Page 1

Red Hat Enterprise Linux 3
Debugging with gdb
Page 2

Red Hat Enterprise Linux 3: Debugging with gdb
Copyright © 1987, 1989, 1991-2003 by Free Software Foundation, Inc.
Copyright © 2003 by Red Hat, Inc.
This documentation has been prepared by Red Hat, Inc.
Red Hat, Inc.
1801 Varsity Drive
Raleigh NC 27606-2072 USA
Phone: +1 919 754 3700
Phone: 888 733 4281
Fax: +1 919 754 3701
PO Box 13588
Research Triangle Park NC 27709 USA
Manual identifier:
• PDF: rhds-gdb-EN-3-PDF-RHI (2003-09-24T01:08)
• HTML: rhds-gdb-EN-3-HTML-RHI (2003-09-24T01:08)
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation
License, Version 1.1 or any later version published by the Free Software Foundation; with no InvariantSections, with no
Front-Cover Texts, and with no Back-Cover Texts. A copy of the licenseis included in the section entitled “GNU Free
Documentation License”.
Red Hat, Inc. is not granting permission to any redistributor to use the Red Hat name.
Red Hat is a registered trademark and the Red Hat Shadow Man logo, RPM, and the RPM logo are trademarks of Red Hat, Inc.
Linux is a registered trademark of Linus Torvalds.
All other trademarks and copyrights referred to are the property of their respective owners.
HTML, PDF, and RPM versions of the manuals are availableon the Documentation CD and online at
http://www.redhat.com/docs/.
The GPG fingerprint of the security@redhat.com key is:
CA 20 86 86 2B D6 9D FC 65 F6 EC C4 21 91 80 CD DB 42 A6 0E
Page 3

Table of Contents
1. Debugging with gdb ........................................................................................................................ 1
2. Summary of gdb.............................................................................................................................. 3
2.1. Free software...................................................................................................................... 3
2.2. Free Software Needs Free Documentation ........................................................................ 3
2.3. Contributors to gdb ............................................................................................................ 4
3. A Sample gdb Session ..................................................................................................................... 7
4. Getting In and Out of gdb............................................................................................................ 11
4.1. Invoking gdb .................................................................................................................... 11
4.1.1. Choosing files ................................................................................................... 12
4.1.2. Choosing modes................................................................................................ 13
4.2. Quitting gdb .....................................................................................................................16
4.3. Shell commands ............................................................................................................... 16
4.4. Logging output................................................................................................................. 16
5. gdb Commands .............................................................................................................................19
5.1. Command syntax .............................................................................................................19
5.2. Command completion......................................................................................................19
5.3. Getting help......................................................................................................................21
6. Running Programs Under gdb ....................................................................................................25
6.1. Compiling for debugging ................................................................................................. 25
6.2. Starting your program ...................................................................................................... 25
6.3. Your program’s arguments...............................................................................................26
6.4. Your program’s environment ........................................................................................... 27
6.5. Your program’s working directory................................................................................... 28
6.6. Your program’s input and output .....................................................................................28
6.7. Debugging an already-running process ...........................................................................29
6.8. Killing the child process .................................................................................................. 29
6.9. Debugging programs with multiple threads..................................................................... 30
6.10. Debugging programs with multiple processes...............................................................32
7. Stopping and Continuing .............................................................................................................35
7.1. Breakpoints, watchpoints, and catchpoints...................................................................... 35
7.1.1. Setting breakpoints............................................................................................35
7.1.2. Setting watchpoints...........................................................................................38
7.1.3. Setting catchpoints ............................................................................................40
7.1.4. Deleting breakpoints ......................................................................................... 41
7.1.5. Disabling breakpoints .......................................................................................42
7.1.6. Break conditions ............................................................................................... 43
7.1.7. Breakpoint command lists................................................................................. 44
7.1.8. Breakpoint menus ............................................................................................. 45
7.1.9. "Cannot insert breakpoints" .............................................................................. 46
7.2. Continuing and stepping ..................................................................................................46
7.3. Signals..............................................................................................................................49
7.4. Stopping and starting multi-thread programs ..................................................................51
8. Examining the Stack .....................................................................................................................53
8.1. Stack frames.....................................................................................................................53
8.2. Backtraces........................................................................................................................ 54
8.3. Selecting a frame.............................................................................................................. 55
8.4. Information about a frame ...............................................................................................56
Page 4

9. Examining Source Files ................................................................................................................59
9.1. Printing source lines.........................................................................................................59
9.2. Editing source files........................................................................................................... 60
9.2.1. Choosing your editor.........................................................................................61
9.3. Searching source files ......................................................................................................61
9.4. Specifying source directories........................................................................................... 62
9.5. Source and machine code.................................................................................................63
10. Examining Data........................................................................................................................... 65
10.1. Expressions .................................................................................................................... 65
10.2. Program variables .......................................................................................................... 66
10.3. Artificial arrays ..............................................................................................................67
10.4. Output formats ............................................................................................................... 68
10.5. Examining memory........................................................................................................69
10.6. Automatic display ..........................................................................................................71
10.7. Print settings .................................................................................................................. 72
10.8. Value history ..................................................................................................................77
10.9. Convenience variables ...................................................................................................78
10.10. Registers.......................................................................................................................79
10.11. Floating point hardware ............................................................................................... 80
10.12. Vector Unit................................................................................................................... 81
10.13. Memory region attributes............................................................................................. 81
10.13.1. Attributes.......................................................................................................82
10.14. Copy between memory and a file................................................................................. 83
10.15. Character Sets ..............................................................................................................84
11. C Preprocessor Macros...............................................................................................................89
12. Tracepoints .................................................................................................................................. 93
12.1. Commands to Set Tracepoints ....................................................................................... 93
12.1.1. Create and Delete Tracepoints ........................................................................ 93
12.1.2. Enable and Disable Tracepoints...................................................................... 94
12.1.3. Tracepoint Passcounts..................................................................................... 94
12.1.4. Tracepoint Action Lists................................................................................... 95
12.1.5. Listing Tracepoints ......................................................................................... 96
12.1.6. Starting and Stopping Trace Experiment........................................................ 96
12.2. Using the collected data ................................................................................................. 97
12.2.1. tfind n.......................................................................................................... 97
12.2.2. tdump.............................................................................................................. 99
12.2.3. save-tracepoints filename .................................................................. 100
12.3. Convenience Variables for Tracepoints........................................................................ 100
13. Debugging Programs That Use Overlays................................................................................103
13.1. How Overlays Work.....................................................................................................103
13.2. Overlay Commands .....................................................................................................104
13.3. Automatic Overlay Debugging .................................................................................... 106
13.4. Overlay Sample Program ............................................................................................. 107
14. Using gdb with Different Languages.......................................................................................109
14.1. Switching between source languages........................................................................... 109
14.1.1. List of filename extensions and languages.................................................... 109
14.1.2. Setting the working language........................................................................ 110
14.1.3. Having gdb infer the source language .......................................................... 110
14.2. Displaying the language............................................................................................... 110
14.3. Type and range checking..............................................................................................111
14.3.1. An overview of type checking ......................................................................111
14.3.2. An overview of range checking .................................................................... 112
14.4. Supported languages .................................................................................................... 113
Page 5

14.4.1. C and C++ ....................................................................................................113
14.4.2. Objective-C................................................................................................... 119
14.4.3. Modula-2.......................................................................................................121
14.5. Unsupported languages................................................................................................ 126
15. Examining the Symbol Table ................................................................................................... 129
16. Altering Execution .................................................................................................................... 135
16.1. Assignment to variables............................................................................................... 135
16.2. Continuing at a different address ................................................................................. 136
16.3. Giving your program a signal ......................................................................................137
16.4. Returning from a function............................................................................................ 137
16.5. Calling program functions ...........................................................................................137
16.6. Patching programs .......................................................................................................138
17. gdb Files ..................................................................................................................................... 139
17.1. Commands to specify files ........................................................................................... 139
17.2. Debugging Information in Separate Files ....................................................................145
17.3. Errors reading symbol files ..........................................................................................147
18. Specifying a Debugging Target ................................................................................................ 149
18.1. Active targets ............................................................................................................... 149
18.2. Commands for managing targets ................................................................................. 149
18.3. Choosing target byte order ...........................................................................................151
18.4. Remote debugging ....................................................................................................... 151
18.5. Kernel Object Display.................................................................................................. 151
19. Debugging remote programs.................................................................................................... 153
19.1. Connecting to a remote target ...................................................................................... 153
19.2. Using the gdbserverprogram .................................................................................... 154
19.3. Using the gdbserve.nlmprogram..............................................................................155
19.4. Remote configuration...................................................................................................155
19.5. Implementing a remote stub......................................................................................... 156
19.5.1. What the stub can do for you ........................................................................ 157
19.5.2. What you must do for the stub ...................................................................... 157
19.5.3. Putting it all together..................................................................................... 158
20. Configuration-Specific Information ........................................................................................ 161
20.1. Native...........................................................................................................................161
20.1.1. HP-UX .......................................................................................................... 161
20.1.2. SVR4 process information............................................................................161
20.1.3. Features for Debugging djgpp Programs ......................................................161
20.1.4. Features for Debugging MS Windows PE executables................................. 163
20.2. Embedded Operating Systems ..................................................................................... 166
20.2.1. Using gdb with VxWorks.............................................................................. 166
20.3. Embedded Processors .................................................................................................. 168
20.3.1. ARM ............................................................................................................. 168
20.3.2. Hitachi H8/300.............................................................................................. 168
20.3.3. H8/500........................................................................................................... 171
20.3.4. Mitsubishi M32R/D ...................................................................................... 171
20.3.5. M68k.............................................................................................................171
20.3.6. MIPS Embedded ...........................................................................................172
20.3.7. OpenRISC 1000 ............................................................................................173
20.3.8. PowerPC ....................................................................................................... 175
20.3.9. HP PA Embedded.......................................................................................... 176
20.3.10. Hitachi SH................................................................................................... 176
20.3.11. Tsqware Sparclet......................................................................................... 176
20.3.12. Fujitsu Sparclite .......................................................................................... 178
20.3.13. Tandem ST2000 ..........................................................................................178
Page 6

20.3.14. Zilog Z8000 ................................................................................................179
20.4. Architectures ................................................................................................................ 180
20.4.1. A29K............................................................................................................. 180
20.4.2. Alpha............................................................................................................. 180
20.4.3. MIPS ............................................................................................................. 180
21. Controlling gdb .........................................................................................................................181
21.1. Prompt.......................................................................................................................... 181
21.2. Command editing......................................................................................................... 181
21.3. Command history.........................................................................................................181
21.4. Screen size ...................................................................................................................183
21.5. Numbers.......................................................................................................................183
21.6. Configuring the current ABI ........................................................................................ 184
21.7. Optional warnings and messages................................................................................. 185
21.8. Optional messages about internal happenings ............................................................. 186
22. Canned Sequences of Commands............................................................................................ 189
22.1. User-defined commands............................................................................................... 189
22.2. User-defined command hooks...................................................................................... 190
22.3. Command files .............................................................................................................191
22.4. Commands for controlled output ................................................................................. 192
23. Command Interpreters............................................................................................................. 195
24. gdb Text User Interface ............................................................................................................ 197
24.1. TUI overview ............................................................................................................... 197
24.2. TUI Key Bindings........................................................................................................198
24.3. TUI Single Key Mode.................................................................................................. 200
24.4. TUI specific commands ...............................................................................................200
24.5. TUI configuration variables ......................................................................................... 201
25. Using gdb under gnu Emacs .................................................................................................... 203
26. The gdb/mi Interface ................................................................................................................207
26.1. Function and Purpose................................................................................................... 207
26.2. Notation and Terminology ...........................................................................................207
26.3. Acknowledgments........................................................................................................207
26.4. gdb/mi Command Syntax ............................................................................................ 207
26.4.1. gdb/mi Input Syntax...................................................................................... 207
26.4.2. gdb/mi Output Syntax ...................................................................................208
26.4.3. Simple Examples of gdb/mi Interaction ....................................................... 210
26.5. gdb/mi Compatibility with CLI ...................................................................................211
26.6. gdb/mi Output Records ................................................................................................211
26.6.1. gdb/mi Result Records .................................................................................. 211
26.6.2. gdb/mi Stream Records................................................................................. 212
26.6.3. gdb/mi Out-of-band Records ........................................................................ 212
26.7. gdb/mi Command Description Format ........................................................................ 212
26.7.1. Motivation..................................................................................................... 212
26.7.2. Introduction................................................................................................... 213
26.7.3. Commands ....................................................................................................213
26.8. gdb/mi Breakpoint table commands ............................................................................ 213
26.8.1. The -break-afterCommand..................................................................... 213
26.8.2. The -break-conditionCommand ............................................................214
26.8.3. The -break-deleteCommand................................................................... 215
26.8.4. The -break-disableCommand ................................................................216
26.8.5. The -break-enableCommand................................................................... 216
26.8.6. The -break-infoCommand....................................................................... 217
26.8.7. The -break-insertCommand................................................................... 217
26.8.8. The -break-listCommand....................................................................... 219
Page 7

26.8.9. The -break-watchCommand..................................................................... 220
26.9. gdb/mi Data Manipulation ........................................................................................... 223
26.9.1. The -data-disassembleCommand.......................................................... 223
26.9.2. The -data-evaluate-expressionCommand......................................... 225
26.9.3. The -data-list-changed-registersCommand ..................................226
26.9.4. The -data-list-register-namesCommand......................................... 227
26.9.5. The -data-list-register-valuesCommand ......................................227
26.9.6. The -data-read-memoryCommand.......................................................... 229
26.9.7. The -display-deleteCommand .............................................................. 231
26.9.8. The -display-disableCommand ............................................................231
26.9.9. The -display-enableCommand .............................................................. 231
26.9.10. The -display-insertCommand ............................................................ 232
26.9.11. The -display-listCommand................................................................. 232
26.9.12. The -environment-cdCommand ............................................................ 233
26.9.13. The -environment-directoryCommand ............................................. 233
26.9.14. The -environment-pathCommand........................................................234
26.9.15. The -environment-pwdCommand .......................................................... 235
26.10. gdb/mi Program control .............................................................................................235
26.10.1. Program termination ................................................................................... 235
26.10.2. Examples.....................................................................................................235
26.11. Command Descriptions..............................................................................................236
26.11.1. The -exec-abortCommand.....................................................................236
26.11.2. The -exec-argumentsCommand ............................................................ 236
26.11.3. The -exec-continueCommand .............................................................. 237
26.11.4. The -exec-finishCommand...................................................................237
26.11.5. The -exec-interruptCommand ............................................................ 238
26.11.6. The -exec-nextCommand ....................................................................... 239
26.11.7. The -exec-next-instructionCommand ............................................. 239
26.11.8. The -exec-returnCommand...................................................................240
26.11.9. The -exec-runCommand ......................................................................... 241
26.11.10. The -exec-show-argumentsCommand ............................................... 242
26.11.11. The -exec-stepCommand ..................................................................... 242
26.11.12. The -exec-step-instructionCommand ........................................... 243
26.11.13. The -exec-untilCommand...................................................................243
26.11.14. The -file-exec-and-symbolsCommand ........................................... 244
26.11.15. The -file-exec-fileCommand ..........................................................245
26.11.16. The -file-list-exec-sectionsCommand....................................... 245
26.11.17. The -file-list-exec-source-fileCommand ................................246
26.11.18. The -file-list-exec-source-filesCommand .............................. 246
26.11.19. The -file-list-shared-librariesCommand ................................247
26.11.20. The -file-list-symbol-filesCommand.........................................247
26.11.21. The -file-symbol-fileCommand......................................................247
26.12. Miscellaneous gdb commands in gdb/mi................................................................... 248
26.12.1. The -gdb-exitCommand ......................................................................... 248
26.12.2. The -gdb-setCommand ........................................................................... 249
26.12.3. The -gdb-showCommand ......................................................................... 249
26.12.4. The -gdb-versionCommand...................................................................250
26.12.5. The -interpreter-execCommand........................................................250
26.12.6. Synopsis ......................................................................................................250
26.12.7. gdb Command............................................................................................. 251
26.12.8. Example ......................................................................................................251
26.13. gdb/mi Stack Manipulation Commands ....................................................................251
26.13.1. The -stack-info-frameCommand........................................................251
26.13.2. The -stack-info-depthCommand........................................................251
26.13.3. The -stack-list-argumentsCommand ............................................... 252
26.13.4. The -stack-list-framesCommand...................................................... 253
Page 8

26.13.5. The -stack-list-localsCommand...................................................... 255
26.13.6. The -stack-select-frameCommand.................................................... 256
26.14. gdb/mi Symbol Query Commands ............................................................................ 256
26.14.1. The -symbol-info-addressCommand ................................................. 256
26.14.2. The -symbol-info-fileCommand........................................................257
26.14.3. The -symbol-info-functionCommand ............................................... 257
26.14.4. The -symbol-info-lineCommand........................................................258
26.14.5. The -symbol-info-symbolCommand.................................................... 258
26.14.6. The -symbol-list-functionsCommand ............................................. 258
26.14.7. The -symbol-list-linesCommand...................................................... 259
26.14.8. The -symbol-list-typesCommand...................................................... 259
26.14.9. The -symbol-list-variablesCommand ............................................. 260
26.14.10. The -symbol-locateCommand ............................................................ 260
26.14.11. The -symbol-typeCommand.................................................................261
26.15. gdb/mi Target Manipulation Commands ...................................................................261
26.15.1. The -target-attachCommand .............................................................. 261
26.15.2. The -target-compare-sectionsCommand......................................... 262
26.15.3. The -target-detachCommand .............................................................. 262
26.15.4. The -target-disconnectCommand...................................................... 262
26.15.5. The -target-downloadCommand .......................................................... 263
26.15.6. The -target-exec-statusCommand.................................................... 265
26.15.7. The -target-list-available-targetsCommand............................ 265
26.15.8. The -target-list-current-targetsCommand ................................ 266
26.15.9. The -target-list-parametersCommand...........................................266
26.15.10. The -target-selectCommand ............................................................ 266
26.16. gdb/mi Thread Commands.........................................................................................267
26.16.1. The -thread-infoCommand...................................................................267
26.16.2. The -thread-list-all-threadsCommand......................................... 268
26.16.3. The -thread-list-idsCommand .......................................................... 268
26.16.4. The -thread-selectCommand .............................................................. 269
26.17. gdb/mi Tracepoint Commands...................................................................................270
26.18. gdb/mi Variable Objects.............................................................................................270
26.18.1. Motivation for Variable Objects in gdb/mi .................................................270
26.18.2. Introduction to Variable Objects in gdb/mi................................................. 270
26.18.3. Description And Use of Operations on Variable Objects ........................... 271
26.18.4. The -var-createCommand.....................................................................271
26.18.5. The -var-deleteCommand.....................................................................272
26.18.6. The -var-set-formatCommand ............................................................ 272
26.18.7. The -var-show-formatCommand .......................................................... 272
26.18.8. The -var-info-num-childrenCommand ............................................. 273
26.18.9. The -var-list-childrenCommand...................................................... 273
26.18.10. The -var-info-typeCommand ............................................................ 273
26.18.11. The -var-info-expressionCommand ............................................... 274
26.18.12. The -var-show-attributes Command .............................................. 274
26.18.13. The -var-evaluate-expression Command...................................... 274
26.18.14. The -var-assignCommand...................................................................275
26.18.15. The -var-updateCommand...................................................................275
27. gdb Annotations ........................................................................................................................277
27.1. What is an Annotation?................................................................................................277
27.2. The Server Prefix .........................................................................................................277
27.3. Values........................................................................................................................... 277
27.4. Frames.......................................................................................................................... 279
27.5. Displays........................................................................................................................ 281
27.6. Annotation for gdb Input .............................................................................................281
27.7. Errors............................................................................................................................282
Page 9

27.8. Information on Breakpoints ......................................................................................... 282
27.9. Invalidation Notices .....................................................................................................283
27.10. Running the Program ................................................................................................. 283
27.11. Displaying Source ......................................................................................................284
27.12. Annotations We Might Want in the Future ................................................................285
28. Reporting Bugs in gdb .............................................................................................................. 287
28.1. Have you found a bug? ................................................................................................287
28.2. How to report bugs.......................................................................................................287
29. Command Line Editing ............................................................................................................ 291
29.1. Introduction to Line Editing.........................................................................................291
29.2. Readline Interaction ..................................................................................................... 291
29.2.1. Readline Bare Essentials...............................................................................291
29.2.2. Readline Movement Commands ................................................................... 292
29.2.3. Readline Killing Commands......................................................................... 292
29.2.4. Readline Arguments...................................................................................... 293
29.2.5. Searching for Commands in the History.......................................................293
29.3. Readline Init File.......................................................................................................... 294
29.3.1. Readline Init File Syntax .............................................................................. 294
29.3.2. Conditional Init Constructs...........................................................................298
29.3.3. Sample Init File............................................................................................. 299
29.4. Bindable Readline Commands..................................................................................... 301
29.4.1. Commands For Moving ................................................................................301
29.4.2. Commands For Manipulating The History ...................................................302
29.4.3. Commands For Changing Text ..................................................................... 303
29.4.4. Killing And Yanking..................................................................................... 304
29.4.5. Specifying Numeric Arguments ...................................................................305
29.4.6. Letting Readline Type For You.....................................................................305
29.4.7. Keyboard Macros.......................................................................................... 306
29.4.8. Some Miscellaneous Commands .................................................................. 306
29.5. Readline vi Mode.........................................................................................................308
30. Using History Interactively ...................................................................................................... 309
30.1. History Expansion........................................................................................................ 309
30.1.1. Event Designators ......................................................................................... 309
30.1.2. Word Designators.......................................................................................... 310
30.1.3. Modifiers....................................................................................................... 311
A. Formatting Documentation.......................................................................................................313
B. Installing gdb .............................................................................................................................. 315
B.1. Compiling gdb in another directory ..............................................................................316
B.2. Specifying names for hosts and targets ......................................................................... 317
B.3. configure options....................................................................................................... 318
C. Maintenance Commands ........................................................................................................... 319
D. gdb Remote Serial Protocol....................................................................................................... 321
D.1. Overview.......................................................................................................................321
D.2. Packets ..........................................................................................................................322
D.3. Stop Reply Packets........................................................................................................ 330
D.4. General Query Packets..................................................................................................331
D.5. Register Packet Format ................................................................................................. 334
D.6. Examples.......................................................................................................................334
D.7. File-I/O remote protocol extension ...............................................................................335
D.7.1. File-I/O Overview .......................................................................................... 335
D.7.2. Protocol basics ...............................................................................................335
D.7.3. The Frequest packet ....................................................................................... 336
D.7.4. The Freply packet...........................................................................................336
Page 10

