Page 1

Red Hat Certificate
System 8
Install Guide
Ella Deon Lackey
Publication date: July 22, 2009, updated on March 25, 2010
Page 2

Install Guide
Red Hat Certificate System 8 Install Guide
Author Ella Deon Lackey
Copyright © 2009 Red Hat, Inc.
Copyright © 2009 Red Hat, Inc.
The text of and illustrations in this document are licensed by Red Hat under a Creative Commons
Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available
at http://creativecommons.org/licenses/by-sa/3.0/. In accordance with CC-BY-SA, if you distribute this
document or an adaptation of it, you must provide the URL for the original version.
Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert,
Section 4d of CC-BY-SA to the fullest extent permitted by applicable law.
Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity
Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries.
Linux® is the registered trademark of Linus Torvalds in the United States and other countries.
All other trademarks are the property of their respective owners.
1801 Varsity Drive
Raleigh, NC 27606-2072 USA
Phone: +1 919 754 3700
Phone: 888 733 4281
Fax: +1 919 754 3701
PO Box 13588
Research Triangle Park, NC 27709 USA
Page 3

About This Guide vii
1. Examples and Formatting .............................................................................................. vii
1.1. Formatting for Examples and Commands ............................................................. vii
1.2. Tool Locations .................................................................................................... vii
1.3. Guide Formatting ................................................................................................ vii
2. Additional Reading ........................................................................................................ viii
3. Giving Feedback ............................................................................................................ ix
4. Document History ............................................................................................................ x
1. Overview of Certificate System Subsystems 1
1.1. Subsystems for Managing Certificates ........................................................................... 1
1.1.1. Certificate Manager ........................................................................................... 3
1.1.2. Registration Authority ......................................................................................... 3
1.1.3. Data Recovery Manager .................................................................................... 3
1.1.4. Online Certificate Status Manager ...................................................................... 4
1.2. Subsystems for Managing Tokens ................................................................................. 4
1.2.1. Token Processing System .................................................................................. 5
1.2.2. Token Key Service ............................................................................................ 5
1.2.3. Enterprise Security Client ................................................................................... 5
1.3. Planning the Installation ................................................................................................ 6
2. Prerequisites Before Installing Certificate System 9
2.1. Supported Platforms, Hardware, and Programs .............................................................. 9
2.1.1. Supported Platforms .......................................................................................... 9
2.1.2. Supported Web Browsers .................................................................................. 9
2.1.3. Supported Smart Cards ................................................................................... 10
2.1.4. Supported HSM ............................................................................................... 10
2.1.5. Supported Charactersets .................................................................................. 10
2.2. Required Programs, Dependencies, and Configuration ................................................. 11
2.2.1. Java Development Kit (JDK) ............................................................................ 11
2.2.2. Apache ........................................................................................................... 11
2.2.3. Red Hat Directory Server ................................................................................. 12
2.2.4. Additional Packages ........................................................................................ 12
2.2.5. Firewall Configuration and iptables ................................................................... 13
2.2.6. SELinux Settings ............................................................................................. 13
2.3. Packages Installed on Red Hat Enterprise Linux .......................................................... 13
2.4. Required Information for Subsystem Configuration ....................................................... 15
2.5. Setting up Tokens for Storing Certificate System Subsystem Keys and Certificates .......... 16
2.5.1. Types of Hardware Tokens ............................................................................... 16
2.5.2. Using Hardware Security Modules with Subsystems .......................................... 17
2.5.3. Viewing Tokens ............................................................................................... 21
2.5.4. Detecting Tokens ............................................................................................. 21
3. Installation and Configuration 23
3.1. Overview of Installation ............................................................................................... 23
3.2. Installing the Certificate System Packages ................................................................... 25
3.2.1. Installing through yum ...................................................................................... 25
3.2.2. Installing from an ISO Image ............................................................................ 27
3.3. Configuring a CA ........................................................................................................ 27
3.4. Configuring an RA ...................................................................................................... 36
3.5. Configuring a DRM, OCSP, or TKS ............................................................................. 43
3.6. Configuring a TPS ...................................................................................................... 50
iii
Page 4

Install Guide
4. Additional Installation Options 61
4.1. Requesting Subsystem Certificates from an External CA ............................................... 61
4.2. Installing a CA with ECC Enabled ............................................................................... 64
4.2.1. Loading a Third-Party ECC Module .................................................................. 64
4.2.2. Loading the Certicom ECC Module ................................................................... 65
4.3. Changing the Hashing Algorithm Used for Subsystem Keys .......................................... 69
4.4. Enabling IPv6 for a Subsystem ................................................................................... 70
4.5. Configuring Separate RA Instances ............................................................................. 71
5. Creating Additional Subsystem Instances 75
5.1. About pkicreate .......................................................................................................... 75
5.2. Running pkicreate for a Single SSL Port ...................................................................... 77
5.3. Running pkicreate with Port Separation ....................................................................... 78
6. Cloning Subsystems 79
6.1. About Cloning ............................................................................................................ 79
6.1.1. Cloning for CAs ............................................................................................... 80
6.1.2. Cloning for DRMs ............................................................................................ 81
6.1.3. Cloning for Other Subsystems .......................................................................... 81
6.1.4. Cloning and Key Stores ................................................................................... 81
6.1.5. Cloning Considerations .................................................................................... 82
6.2. Exporting Keys from a Software Database ................................................................... 82
6.3. Cloning a CA ............................................................................................................. 82
6.4. Cloning OCSP Subsystems ........................................................................................ 85
6.5. Cloning DRM and TKS Subsystems ............................................................................ 88
6.6. Converting Masters and Clones .................................................................................. 90
6.6.1. Converting CA Clones and Masters .................................................................. 90
6.6.2. Converting OCSP Clones ................................................................................. 92
6.7. Updating CA Clones ................................................................................................... 92
7. Silent Configuration 95
7.1. About pkisilent ............................................................................................................ 95
7.2. Silently Configuring Subsystem ................................................................................... 99
7.3. Cloning a Subsystem Silently .................................................................................... 102
7.4. Performing Silent Configuration Using an External CA ................................................ 102
8. Updating and Removing Subsystem Packages 105
8.1. Updating Certificate System Packages ....................................................................... 105
8.2. Uninstalling Certificate System Subsystems ............................................................... 106
8.2.1. Removing a Subsystem Instance .................................................................... 106
8.2.2. Removing Certificate System Subsystem Packages ......................................... 107
9. Using Certificate System 109
9.1. Starting the Certificate System Console ..................................................................... 109
9.2. Starting, Stopping, and Restarting an Instance ........................................................... 109
9.3. Starting the Subsystem Automatically ........................................................................ 109
9.4. Finding the Subsystem Web Services Pages ............................................................. 111
9.5. Default File and Directory Locations for Certificate System .......................................... 114
9.5.1. Default CA Instance Information ..................................................................... 115
9.5.2. Default RA Instance Information ..................................................................... 116
9.5.3. Default DRM Instance Information .................................................................. 116
9.5.4. Default OCSP Instance Information ................................................................. 117
9.5.5. Default TKS Instance Information .................................................................... 118
9.5.6. Default TPS Instance Information .................................................................... 118
iv
Page 5

9.5.7. Shared Certificate System Subsystem File Locations ....................................... 119
Index 121
v
Page 6

vi
Page 7

About This Guide
This guide explains how to install and configure Red Hat Certificate System subsystems, as well as
covering some basic administrative tasks and advanced installation techniques. This guide also lists
the supported platforms and dependencies for Red Hat Certificate System; for other information, see
the Release Notes.
The Certificate System Deployment Guide explains different usage scenarios, and it is a good idea to
understand the major concepts in that guide before installing the Certificate System subsystems. The
Certificate System Administrator's Guide covers all of the administrative tasks of Red Hat Certificate
System, such as configuring logging, setting up certificate and CRL publishing, requesting and issuing
certificates, and building CRLs.
Certificate System agents should refer to the Certificate System Agent's Guide for information on
performing agent tasks, such as handling certificate requests and revoking certificates. For information
on using Certificate System to manage smart cards and security tokens, see Managing Smart Cards
with the Enterprise Security Client.
1. Examples and Formatting
1.1. Formatting for Examples and Commands
All of the examples for Red Hat Certificate System commands, file locations, and other usage are
given for Red Hat Enterprise Linux 5 (32-bit) systems. Be certain to use the appropriate commands
and files for your platform.
To start the Red Hat Certificate System:
service pki-ca start
Example 1. Example Command
1.2. Tool Locations
All of the tools for Red Hat Certificate System are located in the /usr/bin directory. These tools can
be run from any location without specifying the tool location.
1.3. Guide Formatting
Certain words are represented in different fonts, styles, and weights. Different character formatting is
used to indicate the function or purpose of the phrase being highlighted.
Formatting Style Purpose
Monospace font Monospace is used for commands, package names, files and
Monospace
with a
background
vii
Page 8
About This Guide
Formatting Style Purpose
Italicized text Any text which is italicized is a variable, such as
Bolded text Most phrases which are in bold are application names, such as
Other formatting styles draw attention to important text.
NOTE
A note provides additional information that can help illustrate the behavior of the system or
provide more detail for a specific issue.
IMPORTANT
Important information is necessary, but possibly unexpected, such as a configuration
change that will not persist after a reboot.
WARNING
A warning indicates potential data loss, as may happen when tuning hardware for
maximum performance.
2. Additional Reading
The documentation for Certificate System includes the following guides:
• Certificate System Deployment Guide1 describes basic PKI concepts and gives an overview of the
planning process for setting up Certificate System.
This manual is intended for Certificate System administrators.
• Certificate System Installation Guide2 covers the installation process for all Certificate System
subsystems.
This manual is intended for Certificate System administrators.
• Certificate System Administrator's Guide3 explains all administrative functions for the Certificate
System. Administrators maintain the subsystems themselves, so this manual details backend
configuration for certificate profiles, publishing, and issuing certificates and CRLs. It also covers
managing subsystem settings like port numbers, users, and subsystem certificates.
This manual is intended for Certificate System administrators.
• Certificate System Agent's Guide4 describes how agents — users responsible for processing
certificate requests and managing other aspects of certificate management — can use the
Certificate System subsystems web services pages to process certificate requests, key recovery,
OCSP requests and CRLs, and other functions.
viii
Page 9

Giving Feedback
This manual is intended for Certificate System agents.
• Managing Smart Cards with the Enterprise Security Client5 explains how to install, configure,
and use the Enterprise Security Client, the user client application for managing smart cards, user
certificates, and user keys.
This manual is intended for Certificate System administrators, agents, privileged users (such as
security officers), and regular end users.
• Using End User Services6 is a quick overview of the end-user services in Certificate System, a
simple way for users to learn how to access Certificate System services.
This manual is intended for regular end users.
• Certificate System Command-Line Tools Guide7 covers the command-line scripts supplied with Red
Hat Certificate System.
This manual is intended for Certificate System administrators.
• Certificate System Migration Guide8 covers version-specific procedures for migrating from older
versions of Certificate System to Red Hat Certificate System 8.0.
This manual is intended for Certificate System administrators.
• Release Notes9 contains important information on new features, fixed bugs, known issues and
workarounds, and other important deployment information for Red Hat Certificate System 8.0.
All of the latest information about Red Hat Certificate System and both current and archived
documentation is available at http://www.redhat.com/docs/manuals/cert-system/.
3. Giving Feedback
If there is any error in this Installation Guide or there is any way to improve the documentation, please
let us know. Bugs can be filed against the documentation for Red Hat Certificate System through
Bugzilla, http://bugzilla.redhat.com/bugzilla. Make the bug report as specific as possible, so we can be
more effective in correcting any issues:
• Select the Red Hat Certificate System product.
• Set the component to Doc - quick install guide.
• Set the version number to 8.0.
• For errors, give the page number (for the PDF) or URL (for the HTML), and give a succinct
description of the problem, such as incorrect procedure or typo.
For enhancements, put in what information needs to be added and why.
• Give a clear title for the bug. For example, "Incorrect command example for setup
script options" is better than "Bad example".
We appreciate receiving any feedback — requests for new sections, corrections, improvements,
enhancements, even new ways of delivering the documentation or new styles of docs. You are
welcome to contact Red Hat Content Services directly at docs@redhat.com.
ix
Page 10

About This Guide
4. Document History
Revision
8.0.10
Adding information on new end-entities client authentication port for the CA, related to the MitM
resolution in Errata RHBA-2010:0169.
Revision 8.0.9 February 18, 2009 Ella Deon Lackey dlackey@redhat.com
Changing LunaSA setup, per Bugzilla 537529.
Correcting the cs_port definition, per Bugzilla 533303.
Revision 8.0.8 December 21, 2009 Ella Deon Lackey dlackey@redhat.com
Updating platform support to include 64-bit Windows platforms, per Errata RHBA-2009:1687.
Revision 8.0.7 November 25, 2009 Ella Deon Lackey
Updating the pkisilent documentation and expanding the CA configuration section to add ability to
specify the CA siging algorithm at installation, per Errata RHBA-2009:1602.
Revision 8.0.6 November 12, 2009 Ella Deon Lackey
Updating the Certicom ECC configuration per comment #3 in Bugzilla 507428.
Correcting the 'rpm -qi' example in checking prerequisites, per QE feedback.
Adding note about (no) 64-bit support for ESC.
Revision 8.0.5 November 3, 2009 Ella Deon Lackey
Adding information on setting the NSS_USE_DECODED_CKA_EC_POINT environment variable
for the console and clarifying the security database argument in the modutil step for configuring the
Certicom ECC module.
Revision 8.0.4 August 28, 2009 Ella Deon Lackey
Removing the draft watermarks.
Tech reviews for chapter 2 (prerequisites) and chapter 9 (basic usage), per Bugzilla #510578 and
#510587.
Revision 8.0.3 August 11, 2009 Ella Deon Lackey
March 25, 2010 Ella Deon Lackey dlackey@redhat.com
Tech reviews for chapter 8, per Bugzilla #510586.
Adding extra bullet point on using unique certificate nicknames for HSMs, related to Bugzilla
#510987.
Revision 8.0.2 August 3, 2009 Ella Deon Lackey
Tech reviews for chapter 4, per Bugzilla #510580.
Revision 8.0.1 July 26, 2009 Ella Deon Lackey
Tech reviews for chapters 1, 3, 5, 6, and 7, per Bugzilla #510577, #510579, #510581, #510582,
#510585.
Adding a section for configuring netHSM to work with SELinux, per Bugzilla #513312, with cross
references in the instance configuration sections.
Revision 8.0.0 July 22, 2009 Ella Deon Lackey
Initial draft for Certificate System 8.0 Installation Guide.
x
Page 11

