Page 1

Configuration, Command, and
File Reference
Netscape Directory Server
Version 6.2
December 2003
Page 2

Netscape Communications Corporation ("Netscape") and its licensors retain all ownership rights to the so ftware programs offere d by Netscape (referred
to herein as "Software") and related documentation. Use of the Software and related documentation is governed by the license agreement for the
Software and applicable copyright law.
Your right to copy this documentation is limited by copyright law. Making unauthorized copies, adaptations or compilation works is prohibited and
constitutes a punishable violation of the law. Netscape may revise this documentation from time to time without notice.
THIS DOCUMENTATION IS PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND. IN NO EVENT SHALL NETSCAPE BE LIABLE FOR
INDIRECT, SPECIAL, INCIDENTAL, OR CONSE Q UE NT IAL DAMAGES OF ANY KIND ARISING FROM ANY ERROR IN THIS
DOCUMENTATION, INCLUDING WITHOUT LIMITATION ANY LOSS OR INTERRUPTION OF BUSINESS, PROFITS, USE, OR DATA.
The downloading, exporting, or reexporting of Netscape software or any underlying information or technology must be in full compliance with all
United States and other applicable laws and regulations. Any provision of Netscape software o r documentation to the U.S. governmen t is with restricted
rights as described in the license agreement for that Software.
Netscape and the Netscape N logo are registered trademarks of Netscape Communications Corporation in the United States and other countries. Other
Netscape logos, product names, and service names are also trademarks of Netscape Communications Corporation, which may be register ed in some
countries. Other product and brand names are the exclusive property of their respective owners.
The Software and documentation are copyright © 2001 Sun Microsystems, Inc. Portions copyright 1999, 2002, 2003 Netscape Communications
Corporation. All rights reserved.
================================================================================================================================
Portions of the Software copyright © 1995 PEER Networks, Inc. All rights reserved.
================================================================================================================================
The Software contains the Taligent International Classes from Taligent, Inc. and IBM Corp.
================================================================================================================================
Portions of the Software copyright ©1992-1998 Regents of the University of Michigan. All rights reserved.
================================================================================================================================
The Software contains encryption software from RSA Security Inc. Copyright © 1994 RSA Data Security, Inc. All rights reserved.
This product contains software derived from the RSA Data Security, Inc. MD5 Mes sage-Digest Algorithm.
================================================================================================================================
This product incorporates International Components for Unicode (ICU) libraries, ICU is an open source development project sponsored, su pport ed, a nd
used by IBM.
================================================================================================================================
The source code to the Standard Version of Perl can be obtained from CPAN sites, including http://www.perl.com/.
================================================================================================================================
This product incorporates compression code by the Info-ZIP group. There are no extra charges or costs due to the use of this code, and the original
compression sources are freely available from http://www.infozip.com/ on the Internet.
================================================================================================================================
This product includes software developed by the Apache Software Foundation (http://www.apache.org/).
================================================================================================================================
Portions of the Software copyright © 1989 The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms of such U.C. Regents software, with or without modification, are permitted provided that the
following conditions are met:
1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation
and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgment: This product includes software
developed by the University of California, Berkeley and its contributors.
4. Neither the name of the University nor the names of its contributors may be used to endorse or promote pro ducts derived from this software w ithout
specific prior written permission.
THIS SOFTWARE IS PRO VIDED B Y TH E REGE NTS AND CONTRI BUTOR S "AS IS" A ND AN Y EXPRE SS OR IMP LIED W ARRA NTIES , INCLU DING ,
BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL,
EXEMPLARY, OR C ONS EQUE NTIA L DA MAGE S (IN CLU DIN G, B UT N OT LIMI TED TO, P ROCU REMEN T OF SUB STITU TE GOOD S OR S ERV ICE S;
LOSS OF USE, DATA, OR PROFITS; OR BU SIN ESS INTERRUPTION) HOWEVER CAU SED AND ON ANY THEORY OF LIABILITY, WHETHER IN
CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
================================================================================================================================
Portions of the Software copyright (C) 1987, 1988 Student Information Processing Board of the Massachusetts Institute of Technology.
Permission to use, copy, modify, and distribute such M.I.T. s oftware and its documentation for any purpos e and wi thout fee is hereby granted, provided
that the above copyright notice appear in all copies and that both that copyright notice and this permission notice appear in supporting documentation,
and that the names of M.I.T. and the M.I.T. S.I.P.B. not be used in advertising or publicity pertaining to distribution of the software without specific,
written prior permission. M.I.T. and the M.I.T. S.I.P.B. make no representations about the suitability of this software for any purpose. It is provided "as
is" without express or implied warranty.
Page 3

Contents
About This Reference Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Directory Server Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Prerequisite Reading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
What Is In This Reference Guide? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20
Conventions Used In This Reference Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Related Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Chapter 1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Overview of Directory Server Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23
Directory Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Directory Server Instance File Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Migrating Directory Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24
Using Directory Server Command-Line Utilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Using Directory Server Command-Line Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25
Chapter 2 Core Server Configuration Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Server Configuration - Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
LDIF Configuration Files - Location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Schema Configuration Files - Location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
How the Server Configuration is Organized . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Configuration Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Configuration of Plug-in Functionality . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30
Configuration of Databases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Configuration of Indexes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31
Migration of Pre-Directory Server 6.x Configuration Files to LDIF Format . . . . . . . . . . . . . . . . . . . 32
Accessing and Modifying Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Access Control For Configuration Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Changing Configuration Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Modifying Configuration Entries Using LDAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34
Restrictions to Modifying Configuration Entries and Attributes . . . . . . . . . . . . . . . . . . . . . . . . . 35
3
Page 4

Configuration Changes Requiring Server Restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Core Server Configuration Attributes Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
nsslapd-accesscontrol (Enable Access Control) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
nsslapd-accesslog (Access Log) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
nsslapd-accesslog-level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
nsslapd-accesslog-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
nsslapd-accesslog-logbuffering (Log Buffering) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39
nsslapd-accesslog-logexpirationtime (Access Log Expiration Time) . . . . . . . . . . . . . . . . . . . . . . 39
nsslapd-accesslog-logexpirationtimeunit (Access Log Expiration Time Unit) . . . . . . . . . . . . . . 40
nsslapd-accesslog-logging-enabled (Access Log Enable Logging) . . . . . . . . . . . . . . . . . . . . . . . . 40
nsslapd-accesslog-logmaxdiskspace (Access Log Maximum Disk Space) . . . . . . . . . . . . . . . . . 41
nsslapd-accesslog-logminfreediskspace (Access Log Minimum Free Disk Space) . . . . . . . . . . 42
nsslapd-accesslog-logrotationsync-enabled (Access Log Rotation Sync Enabled) . . . . . . . . . . . 42
nsslapd-accesslog-logrotationsynchour (Access Log Rotation Sync Hour) . . . . . . . . . . . . . . . . 43
nsslapd-accesslog-logrotationsyncmin (Access Log Rotation Sync Minute) . . . . . . . . . . . . . . . 43
nsslapd-accesslog-logrotationtime (Access Log Rotation Time) . . . . . . . . . . . . . . . . . . . . . . . . . . 43
nsslapd-accesslog-logrotationtimeunit (Access Log Rotation Time Unit) . . . . . . . . . . . . . . . . . . 44
nsslapd-accesslog-maxlogsize (Access Log Maximum Log Size) . . . . . . . . . . . . . . . . . . . . . . . . . 44
nsslapd-accesslog-maxlogsperdir (Access Log Maximum Number of Log Files) . . . . . . . . . . . 45
nsslapd-accesslog-mode (Access Log File Permission) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
nsslapd-attribute-name-exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46
nsslapd-auditlog (Audit Log) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
nsslapd-auditlog-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47
nsslapd-auditlog-logexpirationtime (Audit Log Expiration Time) . . . . . . . . . . . . . . . . . . . . . . . 48
nsslapd-auditlog-logexpirationtimeunit (Audit Log Expiration Time Unit) . . . . . . . . . . . . . . . 48
nsslapd-auditlog-logging-enabled (Audit Log Enable Logging) . . . . . . . . . . . . . . . . . . . . . . . . . 48
nsslapd-auditlog-logmaxdiskspace (Audit Log Maximum Disk Space) . . . . . . . . . . . . . . . . . . . 49
nsslapd-auditlog-logminfreediskspace (Audit Log Minimum Free Disk Space) . . . . . . . . . . . . 50
nsslapd-auditlog-logrotationsync-enabled (Audit Log Rotation Sync Enabled) . . . . . . . . . . . . 50
nsslapd-auditlog-logrotationsynchour (Audit Log Rotation Sync Hour) . . . . . . . . . . . . . . . . . . 51
nsslapd-auditlog-logrotationsyncmin (Audit Log Rotation Sync Minute) . . . . . . . . . . . . . . . . . 51
nsslapd-auditlog-logrotationtime (Audit Log Rotation Time) . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
nsslapd-auditlog-logrotationtimeunit (Audit Log Rotation Time Unit) . . . . . . . . . . . . . . . . . . . 52
nsslapd-auditlog-maxlogsize (Audit L o g Maxi mum Log Size) . . . . . . . . . . . . . . . . . . . . . . . . . . 53
nsslapd-auditlog-maxlogsperdir (Audit Log Maximum Number of Log Files) . . . . . . . . . . . . . 53
nsslapd-auditlog-mode (Audit Log File Permission) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
nsslapd-certmap-basedn (Certificate Map Search Base) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
nsslapd-config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
nsslapd-conntablesize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
nsslapd-csnlogging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
nsslapd-ds4-compatible-schema . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56
nsslapd-enquote-sup-oc (Enable Superior Object Class Enquoting) . . . . . . . . . . . . . . . . . . . . . . 56
4 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 5

nsslapd-errorlog (Error Log) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
nsslapd-errorlog-level (Error Log Level) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
nsslapd-errorlog-list . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
nsslapd-errorlog-logexpirationtime (Error Log Expiration Time) . . . . . . . . . . . . . . . . . . . . . . . . 60
nsslapd-errorlog-logexpirationtimeunit (Error Log Expiration Time Unit) . . . . . . . . . . . . . . . . 60
nsslapd-errorlog-logging-enabled (Enable Error Logging) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
nsslapd-errorlog-logmaxdiskspace (Error Log Maximum Disk Space) . . . . . . . . . . . . . . . . . . . . 61
nsslapd-errorlog-logminfreediskspace (Error Log Minimum Free Disk Space) . . . . . . . . . . . . . 61
nsslapd-errorlog-logrotationsync-enabled (Error Log Rotation Sync Enabled) . . . . . . . . . . . . . 62
nsslapd-errorlog-logrotationsynchour (Error Log Rotation Sync Hour) . . . . . . . . . . . . . . . . . . . 62
nsslapd-errorlog-logrotationsyncmin (Error Log Rotation Sync Minute) . . . . . . . . . . . . . . . . . . 63
nsslapd-errorlog-logrotationtime (Error Log Rotation Time) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63
nsslapd-errorlog-logrotationtime (Error Log Rotation Time) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
nsslapd-errorlog-logrotationtimeunit (Error Log Rotation Time Unit) . . . . . . . . . . . . . . . . . . . . 64
nsslapd-errorlog-maxlogsize (Maximum Error Log Size) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65
nsslapd-errorlog-maxlogsperdir (Maximum Number of Error Log Files) . . . . . . . . . . . . . . . . . 65
nsslapd-errorlog-mode (Error Log File Permission) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
nsslapd-groupevalnestlevel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66
nsslapd-idletimeout (Default Idle Timeout) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
nsslapd-instancedir (Instance Directory) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67
nsslapd-ioblocktimeout (IO Block Time Out) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
nsslapd-lastmod (Track Modification Time) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
nsslapd-listenhost (Listen to IP Address) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
nsslapd-localhost (Local Host) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
nsslapd-localuser (Local User) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
nsslapd-maxbersize (Maximum Message Size) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
nsslapd-maxdescriptors (Maximum File Descriptors) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
nsslapd-maxthreadsperconn (Maximum Threads Per Connection) . . . . . . . . . . . . . . . . . . . . . . . 71
nsslapd-nagle . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
nsslapd-outbound-ldap-io-timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
nsslapd-plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72
nsslapd-port (Port Number) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
nsslapd-privatenamespaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73
nsslapd-pwpolicy-local (Enable Subtree- and User-Level Password Policy) . . . . . . . . . . . . . . . 73
nsslapd-readonly (Read Only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
nsslapd-referral (Referral) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 74
nsslapd-referralmode (Referral Mode) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
nsslapd-reservedescriptors (Reserved File Descriptors) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75
nsslapd-return-exact-case (Return Exact Case) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
nsslapd-rootdn (Manager DN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
nsslapd-rootpw (Root Password) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
nsslapd-rootpwstoragescheme (Root Password Storage Scheme) . . . . . . . . . . . . . . . . . . . . . . . . 79
nsslapd-schema-ignore-trailing-spaces (Ignore Trailing Spaces in Object Class Names) . . . . . 79
5
Page 6

nsslapd-schemacheck (Schema Checking) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
nsslapd-schemareplace . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
nsslapd-securelistenhost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
nsslapd-securePort (Encrypted Port Number) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
nsslapd-security (Security) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
nsslapd-sizelimit (Size Limit) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
nsslapd-ssl-check-hostname (Verify Hostname for Outbound Connections) . . . . . . . . . . . . . . . 83
nsslapd-threadnumber (Thread Number) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
nsslapd-timelimit (Time Limit) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84
nsslapd-versionstring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
passwordChange (Password Change) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
passwordCheckSyntax (Check Password Syntax) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
passwordExp (Password Expiration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
passwordHistory (Password History) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
passwordInHistory (Number of Passwords to Remember) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
passwordLockout (Account Lockout) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
passwordLockoutDuration (Lockout Duration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
passwordMaxAge (Password Maximum Age) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88
passwordMaxFailure (Maximum Password Failures) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
passwordMinAge (Password Minimum Age) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
passwordMinLength (Password Minimum Length) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
passwordMustChange (Password Must Change) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90
passwordResetFailureCount (Reset Password Failure Count After) . . . . . . . . . . . . . . . . . . . . . . 90
passwordStorageScheme (Password Storage Scheme) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
passwordUnlock (Unlock Account) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
passwordWarning (Send Warning) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
cn=changelog5 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92
nsslapd-changelogdir . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
nsslapd-changelogmaxage (Max Changelog Age) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
nsslapd-changelogmaxentries (Max Changelog Records) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94
cn=encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
nssslsessiontimeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
nssslclientauth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 95
nsssl2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
nsssl3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
nsssl3ciphers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
cn=features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
cn=mapping tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Suffix Configuration Attributes Under cn="suffixName" . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
nsslapd-state . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
nsslapd-backend . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Replication Attributes Under cn=replica, cn=“suffixName”, cn=mapping tree,cn=config . . . . . . 100
cn . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
6 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 7

nsDS5Flags . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
nsDS5ReplicaBindDN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
nsDS5ReplicaChangeCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
nsDS5ReplicaId . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
nsDS5ReplicaLegacyConsumer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
nsDS5ReplicaName . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
nsDS5ReplicaPurgeDelay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
nsDS5ReplicaReferral . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
nsDS5ReplicaRoot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
nsDS5ReplicaTombstonePurgeInterval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
nsDS5ReplicaType . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104
nsState . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
Replication Attributes Under cn=ReplicationAgreementNa me ,cn= repli ca , cn="suffixName",
cn=mapping tree,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
nsDS5ReplicaBindDN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
nsDS5ReplicaBindMethod . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
nsDS5ReplicaBusyWaitTime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106
nsDS5ReplicaChangesSentSinceStartup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
nsDS5ReplicaCredentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107
nsDS5ReplicaHost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
nsDS5ReplicaLastInitEnd . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
nsDS5ReplicaLastInitStart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
nsDS5ReplicaLastInitStatus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
nsDS5ReplicaLastUpdateEnd . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
nsDS5ReplicaLastUpdateStart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
nsDS5ReplicaLastUpdateStatus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
nsDS5ReplicaPort . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110
nsDS5ReplicaReapActive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
nsDS5ReplicaRefresh . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
nsDS5ReplicaRoot . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111
nsDS5ReplicaSessionPauseTime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112
nsDS5ReplicaTimeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
nsDS5ReplicaTransportInfo . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113
nsDS5ReplicaUpdateInProgress . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
nsDS5ReplicaUpdateSchedule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
nsDS50ruv . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
cn=monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
currentConnections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
totalConnections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
dTableSize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
readWaiters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
7
Page 8