D.7.5. Memory transfer.............................................................................................337
D.7.6. The Ctrl-C message........................................................................................337
D.7.7. Console I/O ....................................................................................................337
D.7.8. The isatty(3) call ............................................................................................ 338
D.7.9. The system(3) call.......................................................................................... 338
D.7.10. List of supported calls ..................................................................................338
D.7.11. Protocol specific representation of datatypes............................................... 347
D.7.12. Constants...................................................................................................... 349
D.7.13. File-I/O Examples ........................................................................................ 350
E. The GDB Agent Expression Mechanism..................................................................................353
E.1. General Bytecode Design.............................................................................................. 353
E.2. Bytecode Descriptions...................................................................................................355
E.3. Using Agent Expressions .............................................................................................. 359
E.4. Varying Target Capabilities ...........................................................................................359
E.5. Tracing on Symmetrix...................................................................................................360
E.6. Rationale........................................................................................................................361
F. GNU GENERAL PUBLIC LICENSE...................................................................................... 365
F.1. Preamble ........................................................................................................................ 365
F.2. How to Apply These Terms to Your New Programs...................................................... 368
G. GNU Free Documentation License........................................................................................... 371
G.1. ADDENDUM: How to use this License for your documents.......................................375
Index.................................................................................................................................................377
Page 11

Chapter 1.
Debugging with gdb
This file describes gdb, the gnu symbolic debugger.
This is the Ninth Edition, for gdb Version 2003-07-22-cvs.
Copyright (C) 1988-2003 Free Software Foundation, Inc.
Page 12

2 Chapter 1. Debugging with gdb
Page 13

Chapter 2.
Summary of gdb
The purpose of a debugger such as gdb is to allow you to see what is going on "inside" another
program while it executes--or what another program was doing at the moment it crashed.
gdb can do four main kinds of things (plus other things in support of these) to help you catch bugs in
the act:
• Start your program, specifying anything that might affect its behavior.
• Make your program stop on specified conditions.
• Examine what has happened, when your program has stopped.
• Change things in your program, so you can experiment with correcting the effects of one bug and
go on to learn about another.
You can use gdb to debug programs written in C and C++. For more information, (refer to Section
14.4 Supported languages. For more information, (refer to Section 14.4.1 C and C++.
Support for Modula-2 is partial. For information on Modula-2, refer to (refer to Section 14.4.3
Modula-2.
Debugging Pascal programs which use sets, subranges, file variables, or nested functions does not
currently work. gdb does not support entering expressions, printing values, or similar features using
Pascal syntax.
gdb can be used to debug programs written in Fortran, although it may be necessary to refer to some
variables with a trailing underscore.
gdb can be used to debug programs written in Objective-C, using either the Apple/NeXT or the GNU
Objective-C runtime.
2.1. Free software
gdb is free software, protected by the gnu General Public License (GPL). The GPL gives you the free-
dom to copy or adapt a licensed program--but every person getting a copy also gets with it the freedom
to modify that copy (which means that they must get access to the source code), and the freedom to
distribute further copies. Typical software companies use copyrights to limit your freedoms; the Free
Software Foundation uses the GPL to preserve these freedoms.
Fundamentally, the General Public License is a license which says that you have these freedoms and
that you cannot take these freedoms away from anyone else.
2.2. Free Software Needs Free Documentation
The biggest deficiency in the free software community today is not in the software--it is the lack of
good free documentation that we can include with the free software. Many of our most important
programs do not come with free reference manuals and free introductory texts. Documentation is an
essential part of any software package; when an important free software package does not come with
a free manual and a free tutorial, that is a major gap. We have many such gaps today.
Consider Perl, for instance. The tutorial manuals that people normally use are non-free. How did this
come about? Because the authors of those manuals published them with restrictive terms--no copying,
no modification, source files not available--which exclude them from the free software world.
Page 14

4 Chapter 2. Summary of gdb
That wasn’t the first time this sort of thing happened, and it was far from the last. Many times we
have heard a GNU user eagerly describe a manual that he is writing, his intended contribution to the
community, only to learn that he had ruined everything by signing a publication contract to make it
non-free.
Free documentation, like free software, is a matter of freedom, not price. The problem with the nonfree manual is not that publishers charge a price for printed copies--that in itself is fine. (The Free
Software Foundation sells printed copies of manuals, too.) The problem is the restrictions on the use
of the manual. Free manuals are available in source code form, and give you permission to copy and
modify. Non-free manuals do not allow this.
The criteria of freedom for a free manual are roughly the same as for free software. Redistribution
(including the normal kinds of commercial redistribution) must be permitted, so that the manual can
accompany every copy of the program, both on-line and on paper.
Permission for modification of the technical content is crucial too. When people modify the software,
adding or changing features, if they are conscientious they will change the manual too--so they can
provide accurate and clear documentation for the modified program. A manual that leaves you no
choice but to write a new manual to document a changed version of the program is not really available
to our community.
Some kinds of limits on the way modification is handled are acceptable. For example, requirements
to preserve the original author’s copyright notice, the distribution terms, or the list of authors, are ok.
It is also no problem to require modified versions to include notice that they were modified. Even
entire sections that may not be deleted or changed are acceptable, as long as they deal with nontechnical topics (like this one). These kinds of restrictions are acceptable because they don’t obstruct the
community’s normal use of the manual.
However, it must be possible to modify all the technical content of the manual, and then distribute the
result in all the usual media, through all the usual channels. Otherwise, the restrictions obstruct the
use of the manual, it is not free, and we need another manual to replace it.
Please spread the word about this issue. Our community continues to lose manuals to proprietary
publishing. If we spread the word that free software needs free reference manuals and free tutorials,
perhaps the next person who wants to contribute by writing documentation will realize, before it is
too late, that only free manuals contribute to the free software community.
If you are writing documentation, please insist on publishing it under the GNU Free Documentation
License or another free documentation license. Remember that this decision requires your approval-you don’t have to let the publisher decide. Some commercial publishers will use a free license if you
insist, but they will not propose the option; it is up to you to raise the issue and say firmly that this is
what you want. If the publisher you are dealing with refuses, please try other publishers. If you’re not
sure whether a proposed license is free, write to mailto:licensing@@gnu.org.
You can encourage commercial publishers to sell more free, copylefted manuals and tutorials by
buying them, and particularly by buying copies from the publishers that paid for their writing or
for major improvements. Meanwhile, try to avoid buying non-free documentation at all. Check the
distribution terms of a manual before you buy it, and insist that whoever seeks your business must
respect your freedom. Check the history of the book, and try to reward the publishers that have paid
or pay the authors to work on it.
The Free Software Foundation maintains a list of free documentation published by other publishers,
at http://www.fsf.org/doc/other-free-books.html.
2.3. Contributors to gdb
Richard Stallman was the original author of gdb, and of many other gnu programs. Many others have
contributed to its development. This section attempts to credit major contributors. One of the virtues
of free software is that everyone is free to contribute to it; with regret, we cannot actually acknowledge
everyone here. The file ChangeLog in the gdb distribution approximates a blow-by-blow account.
Page 15

Chapter 2. Summary of gdb 5
Changes much prior to version 2.0 are lost in the mists of time.
Plea: Additions to this section are particularly welcome. If you or your friends (or enemies, to be evenhanded) have been unfairly omitted from this list, we would like to add your names!
So that they may not regard their many labors as thankless, we particularly thank those who shepherded gdb through major releases: Andrew Cagney (releases 6.0, 5.3, 5.2, 5.1 and 5.0); Jim Blandy
(release 4.18); Jason Molenda (release 4.17); Stan Shebs (release 4.14); Fred Fish (releases 4.16, 4.15,
4.13, 4.12, 4.11, 4.10, and 4.9); Stu Grossman and John Gilmore (releases 4.8, 4.7, 4.6, 4.5, and 4.4);
John Gilmore (releases 4.3, 4.2, 4.1, 4.0, and 3.9); Jim Kingdon (releases 3.5, 3.4, and 3.3); and Randy
Smith (releases 3.2, 3.1, and 3.0).
Richard Stallman, assisted at various times by Peter TerMaat, Chris Hanson, and Richard Mlynarik,
handled releases through 2.8.
Michael Tiemann is the author of most of the gnu C++ support in gdb, with significant additional
contributions from Per Bothner and Daniel Berlin. James Clark wrote the gnu C++ demangler. Early
work on C++ was by Peter TerMaat (who also did much general update work leading to release 3.0).
gdb uses the BFD subroutine library to examine multiple object-file formats; BFD was a joint project
of David V. Henkel-Wallace, Rich Pixley, Steve Chamberlain, and John Gilmore.
David Johnson wrote the original COFF support; Pace Willison did the original support for encapsulated COFF.
Brent Benson of Harris Computer Systems contributed DWARF 2 support.
Adam de Boor and Bradley Davis contributed the ISI Optimum V support. Per Bothner, Noboyuki
Hikichi, and Alessandro Forin contributed MIPS support. Jean-Daniel Fekete contributed Sun 386i
support. Chris Hanson improved the HP9000 support. Noboyuki Hikichi and Tomoyuki Hasei contributed Sony/News OS 3 support. David Johnson contributed Encore Umax support. Jyrki Kuoppala contributed Altos 3068 support. Jeff Law contributed HP PA and SOM support. Keith Packard
contributed NS32K support. Doug Rabson contributed Acorn Risc Machine support. Bob Rusk contributed Harris Nighthawk CX-UX support. Chris Smith contributed Convex support (and Fortran
debugging). Jonathan Stone contributed Pyramid support. Michael Tiemann contributed SPARC support. Tim Tucker contributed support for the Gould NP1 and Gould Powernode. Pace Willison contributed Intel 386 support. Jay Vosburgh contributed Symmetry support. Marko Mlinar contributed
OpenRISC 1000 support.
Andreas Schwab contributed M68K gnu/Linux support.
Rich Schaefer and Peter Schauer helped with support of SunOS shared libraries.
Jay Fenlason and Roland McGrath ensured that gdb and GAS agree about several machine instruction
sets.
Patrick Duval, Ted Goldstein, Vikram Koka and Glenn Engel helped develop remote debugging. Intel
Corporation, Wind River Systems, AMD, and ARM contributed remote debugging modules for the
i960, VxWorks, A29K UDI, and RDI targets, respectively.
Brian Fox is the author of the readline libraries providing command-line editing and command history.
Andrew Beers of SUNY Buffalo wrote the language-switching code, the Modula-2 support, and contributed the Languages chapter of this manual.
Fred Fish wrote most of the support for Unix System Vr4. He also enhanced the command-completion
support to cover C++ overloaded symbols.
Hitachi America, Ltd. sponsored the support for H8/300, H8/500, and Super-H processors.
NEC sponsored the support for the v850, Vr4xxx, and Vr5xxx processors.
Mitsubishi sponsored the support for D10V, D30V, and M32R/D processors.
Toshiba sponsored the support for the TX39 Mips processor.
Page 16

6 Chapter 2. Summary of gdb
Matsushita sponsored the support for the MN10200 and MN10300 processors.
Fujitsu sponsored the support for SPARClite and FR30 processors.
Kung Hsu, Jeff Law, and Rick Sladkey added support for hardware watchpoints.
Michael Snyder added support for tracepoints.
Stu Grossman wrote gdbserver.
Jim Kingdon, Peter Schauer, Ian Taylor, and Stu Grossman made nearly innumerable bug fixes and
cleanups throughout gdb.
The following people at the Hewlett-Packard Company contributed support for the PA-RISC 2.0 architecture, HP-UX 10.20, 10.30, and 11.0 (narrow mode), HP’s implementation of kernel threads,
HP’s aC++ compiler, and the terminal user interface: Ben Krepp, Richard Title, John Bishop, Susan Macchia, Kathy Mann, Satish Pai, India Paul, Steve Rehrauer, and Elena Zannoni. Kim Haase
provided HP-specific information in this manual.
DJ Delorie ported gdb to MS-DOS, for the DJGPP project. Robert Hoehne made significant contributions to the DJGPP port.
Cygnus Solutions has sponsored gdb maintenance and much of its development since 1991. Cygnus
engineers who have worked on gdb fulltime include Mark Alexander, Jim Blandy, Per Bothner, Kevin
Buettner, Edith Epstein, Chris Faylor, Fred Fish, Martin Hunt, Jim Ingham, John Gilmore, Stu Grossman, Kung Hsu, Jim Kingdon, John Metzler, Fernando Nasser, Geoffrey Noer, Dawn Perchik, Rich
Pixley, Zdenek Radouch, Keith Seitz, Stan Shebs, David Taylor, and Elena Zannoni. In addition, Dave
Brolley, Ian Carmichael, Steve Chamberlain, Nick Clifton, JT Conklin, Stan Cox, DJ Delorie, Ulrich
Drepper, Frank Eigler, Doug Evans, Sean Fagan, David Henkel-Wallace, Richard Henderson, Jeff
Holcomb, Jeff Law, Jim Lemke, Tom Lord, Bob Manson, Michael Meissner, Jason Merrill, Catherine
Moore, Drew Moseley, Ken Raeburn, Gavin Romig-Koch, Rob Savoye, Jamie Smith, Mike Stump,
Ian Taylor, Angela Thomas, Michael Tiemann, Tom Tromey, Ron Unrau, Jim Wilson, and David Zuhn
have made contributions both large and small.
Jim Blandy added support for preprocessor macros, while working for Red Hat.
Page 17

Chapter 3.
A Sample gdb Session
You can use this manual at your leisure to read all about gdb. However, a handful of commands are
enough to get started using the debugger. This chapter illustrates those commands.
One of the preliminary versions of gnu m4 (a generic macro processor) exhibits the following bug:
sometimes, when we change its quote strings from the default, the commands used to capture one
macro definition within another stop working. In the following short m4 session, we define a macro
foo which expands to 0000; we then use the m4 built-in defn to define bar as the same thing. How-
ever, when we change the open quote string to
QUOTE
and the close quote string to
UNQUOTE
,
the same procedure fails to define a new synonym baz:
$ cd gnu/m4
$ ./m4
define(foo,0000)
foo
0000
define(bar,defn(‘foo’))
bar
0000
changequote(
QUOTE,UNQUOTE)
define(baz,defn(QUOTEfooUNQUOTE))
baz
C-d
m4: End of input: 0: fatal error: EOF in string
Let us use gdb to try to see what is going on.
$ gdb m4
gdb is free software and you are welcome to distribute copies
of it under certain conditions; type "show copying" to see
the conditions.
There is absolutely no warranty for gdb; type "show warranty"
for details.
gdb 2003-07-22-cvs, Copyright 1999 Free Software Foundation, Inc...
(gdb)
gdb reads only enough symbol data to know where to find the rest when needed; as a result, the first
prompt comes up very quickly. We now tell gdb to use a narrower display width than usual, so that
examples fit in this manual.
(gdb) set width 70
We need to see how the m4 built-in changequote works. Having looked at the source, we know the
relevant subroutine is m4_changequote, so we set a breakpoint there with the gdb break command.
Page 18

8 Chapter 3. A Sample gdb Session
(gdb) break m4_changequote
Breakpoint 1 at 0x62f4: file builtin.c, line 879.
Using the run command, we start m4 running under gdb control; as long as control does not reach the
m4_changequote subroutine, the program runs as usual:
(gdb) run
Starting program: /work/Editorial/gdb/gnu/m4/m4
define(foo,0000)
foo
0000
To trigger the breakpoint, we call changequote. gdb suspends execution of m4, displaying information about the context where it stops.
changequote(QUOTE,UNQUOTE)
Breakpoint 1, m4_changequote (argc=3, argv=0x33c70)
at builtin.c:879
879 if (bad_argc(TOKEN_DATA_TEXT(argv[0]),argc,1,3))
Now we use the command n (next) to advance execution to the next line of the current function.
(gdb) n
882 set_quotes((argc= 2) ? TOKEN_DATA_TEXT(argv[1])\
: nil,
set_quotes looks like a promising subroutine. We can go into it by using the command s (step)
instead of next. step goes to the next line to be executed in any subroutine, so it steps into
set_quotes.
(gdb) s
set_quotes (lq=0x34c78 "QUOTE", rq=0x34c88 "UNQUOTE")
at input.c:530
530 if (lquote != def_lquote)
The display that shows the subroutine where m4 is now suspended (and its arguments) is called a stack
frame display. It shows a summary of the stack. We can use the backtrace command (which can
also be spelled bt), to see where we are in the stack as a whole: the backtrace command displays a
stack frame for each active subroutine.
(gdb) bt
#0 set_quotes (lq=0x34c78 "
QUOTE", rq=0x34c88 "UNQUOTE")
at input.c:530
#1 0x6344 in m4_changequote (argc=3, argv=0x33c70)
at builtin.c:882
#2 0x8174 in expand_macro (sym=0x33320) at macro.c:242
#3 0x7a88 in expand_token (obs=0x0, t=209696, td=0xf7fffa30)
at macro.c:71
Page 19

Chapter 3. A Sample gdb Session 9
#4 0x79dc in expand_input () at macro.c:40
#5 0x2930 in main (argc=0, argv=0xf7fffb20) at m4.c:195
We step through a few more lines to see what happens. The first two times, we can use s; the next two
times we use n to avoid falling into the xstrdup subroutine.
(gdb) s
0x3b5c 532 if (rquote != def_rquote)
(gdb) s
0x3b80 535 lquote = (lq == nil || *lq == ’\0’) ? \
def_lquote : xstrdup(lq);
(gdb) n
536 rquote = (rq == nil || *rq == ’\0’) ? def_rquote\
: xstrdup(rq);
(gdb) n
538 len_lquote = strlen(rquote);
The last line displayed looks a little odd; we can examine the variables lquote and rquote to see
if they are in fact the new left and right quotes we specified. We use the command p (print) to see
their values.
(gdb) p lquote
$1 = 0x35d40 "QUOTE"
(gdb) p rquote
$2 = 0x35d50 "UNQUOTE"
lquote and rquote are indeed the new left and right quotes. To look at some context, we can display
ten lines of source surrounding the current line with the l (list) command.
(gdb) l
533 xfree(rquote);
534
535 lquote = (lq == nil || *lq == ’\0’) ? def_lquote\
: xstrdup (lq);
536 rquote = (rq == nil || *rq == ’\0’) ? def_rquote\
: xstrdup (rq);
537
538 len_lquote = strlen(rquote);
539 len_rquote = strlen(lquote);
540 }
541
542 void
Let us step past the two lines that set len_lquote and len_rquote, and then examine the values of
those variables.
(gdb) n
539 len_rquote = strlen(lquote);
(gdb) n
540 }
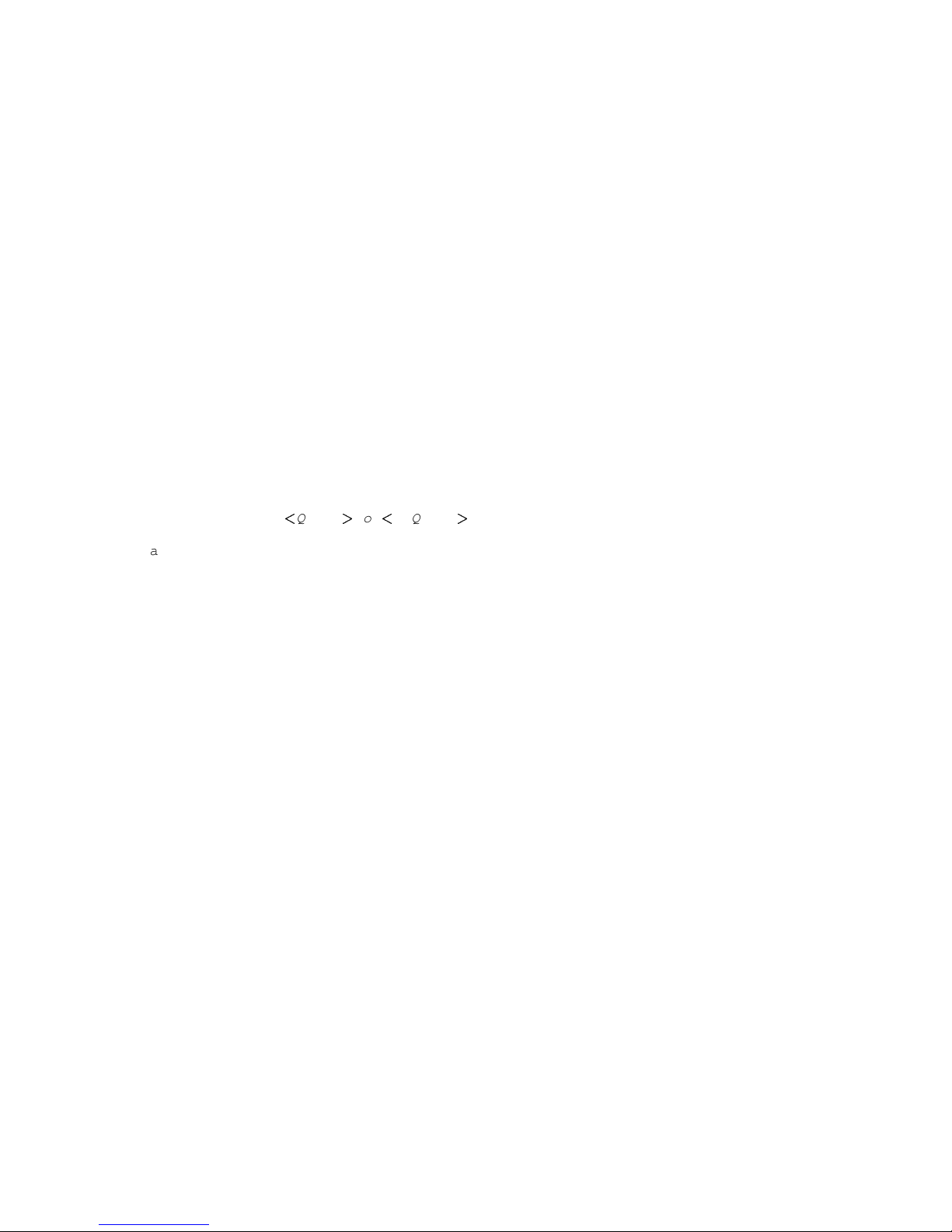
(gdb) p len_lquote
$3 = 9
Page 20
10 Chapter 3. A Sample gdb Session
(gdb) p len_rquote
$4 = 7
That certainly looks wrong, assuming len_lquote and len_rquote are meant to be the lengths of
lquote and rquote respectively. We can set them to better values using the p command, since it can
print the value of any expression--and that expression can include subroutine calls and assignments.
(gdb) p len_lquote=strlen(lquote)
$5 = 7
(gdb) p len_rquote=strlen(rquote)
$6 = 9
Is that enough to fix the problem of using the new quotes with the m4 built-in defn? We can allow m4
to continue executing with the c (continue) command, and then try the example that caused trouble
initially:
(gdb) c
Continuing.
define(baz,defn(
QUOTEfooUNQUOTE))
baz
0000
Success! The new quotes now work just as well as the default ones. The problem seems to have been
just the two typos defining the wrong lengths. We allow m4 exit by giving it an EOF as input:
C-d
Program exited normally.
The message Program exited normally. is from gdb; it indicates m4 has finished executing. We
can end our gdb session with the gdb quit command.
(gdb) quit
Page 21