Chapter 1.
Overview of Certificate System
Subsystems
Red Hat Certificate System is a highly configurable set of components which create and manage
certificates and keys at every point of the certificate lifecycle. Certificate System is based on open
standards so that it effectively creates a scalable, customizable, and robust public-key infrastructure
(PKI).
Certificate System has subsystems which discretely handle different PKI management functions.
These subsystems interact in flexibly established ways to manage certificates and to manage tokens.
1.1. Subsystems for Managing Certificates
Up to four Certificate System subsystems work together to manage certificates:
• Certificate Manager, a certificate authority (CA) which issues, renews, and revokes certificates and
publishes certificate revocation lists (CRLs)
• Data Recovery Manager (DRM), which archives and recovers keys
• Online Certificate Status Manager (OCSP), which processes requests for certificates' revocation
status
• Registration Authority (RA), which validates and approves certificate requests locally and then
forwards approval to the CA to issue the certificates
1
Page 12
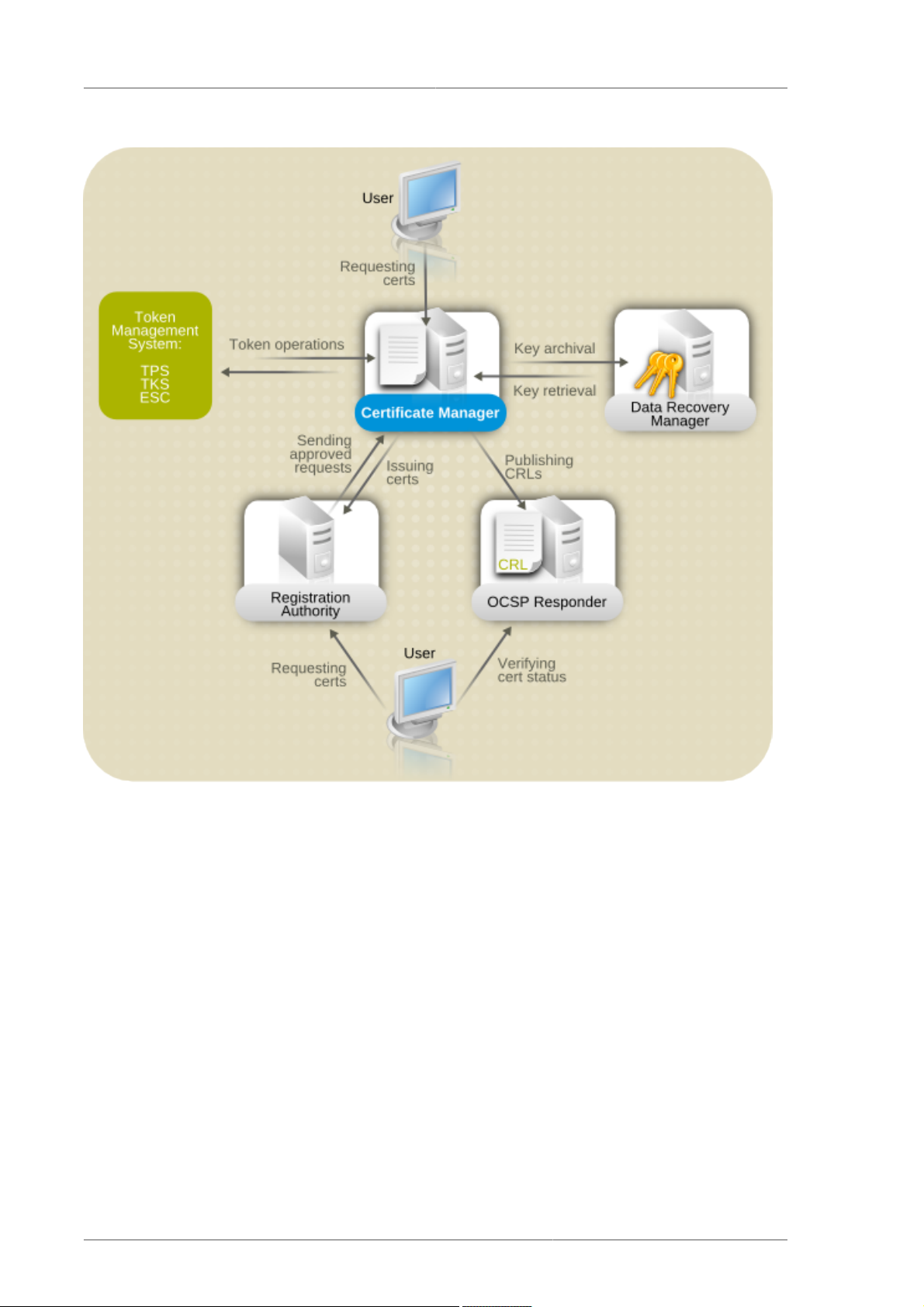
Chapter 1. Overview of Certificate System Subsystems
The core of the Certificate System is the Certificate Manager. This is the only required subsystem and
handles the actual certificate management tasks. The other subsystems can be added for additional
functionality (the DRM) or to move the load for some common operations off of the CA, such as using
an OCSP for status requests and an RA to process certificate requests.
The CA, RA, DRM, and OCSP are the subsystems used to manage certificates, keys, and CRLs,
through every step of the cycle of a certificate:
1. Generating a certificate request (CA or RA)
2. Submitting the request to a CA (CA or RA)
3. Generating key pairs (CA)
4. Storing the key pairs (DRM)
5. Issuing the certificate (CA)
6. Recovering the keys if the certificate is lost (DRM)
2
Page 13

Certificate Manager
7. Revoking the certificate (CA)
8. Checking whether the certificate is revoked or active when an entity tries to use the certificate for
authentication (OCSP)
All of the subsystems (CA, RA, DRM, and OCSP, as well as the token subsystems) are organized
together in security domains. Security domains define communication between subsystems, and this
makes the Certificate System very efficient. For example, if a user needs to archive keys, the request
can be processed by the first available DRM in the domain, automatically. The available DRMs in the
domain are automatically updated every time a new DRM is configured.
1.1.1. Certificate Manager
The Certificate Manager subsystem is a certificate authority. It issues, renews, revokes, and publishes
a wide variety of certificates: for servers, for users, for routers, for other subsystems, and for file or
object signing. The Certificate Manager also compiles and publishes CRLs.
Certificate Managers can be structured in series (hierarchy), so that one Certificate Manager sets
policies and issues signing certificates to a subordinate CA. The highest Certificate Manager in the
chain is a root CA.
A special kind of certificate is used by CAs to sign certificates they issue, sort of like a stamp or seal.
This is called a CA signing certificate. A subordinate CA is issued a CA signing certificate by a CA
higher in the hierarchy, and the parameters of the CA signing certificate are set by the superior CA. A
CA which issues its own signing certificate has a self-signed certificate. There are benefits to having a
self-signed CA certificate for your root CA, as well as some benefits to having the certificate signed by
a third-party CA.
Additionally, a Certificate Manager is always the subsystem which works as the registry for the security
domain. The very first Certificate Manager configured must create a security domain, but every
Certificate Manager configured after has the option of joining an existing security domain rather than
creating a new one. The configuration of your PKI deployment determines whether you need multiple
security domains; for more information, see the Red Hat Certificate System Deployment Guide.
1.1.2. Registration Authority
The Registration Authority subsystem handles certain certificate issuing tasks locally, such as
generating and submitting certificate requests. This effectively makes the RA a load-balancer for the
CA; a local RA can receive and verify the legitimacy of a certificate request (authenticate it) and then
forward valid requests to the CA to issue the certificate. Certificates can also be retrieved through the
RA and the status of the request can be checked through the RA, both of which lower demand on the
CA.
The RA is normally set up outside of the firewall, and the CA is set up behind the firewall so that
requests can be submitted to Certificate System externally, while the CA is protected.
The RA accepts requests for a smaller number of certificate types than the CA, including user, server,
and router certificates.
1.1.3. Data Recovery Manager
The Data Recovery Manager (DRM) is a key recovery authority, which means it works with the
Certificate Manager when a certificate is issued and stores private encryption keys. Those private keys
can be restored (in a PKCS #12 file) if a certificate is lost.
3
Page 14

Chapter 1. Overview of Certificate System Subsystems
NOTE
The DRM only archives encryption keys, not signing keys, because that compromises
the non-repudiation properties of signing keys. Non-repudiation means that a user cannot
deny having performed some action, such as sending an encrypted email, because they
are the only possessor of that key.
1.1.4. Online Certificate Status Manager
The Online Certificate Status Manager is an OCSP service, external to the Certificate Manager.
Although the Certificate Manager is configured initially with an internal OCSP service, an external
OCSP responder allows the OCSP subsystem to be outside the firewall and accessible externally,
while keeping the Certificate Manager behind the firewall. Like the RA, the OCSP acts as a loadbalancer for requests to the Certificate Manager.
The Online Certificate Status Manager verifies the status of a certificate by checking a certificate
revocation list, published by the Certificate Manager, to see if the specified certificate has been
revoked. More than one Certificate Manager can publish CRLs to a single OCSP.
1.2. Subsystems for Managing Tokens
Two subsystems are required to manage tokens:
• Token Processing System (TPS), which accepts operations from a token and forwards them to the
CA (for processing certificate requests, renewal, issuing, and revocation) and to the DRM (to archive
or restore keys)
• Token Key Service (TKS), which generates master keys and symmetric keys for the TPS to use
when communicating with other subsystems
A third application, the Enterprise Security Client, is the interface between the user and the TPS.
4
Page 15
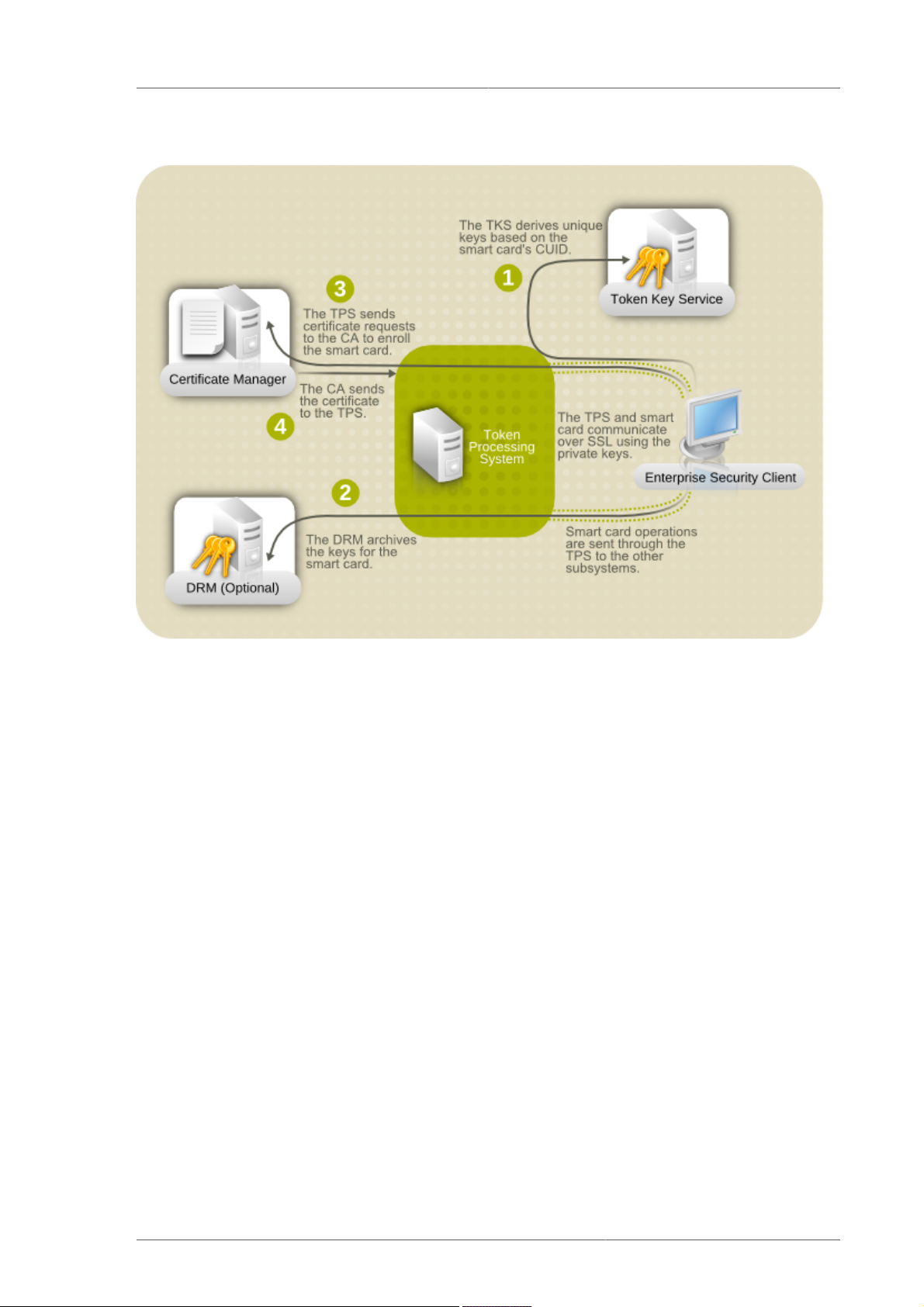
Token Processing System
1.2.1. Token Processing System
The Token Processing System (TPS) is the conduit between the user-centered Enterprise Security
Client, which interacts with the tokens, and the Certificate System backend subsystems, such as the
Certificate Manager. The TPS is required in order to manage smart cards.
The TPS communicates with the CA and DRM for processing token operations. The TPS also
communicates with the TKS to derive token-specific secret keys.
1.2.2. Token Key Service
The Token Key Service (TKS) uses a master key to derive specific, separate keys for every smart
card. The TPS uses these secret keys to communicate with each smart card securely, since all
communication between the TPS and the smart card is encrypted.
The only Certificate System subsystem which the TKS interacts with is the TPS.
1.2.3. Enterprise Security Client
The Enterprise Security Client is not a subsystem since it does not perform any operations with
certificates, keys, or tokens. The Enterprise Security Client, as the name implies, is a user interface
which allows people to manage certificates on smart cards very easily. The Enterprise Security Client
sends all token operations, such as certificate requests, to the TPS, which then sends them to the CA.
5
Page 16
Chapter 1. Overview of Certificate System Subsystems
1.3. Planning the Installation
Before beginning to install and configure the Certificate System subsystems, determine what the
organization of the PKI is.
Q: What types of subsystems do you need to install?
A: This depends on the kind of functionality you need and the load you expect to have. There
are several different kinds of subsystems for managing certificates (Section 1.1, “Subsystems
for Managing Certificates”) and for managing tokens (Section 1.2, “Subsystems for Managing
Tokens”).
Q: How many subsystems do you need to install?
A: This depends very much on the expected load and also on geographical or departmental
divisions. Subsystems can be cloned, meaning they essentially are clustered, operating as a
single unit, which is good for load balancing and high availability. Additionally, security domains
create trusted relationships between subsystems, allowing them to work together to find
available subsystems to respond to immediate needs. Multiple security domains can be used in
a single PKI, with multiple instances of any kind of subsystem.
Q: Will the subsystem certificates and keys be stored on the internal software token in
Certificate System or on an external hardware token?
A: Certificate System supports two hardware security modules (HSM): nCipher netHSM 2000 and
Safenet LunaSA. Using a hardware token can require additional setup and configuration before
installing the subsystems, but it also adds another layer of security.
Q: What machines should the subsystem be installed on?
A: This depends on the network design. The RA and OCSP subsystems are specifically designed
to operate outside a firewall for user convenience, while the CA, DRM, and TPS should all be
secured behind a firewall.
Q: To what security domain should a subsystem instance be added?
A: Because the subsystems within a security domain have trusted relationships with each other, it is
important what domain a subsystem joins. Security domains can have different certificate issuing
policies, different kinds of subsystems within them, or a different Directory Server database. Map
out where (both on the physical machine and in relation to each other) each subsystem belongs,
and assign it to the security domain accordingly.
Q: Should a subsystem be cloned?
A: Cloned subsystems work together, essentially as a single instance. This can be good for high
demand systems, failover, or load balancing, but it can become difficult to maintain. For example,
cloned CAs have serial number ranges for the certificates they issue, and a clone could hit the
end of its range.
Q: Should the Certificate Manager be a self-signed root CA or a subordinate CA?
6
Page 17

