Page 1

Red Hat Network
User Reference Guide 3.1
Page 2

ISBN: N/A
Red Hat, Inc.
2600 Meridian Parkway
Durham, NC 27713 USA
+1 919 547 0012 (Voice)
+1 919 547 0024 (FAX)
888 733 4281 (Voice)
P.O. Box 13588
Research Triangle Park, NC 27709 USA
© 2001 Red Hat, Inc.
RHNurg(EN)-3.1-Print-RHI (2001-09-05T14:52-0400)
Copyright © 2001 by Red Hat, Inc. This material may be distributed only subject to the terms and con-
ditions set forth in the Open Publication License, V1.0 or later (the latest version is presently available
at http://www.opencontent.org/openpub/).
Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder.
Distribution of the work or derivative of the work in any standard (paper) book form for commercial
purposes is prohibited unless prior permission is obtained from the copyright holder.
Red Hat, Red Hat Network, the Red Hat "Shadow Man" logo, RPM, Maximum RPM, the RPM logo,
Linux Library, PowerTools, Linux Undercover, RHmember, RHmember More, Rough Cuts, Rawhide
and all Red Hat-basedtrademarks and logos are trademarks orregisteredtrademarks of Red Hat, Inc.
in the United States and other countries.
Linux is a registered trademark of Linus Torvalds.
Motif and UNIX are registered trademarks of The Open Group.
Itanium is a registered trademark of Intel Corporation.
Netscape is a registered trademark of Netscape Communications Corporation in the United States and
other countries.
Windows is a registered trademark of Microsoft Corporation.
SSH and Secure Shell are trademarks of SSH Communications Security, Inc.
FireWire is a trademark of Apple Computer Corporation.
S/390 and zSeries are trademarks of International Business Machines Corporation.
All other trademarks and copyrights referred to are the property of their respective owners.
Printed in Canada, Ireland, and Japan
ii
Page 3

Contents
Red Hat Network
Introduction................... ..................... ..................... ..................... . v
Document Conventions.................................................................... v
More to Come .............................................................................. viii
Chapter 1 What is Red Hat Network? . ..................... .............. 9
1.1 Software Manager................................................................ 10
1.2 Automatic Notifications........................................................... 10
1.3 Security, Quality Assurance, and Red Hat Network .......................... 11
1.4 Before You Begin ................................................................. 11
Chapter 2 Red Hat Network Registration Client....... ............ 13
2.1 Configuring the Red Hat Network Registration Client ........................ 13
2.2 Starting the Red Hat Network Registration Client............................. 14
2.3 Registering a User Account ..................................................... 16
2.4 Registering a System Profile .................................................... 19
2.5 Finishing Registration ............................................................ 22
2.6 Entitling Your System............................................................. 24
2.7 Text Mode RHN Registration Client............................................. 25
Chapter 3 Red Hat Update Agent Configuration Tool ......... 27
3.1 Configuring the Red Hat Update Agent ........................................ 27
3.2 General Settings.................................................................. 27
3.3 Retrieval/Installation Settings ................................................... 28
3.4 Package Exceptions Settings ................................................... 30
3.5 Command Line Version of Red Hat Update Agent Configuration Tool...... 31
Chapter 4 Red Hat Update Agent ................ ..................... ...... 33
4.1 Starting the Red Hat Update Agent ............................................ 33
4.2 Choosing a Channel ............................................................. 35
iii
Page 4

4.3 Choosing Packages to Update.................................................. 36
4.4 Installing Updated Packages.................................................... 39
4.5 Update Agent Finished........................................................... 40
4.6 Command Line Version of Red Hat Update Agent............................ 41
4.7 Manual Package Installation..................................................... 45
4.8 Synchronizing Your System Profile ............................................. 46
4.9 Log File ............................................................................ 46
Chapter 5 Software Manager ............ ..................... ................. 47
5.1 Logging into Software Manager................................................. 47
5.2 Introduction to the Web Interface ............................................... 48
5.3 Your RHN....... ..................... ..................... ..................... .... 51
5.4 Systems ........................................................................... 53
5.5 Channels and Packages...... ..................... ..................... ......... 57
5.6 Errata ........... ..................... ..................... ..................... .... 60
5.7 Scheduled Actions................................................................ 62
Chapter 6 Red Hat Network Daemon............ ..................... .... 65
Chapter 7 Using Red Hat Network with Red Hat Linux 6.2.67
Chapter 8 Frequently Asked Questions ..... ..................... ...... 69
Glossary.... .................. ..................... ..................... ..................... .... 73
iv
Page 5

Section 0.1:Document Conventions v
Introduction
Welcome to the Red Hat Network User Reference Guide 3.1.
The Red Hat Network User Reference Guide will guide you through registering your system for Red
Hat Network and using its many features. Depending on which version of Red Hat Linux you have
installed, the Red Hat Network Registration Client and the Red Hat Update Agent might be
different than the ones described in this manual as new features are added. All version of this manual
are available in HTML and PDF formats at http://www.redhat.com/docs/manuals/RHNetwork/. Once
you use Red Hat Network to update these applications, you can use the latest version of this manual.
This version of the manual covers version 2.7.0 of the Red Hat Update Agent and version 1.5.0 of the
Red Hat Network Registration Client.
For a more detailed, technical overview of Red Hat Network, please refer to the Red Hat Network
Technical Paper available at http://www.redhat.com/products/network/.
Document Conventions
When you read this manual, you will see that certain words are represented in different fonts, typefaces, sizes and weights. This highlighting is systematic; different words are represented in the same
style to indicate their inclusion in a specific category. The types of words that are represented this way
include the following:
command
Linux commands (and other operating system commands, when used) are represented this way.
This style should indicate to you that you can type in the word or phrase on the command line
and press
displayed in a different style on their own (e.g., filenames). In these cases, they are considered
to be part of the command, so the entire phrase will be displayed as a command. For example:
Use the cat testfile command to view the contents of a file, named testfile, in the
current working directory.
filename
Filenames, directory names, paths and RPM package names are represented this way. This style
should indicate that a particular file or directory exists by that name on your Red Hat Linux
system. Examples:
The .bashrc file in your home directory contains bash shell definitions and aliases for your
own use.
The /etc/fstab file contains information about different system devices and filesystems.
[Enter] to invoke a command. Sometimes a command contains words that would be
Page 6

vi Introduction
The /usr/share/doc directory contains documentation for various programs.
Install the webalizer RPM if you want to use a Web server log file analysis program.
application
This style should indicate to you that the program named is an end-user application (as opposed
to system software). For example:
Use Netscape Navigator to browse the Web.
[key]
A key on the keyboard is shown in this style. For example:
[Tab]
To use
completion, type in a character and then press the [Tab] key. Your terminal will
display the list of files in the directory that start with that letter.
[key]-[combination]
A combination of keystrokes is represented in this way. For example:
The
[Ctrl]-[Alt]-[Backspace] key combination will restart the X Window System.
text found on a GUI interface
A title, word or phrase found on a GUI interface screen or window will be shown in this style.
When you see text shown in this style, it is being used to identify a particular GUI screen or an
element on a GUI screen (e.g., text associated with a checkbox or field). Examples:
On the GNOME
Selectthe
Control Center screen, you can customize your GNOME window manager.
RequirePasswordcheckbox if you would like your screensaverto require a password
before stopping.
top level of a menu on a GUI screen or window
When you see a word in this style, it indicates that the word is the top level of a pulldown menu.
If you click on the word on the GUI screen, the rest of the menu should appear. For example:
Settings on a GNOME terminal, you will see the following menu items: Preferences,
Under
Reset Terminal, Reset and Clear, and Color selector.
If you need to type in a sequence of commands from a GUI menu, they will be shown like the
following example:
Click on
button on a GUI screen or window
Programs=>Applications=>Emacs to start the Emacs text editor.
This style indicates that the text will be found on a clickable button on a GUI screen. For example:
Page 7

Section 0.1:Document Conventions vii
Click on the Back button to return to the Web page you last viewed.
computer output
When you see text in this style, it indicates text displayed by the computer on the command line.
You will see responses to commands you typed in, error messages and interactive prompts for
your input during scripts or programs shown this way. For example:
Use the ls to display the contents of a directory:
$ls
Desktop axhome logs paulwesterberg.gif
Mail backupfiles mail reports
The output returned in response to the command (in this case, the contents of the directory) is
shown in this style.
prompt
A prompt, which is a computer’s way of signifying that it is ready for you to input something,
will be shown in this style. Examples:
$
#
[stephen@maturin stephen]$
leopard login:
user input
Text that the user has to type, either on the command line, or into a text box on a GUI screen, is
displayed in this style. In the following example, text is displayed in this style:
To boot your system into the text based installation program, you will need to type in the text
command at the boot: prompt.
Another example, with the word root displayed as something the user needs to type in:
If you need to log in as root when you first log into your system, and you are using the graphical
login screen, at the Login prompt, type root. At the Password prompt, type in the root
password.
Additionally,we use several different strategies to draw your attention to certain pieces of information.
In order of how critical the information is to your system, these items will be marked as a note, a
caution or a warning. For example:
Page 8

viii Introduction
Note
Remember that Linux is case sensitive. In other words, a rose is not a ROSE
is not a rOsE.
CAUTION
Do not do routine tasks as root — use a regular user account unless you need
to use the root account to administer your system.
WARNING
If you choose not to partition manually, a server installation will remove
all existing partitions on all installed hard drives. Do not choose this
installation class unless you are sure you have no data you need to save.
More to Come
The Red Hat Network User Reference Guide is constantly expanding as newRed Hat Network features
and service plans are launched.
Send in Your Feedback
If you would like to make suggestions about the Red Hat Network User Reference Guide, please mention this guide’s identifier:
RHNurg(EN)-3.1-Print-RHI (2001-09-05T14:52-0400)
You can send mail to:
rhn-feedback@redhat.com
Page 9

What is Red Hat Network? 9
1 What is Red Hat Network?
Have you ever read about a new version of a software package and wanted to install it but could not
find it?
Haveyou ever tried to find an RPM through an Internet search engine or an RPM Repository and been
linked to a site that you have never heard of?
Have you ever tried to find an RPM but instead you are only able to find the source files that you have
to compile yourself?
Haveyoueverspenthours or even days visiting different websites to see if you havethelatest packages
installed on your system, only to have to do it again in a few months?
Those days are over with Red Hat Network (RHN). RHN provides the solution to all your system
software management needs.
Red Hat Network is an Internet solution for managing a Red Hat Linux system or a network of Red
Hat Linux systems. All Security Alerts, Bug Fix Alerts, and Enhancement Alerts (collective known
as Errata Alerts) can be downloaded directly from Red Hat. You can even have updates automatically
delivered directly to your system as soon as they are released.
The three main components of Red Hat Network are as follows:
• The Red Hat Network Registration Client
• The Red Hat Network user interface
• Red Hat Network Daemon
The Red Hat Network Registration Client allows you to create a unique RHN user name and password and probes the hardware and software on your system to create a System Profile. The System
Profile is sent to RHN and RHN returns a unique System ID to your system (see Chapter 2,
Network Registration Client
You can use either of the two Red Hat Network user interfaces:
• Software Manager Web interface available at http://rhn.redhat.com
• The Red Hat Update Agent
Both the Webinterfaceand the Red Hat UpdateAgent allow you to view all Errata Alerts included in
the Red Hat Errata list. Only packages relevant to your system are shown. Red Hat Network can also
be configured to verify packages once downloaded, ignore update notifications for certain packages,
and view package details before downloading them.
for further information).
Red Hat
Page 10