Chapter 4.
Getting In and Out of gdb
This chapter discusses how to start gdb, and how to get out of it. The essentials are:
• type gdb to start gdb.
• type quit or C-d to exit.
4.1. Invoking gdb
Invoke gdb by running the program gdb. Once started, gdb reads commands from the terminal until
you tell it to exit.
You can also run gdb with a variety of arguments and options, to specify more of your debugging
environment at the outset.
The command-line options described here are designed to cover a variety of situations; in some environments, some of these options may effectively be unavailable.
The most usual way to start gdb is with one argument, specifying an executable program:
gdb program
You can also start with both an executable program and a core file specified:
gdb program core
You can, instead, specify a process ID as a second argument, if you want to debug a running process:
gdb program 1234
would attach gdb to process 1234 (unless you also have a file named 1234; gdb does check for a core
file first).
Taking advantage of the second command-line argument requires a fairly complete operating system;
when you use gdb as a remote debugger attached to a bare board, there may not be any notion of
"process", and there is often no way to get a core dump. gdb will warn you if it is unable to attach or
to read core dumps.
You can optionally have gdb pass any arguments after the executable file to the inferior using -args.
This option stops option processing.
gdb --args gcc -O2 -c foo.c
This will cause gdb to debug gcc, and to set gcc’s command-line arguments (Refer to Section 6.3
Your program’s arguments) to -O2 -c foo.c.
You can run gdb without printing the front material, which describes gdb’s non-warranty, by specifying -silent:
Page 22

12 Chapter 4. Getting In and Out of gdb
gdb -silent
You can further control how gdb starts up by using command-line options. gdb itself can remind you
of the options available.
Type
gdb -help
to display all available options and briefly describe their use (gdb -h is a shorter equivalent).
All options and command line arguments you give are processed in sequential order. The order makes
a difference when the -x option is used.
4.1.1. Choosing files
When gdb starts, it reads any arguments other than options as specifying an executable file and core
file (or process ID). This is the same as if the arguments were specified by the -se and -c (or -p
options respectively. (gdb reads the first argument that does not have an associated option flag as
equivalent to the -se option followed by that argument; and the second argument that does not have
an associated option flag, if any, as equivalent to the -c/-p option followed by that argument.) If the
second argument begins with a decimal digit, gdb will first attempt to attach to it as a process, and if
that fails, attempt to open it as a corefile. If you have a corefile whose name begins with a digit, you
can prevent gdb from treating it as a pid by prefixing it with ./, eg. ./12345.
If gdb has not been configured to included core file support, such as for most embedded targets, then
it will complain about a second argument and ignore it.
Many options have both long and short forms; both are shown in the following list. gdb also recognizes
the long forms if you truncate them, so long as enough of the option is present to be unambiguous.
(If you prefer, you can flag option arguments with - rather than -, though we illustrate the more usual
convention.)
-symbols file
-s file
Read symbol table from file file.
-exec file
-e file
Use file file as the executable file to execute when appropriate, and for examining pure data in
conjunction with a core dump.
-se file
Read symbol table from file file and use it as the executable file.
-core file
-c file
Use file file as a core dump to examine.
Page 23

Chapter 4. Getting In and Out of gdb 13
-c number
-pid number
-p number
Connect to process ID number, as with the attach command. If there is no such process, gdb
will attempt to open a core file named number.
-command file
-x file
Execute gdb commands from file file. Refer to Section 22.3 Command files.
-directory directory
-d directory
Add directory to the path to search for source files.
-m
-mapped
Warning: this option depends on operating system facilities that are not supported on all systems.
If memory-mapped files are available on your system through the mmap system call, you can
use this option to have gdb write the symbols from your program into a reusable file in the
current directory. If the program you are debugging is called /tmp/fred, the mapped symbol
file is /tmp/fred.syms. Future gdb debugging sessions notice the presence of this file, and
can quickly map in symbol information from it, rather than reading the symbol table from the
executable program.
The .syms file is specific to the host machine where gdb is run. It holds an exact image of the
internal gdb symbol table. It cannot be shared across multiple host platforms.
-r
-readnow
Read each symbol file’s entire symbol table immediately, rather than the default, which is to read
it incrementally as it is needed. This makes startup slower, but makes future operations faster.
You typically combine the -mapped and -readnow options in order to build a .syms file that contains
complete symbol information. (Refer to Section 17.1 Commands to specify files for information on
.syms files.) A simple gdb invocation to do nothing but build a .syms file for future use is:
gdb -batch -nx -mapped -readnow programname
4.1.2. Choosing modes
You can run gdb in various alternative modes--for example, in batch mode or quiet mode.
-nx
-n
Do not execute commands found in any initialization files. Normally, gdb executes the commands
in these files after all the command options and arguments have been processed. Refer to Section
22.3 Command files.
Page 24

14 Chapter 4. Getting In and Out of gdb
-quiet
-silent
-q
"Quiet". Do not print the introductory and copyright messages. These messages are also suppressed in batch mode.
-batch
Run in batch mode. Exit with status 0 after processing all the command files specified with -x
(and all commands from initialization files, if not inhibited with -n). Exit with nonzero status if
an error occurs in executing the gdb commands in the command files.
Batch mode may be useful for running gdb as a filter, for example to download and run a program
on another computer; in order to make this more useful, the message
Program exited normally.
(which is ordinarily issued whenever a program running under gdb control terminates) is not
issued when running in batch mode.
-nowindows
-nw
"No windows". If gdb comes with a graphical user interface (GUI) built in, then this option tells
gdb to only use the command-line interface. If no GUI is available, this option has no effect.
-windows
-w
If gdb includes a GUI, then this option requires it to be used if possible.
-cd directory
Run gdb using directory as its working directory, instead of the current directory.
-fullname
-f
gnu Emacs sets this option when it runs gdb as a subprocess. It tells gdb to output the full file
name and line number in a standard, recognizable fashion each time a stack frame is displayed
(which includes each time your program stops). This recognizable format looks like two \032
characters, followed by the file name, line number and character position separated by colons,
and a newline. The Emacs-to-gdb interface program uses the two \032 characters as a signal to
display the source code for the frame.
-epoch
The Epoch Emacs-gdb interface sets this option when it runs gdb as a subprocess. It tells gdb
to modify its print routines so as to allow Epoch to display values of expressions in a separate
window.
-annotate level
This option sets the annotation level inside gdb. Its effect is identical to using set annotate
level (refer to Chapter 27 gdb Annotations). Annotation level controls how much information
does gdb print together with its prompt, values of expressions, source lines, and other types of
output. Level 0 is the normal, level 1 is for use when gdb is run as a subprocess of gnu Emacs,
level 2 is the maximum annotation suitable for programs that control gdb.
Page 25

Chapter 4. Getting In and Out of gdb 15
-async
Use the asynchronous event loop for the command-line interface. gdb processes all events, such
as user keyboard input, via a special event loop. This allows gdb to accept and process user
commands in parallel with the debugged process being run1, so you don’t need to wait for control
to return to gdb before you type the next command. (Note: as of version 5.1, the target side of
the asynchronous operation is not yet in place, so -async does not work fully yet.)
When the standard input is connected to a terminal device, gdb uses the asynchronous event loop
by default, unless disabled by the -noasync option.
-noasync
Disable the asynchronous event loop for the command-line interface.
-args
Change interpretation of command line so that arguments following the executable file are passed
as command line arguments to the inferior. This option stops option processing.
-baud bps
-b bps
Set the line speed (baud rate or bits per second) of any serial interface used by gdb for remote
debugging.
-tty device
-t device
Run using device for your program’s standard input and output.
-tui
Activate the Terminal User Interface when starting. The Terminal User Interface manages several
text windows on the terminal, showing source, assembly, registers and gdb command outputs
(refer to Chapter 24 gdb Text User Interface). Do not use this option if you run gdb from Emacs
(refer to Chapter 25 Using gdb under gnu Emacs).
-interpreter interp
Use the interpreter interp for interface with the controlling program or device. This option is
meant to be set by programs which communicate with gdb using it as a back end (refer to Chapter
23 Command Interpreters.
-interpreter=mi (or -interpreter=mi2) causes gdb to use the current gdb/mi interface
(refer to Chapter 26 The gdb/mi Interface). The previous gdb/mi interface, included in gdb version 5.3, can be selected with -interpreter=mi1. Earlier gdb/mi interfaces are not supported.
-write
Open the executable and core files for both reading and writing. This is equivalent to the set
write on command inside gdb (refer to Section 16.6 Patching programs).
-statistics
This option causes gdb to print statistics about time and memory usage after it completes each
command and returns to the prompt.
1. gdb built with djgpp tools for MS-DOS/MS-Windows supports this mode of operation, but the event loop is
suspended when the debuggee runs.
Page 26

16 Chapter 4. Getting In and Out of gdb
-version
This option causes gdb to print its version number and no-warranty blurb, and exit.
4.2. Quitting gdb
quit [expression]
q
To exit gdb, use the quit command (abbreviated q), or type an end-of-file character (usually
C-d). If you do not supply expression, gdb will terminate normally; otherwise it will terminate
using the result of expression as the error code.
An interrupt (often C-c) does not exit from gdb, but rather terminates the action of any gdb command
that is in progress and returns to gdb command level. It is safe to type the interrupt character at any
time because gdb does not allow it to take effect until a time when it is safe.
If you have been using gdb to control an attached process or device, you can release it with the detach
command (refer to Section 6.7 Debugging an already-running process).
4.3. Shell commands
If you need to execute occasional shell commands during your debugging session, there is no need to
leave or suspend gdb; you can just use the shell command.
shell command string
Invoke a standard shell to execute command string. If it exists, the environment variable SHELL
determines which shell to run. Otherwise gdb uses the default shell (/bin/sh on Unix systems,
COMMAND.COM on MS-DOS, etc.).
The utility make is often needed in development environments. You do not have to use the shell
command for this purpose in gdb:
make make-args
Execute the make program with the specified arguments. This is equivalent to shell make
make-args.
4.4. Logging output
You may want to save the output of gdb commands to a file. There are several commands to control
gdb’s logging.
set logging on
Enable logging.
set logging off
Disable logging.
Page 27

Chapter 4. Getting In and Out of gdb 17
set logging file file
Change the name of the current logfile. The default logfile is gdb.txt.
set logging overwrite [on|off]
By default, gdb will append to the logfile. Set overwrite if you want set logging on to
overwrite the logfile instead.
set logging redirect [on|off]
By default, gdb output will go to both the terminal and the logfile. Set redirect if you want
output to go only to the log file.
show logging
Show the current values of the logging settings.
Page 28

18 Chapter 4. Getting In and Out of gdb
Page 29

Chapter 5.
gdb Commands
You can abbreviate a gdb command to the first few letters of the command name, if that abbreviation
is unambiguous; and you can repeat certain gdb commands by typing just [RET]. You can also use
the [TAB] key to get gdb to fill out the rest of a word in a command (or to show you the alternatives
available, if there is more than one possibility).
5.1. Command syntax
A gdb command is a single line of input. There is no limit on how long it can be. It starts with a
command name, which is followed by arguments whose meaning depends on the command name.
For example, the command step accepts an argument which is the number of times to step, as in
step 5. You can also use the step command with no arguments. Some commands do not allow any
arguments.
gdb command names may always be truncated if that abbreviation is unambiguous. Other possible
command abbreviations are listed in the documentation for individual commands. In some cases,
even ambiguous abbreviations are allowed; for example, s is specially defined as equivalent to step
even though there are other commands whose names start with s. You can test abbreviations by using
them as arguments to the help command.
A blank line as input to gdb (typing just [RET]) means to repeat the previous command. Certain
commands (for example, run) will not repeat this way; these are commands whose unintentional
repetition might cause trouble and which you are unlikely to want to repeat.
The list and x commands, when you repeat them with [RET], construct new arguments rather than
repeating exactly as typed. This permits easy scanning of source or memory.
gdb can also use [RET] in another way: to partition lengthy output, in a way similar to the common
utility more (refer to Section 21.4 Screen size). Since it is easy to press one [RET] too many in this
situation, gdb disables command repetition after any command that generates this sort of display.
Any text from a # to the end of the line is a comment; it does nothing. This is useful mainly in
command files (refer to Section 22.3 Command files).
The C-o binding is useful for repeating a complex sequence of commands. This command accepts
the current line, like RET, and then fetches the next line relative to the current line from the history
for editing.
5.2. Command completion
gdb can fill in the rest of a word in a command for you, if there is only one possibility; it can also
show you what the valid possibilities are for the next word in a command, at any time. This works for
gdb commands, gdb subcommands, and the names of symbols in your program.
Press the [TAB] key whenever you want gdb to fill out the rest of a word. If there is only one possibility,
gdb fills in the word, and waits for you to finish the command (or press [RET] to enter it). For example,
if you type
(gdb) info bre [TAB]
gdb fills in the rest of the word breakpoints, since that is the only info subcommand beginning
with bre:
Page 30

20 Chapter 5. gdb Commands
(gdb) info breakpoints
You can either press [RET] at this point, to run the info breakpoints command, or backspace
and enter something else, if breakpoints does not look like the command you expected. (If you
were sure you wanted info breakpoints in the first place, you might as well just type [RET]
immediately after info bre, to exploit command abbreviations rather than command completion).
If there is more than one possibility for the next word when you press [TAB], gdb sounds a bell.
You can either supply more characters and try again, or just press [TAB] a second time; gdb displays
all the possible completions for that word. For example, you might want to set a breakpoint on a
subroutine whose name begins with make_, but when you type b make_[TAB] gdb just sounds
the bell. Typing [TAB] again displays all the function names in your program that begin with those
characters, for example:
(gdb) b make_ [TAB]
gdb sounds bell; press [TAB] again, to see: make_a_section_from_file make_environ
make_abs_section make_function_type
make_blockvector make_pointer_type
make_cleanup make_reference_type
make_command make_symbol_completion_list
(gdb) b make_
After displaying the available possibilities, gdb copies your partial input (b make_ in the example)
so you can finish the command.
If you just want to see the list of alternatives in the first place, you can press M-? rather than pressing
[TAB] twice. M-? means [META] ?. You can type this either by holding down a key designated as
the [META] shift on your keyboard (if there is one) while typing ?, or as [ESC] followed by ?.
Sometimes the string you need, while logically a "word", may contain parentheses or other characters
that gdb normally excludes from its notion of a word. To permit word completion to work in this
situation, you may enclose words in ’ (single quote marks) in gdb commands.
The most likely situation where you might need this is in typing the name of a C++ function. This
is because C++ allows function overloading (multiple definitions of the same function, distinguished
by argument type). For example, when you want to set a breakpoint you may need to distinguish
whether you mean the version of name that takes an int parameter, name(int), or the version that
takes a float parameter, name(float). To use the word-completion facilities in this situation, type
a single quote ’ at the beginning of the function name. This alerts gdb that it may need to consider
more information than usual when you press [TAB] or M-? to request word completion:
(gdb) b ’bubble( M-?
bubble(double,double) bubble(int,int)
(gdb) b ’bubble(
In some cases, gdb can tell that completing a name requires using quotes. When this happens, gdb
inserts the quote for you (while completing as much as it can) if you do not type the quote in the first
place:
(gdb) b bub [TAB]
gdb alters your input line to the following, and rings a bell: (gdb) b ’bubble(
Page 31

Chapter 5. gdb Commands 21
In general, gdb can tell that a quote is needed (and inserts it) if you have not yet started typing the
argument list when you ask for completion on an overloaded symbol.
For more information about overloaded functions, refer to Section 14.4.1.3 C++expressions. You can
use the command set overload-resolution off to disable overload resolution; refer to Section
14.4.1.7 gdb features for C++.
5.3. Getting help
You can always ask gdb itself for information on its commands, using the command help.
help
h
You can use help (abbreviated h) with no arguments to display a short list of named classes of
commands:
(gdb) help
List of classes of commands:
aliases -- Aliases of other commands
breakpoints -- Making program stop at certain points
data -- Examining data
files -- Specifying and examining files
internals -- Maintenance commands
obscure -- Obscure features
running -- Running the program
stack -- Examining the stack
status -- Status inquiries
support -- Support facilities
tracepoints -- Tracing of program execution without
stopping the program
user-defined -- User-defined commands
Type "help" followed by a class name for a list of
commands in that class.
Type "help" followed by command name for full
documentation.
Command name abbreviations are allowed if unambiguous.
(gdb)
help class
Using one of the general help classes as an argument, you can get a list of the individual commands in that class. For example, here is the help display for the class status:
(gdb) help status
Status inquiries.
List of commands:
info -- Generic command for showing things
about the program being debugged
show -- Generic command for showing things
about the debugger
Type "help" followed by command name for full
documentation.
Command name abbreviations are allowed if unambiguous.
(gdb)
Page 32

22 Chapter 5. gdb Commands
help command
With a command name as help argument, gdb displays a short paragraph on how to use that
command.
apropos args
The apropos args command searches through all of the gdb commands, and their documentation, for the regular expression specified in args. It prints out all matches found. For example:
apropos reload
results in:
set symbol-reloading -- Set dynamic symbol table reloading
multiple times in one run
show symbol-reloading -- Show dynamic symbol table reloading
multiple times in one run
complete args
The complete args command lists all the possible completions for the beginning of a command. Use args to specify the beginning of the command you want completed. For example:
complete i
results in:
if
ignore
info
inspect
This is intended for use by gnu Emacs.
In addition to help, you can use the gdb commands info and show to inquire about the state of
your program, or the state of gdb itself. Each command supports many topics of inquiry; this manual
introduces each of them in the appropriate context. The listings under info and under show in the
Index point to all the sub-commands. Refer to Red Hat Enterprise Linux 3.
info
This command (abbreviated i) is for describing the state of your program. For example, you can
list the arguments given to your program with info args, list the registers currently in use with
info registers, or list the breakpoints you have set with info breakpoints. You can get
a complete list of the info sub-commands with help info.
set
You can assign the result of an expression to an environment variable with set. For example,
you can set the gdb prompt to a $-sign with set prompt $.
show
In contrast to info, show is for describing the state of gdb itself. You can change most of the
things you can show, by using the related command set; for example, you can control what
number system is used for displays with set radix, or simply inquire which is currently in use
with show radix.
To display all the settable parameters and their current values, you can use show with no arguments; you may also use info set. Both commands produce the same display.
Page 33

Chapter 5. gdb Commands 23
Here are three miscellaneous show subcommands, all of which are exceptional in lacking corresponding set commands:
show version
Show what version of gdb is running. You should include this information in gdb bug-reports. If
multiple versions of gdb are in use at your site, you may need to determine which version of gdb
you are running; as gdb evolves, new commands are introduced, and old ones may wither away.
Also, many system vendors ship variant versions of gdb, and there are variant versions of gdb in
gnu/Linux distributions as well. The version number is the same as the one announced when you
start gdb.
show copying
Display information about permission for copying gdb.
show warranty
Display the gnu "NO WARRANTY" statement, or a warranty, if your version of gdb comes with
one.
Page 34

24 Chapter 5. gdb Commands
Page 35

Chapter 6.
Running Programs Under gdb
When you run a program under gdb, you must first generate debugging information when you compile
it.
You may start gdb with its arguments, if any, in an environment of your choice. If you are doing native
debugging, you may redirect your program’s input and output, debug an already running process, or
kill a child process.
6.1. Compiling for debugging
In order to debug a program effectively, you need to generate debugging information when you compile it. This debugging information is stored in the object file; it describes the data type of each variable
or function and the correspondence between source line numbers and addresses in the executable code.
To request debugging information, specify the -g option when you run the compiler.
Most compilers do not include information about preprocessor macros in the debugging information
if you specify the -g flag alone, because this information is rather large. Version 3.1 of gcc, the
gnu C compiler, provides macro information if you specify the options -gdwarf-2 and -g3; the
former option requests debugging information in the Dwarf 2 format, and the latter requests "extra
information". In the future, we hope to find more compact ways to represent macro information, so
that it can be included with -g alone.
Many C compilers are unable to handle the -g and -O options together. Using those compilers, you
cannot generate optimized executables containing debugging information.
gcc, the gnu C compiler, supports -g with or without -O, making it possible to debug optimized
code. We recommend that you always use -g whenever you compile a program. You may think your
program is correct, but there is no sense in pushing your luck.
When you debug a program compiled with -g -O, remember that the optimizer is rearranging your
code; the debugger shows you what is really there. Do not be too surprised when the execution path
does not exactly match your source file! An extreme example: if you define a variable, but never use
it, gdb never sees that variable--because the compiler optimizes it out of existence.
Some things do not work as well with -g -O as with just -g, particularly on machines with instruction
scheduling. If in doubt, recompile with -g alone, and if this fixes the problem, please report it to us as
a bug (including a test case!).
Older versions of the gnu C compiler permitted a variant option -gg for debugging information. gdb
no longer supports this format; if your gnu C compiler has this option, do not use it.
6.2. Starting your program
run
r
Use the run command to start your program under gdb. You must first specify the program name
(except on VxWorks) with an argument to gdb (refer to Chapter 4 Getting In and Out of gdb), or
by using the file or exec-file command (refer to Section 17.1 Commands to specify files).
Page 36