Planning the Installation
A: A Certificate Manager can be configured as either a root CA or a subordinate CA. The difference
between a root CA and a subordinate CA is who signs the CA signing certificate. A root CA
signs its own certificate. A subordinate CA has another CA (either internal or external) sign its
certificate.
A self-signing root CA issues and signs its own CA signing certificate. This allows the CA to set
its own configuration rules, like validity periods and the number of allowed subordinate CAs.
A subordinate CA has its certificates issued by a public CA or another Certificate System root
CA. This CA is subordinate to the other CA's rules about its certificate settings and how the
certificate can be used, such as the kinds of certificates that it can issue, the extensions that it
is allowed to include in certificates, and the levels of subordinate CAs the subordinate CA can
create.
One option is to have the Certificate manager subordinate to a public CA. This can be very
restrictive, since it introduces the restrictions that public CAs place on the kinds of certificates
the subordinate CA can issue and the nature of the certificate chain. On the other hand, one
benefit of chaining to a public CA is that the third party is responsible for submitting the root CA
certificate to a web browser or other client software, which is a major advantage for certificates
that are accessed by different companies with browsers that cannot be controlled by the
administrator.
The other option is make the CA subordinate to a Certificate System CA. Setting up a Certificate
System CA as the root CA means that the Certificate System administrator has control over
all subordinate CAs by setting policies that control the contents of the CA signing certificates
issued.
It is easiest to make the first CA installed a self-signed root, so that it is not necessary to apply
to a third party and wait for the certificate to be issued. Make sure that you determine how many
root CAs to have and where both root and subordinate CAs will be located.
7
Page 18

8
Page 19

Chapter 2.
Prerequisites Before Installing
Certificate System
Before installing the Red Hat Certificate System subsystems, check out the requirements and
dependencies for the specific platform, as well as looking at the installed packages.
2.1. Supported Platforms, Hardware, and Programs
2.1.1. Supported Platforms
The Certificate System subsystems (CA, RA, DRM, OCSP, TKS, and TPS) are supported on the
following platforms:
• Red Hat Enterprise Linux 5.3 (x86, 32-bit)
• Red Hat Enterprise Linux 5.3 (x86_64, 64-bit)
The Enterprise Security Client, which manages smart cards for end users, is supported on the
following platforms:
• Red Hat Enterprise Linux 5.3 (x86, 32-bit)
• Red Hat Enterprise Linux 5.3 (x86_64, 64-bit)
• Microsoft Windows Vista 32-bit
• Microsoft Windows Vista 64-bit
• Microsoft Windows XP 32-bit
• Microsoft Windows XP 64-bit
2.1.2. Supported Web Browsers
The services pages for the subsystems require a web browser that supports SSL. It is strongly
recommended that users such as agents or administrators use Mozilla Firefox to access the agent
services pages. Regular users should use Mozilla Firefox or Microsoft Internet Explorer.
NOTE
The only browser that is fully-supported for the HTML-based instance configuration wizard
is Mozilla Firefox.
Platform Agent Services End User Pages
Red Hat Enterprise Linux Firefox 3.x Firefox 3.x
Windows Vista Firefox 2.x Firefox 2.x
Internet Explorer 7 and higher
Windows XP Firefox 2.x Firefox 2.x
9
Page 20

Chapter 2. Prerequisites Before Installing Certificate System
Platform Agent Services End User Pages
Internet Explorer 6 and higher
Mac OS 10.x Agent services are not
supported for Mac
Table 2.1. Supported Web Browsers by Platform
Firefox 2.x
2.1.3. Supported Smart Cards
The Enterprise Security Client supports Global Platform 2.01-compliant smart cards and JavaCard 2.1
or higher.
The Certificate System subsystems have been tested using the following tokens:
• Gemalto TOP IM FIPS CY2 64K token, both as a smart card and GemPCKey USB form factor key
• Gemalto Cyberflex e-gate 32K token
• Safenet 330J Java smart card
Smart card testing was conducted using the SCM SCR331 CCID reader.
The only card manager applet supported with Certificate System is the CoolKey applet which ships
with Red Hat Enterprise Linux 5.3.
2.1.4. Supported HSM
Red Hat Certificate System supports two hardware security modules (HSM), nCipher netHSM 2000
and Chrysalis-IT LunaSA.
HSM Firmware Appliance Software Client Software
Safenet Chrysalis-ITS
LunaSA
nCipher netHSM 2000 2.33.60 11.10
4.5.2 3.2.4 3.2.4
2.1.5. Supported Charactersets
Red Hat Certificate System fully supports UTF-8 characters in the CA end users forms for specific
fields. This means that end users can submit certificate requests with UTF-8 characters in those fields
and can search for and retrieve certificates and CRLs in the CA and retrieve keys in the DRM when
using those field values as the search parameters.
Four fields fully-support UTF-8 characters:
• Common name (used in the subject name of the certificate)
• Organizational unit (used in the subject name of the certificate)
• Requester name
• Additional notes (comments appended by the agent to the certificate)
10
Page 21

Required Programs, Dependencies, and Configuration
NOTE
This support does not include supporting internationalized domain names, like in email
addresses.
2.2. Required Programs, Dependencies, and Configuration
To install any Red Hat Certificate System subsystems on Red Hat Enterprise Linux, three programs
are required: OpenJDK, Apache or Tomcat (depending on the subsystem), and Red Hat Directory
Server. All other require packages should be present as part of the base Red Hat Enterprise Linux
operating system packages.
2.2.1. Java Development Kit (JDK)
Certificate System requires OpenJDK 1.6.0. On Red Hat Enterprise Linux systems, this must be
installed separately. The OpenJDK can be installed by using yum or by downloading the packages
directly from http://openjdk.java.net/install/. For example:
yum install java-1.6.0-openjdk
After installing the JDK, run /usr/sbin/alternatives as root to insure that the proper JDK is
available:
/usr/sbin/alternatives --config java
There are 3 programs which provide 'java'.
Selection Command
---------------------------------------------- 1 /usr/lib/jvm/jre-1.4.2-gcj/bin/java
2 /usr/lib/jvm/jre-1.6.0-openjdk/bin/java
*+ 3 /usr/lib/jvm/jre-1.6.0-sun.x86_64/bin/java
See http://kbase.redhat.com/faq/FAQ_54_4667.shtm for more information on using the JDK for Red
Hat Certificate System.
2.2.2. Apache
Apache 2.x must be installed in order to install the TPS subsystem. Check that the appropriate version
of Apache is installed.
yum info httpd
Installed Packages
Name : httpd
Arch : x86_64
Version: 2.2.3
Release: 22.el5_3.2
Size : 2.9 M
Repo : installed
...
Install Apache if it is not already available. For example:
11
Page 22
Chapter 2. Prerequisites Before Installing Certificate System
yum install httpd
2.2.3. Red Hat Directory Server
All subsystems require access to Red Hat Directory Server 8.1 on the local machine or a remote
machine. This Directory Server instance is used by the subsystems to store their system certificates
and user data.
The Directory Server used by the Certificate System subsystems can be installed on Red Hat
Enterprise Linux 5.3 32-bit, Red Hat Enterprise Linux 5.3 64-bit, or Solaris 9 Sparc 64-bit, regardless
of the system on which Red Hat Certificate System is installed.
Check that the Red Hat Directory Server is already installed. For example:
yum info redhat-ds
Installed Packages
Name : redhat-ds
Arch : x86_64
Version : 8.1.0
Release : 0.14el5dsrv
Size : 136M
Repo : installed
...
Install and configure Red Hat Directory Server 8.1, if a directory service is not already available. For
example:
yum install redhat-ds
setup-ds-admin.pl
Go through the configuration wizard; the default settings are fine for the Certificate System needs.
Installing Red Hat Directory Server is described in more detail in the Red Hat Directory Server
Installation Guide.
2.2.4. Additional Packages
The following package groups and packages must be installed on all Red Hat Enterprise Linux
systems:
• gnome-desktop (package group)
• compat-arch-support (package group)
• web-server (package group)
• kernel-smp (package)
• e2fsprogs (package)
• firefox (package)
To verify that the packages are installed, just run rpm -qi For example:
rpm -qi gnome-desktop
12
Page 23

Firewall Configuration and iptables
gnome-desktop-2.16.0-1.el5
On 64-bit Red Hat Enterprise Linux platforms, be certain that the 64-bit (x86_64) compat-libstdc
++ libraries are installed, and not only the 32-bit (i386) libraries. To confirm this, run the following as
root:
rpm -qi compat-libstdc++ --queryformat '%{NAME}-%{VERSION}-%{RELEASE}.%{ARCH}.rpm\n' | grep
x86_64
Numerous libraries should be displayed.
2.2.5. Firewall Configuration and iptables
Any firewalls must be configured to allow access to the Certificate System ports and to any other
applications, like Red Hat Directory Server, which are required for the operation of the subsystems.
Use caution when configuring the firewall, so that the system remains secure. The port numbers for
the default instances are listed in Section 9.5, “Default File and Directory Locations for Certificate
System”.
As part of configuring the firewalls, if iptables is enabled, then it must have configured policies to allow
communication over the appropriate Certificate System ports. Configuring iptables is described in the
Red Hat Enterprise Linux Deployment Guide, such as "Using iptables."1 Installing the subsystems will
fail unless iptables is turned on and properly configured.
2.2.6. SELinux Settings
SELinux policies for Certificate System subsystems are installed as a dependency for Certificate
System 8.0, in the pki-selinux package. The SELinux policies are automatically configured
whenever a new instance is created by the pkicreate command.
Red Hat recommends running Certificate System with SELinux in enforcing mode, to make the
most of the security policies.
If SELinux is set to enforcing, then any external modules or hardware which interact with the
subsystems must be configured with the proper SELinux settings to proceed with subsystem
installation:
• Third-party modules, such as for ECC or HSM, must have an SELinux policy configured for them, or
SELinux needs to be changed from enforcing mode to permissive mode to allow the module to
function. Otherwise, any subsystem operations which require the ECC module will fail.
Changing SELinux policies is covered in the Red Hat Enterprise Linux Deployment Guide, such as
chapter 46, "Customizing SELinux Policy2."
• SELinux policies must be set for any nCipher netHSM 2000 modules, as described in
Section 2.5.2.4, “Setting up SELinux on nCiper netHSM 2000”.
2.3. Packages Installed on Red Hat Enterprise Linux
Multiple packages are installed with the Certificate System, in addition to the core Certificate System
components.
1
http://www.redhat.com/docs/en-US/Red_Hat_Enterprise_Linux/5.2/html/Deployment_Guide/s1-fireall-ipt-act.html
13
Page 24

Chapter 2. Prerequisites Before Installing Certificate System
RPMs for Certificate System Subsystems and Components
osutil pki-kra pki-tks
pki-setup pki-tps
pki-ca pki-migrate
pki-common pki-native-tools symkey
pki-console pki-ocsp
pki-java-tools
RPMs for Tomcat Web Services
ant jakarta-commons-discovery jakarta-oro
avalon-framework jakarta-commons-el regexp
avalon-logkit jakarta-commons-fileupload tomcat5
axis jakarta-commons-httpclient tomcat5-common
bcel jakarta-commons-launcher tomcat5-jasper
classpathx-jaf jakarta-commons-logging tomcat5-server
classpathx-mail jakarta-commons-modeler velocity
eclipse-ecj jakarta-commons-pool werken.xpath
geronimo-specs jdom wsdl4j
xalan-j2
geronimo-specs-compat jakarta-commons-beanutils xerces-j2
jakarta-commons-collections ldapjdk xml-commons
jakarta-commons-daemon log4j xml-commons-apis
jakarta-commons-dbcp mx4j xml-commons-resolver
jakarta-commons-digester
RPMs for Apache Web Services
mod_perl perl-XML-NamespaceSupport
pcre-devel perl-XML-Parser
perl-XML-SAX perl-Parse-RecDescent
tcl perl-XML-Simple
tcl-devel
RPMs for LDAP Support
cyrus-sasl mozldap-devel mozldap-tools
RPMs for SQL Lite Support for the RA
perl-DBD-SQLite perl-DBI sqlite-devel
RPMs for NSS and NSPR
jss
14
Page 25
Required Information for Subsystem Configuration
RPMs for NSS and NSPR
nspr
nss
svrcore
2.4. Required Information for Subsystem Configuration
When the Certificate System subsystems are configured, some outside information must be available,
as listed in Table 2.2, “Required Information for Configuring Subsystems”.
Information Description
Login PIN There is a randomly-generated PIN in the
preop.pin parameter in the CS.cfg file in the
instance conf/ directory. This is used to log into
the configuration wizard.
Security domain information CAs can create a new security domain, which
requires a unique name and a username and
password for the CA agent who administers
the domain. All other subsystems must join an
existing security name. Have the username and
password of the CA agent who administers the
domain.
CA information If the subsystem is not a CA, then it is necessary
to select a CA from a drop-down menu or add
an external CA. If a Certificate System CA is
selected, then supply the CA agent username
and password.
Subsystem information (for TPS configuration) When installing a TPS, you must have already
configured the other subsystem and have their
bind information available:
The CA
The TKS (required)
The DRM (optional, for server-side key
generation)
When configuring the TPS, the TKS and DRM to
connect with the TPS are selected from a dropdown list of all subsystems within the security
domain.
Directory Server hostname and port number The Certificate System uses the user database
of the Directory Server to store its information,
and the hostname and port number of the LDAP
directory is required for the Certificate System to
access the database.
Directory Manager DN and password The Certificate System must be able to bind to
the user database, so a user ID and password
must be supplied to bind to the Directory Server.
This user is normally the Directory Manager. The
15
Page 26

Chapter 2. Prerequisites Before Installing Certificate System
Information Description
default Directory Manager DN is cn=Directory
Manager.
Certificate and key recovery files (for cloning) If the subsystem being configured is a clone of
another subsystem, then the backup files for the
master subsystem must be locally accessible.
Table 2.2. Required Information for Configuring Subsystems
2.5. Setting up Tokens for Storing Certificate System
Subsystem Keys and Certificates
A subsystem instance generates and stores its key information in a key store, called a token. A
subsystem instance can be configured for the keys to be generated and stored using the internal NSS
token or on a separate cryptographic device, a hardware token.
2.5.1. Types of Hardware Tokens
A token is a hardware or software device that performs cryptographic functions and stores public-key
certificates, cryptographic keys, and other data.
The Certificate System defines two types of tokens, internal and external, for storing key pairs and
certificates that belong to the Certificate System subsystems.
2.5.1.1. Internal Tokens
An internal (software) token is a pair of files, usually called the certificate database and key database,
that the Certificate System uses to generate and store its key pairs and certificates. The Certificate
System automatically generates these files in the filesystem of its host machine when first using the
internal token. These files were created during the Certificate System subsystem configuration if the
internal token was selected for key-pair generation.
In the Certificate System, the certificate database is named cert8.db; the key database is named
key3.db. These files are located in the instanceID/alias directory.
2.5.1.2. External Tokens
An external token refers to an external hardware device, such as a smart card or hardware security
module (HSM), that the Certificate System uses to generate and store its key pairs and certificates.
The Certificate System supports any hardware tokens that are compliant with PKCS #11.
PKCS #11 is a standard set of APIs and shared libraries which isolate an application from the details
of the cryptographic device. This enables the application to provide a unified interface for PKCS #11compliant cryptographic devices.
The PKCS #11 module implemented in the Certificate System supports cryptographic devices supplied
by many different manufacturers. This module allows the Certificate System to plug in shared libraries
supplied by manufacturers of external encryption devices and use them for generating and storing
keys and certificates for the Certificate System managers.
Consider using external tokens for generating and storing the key pairs and certificates used by
Certificate System. These devices are another security measure to safeguard private keys because
hardware tokens are sometimes considered more secure than software tokens.
16
Page 27