opsInitiated . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
opsCompleted . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
entriesSent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115
bytesSent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
currentTime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
startTime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
nbackEnds . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
backendMonitorDN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
cn=replication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116
cn=SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
nssnmpenabled . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
nssnmporganization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
nssnmplocation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 117
nssnmpcontact . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
nssnmpdescription . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
nssnmpmasterhost . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 118
nssnmpmasterport . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
cn=tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
cn=uniqueid generator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
nsstate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119
Configuration Quick Reference Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
LDIF Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120
Configuration Changes Requiring Server Restart . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Chapter 3 Plug-in Implemented Server Functionality Reference . . . . . . . . . . . . . . . . . . . . 125
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125
Object Classes for Plug-In Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Server Plug-in Functionality Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
7-bit check Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
ACL Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
ACL preoperation Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Binary Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Boolean Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Case Exact String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
Case Ignore String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Chaining database Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130
Class of Service Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Country String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Distinguished Name Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
Generalized Time Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132
HTTP Client Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Integer Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133
Internationalization Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
8 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 9

ldbm database Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134
Legacy Replication Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Multimaster Replication Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135
Octet String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
CLEAR Password Storage Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
CRYPT Password Storage Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
NS-MTA-MD5 Password Storage Scheme Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
SHA Password Storage Scheme Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
SSHA Password Storage Scheme Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Postal Address String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 139
Presence Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
PTA Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140
Referential Integrity Postoperation Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Retro Changelog Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Roles Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
Space Insensitive String Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143
State Change Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144
Telephone Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
UID Uniqueness Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145
URI Syntax Plug-in . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
List of Attributes Common to All Plug-ins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
nsslapd-pluginPath . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
nsslapd-pluginInitfunc . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
nsslapd-pluginType . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
nsslapd-pluginEnabled . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 148
nsslapd-pluginId . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
nsslapd-pluginVersion . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
nsslapd-pluginVendor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
nsslapd-pluginDescription . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Attributes Allowed by Certain Plug-ins . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
nsslapd-plugin-depends-on-type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
nsslapd-plugin-depends-on-named . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Database Plug-in Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Database Attributes Under cn=config,cn=ldbm database,cn=plugins,cn=config . . . . . . . . . . . . . 152
nsLookthroughLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
nsslapd-allidsthreshold . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
nsslapd-cache-autosize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
nsslapd-cache-autosize-split . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
nsslapd-dbcachesize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
nsslapd-db-checkpoint-interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
nsslapd-db-circular-logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
nsslapd-db-debug . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
nsslapd-db-durable-transactions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
9
Page 10

nsslapd-db-home-directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157
nsslapd-db-idl-divisor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
nsslapd-db-logbuf-size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
nsslapd-db-logdirectory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
nsslapd-db-logfile-size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
nsslapd-db-page-size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160
nsslapd-db-spin-count . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
nsslapd-db-transaction-batch-val . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161
nsslapd-db-transaction-logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
nsslapd-db-trickle-percentage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
nsslapd-db-verbose . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
nsslapd-dbncache . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
nsslapd-import-cachesize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
nsslapd-import-cache-autosize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164
nsslapd-mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
Database A t tributes Under cn=monitor,cn=ldbm database, cn=plugins,cn=config . . . . . . . . . . . 166
dbcachehits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
dbcachetries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166
dbcachehitratio . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
dbcachepagein . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
dbcachepageout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
dbcacheroevict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
dbcacherwevict . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
Database Attributes Under cn=Ne tsca p eRoot ,cn= ldb m data ba se, cn =pl ug ins ,c n= co nfig and
cn=UserRoot,cn=ldbm database, cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167
nsslapd-cachesize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
nsslapd-cachememsize . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168
nsslapd-directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
nsslapd-readonly . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
nsslapd-require-index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169
nsslapd-suffix . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
Database Attributes Under cn=database,cn=monitor,cn=ldbm database, cn=plugins,cn=config . .
170
nsslapd-db-abort-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
nsslapd-db-active-txns . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170
nsslapd-db-cache-hit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-cache-try . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-cache-region-wait-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-cache-size-bytes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-clean-pages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-commit-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-deadlock-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-dirty-pages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
10 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 11

nsslapd-db-hash-buckets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-hash-elements-examine-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-hash-search-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171
nsslapd-db-lock-conflicts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-lock-region-wait-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-lock-request-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-lockers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-log-bytes-since-checkpoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-log-region-wait-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-log-write-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-longest-chain-length . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-page-create-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-page-read-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-page-ro-evict-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172
nsslapd-db-page-rw-evict-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsslapd-db-page-trickle-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsslapd-db-page-write-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsslapd-db-pages-in-use . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsslapd-db-txn-region-wait-rate . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Database Attributes Under cn=default indexes,cn=config,cn=ldbm database,
cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsSystemIndex . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
nsIndexType . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
nsMatchingRule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
cn . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Database Attributes Under c n=monitor,cn=Net scaperoot,cn=ldbm database,cn=plugin s,cn=config
175
dbfilenamenumber . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
dbfilecachehit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
dbfilecachemiss . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
dbfilepagein . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
dbfilepageout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 176
Database Attributes Under cn=index,cn=Netscaperoot,cn=ldbm database, cn=plugins,cn=config
and cn=index,cn=UserRoot,cn=ldbm database, cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . 176
Database Link Plug-in Attributes (chaining attributes) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177
Database Link Attributes Under cn=config,cn=chaining database, cn=plugins,cn=config . . . . . 178
nsActiveChainingComponents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
nsMaxResponseDelay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
nsMaxTestResponseDelay . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179
nsTransmittedControls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Database Link Attributes Under cn=default instance config,cn=chaining
database,cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
11
Page 12

nsAbandonedSearchCheckInterval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
nsBindConnectionsLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
nsBindRetryLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
nsBindTimeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181
nsCheckLocalACI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
nsConcurrentBindLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
nsConcurrentOperationsLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
nsConnectionLife . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
nsOperationConnectionsLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
nsProxiedAuthorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
nsReferralOnScopedSearch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
nsSizeLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 184
nsTimeLimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
Database Link Attributes Under cn=database link instance name,cn=chaining database,
cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
nsFarmServerURL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 185
nsMultiplexorBindDN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
nsMultiplexorCredentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
nshoplimit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Database Link Attributes Under cn=monitor,cn=database instance name,cn=chaining database,
cn=plugins,cn=config . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsAddCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsDeleteCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsModifyCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsRenameCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsSearchBaseCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsSearchOneLevelCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187
nsSearchSubtreeCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsAbandonCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsBindCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsUnbindCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsCompareCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsOperationConnectionCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsBindConnectionCount . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
Retro Changelog Plug-in Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188
nsslapd-changelogdir . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
nsslapd-changelogmaxage (Max Changelog Age) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Chapter 4 Server Instance File Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Overview of Directory Server Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191
Backup Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Database Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
12 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 13

ldif Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Lock Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196
Chapter 5 Access Log and Connection Code Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
Access Log Content . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
Access Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Default Access Logging Content . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Connection Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
File Descriptor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200
Slot Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Operation Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Method Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Version Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Error Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Tag Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201
Number of Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
Elapsed Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
LDAP Request Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202
LDAP Response Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Unindexed Search Indicator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
VLV-Related Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203
Search Scope . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 204
Extended Operation OID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Change Sequence Number . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205
Abandon Message . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Message ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
SASL Multi-Stage Bind Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206
Access Log Content for Additional Access Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207
Connection Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Options Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208
Common Connection Codes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209
LDAP Result Codes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210
Chapter 6 Migration from Earlier Versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Migration from 4.x Directory Server to 6.x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213
Server Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 214
Database Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 217
Upgrade from Directory Server 5.x to 6.x . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
General Server Configuration Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 218
Database Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 222
Database Link Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 223
13
Page 14

SNMP Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 224
Chapter 7 Command-Line Utilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Finding and Executing Command-Line Utilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Command-Line Utilities Quick Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 226
Using Special Characters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
Syntax for Using Special Characters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
ldapsearch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
ldapsearch Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
Commonly Used ldapsearch Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228
SSL Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230
Additional ldapsearch Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 231
ldapmodify . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
ldapmodify Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234
Commonly Used ldapmodify Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 235
SSL Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 236
Additional ldapmodify Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 237
ldapdelete . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
ldapdelete Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Commonly Used ldapdelete Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
SSL Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 240
Additional ldapdelete Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241
ldif . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
dbscan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 244
Chapter 8 Command-Line Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Finding and Executing Command-Line Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
Command-Line Scripts Quick Reference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 246
Shell and Batch Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 249
bak2db (Restore database from backup) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
db2bak (Create backup of database) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
db2ldif (Export database contents to LDIF) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 251
14 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 15

db2dsml (Export database contents to DSML) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
db2index (Reindex database index files) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 253
dsml2db (Import DSML document contents into database) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
getpwenc (Print encrypted password) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
ldif2db (Import) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 256
ldif2ldap (Perform import operation over LDAP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
monitor (Retrieve monitoring information) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 257
restart-slapd (Restart the Directory Server) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Exit Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
restoreconfig (Restore Administration Server Configuration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 258
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
saveconfig (Save Administration Server Configuration) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
start-slapd (Start the Directory Server) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Exit Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
stop-slapd (Stop the Directory Server) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
Exit Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260
suffix2instance (Map Suffix to Backend Name) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
15
Page 16

vlvindex (Create virtual list view indexes) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Perl Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
bak2db.pl (Restore database from backup) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
db2bak.pl (Create backup of database) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
db2index.pl (Create and generate indexes) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
db2ldif.pl (Export database contents to LDIF) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 265
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 266
ldif2db.pl (Import) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267
logconv.pl (Log converter) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 271
migrateInstance6 (Migrate to Directory Server 6.x) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
ns-accountstatus.pl (Establish account status) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 274
ns-activate.pl (Activate an entry or group of entries) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
ns-inactivate.pl (Inactivate an entry or group of entries) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 275
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
ns-newpwpolicy.pl (Add attributes for fine-grained password policy) . . . . . . . . . . . . . . . . . . . . . 276
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
template-cl-dump.pl (Dump and decode changelog) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 277
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
template-repl-monitor.pl (Monitor replication status) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 278
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
16 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 17

Configuration File Format . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 280
Appendix A Using the ns-slapd and slapd.exe Command-Line Utilities . . . . . . . . . . . . . . . 283
Overview of ns-slapd and slapd.exe Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
ns-slapd (UNIX) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 284
slapd.exe (Windows) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 284
Finding and Executing the ns-slapd and slapd.exe Command-Line Utilities . . . . . . . . . . . . . . . . . . . 284
ns-slapd and slapd.exe Command-Line Utilities for Exporting Databases . . . . . . . . . . . . . . . . . . . . . 285
db2ldif . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
ns-slapd and slapd.exe Command-Line Utilities for Restoring and Backing up Databases . . . . . . . 287
ldif2db . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
archive2db . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 289
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
db2archive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290
ns-slapd and slapd.exe Command-Line Utilities for Creating and Regenerating Indexes . . . . . . . . 291
db2index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
Syntax . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291
Glossary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 293
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 309
17
Page 18

18 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 19

About This Reference Guide
Netscape Directory Server (Directory Server) is a powerful and scalable
distributed directory server based on the industry-standard Lightweight
Directory Access Protocol (LDAP). Directory Server is the cornerstone for
building a centralized and distributed data repository that can be used in your
intranet, over your extranet with your trading partners, or over the public
Internet to reach your customers.
This Configuration, Command, and File Refere nce documents server configuration
and command-line utilities provided with Directory Server.
This preface contains the following sections:
• Directory Server Overview (page 19)
• Prerequisite Reading (pa ge 20)
• What Is In This Reference Guide? (page 20)
• Conventions Used In This Reference Guide (page 21)
• Related Information (page 21)
Directory Server Overview
The major components of Directory Server include:
• An LDAP server—The core of the directory service, provided by the
daemon, and compliant with the LDAP v3 Internet standards.
• Directory Server Console—An improved management console that
dramatically reduces the effort of sett ing up and maintaining your directory
service. Directory Server Console is part of Netscape Console, the common
management frame work for Netscape servers.
ns-slapd
19
Page 20

Prerequisite Reading
• SNMP Agent—Permits you to monitor Directory Server in real time using
the Simple Network Management Protocol (SNM P).
• Online backup and restore—Allows you to create backups and restore from
backups while the server is running.
Prerequisite Reading
This reference guide does not describe many of the basic directory and
architectural concepts that you need to successfully design, implement, and
administer your directory service. Those concepts are described in the Netscape
Directory Server Administrator’s Guid e. You should read that book before
continuing with this reference guide.
When you are familiar with Directory Server concepts and have done some
preliminary planning for your directory service, you can install the Directory
Server. The instructions for installing the various Directory Server components
are contained in the N ets cape Dire cto ry Server Inst allation Guide .
Managing Servers with Netscap e Consol e contains general background
information on how to use Netscape servers. You should read and understand
the concepts in this book before you attempt to administer the Di rectory Server.
What Is In This Reference Guide?
This book is a reference guide for the server configuration and the command-line
utilities. It is designed primarily for directory administrators and experienced
directory users who want to use the command line to access the directory. After
configuring your server, use this reference guide to help you maintain it.
You can also manage the Directory Server using the Directory Server Console, a
graphical user interface. The Netscape Directory Server Administrator’s Guide
describes how to do this and explains individual administration tasks more
fully.
20 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 21

Conventions Used In This Reference Guide
Conventions Used In This Reference Guide
This section explains the conventions used in this book.
Monospaced font—This typeface is u sed for any text that appears on the co mputer
screen or text that you should type. It is also used for filenames, functions, and
examples.
NOTE Notes and Warnings mark important information. Make sure you
read the information before continuing with a task.
Throughout this book you will see path references of the form:
serverRoot/slapd-serverID/...
serverRoot is the installation directory. For Directory Server 5.x and 6.x,
/usr/netscape/servers is the default installation directory on UNIX. On
Windows, it is
Server in a different location, you should ada p t the path accordingly.
serverID is the ID or identifier you assigned to an instance of Directory
Server when you installed it. For example, if you gave the server an
identifier of
/usr/netscape/servers/slapd-phonebook/. . .
c:\usr\netscape\servers. If you have installed Directory
phonebook, then the actual path would look like this:
All paths specified in this manual are in UNIX f orma t. If you are using a
Windows-based Directory Server, you should assume the equivalent file paths
whenever UNIX file paths are shown in this book.
In examples/sample code, paths assume that the Directory Server is installed in
the default location
Directory Server in a different lo cation, adapt the paths accordingly. Also, all
examples use
/usr/netscape/servers. If you have installed your
phonebook for the server identifier where appropriate.
Related Information
The document set for Directory Server also contains the follo wing guides:
• Netscape Directo ry Server Installation Guide. Procedures for installing
Directory Server as well as procedures for migrating y our D irectory S e rver.
About This Reference Guide 21
Page 22

Related Information
• Netscape Directory Ser ver De ploy ment Guid e. Prov ides an overview for
planning your deployment of the Directory Server. Includes deployment
examples.
• Netscape Directory Ser ver Adminis trato r’s Guide . Procedures for the
day-to-day maintenance of your di recto r y service. Includes information on
configuring server-side plug-ins.
• Netscape Directory Ser ver Sch ema Refe renc e. Prov id es information about the
Netscape Directory Server schema.
• Netscape Directory Server Plug-In Programmer’s Guide . Describes how to
write server plug-ins in order to customize and extend the capabilities of
Directory Server.
For a list of documentation installed with Directory Server, open the
serverRoot/manual/en/slapd/index.htm file.
For the latest information about Directory Server, including current release
notes, complete product documentation, technical notes, and deployment
information, check this site:
http://enterprise.netscape.com/docs
22 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 23

Chapter 1
Introduction
This chapter provides a brief overview of the configuration and administration
utilities provided to manage the Netscape Directory Server (Directory Server).
This chapter is divided into the following sections:
• Overview of Directory Server Management (page 23)
• Directory Server Configuration (page 24)
• Directory Server Instance File Reference (page 24)
• Migrating Directory Server (page 24)
• Using Directory Server Command-Line Utilities (page 25)
• Using Directory Server Command-Line Scripts (page 25)
Overview of Directory Server Manageme nt
Directory Server is based on an open-systems server protocol called the
Lightweight Director y Access Protocol (LDAP). The Directory S erver is a
robust, scalable server designed to manage large scale directories to support
enterprise-wide directory of users and resources, extranets and e-commerce
applications over the Internet. The Directory Server runs as the
process or service (
the directory databases and responds to client requests.
You can perform most Directory Server administrative tasks through Netscape
Console, the graphical user interface provided with the Directory Server. For
information on the general use of the Netscape Console see Managing Servers
with Netscape Console, and for details on how to use the console to manage the
Directory Server in particular, see Net scape Dir ec tory S erver Adm inist rator’s
Guide.
slapd on Windows) on your machine. The server manages
ns-slapd
23
Page 24

