Page 1

Red Hat Directory Server 8.1
Configuration and Command Reference
Co nfiguring and mana ging Red Ha t Directory Server 8.1 wit h command-line
utilities
Edition 8.1.10
Ella Deon La cke y
Copyright © 2009 Red Hat, Inc.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 1
Page 2
Legal Notice
Copyright © 2009 Red Hat, Inc..
The text of and illus trations in this document are licensed by Red Hat under a Creative Commons
Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at
http://creativecommons.org/licens es/by-s a/3.0/. In accordance with CC-BY-SA, if you dis tribute this
document or an adaptation of it, you must provide the URL for the original version.
Red Hat, as the licens or of this document, waives the right to enforce, and agrees not to as sert, Section
4d of CC-BY-SA to the fullest extent permitted by applicable law.
Red Hat, Red Hat Enterpris e Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo,
and RHCE are trademarks of Red Hat, Inc., regis tered in the United States and other countries.
Linux® is the regis tered trademark of Linus T orvalds in the United States and other countries.
Java® is a registered trademark of Oracle and/or its affiliates.
XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States
and/or other countries .
MySQL® is a registered trademark of MySQL AB in the United States, the European Union and other
countries.
All other trademarks are the property of their res pective owners.
180 1 Vars ity Drive
Raleigh, NC 2760 6-2072 USA
Phone: +1 919 754 370 0
Phone: 888 733 4281
Fax: +1 919 754 3701
April 28, 20 09, updated on February 11, 20 10
2 Lega l Notice
Page 3

Abstract
This reference covers the s erver configuration and the command-line utilities. It is designed primarily for
directory administrators and experienced directory users who want to use the command-line to access
the directory. After configuring the server, use this reference to help maintain it.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 3
Page 4

Table of Contents
About T his Reference
1. Directory Server Overview
2. Examples and Formatting
2.1. Command and File Examples
2.2. T ool Locations
2.3. LDAP Locations
2.4. Text Formatting and Styles
3. Additional Reading
4. Giving Feedback
5. Documentation History
1. Introduction
1.1. Directory Server Configuration
1.2. Directory Server Instance File Reference
1.3. Using Directory Server Command-Line Utilities
1.4. Using Directory Server Command-Line Scripts
2. Core Server Configuration Reference
2.1. Overview of the Directory Server Configuration
2.1.1. LDIF and Schema Configuration Files
2.1.2. How the Server Configuration Is Organized
2.2. Accessing and Modifying Server Configuration
2.2.1. Access Control for Configuration Entries
2.2.2. Changing Configuration Attributes
2.3. Core Server Configuration Attributes Reference
2.3.1. cn=config
2.3.2. cn=changelog5
2.3.3. cn=encryption
2.3.4. cn=features
2.3.5. cn=mapping tree
2.3.6. Suffix Configuration Attributes under cn="suffixName"
2.3.7. Replication Attributes under cn=replica, cn="suffixDN", cn=mapping tree, cn=config
2.3.8. Replication Attributes under cn=ReplicationAgreementName, cn=replica,
cn="suffixName", cn=mapping tree, cn=config
2.3.9. Synchroniz ation Attributes under cn=s yncAgreementName,
cn=WindowsReplica,cn="suffixName", cn=mapping tree, cn=config
2.3.10 . cn=monitor
2.3.11. cn=replication
2.3.12. cn=s as l
2.3.13. cn=SNMP
2.3.14 . SNMP Statistic Attributes
2.3.15. cn=tasks
2.3.16. cn=uniqueid generator
2.4. Configuration Object Class es
2.4.1. changeLogEntry (Object Clas s)
2.4.2. directoryServerFeature (Object Class)
2.4.3. nsBackendInstance (Object Clas s)
2.4.4. ns Changelog4Config (Object Class )
2.4.5. nsContainer (Object Class)
2.4.6. nsDS5Replica (Object Clas s)
2.4.7. nsDS5ReplicationAgreement (Object Clas s)
2.4.8. nsDSWindows ReplicationAgreement (Object Class)
2.4.9. nsMappingTree (Object Class )
2.4.10. nsSaslMapping (Object Clas s)
2.4.11. nss lapdConfig (Object Class )
2.4.12. passwordpolicy (Object Class )
2.5. Legacy Attributes
2.5.1. Legacy Server Attributes
2.5.2. Legacy Replication Attributes
3. Plug-in Implemented Server Functionality Reference
3.1. Server Plug-in Functionality Reference
3.1.1. 7-bit Check Plug-in
3.1.2. ACL Plug-in
3.1.3. ACL Preoperation Plug-in
3.1.4. Attribute Uniquenes s Plug-in
3.1.5. Binary Syntax Plug-in
3.1.6. Boolean Syntax Plug-in
4 Tabl e of Co n tents
Page 5

3.1.7. Case Exact String Syntax Plug-in
3.1.8. Case Ignore String Syntax Plug-in
3.1.9. Chaining Database Plug-in
3.1.10 . Class of Service Plug-in
3.1.11. Country String Syntax Plug-in
3.1.12. Distinguished Name Syntax Plug-in
3.1.13. Distributed Numeric Assignment Plug-in
3.1.14 . Generalized T ime Syntax Plug-in
3.1.15. HTTP Client Plug-in
3.1.16. Integer Syntax Plug-in
3.1.17. Internationalization Plug-in
3.1.18. JPEG Syntax Plug-in
3.1.19. ldbm database Plug-in
3.1.20 . Legacy Replication Plug-in
3.1.21. MemberOf Plug-in
3.1.22. Multi-master Replication Plug-in
3.1.23. Octet String Syntax Plug-in
3.1.24 . OID Syntax Plug-in
3.1.25. Pass word Storage Schemes
3.1.26. Postal Address String Syntax Plug-in
3.1.27. PTA Plug-in
3.1.28. Referential Integrity Pos toperation Plug-in
3.1.29. Retro Changelog Plug-in
3.1.30 . Roles Plug-in
3.1.31. Schema Reload Plug-in
3.1.32. Space Insensitive String Syntax Plug-in
3.1.33. State Change Plug-in
3.1.34 . Telephone Syntax Plug-in
3.1.35. URI Syntax Plug-in
3.1.36. Views Plug-in
3.2. List of Attributes Common to All Plug-ins
3.2.1. nsSlapdPlugin
3.2.2. nss lapd-pluginPath
3.2.3. nss lapd-pluginInitfunc
3.2.4. nsslapd-pluginT ype
3.2.5. nss lapd-pluginEnabled
3.2.6. nss lapd-pluginId
3.2.7. nss lapd-pluginVers ion
3.2.8. nss lapd-pluginVendor
3.2.9. nss lapd-pluginDescription
3.3. Attributes Allowed by Certain Plug-ins
3.3.1. nss lapd-pluginLoadNow
3.3.2. nss lapd-pluginLoadGlobal
3.3.3. nss lapd-plugin-depends-on-type
3.3.4. nsslapd-plugin-depends -on-named
3.4. Databas e Plug-in Attributes
3.4.1. Database Attributes under cn= config, cn=ldbm databas e, cn=plugins, cn=config
3.4.2. Database Attributes under cn= monitor, cn=ldbm databas e, cn=plugins, cn=config
3.4.3. Database Attributes under cn= NetscapeRoot, cn=ldbm databas e, cn=plugins, cn=config
and cn=userRoot, cn=ldbm database, cn=plugins, cn=config
3.4.4. Database Attributes under cn=database, cn=monitor, cn=ldbm database, cn=plugins,
cn=config
3.4.5. Database Attributes under cn= default indexes, cn=config, cn=ldbm databas e,
cn=plugins, cn=config
3.4.6. Database Attributes under cn= monitor, cn=NetscapeRoot, cn=ldbm database,
cn=plugins, cn=config
3.4.7. Database Attributes under cn= index, cn=NetscapeRoot, cn=ldbm database, cn=plugins,
cn=config and cn=index, cn=UserRoot, cn=ldbm database, cn=plugins, cn=config
3.4.8. Database Attributes under cn= attributeName, cn=encrypted attributes,
cn=databas e_name, cn=ldbm databas e, cn=plugins, cn=config
3.5. Database Link Plug-in Attributes (Chaining Attributes)
3.5.1. Databas e Link Attributes under cn=config, cn=chaining database, cn=plugins, cn=config
3.5.2. Databas e Link Attributes under cn=default instance config, cn=chaining database,
cn=plugins, cn=config
3.5.3. Databas e Link Attributes under cn=database_link_name, cn=chaining database,
cn=plugins, cn=config
3.5.4. Database Link Attributes under cn=monitor, cn=databas e ins tance name, cn=chaining
database, cn=plugins, cn=config
3.6. Retro Changelog Plug-in Attributes
3.6.1. nss lapd-changelogdir
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 5
Page 6

3.6.2. nss lapd-changelogmaxage (Max Changelog Age)
3.7. Distributed Numeric Assignment Plug-in Attributes
3.7.1. dnaFilter
3.7.2. dnaMagicRegen
3.7.3. dnaMaxValue
3.7.4. dnaNextRange
3.7.5. dnaNextValue
3.7.6. dnaPrefix
3.7.7. dnaRangeReques tTimeout
3.7.8. dnaScope
3.7.9. dnaSharedCfgDN
3.7.10 . dnaThreshold
3.7.11. dnaT ype
3.8. MemberOf Plug-in Attributes
3.8.1. memberofattr
3.8.2. memberofgroupattr
4. Server Instance File Reference
4.1. Overview of Directory Server Files
4.2. Backup Files
4.3. Configuration Files
4.4. Database Files
4.5. LDIF Files
4.6. Lock Files
4.7. Log Files
4.8. PID Files
4.9. Tools
4.10. Scripts
5. Log File Reference
5.1. Access Log Reference
5.1.1. Access Logging Levels
5.1.2. Default Acces s Logging Content
5.1.3. Access Log Content for Additional Access Logging Levels
5.1.4. Common Connection Codes
5.2. Error Log Reference
5.2.1. Error Log Logging Levels
5.2.2. Error Log Content
5.2.3. Error Log Content for Other Log Levels
5.3. Audit Log Reference
5.4. LDAP Result Codes
6. Command-Line Utilities
6.1. Finding and Executing Command-Line Utilities
6.2. Using Special Characters
6.3. Command-Line Utilities Quick Reference
6.4. ldaps earch
6.5. ldapmodify
6.6. ldapdelete
6.7. ldappass wd
6.8. ldif
6.9. dbs can
7. Command-Line Scripts
7.1. Finding and Executing Command-Line Scripts
7.2. Command-Line Scripts Quick Reference
7.3. Shell Scripts
7.3.1. bak2db (Restores a Databas e from Backup)
7.3.2. cl-dump (Dumps and Decodes the Changelog)
7.3.3. db2bak (Creates a Backup of a Database)
7.3.4. db2ldif (Exports Database Contents to LDIF)
7.3.5. db2index (Reindexes Database Index Files)
7.3.6. dbverify (Checks for Corrupt Databases )
7.3.7. ds_removal
7.3.8. ldif2db (Import)
7.3.9. ldif2ldap (Performs Import Operation over LDAP)
7.3.10 . monitor (Retrieves Monitoring Information)
7.3.11. repl-monitor (Monitors Replication Status)
7.3.12. pwdhas h (Prints Encrypted Passwords)
7.3.13. restart-s lapd (Restarts the Directory Server)
7.3.14 . restoreconfig (Restores Administration Server Configuration)
7.3.15. saveconfig (Saves Administration Server Configuration)
6 Tabl e of Co n tents
Page 7