Using Hardware Security Modules with Subsystems
Before using external tokens, plan how the external token is going to be used with the subsystem:
• All system keys for a subsystem must be generated on the same token.
• The subsystem keys must be installed in an empty HSM slot. If the HSM slot has previously been
used to store other keys, then use the HSM vendor's utilities to delete the contents of the slot. The
Certificate System has to be able to create certificates and keys on the slot with default nicknames.
If not properly cleaned up, the names of these objects may collide with previous instances.
• A single HSM can be used to store certificates and keys for mulitple subsystem instances, which
may be installed on multiple hosts. When an HSM is used, any certificate nickname for a subsystem
must be unique for every subsystem instance managed on the HSM.
2.5.1.3. Hardware Cryptographic Accelerators
The Certificate System can use hardware cryptographic accelerators with external tokens. Many of the
accelerators provide the following security features:
• Fast SSL connections. Speed is important to accommodate a high number of simultaneous
enrollment or service requests.
• Hardware protection of private keys. These devices behave like smart cards by not allowing private
keys to be copied or removed from the hardware token. This is important as a precaution against
key theft from an active attack of an online Certificate Manager.
2.5.2. Using Hardware Security Modules with Subsystems
The Certificate System supports the nCipher netHSM hardware security module (HSM) by default.
Certificate System-supported HSMs are automatically added to the secmod.db database with
modutil during the pre-configuration stage of the installation, if the PKCS #11 library modules are in
the default installation paths.
During configuration, the Key Store panel displays the supported modules, along with the NSS
internal software PKCS #11 module. All supported modules that are detected show a status of
Found and is individually marked as either Logged in or Not logged in. If a token is found but not
logged in, it is possible to log in using the Login under Operations. If the administrator can log into
a token successfully, the password is stored in a configuration file. At the next start or restart of the
Certificate System instance, the passwords in the password store are used to attempt a login for each
corresponding token.
Administrators are allowed to select any of the tokens that are logged in as the default token, which is
used to generate system keys.
2.5.2.1. Adding or Managing the HSM Entry for a Subsystem
When an HSM is selected as the default token, the following parameters are set in instance's CS.cfg
file to configure the HSM:
#RHCS supported modules
preop.configModules.module0.commonName=NSS Internal PKCS #11 Module
preop.configModules.module0.imagePath=../img/mozilla.png
preop.configModules.module0.userFriendlyName=NSS Internal PKCS #11 Module
preop.configModules.module1.commonName=nfast
preop.configModules.module1.imagePath=../img/ncipher.png
17
Page 28

Chapter 2. Prerequisites Before Installing Certificate System
preop.configModules.module1.userFriendlyName=nCipher's nFast Token Hardware Module
preop.configModules.module2.commonName=lunasa
preop.configModules.module2.imagePath=../img/safenet.png
preop.configModules.module2.userFriendlyName=SafeNet's LunaSA Token Hardware Module
#selected token
preop.module.token=Internal Key Storage Token
In addition, the following parameter is set in the password.conf for the HSM password:
hardware-nethsm=caPassword
2.5.2.2. Using Chrysalis LunaSA HSM
To make sure that a LunaSA HSM works with Certificate System, edit the configuration files for the
HSM before configuring the subsystems:
1. Check that the LunaSA module has been properly installed:
modutil -dbdir /var/lib/subsystem_name/alias -list
Listing of PKCS #11 Modules
-----------------------------------------------------------
1. NSS Internal PKCS #11 Module
slots: 2 slots attached
status: loaded
slot: NSS Internal Cryptographic Services
token: NSS Generic Crypto Services
slot: NSS User Private Key and Certificate Services
token: NSS Certificate DB
2. lunasa
library name: /usr/lunasa/lib/libCryptoki2_64.so
slots: 1 slot attached
status: loaded
slot: LunaNet Slot
token: lunasa3-ca
If the LunaSA module isn't listed, then install the module manually:
a. Stop the subsystem.
service subsystem_name stop
b. Load the module.
modutil -dbdir /var/lib/subsystem_name/alias -nocertdb -add lunasa -libfile /usr/
lunasa/lib/libCryptoki2_64.so
c. Verify that the module has been loaded.
modutil -dbdir /var/lib/subsystem_name/alias -list
d. Start the subsystem.
18
Page 29

Using Hardware Security Modules with Subsystems
service subsystem_name start
2. Open the /etc/Chrystoki.conf configuration file.
3. Add this configuration parameter.
Misc { NetscapeCustomize=1023; }
4. If they are there, remove these two configuration lines for the applet version.
AppIdMajor=2;
AppIdMinor=4;
Then, after going through the subsystem configuration, but before restarting the server when
completing the configuration wizard, edit the subsystem configuration to recognize the token:
1. Stop the server.
service subsystem_name stop
2. Edit the instance's serverCertNick.conf file in the /var/lib/subsystem_name/conf
directory. Add the HSM token name to the serverCert parameter.
The original value only points to the server:
Server-Cert instanceID
The new value includes a reference to the LunaSA HSM:
lunasa3-ca:Server-Cert instanceID"
3. Start the server.
service subsystem_name start
2.5.2.3. Installing External Tokens and Unsupported HSM
To use HSMs which are not officially supported by the Certificate System, add the module to the
subsystem database manually. If the desired HSM does not appear in the Security Modules panel
during the subsystem configuration, check that the HSM is installed and activated correctly. Then run
modutil manually to add the module to the secmod.db database.
1. Install the cryptographic device, using the manufacturer's instructions. Be sure to name the token
something that will help identify it easily later.
2. Install the PKCS #11 module using the modutil command-line utility.
a. Open the alias directory for the subsystem which is being configured with the PKCS #11
module. For example:
19
Page 30
Chapter 2. Prerequisites Before Installing Certificate System
cd /var/lib/pki-ca/alias
b. The required security module database file, secmod.db, should be created by default when
the subsystem is created. If it does not exist, use the modutil utility to create secmod.db.
modutil -dbdir . -nocertdb -create
c. Use the modutil utility to set the library information.
modutil -dbdir . -nocertdb / -add module_name -libfile library_file
library_file specifies the path to the library file containing the PKCS #11 interface module and
module_name gives the name of the PKCS #11 module which was set when the drivers were
installed.
• For the LunaSA HSM:
modutil -dbdir . -nocertdb -add lunasa -libfile /usr/lunasa/lib/libCryptoki2.so
• For an nCipher HSM:
modutil -dbdir . -nocertdb -add nethsm -libfile /opt/nfast/toolkits/pkcs11/
libcknfast.so
2.5.2.4. Setting up SELinux on nCiper netHSM 2000
SELinux policies are created and configured automatically for all Certificate System instances, so
Certificate System can run with SELinux in enforcing or permissive modes.
If SELinux is in enforcing mode, than any hardware tokens to be used with the Certificate System
instances must also be configured to run with SELinux in enforcing mode, or the HSM will not be
available during subsystem installation.
IMPORTANT
SELinux must be configured for the HSM before installing any Certificate System
instances.
1. Install the SELinux packages for Certificate System.
yum install pki-selinux
2. Reset the context of files in /dev/nfast to match the newly-installed policy.
/sbin/restorecon -R /dev/nfast
3. Restart the netHSM software.
20
Page 31

Viewing Tokens
2.5.3. Viewing Tokens
To view a list of the tokens currently installed for a Certificate System instance, use the modutil
utility.
1. Open the instance alias directory. For example:
cd /var/lib/pki-ca/alias
2. Show the information about the installed PKCS #11 modules installed as well as information on
the corresponding tokens using the modutil tool.
modutil -dbdir . -nocertdb -list
2.5.4. Detecting Tokens
To see if a token can be detected by Certificate System, use the TokenInfo utility. This is a
Certificate System tool which is available after the Certificate System packages are installed.
TokenInfo
This utility will return all tokens which can be detected by the Certificate System, not only tokens which
are installed in the Certificate System.
21
Page 32

22
Page 33

Chapter 3.
Installation and Configuration
The Certificate System is comprised of subsystems which can be independently installed on different
servers, multiple instances installed on a single server, and other flexible configurations for availability,
scalability, and failover support. The procedures for downloading, installing, and configuring instances
of Certificate System subsystems are described in this chapter.
The Certificate System servers include six subsystems:
• Certificate Authority (CA)
• Registration Authority (RA)
• Data Recovery Manager (DRM), sometimes referred to as a Key Recovery Authority (KRA)
• Online Certificate Status Protocol (OCSP) Responder
• Token Key Service (TKS)
• Token Processing System (TPS)
The Certificate System client is the Enterprise Security Client. For information about the Enterprise
Security Client, see the Certificate System Enterprise Security Client Guide.
3.1. Overview of Installation
The individual subsystems for Red Hat Certificate System are installed and then configured
individually. The initial installation is done using package management tools such as RPM; the
subsystem setup is done through an HTML-based configuration wizard.
1. Install a Red Hat Directory Server. This can be on a different machine from the Certificate System,
which is the recommended scenario for most deployments.
2. Download the Certificate System packages from the Red Hat Network channel. Each subsystem
has its own packages, as well as dependencies and related packages. These are listed in
Section 2.3, “Packages Installed on Red Hat Enterprise Linux”.
3. Install the packages, as described in Section 3.2, “Installing the Certificate System Packages”.
By default, the installation process immediately launches pkicreate to create the default
instances as soon as the subsystem packages are installed. The default instances are configured
with the default settings listed in Section 9.5, “Default File and Directory Locations for Certificate
System”. It is also possible to prevent the pkicreate command from running so that you can
configure an instance with custom settings, which is described in Chapter 5, Creating Additional
Subsystem Instances.
4. Configure the Certificate System CA subsystem. At least one CA subsystem must be installed and
fully configured before any other type of subsystem can be configured.
See Section 3.3, “Configuring a CA” for instructions on setting up the Certificate Manager.
5. Configure the RA, OCSP, DRM, and TKS subsystems. Once the CA is installed, the other
subsystems, except for the TPS, can be installed and configured in any order.
23
Page 34

Chapter 3. Installation and Configuration
See Section 3.5, “Configuring a DRM, OCSP, or TKS” and Section 3.4, “Configuring an RA” for the
process on installing and configuring the OCSP, DRM, TKS, and RA subsystems.
6. Configure the TPS subsystem. The TPS requires having an existing TKS and DRM available when
it is configured, so this is the last subsystem to set up.
See Section 3.6, “Configuring a TPS” for the process on installing and configuring the TPS.
The order in which subsystems are configured is very important because of the basic relationships
which are established between subsystems at the time they are installed. For example, every
subsystem depends on a certificate authority; the TPS also depends on a TKS and (optionally) DRM.
Figure 3.1. Order of Subsystem Configuration
24
Page 35

Installing the Certificate System Packages
3.2. Installing the Certificate System Packages
There are two ways to obtain and install the subsystem packages. For all supported platforms, the
Certificate System packages can be downloaded as ISO images through the appropriate Red Hat
Network channel. These packages are then installed through a package utility, such as rpm.
Alternatively, if the appropriate network access is available, the subsystems and dependencies can be
downloaded and installed on Red Hat Enterprise Linux systems using the yum command.
Several packages are installed with the Certificate System packages for related applications and
dependencies, not only for the subsystems. These packages are listed in Section 2.3, “Packages
Installed on Red Hat Enterprise Linux”.
• Section 3.2.1, “Installing through yum”
• Section 3.2.2, “Installing from an ISO Image”
NOTE
When the first subsystem is installed on a machine, the installation process automatically
creates a new user (pkiuser) and group (pkiuser). All default Certificate System
instances run as this user and group.
3.2.1. Installing through yum
NOTE
pkicreate is launched by the installer to create the default instances, using default
settings. There is an environment variable, DONT_RUN_PKICREATE, which stops the
pkicreate script from running automatically after the subsystems are installed.
Setting DONT_RUN_PKICREATE allows the default instances to be installed in userdefined installation directories, instead of the default locations in /var/lib. It can be
preferable to install through the ISO image with this environment variable set to block
the pkicreate script for deployments where the default instances must be installed in
custom locations.
NOTE
To use an IPv6 hostname for configuration, set the hostname in the PKI_HOSTNAME
environment variable before installing the packages. This is described in Section 4.4,
“Enabling IPv6 for a Subsystem”.
To install the initial subsystems on Red Hat Enterprise Linux 5 (32-bit), run a command like the
following for each subsystem:
yum install pki-subsystem
25
Page 36

Chapter 3. Installation and Configuration
NOTE
yum is used only for the first subsystem instance; any additional subsystem instances are
added using pkicreate.
subsystem can be any of the Certificate System subsystems:
• ca for the Certificate Manager.
• ra for the Registration Authority.
• kra for the Data Recovery Manager.
• ocsp for the Online Certificate Status Protocol Responder.
• tks for the Token Key System.
• tps for the Token Processing System.
• console for the Java console.
Once the packages are installed, then the installer automatically launches the pkicreate script to
create the default subsystem instance automatically. A URL to access the new instance is printed
to the screen which gives the subsystem instances hostname, port, and a login PIN to access the
configuration wizard.
PKI instance creation Utility ...
PKI instance creation completed ...
Starting instance_name: [ OK ]
instance_name (pid 17990) is running ...
'instance_name' must still be CONFIGURED!
(see /var/log/instance_name-install.log)
Before proceeding with the configuration, make sure
the firewall settings of this machine permit proper
access to this subsystem.
Please start the configuration by accessing:
https://hostname.domainname:admin-port/subsystem_type/admin/console/config/login?pin=pin
After configuration, the server can be operated by the command:
/sbin/service instance_name start | stop | restart
To install the pkiconsole to administer the subsystems, run the following:
yum install pki-console
26
Page 37

Installing from an ISO Image
3.2.2. Installing from an ISO Image
Red Hat Certificate System 8.0 can also be downloaded from Red Hat Network as an ISO image. This
ISO image contains an RPMS/ directory which can be used as a local yum repository.
1. Open the Red Hat Certificate System 8.0 Red Hat Network channel and download the ISO
image.
2. Place that RPMS/ directory on a web server and then configure yum to use that location as a
repository.
3. Install Certificate System as described in Section 3.2.1, “Installing through yum”, including setting
any environment variables, HSMs, or IPv6 settings.
3.3. Configuring a CA
The CA is always the first subsystem to be configured; every other subsystem depends on the CA
for its configuration. The CA, along with setting up the CA hierarchy for the PKI, issues certificates
which every subsystem uses to function and sets up a security domain which establishes trusted
relationships between subsystems.
NOTE
If a CA has an ECC signing certificate, it can issue both RSA and ECC client certificates.
To enable ECC for the CA, load an ECC module first (described in Section 4.2, “Installing
a CA with ECC Enabled”) and then configure the CA.
Subsystem configuration is done by accessing a unique web-based configuration page for the
instance. The only supported web browser for subsystem configuration is Mozilla Firefox.
1. Install the subsystem packages. For example:
yum install pki-ca
Once the packages are installed, then the installer automatically launches the pkicreate script
to create the default subsystem instance automatically. A URL to access the new instance is
printed to the screen which gives the subsystem instances hostname, port, and a login PIN to
access the configuration wizard.
http://server.example.com:9180/ca/admin/console/config/login?pin=
2. Open the configuration wizard using the URL returned from the package installation.
Alternatively, log into the setup wizard through admin link on the services page and supply the
preop.pin value from the /var/lib/pki-ca/conf/CS.cfg file when prompted.
https://server.example.com:9444/ca/services
3. Create a new security domain.
27
Page 38

Chapter 3. Installation and Configuration
The default CA instance must create a new security domain. Subsequent CAs can create a new
domain or join an existing security domain, but it is recommended that each CA have its own
security domain.
4. Enter a name for the new instance.
28
Page 39

Configuring a CA
5. Set up the PKI hierarchy. Commonly, the first CA is a root, or self-signed, CA, meaning that it signs
its own CA signing certificate rather than submitting its certificates to a third-party CA for issuance.
Subsequent CAs can be subordinate CAs to that root. There are many other options, depending
on the PKI environment.
For a CA, there are two possible configuration options:
• Root CA. A root CA signs its own CA signing certificate and, therefore, can set its own certificate
issuance rules.
29
Page 40

