hat Network features available to you depend on the subscription level for each Red Hat
Enterprise Linux system. With each Management subscription, you receive the functionality provided
to Demo and Update users, plus:
• Package Profile Comparison — Compare the package set on a system with the package sets of
similar systems with one click.
• Search Systems — Search through systems based on a number of criteria: packages, networking
information, even hardware asset tags.
• System Grouping — Web servers, database servers, workstations and other workload-focused sys-
tems may be grouped so that each set can be administered in common ways.
• Multiple Administrators — Administrators may be given rights to particular system groups, easing
the burden of system management over very large organizations.
• System Set Manager — You may now apply actions to sets of systems instead of single systems.
Work with members of a predefined system group, or work with an ad-hoc collection of systems.
Install a single software package to each, subscribe the systems to a new channel, or apply all Errata
to them with a single action.
• Batch Processing — Figuring out a list of outdated packages for a thousand systems would take
days for a dedicated sysadmin. Red Hat Network Management service can do it for you in seconds.
1.4. Provisioning
As the highest management service level, RHN Provisioning encompasses all of the features offered
in the RHN Demo, Update, and Management subscription levels. It is designed to allow you to deploy
and manage your network of Red Hat Enterprise Linux systems, users, and system groups.
Like, Management, Provisioning is based upon an organization. But it takes this concept a step further by enabling customers with Provisioning entitlements to kickstart, reconfigure, track, and revert
systems on the fly.
In addition to all of the features mentioned in lower service levels, Provisioning provides:
• Kickstarting — Systems with Provisioning entitlements may be re-installed through RHN with a
whole host of options established in kickstart profiles. Options include everything from the type of
bootloader and time zone to packages included/excluded and IP address ranges allowed. Even GPG
and SSL keys can be pre-configured.
• Client Configuration — Customers may use RHN to manage the configuration files on
Provisioning-entitled systems. Users can upload files to RHN’s central configuration manager,
verify local configuration files against those stored by RHN, and deploy files from RHN. Further,
custom configuration channels can be created to help manage this process.
• Snapshot Rollbacks — Provisioning-level users have the ability to revert the package profile, con-
figuration files, and RHN settings of systems. This is possible because snapshots are captured whenever an action takes place on a system. These snapshots identify groups, channels, packages, and
configuration files.
Page 16

4 Chapter 1. Red Hat Network Overview
• Custom System Information — Provisioning customers may identify any type of information they
choose about their systems. This differs from the more rigorous System Profile information and the
completely arbitrary Notes in that it allows you to develop specific keys of your choosing and then
assign searchable values for that key to each Provisioning-entitled system. For instance, this feature
would allow you to identify the cubicle in which each system is located.
1.5. Monitoring
Unlike the other service levels, RHN Monitoring does not include the systems management functions
of other entitlements. Instead it is a separate entitlement available to Management- and Provisioninglevel customers with Red Hat Enterprise Linux systems.
Monitoring allows an organization to install probes that can immediately detect failures and identify
performance degradation before it becomes critical. Used properly, the Monitoring entitlement can
give you insight into the applications, services, and devices on each system.
Specifically, Monitoring provides:
• Probes — Dozens of probes can be run against each system. These range from simple ping checks
to custom remote programs designed to return valuable data.
• Notification — Alerts resulting from probes entering WARNING and CRITICAL states can be sent
to email and pager addresses with contact methods identified by you. Each probe notification can
be sent to a different method, or address.
• Central Status — The results of all probes are summarized in a single Probe Status page, with the
systems affected broken down by state.
• Reporting — By selecting a probe and identifying the particular metric and a range of time, you
can generate graphs and event logs depicting precisely how the probe has performed.
1.6. Errata Notifications and Scheduled Package Installations
You can configure Red Hat Network to send you email notifications of new and updated software
packages as soon as the packages are available through RHN. You receive one email per Errata,
regardless of the number of your systems affected. You can also schedule package installs or package
updates. The benefits include:
• Reduced time and effort required by system administrators to stay on top of the Red Hat Errata list
• Minimized security vulnerabilities in your network by providing the patches as soon as Red Hat
releases them
• Filtered list of package updates (packages not relevant to your network are not included)
• Reliable method of managing multiple systems with similar configurations
1.7. Security, Quality Assurance, and Red Hat Network
Red Hat Network provides significant benefits to your network including security and quality assurance. All transactions made between you and Red Hat Network are encrypted, and all RPM packages
are signed with Red Hat’s GNU Privacy Guard (GPG) signature to ensure authenticity.
Red Hat Network incorporates the following security measures:
1. Your System Profile available at http://rhn.redhat.com is accessible only with an RHN-verified
username and password.
Page 17

Chapter 1. Red Hat Network Overview 5
2. A Digital Certificate is written to the client system after registration and is used to authenticate
the system during each transaction between the client and Red Hat Network. The file is only
readable by the root user on the client system.
3. All notifications and information messages are signed by Red Hat with an electronic signature
using GPG. RPM can be used to verify the authenticity of the package before it is installed.
4. All transactions are encrypted using a Secure Sockets Layer (SSL) connection.
5. All packages are tested and verified by the Red Hat Quality Assurance Team before they are
added to the Red Hat Errata list and Red Hat Network.
1.8. Before You Begin
By default, all the software packages you need to use Red Hat Network are installed with Red Hat
distributions. However, if you chose not to install them during the installation process, you will need
to obtain the Red Hat Update Agent (up2date) and possibly the Red Hat Network Registration
Client (rhn_register). In Red Hat Enterprise Linux 3, registration functionality is built into the
Red Hat Update Agent, while Red Hat Enterprise Linux 2.1 users will need the Red Hat Network
Registration Client.
Warning
The SSL certificate packaged with older versions of the Red Hat Update Agent and the Red Hat
Network Registration Client reached its end of life August 28, 2003. Users attempting to connect
using this certificate will receive SSL connection or certificate verification errors. You may view and
obtain the versions of these applications containing new certificates at the RHN Client Software page.
In the RHN website, click Help at the top-right corner, Get RHN Software in the left navigation bar,
and scroll down to examine the packages and versions.
To determine the versions of the client applications installed, run the rpm -q command followed by
the package name. For instance, for the Red Hat Network Registration Client, type the following
command:
rpm -q rhn_register
If the Red Hat Network Registration Client is installed, it will return something similar to:
rhn_register-2.9.3-1
The version number might differ slightly.
If you do not have the Red Hat Network Registration Client installed, the command will return:
package rhn_register is not installed
Perform this check for every package in Table 1-1 relevant to your system. Remember, only Red Hat
Enterprise Linux 2.1 users need the separate Red Hat Network Registration Client. If you prefer to
use the command line versions, you do not have to install the two packages ending in gnome.
Package Name Description
rhn_register Provides the Red Hat Network Registration Client program and the
text mode interface
Page 18

6 Chapter 1. Red Hat Network Overview
Package Name Description
rhn_register-gnome Provides the GNOME interface (graphical version) for the Red Hat
Network Registration Client; runs if the X Window System is available
up2date Provides the Red Hat Update Agent command line version and the Red
Hat Network Daemon
up2date-gnome Provides the GNOME interface (graphical version) for the Red Hat
Update Agent; runs if the X Window System is available
Table 1-1. Red Hat Network Packages
Page 19

Chapter 2.
Red Hat Update Agent
The Red Hat Update Agent is your connection to Red Hat Network. It enables you to register your
systems, create System Profiles, and alter the settings by which your organization and RHN interact.
Once registered, your systems can use the Red Hat Update Agent to retrieve the latest software packages from Red Hat. This tool will allow you to always have the most up-to-date Red Hat Enterprise
Linux systems with all security patches, bug fixes, and software package enhancements.
Remember, this tool must be run on the system you wish to update. You cannot use the Red Hat
Update Agent on the system if it is not entitled to an RHN service offering.
Warning
Only systems running Red Hat Enterprise Linux 3 can use the Red Hat Update Agent to register
with RHN. Systems running Red Hat Enterprise Linux 2.1 will need to use the separate Red Hat
Network Registration Client before starting the Red Hat Update Agent. Refer to Chapter 5 Red
Hat Network Registration Client for instructions. Then return to this chapter for instructions on
using the Red Hat Update Agent.
Important
You must use Red Hat Update Agent Version 2.5.4 or higher to upgrade your kernel automatically.
It will install the updated kernel and configure LILO or GRUB to boot the new kernel the next time
the system is rebooted. To ensure you are running the latest version, execute the command up2date
up2date. If you do not have the latest version installed, this command will update it.
2.1. Starting the Red Hat Update Agent
If you are not running the X Window System or prefer the command line version of the Red Hat
Update Agent, skip to Section 2.3.5 Command Line Version.
You must be root to run the Red Hat Update Agent. If you start it as a standard user, you will be
prompted to enter the root password before proceeding. The Red Hat Update Agent can be started
using one of the following methods:
For Red Hat Enterprise Linux 3:
• On the GNOME and KDE desktops, go to the Main Menu Button (on the Panel) => System Tools
=> Red Hat Network.
• At a shell prompt (for example, an xterm or gnome-terminal), type the command up2date.
For Red Hat Enterprise Linux 2.1:
• On the GNOME desktop, go to the Main Menu Button (on the Panel) => Programs => System
=> Update Agent.
• On the KDE desktop, go to the Main Menu Button (on the Panel) => Update Agent.
• At a shell prompt (for example, an xterm or gnome-terminal), type the command up2date.
Page 20

8 Chapter 2. Red Hat Update Agent
If you choose the last option and start the application from a shell prompt, you can specify the options
in Table 2-1 to the Red Hat Update Agent. To view these options, type the command up2date
--help.
For example, use the following command to specify the directory in which to download the updated
packages (temporarily overriding your saved configuration):
up2date --tmpdir=/tmp/up2date
Argument Description
--configure Configure Red Hat Update Agent options. Refer to Section 2.4
Configuration for detailed instructions.
-d, --download Download packages only; do not install them. This argument
temporarily overrides the configuration option Do not install
packages after retrieval. Use this option if you prefer to install
the packages manually.
-f, --force Force package installation. This option temporarily overrides the
file, package, and configuration skip lists.
-i, --install Install packages after they are downloaded. This argument
temporarily overrides the configuration option Do not install
packages after retrieval.
-k, --packagedir Specify a colon separated path of directories to look for packages
before trying to download them.
--nosig Do not use GPG to check package signatures. This option
temporarily overrides the saved configuration option.
--tmpdir=directory Temporarily override the configured package directory. The
default location is /var/spool/up2date. This option is useful
if you do not have enough space in the configured location.
--justdb Only add packages to the database and do not install them.
--dbpath=dir Specify an alternate RPM database to use temporarily.
Table 2-1. Graphical Update Agent Options
The first time you run the Red Hat Update Agent, two dialog boxes will appear that you will not see
in subsequent startups: Configure Proxy Server and Install GPG Key.
As shown in Figure 2-1, the first dialog box to appear will prompt you for HTTP Proxy Server information. This is useful if your network connection requires you to use a proxy server to make HTTP connections. To use this feature, select the Enable HTTP Proxy checkbox and type your proxy server in
the text field with the format http://HOST:PORT, such as http://squid.mysite.org:3128.
Additionally, if your proxy server requires a username and password, select the Use Authentication
checkbox and enter your username and password in the respective text fields.
An HTTP Proxy Server is not required by Red Hat Network. If you do not want to use this feature,
click the OK button without making any selections. Note that the Red Hat Network Server dropdown
menu at the top of the dialog box is only useful to RHN Proxy and Satellite customers. These customers should refer to the RHN Client Configuration Guide for registration steps. Also note this dialox
box is actually the General tab of the Red Hat Update Agent Configuration Tool. Refer to Section
2.4 Configuration for detailed instructions.
Page 21

Chapter 2. Red Hat Update Agent 9
Figure 2-1. Configure Proxy Server
The second dialog box to appear will prompt you to install the Red Hat GPG key, as shown in Figure
2-2. This key is used to verify the packages you download for security purposes. Click Yes to install
the key, and you will not see this message again.
Figure 2-2. Install GPG Key
2.2. Registration
Before you begin using Red Hat Network, you need to create a username, password, and System
Profile. Upon launch, the Red Hat Update Agent senses whether these tasks have been accomplished.
If not, it guides you through the registration process. If you ever need to force the Red Hat Update
Agent into registration mode, say to re-register an existing system, you may do so by issuing the
following command at a shell prompt:
up2date --register
Page 22
10 Chapter 2. Red Hat Update Agent
Important
If your username is part of a larger organizational account, you should take caution when registering your systems. By default, all systems registered with the Red Hat Update Agent end up in
the Ungrouped section of systems visible only to Organization Administrators. To ensure you retain
management of these systems, Red Hat recommends your organization create an activation key associated with a specific system group and grant you permissions to that group. You may then register
your systems using that activation key and find those System Profiles within RHN immediately. Refer
to Section 2.5 Registering with Activation Keys for instructions.
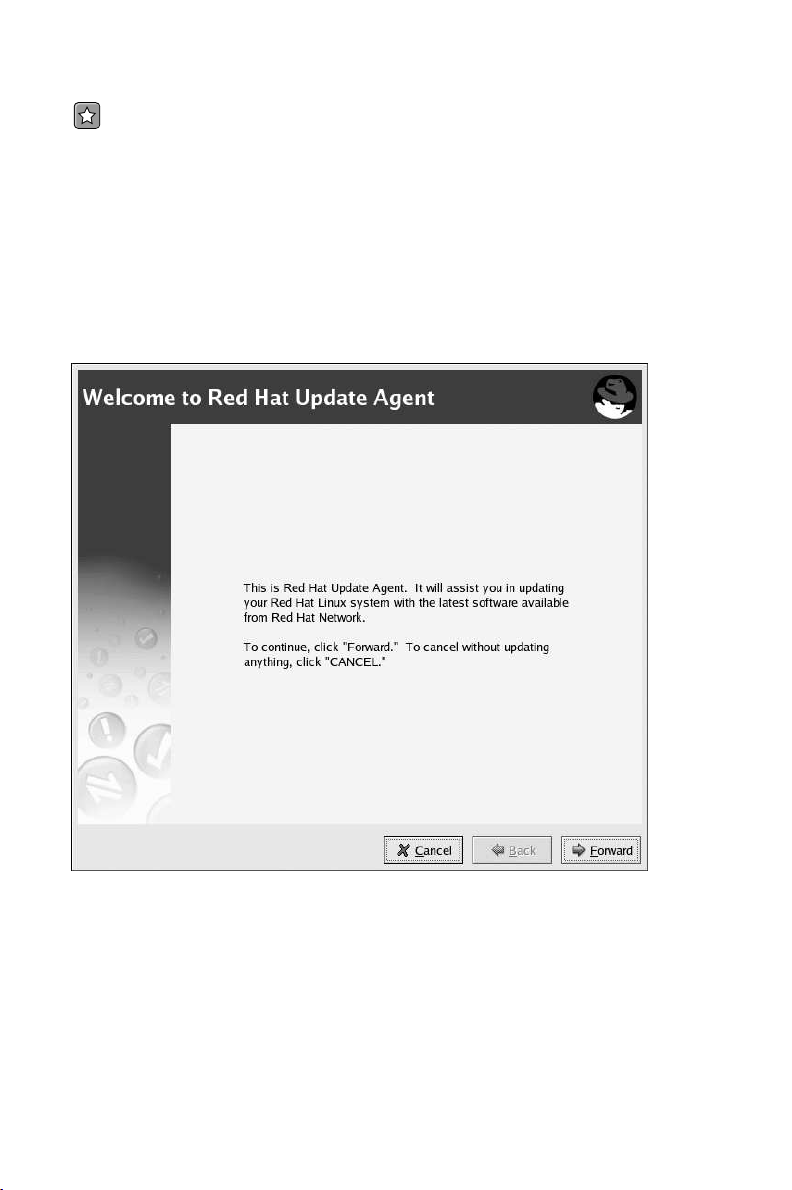
After installing the Red Hat GPG key, the screen in Figure 2-3 will appear. It appears every time you
start the Red Hat Update Agent. Click Forward to continue.
Figure 2-3. Welcome Screen
After clicking through the Welcome Screen, the Red Hat Privacy Statement appears. (See Figure 2-
4). Red Hat is committed to protecting your privacy. The information gathered during the Red Hat
Network registration process is used to create a System Profile, which is essential to receiving update
notifications about your system. When satisfied, click Forward.
Page 23

Chapter 2. Red Hat Update Agent 11
Figure 2-4. Red Hat Privacy Statement
2.2.1. Registering a User Account
Before you can create a System Profile, you must create a user account. Red Hat recommends you
create your account through the RHN website, but you may also do so through up2date. All that is
required is a unique username-password combination and a valid email address.
In the screen shown in Figure 2-5, choose a username and password. Once logged in to Red Hat
Network, you can modify your preferences, view your existing System Profile, or obtain the latest
Red Hat software packages.
Note
If you are already a member of redhat.com, you can and should use the same username and password. However, you will still need to continue with the registration process to create your System
Profile.
Your username has the following restrictions:
• Cannot contain any spaces
• Cannot contain the characters &, +, %, or ’
Page 24