10 Chapter 1:What is Red Hat Network?
The Red Hat Network Daemon (rhnsd) runs in the background as a service and probes the Red Hat
Network for notifications and updates at set time intervals (see Chapter 6, Red Hat Network Daemon
for further information).
Many Red Hat Network terms are used throughout this manual. As you read the Red Hat Network
User Reference Guide, refer to the Glossary as necessary for explanation of common terms.
1.1 Software Manager
The first subscription service offered through Red Hat Network is Software Manager. Additional
service offerings will be available in the near future. Registering a system with Red Hat Network is
free as well as one subscription to Software Manager. Additional subscription to Software Manager
can be purchased at http://rhn.redhat.com/purchase_info.pxt.
With each Software Manager subscription, you receive:
• Errata Alerts — learn when Security Alerts, Bug Fix Alerts, and Enhancement Alerts are issued
for all the systems in your network through the Software Manager interface
• Automatic email notifications — receive an email notification when an Errata Alert is issued for
your system
• Scheduled Errata Updates — schedule delivery of Errata Updates with optional automatic installation
• Package installation — Schedule package installation on one or more systems with the click of a
button.
• Red Hat Update Agent — use the Red Hat Update Agent to download the lastest software
packages for your system with optional installation of packages
1.2 Automatic Notifications
During registration, you can configure Red Hat Network to send you email notifications of new and
updated software packages. Automated notifications of the latest updates:
• Reduce the time and effort required by system administrators to stay on top of the Red Hat errata
list
• Minimize security vulnerabilities in your network by providing the patches as soon as Red Hat
releases them
• Filter out package updates not relevant to your network
• Provide a reliable method of managing multiple systems with similar configurations
Page 11

Section 1.4:Before You Begin 11
1.3 Security, Quality Assurance, and Red Hat
Network
Red Hat Network provides significant benefits to your network including security and quality assurance. All transactions made between you and Red Hat Network are encrypted, and all RPM packages
are signed with Red Hat’s GNU Privacy Guard (GPG) signature to ensure authenticity.
Red Hat Network incorporates the following security measures:
1. Your System Profile available at http://rhn.redhat.com is only accessible with the correct user
name and password.
2. A Digital Certificate stored on the client system in the file /etc/sysconfig/rhn/systemid
after registration is used to authenticate the system during each transaction between the client and
Red Hat Network.
3. All notifications and information messages are signed by Red Hat with an electronic signature using GPG. The rpm utility can be used to verify the authenticity of the package before it is installed.
4. All transactions are encrypted using a Secure Sockets Layer (SSL) connection.
5. All packages are tested and verified by the Red Hat Quality Assurance Teambefore they are added
to the Red Hat errata list and Red Hat Network.
1.4 Before You Begin
Red Hat Network is available for Red Hat Linux 6.2 and higher. For instructions on configuring Red
Hat Linux 6.2 for Red Hat Network, refer to Chapter 7, Using Red Hat Network with Red Hat Linux
6.2.
By default, all the software packages you need to use Red Hat Network are installed with Red Hat
Linux 7 and higher. However, if you chose not to install them during the installation process or performed an upgrade from Red Hat Linux 6.2 or lower, you might not have the Red Hat Network
Registration Client or the Red Hat Update Agent installed. To verify that the Red Hat Network
Registration Client is installed, type the following command:
rpm -q rhn_register
If the Red Hat Network Registration Client is installed, it will return something similar to
rhn_register-1.5.0-1
The version number might differ slightly if you have a newer version installed.
If you do not have Red Hat Network Registration Client installed, the command will return
Page 12

12 Chapter 1:What is Red Hat Network?
package rhn_register is not installed
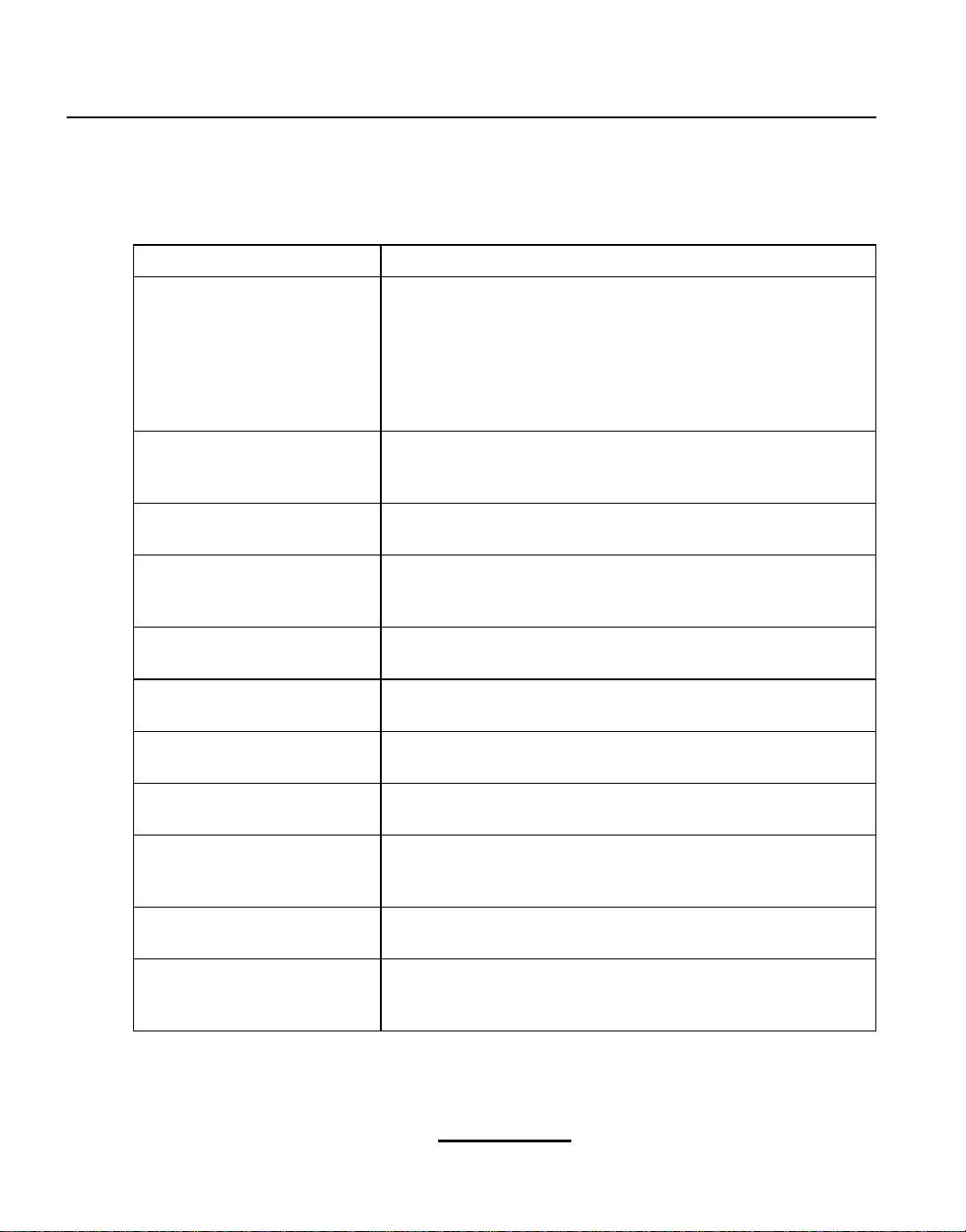
Perform this check for every package in Table 1–1, Red Hat Network Packages. If you do not want to
use the graphical versions, you do not have to install the two packages ending in gnome.
Table 1–1 Red Hat Network Packages
Package Name Description
rhn_register
Provides the Red Hat Network Registration Client program and the
text mode interface
rhn_register-gnome
Provides the GNOME interface (graphical version) for the Red Hat
Network Registration Client; runs if the X Window System is available
up2date
Provides the Red Hat Update Agent command line version and the
Red Hat Network Daemon
up2date-gnome
Provides the GNOME interface (graphical version) for the Red Hat
Update Agent; runs if the X Window System is available
Ifthe packages are not installed, theycan be found on the RedHat Linux 7 or higher CD-ROM #1 in the
RedHat/RPMS directory or downloaded from the Red Hat FTP site available at ftp://ftp.redhat.com
(or from a Red Hat FTP mirror available at http://www.redhat.com/mirrors.html). Always check the
Red Hat errata page, available at http://www.redhat.com/errata/, for package updates. If you install
an older version of these packages, you can retreive the latest versions using Red Hat Network. The
first time that you request the RPM Updates for your system, they will be included.
Page 13

Section 2.1:Configuring the Red Hat Network Registration Client 13
2 Red Hat Network Registration Client
Before you begin using Red Hat Network, you need to create a user name, password, and System
Profile. The Red Hat Network Registration Client will walk you through this process.
2.1 Configuring the Red Hat Network Registration
Client
WARNING
Mostusers do not need toconfiguretheRed Hat NetworkRegistration
Clientbeforeregistering their systems. Do not attempt to use this option
unless you are required to.
To start the configuration tool, use the command:
rhn_register --configure
You will be presented with a list of options and their current values:
0. enableProxyAuth No
1. noSSLServerURL http://www.rhns.redhat.com/XMLRPC
2. enableProxy No
3. httpProxy
4. proxyUser
5. serverURL https://www.rhns.redhat.com/XMLRPC
6. proxyPassword
7. debug No
Enter number of item to edit <return to exit, q to quit without saving>:
Enter the number of the item that you want to modify, and enter a new value for the option. When
you finish changing your configuration, press
[Enter] to quit without saving your changes.
The most common options configured are numbers 1 and 2 to enable a proxy server. To enable
a proxy server, change the value for enableProxy to Yes and the value of httpProxy to
the name of the proxy server and port number in the format http://HOST:PORT. For example,
to use the proxy server http://squid.mysite.org on port 3128, you would change the value to
http://squid.mysite.org:3128.
[Enter] to save your changes and exit. Press [q] and then
Page 14

14 Chapter 2:Red Hat Network Registration Client
If you require a proxy username and password, change the values of numbers 0, 4, and 6. Set enableProxyAuth to Yes to enable username/password authentication for the proxy. Set proxyUser and proxyPassword to the appropriate username and password for the proxy.
2.2 Starting the Red Hat Network Registration Client
You must be root to register a system with RHN. If you start the Red Hat Network Registration
Client as a standard user, you will be prompted to enter the root password before proceeding. To start
the Red Hat Network Registration Client in Red Hat Linux 6.2 or higher, use one of the following
methods:
1. On the GNOME desktop, go to the
=> Red Hat Network
2. On the KDE desktop, go to the
Hat Network
3. Type the command rhn_register at a shell prompt (for example an xterm or gnome-terminal)
4. If you are not running the X Window System, type the command rhn_register at a virtual
console or remote terminal. Please refer to Section 2.7, Text Mode RHN Registration Client for
further details.
Main Menu Button (on the Panel) => Programs => System
Main Menu Button (on the Panel) => Red Hat => System => Red
CAUTION
You must use Python 1.5.2-24 or later with Secure Sockets Layer (SSL)
support. If not, the information you transfer will not be encrypted. If you
have an earlier version of Python, you will see the message shown in Figure 2–1, Use Python 1.5.2-24 or later. To determine the version of Python
on your system, use the command rpm -q python. It is strongly recommended you use Python 1.5.2-24 or later.
Page 15

Section 2.2:Starting the Red Hat Network Registration Client 15
Figure 2–1 Use Python 1.5.2-24 or later
The opening screen for the Red Hat Network Registration Client gives you a brief overview of the
services available and the steps required to register (see Figure 2–2, Welcome Screen). Click
continue with the registration process. If you click
Cancel, the registration process will end and no
Next to
information will be sent.
Figure 2–2 Welcome Screen
Red Hat is committed to protecting your privacy (see Figure 2–3, Red Hat Privacy Statement). The
information gathered during the Red Hat Network Registration process is used to create a System
Profile. The System Profile is essential if you wish to receive update notifications about your system.
If you have any questions about how your information is being used, please contact us at feed-
back@redhat.com.
Page 16

16 Chapter 2:Red Hat Network Registration Client
Figure 2–3 Red Hat Privacy Statement
2.3 Registering a User Account
Before you can create a System Profile, you must create a user account. The only required information
in this section is a unique user name and password and a valid email address.
In the screen shown in Figure 2–6, Create a Unique User Name and Password, you must choose a user
name and password. Once logged into Red Hat Network, you can modify your preferences, view your
existing System Profile, or obtain the lastest Red Hat software packages. You must choose a unique
user name. If you enter one already in use, you will see an error message (see Figure 2–4, Error:
Username Already Exists).
Page 17