Chapter 3. Installation and Configuration
• Subordinate CA. A subordinate CA receives its CA signing certificate from a root CA. The root
CA must be referenced here; it can be another Certificate System CA, but, for the default (i.e.,
first) CA instance, this will probably be an external root CA. The certificate requests generated in
this process must be submitted to the external CA and be approved before configuration can be
completed.
See the planning question Should the Certificate Manager be a self-signed root CA or a
subordinate CA?1.
6. Fill in the information for the LDAP server which will be used for the instance's internal database.
This requires connection information for the Directory Server instance, such as the hostname, port
number, bind DN (username), and password. This step also creates a database in the Directory
Server and a corresponding base directory entry (base DN) to use for the subsystem's entries.
The hostname can be the fully-qualified domain name or an IPv4 or IPv6 address, if IPv6 was
configured before the packages were installed.
NOTE
One thing that can derail subsystem configuration or function is having services that
are unable to connect with each other. If servers that need to communicate with each
other are on different servers or networks, when the firewalls and iptables must be
configured to give the required access.
30
Page 41

Configuring a CA
If the Red Hat Directory Server instances is on a different server or network than
the Certificate System subsystem, then make sure that the Certificate System host's
firewall allows access to whatever LDAP port was set in the previous configuration
panel.
Installation will not complete if iptables is not configured properly. To configure
iptables, see the Red Hat Enterprise Linux Deployment Guide, such as "Using
iptables."2 It is also possible to simply turn iptables off.
7. Select the token which will store the Certificate System certificates and keys; a list of detected
hardware tokens and databases is given.
IMPORTANT
Any hardware tokens used with the instance must be configured before configuring
the subsystem instance. If the HSM is not properly configured, it may not be listed in
the key stores panel or the instance may not function properly. HSM configuration is
described in Section 2.5.2, “Using Hardware Security Modules with Subsystems”.
To determine whether a token is detected by the Certificate System, use the TokenInfo tool, as
described in Section 2.5.4, “Detecting Tokens”.
The Certificate System automatically discovers Safenet's LunaSA and nCipher's netHSM
hardware security modules. The discovery process assumes that the client software installations
for these modules are local to the Certificate System subsystem and are in the following locations:
31
Page 42

Chapter 3. Installation and Configuration
• LunaSA: /usr/lunasa/lib/libCryptoki2.so
• nCipher: /opt/nfast/toolkits/pkcs11/libcknfast.so
8. Set the key size and the hashing algorithm to use. By default, the settings for the signing key are
applied to the keys for every certificate for the CA. To set different key types, sizes, or hashing
algorithms for each certificate, click the [Advanced] link to expand the form so each key pair is
listed.
The default RSA key size is 2048 and for ECC, 256.
NOTE
An ECC CA signing certificate can be used to sign both ECC and RSA certificates.
If you do not want to use the ECC client certificate that is generated at installation,
simply replace the client certificate after configuration, and keep the ECC CA signing
certificate.
An ECC module must be loaded for ECC certificates to be generated. Adding ECC support is
covered in Section 4.2, “Installing a CA with ECC Enabled”. Any ECC-enabled PKCS#11 module
must be loaded before beginning to configure the CA.
32
Page 43

Configuring a CA
The hashing algorithms that are available depend on whether RSA or ECC is selected as the key
type. For RSA, the available algorithms are as follows:
• SHA256withRSA (the default)
• SHA1withRSA
• SHA256withRSA
• SHA512withRSA
• MD5withRSA
• MD2withRSA
For ECC:
• SHA256withEC (the default)
• SHA1withEC
• SHA384withEC
• SHA512withEC
9. Optionally, change the subject names for the certificates.
NOTE
Certificate nicknames must be unique, and changing the default nicknames is one
way to ensure that.
33
Page 44

Chapter 3. Installation and Configuration
Having unique certificate nicknames is vital for using an HSM, since any nickname
conflicts (even for subsystems on different servers) will cause configuration to fail.
10. The next panels generate and show certificate requests, certificates, and key pairs.
If an external CA is used to issue the certificates, configuration cannot go forward until they are
received from the external CA. When they are issued, paste the certificates into this panel to
add them to the CA database, and then proceed with the installation. Click Apply to view the
certificates as they are imported.
11. If the subsystem will ever be cloned, or as a protection if keys or certificates are ever lost, back up
the keys and certificates when prompted. It is also possible to extract these keys later, as long as
they are not stored on an HSM.
NOTE
It is not possible to export keys and certificates stored on an HSM to a .p12 file. It is
also not necessary to extract keys from the HSM to clone a subsystem. The keys are
already stored on the HSM and accessible to any cloned instances.
34
Page 45

Configuring a CA
12. Provide the information for the new subsystem administrator.
13. Click Next through the remaining panels to import the agent certificate into the browser and
complete the configuration.
14. When the configuration is complete, restart the subsystem.
35
Page 46

Chapter 3. Installation and Configuration
service pki-ca restart
IMPORTANT
The new instance is not active until it is restarted, and weird behaviors can occur if
you try to use the instance without restarting it first.
3.4. Configuring an RA
Subsystem configuration is done by accessing a unique web-based configuration page for the
instance. The only supported web browser for subsystem configuration is Mozilla Firefox.
IMPORTANT
Before any RA can be set up, a Certificate System CA must be installed, configured, and
running. This subsystem depends on the CA to issue their certificates and to create a
security domain. If the security domain CA is not available, then the configuration process
fails.
1. Install the subsystem packages. For example:
yum install pki-ra
Once the packages are installed, then the installer automatically launches the pkicreate script
to create the default subsystem instance automatically. A URL to access the new instance is
printed to the screen which gives the subsystem instances hostname, port, and a login PIN to
access the configuration wizard.
https://server.example.com:12889//ra/admin/console/config/login?pin=kI7E1MByNIUcPJ6RKHmH
2. Open the configuration wizard using the URL returned by the package installation.
https://server.example.com:12889//ra/admin/console/config/login?pin=kI7E1MByNIUcPJ6RKHmH
Alternatively, log into the setup wizard through admin link on the services page and supply the
preop.pin value from the /var/lib/pki-ra/conf/CS.cfg file when prompted.
https://server.example.com:12889/services
3. Join an existing security domain by entering the CA information. This URL can be identified by
running service pki-ca status on the CA's host; the security domain URL is returned with
the other configuration settings. For example:
https://server.example.com:9445
When the CA is successfully contacted, then supply the admin username and password for the CA
so that it can be properly accessed.
36
Page 47

Configuring an RA
The hostname for the security domain CA can be the fully-qualified domain name or an IPv4 or
IPv6 address, if IPv6 was configured before the packages were installed.
4. Enter a name for the new instance.
37
Page 48

Chapter 3. Installation and Configuration
5. Select the CA which will issue, renew, and revoke certificates for certificates processed through
the RA. All of the CAs configured in the security domain are listed in a dropdown menu.
6. Click Next on the Internal Database panel; the SQLite database is created automatically.
NOTE
The RA uses a SQLite database to store its configuration and user data rather than an
LDAP database, as the other subsystems do.
7. Select the token which will store the Certificate System certificates and keys; a list of detected
hardware tokens and databases is given.
IMPORTANT
Any hardware tokens used with the instance must be configured before configuring
the subsystem instance. If the HSM is not properly configured, it may not be listed in
the key stores panel or the instance may not function properly. HSM configuration is
described in Section 2.5.2, “Using Hardware Security Modules with Subsystems”.
To determine whether a token is detected by the Certificate System, use the TokenInfo tool, as
described in Section 2.5.4, “Detecting Tokens”.
38
Page 49

Configuring an RA
The Certificate System automatically discovers Safenet's LunaSA and nCipher's netHSM
hardware security modules. The discovery process assumes that the client software installations
for these modules are local to the Certificate System subsystem and are in the following locations:
• LunaSA: /usr/lunasa/lib/libCryptoki2.so
• nCipher: /opt/nfast/toolkits/pkcs11/libcknfast.so
8. Set the key size. The default RSA key size is 2048.
39
Page 50

Chapter 3. Installation and Configuration
9. Optionally, change the subject names for the certificates.
40
Page 51

Configuring an RA
NOTE
Certificate nicknames must be unique, and changing the default nicknames is one
way to ensure that.
Having unique certificate nicknames is vital for using an HSM, since any nickname
conflicts (even for subsystems on different servers) will cause configuration to fail.
10. The next panels generate and show certificate requests, certificates, and key pairs.
41
Page 52

Chapter 3. Installation and Configuration
If an external CA is used to issue the certificates, configuration cannot go forward until they
are received from the CA. When they are issued, paste the certificates into this panel to add
them to the subsystem database, and then proceed with the installation. Click Apply to view the
certificates as they are imported.
11. Provide the information for the new subsystem administrator.
42
Page 53

Configuring a DRM, OCSP, or TKS
12. Click Next through the remaining panels to import the agent certificate into the browser and
complete the configuration.
13. When the configuration is complete, restart the subsystem.
service pki-ra restart
IMPORTANT
The new instance is not active until it is restarted, and weird behaviors can occur if
you try to use the instance without restarting it first.
3.5. Configuring a DRM, OCSP, or TKS
Subsystem configuration is done by accessing a unique web-based configuration page for the
instance. The only supported web browser for subsystem configuration is Mozilla Firefox.
IMPORTANT
Before any DRM, OCSP, or TKS subsystem can be set up, a Certificate System CA must
be installed, configured, and running. These subsystems depend on the CA to issue their
certificates and to create a security domain. If the security domain CA is not available,
then the configuration process fails.
1. Install the subsystem packages. For example, to install a DRM:
yum install pki-kra
43
Page 54

Chapter 3. Installation and Configuration
NOTE
A Data Recovery Manager (DRM) is also known as a Key Recovery Agent (KRA).
All command-line tools and many files for the DRM use the abbreviation kra for this
reason. In the documentation, the subsystem used to archive and recover keys is
called the DRM or KRA interchangeably.
Once the packages are installed, then the installer automatically launches the pkicreate script
to create the default subsystem instance automatically. A URL to access the new instance is
printed to the screen which gives the subsystem instances hostname, port, and a login PIN to
access the configuration wizard.
http://server.example.com:10180/kra/admin/console/config/login?pin=kI7E1MByNIUcPJ6RKHmH
2. Open the configuration wizard using the URL returned by the package installation.
http://server.example.com:10180/kra/admin/console/config/login?pin=kI7E1MByNIUcPJ6RKHmH
Alternatively, log into the setup wizard through admin link on the services page and supply the
preop.pin value from the /var/lib/subsystem_name/conf/CS.cfg file when prompted.
https://server.example.com:10444/kra/services
3. Join an existing security domain by entering the CA information. This URL can be identified by
running service pki-ca status on the CA's host; the security domain URL is returned with
the other configuration settings. For example:
https://server.example.com:9445
When the CA is successfully contacted, then supply the admin username and password for the CA
so that it can be properly accessed.
4. Enter a name for the new instance.
44
Page 55

Configuring a DRM, OCSP, or TKS
5. Select the CA which will perform the operations processed through the subsystem, such as key
archival.
6. Fill in the information for the LDAP server which will be used for the instance's internal database.
This requires connection information for the Directory Server instance, such as the hostname, port
number, bind DN (username), and password. This step also creates a database in the Directory
Server and a corresponding base directory entry (base DN) to use for the subsystem's entries.
45
Page 56

Chapter 3. Installation and Configuration
The hostname can be the fully-qualified domain name or an IPv4 or IPv6 address.
NOTE
One thing that can derail subsystem configuration or function is having services that
are unable to connect with each other. If servers that need to communicate with each
other are on different servers or networks, when the firewalls and iptables must be
configured to give the required access.
If the Red Hat Directory Server instances is on a different server or network than
the Certificate System subsystem, then make sure that the Certificate System host's
firewall allows access to whatever LDAP port was set in the previous configuration
panel.
Installation will not complete if iptables is not configured properly. To configure
iptables, see the Red Hat Enterprise Linux Deployment Guide, such as "Using
iptables."3 It is also possible to simply turn iptables off.
7. Select the token which will store the Certificate System certificates and keys; a list of detected
hardware tokens and databases is given.
46
Page 57

Configuring a DRM, OCSP, or TKS
IMPORTANT
Any hardware tokens used with the instance must be configured before configuring
the subsystem instance. If the HSM is not properly configured, it may not be listed in
the key stores panel or the instance may not function properly. HSM configuration is
described in Section 2.5.2, “Using Hardware Security Modules with Subsystems”.
To determine whether a token is detected by the Certificate System, use the TokenInfo tool, as
described in Section 2.5.4, “Detecting Tokens”.
The Certificate System automatically discovers Safenet's LunaSA and nCipher's netHSM
hardware security modules. The discovery process assumes that the client software installations
for these modules are local to the Certificate System subsystem and are in the following locations:
• LunaSA: /usr/lunasa/lib/libCryptoki2.so
• nCipher: /opt/nfast/toolkits/pkcs11/libcknfast.so
8. Set the key size. The default RSA key size is 2048.
47
Page 58

Chapter 3. Installation and Configuration
9. Optionally, change subject names to the listed certificates.
NOTE
Certificate nicknames must be unique, and changing the default nicknames is one
way to ensure that.
48
Page 59

Configuring a DRM, OCSP, or TKS
Having unique certificate nicknames is vital for using an HSM, since any nickname
conflicts (even for subsystems on different servers) will cause configuration to fail.
10. The next panels generate and show certificate requests, certificates, and key pairs.
If an external CA is used to issue the certificates, configuration cannot go forward until they
are received from the CA. When they are issued, paste the certificates into this panel to add
them to the subsystem database, and then proceed with the installation. Click Apply to view the
certificates as they are imported.
11. Provide the information for the new subsystem administrator.
49
Page 60

Chapter 3. Installation and Configuration
12. Click Next through the remaining panels to import the agent certificate into the browser and
complete the configuration.
13. When the configuration is complete, restart the subsystem.
service pki-kra restart
IMPORTANT
The new instance is not active until it is restarted, and weird behaviors can occur if
you try to use the instance without restarting it first.
3.6. Configuring a TPS
Subsystem configuration is done by accessing a unique web-based configuration page for the
instance. The only supported web browser for subsystem configuration is Mozilla Firefox.
IMPORTANT
Before the TPS can be set up, a Certificate System CA and TKS must be installed and
configured. If you want to enable server-side key generation, then the DRM must also
be installed and configured. The TPS configuration wizard automatically establishes
relationships between the CA, TKS, and DRM and the TPS, so specific CA, TKS, and
DRM instances must be available to the TPS.
1. Install the subsystem packages. For example:
yum install pki-tps
50
Page 61

Configuring a TPS
Once the packages are installed, then the installer automatically launches the pkicreate script
to create the default subsystem instance automatically. A URL to access the new instance is
printed to the screen which gives the subsystem instances hostname, port, and a login PIN to
access the configuration wizard.
2. Open the configuration wizard using the URL returned by the package installation. For example:
http://server.example.com:7888/tps/admin/console/config/login?pin=kI7E1MByNIUcPJ6RKHmH
Alternatively, log into the setup wizard through admin link on the services page and supply the
preop.pin value from the /var/lib/pki-tps/conf/CS.cfg file when prompted.
http://server.example.com:7888/tps/services
3. Join an existing security domain by entering the CA information. This URL can be identified by
running service pki-ca status on the CA's host; the security domain URL is returned with
the other configuration settings. For example:
https://server.example.com:9445
When the CA is successfully contacted, then supply the admin username and password for the CA
so that it can be properly accessed.
4. Enter a name for the new instance.
51
Page 62

Chapter 3. Installation and Configuration
5. Select the CA which will issue, renew, and revoke certificates for token operations requested
through the TPS subsystem.
6. Supply information about the TKS which will manage the TPS keys. Select the TKS from the dropdown menu of TKS subsystems within the security domain.
52
Page 63

Configuring a TPS
7. There is an option for server-side key generation for tokens enrolled through the TPS. If serverside key generation is selected, supply information about the DRM which will generate keys and
archive encryption keys. Key and certificate recovery is initiated automatically through the TPS,
which is a DRM agent. Select the DRM from the drop-down menu of DRM subsystems within the
security domain.
The hostname for the DRM can be the fully-qualified domain name or an IPv4 or IPv6 address.
8. Fill in the Directory Server authentication directory. This directory is used by the TPS to
authenticate users which access the Enterprise Security Client and as an additional database for
certificates and keys.
This Directory Server instance is not the same Directory Server instance used as the TPS's
internal database. This is a general user directory, which may be accessed by other applications
or users. The TPS's internal database is used exclusively by the TPS and is created on the fly as
the TPS is configured.
53
Page 64