Directory Server Configuration
This reference manual deals with the other methods of ma naging the Directory
Server, namely altering the server configuration attributes via the command
line and using the command-line utilities.
Directory Server Configuration
The format and method for storing configuration information for Directory
Server mark a significant change from previous versions of the Directory
Server. A full explanation of these changes and a listing for all s erver attributes
can be found in Chapter 2, “Core Server Configuration Reference” and Chapter 3,
“Plug-in Implemented Server Functionality Reference.”
Directory Server Instance File Reference
Having an overview of the files and configuration information stored in each
instance of Directory Server is useful, as this helps administrators understand
the changes or absence of chan ge s in the course of directory activity. From a
security standpoint, such an overview can help customers detect errors and
intrusion as they know what kind of cha nges to expect and what will be
considered abnormal behavior. See Chapter 4, “Server Instance File Reference” for
further information.
Migrating Directory Server
In earlier versions of the Directory Server (for example, versions 4.1x), all
configuration parameters were stored in text files. In Directory Server 5.x
onwards, configuration attributes are stored as LDAP configuration entries in
the
dse.ldif file. The mapping of configuration parameters between earlier
versions of Directory Server and Directory Server 6.x is described in Chapter 6,
“Migration from Earlier Versions.”
24 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 25

Using Directory Server Command-Line Utilities
Using Directory Server Command-Line Utilities
Directory Server comes with a set of configura ble command-line utilities that
you can use to search and modify entries in the directory and administer the
server. Chapter 7, “Command-Line Utilities” describes these command-line utilities
and contains information on where the utilities are stored and how to access them.
In addition to these command-line utiltiies, Directory Server also provides
ns-slapd and slapd.exe command-line utilities for performing directory
operations as described in Appendix A, “Using the ns-slapd and slapd.exe
Command-Line Utilities.”
Using Directory Server Command-Line Scripts
In addition to command-line utilities, several non-configurable scripts are
provided with the Directory Server that make it quick and easy to perform
routine server administration tasks from the command line. Chapter 8,
“Command-Line Scripts” lists the mos t frequently used scripts and contains
information on where the scripts are stored and how to access them.
Chapter 1 Introduction 25
Page 26

Using Directory Server Command-Line Scripts
26 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 27

Chapter 2
Core Server Configuration Reference
The configuration information for Netscape Directory Server (Directory Server)
is stored as LDAP entries within the directory itself. Therefore, changes to the
server configuration must be implemented through the use of the server itself
rather than by simply editing configuration files. The principal advantage of
this method of configuration storage is that it allow s a director y administrator
to reconfigure the server via LDAP while it is still running, and thus avoid the need
to shut the server down.
This chapter gives details on how the configuration is organized and how to alter
it. The chapter also provides an alphabetical reference for all attributes. The chapter
is divided into the following sections:
• Server Configuration - Overview (page 27)
• Accessing and Modifying Server Configuration (page 32)
• Core Server Configuration Attributes Reference (page 35)
• Configuration Quick Reference Tables (page 120)
Server Configuration - Overview
When you install the Directory Server, its default configuration is stored as a
series of LDAP entries within the directory, under the subtree
When the server is started, the contents of the
a file (
dse.ldif) in LDIF format. This dse.ldif file contains all of the server
configuration information. Note that the la test version of this file is called
dse.ldif, the version prior to the last modification is called dse.ldif.bak, and
the latest file with which the server successfully started is called
dse.ldif.startOK.
cn=config subtree are read from
cn=config.
27
Page 28
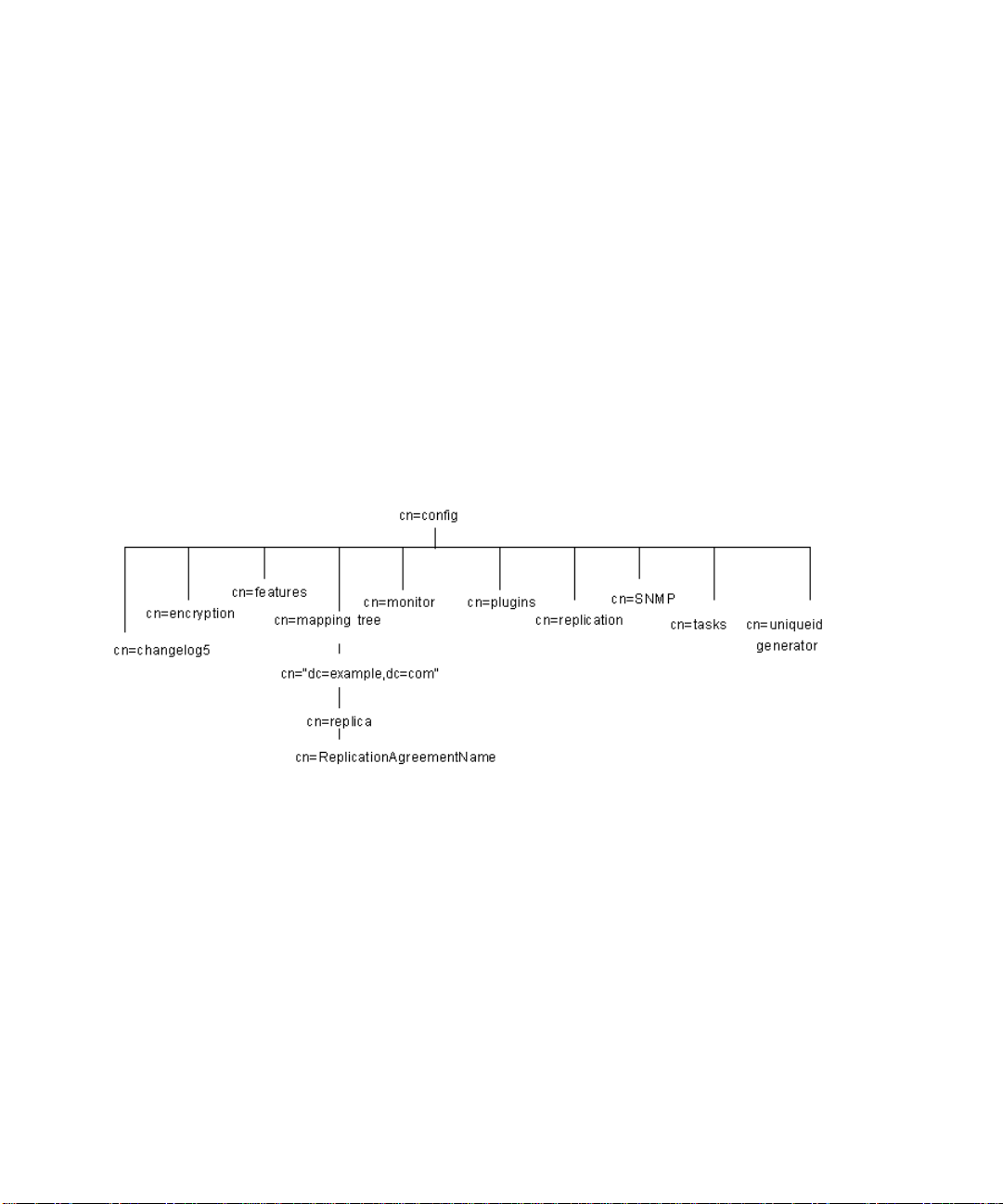
Server Configuration - Overview
Many of the features of the Directory Server are designed as discrete modules
that plug into the core server. The details of the internal configuration for each
plug-in are contained in separate entries under
example, the configuration of the Telephone Syntax plug-in is contained in this
entry:
cn=Telephone Syntax,cn=plugins,cn=config
Similarly, database-specific configuration is stored under:
cn=ldbm database,cn=plugins,cn=config and cn=chaining
database,cn=plugins,cn=config
Figure 2-1 sho ws how the configuration data fits within the cn=config Directory
Information Tree.
Figure 2-1 Directory Information Tree Showing Configuration Data
cn=plugins,cn=config. For
This overview is divided into the following sections:
• LDIF Configuration Files - Location
• Schema Configuration Files - Location
• How the Server Configuration is Organiz e d
• Migration of Pre-Directory Server 6.x Configuration Files to LDIF Format
28 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 29

Server Conf iguration - Overview
LDIF Configuration Fil e s - Location
The Directory Server configuration data is auto matically output to files in LDIF
format that are located in the following directo ry:
serverRoot/slapd-serverID/config
Thus, if you specified a server identifier of phonebook for example, then in a
default installation, your configuration LDIF files are all stored under:
/usr/netscape/servers/slapd-phonebook/config
Schema Configuration Files - Location
Schema configuration is also stored in LDIF format and these files are located in the
following directory:
serverRoot/slapd-serverID/config/schema
For a full list of the LDIF configuratio n f iles that are supplied with Directory
Server, see Table 2-3 under “Configuration Quick Reference Tables” at the end of
this chapter.
How the Server Configuration is Organized
The dse.ldif file contains all configuration informatio n including directory
specific entries created by the directory at server startup, as well as directory
specific entries related to the database, also created by the directory at server
startup. The file includes the Root DSE (named by
cn=config. When the server generates the dse.ldif file it lists the entries in
hierarchical order. It does so in the order that the entries appear in the directory
under
cn=config.
Configuration A ttributes
Within a configuration entry, each attribute is represented a s an attribute name.
The value of the attribute corresponds to the attribute’s configura tion.
Code Example 2-1 gives an example of part of the
Server. The example shows, amongst other things, that schema checking has been
turned on; this is represented by the attribute
the value
Code Example 2-1 Extract of dse.ldif File
on.
Chapter 2 Core Server Configuration Reference 29
"") and the entire contents of
dse.ldif file for a Directory
nsslapd-schemacheck, which takes
Page 30

Server Configuration - Overview
dn: cn=config
objectclass: top
objectclass: extensibleObject
objectclass: nsslapdConfig
nsslapd-accesslog-logging-enabled: on
nsslapd-enquote-sup-oc: on
nsslapd-localhost: phonebook.example.com
nsslapd-errorlog:
/usr/netscape/servers/slapd-phonebook/logs/errors
nsslapd-schemacheck: on
nsslapd-store-state-info: on
nsslapd-port: 389
nsslapd-localuser: nobody
...
Configuration of Plug-in Functionality
The configuration for each part of Directory Server plug-in functionality has its
own separate entry and set of attributes under the subtree
cn=plugins,cn=config. Code Example 2-2 shows an example of the confi guration
entry for a plug-in, the Telephone Syntax plug-in.
Code Example 2-2 Configuration Entry for Telephone Syntax Plug-in
dn: cn=Telephone Syntax,cn=plugins,cn=config
objectclass: top
objectclass: nsSlapdPlugin
objectclass: extensibleObject
cn: Telephone Syntax
nsslapd-pluginPath: /usr/netscape/servers/lib/syntax-plug-in.so
nsslapd-pluginInitfunc: tel_init
nsslapd-pluginType: syntax
nsslapd-pluginEnabled: on
Some of these attributes are common to all plug-ins and some may be particular to
a specific plug-in. You can check which attributes a re currently being used by a
given plug-in by performing an
30 Netscape Directory Server Configuration, Command, and File Reference • December 2003
ldapsearch on the cn=config subtree.
Page 31

Server Conf iguration - Overview
For a list of plug-ins supported by Directory Server, general plug-in
configuration information, the plug- in configuration attribute referen ce, and a
list of plug-ins requiring restart, see Chapter 3, “Plug- in Implemented Server
Functionality Reference.”
Configuration of Databases
The cn=NetscapeRoot and cn=UserRoot subtrees contain configuration data for
the databases containing the
o=NetscapeRoot and o=UserRoot suffixes.
•The
cn=NetscapeRoot subtree contains the configuration data used by the
Netscape Administration Server for authentication and all actio ns that
cannot be performed through LDAP (such as start/stop).
•The
cn=UserRoot subtree contains all the configuration data for the first
user-defined database created during server installation. The
cn=UserRoot
subtree is called UserRoot by default. However, this is not hard-coded, and,
given the fact that there will be multiple database instances, this name will be
changed and defined by the user as and when new databases are added.
Configuration of Indexes
Configuration information for indexing is stored as entries in the Directory
Server under the following information-tree nodes:
•
cn=index,cn=NetscapeRoot,cn=ldbm database,cn=plugins,cn=config
•
cn=index,cn=UserRoot,cn=ldbm database,cn=plugins,cn=config
cn=default indexes,cn=config,cn=ldbm database,
•
cn=plugins,cn=config
For more information regarding indexes in general, see Net sc ape D irecto ry Serv er
Administrator’s Guide. For information regarding the index configuration
attributes, see “Database Attributes Under cn=default indexes,cn=config,cn=ldbm
database, cn=plugins,cn=config” on page 173. Th e attributes are presented here as
this node is the first to appear in our representation of the configuration attributes
that is based on the
cn=config informatio n tr e e.
Chapter 2 Core Server Configuration Reference 31
Page 32

Accessing and Modifying Server Configuration
Migration of Pre-Directory Server 6.x Configuration Files to LDIF Format
The Directory Server will only recognize configuration files that are in the LDIF
format, which means that the
configuration files from 4.x versions o f D irectory Server must be converted to
the LDIF format. Directory Server 4.x configurations can be migrated to the new
LDIF format using the tool
Chapter 6, “Migrating and Upgrading From Previous Versions” in the Netscape
Directory Server Installation Guide.
slapd.conf and slapd.ldbm.conf
migrateInstance6 tool. For more information, see
Accessing and Modifying Server Configuration
This section discusses access contro l for configuration entries and describes the
various ways in which the server configuration can be viewed and modified. It also
covers restrictions to the kinds of modification that can be made and discusses
attributes that require the server to be restarted for changes to take effect.
• Access Control For Configuration Entries
• Changing Configuration Attributes
Access Control For Configuration Entries
When the Directory Server is installed, a default set of A ccess Control
Instructions (ACIs) is implemented for all entries und e r
Example 2-3 shows an example of these default ACIs.
32 Netscape Directory Server Configuration, Command, and File Reference • December 2003
cn=config. Code
Page 33

Accessing and Modifying Server Configuration
Code Example 2-3 Default ACIs in dse.ldif
aci: (targetattr = "*")(version 3.0; acl "Configuration
Adminstrators Group"; allow (all)
groupdn = "ldap:///cn=Configuration Administrators,ou=Groups,
ou=TopologyManagement, o=NetscapeRoot";)
aci: (targetattr = "*")(version 3.0; acl "Configuration
Adminstrator"; allow (all)
userdn = "ldap:///uid=admin,ou=Administrators,
ou=TopologyManagement, o=NetscapeRoot";)
aci: (targetattr = "*")(version 3.0; acl "Local Directory
Adminstrators Group"; allow (all)
groupdn = "ldap:///ou=Directory Administrators,
dc=example,dc=com";)
aci: (targetattr = "*")(version 3.0; acl "SIE Group"; allow(all)
groupdn = "ldap:///cn=slapd-phonebook, cn=Netscape Directory
Server, cn=Server Group, cn=phonebook.example.com,
dc=example,dc=com, o=NetscapeRoot";)
These default ACIs allow all LDAP operations to be carried out on all configuration
attributes by the following users:
• Members of the Configuration Administrators Group.
• The user acting as the Administrator, who has the U I D
admin that can be
configur e d a t in stallatio n ti me.
• Members of local Directory Administrators Group.
• The local Directory Administrator (root DN).
• The SIE (Server Instance Entry) Group that is usua lly assigned using the Set
Access Permissions from the main topology view in the main console.
For more information on Access Control, see the Netscape Directory Server
Administrator’s Guide.
Changing Configuration Attributes
You can view and change server attribute values in one of three ways. You make
the changes by using LDAP through Netscape Console, by performing
ldapsearch and ldapmodify commands, or by manually editing the dse.ldif
file.
Chapter 2 Core Server Configuration Reference 33
Page 34

Accessing and Modifying Server Configuration
NOTE If you edit the
otherwise your changes will be lost. Editing the
dse.ldif file, you must stop the server beforehand,
dse.ldif file is
recommended only for changes to attrib utes which cannot be
altered dynamically. See “Configuration Changes Requiring Server
Restart” on page 123 for further information.
The following sections describe how to modify entries using LDAP (both via
Netscape Console and over the command line), the restrictions to modifying
entries, the restrictions to modifying attributes, and the configuration changes
requiring restart.
Modifying Configuration Entries Using LDAP
The configuration entries in the directory can be searched and modified usin g
LDAP either via the Netscape Console or by performing
ldapmodify operations in the same way as other directory entries. The
advantage of using LDAP to modi fy entries is that you can make the changes
while the server is running. You must remember to specify the port number
when modifying configuration entries as the server is not necessarily running
on port 389. For further information, see Chapter 2, “Creating Directory
Entries” in the Netscape Directory Server Administrator’s Guide. However, certain
changes do require the server to be restarted before they are taken into account.
See “Configuration Changes Requiring Server Restart” on page 123 for further
information.
ldapsearch and
NOTE As with any set of configuration files, care should be taken when
changing or deleting nodes in the
cn=config subtree, as this risks
affecting Directory Server functionali ty.
The entire configuration, including attributes that always take default values, can
be viewed by performing an
ldapsearch -b cn=config -D bindDN -w password
ldapsearch operation on the cn=config subtree:
where bindDN is the DN chosen for the Directory Manager when the server was
installed and password is the password chosen for Directory Manager. For more
information on using
ldapsearch, see “ldapsearch” on page 228.
Previously, we saw an example of the configuration entry for the Telephone Syntax
plug-in where the plug-in is enabled. If you wanted to disable this feature you
might use the following series of commands to implement this change.
34 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 35