12 Chapter 2. Red Hat Update Agent
• Is not case-sensitive, thereby eliminating the possibility of duplicate usernames differing only by
capitalization
In addition, the following restrictions apply to both your username and password:
• Must be at least four characters long
• Cannot contain any tabs
• Cannot contain any line feeds
Passwords are case-sensitive for obvious reasons.
Figure 2-5. Create a User Account
You must choose a unique username. If you enter one already in use, you will see an error message
(see Figure 2-6). Try different usernames until you find one that has not been used.
Warning
Be sure to identify a username that you will be satisfied with permanently, as this cannot be changed
after account creation.
Page 25

Chapter 2. Red Hat Update Agent 13
Figure 2-6. Error: Username Already Exists
Most users can leave the Org Info section blank. If you have an existing organization account, enter
your organization’s ID and password in the provided text fields. If the values are valid, the system will
be added to the organization’s Red Hat Network account.
If you have already registered a machine and created a System Profile, you can add a new machine to
your account. Run the Red Hat Update Agent on the new machine you wish to add, and enter your
existing Red Hat Network username and password. The new machine will be added to your existing
account, and you can log into Red Hat Network with your username and password to view all your
systems simultaneously.
In the Create Account screen, click Forward to continue.
If you are a new user to RHN, the Red Hat Update Agent takes you to the screen shown in Figure 2-
7. Here you will add details about yourself and your business, if applicable, and identify the methods
by which you should be reached.
Note
Unlike other details, your company name can be changed only through Red Hat Customer Service,
so enter it carefully. If you do need to have your company name changed, send your request to
customerservice@redhat.com.
Page 26

14 Chapter 2. Red Hat Update Agent
Figure 2-7. Register a User Account
Once satsfied with the information supplied, click Forward to continue.
2.2.2. Registering a System Profile
Now that you have a user account, you can create a System Profile that consists of hardware and
software information about your Red Hat Enterprise Linux system. The System Profile information is
used by Red Hat Network to determine what software update notifications you receive.
2.2.2.1. Hardware System Profile
After creating a username and password for your Red Hat Network account, the Red Hat Update
Agent probes your system for the following information:
• Red Hat Linux version
• Hostname
• IP address
• CPU model
• CPU speed
• Amount of RAM
• PCI devices
Page 27

Chapter 2. Red Hat Update Agent 15
• Disk sizes
• Mount points
The next step is choosing a profile name for your system as shown in Figure 2-8. The default value
is the hostname for the system. You may modify this to be a more descriptive string, such as Email
Server for Support Team, if you find it more helpful. Optionally, you can enter a computer
serial or identification number for the system.
If you do not wish to include information about your hardware or network in your System Profile,
deselect Include information about hardware and network (see Figure 2-8).
Figure 2-8. System Profile - Hardware
Click Forward to continue with the registration process.
2.2.2.2. Software System Profile
The software System Profile consists of a list of RPM packages for which you wish to receive notifications. The Red Hat Update Agent shows you a list of all RPM packages listed in the RPM database
on your system and then allows you to customize the list by deselecting packages.
2.2.2.2.1. Gathering RPM Database Information
Only those packages you choose during this part of the registration will be included in your System
Profile, and you will receive notifications only about the packages in your System Profile. Therefore,
Page 28

16 Chapter 2. Red Hat Update Agent
you must include packages in your profile to have RHN send you Errata regarding them. You should
also note if you use an older version of a package and deselect it from the list, it will not be replaced
with a newer version.
This RPM list can be modified through the Red Hat Network Web interface or by using the Red Hat
Update Agent. Figure 2-9 shows the progress bar you will see while the Red Hat Update Agent
gathers a list of the RPM packages installed on your system. This operation may take some time,
depending on your system installation.
Figure 2-9. Registration Wizard
Once the RPM package list is built, the list will be displayed as shown in Figure 2-10. Deselecting
Include RPM Packages installed on this system in my System Profile will omit this information
from your System Profile.
Figure 2-10. RPM Package Information
Page 29

Chapter 2. Red Hat Update Agent 17
2.2.2.2.2. Choosing RPM Packages to Exclude from the System Profile
By default, all RPM packages in your RPM database are included in your System Profile to be updated
by Red Hat Network. To exclude a package, uncheck the package from the list by clicking the checkbox beside the package name. For example, Figure 2-11 shows that the Canna-devel and Canna-libs
packages have been omitted from the package list.
Choose which packages to exclude, if any, from the System Profile, and click Forward to continue
with the registration process.
Figure 2-11. Choose which RPM Packages to Exclude from System Profile
2.2.2.3. Finishing Registration
As seen in Figure 2-12, the last step of registration is to confirm that you want to send your System
Profile to the Red Hat Network. If you choose Cancel at this point, no information will be sent.
Clicking Forward will submit your RHN System Profile.
Page 30

18 Chapter 2. Red Hat Update Agent
Figure 2-12. Finished Collecting Information for System Profile
Figure 2-13 shows the progress bar you will see while your profile is being sent. This process may
take some time depending on your connection speed.
Figure 2-13. Send System Profile to Red Hat Network
You will know your System Profile has been successfully sent when you see the Channels screen
(Figure 2-14) appear. Refer to Section 2.3.1 Choosing a Software Channel for continued instructions.
2.3. Setup and Use
After completing the registration process, you should set up the Red Hat Update Agent to effectively
manage all of your system’s package updates. This requires selecting its channel, identifying the
packages requiring maintenance, and making your first installation.
Page 31

Chapter 2. Red Hat Update Agent 19
Before you proceed, however, you should consider ensuring you have the latest version of the Red
Hat Update Agent, as development on it is continuous. This task is as simple as running the tool
against its own package. Shut down the GUI version and run this command in a terminal (as root),
like so:
up2date up2date
2.3.1. Choosing a Software Channel
The first step is to select the channel from which you want the updated packages to be retrieved. After
you send your System Profile, the Channels screen (Figure 2-14) appears. Select the appropriate
base channel and click Forward to continue. The Red Hat Update Agent offers only the channels
enabled for the system in RHN (or your RHN Satellite Server). Refer to Section 6.6 Channels for
more information on channels and how channels are used to determine which packages are installed.
Figure 2-14. Channels
2.3.2. Choosing Packages to Update
After clicking Forward, the dialog box in Figure 2-15 will appear. This means a connection to Red
Hat Network is being established and your customized list of updates is being retrieved. This might
take some time, depending on the speed of your connection and the number of packages you have
installed.
Page 32

20 Chapter 2. Red Hat Update Agent
Figure 2-15. Retrieve Update Information
While you see this dialog box, the Red Hat Update Agent uses your unique Digital Certificate
(/etc/sysconfig/rhn/systemid) to determine if there are any updated packages available for
your system. If there are no updated packages available for your system, the dialog box in Figure 2-16
appears. Click OK to exit the Red Hat Update Agent.
Figure 2-16. No new packages needed
If you excluded any packages while registering your System Profile, these are displayed in Figure
2-17. You may override these settings and include any of these packages in the update by selecting
the checkboxes next to them. To see a summary of each package in the Package Information section
at the bottom of the screen, click the name of the package.
Page 33

Chapter 2. Red Hat Update Agent 21
Figure 2-17. Packages Flagged to be Skipped
If you want to view the advisory for the RPM Alert, click the View Advisory button. This will display
what type of Errata Alert it is and what problem(s) it addresses as shown in Figure 2-18. Click OK to
close the advisory. Click Finished when you are finished selecting packages to include.
Page 34

22 Chapter 2. Red Hat Update Agent
Figure 2-18. View Advisory
The Available Package Updates screen is the next to appear. If your system is not up-to-date, your
customized list of available updated packages is displayed as shown in Figure 2-19.
Page 35

Chapter 2. Red Hat Update Agent 23
Figure 2-19. List of Available Updates
By default, no packages are selected for download. To select a package for download (and installation,
if you chose that option), click its checkbox. To select all the packages listed, click the checkbox next
to Select all packages.
After choosing which packages to update, the Red Hat Update Agent tests for RPM dependencies
and prompts you if you have chosen to omit packages that are required for software updates that you
did choose. The dialog box in Figure 2-20 is shown while it is testing for dependencies. This process
might take some time depending upon how many packages are updating.
Figure 2-20. Testing Packages
After testing is complete, package retrieval begins. The progress of each package retrieval is shown in
Figure 2-21. When they have all been retrieved, the message All finished is displayed at the bottom
of the screen. Click Forward to continue.
Page 36

24 Chapter 2. Red Hat Update Agent
Figure 2-21. Retrieval Finished
2.3.3. Installing Updated Packages
After downloading the packages through the Red Hat Update Agent, they must be installed. If you
chose not to have the packages installed via the Red Hat Update Agent, skip to Section 2.3.5.2
Manual Package Installation for further instructions. If you configured it to install the packages (the
default setting), the selected packages are installed. The progress of installing each package, as well
as the total progress, is displayed. When the packages have been installed, as seen in Figure 2-22,
click Forward to continue.
Page 37

Chapter 2. Red Hat Update Agent 25
Figure 2-22. Installation Finished
2.3.4. Update Agent Finished
When the Red Hat Update Agent has finished downloading the desired packages (and installing them
if you chose the install option), you will see the screen in Figure 2-23. Click Finish to exit the Red
Hat Update Agent.
Page 38

26 Chapter 2. Red Hat Update Agent
Figure 2-23. Update Agent Finished
2.3.5. Command Line Version
If you are not running X, you can still run the Red Hat Update Agent from a virtual console or
remote terminal. If you are running X but want to use the command line version, you can force it not
to display the graphical interface with the following command:
up2date --nox
The command line version of the Red Hat Update Agent allows you to perform advanced functions
or to perform actions with little or no interaction. For example, the following command updates your
system with no interaction. It will download the newer packages and install them if you configured it
to install them.
up2date -u
The command line version of the Red Hat Update Agent accepts the following arguments:
Argument Description
-?, --usage Briefly describe the available options.
-h, --help List the available options and exit.
Page 39

Chapter 2. Red Hat Update Agent 27
Argument Description
--arch=architecture Force up2date to install this architecture of the package. Not
valid with --update, --list, or --dry-run.
--channel=channel Specify which channels to update from using channel labels.
--configure Configure Red Hat Update Agent options. Refer to Section 2.4
Configuration for detailed instructions.
-d, --download Download packages only; do not install them. This argument
temporarily overrides the configuration option Do not install
packages after retrieval. Use this option if you prefer to install
the packages manually.
--dbpath=dir Specify an alternate RPM database to use temporarily.
--dry-run Do everything but download and install packages. This is useful
in checking dependencies and other requirements prior to actual
installation.
-f, --force Force package installation. This option temporarily overrides the
file, package, and configuration skip lists.
--firstboot Pop up in the center of the screen for Firstboot.
--get Fetch the package specified without resolving dependencies.
--get-source Fetch the source package specified without resolving
dependencies.
--gpg-flags Show the flags GPG will be invoked with, such as the keyring.
--hardware Update this system’s hardware profile on RHN.
-i, --install Install packages after they are downloaded. This argument
temporarily overrides the configuration option Do not install
packages after retrieval.
--installall Install all available packages. Used with --channel.
--justdb Only add packages to the database and do not install them.
-k, --packagedir Specify a colon-separated path of directories to look for packages
in before trying to download them.
-l, --list List packages relevant to the system.
--list-rollbacks Show the package rollbacks available.
--nodownload Do not download packages at all. This is useful in testing.
--nosig Do not use GPG to check package signatures. This option
temporarily overrides the saved configuration option.
--nosrc Do not download source packages (SRPMs).
--nox Do not attempt to run in X. This launches the command line
version of the Red Hat Update Agent.
-p, --packages Update packages associated with this System Profile.
--proxy=proxy URL Specify an HTTP proxy to use.
--proxyPassword=proxy
password
Specify a password to use with an authenticated HTTP proxy.
Page 40

28 Chapter 2. Red Hat Update Agent
Argument Description
--proxyUser=proxy user
ID
--register Register (or re-register) this system with RHN. Refer to Section
Specify a username to use with an authenticated HTTP proxy.
2.2 Registration for detailed instructions.
--serverUrl=server URL Specify an alternate server from which to retrieve packages.
--showall List all packages available for download.
--show-available List all packages available that are not currently installed.
--show-channels Show the channel name associated with each package.
--show-orphans List all packages currently installed that are not in channels the
system is subscribed to.
--show-package-dialog Show the package installation dialog in GUI mode.
--solvedeps=dependencies Find, download, and install the packages necessary to resolve
dependencies.
--src Download source packages, as well as binary RPMs.
--tmpdir=directory Temporarily override the configured package directory. The
default location is /var/spool/up2date. This option is useful
if you do not have enough space in the configured location.
--undo Reverse the last package set update.
-u, --update Update system with all relevant packages.
--upgrade-to-release=release
version
--uuid=uuid Pass in a Unique User ID generated by the Alert Notification
Upgrade to the channel specified.
tool.
-v, --verbose Show additional output while updating.
--version Show up2date version information.
--whatprovides=dependenciesShow the packages that resolve the comma-separated list of
dependencies.
Table 2-2. Update Agent Command Line Arguments
2.3.5.1. Installing the Red Hat GPG key
The first time you run the graphical version of the Red Hat Update Agent, it prompts you to install the Red Hat GPG key. This key is required to authenticate the packages downloaded from Red
Hat Network. If you run the command line version the first time you start Red Hat Update Agent,
you need to install the Red Hat GPG key manually. If you do not have it installed, you will see the
following message:
Your GPG keyring does not contain the Red Hat, Inc. public key.
Without it, you will be unable to verify that packages Update Agent downloads
are securely signed by Red Hat.
Page 41

Chapter 2. Red Hat Update Agent 29
Note
GPG keys must be installed for each user. To install the key to use with Red Hat Network, import the
key while logged in as root.
The method for installing the key varies depending on your version of RPM. Starting with version
4.1, which shipped with Red Hat Enterprise Linux 3, you may import GPG keys using rpm, like so
(as root):
rpm --import /usr/share/doc/rpm-4.1/RPM-GPG-KE Y
For older versions of RPM, such as the one that came with Red Hat Enterprise Linux 2.1, use the gpg
command (as root):
/usr/bin/gpg --import /usr/share/rhn/RPM-GPG- KEY
If you need to download the Red Hat GPG key first, you may obtain it from
https://www.redhat.com/security/team/key.html . Here’s an example:
Type bits/keyID Date User ID
pub 1024D/650D5882 2001-11-21 Red Hat, Inc. (Security Response Team)
sub 2048g/7EAB9AFD 2001-11-21
-----BEGIN PGP PUBLIC KEY BLOCK----Version: GnuPG v1.2.1 (GNU/Linux)
mQGiBDv70vQRBADh701rf8WUzDG88kqlV/N5KQ1PF0amnODB/1EeuAD7n6bCBRmV
ekQWJCdfab0Rf1S+VsFg6IAAAmDIarVnacTLQzqCdGJqTpXm/rGVpLv+mCh+OmT9
QRFbjSzB0uPJOpiIvJwSS00D/wJ8XKzHkVNgW3DiJ9Qz2BHYszU2ISI6FwCgxY6d
IVjWT5jblkLNjtD3+fR024ED/i0e2knetTX3S9LjC+HdGvP8Eds92Ti2CnJLaFJk
Rp749PucnK9mzxPcO2jSHgdtjWAXst/st+gWFVbFmkjBQDVSd00B/xEwI1T1+LN8
V7R8BElBmg99IlJmDvA2BI/seXvafhzly9bxSHScFnceco/Az9umIs3NXwv3/yOm
ZakDBAC6SAGHBmpVkOdeXJDdb4LcbEhErFU3CpRCjZ6AOnFuiV1MGdulZXvEUgBA
I6/PDE5nBHfZY3zPjyLPZVtgYioJpZqcRIx/g+bX2O8kPqvJEuZ19tLCdykfZGpy
bsV7QdSGqBk3snNOizmFj543RaHyEbnwKWbNADhujWMeUAxN+7Q8UmVkIEhhdCwg
SW5jLiAoU2VjdXJpdHkgUmVzcG9uc2UgVGVhbSkgPHNlY2FsZXJ0QHJlZGhhdC5j
b20+iFcEExECABcFAj3GczYFCwcKAwQDFQMCAxYCAQIXgAAKCRBeVICDZQ1YghAU
AJoCeQfuMR2dKyLft/10O6qUs+MNLQCggJgdO8MUO2y11TWID3XOYgyQG+2InAQT
AQIABgUCPtyYpQAKCRDurUz9SaVj2e97A/0b2s7OhhAMljNwMQS4I2UWVGbgtxdu
D+yBcG/3mwL76MJVY7aX+NN/tT9yDGU+FSiQZZCL/4OFOHMvjpcDqfJY+zpTlBii
ZMAPJWTs2bB+0QaXxUgWlwW84GVf2rA6RSbvMLTbDjTH8t7J1RGP9zAqu8SgraTA
QbQdao6TNxVt+ohGBBMRAgAGBQI+3LjCAAoJECGRgM3bQqYOf5MAoIjiJDe+hDOj
9+jlR0qDs9lIi/C2AJ9SBBfd4A8hyR4z3lY7e0LzjWF51LkCDQQ7+9O3EAgA8tMs
xdUmuTfA+X78fMXh7LCvrL4Hi28CqvNM+Au81XJjDLNawZvpVmFlMmd9h0Xb5Jt2
BZWLR13rcDUByNdw1EWhVAzCz6Bp9Z3MIDhcP00iIBctIHn7YP9fi5vV0G03iryT
XE01mhWoBlC233wr3XHwsqxFfZzaCZqqNKTl0+PNfEAIzJRgtYiW8nzFTPpIR05E
oRn6EvmQfayOF2uYDX9Sk//lOD7T7RLtKjM/hPW/9NoCGwwROaG+VUzVv4aelh1L
dJGEjpFtdxcrOUMD8xbkuGMznu0mpDI+J2BUDh5n57yOyEMaGrQ0jfY1ZqdqDvZg
osY1ZHa6KlmuCWNTnwADBQf/XYhCicp6iLetnPv6lYtyRfFRpnK98w3br+fThywC
t81P2nKv8lio6OsRbksGc1gX8Zl6GoHQYfDe7hYsCHZPoWErobECFds5E9M7cmzV
TTyNTvrELrs07jyuPb4Q+mHcsYPILGR3M+rnXKGjloz+05kOPRJaBEBzP6B8SZKy
QNqEfTkTYU4Rbhkzz/UxUxZoRZ+tqVjNbPKFpRraiQrUDsZFbgksBCzkzd0YURvi
CegO2K7JPKbZJo6eJA10qiBQvAx2EUijZfxIKqZeLx40EKMaL7Wa2CM/xmkQmCgg
Hyu5bmLSMZ7cxFSWyXOst78dehCKv9WyPxHV3m4iANWFL4hGBBgRAgAGBQI7+9O3
AAoJEF5UgINlDViCKWcAoMCeYStWVKXJTytzHEL6Wl8rXr8WAKCHuapJIA4/eFsf
4ciWtjY8cO0v8Q==
Page 42