Chapter 3. Installation and Configuration
The hostname of the LDAP server can be the fully-qualified domain name or an IPv4 or IPv6
address.
9. Fill in the information for the LDAP server which will be used for the instance's internal database.
This requires connection information for the Directory Server instance, such as the hostname, port
number, bind DN (username), and password. This step also creates a database in the Directory
Server and a corresponding base directory entry (base DN) to use for the subsystem's entries.
54
Page 65

Configuring a TPS
The hostname can be the fully-qualified domain name or an IPv4 or IPv6 address.
NOTE
One thing that can derail subsystem configuration or function is having services that
are unable to connect with each other. If servers that need to communicate with each
other are on different servers or networks, when the firewalls and iptables must be
configured to give the required access.
If the Red Hat Directory Server instances is on a different server or network than
the Certificate System subsystem, then make sure that the Certificate System host's
firewall allows access to whatever LDAP port was set in the previous configuration
panel.
Installation will not complete if iptables is not configured properly. To configure
iptables, see the Red Hat Enterprise Linux Deployment Guide, such as "Using
iptables."4 It is also possible to simply turn iptables off.
10. Select the token which will store the Certificate System certificates and keys; a list of detected
hardware tokens and databases is given.
55
Page 66

Chapter 3. Installation and Configuration
IMPORTANT
Any hardware tokens used with the instance must be configured before configuring
the subsystem instance. If the HSM is not properly configured, it may not be listed in
the key stores panel or the instance may not function properly. HSM configuration is
described in Section 2.5.2, “Using Hardware Security Modules with Subsystems”.
To determine whether a token is detected by the Certificate System, use the TokenInfo tool, as
described in Section 2.5.4, “Detecting Tokens”.
The Certificate System automatically discovers Safenet's LunaSA and nCipher's netHSM
hardware security modules. The discovery process assumes that the client software installations
for these modules are local to the Certificate System subsystem and are in the following locations:
• LunaSA: /usr/lunasa/lib/libCryptoki2.so
• nCipher: /opt/nfast/toolkits/pkcs11/libcknfast.so
11. Set the key size.
56
Page 67

Configuring a TPS
12. Optionally, change subject names to the listed certificates.
NOTE
Certificate nicknames must be unique, and changing the default nicknames is one
way to ensure that.
Having unique certificate nicknames is vital for using an HSM, since any nickname
conflicts (even for subsystems on different servers) will cause configuration to fail.
57
Page 68

Chapter 3. Installation and Configuration
13. The next panels generate and show certificate requests, certificates, and key pairs.
If an external CA is used to issue the certificates, configuration cannot go forward until they are
received from the CA. When they are issued, paste the certificates into this panel to add them to
the TPS database, and then proceed with the installation. Click Apply to view the certificates as
they are imported.
14. Provide the information for the new subsystem administrator.
58
Page 69

Configuring a TPS
15. Click Next through the remaining panels to import the agent certificate into the browser and
complete the configuration.
16. When the configuration is complete, restart the subsystem.
service pki-tps restart
IMPORTANT
The new instance is not active until it is restarted, and weird behaviors can occur if
you try to use the instance without restarting it first.
59
Page 70

60
Page 71

Chapter 4.
Additional Installation Options
The Certificate System default installation, and all subsequent instances created with pkicreate,
make certain assumptions about the instances being installed, such as the default signing algorithm to
use for CA signing certificates and whether to allow IPv6 addresses for hosts.
This chapter describes additional configuration options that impact the installation and configuration for
new instances, so many of these procedures occur before the instance is created.
4.1. Requesting Subsystem Certificates from an External
CA
Most of the time, it is easier and simpler to have a CA within your PKI be the root CA, since this affords
a lot of flexibility for defining the rules and settings of the PKI deployment. However, for public-facing
networks, this can be a difficult thing to implement, because web administrators have to find some
way to propagate and update CA certificate chains to their clients so that any site is trusted. For this
reason, people often use public CAs, hosted by companies like VeriSign or Thawte, to issue CA
signing certificates and make all of their CAs subordinate to the public CA. This is one of the planning
considerations covered in the Certificate System Deployment Guide.
All subsystem certificates can be submitted to an external CA when the subsystem is configured.
When the certificates are generated from a CA outside the Certificate System deployment (or from a
Certificate System CA in a different security domain), then the configuration process does not occur in
one sitting. The configuration process is on hold until the certificates can be retrieved. Aside from that
delay, the process is more or less the same as in Chapter 3, Installation and Configuration.
1. Install the subsystem packages, and open the configuration URL.
2. Join a security domain. For a CA, it is also possible to create a new security domain.
3. Set the subsystem information, like its name.
4. For a CA, set the CA to be a subordinate CA. This is required in order to submit CA subsystem
certificates to an external CA; making a root CA automatically generates self-signed certificates.
5. Set up the internal database.
6. Select the key store, and generate the key pairs.
7. Set the subsystem certificate names; you can set these to whatever you want, but make sure that
they conform to any requirements that the external CA sets for the subject names of certificates.
At the bottom of the screen is the list of CAs which are available to accept the submitted certificate
requests. Choose External CA from the drop-down menu.
61
Page 72

Chapter 4. Additional Installation Options
8. In the Requests and Certificates panel, the CA signing certificate is listed, with an action
required label. Once that certificate is generated, the other certificates for the CA will be
automatically generated.
For other subsystems, each subsystem certificate has an action required label and must be
submitted to the external CA.
62
Page 73

Requesting Subsystem Certificates from an External CA
9. Click the Step 1: Copy the certificate request link, and copy the certificate request to a file or the
clipboard.
10. Submit the request to the external CA. Leave the browser with the configuration wizard open as
you wait for the certificates to be generated, so that it is easier to pick up the process.
11. Click Step 2, and import the certificate chain for the issuing CA. This certificate chain must not
contain the leaf certificate (the certificate being requested).
12. After retrieving the issued certificates, click the Step 3: Paste in the base 64-encoded certificate
link, and paste in the new certificate (this should be only the new certificate, not a certificate
chain).
13. For the CA, this only has to be done for the signing certificate. For the other subsystems, repeat
steps 9, 10, and 12 for each certificate.
When all the certificates have been submitted, click Next to resume the configuration process.
14. Export the keys for the certificates, if the subsystem will be cloned.
15. Create the administrator user.
16. When the configuration is done, restart the subsystem.
63
Page 74

Chapter 4. Additional Installation Options
service subsystem_name restart
4.2. Installing a CA with ECC Enabled
Elliptic curve cryptography (ECC) is much more secure than the more common RSA-style encryption,
which allows it to use much shorter key lengths and makes it faster to generate certificates. CAs which
are ECC-enabled can issue both RSA and ECC certificates, using their ECC signing certificate.
Certificate System does not include a module natively to enable ECC, but it is possible to load and use
a third-party PKCS #11 module with ECC-enabled.
To use the ECC module, it must be loaded before the subsystem instance is configured.
IMPORTANT
Third-party ECC modules must have an SELinux policy configured for them, or SELinux
needs to be changed from enforcing mode to permissive mode to allow the module
to function. Otherwise, any subsystem operations which require the ECC module will fail.
4.2.1. Loading a Third-Party ECC Module
1. Copy the third-party module to a common directory, like /usr/lib for 32-bit systems or /usr/
lib64 for 64-bit systems.
2. Create a new CA instance by running pkicreate, but do not go through the configuration wizard.
3. Stop the CA.
service pki-ca stop
4. The CA runs as the pkiuser user. As root, create a home directory for pkiuser.
/usr/sbin/usermod --home /usr/share/pki/pkiuser pkiuser
cd /usr/share/pki
mkdir pkiuser
HOME=/usr/share/pki/pkiuser
export HOME
5. Install the third-party module in the CA's security databases so it is available for the configuration.
cd /var/lib/pki-ca/alias
modutil -dbdir . -nocertdb -add THIRD_PARTY_MODULE -libfile /usr/lib/libYourNewModule.so
This creates a directory called .THIRD_PARTY_MODULE in the new home directory created for
root (the new pkiuser home directory). For example, if the module's name is EccForPki, then
the directory is named .EccForPki/
6. Using modutil, set the password for the new ECC module token.
64
Page 75

Loading the Certicom ECC Module
modutil -dbdir . -nocertdb -changepw "THIRD_PARTY_MODULE_TOKEN"
7. Change the ownership of the new home directory from root to pkiuser.
cd /usr/share/pki
chown -R pkiuser:pkiuser pkiuser
8. Add the password for the ECC token to the CA's password file.
vim /etc/pki-ca/password.conf
hardware-THIRD_PARTY_MODULE_TOKEN=secret
The hardware- prefix is required.
9. Edit the CA configuration and add a line to require signature verification.
ca.requestVerify.token=THIRD_PARTY_MODULE_TOKEN
10. Start the CA.
service pki-ca start
11. Continue with the CA configuration, with two important configuration settings:
• In the Key Store panel, the ECC module should be listed as an available token. Select that
module for the key store.
• In the Key Pairs panel, ECC should be listed as an option to use to generate the keys used for
the CA's certificates. Select the ECC key type.
12. After completing the configuration for the CA, try to log into the CA console.
pkiconsole https://server.example.com:9445/ca
This fails, because the console is not yet configured to run with ECC enabled. However, this does
create the security databases for the console, so the ECC module can be loaded.
13. Load the ECC module into the console security databases.
cd ~/.redhat-idm-console/
modutil -dbdir . -nocertdb -add THIRD_PARTY_MODULE -libfile /usr/lib/libYourNewModule.so
Now, logging into the console succeeds.
4.2.2. Loading the Certicom ECC Module
Certicom's ECC module has a slightly different configuration process than the procedure for loading a
general ECC module.
65
Page 76

Chapter 4. Additional Installation Options
1. Copy the third-party libraries to a common directory, like /usr/lib for 32-bit systems or /usr/
lib64 for 64-bit systems.
There are two library files for the Certicom ECC modules, libsbcpgse.so and libsbgse2.so.
2. Cache the recent shared libraries.
ldconfig
3. Install the CA, but do not go through the configuration wizard.
4. Stop the CA.
service pki-ca stop
5. The CA runs as the pkiuser user. As root, create a home directory for pkiuser.
/usr/sbin/usermod --home /usr/share/pki/pkiuser pkiuser
cd /usr/share/pki
mkdir pkiuser
HOME=/usr/share/pki/pkiuser
export HOME
6. Open the subsystem's alias directory. For example:
cd /var/lib/pki-ca/alias
7. Install the third-party module in the CA's security databases so it is available for the configuration.
modutil -dbdir . -nocertdb -add certicom -libfile /usr/lib/libsbcpgse.so
This creates a .certicom directory in the new pkiuser home directory.
8. Certicom's ECC module includes an initpin file; copy this into the new pkiuser directory and give
it execute permissions. For example:
cp /tmp/initpin /usr/share/pki/pkiuser
chmod +x initpin
9. Run Certicom's initpin file from the /usr/share/pki/pkiuser directory. This first prompts
for the directory to use for the Certicom token databases; use the pkiuser home directory, /
usr/share/pki/pkiuser. This also prompts to set a password for the module, and then
proceed with configuring the module.
/usr/share/pki/pkiuser/initpin
Please enter the directory where the token databases exist or will
be created: /usr/share/pki/pkiuser
Enter PIN:
Confirm PIN:
Security Builder API for PKCS #11 Samples
66
Page 77

Loading the Certicom ECC Module
CryptoAes() success
CryptoArc4() success
CryptoDes() success
CryptoDh() success
CryptoDsa() success
CryptoEcdh() success
CryptoEcdsa() success
CryptoEcmqv() success
CryptoPkcs1Enc() success
CryptoPkcs1Sig() success
CryptoRsaEnc() success
CryptoRsaSig() success
CryptoSha1() success
Token() samples starting
Slot info for Slot 0
Desc: FIPS Generic Crypto Services V1.0.1d
manufacturerID: Certicom Corp.
flags: 0x1
CKF_TOKEN_PRESENT
hardwareVersion: 1.0
...
10. Edit the pkiuser's home directory so that every file is owned by pkiuser.
cd /usr/share/pki; chown -R pkiuser:pkiuser pkiuser
11. List the Certicom ECC module to make sure it has been properly loaded. The module is in security
databases in the subsystem's alias directory. For example:
modutil -dbdir /var/lib/pki-ca/alias -list certicom
12. Add the password for the ECC token to the subsystem's password file. Escape any spaces or
special characters in the name. For example:
vim /etc/pki-ca/password.conf
hardware-Certicom\ FIPS\ Cert/Key\ Services=secret
The hardware- prefix is required.
13. Edit the CA configuration and add a line to require signature verification. In this file, spaces and
special characters do not need to be escaped. For example:
ca.requestVerify.token=Certicom FIPS Cert/Key Services
14. Edit file dtomcat5-instance file for the subsystem in the /usr/bin directory, and add a line to
use the ECC module.
umask 00002
NSS_USE_DECODED_CKA_EC_POINT=1
export NSS_USE_DECODED_CKA_EC_POINT
15. Start the CA.
67
Page 78

Chapter 4. Additional Installation Options
service pki-ca start
16. Continue with the CA configuration, with two important configuration settings:
• In the Key Store panel, the ECC module should be listed as an available token. Select that
module for the key store.
• In the Key Pairs panel, ECC should be listed as an option to use to generate the keys used for
the CA's certificates. Select the ECC key type.
17. After completing the configuration, try to log into the subsystem console.
pkiconsole https://server.example.com:9445/ca
This fails, because the console is not yet configure to run in ECC. However, this does create the
security databases for the console, so the ECC module can be loaded.
Load the ECC module into the console security databases.
cd ~/.redhat-idm-console/
modutil -dbdir . -nocertdb -add certicom -libfile /usr/lib/libsbcpgse.so
Now, logging into the console succeeds.
18. The web browser used to access administrative and agent services pages also needs to be
configured to support ECC.
a. Create a user for the browser profile, such as agent-pki.
b. Launch Firefox and create a profile for this user; this automatically creates the required
security databases and directory.
c. Set the root home directory to /home/agent-pki, and make sure the directory is owned by
root.
chown -R root:root /home/agent-pki
d. Copy the ECC module libraries and initpin file to the /home/agent-pki directory. All
these files should be owned by root.
e. Load the ECC module.
modutil -dbdir /home/agent-pki/.mozilla/profile.default -nocertdb -add certicom libfile /usr/lib/libsbcpgse.so
f. Run the initpin file. When prompted, enter the Certicom token database directory, /usr/
share/pki/pkiuser, and enter the PIN configured for those databases.
./initpin
g. Change the ownership of the new user's home directory from root to the user. For example:
68
Page 79