Core Server Configuration Attributes Reference
Code Example 2-4 Disabling the Telephone Syntax Plug-in
ldapmodify -D bindDN -w password
dn: cn=Telephone Syntax,cn=plugins,cn=config
changetype: modify
replace: nsslapd-pluginEnabled
nsslapd-pluginEnabled: off
Restrictions to Modifying Configuration Entries and Attributes
Certain restrictions apply when modifying server entries and attributes:
•The
cn=monitor entry and its child entries are read-only and cannot be
modified.
• If an attribute is added to
cn=config, the server will ignore it.
• If an invalid value is entered for an attribute, this will be ignored by the server.
•Because
ldapmodify if you want to remove an attribute from an entry.
ldapdelete is used for deleting an entire entry, you should use
Configuration Changes Requiring Server Restar t
Some configuration attributes cannot be altered dynamically while the server is
running. In these cases, for the changes to take effect, the server needs to be shut
down and restarted. The modifications should be made either through the
Directory Server Console or by manually editing the
dse.ldif file. Table 2-4 under
“Configuration Quick Reference Tables” at the end of this chapter contains a list of
these attributes.
Core Server Configuration Attributes Reference
This section contains reference information on the configuration attributes that are
relevant to the core server functionality. For information on cha nging server
configuration, see “Accessing and Modify ing Server Configuration” on page 32.
For a list of server features that are implemented as plug-ins, see Table 2-1 in the
section “Configuration Quick Reference Tables” on page 120. For implementing
your own server functionality, contact Netscape Professional Services.
The configuration information which is stored in the
dse.ldif file is organized
as an information tree under the general conf iguration entry
shown in Figure 2-2.
Chapter 2 Core Server Configuration Reference 35
cn=config as
Page 36

Core Server Configuration Attributes Reference
Figure 2-2 Directory Information Tree Showing Configuration Data
The list of configuration tree nodes covered in this section is as follows:
•cn=config
• cn=changelog5
•cn=encryption
•cn=features
• cn=mapping tree
• cn=monitor
• cn=replication
•cn=SNMP
•cn=tasks
• cn=uniq ueid genera tor
cn=plugins node is covered in the “Configuration Quick Reference Tables” on
The
page 120” section. The attributes are listed alphabetically, and the description of
each attribute contains details such as the DN of its directory entry, its default
value, the valid range of values, and an example of its use.
NOTE Some of the entries and attributes described in this chapter may
change in future releases of the product.
36 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 37

Core Server Configuration Attributes Reference
cn=config
General configuration entries are stored under the cn=config entry. The
cn=config entry is an instance of the nsslapdConfig object class, which in turn
inherits from
account by the server, both of these object classes (in additio n to th e
class) must be present in the entry. General configuration entries are presented in
this section.
nsslapd-accesscontrol (Enable Access Control)
Turns access control on and off. If this a ttribute has a value off, then any valid
bind attempt (including an anonymous bind) results in full access to all
information stored in the Directory Server.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-accesscontrol: off
extensibleObject object class. For attributes to be taken into
top object
nsslapd-accesslog (Access Log)
Specifies the path and filename of the log used to record each database access. The
following information is recorded by default in the log file:
• IP address of the client machine that accessed the database
• Operations performed (for example, search, add, modify)
• Result of the access (for example, the number of entries returned)
For more information on turning access logging off, see Chapter 12, “Monitoring
Server and Database Activity” in the Netscape Direct ory Ser ver Ad ministrat or’s
Guide.
For access logging to be enabled, this attribute must have a valid path and filename
and the
switched to
these two configuration attributes and their outcome in terms of disabling or
enabling of access logging.
nsslapd-accesslog-logging-enabled configuration attribute must be
on. The table below lists the four possible combinations of values for
Chapter 2 Core Server Configuration Reference 37
Page 38

Core Server Configuration Attributes Reference
Attributes in dse.ldif Value Logging enabled or
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
on
empty string
on
filename
off
empty string
off
filename
disabled
Disabled
Enabled
Disabled
Disabled
Entry DN: cn=config
Valid Values: Any valid filename.
Default Value: serverRoot/slapd-serverID/logs/access
Syntax: DirectoryString
Example: nsslapd-accesslog:
/usr/netscape/servers/slapd-phonebook/logs/access
nsslapd-accesslog-level
Controls what is logged to the access log.
Entry DN: cn=config
Valid Values: 0—No access logging
4—Logging for internal access operations
256—Logging for access to an entry
512—Logging for access to an entry and referrals
These values can be added tog ether to provid e you wi th t he exact t ype
of logging you require, for example 516 (4 + 512) to obtain internal
access operation, entry access, and referral logging.
38 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 39

Core Server Configuration Attributes Reference
Default Value: 256
Syntax: Integer
Example: nsslapd-accesslog-level: 256
nsslapd-accesslog-list
This read-only attribute, which cannot be set, provides a list of access log files
used in access log rotation.
Entry DN: cn=config
Valid Values: N/A
Default Value: None
Syntax: DirectoryString
Example: nsslapd-accesslog-list:accesslog2,accesslog3
nsslapd-accesslog-logbuffering (Log Buffering)
When set to off, the server writes all access log entries directly to disk.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-accesslog-logbuffering: off
nsslapd-accesslog-logexpirationtime (Access Log E xpiration Time)
Specifies the maximum age that a log file is allowed to reach before it is deleted.
This attribute supplies only the number of units. The units are provided by the
nsslapd-accesslog-logexpirationtimeunit attribute.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Chapter 2 Core Server Configuration Reference 39
Page 40

Core Server Configuration Attributes Reference
Default Value: 1
Syntax: Integer
Example: nsslapd-accesslog-logexpirationtime: 2
nsslapd-accesslog-logexpirationtimeunit (Access Log Expiration Time Unit)
Specifies the units for nsslapd-accesslog-logexpirationtime attribute. If the
unit is unknown by the server, then the log wi ll never expire.
Entry DN: cn=config
Valid Values: month | week | day
Default Value: month
Syntax: DirectoryString
Example: nsslapd-accesslog-logexpirationtimeunit: week
nsslapd-accesslog-logging-enabled (Access Log Enable Logging)
Disables and enables accesslog logging but only in conjunction with the
nsslapd-accesslog attribute that specifies the path and filename of the log used
to record each database access.
For access logging to be enabled this attrib ute must be switched to
nsslapd-accesslog configuration attribute must have a valid path and filename.
The table below lists the four possible combinations of values for these two
configuration attributes and their outcom e in terms of disabling or enabling of
access logging.
Attributes in dse.ldif Value Logging Enabled or Di sa bled
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
40 Netscape Directory Server Configuration, Command, and File Reference • December 2003
on
empty string
on
filename
off
empty string
on and the
Disabled
Enabled
Disabled
Page 41

Core Server Configuration Attributes Reference
Attributes in dse.ldif Value Logging Enabled or Di sa bled
nsslapd-accesslog-logging-enabled
nsslapd-accesslog
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-accesslog-logging-enabled: off
off
filename
Disabled
nsslapd-accesslog-logmaxdiskspace (Access Log Maximum Disk Space)
Specifies the maximum amount of disk space in megabytes that the access logs are
allowed to consume. If this value is exceeded, the oldest access log is deleted.
When setting a maximum disk space, consider the total number of log files tha t can
be created due to log file rotation. Also remember that ther e a re 3 diff erent log files
(access log, audit log, and error log) maintained by the Directory Server, each of
which will consume disk space. Compa r e these considerations to the total
amount of disk space that you want to be used by the access log.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647)
Default Value: 500 (A value of -1 means that the disk space allowed to the access log
is unlimited in size).
Syntax: Integer
Example: nsslapd-accesslog-logmaxdiskspace: 200
Chapter 2 Core Server Configuration Reference 41
Page 42

Core Server Configuration Attributes Reference
nsslapd-accesslog-logminfreediskspace (Access Log Minimum Free Disk Space)
Specifies the minimum allowed free disk space in megabytes. When the amount of
free disk space falls below the value specified on this attribute, the oldest access log
is deleted until enough disk space is freed to satis fy this attribute.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 5
Syntax: Integer
Example: nsslapd-accesslog-logminfreediskspace: 4
nsslapd-accesslog-logrotationsync-enabled (Access Log Rotation Sync Enabled)
Specifies whether access log rotation is to be synchronized with a particular time of
the day. Synchronizing log rotation this way enables you to generate log files at a
specified time during a day, say midnigh t to midnight everyday, making analysis
of the log files much easier because they then map directly to the calendar.
For access log rotation to be synchronized with time-of-day, this attribute must be
enabled with the
nsslapd-accesslog-logrotationsyncmin attribute values set to the hour and
nsslapd-accesslog-logrotationsynchour and
minute of the day for rotating log files.
For example, to rotate access log files everyday at midnight, enable this attribute by
setting its value to
nsslapd-accesslog-logrotationsynchour and
nsslapd-accesslog-logrotationsyncmin attributes to 0.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-accesslog-logrotationsync-enabled: on
42 Netscape Directory Server Configuration, Command, and File Reference • December 2003
on and then set the values of the
Page 43

Core Server Configuration Attributes Reference
nsslapd-accesslog-logrotationsynchour (Access Log Rotation Sync Hour)
Specifies the hour of the day for rotating access logs. This attribute must be used in
conjunction with
nsslapd-accesslog-logrotationsyncmin attributes.
Entry DN: cn=config
Valid Range: 0 through 23
Default Value: 0
Syntax: Integer
Example: nsslapd-accesslog-logrotationsynchour: 23
nsslapd-accesslog-logrotationsync-enabled and
nsslapd-accesslog-logrotationsyncmin (Access Log Rotation Sync Minute)
Specifies the minute of the day for rotating access logs. This attribute must be used
in conjunction with
nsslapd-accesslog-logrotationsynchour attributes.
nsslapd-accesslog-logrotationsync-enabled and
Entry DN: cn=config
Valid Range: 0 through 59
Default Value: 0
Syntax: Integer
Example: nsslapd-accesslog-logrotationsyncmin: 30
nsslapd-accesslog-logrotationtime (Access Log Rotation Time)
Specifies the time between access log file rotations. The access log will be rotated
when this time interval is up, regardless of the current size of the access log. This
attribute supplies only the number of units. The units (day, week, month, and so
forth) are given by the
Although it is not recommended for performance reasons to specify no log rotation
as the log will grow indefinitely, you have two ways of specifying this. Eith er y ou
set the
nsslapd-accesslog-logrotationtime attribute to -1. The server checks the
nsslapd-accesslog-maxlogsperdir attribute value to 1 or the
nsslapd-accesslog-logrotationtimeunit attribute.
Chapter 2 Core Server Configuration Reference 43
Page 44

Core Server Configuration Attributes Reference
nsslapd-accesslog-maxlogsperdir attribute first and if this attribute value is
larger than 1, the server then checks the
attribute. See “nsslapd-accesslog-maxlogsperdir (Access Log Maximum Number of
Log Files)” on page 45 for more information.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
Default Value: 1
Syntax: Integer
Example: nsslapd-accesslog-logrotationtime: 100
nsslapd-accesslog-logrotationtimeunit (Access Log Rotation Time Unit)
Specifies the units for the nsslapd-accesslog-logrotationtime attribute.
Entry DN: cn=config
Valid Values: month | week | day | hour | minute
nsslapd-accesslog-logrotationtime
of -1 means that the time between access log file rotat ion is unlim it ed.
Default Value: day
Syntax: DirectoryString
Example: nsslapd-accesslog-logrotationtimeunit: week
nsslapd-accesslog-maxlogsize (Access Log Maximum Log Size)
Specifies the maximum access log size in megabytes. When this value is reached,
the access log is rotated. That is, the server starts writing log information to a new
log file. If you set
ignores this attribute.
When setting a maximum log size, consider the total number of log files that can be
created due to log file rotation. Also remember that there are 3 different log files
(access log, audit log, and error log) maintained by the Directory Server, each of
which will consume disk space. Compar e these co nsiderations to the total
amount of disk space that you want to be used by the access log.
44 Netscape Directory Server Configuration, Command, and File Reference • December 2003
nsslapd-accesslog-maxlogsperdir attribute to 1, the server
Page 45

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
of -1 means the log file is unlimited in size.
Default Value: 100
Syntax: Integer
Example: nsslapd-accesslog-maxlogsize: 100
nsslapd-accesslog-maxlogsperdir (Access Log Maximum Number of Log Files)
Specifies the total number of access logs that can be contained in the directory
where the access log is stored. If you are using log file rotation, then each time the
access log is rotated, a new log file is creat ed. When the number of files contained
in the access log directory exceeds the value stored on this attribute, then the oldest
version of the log file is deleted. For performance reas ons it is not recommended
that you set this value to 1, as the server will not rotate the log and it will grow
indefinitely.
If the value for this attribute is higher than 1, then you need to check the
nsslapd-accesslog-logrotationtime attribute to establish whether or not log
rotation is specified. If the
nsslapd-accesslog-logrotationtime attribute has a
value of -1 then there is no log rotation. See “nsslapd -accesslog-logrotationtime
(Access Log Rotation Time)” on page 43 for more information.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 10
Syntax: Integer
Example: nsslapd-accesslog-maxlogsperdir: 10
Chapter 2 Core Server Configuration Reference 45
Page 46

Core Server Configuration Attributes Reference
nsslapd-accesslog-mode (Access Log File Permission)
Specifies the access mode or file permission with which access log files are to be
created. The valid values are any combination of 000 to 777, as they mirror
numbered or absolute UNIX file permissions. That is, the value must be a
combination of a 3-digit number, the digits varying from 0 through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the
second digit represents the group’s permissions, and the third digit represen ts
everyone’s permissions. When changing the default value, keep in mind that
000 will not allow access to the logs and allowing write permissions to everyone
can result in the logs being overwritten or deleted by anyone.
Note that the newly configured access m ode will only affect new logs that are
created; the mode will be set when the log rotates to a new file.
Entry DN: cn=config
Valid Range: 000 through 777
Default Value: 600
Syntax: Integer
Example: nsslapd-accesslog-mode: 600
nsslapd-attribute-name-exceptions
Allows non-standard characters in attribute names to be used for backwards
compatibility with older servers.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
46 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 47

Core Server Configuration Attributes Reference
Example: nsslapd-attribute-name-exceptions: on
nsslapd-auditlog (Audit Log)
Specifies the pathname and filename of the log used to record changes made to
each database.
Entry DN: cn=config
Valid Values: Any valid filename
Default Value: serverRoot/slapd-serverID/logs/audit
Syntax: DirectoryString
Example: nsslapd-auditlog:
/usr/netscape/servers/slapd-phonebook/logs/audit
For audit logging to be enabled this attribute must have a valid path and file name
and the
switched to
these two configuration attributes and their outcome in terms of disabling or
enabling of audit logging.
nsslapd-auditlog-logging-enabled configuration attribute must be
on. The table below lists the four possible combinations of values for
Attributes in dse.ldif Value Logging enabled or disa bled
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
on
empty string
on
filename
off
empty string
off
filename
Disabled
Enabled
Disabled
Disabled
nsslapd-auditlog-list
Provides a list of audit log files.
Chapter 2 Core Server Configuration Reference 47
Page 48

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Values: N/A
Default Value: None
Syntax: DirectoryString
Example: nsslapd-auditlog-list: auditlog2,auditlog3
nsslapd-auditlog-logexpirationtime (Audit Log Expiration Time)
Specifies the maximum age that a log f ile is allowed to be before it is deleted. This
attribute supplies only the number of units. The units (day, week, month, and so
forth) are given by the
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 1
Syntax: Integer
Example: nsslapd-auditlog-logexpirationtime: 1
nsslapd-auditlog-logexpirationtimeunit attribute.
nsslapd-auditlog-logexpirationtimeunit (Audit Log Expiration Time Unit)
Specifies t he uni ts fo r t he nsslapd-auditlog-logexpirationtime attribute. If the
unit is unknown by the server, then the log wi ll never expire.
Entry DN: cn=config
Valid Values: month | week | day
Default Value: week
Syntax: DirectoryString
Example: nsslapd-auditlog-logexpirationtimeunit: day
nsslapd-auditlog-logging-enabled (Audit Log Enable Logging)
Turns audit logging on and off.
48 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 49