30 Chapter 2. Red Hat Update Agent
=yOVZ
-----END PGP PUBLIC KEY BLOCK-----
Save the text file and import it into your keyring using the method applicable for your version of RPM.
2.3.5.2. Manual Package Installation
If you chose to download the software updates with the Red Hat Update Agent or from the RHN
website, you must install them manually using RPM.
To install them, change to the directory that contains the downloaded packages. The default directory is /var/spool/up2date. Then, type the command rpm -Uvh *.rpm. When the packages are
finished installing, you can delete them if you wish. You do not need them anymore.
After installing the packages, you must update your System Profile so that you are not prompted to
download them again. Refer to Section 2.3.5.3 Synchronizing Your System Profile for details.
2.3.5.3. Synchronizing Your System Profile
If you configured the Red Hat Update Agent to install the latest packages, then your System Profile
stored by Red Hat Network will be updated after the packages are installed. However, if you only
download the latest RPM packages using the Red Hat Update Agent, download the RPM packages
from the website, or upgrade/install/remove RPM packages yourself, your System Profile will not be
updated automatically. You will need to send your updated System Profile to the RHN Servers.
To synchronize the RPM package list on your local system and on Red Hat Network, run the command:
up2date -p
After running this command, your RHN System Profile will reflect the latest software versions installed on your system.
2.3.5.4. Log File
The Red Hat Update Agent keeps a log of all the actions that it performs on your system in
the file /var/log/up2date. It uses the standard rotating log method. Thus, older logs are in
/var/log/up2date.1, /var/log/up2date.2, and /var/log/up2date.3. The log files store
actions performed by the Red Hat Update Agent such as when your RPM database is opened,
when it connects to Red Hat Network to retrieve information from your System Profile, which
packages are downloaded, which packages are installed using the Red Hat Update Agent, and
which packages are deleted from your system after installation. If you choose to install and delete
packages yourself, it will not be logged in this file. You should keep your own log of actions not
performed with the Red Hat Update Agent.
2.4. Configuration
The Red Hat Update Agent offers various options to configure its settings.
If you are not running the X Window System or prefer the command line version, skip to Section 2.4.2
Command Line Version.
Page 43

Chapter 2. Red Hat Update Agent 31
2.4.1. Using the Red Hat Update Agent Configuration Tool
You must be root to run the Red Hat Update Agent Configuration Tool. If you start the Red Hat
Update Agent Configuration Tool as a standard user, you will be prompted to enter the root password
before proceeding. The Red Hat Update Agent Configuration Tool can be started by typing the
command up2date-config at a shell prompt (for example, an xterm or a gnome-terminal).
2.4.1.1. General Settings
The General tab allows you to enable an HTTP Proxy Server. If your network connection
requires you to use an HTTP Proxy Server to make HTTP connections, select the Enable HTTP
Proxy option and type your proxy server in the text field with the format http://HOST:PORT.
For example, to use the proxy server http://squid.mysite.org on port 3128, you would enter
http://squid.mysite.org:3128 in the text field. Additionally, if your proxy server requires
a username and password, select the Use Authentication option and enter your username and
password in the respective text fields.
Figure 2-24. General Settings
In addition, RHN Proxy and Satellite customers have the option of selecting Red Hat Network Servers
here. These customers should refer to the RHN Client Configuration Guide for detailed instructions.
2.4.1.2. Retrieval/Installation Settings
The Retrieval/Installation tab allows you to customize your software package retrieval and package
installation preferences.
Warning
You must use Red Hat Update Agent Version 2.5.4 or higher to upgrade your kernel automatically.
Red Hat Update Agent will install the updated kernel and configure LILO or GRUB to boot the new
kernel the next time the system is rebooted.
Page 44

32 Chapter 2. Red Hat Update Agent
Figure 2-25. Retrieval/Installation Settings
The following package retrieval options can be selected (see Figure 2-25):
• Do not install packages after retrieval — download selected RPM packages to desired directory
and ignore the installation preferences
• Do not upgrade packages when local configuration file has been modified — if the configuration
file has been modified for a package such as apache or squid, do not attemp to upgrade it. This
option is useful if you are installing custom RPMs on your system and you do not want them
updated or reverted to the default Red Hat Enterprise Linux packages.
• Retrieve source RPM along with binary package — download both the source (*.src.rpm)
and the binary (*.[architecture].rpm) files
The following installation options are configurable (see Figure 2-25):
• Use GPG to verify package integrity — before installing the packages, verify Red Hat’s GPG
signature (highly recommended for security reasons)
• After installation, keep binary packages on disk — save binary packages in desired directory
instead of deleting them after installation
The following additional options are configurable from this tab:
• Override version stored in System Profile — override the Red Hat Linux version in your System
Profile
• Package storage directory — change the directory where packages are downloaded; the default
location is /var/spool/up2date
Page 45

Chapter 2. Red Hat Update Agent 33
2.4.1.3. Package Exceptions Settings
The Package Exceptions tab allows you to define which packages to exclude from the list of updated
RPM packages according to the package name or file name (see Figure 2-26).
To define a set of packages to be excluded according to the package name, enter a character string
including wild cards (*) in the Add new text field under in the Package Names to Skip section. A
wild card at the end of the character string means all packages beginning with the character string will
be excluded from the list. A wild card at the beginning of the character string means any packages
that end with the character string will be excluded from the list.
For example, if the string kernel* in the Package Names to Skip section, the Red Hat Update
Agent will not display any packages beginning with kernel.
To exclude packages by file name, follow the same rules except click the Add button next to the File
Names to Skip section.
Figure 2-26. Package Exceptions Settings
2.4.2. Command Line Version
The command line version of this tool performs the same function as the graphical version. It allows
you to configure the settings used by the Red Hat Update Agent and store them in the configuration
file /etc/sysconfig/rhn/up2date.
To run the command line version of the Red Hat Update Agent Configuration Tool, use the following command:
up2date --nox --configure
You will be presented with a list of options and their current values:
0. debug No
1. isatty Yes
Page 46

34 Chapter 2. Red Hat Update Agent
2. depslist []
3. networkSetup Yes
4. retrieveOnly No
5. enableRollbacks No
6. pkgSkipList [’kernel*’]
7. storageDir /var/spool/up2date
8. adminAddress [’root@localhost’]
9. noBootLoader No
10. serverURL https://xmlrpc.rhn.redhat.com/XMLRPC
11. fileSkipList []
12. sslCACert /usr/share/rhn/RHNS-CA-CERT
13. noReplaceConfig Yes
14. useNoSSLForPackage No
15. systemIdPath /etc/sysconfig/rhn/systemid
16. enableProxyAuth No
17. retrieveSource No
18. versionOverride
19. headerFetchCount 10
20. networkRetries 5
21. enableProxy No
22. proxyPassword
23. noSSLServerURL http://xmlrpc.rhn.redhat.com/XMLRPC
24. keepAfterInstall No
25. proxyUser
26. removeSkipList [’kernel*’]
27. useGPG Yes
28. gpgKeyRing /etc/sysconfig/rhn/up2date-keyring.gpg
29. httpProxy
30. headerCacheSize 40
31. forceInstall No
Enter number of item to edit
return to exit, q to quit without saving:
Enter the number of the item that you want to modify and enter a new value for the option. When you
finish changing your configuration, press [Enter] to save your changes and exit. Press [q] and then
[Enter] to quit without saving your changes.
Important
Although this isn’t configurable, users should still make note that the port used by the Red Hat Update
Agent is 443 for SSL (HTTPS) and 80 for non-SSL (HTTP). By default, up2date uses SSL only. For
this reason, users should ensure their firewalls allow connections over por t 443. To bypass SSL, in
/etc/sysconfig/rhn/up2date change the protocol for serverURL from https to http.
2.5. Registering with Activation Keys
In addition, to the standard Red Hat Update Agent interface, up2date offers a utility aimed at batch
processing the registration of systems: activation keys. Each unique key can be used to register Red
Hat Enterprise Linux systems, entitle them to an RHN service level, and subscribe them to specific
channels and system groups, all in one action.
Page 47

Chapter 2. Red Hat Update Agent 35
Thus, channel and group subscriptions can be automated along with registration, thereby bypassing
entitlement and registration through either the Red Hat Network Registration Client or the Red Hat
Update Agent, both of which offer the activation keys utility rhnreg_ks as part of their packages.
Note
Systems running Red Hat Enter prise Linux 2.1 need version 2.9.3-1 or higher of the rhn_register
package. It is highly recommended you obtain the latest version before using activation keys.
Before using an activation key, you must first generate one through the RHN website. Refer to Section
6.4.7 Activation Keys —
for precise steps.
Touse an activation key, as root from a shell prompt on the system to be registered, run the rhnreg_ks
command followed by the key. For example:
rhnreg_ks --activationkey=7202f3b7d218cf59b764f9f6e9fa281b
Systems running Red Hat Enterprise Linux 2.1 will use the --serialnumber instead of
--activationkey, like so:
rhnreg_ks --serialnumber=7202f3b7d218cf59b764f9f6e9fa281b
In addition, Provisioning-entitled systems may use multiple activation keys at once, either at the command line or within kickstart profiles, to include a variety of values without creating a special key for
the desired results. To do this, specify the keys separated by commas, like this:
rhnreg_ks --activationkey=7202f3b7d218cf59b764f9f6e9fa281b,\
39f41081f0329c20798876f37cb9p6a3
Note
The trailing backslash (\) in this command example is a continuation character; it may safely be
omitted.
Refer to Section 6.4.7.2 Using Multiple Activation Keys at Once — to understand how differences
in activation keys are handled.
This command performs all the actions of the Red Hat Network Registration Client and the registration function of the Red Hat Update Agent. Do not run either of these applications for registration
after running rhnreg_ks.
A System Profile, including software and hardware information, is created for the system and sent
to the RHN Servers along with the unique activation key. The system is registered with RHN under
the account used to generate the key, entitled to an RHN service offering, and subscribed to the RHN
channels and system groups selected during key generation. The system will not be subscribed to
channels that contain packages not suitable for the system. For example, a Red Hat Enterprise Linux
2.1 system cannot be subscribed to the Red Hat Enterprise Linux 3 channel.
The unique Digital Certificate for the system is generated on the system in
/etc/sysconfig/rhn/systemid.
When using activation keys to assign channels, a couple of rules should be kept in mind:
Page 48

36 Chapter 2. Red Hat Update Agent
• A key may specify either zero or one base channel. If specified, it must be a custom base channel.
If not, the base channel corresponding to the system’s Red Hat distribution will be chosen. For
instance, you may not take a Red Hat Enterprise Linux 2.1 system and subscribe it to the Red Hat
Enterprise Linux 3 channel.
• A key may specify any number of child channels. For each child channel, subscription is attempted.
If the child channel matches the system’s base channel, subscription succeeds. If it does not, the
subscription fails silently. Refer to Section 6.6 Channels for more information.
• Keys may be modified by any user with the role of Activation Key Administrator or Organization
Administrator (or both). These permissions are set through the Users tab of the RHN website. Refer
to Section 6.8 Users —
• Systems registered by activation keys are tied to the organization or overall account in which the
for details.
key was created, not the key itself. After registration, a key can be safely deleted without any effect
on the systems it was used to register.
Page 49

Chapter 3.
Red Hat Network Daemon
The Red Hat Network Daemon (rhnsd) periodically connects to Red Hat Network to check for updates and notifications. The daemon, which runs in the background, is typically started from the initialization scripts in /etc/init.d/rhnsd or /etc/rc.d/init.d/rhnsd.
Tip
Provisioning-entitled systems served by an RHN Satellite Server may have actions immediately initiated or pushed to them. Refer to Section 6.4.2.6.1 System Details
enabling this feature.
To check for updates, rhnsd runs an external program called rhn_check located in /usr/sbin/.
This is a small application that actually makes the network connection to RHN. The Red Hat Network
Daemon does not listen on any network ports or talk to the network directly. All network activity is
done via the rhn_check utility.
3.1. Configuring
The Red Hat Network Daemon can be configured by editing the /etc/sysconfig/rhn/rhnsd
configuration file. This is actually the configuration file the rhnsd initialization script uses. The most
important setting offered by the daemon is its check-in frequency. The default interval time is four
hours (240 minutes). If you modify the configuration file, you must (as root) restart the daemon with
the command service rhnsd restart or /etc/rc.d/init.d/rhnsd restart.
Important
The minimum time interval allowed is one hour (60 minutes). If you set the interval below one hour, it
will default to four hours (240 minutes).
Details for instructions on
3.2. Viewing Status
You can view the status of the rhnsd by typing the command service rhnsd status or
/etc/rc.d/init.d/rhnsd status at a shell prompt.
3.3. Disabling
To disable the daemon, (as root) run the ntsysv utility and uncheck rhnsd. You can also (as root)
execute the command chkconfig rhnsd off. Using these two methods will only disable the service the next time the system is started. To stop the service immediately, use the command service
rhnsd stop or /etc/rc.d/init.d/rhnsd stop.
Page 50

38 Chapter 3. Red Hat Network Daemon
3.4. Troubleshooting
If you are seeing messages indicating checkins are not taking place, the RHN client on your system is
not successfully reaching Red Hat Network. Make certain:
• your client is configured correctly.
• your system can communicate with RHN via SSL (port 443). You may test this by running the
following command from a shell prompt:
telnet xmlrpc.rhn.redhat.com 443
• the Red Hat Network Daemon is activated and running. You may ensure this by running the follow-
ing commands:
chkconfig --level 345 rhnsd on
service rhnsd start
If these are correct and your systems still indicate they are not checking in, please contact our
technical support team.
Page 51