26 Chapter 6. Running Programs Under gdb
If you are running your program in an execution environment that supports processes, run creates an
inferior process and makes that process run your program. (In environments without processes, run
jumps to the start of your program.)
The execution of a program is affected by certain information it receives from its superior. gdb provides ways to specify this information, which you must do before starting your program. (You can
change it after starting your program, but such changes only affect your program the next time you
start it.) This information may be divided into four categories:
The arguments.
Specify the arguments to give your program as the arguments of the run command. If a shell
is available on your target, the shell is used to pass the arguments, so that you may use normal
conventions (such as wildcard expansion or variable substitution) in describing the arguments. In
Unix systems, you can control which shell is used with the SHELL environment variable. Refer
to Section 6.3 Your program’s arguments.
The environment.
Your program normally inherits its environment from gdb, but you can use the gdb commands
set environment and unset environment to change parts of the environment that affect
your program. Refer to Section 6.4 Your program’s environment.
The working directory.
Your program inherits its working directory from gdb. You can set the gdb working directory
with the cd command in gdb. Refer to Section 6.5 Your program’s working directory.
The standard input and output.
Your program normally uses the same device for standard input and standard output as gdb is
using. You can redirect input and output in the run command line, or you can use the tty
command to set a different device for your program. Refer to Section 6.6 Your program’s input
and output.
Warning: While input and output redirection work, you cannot use pipes to pass the output of
the program you are debugging to another program; if you attempt this, gdb is likely to wind up
debugging the wrong program.
When you issue the run command, your program begins to execute immediately. Refer to Chapter
7 Stopping and Continuing for discussion of how to arrange for your program to stop. Once your
program has stopped, you may call functions in your program, using the print or call commands.
Refer to Chapter 10 Examining Data.
If the modification time of your symbol file has changed since the last time gdb read its symbols,
gdb discards its symbol table, and reads it again. When it does this, gdb tries to retain your current
breakpoints.
6.3. Your program’s arguments
The arguments to your program can be specified by the arguments of the run command. They are
passed to a shell, which expands wildcard characters and performs redirection of I/O, and thence to
your program. Your SHELL environment variable (if it exists) specifies what shell gdb uses. If you do
not define SHELL, gdb uses the default shell (/bin/sh on Unix).
On non-Unix systems, the program is usually invoked directly by gdb, which emulates I/O redirection
via the appropriate system calls, and the wildcard characters are expanded by the startup code of the
program, not by the shell.
Page 37

Chapter 6. Running Programs Under gdb 27
run with no arguments uses the same arguments used by the previous run, or those set by the set
args command.
set args
Specify the arguments to be used the next time your program is run. If set args has no arguments, run executes your program with no arguments. Once you have run your program with
arguments, using set args before the next run is the only way to run it again without arguments.
show args
Show the arguments to give your program when it is started.
6.4. Your program’s environment
The environment consists of a set of environment variables and their values. Environment variables
conventionally record such things as your user name, your home directory, your terminal type, and
your search path for programs to run. Usually you set up environment variables with the shell and
they are inherited by all the other programs you run. When debugging, it can be useful to try running
your program with a modified environment without having to start gdb over again.
path directory
Add directory to the front of the PATH environment variable (the search path for executables)
that will be passed to your program. The value of PATH used by gdb does not change. You may
specify several directory names, separated by whitespace or by a system-dependent separator
character (: on Unix, ; on MS-DOS and MS-Windows). If directory is already in the path, it
is moved to the front, so it is searched sooner.
You can use the string $cwd to refer to whatever is the current working directory at the time gdb
searches the path. If you use . instead, it refers to the directory where you executed the path
command. gdb replaces . in the directory argument (with the current path) before adding
directory to the search path.
show paths
Display the list of search paths for executables (the PATH environment variable).
show environment [varname]
Print the value of environment variable varname to be given to your program when it starts. If
you do not supply varname, print the names and values of all environment variables to be given
to your program. You can abbreviate environment as env.
set environment varname [=value]
Set environment variable varname to value. The value changes for your program only, not for
gdb itself. value may be any string; the values of environment variables are just strings, and
any interpretation is supplied by your program itself. The value parameter is optional; if it is
eliminated, the variable is set to a null value.
For example, this command:
set env USER = foo
Page 38

28 Chapter 6. Running Programs Under gdb
tells the debugged program, when subsequently run, that its user is named foo. (The spaces
around = are used for clarity here; they are not actually required.)
unset environment varname
Remove variable varname from the environment to be passed to your program. This is different
from set env varname =; unset environment removes the variable from the environment,
rather than assigning it an empty value.
Warning: On Unix systems, gdb runs your program using the shell indicated by your SHELL envi-
ronment variable if it exists (or /bin/sh if not). If your SHELL variable names a shell that runs an
initialization file--such as .cshrc for C-shell, or .bashrc for BASH--any variables you set in that
file affect your program. You may wish to move setting of environment variables to files that are only
run when you sign on, such as .login or .profile.
6.5. Your program’s working directory
Each time you start your program with run, it inherits its working directory from the current working
directory of gdb. The gdb working directory is initially whatever it inherited from its parent process
(typically the shell), but you can specify a new working directory in gdb with the cd command.
The gdb working directory also serves as a default for the commands that specify files for gdb to
operate on. Refer to Section 17.1 Commands to specify files.
cd directory
Set the gdb working directory to directory.
pwd
Print the gdb working directory.
6.6. Your program’s input and output
By default, the program you run under gdb does input and output to the same terminal that gdb uses.
gdb switches the terminal to its own terminal modes to interact with you, but it records the terminal
modes your program was using and switches back to them when you continue running your program.
info terminal
Displays information recorded by gdb about the terminal modes your program is using.
You can redirect your program’s input and/or output using shell redirection with the run command.
For example,
run
outfile
starts your program, diverting its output to the file outfile.
Another way to specify where your program should do input and output is with the tty command.
This command accepts a file name as argument, and causes this file to be the default for future run
commands. It also resets the controlling terminal for the child process, for future run commands. For
example,
Page 39

Chapter 6. Running Programs Under gdb 29
tty /dev/ttyb
directs that processes started with subsequent run commands default to do input and output on the
terminal /dev/ttyb and have that as their controlling terminal.
An explicit redirection in run overrides the tty command’s effect on the input/output device, but not
its effect on the controlling terminal.
When you use the tty command or redirect input in the run command, only the input for your
program is affected. The input for gdb still comes from your terminal.
6.7. Debugging an already-running process
attach process-id
This command attaches to a running process--one that was started outside gdb. (info files
shows your active targets.) The command takes as argument a process ID. The usual way to find
out the process-id of a Unix process is with the ps utility, or with the jobs -l shell command.
attach does not repeat if you press [RET] a second time after executing the command.
To use attach, your program must be running in an environment which supports processes; for
example, attach does not work for programs on bare-board targets that lack an operating system.
You must also have permission to send the process a signal.
When you use attach, the debugger finds the program running in the process first by looking in
the current working directory, then (if the program is not found) by using the source file search path
(refer to Section 9.4 Specifying source directories). You can also use the file command to load the
program. Refer to Section 17.1 Commands to specify files.
The first thing gdb does after arranging to debug the specified process is to stop it. You can examine
and modify an attached process with all the gdb commands that are ordinarily available when you start
processes with run. You can insert breakpoints; you can step and continue; you can modify storage. If
you would rather the process continue running, you may use the continue command after attaching
gdb to the process.
detach
When you have finished debugging the attached process, you can use the detach command to
release it from gdb control. Detaching the process continues its execution. After the detach
command, that process and gdb become completely independent once more, and you are ready
to attach another process or start one with run. detach does not repeat if you press [RET]
again after executing the command.
If you exit gdb or use the run command while you have an attached process, you kill that process. By
default, gdb asks for confirmation if you try to do either of these things; you can control whether or not
you need to confirm by using the set confirm command (refer to Section 21.7 Optional warnings
and messages).
6.8. Killing the child process
kill
Kill the child process in which your program is running under gdb.
Page 40

30 Chapter 6. Running Programs Under gdb
This command is useful if you wish to debug a core dump instead of a running process. gdb ignores
any core dump file while your program is running.
On some operating systems, a program cannot be executed outside gdb while you have breakpoints
set on it inside gdb. You can use the kill command in this situation to permit running your program
outside the debugger.
The kill command is also useful if you wish to recompile and relink your program, since on many
systems it is impossible to modify an executable file while it is running in a process. In this case, when
you next type run, gdb notices that the file has changed, and reads the symbol table again (while trying
to preserve your current breakpoint settings).
6.9. Debugging programs with multiple threads
In some operating systems, such as HP-UX and Solaris, a single program may have more than one
thread of execution. The precise semantics of threads differ from one operating system to another, but
in general the threads of a single program are akin to multiple processes--except that they share one
address space (that is, they can all examine and modify the same variables). On the other hand, each
thread has its own registers and execution stack, and perhaps private memory.
gdb provides these facilities for debugging multi-thread programs:
• automatic notification of new threads
• thread threadno, a command to switch among threads
• info threads, a command to inquire about existing threads
• thread apply [threadno] [all] args, a command to apply a command to a list of threads
• thread-specific breakpoints
Warning: These facilities are not yet available on every gdb configuration where the operating system supports threads. If your gdb does not support threads, these commands have no effect. For example, a system
without thread support shows no output from info threads, and always rejects the thread command,
like this:
(gdb) info threads
(gdb) thread 1
Thread ID 1 not known. Use the "info threads" command to
see the IDs of currently known threads.
The gdb thread debugging facility allows you to observe all threads while your program runs--but
whenever gdb takes control, one thread in particular is always the focus of debugging. This thread is
called the current thread. Debugging commands show program information from the perspective of
the current thread.
Whenever gdb detects a new thread in your program, it displays the target system’s identification for
the thread with a message in the form [New systag]. systag is a thread identifier whose form varies
depending on the particular system. For example, on LynxOS, you might see
[New process 35 thread 27]
when gdb notices a new thread. In contrast, on an SGI system, the systag is simply something like
process 368, with no further qualifier.
Page 41

Chapter 6. Running Programs Under gdb 31
For debugging purposes, gdb associates its own thread number--always a single integer--with each
thread in your program.
info threads
Display a summary of all threads currently in your program. gdb displays for each thread (in this
order):
1. the thread number assigned by gdb
2. the target system’s thread identifier (systag)
3. the current stack frame summary for that thread
An asterisk * to the left of the gdb thread number indicates the current thread.
For example,
(gdb) info threads
3 process 35 thread 27 0x34e5 in sigpause ()
2 process 35 thread 23 0x34e5 in sigpause ()
* 1 process 35 thread 13 main (argc=1, argv=0x7ffffff8)
at threadtest.c:68
On HP-UX systems:
For debugging purposes, gdb associates its own thread number--a small integer assigned in threadcreation order--with each thread in your program.
Whenever gdb detects a new thread in your program, it displays both gdb’s thread number and the
target system’s identification for the thread with a message in the form [New systag]. systag is a
thread identifier whose form varies depending on the particular system. For example, on HP-UX, you
see
[New thread 2 (system thread 26594)]
when gdb notices a new thread.
info threads
Display a summary of all threads currently in your program. gdb displays for each thread (in this
order):
1. the thread number assigned by gdb
2. the target system’s thread identifier (systag)
3. the current stack frame summary for that thread
An asterisk * to the left of the gdb thread number indicates the current thread.
For example,
(gdb) info threads
* 3 system thread 26607 worker (wptr=0x7b09c318 "@") \
at quicksort.c:137
2 system thread 26606 0x7b0030d8 in __ksleep () \
from /usr/lib/libc.2
Page 42

32 Chapter 6. Running Programs Under gdb
1 system thread 27905 0x7b003498 in _brk () \
from /usr/lib/libc.2
thread threadno
Make thread number threadno the current thread. The command argument threadno is the
internal gdb thread number, as shown in the first field of the info threads display. gdb responds by displaying the system identifier of the thread you selected, and its current stack frame
summary:
(gdb) thread 2
[Switching to process 35 thread 23]
0x34e5 in sigpause ()
As with the [New ...] message, the form of the text after Switching to depends on your
system’s conventions for identifying threads.
thread apply [threadno] [all] args
The thread apply command allows you to apply a command to one or more threads. Specify the numbers of the threads that you want affected with the command argument threadno.
threadno is the internal gdb thread number, as shown in the first field of the info threads
display. To apply a command to all threads, use thread apply all args.
Whenever gdb stops your program, due to a breakpoint or a signal, it automatically selects the thread
where that breakpoint or signal happened. gdb alerts you to the context switch with a message of the
form [Switching to systag] to identify the thread.
Refer to Section 7.4 Stopping and starting multi-thread programs for more information about how
gdb behaves when you stop and start programs with multiple threads.
Refer to Section 7.1.2 Setting watchpoints, for information about watchpoints in programs with multiple threads.
6.10. Debugging programs with multiple processes
On most systems, gdb has no special support for debugging programs which create additional processes using the fork function. When a program forks, gdb will continue to debug the parent process
and the child process will run unimpeded. If you have set a breakpoint in any code which the child
then executes, the child will get a SIGTRAP signal which (unless it catches the signal) will cause it to
terminate.
However, if you want to debug the child process there is a workaround which isn’t too painful. Put
a call to sleep in the code which the child process executes after the fork. It may be useful to sleep
only if a certain environment variable is set, or a certain file exists, so that the delay need not occur
when you don’t want to run gdb on the child. While the child is sleeping, use the ps program to get
its process ID. Then tell gdb (a new invocation of gdb if you are also debugging the parent process)
to attach to the child process (refer to Section 6.7 Debugging an already-running process). From that
point on you can debug the child process just like any other process which you attached to.
On HP-UX (11.x and later only?), gdb provides support for debugging programs that create additional
processes using the fork or vfork function.
By default, when a program forks, gdb will continue to debug the parent process and the child process
will run unimpeded.
If you want to follow the child process instead of the parent process, use the command set
follow-fork-mode.
Page 43

Chapter 6. Running Programs Under gdb 33
set follow-fork-mode mode
Set the debugger response to a program call of fork or vfork. A call to fork or vfork creates
a new process. The mode can be:
parent
The original process is debugged after a fork. The child process runs unimpeded. This is the
default.
child
The new process is debugged after a fork. The parent process runs unimpeded.
ask
The debugger will ask for one of the above choices.
show follow-fork-mode
Display the current debugger response to a fork or vfork call.
If you ask to debug a child process and a vfork is followed by an exec, gdb executes the new target
up to the first breakpoint in the new target. If you have a breakpoint set on main in your original
program, the breakpoint will also be set on the child process’s main.
When a child process is spawned by vfork, you cannot debug the child or parent until an exec call
completes.
If you issue a run command to gdb after an exec call executes, the new target restarts. To restart the
parent process, use the file command with the parent executable name as its argument.
You can use the catch command to make gdb stop whenever a fork, vfork, or exec call is made.
Refer to Section 7.1.3 Setting catchpoints.
Page 44

34 Chapter 6. Running Programs Under gdb
Page 45

Chapter 7.
Stopping and Continuing
The principal purposes of using a debugger are so that you can stop your program before it terminates;
or so that, if your program runs into trouble, you can investigate and find out why.
Inside gdb, your program may stop for any of several reasons, such as a signal, a breakpoint, or
reaching a new line after a gdb command such as step. You may then examine and change variables,
set new breakpoints or remove old ones, and then continue execution. Usually, the messages shown
by gdb provide ample explanation of the status of your program--but you can also explicitly request
this information at any time.
info program
Display information about the status of your program: whether it is running or not, what process
it is, and why it stopped.
7.1. Breakpoints, watchpoints, and catchpoints
A breakpoint makes your program stop whenever a certain point in the program is reached. For each
breakpoint, you can add conditions to control in finer detail whether your program stops. You can set
breakpoints with the break command and its variants (refer to Section 7.1.1 Setting breakpoints), to
specify the place where your program should stop by line number, function name or exact address in
the program.
In HP-UX, SunOS 4.x, SVR4, and Alpha OSF/1 configurations, you can set breakpoints in shared
libraries before the executable is run. There is a minor limitation on HP-UX systems: you must wait
until the executable is run in order to set breakpoints in shared library routines that are not called
directly by the program (for example, routines that are arguments in a pthread_create call).
A watchpoint is a special breakpoint that stops your program when the value of an expression changes.
You must use a different command to set watchpoints (refer to Section 7.1.2 Setting watchpoints), but
aside from that, you can manage a watchpoint like any other breakpoint: you enable, disable, and
delete both breakpoints and watchpoints using the same commands.
You can arrange to have values from your program displayed automatically whenever gdb stops at a
breakpoint. Refer to Section 10.6 Automatic display.
A catchpoint is another special breakpoint that stops your program when a certain kind of event
occurs, such as the throwing of a C++ exception or the loading of a library. As with watchpoints, you
use a different command to set a catchpoint (refer to Section 7.1.3 Setting catchpoints), but aside from
that, you can manage a catchpoint like any other breakpoint. (To stop when your program receives a
signal, use the handle command. Refer to Section 7.3 Signals.
gdb assigns a number to each breakpoint, watchpoint, or catchpoint when you create it; these numbers
are successive integers starting with one. In many of the commands for controlling various features
of breakpoints you use the breakpoint number to say which breakpoint you want to change. Each
breakpoint may be enabled or disabled; if disabled, it has no effect on your program until you enable
it again.
Some gdb commands accept a range of breakpoints on which to operate. A breakpoint range is either
a single breakpoint number, like 5, or two such numbers, in increasing order, separated by a hyphen,
like 5-7. When a breakpoint range is given to a command, all breakpoint in that range are operated
on.
Page 46

36 Chapter 7. Stopping and Continuing
7.1.1. Setting breakpoints
Breakpoints are set with the break command (abbreviated b). The debugger convenience variable
$bpnum records the number of the breakpoint you’ve set most recently; refer to Section 10.9 Conve-
nience variables, for a discussion of what you can do with convenience variables.
You have several ways to say where the breakpoint should go.
break function
Set a breakpoint at entry to function function. When using source languages that permit overloading of symbols, such as C++, function may refer to more than one possible place to break.
Refer to Section 7.1.8 Breakpoint menus, for a discussion of that situation.
break +offset
break -offset
Set a breakpoint some number of lines forward or back from the position at which execution
stopped in the currently selected stack frame. Refer to Section 8.1 Stack frames for a description
of stack frames.)
break linenum
Set a breakpoint at line linenum in the current source file. The current source file is the last file
whose source text was printed. The breakpoint will stop your program just before it executes any
of the code on that line.
break filename:linenum
Set a breakpoint at line linenum in source file filename.
break filename:function
Set a breakpoint at entry to function function found in file filename. Specifying a file name
as well as a function name is superfluous except when multiple files contain similarly named
functions.
break *address
Set a breakpoint at address address. You can use this to set breakpoints in parts of your program
which do not have debugging information or source files.
break
When called without any arguments, break sets a breakpoint at the next instruction to be executed in the selected stack frame (refer to Chapter 8 Examining the Stack). In any selected frame
but the innermost, this makes your program stop as soon as control returns to that frame. This is
similar to the effect of a finish command in the frame inside the selected frame--except that
finish does not leave an active breakpoint. If you use break without an argument in the in-
nermost frame, gdb stops the next time it reaches the current location; this may be useful inside
loops.
gdb normally ignores breakpoints when it resumes execution, until at least one instruction has
been executed. If it did not do this, you would be unable to proceed past a breakpoint without first
disabling the breakpoint. This rule applies whether or not the breakpoint already existed when
your program stopped.
break ... if cond
Set a breakpoint with condition cond; evaluate the expression cond each time the breakpoint
is reached, and stop only if the value is nonzero--that is, if cond evaluates as true. ... stands
Page 47

Chapter 7. Stopping and Continuing 37
for one of the possible arguments described above (or no argument) specifying where to break.
Refer to Section 7.1.6 Break conditions for more information on breakpoint conditions.
tbreak args
Set a breakpoint enabled only for one stop. args are the same as for the break command, and
the breakpoint is set in the same way, but the breakpoint is automatically deleted after the first
time your program stops there. Refer to Section 7.1.5 Disabling breakpoints.
hbreak args
Set a hardware-assisted breakpoint. args are the same as for the break command and the breakpoint is set in the same way, but the breakpoint requires hardware support and some target hardware may not have this support. The main purpose of this is EPROM/ROM code debugging, so
you can set a breakpoint at an instruction without changing the instruction. This can be used with
the new trap-generation provided by SPARClite DSU and some x86-based targets. These targets
will generate traps when a program accesses some data or instruction address that is assigned
to the debug registers. However the hardware breakpoint registers can take a limited number of
breakpoints. For example, on the DSU, only two data breakpoints can be set at a time, and gdb
will reject this command if more than two are used. Delete or disable unused hardware breakpoints before setting new ones (refer to Section 7.1.5 Disabling breakpoints and Section 7.1.6
Break conditions.
thbreak args
Set a hardware-assisted breakpoint enabled only for one stop. args are the same as for the
hbreak command and the breakpoint is set in the same way. However, like the tbreak com-
mand, the breakpoint is automatically deleted after the first time your program stops there. Also,
like the hbreak command, the breakpoint requires hardware support and some target hardware
may not have this support. Refer to Section 7.1.5 Disabling breakpoints and Section 7.1.6 Break
conditions.
rbreak regex
Set breakpoints on all functions matching the regular expression regex. This command sets
an unconditional breakpoint on all matches, printing a list of all breakpoints it set. Once these
breakpoints are set, they are treated just like the breakpoints set with the break command. You
can delete them, disable them, or make them conditional the same way as any other breakpoint.
The syntax of the regular expression is the standard one used with tools like grep. Note that
this is different from the syntax used by shells, so for instance foo* matches all functions that
include an fo followed by zero or more os. There is an implicit .* leading and trailing the regular
expression you supply, so to match only functions that begin with foo, use ^foo.
When debugging C++ programs, rbreak is useful for setting breakpoints on overloaded functions that are not members of any special classes.
info breakpoints [n]
info break [n]
info watchpoints [n]
Print a table of all breakpoints, watchpoints, and catchpoints set and not deleted, with the following columns for each breakpoint:
Breakpoint Numbers
Type
Breakpoint, watchpoint, or catchpoint.
Page 48