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-auditlog-logging-enabled: off
For audit logging to be enabled this attribute must have a valid path and file name
and the
switched to
nsslapd-auditlog-logging-enabled configuration attribute must be
on. The table below lists the four possible combinations of values for
these two configuration attributes and their outcome in terms of disabling or
enabling of audit logging.
Attributes in dse.ldif Value Logging enabled or disa bled
nsslapd-auditlog-logging-enabled
on
Disabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
nsslapd-auditlog-logging-enabled
nsslapd-auditlog
empty string
on
filename
off
empty string
off
filename
Enabled
Disabled
Disabled
nsslapd-auditlog-logmaxdiskspace (Audit Log Maximum Disk Space)
Specifies the maximum amount of disk space in megabytes that the audit logs are
allowed to consume. If this value is exceeded, the oldest audit log is deleted.
When setting a maximum disk space, consider the total number of log files tha t can
be created due to log file rotation. Also remember that there are three different log
files (access log, audit log, and error log) maintained by the Directory S e rver,
each of which will consume disk space. Com p are these considerations with the
total amount of disk space that you want to be used by the audit log.
Chapter 2 Core Server Configuration Reference 49
Page 50

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
Default Value: 500
Syntax: Integer
Example: nsslapd-auditlog-logmaxdiskspace: 500
nsslapd-auditlog-logminfreediskspace (Audit Log Mini mum Free Disk Space)
Specifies the minimum permissible free disk space in megabytes. When the
amount of free disk space falls below the value specified on this attribute, the
oldest audit log is deleted until enough disk space is freed to satisfy this attribute.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 5
of -1 means that t he di sk s p ace a llow e d t o t he a udit log is u nl im ited in
size.
Syntax: Integer
Example: nsslapd-auditlog-logminfreediskspace: 3
nsslapd-auditlog-logrotationsync-enabled (Audit Log Rotation Sync Enabled)
Specifies whether audit log rotation is to be synchronized with a particular time of
the day. Synchronizing log rotation this way enables you to generate log files at a
specified time during a day, say midnigh t to midnight everyday, making analysis
of the log files much easier because they then map directly to the calendar.
For audit log rotation to be synchronized with time-of-day, this attribute must be
enabled with the
nsslapd-auditlog-logrotationsyncmin attribute values set to the hour and
minute of the day for rotating log files.
50 Netscape Directory Server Configuration, Command, and File Reference • December 2003
nsslapd-auditlog-logrotationsynchour and
Page 51

Core Server Configuration Attributes Reference
For example, to rotate audit log files everyday at midnight, enable this attribute by
setting its value to
nsslapd-auditlog-logrotationsynchour and
nsslapd-auditlog-logrotationsyncmin attributes to 0.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-auditlog-logrotationsync-enabled: on
on and then set the values of the
nsslapd-audit l og-logrotationsynchour (Audit Log Rotation Sync Hour)
Specifies the hour of the day for rotating audit logs. This attribute must be used in
conjunction with
nsslapd-auditlog-logrotationsyncmin attributes.
Entry DN: cn=config
nsslapd-auditlog-logrotationsync-enabled and
Valid Range: 0 through 23
Default Value: None (because nsslapd-auditlog-logrotationsync-enabled
is off)
Syntax: Integer
Example: nsslapd-auditlog-logrotationsynchour: 23
nsslapd-audit l og-logrotationsyncmin (Audit Log Rotation Sync Minute)
Specifies the minute of the day for rotating audit logs. This attribute must be used
in conjunction with
nsslapd-auditlog-logrotationsynchour attributes.
Entry DN: cn=config
Valid Range: 0 through 59
Default Value: None (because nsslapd-auditlog-logrotationsync-enabled
nsslapd-auditlog-logrotationsync-enabled and
is off)
Chapter 2 Core Server Configuration Reference 51
Page 52

Core Server Configuration Attributes Reference
Syntax: Integer
Example: nsslapd-auditlog-logrotationsyncmin: 30
nsslapd-auditlog-logrotationtime (Audit Log Rotation Time)
Specifies the time between audit log file rotations. The audit log will be rotated
when this time interval is up, regardless of the current size of the audit log. This
attribute supplies only the number of units. The units (day, week, month, and so
forth) are given by the
set the
attribute.
Although it is not recommended for performance reasons to specify no log rotation
as the log will grow indefinitely, you have two ways of specifyin g this. Either you
set the
nsslapd-auditlog-logrotationtime attribute to -1. The server checks the
nsslapd-auditlog-maxlogsperdir attribute first and if this attribute value is
larger than 1, the server then checks the
attribute. See “nsslapd-auditlog-maxlogsperd ir (Audit Log Maximum Number of
Log Files)” on page 53 for more information.
nsslapd-auditlog-maxlogsperdir attribute to 1, the server ignores this
nsslapd-auditlog-maxlogsperdir attribute value to 1 or the
nsslapd-auditlog-logrotationtimeunit attribute. If you
nsslapd-auditlog-logrotationtime
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
of -1 means that the time between audit log file rotation is unlimited.
Default Value: 1
Syntax: Integer
Example: nsslapd-auditlog-logrotationtime: 100
nsslapd-auditlog-logrotationtimeunit (Audit Log Rotation Time Unit)
Specifies the units for the nsslapd-auditlog-logrotationtime attribute.
Entry DN: cn=config
Valid Values: month | week | day | hour | minute
Default Value: week
Syntax: DirectoryString
52 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 53

Core Server Configuration Attributes Reference
Example: nsslapd-auditlog-logrotationtimeunit: day
nsslapd-auditlog-maxlogsize (Audit Log Maximum Log Size)
Specifies the m aximu m aud it lo g si ze in megab ytes. When this va lue is reac hed, the
audit log is rotated. That is, the server starts writing log information to a new log
file. If you set
attribute.
When setting a maximum log size, consider the total number of log files that can be
created due to log file rotation. Also remember that there are 3 different log files
(access log, audit log, and error log) maintained by the Directory Server, each of
which will consume disk space. Compa r e these considerations to the total
amount of disk space that you want to be used by the audit log.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
Default Value: 100
nsslapd-auditlog-maxlogsperdir to 1, the server ignores this
of -1 means the log file is unlimited in size.
Syntax: Integer
Example: nsslapd-auditlog-maxlogsize: 50
nsslapd-audit log-maxlogsperdir (Audit Log Max imum Number of Log Files)
Specifies the total number of audit logs that can be contained in the directory
where the audit log is stored. If you are using log file rotation, then each time the
audit log is rotated, a new log file is created. When the number of files contained in
the audit log directory exceeds the value stored on this attribute, then the oldest
version of the log file is deleted. The default is 1 log. If yo u accept this default, the
server will not rotate the log and it will grow indefinitely.
If the value for this attribute is higher than 1, then you need to check the
nsslapd-auditlog-logrotationtime attribute to establish whether or not log
rotation is specified. If the
value of -1 then there is no log rotation. See “nsslapd-auditlog-logrotationtime
(Audit Log Rotation Time)” on page 52 for more information.
Entry DN: cn=config
nsslapd-auditlog-logrotationtime attribute has a
Chapter 2 Core Server Configuration Reference 53
Page 54

Core Server Configuration Attributes Reference
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 1
Syntax: Integer
Example: nsslapd-auditlog-maxlogsperdir: 10
nsslapd-auditlog-mode (Audit Log File Permission)
Specifies the access mode or file permissions with which audit log files are to be
created. The valid values are any combination of 000 to 777, as they mirror
numbered or absolute UNIX file permissions. That is, the value must be a
combination of a 3-digit number, the digits varying from 0 through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the
second digit represents the group’s permissions, and the third digit represen ts
everyone’s permissions. When changing the default value, keep in mind that
000 will not allow access to the logs and allowing write permissions to everyone
can result in the logs being overwritten or deleted by anyone.
Note that the newly configured access m ode will only affect new logs that are
created; the mode will be set when the log rotates to a new file.
Entry DN: cn=config
Valid Range: 000 through 777
Default Value: 600
Syntax: Integer
Example: nsslapd-auditlog-mode: 600
54 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 55

Core Server Configuration Attributes Reference
nsslapd-certmap-basedn (Certificate Map Search Base)
This attribute can be used when client authentication is performed using SSL
certificates in order to avoid limitation of the security subsystem certificate
mapping, configured in the
certmap.conf file. Depending on the certmap.conf
configuration, the certificate mapping may be done using a directory subtree
search based at the root DN. Note that if the search is based at the root DN, then the
nsslapd-certmap-basedn attribute may force the search to be based at some entry
other than the root. For further information see Chapter 11, “Ma naging SSL” in the
Netscape Directory Server Administrator’s Guide.
nsslapd-config
This read-only attribute is the config DN.
Entry DN: cn=config
Valid Values: Any valid config DN.
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-config:cn=config
nsslapd-conntablesize
Specifies the connection table size, which determines the total number of
connections supported by the server.
Entry DN: cn=config
Valid Values: Operating-system dependant
Default Value: On Windows 2000, the default value is 4093, a prime number to
hash into the table.
On UNIX, the default value is the system’s max descriptors, which
can be configured using the nsslapd-maxdescriptors (Maximum
File Descriptors) attribute.
Syntax: Integer
Example: nsslapd-ntconntablesize: 4093
Chapter 2 Core Server Configuration Reference 55
Page 56

Core Server Configuration Attributes Reference
Consider increasing the value of this attribute if Directory Server is refusing
connections because it is out of connection slots. W hen th is occurs, the
following message is written to the Directory Server’s error lo g file:
listening for new connections -- too many fds open
A server restart is required for the change to take effect.
nsslapd-csnlogging
Specifies whether change sequence numbers (CSNs), when available, are to be
logged in the access log. By default, CSN logging is turned on.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-csnlogging:on
Not
.
nsslapd-ds4-compatible-schema
Makes the schema in cn=schema compatible with 4.x versions of Directory
Server.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-ds4-compatible-schema: off
nsslapd-enquote-sup-oc (Enable Superior Object Class Enquoting)
Controls whether quoting in the objectclasses attributes contained in the
cn=schema entry will conform to the quoting specified by internet draft RFC 2252.
By default, the Directory Server places single quotes around the superior object
class identified on the
2252 indicates that this value should not be quoted.
56 Netscape Directory Server Configuration, Command, and File Reference • December 2003
objectclasses attributes contained in cn=schema. RFC
Page 57

Core Server Configuration Attributes Reference
That is, the Directory Server publishes objectclasses attributes in the
cn=schema entry as follows:
objectclasses: ( 2.5.6.6 NAME ’person’ DESC ’Standard ObjectClass’
SUP ’top’ MUST ( objectclass $ sn $ cn ) MAY ( aci $ description $
seealso $ telephonenumber $ userpassword ) )
However, RFC 2252 indicates that this attribute should be published as follows:
objectclasses: ( 2.5.6.6 NAME ’person’ DESC ’Standard ObjectClass’
SUP top MUST ( objectclass $ sn $ cn ) MAY ( aci $ description $
seealso $ telephonenumber $ userpassword ) )
Notice the absence of single quotes around the word top.
Turning this attribute on will cause the Directory Server Resource Kit LDAP clients
to no longer function, as they require the schema as defined in RF C 2252.
Turning this attribute off causes the Directory S e rver to conform to RFC 2252,
but doing so may interfere with some earlier LDAP clients. Specifically, any
client written using the Netscape Java LDAP SDK 4.x will no longer be able to
correctly read and modify schema. This includes the 4.x version of the Netscape
Console. Please note that turning this attribute on or off does not affect versions
6.x of Netscape Console.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-enquote-sup-oc: off
nsslapd-errorlog (Error Log)
Specifies the pathname and filename of the log used to record error messages
generated by the Directory Server. These messages can describe error
conditions, but more often they will contain informative conditions such as
these:
• Server startup and shutdown times
• Port number the server uses
Chapter 2 Core Server Configuration Reference 57
Page 58

Core Server Configuration Attributes Reference
This log will contain dif ferin g amounts of information depending on the current
setting of the Log Level attribute. See “nsslapd-errorlog-level (Error Log Level)” on
page 58 for more information.
Entry DN: cn=config
Valid Values: Any valid filename
Default Value: serverRoot/slapd-serverID/logs/error
Syntax: DirectoryString
Example: nsslapd-errorlog:
For error logging to be enabled this attribute must have a valid path and filename
and the
switched to
nsslapd-errorlog-logging-enabled configuration attribute must be
on. The table below lists the four possible combinations of values for
these two configuration attributes and their outco me in terms of disabling or
enabling of error logging.
/usr/netscape/servers/slapd-phonebook/logs/error
Attributes in dse.ldif Value Logging enabled or disa bled
nsslapd-errorlog-logging-enabled
nsslapd-errorlog
nsslapd-errorlog-logging-enabled
nsslapd-errorlog
nsslapd-errorlog-logging-enabled
nsslapd-errorlog
nsslapd-errorlog-logging-enabled
nsslapd-errorlog
on
empty string
on
filename
off
empty string
off
filename
nsslapd-errorl og-level (Error Log Level)
Specifies the level of logging to be used by the Directory Server. The log level is
additive; that is, specifying a value of 3 causes both levels 1 and 2 to be
performed.
58 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Disabled
Enabled
Disabled
Disabled
Page 59

Core Server Configuration Attributes Reference
To turn logging off, remove the nsslapd-errorlog-level attribute from
dse.ldif and restart the Directory Server.
Entry DN: cn=config
Valid Values: 1 = Trace function calls. Logs a message when the server enters and
exits a function.
2 = Debug Packet handling
4 = Heavy trace output debugging
8 = Connection management
16 = Print out packets sent/received
32 = Search filter processing
64 = Config file processing
128 = Access control list processing
2048 = Log entry parsing debugging
4096 = Housekeeping thread debugging
8192 = Replication debugging
16384 = Default level of logging used for critical errors and other
messages that are always written to the error log, for example server
startup messages. Messages at this level are always included in the
error log regardless of the log level setting.
32768 = Database cache debugging.
65536 = Server plug-in debugging. It writes an entry to the log file
when a server plug-in calls slapi-log-error.
Default Value: Logging is turned off (the nsslapd-errorlog-level attribute is
not included in the dse.ldif file).
Syntax: Integer
Example: nsslapd-errorlog-level: 8192
nsslapd-errorlog-list
This read-only attribute provides a list of error log files.
Entry DN: cn=config
Valid Values: N/A
Chapter 2 Core Server Configuration Reference 59
Page 60

Core Server Configuration Attributes Reference
Default Value: None
Syntax: DirectoryString
Example: nsslapd-errorlog-list:errorlog2,errorlog3
nsslapd-error lo g- lo g expi rationtime (Error Log Expiration Time)
Specifies the maximum age that a log file is allowed to reach before it is deleted.
This attribute supplies only the number of units. The units (day, week, month, and
so forth) are given by the
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 1
Syntax: Integer
Example: nsslapd-errorlog-logexpirationtime: 1
nsslapd-errorlog-logexpirationtimeunit attribute.
nsslapd-errorlog-logexpirationtimeunit (Error Log Expiration Time Unit)
Specifies t he uni ts fo r t he nsslapd-errorlog-logexpirationtime attribute. If the
unit is unknown by the server, then the log wi ll never expire.
Entry DN: cn=config
Valid Values: month | week | day
Default Value: month
Syntax: DirectoryString
Example: nsslapd-errorlog-logexpirationtimeunit: week
nsslapd-errorl og-logging-enabled (Enable Error Logging)
Turns error logging on and off.
Entry DN: cn=config
60 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 61

Core Server Configuration Attributes Reference
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-errorlog-logging-enabled: on
nsslapd-errorlog-logmaxdiskspace (Error Log Maximum Disk Space)
Specifies the maximum am ount of disk space in megabytes that the error logs are
allowed to consume. If this value is exceeded, the oldest error log is deleted.
When setting a maximum disk space, consider the total number of log files tha t can
be created due to log file rotation. Also remember that ther e a re 3 diff erent log files
(access log, audit log, and error log) maintained by the Directory Server, each of
which will consume disk space. Compa r e these considerations to the total
amount of disk space that you want to be used by the error log.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
of -1 means that the disk space allowed to the error log is unlimited in
size.
Default Value: 500
Syntax: Integer
Example: nsslapd-errorlog-logmaxdiskspace: 500
nsslapd-errorlog-logminfreediskspace (Error Log Minimum Free Disk Space)
Specifies the minimum allowed free disk space in megabytes. When the amount of
free disk space falls below the value specified on this attribute, the oldest error log
is deleted until enough disk space is freed to satisfy this attribute.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 5
Syntax: Integer
Chapter 2 Core Server Configuration Reference 61
Page 62