Chapter 4.
Red Hat Network Alert Notification Tool
The Red Hat Network Alert Notification Tool is a notifier that appears on the panel and alerts users
when software package updates are available for their systems. The list of updates is retrieved from
the RHN Servers. The system does not have to be registered with Red Hat Network to display a list
of updates; however, retrieving the updates with the Red Hat Update Agent requires registration
with Red Hat Network and a subscription to an RHN service offering. The notifier does not send any
identifiable information about the user or the system to the RHN Servers.
To use the Red Hat Network Alert Notification Tool, you must install the rhn-applet RPM package and use the X Window System.
Starting with Red Hat Enterprise Linux 3, the Red Hat Network Alert Notification Tool appears on
the panel by default as shown in Figure 4-1.
Figure 4-1. GNOME Panel with Red Hat Network Alert Notification Tool
If it does not appear on the panel, you can add it:
• In Red Hat Enterprise Linux 3, select the Main Menu Button => System Tools => Red Hat
Network Alert Icon. To ensure the icon appears on subsequent sessions, select the Save current
setup checkbox when logging out.
• In Red Hat Enterprise Linux 2.1, select the Main Menu Button => Panel => Add to Panel =>
Applet => Red Hat Network Monitor. To move it around the panel, right-click on the applet,
select Move, move the mouse left and right until it is in the desired location, and click the mouse
to place the applet.
4.1. Configuring the Applet
The first time the Red Hat Network Alert Notification Tool is run, a configuration wizard starts. It
displays the terms of service and allows the user to configure an HTTP proxy as shown in Figure 4-2.
Page 52

40 Chapter 4. Red Hat Network Alert Notification Tool
Figure 4-2. HTTP Proxy Configuration
If your network connection requires you to use an HTTP Proxy Server to make HTTP connections, on the Proxy Configuration screen, type your proxy server in the text field with the format HOST:PORT. For example, to use the proxy server http://squid.mysite.org on port 3128, enter
squid.mysite.org:3128 in the text field. Additionally, if your proxy server requires a username and password, select the Use Authentication option and enter your username and password in
the respective text fields.
Tip
To run the configuration wizard again, right-click on the applet, and select Configuration.
Your preferences are written to the file .rhn-applet.conf in your home directory. The
Red Hat Network Alert Notification Tool also uses the system-wide configuration file
/etc/sysconfig/rhn/rhn-applet. Do not modify the system-wide configuration file; it is
automatically generated by the application.
You can also configure the Red Hat Network Alert Notification Tool not to list specific packages.
To configure which packages to ignore, click on the applet, and select the Ignored Packages tab.
4.2. Notification Icons
The applet displays a different icon, depending on the status of the updates. Refer to Table 4-1 for
details.
Icon Description
Updates are available
System is up-to-date
Checking for updates
Error has occurred
Table 4-1. Red Hat Network Alert Notification Tool Icons
Page 53

Chapter 4. Red Hat Network Alert Notification Tool 41
If you see the icon, it is highly recommended that you apply the updates. Refer to Section 4.4
Applying Updates for information on applying updates.
If you have scheduled updates to be installed, you can watch the applet icon to determine when updates
are applied. The icon changes to the
If you apply a kernel update (or the kernel update is automatically applied), the applet will display the
until the system is rebooted with the new kernel. If you click on the applet, the Available Updates
tab displays a list of packages that can be updated on your system.
icon after the Errata Updates are applied.
4.3. Viewing Updates
Clicking on the Red Hat Network Alert Notification Tool displays a list of available updates. To
alter your list of excluded packages, click the Ignored Packages tab and make your modifications.
Figure 4-3. Available Updates
4.4. Applying Updates
If the system is registered with RHN and entitled to a service offering, you can apply the Errata
Updates with the Red Hat Update Agent. To launch the Red Hat Update Agent, click on the applet,
and then click on the Launch up2date button. You can also right-click on the icon and select Launch
up2date. For more information on the Red Hat Update Agent, refer to Chapter 2 Red Hat Update
Agent.
4.5. Launching the RHN Website
The simplest way to obtain a comprehensive view of your system’s status is to access the RHN website. This can be accomplished through the Red Hat Network Alert Notification Tool by rightclicking on it and selecting RHN Website. For more information on the RHN website, refer to Section
6.1 Navigation.
Page 54

42 Chapter 4. Red Hat Network Alert Notification Tool
Page 55

Chapter 5.
Red Hat Network Registration Client
Before you begin using Red Hat Network, you need to create a username, password, and System
Profile. The Red Hat Network Registration Client walks you through this process.
Warning
Only systems running Red Hat Enterprise Linux 2.1 need to use this separate Red Hat Network
Registration Client before starting the Red Hat Update Agent. Systems running Red Hat Enterprise
Linux 3 have this registration functionality built into the Red Hat Update Agent. After registering your
system, refer to Chapter 2 Red Hat Update Agent for instructions on star ting the Red Hat Update
Agent and begin steps listed in Section 2.3 Setup and Use.
5.1. Configuring the Red Hat Network Registration Client
To start the graphical interface for configuring the application to connect through an HTTP proxy
server, type the following command at a shell prompt:
rhn_register --configure
The window shown in Figure 5-1 will appear.
Figure 5-1. Red Hat Network Registration Client Configuration
To start the command line version, use the command:
rhn_register --nox --configure
Page 56

44 Chapter 5. Red Hat Network Registration Client
It has more configuration options than the graphical version.
You will be presented with a list of options and their current values:
0. enableProxyAuth No
1. noSSLServerURL http://xmlrpc.rhn.redhat.com/XMLRPC
2. oemInfoFile /etc/sysconfig/rhn/oeminfo
3. enableProxy No
4. networkSetup Yes
5. httpProxy
6. proxyUser
7. serverURL https://xmlrpc.rhn.redhat.com/XMLRPC
8. proxyPassword
9. debug No
Enter number of item to edit
return to exit, q to quit without saving:
Enter the number of the item that you want to modify, and enter a new value for the option. When
you finish changing your configuration, press [Enter] to save your changes and exit. Press [q] and then
[Enter] to quit without saving your changes.
The most common options configured are enableProxy and httpProxy to enable a proxy server.
To enable a proxy server, change the value for enableProxy to Yes and the value of httpProxy to
the name of the proxy server and port number in the format http://HOST:PORT. For example, to
use the proxy server http://squid.mysite.org on port 3128, you would change the value to
http://squid.mysite.org:3128.
If you require a proxy username and password, set enableProxyAuth to Yes to enable
username/password authentication for the proxy, and set proxyUser and proxyPassword to the
appropriate username and password for the proxy.
To bypass SSL, in /etc/sysconfig/rhn/rhn_register change the protocol for serverURL
from https to http.
5.2. Starting the Red Hat Network Registration Client
You must be root to register a system with RHN. If you start the Red Hat Network Registration
Client as a standard user, you will be prompted to enter the root password before proceeding.
Important
If your username is part of a larger organizational account, you should take caution when registering
your systems. By default, all systems registered with the Red Hat Network Registration Client end
up in the Ungrouped section of systems visible only to Organization Administrators. To ensure you retain management of these systems, Red Hat recommends your organization create an activation key
associated with a specific system group and grant you permissions to that group. You may then register your systems using that activation key and find those System Profiles within RHN immediately.
Refer to Section 2.5 Registering with Activation Keys for instructions.
To start the Red Hat Network Registration Client, use one of the following methods:
1. On the GNOME desktop, go to the Main Menu Button (on the Panel) => Programs => System
=> Red Hat Network
2. On the KDE desktop, go to the Main Menu Button (on the Panel) => System => Red Hat
Network
Page 57

Chapter 5. Red Hat Network Registration Client 45
3. Type the command rhn_register at a shell prompt (for example an XTerm or GNOME
terminal)
4. If you are not running the X Window System, type the command rhn_register at a virtual
console or remote terminal. Refer to Section 5.7 Text Mode RHN Registration Client for further
details.
Caution
You must use Python 1.5.2-24 or later with Secure Sockets Layer (SSL) support. If not, the information you transfer will not be encrypted. If you have an earlier version of Python, you will see the
message shown in Figure 5-2. To determine the version of Python on your system, use the command
rpm -q python. It is strongly recommended you use Python 1.5.2-24 or later.
Figure 5-2. Use Python 1.5.2-24 or later
If you have already registered your system and try to register it again, the dialog box shown in
Figure 5-3 will appear. If you continue, it will overwrite your existing Digital Certificate file
(/etc/sysconfig/rhn/systemid), and you will create a different System Profile. You will no
longer be able to use your previous System Profile — be sure this is what you want to do before you
choose Yes.
If you overwrite an existing system registration, you can delete the unused profile via the website at
https://rhn.redhat.com.
Figure 5-3. Warning: This System Already Registered
The opening screen for the Red Hat Network Registration Client gives you a brief overview of the
services available and the steps required to register (see Figure 5-4). Click Next to continue with the
registration process. If you click Cancel, the registration process will end and no information will be
sent.
Page 58

46 Chapter 5. Red Hat Network Registration Client
Figure 5-4. Welcome Screen
Red Hat is committed to protecting your privacy (see Figure 5-5). The information gathered during
the Red Hat Network registration process is used to create a System Profile. The System Profile is
essential if you wish to receive update notifications about your system.
Page 59

Chapter 5. Red Hat Network Registration Client 47
Figure 5-5. Red Hat Privacy Statement
5.3. Registering a User Account
Before you can create a System Profile, you must create a user account. The only required information
in this section is a unique username, password, and a valid email address.
In the screen shown in Figure 5-7, you must choose a username and password. Once logged in to Red
Hat Network, you can modify your preferences, view your existing System Profile, or obtain the latest
Red Hat software packages. You must choose a unique username. If you enter one already in use, you
will see an error message (see Figure 5-6). Try different usernames until you find one that has not
been used.
Figure 5-6. Error: Username Already Exists
Page 60

48 Chapter 5. Red Hat Network Registration Client
Note
If you are already a member of redhat.com, you can use the same user name and password. However, you will still need to continue with the registration process to create your System Profile.
Your username has the following restrictions:
• Cannot contain any spaces
• Cannot contain the characters &, +, %, or ’
• Is not case-sensitive, thereby eliminating the possibility of duplicate usernames differing only by
capitalization
In addition, the following restrictions apply to both your username and password:
• Must be at least four characters long
• Cannot contain any tabs
• Cannot contain any line feeds
Passwords are case-sensitive for obvious reasons.
If you have already registered a machine and created a System Profile, you can add a new machine to
your account. Run the Red Hat Network Registration Client on the new machine you wish to add,
and enter your existing Red Hat Network username and password. The new machine will be added to
your existing account, and you can log into Red Hat Network with your username and password to
view all your systems simultaneously.
Figure 5-7. Create a Unique Username and Password
Page 61

Chapter 5. Red Hat Network Registration Client 49
Most users can leave the Org Info section blank. If you have an existing organization account, work
with your Organization Administrator to ensure your system is added to that account. This will require entering your organization’s ID and password in the provided text fields. If the values are valid,
the system will be added to the organization’s Red Hat Network account. Your Organization Administrator can then create your user account through the Users category of the RHN website. Refer to
Section 6.8.2.1 Create User —
for instructions.
Click Next to continue.
5.4. Registering a System Profile
Now that you have a user account, you can create a System Profile that consists of hardware and
software information about your Red Hat Linux system. The software System Profile information is
used by Red Hat Network to determine what software update notifications you receive.
5.4.1. Hardware System Profile
After creating a username and password for your Red Hat Network account, the Red Hat Network
Registration Client probes your system for the following information:
• Red Hat Linux version
• Hostname
• IP address
• CPU model
• CPU speed
• Amount of RAM
• PCI devices
• Disk sizes
• Mount points
The next step is choosing a profile name for your system as shown in Figure 5-8. The default value
is the hostname for the system. You may modify this to be a more descriptive string, such as Email
Server for Support Team, if you find it more helpful. Optionally, you can enter a computer
serial or identification number for the system.
If you do not wish to include information about your hardware or network in your System Profile,
deselect Include information about hardware and network (see Figure 5-8).
Click Next to continue with the registration process.
Page 62

50 Chapter 5. Red Hat Network Registration Client
Figure 5-8. System Profile - Hardware
5.4.2. Software System Profile
The software System Profile consists of a list of RPM packages for which you wish to receive notifications. The Red Hat Network Registration Client shows you a list of all RPM packages listed in
the RPM database on your system and then allows you to customize the list by deselecting packages.
5.4.2.1. Gathering RPM Database Information
Only those packages you choose during this part of the registration will be included in your System
Profile, and you will only receive notifications about the packages in your System Profile. Thus, if
you use an older version of a package and deselect it from the list, it will not be replaced with a newer
version. This RPM list can be modified through the Red Hat Network website or by using the Red
Hat Update Agent. Figure 5-9 shows the progress bar you will see while the Red Hat Network
Registration Client gathers a list of the RPM packages installed on your system. This operation may
take some time depending on your system.
Figure 5-9. Registration Wizard
Once the RPM package list is built, the list will be displayed as shown in Figure 5-10. Deselecting
Include RPM Packages installed on this system in my System Profile will omit this information
from your System Profile.
Page 63

Chapter 5. Red Hat Network Registration Client 51
Figure 5-10. RPM Package Information
5.4.2.2. Choosing RPM Packages to Exclude from the System Profile
By default, all RPM packages in your RPM database are included in your System Profile to be updated by Red Hat Network. To exclude a package, uncheck the package from the list by clicking the
checkbox beside the package name. For example, Figure 5-11 shows that the procmail, procps, and
psgml packages have been omitted from the package list.
Choose which packages to exclude, if any, from the System Profile, and click Next to continue with
the registration process.
Page 64

52 Chapter 5. Red Hat Network Registration Client
Figure 5-11. Choose which RPM Packages to Exclude from System Profile
5.5. Finishing Registration
As seen in Figure 5-12, the last step of registration is to confirm that you want to send your System
Profile to the Red Hat Network. If you choose Cancel at this point, no information will be sent.
Clicking Next will submit your RHN System Profile.
Page 65

Chapter 5. Red Hat Network Registration Client 53
Figure 5-12. Finished Collecting Information for System Profile
Figure 5-13 shows the progress bar you will see while your profile is being sent. This process may
take some time depending on your connection speed.
Figure 5-13. Send System Profile to Red Hat Network
You will know your System Profile has been successfully sent when you see the Registration Finished screen (Figure 5-14). Click Finish to exit the Red Hat Network Registration Client.
After completing the registration, you must entitle your system to an RHN service level. Refer to
Section 5.6 Entitling Your System for details.
Page 66

54 Chapter 5. Red Hat Network Registration Client
Figure 5-14. Registration Finished
5.6. Entitling Your System
Now that you have registered your system, it must be entitled before you can receive updated packages. In other words, you must subscribe it to a service level offering. Everyone automatically receives
one free Demo entitlement after creating an account by registering a system for RHN or creating a
redhat.com account.
To entitle a system, go to http://rhn.redhat.com and log in using the same username and password you
just used in the Red Hat Network Registration Client. Click Systems on the top navigation bar and
then Systems Entitlements in the left navigation bar. The System Entitlements page displays the
number of available entitlements, or subscriptions, at the bottom.
If you have one or more subscriptions left, make a selection from the dropdown menu under the
Entitlement column beside the name of the system you just registered. Only increases in entitlement
levels are allowed. Systems cannot be re-entitled to a lower entitlement level. For instance, a system
entitled to the Update service level can be promoted to the Management level, but this action cannot
be reversed. Then click the Update Entitlements button at the bottom of the page.
Warning
Changing a system’s entitlement is an irreversible action. You may be unable to change the entitlement levels of some systems. For more information, refer to the RHN entitlement policy linked from
the System Entitlements page.
The number of entitlements remaining decreases, and your system becomes ready to use the Red Hat
Update Agent and RHN website. Refer to Chapter 2 Red Hat Update Agent and Chapter 6 Red Hat
Network Website for details on how to use them. If you do not have any entitlements left, click the Buy
more system entitlements now link at the top of the System Entitlements page to make additional
purchases.
Page 67
Chapter 5. Red Hat Network Registration Client 55
5.7. Text Mode RHN Registration Client
If you are not running the X Window System, the Red Hat Network Registration Client starts in
text mode.
You can force the Red Hat Network Registration Client to run in text mode with the command:
rhn_register --nox
The screens for the text mode Red Hat Network Registration Client are almost identical to the
screens for the graphical Red Hat Network Registration Client. Some of the text in the text mode
version is more concise due to lack of space in the interface. However, there is an equal number of
screens and fields in both versions. Thus, if you are using the text mode version, you can still follow
the instructions that begin in Section 5.2 Starting the Red Hat Network Registration Client.
Figure 5-15. Text Mode Welcome Screen
Page 68