38 Chapter 7. Stopping and Continuing
Disposition
Whether the breakpoint is marked to be disabled or deleted when hit.
Enabled or Disabled
Enabled breakpoints are marked with y. n marks breakpoints that are not enabled.
Address
Where the breakpoint is in your program, as a memory address.
What
Where the breakpoint is in the source for your program, as a file and line number.
If a breakpoint is conditional, info break shows the condition on the line following the affected
breakpoint; breakpoint commands, if any, are listed after that.
info break with a breakpoint number n as argument lists only that breakpoint. The conve-
nience variable $_ and the default examining-address for the x command are set to the address
of the last breakpoint listed (refer to Section 10.5 Examining memory).
info break displays a count of the number of times the breakpoint has been hit. This is es-
pecially useful in conjunction with the ignore command. You can ignore a large number of
breakpoint hits, look at the breakpoint info to see how many times the breakpoint was hit, and
then run again, ignoring one less than that number. This will get you quickly to the last hit of that
breakpoint.
gdb allows you to set any number of breakpoints at the same place in your program. There is nothing
silly or meaningless about this. When the breakpoints are conditional, this is even useful (refer to
Section 7.1.6 Break conditions).
gdb itself sometimes sets breakpoints in your program for special purposes, such as proper handling of
longjmp (in C programs). These internal breakpoints are assigned negative numbers, starting with -1;
info breakpoints does not display them. You can see these breakpoints with the gdb maintenance
command maint info breakpoints (refer to Appendix C Maintenance Commands).
7.1.2. Setting watchpoints
You can use a watchpoint to stop execution whenever the value of an expression changes, without
having to predict a particular place where this may happen.
Depending on your system, watchpoints may be implemented in software or hardware. gdb does
software watchpointing by single-stepping your program and testing the variable’s value each time,
which is hundreds of times slower than normal execution. (But this may still be worth it, to catch
errors where you have no clue what part of your program is the culprit.)
On some systems, such as HP-UX, gnu/Linux and some other x86-based targets, gdb includes support
for hardware watchpoints, which do not slow down the running of your program.
watch expr
Set a watchpoint for an expression. gdb will break when expr is written into by the program and
its value changes.
rwatch expr
Set a watchpoint that will break when watch expr is read by the program.
Page 49

Chapter 7. Stopping and Continuing 39
awatch expr
Set a watchpoint that will break when expr is either read or written into by the program.
info watchpoints
This command prints a list of watchpoints, breakpoints, and catchpoints; it is the same as info
break.
gdb sets a hardware watchpoint if possible. Hardware watchpoints execute very quickly, and the
debugger reports a change in value at the exact instruction where the change occurs. If gdb cannot
set a hardware watchpoint, it sets a software watchpoint, which executes more slowly and reports the
change in value at the next statement, not the instruction, after the change occurs.
When you issue the watch command, gdb reports
Hardware watchpoint num: expr
if it was able to set a hardware watchpoint.
Currently, the awatch and rwatch commands can only set hardware watchpoints, because accesses
to data that don’t change the value of the watched expression cannot be detected without examining
every instruction as it is being executed, and gdb does not do that currently. If gdb finds that it is
unable to set a hardware breakpoint with the awatch or rwatch command, it will print a message
like this:
Expression cannot be implemented with read/access watchpoint.
Sometimes, gdb cannot set a hardware watchpoint because the data type of the watched expression
is wider than what a hardware watchpoint on the target machine can handle. For example, some
systems can only watch regions that are up to 4 bytes wide; on such systems you cannot set hardware
watchpoints for an expression that yields a double-precision floating-point number (which is typically
8 bytes wide). As a work-around, it might be possible to break the large region into a series of smaller
ones and watch them with separate watchpoints.
If you set too many hardware watchpoints, gdb might be unable to insert all of them when you resume
the execution of your program. Since the precise number of active watchpoints is unknown until such
time as the program is about to be resumed, gdb might not be able to warn you about this when you
set the watchpoints, and the warning will be printed only when the program is resumed:
Hardware watchpoint num: Could not insert watchpoint
If this happens, delete or disable some of the watchpoints.
The SPARClite DSU will generate traps when a program accesses some data or instruction address
that is assigned to the debug registers. For the data addresses, DSU facilitates the watch command.
However the hardware breakpoint registers can only take two data watchpoints, and both watchpoints
must be the same kind. For example, you can set two watchpoints with watch commands, two with
rwatch commands, or two with awatch commands, but you cannot set one watchpoint with one
command and the other with a different command. gdb will reject the command if you try to mix
watchpoints. Delete or disable unused watchpoint commands before setting new ones.
If you call a function interactively using print or call, any watchpoints you have set will be inactive
until gdb reaches another kind of breakpoint or the call completes.
Page 50

40 Chapter 7. Stopping and Continuing
gdb automatically deletes watchpoints that watch local (automatic) variables, or expressions that involve such variables, when they go out of scope, that is, when the execution leaves the block in which
these variables were defined. In particular, when the program being debugged terminates, all local
variables go out of scope, and so only watchpoints that watch global variables remain set. If you rerun
the program, you will need to set all such watchpoints again. One way of doing that would be to set a
code breakpoint at the entry to the main function and when it breaks, set all the watchpoints.
Warning: In multi-thread programs, watchpoints have only limited usefulness. With the current watchpoint
implementation, gdb can only watch the value of an expression in a single thread. If you are confident that
the expression can only change due to the current thread’s activity (and if you are also confident that no
other thread can become current), then you can use watchpoints as usual. However, gdb may not notice
when a non-current thread’s activity changes the expression.
HP-UX Warning: In multi-thread programs, software watchpoints have only limited usefulness. If gdb creates a software watchpoint, it can only watch the value of an expression in a single thread. If you are
confident that the expression can only change due to the current thread’s activity (and if you are also confident that no other thread can become current), then you can use software watchpoints as usual. However,
gdb may not notice when a non-current thread’s activity changes the expression. (Hardware watchpoints, in
contrast, watch an expression in all threads.)
7.1.3. Setting catchpoints
You can use catchpoints to cause the debugger to stop for certain kinds of program events, such as
C++ exceptions or the loading of a shared library. Use the catch command to set a catchpoint.
catch event
Stop when event occurs. event can be any of the following:
throw
The throwing of a C++ exception.
catch
The catching of a C++ exception.
exec
A call to exec. This is currently only available for HP-UX.
fork
A call to fork. This is currently only available for HP-UX.
vfork
A call to vfork. This is currently only available for HP-UX.
load
load libname
The dynamic loading of any shared library, or the loading of the library libname. This is
currently only available for HP-UX.
Page 51

Chapter 7. Stopping and Continuing 41
unload
unload libname
The unloading of any dynamically loaded shared library, or the unloading of the library
libname. This is currently only available for HP-UX.
tcatch event
Set a catchpoint that is enabled only for one stop. The catchpoint is automatically deleted after
the first time the event is caught.
Use the info break command to list the current catchpoints.
There are currently some limitations to C++ exception handling (catch throw and catch catch)
in gdb:
• If you call a function interactively, gdb normally returns control to you when the function has
finished executing. If the call raises an exception, however, the call may bypass the mechanism that
returns control to you and cause your program either to abort or to simply continue running until it
hits a breakpoint, catches a signal that gdb is listening for, or exits. This is the case even if you set
a catchpoint for the exception; catchpoints on exceptions are disabled within interactive calls.
• You cannot raise an exception interactively.
• You cannot install an exception handler interactively.
Sometimes catch is not the best way to debug exception handling: if you need to know exactly where
an exception is raised, it is better to stop before the exception handler is called, since that way you
can see the stack before any unwinding takes place. If you set a breakpoint in an exception handler
instead, it may not be easy to find out where the exception was raised.
To stop just before an exception handler is called, you need some knowledge of the implementation. In
the case of gnu C++, exceptions are raised by calling a library function named __raise_exception
which has the following ANSI C interface:
/* addr is where the exception identifier is stored.
id is the exception identifier. */
void __raise_exception (void **addr, void *id);
To make the debugger catch all exceptions before any stack unwinding takes place, set a breakpoint
on __raise_exception (refer to Section 7.1 Breakpoints, watchpoints, and catchpoints).
With a conditional breakpoint (refer to Section 7.1.6 Break conditions) that depends on the value of
id, you can stop your program when a specific exception is raised. You can use multiple conditional
breakpoints to stop your program when any of a number of exceptions are raised.
7.1.4. Deleting breakpoints
It is often necessary to eliminate a breakpoint, watchpoint, or catchpoint once it has done its job and
you no longer want your program to stop there. This is called deleting the breakpoint. A breakpoint
that has been deleted no longer exists; it is forgotten.
With the clear command you can delete breakpoints according to where they are in your program.
With the delete command you can delete individual breakpoints, watchpoints, or catchpoints by
specifying their breakpoint numbers.
Page 52

42 Chapter 7. Stopping and Continuing
It is not necessary to delete a breakpoint to proceed past it. gdb automatically ignores breakpoints
on the first instruction to be executed when you continue execution without changing the execution
address.
clear
Delete any breakpoints at the next instruction to be executed in the selected stack frame (refer
to Section 8.3 Selecting a frame). When the innermost frame is selected, this is a good way to
delete a breakpoint where your program just stopped.
clear function
clear filename:function
Delete any breakpoints set at entry to the function function.
clear linenum
clear filename:linenum
Delete any breakpoints set at or within the code of the specified line.
delete [breakpoints] [range...]
Delete the breakpoints, watchpoints, or catchpoints of the breakpoint ranges specified as arguments. If no argument is specified, delete all breakpoints (gdb asks confirmation, unless you have
set confirm off). You can abbreviate this command as d.
7.1.5. Disabling breakpoints
Rather than deleting a breakpoint, watchpoint, or catchpoint, you might prefer to disable it. This makes
the breakpoint inoperative as if it had been deleted, but remembers the information on the breakpoint
so that you can enable it again later.
You disable and enable breakpoints, watchpoints, and catchpoints with the enable and disable
commands, optionally specifying one or more breakpoint numbers as arguments. Use info break
or info watch to print a list of breakpoints, watchpoints, and catchpoints if you do not know which
numbers to use.
A breakpoint, watchpoint, or catchpoint can have any of four different states of enablement:
• Enabled. The breakpoint stops your program. A breakpoint set with the break command starts out
in this state.
• Disabled. The breakpoint has no effect on your program.
• Enabled once. The breakpoint stops your program, but then becomes disabled.
• Enabled for deletion. The breakpoint stops your program, but immediately after it does so it is
deleted permanently. A breakpoint set with the tbreak command starts out in this state.
You can use the following commands to enable or disable breakpoints, watchpoints, and catchpoints:
disable [breakpoints] [range...]
Disable the specified breakpoints--or all breakpoints, if none are listed. A disabled breakpoint
has no effect but is not forgotten. All options such as ignore-counts, conditions and commands
are remembered in case the breakpoint is enabled again later. You may abbreviate disable as
dis.
Page 53

Chapter 7. Stopping and Continuing 43
enable [breakpoints] [range...]
Enable the specified breakpoints (or all defined breakpoints). They become effective once again
in stopping your program.
enable [breakpoints] once range...
Enable the specified breakpoints temporarily. gdb disables any of these breakpoints immediately
after stopping your program.
enable [breakpoints] delete range...
Enable the specified breakpoints to work once, then die. gdb deletes any of these breakpoints as
soon as your program stops there.
Except for a breakpoint set with tbreak (refer to Section 7.1.1 Setting breakpoints), breakpoints that
you set are initially enabled; subsequently, they become disabled or enabled only when you use one
of the commands above. (The command until can set and delete a breakpoint of its own, but it does
not change the state of your other breakpoints; (refer to Section 7.2 Continuing and stepping.)
7.1.6. Break conditions
The simplest sort of breakpoint breaks every time your program reaches a specified place. You can also
specify a condition for a breakpoint. A condition is just a Boolean expression in your programming
language (refer to Section 10.1 Expressions). A breakpoint with a condition evaluates the expression
each time your program reaches it, and your program stops only if the condition is true.
This is the converse of using assertions for program validation; in that situation, you want to stop
when the assertion is violated--that is, when the condition is false. In C, if you want to test an assertion expressed by the condition assert, you should set the condition ! assert on the appropriate
breakpoint.
Conditions are also accepted for watchpoints; you may not need them, since a watchpoint is inspecting
the value of an expression anyhow--but it might be simpler, say, to just set a watchpoint on a variable
name, and specify a condition that tests whether the new value is an interesting one.
Break conditions can have side effects, and may even call functions in your program. This can be
useful, for example, to activate functions that log program progress, or to use your own print functions
to format special data structures. The effects are completely predictable unless there is another enabled
breakpoint at the same address. (In that case, gdb might see the other breakpoint first and stop your
program without checking the condition of this one.) Note that breakpoint commands are usually
more convenient and flexible than break conditions for the purpose of performing side effects when a
breakpoint is reached (refer to Section 7.1.7 Breakpoint command lists).
Break conditions can be specified when a breakpoint is set, by using if in the arguments to the break
command. Refer to Section 7.1.1 Setting breakpoints. They can also be changed at any time with the
condition command.
You can also use the if keyword with the watch command. The catch command does not recognize
the if keyword; condition is the only way to impose a further condition on a catchpoint.
condition bnum expression
Specify expression as the break condition for breakpoint, watchpoint, or catchpoint number bnum. After you set a condition, breakpoint bnum stops your program only if the value of
expression is true (nonzero, in C). When you use condition, gdb checks expression im-
mediately for syntactic correctness, and to determine whether symbols in it have referents in the
context of your breakpoint. If expression uses symbols not referenced in the context of the
breakpoint, gdb prints an error message:
Page 54

44 Chapter 7. Stopping and Continuing
No symbol "foo" in current context.
gdb does not actually evaluate expression at the time the condition command (or a command that sets a breakpoint with a condition, like break if ...) is given, however. Refer to
Section 10.1 Expressions.
condition bnum
Remove the condition from breakpoint number bnum. It becomes an ordinary unconditional
breakpoint.
A special case of a breakpoint condition is to stop only when the breakpoint has been reached a certain
number of times. This is so useful that there is a special way to do it, using the ignore count of the
breakpoint. Every breakpoint has an ignore count, which is an integer. Most of the time, the ignore
count is zero, and therefore has no effect. But if your program reaches a breakpoint whose ignore
count is positive, then instead of stopping, it just decrements the ignore count by one and continues.
As a result, if the ignore count value is n, the breakpoint does not stop the next n times your program
reaches it.
ignore bnum count
Set the ignore count of breakpoint number bnum to count. The next count times the breakpoint
is reached, your program’s execution does not stop; other than to decrement the ignore count,
gdb takes no action.
To make the breakpoint stop the next time it is reached, specify a count of zero.
When you use continue to resume execution of your program from a breakpoint, you can
specify an ignore count directly as an argument to continue, rather than using ignore. Refer
to Section 7.2 Continuing and stepping.
If a breakpoint has a positive ignore count and a condition, the condition is not checked. Once
the ignore count reaches zero, gdb resumes checking the condition.
You could achieve the effect of the ignore count with a condition such as $foo-
= 0 using a
debugger convenience variable that is decremented each time. Refer to Section 10.9 Convenience
variables.
Ignore counts apply to breakpoints, watchpoints, and catchpoints.
7.1.7. Breakpoint command lists
You can give any breakpoint (or watchpoint or catchpoint) a series of commands to execute when
your program stops due to that breakpoint. For example, you might want to print the values of certain
expressions, or enable other breakpoints.
commands [bnum]
... command-list ...
end
Specify a list of commands for breakpoint number bnum. The commands themselves appear on
the following lines. Type a line containing just end to terminate the commands.
To remove all commands from a breakpoint, type commands and follow it immediately with end;
that is, give no commands.
With no bnum argument, commands refers to the last breakpoint, watchpoint, or catchpoint set
(not to the breakpoint most recently encountered).
Pressing [RET] as a means of repeating the last gdb command is disabled within a command-list.
Page 55

Chapter 7. Stopping and Continuing 45
You can use breakpoint commands to start your program up again. Simply use the continue command, or step, or any other command that resumes execution.
Any other commands in the command list, after a command that resumes execution, are ignored. This
is because any time you resume execution (even with a simple next or step), you may encounter
another breakpoint--which could have its own command list, leading to ambiguities about which list
to execute.
If the first command you specify in a command list is silent, the usual message about stopping at a
breakpoint is not printed. This may be desirable for breakpoints that are to print a specific message and
then continue. If none of the remaining commands print anything, you see no sign that the breakpoint
was reached. silent is meaningful only at the beginning of a breakpoint command list.
The commands echo, output, and printf allow you to print precisely controlled output, and are
often useful in silent breakpoints. Refer to Section 22.4 Commands for controlled output.
For example, here is how you could use breakpoint commands to print the value of x at entry to foo
whenever x is positive.
break foo if x
0
commands
silent
printf "x is %d\n",x
cont
end
One application for breakpoint commands is to compensate for one bug so you can test for another.
Put a breakpoint just after the erroneous line of code, give it a condition to detect the case in which
something erroneous has been done, and give it commands to assign correct values to any variables
that need them. End with the continue command so that your program does not stop, and start with
the silent command so that no output is produced. Here is an example:
break 403
commands
silent
set x = y + 4
cont
end
7.1.8. Breakpoint menus
Some programming languages (notably C++ and Objective-C) permit a single function name to be
defined several times, for application in different contexts. This is called overloading. When a function
name is overloaded, break function is not enough to tell gdb where you want a breakpoint. If you
realize this is a problem, you can use something like break function(types) to specify which
particular version of the function you want. Otherwise, gdb offers you a menu of numbered choices
for different possible breakpoints, and waits for your selection with the prompt
. The first two options
are always [0] cancel and [1] all. Typing 1 sets a breakpoint at each definition of function,
and typing 0 aborts the break command without setting any new breakpoints.
For example, the following session excerpt shows an attempt to set a breakpoint at the overloaded
symbol String::after. We choose three particular definitions of that function name:
(gdb) b String::after
[0] cancel
Page 56

46 Chapter 7. Stopping and Continuing
[1] all
[2] file:String.cc; line number:867
[3] file:String.cc; line number:860
[4] file:String.cc; line number:875
[5] file:String.cc; line number:853
[6] file:String.cc; line number:846
[7] file:String.cc; line number:735
2 4 6
Breakpoint 1 at 0xb26c: file String.cc, line 867.
Breakpoint 2 at 0xb344: file String.cc, line 875.
Breakpoint 3 at 0xafcc: file String.cc, line 846.
Multiple breakpoints were set.
Use the "delete" command to delete unwanted
breakpoints.
(gdb)
7.1.9. "Cannot insert breakpoints"
Under some operating systems, breakpoints cannot be used in a program if any other process is running that program. In this situation, attempting to run or continue a program with a breakpoint causes
gdb to print an error message:
Cannot insert breakpoints.
The same program may be running in another process.
When this happens, you have three ways to proceed:
1. Remove or disable the breakpoints, then continue.
2. Suspend gdb, and copy the file containing your program to a new name. Resume gdb and use
the exec-file command to specify that gdb should run your program under that name. Then
start your program again.
3. Relink your program so that the text segment is nonsharable, using the linker option -N. The
operating system limitation may not apply to nonsharable executables.
A similar message can be printed if you request too many active hardware-assisted breakpoints and
watchpoints:
Stopped; cannot insert breakpoints.
You may have requested too many hardware breakpoints and watchpoints.
This message is printed when you attempt to resume the program, since only then gdb knows exactly
how many hardware breakpoints and watchpoints it needs to insert.
When this message is printed, you need to disable or remove some of the hardware-assisted breakpoints and watchpoints, and then continue.
Page 57

Chapter 7. Stopping and Continuing 47
7.2. Continuing and stepping
Continuing means resuming program execution until your program completes normally. In contrast,
stepping means executing just one more "step" of your program, where "step" may mean either one
line of source code, or one machine instruction (depending on what particular command you use).
Either when continuing or when stepping, your program may stop even sooner, due to a breakpoint
or a signal. (If it stops due to a signal, you may want to use handle, or use signal 0 to resume
execution. Refer to Section 7.3 Signals.)
continue [ignore-count]
c [ignore-count]
fg [ignore-count]
Resume program execution, at the address where your program last stopped; any breakpoints
set at that address are bypassed. The optional argument ignore-count allows you to specify a
further number of times to ignore a breakpoint at this location; its effect is like that of ignore
(refer to Section 7.1.6 Break conditions).
The argument ignore-count is meaningful only when your program stopped due to a breakpoint. At other times, the argument to continue is ignored.
The synonyms c and fg (for foreground, as the debugged program is deemed to be the foreground
program) are provided purely for convenience, and have exactly the same behavior as continue.
To resume execution at a different place, you can use return (refer to Section 16.4 Returning from a
function) to go back to the calling function; or jump (refer to Section 16.2 Continuing at a different
address) to go to an arbitrary location in your program.
A typical technique for using stepping is to set a breakpoint (refer to Section 7.1 Breakpoints, watchpoints, and catchpoints) at the beginning of the function or the section of your program where a
problem is believed to lie, run your program until it stops at that breakpoint, and then step through the
suspect area, examining the variables that are interesting, until you see the problem happen.
step
Continue running your program until control reaches a different source line, then stop it and
return control to gdb. This command is abbreviated s.
Warning: If you use the step command while control is within a function that was compiled without
debugging information, execution proceeds until control reaches a function that does have debugging
information. Likewise, it will not step into a function which is compiled without debugging information. To step through functions without debugging information, use the stepi command, described
below.
The step command only stops at the first instruction of a source line. This prevents the multiple
stops that could otherwise occur in switch statements, for loops, etc. step continues to stop
if a function that has debugging information is called within the line. In other words, step steps
inside any functions called within the line.
Also, the step command only enters a function if there is line number information for the function. Otherwise it acts like the next command. This avoids problems when using cc -gl on
MIPS machines. Previously, step entered subroutines if there was any debugging information
about the routine.
step count
Continue running as in step, but do so count times. If a breakpoint is reached, or a signal not
related to stepping occurs before count steps, stepping stops right away.
Page 58