Core Server Configuration Attributes Reference
Example: nsslapd-errorlog-logminfreediskspace: 5
nsslapd-errorlog-logrotationsync-enabled (Error Log Rotation Sync Enabled)
Specifies whether error log rotation is to be synchroniz ed with a particular time of
the day. Synchronizing log rotation this way enables you to generate log files at a
specified time during a day, say midnigh t to midnight everyday, making analysis
of the log files much easier because they then map directly to the calendar.
For error log rotation to be synchronized with time-of-day, this attribute must be
enabled with the
nsslapd-errorlog-logrotationsyncmin attribute values set to the hour and
minute of the day for rotating log files.
For example, to rotate error log files everyday at midnight, enable this attribute by
setting its value to
nsslapd-errorlog-logrotationsynchour and
nsslapd-errorlog-logrotationsyncmin attributes to 0.
Entry DN: cn=config
nsslapd-errorlog-logrotationsynchour and
on and then set the values of the
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-errorlog-logrotationsync-enabled: on
nsslapd-errorlog-logrotationsynchour (Error Log Rotation Sync Hour)
Specifies the hour of the day for rotating error logs. This attribute m ust be used in
conjunction with
nsslapd-errorlog-logrotationsyncmin attributes.
Entry DN: cn=config
Valid Range: 0 through 23
Default Value: 0
Syntax: Integer
Example: nsslapd-errorlog-logrotationsynchour: 23
62 Netscape Directory Server Configuration, Command, and File Reference • December 2003
nsslapd-errorlog-logrotationsync-enabled and
Page 63

Core Server Configuration Attributes Reference
nsslapd-errorlog-logrotationsyncmin (E rror Log Rotation Sync Minute)
Specifies the minute of the day for rotating error logs. This attribute must be used
in conjunction with
nsslapd-errorlog-logrotationsynchour attributes.
Entry DN: cn=config
Valid Range: 0 through 59
Default Value: 0
Syntax: Integer
Example: nsslapd-errorlog-logrotationsyncmin: 30
nsslapd-errorlog-logrotationsync-enabled and
nsslapd-errorlog-logrotationtime (Error Log Rotation Time)
Specifies the time between error log file rotations. The error log will be rotated
when this time interval is up, regardless of the current size of the error log. This
attribute supplies only the number of units. The units (day, week, month, and so
forth) are given by the
Rotation Time Unit) attribute.
nsslapd-errorlog-logrotationtimeunit (Error Log
Although it is not recommended for performance reasons to specify no log rotation
as the log will grow indefinitely, you have two ways of specifying this. Eith er y ou
set the
nsslapd-errorlog-logrotationtime attribute to -1. The server checks the
nsslapd-errorlog-maxlogsperdir attribute first and if this attribute value is
larger than 1, the server then checks the
nsslapd-errorlog-maxlogsperdir attribute value to 1 or the
nsslapd-errorlog-logrotationtime
attribute. See “nsslapd-errorlog-maxlogsperdir (Maximum Number of Error Log
Files)” on page 65 for more information.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
of -1 means that the time between error log file rotation is unlimited).
Default Value: 1
Syntax: Integer
Example: nsslapd-errorlog-logrotationtime: 100
Chapter 2 Core Server Configuration Reference 63
Page 64

Core Server Configuration Attributes Reference
nsslapd-errorl og-logrotationtime (Error Log Rotation Time)
Specifies the time between error log file rotations. The error log will be rotated
when this time interval is up, regardless of the current size of the error log. This
attribute supplies only the number of units. The units (day, week, month, and so
forth) are given by the
Rotation Time Unit) attribute.
Although it is not recommended for performance reasons to specify no log rotation
as the log will grow indefinitely, you have two ways of specifying this. Either you
set the
nsslapd-errorlog-logrotationtime attribute to -1. The server checks the
nsslapd-errorlog-maxlogsperdir attribute first and if this attribute value is
larger than 1, the server then checks the
attribute. See “nsslapd-errorlog-maxlogsperdir (Maximum Number of Error Log
Files)” on page 65 for more information.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
Default Value: 1
nsslapd-errorlog-maxlogsperdir attribute value to 1 or the
nsslapd-errorlog-logrotationtimeunit (Error Log
nsslapd-errorlog-logrotationtime
of -1 means that the time between error log file rotation is unlimited).
Syntax: Integer
Example: nsslapd-errorlog-logrotationtime: 100
nsslapd-errorlog-logrotationtimeunit (Error Log Rotation Time Unit)
Specifies the units for nsslapd-errorlog-logrotationtime (Error Log Rotation
Time). If the unit is unknown by the server, then the log w ill never expire.
Entry DN: cn=config
Valid Values: month | week | day | hour | minute
Default Value: week
Syntax: DirectoryString
Example: nsslapd-errorlog-logrotationtimeunit: day
64 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 65

Core Server Configuration Attributes Reference
nsslapd-errorlog-maxlogsize (Maximum Error Log Size)
Specifies the maximum error log size in megabytes. When this value is rea ched, the
error log is rotated. That is, the server starts wr iting log information to a new log
file. If you set
attribute.
When setting a maximum log size, consider the total number of log files that can be
created due to log file rotation. Also remember that there are 3 different log files
(access log, audit log, and error log) maintained by the Directory Server, each of
which will consume disk space. Compa r e these considerations to the total
amount of disk space that you want to be used by the error log.
Entry DN: cn=config
Valid Range: -1 | 1 to the maximum 32 bit integer value (2147483647) where a value
Default Value: 100
Syntax: Integer
Example: nsslapd-errorlog-maxlogsize: 100
nsslapd-errorlog-maxlogsperdir to 1, the server ignores this
of -1 means the log file is unlimited in size.
nsslapd-errorlog-maxlogsperdir (Maximum Num ber of Error Log Files)
Specifies the total number of error logs that can be contained in the directory where
the error log is stored. If you are using log file rotation, then each time the error log
is rotated, a new log file is created. When the number of files contained in the error
log directory exceeds the value stored on this attribute, then the oldest version of
the log file is deleted. The default is
not rotate the log and it will grow indefinitely.
If the value for this attribute is higher than 1, then you need to check the
nsslapd-errorlog-logrotationtime attribute to establish whether or not log
rotation is specified. If the
nsslapd-errorlog-logrotationtime attribute has a
value of -1 then there is no log rotation. See “nsslapd-errorlog-logrotationtime
(Error Log Rotation Time)” on page 64 for more information.
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647)
Default Value: 1
1 log. If you accept this default, the server will
Chapter 2 Core Server Configuration Reference 65
Page 66

Core Server Configuration Attributes Reference
Syntax: Integer
Example: nsslapd-errorlog-maxlogsperdir: 10
nsslapd-errorlog-mode (Error Log File Permission)
Specifies the access mode or file permissions with which error log files are to be
created. The valid values are any combination of 000 to 777, as they mirror
numbered or absolute UNIX file permissions. That is, the value must be a
combination of a 3-digit number, the digits varying from 0 through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit represents the owner’s permissions, the
second digit represents the group’s permissions, and the third digit represen ts
everyone’s permissions. When changing the default value, keep in mind that
000 will not allow access to the logs and allowing write permissions to everyone
can result in the logs being overwritten or deleted by anyone.
Note that the newly configured access m ode will only affect new logs that are
created; the mode will be set when the log rotates to a new file.
Entry DN: cn=config
Valid Range: 000 through 777
Default Value: 600
Syntax: Integer
Example: nsslapd-errorlog-mode: 600
nsslapd-groupevalnestlevel
Specifies the number of levels of nesting that the access-control system will
perform for group evaluation.
66 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 67

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Range: 0 to 5
Default Value: 5
Syntax: Integer
Example: nsslapd-groupevalnestlevel:5
nsslapd-idletimeout (Default Idle Timeout)
Specifies the amount of time in seconds after which an idle LDAP client connection
is closed by the server. A value of 0 indicates that the server will never close idle
connections. You can use the
added to user entries, to override the value assigned to this attribute. For details,
see “Setting Resource Limits Based on the Bind DN” in the Netsc ape D irec tory
Server Administrator’s Guide.
Entry DN: cn=config
Valid Range: 0 to the maximum 32 bit integer value (2147483647)
nsIdleTimeout operational attribute, which can be
Default Value: 0
Syntax: Integer
Example: nsslapd-idletimeout: 0
nsslapd-instancedir (Instance Directory)
Specifies the full path to the directory where this server insta nce is installed. The
serverID from installation time is the default ID.
Entry DN: cn=config
Valid Values: Any valid file path.
Default Value: serverRoot/slapd-serverID
Syntax: DirectoryString
Example: nsslapd-instancedir:
/usr/netscape/servers/slapd-phonebook
Chapter 2 Core Server Configuration Reference 67
Page 68

Core Server Configuration Attributes Reference
nsslapd-ioblocktimeout (IO Block Time Out)
Specifies the amount of time in milliseconds after which the connection to a stalled
LDAP client is closed. An LDAP client is considered to be stalled when it has not
made any I/O progress for read or write operations.
Entry DN: cn=config
Valid Range: 0 to the maximum 32 bit integer value (2147483647) in ticks
Default Value: 1800000
Syntax: Integer
Example: nsslapd-ioblocktimeout: 1800000
nsslapd-lastmod (Track Modification Time)
Specifies whether the Directory Server maintains the modification attributes for
Directory Server entries. These attributes include:
•
modifiersname—The distinguished name of the person who last modified the
entry.
modifytimestamp—The timestamp, in GMT format, for when the entry was
•
last modified.
•
creatorsname—The distinguished name of the person who initia lly created
the entry.
•
createtimestamp—The timestamp for when the entry was created in GMT
format.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-lastmod: off
68 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 69

Core Server Configuration Attributes Reference
nsslapd-listenhost (Listen to IP Address)
Allows multiple Directory Server instances to run on a multihomed machine (or
makes it possible to limit listening to one in terfac e of a multihomed machine).
Provide the hostname which corresponds to the IP interface you want to specify as
a value for this attribute. Directory Server will only respond to requests sent to the
interface that corresponds to the hostname provided on this attribute.
Entry DN: cn=config
Valid Value s: Any hostnam e
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-listenhost: host_name
nsslapd-loca lhost (Local Host)
This read-only attribute specifies the host machine on which the Directory
Server runs.
Entry DN: cn=config
Valid Values: Any fully qualified hostname.
Default Value: Hostname of installed machine.
Syntax: DirectoryString
Example: nsslapd-localhost:phonebook.example.com
nsslapd-localuser (Local User)
Applicable to Directory Server installations on Unix machines.
Specifies the user that the Directory Server runs as. The group that the user runs
as is derived from this attribute, by examining the g roups that the user is a
member of. Should the user change, then all the files in the installation directory
will need to be owned by this user.
Entry DN: cn=config
Valid Values: Any valid user on the local UNIX machine.
Chapter 2 Core Server Configuration Reference 69
Page 70

Core Server Configuration Attributes Reference
Default Value: To run as the same user who started the Directory Server.
Syntax: DirectoryString
Example: nsslapd-localuser: nobody
nsslapd-maxbersize (Maximum Message Size)
Defines the maximum size in bytes allowed for an incoming message. This limits
the size of LDAP requests that can be handled by the Directory Server. Limiting
the size of requests prevents some kinds of denial of service attacks.
The limit applies to the total size of the LDAP request. For example, if the request is
to add an entry and if the entry in the request is larger than two megabytes, then
the add request is denied. Care should be taken when changing this attribute, and
we recommend contacting Netscape Professional Services before doing so.
Entry DN: cn=config
Valid Range: 0 - 2GB (2,147,483,647 bytes) where a value of 0 indicates that the
Default Value: 2097152
default valu e should be used.
Syntax: Integer
Example: nsslapd-maxbersize: 2097152
nsslapd-maxdescriptors (Maximum File Descriptors)
Not applicable to Directory Server in stallations on Windows and AIX machines.
This attribute sets the maximum, platform-dependent number of file descriptors
that the Directory Server will try to use. A file descriptor is used whenever a
client connects to the server, and for some server activities such as index
maintenance. The number of available file descriptors for TCP/IP connections
is the total for the
descriptors used by the server as specified in the
nsslapd-reservedescriptors attribute for non-client connections, such as
index management and managing replicatio n. (s ee “nsslapd-reservedescriptors
(Reserved File Descriptors)” on page 75).
70 Netscape Directory Server Configuration, Command, and File Reference • December 2003
nsslapd-maxdescriptors attribute minus the number of file
Page 71

Core Server Configuration Attributes Reference
The number that you specify here should not be greater than the total number of
file descriptors that your operating system allows the
ns-slapd process to use.
This number will differ depending on your operating system. Some operating
systems allow you to configure the number of file descriptors available to a
process. See your operating-system documentation for details on file descriptor
limits and configuration. Note that the
dsktune program (explained in the
Netscape Directory Server Installation Guide) can be used to suggest changes to
the system kernel or TCP/IP tuning attributes, including increasing the number
of file descriptors if necessary. You should consider increasing the value on this
attribute if the Directory Server is refusing connections because it is out of file
descriptors. When this occurs, the following message is written to the Directory
Server’s error log file:
Not listening for new connections -- too many fds open
NOTE UNIX shells usually have configurable limits on the number of file
descriptors. See your operating-system documentation for further
information regarding limit and ulimit as these limits can often
cause problems.
Entry DN: cn=config
Valid Range: 1 to 65535
Default Value: 1024
Syntax: Integer
Example: nsslapd-maxdescriptors: 1024
nsslapd-maxthreadsperconn (Maximum Threads Per Connection)
Defines the maximum number of threads that a connection should use. For normal
operations where a client binds and only performs one or two operation s before
unbinding, you should use the default value. For situations where a client binds
and simultaneously issues many requests, you should increase this value to allow
each connection enough resources to perform all the operations. This attribute is
not available from the server console.
Entry DN: cn=config
Valid Range: 1 to maximum threadnumber
Chapter 2 Core Server Configuration Reference 71
Page 72

Core Server Configuration Attributes Reference
Default Value: 5
Syntax: Integer
Example: nsslapd-maxthreadsperconn: 5
nsslapd-nagle
When the value of this attribute is off, the TCP_NODELAY option is set so that LDAP
responses (such as entries or result messages) are sent back to a client immediately.
When the attribute is turned on, default TCP behavior applie s, namely the sending
of data is delayed, in the hope that this will enable additional data to be grouped
into one packet of the underlying network MTU size (typically 1500 bytes for
Ethernet).
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-nagle: off
nsslapd-outbound-ldap-io-timeout
This attribute limits the I/O wait time for all outbound LDAP connections. The
default is 300000 milliseconds (5 minutes). A value of 0 indicates that the server
will impose no limit on I/O wait time .
Entry DN: cn=config
Valid Range: 0 to the maximum 32 bit integer value (2147483647)
Default Value: 300000
Syntax: DirectoryString
Example: nsslapd-outbound-ldap-io-timeout: 300000
nsslapd-plug-in
This read-only attribute lists the syntaxes and matching rules loaded by the server.
72 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 73

Core Server Configuration Attributes Reference
nsslapd-port (Port Number)
TCP/IP port number used for LDAP communications. If you want to run SSL/TLS
over this port you can do so through the Start TLS extended operation. This
selected port must be unique on the host system; make sure no other application is
attempting to use the same port number. On UNIX systems, specifying a port
number of less than 1024 requires the Directory Server to run as
If you are changing the port number for a configuration directory, you must also
update the corresponding Server Instance Entry in the configuration d irectory.
Note that you need to restart the server for the port number change to be taken into
account.
Entry DN: cn=config
Valid Range: 1 to 65535
Default Value: 389
Syntax: Integer
Example: nsslapd-port: 389
root.
nsslapd-privatenamespaces
Contains the list of the p rivate naming contexts cn=config, cn=schema and
cn=monitor.
Entry DN: cn=config
Valid Values: cn=config, cn=schema and cn=m onit or
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-privatenamespaces: cn=config
nsslapd-pwpolicy-local (Enable Subtree- and User-Level Password Policy)
Turns fine-grained (subtree- and user-level) password policy on and off.
If this attribute has a value
in the directory will be subjected to the global passwo rd policy; the server will
ignore any defined subtree/user level password policy.
off, all entries (except for cn=Directory Manager)
Chapter 2 Core Server Configuration Reference 73
Page 74