Section 2.3:Registering a User Account 17
Figure 2–4 Error: Username Already Exists
Note
If you are already a member of redhat.com, you can use the same user name
and password. However, you will still need to continue with the registration
process to create your System Profile.
Your user name and password have the following restrictions:
• Must be at least four characters long
• Are case-insentitive
• Can not contain any spaces
• Can not contain any tabs
• Can not contain any line feeds
• Can not contain the characters &, +, %, or ’
If you have already registered your system and try to register it again, the dialog box shown in Figure
2–5, Warning: This System Already Registeredwill appear. If you continue, it will overwrite your ex-
isting systemid file (/etc/sysconfig/rhn/systemid) and you will create a different System
Profile. You will no longer be able to use your previous System Profile — be sure this is what you
want to do before you choose
Yes.
Page 18

18 Chapter 2:Red Hat Network Registration Client
Figure 2–5 Warning: This System Already Registered
If you have already registered a machine and created a System Profile, you can add a new machine to
your account. Run the Red Hat Network Registration Client on the new machine you wish to add
and enter your existing Red Hat Network user name and password. The new machine will be added
to your existing account, and you can log into Red Hat Network with your user name and password
to view all your systems simultaneously.
Figure 2–6 Create a Unique User Name and Password
Page 19

Section 2.4:Registering a System Profile 19
Most users can leave the Org Info section blank. If you have an existing organization account, enter
your organization’s ID and password in the provided text fields. If the values are valid, the system
will be added to the organization’s Red Hat Network account.
Next to continue.
Click
2.4 Registering a System Profile
Now that you have a user account, you can create a System Profile that consists of hardware and
software information about your Red Hat Linux system. The software System Profile information is
used by Red Hat Network to determine what software update notifications you receive.
2.4.1 Hardware System Profile
After creating a user name and password for your Red Hat Network account, the Red Hat Network
Registration Client probes your system for the following information:
• Red Hat Linux version
• Hostname
• IP address
• CPU model
• CPU speed
• Amount of RAM
• PCI devices
• Disk sizes
• Mount points
The next step is choosing a profile name for your system as shown in Figure 2–7, System Profile -
Hardware. The default value is the hostname for the system. You may modify this to be a more
descriptive string such as Email Server for Support Team if you find it more helpful. Optionally,
you can enter a computer serial or identification number for the system.
If you do not wish to include information about your hardware or network in your System Profile,
deselect
ware).
Click
Include information about hardware and network (see Figure 2–7, System Profile - Hard-
Next to continue with the registration process.
Page 20

20 Chapter 2:Red Hat Network Registration Client
Figure 2–7 System Profile - Hardware
2.4.2 Software System Profile
The software System Profile consists of a list of RPM packages for which you wish to receive notifications. The Red Hat Network Registration Client shows you a list of all RPM packages listed in
the RPM database on your system and then allows you to customize the list by deselecting packages.
Gathering RPM Database Information
Only those packages you choose during this part of the registration will be included in in your System
Profile, and you will only receive notifications about the packages in your System Profile. Thus, if
you use an older version of a package and deselect it from the list, it will not be replaced with a newer
version. This RPM list can be modifed through the Red Hat Network web interface or by using the
Red Hat Update Agent. As shown in Figure 2–8, RegistrationWizard , querying the RPM database
may take some time depending on your system.
Page 21

Section 2.4:Registering a System Profile 21
Figure 2–8 Registration Wizard
Once the RPM package list is built, the list will be displayed as shown in Figure 2–9, RPM Package
Information. Deselecting
will omit this information from your System Profile.
Include RPM Packages installed on this system in my System Profile
Figure 2–9 RPM Package Information
Choosing Which RPM Packages to Exclude from the System Profile
By default, all RPM packages in your RPM database are included in your System Profile to be updated
by Red Hat Network. Toexcludeapackage, uncheck the package from the list by clicking theX beside
the package name. For example, Figure 2–10, Choose which RPM Packages to Exclude from System
Page 22

22 Chapter 2:Red Hat Network Registration Client
Profile shows that the procmail, procps, and psgml packages have been omitted from the package
list.
Choose which packages to exclude from the system profile, and click
tration process.
Next to continue with the regis-
Figure 2–10 Choose which RPM Packages to Exclude from System Profile
2.5 Finishing Registration
As seen in Figure 2–11, Finished Collecting Information for System Profile,thelast step of registration
is to confirm that you want to send your System Profile to the Red Hat Network. If you choose Cancel
at this point, no information will be sent. Clicking Next will send your profile.
Page 23

Section 2.5:Finishing Registration 23
Figure 2–11 Finished Collecting Information for System Profile
Figure 2–12, Send System Profileto Red Hat Network shows the progress bar you will see while your
profile is being sent. This process may take some time depending on your connection speed.
Figure 2–12 Send System Profile to Red Hat Network
You will know your System Profile has been successfully sent when you see the Registration Finished
screen (Figure 2–13, RegistrationFinished). Click Finish to exit the Red Hat Network Registration
Client.
After completing registration, visit http://rhn.redhat.com to verify your System Profile and make any
changes.
Page 24

24 Chapter 2:Red Hat Network Registration Client
Figure 2–13 Registration Finished
2.6 Entitling Your System
Nowthatyou haveregistered your system, it must be entitled before you can receiveupdated packages.
In other words, you must subscribe it to Software Manager. Everyone automatically receives one free
Software Manager subscription after creating an account through registering a system for RHN or
creating a redhat.com account.
To entitle a system, go to http://rhn.redhat.com and login using the same username and password you
just used in the Red HatNetwork RegistrationClient. On the left navigation bar, click
under the Your RHN category. The Entitlement Manager tells you how many entitlements you have
left. If you have one or more left, check the checkbox under the
the system that you just registered. Then click the
page. The number of entitlements remaining will decrease, and your system is now ready to use the
Red Hat Update Agent and Software Manager. Refer to Chapter 4,
Chapter 5, Software Manager for details on how to use them. If you do not have any entitlement slots
left, enter the number you want to purchase and click the
subscriptions.
Update Entitlements button at the bottom of the
Entitled column beside the name of
Red Hat Update Agent
Buy Now! button to purchase additional
Entitlements
and
Page 25

Section 2.7:Text Mode RHN Registration Client 25
2.7 Text Mode RHN Registration Client
You can force the Red Hat Network Registration Client to run in text mode with the command:
rhn_register --nox
The screens for the Text Mode Red Hat Network Registration Client are almost identical to the
screens for the graphical version of Red Hat Network Registration Client. Some of the text in the
text mode version is more concise due to lack of space in the interface. However, there is an equal
number of screens and fields in both versions. Thus, if you are using the text mode version, you can
still follow the instructions that begin in Section 2.2, Starting the
.
Client
Figure 2–14 Text Mode Welcome Screen
Red Hat Network Registration
Page 26

26 Chapter 2:Red Hat Network Registration Client
Page 27

Section 3.2:General Settings 27
3 Red Hat Update Agent Configuration
Tool
Before using the Red Hat Update Agent, you should configure the settings. This can be done with
the Red Hat Update Agent Configuration Tool.
If you are not running the X Window System or prefer the command line version, skip to Section 3.5,
Command Line Version of
Red Hat Update Agent Configuration Tool
3.1 Configuring the Red Hat Update Agent
You must be root to run the Red Hat Update Agent Configuration Tool. If you start the Red Hat
UpdateAgent ConfigurationTool as a standard user, you will beprompted to enter the root password
before proceeding. The Red Hat Update Agent Configuration Tool can be started using one of the
following methods:
• On the GNOME desktop, go to the
=> Update Agent Configuration
• On the KDE desktop, go to the
Configuration
• Type the command up2date-config at a shell prompt (for example, an xterm or a gnometerminal)
Main Menu Button (on the Panel) => Programs => System
Main Menu Button (on the Panel) => Red Hat => Update Agent
.
3.2 General Settings
The General tab allows you to enable an HTTP Proxy Server. If your network connection
requires you to use an HTTP Proxy Server to make HTTP connections, select the
Proxy
option and type your proxy server in the text field with the format http://HOST:PORT.
For example, to use the proxy server http://squid.mysite.org on port 3128, you would enter
http://squid.mysite.org:3128 in the text field. Additionally, if your proxy server
requires a username and password, select the
and password in the respective text fields.
Use Authenication option and enter your username
Enable HTTP
Page 28

28 Chapter 3:Red Hat Update Agent Configuration Tool
Figure 3–1 General Settings
3.3 Retrieval/Installation Settings
The Retrieval/Installation tab allows you to customize your software package retrieval and package
installation preferences.
Note
You must use Red Hat Update Agent Version 2.5.4 or higher to upgrade
your kernel automatically. Red Hat Update Agent will install the updated
kernel and configure LILO to boot the new kernel the next time the system
is rebooted.
Page 29

Section 3.3:Retrieval/Installation Settings 29
Figure 3–2 Retrieval/Installation Settings
The following retrieval options can be selected (see Figure 3–2, Retrieval/Installation Settings):
Do not install packages after retrieval — download selected RPM packages to desired directory
•
and ignore the installation preferences
Do not display packages when local configuration file has been modified — if the configura-
•
tion file has been modified for a package such as Apache or Squid, do not display them in the list
of available packages
Retrieve source RPM along with binary package — download both the source (*.src.rpm) and
•
the binary (*.[architecture].rpm) files
The following installation options are configurable (see Figure 3–2, Retrieval/Installation Settings):
After installation, keep binary packages on disk
•
— save binary packages in desired directory
instead of deleting them after installing them
Use GPG to verify package integrity — before installing the packages, verify Red Hat’s GPG
•
signature
The following additional options are configurable from this tab:
Page 30

30 Chapter 3:Red Hat Update Agent Configuration Tool
• Overrideversion stored in System Profile— overridethe Red Hat Linux versionin your System
Profile
Packagestorage directory — change the directory where packages are downloaded; the default
•
location is /var/spool/up2date
3.4 Package Exceptions Settings
The Package Exceptions tab allows you to define which packages to exclude from the list of updated
RPM packages according to the package name or file name (see Figure 3–3, Package Exceptions Set-
tings).
To define a set of packages to be excluded according to the package name, click the
Package Names to Skip section and enter a character string including wild cards (*). A wild
to the
card (*) at the end of the character string means all packages beginning with the character string will
be excluded from the list. A wild card (*) at the beginning of the character string means any packages
that end with the character string will be excluded from the list.
Forexample, if the string kernel* in the
PackageNames to Skip section, the Red Hat Update Agent
will not display any packages beginning with kernel.
Add button next
To exclude packages by file name, follow the same rules except click the
Names to Skip
section.
Add button next to the File
Page 31

Section 3.5:Command Line Version of Red Hat Update Agent Configuration Tool 31
Figure 3–3 Package Exceptions Settings
3.5 Command Line Version of Red Hat Update Agent
Configuration Tool
The command line version of this tool performs the same function as the graphical version. It allows
you to configure the settings used by the Red Hat Update Agent and store them in the configuration
file /etc/sysconfig/rhn/up2date.
To run the command line version of the Red Hat Update Agent Configuration Tool, use the follow-
ing command:
up2date --nox --configure
You will be presented with a list of options and their current values:
0. storageDir /var/spool/up2date
1. headerCacheSize 40
2. httpProxy
3. debug No
4. useGPG Yes
Page 32

32 Chapter 3:Red Hat Update Agent Configuration Tool
5. networkRetries 5
6. removeSkipList [’kernel*’]
7. retrieveOnly No
8. enableProxy No
9. keepAfterInstall No
10. proxyPassword
11. proxyUser
12. headerFetchCount 10
13. versionOverride
14. enableProxyAuth No
15. noSSLServerURL http://www.rhns.redhat.com/XMLRPC
16. noReplaceConfig Yes
17. noBootLoader No
18. systemIdPath /etc/sysconfig/rhn/systemid
19. serverURL https://beta.rhns.redhat.com/XMLRPC
20. pkgSkipList [’kernel*’]
21. adminAddress [’root@localhost’]
22. forceInstall No
23. fileSkipList []
24. retrieveSource No
Enter number of item to edit <return to exit, q to quit without saving>:
Enter the number of the item that you want to modify and enter a new value for the option. When
you finish changing your configuration, press
[Enter] to quit without saving your changes.
[Enter] to save your changes and exit. Press [q] and then
Page 33