7.3.16. start-slapd (Starts the Directory Server)
7.3.17. stop-slapd (Stops the Directory Server)
7.3.18. suffix2instance (Maps a Suffix to a Backend Name)
7.3.19. vlvindex (Creates Virtual List View Indexes )
7.4. Perl Scripts
7.4.1. bak2db.pl (Res tores a Database from Backup)
7.4.2. cl-dump.pl (Dumps and Decodes the Changelog)
7.4.3. db2bak.pl (Creates a Backup of a Databas e)
7.4.4. db2index.pl (Creates and Generates Indexes)
7.4.5. db2ldif.pl (Exports Database Contents to LDIF)
7.4.6. fixup-memberof.pl (Regenerate memberOf Attributes )
7.4.7. ldif2db.pl (Import)
7.4.8. logconv.pl (Log Converter)
7.4.9. migrate-ds.pl
7.4.10. migrate-ds-admin.pl
7.4.11. ns-accounts tatus .pl (Establishes Account Status)
7.4.12. ns-activate.pl (Activates an Entry or Group of Entries)
7.4.13. ns-inactivate.pl (Inactivates an Entry or Group of Entries)
7.4.14. ns-newpwpolicy.pl (Adds Attributes for Fine-Grained Pass word Policy)
7.4.15. register-ds -admin.pl
7.4.16. remove-ds .pl
7.4.17. repl-monitor.pl (Monitors Replication Status )
7.4.18. schema-reload.pl (Reload Schema Files Dynamically)
7.4.19. setup-ds.pl
7.4.20. setup-ds -admin.pl
7.4.21. verify-db.pl (Check for Corrupt Databases )
A. Using the ns-slapd Command-Line Utilities
A.1. Overview of ns-slapd
A.2. Finding and Executing the ns-s lapd Command-Line Utilities
A.3. Utilities for Exporting Databas es: db2ldif
A.4. Utilities for Restoring and Backing up Databases: ldif2db
A.5. Utilities for Restoring and Backing up Databas es: archive2db
A.6. Utilities for Restoring and Backing up Databas es: db2archive
A.7. Utilities for Creating and Regenerating Indexes: db2index
Glossary
Index
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 7
Page 8

About T his Reference
Red Hat Directory Server (Directory Server) is a powerful and scalable dis tributed directory server
based on the indus try-s tandard Lightweight Directory Acces s Protocol (LDAP). Directory Server is the
cornerstone for building a centralized and distributed data repos itory that can be used in an intranet,
over an extranet with trading partners, or over the public Internet to reach customers .
This reference covers the s erver configuration and the command-line utilities. It is designed primarily for
directory administrators and experienced directory users who want to use the command-line to access
the directory. After configuring the server, use this reference to help maintain it.
The Directory Server can also be managed through the Directory Server Console, a graphical user
interface. The Red Hat Directory Server Administrator's Guide describes how to do this and explains
individual administration tasks more fully.
1. Directory Server Overview
The major components of Directory Server include:
An LDAP server – The LDAP v3-compliant network daemon.
Directory Server Console – A graphical management console that dramatically reduces the effort of
setting up and maintaining your directory service.
SNMP agent – Can monitor the Directory Server using the Simple Network Management Protocol
(SNMP).
2. Examples and Formatting
Each of the examples used in this guide, such as file locations and commands , have certain defined
conventions.
2.1. C ommand a nd F ile Exa mples
All of the examples for Red Hat Directory Server commands, file locations, and other us age are given for
Red Hat Enterpris e Linux 5 (32-bit) s ystems. Be certain to use the appropriate commands and files for
your platform.
Exa mple 1. Exa mple Co mmand
To start the Red Hat Directory Server:
service dirsv start
2.2. T ool Locat ions
The tools for Red Hat Directory Server are located in the /usr/bin and the /usr/sbin directories.
These tools can be run from any location without specifying the tool location.
2.3. LDAP Locations
There is another important consideration with the Red Hat Directory Server tools. The LDAP tools
referenced in this guide are Moz illa LDAP, installed with Red Hat Directory Server in the
/usr/lib/mozldap directory on Red Hat Enterprise Linux 5 (32-bit) (or /usr/lib64 /m ozldap for
64-bit systems).
However, Red Hat Enterprise Linux systems also include LDAP tools from OpenLDAP in the /usr/bin
directory. It is poss ible to use the OpenLDAP commands as shown in the examples, but you must us e
the -x argument to disable SASL, which OpenLDAP tools use by default.
2.4 . T ext Forma tting and Styles
Certain words are represented in different fonts, styles, and weights. Different character formatting is
used to indicate the function or purpos e of the phras e being highlighted.
Format ting S tyle Purpose
Monospa ce font Monospace is used for commands , package names, files and directory
paths , and any text displayed in a prompt.
8 Abo ut This Reference
Page 9

Monospace
with a
background
This type of formatting is used for anything entered or returned in a
command prompt.
Italicized text Any text which is italiciz ed is a variable, such as instance_name or
hostname. Occasionally, this is also used to emphas ize a new term or other
phrase.
Bolded text Most phrases which are in bold are application names, such as C ygwin, or
are fields or options in a user interface, such as a User Nam e Here: field
or Save button.
Other formatting s tyles draw attention to important text.
NOT E
A note provides additional information that can help illustrate the behavior of the s ystem or
provide more detail for a specific issue.
IMPORTANT
Important information is necessary, but pos sibly unexpected, such as a configuration change that
will not persis t after a reboot.
WARNING
A warning indicates potential data los s, as may happen when tuning hardware for maximum
performance.
3. Additional Reading
The Directory Server Administrator's Guide describes how to set up, configure, and administer Red Hat
Directory Server and its contents . this manual does not des cribe many of the bas ic directory and
architectural concepts that you need to deploy, install, and administer a directory service success fully.
Those concepts are contained in the Red Hat Directory Server Deployment Guide. You should read that
book before continuing with this manual.
When you are familiar with Directory Server concepts and have done s ome preliminary planning for your
directory service, install the Directory Server. The instructions for installing the various Directory Server
components are contained in the Red Hat Directory Server Installation Guide. Many of the scripts and
commands used to install and administer the Directory Server are explained in detail in the Red Hat
Directory Server Configuration, Command, and F ile Reference.
Also, Managing Servers with Red Hat Console contains general background information on how to use
the Red Hat Cons ole. You should read and understand the concepts in that book before you attempt to
administer Directory Server.
The document s et for Directory Server contains the following guides:
Red Hat Directory Server Release Notes contain important information on new features, fixed bugs,
known is sues and workarounds , and other important deployment information for this specific vers ion
of Directory Server.
Red Hat Directory Server Deployment Guide provides an overview for planning a deployment of the
Directory Server.
Red Hat Directory Server Administrator's Guide contains procedures for the day-to-day maintenance
of the directory service. Includes information on configuring server-side plug-ins.
Red Hat Directory Server Configuration, Command, and File Reference provides reference
information on the command-line scripts, configuration attributes, and log files shipped with Directory
Server.
Red Hat Directory Server Installation Guide contains procedures for ins talling your Directory Server
as well as procedures for migrating from a previous ins tallation of Directory Server.
Red Hat Directory Server Schema Reference provides reference information about the Directory
Server schema.
Red Hat Directory Server Plug-in Programmer's Guide describes how to write server plug-ins in
order to cus tomize and extend the capabilities of Directory Server.
Using Red Hat Console gives an overview of the primary us er interface and how it interacts with the
Directory Server and Administration Server, as well as how to perform bas ic management tasks
through the main Console window.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 9
Page 10

Using the Admin Server describes the different tas ks and tools as sociated with the Administration
Server and how to use the Administration Server with the Configuration and Us er Directory Server
instances.
For the latest information about Directory Server, including current releas e notes, complete product
documentation, technical notes, and deployment information, see the Red Hat Directory Server
documentation site at http://www.redhat.com/docs/manuals/dir-server/.
4. Giving Feedback
If there is any error in this Configuration, Command, and File Reference or there is any way to improve
the documentation, pleas e let us know. Bugs can be filed agains t the documentation for Red Hat
Directory Server through Bugzilla, http://bugz illa.redhat.com/bugz illa. Make the bug report as specific as
possible, so we can be more effective in correcting any issues:
Select the Red Hat Directory Server product.
Set the component to D oc - cli -guide.
Set the version number to 8.1.
For errors, give the page number (for the PDF) or URL (for the HT ML), and give a succinct
description of the problem, such as incorrect procedure or typo.
For enhancements, put in what information needs to be added and why.
Give a clear title for the bug. For example, "Inc orrect com m and exam pl e for setup
scri pt options" is better than "Bad exam ple" .
We appreciate receiving any feedback — reques ts for new s ections , corrections, improvements ,
enhancements, even new ways of delivering the documentation or new styles of docs. You are welcome
to contact Red Hat Content Services directly at mailto:docs@redhat.com.
5. Documentation History
Revision 8.1 .1 0 July 29 , 2 01 0 Ella Deon La cke y
Adding information about setting an idle timeout period for large databases for the replication user, per
Bugzilla #6180 55.
Revision 8.1 .9 Fe bruary 11, 2 0 10 Ella Deon La cke y
Clarifying how passwordUnlock works, per Bugz illa #552377.
Changing thens DirectoryServerT ask object class to extensibleObject, per Bugzilla #555787.
Adding extra reference to the 64 -bit tools directory, per Bugzilla #554972.
Revision 8.1 .8 Janua ry 1 1 , 201 0 Ella Deon La cke y
Adding s ection on nsslapd-cachememsiz e and the import buffer size, per Bugzilla #531043.
Revision 8.1 .7 October 10, 20 09 Ella Deon La cke y
Fixing two plug-in des criptions .
Revision 8.1 .6 Se pt ember 19 , 2 009 Ella Deon La cke y
Removing the silent configuration parameters for the register-ds-admin.pl script, per Bugzilla #514 231.
Revision 8.1 .5 Se pt ember 9, 20 09 Ella Deon La cke y
Removing any references to the Directory Server Gateway or Org Chart.
Revision 8.1 .4 Se pt ember 4 , 2 009 Ella Deon La cke y
Correcting the directory paths for configuration LDIF files, per Bugz illa #521139.
Revision 8.1 .3 August 26 , 2 009 Ella Deon La cke y
Adding information about setting database and entry cache memory s izes and clarifying the units of
measurement for the attributes, per Bugzilla #50 3615.
Revision 8.1 .2 August 4 , 200 9 Ella Deon La cke y
Changed the default on the nsslapd-cache-autosiz e parameter to 0 , per Bugz illa #514282.
Revision 8.1 .1 July 19 , 2 00 9 Ella Deon La cke y
Expanding the des cription of dnaNextRange, Bugzilla #512557.
Revision 8.1 .0 April 28 , 2 009 Ella Deon La cke y
Initial draft for vers ion 8.1.
10 Abo ut This Reference
Page 11