Changing the Hashing Algorithm Used for Subsystem Keys
chown -R agent-pki:agent-pki /home/agent-pki
h. In the terminal with the /home/agent-pki directory open, export the environment variable
that allows ECC support.
export NSS_USE_DECODED_CKA_EC_POINT=1
i. Open Firefox again. The Certicom module should be available and you should be able to log
into it successfully.
j. Then, import the agent certificate and root CA certificate or certificate chain into Firefox so that
the user profile can access the agent services pages.
19. The NSS_USE_DECODED_CKA_EC_POINT environment variable also needs to be set to access
the subsystem Java console with an ECC certificate. This can be set in the .bashrc file for the
user who uses the console. For example:
vim /home/jsmith/.bashrc
# User specific aliases and functions
NSS_USE_DECODED_CKA_EC_POINT=1
export NSS_USE_DECODED_CKA_EC_POINT
4.3. Changing the Hashing Algorithm Used for Subsystem
Keys
When a CA is installed, along with determining the key type and size, the hashing algorithm for the
key pair is set. However, for other subsystems, the hashing algorithm is not configurable, so they use
whatever the default is for the CA which issues their certificates.
Instead of using the CA's hashing algorithm, it is possible to edit the profiles used to generate the
subsystem certificates; then, the configuration wizard will use whatever hashing algorithm is in the
profile instead of the one used by the CA.
NOTE
This is true for subordinate CAs as well as other subsystems. While some of the
certificates for a sub CA are generated locally — and therefore can take a user-defined
hashing algorithm for their keys in the configuration wizard — other certificates for the sub
CA (like its signing certificate) are generated by another CA and default to that CA's key
hashing algorithm.
To assign the hashing algorithm to the certificate, add this line to the profile in the CA's profile
directory, such as /var/lib/instance_name/profiles/ca:
default.params.signingAlg=hashing_alg
69
Page 80

Chapter 4. Additional Installation Options
TIP
Editing certificate profiles is covered in the Administrator's Guide.
Each of the subsystem certificate profiles can be edited:
• caInternalAuthOCSPCert.cfg
• caInternalAuthTransportCert.cfg
• caInternalAuthAuditSigningCert.cfg
• caInternalAuthServerCert.cfg
• caInternalAuthDRMstorageCert.cfg
• caInternalAuthSubsystemCert.cfg
The hashing algorithms that are available depend on whether RSA or ECC is selected as the key type.
For RSA, the available algorithms are as follows:
• SHA256withRSA (the default)
• SHA1withRSA
• SHA256withRSA
• SHA512withRSA
• MD5withRSA
• MD2withRSA
For ECC:
• SHA256withEC (the default)
• SHA1withEC
• SHA384withEC
• SHA512withEC
4.4. Enabling IPv6 for a Subsystem
Certificate System automatically configures and manages connections between subsystems. Every
subsystem must interact with a CA as members of a security domain and to perform their PKI
operations.
For these connections, Certificate System subsystems can be recognized by their host's fullyqualified domain name or an IP address. By default, Certificate System resolves IPv4 addresses
and hostnames automatically, but Certificate System can also use IPv6 for their connections.
IPv6 is supported for all server connections: to other subsystems, to the administrative console
(pkiconsole), or through command-line scripts such as tpsclient.
70
Page 81

Configuring Separate RA Instances
op=var_set name=ca_host value=IPv6 address
If a host has both an IPv4 address and an IPv6 name, then an environment variable can be set before
the Certificate System packages are installed so that Certificate System setup scripts will recognize
the IPv6 name.
1. If the default (first) instances should use IPv6, set the environment variable to keep pkicreate
from running.
export DONT_RUN_PKICREATE=1
2. Install the Red Hat Certificate System packages.
3. Set the IPv4 and IPv6 addresses in the /etc/hosts file. For example:
vim /etc/hosts
192.0.0.0 server.example.com IPv4 address
3ffe:1234:2222:2000:202:55ff:fe67:f527 server6.example.com IPv6 address
4. Then, export the environment variable to use the IPv6 address for the server. For example:
export PKI_HOSTNAME=server6.example.com
5. Unset the DONT_RUN_PKICREATE variable so that the new instances can be created.
export DONT_RUN_PKICREATE=0
6. Run pkicreate to create the new instance. The values for the server hostname in the CS.cfg
file will be set to the IPv6 address.
4.5. Configuring Separate RA Instances
When an RA is installed or created, it is automatically added to a default Registration Managers Group
on the CA. This means that all RA managers belong to the same group, by default.
However, a particular site might require more than one RA instance, each having its own set of
RA agents. If the site policy disallows cross-management between the RA instances, then extra
configuration is needed to create separate RA groups.
1. Install and configure the first RA instance.
2. Add the new RA group to the Certificate Manager.
a. Start the Console. For example:
pkiconsole https://server.example.com:9445/ca
b. Click Users and Groups, and then click Groups.
c. Click Add to open the Edit Group Information dialog box.
d. Enter the group name and description, such as Registration Manager2 Agents.
71
Page 82

Chapter 4. Additional Installation Options
e. Click OK.
3. Add the new RA authentication instance to the CA:
a. Open the CA configuration directory, and edit the CS.cfg file
cd /etc/pki-ca
vi CS.cfg
b. Search for the string raCertAuth.
c. Copy those lines for the first RA instance, paste them, and edit them for the second RA
instance's information. For example:
auths.instance.raCertAuth.agentGroup=Registration Manager Agents
auths.instance.raCertAuth.plug-inName=AgentCertAuth
auths.instance.ra2CertAuth.agentGroup=Registration Manager2 Agents
auths.instance.ra2CertAuth.plug-inName=AgentCertAuth
4. Add the new RA user enrollment profile to the Certificate Manager's certificate profiles list to utilize
the new RA authentication instance.
a. Open the CA profiles directory.
cd /var/lib/pki-ca/profiles/ca
b. Copy the current RA profile to create the new profile. For example:
cp caDualRAuserCert.cfg caDualRA2userCert.cfg
c. Edit the new file to contain the second RA instance's information. Change raCertAuth to
ra2CertAuth.
5. Open the CA configuration directory, and edit the CS.cfg file.
cd /var/lib/pki-ca/conf
vi CS.cfg
a. Add caDualRA2userCert to the profiles list. For example:
profile.list=...[snip]...caRAserverCert,caRA2userCert
Make sure to use a comma to separate the entries.
b. Search for the lines for the caDualRAuserCert profile configuration, copy them, and edit
them for the second RA instance's information.
profile.caDualRAuserCert.class_id=caEnrollImpl
profile.caDualRAuserCert.config=/var/lib/pki-ca/profiles/ca/caDualRAuserCert.cfg
profile.caDualRA2userCert.class_id=caEnrollImpl
72
Page 83

Configuring Separate RA Instances
profile.caDualRA2userCert.config=/var/lib/pki-ca/profiles/ca/caDualRA2userCert.cfg
6. Add a new URI mapping to allow the new RA agent to be registered in the new RA group.
a. Open the CA web applications directory, and edit the web.xml file:
cd /var/lib/pki-ca/webapps/ca/WEB-INF
vi web.xml
b. At about line 288 in the web.xml file is the servlet setting for the first RA's user. Copy the
entire entry, including the opening and closing <servlet> tags, and edit the information to
match the second RA's user. For example:
<servlet>
<servlet-name> caRegisterRa2User </servlet-name>
<servlet-class> com.netscape.cms.servlet.csadmin.RegisterUser </servlet-class>
<init-param><param-name> GetClientCert </param-name>
<param-value> false </param-value> </init-param>
<init-param><param-name> authority </param-name>
<param-value> ca </param-value> </init-param>
<init-param><param-name> ID </param-name>
<param-value> caRegisterRaUser </param-value> </init-param>
<init-param><param-name> AuthMgr </param-name>
<param-value> TokenAuth </param-value> </init-param>
<init-param><param-name> GroupName </param-name>
<param-value> Registration Manager2 Agents </param-value> </initparam>
<init-param><param-name> AuthzMgr </param-name>
<param-value> BasicAclAuthz </param-value> </init-param>
<init-param><param-name> resourceID </param-name>
<param-value> certServer.ca.registerUser </param-value> </initparam>
</servlet>
c. At about line 2510 in the web.xml file is the servlet-mapping setting for the first RA's user
mapping. Copy the entire entry, including the opening and closing <servlet-mapping>
tags, and edit the information to match the second RA's user. For example:
<servlet-mapping>
<servlet-name> caRegisterRa2User </servlet-name>
<url-pattern> /admin/ca/registerRa2User </url-pattern>
</servlet-mapping>
7. Restart the CA. For example:
service pki-ca restartt
8. Create the new RA instance using the pkicreate.
pkicreate -pki_instance_root=/var/lib -subsystem_type=ra -pki_instance_name=pki-ra2 secure_port=12899 -unsecure_port=12898 -verbose -user=pkiuser -group=pkiuser
9. Open the configuration file for the new RA instance, and edit its parameters to reflect the second
RA instance information.
73
Page 84

Chapter 4. Additional Installation Options
cd /var/lib/pki-ra2/conf/
vi CS.cfg
10. Change the registerRaUser setting to registerRa2User.
conn.ca1.servlet.addagent=/ca/admin/ca/registerRa2User
11. Change the caDualRAuserCert setting to caDualRA2userCert.
request.renewal.approve_request.0.profileId=caDualRAuser2Cert
...
request.user.approve_request.0.profileId=caDualRA2userCert
12. Restart the new RA instance. For example:
# service pki-ra2 restart
13. A URL was generated at the end of the pkicreate command; go to that URL to configure the
second RA. For example:
http://server.example.com:12898/ra/admin/console/config/login?pin=bFyAk9nWPfgLZXffRBT9
14. When the new RA is completely configured, restart the instance.
# service pki-ra2 restart
74
Page 85

Chapter 5.
Creating Additional Subsystem
Instances
The number of subsystems that you have is flexible. There can be a single instance, there can be
multiple instances on the same machine, or there can be multiple instances on multiple servers.
Creating additional subsystem instances is similar to installing and configuring the default instances;
there is a script to run to create a basic installation and then an HTML-based configuration wizard to
complete the setup for the instance.
All additional CA, RA, DRM, OCSP, TKS, and TPS instances are installed by running a special tool,
pkicreate. After that, they are configured through the HTML-based administration page. For more
information on pkicreate, see the Certificate System Command-Line Tools Guide.
TIP
Existing instances can be duplicated (cloned) for load balancing for heavily trafficked
servers and for failover support. Cloning is described in Chapter 6, Cloning Subsystems.
5.1. About pkicreate
Certificate System subsystem instances are created and defined using a script called pkicreate.
This script is run automatically when the subsystem packages are first installed, and it creates the
default subsystem instances with their predefined settings.
The pkicreate script can be invoked after the packages are installed to create additional individual
subsystem instances, with user-defined settings like the configuration and log directories and port
numbers. After the instance is created, it is then configured through the HTML-based configuration
wizard or by using the pkisilent script.
The syntax for pkicreate is slightly different between subsystems because of the different port
configurations. The CA, OCSP, DRM, and TKS all have three SSL service ports and an unsecure
service port, while the RA and TPS have two SSL service ports and an unsecure service port.
pkicreate -pki_instance_root=/directory/path -subsystem_type=type -pkiinstance_name=instance_ID -secure_port=SSLport | {-agent_secure_port=SSLport ee_secure_port=SSLport -admin_secure_port=SSLport -ee_secure_client_auth_port=SSLport_CA_only}
-unsecure_port=port -tomcat_server_port=port [-user=user_name] [-group=group_name] [-
redirect_conf=conf_directory] [-redirect_logs=log_directory]
Example 5.1. Syntax for Creating a CA, OCSP, DRM, or TKS
pkicreate -pki_instance_root=/directory/path -subsystem_type=type -pkiinstance_name=instance_ID -secure_port=SSLport -non_clientauth_secure_port=SSLport unsecure_port=port [-user=user_name] [-group=group_name] [-redirect_conf=conf_directory] [redirect_logs=log_directory]
Example 5.2. Syntax for Creating an RA or TPS
75
Page 86

Chapter 5. Creating Additional Subsystem Instances
TIP
To get full usage examples and syntax for the pkicreate command, run pkicreate -help.
Parameter Description
pki_instance_root Gives the full path to the new instance
configuration directory.
subsystem_type Gives the type of subsystem being created.
pki_instance_name Gives the name of the new instance. Instance
names must be unique on a single machine,
but do not have to be unique within the security
domain (since instances are identified by
hostname and port, not instance name).
secure_port
agent_secure_port
ee_secure_port
ee_secure_client_auth_port
admin_secure_port
non_clientauth_secure_port
unsecure_port
1
Sets a single SSL port number for the
subsystem. This parameter is required if
port separation is not configured, meaning
that separate ports are not assigned for the
administrator, agent, and end-entities services.
1
Sets the SSL port for the agent web services. If
this is specified, then both ee_secure_port
and admin_secure_port must be
specified. For CAs only, an end-entities client
authentication port is also required with the
ee_secure_client_auth_port option.
1
Sets the SSL port for the end-entities
web services. If this is specified, then
both agent_secure_port and
admin_secure_port must be specified.
For CAs only, an end-entities client
authentication port is also required with the
ee_secure_client_auth_port option.
1
For CAs only. Sets the SSL port for the endentity client authentication. If this is specified,
then ee_secure_port, agent_secure_port,
and admin_secure_port must be specified.
1
Sets the SSL port number for the administrator
services, usually the pkiconsole. If this is
specified, then both agent_secure_port
and ee_secure_port must be specified.
For CAs only, an end-entities client
authentication port is also required with the
ee_secure_client_auth_port option.
1
Sets the end entities SSL port for RA and TPS
subsystems.
1
Sets the regular port number. If this is not set,
the number is randomly generated. Still, it is
76
Page 87

Running pkicreate for a Single SSL Port
Parameter Description
recommended that administrators set this value
to make sure there are no conflicts with SELinux
labels for other services.
tomcat_server_port
1
Sets the port number for the Tomcat web server
for OCSP, TKS, and DRM instances.
redirect_conf Sets the location for the configuration files for the
new instance.
redirect_logs Sets the location for the log files for the new
instance.
user Sets the user as which the Certificate System
instance will run. This option must be set.
group Sets the group as which the Certificate System
instance will run. This option must be set.
The ports selected for the new instance should not conflict with any other ports assigned on the host or SELinux. Check the /
etc/services file to see port assignments for the system. Then, run semanage port -l |grep port# to check SELinux; if
there is no output, then there is no conflict with SELinux assignments.
Table 5.1. pkicreate Parameters
For more information on the pkicreate tool options, see the Certificate System Command-Line Tools
Guide.
5.2. Running pkicreate for a Single SSL Port
1. Run the pkicreate command, specifying the type of subsystem being created, the configuration
directory, instance name, and port numbers. For example, this created a second DRM instance:
pkicreate -pki_instance_root=/var/lib/pki-drm2 -subsystem_type=kra -pki_instance_name=pkidrm2 -secure_port=10543 -unsecure_port=10180 -tomcat_server_port=1802 -verbose
2. When the instance is successfully created, the process returns a URL for the HTML configuration
page. For example:
http://server.example.com:10180/kra/admin/console/config/login?pin=nt2z2keqcqAZiBRBGLDf
TIP
The configuration URL is written to the end of the instance's installation file, /var/
log/subsystem_name-install.log. This log is also useful for debugging an
instance.
3. Open the new instance URL, and go through the configuration wizard as described in Chapter 3,
Installation and Configuration. Supply the security domain, CA, instance ID, internal LDAP
database, and agent information.
4. When the configuration is complete, restart the subsystem.
service instance_ID restart
77
Page 88

Chapter 5. Creating Additional Subsystem Instances
5.3. Running pkicreate with Port Separation
To create an instance with three separate ports for the different subsystem services, run pkicreate
with three options which specify the services ports: -admin_secure_port, -agent_secure_port,
and -ee_secure_port. For CAs only, there is an additional port for end-entity client authentication, ee_secure_client_auth_port.
Separated SSL ports is the default instance configuration because it is more secure than using a
single SSL port.
1. Run the pkicreate command. For example:
pkicreate -pki_instance_root=/var/lib/pki-ca2 -subsystem_type=ca -pki_instance_name=pkica2 -admin_secure_port=9545 -agent_secure_port-9544 -ee_secure_port=9543 ee_secure_client_auth_port=9546 -unsecure_port=9180 -tomcat_server_port=1802 -verbose
2. When the instance is successfully created, the process returns a URL for the HTML configuration
page. For example:
http://server.example.com:10180/kra/admin/console/config/login?pin=nt2z2keqcqAZiBRBGLDf
TIP
The configuration URL is written to the end of the instance's installation file, /var/
log/subsystem_name-install.log. This log is also useful for debugging an
instance.
3. Open the new instance URL, and go through the configuration wizard as described in Chapter 3,
Installation and Configuration. Supply the security domain, CA, instance ID, internal LDAP
database, and agent information.
4. When the configuration is complete, restart the subsystem.
service subsystem_name restart
For more information on the pkicreate tool options, see the Certificate System Command-Line Tools
Guide.
78
Page 89