48 Chapter 7. Stopping and Continuing
next [count]
Continue to the next source line in the current (innermost) stack frame. This is similar to step,
but function calls that appear within the line of code are executed without stopping. Execution
stops when control reaches a different line of code at the original stack level that was executing
when you gave the next command. This command is abbreviated n.
An argument count is a repeat count, as for step.
The next command only stops at the first instruction of a source line. This prevents multiple
stops that could otherwise occur in switch statements, for loops, etc.
set step-mode
set step-mode on
The set step-mode on command causes the step command to stop at the first instruction of
a function which contains no debug line information rather than stepping over it.
This is useful in cases where you may be interested in inspecting the machine instructions of a
function which has no symbolic info and do not want gdb to automatically skip over this function.
set step-mode off
Causes the step command to step over any functions which contains no debug information. This
is the default.
finish
Continue running until just after function in the selected stack frame returns. Print the returned
value (if any).
Contrast this with the return command (refer to Section 16.4 Returning from a function).
until
u
Continue running until a source line past the current line, in the current stack frame, is reached.
This command is used to avoid single stepping through a loop more than once. It is like the next
command, except that when until encounters a jump, it automatically continues execution until
the program counter is greater than the address of the jump.
This means that when you reach the end of a loop after single stepping though it, until makes
your program continue execution until it exits the loop. In contrast, a next command at the end
of a loop simply steps back to the beginning of the loop, which forces you to step through the
next iteration.
until always stops your program if it attempts to exit the current stack frame.
until may produce somewhat counterintuitive results if the order of machine code does not
match the order of the source lines. For example, in the following excerpt from a debugging
session, the f (frame) command shows that execution is stopped at line 206; yet when we use
until, we get to line 195:
(gdb) f
#0 main (argc=4, argv=0xf7fffae8) at m4.c:206
206 expand_input();
(gdb) until
195 for ( ; argc0; NEXTARG) {
This happened because, for execution efficiency, the compiler had generated code for the loop
closure test at the end, rather than the start, of the loop--even though the test in a C for-loop is
Page 59

Chapter 7. Stopping and Continuing 49
written before the body of the loop. The until command appeared to step back to the beginning
of the loop when it advanced to this expression; however, it has not really gone to an earlier
statement--not in terms of the actual machine code.
until with no argument works by means of single instruction stepping, and hence is slower than
until with an argument.
until location
u location
Continue running your program until either the specified location is reached, or the current stack
frame returns. location is any of the forms of argument acceptable to break (refer to Section
7.1.1 Setting breakpoints). This form of the command uses breakpoints, and hence is quicker
than until without an argument. The specified location is actually reached only if it is in the
current frame. This implies that until can be used to skip over recursive function invocations.
For instance in the code below, if the current location is line 96, issuing until 99 will execute
the program up to line 99 in the same invocation of factorial, that is, after the inner invocations
have returned.
94 int factorial (int value)
95 {
96 if (value
1) {
97 value *= factorial (value - 1);
98 }
99 return (value);
100 }
advance location
Continue running the program up to the given location. An argument is required, anything of the
same form as arguments for the break command. Execution will also stop upon exit from the
current stack frame. This command is similar to until, but advance will not skip over recursive
function calls, and the target location doesn’t have to be in the same frame as the current one.
stepi
stepi arg
si
Execute one machine instruction, then stop and return to the debugger.
It is often useful to do display/i $pc when stepping by machine instructions. This makes gdb
automatically display the next instruction to be executed, each time your program stops. Refer to
Section 10.6 Automatic display.
An argument is a repeat count, as in step.
nexti
nexti arg
ni
Execute one machine instruction, but if it is a function call, proceed until the function returns.
An argument is a repeat count, as in next.
7.3. Signals
A signal is an asynchronous event that can happen in a program. The operating system defines the
possible kinds of signals, and gives each kind a name and a number. For example, in Unix SIGINT is
the signal a program gets when you type an interrupt character (often C-c); SIGSEGV is the signal a
Page 60

50 Chapter 7. Stopping and Continuing
program gets from referencing a place in memory far away from all the areas in use; SIGALRM occurs
when the alarm clock timer goes off (which happens only if your program has requested an alarm).
Some signals, including SIGALRM, are a normal part of the functioning of your program. Others,
such as SIGSEGV, indicate errors; these signals are fatal (they kill your program immediately) if the
program has not specified in advance some other way to handle the signal. SIGINT does not indicate
an error in your program, but it is normally fatal so it can carry out the purpose of the interrupt: to kill
the program.
gdb has the ability to detect any occurrence of a signal in your program. You can tell gdb in advance
what to do for each kind of signal.
Normally, gdb is set up to let the non-erroneous signals like SIGALRM be silently passed to your program (so as not to interfere with their role in the program’s functioning) but to stop your program
immediately whenever an error signal happens. You can change these settings with the handle command.
info signals
info handle
Print a table of all the kinds of signals and how gdb has been told to handle each one. You can
use this to see the signal numbers of all the defined types of signals.
info handle is an alias for info signals.
handle signal keywords...
Change the way gdb handles signal signal. signal can be the number of a signal or its name
(with or without the SIG at the beginning); a list of signal numbers of the form low-high; or the
word all, meaning all the known signals. The keywords say what change to make.
The keywords allowed by the handle command can be abbreviated. Their full names are:
nostop
{No value for ‘
listitem>GDBN’} should not stop your program when this signal happens. It
may still print a message telling you that the signal has come in.
stop
{No value for ‘
listitem>GDBN’} should stop your program when this signal happens. This
implies the print keyword as well.
print
{No value for ‘
listitem>GDBN’} should print a message when this signal happens.
noprint
{No value for ‘listitem>GDBN’} should not mention the occurrence of the signal at all. This
implies the nostop keyword as well.
pass
noignore
{No value for ‘
listitem>GDBN’} should allow your program to see this signal; your program
can handle the signal, or else it may terminate if the signal is fatal and not handled. pass and
noignore are synonyms.
Page 61

Chapter 7. Stopping and Continuing 51
nopass
ignore
{No value for ‘
listitem>GDBN’} should not allow your program to see this signal. nopass
and ignore are synonyms.
When a signal stops your program, the signal is not visible to the program until you continue. Your
program sees the signal then, if pass is in effect for the signal in question at that time. In other words,
after gdb reports a signal, you can use the handle command with pass or nopass to control whether
your program sees that signal when you continue.
The default is set to nostop, noprint, pass for non-erroneous signals such as SIGALRM, SIGWINCH
and SIGCHLD, and to stop, print, pass for the erroneous signals.
You can also use the signal command to prevent your program from seeing a signal, or cause it
to see a signal it normally would not see, or to give it any signal at any time. For example, if your
program stopped due to some sort of memory reference error, you might store correct values into the
erroneous variables and continue, hoping to see more execution; but your program would probably
terminate immediately as a result of the fatal signal once it saw the signal. To prevent this, you can
continue with signal 0. Refer to Section 16.3 Giving your program a signal.
7.4. Stopping and starting multi-thread programs
When your program has multiple threads (refer to Section 6.9 Debugging programs with multiple
threads), you can choose whether to set breakpoints on all threads, or on a particular thread.
break linespec thread threadno
break linespec thread threadno if ...
linespec specifies source lines; there are several ways of writing them, but the effect is always
to specify some source line.
Use the qualifier thread threadno with a breakpoint command to specify that you only want
gdb to stop the program when a particular thread reaches this breakpoint. threadno is one of
the numeric thread identifiers assigned by gdb, shown in the first column of the info threads
display.
If you do not specify thread threadno when you set a breakpoint, the breakpoint applies to all
threads of your program.
You can use the thread qualifier on conditional breakpoints as well; in this case, place thread
threadno before the breakpoint condition, like this:
(gdb) break frik.c:13 thread 28 if bartab
lim
Whenever your program stops under gdb for any reason, all threads of execution stop, not just the current thread. This allows you to examine the overall state of the program, including switching between
threads, without worrying that things may change underfoot.
Conversely, whenever you restart the program, all threads start executing. This is true even when
single-stepping with commands like step or next.
In particular, gdb cannot single-step all threads in lockstep. Since thread scheduling is up to your
debugging target’s operating system (not controlled by gdb), other threads may execute more than
one statement while the current thread completes a single step. Moreover, in general other threads
stop in the middle of a statement, rather than at a clean statement boundary, when the program stops.
You might even find your program stopped in another thread after continuing or even single-stepping.
This happens whenever some other thread runs into a breakpoint, a signal, or an exception before the
first thread completes whatever you requested.
On some OSes, you can lock the OS scheduler and thus allow only a single thread to run.
Page 62

52 Chapter 7. Stopping and Continuing
set scheduler-locking mode
Set the scheduler locking mode. If it is off, then there is no locking and any thread may run at any
time. If on, then only the current thread may run when the inferior is resumed. The step mode
optimizes for single-stepping. It stops other threads from "seizing the prompt" by preempting the
current thread while you are stepping. Other threads will only rarely (or never) get a chance to
run when you step. They are more likely to run when you next over a function call, and they are
completely free to run when you use commands like continue, until, or finish. However,
unless another thread hits a breakpoint during its timeslice, they will never steal the gdb prompt
away from the thread that you are debugging.
show scheduler-locking
Display the current scheduler locking mode.
Page 63

Chapter 8.
Examining the Stack
When your program has stopped, the first thing you need to know is where it stopped and how it got
there.
Each time your program performs a function call, information about the call is generated. That information includes the location of the call in your program, the arguments of the call, and the local
variables of the function being called. The information is saved in a block of data called a stack frame.
The stack frames are allocated in a region of memory called the call stack.
When your program stops, the gdb commands for examining the stack allow you to see all of this
information.
One of the stack frames is selected by gdb and many gdb commands refer implicitly to the selected
frame. In particular, whenever you ask gdb for the value of a variable in your program, the value
is found in the selected frame. There are special gdb commands to select whichever frame you are
interested in. Refer to Section 8.3 Selecting a frame.
When your program stops, gdb automatically selects the currently executing frame and describes it
briefly, similar to the frame command (refer to Section 8.4 Information about a frame).
8.1. Stack frames
The call stack is divided up into contiguous pieces called stack frames, or frames for short; each frame
is the data associated with one call to one function. The frame contains the arguments given to the
function, the function’s local variables, and the address at which the function is executing.
When your program is started, the stack has only one frame, that of the function main. This is called
the initial frame or the outermost frame. Each time a function is called, a new frame is made. Each
time a function returns, the frame for that function invocation is eliminated. If a function is recursive,
there can be many frames for the same function. The frame for the function in which execution is
actually occurring is called the innermost frame. This is the most recently created of all the stack
frames that still exist.
Inside your program, stack frames are identified by their addresses. A stack frame consists of many
bytes, each of which has its own address; each kind of computer has a convention for choosing one
byte whose address serves as the address of the frame. Usually this address is kept in a register called
the frame pointer register while execution is going on in that frame.
gdb assigns numbers to all existing stack frames, starting with zero for the innermost frame, one for
the frame that called it, and so on upward. These numbers do not really exist in your program; they
are assigned by gdb to give you a way of designating stack frames in gdb commands.
Some compilers provide a way to compile functions so that they operate without stack frames. (For
example, the gcc option
-fomit-frame-pointer
generates functions without a frame.) This is occasionally done with heavily used library functions
to save the frame setup time. gdb has limited facilities for dealing with these function invocations. If
the innermost function invocation has no stack frame, gdb nevertheless regards it as though it had a
separate frame, which is numbered zero as usual, allowing correct tracing of the function call chain.
However, gdb has no provision for frameless functions elsewhere in the stack.
Page 64

54 Chapter 8. Examining the Stack
frame args
The frame command allows you to move from one stack frame to another, and to print the stack
frame you select. args may be either the address of the frame or the stack frame number. Without
an argument, frame prints the current stack frame.
select-frame
The select-frame command allows you to move from one stack frame to another without
printing the frame. This is the silent version of frame.
8.2. Backtraces
A backtrace is a summary of how your program got where it is. It shows one line per frame, for many
frames, starting with the currently executing frame (frame zero), followed by its caller (frame one),
and on up the stack.
backtrace
bt
Print a backtrace of the entire stack: one line per frame for all frames in the stack.
You can stop the backtrace at any time by typing the system interrupt character, normally C-c.
backtrace n
bt n
Similar, but print only the innermost n frames.
backtrace -n
bt -n
Similar, but print only the outermost n frames.
The names where and info stack (abbreviated info s) are additional aliases for backtrace.
Each line in the backtrace shows the frame number and the function name. The program counter value
is also shown--unless you use set print address off. The backtrace also shows the source file
name and line number, as well as the arguments to the function. The program counter value is omitted
if it is at the beginning of the code for that line number.
Here is an example of a backtrace. It was made with the command bt 3, so it shows the innermost
three frames.
#0 m4_traceon (obs=0x24eb0, argc=1, argv=0x2b8c8)
at builtin.c:993
#1 0x6e38 in expand_macro (sym=0x2b600) at macro.c:242
#2 0x6840 in expand_token (obs=0x0, t=177664, td=0xf7fffb08)
at macro.c:71
(More stack frames follow...)
The display for frame zero does not begin with a program counter value, indicating that your program
has stopped at the beginning of the code for line 993 of builtin.c.
Most programs have a standard entry point--a place where system libraries and startup code transition
into user code. For C this is main. When gdb finds the entry function in a backtrace it will terminate
Page 65

Chapter 8. Examining the Stack 55
the backtrace, to avoid tracing into highly system-specific (and generally uninteresting) code. If you
need to examine the startup code, then you can change this behavior.
set backtrace-below-main off
Backtraces will stop when they encounter the user entry point. This is the default.
set backtrace-below-main
set backtrace-below-main on
Backtraces will continue past the user entry point to the top of the stack.
show backtrace-below-main
Display the current backtrace policy.
8.3. Selecting a frame
Most commands for examining the stack and other data in your program work on whichever stack
frame is selected at the moment. Here are the commands for selecting a stack frame; all of them finish
by printing a brief description of the stack frame just selected.
frame n
f n
Select frame number n. Recall that frame zero is the innermost (currently executing) frame, frame
one is the frame that called the innermost one, and so on. The highest-numbered frame is the one
for main.
frame addr
f addr
Select the frame at address addr. This is useful mainly if the chaining of stack frames has been
damaged by a bug, making it impossible for gdb to assign numbers properly to all frames. In
addition, this can be useful when your program has multiple stacks and switches between them.
On the SPARC architecture, frame needs two addresses to select an arbitrary frame: a frame
pointer and a stack pointer.
On the MIPS and Alpha architecture, it needs two addresses: a stack pointer and a program
counter.
On the 29k architecture, it needs three addresses: a register stack pointer, a program counter, and
a memory stack pointer.
up n
Move n frames up the stack. For positive numbers n, this advances toward the outermost frame,
to higher frame numbers, to frames that have existed longer. n defaults to one.
down n
Move n frames down the stack. For positive numbers n, this advances toward the innermost
frame, to lower frame numbers, to frames that were created more recently. n defaults to one. You
may abbreviate down as do.
All of these commands end by printing two lines of output describing the frame. The first line shows
the frame number, the function name, the arguments, and the source file and line number of execution
in that frame. The second line shows the text of that source line.
Page 66

56 Chapter 8. Examining the Stack
For example:
(gdb) up
#1 0x22f0 in main (argc=1, argv=0xf7fffbf4, env=0xf7fffbfc)
at env.c:10
10 read_input_file (argv[i]);
After such a printout, the list command with no arguments prints ten lines centered on the point
of execution in the frame. You can also edit the program at the point of execution with your favorite
editing program by typing edit. Refer to Section 9.1 Printing source lines for details.
up-silently n
down-silently n
These two commands are variants of up and down, respectively; they differ in that they do their
work silently, without causing display of the new frame. They are intended primarily for use in
gdb command scripts, where the output might be unnecessary and distracting.
8.4. Information about a frame
There are several other commands to print information about the selected stack frame.
frame
f
When used without any argument, this command does not change which frame is selected, but
prints a brief description of the currently selected stack frame. It can be abbreviated f. With an
argument, this command is used to select a stack frame. Refer to Section 8.3 Selecting a frame.
info frame
info f
This command prints a verbose description of the selected stack frame, including:
• the address of the frame
• the address of the next frame down (called by this frame)
• the address of the next frame up (caller of this frame)
• the language in which the source code corresponding to this frame is written
• the address of the frame’s arguments
• the address of the frame’s local variables
• the program counter saved in it (the address of execution in the caller frame)
• which registers were saved in the frame
The verbose description is useful when something has gone wrong that has made the stack format
fail to fit the usual conventions.
Page 67

Chapter 8. Examining the Stack 57
info frame addr
info f addr
Print a verbose description of the frame at address addr, without selecting that frame. The selected frame remains unchanged by this command. This requires the same kind of address (more
than one for some architectures) that you specify in the frame command. Refer to Section 8.3
Selecting a frame.
info args
Print the arguments of the selected frame, each on a separate line.
info locals
Print the local variables of the selected frame, each on a separate line. These are all variables
(declared either static or automatic) accessible at the point of execution of the selected frame.
info catch
Print a list of all the exception handlers that are active in the current stack frame at the current
point of execution. To see other exception handlers, visit the associated frame (using the up,
down, or frame commands); then type info catch. Refer to Section 7.1.3 Setting catchpoints.
Page 68

58 Chapter 8. Examining the Stack
Page 69

Chapter 9.
Examining Source Files
gdb can print parts of your program’s source, since the debugging information recorded in the program
tells gdb what source files were used to build it. When your program stops, gdb spontaneously prints
the line where it stopped. Likewise, when you select a stack frame (refer to Section 8.3 Selecting a
frame), gdb prints the line where execution in that frame has stopped. You can print other portions of
source files by explicit command.
If you use gdb through its gnu Emacs interface, you may prefer to use Emacs facilities to view source;
refer to Chapter 25 Using gdb under gnu Emacs.
9.1. Printing source lines
To print lines from a source file, use the list command (abbreviated l). By default, ten lines are
printed. There are several ways to specify what part of the file you want to print.
Here are the forms of the list command most commonly used:
list linenum
Print lines centered around line number linenum in the current source file.
list function
Print lines centered around the beginning of function function.
list
Print more lines. If the last lines printed were printed with a list command, this prints lines
following the last lines printed; however, if the last line printed was a solitary line printed as part
of displaying a stack frame (refer to Chapter 8 Examining the Stack), this prints lines centered
around that line.
list -
Print lines just before the lines last printed.
By default, gdb prints ten source lines with any of these forms of the list command. You can change
this using set listsize:
set listsize count
Make the list command display count source lines (unless the list argument explicitly specifies some other number).
show listsize
Display the number of lines that list prints.
Repeating a list command with [RET] discards the argument, so it is equivalent to typing just list.
This is more useful than listing the same lines again. An exception is made for an argument of -; that
argument is preserved in repetition so that each repetition moves up in the source file.
In general, the list command expects you to supply zero, one or two linespecs. Linespecs specify
source lines; there are several ways of writing them, but the effect is always to specify some source
line. Here is a complete description of the possible arguments for list:
Page 70

60 Chapter 9. Examining Source Files
list linespec
Print lines centered around the line specified by linespec.
list first,last
Print lines from first to last. Both arguments are linespecs.
list ,last
Print lines ending with last.
list first,
Print lines starting with first.
list +
Print lines just after the lines last printed.
list -
Print lines just before the lines last printed.
list
As described in the preceding table.
Here are the ways of specifying a single source line--all the kinds of linespec.
number
Specifies line number of the current source file. When a list command has two linespecs, this
refers to the same source file as the first linespec.
+offset
Specifies the line offset lines after the last line printed. When used as the second linespec in a
list command that has two, this specifies the line offset lines down from the first linespec.
-offset
Specifies the line offset lines before the last line printed.
filename:number
Specifies line number in the source file filename.
function
Specifies the line that begins the body of the function function. For example: in C, this is the
line with the open brace.
filename:function
Specifies the line of the open-brace that begins the body of the function function in the file
filename. You only need the file name with a function name to avoid ambiguity when there are
identically named functions in different source files.
*address
Specifies the line containing the program address address. address may be any expression.
Page 71

Chapter 9. Examining Source Files 61
9.2. Editing source files
To edit the lines in a source file, use the edit command. The editing program of your choice is
invoked with the current line set to the active line in the program. Alternatively, there are several ways
to specify what part of the file you want to print if you want to see other parts of the program.
Here are the forms of the edit command most commonly used:
edit
Edit the current source file at the active line number in the program.
edit number
Edit the current source file with number as the active line number.
edit function
Edit the file containing function at the beginning of its definition.
edit filename:number
Specifies line number in the source file filename.
edit filename:function
Specifies the line that begins the body of the function function in the file filename. You only
need the file name with a function name to avoid ambiguity when there are identically named
functions in different source files.
edit *address
Specifies the line containing the program address address. address may be any expression.
9.2.1. Choosing your editor
You can customize gdb to use any editor you want1. By default, it is /bin/ex, but you can change this
by setting the environment variable EDITOR before using gdb. For example, to configure gdb to use
the vi editor, you could use these commands with the sh shell:
EDITOR=/usr/bin/vi
export EDITOR
gdb ...
or in the csh shell,
setenv EDITOR /usr/bin/vi
gdb ...
9.3. Searching source files
There are two commands for searching through the current source file for a regular expression.
1. The only restriction is that your editor (say ex), recognizes the following command-line syntax:
ex +number file The optional numeric value +number designates the active line in the file.
Page 72

62 Chapter 9. Examining Source Files
forward-search regexp
search regexp
The command forward-search regexp checks each line, starting with the one following the
last line listed, for a match for regexp. It lists the line that is found. You can use the synonym
search regexp or abbreviate the command name as fo.
reverse-search regexp
The command reverse-search regexp checks each line, starting with the one before the last
line listed and going backward, for a match for regexp. It lists the line that is found. You can
abbreviate this command as rev.
9.4. Specifying source directories
Executable programs sometimes do not record the directories of the source files from which they were
compiled, just the names. Even when they do, the directories could be moved between the compilation
and your debugging session. gdb has a list of directories to search for source files; this is called the
source path. Each time gdb wants a source file, it tries all the directories in the list, in the order they
are present in the list, until it finds a file with the desired name. Note that the executable search path
is not used for this purpose. Neither is the current working directory, unless it happens to be in the
source path.
If gdb cannot find a source file in the source path, and the object program records a directory, gdb tries
that directory too. If the source path is empty, and there is no record of the compilation directory, gdb
looks in the current directory as a last resort.
Whenever you reset or rearrange the source path, gdb clears out any information it has cached about
where source files are found and where each line is in the file.
When you start gdb, its source path includes only cdir and cwd, in that order. To add other directories,
use the directory command.
directory dirname ...
dir dirname ...
Add directory dirname to the front of the source path. Several directory names may be given to
this command, separated by : (; on MS-DOS and MS-Windows, where : usually appears as part
of absolute file names) or whitespace. You may specify a directory that is already in the source
path; this moves it forward, so gdb searches it sooner.
You can use the string $cdir to refer to the compilation directory (if one is recorded), and $cwd
to refer to the current working directory. $cwd is not the same as .--the former tracks the current
working directory as it changes during your gdb session, while the latter is immediately expanded
to the current directory at the time you add an entry to the source path.
directory
Reset the source path to empty again. This requires confirmation.
show directories
Print the source path: show which directories it contains.
If your source path is cluttered with directories that are no longer of interest, gdb may sometimes
cause confusion by finding the wrong versions of source. You can correct the situation as follows:
1. Use directory with no argument to reset the source path to empty.
2. Use directory with suitable arguments to reinstall the directories you want in the source path.
You can add all the directories in one command.
Page 73