Chapter 1. Introduction
Directory Server is bas ed on an open-sys tems s erver protocol called the Lightweight Directory Access
Protocol (LDAP). The Directory Server is a robust, scalable server designed to manage large s cale
directories to support an enterprise-wide directory of us ers and resources, extranets, and e-commerce
applications over the Internet. The Directory Server runs as the n s-slapd proces s or service on the
machine. The server manages the directory databases and responds to client requests.
This reference deals with the other methods of managing the Directory Server by altering the server
configuration attributes using the command line and us ing command-line utilities and scripts.
1.1. Directory Server Configuration
The format and method for storing configuration information for Directory Server and a listing for all
server attributes are found in two chapters , Chapter 2, Core Server Configuration Reference and
Chapter 3, Plug-in Implemented Server Functionality Reference.
1.2. Directory Server Instance File Reference
Chapter 4, Server Instance File Reference has an overview of the files and configuration information
stored in each instance of Directory Server. This is useful reference to helps administrators unders tand
the changes or abs ence of changes in the cours e of directory activity. From a security s tandpoint, this
also helps users detect errors and intrusion by highlighting normal changes and abnormal behavior.
1.3. Using Directory Server Command-Line Utilities
Directory Server comes with a s et of configurable command-line utilities that can s earch and modify
entries in the directory and administer the server. Chapter 6, Command-Line Utilities describes these
command-line utilities and contains information on where the utilities are stored and how to access them.
In addition to these command-line utilities, Directory Server als o provides ns-slapd command-line
utilities for performing directory operations , as described in Appendix A, Using the ns-slapd Command-
Line Utilities.
1.4. Using Directory Server Command-Line Scripts
In addition to command-line utilities , several non-configurable scripts are provided with the Directory
Server that make it quick and eas y to perform routine server administration tasks from the command-line.
Chapter 7, Command-Line Scripts lists the most frequently used scripts and contains information on
where the scripts are stored and how to access them.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 11
Page 12
Chapter 2. Core Server Configuration Reference
The configuration information for Red Hat Directory Server is s tored as LDAP entries within the directory
itself. T herefore, changes to the server configuration mus t be implemented through the us e of the server
itself rather than by simply editing configuration files. T he principal advantage of this method of
configuration s torage is that it allows a directory administrator to reconfigure the server using LDAP
while it is still running, thus avoiding the need to shut the s erver down for most configuration changes.
This chapter gives details on how the configuration is organiz ed and how to alter it. The chapter also
provides an alphabetical reference for all attributes.
2.1. Overview of the Directory Server Configuration
When the Directory Server is set up, its default configuration is stored as a s eries of LDAP entries within
the directory, under the subtree cn=con fig . When the s erver is s tarted, the contents of the
cn=config subtree are read from a file (dse.ld if) in LDIF format. This dse.ldif file contains all of
the s erver configuration information. The latest version of this file is called dse.ldif, the vers ion prior
to the last modification is called dse.ldif .bak, and the latest file with which the server s ucces sfully
started is called dse.ldi f.startOK.
Many of the features of the Directory Server are des igned as dis crete modules that plug into the core
server. The details of the internal configuration for each plug-in are contained in separate entries under
cn=plugins,cn=confi g. For example, the configuration of the T elephone Syntax Plug-in is contained
in this entry:
cn=Telephone Syntax,cn=plugins,cn=config
Similarly, database-specific configuration is stored under cn=ldbm
database,cn=plugi ns,cn=config for local databases and cn=chaini ng
database,cn=plugi ns,cn=config for databas e links .
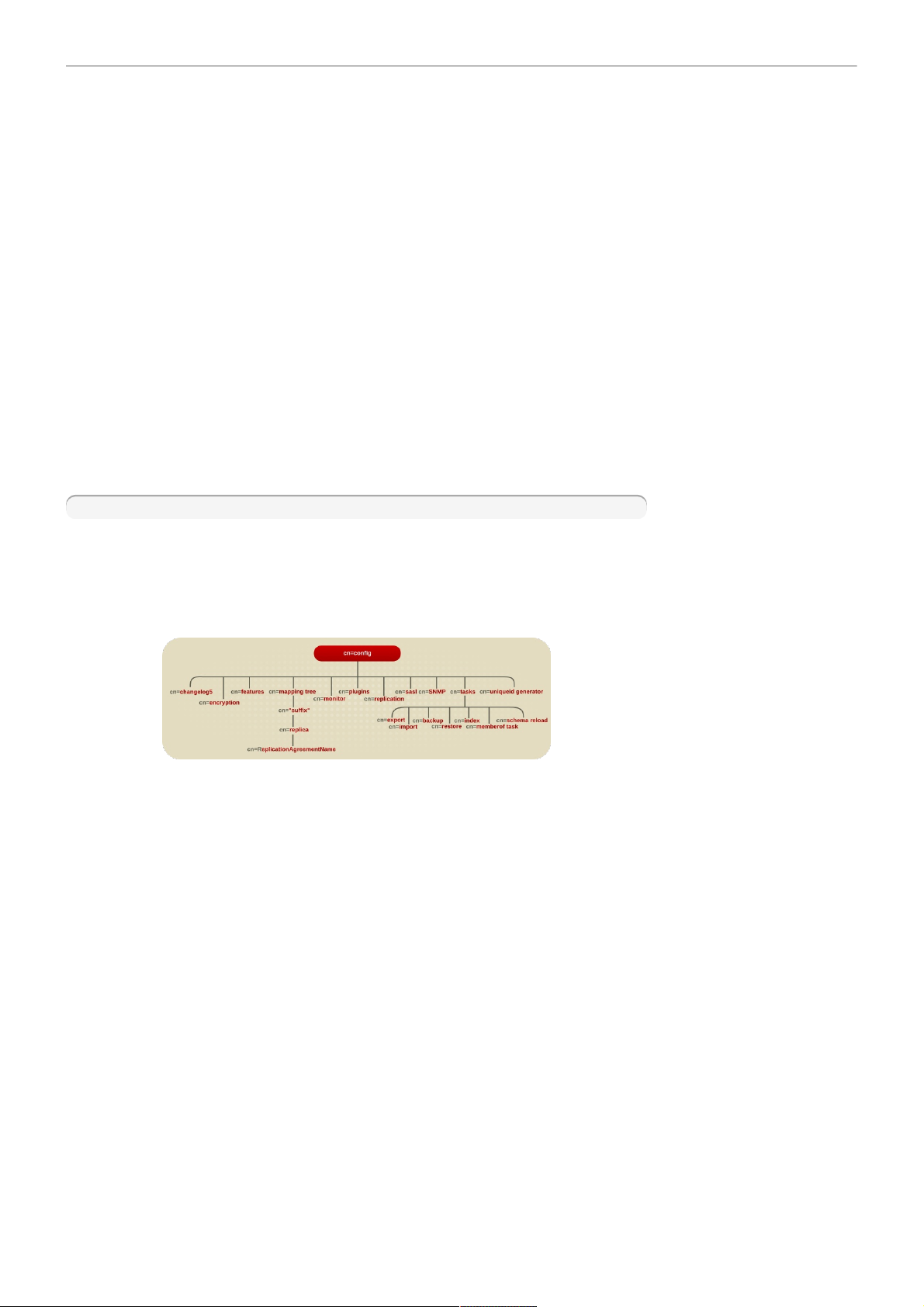
The following diagram illustrates how the configuration data fits within the cn=conf ig directory
information tree.
Figu re 2.1. D ire ct ory Informat ion Tree Showing Configura tion D ata
2.1.1 . LD IF a nd Schema Configuratio n Files
The Directory Server configuration data are stored in LDIF files in the
/etc/di rsrv/slap d-instance_name directory (/etc/opt/dirsrv/slapd -instance_name on HP-
UX). Thus, if a server identifier is phoneboo k, then for a Directory Server on Red Hat Enterprise Linux 5
(32-bit), the configuration LDIF files are all stored under /etc/dirsrv/slapd-phonebook.
This directory also contains other s erver instance-specific configuration files.
Schema configuration is also stored in LDIF format, and these files are located in the
/etc/di rsrv/slap d-instance_name/schema directory
(/etc/opt/dirsrv/slapd ->instance_name on HP-UX).
The following table lists all of the configuration files that are s upplied with the Directory Server, including
thos e for the schema of other compatible s ervers. Each file is preceded by a number which indicates the
order in which they should be loaded (in ascending numerical and then alphabetical order).
12 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 13

Table 2 .1 . Directory Server LDIF Config ura t ion F iles
Configu ra tion Filename Purpose
dse.ldif Contains front-end Directory Specific Entries
created by the directory at server startup. These
include the Root DSE ("") and the contents of
cn=config and cn=monitor (ACIs only).
00core.ldif Contains only those schema definitions
neces sary for s tarting the s erver with the bare
minimum feature set (no user s chema, no s chema
for any non-core features). T he rest of the
schema used by users, features, and applications
is found in 01co mmon.ld if and the other
schema files. Do not modify this file.
01common.ldif Contains LDAPv3 standard operational schema,
such as subschema Subentry, LDAPv3
standard user and organization schema defined
in RFC 2256 (based on X.520/X.521),
inetOrg Person and other widely-us ed
attributes, and the operational attributes used by
Directory Server configuration. Modifying this file
causes interoperability problems. User-defined
attributes s hould be added through the Directory
Server Console.
05rfc224 7.ldif Schema from RFC 224 7 and related pilot schema,
from "Using Domains in LDAP/X500
Distinguished Names."
05rfc2927.ldif Schema from RFC 2927, "MIME Directory Profile
for LDAP Schema." Contains the ldapSchemas
operational attribute required for the attribute to
show up in the subschema subentry.
10presence.ldif Legacy. Schema for ins tant messaging pres ence
(online) information; the file lis ts the default object
classes with the allowed attributes that must be
added to a us er's entry in order for ins tantmess aging presence information to be available
for that user.
10rfc230 7.ldif Schema from RFC 230 7, "An Approach for Using
LDAP as a Network Information Service." T his
may be supers eded by 10rfc2307bi s, the new
vers ion of r fc2 307, when that schema becomes
available.
20subscriber.ldif Contains new s chema elements and the Nortel
subscriber interoperability specification. Also
contains the adminRole and memberOf attributes
and inetAdm in object class , previous ly stored
in the 5 0ns-delegated-adm in.ldif file.
25java-object.ldif Schema from RFC 2713, "Schema for
Repres enting Java® Objects in an LDAP
Directory."
28pilot.ldif Contains pilot directory s chema from RFC 1274 ,
which is no longer recommended for new
deployments . Future RFCs which succeed RFC
1274 may deprecate s ome or all of
28pilot.ldif attribute types and class es.
30ns-common.ldif Schema that contains objects classes and
attributes common to the Directory Server
Console framework.
50ns-admin.ldif Schema used by Red Hat Administration Server.
50ns-certificate.ldif Schema for Red Hat Certificate Management
System.
50ns-directory.ldif Contains additional configuration s chema us ed by
Directory Server 4 .12 and earlier versions of the
directory, which is no longer applicable to current
releas es of Directory Server. This s chema is
required for replicating between Directory Server
4.12 and current releas es.
50ns-mail.ldif Schema used by Nets cape Messaging Server to
define mail users and mail groups .
50ns-value.ldif Schema for s ervers' value item attributes.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 13
Page 14