Chapter 6.
Cloning Subsystems
When a new subsystem instance is first configured, the Red Hat Certificate System allows subsystems
to be cloned, or duplicated, for high availability of the Certificate System. The cloned instances run
on different machines to avoid a single point of failure and their databases are synchronized through
replication.
6.1. About Cloning
Planning for high availability reduces unplanned outages and other problems by making one or more
subsystem clones available. When a host machine goes down, the cloned subsystems can handle
requests and perform services, taking over from the master (original) subsystem seamlessly and
keeping uninterrupted service.
Using cloned subsystems also allows systems to be taken offline for repair, troubleshooting, or other
administrative tasks without interrupting the services of the overall PKI system.
NOTE
All of the subsystems except the TPS and RA can be cloned.
Cloning is one method of providing scalability to the PKI by assigning the same task, such as handling
certificate requests, to separate instances on different machines. The internal databases for the
master and its clones are replicated between each other, so the information about certificate requests
or archived keys on one subsystem is available on all the others.
Typically, master and cloned instances are installed on different machines, and those machines are
placed behind a load balancer. The load balancer accepts HTTP and HTTPS requests made to the
Certificate System subsystems and directs those requests appropriately between the master and
cloned instances. In the event that one machine fails, the load balancer transparently redirects all
requests to the machine that is still running until the other machine is brought back online.
79
Page 90

Chapter 6. Cloning Subsystems
Figure 6.1. Cloning Example
The load balancer in front of a Certificate System subsystem is what provides the actual failover
support in a high availability system. A load balancer can also provide the following advantages as
part of a Certificate System subsystem:
• DNS round-robin, a feature for managing network congestion that distributes load across several
different servers.
• Sticky SSL, which makes it possible for a user returning to the system to be routed the same host
used previously.
6.1.1. Cloning for CAs
Cloned instances have the exact same private keys as the master, so their certificates are identical.
For CAs, that means that the CA signing certificates are identical for the original master CA and its
cloned CAs. From the perspectives of clients, these look like a single CA.
Every CA, both cloned and master, can issue certificates and process revocation requests.
The main issue with managing cloned CAs is how to assign serial numbers to the certificates they
issue. Different CAs can have different levels of traffic, using serial numbers at different rates, and it is
imperative that no CA issue the certificates with the same serial number. These serial number ranges
are assigned and managed dynamically by using a shared, replicated entry that defines the ranges for
each CA and the next available range to reassign when one CA range runs low.
80
Page 91

Cloning for DRMs
Cloned CAs do have limits on what operations they can perform. Most important, cloned CAs cannot
generate or publish CRLs. Any CRL requests submitted to a cloned CA are immediately redirected to
the master CA. Anything related to generating or caching CRLs is disabled in the CS.cfg file for the
clone. Clones can revoke, display, import, and download CRLs previously generated by master CAs,
but having them generate new CRLs may cause synchronization problems. Only a single CA should
generate CRLs, and this task is always left to the master CA, which also maintains the CRL cache.
Master CAs also manage the relationships and information sharing between the cloned CAs by
monitoring replication changes to the internal databases.
6.1.2. Cloning for DRMs
With DRMs, all keys archived in one DRM are replicated to the internal databases of the other DRMs.
This allows a key recovery to be initiated on any clone DRM, regardless of which DRM the key was
originally archived on.
After a key recovery is processed, the record of the recovery is stored in the internal database of all of
the cloned DRMs.
Although key recovery can be initiated on any clone, once the recovery is initiated, it must be
completed on the same single DRM. This is because a recovery operation is recorded in the replicated
database only after the appropriate number of approvals have been obtained from the DRM agents.
Until then, the DRM on which the recovery is initiated is the only one which knows about the recovery
operation.
6.1.3. Cloning for Other Subsystems
There is no real operational difference between masters and clones for TKSs; the information created
or maintained on one is replicated along the other servers.
For OCSPs, only the master OCSP receives CRL updates, and then the published CRLs are
replicated to the clones.
6.1.4. Cloning and Key Stores
Cloning a subsystem creates two server processes performing the same functions: another new
instance of the subsystem is created and configured to use the same keys and certificates to perform
its operations. Depending on where the keys are stored for the master clone, the method for the clone
to access the keys is very different.
If the keys and certificates are stored in the internal software token, then the keys must be exported
from the master subsystem when it is first configured. When configuring the master instance, there
is an option in the Export Keys and Certificates panel to back up the keys and certificates to a
PKCS#12 file. Before the clone instance is configured, the PKCS#12 file is copied to the alias/
directory for the clone instance. Then, the PKCS#12 filename is given in the Restore Keys and
Certificates screen during the clone's configuration.
If the keys and certificates are stored on a hardware token, then the keys and certificates can be
copied or referenced directly in the token:
• Duplicate all the required keys and certificates, except the SSL server key and certificate to the
clone instance. Keep the nicknames for those certificates the same. Additionally, copy all the
necessary trusted root certificates from the master instance to the clone instance, such as chains or
cross-pair certificates.
81
Page 92

Chapter 6. Cloning Subsystems
• If the token is network-based, then the keys and certificates simply need to be available to the
token; the keys and certificates do not need to be copied.
• When using a network-based hardware token, make sure the high-availability feature is enabled on
the hardware token to avoid single point of failure.
6.1.5. Cloning Considerations
As mentioned in Section 6.1, “About Cloning”, part of the behavior of cloning is to replication
information between the master and the clone, so that they work from an identical set of data
and records. This means that the LDAP servers for the master and clones need to be able to
communicate. If these servers are on different hosts, then make sure that there is appropriate firewall
access to allow the Directory Server instances to connect with each other.
6.2. Exporting Keys from a Software Database
Ideally, the keys for the master instance are exported when the instance is first created. If the keys
were not exported then or if the backup file is lost, then it is possible to extract the keys from the
internal software database for the subsystem instance using the PKCS12Export command. For
example:
PKCS12Export -debug -d /var/lib/subsystem_name/alias -w p12pwd.txt -p internal.txt -o
master.p12
The PKCS#12 file (in this example, master.p12) can then be copied to the clone instance's alias/
directory and imported during the clone configuration.
NOTE
Keys and certificates do not need to be exported from an HSM, so long as the clone
instance is installed using the same HSM as the master. If both instances use the same
key store, then the keys are naturally available to the clone.
6.3. Cloning a CA
1. Configure the master CA, as described in Section 3.3, “Configuring a CA”, and back up the keys.
2. In the CS.cfg file for the master CA, enable the the master CA to monitor replication database
changes by adding the ca.listenToCloneModifications parameter:
cd /etc/subsystem_name
ca.listenToCloneModifications=true
3. Create the clone subsystem instance.
IMPORTANT
Do not go through the setup wizard for the instance yet.
82
Page 93

Cloning a CA
4. Copy the exported PKCS#12 file containing the master instance's keys to the clone's alias/
directory.
The keys for the master instance could have been exported to a .p12 file when the instance was
configured. Alternatively, the keys can be exported using the PKCS12Export command, as in
Section 6.2, “Exporting Keys from a Software Database”.
5. Make sure the PKCS#12 file is accessible by the Certificate System user. If necessary, change the
file permissions to pkiuser. For example:
chown pkiuser:pkiuser example.p12
6. Open the setup wizard URL, which was returned when the instance was created. For example:
http://server.example.com:9180/ca/admin/console/config/login?pin=HIsd90RJSioDK==
7. In the Security Domain panel, add the clone to the same security domain to which the master
belongs.
8. The Subsystem Type panel sets whether to create a new instance or a clone; select the clone
radio button.
9. Give the path and filename of the PKCS #12 backup file which was saved when the master
instance was created or that were exported in 4.
If the keys are stored on an HSM that is accessible to the clone, then they are picked up
automatically.
83
Page 94

Chapter 6. Cloning Subsystems
NOTE
When cloning a CA, the master and clone instances have the same CA signing key.
10. The subsystem information is automatically supplied from the master instance to the clone
instance once the keys are successfully restored. Complete the configuration process.
NOTE
By default, the instance configuration wizard uses localhost as the location for the
internal LDAP database for a new instance. However, with cloning, the configuration
process will spin endlessly and never complete if localhost is used for the internal
database location, even if the LDAP database is indeed installed on the localhost.
Use the the fully-qualified domain name for the LDAP database in the Internal
Database panel when configuring a clone.
11. Edit the CS.cfg file for the clone. Certain parameters must be added to the clone configuration to
disable caching and generating CRLs.
• Disable control of the database maintenance thread:
ca.certStatusUpdateInterval=0
• Disable monitoring database replication changes:
ca.listenToCloneModifications=false
• Disable maintenance of the CRL cache:
ca.crl.IssuingPointId.enableCRLCache=false
• Disable CRL generation:
84
Page 95

Cloning OCSP Subsystems
ca.crl.IssuingPointId.enableCRLUpdates=false
• Enable the clone to redirect CRL requests to the master clone:
master.ca.agent.host=master_hostname
master.ca.agent.port=master_port
12. Restart the clone instance.
service subsystem_name restart
After configuring the clone, test to make sure that the master-clone relationship is functioning:
1. Request a certificate from the cloned CA.
2. Approve the request.
3. Download the certificate to the browser.
4. Revoke the certificate.
5. Check master CA's CRL for the revoked certificate. In the master Certificate Manager's agent
services page, click Update Certificate Revocation List. Find the CRL in the list.
The CRL should show the certificate revoked by the cloned Certificate Manager. If that certificate
is not listed, check logs to resolve the problem.
6.4. Cloning OCSP Subsystems
1. Configure the master OCSP, as described in Section 3.5, “Configuring a DRM, OCSP, or TKS”,
and back up the keys.
2. In the CS.cfg file for the master OCSP, set the
OCSP.Responder.store.defStore.refreshInSec parameter to any non-zero number other
than 21600; 21600 is the setting for a clone.
vim /etc/subsystem_name/CS.cfg
OCSP.Responder.store.defStore.refreshInSec=15000
3. Create the clone subsystem instance.
IMPORTANT
Do not go through the setup wizard for the instance yet.
4. Copy the exported PKCS#12 file containing the master instance's keys to the clone's alias/
directory.
85
Page 96

Chapter 6. Cloning Subsystems
The keys for the master instance could have been exported to a .p12 file when the instance was
configured. Alternatively, the keys can be exported using the PKCS12Export command, as in
Section 6.2, “Exporting Keys from a Software Database”.
5. Make sure the PKCS#12 file is accessible by the Certificate System user. If necessary, change the
file permissions to pkiuser. For example:
chown pkiuser:pkiuser example.p12
6. Open the setup wizard URL, which was returned when the instance was created. For example:
http://server.example.com:11180/ocsp/admin/console/config/login?pin=IOjh7fIOjkld90k
7. In the Security Domain panel, add the clone to the same security domain to which the master
belongs.
8. The Subsystem Type panel sets whether to create a new instance or a clone; select the clone
radio button.
9. Give the path and filename of the PKCS #12 backup file which was saved when the master
instance was created or that were exported in 3.
If the keys are stored on an HSM that is accessible to the clone, then they are picked up
automatically.
86
Page 97

Cloning OCSP Subsystems
10. The subsystem information is automatically supplied from the master instance to the clone
instance once the keys are successfully restored. Complete the configuration process.
NOTE
By default, the instance configuration wizard uses localhost as the location for the
internal LDAP database for a new instance. However, with cloning, the configuration
process will spin endlessly and never complete if localhost is used for the internal
database location, even if the LDAP database is indeed installed on the localhost.
Use the the fully-qualified domain name for the LDAP database in the Internal
Database panel when configuring a clone.
11. Edit the CS.cfg file for the clone. Set the
OCSP.Responder.store.defStore.refreshInSec parameter in the clone instance to
21600.
vim /etc/subsystem_name/CS.cfg
OCSP.Responder.store.defStore.refreshInSec=21600
12. Restart the clone instance.
service subsystem_name start
After configuring the clone, test to make sure that the master-clone relationship is functioning:
1. Set up OCSP publishing in the master CA so that the CRL is published to the master OCSP.
2. Once the CRL is successfully published, check both the master and cloned OCSP's List
Certificate Authorities link in the agent pages. The list should be identical.
3. Use the OCSPClient tool to submit OCSP requests to the master and the cloned Online
Certificate Status Manager. The tool should receive identical OCSP responses from both
managers.
87
Page 98

Chapter 6. Cloning Subsystems
6.5. Cloning DRM and TKS Subsystems
1. Configure the master subsystem, as described in Section 3.5, “Configuring a DRM, OCSP, or
TKS”, and back up the keys.
2. Create the clone subsystem instance.
IMPORTANT
Do not go through the setup wizard for the instance yet.
3. Copy the exported PKCS#12 file containing the master instance's keys to the clone's alias/
directory.
The keys for the master instance could have been exported to a .p12 file when the instance was
configured. Alternatively, the keys can be exported using the PKCS12Export command, as in
Section 6.2, “Exporting Keys from a Software Database”.
4. Make sure the PKCS#12 file is accessible by the Certificate System user. If necessary, change the
file permissions to pkiuser. For example:
chown pkiuser:pkiuser example.p12
5. Open the setup wizard URL, which was returned when the instance was created. For example:
http://server.example.com:10180/kra/admin/console/config/login?pin=Jhu7HBJiodljnw3oijs
6. In the Security Domain panel, add the clone to the same security domain to which the master
belongs.
7. The Subsystem Type panel sets whether to create a new instance or a clone; select the clone
radio button.
88
Page 99

Cloning DRM and TKS Subsystems
8. Give the path and filename of the PKCS #12 backup file which was saved when the master
instance was created or that were exported in 3.
If the keys are stored on an HSM that is accessible to the clone, then they are picked up
automatically.
NOTE
When cloning a DRM, the master and clone instances have the same storage and
transport keys.
89
Page 100

Chapter 6. Cloning Subsystems
9. The subsystem information is automatically supplied from the master instance to the clone
instance once the keys are successfully restored. Complete the configuration process.
NOTE
By default, the instance configuration wizard uses localhost as the location for the
internal LDAP database for a new instance. However, with cloning, the configuration
process will spin endlessly and never complete if localhost is used for the internal
database location, even if the LDAP database is indeed installed on the localhost.
Use the the fully-qualified domain name for the LDAP database in the Internal
Database panel when configuring a clone.
10. Restart the clone instance.
service subsystem_name restart
For the DRM clone, test to make sure that the master-clone relationship is functioning:
1. Go to the DRM agent's page.
2. Click List Requests.
3. Select Show all requests for the request type and status.
4. Click Submit.
5. Compare the results from the cloned DRM and the master DRM. The results ought to be identical.
For the TKS, enroll a smart card and then run an ldapsearch to make sure that the same key
information is contained in both databases.
6.6. Converting Masters and Clones
There can be any number of clones, but there can only be a single configured master. For DRMs and
TKSs, there is no configuration difference between masters and clones, but CAs and OCSPs do have
some configuration differences. This means that when a master is taken offline — because of a failure
or for maintenance or to change the function of the subsystem in the PKI — then the existing master
must be reconfigured to be a clone, and one of the clones promoted to be the master.
6.6.1. Converting CA Clones and Masters
1. Stop the master CA if it is still running.
2. Open the existing master CA configuration directory:
cd /var/lib/pki-ca/conf
3. Edit the CS.cfg file for the master, and change the CRL and maintenance thread settings so that
it is set as a clone:
• Disable control of the database maintenance thread:
90
 Loading...
Loading...