Section 4.1:Starting the Red Hat Update Agent 33
4 Red Hat Update Agent
After configuring the settings for the Red Hat Update Agent using the instructions in Chapter 3,
HatUpdate Agent Configuration Tool
software packages from Red Hat. Using this tool will allow you to always have the most up-to-date
Red Hat Linux system with all security patches, bug fixes, and software package enhancements.
Remember that you can not use the Red Hat Update Agent on a system unless it is subscribed to
Software Manager.
If you are not running the X WindowsSystemor prefer the command-line version of Red Hat Update
Agent, skip to Section 4.6, Command Line Version of Red Hat Update Agent.
, you can use the Red HatUpdate Agentto retrieve the latest
Red
4.1 Starting the Red Hat Update Agent
You must be root to run the Red Hat Update Agent. If you start the Red Hat Update Agent as
a standard user, you will be prompted to enter the root password before proceeding. The Red Hat
Update Agent can be started using one of the following methods:
• On the GNOME desktop, go to the
=> Update Agent
• On the KDE desktop, go to the
• Type the command up2date at a shell prompt (for example, an xterm or gnome-terminal)
If you choose the last option and start the application from a shell prompt, you can specify the options
in Table 4–1, Graphical Update Agent Options to the Red Hat Update Agent.
Table 4–1 Graphical Update Agent Options
Argument Description
Main Menu Button (on the Panel) => Programs => System
Main Menu Button (on the Panel) => Red Hat => Update Agent
--configure
-d, --download Download packages only, do not install them. This argument
-f, --force Force package installation. This option overrides the file,
Configure Red Hat Update Agent options. This is equivalent
to running the Red Hat Update Agent Configuration Tool
(up2date-config).
will override the configuraton option
after retrieval.
package, and configuration skip lists.
Do not install packages
Page 34

34 Chapter 4:Red Hat Update Agent
Argument Description
-i, --install Install packages after they are downloaded. This argument will
override the configuraton option
retrieval.
Do not install packages after
-k, --packagedir Specify a colon separated path of directories to look for packages
before trying to download them.
--nosig Do not use GPG to check package signatures. This option will
override the saved configuration option.
--tmpdir=directory Override the configured package directory. The default location
is /var/spool/up2date. This option is useful if you do not
have enough space in the configured location.
--justdb Only add packages to the database and do not install them.
--dbpath Specify a path where an alternate RPM database to use is found.
The first time you run the Red Hat Update Agent, the dialog window in Figure 4–1, Install GPG
Key will prompt you to install the Red Hat GPG key. This is used to verify the RPM packages you
download for security purposes. Click
Yes to install the key,and you will not see this message again.
Figure 4–1 Install GPG Key
After installing the Red Hat GPG key,the screen in Figure 4–2, WelcomeScreenwillappear. It appears
every time you start the Red Hat Update Agent. Click
Next to continue.
Page 35

Section 4.2:Choosing a Channel 35
Figure 4–2 Welcome Screen
4.2 Choosing a Channel
The first step is to select the channel(s) from which you want the updated packages to be retreived.
Select one or more channels and click
information on channels and how channels are used to determine which packages to install.
Next. Refer to Section 5.5, Channels and Packages for more
Page 36

36 Chapter 4:Red Hat Update Agent
Figure 4–3 Channels
4.3 Choosing Packages to Update
Afterclicking Next on the WelcomeScreen,the dialog box in Figure 4–4, Retrieve Update Information
will appear. This means that a connection to Red Hat Network is being established and that your
customized list of updates is being retreived. This might take some time, depending on the speed of
your connection and the number of packages you have installed.
Figure 4–4 Retrieve Update Information
While you see this dialog box, Red Hat Update Agent uses your unique Digital Certificate
(/etc/sysconfig/rhn/systemid) to determine if there are any updated packages available
Page 37

Section 4.3:Choosing Packages to Update 37
for your system. If there are no updated packages available for your system, the dialog box in Figure
4–5, No new packages needed appears. Click
Ok to exit Red Hat Update Agent.
Figure 4–5 No new packages needed
If your system is not up-to-date, your customized list of available updated packages is displayed as
shown in Figure 4–6, List of Available Updates.
Figure 4–6 List of Available Updates
By default, no packages are selected for download. If you highlight each package, a brief package
description is displayed in the
Package Information section at the bottom of the screen. To select the
package for download (and installation if you chose that option), click the checkbox. You can select
all the packages listed by clicking the button next to
Select all packages.
Page 38

38 Chapter 4:Red Hat Update Agent
If you want to view the advisory for the RPM Update, click the View Advisory button. This will
display what type of Errata Alert it is and what problems it addresses as shown in Figure 4–7, View
Advisory. Click
Next when you are finished selecting packages.
Figure 4–7 View Advisory
After choosing which packages to update, the Red Hat Update Agent tests for RPM dependencies
and prompt you if you have chosen to omit packages that are required for software updates that you
did choose. The dialog box in Figure 4–8, Testing Packages is shown while it is testing. This process
might take some time depending upon how many packages are are updating.
Figure 4–8 Testing Packages
Page 39

Section 4.4:Installing Updated Packages 39
Red Hat Update Agent shows the progress of each package retrieval as shown in Figure 4–9, Re-
trievalFinished. When they haveallbeenretrieved,themessage
of the screen. Click Next to continue. If you did not chose to install the packages automatically, skip
the next section and go to Section 4.5, Update Agent Finished.
Allfinished is displayed at the bottom
Figure 4–9 Retrieval Finished
4.4 Installing Updated Packages
After downloading the packages through the Red Hat Update Agent, they must be installed. If you
chose not to have the packages installed automatically, skip to Section 4.7, Manual Package Installa-
tion for further instructions. If you chose to have all the packages installed automatically (see Chapter
Red Hat Update Agent Configuration Tool
3,
of installing each package, as well as the total progress, is displayed. When the packages have been
installed, as seen in Figure 4–10, Installation Finished, click
), the selected packages are installed. The progress
Next to continue.
Page 40

40 Chapter 4:Red Hat Update Agent
Figure 4–10 Installation Finished
4.5 Update Agent Finished
When the Red Hat Update Agent has finished downloading the desired packages (and installing
them if you chose the install option), you will see the screen in Figure 4–11, Update Agent Finished.
Finish to exit the Red Hat Update Agent.
Click
Page 41

Section 4.6:Command Line Version of Red Hat Update Agent 41
Figure 4–11 Update Agent Finished
4.6 Command Line Version of Red Hat Update Agent
If you are not running X, you can still run the Red Hat Update Agent from a virtual console or
remote terminal. If you are running X but want to use the command line version, you can force it not
to display the graphical interface with the following command:
up2date --nox
The command line version of the Red Hat Update Agent accepts the following arguments:
Page 42
42 Chapter 4:Red Hat Update Agent
Table 4–2 Update Agent Command Line Arguments
Argument Description
--configure
Configure Red Hat Update Agent options. This is equivalent
to running the Red Hat Update Agent Configuration Tool
(up2date-config). To run the command line version of
up2date-config, use this option in conjunction with the
--nox option: up2date --nox --configure. Refer to
Section 3.5, Command Line Version of
Configuration Tool
for details.
Red Hat Update Agent
-d, --download Download packages only, do not install them. This argument
will override the configuraton option
after retrieval.
Do not install packages
-f, --force Force package installation. This option overrides the file,
package, and configuration skip lists.
-i, --install Install packages after they are downloaded. This argument will
override the configuraton option
retrieval.
Do not install packages after
-l, --list Display the list of updated packages that are available for the
system.
--showall Show a list of all packages available for your release of Red Hat
Linux, including those not currently installed.
-k, --packagedir=STRING Specify a colon separated path of directories to look for packages
before trying to download them.
--nosig Do not use GPG to check package signatures. This option will
override the saved configuration option.
-p, --packages Update the packages associated with your System Profile on
Red Hat Network. Use this option if you install RPM packages
without using the Red Hat Update Agent.
--whatprovides=<deps> Sends a comma separated list of dependencies to the RHN servers
and returns a list of packages that satisfies the dependencies.
--solvesdeps=<deps> Performs the same action as --whatprovides in addition to
downloading the packages that are needed to resolve the
dependencies.
Page 43

Section 4.6:Command Line Version of Red Hat Update Agent 43
Argument Description
--tmpdir=directory Override the configured package directory. The default location
is /var/spool/up2date. This option is useful if you do not
have enough space in the configured location.
-u, --update Update the system. All package updates for your system will be
downloaded based on your configured preferences (and installed
if you chose that option).
--nox
Force the program to run in command line mode. Do not display
the graphical interface.
-h, --help Display help on command line arguments.
-v, --verbose
Display more information about what actions Red Hat Update
Agent is performing.
--justdb Only add packages to the database and do not install them.
--dbpath Specify a path where an alternate RPM database to use is found.
--version
Display which version of Red Hat Update Agent you are
running.
-?, --usage Briefly describe the options for up2date.
packagename Specify a package name to download (and install if you chose
that option). Only specify the package name. Do not include
the version or release numbers. For example, the command
up2date python downloads (and optionally installs) the
python package if there is a newer version available and all of its
dependencies. If the package specified is not already installed,
it will download it and all of its dependencies (and optionally
install it) even if it is not already installed.
The command line version of the Red Hat Update Agent allows you to perform advanced functions
or to perform actions with little or no interaction. For example, the following command updates your
system with no interaction. It will download the newer packages and install them if you configured it
to install them automatically.
up2date -u
Page 44

44 Chapter 4:Red Hat Update Agent
4.6.1 Installing the Red Hat GPG key
The first time you run the graphical version of Red Hat Update Agent, it prompts you to install
the Red Hat GPG key. This key is required to authenticate the packages downloaded from Red Hat
Network. If you run the command line version the first time you start Red Hat Update Agent, you
need to install the Red Hat GPGkeymanually. Ifyou do not have it installed, you willsee the following
message:
Your GPG keyring does not contain the Red Hat, Inc. public key.
Without it, you will be unable to verify that packages Update Agent downloads
are securely signed by Red Hat.
Your Update Agent options specify that you want to use GPG.
To install the key, run the following as root:
/usr/bin/gpg --import /usr/share/rhn/RPM-GPG-KEY
To install the Red Hat GPG key, use the command it displays: /usr/bin/gpg --import
/usr/share/rhn/RPM-GPG-KEY, or use the following steps:
Note
GPG keys must be installed for each user. To install the key to use with Red
Hat Network, import the key while logged in as root.
1. Cut and paste the following into a file and save it as redhat2.asc or download it from
http://www.redhat.com/about/contact/.
Type bits/keyID Date User ID
pub 1024D/DB42A60E 1999-09-23 Red Hat Software, Inc. (security@redhat.com)
sub 2048g/961630A2 1999-09-23
-----BEGIN PGP PUBLIC KEY BLOCK----Version: GnuPG v1.0.0 (GNU/Linux)
Comment: For info see http://www.gnupg.org
mQGiBDfqVDgRBADBKr3Bl6PO8BQ0H8sJoD6p9U7Yyl7pjtZqioviPwXP+DCWd4u8
HQzcxAZ57m8ssA1LK1Fx93coJhDzM130+p5BG9mYSWShLabR3N1KXdXQYYcowTOM
GxdwYRGr1Spw8QydLhjVfU1VSl4xt6bupPbWJbyjkg5Z3P7BlUOUJmrx3wCgobNV
EDGaWYJcch5z5B1of/41G8kEAKii6q7Gu/vhXXnLS6m15oNnPVybyngiw/23dKjS
ZVG7rKANEK2mxg1VB+vc/uUc4k49UxJJfCZg1gu1sPFV3GSa+Y/7jsiLktQvCiLP
lncQt1dV+ENmHR5BdIDPWDzKBVbgWnSDnqQ6KrZ7T6AlZ74VMpjGxxkWU6vV2xsW
Page 45