56 Chapter 5. Red Hat Network Registration Client
Page 69

Chapter 6.
Red Hat Network Website
You can use the Red Hat Network website to manage multiple Red Hat Enterprise Linux systems
simultaneously, including viewing Errata Alerts, applying Errata Updates, and installing packages.
This chapter seeks to identify all of categories, pages, and tabs within the website and explain how to
use them.
6.1. Navigation
The top navigation bar is divided into tabs of primary categories containing pages linked from the
left navigation bar.
6.1.1. Entitlement Views
Keep in mind, since this guide covers all entitlement levels, some tabs, pages, and even whole categories described here may not be visible to you. For this reason, icons are used here to identify which
functions are available to each entitlement level.
Icon Entitlement
Management or higher
Provisioning
Monitoring
Table 6-1. Entitlement Icons
If no icon follows a category, page, or tab label within this chapter, the area described is available to
all Red Hat Network users. If an icon does follow, the associated entitlement is needed. Remember
that Provisioning inherits all of the functions of Management.
If an icon precedes a paragraph, only the specific portion of the page or tab discussed afterward
required the indicated entitlement level. When a page or tab is associated with a particular entitlement
level, all of its tabs and subtabs require at least the same entitlement level but may need a higher
entitlement. Regardless, each tab is identified separately.
6.1.2. Categories and Pages
This section summarizes all of the categories and primary pages (those linked from the top and left
navigation bars) within the RHN website. It does not list the many subpages, tabs and subtabs accessible from the left navigation bar and individual pages. Each area of the website is explained in detail
later in this chapter:
• Your RHN — View and manage your primary account information and obtain help.
• Your RHN — Obtain a quick overview of your account. It notifies you if your systems need
attention, provides a quick link to go directly to them, and displays the most recent Errata Alerts
for your account.
• Your Account — Update your personal profile and addresses.
Page 70

58 Chapter 6. Red Hat Network Website
• Your Preferences — Indicate if you wish to receive email notifications about Errata Alerts for
your systems, set how many items are displayed at one time for lists such as system lists and
system group lists, set your time zone, and identify your contact options.
• Purchase History — View a history of your entitlements, including the expiration date and the
number available.
• Help — Learn how to use Red Hat Network and receive support if needed.
• Systems — Manage your systems here.
• Overview —
— View a summary of your systems or system groups showing how many
Errata Alerts each system has and which systems are entitled.
• Systems — Select and view subsets of your systems by specific criteria, such as Out of Date,
Unentitled, Ungrouped, and Inactive.
• System Groups —
• System Set Manager — — Perform actions on currently selected systems.
• System Entitlements — Change the entitlement levels of systems.
• Advanced Search — — Quickly search all of your systems by specific criteria, such as
— List your system groups. Create additional groups.
name, hardware, devices, system info, networking, packages, and location.
• Activation Keys —
— Generate an activation key for an RHN-entitled system. This activation key can be used to grant a specified level of entitlement or group membership to a newly
registered system with the rhnreg_ks command.
• Stored Profiles — — View system profiles used to provision systems.
• Custom System Info — — Create and edit system information keys containing completely
customizable values that can be assigned while provisioning systems.
• Kickstart —
— Display and modify various aspects of kickstart profiles used in provisioning
systems.
• Errata — View and manage Errata Alerts here.
• Errata — List Errata Alerts and download associated RPMs.
• Advanced Search — Search Errata Alerts based on specific criteria, such as synopsis, advisory
type, and package name.
• Channels — View and manage the available RHN channels and the files they contain.
• Software Channels — View a list of all software channels and those applicable to your systems.
• Channel Entitlements — View a list of software channels for which you have paid, as well as
the systems associated with each.
• Easy ISOs — Access priority downloading of Red Hat ISO images. ISO images are used to
write to CD.
• Package Search — Search packages using all or some portion of the package name.
• Manage Config Channels —
• Schedule — Keep track of your scheduled actions.
— Create and edit channels used to deploy configuration files.
Page 71

Chapter 6. Red Hat Network Website 59
• Pending Actions — List scheduled actions that have not been completed.
• Failed Actions — List scheduled actions that have failed.
• Completed Actions — List scheduled actions that have been completed. Completed actions can
be archived at any time.
• Archived Actions — List completed actions that have been selected to archive.
• Users —
• User List — — List users for your organization.
• Monitoring —
• Probe Status — — View probes by state.
• Notification — — View contact methods established for yor organization.
• Scout Config Push — — Reconfigure your monitoring infrastructure.
• Global Config — — Change organization-wide monitoring settings.
— View and manage users for your organization.
— Run probes and receive notifications regarding systems.
6.1.3. Errata Alert Icons
Throughout Red Hat Network you will see three Errata Alert icons. represents a Security Alert.
represents a Bug Fix Alert. represents an Enhancement Alert.
In the Your RHN page, click on the Errata advisory to view details about the Erratum or click on the
number of affected systems to see which are affected by the Errata Alert. Both links take you to tabs
of the Errata Details page. Refer to Section 6.5.2.2 Errata Details for more information.
6.1.4. Quick Search
In addition to the Advanced Search functionality offered within some categories, the RHN website
also offers a Quick Search tool near the top of each page. To use it, select the item type (such as packages) and type a keyword that will be used to look for a name match. Then click the Search button.
Your results will appear at the bottom of the page. Refer to the appropriate category for instructions
on using these results.
6.1.5. Systems Selected
Also near the top of the page is a tool for keeping track of the systems you’ve selected for use in the
System Set Manager. It identifies the number selected at all times and provides the means to work with
them. Clicking the Clear button deselects all systems, while clicking the Manage button launches the
System Set Manager with your selected systems in place.
These systems can be selected in a number of ways. Only systems entitled to the Management and
Provisioning service are eligible for selection. On all system and system group lists, a Select column
exists for this purpose. Select the checkboxes next to the systems or groups and click the Update List
button below the column. Each time, the Systems Selected tool at the top of the page will change to
reflect the new number of systems ready for use in the System Set Manager. Refer to Section 6.4.4
System Set Manager — for details.
Page 72

60 Chapter 6. Red Hat Network Website
6.1.6. Lists
The information within most categories is presented as lists. These lists have some common features
for navigation. For instance, you can navigate through virtually all lists by clicking the back and next
arrows above and below the right side of the table. Some lists also offer the ability to retrieve items
alphabetically by clicking the letters above the table.
6.2. Logging into the RHN Website
In a Web browser, go to http://rhn.redhat.com. The page shown in Figure 6-1 will be displayed.
Figure 6-1. RHN Website
If you have not registered a system yet or do not have a redhat.com account, create a new account by
clicking Create Account. After creating a new user account, you must register your system before
using RHN. Refer to Chapter 2 Red Hat Update Agent for step-by-step instructions.
After registering your system with Red Hat Network, go back to http://rhn.redhat.com and complete
the username and password fields with the same information established during registration. Click the
Sign In link near the top to display the fields, if they are not already visible. Once complete, click the
Sign In button.
6.3. Your RHN
After logging into the website of Red Hat Network, the first page to appear is Your RHN. This page
contains important information about your systems, including summaries of system status, actions,
and Errata Alerts.
Page 73

Chapter 6. Red Hat Network Website 61
Tip
If you are new to the RHN website, it is recommended that you read Section 6.1 Navigation to become
familiar with the layout and symbols used throughout the website.
Figure 6-2. Your Red Hat Network
The top of the page shows how many systems need attention, provides a link to quickly view those
systems, and displays a summary of scheduled actions. Refer to Section 6.4.2 Systems for information
on using the Systems pages.
The System Summary section of Your RHN page provides the following information:
• Total Systems — Number of total systems that you have registered for your organization.
• Out of Date Systems — Number of registered systems that have applicable Errata Alerts that have
not been applied.
• Unentitled Systems — Number of systems that are not entitled.
• Ungrouped Systems — Each system may be a member of one or more groups. The number of
ungrouped systems refers to systems that are not yet members of any system group.
• Inactive Systems — Number of systems that have not checked into RHN for 24 hours or more.
Refer to Section 6.4.2.5 Inactive for details.
Page 74

62 Chapter 6. Red Hat Network Website
The Action Summary section provides the following information about events scheduled in the past
week:
• Recently Failed Actions — Number of scheduled actions that did not succeed.
• Pending Actions — Number of scheduled actions that have not yet been completed.
• Recently Completed Actions — Number of scheduled actions that succeeded.
The System Groups section gives you access to the groups of systems you establish. Clicking on the
links in this section takes you to the System Group Details pages. Refer to Section 6.4.3.3 System
Group Details —
for more information.
The Errata section lists all and relevant Errata Alerts. You may toggle between All and Relevant by
clicking the View All or View Relevant link at the top of the table. This view is retained until you
toggle it by again clicking the link.
Relevant Errata are those derived from software channels to which your systems are subscribed. They
refer to versions of packages that are newer than those installed on the systems. To goto a complete list
of applicable Errata Alerts for your systems stored in the Errata category, click View All Relevant
Errata in the bottom right-hand corner.
You can return to this page by clicking Your RHN on the left navigation bar.
6.3.1. Your Account
The Your Account page allows you to modify your personal information, such as name, password,
and title. To modify any of this information, merely make the changes in the appropriate text fields
and click the Update button in the bottom right-hand corner.
Remember, if you change your Red Hat Network password (the one used to log into RHN and redhat.com), you will not see your new one as you type it for security reasons. Also for security, your
password is represented by 12 asterisks no matter how many characters it actually contains. Replace
the asterisks in the Password and Password Confirmation text fields with your new password.
6.3.1.1. Addresses
The Addresses page allows you to manage your mailing, billing and shipping addresses, as well as
the associated phone numbers. Just click Edit this address below the address to be modified, make
the changes, and click Update Address.
6.3.1.2. Change Email
The email address listed in the Your Account page is the address Red Hat Network sends email
notifications to, if you select to receive Errata Alerts or daily summaries for your systems on the Your
Preferences page.
To change your preferred email address, click Change Email in the left navigation bar. You will then
be asked for the new email address. Enter it and click the Update button. A confirmation email will
be sent to the new email address; responding to the confirmation email will validate the new email
address. Note that false email addresses such as those ending in "@localhost" are filtered and rejected.
6.3.1.3. Account Deactivation
The Account Deactivation page provides a means to cancel your Red Hat Network service. It presents
steps for manual deactivation or instructions for contacting Customer Service, depending on your level
of service. Deactivation of the account should occur within one business week.
Page 75

Chapter 6. Red Hat Network Website 63
6.3.2. Your Preferences
The Your Preferences page allows you to configure Red Hat Network options, including:
• Email Notifications — Determine whether you want to receive email every time an Errata Alert is
applicable to one or more systems in your RHN account.
Important
This setting also enables Management and Provisioning customers to receive a daily summar y
of system events. These include actions affecting packages, such as scheduled Errata Updates,
and system reboots or failures to check in. In addition to selecting this checkbox, you must identify
each system to be included in this summary email. (By default, all Management and Provisioning
systems are included in the summary.) This can be done either through the System Details page
individually or through the System Set Manager interface for multiple systems at once. Note that
RHN will send these summaries only to verified email addresses. To disable all messages, simply
deselect this checkbox.
• RHN List Page Size — Maximum number of items that will appear in a list on a single page. If more
items are in the list, clicking the Next button will display the next group of items. This preference
applies to system lists, Errata lists, package lists, and so on.
• Time Zone — Set your time zone so that scheduled actions are scheduled according to the time in
your time zone.
• Red Hat Contact Options — Identify what ways (email, phone, fax, or mail) Red Hat may contact
you.
After making changes to any of these options, click the Save Preferences button on the bottom righthand corner.
6.3.3. Purchase History
The Purchase History page displays a list of your RHN purchases, including the dates bought and
expired and the number purchased.
6.3.4. Help
The Help pages provide access to the full suite of documentation and support available to RHN users.
Click Help in the Your RHN category to see a list of options available to you.
6.3.4.1. Help Desk
The Help Desk page summarizes the help options available within this section. Click either the links
within this page or the buttons on the left navigation bar to explore further.
6.3.4.2. Quick Start Guide
The Quick Start Guide page contains a brief overview of Red Hat Network and its many features. If
you are unfamiliar with RHN, it is recommended you read this guide in its entirety. Topics covered
include registering your systems, applying Errata Updates, using one-click updates, and troubleshooting.
Page 76

64 Chapter 6. Red Hat Network Website
6.3.4.3. FAQ
The FAQ page lists Frequently Asked Questions and answers to those questions. These are broken
down into the following categories, each represented by a separate button and page: Top Ten, General,
Account Management, Getting Started, Service Levels, Using RHN, Technical Questions, Management Service, Privacy/Legal, Policies, Definitions, and All.
6.3.4.4. Reference Guide
The Reference Guide page takes you to this same document, the most comprehensive set of instructions for using Red Hat Network. Note that links to other technical guides may also appear in the left
navigation bar, depending on the entitlement level and product offering of the account with which you
logged in.
6.3.4.5. Contact RHN
The Contact RHN page provides methods by which customers may obtain help. Specifically, logged
out users have access to the FAQ, Customer Service email address, and rhn-users mailing list. Logged
in Demo customers have access to the above, as well as an online form that can be submitted to rhnfeedback or the Customer Service address. Logged in paid users have access to all of the above. In
addition, the online form enables them to submit requests for technical support.
The Customer Service address handles billing and purchasing questions, while the rhn-users list enables customers to help one another. The rhn-feedback address collects customer input and provides
an auto response, but nothing more. The technical support form ensures the customer will get a personalized and helpful response in a timely manner.
6.3.4.6. Terms & Conditions
The Terms & Conditions page displays the RHN Network Services Useand Subscription Agreement.
6.3.4.7. Outage Policy
The Outage Policy page identifies scheduled maintenance windows for Red Hat Network and provides the means to subscribe to the Email Outage List (rhn-outage-list@redhat.com) to be notified of
emergency and other unscheduled outages.
6.3.4.8. Release Notes
The Release Notes page lists the notes accompanying every recent release of Red Hat Network. These
notes describe all significant changes occurring in a given release cycle, from major enhancements to
the user interface to minor changes to the related documentation.
6.3.4.9. Get RHN Software
The RHN Software page provides direct links to the Red Hat Update Agent and Red Hat Network
Registration Client for every supported distribution. In addition, it describes how to resolve expired
Secure Sockets Layers (SSL) certificates if you are using an older version of Red Hat Enterprise Linux
that shipped with a certificate that is now expired.
Page 77
Chapter 6. Red Hat Network Website 65
6.4. Systems
If you click the Systems tab on the top navigation bar, the Systems category and links appear. The
pages in the Systems category allow you to select systems so that you can perform actions on them
and create System Profiles.
6.4.1. Overview —
As shown in Figure 6-3, the Overview page provides a summary of your systems, including their
status, number of associated Errata and packages, and entitlement level. Clicking on the name of
a system takes you to its System Details page. Refer to Section 6.4.2.6 System Details for more
information.
Figure 6-3. Systems Overview
Clicking the View System Groups link at the top of the Overview page takes you to a similar summary of your system groups. It identifies group status and displays the number of systems contained.
Clicking on the number of systems takes you to the Systems tab of the System Group Details page,
while clicking on the system name takes you to the Details tab. Refer to Section 6.4.3.3 System Group
Details —
for more information.
Page 78

66 Chapter 6. Red Hat Network Website
You can also click the Use Group button in the System Groups section of the Overview page to
go directly to the System Set Manager. Refer to Section 6.4.4 System Set Manager — for more
information.
6.4.2. Systems
The Systems page displays a list of all your registered systems. The Systems list contains several
columns of information for each system:
• Select — Update-entitled systems cannot be selected. To select systems, mark the appropriate
checkboxes and click the Update List button below the column. Selected systems are added to
the System Set Manager. After adding systems to the System Set Manager, you can use it to
perform actions on them simultaneously. Refer to Section 6.4.4 System Set Manager —
details.
• Status — Shows which type of Errata Alerts are applicable to the system or confirms that it is
up-to-date. Some icons are linked to pages providing resolution. For instance, the standard Updates
icon is linked to the Upgrade subtab of the packages list, while the Critical Updates icon goes
directly to the Update Confirmation page. Also, the Not Checking In icon is linked to instructions
for resolving the issue.
— System is up-to-date
•
• — Critical Errata available, update strongly recommended
• — Updates available and recommended
• — System is locked; Actions prohibited
• — System is being kickstarted
• — Updates have been scheduled
• — System not checking in properly (for 24 hours or more)
• — System not entitled to any update service
for
• Errata — Total number of Errata Alerts applicable to the system.
• Packages — Total number of package updates for the system. Includes packages from Errata Alerts
as well as newer packages that are not from Errata Alerts. For example, if a system is subscribed
to the Red Hat Enterprise Linux 2.1 i386 channel that contains version 2.5.4 of a package because
that is the version that shipped with Red Hat Enterprise Linux 2.1, but the system has version 2.5.2
of the package installed, the newer version of the package will be in the list of updated packages
for the system.
Important
If the RHN website identifies package updates for the system, yet the Red Hat Update Agent
responds with "Your system is fully updated" when run, a conflict likely exists in the system’s package profile or in the up2date configuration file. To resolve the conflict, either schedule a package
list update or remove the packages from the Package Exceptions list for the Red Hat Update
Agent. Refer to Section 6.4.2.6 System Details or Section 2.4.1.3 Package Exceptions Settings,
respectively, for instructions.
Page 79