50ns-web.ldif Schema for Netscape Web Server.
60pam-plugin.ldif Reserved for future us e.
99us er.ldif User-defined schema maintained by Directory
Server replication consumers which contains the
attributes and object class es from the s uppliers .
2.1.2 . How the S er ver Configura tion Is Organize d
The dse.ldif file contains all configuration information including directory-specific entries created by
the directory at server startup, such as entries related to the databas e. The file includes the root
Directory Server entry (or DSE, named by "") and the contents of cn=confi g and cn= monitor.
When the server generates the dse.ldi f file, it lists the entries in hierarchical order in the order that
the entries appear in the directory under cn =config, which is usually the s ame order in which an LDAP
search of s ubtree scope for base cn=con fig returns the entries.
dse.ldif also contains the cn=m onitor entry, which is mostly read-only, but can have ACIs s et on it.
NOT E
The dse.ldif file does not contain every attribute in cn=config. If the attribute has not been
set by the administrator and has a default value, the server will not write it to dse.ldi f. To see
every attribute in cn= con fig, use l dapsear ch.
2.1.2 .1 . Co nfigura tion At tribute s
Within a configuration entry, each attribute is represented as an attribute name. The value of the
attribute corresponds to the attribute's configuration.
The following code sample is an example of part of the dse.ldif file for a Directory Server. The
example s hows, among other things, that s chema checking has been enabled; this is represented by the
attribute nsslapd-schemacheck, which takes the value on.
dn: cn=config
objectclass: top
objectclass: extensibleObject
objectclass: nsslapdConfig
nsslapd-accesslog-logging-enabled: on
nsslapd-enquote-sup-oc: off
nsslapd-localhost: phonebook.example.com
nsslapd-schemacheck: on
nsslapd-port: 389
nsslapd-localuser: nobody
...
2.1.2 .2 . Co nfigura tion of Plug-in Functiona lit y
The configuration for each part of Directory Server plug-in functionality has its own separate entry and
set of attributes under the subtree cn=p lugins,cn= config. The following code sample is an
example of the configuration entry for an example plug-in, the Telephone Syntax plug-in.
dn: cn=Telephone Syntax,cn=plugins,cn=config
objectclass: top
objectclass: nsSlapdPlugin
objectclass: extensibleObject
cn: Telephone Syntax
nsslapd-pluginType: syntax
nsslapd-pluginEnabled: on
Some of thes e attributes are common to all plug-ins, and some may be particular to a specific plug-in.
Check which attributes are currently being used by a given plug-in by performing an lda psearch on
the cn=conf ig subtree.
For a list of plug-ins s upported by Directory Server, general plug-in configuration information, the plug-in
configuration attribute reference, and a list of plug-ins requiring res tart for configuration changes, see
Chapter 3, Plug-in Implemented Server Functionality Reference.
2.1.2 .3. C onfigurat ion of D at a ba ses
The o=Netsca peRoot and cn=UserRoot subtrees under the database plug-in entry contain
configuration data for the databases containing the o=Netscape Root suffix and the default s uffix
created during setup, such as dc =example,dc=com .
14 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 15
These entries and their children have many attributes used to configure different database settings, like
the cache siz es, the paths to the index files and transaction logs, entries and attributes for monitoring
and s tatistics; and databas e indexes.
2.1.2 .4 . Configurat ion of Indexes
Configuration information for indexing is stored as entries in the Directory Server under the following
information-tree nodes:
cn=index,o=Netsca peRoot,cn=ldbm da tabase,cn= plugins,cn =config
cn=index,cn=UserRoot,cn= ldbm datab ase,cn=plugins,cn=config
cn=default indexes,cn=config,cn=ldbm database,cn=p lugins,cn= config
For more information about indexes in general, see the Directory Server Administrator's Guide. For
information about the index configuration attributes, see Section 3.4.1, “Databas e Attributes under
cn=config, cn=ldbm database, cn=plugins, cn=config”.
2.2. Accessing and Modifying Server Configuration
This s ection discus ses access control for configuration entries and describes the various ways in which
the s erver configuration can be viewed and modified. It also covers res trictions to the kinds of
modification that can be made and discus ses attributes that require the server to be restarted for
changes to take effect.
2.2.1 . Acce ss Control for Configura tion Entries
When the Directory Server is installed, a default set of access control instructions (ACIs) is implemented
for all entries under cn=con fig. The following code sample is an example of thes e default ACIs.
aci: (targetattr = "*")(version 3.0; acl "Configuration Adm inistrators Group";
allow (all)
groupdn = "ldap:///cn=Configuration Adm inistrators,u=Groups,
ou=TopologyManagement, o=NetscapeRoot";)
aci: (targetattr = "*")(version 3.0; acl "Configuration Adm inistrator"; allow (all)
userdn = "ldap:///uid=admin, ou=Administrators, ou=TopologyManagement,
o=NetscapeRoot";)
aci: (targetattr = "*")(version 3.0; acl "Local Directory Adm inistrators Group";
allow (all)
groupdn = "ldap:///ou=Directory Adm inistrators, dc=example,dc=com";)
aci: (targetattr = "*")(version 3.0; acl "SIE Group"; allow(all)
groupdn = "ldap:///cn=slapd-phonebook, cn=Red Hat Directory Server,
cn=Server Group, cn=phonebook.example.com, dc=example,dc=com,
o=NetscapeRoot";)
These default ACIs allow all LDAP operations to be carried out on all configuration attributes by the
following users:
Members of the Configuration Administrators group.
The user acting as the administrator, the a dm in account that was configured at s etup. By default,
this is the same us er account which is logged into the Console.
Members of local Directory Administrators group.
The SIE (Server Instance Entry) group, us ually as signed using the S et Access Perm issions
process the main console.
For more information on access control, see the Directory Server Administrator's Guide.
2.2.2 . Changing Configura tion At tribute s
Server attributes can be viewed and changed in one of three ways: through the Directory Server
Console, by performing lda psearch and ldap modi fy commands, or by manually editing the
dse.ldif file.
NOT E
Before editing the dse.ldif file, the s erver must be stopped; otherwis e, the changes are lost.
Editing the dse.ldif file is recommended only for changes to attributes which cannot be altered
dynamically. See Section 2.2.2.3, “Configuration Changes Requiring Server Restart” for further
information.
The following sections describe how to modify entries using LDAP (both by using Directory Server
Console and by using the command line), the restrictions that apply to modifying entries , the res trictions
that apply to modifying attributes , and the configuration changes requiring restart.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 15
Page 16

2.2.2 .1 . Modifying Configu ra tion Entries Using LDAP
The configuration entries in the directory can be searched and modified using LDAP either via the
Directory Server Console or by performing ld apsearc h and lda pm od ify operations in the same way
as other directory entries. T he advantage of using LDAP to modify entries is changes can be made while
the s erver is running.
For further information, see the "Creating Directory Entries " chapter in the Directory Server
Administrator's Guide. However, certain changes do require the server to be restarted before they are
taken into account. See Section 2.2.2.3, “Configuration Changes Requiring Server Res tart” for further
information.
NOT E
As with any set of configuration files, care s hould be taken when changing or deleting nodes in
the cn=conf ig subtree as this risks affecting Directory Server functionality.
The entire configuration, including attributes that always take default values, can be viewed by
performing an ldapsearc h operation on the cn=conf ig subtree:
ldapsearch -b cn=config -D bindDN -w password
bindDN is the DN chosen for the Directory Manager when the server was ins talled (cn=Directory
Manager by default).
password is the password chosen for the Directory Manager.
For more information on using l dapsear ch, see Section 6.4, “ldaps earch”.
To disable a plug-in, use l dapm odify to edit the nsslapd-pluginEnabled attribute:
ldapmodify -D cn="directory m anager" -w password
dn: cn=Telephone Syntax,cn=plugins,cn=config
changetype: modify
replace: nsslapd-pluginEnabled
nsslapd-pluginEnabled: off
2.2.2 .2 . Restr ict ions to Modifying Configurat ion Entries and Attribut e s
Certain restrictions apply when modifying server entries and attributes :
The cn=m onitor entry and its child entries are read-only and cannot be modified, except to
manage ACIs.
If an attribute is added to cn=con fig , the server ignores it.
If an invalid value is entered for an attribute, the s erver ignores it.
Because ldapd ele te is used for deleting an entire entry, use ldapmodify to remove an attribute
from an entry.
2.2.2 .3. C onfigurat ion Chang es Requiring Se rver Rest a rt
Some configuration attributes cannot be altered while the s erver is running. In these cases, for the
changes to take effect, the s erver needs to be shut down and restarted. The modifications should be
made either through the Directory Server Console or by manually editing the dse.ldif file. Some of the
attributes that require a s erver restart for any changes to take effect are listed below. This lis t is not
exhaus tive; to see a complete list, run l dapsear ch and search for the nsslapd-requiresrestart
attribute. For example:
ldapsearch -p 389 -D "cn=directory m anager" -w password -s sub -b "cn=config"
"(objectclass=*)" | grep nsslapd-requiresrestart
nsslapd-caches ize nss lapd-certdir
nsslapd-dbcachesize nsslapd-dbncache
nsslapd-plugin nsslapd-changelogdir
nsslapd-changelogmaxage nsslapd-changelogmaxentries
nsslapd-port nsslapd-schemadir
nsslapd-sas lpath nsslapd-secureport
nsslapd-tmpdir nsSSL2
nsSSL3 nsSSLclientauth
nsSSLSessionT imeout nsslapd-conntablesize
nsslapd-lockdir nsslapd-maxdescriptors
nsslapd-reservedes criptors nsslapd-listenhost
16 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 17

nsslapd-schema-ignore-trailing-s paces nss lapd-s ecurelistenhost
nsslapd-workingdir nsslapd-return-exact-case
nsslapd-maxbersize
2.3. Core Server Configuration Attributes Reference
This s ection contains reference information on the configuration attributes that are relevant to the core
server functionality. For information on changing server configuration, see Section 2.2, “Accessing and
Modifying Server Configuration”. For a lis t of s erver features that are implemented as plug-ins, see
Section 3.1, “Server Plug-in Functionality Reference”. For help with implementing custom server
functionality, contact Directory Server support.
The configuration information stored in the dse.ldif file is organized as an information tree under the
general configuration entry cn=config, as s hown in the following diagram.
Figu re 2.2. D ire ct ory Informat ion Tree Showing Configura tion D ata
Most of these configuration tree nodes are covered in the following sections.
The cn=pl ugins node is covered in Chapter 3, Plug-in Implemented Server Functionality Reference.
The des cription of each attribute contains details such as the DN of its directory entry, its default value,
the valid range of values, and an example of its use.
NOT E
Some of the entries and attributes des cribed in this chapter may change in future releases of the
product.
2.3.1. cn=config
General configuration entries are stored in the cn=co nfig entry. The cn=con fig entry is an instance
of the nsslapdConfi g object class, which in turn inherits from extensibleObjec t object clas s.
2.3.1.1. nsslapd- accesslog (Acce ss Log)
This attribute s pecifies the path and filename of the log used to record each LDAP acces s. T he following
information is recorded by default in the log file:
IP address of the client machine that accessed the databas e.
Operations performed (for example, search, add, and modify).
Result of the access (for example, the number of entries returned or an error code).
For more information on turning access logging off, see the "Monitoring Server and Database Activity"
chapter in the Directory Server Administrator's Guide.
For acces s logging to be enabled, this attribute must have a valid path and parameter, and the
nsslapd-accesslog-logging-enabled configuration attribute must be switched to o n. The table lists
the four pos sible combinations of values for these two configuration attributes and their outcome in
terms of disabling or enabling of access logging.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 17
Page 18

Table 2 .2 . dse .ldif File At tribut e s
Attribut e Valu e Logging enabled or disabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
on
empty string
Disabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
on
filename
Enabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
off
empty string
Disabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
off
filename
Disabled
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid filename.
Default Value /var/log/dirs rv/slapd-instance_name/access
Syntax DirectoryString
Example nsslapd-accesslog:
/var/log/dirsrv/slapd-instance_name/acces s
2.3.1.2. nsslapd- accesslog-le ve l (Access Log L evel)
This attribute controls what is logged to the access log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values
0 - No access logging
4 - Logging for internal access operations
256 - Logging for connections, operations,
and results
512 - Logging for access to an entry and
referrals
1310 72 - Provides microsecond operation
timing
These values can be added together to
provide the exact type of logging required; for
example, 516 (4 + 512) to obtain internal
acces s operation, entry access , and referral
logging.
Default Value 256
Syntax Integer
Example nsslapd-accesslog-level: 256
2.3.1.3. nsslapd -a cce sslog- list (List of Acce ss Log Files)
This read-only attribute, which cannot be s et, provides a lis t of access log files used in access log
rotation.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values
Default Value None
Syntax DirectoryString
Example nsslapd-accesslog-list: accesslog2,accesslog3
2.3.1.4 . nsslapd-accesslog- logb uffe ring (Log B uffe ring)
When s et to o ff, the s erver writes all access log entries directly to disk. Buffering allows the server to
use access logging even when under a heavy load without impacting performance. However, when
debugging, it is s ometimes useful to disable buffering in order to s ee the operations and their results
18 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 19

right away instead of having to wait for the log entries to be flushed to the file. Disabling log buffering can
severely impact performance in heavily loaded servers.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-accesslog-logbuffering: off
2.3.1.5. nsslapd- accesslog-logexpira t iont ime (Acce ss Log Expira t ion Time )
This attribute s pecifies the maximum age that a log file is allowed to reach before it is deleted. This
attribute supplies only the number of units. The units are provided by the nsslapd-accesslog-
logexpirationtimeunit attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 to the maximum 32 bit integer value
(214 74 8364 7)
A value of -1 or 0 means that the log never
expires .
Default Value -1
Syntax Integer
Example nsslapd-accesslog-logexpirationtime: 2
2.3.1.6. nsslapd- accesslog-logexpira t iont ime unit (Access Log Expiration T ime Unit)
This attribute s pecifies the units for nsslapd-accesslog-logexpirationtime attribute. If the unit is
unknown by the s erver, then the log never expires.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day
Default Value month
Syntax DirectoryString
Example nsslapd-accesslog-logexpirationtimeunit: week
2.3.1.7. nsslapd- accesslog-logging-enabled (Acce ss Log Enable Logging)
Disables and enables accesslog logging but only in conjunction with the nsslapd-accesslog attribute
that s pecifies the path and parameter of the log used to record each databas e acces s.
For acces s logging to be enabled, this attribute must be switched to on, and the nsslapd-accesslog
configuration attribute must have a valid path and parameter. The table lists the four poss ible
combinations of values for thes e two configuration attributes and their outcome in terms of dis abling or
enabling of acces s logging.
Table 2 .3. dse.ldif At t ribu tes
Attribut e Valu e Logging Ena ble d or Disab led
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
on
empty string
Disabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
on
filename
Enabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
off
empty string
Disabled
nsslapd-accesslog-loggingenabled
nsslapd-accesslog
off
filename
Disabled
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 19
Page 20

Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-accesslog-logging-enabled: off
2.3.1.8. nsslapd- accesslog-logmaxdiskspace (Access Log Maximum Disk Spa ce )
This attribute s pecifies the maximum amount of disk space in megabytes that the access logs are
allowed to consume. If this value is exceeded, the oldest access log is deleted.
When s etting a maximum disk space, cons ider the total number of log files that can be created due to log
file rotation. Also, remember that there are three different log files (acces s log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
to the total amount of disk space for the access log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the dis k space allowed to the access log is
unlimited in s ize.
Default Value -1
Syntax Integer
Example nsslapd-accesslog-logmaxdisks pace: 1000 00
2.3.1.9. nsslapd- accesslog-logminfree diskspace (Acce ss Log Minimum Fre e Disk Spa ce )
This attribute s ets the minimum allowed free disk space in megabytes . When the amount of free disk
space falls below the value specified on this attribute, the oldest access logs are deleted until enough
disk space is freed to s atisfy this attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value -1
Syntax Integer
Example nsslapd-accesslog-logminfreedis kspace: -1
2.3.1.10 . nsslapd-accesslog- logrot ationsync-e na ble d (Access Log Rot ation Sync Enabled)
This attribute s ets whether access log rotation is to be synchroniz ed with a particular time of the day.
Synchronizing log rotation this way can generate log files at a specified time during a day, such as
midnight to midnight every day. This makes analysis of the log files much eas ier because they then map
directly to the calendar.
For acces s log rotation to be synchronized with time-of-day, this attribute must be enabled with the
nsslapd-accesslog-logrotationsynchour and nsslapd-accesslog-logrotationsyncmin
attribute values set to the hour and minute of the day for rotating log files.
For example, to rotate acces s log files every day at midnight, enable this attribute by setting its value to
on, and then set the values of the nsslapd-accesslog-logrotationsynchour and nsslapd-
accesslog-logrotationsyncmin attributes to 0.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-accesslog-logrotationsync-enabled: on
2.3.1.11 . nsslapd-accesslog- logrot ationsynchour (Acce ss Log Rota t ion S ync Ho ur)
This attribute s ets the hour of the day for rotating access logs . This attribute must be us ed in
conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-
logrotationsyncmin attributes.
20 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 21

Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 23
Default Value 0
Syntax Integer
Example nsslapd-accesslog-logrotationsynchour: 23
2.3.1.12 . nsslapd-accesslog- logrot ationsyncmin (Acce ss L og Rota t ion S ync Minut e )
This attribute s ets the minute of the day for rotating acces s logs. T his attribute must be used in
conjunction with nsslapd-accesslog-logrotationsync-enabled and nsslapd-accesslog-
logrotationsynchour attributes .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 59
Default Value 0
Syntax Integer
Example nsslapd-accesslog-logrotationsyncmin: 30
2.3.1.13. nssla pd- a cce sslog-logrota t iont ime (Acce ss Log Rota tion T ime )
This attribute s ets the time between acces s log file rotations. T he acces s log is rotated when this time
interval is up, regardless of the current size of the access log. This attribute supplies only the number of
units. The units (day, week, month, and so forth) are given by the nsslapd-accesslog-
logrotationtimeunit attribute.
Although it is not recommended for performance reasons to s pecify no log rotation since the log grows
indefinitely, there are two ways of specifying this. Either s et the nsslapd-accesslog-maxlogsperdir
attribute value to 1 or set the nsslapd-accesslog-logrotationtime attribute to -1. The server
checks the nsslapd-accesslog-maxlogsperdir attribute first, and, if this attribute value is larger than
1, the s erver then checks the nsslapd-accesslog-logrotationtime attribute. See Section 2.3.1.16,
“ns slapd-acces slog-maxlogsperdir (Access Log Maximum Number of Log Files)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the time between acces s log file rotation is
unlimited.
Default Value 1
Syntax Integer
Example nsslapd-accesslog-logrotationtime: 10 0
2.3.1.14 . nssla pd- a cce sslog-logrota t iont ime unit (Access Log Rotat ion Time Unit)
This attribute s ets the units for the nsslapd-accesslog-logrotationtime attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day | hour | minute
Default Value day
Syntax DirectoryString
Example nsslapd-accesslog-logrotationtimeunit: week
2.3.1.15 . nsslapd-accesslog- maxlogsiz e (Acce ss Log Ma ximum Log Size )
This attribute s ets the maximum access log size in megabytes. When this value is reached, the access
log is rotated. That means the server starts writing log information to a new log file. If the nsslapd-
accesslog-maxlogsperdir attribute is set to 1, the s erver ignores this attribute.
When s etting a maximum log size, cons ider the total number of log files that can be created due to log
file rotation. Also, remember that there are three different log files (acces s log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
to the total amount of disk space for the access log.
Pa ra met e r De script ion
Entry DN cn=config
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 21
Page 22

Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means the log
file is unlimited in size.
Default Value 10 0
Syntax Integer
Example nsslapd-accesslog-maxlogsiz e: 100
2.3.1.16 . nsslapd-accesslog- maxlogsperdir (Access Log Ma ximum Numbe r of Log File s)
This attribute s ets the total number of access logs that can be contained in the directory where the
acces s log is s tored. Each time the access log is rotated, a new log file is created. When the number of
files contained in the access log directory exceeds the value s tored in this attribute, then the oldes t
vers ion of the log file is deleted. For performance reasons, Red Hat recommends not setting this value to
1 because the server does not rotate the log, and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-accesslog-logrotationtime
attribute to es tablish whether log rotation is specified. If the nsslapd-accesslog-logrotationtime
attribute has a value of -1, then there is no log rotation. See Section 2.3.1.13, “nsslapd-accesslog-
logrotationtime (Acces s Log Rotation T ime)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value 10
Syntax Integer
Example nsslapd-accesslog-maxlogsperdir: 10
2.3.1.17 . nsslapd-accesslog- mode (Access Log File Pe rmission)
This attribute s ets the access mode or file permiss ion with which acces s log files are to be created. The
valid values are any combination of 000 to 777 (thes e mirror the numbered or absolute UNIX file
permissions ). The value mus t be a 3-digit number, the digits varying from 0 through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit repres ents the owner's permissions , the second digit repres ents the
group's permissions, and the third digit represents everyone's permissions. When changing the default
value, remember that 000 does not allow access to the logs and that allowing write permissions to
everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log
rotates to a new file.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 00 0 through 777
Default Value 60 0
Syntax Integer
Example nsslapd-accesslog-mode: 600
2.3.1.18 . nsslapd-allow-una ut he nt ica te d- binds
An unauthenticated bind is a bind where the user supplies a username but not a pas sword. For
example, running an ld apsearch without supplying a password option:
/usr/lib/mozldap/ldapsearch -D "cn=directory m anager" -b "dc=example,dc=com" -s
sub "(objectclass=*)"
When unauthenticated binds are allowed, the bind attempt goes through as an anonymous bind
(as suming anonymous access is allowed).
22 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 23

The nsslapd-allow-unauthenticated-binds attribute sets whether to allow an unauthenticated bind
to succeed as an anonymous bind. By default, unauthenticated binds are disabled.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-allow-unauthenticated-binds : on
2.3.1.19 . nsslapd-at t ribute- na me- e xce pt ions
This attribute allows non-standard characters in attribute names to be used for backwards compatibility
with older servers, such as "_" in s chema-defined attributes.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-attribute-name-exceptions: on
2.3.1.20 . nsslapd-auditlog (Audit Log)
This attribute s ets the path and filename of the log used to record changes made to each databas e.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid filename
Default Value /var/log/dirs rv/slapd-instance_name/audit
Syntax DirectoryString
Example nsslapd-auditlog:
/var/log/dirsrv/slapd-instance_name/audit
For audit logging to be enabled, this attribute must have a valid path and parameter, and the nsslapd-
auditlog-logging-enabled configuration attribute must be s witched to on. T he table lists the four
possible combinations of values for these two configuration attributes and their outcome in terms of
disabling or enabling of audit logging.
Table 2 .4 . Possible Combinations for nsslapd-auditlog
Attribut es in dse.ldif Valu e Logging enabled or disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
on
empty string
Disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
on
filename
Enabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
off
empty string
Disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
off
filename
Disabled
2.3.1.21 . nsslapd-auditlog- list
Provides a list of audit log files.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values
Default Value None
Syntax DirectoryString
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 23
Page 24

Example nsslapd-auditlog-list: auditlog2,auditlog3
2.3.1.22 . nsslapd-auditlog- logexpira tiont ime (Audit Log Expira t ion T ime )
This attribute s ets the maximum age that a log file is allowed to be before it is deleted. T his attribute
supplies only the number of units. The units (day, week, month, and s o forth) are given by the nsslapd-
auditlog-logexpirationtimeunit attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 to the maximum 32 bit integer value
(214 74 8364 7)
A value of -1 or 0 means that the log never
expires .
Default Value -1
Syntax Integer
Example nsslapd-auditlog-logexpirationtime: 1
2.3.1.23. nssla pd- a udit log-loge xpirat iontimeunit (Audit Log Expira tion T ime Unit )
This attribute s ets the units for the nsslapd-auditlog-logexpirationtime attribute. If the unit is
unknown by the s erver, then the log never expires.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day
Default Value week
Syntax DirectoryString
Example nsslapd-auditlog-logexpirationtimeunit: day
2.3.1.24 . nssla pd- a udit log-logging- enab led (Audit L og E nable Logging)
Turns audit logging on and off.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-auditlog-logging-enabled: off
For audit logging to be enabled, this attribute must have a valid path and parameter and the nsslapd-
auditlog-logging-enabled configuration attribute must be s witched to on. T he table lists the four
possible combinations of values for these two configuration attributes and their outcome in terms of
disabling or enabling of audit logging.
Table 2 .5 . Possible combinations fo r nsslap d- audit log a nd nssla pd-a uditlog- logging- e nabled
Attribut e Valu e Logging enabled or disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
on
empty string
Disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
on
filename
Enabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
off
empty string
Disabled
nsslapd-auditlog-loggingenabled
nsslapd-auditlog
off
filename
Disabled
2.3.1.25 . nsslapd-auditlog- logmaxdiskspa ce (Aud it Log Maximum Disk Spa ce )
24 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 25

This attribute s ets the maximum amount of disk s pace in megabytes that the audit logs are allowed to
consume. If this value is exceeded, the oldest audit log is deleted.
When s etting a maximum disk space, cons ider the total number of log files that can be created due to log
file rotation. Also remember that there are three different log files (access log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
with the total amount of disk s pace for the audit log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the dis k space allowed to the audit log is
unlimited in s ize.
Default Value -1
Syntax Integer
Example nsslapd-auditlog-logmaxdisks pace: 1000 0
2.3.1.26 . nsslapd-auditlog- logminfre e diskspace (Audit Log Minimum Fre e Disk Spa ce)
This attribute s ets the minimum permiss ible free disk space in megabytes . When the amount of free disk
space falls below the value specified by this attribute, the oldest audit logs are deleted until enough disk
space is freed to satis fy this attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 (unlimited) | 1 to the maximum 32 bit integer
value (2147483647)
Default Value -1
Syntax Integer
Example nsslapd-auditlog-logminfreedis kspace: -1
2.3.1.27 . nsslapd-auditlog- logrot ationsync-enabled (Audit Log Rot a tion Sync Enabled)
This attribute s ets whether audit log rotation is to be synchroniz ed with a particular time of the day.
Synchronizing log rotation this way can generate log files at a specified time during a day, such as
midnight to midnight every day. This makes analysis of the log files much eas ier because they then map
directly to the calendar.
For audit log rotation to be synchronized with time-of-day, this attribute must be enabled with the
nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-logrotationsyncmin attribute
values set to the hour and minute of the day for rotating log files.
For example, to rotate audit log files every day at midnight, enable this attribute by setting its value to on,
and then set the values of the nsslapd-auditlog-logrotationsynchour and nsslapd-auditlog-
logrotationsyncmin attributes to 0 .
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-auditlog-logrotationsync-enabled: on
2.3.1.28 . nsslapd-auditlog- logrot ationsynchour (Aud it Log Rotat ion Sync Hour)
This attribute s ets the hour of the day for rotating audit logs . This attribute must be used in conjunction
with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-logrotationsyncmin
attributes.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 23
Default Value None (becaus e nsslapd-auditlog-
logrotationsync-enabled is off)
Syntax Integer
Example nsslapd-auditlog-logrotationsynchour: 23
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 25
Page 26