Section 4.7:Manual Package Installation 45
XCLPA/9P/vtImA8CZN3jxGgtK5GGtDNJ/cMhhuv5tnfwFg4b/VGo2Jr8mhLUqoIb
E6zeGAmZbUpdckDco8D5fiFmqTf5+++pCEpJLJkkzel/32N2w4qzPrcRMCiBURES
PjCLd4Y5rPoU8E4kOHc/4BuHN903tiCsCPloCrWsQZ7UdxfQ5LQiUmVkIEhhdCwg
SW5jIDxzZWN1cml0eUByZWRoYXQuY29tPohVBBMRAgAVBQI36lQ4AwsKAwMVAwID
FgIBAheAAAoJECGRgM3bQqYOsBQAnRVtg7B25Hm11PHcpa8FpeddKiq2AJ9aO8sB
XmLDmPOEFI75mpTrKYHF6rkCDQQ36lRyEAgAokgI2xJ+3bZsk8jRA8ORIX8DH05U
lMH27qFYzLbT6npXwXYIOtVn0K2/iMDj+oEB1Aa2au4OnddYaLWp06v3d+XyS0t+
5ab2ZfIQzdh7wCwxqRkzR+/H5TLYbMG+hvtTdylfqIX0WEfoOXMtWEGSVwyUsnM3
Jy3LOi48rQQSCKtCAUdV20FoIGWhwnb/gHU1BnmES6UdQujFBE6EANqPhp0coYoI
hHJ2oIO8ujQItvvNaU88j/s/izQv5e7MXOgVSjKe/WX3s2JtB/tW7utpy12wh1J+
JsFdbLV/t8CozUTpJgx5mVA3RKlxjTA+On+1IEUWioB+iVfT7Ov/0kcAzwADBQf9
E4SKCWRand8K0XloMYgmipxMhJNnWDMLkokvbMNTUoNpSfRoQJ9EheXDxwMpTPwK
ti/PYrrL2J11P2ed0x7zm8v3gLrY0cue1iSba+8glY+p31ZPOr5ogaJw7ZARgoS8
BwjyRymXQp+8Dete0TELKOL2/itDOPGHW07SsVWOR6cmX4VlRRcWB5KejaNvdrE5
4XFtOd04NMgWI63uqZc4zkRa+kwEZtmbz3tHSdRCCE+Y7YVP6IUf/w6YPQFQriWY
FiA6fD10eB+BlIUqIw80VgjsBKmCwvKkn4jg8kibXgj4/TzQSx77uYokw1EqQ2wk
OZoaEtcubsNMquuLCMWijYhGBBgRAgAGBQI36lRyAAoJECGRgM3bQqYOhyYAnj7h
VDY/FJAGqmtZpwVp9IlitW5tAJ4xQApr/jNFZCTksnI+4O1765F7tA==
=3AHZ
-----END PGP PUBLIC KEY BLOCK-----
2. At the shell prompt, import the key with the following command:
gpg --import redhat2.asc
The resulting message tells you that the key was processed. To check that the key was added, type
gpg --list-keys. You will see the key you just downloaded from Red Hat, as well as your
own keys.
4.7 Manual Package Installation
Ifyou chose to download the software updates withtheRed Hat UpdateAgent, overtheWeb through
Software Manager, or have RPM Updates delivered to your system automatically (but not have them
automatically installed), you must install them manually using the rpm utility.
To install them, change to the directory that contains the downloaded packages. The default directory
is /var/spool/up2date. Then, type the command rpm -Uvh *.rpm. Whenthe packages are
finished installing, you can delete them if you wish. You do not need them anymore.
After installing the packages, you must update your System Profile so that you are not prompted to
download them again. Refer to Section 4.8, Synchronizing Your System Profile for details.
Page 46

46 Chapter 4:Red Hat Update Agent
4.8 Synchronizing Your System Profile
If you configured the Red Hat Update Agent to install the latest packages automatically, then your
System Profile stored by Red Hat Network will be updated automatically also. However, if you only
download the latest RPM packages using the Red Hat Update Agent or through the Web interface
and upgrade or install the packages yourself, your System Profile will not be updated automatically.
If you remove packages, you need to update your RPM package list in your System Profile.
To synchronize the RPM package list on your local system and on Red Hat Network run the command
up2date -p
After running this command, your System Profile on Red Hat Network will reflect the latest software
versions installed on your system.
4.9 Log File
The Red Hat Update Agent keeps a log of all the actions that it peforms on your system in the
file /var/log/up2date. It uses the standard rotating log method. Thus, older logs are in
/var/log/up2date.1, /var/log/up2date.2, and /var/log/up2date.3. The log
files store actions performed by the Red Hat Update Agent such as when your RPM database is
opened, when it connects to Red Hat Network to retreive information from your System Profile,
which packages are downloaded, which packages are installed using the Red Hat Update Agent,
and which packages are deleted from your system after installation. If you choose to install and
delete packages yourself, it will not be logged in this file. You will have to keep your own log of
actions not performed with the Red Hat Update Agent.
Page 47

Section 5.1:Logging into Software Manager 47
5 Software Manager
SoftwareManageralsorefers to the Webinterface to RedHatNetwork. You can use SoftwareManager
to manage multiple Red Hat Linux systems simultaneously including viewing Errata Alerts, applying
Errata Updates, and installing packages.
Before you can use Red Hat Network, you must register each system that you want to benefit from its
services. The only information required is a unique username and password combination and a valid
email address. Refer to Chapter 2,
Your system must be subscribed to Software Manager to fully utilize the Software Manager interface.
If a system is not subscribed (entitled), it will appear in the list of systems but will not be available for
RPM Updates through Software Manager.
Red Hat Network Registration Client
5.1 Logging into Software Manager
In a Web browser, go to http://rhn.redhat.com. The page shown in Figure 5–1, Logging into Red Hat
Network will be displayed.
If you have not registered a system yet or do not have a redhat.com account, create a new account by
clicking
new user account, you must register your system before using Software Manager. Refer to Chapter 2,
Red Hat Network Registration Client
After registering your system with Red Hat Network through the Red Hat Network Registration
Client, use the same username and password combination to log into Software Manager. Type them
in the provided text entry boxes, and click the
Create Account under the Your RHN category on the left navigation bar. After creating a
for step-by-step instructions.
Login button.
for more information.
Note
If you have an SSL-enabled Web browser, it is recommended that you use
the secure version of Software Manager available at https://rhn.redhat.com.
Information transferred with the secure version is encrypted.
Page 48

48 Chapter 5:Software Manager
Figure 5–1 Logging into Red Hat Network
5.2 Introduction to the Web Interface
The left navigation bar is divided into categories and pages within the categories.
A user with entitled systems has permission to use the following categories and pages. Each will be
explained in more detail throughout this manual.
Your RHN — Displays a quick overviewofyour account. It notifies you if systems need attention,
•
provides a quick link to go directly to them, and displays the most recent Errata Alerts for your
account.
Your Account — Update your personal profile and addresses. Indicate if you wish to receive
–
email notifications about Errata Alerts for your systems.
Entitlements — Select systems that you want to be entitled to use Software Manager. Pur-
–
chase additional Software Manager subscriptions.
The New RHN — Explains the differences between the previous Software Manager interface
–
and the current interface.
Page 49

Section 5.2:Introduction to the Web Interface 49
• Systems — Manage your systems here.
System List
–
— Viewa list of all your systems along with how many Errata Alerts each system
has, which channels the systems are subscribed to, and which systems are entitled.
System Search — Quickly search all of your systems by specific criteria.
–
System Preferences — Change the preferences for one or more selected systems.
–
Channels and Packages
•
– System List — Viewa list of all your systems along with how many Errata Alerts each system
has, which channels the systems are subscribed to, and which systems are entitled.
Channel List — View a list of all channels available through Red Hat Network.
–
Errata
•
– All Errata — List of all released Errata Alerts.
Applicable Errata — List of all applicable Errata Alerts for all of your systems.
–
–
Errata Search — Search Errata Alerts based on specific criteria.
Scheduled Actions
•
– Pending Actions — List of scheduled actions that have not been completed.
–
Completed Actions — List of scheduled actions that have been completed. Completed ac-
tions can be archived at any time.
Archived Actions — List of completed actions that have been selected to archive.
–
Help Desk
•
– Terms and Conditions — License Agreement and Limited Product Warranty.
FAQ — List of Frequently Asked Questions.
–
Contact Customer Support — Form to send an email to Red Hat Customer Service for sup-
–
port.
RHN and Red Hat Linux 6.2 — Help for using RHN on Red Hat Linux 6.2.
–
Support Forums — Link to Red Hat Developer Network Forums.
–
Page 50

50 Chapter 5:Software Manager
– RHN User Reference — Link to RHN User Reference Guide that provides step-by-step in-
structions for using RHN.
Security and Privacy — Detailed information about how Red Hat protects the information about
•
your systems and the personal information that you provide.
Current Selections
•
Refer to Section 5.2.2, Selection List for details.
Recent Wizards — List of recently selected wizards.
•
— List of currently selected items on which you want to perform an action.
5.2.1 Errata Alerts
Throughout Red Hat Network you will see three Errata Alert icons. represents a Security Alert.
represents a Bug Fix Alert. represents an Enhancement Alert.
Clickon the Errata synopsis to view details about the Errata, or click on the number of systems affected
to view a list of systems affected by the Errata Alert.
5.2.2 Selection List
Before performing actions such as applying errata updates, you must select the packages and systems
you wish to modify. Pages including System List and System Search have a column of checkboxes under the
Current Selections
The
tions
)helps you keep track of your current selections. Click the name of the category(Errata, Systems,
etc.) to view the selected items in a specific category.
Select column. Click the checkbox beside the item that you want to select, and click
to add the selected items to the Current Selections list.
box below the left navigation bar (as shown in Figure 5–2, Current Selec-
Figure 5–2 Current Selections
To clear all items in a selection category, click clear selection under the category name.
To clear all items in all categories, click
To remove individual items from a selection list, follow these steps:
clear all.
Page 51

Section 5.3:Your RHN 51
1. Click the category name in the Current Selections box.
2. Unselect the items from the list by clicking the checkbox under the
Select column.
3. Click
After clicking
rent Selections
box.
.
, the number of selections in the category will change in the
Cur-
5.3 Your RHN
After logging into the Web interface of Red Hat Network, the first page you see is the main page,
Your Red Hat Network page. This page displays important information about your systems
or the
including Recent Errata Alerts for your systems under the title
of applicable Errata Alerts for a system, click View All Applicable Errata in the bottom right-hand
corner.
Tip
If you are newto the SoftwareManager interface, it is recommended that you
read Section 5.2, Introduction to the Web Interface to become familar with
the layout and symbols used through the interface.
Recent Errata. To view a complete list
Page 52

52 Chapter 5:Software Manager
Figure 5–3 Your Red Hat Network
The first line of the YourRedHat Network page showshowmany systems need attention and provides
a link to quickly view those systems. Clicking the
here link displays the System List page that lists
the systems that need attention. Refer to Section 5.4.1, System List for information on using this page.
Statistics section, the number of total systems refers to the number of total systems that you
In the
have registered for your account.
You can return to this page by click
Your RHN on the left navigation bar.
5.3.1 Your Account
The Your Account page under the YourRHN categoryallowsyou to modify your personal information
as well as set some RHN preferences. Tomodify any information on the
tab, change the information and click the Update button on the page.
If you want to change your Red Hat Network password (the one used to log into SoftwareManager and
redhat.com) click the
Details tab on the
Your Account page and replace the asterisks in the Password
and Password Confirmation text fields with your new password. You will not see your password as
you type it for security reasons. Click
Update to change your password.
Details
tab or the Addresses
Page 53