Chapter 6. Red Hat Network Website 67
• System — The name of the system as configured when registering it. The default name is the
hostname of the system. Clicking on the name of a system takes you to the System Details page
for the system. Refer to Section 6.4.2.6 System Details for more information.
• Base Channel — The primary channel for the system, based upon its operating system distribution.
Refer to Section 6.6.1 Software Channels for more information.
• Entitlement — Whether or not the system is entitled and at what service level.
Links in the left navigation bar below Systems enable you to select and view predefined sets of your
systems. All of the options described above can be applied within these pages.
6.4.2.1. All
The All page contains the default set of your systems. It displays every system you have permission
to manage. A user has permission to manage a system if he is the only user in his organization, if he is
an Organization Administrator, or if the system is a member of a group to which he has admin rights.
6.4.2.2. Out of Date
The Out of Date page displays the systems that have applicable Errata Alerts that have not been
applied.
6.4.2.3. Unentitled —
The Unentitled page displays the systems that have not yet been entitled for Red Hat Network service.
6.4.2.4. Ungrouped
The Ungrouped page displays the systems that have not yet been assigned to a specific system group.
6.4.2.5. Inactive
The Inactive page displays the systems that have not checked into RHN for 24 hours or more. When
the Red Hat Update Agent connects to RHN to see if there are any updates available or if any actions
have been scheduled, this is considered a checkin. If you are seeing a message indicating checkins are
not taking place, the RHN client on your system is not successfully reaching Red Hat Network for
some reason. This indicates:
• The system is not entitled to any RHN service. System Profiles that remain unentitled for 180 days
(6 months) are removed.
• The system is entitled, but the Red Hat Network Daemon has been disabled on the system. Refer to
Chapter 3 Red Hat Network Daemon for instructions on restarting and troubleshooting.
• The system is behind a firewall that does not allow connections over https (port 443).
• The system is behind an HTTP proxy server that has not been properly configured.
• The system is connected to an RHN Proxy Server or RHN Satellite Server that has not been properly
configured.
• The system itself has not been properly configured, perhaps pointing at the wrong RHN Server.
• The system is not on the network.
• Some other barrier exists between the system and the RHN Servers.
Page 80

68 Chapter 6. Red Hat Network Website
6.4.2.6. System Details
If you click on the name of a system on any page, it will display the System Details page for the
system. From here, you may modify this information or remove the system altogether by clicking the
delete system link on the top-right corner.
The System Details page is further divided into tabs:
6.4.2.6.1. System Details
Details
Displays information about the system. This is the first tab you see when you click on a system.
It offers direct access to some of the functionality provided in subsequent tabs. For instance, under
the System Info heading, a message should appear describing the status of this machine. If it states
"Critical updates available" you may click the update now link to apply all relevant Errata Updates
to the individual system, as you would under the Errata tab.
— In addition, some Management-level functions can be accessed only on this tab. Most importantly, a system may be locked by clicking the Lock system link near the bottom-left corner of the
page. This prohibits the scheduling of any action through RHN that would affect the system, including
package updates and system reboots. To undo this, click the Unlock system link in the same location.
— Finally, still other Provisioning-level features can be found here, as well. The most important
of these is the marker indicating the client system can have actions pushed to it. This feature requires
it be connected to an RHN Satellite Server that has this feature enabled and is identified by the OSA
Status section within the System Details page.
Push enables Satellite customers to immediately initiate tasks on Provisioning-entitled systems, rather
than wait for those systems to check in with RHN. Scheduling actions through push is identical to the
process of scheduling any other action except the task will begin immediately instead of waiting the
set interval.
In addition to the configuration of the Satellite, each client system to receive pushed actions must have
the osad package installed and its service started. Refer to the Enabling Push to Clients section of the
RHN Satellite Server Installation Guide for details.
The Details tab contains the following subsets of information:
6.4.2.6.1.1. System Details
DetailsOverview
A summary of the system’s details. In addition to the system status message, the Overview subtab
contains basic System Info, Subscribed Channels, and System Properties. Clicking the Alter Channel
Subscriptions link takes you to the Channels tab, while clicking the Edit these properties link takes
you to the Properties subtab. See the following sections for more information.
6.4.2.6.1.2. System Details
DetailsProperties
The profile name, entitlement level, notification choice, daily summary, auto-Errata update, and physical location of the system, including street address, city, state, country, building, room, and rack. To
modify this information, make your changes and click the Update Properties button. Note that many
of these properties can be set for multiple systems at once through the System Set Manager inter-
face. Refer to Section 6.4.4 System Set Manager —
for details. The following properties deserve
additional explanation:
• Receive Notifications of Updates/Errata — This setting keeps you abreast of all advisories per-
taining to the system. Anytime an update is produced and released for the system, a notification is
sent via email.
Page 81

Chapter 6. Red Hat Network Website 69
• Include system in daily summary report calculations — This setting includes the system in
a daily summary of system events. (By default, all Management and Provisioning systems are
included in the summary.) These are actions affecting packages, such as scheduled Errata Updates,
and system reboots or failures to check in. In addition to including the system here, you must choose
to receive email notifications in the Your Preferences page of the Your RHN category. Refer to
Section 6.3.2 Your Preferences for instructions. Note that RHN will send these summaries only to
verified email addresses.
• Automatic application of relevant errata — This setting allows you have all Errata Updates auto-
matically applied to a system. This means packages associated with Errata will be updated without
any user intervention. Customers should note that Red Hat does not recommend the use of the
auto-update feature for production systems because conflicts between packages and environments
can cause system failures. The Red Hat Network Daemon must be enabled on the systems for this
feature to work.
6.4.2.6.1.3. System Details
DetailsHardware
Detailed information about the system, including networking, BIOS, storage, and other devices. This
appears only if you selected to include the hardware profile for this machine during registration. If
the hardware profile looks incomplete or outdated, click the Schedule Hardware Refresh button to
schedule a Hardware Profile update for your system. The next time the RHN Daemon connects to
RHN, it will update your System Profile with the latest list of hardware.
6.4.2.6.1.4. System Details
DetailsNotes
A place to create notes about the system. To add a new note, click the create new note button, type
a subject and details, and click the Create button. To modify a note, click on its subject in the list of
notes, make your changes, and click the Update button. To remove a note, click on its subject in the
list of notes and then click the delete note button.
6.4.2.6.1.5. System Details
DetailsCustom Info —
Completely customizable information about the system. Unlike a note, information included here is
more formal and can be searched upon. For instance, you may decide to identify an asset tag for each
system. To do this, you must first create an asset key within the Custom System Info page. Refer
to Section 6.4.9 Custom System Info — for instructions. Once the key exists, you may assign a
value to it by clicking create new value here. Click the name of the key in the resulting list and enter
a value for it in the Description field, such as "Example#456." Then click the Update Key button.
6.4.2.6.1.6. System DetailsDetailsReactivation —
A System Profile-specific activation key. This allows you to create an activation key encompassing this
system’s ID, history, groups, and channels. You may then use this key only once with the rhnreg_ks
command line utility to re-register this system and regain all Red Hat Network settings. Refer to
Section 2.5 Registering with Activation Keys for instructions. Unlike typical activation keys, which
are not associated with a specific system ID, keys created here do not show up within the Activation
Keys page.
Warning
When kickstarting a system with its existing RHN profile, it will use the system-specific activation key
created here to reregister the system and return its other RHN settings. For this reason, you should
Page 82

70 Chapter 6. Red Hat Network Website
not regenerate, delete, or use this key (with rhnreg_ks) while a profile-based kickstart is in progress.
If you do, the kickstart will fail.
6.4.2.6.1.7. System Details
DetailsRemote Command —
The method for running a remote command on the system. To allow remote commands to be run on
the client through RHN, first install the latest rhncfg* packages available within the RHN Provisioning child channel for the system. These may already be installed if you kickstarted the system with
configuration management functionality.
Next, create the necessary directory on the target system:
mkdir -p /etc/sysconfig/rhn/allowed-actions/sc ript
Then create a run file in that directory to act as a flag to RHN signaling permission to allow remote
commands:
touch /etc/sysconfig/rhn/allowed-actions/script/run
You may then identify a specific user, group, and timeout period, as well as the script itself on this
page. Select a date and time to begin attempting the command, and click Schedule Remote Com-
mand.
6.4.2.6.1.8. System Details
DetailsConnection
The system’s path to the package repository. This tab appears for any system in an organization that
has a registered RHN Proxy Server version 3.1 or later. This subtab is designed to help you determine
if updates and other information are passing through one or more RHN Proxy Servers. It identifies the
Proxies being used and the order in which data passes through them to reach this system. The Proxy
connecting directly to the central RHN Servers or your RHN Satellite Server is numbered ’1’.
6.4.2.6.2. System DetailsErrata
Contains a list of Errata Alerts applicable to the system. Refer to Section 6.1.3 Errata Alert Icons for
meanings of the icons on this tab. To apply updates, select them and click the Apply Errata button.
Double-check the updates to be applied on the confirmation page, then click the Confirm button.
After confirming, the action is added to the Pending Actions list under Schedule. Errata that have
been scheduled cannot be selected for update. In the place of a checkbox, you will find a clock icon
that, when clicked, takes you to the Action Details page.
To help users determine whether an update has been scheduled, a Status column exists within the
Errata table. Possible values are: None, Pending, Picked Up, Completed, and Failed. This column
identifies only the latest action related to an Errata. For instance, if an action fails and you reschedule
it, this column will show the status of the Errata as Pending only (with no mention of the previous failure). Clicking a status other than None takes you to the Action Details page. This column corresponds
to one on the Affected Systems tab of the Errata Details page.
6.4.2.6.3. System Details
Packages
Manages the packages on the system.
Page 83

Chapter 6. Red Hat Network Website 71
— When selecting packages to install, upgrade, or remove, Provisioning customers have the
option of running a remote command automatically before or after the package installation. Refer to
Section 6.4.2.6.1.7 System Details
DetailsRemote Command — for more information.
6.4.2.6.3.1. System DetailsPackagesPackages
The default display of the Packages tab describes the options available to you and provides the means
to update your package list. If after exploring the packages, you believe the list is outdated or incomplete (or you installed the packages manually and did not have RHN install them), click the Update
Package List button on the bottom right-hand corner of this page. The next time the RHN Daemon
connects to RHN, it will update your System Profile with the latest list of installed packages.
6.4.2.6.3.2. System Details
PackagesList/Remove
Lists installed packages from the system’s software System Profile and enables you to remove them.
Click on a package name to view its Package Details page. (Refer to Section 6.6.5.3 Package Details.)
To delete packages from the system, select their checkboxes and click the Remove Packages button
on the bottom right-hand corner of the page. A confirmation page will appear with the packages listed.
Click the Confirm button to remove the packages.
6.4.2.6.3.3. System DetailsPackagesUpgrade
Displays a list of packages that have a new version available based on the package versions in the
channels for the system. Click on the latest package name to view its Package Details page. To
upgrade packages immediately, select them and click the Upgrade Packages button. To download
the packages as a .tar file, select them and click the Download Packages button. Refer to Section
6.6.5.2 Package Download for details.
6.4.2.6.3.4. System Details
PackagesInstall
Enables you to install new packages on the system from the available channels. Click on the package
name to view its Package Details page. To install packages, select them and click the Install Selected
Packages button.
6.4.2.6.3.5. System DetailsPackagesVerify —
Validates the packages installed on the system against its RPM database. This is the equivalent of
running rpm -V. Specifically, this tab allows you to compare the metadata of the system’s packages
with information from the database, such as MD5 sum, filesize, permissions, owner, group and file
size and type. To verify a package or packages, select them and click the Verify Selected Packages
button and then confirm this action. Once finished, you can view the results by selecting this action
within the History subtab under Events.
6.4.2.6.3.6. System Details
PackagesProfiles —
Gives you the ability to compare the packages on this system with the packages of stored profiles and
other Management and Provisioning systems. To make the comparison with a stored profile, select
that profile from the pulldown menu and click the Compare button. To make the comparison with
another system, select it from the associated pulldown menu and click the Compare button. To create
a stored profile based upon the existing system, click the Create System Profile button, enter any
Page 84

72 Chapter 6. Red Hat Network Website
additional information you desire, and click the Create Profile button. These profiles are kept within
the Stored Profiles page linked from the left navigation bar.
— Once package profiles have been compared, Provisioning customers have the ability to synchronize the packages of the selected system with the package manifest of the compared profile. Note
that this action may delete packages on the system not in the profile, as well as install packages from
the profile. To install specific packages, select the checkboxes of packages from the profile. To remove
specific packages already installed on the system itself, select the checkboxes of packages showing
a difference of "This system only." To synchronize the system’s packages with the compared profile
entirely, select the master checkbox at the top of the column. Then click the Sync Packages to button. On the confirmation screen, review the changes, select a time frame for the action, and click the
Schedule Sync button.
6.4.2.6.4. System DetailsChannels
Manage the channels associated with the system.
6.4.2.6.4.1. System DetailsChannelsSoftware
Software channels provide a well-defined method to determine which packages should be available
to a system for installation or upgrade, based upon its operating systems, packages and, functionality.
Click a channel name to view its Channel Details page. To modify the child channels associated with
this system, use the checkboxes next to the channels and click the Change Subscriptions button. You
will receive a success message or be notified of any errors. To change the system’s base channel, select
the new one from the pulldown menu and click the Modify Base Channel button. Refer to Section
6.6.1 Software Channels for more information.
6.4.2.6.4.2. System Details
ChannelsConfiguration —
Assists in managing the configuration of the system. This section is available to normal users with
access to systems that have configuration management enabled. Like software channels, configuration channels store files to be installed on systems. While software updates are provided by RHN,
configuration files are managed solely by you. Also unlike software packages, various versions of
configuration files may prove useful to a system at any given time. Remember, only the latest version
can be deployed. If you want to distribute an older version through RHN, make it the latest version
first.
To manage the configuration of a system, it must have the latest rhncfg* packages installed and
the configfiles/ directory and associated files created on it. Refer to Section 6.6.6.1 Preparing
Systems for Config Management for instructions. Command line tools also exist for many of these
functions. Refer to Appendix A Command Line Config Management Tools for instructions.
Here are the options available within the system’s Configuration tab, each of which results in a
separate subtab:
• Managed Files — List all configuration files currently associated with the system. The Overrides
column identifies which config file from which channel will apply if the system is unsubscribed
from the config channel that provides the file now. For instance, if a system has ’/etc/foo’ from
channel ’bar’ and ’/etc/foo’ from channel ’baz’ is in the Overrides column, then unsubscribing
from channel ’bar’ will mean that the file from channel ’baz’ will be applicable. Also, if nothing
is in the ’Overrides’ column for a given file path, then unsubscribing from the channel providing
the file will mean that the file is no longer managed (though it will (not remove the file from the
system).
Page 85

Chapter 6. Red Hat Network Website 73
• Diff — Validate the configuration files installed on the system by comparing them to versions stored
in RHN’s central configuration manager. Select the files to be diffed and click Analyze Differences.
• Config Channels — Set the subscription and rank of configuration channels that may be associated
with the system, lowest first. Enter numbers in the Rank fields to establish the order in which channels are used. Channels with no numeric value are not associated with the system. This system’s
local configuration channel will always override all other channels for this system and therefore
cannot have its rank adjusted from 1. All other channels are created in the Manage Config Chan-
nels interface within the Channels category. Refer to Section 6.6.6 Manage Config Channels —
for instructions. When satisfied, click Update.
• Local Overrides — View and manage the default configuration files for the system. If no files exist,
you may use the add files, upload files, and add directories links within the page description to
associate files with this system. These tabs correspond to those within the Configuration Channel
Details page, affecting your entire organization and available only to Configuration Administrators.
Refer to Section 6.6.6.5 Configuration Channel Details —
for instructions.
If a file exists, click its name to go to the Configuration File Details page. Refer to Section 6.6.6.6
Configuration File Details — for instructions. To replicate the file within a config channel,
select its checkbox, click the Copy to Config Channel button, and select the destination channel.
To remove a file, select it and click Delete Selected Files.
• Sandbox — Manipulate configuration files without deploying them. This sandbox provides you
with an area to experiment with files without affecting systems. To add files, click the import new
files link, select an option for their addition from the dropdown menu, and click Go. Ensure you
have the latest rhncfg* packages. The rest of the functions work like those on the Local Overrides
subtab.
6.4.2.6.5. System DetailsGroups —
Lists the system’s associated groups and enables you to change these associations.
6.4.2.6.5.1. System DetailsGroupsList/Remove —
Lists groups to which the system belongs and enables you to cancel those associations. Only System
Group Administrators and Organization Administrators can remove the system from groups. Nonadmins just see a ’Review this system’s group membership’ page. To remove the system from groups,
select the groups’ checkboxes and click the Leave Selected Groups button. Click on a group’s name
to go to its System Group Details page. Refer to Section 6.4.3.3 System Group Details —
for
more information.
6.4.2.6.5.2. System Details
GroupsJoin —
Lists groups that the system may be subscribed to. Only System Group Administrators and Organization Administrators can add the system to groups. Non-admins just see a ’Review this system’s group
membership’ page. To add the system to groups, select the groups’ checkboxes and click the Join
Selected Groups button.
Page 86