2.3.1.29 . nsslapd-auditlog- logrot ationsyncmin (Audit Log Rotat ion Sync Minute )
This attribute s ets the minute of the day for rotating audit logs. T his attribute must be used in
conjunction with nsslapd-auditlog-logrotationsync-enabled and nsslapd-auditlog-
logrotationsynchour attributes .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 59
Default Value None (becaus e nsslapd-auditlog-
logrotationsync-enabled is off)
Syntax Integer
Example nsslapd-auditlog-logrotationsyncmin: 30
2.3.1.30. nssla pd- a udit log-logrotat iontime (Audit Log Rota t ion Time )
This attribute s ets the time between audit log file rotations. The audit log is rotated when this time
interval is up, regardless of the current size of the audit log. This attribute supplies only the number of
units. The units (day, week, month, and so forth) are given by the nsslapd-auditlog-
logrotationtimeunit attribute. If the nsslapd-auditlog-maxlogsperdir attribute is s et to 1, the
server ignores this attribute.
Although it is not recommended for performance reasons to s pecify no log rotation, as the log grows
indefinitely, there are two ways of specifying this. Either s et the nsslapd-auditlog-maxlogsperdir
attribute value to 1 or set the nsslapd-auditlog-logrotationtime attribute to -1. T he server checks
the nsslapd-auditlog-maxlogsperdir attribute firs t, and, if this attribute value is larger than 1, the
server then checks the nsslapd-auditlog-logrotationtime attribute. See Section 2.3.1.33,
“ns slapd-auditlog-maxlogsperdir (Audit Log Maximum Number of Log Files)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the time between audit log file rotation is
unlimited.
Default Value 1
Syntax Integer
Example nsslapd-auditlog-logrotationtime: 10 0
2.3.1.31. nssla pd- a udit log-logrotat iontime unit (Audit Log Rot ation T ime Unit)
This attribute s ets the units for the nsslapd-auditlog-logrotationtime attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day | hour | minute
Default Value week
Syntax DirectoryString
Example nsslapd-auditlog-logrotationtimeunit: day
2.3.1.32. nssla pd- a udit log-maxlogsize (Audit Log Ma ximum Log Siz e)
This attribute s ets the maximum audit log size in megabytes. When this value is reached, the audit log is
rotated. That means the server s tarts writing log information to a new log file. If nsslapd-auditlog-
maxlogsperdir to 1, the s erver ignores this attribute.
When s etting a maximum log size, cons ider the total number of log files that can be created due to log
file rotation. Also, remember that there are three different log files (acces s log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
to the total amount of disk space for the audit log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means the log
file is unlimited in size.
Default Value 10 0
Syntax Integer
Example nsslapd-auditlog-maxlogsiz e: 50
26 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 27

2.3.1.33. nsslapd-auditlog- maxlogsperdir (Audit Log Ma ximum Numbe r of Log File s)
This attribute s ets the total number of audit logs that can be contained in the directory where the audit
log is stored. Each time the audit log is rotated, a new log file is created. When the number of files
contained in the audit log directory exceeds the value stored on this attribute, then the oldest version of
the log file is deleted. The default is 1 log. If this default is accepted, the server will not rotate the log,
and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-auditlog-logrotationtime
attribute to es tablish whether log rotation is specified. If the nsslapd-auditlog-logrotationtime
attribute has a value of -1, then there is no log rotation. See Section 2.3.1.30, “ns slapd-auditlog-
logrotationtime (Audit Log Rotation T ime)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value 1
Syntax Integer
Example nsslapd-auditlog-maxlogsperdir: 10
2.3.1.34 . nsslapd-auditlog- mode (Audit Log File Pe rmission)
This attribute s ets the access mode or file permiss ions with which audit log files are to be created. The
valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file
permissions . The value must be a combination of a 3-digit number, the digits varying from 0 through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit repres ents the owner's permissions , the second digit repres ents the
group's permissions, and the third digit represents everyone's permissions. When changing the default
value, remember that 000 does not allow access to the logs and that allowing write permissions to
everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log
rotates to a new file.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 00 0 through 777
Default Value 60 0
Syntax Integer
Example nsslapd-auditlog-mode: 600
2.3.1.35. nssla pd- ce rt dir (Certificat e and Ke y Dat abase Dire ct ory)
This is the full path to the directory holding the certificate and key databases for a Directory Server
instance. This directory must contain only the certificate and key databases for this instance and no
other instances. T his directory must be owned and allow read-write access for the server user ID. No
other user should have read-right acces s to this directory. The default location is the configuration file
directory, /etc/dirsrv/slap d-instance_name.
Changes to this value will not take effect until the server is res tarted.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Absolute path to any directory which is owned by
the s erver user ID and only allows read and write
acces s to the server user ID
Default Value /etc/dirsrv/slapd-instance_name
Syntax DirectoryString
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 27
Page 28

Example /etc/dirsrv/s lapd-phonebook
2.3.1.36. nssla pd- ce rt map-basedn (Certificate Ma p Sea rch Ba se )
This attribute can be us ed when client authentication is performed us ing SSL certificates in order to
avoid limitations of the security subsystem certificate mapping, configured in the cer tmap.co nf file.
Depending on the cer tma p.conf configuration, the certificate mapping may be done us ing a directory
subtree s earch based at the root DN. If the search is based at the root DN, then the nsslapd-certmap-
basedn attribute may force the search to be based at some entry other than the root. The valid value for
this attribute is the DN of the suffix or subtree to use for certificate mapping. For further information on
configuring for SSL, see the " Managing SSL" chapter in the Directory Server Administrator's Guide.
2.3.1.37. nssla pd- config
This read-only attribute is the config DN.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid configuration DN
Default Value
Syntax DirectoryString
Example nsslapd-config: cn=config
2.3.1.38. nssla pd- connt ablesize
This attribute s ets the connection table siz e, which determines the total number of connections
supported by the s erver.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Operating-system dependent
Default Value T he default value is the sys tem's max
descriptors , which can be configured using the
Section 2.3.1.77, “ns slapd-maxdescriptors
(Maximum File Des criptors)” attribute.
Syntax Integer
Example nsslapd-conntablesize: 40 93
Increase the value of this attribute if Directory Server is refusing connections because it is out of
connection slots. When this occurs, the Directory Server's error log file records the mess age N ot
listening for new connection s -- too m any fds open.
A server restart is required for the change to take effect.
It may be neces sary to increase the operating s ystem limits for the number of open files and number of
open files per process, and it may be neces sary to increase the ulimi t for the number of open files
(ulimit -n) in the shell that starts the Directory Server. See Section 2.3.1.77, “nss lapd-maxdescriptors
(Maximum File Des criptors)” for more information.
2.3.1.39. nssla pd- count ers
The nsslapd-counters attribute enables and dis ables Directory Server databas e and server
performance counters.
There can be a performance impact by keeping track of the larger counters . Turning off 64-bit integers
for counters can have a minimal improvement on performance, although it negatively affects long term
statistics tracking.
This parameter is enabled by default. To disable counters , stop the Directory Server, edit the dse.ldif
file directly, and restart the s erver.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-counters: on
2.3.1.4 0. nssla pd- csnlogging
28 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 29

This attribute s ets whether change sequence numbers (CSNs ), when available, are to be logged in the
acces s log. By default, CSN logging is turned on.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-csnlogging: on
2.3.1.4 1. nssla pd- ds4 -compa tible-schema
Makes the schema in cn=schem a compatible with 4.x vers ions of Directory Server.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-ds4 -compatible-schema: off
2.3.1.4 2. nssla pd- e nquot e- sup-oc (Enable Superior O bje ct Class Enquot ing)
This attribute is deprecated and will be removed in a future vers ion of Directory Server.
This attribute controls whether quoting in the ob jectcla ss attributes contained in the cn= schema
entry conforms to the quoting specified by Internet draft RFC 2252. By default, the Directory Server
conforms to RFC 2252, which indicates that this value s hould not be quoted. Only very old clients need
this value set to on, so leave it off.
Turning this attribute on or off does not affect Directory Server Cons ole.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-enquote-sup-oc: off
2.3.1.4 3. nsslapd-errorlog (Error Lo g)
This attribute s ets the path and filename of the log used to record error mess ages generated by the
Directory Server. These mess ages can describe error conditions , but more often they contain
informative conditions , such as:
Server startup and s hutdown times.
The port number that the server uses .
This log contains differing amounts of information depending on the current setting of the Log Level
attribute. See Section 2.3.1.44, “nsslapd-errorlog-level (Error Log Level)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid filename
Default Value /var/log/dirs rv/slapd-instance_name/errors
Syntax DirectoryString
Example nsslapd-errorlog:
/var/log/dirsrv/slapd-instance_name/errors
For error logging to be enabled, this attribute must have a valid path and filename, and the nsslapd-
errorlog-logging-enabled configuration attribute must be s witched to on. T he table lists the four
possible combinations of values for these two configuration attributes and their outcome in terms of
disabling or enabling of error logging.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 29
Page 30

Table 2 .6 . Possible Combina t ions for nssla pd- e rrorlog Configuration At tribut e s
Attribut es in dse.ldif Valu e Logging enabled or disabled
nsslapd-errorlog-loggingenabled
nsslapd-errorlog
on
empty string
Disabled
nsslapd-errorlog-loggingenabled
nsslapd-errorlog
on
filename
Enabled
nsslapd-errorlog-loggingenabled
nsslapd-errorlog
off
empty string
Disabled
nsslapd-errorlog-loggingenabled
nsslapd-errorlog
off
filename
Disabled
2.3.1.4 4 . nsslap d- er rorlog- le vel (Error Log Level)
This attribute s ets the level of logging for the Directory Server. The log level is additive; that is ,
specifying a value of 3 includes both levels 1 and 2.
The default value for nsslapd-errorlog-level is 16 384.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values
1 — T race function calls. Logs a message
when the server enters and exits a function.
2 — Debug packet handling.
4 — Heavy trace output debugging.
8 — Connection management.
16 — Print out packets s ent/received.
32 — Search filter processing.
64 — Config file proces sing.
128 — Access control list process ing.
10 24 — Log communications with shell
databases .
20 48 — Log entry parsing debugging.
4096 — Housekeeping thread debugging.
8192 — Replication debugging.
16384 — Default level of logging us ed for
critical errors and other messages that are
always written to the error log; for example,
server s tartup messages. Mess ages at this
level are always included in the error log,
regardless of the log level setting.
32768 — Database cache debugging.
65536 — Server plug-in debugging. It writes
an entry to the log file when a server plug-in
calls slapi -log-error.
1310 72 — Micros econd resolution for
timestamps instead of the default s econds.
262144 — Access control summary
information, much less verbose than level
128. This value is recommended for us e
when a summary of access control
processing is needed. Use 128 for very
detailed proces sing messages.
Default Value 16384
Syntax Integer
Example nsslapd-errorlog-level: 8192
2.3.1.4 5. nssla pd- e rrorlog -list
This read-only attribute provides a list of error log files.
Pa ra met e r De script ion
30 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 31

Entry DN cn=config
Valid Values
Default Value None
Syntax DirectoryString
Example nsslapd-errorlog-list: errorlog2,errorlog3
2.3.1.4 6. nssla pd- e rrorlog -loge xpirat iontime (Error Log Expiration T ime)
This attribute s ets the maximum age that a log file is allowed to reach before it is deleted. This attribute
supplies only the number of units. The units (day, week, month, and s o forth) are given by the nsslapd-
errorlog-logexpirationtimeunit attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 to the maximum 32 bit integer value
(214 74 8364 7)
A value of -1 or 0 means that the log never
expires .
Default Value -1
Syntax Integer
Example nsslapd-errorlog-logexpirationtime: 1
2.3.1.4 7. nssla pd- e rrorlog -loge xpirat iontime unit (Error Log Expira t ion Time Unit )
This attribute s ets the units for the nsslapd-errorlog-logexpirationtime attribute. If the unit is
unknown by the s erver, then the log never expires.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day
Default Value month
Syntax DirectoryString
Example nsslapd-errorlog-logexpirationtimeunit: week
2.3.1.4 8. nssla pd- e rrorlog -loggin g- enabled (Enable E rror Logging)
Turns error logging on and off.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-errorlog-logging-enabled: on
2.3.1.4 9. nssla pd- e rrorlog -logmaxdiskspace (Error Log Ma ximum D isk Space)
This attribute s ets the maximum amount of disk s pace in megabytes that the error logs are allowed to
consume. If this value is exceeded, the oldest error log is deleted.
When s etting a maximum disk space, cons ider the total number of log files that can be created due to log
file rotation. Also, remember that there are three different log files (acces s log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
to the total amount of disk space for the error log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the dis k space allowed to the error log is
unlimited in s ize.
Default Value -1
Syntax Integer
Example nsslapd-errorlog-logmaxdis kspace: 100 00
2.3.1.50 . nsslapd-errorlog- logminfre ediskspace (E rror Log Minimum Fre e Disk Spa ce )
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 31
Page 32