Section 5.4:Systems 53
The email address on the Details tab is the one Red Hat Network sends email notification to if you
have selected to receive Errata Alert email for your systems under the
your preferred email address, replace in on the
Preferences tab allows you to configure two Red Hat Network options:
The
• Email notifications — Determine whether you want to receive email everytime an Errata Alert is
applicable to one or more systems in your RHN account.
• Don’t clear selections — Determine whether you want to remove selections the
tions
list after an action has been completed on the selection. For example, if you select five
packages and apply Errata Updates to them, the five packages will be removed from the selection
list after the action is confirmed and is added to the scheduled actions list. If you select
selection set when completing an action in a wizard
the selection list until you remove them.
Details page and click
, the packages would not be removed from
Preferences tab. To change
Update.
Current Selec-
Don’t clear
5.3.2 Entitlements
To use all of the features in Software Manager, your systems must be entitled — they must be subscribed to the Software Manager subscription service. Every user receives one free entitlement slot.
Entitlement Manager page displays the number of total, used, and available entitlement slots for
The
your account. To buy more entitlement slots, enter the number to purchase and click the
button.
This page also allows you to change the entitlement of a system. The systems that are currently entitled
have a check under the
a system, uncheck its entitlement box. Click the
Entitled column. To entitle a system, check its entitlement box. To unentitle
Update Entitlements to apply the changes.
Buy Now!
5.3.3 The New RHN
The New RHN page explains the differences between the previous Software Manager interface and
the current interface.
5.4 Systems
If you click the Systems link on the left navigation bar, the Systems Overview page appears. The
pages in the System category allow you to select systems so that you can peform actions on them. It
also allows you to set system preferences.
After selecting systems (adding them to the current selections list), you have the following options:
• Apply Errata Updates (Refer to Section 5.6.4, Apply Errata Updates for instructions.)
• Install Packages (Refer to Section 5.5.4, Package Install for instructions.)
Page 54
54 Chapter 5:Software Manager
5.4.1 System List
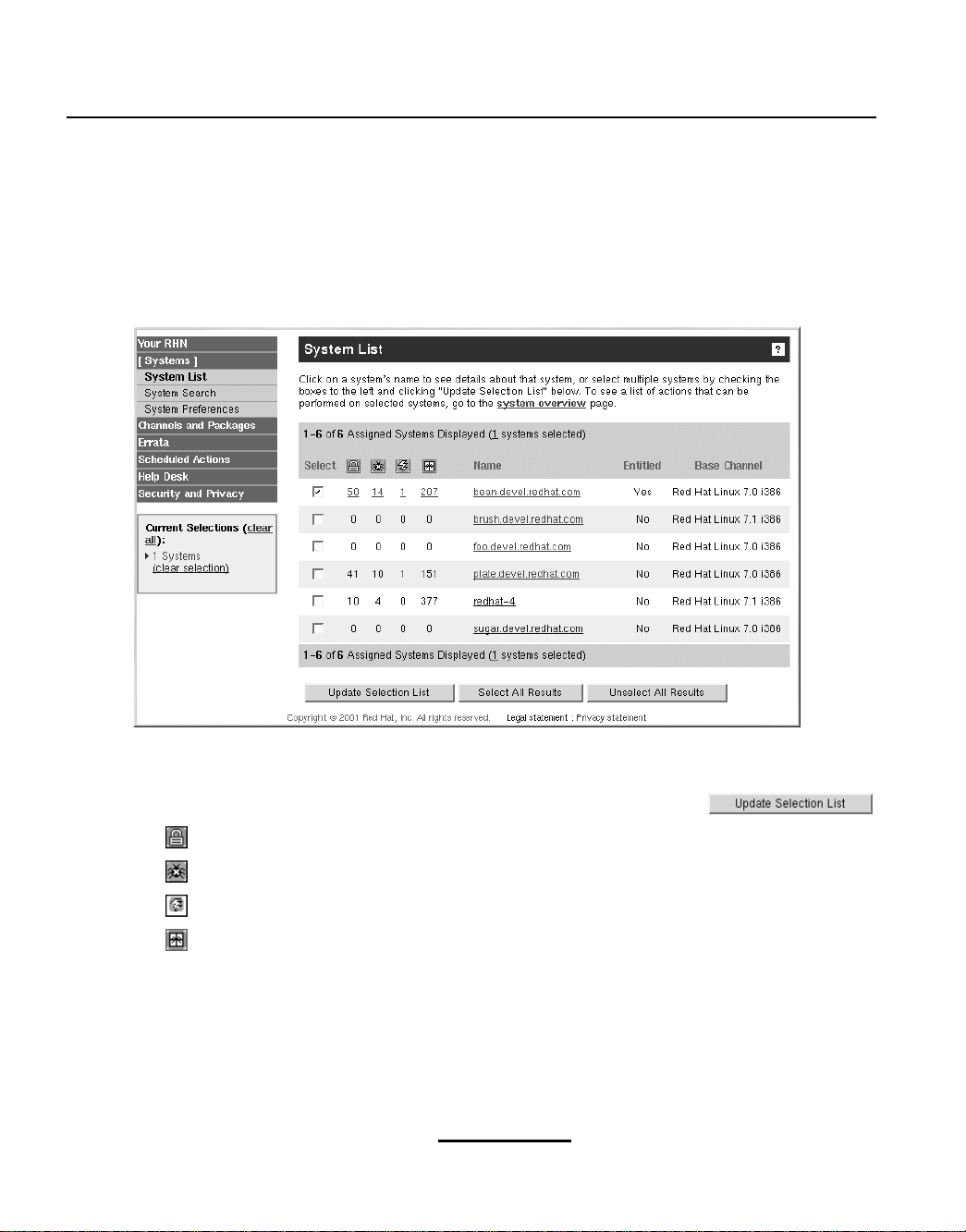
As shown in Figure 5–4, Systems List, the System List page displays a list of all your registered
systems.
Figure 5–4 Systems List
The System List contains several columns for each registered system:
Select — Toselect systems so that you can perform actions such as package installation on them,
•
check the
•
•
•
•
well as newer packages that are not from Errata Alerts. For example, if a system is subscribed
to the Red Hat Linux 7.1 i386 channel that contains version 2.5.4 of a package because that is
the version that shipped with Red Hat Linux 7.1, but the system has version 2.5.2 of the package
installed, the newer version of the package will be in the list of updated packages for the system.
Select box beside each system that you want to select and click
— Number of Security Alerts for the system.
— Number of Bug Fix Alerts for the system.
— Number of Enhancement Alerts for the system.
— Total number of package updates for the system. Includes packages from Errata Alerts as
.
Page 55

Section 5.4:Systems 55
• Name — The name of the system as configured when registering the system. The default name
is the hostname of the system. Clicking on the name of a system takes you to the System Details
page for the system. Refer to Section 5.4.4, System Details for more information.
Entitled —If
•
Base Channel — The base channel for the system. To view all the channels for a system, go to
•
its System Detail page by clicking on the name of the system in the
Yes, the system is entitled (subscribed to the Software Manager service level).
System List.
5.4.2 System Search
The results of the last search are on the bottom of the page. You can create a new result set, choose to
union with the previous result set, or intersect with the previous result set.
System Search page allows you to search through your systems according to specific criteria.
The
Select the criteria to search by and click Submit Query. The results appear at the bottom of the page.
For details about the resulting system list, refer to Section 5.4.1, System List.
5.4.3 System Preferences
From the System Preferences page, you can select three configuration preferences:
Receive Notifications of Updates
•
Errata Alerts are issued for any of your registered systems.
Automatic Download of New Packages — If you select this, packages will be automatically
•
downloaded to your systems when Errata Alerts are issued for them. The download is peformed
the next time the RHN Daemon connects to RHN and asks if any actions are required for the system. The packages are downloaded into the directory /var/spool/up2date by default. Run
up2date-config to specify a different directory. You must have the RHN Daemon enabled on
your systems. Refer to Chapter 6, Red Hat Network Daemon for more details.
— If you select this, you will receive email notifications when
Automatic Installation of New Packages — If you select this, packages will be automatically
•
downloaded and installed on your systems when Errata Alerts are issued for them. These actions
are performed by the RHN Daemon. You must have the RHN Daemon enabled on your systems.
Refer to Chapter 6, Red Hat Network Daemon for more details.
Before you can configure the preferences for one or more systems using the
ard
, you must select one or more systems and add them to the current selections list. Refer to Section
System Preference Wiz-
5.2.2, Selection List for details. After the systems have been added to the selection list, go to the
tab of the System Preference Wizard, choose your preferences, and click
Confirm. The preferences
are applied to all selected systems.
Do It!
Page 56

56 Chapter 5:Software Manager
5.4.4 System Details
If you click on the name of a system on any page, it will display the System Details page for the system.
The System Details page is further divided into tabbed pages. The first tabbed page you see is the
Details page. Notice the button Update this System. If you click it, you can apply all relevant Errata
Updates to the individual system. Be sure you review the Errata List for the system before performing
this action. After clicking the button, you will be asked to confirm the update. Click the
Update For This System
to confirm. After confirming, the action is added to the Pending Actions
list under Actions => Pending Actions from the left navigation bar.
The packages will be updated by the RHN Daemon. You must have the RHN Daemon enabled on
your systems. Refer to Chapter 6, Red Hat Network Daemon for more details.
The following tabbed pages are available:
Details — Includes the system’s unique System ID, entitlement status, profile name, description,
•
OS Release, channels, automation options, and notification options. To change the system’s profile name, description, automation options, or notification options make the change and click the
Modify System Profile button. To delete a system from your account, click the Delete System
Profile
•
button.
Errata — List of Errata Alerts applicable to the system. You can select one more Errata to add
to your selection list from here. Clicking on the Synposis displays the Errata Details page for the
Errata Alert. Refer to Section 5.6.5, Errata Details for more information about the Errata Details
page. This tab only appears for entitled systems.
Confirm
Installed Packages— Listof installed packages from the system’s Sofware System Profile. Click
•
on a package name to view its Package Details page. (Refer to Section 5.5.3, Package Details.) If
the package list looks incomplete or outdated, click the
Schedule Package List Refresh button to
schedule a Package List Profile Update for your system. The nexttime the RHN Daemon connects
to RHN, it will update your System Profile with the latest list of installed packages. To look for
particular packages by name, use the
Outdated Packages — List of packages that have a new version available based on the package
•
filter by name field.
versions in the channel for the system. Click on the newer package name to view the Package
Details page for it. Click on the Related Errata number to view the Errata Details page for the
Errata Alert if an Errata Alert is associated with the newer package. This tab is only displayed
for entitled systems. To add one or more packages to your selection list, select the package(s)
and click
viewing, select the package(s) and click the
. To install one or more packages on the system you are currently
Install Selected Packages on This System button.
To download one or more packages immediately, select the package(s) and click the Download
Selected Packages
button. Refer to Section 5.5.5, Package Download for details.
Page 57

Section 5.5:Channels and Packages 57
• Hardware— During registration, if you selected to include the Hardware Profile for this machine,
this tabbed page displays the Hardware Profile. If the hardware profile looks incomplete or outdated, click the
for your system. The next time the RHN Daemon connects to RHN, it will update your System
Profile with the latest list of hardware.
Notes — Create notes about the system. Click Add a new note, type a subject and the note, and
•
click
Update Note. To delete a note, click on its title for the list of notes, check Delete this note,
and click Update Note.
History — A history of events for your system that is automatically generated by Software Man-
•
ager.
Schedule Hardware List Refresh button to schedule a Hardware Profile Update
5.5 Channels and Packages
A channel is a list of Red Hat Linux packages. Channels are used to choose packages to be installed
in the Channels and Packages section of Software Manager.
There are two types of channels: base channels and child channels. A basechannel consists of a list of
packages based on a specific architecture and Red Hat Linux release. For example, all the packages in
Red Hat Linux 7.1 for the x86 architecture is a base channel. The list of packages in Red Hat Linux 7.1
for the Itanium architecture is a different base channel. A child channel is a channel associated with
a base channel but contains extra packages. For example, an organization can create a child channel
that is associated with the Red Hat Linux 7.1 for the x86 architecture and that contains extra packages
needed only for the organization, such as a custom engineering application.
5.5.1 Channel List
The Channel List page provides a list of all base channels and their child channels. To view a list
of individual packages in a channel, click on the name of the channel (base or child). You will be
presented with a list of packages in the channel in groups of 20. Click
packages. Click
If you are looking for a specific package or a subset of packages, you can use the package filter on the
top of the list. Enter a substring to search for. It will search all the packages in the list for the substring
at the beginning, in the middle, or at the end of the package name. The filter is case-insensitive. For
example,typing ks in the filter might return all the ksconfig, krb5-workstation, and links.
You can also use this list to select packages and add them to your current selections list. To do so, click
the checkbox beside the package name and under the
To downloadpackages, select the packages and click the
to Section 5.5.5, Package Download for details.
Prev to see the previous group of packages.
Select column. Click
Download Selected Packagesbutton. Refer
Next to see the next group of
.
Page 58