Core Server Configuration Attributes Reference
If this attribute has a value on, the server will check for password policies at the
subtree- and user-level and enforce those policies.
(This feature was introduced in the Directory Server 6. 2 release.)
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-pwpolicy-local: off
nsslapd-readonly (Read Only)
Specifies whether the whole server is in read-only mode, meaning that neither
data in the database(s) nor configuration information can be modified. Any
attempt to modify a database in read-only mode returns an error indicating that
the server is unwilling to perform the operation.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-readonly: off
nsslapd-referral (Referral)
This multi-valued attribute specifies the LDAP URL(s) to be returned by the suffix
when the server receives a request for an entry not belonging to the local tree; tha t
is, an entry whose suffix does not match the value specified on any of the suffix
attributes. For example, assume the database contains only entries:
ou=People,dc=example,dc=com
but the request is for this entry:
ou=Groups,dc=example,dc=com
74 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 75

Core Server Configuration Attributes Reference
In this case, the referral would be passed back to the client in an attempt to allow
the LDAP client to locate a database that contains the requested entry. Although
only one referral is allowed per Directory Server instance, this referral can have
multiple values.
NOTE If you want to use SSL and TLS communications, the Referral
attribute should be in the following form:
ldaps://server-location
Start TLS does not support referrals.
For more information on managing referrals, see Chapter 3, “Configuring
Directory Databases” in the Netscape Directory Server Administrator’s Guide.
Entry DN: cn=config
Valid Values: Valid LDAP URL in the following format: ldap://server-location
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-referral: ldap://ldap.example.com
nsslapd-referralmode (Referral Mode)
When set this attribute will send back the referral for any request on any suffix.
Entry DN: cn=config
Valid Values: Valid LDAP URL in the following format: ldap://server-location
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-referralmode: ldap://ldap.example.com
nsslapd-reservedescriptors (Reserved File Descriptors)
Not applicable to Directory Server installations on Windows and AIX machines.
Chapter 2 Core Server Configuration Reference 75
Page 76

Core Server Configuration Attributes Reference
This read-only attribute specifies the number of file descriptors that Directory
Server reserves for managing non-client connections, such as index
management and managing replication. The number of file descriptors that the
server reserves for this purpose subtracts from the total number of file descriptors
available for servicing LDAP client connections (see “ nsslapd-maxdescriptors
(Maximum File Descriptors)” on page70).
Most installations of Directory Server should never need to change thi s
attribute. However, consider increasing the value on this attribute if all of the
following are true:
• The server is replicating to a large number of consumer servers (more than 10)
and/or the server is maintaining a large number of index files ( mo r e tha n 30).
• The server is servicing a large number of LDAP connections.
• You are seeing error messages reporting that the server is unable to open file
descriptors (the actual error message will d if f er depending on the operation
that the server is attempting to perform), but these error messages are NOT
related to managing client LDAP connections.
Increasing the value on this attribute may result in more LDAP clients being unable
to access your directory. Therefore, when you increase the value on this attribute,
you should also increase the value on the
Note that you may not be able to increase the
your server is already using the maximum num b er of file de scriptors that your
operating system allows a process to use (see your operating system
documentation for details). If this is the case, then reduce the load on your server
by causing LDAP clients to search alternative directory replicas.
nsslapd-maxdescriptors attribute.
nsslapd-maxdescriptors value if
To assist you in computing the nu mber of file descriptors you set for this attribute
we suggest you use the following formula:
nsslapd-reservedescriptor = 20 + (NldbmBackends * 4) + NglobalIndex
+ ReplicationDescriptor + ChainingBackendDescriptors +
PTADescriptors + SSLDescriptors
where:
NldbmBackends Number of ldbm databases.
NglobalIndex Total numb er of configured indexes for all
databases including system indexes.
(By default 8 system indexes and 17 additio nal
indexes per database).
76 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 77

Core Server Configuration Attributes Reference
ReplicationDescriptor NSupplierReplica + 8
(where NSupplierReplica is number of replicas
in the server that can act as a supplier (hub or
master)).
ChainingBackendDescriptors NchainingBackend *
nsOperationConnectionsLimit
(where nsOperationConnectionsLimit is
configurable in database link (chaining)
configuration and 10 by default).
PTADescriptors 3 if PTA is configured, 0 if PTA is not configured
SSLDescriptors 5 (4 files + 1 listensocket) if SSL is configured, 0 if
SSL is not configured.
Entry DN: cn=config
Valid Range: 1 to 65535
Default Value: 64
Syntax: Integer
Example: nsslapd-reservedescriptors: 64
nsslapd-return-exact-case (Return Exact Case)
Returns the exact case of attribute type names as requested by the client. Some
client applications require attribute names to exactly match the case of the attribute
as it is listed in the schema when the attribute is returned by the Directory
Server, as the result of a search or modify operation. However, most client
applications ignore the case of attributes, therefore, by d e fault this attribute is
disabled. Do not modify it unless you have legacy clien ts that can check the case
of attribute names in results returned from the server.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-return-exact-case: off
Chapter 2 Core Server Configuration Reference 77
Page 78

Core Server Configuration Attributes Reference
nsslapd-rootdn (Manager DN)
Specifies the distinguished name (DN) of an entry that is not subject to
access-control restrictions, administrative limit restrictions for operations on the
directory or resource limits in general. The attributes
nsslapd-timelimit, and nsslapd-schemacheck do not apply to this DN either.
For information on changing the Root DN, see Chapter 2, “Creating Directory
Entries” in the Netscape Directory Server Administrator’s Guide
.
Entry DN: cn=config
Valid Values: Any valid distinguished name
Default Value: N/A
Syntax: DN
Example: nsslapd-rootdn: cn=Directory Manager
nsslapd-root pw (Root Password)
Allows you to specify the password associated wi th the "Manager DN". When you
provide the root password, it will be encrypted according to the encryption
method you selected for “nsslapd-rootpwstoragescheme (Root Password Storage
Scheme)” on page 79. When viewed from the server console, this attribute shows
the value:
encryption method followed by the encrypted string of the password. Note that the
example below is what you view, not what you type.
***** When viewed from the dse.ldif file, this attribute shows the
nsslapd-sizelimit,
CAUTION If you configure a root DN at server installation tim e , you must also
provide a root password. However, it is possible for the root
password to be deleted from
dse.ldif by direct editing of the file.
In this situation, the root DN can only obta in the same access to your
directory as you allow for anonymou s access. Always make sure
that a root password is defined in
dse.ldif when a root DN is
configured for your database.
Entry DN: cn=config
Valid Values: Any valid password encrypted by any one of the encryption methods
which are described in “passwordStorageScheme (Password Storage
Scheme)” on page 91.
78 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 79

Core Server Configuration Attributes Reference
Default Value: N/A
Syntax: DirectoryString {encryption_method} encrypted_Password
Example: nsslapd-rootpw: {SSHA}9Eko69APCJfF
nsslapd-roo tpwstoragescheme (Root Password Storage Scheme)
Available only from the server console. This attribute indicates the encryption
method used for the root password.
Entry DN: cn=config
Valid Values: Any encryption method as described in “passwordStorageScheme
(Password Storage Scheme)” on page 91.
Default Value: CLEAR
Syntax: DirectoryString
Example: nsslapd-rootpwstoragescheme: SSHA
nsslapd-schema-ignore-trailing-spaces (Ignore Tr ailing Spaces in Object Class Names)
Ignores trailing spaces in object class names. By default, the attribute is turned off.
If your directory contains entries with object class values that end in one or more
spaces, you should turn this attribute on. (It is preferrab le to remo ve the trailing
spaces because the LDAP standards do not allow them).
A server restart is required for changes to take effect (for performance reasons).
Note that the previous releases of Directory Server (6.0, 6.01, 6.02, 6.1, and 6.11)
allowed object classes that included trailing spaces to be added to entries. In the 6.2
and future releases of the server, an error is returned by default when such an
object class is used. Additionally, during operations such as add, modify, and
import (when object classes are expa nded and missing superiors are added)
trailing spaces are ignored, if appropriate. This means that even when
nsslapd-schema-ignore-trailing-spaces is on, a value such as “top” will not
be added if “top “ is already there. An error message is logged and returned (to the
client) if an object class is not found and it contains trailing spaces.
Entry DN: cn=config
Chapter 2 Core Server Configuration Reference 79
Page 80

Core Server Configuration Attributes Reference
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-schema-ignore-trailing-spaces: on
nsslapd-schemacheck (Schema Checking)
Specifies whether the database schema will be enforced during entry insertion or
modification. When this attribute has a value of on, Directory Server will not
check the schema of existing entries until they are modified. The database
schema defines the type of information allowed in the database. You can extend
the default schema using the
information on how to extend your s chema using the Directory Server Console,
see Chapter 9, “Extending the Directory Schema” in the Netscape Directory
Server Administrator’s Guide.
NOTE Schema checking works by default when database modifi cations
are made using an LDAP client, such as
Directory Server Gateway, or when importing a database from
LDIF using
have to verify manually that your entries conform to the schema.
If schema checking is turned on, the server sends an error
message to inform you of the entr ies which do not match the
schema. Make sure that the attributes and object classes you
create in your LDIF statements are both spelled correctly and
identified in
format in the schema directory or add the elements to
99user.ldif
objectclasses and attribute types. For
ldapmodify, the
ldif2db. If you turn schema checking off, you will
dse.ldif. You will need to create a file in the LDIF
.
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: nsslapd-schemacheck: on
80 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 81

Core Server Configuration Attributes Reference
nsslapd-schemareplace
Determines whether modify operations that replace attribute values are allowed on
the
cn=schema entry.
Entry DN: cn=config
Valid Values: on | off | replication-only
Default Value: replication-only
Syntax: DirectoryString
Example: nsslapd-schemareplace: replication-only
nsslapd-securelistenhost
Allows multiple Directory Server instances to run, usi ng secure SSL/TLS
connections, on a multihomed m ach ine (or makes it possible to limit listening to
one interface of a multihomed machine). Provide the hostname that corresponds to
the IP interface you want to specify as a value for this attribute. Directory Server
will only respond to requests sent to the interface that corresponds to the
hostname provided on this attribute.
Entry DN: cn=config
Valid Values: Any secure hostname.
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-securelistenhost: secure_host_name
nsslapd-securePort (Enc rypted Port Number)
TCP/IP port number used for SSL/TLS communications. This selected port must
be unique on the host system; make sure no other application is attempting to use
the same port number. For UNIX systems, specifying a port number of less than
1024 requires that Directory Server runs as
The default value 636 is only used if the server has been configured with a private
key and a certificate; otherwise it does not listen on this po rt.
Entry DN: cn=config
root.
Chapter 2 Core Server Configuration Reference 81
Page 82

Core Server Configuration Attributes Reference
Valid Range: 1 to 65535
Default Value: 636
Syntax: Integer
Example: nsslapd-securePort: 636
nsslapd-security (Security)
Specifies whether the Directory Server is to accept SSL/TLS communications on
its encrypted port. This attribute should be set to
connections.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-security: off
on, if you want secure
nsslapd-sizelimit (Size Limit)
Specifies the maximum number of entries to return from a search operation. If this
limit is reached,
request, as well as an exceeded size limit error.
When no limit is set,
regardless of the number found. To set a no limit value whereby the Directory
Server will wait indefinitely for the search to comp lete, specif y a value of -1 for
this attribute in the
This limit applies to everyone regardless of their organization.
NOTE A value of -1 on this attribute in the dse.ldif is the same as
82 Netscape Directory Server Configuration, Command, and File Reference • December 2003
ns-slapd returns any entries it has located that match the search
ns-slapd will return every matching entry to the client
dse.ldif file.
leaving the attribute blank in the server console, in that it causes no
limit to be used. Note however, that you cannot specify a negative
integer for this field in the server console nor can you specify a null
value in
dse.ldif as it is not a valid integer.
Page 83

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Range: -1 to the maximum 32 bit integer value (2147483647)
Default Value: 2000
Syntax: Integer
Example: nsslapd-sizelimit: 2000
nsslapd-ssl-check-hostname (Verify Hostname for Outbound Connections)
Specifies whether an SSL-enabled Directory Server (with certificate based client
authentication turned on) should verify authenticity of a request by matching
the hostname against the value assigned to the Common Name (CN) attribute
of the subject name in the certificate being presented. By default, the attribute is set
to off. If it is on and if the hostname does not match the CN attribute of the
certificate, appropriate error and audit messages are logged. For example, in a
replicated environment, messages similar to these are lo gged in the supplier
server’s log files if it finds that the peer server’s hostname doesn’t match the
name specified in its certificate:
[DATE] - SSL alert: ldap_sasl_bind("",LDAP_SASL_EXTERNAL) 81
(Netscape runtime error -12276 - Unable to communicate securely with
peer: requested domain name does not match the server's
certificate.)
[DATE] NSMMReplicationPlugin - agmt="cn=to ultra60 client auth"
(ultra60:1924): Replication bind with SSL client authentication
failed: LDAP error 81 (Can’t contact LDAP server)
It is recommended that you turn this attribute on to protect Directory S e rver’s
outbound SSL connections against a Man In The Middle (MITN) attack.
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsslapd-ssl-check-hostname: on
Chapter 2 Core Server Configuration Reference 83
Page 84

Core Server Configuration Attributes Reference
nsslapd-threadn um be r (Th re ad Numbe r)
Defines the number of operation threads th at the Directory Server will create
during startup. The
have many director y c lients performing time-consuming operations such as
add or modify, as this ensures that there are other threads available for
servicing short-lived operations such as simple se arches. This attribute is not
available from the server console.
Entry DN: cn=config
Valid Range: 1 to the number of threads supported by your system
Default Value: 30
Syntax: Integer
Example: nsslapd-threadnumber: 60
nsslapd-timelimit (Time Limit)
Specifies the maximum number of seconds allocated for a search request. If this
limit is reached, Directory Server returns any entries it has located that match
the search request, as well as an exceeded time limit error.
nsslapd-threadnumber value should be increased if you
When no limit is set
ns-slapd will return every matching entry to the client
regardless of the time it takes. To set a no limit value whereby Directory Server
will wait indefinitely for the search to comp lete, specif y a value of -1 for this
attribute in the
dse.ldif file. A value of zero (0) causes no time to be allowed
for searches. The smallest time limit is 1 second.
NOTE A value of -1 on this attribute in the dse.ldif is the same as
leaving the attribute blank in the server console, in that it causes no
limit to be used. Please note however, that you cannot specify a
negative integer for this field in the server console nor can you
specify a null value in
Entry DN: cn=config
Valid Range: -1 to the maximum 32 bit integer value (2147483647) in seconds
Default Value: 3600
Syntax: Integer
84 Netscape Directory Server Configuration, Command, and File Reference • December 2003
dse.ldif as it is not a valid integer.
Page 85

Core Server Configuration Attributes Reference
Example: nsslapd-timelimit: 3600
nsslapd-versionstring
Specifies the server version number.
Entry DN: cn=config
Valid Values: Any valid server version number.
Default Value: N/A
Syntax: DirectoryString
Example: nsslapd-versionstring: Netscape-Directory/6.2
passwordChange (Password Change)
Indicates whether users may change their passwords.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: passwordChange: on
passwordCheckSyntax (Check Password Syntax)
Indicates whether the password syntax will be checked before the password is
saved. The password syntax checking mechanism checks that the password meets
or exceeds the password minimum length requirement and that the string does not
contain any trivial words, such as the user’s name or user ID or any attribute value
stored in the
entry.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
uid, cn, sn, givenName, ou, or mail attributes of the user’s directory
Chapter 2 Core Server Configuration Reference 85
Page 86

Core Server Configuration Attributes Reference
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: passwordCheckSyntax: off
passwordExp (Password Expir at ion)
Indicates whether user passwords will expire after a given number of seconds. By
default, user passwords do not expire. Once password expiration is enabled, you
can set the number of seconds after which the pass word will expire using the
passwordMaxAge attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: passwordExp: on
passwordHistory (Password History)
Enables password history. Password history refers to whether users are allowed to
reuse passwords. By default, password history is disabled and users can reuse
passwords. If you set this attribute to be on, the directory stores a given number of
old passwords and prevents users from reusing any of the stored passwords. You
set the number of old passwords the Directory Server stores using the
passwordInHistory attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
86 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 87

Core Server Configuration Attributes Reference
Default Value: off
Syntax: DirectoryString
Example: passwordHistory: on
passwordInHistory (Number of Passwords to Remember)
Indicates the number of passwords the Directory Server stores in history.
Passwords that are stored in history cannot be reused by users. By default, the
password history feature is disabled. That is, the Directory Server does not store
any old passwords and so users can reuse passwords. You can enable password
history by using the
To prevent users from rapidly cycling through the number of passwords that you
are tracking, use the
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 2 to 24 passwords
passwordHistory attribute.
passwordMinAge attribute.
Default Value: 6
Syntax: Integer
Example: passwordInHistory: 7
passwordLockout (Account Lockout)
Indicates whether users will be locked out of the directory after a given number of
failed bind attempts. By default, users will no t be locked out of the directory after a
series of failed bind attempts. If you enable account lockout, you can set the
number of failed bind attempts after which the user will be locked out usin g the
passwordMaxFailure attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
Chapter 2 Core Server Configuration Reference 87
Page 88