This attribute s ets the minimum allowed free disk space in megabytes . When the amount of free disk
space falls below the value specified on this attribute, the oldest error log is deleted until enough disk
space is freed to satis fy this attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 (unlimited) | 1 to the maximum 32 bit integer
value (2147483647)
Default Value -1
Syntax Integer
Example nsslapd-errorlog-logminfreedisks pace: -1
2.3.1.51 . nsslapd-errorlog- logrot ationsync-e na ble d (Error Log Rot a tion Sync E nabled)
This attribute s ets whether error log rotation is to be s ynchronized with a particular time of the day.
Synchronizing log rotation this way can generate log files at a specified time during a day, such as
midnight to midnight every day. This makes analysis of the log files much eas ier because they then map
directly to the calendar.
For error log rotation to be synchroniz ed with time-of-day, this attribute mus t be enabled with the
nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-logrotationsyncmin attribute
values set to the hour and minute of the day for rotating log files.
For example, to rotate error log files every day at midnight, enable this attribute by setting its value to o n,
and then set the values of the nsslapd-errorlog-logrotationsynchour and nsslapd-errorlog-
logrotationsyncmin attributes to 0 .
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-errorlog-logrotations ync-enabled: on
2.3.1.52 . nsslapd-errorlog- logrot ationsynchour (Er ror Log Rotat ion Sync Hour)
This attribute s ets the hour of the day for rotating error logs. T his attribute must be used in conjunction
with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-logrotationsyncmin
attributes.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 23
Default Value 0
Syntax Integer
Example nsslapd-errorlog-logrotations ynchour: 23
2.3.1.53. nssla pd- e rro rlog-logrota t ionsyncmin (Error Log Rot a tion Sync Minut e)
This attribute s ets the minute of the day for rotating error logs . This attribute must be used in
conjunction with nsslapd-errorlog-logrotationsync-enabled and nsslapd-errorlog-
logrotationsynchour attributes .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 through 59
Default Value 0
Syntax Integer
Example nsslapd-errorlog-logrotations yncmin: 30
2.3.1.54 . nssla pd- e rro rlog-logrota t iont ime (Error Log Rotat ion Time)
This attribute s ets the time between error log file rotations . The error log is rotated when this time
interval is up, regardless of the current size of the error log. T his attribute supplies only the number of
units. The units (day, week, month, and so forth) are given by the nsslapd-errorlog-
logrotationtimeunit (Error Log Rotation T ime Unit) attribute.
Although it is not recommended for performance reasons to s pecify no log rotation, as the log grows
indefinitely, there are two ways of specifying this. Either s et the nsslapd-errorlog-maxlogsperdir
32 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 33

attribute value to 1 or set the nsslapd-errorlog-logrotationtime attribute to -1. T he server checks
the nsslapd-errorlog-maxlogsperdir attribute firs t, and, if this attribute value is larger than 1, the
server then checks the nsslapd-errorlog-logrotationtime attribute. See Section 2.3.1.57,
“ns slapd-errorlog-maxlogs perdir (Maximum Number of Error Log Files)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7), where a value of -1 means that
the time between error log file rotation is
unlimited).
Default Value 1
Syntax Integer
Example nsslapd-errorlog-logrotationtime: 100
2.3.1.55 . nsslapd-errorlog- logrot ationtimeunit (Error Log Rotat ion Time Unit )
This attribute s ets the units for nsslapd-errorlog-logrotationtime (Error Log Rotation T ime). If the
unit is unknown by the s erver, then the log never expires.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values month | week | day | hour | minute
Default Value week
Syntax DirectoryString
Example nsslapd-errorlog-logrotationtimeunit: day
2.3.1.56 . nsslapd-errorlog- maxlogsiz e (Ma ximum Er ror Log Size)
This attribute s ets the maximum error log size in megabytes. When this value is reached, the error log is
rotated, and the s erver starts writing log information to a new log file. If nsslapd-errorlog-
maxlogsperdir is s et to 1 , the server ignores this attribute.
When s etting a maximum log size, cons ider the total number of log files that can be created due to log
file rotation. Also, remember that there are three different log files (acces s log, audit log, and error log)
maintained by the Directory Server, each of which cons umes disk s pace. Compare these considerations
to the total amount of disk space for the error log.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 | 1 to the maximum 32 bit integer value
(214 74 8364 7) where a value of -1 means the log
file is unlimited in size.
Default Value 10 0
Syntax Integer
Example nsslapd-errorlog-maxlogs ize: 10 0
2.3.1.57 . nsslapd-errorlog- maxlogsperdir (Maximum Number of Error Log Files)
This attribute s ets the total number of error logs that can be contained in the directory where the error
log is stored. Each time the error log is rotated, a new log file is created. When the number of files
contained in the error log directory exceeds the value stored on this attribute, then the oldes t version of
the log file is deleted. The default is 1 log. If this default is accepted, the server does not rotate the log,
and it grows indefinitely.
If the value for this attribute is higher than 1, then check the nsslapd-errorlog-logrotationtime
attribute to es tablish whether log rotation is specified. If the nsslapd-errorlog-logrotationtime
attribute has a value of -1, then there is no log rotation. See Section 2.3.1.54, “ns slapd-errorlog-
logrotationtime (Error Log Rotation Time)” for more information.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value 1
Syntax Integer
Example nsslapd-errorlog-maxlogs perdir: 10
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 33
Page 34

2.3.1.58 . nsslapd-errorlog- mode (Error Log File Pe rmission)
This attribute s ets the access mode or file permiss ions with which error log files are to be created. The
valid values are any combination of 000 to 777 since they mirror numbered or absolute UNIX file
permissions . That is, the value must be a combination of a 3-digit number, the digits varying from 0
through 7:
0 - None
1 - Execute only
2 - Write only
3 - Write and execute
4 - Read only
5 - Read and execute
6 - Read and write
7 - Read, write, and execute
In the 3-digit number, the first digit repres ents the owner's permissions , the second digit repres ents the
group's permissions, and the third digit represents everyone's permissions. When changing the default
value, remember that 000 does not allow access to the logs and that allowing write permissions to
everyone can result in the logs being overwritten or deleted by anyone.
The newly configured access mode only affects new logs that are created; the mode is set when the log
rotates to a new file.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 00 0 through 777
Default Value 60 0
Syntax Integer
Example nsslapd-errorlog-mode: 600
2.3.1.59 . nsslapd-groupe valnestleve l
This attribute is deprecated, and documented here only for historical purposes.
The Access Control Plug-in does not use the value specified by the nsslapd-groupevalnestlevel
attribute to set the number of levels of nesting that access control performs for group evaluation.
Instead, the number of levels of nesting is hard-coded as 5.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 5
Default Value 5
Syntax Integer
Example nsslapd-groupevalnestlevel: 5
2.3.1.60 . nsslapd-idle timeout (De fa ult Idle T imeout )
This attribute s ets the amount of time in seconds after which an idle LDAP client connection is closed by
the s erver. A value of 0 means that the server never closes idle connections. This s etting applies to all
connections and all us ers. Idle timeout is enforced when the connection table is walked, when poll()
does not return z ero. T herefore, a server with a single connection never enforces the idle timeout.
Use the nsIdleTimeout operational attribute, which can be added to user entries, to override the value
assigned to this attribute. For details, see the " Setting Res ource Limits Bas ed on the Bind DN" section in
the Directory Server Administrator's Guide.
NOT E
For very large databases, with millions of entries, this attribute must have a high enough value
that the online initialization proces s can complete or replication will fail when the connection to the
server times out. Alternatively, the nsIdleTimeout attribute can be s et to a high value on the
entry used as the supplier bind DN.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to the maximum 32 bit integer value
(214 74 8364 7)
34 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 35

Default Value 0
Syntax Integer
Example nsslapd-idletimeout: 0
2.3.1.61 . nsslapd-inst ancedir (Inst ance Direct or y)
This attribute is deprecated. T here are now s eparate configuration parameters for instance-specific
paths , such as nsslapd-certdir and nsslapd-lockdir. See the documentation for the specific
directory path that is set.
2.3.1.62 . nsslapd-ioblocktimeout (IO Block Time O ut )
This attribute s ets the amount of time in milliseconds after which the connection to a stalled LDAP client
is closed. An LDAP client is considered to be stalled when it has not made any I/O progres s for read or
write operations .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to the maximum 32 bit integer value
(214 74 8364 7) in ticks
Default Value 180 0 00 0
Syntax Integer
Example nsslapd-ioblocktimeout: 180 000 0
2.3.1.63. nssla pd- la st mod (T rack Modification T ime)
This attribute s ets whether the Directory Server maintains the modification attributes for Directory Server
entries. These are operational attributes . These attributes include:
m odi fiersNa me - T he distinguished name of the person who last modified the entry.
m odi fyT im estam p - The timestamp, in GMT format, for when the entry was last modified.
creator sNam e - T he dis tinguis hed name of the person who initially created the entry.
createT imestam p - The timestamp for when the entry was created in GMT format.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-lastmod: on
WARNING
This attribute s hould never be turned off. If the nsslapd-lastmod is set to off, then generating
nsUniqueIDs is also disabled, replication does not work, and other issues may arise.
If for some reason this attribute were s et to off, the solution is to export the database to ldif
(db 2ldif or db 2ldif.pl or from the console), set the value to on, and import the data. The
import process assigns each entry a unique id.
2.3.1.64 . nssla pd- ldapiautobind (Ena ble Aut obind)
The nsslapd-ldapiautobind sets whether the server will allow us ers to autobind to Directory Server
using LDAPI. Autobind maps the UID or GUID number of a system us er to a Directory Server us er, and
automatically authenticates the user to Directory Server based on those credentials . The Directory
Server connection occurs over UNIX socket.
Along with enabling autobind, configuring autobind requires configuring mapping entries. T he nsslapd-
ldapimaprootdn maps a root us er on the system to the Directory Manager. The nsslapdldapimaptoentries maps regular users to Directory Server users, bas ed on the parameters defined in
the nsslapd-ldapiuidnumbertype, nsslapd-ldapigidnumbertype, and nsslapd-
ldapientrysearchbase attributes.
Autobind can only be enabled if LDAPI is enabled, meaning the nsslapd-ldapilisten is on and the
nsslapd-ldapifilepath attribute is s et to an LDAPI socket.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 35
Page 36

Default Value off
Syntax DirectoryString
Example nsslapd-ldapiautobind: off
2.3.1.65 . nsslapd-ldapie nt ryse archb ase (Search Base for LD API Authenticat ion Ent rie s)
With autobind, it is possible to map s ystem users to Directory Server user entries, bas ed on the system
user's UID and GUID numbers. This requires setting Directory Server parameters for which attribute to
use for the UID number (nsslapd-ldapiuidnumbertype) and GUID number (nsslapd-
ldapigidnumbertype) and s etting the search bas e to use to search for matching user entries.
The nsslapd-ldapientrysearchbase gives the subtree to search for us er entries to use for autobind.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values DN
Default Value T he s uffix created when the server instance was
created, such as dc =example,dc=com
Syntax DN
Example nsslapd-ldapientrysearchbas e:
ou=people,dc=example,dc=om
2.3.1.66 . nsslapd-ldapifile pa t h (File Loca tion for LD API Socke t )
LDAPI connects a us er to an LDAP server over a UNIX socket rather than T CP. In order to configure
LDAPI, the server must be configured to communicate over a UNIX socket. The UNIX socket to us e is set
in the nsslapd-ldapifilepath attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any directory path
Default Value /var/run/dirsrv/s lapd-example.socket
Syntax Case-exact s tring
Example nsslapd-ldapifilepath: /var/run/s lapd-
example.socket
2.3.1.67 . nsslapd-ldapigidnumbe rt ype (At t ribute Mapping for S yst em G UID Number)
Autobind can be us ed to authenticate system us ers to the server automatically and connect to the
server us ing a UNIX socket. To map the system us er to a Directory Server us er for authentication, the
sys tem user's UID and GUID numbers should be mapped to be a Directory Server attribute. The
nsslapd-ldapigidnumbertype attribute points to the Directory Server attribute to map s ystem GUIDs
to us er entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and
nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is
enabled for regular us ers (nsslapd-ldapimaptoentries).
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any Directory Server attribute
Default Value gidNumber
Syntax DirectoryString
Example nsslapd-ldapigidnumbertype: gidNumber
2.3.1.68 . nsslapd-ldapilist e n (Enable LDAPI)
The nsslapd-ldapilisten enables LDAPI connections to the Directory Server. LDAPI allows us ers to
connect to the Directory Server over a UNIX socket rather than a standard T CP port. Along with enabling
LDAPI by setting nsslapd-ldapilisten to on, there must also be a UNIX socket set for LDAPI in the
nsslapd-ldapifilepath attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-ldapilisten: off
36 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 37