Chapter 9. Examining Source Files 63
9.5. Source and machine code
You can use the command info line to map source lines to program addresses (and vice versa),
and the command disassemble to display a range of addresses as machine instructions. When run
under gnu Emacs mode, the info line command causes the arrow to point to the line specified.
Also, info line prints addresses in symbolic form as well as hex.
info line linespec
Print the starting and ending addresses of the compiled code for source line linespec. You can
specify source lines in any of the ways understood by the list command (refer to Section 9.1
Printing source lines).
For example, we can use info line to discover the location of the object code for the first line of
function m4_changequote:
(gdb) info line m4_changequote
Line 895 of "builtin.c" starts at pc 0x634c and ends at 0x6350.
We can also inquire (using *addr as the form for linespec) what source line covers a particular
address:
(gdb) info line *0x63ff
Line 926 of "builtin.c" starts at pc 0x63e4 and ends at 0x6404.
After info line, the default address for the x command is changed to the starting address of the
line, so that x/i is sufficient to begin examining the machine code (refer to Section 10.5 Examining
memory). Also, this address is saved as the value of the convenience variable $_ (refer to Section 10.9
Convenience variables).
disassemble
This specialized command dumps a range of memory as machine instructions. The default memory range is the function surrounding the program counter of the selected frame. A single argument to this command is a program counter value; gdb dumps the function surrounding this
value. Two arguments specify a range of addresses (first inclusive, second exclusive) to dump.
The following example shows the disassembly of a range of addresses of HP PA-RISC 2.0 code:
(gdb) disas 0x32c4 0x32e4
Dump of assembler code from 0x32c4 to 0x32e4:
0x32c4
main+204: addil 0,dp
0x32c8main+208: ldw 0x22c(sr0,r1),r26
0x32cc
main+212: ldil 0x3000,r31
0x32d0main+216: ble 0x3f8(sr4,r31)
0x32d4main+220: ldo 0(r31),rp
0x32d8main+224: addil -0x800,dp
0x32dcmain+228: ldo 0x588(r1),r26
0x32e0main+232: ldil 0x3000,r31
End of assembler dump.
Some architectures have more than one commonly-used set of instruction mnemonics or other syntax.
Page 74

64 Chapter 9. Examining Source Files
set disassembly-flavor instruction-set
Select the instruction set to use when disassembling the program via the disassemble or x/i
commands.
Currently this command is only defined for the Intel x86 family. You can set instruction-set
to either intel or att. The default is att, the AT&T flavor used by default by Unix assemblers
for x86-based targets.
Page 75

Chapter 10.
Examining Data
The usual way to examine data in your program is with the print command (abbreviated p), or its
synonym inspect. It evaluates and prints the value of an expression of the language your program is
written in (refer to Chapter 14 Using gdb with Different Languages).
print expr
print /f expr
expr is an expression (in the source language). By default the value of expr is printed in a
format appropriate to its data type; you can choose a different format by specifying /f, where f
is a letter specifying the format; refer to Section 10.4 Output formats.
print
print /f
If you omit expr, gdb displays the last value again (from the value history; (refer to Section 10.8
Value history). This allows you to conveniently inspect the same value in an alternative format.
A more low-level way of examining data is with the x command. It examines data in memory at a
specified address and prints it in a specified format. Refer to Section 10.5 Examining memory.
If you are interested in information about types, or about how the fields of a struct or a class are
declared, use the ptype exp command rather than print. Refer to Chapter 15 Examining the Symbol
Table.
10.1. Expressions
print and many other gdb commands accept an expression and compute its value. Any kind of
constant, variable or operator defined by the programming language you are using is valid in an
expression in gdb. This includes conditional expressions, function calls, casts, and string constants. It
also includes preprocessor macros, if you compiled your program to include this information; refer to
Section 6.1 Compiling for debugging.
gdb supports array constants in expressions input by the user. The syntax is {element, element.. . }.
For example, you can use the command print {1, 2, 3} to build up an array in memory that is
malloced in the target program.
Because C is so widespread, most of the expressions shown in examples in this manual are in C. Refer
to Chapter 14 Using gdb with Different Languages, for information on how to use expressions in other
languages.
In this section, we discuss operators that you can use in gdb expressions regardless of your programming language.
Casts are supported in all languages, not just in C, because it is so useful to cast a number into a
pointer in order to examine a structure at that address in memory.
gdb supports these operators, in addition to those common to programming languages:
@
@ is a binary operator for treating parts of memory as arrays. Refer to Section 10.3 Artificial
arrays, for more information.
Page 76

66 Chapter 10. Examining Data
::
:: allows you to specify a variable in terms of the file or function where it is defined. Refer to
Section 10.2 Program variables.
{type} addr
Refers to an object of type type stored at address addr in memory. addr may be any expression
whose value is an integer or pointer (but parentheses are required around binary operators, just
as in a cast). This construct is allowed regardless of what kind of data is normally supposed to
reside at addr.
10.2. Program variables
The most common kind of expression to use is the name of a variable in your program.
Variables in expressions are understood in the selected stack frame (refer to Section 8.3 Selecting a
frame); they must be either:
• global (or file-static)
or
• visible according to the scope rules of the programming language from the point of execution in
that frame
This means that in the function
foo (a)
int a;
{
bar (a);
{
int b = test ();
bar (b);
}
}
you can examine and use the variable a whenever your program is executing within the function foo,
but you can only use or examine the variable b while your program is executing inside the block where
b is declared.
There is an exception: you can refer to a variable or function whose scope is a single source file even
if the current execution point is not in this file. But it is possible to have more than one such variable
or function with the same name (in different source files). If that happens, referring to that name has
unpredictable effects. If you wish, you can specify a static variable in a particular function or file,
using the colon-colon notation:
file::variable
function::variable
Here file or function is the name of the context for the static variable. In the case of file names,
you can use quotes to make sure gdb parses the file name as a single word--for example, to print a
global value of x defined in f2.c:
Page 77

Chapter 10. Examining Data 67
(gdb) p ’f2.c’::x
This use of :: is very rarely in conflict with the very similar use of the same notation in C++. gdb
also supports use of the C++ scope resolution operator in gdb expressions.
Warning: Occasionally, a local variable may appear to have the wrong value at certain points in a function-
-just after entry to a new scope, and just before exit.
You may see this problem when you are stepping by machine instructions. This is because, on most
machines, it takes more than one instruction to set up a stack frame (including local variable definitions); if you are stepping by machine instructions, variables may appear to have the wrong values
until the stack frame is completely built. On exit, it usually also takes more than one machine instruction to destroy a stack frame; after you begin stepping through that group of instructions, local
variable definitions may be gone.
This may also happen when the compiler does significant optimizations. To be sure of always seeing
accurate values, turn off all optimization when compiling.
Another possible effect of compiler optimizations is to optimize unused variables out of existence, or
assign variables to registers (as opposed to memory addresses). Depending on the support for such
cases offered by the debug info format used by the compiler, gdb might not be able to display values
for such local variables. If that happens, gdb will print a message like this:
No symbol "foo" in current context.
To solve such problems, either recompile without optimizations, or use a different debug info format,
if the compiler supports several such formats. For example, gcc, the gnu C/C++ compiler usually
supports the -gstabs+ option. -gstabs+ produces debug info in a format that is superior to formats
such as COFF. You may be able to use DWARF 2 (-gdwarf-2), which is also an effective form for
debug info. .
10.3. Artificial arrays
It is often useful to print out several successive objects of the same type in memory; a section of an
array, or an array of dynamically determined size for which only a pointer exists in the program.
You can do this by referring to a contiguous span of memory as an artificial array, using the binary
operator @. The left operand of @ should be the first element of the desired array and be an individual
object. The right operand should be the desired length of the array. The result is an array value whose
elements are all of the type of the left argument. The first element is actually the left argument; the
second element comes from bytes of memory immediately following those that hold the first element,
and so on. Here is an example. If a program says
int *array = (int *) malloc (len * sizeof (int));
you can print the contents of array with
p *array@len
Page 78

68 Chapter 10. Examining Data
The left operand of @ must reside in memory. Array values made with @ in this way behave just like
other arrays in terms of subscripting, and are coerced to pointers when used in expressions. Artificial
arrays most often appear in expressions via the value history (refer to Section 10.8 Value history),
after printing one out.
Another way to create an artificial array is to use a cast. This re-interprets a value as if it were an array.
The value need not be in memory:
(gdb) p/x (short[2])0x12345678
$1 = {0x1234, 0x5678}
As a convenience, if you leave the array length out (as in (type[])value) gdb calculates the size to
fill the value (as sizeof(value)/sizeof(type):
(gdb) p/x (short[])0x12345678
$2 = {0x1234, 0x5678}
Sometimes the artificial array mechanism is not quite enough; in moderately complex data structures,
the elements of interest may not actually be adjacent--for example, if you are interested in the values
of pointers in an array. One useful work-around in this situation is to use a convenience variable (refer
to Section 10.9 Convenience variables) as a counter in an expression that prints the first interesting
value, and then repeat that expression via [RET]. For instance, suppose you have an array dtab of
pointers to structures, and you are interested in the values of a field fv in each structure. Here is an
example of what you might type:
set $i = 0
p dtab[$i++]-
fv
[RET]
[RET]
...
10.4. Output formats
By default, gdb prints a value according to its data type. Sometimes this is not what you want. For
example, you might want to print a number in hex, or a pointer in decimal. Or you might want to
view data in memory at a certain address as a character string or as an instruction. To do these things,
specify an output format when you print a value.
The simplest use of output formats is to say how to print a value already computed. This is done by
starting the arguments of the print command with a slash and a format letter. The format letters
supported are:
x
Regard the bits of the value as an integer, and print the integer in hexadecimal.
d
Print as integer in signed decimal.
u
Print as integer in unsigned decimal.
Page 79

Chapter 10. Examining Data 69
o
Print as integer in octal.
t
Print as integer in binary. The letter t stands for "two".
1
a
Print as an address, both absolute in hexadecimal and as an offset from the nearest preceding
symbol. You can use this format used to discover where (in what function) an unknown address
is located:
(gdb) p/a 0x54320
$3 = 0x54320
_initialize_vx+396
The command info symbol 0x54320 yields similar results. info symbol.
c
Regard as an integer and print it as a character constant.
f
Regard the bits of the value as a floating point number and print using typical floating point
syntax.
For example, to print the program counter in hex (refer to Section 10.10 Registers), type
p/x $pc
Note that no space is required before the slash; this is because command names in gdb cannot contain
a slash.
To reprint the last value in the value history with a different format, you can use the print command
with just a format and no expression. For example, p/x reprints the last value in hex.
10.5. Examining memory
You can use the command x (for "examine") to examine memory in any of several formats, independently of your program’s data types.
x/nfu addr
x addr
x
Use the x command to examine memory.
n, f, and u are all optional parameters that specify how much memory to display and how to format
it; addr is an expression giving the address where you want to start displaying memory. If you use
defaults for nfu, you need not type the slash /. Several commands set convenient defaults for addr.
1. b cannot be used because these format letters are also used with the x command, where b stands for "byte";
refer to Section 10.5 Examining memory.
Page 80

70 Chapter 10. Examining Data
n, the repeat count
The repeat count is a decimal integer; the default is 1. It specifies how much memory (counting
by units u) to display.
f, the display format
The display format is one of the formats used by print, s (null-terminated string), or i (machine
instruction). The default is x (hexadecimal) initially. The default changes each time you use either
x or print.
u, the unit size
The unit size is any of
b
Bytes.
h
Halfwords (two bytes).
w
Words (four bytes). This is the initial default.
g
Giant words (eight bytes).
Each time you specify a unit size with x, that size becomes the default unit the next time you use
x. (For the s and i formats, the unit size is ignored and is normally not written.)
addr, starting display address
addr is the address where you want gdb to begin displaying memory. The expression need not
have a pointer value (though it may); it is always interpreted as an integer address of a byte of
memory. Refer to Section 10.1 Expressions, for more information on expressions. The default
for addr is usually just after the last address examined--but several other commands also set the
default address: info breakpoints (to the address of the last breakpoint listed), info line
(to the starting address of a line), and print (if you use it to display a value from memory).
For example, x/3uh 0x54320 is a request to display three halfwords (h) of memory, formatted as
unsigned decimal integers (u), starting at address 0x54320. x/4xw $sp prints the four words (w) of
memory above the stack pointer (here, $sp; (refer to Section 10.10 Registers) in hexadecimal (x).
Since the letters indicating unit sizes are all distinct from the letters specifying output formats, you
do not have to remember whether unit size or format comes first; either order works. The output
specifications 4xw and 4wx mean exactly the same thing. (However, the count n must come first; wx4
does not work.)
Even though the unit size u is ignored for the formats s and i, you might still want to use a count n;
for example, 3i specifies that you want to see three machine instructions, including any operands. The
command disassemble gives an alternative way of inspecting machine instructions; refer to Section
9.5 Source and machine code.
All the defaults for the arguments to x are designed to make it easy to continue scanning memory with
minimal specifications each time you use x. For example, after you have inspected three machine
instructions with x/3i addr, you can inspect the next seven with just x/7. If you use [RET] to repeat
the x command, the repeat count n is used again; the other arguments default as for successive uses
of x.
Page 81

Chapter 10. Examining Data 71
The addresses and contents printed by the x command are not saved in the value history because there
is often too much of them and they would get in the way. Instead, gdb makes these values available
for subsequent use in expressions as values of the convenience variables $_ and $__. After an x
command, the last address examined is available for use in expressions in the convenience variable
$_. The contents of that address, as examined, are available in the convenience variable $__.
If the x command has a repeat count, the address and contents saved are from the last memory unit
printed; this is not the same as the last address printed if several units were printed on the last line of
output.
10.6. Automatic display
If you find that you want to print the value of an expression frequently (to see how it changes), you
might want to add it to the automatic display list so that gdb prints its value each time your program
stops. Each expression added to the list is given a number to identify it; to remove an expression from
the list, you specify that number. The automatic display looks like this:
2: foo = 38
3: bar[5] = (struct hack *) 0x3804
This display shows item numbers, expressions and their current values. As with displays you request
manually using x or print, you can specify the output format you prefer; in fact, display decides
whether to use print or x depending on how elaborate your format specification is--it uses x if you
specify a unit size, or one of the two formats (i and s) that are only supported by x; otherwise it uses
print.
display expr
Add the expression expr to the list of expressions to display each time your program stops. Refer
to Section 10.1 Expressions.
display does not repeat if you press [RET] again after using it.
display/fmt expr
For fmt specifying only a display format and not a size or count, add the expression expr to the
auto-display list but arrange to display it each time in the specified format fmt. Refer to Section
10.4 Output formats.
display/fmt addr
For fmt i or s, or including a unit-size or a number of units, add the expression addr as a
memory address to be examined each time your program stops. Examining means in effect doing
x/fmt addr. Refer to Section 10.5 Examining memory.
For example, display/i $pc can be helpful, to see the machine instruction about to be executed
each time execution stops ($pc is a common name for the program counter; (refer to Section 10.10
Registers).
undisplay dnums...
delete display dnums...
Remove item numbers dnums from the list of expressions to display.
undisplay does not repeat if you press [RET] after using it. (Otherwise you would just get the
error No display number ....)
Page 82

72 Chapter 10. Examining Data
disable display dnums...
Disable the display of item numbers dnums. A disabled display item is not printed automatically,
but is not forgotten. It may be enabled again later.
enable display dnums...
Enable display of item numbers dnums. It becomes effective once again in auto display of its
expression, until you specify otherwise.
display
Display the current values of the expressions on the list, just as is done when your program stops.
info display
Print the list of expressions previously set up to display automatically, each one with its item
number, but without showing the values. This includes disabled expressions, which are marked
as such. It also includes expressions which would not be displayed right now because they refer
to automatic variables not currently available.
If a display expression refers to local variables, then it does not make sense outside the lexical context
for which it was set up. Such an expression is disabled when execution enters a context where one of
its variables is not defined. For example, if you give the command display last_char while inside
a function with an argument last_char, gdb displays this argument while your program continues to
stop inside that function. When it stops elsewhere--where there is no variable last_char--the display
is disabled automatically. The next time your program stops where last_char is meaningful, you
can enable the display expression once again.
10.7. Print settings
gdb provides the following ways to control how arrays, structures, and symbols are printed.
These settings are useful for debugging programs in any language:
set print address
set print address on
{No value for ‘
listitem>GDBN’} prints memory addresses showing the location of stack
traces, structure values, pointer values, breakpoints, and so forth, even when it also displays the
contents of those addresses. The default is on. For example, this is what a stack frame display
looks like with set print address on:
(gdb) f
#0 set_quotes (lq=0x34c78 "
", rq=0x34c88 "
")
at input.c:530
530 if (lquote != def_lquote)
set print address off
Do not print addresses when displaying their contents. For example, this is the same stack frame
displayed with set print address off:
(gdb) set print addr off
(gdb) f
#0 set_quotes (lq="
", rq="
") at input.c:530
530 if (lquote != def_lquote)
Page 83

Chapter 10. Examining Data 73
You can use set print address off to eliminate all machine dependent displays from the
gdb interface. For example, with print address off, you should get the same text for backtraces on all machines--whether or not they involve pointer arguments.
show print address
Show whether or not addresses are to be printed.
When gdb prints a symbolic address, it normally prints the closest earlier symbol plus an offset. If
that symbol does not uniquely identify the address (for example, it is a name whose scope is a single
source file), you may need to clarify. One way to do this is with info line, for example info
line *0x4537. Alternately, you can set gdb to print the source file and line number when it prints a
symbolic address:
set print symbol-filename on
Tell gdb to print the source file name and line number of a symbol in the symbolic form of an
address.
set print symbol-filename off
Do not print source file name and line number of a symbol. This is the default.
show print symbol-filename
Show whether or not gdb will print the source file name and line number of a symbol in the
symbolic form of an address.
Another situation where it is helpful to show symbol filenames and line numbers is when disassembling code; gdb shows you the line number and source file that corresponds to each instruction.
Also, you may wish to see the symbolic form only if the address being printed is reasonably close to
the closest earlier symbol:
set print max-symbolic-offset max-offset
Tell gdb to only display the symbolic form of an address if the offset between the closest earlier
symbol and the address is less than max-offset. The default is 0, which tells gdb to always
print the symbolic form of an address if any symbol precedes it.
show print max-symbolic-offset
Ask how large the maximum offset is that gdb prints in a symbolic address.
If you have a pointer and you are not sure where it points, try set print symbol-filename on.
Then you can determine the name and source file location of the variable where it points, using p/a
pointer. This interprets the address in symbolic form. For example, here gdb shows that a variable
ptt points at another variable t, defined in hi2.c:
(gdb) set print symbol-filename on
(gdb) p/a ptt
$4 = 0xe008
t in hi2.c
Warning: For pointers that point to a local variable, p/a does not show the symbol name and filename of
the referent, even with the appropriate set print options turned on.
Page 84

74 Chapter 10. Examining Data
Other settings control how different kinds of objects are printed:
set print array
set print array on
Pretty print arrays. This format is more convenient to read, but uses more space. The default is
off.
set print array off
Return to compressed format for arrays.
show print array
Show whether compressed or pretty format is selected for displaying arrays.
set print elements number-of-elements
Set a limit on how many elements of an array gdb will print. If gdb is printing a large array,
it stops printing after it has printed the number of elements set by the set print elements
command. This limit also applies to the display of strings. When gdb starts, this limit is set to
200. Setting number-of-elements to zero means that the printing is unlimited.
show print elements
Display the number of elements of a large array that gdb will print. If the number is 0, then the
printing is unlimited.
set print null-stop
Cause gdb to stop printing the characters of an array when the first null is encountered. This is
useful when large arrays actually contain only short strings. The default is off.
set print pretty on
Cause gdb to print structures in an indented format with one member per line, like this:
$1 = {
next = 0x0,
flags = {
sweet = 1,
sour = 1
},
meat = 0x54 "Pork"
}
set print pretty off
Cause gdb to print structures in a compact format, like this:
$1 = {next = 0x0, flags = {sweet = 1, sour = 1}, \
meat = 0x54 "Pork"}
This is the default format.
show print pretty
Show which format gdb is using to print structures.
Page 85

Chapter 10. Examining Data 75
set print sevenbit-strings on
Print using only seven-bit characters; if this option is set, gdb displays any eight-bit characters
(in strings or character values) using the notation \nnn. This setting is best if you are working in
English (ascii) and you use the high-order bit of characters as a marker or "meta" bit.
set print sevenbit-strings off
Print full eight-bit characters. This allows the use of more international character sets, and is the
default.
show print sevenbit-strings
Show whether or not gdb is printing only seven-bit characters.
set print union on
Tell gdb to print unions which are contained in structures. This is the default setting.
set print union off
Tell gdb not to print unions which are contained in structures.
show print union
Ask gdb whether or not it will print unions which are contained in structures.
For example, given the declarations
typedef enum {Tree, Bug} Species;
typedef enum {Big_tree, Acorn, Seedling} Tree_forms;
typedef enum {Caterpillar, Cocoon, Butterfly}
Bug_forms;
struct thing {
Species it;
union {
Tree_forms tree;
Bug_forms bug;
} form;
};
struct thing foo = {Tree, {Acorn}};
with set print union on in effect p foo would print
$1 = {it = Tree, form = {tree = Acorn, bug = Cocoon}}
and with set print union off in effect it would print
$1 = {it = Tree, form = {...}}
These settings are of interest when debugging C++ programs:
set print demangle
set print demangle on
Print C++ names in their source form rather than in the encoded ("mangled") form passed to the
assembler and linker for type-safe linkage. The default is on.
Page 86