Core Server Configuration Attributes Reference
Default Value: on
Syntax: DirectoryString
Example: passwordLockout: off
passwordLockoutDuration (Lockout Duration)
Indicates the amount of time in seconds during which users will be locked out of
the directory after an account lockout. The account lockout feature protects against
hackers who try to break into the directory by repeatedly tryin g to guess a user’s
password. You enable and disable the account lockout feature using the
passwordLockout attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647 ) in seconds
Default Value: 3600
Syntax: Integer
Example: passwordLockoutDuration: 3600
passwordMaxA ge (Password Maximum Age)
Indicates the number of seconds after which user passwords will expire. To use
this attribute, you must enable password expiration using the
attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647 ) in seconds
Default Value: 8640000 (100 days)
Syntax: Integer
Example: passwordMaxAge: 100
88 Netscape Directory Server Configuration, Command, and File Reference • December 2003
passwordExp
Page 89

Core Server Configuration Attributes Reference
passwordMaxFailure (Maximum Password Failures)
Indicates the number of failed bind attempts after which a user will be locked out
of the directory. By default, account lockout is disabled. You can enable account
lockout by modifying the
passwordLockout attribute.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 1 to maximum inte ger bind failures
Default Value: 3
Syntax: Integer
Example: passwordMaxFailure: 3
passwordMinAge (Password Minimum Age)
Indicates the number of second s that must pass before a user can change their
password. Use this attribute in conjunction with the
of Passwords to Remember) attribute to prevent users from quickly cycling
through passwords so that they can use their old password again. A value of zero
(0) indicates that the user can change the password immediately.
passwordInHistory (Number
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
passwordMinLength (Password Minimum Length)
Specifies the minimum number of characters that must be used in Directory
Server user password attributes. In general, shorter passwords are easier to
crack, so you are recommended to set a password length of at least 6 or 7
characters. This is long enough to be difficult to crack, but short enough that
users can remember the password without writing it down.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 2 to 512 characters
Default Value: 6
Chapter 2 Core Server Configuration Reference 89
Page 90

Core Server Configuration Attributes Reference
Syntax: Integer
Example: passwordMinLength: 6
passwordMustChange (Password Must Change)
Indicates whether users must change their passwords when they first bind to
the Directory Server, or when the password has been reset by the
DN"
.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: passwordMustChange: off
"Manager
passwordRese tFailureCount (Reset Passwor d Failure Count After)
Indicates the amount of time in seconds after which the password failure counter
will be reset. Each time an invalid password is sent from the user’s account, the
password failure counter is incremented. If the
to on, users will be locked out of the directory when the counter reaches the
number of failures specified by the
passwordMaxFailure attribute (within 600
seconds by default). After the amount of time specified by the
passwordLockoutDuration attribute, the failure counter is reset to zero (0).
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647 ) in seconds
Default Value: 600
Syntax: Integer
Example: passwordResetFailureCount: 600
90 Netscape Directory Server Configuration, Command, and File Reference • December 2003
passwordLockout attribute is set
Page 91

Core Server Configuration Attributes Reference
passwordStorageScheme (Password Storage Scheme)
Specifies the type of encryption used to store Directory Server passwords. Enter
the password in
in plain text.
The following encryption types are supported by the Directory Server 6.x:
• SSHA (Salted Secure Hash Algorithm) is the recommended method as it is the
most secure.
• SHA (Secure Hash Algorithm). This is the method suppo rted by 4.x
Directory Servers.
• CRYPT is the UNIX crypt algorithm. It is provid ed for compatibility with
UNIX passwords.
NOTE You can no longer choose to encrypt passwords using the
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
CLEAR for this attribute indicates that the password will appear
NS-MTA-MD5 password storage scheme. The storage scheme is
still present but only for reasons of backward compatibility.
passwordUnlock (Unlock Account)
Indicates whether users will be locked out of the directory for a specified amount
of time or until the administrator resets the password after an account lockout. The
account lockout feature protects against hackers who try to break into the directory
by repeatedly trying to guess a user’s password. If this
is set to
off and the operational attribute accountUnlockTime has a value of 0,
then the account will be locked indefinitely.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Values: on | off
Default Value: on
Syntax: DirectoryString
Example: passwordUnlock: off
Chapter 2 Core Server Configuration Reference 91
passwordUnlock attribute
Page 92

Core Server Configuration Attributes Reference
passwordWarning (S en d War ning)
Indicates the number of seconds before a user’s password is due to expire that the
user will receive a password expiration warning control on their next LDAP
operation. Depending on the LDAP client, the user may also be prompted to
change their password at the time the warning is sent.
For more information on password policies, see Chapter 7, “User Account
Management” in the Netscape Directory Se rver Admin istr ator’s Guide .
Entry DN: cn=config
Valid Range: 1 to the maximum 32 bit integer value (2147483647 ) in seconds
Default Value: 86400 (1 day)
Syntax: Integer
Example: passwordWarning: 86400
cn=changelog5
Multi-master replication change log configura tion entries are stored under the
cn=changelog5 entry. The change log behaves much like a database and it has
many of attributes also used by the ldbm databases. The change log entry suppo rts
the following attributes with the same meani ng a s for da tabases:
• “nsslapd-dbcachesize” on page 154
• “nsslapd-db-checkpoint-interval” on page 155
• “nsslapd-db-circular-logging” on page 155
• “nsslapd-db-debug” on page 156
• “nsslapd-db-durable-transactions” on page 156
• “nsslapd-db-logfile- size” on page 16 0
• “nsslapd-db-page-size” on page 160
• “nsslapd-db-spin-count” on page 161
• “nsslapd-db-trickle-percentage” on page 162
• “nsslapd-db-verbose” on page 163
• “nsslapd-cachesize” on page 168
92 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 93

Core Server Configuration Attributes Reference
• “nsslapd-cachememsize” on page 168
Note that the default values for the cache-related memory parameters (tuned for a
single backend replicated to a single consumer) are as follows:
nsslapd-cachesize : 3000 (3000 entries)
nsslapd-cachememsize : 10000000 (10 MB)
When more backends are replicated or when you need to replicate one backend to
more than one consumers, consider tuning the parameters as below:
nsslapd-cachesize = 2000*#repl_agreements_initiated_from_this_server
nsslapd-cachememsize =
5000000*#repl_agreements_initiated_from_this_server
Also, the relationship between the values assigned to the nsslapd-dbcachesize
and
nsslapd-cachememsize parameters should be the same as the relationship
that is described in the database-tuning section.
The
cn=changelog5,cn=config entry is an instance of the extensibleObject
object class. For attributes to be taken into account by the server, both of these
object classes (in addition to the
top object class) must be present in the entry.
It is worth noting that two different types of change logs are maintained by
Directory Server. The first type, which is stored here and referred to as
changelog, is used by multi-master replication; the second change log, which is
actually a plug-in and referred to as retro changelog, is intended for use by Netscape
Meta Directory. See “Retro Changelog Plug-in” on page 142” of Chapter 3,
“Plug-in Implemented Server Functionality Reference” for further information
regarding the Retro Changelog plug-in. Multi-master replication changelog
attributes are presented in this section.
nsslapd-changelogdir
This required attribute specifies the name of the directory in which the change log
database will be created. Whenever a change log configuration entry is created, i t
must contain a valid directory; otherwise, the operation will be rejected. The GUI
proposes by default that this database be stored under:
serverRoot/slapd-serverID/changelogdb
NOTE For performance reasons you will probably want to store this
database on a different physical disk.
Entry DN: cn=changelog5,cn=config
Chapter 2 Core Server Configuration Reference 93
Page 94

Core Server Configuration Attributes Reference
Valid Values: Any valid path to the directory storing the changelog
Default Value: None
Syntax: DirectoryString
Example: nsslapd-changelogdir:
nsslapd-changelogmaxage (Max Changelog Age)
Specifies the maximum age of any entry in the change log. The change log
contains a record for each directory modification and is used when
synchronizing consumer servers. Each record contains a timestamp. Any record
with a timestamp that is older than the value specified in this attribute will be
removed. If this attribute is absent, there is no age limit on change log records.
For information on the change log, see ““nsslapd -changelogdir” on page 93.”
Entry DN: cn=changelog5,cn=config
Valid Range: 0 (meaning that entries are not removed according to their age) to
Default Value: 0
/usr/netscape/servers/slapd-phonebook/changelogdb
maximum integer (21474836 47)
Syntax: DirectoryString IntegerAgeID
where AgeID is as follows:
s for seconds
m for minutes
h for hours
d for days
w for weeks
Example: nsslapd-changelogmaxage: 30d
nsslapd-changelogmaxentries (Max Changelog Records)
Specifies the maximum number of records the change log may contain. If this
attribute is absent, there is no maximum number of records the change log can
contain. For information on the change log, see “nsslapd-changelogdir” on page 93.
Entry DN: cn=changelog5,cn=config
94 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 95

Core Server Configuration Attributes Reference
Valid Range: 0 (meaning that the only maximum limit is the disk size) to maximum
integer (2147 483647)
Default Value: 0
Syntax: Integer
Example: nsslapd-changelogmaxentries: 5000
cn=encryption
Encryption related attributes are stored under the cn=encryption,cn=config
entry. The
nsslapdEncryptionConfig object class. For encryption related attributes to be
taken into account by the server this object class (in addition to the
must be present in the entry. Encryption configuration attributes are presented in
this section.
nssslsessiontimeout
Specifies the lifetime duration of an SSL session for both SSLv2 and SSLv3. The
minimum timeout value is 5 seconds and if you enter a value below this, then it is
automatically replaced by 5 seconds. Values outside the valid ranges are replaced
by the default value of 100 seconds (SSLv2).
cn=encryption,cn=config entry is an instance of the
top object class)
Entry DN: cn=encryption,cn=config
Valid Range: SSLv2 - 5 seconds to 100 seconds
SSLv3 - 5 seconds to 24 hours
Default Value: 0, which stands for 1 00 seconds if you ar e runnin g SSLv2 and 24 hou rs
if you are running SSLv3
Syntax: Integer
Example: nssslsessiontimeout: 5
nssslclientauth
Specifies, or not as the case may be, client authentication using SSL.
Entry DN: cn=encryption,cn=config
Valid Values: off | allowed | required
Chapter 2 Core Server Configuration Reference 95
Page 96

Core Server Configuration Attributes Reference
Default Value: allowed
Syntax: DirectoryString
Example: nssslclientauth: allowed
nsssl2
Supports SSL version 2.
Entry DN: cn=encryption,cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsssl2: on
nsssl3
Supports SSL version 3.
Entry DN: cn=encryption,cn=config
Valid Values: on | off
Default Value: off
Syntax: DirectoryString
Example: nsssl3: on
nsssl3ciphers
This multi-valued attribute specifies the set of encryption ciphers the Directory
Server will use during SSL communications. For more information on the
ciphers supported by the Directory Server, refer to Chapter 11, “Managing
SSL,” in the Netscape Directory Server Administrator’s Guide
Entry DN: cn=config
96 Netscape Directory Server Configuration, Command, and File Reference • December 2003
Page 97

Core Server Configuration Attributes Reference
Valid Values: For domestic versions, any combination of the following:
For SSLv3
rsa_null_md5
rsa_rc4_128_md5
rsa_rc4_40_md5
rsa_rc2_40_md5
rsa_des_sha
rsa_fips_des_sha
rsa_3des_sha
rsa_fips_3des_sha
For TLS
tls_rsa_export1024_with_rc4_56_sha
tls_rsa_export1024_with_des_cbc_sha
Default Value: N/A
Syntax: DirectoryString
+ symbol to enable or - symbol to disable followed by the cipher(s). It
is important to note that blank spaces are not allowed in the list of
ciphers.
To enable all ciphers (except rsa_null_md5 which must be
specifically called) you can specify +all.
Example: nsslapd-SSL3ciphers:
+RSA_NULL_MD5,+RC4_56_SHA,-RC4_56_SHA
If you are using the Directory Server Console to set the cipher preferences, the
values on the SSL 3.0 tab of the Cipher Preference dialog box correspond to the
following:
Table 2-1 SSLv3 Ciphers
Cipher in Console Corresponding SSLv3 Cipher
None rsa_null_md5
RC4 rsa_rc4_128_md5
RC4 (Export) rsa_rc4_40_md 5
Chapter 2 Core Server Configuration Reference 97
Page 98

Core Server Configuration Attributes Reference
Table 2-1 SSLv3 Ciphers (Continued)
Cipher in Console Corresponding SSLv3 Cipher
RC2(Export) rsa_rc2_40_md5
DES rsa_des_sha
DES (FIPS) rsa_fips_des_sha
Triple-DES rsa_3des_sha
Triple-DES (FIPS) rsa_fips_3des_sha
If you are using the Directory Server Console to set the cipher preferences, the
values on the TLS tab of the Cipher Preference dialog box correspond to the
following:
Table 2-2 TLS Ciphers
Cipher in Console Corresponding TLS Cip he r
RC4 (Export) tls_rsa_exp ort1024_with_rc4_56_sha
DES (Export) tls_rsa_export1024_with_des_cbc_sha
cn=features
No attributes to document.
cn=mapping tree
Configuration attributes for suffixes and replication are stored under cn=mapping
tree,cn=config
suffix subentry
cn="suffixName",cn=mapping tree,cn=config (for example, a suffixName may look
like
dc=example,dc=com)
Replication configuration attributes are stored under
cn=replica,cn="suffixName",cn=mapping tree,cn=config
with the replication agreement attributes under
cn=replicationAgreementName,cn=replica,cn="suffixName",cn=mapping
tree,cn=config
98 Netscape Directory Server Configuration, Command, and File Reference • December 2003
. Configuration attributes related to suffixes are found under the
.
Page 99

Core Server Configuration Attributes Reference
Suffix Configuration Attributes Under cn="suffixName"
Suffix configuration attributes are stored under the cn="suffixName" entry. The
cn="suffixName" entry is an instance of the nsMappingTree object class which
inherits from the
attributes to be taken into account by the server these object classes (in addition to
top object class) must be present in the entry. Suffix configuration attributes are
the
presented in this section.
nsslapd-state
Determines how the suffix handles operations.
Entry DN: cn="suffixName",cn=mapping tree,cn=config
Valid Values: backend | disabled | referral | referral on update
extensibleObject object class. For suffix configuration
backend = the backend (database) is used to process all operations
disabled = the database is not availa bl e for process ing o pera tio ns. Th e
server returns a “No such search object” error in response to requests
made by client applications.
referral = a referral is returned for requests made to this suffix.
referral on update = the database is used for all operations except
update requests, which receive a referral.
Default Value: disabled
Syntax: DirectoryString
Example: nsslapd-state: backend
nsslapd-backend
Gives the name of the database or database link used to process requests. This
attribute can be multi valued, with one databas e or d atabase link per value. This
attribute is required when the value of the
backend or referral on update.
Entry DN: cn="suffixName",cn=mapping tree,cn=config
Valid Values: Any valid partition name
nsslapd-state attribute is set to
Chapter 2 Core Server Configuration Reference 99
Page 100

Core Server Configuration Attributes Reference
Default Value: None
Syntax: DirectoryString
Example: nsslapd-backend: NetscapeRoot
Replication Attributes Under cn=replica, cn=“suffixName”, cn=mapping tree,cn=config
Replication configuration attributes are stored under
cn=replica,cn=“suffixName”,cn=mapping tree,cn=config. The cn=replica
entry is an in stanc e of the
attributes to be taken into account by the server this object cla ss (in addition to the
top object class) must be present in the entry. Replication conf iguration attributes
are presented in this section. For further information rega rding replication see
Chapter 8, “Managing Replication” in the Netscape Directory Server Administrator’s
Guide.
cn
This attribute is used for naming. Once this attrib ute has been set it cannot be
modified.
nsDS5Recplia object class. For replication configuration
Entry DN: cn=replica,cn="suffixName",cn=mapping tree,cn=config
Valid Values: Any valid suffix name
Default Value: cn=replica
Syntax: DirectoryString
Example: cn:cn=replica
nsDS5Flags
This attribute allows you to specify replica properties you will have previously
defined in flags. At present only one flag exists, which allows you to specify
whether your log changes or not.
Entry DN: cn=replica,cn="suffixName",cn=mapping tree,cn=config
100 Netscape Directory Server Configuration, Command, and File Reference • December 2003
 Loading...
Loading...