58 Chapter 5:Software Manager
Clicking on a package name displays a set of tabbed pages with information about the package. This
information includes which architectures it runs on, the package size, build date, package dependencies, the change log, list of files in the package, and which systems have the package installed. Refer
to Section 5.5.3, Package Details for more information.
5.5.2 Channel Subscribe and Unsubscribe
Each RHN client system must be subscribed to a base channel and can only be subscribed to one
base channel. This base channel is selected automatically during registration from the Red Hat Linux
release and system architecture selected. Each RHN client system can be subscribed to zero or more
child channels.
To view the list of channels to which each system is subscribed, click
the left navigation bar. From the
System List, click on the name of the system to display the System
Systems => System List from
Details page. On the System Details page, there is a check beside the channels to which the system
is subscribed. To subscribe the system to additional child channels, check the box beside it and click
the
Modify System Profile button at the bottom of the page. To unsubscribe the system from a child
channel, uncheck the box beside the channel name and click
Modify System Profile.
5.5.3 Package Details
If you click on the name of an RPM package or the name of the Newer Package in the
Packages
section of the System Details page, the Package Details page for the package will appear.
This page contains the following tabbed pages:
Details— Details about the package including the package description, packagesize, and package
•
version (This information is similar to issuing the command rpm -qi
Dependencies — Lists the package dependencies, what the package provides, the packages it
•
packagename
obseletes, and the packages with which it conflicts.
Change Log — The Change Log for the package (This information is similar to issuing the com-
•
mand rpm -q --changelog
File List — List of files installed from the package.
•
Installed Systems — List of systems with this package installed.
•
Target Systems — Go here to install packages on entitled systems. Refer to Section 5.5.4, Pack-
•
packagename
).
age Install for instructions.
Outdated
).
5.5.4 Package Install
To install individual packages on one or more entitled systems, follow these steps:
1. Select
Channels and Packages => Channel List from the left navigation bar.
Page 59

Section 5.5:Channels and Packages 59
2. Click on the name of a channel to view its package list.
3. Click on the name of the package that you want to install.
4. Click on the
Target Systems tab.
5. Select the entitled systems that you want to install the package on.
6. Click the
Install Packages on Selected Systems button.
7. Confirm the action.
5.5.5 Package Download
If you do not want to schedule a package installation, you can download the packages immediately. If
you download the packages, you must install them manually.
There are three methods for downloading RPM packages:
1. From the
Package
the
2. From the
want to download. From the list of packages within the channel, use the
packages to download. Click the
3. Add packages to your selection list as described in Section 5.2.2, Selection List. After adding
all the packages that you want to download, click the
Selections
System Details page, click on the Outdated Packages tab. Under the Select Newer
column, click the checkboxes to select the packages that you want to download. Click
Download Selected Packages button on the bottom of the page.
Channel List page, click on the name of the channel that contains the packages that you
Select column to select
Download Selected Packages button on the bottom of the page.
Installable Packages link in the
box.
Current
After choosing to download the packages using one of these methods, you will be presented with a
confirmation page as shown in Figure 5–5, Package Download. If you selected a package that is avail-
able for more than one architecture, you need to select an architecture for the package. For example,
if you want to download the kernel package you will need to choose between
i386, i586, and i686.
Click the Download Selected Packages Now! button to start downloading the packages.
The packages are downloaded into a directory called rhn-packages beneath the current directory
selected after clicking the button. For example, if you want to save the packages in the directory,
/downloads/rhn-packages, select the directory /downloads when prompted. The directory
rhn-packages will be created for you if it does not already exist.
Page 60

60 Chapter 5:Software Manager
Figure 5–5 Package Download
Even if you selected to download more than one package, you will only download one file. This one
TAR file contains all the RPM packages you selected. To extract the packages from the TARfile, open
a shell prompt (such as an XTerm or GNOME terminal), change to the rhn-packages directory,
and issue the command:
tar -xvf rhn-packages.tar
The next step is to install the packages manually. Refer to Section 4.7, Manual Package Installation
for details.
5.6 Errata
Red Hat releases Errata Alerts in three categories: Security Alerts, Bug Fix Alerts, and Enhancement
Alerts. Each Errata Alert is comprised of a summary of the problem and the solution, including the
RPM packages required to fix the problem. The
view all released Errata Alerts, only Errata Alerts applicable to your systems, search Errata Alerts,
and apply Errata Updates to one or more of your systems.
Errata category of Software Manager allows you to
Page 61

Section 5.6:Errata 61
Tip
If you want to receiveanemail when Errata Alerts are issued for your system,
Systems => System Preferences and select Receive Notifications
go to
of Updates
.
5.6.1 All Errata
The All Errata page displays a list of all Errata Alerts released.
If you click on the synopsis of an Errata Alert, the Errata Details page for the Errata Alert will appear.
Refer to Section 5.6.5, Errata Details for more information.
To add Errata to your selection list, check the
.
Select box beside the Errata, and click
5.6.2 Applicable Errata
The Applicable Errata page displays a customized list of Errata Alerts that apply to your registered
systems.
If you click on the synopsis of an Errata Alert, the Errata Details page for the Errata Alert will appear.
Refer to Section 5.6.5, Errata Details for more information.
To add Errata to your selection list, check the
.
Select box beside the Errata, and click
5.6.3 Errata Search
The results of the last search are on the bottom of the page. You can create a new result set, choose to
union with the previous result set, or intersect with the previous result set.
Errata Search page allows you to search through your systems according to specific criteria.
The
Select the criteria to search by and click Submit Query. The results appear at the bottom of the page.
5.6.4 Apply Errata Updates
Errata Alerts include a list of updated packages that are required to apply the Errata Update. You can
use Software Manager to update these packages automatically through the RHN Daemon on the client.
No user intervention is required except selecting the Errata Alerts and systems to update. The system
must be entitled.
You can use one of these methods to apply Errata Updates:
Page 62

62 Chapter 5:Software Manager
1. To apply all applicable Errata Updates to a system, click on Systems => System List on the left
navigation bar. Click on the name of an entitled system, and click the
Update This System button
on the Details tabbed page. This action will apply all available Errata Updates on the system. To
view a list of the Errata, click the
2. To apply a specific Errata Update to one or more systems, click on
bar and use the
All Errata, Applicable Errata,orErrata Search page to find the Errata Update
that you want to apply. From the Errata List, click on the
a summary of it. Click on the
apply this update to. Click
systems, or click
Update All Affected Entitled Systems to apply the update to all the affected
Errata tab on the system details page for the system.
Errata on the left navigation
Synopsis for the Errata Alert to display
Affected Systems tab, and select the systems that you want to
Update Selected Systems
to apply the Errata Update to all selected
systems listed.
The following rules apply to Errata Updates:
1. Each package is a member of one or more channels. If a selected system is not subscribed to the
channel that the selected package is a member of, the package will not be installed on that system.
2. If a newer version of the package is already on the system, the package will not be installed on
that system.
3. If an older version of the package is installed, the package will be upgraded.
The packages will be updated by the RHN Daemon. You must have the RHN Daemon enabled on
your systems. Refer to Chapter 6,
Red Hat Network Daemon for more details.
5.6.5 Errata Details
If you click on the synopsis of an Errata Alert, the Errata Details page for the Errata Alert will appear.
This page is further divided into two tabbed pages:
Details page provides the Errata Report issued by Red Hat. It describes what channels the Errata
The
Details and Systems Affected.
Alert affects, its problem and solution, MD5 verfication for each of the packages, and the packages
required for the Errata Update. Clicking on the RPM package name displays the Package Details page
for the package. Refer to Section 5.5.3, Package Details for more information.
Systems Affected page shows a list of systems affected by the Errata Alert.
The
5.7 Scheduled Actions
An action is a scheduled RHN task that is to be performed on one or more client systems. For example,
an action can be scheduled to apply all Errata Updates to a system.
Each tabbed page on the
of actions:
Scheduled Actions page represents a type of action. There are three types
Page 63

Section 5.7:Scheduled Actions 63
• Pending Actions are actions that have not started or are in progress.
Completed Actions are actions that have been completed.
•
Archived Actions are actions that you have selected to archive.
•
In each tabbed page, each row in the list represents a single scheduled event or action that might affect
multiple systems and involve multiple packages.
The list includes six columns of information:
Select — Use the checkboxes in this column to select actions. After selecting actions, you can
•
either add them to your selection list or move them to the Archived Actions list. If you archive a
pending action, it is not cancelled, the action item just moves to the
do not see it in the
Action Type — Type of action to perform such as Errata Update or Package Install.
•
Earliest Action — The earliest day and time to perform the action.
•
Completed — Number of systems on which this action has been completed.
•
Failed
•
•
— Number of systems on which this action has been tried and failed.
In Progress — Number of systems on which this action is taking place.
Pending Actions list.
Archived Actions list so you
If you click on a link under the
Action Type column, you can view details for the action. For example,
for an Errata Update action, you can view which Errata Updates are to be applied, which systems are
currently performing the Errata Update, which systems havecompleted the action, and which systems
tried the action but failed to complete it.
Page 64

64 Chapter 5:Software Manager
Figure 5–6 Scheduled Actions
Page 65

Red Hat Network Daemon 65
6 Red Hat Network Daemon
The Red Hat Network Daemon periodically connects to the Red Hat Network to check for updates
and notifications. The default interval time is two hours (120 minutes). This can be configured in
the /etc/sysconfig/rhn/rhnsd file by specifying the time interval in minutes. If you modify
the configuration file, you must (as root) restart the daemon with the command service rhnsd
restart or /etc/rc.d/init.d/rhnsd restart.
Note
The minimum time interval allowed is one hour (60 minutes). If you set the
interval below one hour, it will default to two hours (120 minutes).
You can view the status of the rhnsd by typing the command service rhnsd status or
/etc/rc.d/init.d/rhnsd status at a shell prompt.
To disable the daemon, (as root) run the ntsysv utility and uncheck rhnsd. You can also (as root)
execute the command chkconfig rhnsd off. Using these two methods will only disable the
service the next time the system is started. To stop the service immediately, use the command ser-
vice rhnsd stop or /etc/rc.d/init.d/rhnsd stop.
The same rules you configured for the Red Hat Update Agent apply to the Red Hat Network Daemon
(see Section 3.1, Configuring the Red Hat Update Agent).
Page 66

66 Chapter 6:Red Hat Network Daemon
Page 67

Using Red Hat Network with Red Hat Linux 6.2 67
7 Using Red Hat Network with Red Hat
Linux 6.2
Red Hat Linux 6.2 shipped with a program named Red Hat Update Agent (up2date). However,
this version of Red Hat Update Agent can not be used to connect to Red Hat Network to receive
package updates. You need a new version of the Red Hat Update Agent and the Red Hat Network
Registration Client to use Red Hat Network on a Red Hat Linux 6.2 system.
To download and install these programs, use the following steps:
1. In a shell prompt, login as root and execute the command mkdir rhnpackages to create a
new directory in which to download the packages.
2. In the same shell prompt, execute the command cd rhnpackages to change to the new directory.
3. In a Web browser, download the necessary packages from http://rhn.redhat.com/help/rh62.pxt.
4. Go back to the shell prompt in the rhnpackages directory (you must still be root) and execute
the command rpm -Uvh * to upgrade the existing Red Hat Update Agent to the version that
works with Red Hat Network. The Red Hat Network Registration Client will also be installed
with this command along with other packages your system needs to run the Red Hat Network
programs.
5. After they are installed, run the Red Hat Network Registration Client (rhn_register)to
register your system. See Chapter 2,
6. Login to your account at http://rhn.redhat.com to configure your preferences and to configure
which systems you want to subscribe to Software Manager.
Red Hat Network Registration Client
for details.
Page 68