74 Chapter 6. Red Hat Network Website
6.4.2.6.6. System Details
Snapshots —
Provides snapshots enabling rollback of the system’s package profile, configuration files, and RHN
settings. These snapshots are captured whenever an action takes place on the system.
6.4.2.6.6.1. System Details
SnapshotsSnapshots —
The default display of the Snapshots tab lists the reason, dates, and times for snapshots taken, as well
as any tags associated with the snapshots. To revert to a previous configuration, click the Reason of the
snapshot taken at the desired date and time and review the potential changes on the provided subtabs,
starting with Rollback.
You may add a tag to an existing snapshot on the System Details
SnapshotsSnapshots
Snapshot Tags subtab by clicking the create new snapshot tag link, providing a descriptive term,
and clicking Tag This Snapshot button. Refer to Section 6.4.2.6.6.2 System Details
Snapshots
Snapshot Tags — for more information. When satisfied with the reversion, return to the Rollback
subtab and click the Rollback to Snapshot button. To see the list again, click Return to snapshot
list.
6.4.2.6.6.2. System DetailsSnapshotsSnapshot Tags —
Provides a means to add meaningful descriptions to your most recent system snapshot. This can be
used to indicate milestones, such as a known working configuration or a successful upgrade. To tag
the most recent snapshot, click create new system tag, enter a descriptive term in the Tag name field,
and click the Tag Current Snapshot button. Refer to Section 6.4.2.6.6.1 System Details
Snapshots — to tag older snapshots. You may then revert using this tag directly by clicking
Snapshots
its name in the Snapshot Tags list. To delete tags, select their checkboxes, click Remove Tags, and
confirm the action.
6.4.2.6.7. System DetailsKickstart —
Enables the re-installation of the system based upon selectable parameters, including specific Red Hat
distribution. These kickstarts are based upon profiles developed within the Kickstart interface. Refer
to Section 6.4.10 Kickstart —
for details.
6.4.2.6.7.1. System DetailsKickstartSchedule —
The default display of the Kickstart tab, this subtab allows the kickstarting of the selected system. To
schedule a kickstart, select a distribution, identify the type (IP address or manual selection of kickstart
profile), and click Continue. Note that IP address kickstarts require ranges to be defined in kickstart
profiles.
On the next page, finish choosing from the options available. Using the existing RHN profile will rely
upon the system-specific activation key created within the Reactivation tab to reregister the system.
Do not regenerate, delete, or use this key while a profile-based kickstart is in progress. Selecting the
Deploy Configuration checkbox will re-install configuration files from any config channels associated with the system. When finished, click the Schedule Kickstart button.
Caution
It is imperative the kickstart profile selected match the installation files supplied. For instance, it is
possible a given IP address could be associated with a Red Hat Enterprise Linux 2.1 kickstart profile,
Page 87

Chapter 6. Red Hat Network Website 75
but you insert an IP address kickstart CD-ROM built for Red Hat Enterprise Linux 3. This would result
in errors and cause the kickstart to fail.
6.4.2.6.7.2. System Details
KickstartSession Status —
If you’ve scheduled a kickstart, this subtab shows where the system’s kickstart stands. Details include
the kickstart profile used, its state, and pending and latest actions. Kickstarts that do not complete
within approximately two hours will be marked as failed here. Click the profile name to access the
Kickstart Details page. Click the view link to see the actual kickstart configuration file generated by
RHN. To force this page to reload at a set interval, select one from the pulldown menu and click the
Change Reload Time button.
6.4.2.6.7.3. System Details
KickstartSession History —
Displays particular points in a kickstart session’s progress. Like Session Status, this subtab appears
only if you’ve scheduled a kickstart. It lists individual actions, such as package installs, as they occur.
Click the name of an action to see information about it, including summary, details, and time. Failed
kickstarts are shown here, as well. To force this page to reload at a set interval, select one from the
pulldown menu and click the Change Reload Time button.
6.4.2.6.8. System DetailsEvents
Displays past, current, and scheduled actions on the system. You may cancel pending events here. The
following sections describe the Events subtabs and the features they offer.
6.4.2.6.8.1. System Details
EventsHistory
The default display of the Events tab lists the type and status of events that have failed, occurred or
are occurring. To view details of an event, click its summary in the System History list. To again view
the table, click Return to history list at the bottom of the page.
6.4.2.6.8.2. System DetailsEventsPending
Lists events that are scheduled but have not begun. A prerequisite action is required to complete
successfully before a given action will be attempted. If an action has a prerequisite, there will not
be a checkbox available to cancel that specific action. Instead, there will be a checkbox next to the
prerequisite action; Cancelling the prerequisite action will cause the action in question to fail.
Actions can be chained in this manner so that action ’a’ requires action ’b’ which requires action ’c’.
Action ’c’ will be the first one attempted, and will be the one with the checkbox next to it until it is
completed successfully - if any action in the chain fails, the remaining actions also fail. To unschedule
a pending event, select the event and click the Cancel Events button at the bottom of the page. The
following icons indicate the type of events listed here:
•
— Package Event
• — Errata Event
• — Preferences Event
Page 88

76 Chapter 6. Red Hat Network Website
— System Event
•
6.4.2.6.9. System DetailsProbes —
Displays all of the probes monitoring the system. You must be logged into an RHN Satellite Server
with Monitoring enabled to see this tab. The State column shows icons representing the status of
each probe. Refer to Section 6.9 Monitoring —
for descriptions of these states. The Status String
column displays the last message received from the probe. Clicking the probe description takes you
to its Current State page.
To add a probe to the system, click the create new probe link at the top-right corner of the page and
complete the fields on the following page. Refer to Section 7.3.1 Creating Notification Methods for
detailed instructions.
Once the probe has been added, you must reconfigure your Monitoring infrastructure to recognize it.
Refer to Section 6.9.3 Scout Config Push —
for details. After the probe has run, its results become
available on the Current State page. Refer to Section 6.9.1.7 Current State — for details.
6.4.3. System Groups —
The System Groups page allows all RHN Management and Provisioning users to view the System
Groups list. Only System Group Administrators and Organization Administrators may perform the
following additional tasks:
1. Create system groups. (Refer to Section 6.4.3.1 Creating Groups.)
2. Add systems to system groups. (Refer to Section 6.4.3.2 Adding and Removing Systems in
Groups.)
3. Remove systems from system groups. (Refer to Section 6.4.2.6 System Details.)
4. Assign system group permissions to users. (Refer to Section 6.8 Users —
.)
As shown in Figure 6-4, the System Groups list displays all of your system groups.
Page 89

Chapter 6. Red Hat Network Website 77
Figure 6-4. System Group List
The System Groups list contains several columns for each group:
• Select — These checkboxes enable you to add systems in groups to the System Set Manager. To
select groups, mark the appropriate checkboxes and click the Update button below the column.
All systems in the selected groups are added to the System Set Manager. You can then use the
System Set Manager to perform actions on them simultaneously. To add only the systems in all
selected groups, select them and click the Work with Intersection button. To add all systems in
all selected groups, select them and click the Work with Union button. Each system will show up
once, regardless of the number of groups to which it belongs. Refer to Section 6.4.4 System Set
Manager — for details.
• Status — Shows which type of Errata Alerts are applicable to the group or confirms that it is up-
to-date. Clicking on a group’s status icon takes you to the Errata tab of its System Group Details
page. Refer to Section 6.4.3.3 System Group Details —
for more information.
The status icons call for differing degrees of attention:
• — All systems within group are up-to-date
• — Critical Errata available, update strongly recommended
• — Updates available and recommended
• Group Name — The name of the group as configured during its creation. The name should be
explicit enough to easily differentiate between it and other groups. Clicking on the name of a group
takes you to Details tab of its System Group Details page. Refer to Section 6.4.3.3 System Group
Details —
for more information.
Page 90

78 Chapter 6. Red Hat Network Website
• Systems — Total number of systems contained by the group. Clicking on the number takes you to
the Systems tab of the System Group Details page for the group. Refer to Section 6.4.3.3 System
Group Details —
• Use in SSM — Clicking the Use Group button in this column loads the group from that row and
for more information.
launches the System Set Manager immediately. Refer to Section 6.4.4 System Set Manager —
for more information.
6.4.3.1. Creating Groups
To add a new system group, click the create new group button at the top-right corner of the page.
Type a name and description and click the Create Group button. Make sure you use a name that
clearly sets this group apart from others. The new group will appear in the System Groups list.
6.4.3.2. Adding and Removing Systems in Groups
Systems can be added and removed from system groups in two places: the Target Systems tab of the
System Group Details page and the Groups tab of the System Details page. The process is similar
in both instances. Select the systems to be added or removed and click the Add Systems or Remove
Systems button.
6.4.3.3. System Group Details —
At the top of each System Group Details page are two links: work with group and delete group.
Clicking delete group does just that and should be used with caution. Clicking Work with Group
functions similarly to the Use Group button from the System Groups list in that it loads the group’s
systems and launches the System Set Manager immediately. Refer to Section 6.4.4 System Set Man-
ager —
for more information.
The System Group Details page is broken down into tabs:
6.4.3.3.1. System Group DetailsDetails —
Basic information about the system group: the group name and group description. To change this
information, click Edit Group Properties, make your changes in the appropriate fields, and click the
Modify Details button.
6.4.3.3.2. System Group DetailsSystems —
List of systems that are members of the system group. Clicking links within the table takes you to
corresponding tabs within the System Details page for the associated system. To remove systems
from the group, select the appropriate checkboxes and click the Remove from group button on the
bottom of the page. Clicking it does not delete systems from RHN entirely. This is done through the
System Set Manager or System Details pages. Refer to Section 6.4.4 System Set Manager —
Section 6.4.2.6 System Details, respectively.
6.4.3.3.3. System Group Details
Target Systems —
Target Systems — List of all systems in your organization. This tab enables you to add systems to
the specified system group. Merely select the systems using the checkboxes to the left and click the
Add Systems button on the bottom right-hand corner of the page.
or
Page 91

Chapter 6. Red Hat Network Website 79
6.4.3.3.4. System Group Details
Errata —
List of relevant Errata for systems in the system group. Clicking the Advisory takes you to the Details
tab of the Errata Details page. (Refer to Section 6.5.2.2 Errata Details for more information.) Clicking the Affected Systems number lists all of the systems addressed by the Errata. To apply the Errata
Updates in this list, select the systems and click the Apply Errata button.
6.4.3.3.5. System Group Details
Admins —
List of all organization users that potentially have permission to manage the system group. Organization Administrators are clearly identified. System Group Administrators are marked with an asterisk
(*). To change the system group’s users, select and unselect the appropriate checkboxes and click the
Update button.
6.4.4. System Set Manager —
The System Set Manager allows you to perform many actions possible individually through the
System Details page on multiple systems at once, including:
• Apply Errata updates
• Upgrade packages to the most recent versions available
• Add/remove systems to/from system groups
• Subscribe/unsubscribe systems to/from channels
• Update system profiles
• Modify system preferences such as scheduled download and installation of packages
• Kickstart several Provisioning-entitled systems at once
• Set the subscription and rank of configuration channels for Provisioning-entitled systems
• Tag the most recent snapshots of your selected Provisioning-entitled systems
• Revert Provisioning-entitled systems to previous snapshots
• Run remote commands on Provisioning-entitled systems
Before performing actions on multiple systems, you must select the systems you wish to modify. Note
that Update-level systems cannot be selected. Pages including Systems list and System Search have a
column of checkboxes under the Select heading. Mark the checkboxes beside the systems you want to
select, and click the Update List button below the column to add them to the System Set Manager.
You can access the System Set Manager page in three ways: 1)The System Set Manager button in
the left navigation bar. 2)The Use Group button in the System Groups list (or Work with Group on
the System Group Details page to work). 3)The Manage button just below the top navigation bar.
The System Set Manager page is broken down into tabs:
6.4.4.1. System Set Manager
Overview —
Description of the various options available to you in the remaining tabs.
Page 92

80 Chapter 6. Red Hat Network Website
6.4.4.2. System Set Manager
Systems —
List of systems now selected. To remove systems from this set, select them and click the Remove
button.
6.4.4.3. System Set Manager
Errata —
List of Errata Updates applicable to the current system set. Click the number in the Systems column to
see to which systems in the System Set Manager the given Errata applies to. To apply updates, select
the Errata and click the Apply Errata button.
6.4.4.4. System Set Manager
Packages —
Options to modify packages on the system within the following subtabs (Click the number in the
Systems column to see to which systems in the System Set Manager the given package applies to.):
— When selecting packages to install, upgrade, or remove, Provisioning customers have the
option of running a remote command automatically before or after the package installation. Refer to
Section 6.4.2.6.1.7 System Details
DetailsRemote Command — for more information.
6.4.4.4.1. System Set ManagerPackagesInstall —
A list of channels from which you may retrieve packages. The list of channels is the list of all the
channels that systems in the set are subscribed to; a package will be installed on a system only if the
system is subscribed to the channel from which the package comes. Click on the channel name and
select the packages from the list. Then click the Install Packages button.
6.4.4.4.2. System Set ManagerPackagesUpgrade —
A list of all the packages installed on the selected systems that might be upgraded. Systems must be
subscribed to a channel providing the package for the system to be able to upgrade the package. If
multiple versions of a package appear, note that only the latest version available to each system will
be upgraded on that system. Select the packages to be upgraded, then click the Upgrade Packages
button.
6.4.4.4.3. System Set ManagerPackagesRemove —
A list of all the packages installed on the selected systems that might be removed. Multiple versions
will appear if systems in the System Set Manager have more than one version installed. Select the
packages to be deleted, then click the Remove Packages button.
6.4.4.5. System Set ManagerGroups —
Tools to create groups and manage group membership. These functions are limited to Organization
Administrators and System Group Administrators. To add a new group, click create new group on
the top-right corner. In the resulting page, type its name and description in the identified fields and
click the Create Group button. To add or remove the selected systems in any of the system groups,
toggle the appropriate radio buttons and click the Alter Membership button.
Page 93

Chapter 6. Red Hat Network Website 81
6.4.4.6. System Set Manager
Channels —
Options to manage channel associations through the following subtabs:
6.4.4.6.1. System Set Manager
ChannelsChannel Subscriptions —
To subscribe or unsubscribe the selected systems in any of the channels, toggle the appropriate radio
buttons and click the Alter Subscriptions button. Keep in mind, subscribing to channels uses up
channel entitlements, and if not enough channel entitlements are available, not all systems will get an
entitlement. Similarly, systems will be subscribed to a child channel only if they are subscribed to the
base channel that is the parent of the child channel in question.
6.4.4.6.2. System Set Manager
ChannelsConfig Channels —
Like the options within the System DetailsChannelsConfiguration tab, the subtabs here
can be used to subscribe the selected systems to configuration channels and deploy and compare
the configuration files on the systems. The channels are created in the Manage Config Channels
interface within the Channels category. Refer to Section 6.6.6 Manage Config Channels — for
channel creation instructions.
To manage the configuration of a system, it must have the latest rhncfg* packages installed and
the configfiles/ directory and associated files created on it. Refer to Section 6.6.6.1 Preparing
Systems for Config Management for instructions. Command line tools also exist for many of these
functions. Refer to Appendix A Command Line Config Management Tools for instructions.
6.4.4.6.2.1. System Set Manager
ChannelsConfig ChannelsSubscriptions —
On this subtab, available only to Configuration Administrators and Organization Administrators, enter
numbers in the Rank column to establish the order in which channels are used, lowest first. Channels
not assigned a numeric value will not be associated with the systems. Your local configuration channel
will always override all other channels. Once you’ve established the rank of the config channels, you
must decide how they should be applied to the selected systems.
The three buttons below the channels reflect your options. Clicking Add with Highest Rank places
all the ranked channels before any channels already subscribed to by the systems. Clicking Add with
Lowest Rank places the ranked channels after channels subscribed to by the systems. Clicking Replace Existing Config Channels removes any existing association and starts cleanly with the ranked
channels, leaving every system with the same config channels in the same order.
In the first two cases, if any of the newly ranked config channels is already in a system’s existing config channel list, the duplicate channel is removed and re-added according to the new rank, effectively
reordering the system’s existing channels. When such conflicts exist, you’re presented with a confirmation page to ensure the intended action is correct. When the change has taken place, a message
appears at the top of the page indicating the update was successful.
6.4.4.6.2.2. System Set Manager
ChannelsConfig ChannelsDeploy —
Use this subtab to distribute configuration files from your central repository on RHN to the selected
systems at once. The table lists the configuration files associated with any of the selected systems.
Clicking its system count displays the systems already subscribed to the file.
To subscribe the selected systems to the available configuration files, select the checkbox for each
desired file. When done, click Deploy Configuration and schedule the action. Note that the files
deployed are of the latest version at the time of scheduling and do not account for versions that may
appear before the action takes place.
Page 94