76 Chapter 10. Examining Data
show print demangle
Show whether C++ names are printed in mangled or demangled form.
set print asm-demangle
set print asm-demangle on
Print C++ names in their source form rather than their mangled form, even in assembler code
printouts such as instruction disassemblies. The default is off.
show print asm-demangle
Show whether C++ names in assembly listings are printed in mangled or demangled form.
set demangle-style style
Choose among several encoding schemes used by different compilers to represent C++ names.
The choices for style are currently:
auto
Allow gdb to choose a decoding style by inspecting your program.
gnu
Decode based on the gnu C++ compiler (g++) encoding algorithm. This is the default.
hp
Decode based on the HP ANSI C++ (aCC) encoding algorithm.
lucid
Decode based on the Lucid C++ compiler (lcc) encoding algorithm.
arm
Decode using the algorithm in the [C++ Annotated Reference Manual]. Warning: this setting alone is not sufficient to allow debugging cfront-generated executables. gdb would
require further enhancement to permit that.
If you omit style, you will see a list of possible formats.
show demangle-style
Display the encoding style currently in use for decoding C++ symbols.
set print object
set print object on
When displaying a pointer to an object, identify the actual (derived) type of the object rather than
the declared type, using the virtual function table.
set print object off
Display only the declared type of objects, without reference to the virtual function table. This is
the default setting.
show print object
Show whether actual, or declared, object types are displayed.
Page 87

Chapter 10. Examining Data 77
set print static-members
set print static-members on
Print static members when displaying a C++ object. The default is on.
set print static-members off
Do not print static members when displaying a C++ object.
show print static-members
Show whether C++ static members are printed, or not.
set print vtbl
set print vtbl on
Pretty print C++ virtual function tables. The default is off. (The vtbl commands do not work
on programs compiled with the HP ANSI C++ compiler (aCC).)
set print vtbl off
Do not pretty print C++ virtual function tables.
show print vtbl
Show whether C++ virtual function tables are pretty printed, or not.
10.8. Value history
Values printed by the print command are saved in the gdb value history. This allows you to refer to
them in other expressions. Values are kept until the symbol table is re-read or discarded (for example
with the file or symbol-file commands). When the symbol table changes, the value history is
discarded, since the values may contain pointers back to the types defined in the symbol table.
The values printed are given history numbers by which you can refer to them. These are successive
integers starting with one. print shows you the history number assigned to a value by printing $num
= before the value; here num is the history number.
To refer to any previous value, use $ followed by the value’s history number. The way print labels
its output is designed to remind you of this. Just $ refers to the most recent value in the history, and
$$ refers to the value before that. $$n refers to the nth value from the end; $$2 is the value just prior
to $$, $$1 is equivalent to $$, and $$0 is equivalent to $.
For example, suppose you have just printed a pointer to a structure and want to see the contents of the
structure. It suffices to type
p *$
If you have a chain of structures where the component next points to the next one, you can print the
contents of the next one with this:
p *$.next
You can print successive links in the chain by repeating this command--which you can do by just
typing [RET].
Page 88

78 Chapter 10. Examining Data
Note that the history records values, not expressions. If the value of x is 4 and you type these commands:
print x
set x=5
then the value recorded in the value history by the print command remains 4 even though the value
of x has changed.
show values
Print the last ten values in the value history, with their item numbers. This is like p $$9 repeated
ten times, except that show values does not change the history.
show values n
Print ten history values centered on history item number n.
show values +
Print ten history values just after the values last printed. If no more values are available, show
values + produces no display.
Pressing [RET] to repeat show values n has exactly the same effect as show values +.
10.9. Convenience variables
gdb provides convenience variables that you can use within gdb to hold on to a value and refer to
it later. These variables exist entirely within gdb; they are not part of your program, and setting a
convenience variable has no direct effect on further execution of your program. That is why you can
use them freely.
Convenience variables are prefixed with $. Any name preceded by $ can be used for a convenience
variable, unless it is one of the predefined machine-specific register names (refer to Section 10.10
Registers). (Value history references, in contrast, are numbers preceded by $. Refer to Section 10.8
Value history.)
You can save a value in a convenience variable with an assignment expression, just as you would set
a variable in your program. For example:
set $foo = *object_ptr
would save in $foo the value contained in the object pointed to by object_ptr.
Using a convenience variable for the first time creates it, but its value is void until you assign a new
value. You can alter the value with another assignment at any time.
Convenience variables have no fixed types. You can assign a convenience variable any type of value,
including structures and arrays, even if that variable already has a value of a different type. The
convenience variable, when used as an expression, has the type of its current value.
Page 89

Chapter 10. Examining Data 79
show convenience
Print a list of convenience variables used so far, and their values. Abbreviated show conv.
One of the ways to use a convenience variable is as a counter to be incremented or a pointer to be
advanced. For example, to print a field from successive elements of an array of structures:
set $i = 0
print bar[$i++]-
contents
Repeat that command by typing [RET].
Some convenience variables are created automatically by gdb and given values likely to be useful.
$_
The variable $_ is automatically set by the x command to the last address examined (refer to
Section 10.5 Examining memory). Other commands which provide a default address for x to examine also set $_ to that address; these commands include info line and info breakpoint.
The type of $_ is void * except when set by the x command, in which case it is a pointer to the
type of $__.
$__
The variable $__ is automatically set by the x command to the value found in the last address
examined. Its type is chosen to match the format in which the data was printed.
$_exitcode
The variable $_exitcode is automatically set to the exit code when the program being debugged
terminates.
On HP-UX systems, if you refer to a function or variable name that begins with a dollar sign, gdb
searches for a user or system name first, before it searches for a convenience variable.
10.10. Registers
You can refer to machine register contents, in expressions, as variables with names starting with $.
The names of registers are different for each machine; use info registers to see the names used
on your machine.
info registers
Print the names and values of all registers except floating-point and vector registers (in the selected stack frame).
info all-registers
Print the names and values of all registers, including floating-point and vector registers (in the
selected stack frame).
info registers regname ...
Print the relativized value of each specified register regname. As discussed in detail below,
register values are normally relative to the selected stack frame. regname may be any register
name valid on the machine you are using, with or without the initial $.
Page 90

80 Chapter 10. Examining Data
gdb has four "standard" register names that are available (in expressions) on most machines--whenever
they do not conflict with an architecture’s canonical mnemonics for registers. The register names $pc
and $sp are used for the program counter register and the stack pointer. $fp is used for a register that
contains a pointer to the current stack frame, and $ps is used for a register that contains the processor
status. For example, you could print the program counter in hex with
p/x $pc
or print the instruction to be executed next with
x/i $pc
or add four to the stack pointer2with
set $sp += 4
Whenever possible, these four standard register names are available on your machine even though the
machine has different canonical mnemonics, so long as there is no conflict. The info registers
command shows the canonical names. For example, on the SPARC, info registers displays the
processor status register as $psr but you can also refer to it as $ps; and on x86-based machines $ps
is an alias for the eflags register.
gdb always considers the contents of an ordinary register as an integer when the register is examined
in this way. Some machines have special registers which can hold nothing but floating point; these
registers are considered to have floating point values. There is no way to refer to the contents of
an ordinary register as floating point value (although you can print it as a floating point value with
print/f $regname).
Some registers have distinct "raw" and "virtual" data formats. This means that the data format in which
the register contents are saved by the operating system is not the same one that your program normally
sees. For example, the registers of the 68881 floating point coprocessor are always saved in "extended"
(raw) format, but all C programs expect to work with "double" (virtual) format. In such cases, gdb
normally works with the virtual format only (the format that makes sense for your program), but the
info registers command prints the data in both formats.
Normally, register values are relative to the selected stack frame (refer to Section 8.3 Selecting a
frame). This means that you get the value that the register would contain if all stack frames farther in
were exited and their saved registers restored. In order to see the true contents of hardware registers,
you must select the innermost frame (with frame 0).
However, gdb must deduce where registers are saved, from the machine code generated by your compiler. If some registers are not saved, or if gdb is unable to locate the saved registers, the selected stack
frame makes no difference.
2. This is a way of removing one word from the stack, on machines where stacks grow downward in memory
(most machines, nowadays). This assumes that the innermost stack frame is selected; setting $sp is not allowed
when other stack frames are selected. To pop entire frames off the stack, regardless of machine architecture, use
return; (refer to Section 16.4 Returning from a function.
Page 91

Chapter 10. Examining Data 81
10.11. Floating point hardware
Depending on the configuration, gdb may be able to give you more information about the status of the
floating point hardware.
info float
Display hardware-dependent information about the floating point unit. The exact contents and
layout vary depending on the floating point chip. Currently, info float is supported on the
ARM and x86 machines.
10.12. Vector Unit
Depending on the configuration, gdb may be able to give you more information about the status of the
vector unit.
info vector
Display information about the vector unit. The exact contents and layout vary depending on the
hardware.
10.13. Memory region attributes
Memory region attributes allow you to describe special handling required by regions of your target’s
memory. gdb uses attributes to determine whether to allow certain types of memory accesses; whether
to use specific width accesses; and whether to cache target memory.
Defined memory regions can be individually enabled and disabled. When a memory region is disabled,
gdb uses the default attributes when accessing memory in that region. Similarly, if no memory regions
have been defined, gdb uses the default attributes when accessing all memory.
When a memory region is defined, it is given a number to identify it; to enable, disable, or remove a
memory region, you specify that number.
mem lower upper attributes...
Define memory region bounded by lower and upper with attributes attributes. . . . Note that
upper == 0 is a special case: it is treated as the the target’s maximum memory address. (0xffff
on 16 bit targets, 0xffffffff on 32 bit targets, etc.)
delete mem nums...
Remove memory regions nums. . ..
disable mem nums...
Disable memory regions nums. . .. A disabled memory region is not forgotten. It may be enabled
again later.
enable mem nums...
Enable memory regions nums. . . .
Page 92

82 Chapter 10. Examining Data
info mem
Print a table of all defined memory regions, with the following columns for each region.
Memory Region Number
Enabled or Disabled.
Enabled memory regions are marked with y. Disabled memory regions are marked with n.
Lo Address
The address defining the inclusive lower bound of the memory region.
Hi Address
The address defining the exclusive upper bound of the memory region.
Attributes
The list of attributes set for this memory region.
10.13.1. Attributes
10.13.1.1. Memory Access Mode
The access mode attributes set whether gdb may make read or write accesses to a memory region.
While these attributes prevent gdb from performing invalid memory accesses, they do nothing to
prevent the target system, I/O DMA, etc. from accessing memory.
ro
Memory is read only.
wo
Memory is write only.
rw
Memory is read/write. This is the default.
10.13.1.2. Memory Access Size
The acccess size attributes tells gdb to use specific sized accesses in the memory region. Often memory
mapped device registers require specific sized accesses. If no access size attribute is specified, gdb may
use accesses of any size.
8
Use 8 bit memory accesses.
16
Use 16 bit memory accesses.
32
Use 32 bit memory accesses.
Page 93

Chapter 10. Examining Data 83
64
Use 64 bit memory accesses.
10.13.1.3. Data Cache
The data cache attributes set whether gdb will cache target memory. While this generally improves
performance by reducing debug protocol overhead, it can lead to incorrect results because gdb does
not know about volatile variables or memory mapped device registers.
cache
Enable gdb to cache target memory.
nocache
Disable gdb from caching target memory. This is the default.
10.14. Copy between memory and a file
You can use the commands dump, append, and restore to copy data between target memory and
a file. The dump and append commands write data to a file, and the restore command reads data
from a file back into the inferior’s memory. Files may be in binary, Motorola S-record, Intel hex, or
Tektronix Hex format; however, gdb can only append to binary files.
dump [format] memory filename start_addr end_addr
dump [format] value filename expr
Dump the contents of memory from start_addr to end_addr, or the value of expr, to
filename in the given format.
The format parameter may be any one of:
binary
Raw binary form.
ihex
Intel hex format.
srec
Motorola S-record format.
tekhex
Tektronix Hex format.
gdb uses the same definitions of these formats as the gnu binary utilities, like objdump and
objcopy. If format is omitted, gdb dumps the data in raw binary form.
Page 94

84 Chapter 10. Examining Data
append [binary] memory filename start_addr end_addr
append [binary] value filename expr
Append the contents of memory from start_addr to end_addr, or the value of expr, to
filename, in raw binary form. (gdb can only append data to files in raw binary form.)
restore filename [binary] bias start end
Restore the contents of file filename into memory. The restore command can automatically
recognize any known bfd file format, except for raw binary. To restore a raw binary file you must
specify the optional keyword binary after the filename.
If bias is non-zero, its value will be added to the addresses contained in the file. Binary files
always start at address zero, so they will be restored at address bias. Other bfd files have a
built-in location; they will be restored at offset bias from that location.
If start and/or end are non-zero, then only data between file offset start and file offset end
will be restored. These offsets are relative to the addresses in the file, before the bias argument
is applied.
10.15. Character Sets
If the program you are debugging uses a different character set to represent characters and strings
than the one gdb uses itself, gdb can automatically translate between the character sets for you. The
character set gdb uses we call the host character set; the one the inferior program uses we call the
target character set.
For example, if you are running gdb on a gnu/Linux system, which uses the ISO Latin 1 character set,
but you are using gdb’s remote protocol (Remote Debugging) to debug a program running on an IBM
mainframe, which uses the ebcdic character set, then the host character set is Latin-1, and the target
character set is ebcdic. If you give gdb the command set target-charset EBCDIC-US, then gdb
translates between ebcdic and Latin 1 as you print character or string values, or use character and
string literals in expressions.
gdb has no way to automatically recognize which character set the inferior program uses; you must
tell it, using the set target-charset command, described below.
Here are the commands for controlling gdb’s character set support:
set target-charset charset
Set the current target character set to charset. We list the character set names gdb recognizes
below, but if you type set target-charset followed by [TAB][TAB], gdb will list the target
character sets it supports.
set host-charset charset
Set the current host character set to charset.
By default, gdb uses a host character set appropriate to the system it is running on; you can
override that default using the set host-charset command.
gdb can only use certain character sets as its host character set. We list the character set names
gdb recognizes below, and indicate which can be host character sets, but if you type set
target-charset followed by [TAB][TAB], gdb will list the host character sets it supports.
set charset charset
Set the current host and target character sets to charset. As above, if you type set charset
followed by [TAB][TAB], gdb will list the name of the character sets that can be used for both
host and target.
Page 95

Chapter 10. Examining Data 85
show charset
Show the names of the current host and target charsets.
show host-charset
Show the name of the current host charset.
show target-charset
Show the name of the current target charset.
gdb currently includes support for the following character sets:
ASCII
Seven-bit U.S. ascii. gdb can use this as its host character set.
ISO-8859-1
The ISO Latin 1 character set. This extends ascii with accented characters needed for French,
German, and Spanish. gdb can use this as its host character set.
EBCDIC-US
IBM1047
Variants of the ebcdic character set, used on some of IBM’s mainframe operating systems.
(gnu/Linux on the S/390 uses U.S. ascii.) gdb cannot use these as its host character set.
Note that these are all single-byte character sets. More work inside GDB is needed to support multibyte or variable-width character encodings, like the UTF-8 and UCS-2 encodings of Unicode.
Here is an example of gdb’s character set support in action. Assume that the following source code
has been placed in the file charset-test.c:
#include
stdio.h
char ascii_hello[]
= {72, 101, 108, 108, 111, 44, 32, 119,
111, 114, 108, 100, 33, 10, 0};
char ibm1047_hello[]
= {200, 133, 147, 147, 150, 107, 64, 166,
150, 153, 147, 132, 90, 37, 0};
main ()
{
printf ("Hello, world!\n");
}
In this program, ascii_hello and ibm1047_hello are arrays containing the string Hello,
world! followed by a newline, encoded in the ascii and ibm1047 character sets.
We compile the program, and invoke the debugger on it:
$ gcc -g charset-test.c -o charset-test
$ gdb -nw charset-test
GNU gdb 2001-12-19-cvs
Copyright 2001 Free Software Foundation, Inc.
...
(gdb)
Page 96

86 Chapter 10. Examining Data
We can use the show charset command to see what character sets gdb is currently using to interpret
and display characters and strings:
(gdb) show charset
The current host and target character set is ‘ISO-8859-1’.
(gdb)
For the sake of printing this manual, let’s use ascii as our initial character set:
(gdb) set charset ASCII
(gdb) show charset
The current host and target character set is ‘ASCII’.
(gdb)
Let’s assume that ascii is indeed the correct character set for our host system -- in other words, let’s assume that if gdb prints characters using the ascii character set, our terminal will display them properly.
Since our current target character set is also ascii, the contents of ascii_hello print legibly:
(gdb) print ascii_hello
$1 = 0x401698 "Hello, world!\n"
(gdb) print ascii_hello[0]
$2 = 72 ’H’
(gdb)
gdb uses the target character set for character and string literals you use in expressions:
(gdb) print ’+’
$3 = 43 ’+’
(gdb)
The ascii character set uses the number 43 to encode the + character.
gdb relies on the user to tell it which character set the target program uses. If we print ibm1047_hello
while our target character set is still ascii, we get jibberish:
(gdb) print ibm1047_hello
$4 = 0x4016a8 "\310\205\223\223\226k@\246\226\231\223\204Z%"
(gdb) print ibm1047_hello[0]
$5 = 200 ’\310’
(gdb)
If we invoke the set target-charset followed by [TAB][TAB], gdb tells us the character sets it
supports:
(gdb) set target-charset
ASCII EBCDIC-US IBM1047 ISO-8859-1
(gdb) set target-charset
Page 97

Chapter 10. Examining Data 87
We can select ibm1047 as our target character set, and examine the program’s strings again. Now the
ascii string is wrong, but gdb translates the contents of ibm1047_hello from the target character set,
ibm1047, to the host character set, ascii, and they display correctly:
(gdb) set target-charset IBM1047
(gdb) show charset
The current host character set is ‘ASCII’.
The current target character set is ‘IBM1047’.
(gdb) print ascii_hello
$6 = 0x401698 "\110\145%%?\054\040\167?\162%\144\041\012"
(gdb) print ascii_hello[0]
$7 = 72 ’\110’
(gdb) print ibm1047_hello
$8 = 0x4016a8 "Hello, world!\n"
(gdb) print ibm1047_hello[0]
$9 = 200 ’H’
(gdb)
As above, gdb uses the target character set for character and string literals you use in expressions:
(gdb) print ’+’
$10 = 78 ’+’
(gdb)
The ibm1047 character set uses the number 78 to encode the + character.
Page 98

88 Chapter 10. Examining Data
Page 99

Chapter 11.
C Preprocessor Macros
Some languages, such as C and C++, provide a way to define and invoke "preprocessor macros" which
expand into strings of tokens. gdb can evaluate expressions containing macro invocations, show the
result of macro expansion, and show a macro’s definition, including where it was defined.
You may need to compile your program specially to provide gdb with information about preprocessor macros. Most compilers do not include macros in their debugging information, even when you
compile with the -g flag. Refer to Section 6.1 Compiling for debugging.
A program may define a macro at one point, remove that definition later, and then provide a different
definition after that. Thus, at different points in the program, a macro may have different definitions, or
have no definition at all. If there is a current stack frame, gdb uses the macros in scope at that frame’s
source code line. Otherwise, gdb uses the macros in scope at the current listing location; (refer to
Section 9.1 Printing source lines.
At the moment, gdb does not support the ## token-splicing operator, the # stringification operator, or
variable-arity macros.
Whenever gdb evaluates an expression, it always expands any macro invocations present in the expression. gdb also provides the following commands for working with macros explicitly.
macro expand expression
macro exp expression
Show the results of expanding all preprocessor macro invocations in expression. Since gdb
simply expands macros, but does not parse the result, expression need not be a valid expression; it can be any string of tokens.
macro expand-once expression
macro exp1 expression
(This command is not yet implemented.) Show the results of expanding those preprocessor macro
invocations that appear explicitly in expression. Macro invocations appearing in that expansion are left unchanged. This command allows you to see the effect of a particular macro more
clearly, without being confused by further expansions. Since gdb simply expands macros, but
does not parse the result, expression need not be a valid expression; it can be any string of
tokens.
info macro macro
Show the definition of the macro named macro, and describe the source location where that
definition was established.
macro define macro replacement-list
macro define macro(arglist) replacement-list
(This command is not yet implemented.) Introduce a definition for a preprocessor macro named
macro, invocations of which are replaced by the tokens given in replacement-list. The first
form of this command defines an "object-like" macro, which takes no arguments; the second
form defines a "function-like" macro, which takes the arguments given in arglist.
A definition introduced by this command is in scope in every expression evaluated in gdb, until
it is removed with the macro undef command, described below. The definition overrides all
Page 100

90 Chapter 11. C Preprocessor Macros
definitions for macro present in the program being debugged, as well as any previous usersupplied definition.
macro undef macro
(This command is not yet implemented.) Remove any user-supplied definition for the macro
named macro. This command only affects definitions provided with the macro define command, described above; it cannot remove definitions present in the program being debugged.
Here is a transcript showing the above commands in action. First, we show our source files:
$ cat sample.c
#include
stdio.h
!
#include "sample.h"
#define M 42
#define ADD(x) (M + x)
main ()
{
#define N 28
printf ("Hello, world!\n");
#undef N
printf ("We’re so creative.\n");
#define N 1729
printf ("Goodbye, world!\n");
}
$ cat sample.h
#define Q
$
Now, we compile the program using the gnu C compiler, gcc. We pass the -gdwarf-2 and -g3 flags
to ensure the compiler includes information about preprocessor macros in the debugging information.
$ gcc -gdwarf-2 -g3 sample.c -o sample
$
Now, we start gdb on our sample program:
$ gdb -nw sample
GNU gdb 2002-05-06-cvs
Copyright 2002 Free Software Foundation, Inc.
GDB is free software, ...
(gdb)
We can expand macros and examine their definitions, even when the program is not running. gdb uses
the current listing position to decide which macro definitions are in scope:
(gdb) list main
3
4 #define M 42
5 #define ADD(x) (M + x)
6
7 main ()
 Loading...
Loading...