68 Chapter 7:Using Red Hat Network with Red Hat Linux 6.2
Page 69

Frequently Asked Questions 69
8 Frequently Asked Questions
The following contains answers to common questions about Red Hat Network.
Q: What is Red Hat Network?
A: Red Hat Network is a systems support and management environment for Red Hat Linux networks.
For more information, please see the Red Hat Network product information page.
Q: What is Software Manager?
A: Software Manager is the name of the first subscription service offered through Red Hat Network.
Q: What do Red Hat Network and Software Manager cost?
A: Registering with Red Hat Network is free and creating system profiles is free. Every customer
receives a free Software Manager subscription for one system. Additional subscriptions are
$19.95/month for each system.
Q: How do I purchase Software Manager subscriptions?
A: Go to http://rhn.redhat.com/purchase_info.pxt for instructions.
Q: Can I cancel my Red Hat Network Software Manager subscriptions?
A: To cancel your subscriptions, contact Customer Service at (888) RedHat1.
Q: Do I need to use Red Hat Linux to benefit from Red Hat Network?
A: Yes. Currently, you must be running Red Hat Linux 6.2 or higher to utilize Red Hat Network.
Q: How does Software Manager work?
A: Each registered system has a System Profile that contains hardware and software information about
the system. Software Manager uses this information to provide you with customized Errata Alerts
relevantto your systems. RPM package updates can be downloaded to the client system with the Red
Hat Update Agent or scheduled for installation or upgrade with Software Manager.
Q: I’m concerned about my privacy. How secure is Red Hat Network?
A: Security is a high priority for Red Hat Network. Please see the security & privacydocumentation
for more information.
Q: I can’t find the Red Hat Network Registration Client. What is it and where do I find it?
A: The Red Hat Network Registration Client steps you through the process of creating a user ac-
count if you do not already have one and registering your system by creating a System Profile. It can
be started by using one of the following methods:
Page 70

70 Chapter 8:Frequently Asked Questions
1. In GNOME desktop, go to the Main Menu Button (on the Panel) => Programs
Red Hat Network
2. In KDE desktop, go to the Main Menu Button (on the Panel) =>
Network
Red Hat => System => Red Hat
=> System =>
3. Type the command rhn_register at a shell prompt (for example an xterm or gnome-terminal)
Q: I downloaded just the RPM files and installed them myself. Can I update my System Profile to
reflect the changes?
A: Yes. Type the command up2date -p at a shell prompt. It will update your RPM package list
stored on the Red Hat Network servers. Use this command whenever you install, upgrade, or remove
packages without using the Red Hat Update Agent.
Q: I forgot my username and password. How do I access my account?
A: Go to http://rhn.redhat.com, click on the
Forgot your password? link, and complete the form.
Your password will be sent to your email address. If this does not work for you, please call our customer service desk.
Q: Will Red Hat Network update packages that were not installed with the Red Hat distribution?
A: No. Red Hat Network currently supports all RPM packages installed from the Red Hat Linux CD,
Red Hat PowerTools CD, and the Red Hat Linux Applications CD.
Q: What version of Red Hat Linux do I have to run to be able to use Red Hat Network and Software
Manager?
A: You must be running Red Hat Linux 6.2 or higher.
Q: Why is something called rhnsd running on my system and what does it do?
A: rhnsd is the Red Hat Network Daemon. Every other hour, it sends a request to Red Hat Network
asking for any notifications or updates and works in coordination with the Red Hat Network to schedule automated tasks. It only sends information to Red Hat Network requested by you. If you add a
new system through the Web, the next time the Red Hat Network Daemon probes Red Hat Network it
receivesa request to return the information you requested as part of your System Profile, such as what
package versions are installed on your system.
Q: Why does the Red Hat Update Agent no longer work?
A: The Red Hat Update Agent(up2date) requires a valid System Profile on Red Hat Network and
a Software Manager subscription to function properly. To create a System Profile, run the Red Hat
Network Registration Client (rhn_register) on the system that you wish to register with Red
Hat Network. Every user receives one free subscription to Software Manager. To purchase additional
subscriptions, go to rhn.redhat.com/purchase_info.pxt.
Page 71

Frequently Asked Questions 71
Q: Can I use Red Hat Network to upgrade my Red Hat Linux kernel?
A: Yes. You must use Red Hat Update Agent version 2.5.4 or higher. If you choose the kernel
packages and allow Red Hat Network to install them to your system, it will modify your LILO configuration file so that your system boots the new kernel the next time it is rebooted. If you just download
the RPM packages and install them yourself, you will need to modify LILO to boot the new kernel.
Q: Why does the Red Hat Update Agent return the error "No Route to Host"?
A: The system you are running it on is not connected to the Internet, or the system is attempting to
access Red Hat Network through a proxy server. Proxy server settings can be configuredin the newest
version of up2date available at http://www.redhat.com/support/errata/RHBA-2000-138.html. For
instructions on configuring the proxy server, refer to Section 3.2, General Settings.
Q: Why does the Red Hat Network Registration Client return the error "No Route to Host"?
A: The system you are running the Red Hat Network Registration Client (rhn_register)on
is not connected to the Internet, or the system is attempting to access Red Hat Network through a
proxy server. Proxy server settings can be configured in the newest version of rhn_register available
at http://www.redhat.com/support/errata/RHBA-2000-138.html. For instructions on configuring the
proxy server, refer to Section 2.1, Configuring the
Red Hat Network Registration Client
.
Page 72

72 Chapter 8:Frequently Asked Questions
Page 73

Frequently Asked Questions 73
Glossary
A
Action
A task that is scheduled by a system administrator using Red Hat Network to be performed
on one or more client systems. For example, an action can be scheduled to update the kernel
packages on all the systems within a selected group.
B
Base Channel
A base channel is a type of Channel that consists of a list of packages based on a specific architecture and Red Hat Linux release. For example, all the packages in Red Hat Linux 7.2 for the
x86 architecture is a base channel.
Bug Fix Alert
An Errata Alert that pertains to a bug fix.
Bugzilla
Bugzilla is an online application ( http://www.redhat.com/bugzilla) that allows users to communicate directly with the developers. From Bugzilla, users can submit bug reports and feature
requests for Red Hat Linux and related open source packages.
C
Channel
A channel is a list of Red Hat Linux packages. Channels are used to choose packages to be
installed from client systems. Every client system must be subscribed to one Base Channel and
can be subscribed to one or more Child Channel .
Child Channel
A child channel is a Channel associated with a Base Channel but contains extra packages.
Client System
See Registered System .
Page 74

74 Chapter 8:Frequently Asked Questions
D
Digital Certificate
Aclient component in XML format that is stored in the /etc/sysconfig/rhn/systemid
fileonregisteredsystems. Red Hat Network verifiesthis certificate to authenticate the registered
system before each connection. This certificate is issued by Red Hat and passed to the system
as part of the registration process. It includes unique information about the registered system to
avoid fraudulent use.
E
Email Notification
Similar to an Errata Alert , except the information is delivered via email. If the email notifications option is selected, notifications are sent for every Red Hat Network Errata Alert . The
email includes the type of Errata Alert, summary of the Errata, description of the Errata, and a
list of which systems are affected by the report.
Enhancement Alert
An Errata Alert that pertains to a package enhancement request.
Entitled Server
A server that is subscribed to Software Manager . Because the server is entitled, the Software
Manager interface can be used to manage its packages.
Errata
Information published by Red Hat describing security fixes, bug fixes, and package enhancements for Red Hat Linux. The information includes the topics of the Errata, Bugzilla bug IDs,
relevant releases/architectures, solutions including required RPMs, and MD5 checksums for
verification. Errata are also available at http://www.redhat.com/errata/. Each RHN Errata Alert
is based on the Red Hat Linux Errata List.
Security issues and bug fixes are submitted by Red Hat engineers as well as the Linux community through Bugzilla which generates a bug report for each issue. Red Hat engineering
evaluates the reports, resolves the bug, and generates new RPM packages. After the Red Hat
quality assurance team tests new packages they are placed on the Red Hat Public File Server
and on the Red Hat Network Server and an Errata is generated.
Page 75

Frequently Asked Questions 75
Errata Alert
RHN Errata Alert that updated packages based on Red Hat Errata are available for one or more
systems within an organization. There are three types of Errata Alerts: Security Alerts, Bug Fix
Alerts, and Enhancement Alerts.
R
Registered System
A system that is registered with Red Hat Network. Also known as a client system.
Red Hat Network Daemon
The RHN client daemon (rhnsd) that periodically polls Red Hat Network for updates and
notifications.
Red Hat Network Registration Client
The RHN client application (rhn_register) that collects information about the client system, creates a System Profile and Digital Certificate , establishes a connection with the Red Hat
Network servers, and registers the system with Red Hat Network.
Red Hat Update Agent
The RHN client application (up2date) that allows users to retreive and install all updated
packages for the client system on which the application is run. Use the Red Hat Update Agent
Configuration Toolto configure its preferences, including whether to install the packages after
they are downloaded.
RPM
A software package manager that was developed by Red Hat. It can be used to build, install,
query, verify, update, and uninstall software packages. All software updates from RHN are
delivered in RPM format.
RPM Database
Each Red Hat Linux system has an RPM database that stores information about all the RPM
packages installed on the system. This information includes the version of the package, which
files were installed with the package, a brief description of the package, the installation date,
and more.
RPM Update
Red Hat Network option to deliver the RPM packages based on the Errata Alert list to a client
system automatically and without user intervention. If this feature is selected, packages are
delivered through the Red Hat Network Daemon running on the client system.
Page 76

76 Chapter 8:Frequently Asked Questions
S
Security Alert
An Errata Alert that pertains to system security.
Service Level
A Red Hat Network subscription service. Different service levels offer different features of
RHN. The first service level offered is Software Manager .
Software Manager
The name of the first Service Levelofferingfor Red Hat Network. Software Manager also refers
to the Web interface for RHN.
System ID
A unique string of characters and numbers that identifies a registered system. It is stored in the
system’s Digital Certificate .
System Profile
Hardware and software information about the client system. It is created during the registration
process. The software information is a list of RPM packages and their versions installed on the
client system. The System Profile is used to determine everyErrata Alert relevant to each client
system.
Page 77

Index 77
Index
B
base channel.................................. 57
C
Channel List ............................ .....57
channels....................................... 57
base................... ...................... 57
child........................................ 57
package list ........................... .....57
subscribe.............................. .....58
unsubscribe................................ 58
child channel ................................. 57
D
deleting a system............................. 56
Digital Certificate............................ 11
E
email address
change................................. .....52
entitlement.................................... 53
buying more slots ......................... 53
Entitlement Manager ....................... 53
Errata Alerts
applying.................................... 61
explanation of ............................. 50
searching................................... 61
viewing details ............................ 62
viewing list of all errata .................. 61
viewing list of applicable errata..... .....61
F
FAQs .......................................... 69
Frequently Asked Questions ................ 69
Getting started................................ 11
GNU Privacy Guard ......................... 11
H
hardware profile
Updating on server........................ 57
I
Introduction
document ....................................9
L
left navigation bar...... ...................... 48
N
Notifications
Automatic............ ...................... 10
O
overview of Web interface .................. 48
P
package list
Updating on server.................... 46, 56
packages
downloading............................... 59
filter ................................... .....57
installing................................... 58
password
change................................. .....52
proxy server
with Red Hat Network Registration
Client................................. 13
with Red Hat Update Agent......... .....27
G
Q
Page 78

78 Index
left navigation bar......................... 48
Quality Assurance .... ....................... 10
R
Red Hat Linux 6.2
Using Red Hat Network with ............ 67
Red Hat Network Daemon ................9, 65
Disable..................................... 65
Status................ ....................... 65
using to apply Errata Updates........ 56, 62
Red Hat Network Registration Client
( See Registration )
Red Hat Update Agent ....................9,33
Command Line Arguments .............. 41
Configuration....... ....................... 27
with a proxy server........................ 27
logging in.................................. 47
overview................................... 48
Scheduled Actions ........................ 62
Systems ............................... ..... 53
subscribe to channel ......................... 58
system
deleting .................................... 56
System Profile................................ 19
Updating hardware profile ............... 57
Updating package list................. 46, 56
systems
configuring preferences .................. 55
entitling ............................... ..... 53
searching................................... 55
viewing a list of ........................... 54
viewing details for ........................ 56
Registration................................... 13
as part of an organization................. 18
Configuration....... ....................... 13
Email notification......................... 16
Hardware System Profile................. 19
Password................................... 16
RPM Package List ........................ 20
U
unsubscribe to channel ...................... 58
up2date
( See Red Hat Update Agent )
user account .................................. 16
Software System Profile.................. 20
System Profile......................... 16, 19
through the Web........................... 47
User name ................................. 16
with a proxy server........................ 13
rhn_register................................... 14
( See also Registration )
rhnsd . ........................................ 65
S
Secure Sockets Layer........................ 11
Security....................................... 10
Software Manager .... ................... 10, 47
Channels and Packages................... 57
Errata....................................... 60
 Loading...
Loading...