82 Chapter 6. Red Hat Network Website
6.4.4.6.2.3. System Set Manager
ChannelsConfig ChannelsDiff —
Use this subtab to validate configuration files on the selected systems against copies in your central
repository on RHN. The table lists the configuration files associated with any of the selected systems.
Clicking its system count displays the systems already subscribed to the file.
To compare the configuration files deployed on the systems with those in RHN, select the checkbox
for each file to be validated. Then click Analyze Differences and schedule the action. Note that the
files compared are of the latest version at the time of scheduling and do not account for versions that
may appear before the action takes place. Then find the results within the main Schedule category or
within the System Details
Events tab.
6.4.4.6.3. System Set Manager
ChannelsBase Channel Alteration —
Channel Administrators may use this subtab to change the base channels the selected systems are
subscribed to. The default Red Hat base channel selection in the pulldown menu will subscribe the
system to whichever Red Hat-provided base channel representing the operating system installed on
the system. Systems will be unsubscribed from all channels and subscribed to the new base channels.
For this reason, this should be done with caution. Select the new base channel from the pulldown
menus and click the Change Base Channels button.
6.4.4.7. System Set Manager
Provisioning —
Provisioning — Options for provisioning systems through the following subtabs:
6.4.4.7.1. System Set ManagerProvisioningKickstart —
Use this subtab to re-install the selected Provisioning-entitled systems. To schedule a kickstart, select
a distribution, identify the type (IP address or manual), and click Continue. Then finish choosing
from the options available on the subsequent screen and click the Schedule Kickstart button.
6.4.4.7.2. System Set ManagerProvisioningTag Systems —
Use this subtab to to add meaningful descriptions to the most recent snapshots of your selected systems. To tag the most recent system snapshots, enter a descriptive term in the Tag name field, and
click the Tag Current Snapshots button.
6.4.4.7.3. System Set ManagerProvisioningRollback —
Use this subtab to rollback selected Provisioning-entitled systems to previous snapshots marked with
a tag. Click the name of the tag, verify the systems to be reverted, and click the Rollback Systems
button.
6.4.4.7.4. System Set Manager
ProvisioningRemote Command —
Use this subtab to issue remote commands on selected Provisioning-entitled systems. You must have
created a run file on the client systems for this function to be allowed. Refer to the description of
the Configuration subtab of the Channels tab for instructions. You may then identify a specific user,
Page 95

Chapter 6. Red Hat Network Website 83
group, and timeout period, as well as the script itself on this page. Select a date and time to begin
attempting the command, and click Schedule Remote Command.
6.4.4.8. System Set Manager
Misc —
Misc — Tools to update System Profiles and preferences for the system set. Here are the tools broken
down by section:
6.4.4.8.1. System Set Manager
MiscSystem Profile Updates —
Clicking Update Hardware Profile, then the Confirm Refresh button schedules a hardware profile
update. Clicking Update Package Profile, then the Confirm Refresh button schedules a package
profile update.
6.4.4.8.2. System Set Manager
MiscCustom System Information —
Clicking Set a custom value then the name of a key allows you to provide values for all selected
systems. Enter the information and click the Set Values button. Clicking Remove a custom value
then the name of a key allows you to remove values for all selected systems. Click the Remove
Values button to finalize the deletion.
6.4.4.8.3. System Set Manager
MiscReboot Systems —
Selecting the appropriate systems and then clicking the Reboot Systems link sets those systems for
reboot. To immediately cancel this action, click the list of systems link that appears within the confirmation message at the top of the page, select the systems, and click Unschedule Action.
6.4.4.8.4. System Set ManagerMiscLock Systems —
Selecting the appropriate systems and then clicking the Lock Systems link prevents the scheduling of
any action through RHN that would affect the systems. This can be reversed by clicking the Unlock
Systems link.
6.4.4.8.5. System Set Manager
MiscDelete Systems —
Clicking Delete System Profiles, then the Confirm Deletions button removes the selected profiles
permanently.
6.4.4.8.6. System Set Manager
MiscUpgrade System Entitlements —
Clicking Upgrade to * Entitlement upgrades the entitlement for as many selected systems as possible. Keep in mind, entitlements cannot be downgraded.
Page 96

84 Chapter 6. Red Hat Network Website
6.4.4.8.7. System Set Manager
MiscSystem Preferences —
Toggling the Yes and No radio buttons and then clicking the Change Preferences button alters your
notification preferences for the selected systems. All of these preferences may also be applied to
systems individually through the Properties subtab of the System Details page. Refer to Section
6.4.2.6.1.2 System Details
• Receive Notifications of Updates/Errata — This setting keeps you abreast of all advisories per-
DetailsProperties for instructions.
taining to your systems. Anytime an update is produced and released for a system under your
supervision, a notification is sent via email.
• Include system in Daily Summary — This setting includes the selected systems in a daily sum-
mary of system events. (By default, all Management and Provisioning systems are included in the
summary.) These are actions affecting packages, such as scheduled Errata Updates, and system reboots or failures to check in. In addition to including the systems here, you must choose to receive
email notifications in the Your Preferences page of the Your RHN category. Refer to Section 6.3.2
Your Preferences for instructions. Note that RHN will send these summaries only to verified email
addresses.
• Automatic application of relevant Errata — This setting allows you have all Errata Updates au-
tomatically applied to systems. This means packages associated with Errata will be updated without
any user intervention. Customers should note that Red Hat does not recommend the use of the autoupdate feature for production systems because conflicts between packages and environments can
cause system failures.
6.4.5. System Entitlements
To use all of the features of RHN, your systems must be entitled — subscribed to an RHN service
level. Use the System Entitlements page to configure which systems are entitled to which service
offerings. There are three primary types of entitlements:
• Update — should be used to manage a single Red Hat Enterprise Linux system. It includes Errata
Alerts, Scheduled Errata Updates, Package Installation, and the Red Hat Update Agent.
• Management — should be used to manage multiple systems with multiple system administrators.
In addition to the features of the Update offering, it includes system group management, user management, and the System Set Manager interface to quickly perform actions on multiple systems.
• Provisioning — offers the highest level of functionality. It should be used to provision multiple sys-
tems that will need to be re-installed and reconfigured regularly. The Provisioning offering provides
tools for kickstarting machines, managing their configuration files, conducting snapshot rollbacks,
and inputting searchable custom system information, as well as all of the functionality included in
the Management service level.
The System Entitlements page allows you to view and promote the entitlements for your registered
systems. Only increases in entitlement levels are allowed. Systems cannot be re-entitled to a lower
entitlement level. For instance, a system entitled to the Update service level can be promoted to the
Management level, but this action cannot be reversed.
To change an individual entitlement, select the entitlement from the system’s pulldown menu and
click the Update Entitlements button on the bottom right-hand corner of the page. Click the name of
a system to see details about it. If no drop-down menu exists for your Update-level system, you may
need to purchase a Management entitlement. Do this through the Buy Now link at the left of the page.
Page 97

Chapter 6. Red Hat Network Website 85
Warning
Changing a system’s entitlement is an irreversible action. You may be unable to change the entitlement levels of some systems. For more information, refer to the RHN entitlement policy linked from
the System Entitlements page.
In addition, you may entitle all newly registered systems to the Management service level at once
by clicking the Auto-Entitle Newest Servers Now link at the bottom of the page. To use this link,
which appears only when new, unentitled systems exist, first make sure you have enough Management
entitlements available. If you need to purchase additional entitlements, click the Buy more system
entitlements now link at the top of the page. After auto-entitling, a message appears at the top of the
System Entitlements page indicating the number of systems successfully entitled to the Management
service level.
When an entitlement expires, the last system entitled to the same service level (such as Management)
will be unentitled. For instance, if you have 10 Red Hat Enterprise Linux AS systems entitled to
Management and either one of the RHN entitlements or one of the operating system subscriptions
expire, the last system subscribed or entitled will have their subscription or entitlement removed.
6.4.6. Advanced Search —
The System Search page allows you to search through your systems according to specific criteria.
These criteria include custom system information, system details, hardware, devices, interface, networking, packages, and location. The activity selections (Days Since Last Checkin, for instance) can
be especially useful in finding and removing outdated System Profiles. Type the keyword, select the
criterion to search by, use the radio buttons to identify whether you wish to query all systems or only
those loaded in the System Set Manager, and click the Search button. Yo may also select the Invert
Result checkbox to list those systems that do not match the criteria selected.
The results appear at the bottom of the page. For details about using the resulting system list, refer to
Section 6.4.2 Systems.
6.4.7. Activation Keys —
RHN Management and Provisioning customers with the Activation Key Administrator role (including
Organization Administrators) can generate activation keys through the RHN website. These keys can
then be used to register a Red Hat Enterprise Linux system, entitle the system to an RHN service level
and subscribe the system to specific channels and system groups through the command line utility
rhnreg_ks. Refer to Section 2.5 Registering with Activation Keys for instructions on use.
Note
System-specific activation keys created through the Reactivation subtab of the System Details page
do not show up in this list because they are not reusable across systems.
6.4.7.1. Managing Activation Keys
To generate an activation key:
1. Select Systems => Activation Keys from the top and left navigation bars.
Page 98

86 Chapter 6. Red Hat Network Website
2. Click the create new key link at the top-left corner.
Warning
In addition to the fields listed below, RHN Satellite Ser ver customers may also populate the
Key field itself. This user-defined string of characters can then be supplied with rhnreg_ks to
register client systems with the Satellite. Do not insert commas in the key. All other characters
are accepted. Commas are problematic since they are the separator used when including two
or more activation keys at once. Refer to Section 6.4.7.2 Using Multiple Activation Keys at Once
—
for details.
3. Provide the following information:
• Description — User-defined description to identify the generated activation key.
• Usage Limit — The number of times the key can be used to register a system before the
activation key is disabled. Leave blank for unlimited use.
• Base Channel — The primary channel for the key. Selecting nothing will enable you to select
from all child channels, although systems can be subscribed to only those that are applicable.
• Entitlement — The service level for the key, either Management or Provisioning. All systems
will be subscribed at this level with the key.
• Universal default — Whether or not this key should be considered the primary activation
key for your organization.
Click Create Key.
After creating the unique key, it appears in the list of activation keys along with the number of times it
has been used. Note that only Activation Key Administrators can see this list. At this point, you may
associate child channels and groups with the key so systems registered with it will automatically be
subscribed to them.
To change information about a key, such as the channels or groups, click its description in the key
list, make your modifications in the appropriate tab, and click the Update Key button. To disassociate
channels and groups from a key, deselect them in their respective menus by [Ctrl]-clicking their highlighted names. To remove a key entirely, click the delete key link in the top-right corner of the edit
page.
If you do not want a key to be used to activate a system, you can disable it by unselecting the corresponding checkbox under the Enabled column in the key list. The key can be re-enabled by selecting
the checkbox. After making these changes, click the Update Keys button on the bottom right-hand
corner of the page.
6.4.7.2. Using Multiple Activation Keys at Once —
Provisioning customers should note that multiple activation keys can be included at the command
line or in a single kickstart profile. This allows you to aggregate the aspects of various keys without
having to recreate a new key specific to the desired systems, simplifying the registration and kickstart
processes while slowing the growth of your key list.
Without this stacking ability, your organization would need at least six activation keys to manage
four server groups and subscribe a server to any two groups. Factor in two versions of the operating
system, such as Red Hat Enterprise Linux 2.1 and 3, and you need twice the number of activation
keys. A larger organization would need keys in the dozens.
Before specifiying more than one activation key, you must understand how their values are combined
and resolved. These entities are straight unions: server groups, software packages, software child
channels, and config channels. A combination of these will be used. If there is a conflict between the
remaining properties, they will be resolved in the following manner:
Page 99

Chapter 6. Red Hat Network Website 87
• base software channels — registration fails
• entitlements — registration fails
• enable config flag — configuration management is set
Also remember, using a system-specific re-activation key along with a normal activation key will fail.
You’re now ready to use multiple activation keys at once. This is done with comma separation at the
command line with rhnreg_ks or in a kickstart profile within the Post tab of the Kickstart Details
page. Refer to Section 2.5 Registering with Activation Keys and Section 6.4.10.3 Creating Kickstarts,
relatively, for instructions.
6.4.8. Stored Profiles —
RHN Provisioning customers can create package profiles through the Profiles subtab of the Packages
tab within the System Details page. Those profiles end up here, on the Stored Profiles page, where
they may be edited and even deleted.
To edit a profile, click its name in the list, alter its name and description, and click the Update Profile.
To view software associated with the profile, click the Packages subtab. To remove the profile entirely,
click delete stored profile at the upper-right corner of the page.
6.4.9. Custom System Info —
RHN Provisioning customers may include completely customizable information about systems. Unlike notes, the information here is more formal and can be used in searches. For instance, you may
decide to identify an asset tag for each system. To do this, you must create an asset key within the
Custom System Info page.
Click create new key at the upper-right corner of the page. Enter a descriptive label and description,
such as Asset and Precise location of each system, and click the Create Key. The
key will then show up in the custom info keys list.
Once the key exists, you may assign a value to it through the Custom Info tab of the System Details
page. Refer to Section 6.4.2.6.1.5 System Details
DetailsCustom Info — for instructions.
6.4.10. Kickstart —
To satisfy the provisioning needs of customers, RHN provides this interface for developing kickstart
profiles that can be used to install Red Hat Enterprise Linux on either new or already-registered systems. This enables systems to be installed to particular specifications automatically.
Important
If your systems are connected to the central RHN Servers, you will need an external installation
tree for each distribution to be kickstarted. This tree can be hosted anywhere that is accessible by
the target system via HTTP. If the systems are connected through an RHN Proxy Server, then you
may place the installation tree in /var/www/html/pub / on the Proxy. RHN Satellite Servers already
have a tree for each Red Hat distribution and therefore do not require separate trees. Even if the
system connects through an RHN Proxy Server to get to the Satellite, these trees will be available
for kickstart. Refer to Section 6.4.10.9 Kickstart
installation trees.
Distributions — for instructions on setting up
Page 100

88 Chapter 6. Red Hat Network Website
6.4.10.1. Kickstart Prerequisites
Although Red Hat Network has taken great pains to ease the provisioning of systems, some preparation is still required for your infrastructure to handle kickstarts. For instance, before creating kickstart
profiles, you may consider:
• A DHCP server is not required for kickstarting, but it can make things easier. If you are using static
IP addresses, you should select static IP while developing your kickstart profile.
• An FTP server can be used in place of hosting the kickstart distribution trees via HTTP.
• If conducting a bare metal kickstart, you should 1)Configure DHCP to assign required networking
parameters and the bootloader program location. 2)Specify within the bootloader configuration file
the kernel to be used and appropriate kernel options.
For a decription of the innerworkings of the kickstart process, refer to Section 6.4.10.2 Kickstart
Explained.
6.4.10.2. Kickstart Explained
When a machine is to receive a network-based kickstart, the following events must occur in this order:
1. After being placed on the network and turned on, the machine’s PXE logic broadcasts its MAC
address and a request to be discovered.
2. If a static IP address is not being used, the DHCP server recognizes the discovery request and
extends an offer of network information needed for the new machine to boot. This includes an
IP address, the default gateway to be used, the netmask of the network, the IP address of the
TFTP or HTTP server holding the bootloader program, and the full path and filename of that
program (relative to the server’s root).
3. The machine applies the networking information and initiates a session with the server to request
the bootloader program.
4. The bootloader, once loaded, searches for its configuration file on the server from which it was
itself loaded. This file dictates which kernel and kernel options, such as the initial RAM disk
(initrd) image, should be executed on the booting machine. Assuming the bootloader program is
SYSLINUX, this file will be located in the pxelinux.cfg directory on the server and named
the hexadecimal equivalent of the new machine’s IP address. For example, a bootloader configuration file for Red Hat Enterprise Linux AS 2.1 should contain:
port 0
prompt 0
timeout 1
default My_Label
label My_Label
kernel vmlinuz
append ks=http://myrhnsatellite/ initrd=initrd.img network apic
5. The machine accepts and uncompresses the init image and kernel, boots the kernel, and initiates
a kickstart installation with the options supplied in the bootloader configuration file, including
the server containing the kickstart configuration file.
6. This kickstart configuration file in turn directs the machine to the location of the installation
files.
7. The new machine is built based upon the parameters established within the kickstart configuration file.
 Loading...
Loading...