2.3.1.69 . nsslapd-ldapimaprootdn (Autobind Mapping for Root User)
With autobind, a sys tem user is mapped to a Directory Server us er and then automatically authenticated
to the Directory Server over a UNIX socket.
The root sys tem user (the user with a UID of 0) is mapped to whatever Directory Server entry is
specified in the nsslapd-ldapimaprootdn attribute.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any DN
Default Value cn= Directory Manager
Syntax DN
Example nsslapd-ldapimaprootdn: cn=Directory Manager
2.3.1.70 . nsslapd-ldapimaptoentries (Enable Au to bind Mapping for Regular Use rs)
With autobind, a sys tem user is mapped to a Directory Server us er and then automatically authenticated
to the Directory Server over a UNIX socket. T his mapping is automatic for root users, but it must be
enabled for regular s ystem users through the nsslapd-ldapimaptoentries attribute. Setting this
attribute to on enables mapping for regular s ystem users to Directory Server entries. If this attribute is
not enabled, then only root us ers can use autobind to authenticate to the Directory Server, and all other
users connect anonymously.
The mappings themselves are configured through the nsslapd-ldapiuidnumbertype and nsslapd-
ldapigidnumbertype attributes, which map Directory Server attributes to the user's UID and GUID
numbers .
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and
nsslapd-ldapifilepath) and autobind is enabled (nsslapd-ldapiautobind).
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-ldapimaptoentries: on
2.3.1.71 . nsslapd-ldapiuidnumbe rt ype
Autobind can be us ed to authenticate system us ers to the server automatically and connect to the
server us ing a UNIX socket. To map the system us er to a Directory Server us er for authentication, the
sys tem user's UID and GUID numbers must be mapped to be a Directory Server attribute. The
nsslapd-ldapiuidnumbertype attribute points to the Directory Server attribute to map s ystem UIDs to
user entries.
Users can only connect to the server with autobind if LDAPI is enabled (nsslapd-ldapilisten and
nsslapd-ldapifilepath), autobind is enabled (nsslapd-ldapiautobind), and autobind mapping is
enabled for regular us ers (nsslapd-ldapimaptoentries).
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any Directory Server attribute
Default Value uidNumber
Syntax DirectoryString
Example nsslapd-ldapiuidnumbertype: uidNumber
2.3.1.72 . nsslapd-listenhost (Listen to IP Addre ss)
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it
possible to limit listening to one interface of a multihomed machine). T here can be multiple IP address es
associated with a s ingle hostname, and these IP addresses can be a mix of both IPv4 and IPv6. This
parameter can be us ed to restrict the Directory Server instance to a single IP interface.
If a hostname is given as the nsslapd-listenhost value, then the Directory Server responds to
requests for every interface associated with the hostname. If a single IP interface (either IPv4 or IPv6) is
given as the nsslapd-listenhost value, Directory Server only res ponds to requests s ent to that
specific interface. Either an IPv4 or IPv6 address can be used.
The server has to be res tarted for changes to this attribute to go into effect.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 37
Page 38

Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any local hostname, IPv4 or IPv6 address
Default Value
Syntax DirectoryString
Example nsslapd-listenhost: ldap.example.com
NOT E
On HP-UX the hostname value can be a relocatable IP address.
2.3.1.73. nssla pd- localhost (Local Host )
This attribute s pecifies the host machine on which the Directory Server runs. This attribute is us ed to
create the referral URL that forms part of the MMR protocol. In a high-availability configuration with
failover nodes, that referral should point to the virtual name of the cluster, not the local hostname.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any fully qualified hos tname.
Default Value Hos tname of installed machine.
Syntax DirectoryString
Example nsslapd-localhos t: phonebook.example.com
2.3.1.74 . nssla pd- localuser (Local User )
This attribute s ets the us er as whom the Directory Server runs. The group as which the user runs is
derived from this attribute by examining the user's primary group. Should the user change, then all of the
instance-s pecific files and directories for this instance need to be changed to be owned by the new user,
using a tool such as chown.
The value for the nsslapd-localuser is s et initially when the s erver instance is configured.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid us er
Default Value
Syntax DirectoryString
Example nsslapd-localuser: nobody
2.3.1.75 . nsslapd-lockdir (Server Lock File Directory)
This is the full path to the directory the s erver uses for lock files. T he default value is
/var/lo ck/dir srv/slapd-instance_name. Changes to this value will not take effect until the server
is restarted.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Absolute path to a directory owned by the s erver
user ID with write access to the server ID
Default Value /var/lock/dirs rv/slapd-instance_name
Syntax DirectoryString
Example nsslapd-lockdir:
/var/lock/dirsrv/slapd-instance_name
2.3.1.76 . nsslapd-maxbersize (Maximum Message S ize )
Defines the maximum siz e in bytes allowed for an incoming mess age. T his limits the size of LDAP
requests that can be handled by the Directory Server. Limiting the size of requests prevents some kinds
of denial of service attacks.
The limit applies to the total size of the LDAP reques t. For example, if the request is to add an entry and
if the entry in the reques t is larger than two megabytes, then the add reques t is denied. Be cautious
before changing this attribute.
The server s hould be res tarted for changes in this attribute to take effect.
Pa ra met e r De script ion
38 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 39

Entry DN cn=config
Valid Range 0 - 2 gigabytes (2,147,483,647 bytes)
Zero 0 means that the default value should be
used.
Default Value 20 97152
Syntax Integer
Example nsslapd-maxbersize: 20 97152
2.3.1.77 . nsslapd-maxdescript ors (Ma ximum File D escript or s)
This attribute s ets the maximum, platform-dependent number of file des criptors that the Directory Server
tries to us e. A file descriptor is us ed whenever a client connects to the server and also for some server
activities , such as index maintenance. File des criptors are also used by acces s logs, error logs, audit
logs, database files (indexes and transaction logs ), and as sockets for outgoing connections to other
servers for replication and chaining.
The number of descriptors available for T CP/IP to serve client connections is determined by nsslapd-
conntablesize, and is equal to the nsslapd-maxdescriptors attribute minus the number of file
descriptors us ed by the server as specified in the nsslapd-reservedescriptors attribute for non-
client connections , such as index management and managing replication. The nsslapd-
reservedescriptors attribute is the number of file descriptors available for other uses as des cribed
above. See Section 2.3.1.89, “nss lapd-reservedescriptors (Res erved File Descriptors)”.
The number given here should not be greater than the total number of file descriptors that the operating
sys tem allows the ns-slapd process to use. This number differs depending on the operating s ystem.
If this value is s et too high, the Directory Server queries the operating sys tem for the maximum allowable
value, and then use that value. It also iss ues a warning in the error log. If this value is s et to an invalid
value remotely, by using the Directory Server Console or ldapmo dify, the server rejects the new
value, keep the old value, and respond with an error.
Some operating systems let users configure the number of file des criptors available to a proces s. See
the operating s ystem documentation for details on file descriptor limits and configuration. The dsktune
program (explained in the Directory Server Installation Guide) can be us ed to suggest changes to the
sys tem kernel or T CP/IP tuning attributes, including increasing the number of file descriptors if
neces sary. Increas ed the value on this attribute if the Directory Server is refusing connections because
it is out of file descriptors. When this occurs, the following mess age is written to the Directory Server's
error log file:
Not listening for new connections -- too m any fds open
See Section 2.3.1.38, “ns slapd-conntablesiz e” for more information about increas ing the number of
incoming connections.
NOT E
UNIX shells usually have configurable limits on the number of file descriptors. See the operating
sys tem documentation for further information about li mit and ulim it, as these limits can often
cause problems.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to 65535
Default Value 10 24
Syntax Integer
Example nsslapd-maxdescriptors : 1024
2.3.1.78 . nsslapd-maxsa sliosize (Maximum SASL Pa cket Size)
When a user is authenticated to the Directory Server over SASL GSS-API, the s erver must allocate a
certain amount of memory to the client to perform LDAP operations, according to how much memory the
client requests. It is pos sible for an attacker to send such a large packet s ize that it crashes the
Directory Server or ties it up indefinitely as part of a denial of service attack.
The packet siz e which the Directory Server will allow for SASL clients can be limited us ing the nsslapd-
maxsasliosize attribute. This attribute sets the maximum allowed SASL IO packet size that the s erver
will accept.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 39
Page 40

When an incoming SASL IO packet is larger than the nsslapd-maxsasliosize limit, the server
immediately disconnects the client and logs a mess age to the error log, so that an administrator can
adjus t the s etting if necessary.
This attribute value is specified in bytes .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range
-1 (unlimited) to the maximum 32-bit integer value
(214 74 8364 7) on 32-bit systems
-1 (unlimited) to the maximum 64-bit integer value
(92233720 36854 775807) on 64 -bit s ystems
Default Value 20 000 00 (2MB)
Syntax Integer
Example nsslapd-maxsas liosize: 5000 000
2.3.1.79 . nsslapd-maxt hrea dsperconn (Ma ximum T hre a ds per Con nection)
Defines the maximum number of threads that a connection should us e. For normal operations where a
client binds and only performs one or two operations before unbinding, use the default value. For
situations where a client binds and simultaneously is sues many requests, increase this value to allow
each connection enough resources to perform all the operations . This attribute is not available from the
server console.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to maximum threadnumber
Default Value 5
Syntax Integer
Example nsslapd-maxthreads perconn: 5
2.3.1.80 . nsslapd-nagle
When the value of this attribute is off, the T CP_NODELAY option is set so that LDAP responses (s uch
as entries or result messages) are sent back to a client immediately. When the attribute is turned on,
default TCP behavior applies; specifically, sending data is delayed so that additional data can be
grouped into one packet of the underlying network MTU siz e, typically 150 0 bytes for Ethernet.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-nagle: off
2.3.1.81 . nsslapd-out bound- lda p- io- t imeout
This attribute limits the I/O wait time for all outbound LDAP connections. The default is 3000 00
milliseconds (5 minutes). A value of 0 means that the server does not impose a limit on I/O wait time.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to the maximum 32-bit integer value
(214 74 8364 7)
Default Value 30 000 0
Syntax DirectoryString
Example nsslapd-outbound-ldap-io-timeout: 3000 00
2.3.1.82 . nsslapd-plug-in
This read-only attribute lists the DNs of the plug-in entries for the syntax and matching rule plug-ins
loaded by the s erver.
2.3.1.83. nssla pd- port (Port Numbe r)
This attribute gives the TCP/IP port number used for s tandard LDAP communications . To run SSL/TLS
over this port, use the Start T LS extended operation. This selected port must be unique on the host
4 0 Cha pter 2. Co re Server Con fig uration Reference
Page 41

sys tem; make sure no other application is attempting to use the same port number. Specifying a port
number of less than 1024 means the Directory Server has to be started as ro ot.
The server s ets its uid to the nsslapd-localuser value after startup. When changing the port number
for a configuration directory, the corresponding server instance entry in the configuration directory mus t
be updated.
The server has to be res tarted for the port number change to be taken into account.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to 65535
Default Value 389
Syntax Integer
Example nsslapd-port: 389
NOT E
Set the port number to zero (0) to dis able the LDAP port if the LDAPS port is enabled.
2.3.1.84 . nssla pd- pr ivate na mespaces
This read-only attribute contains the lis t of the private naming contexts cn =co nfig, cn=schem a, and
cn=m onitor.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values cn=config, cn=s chema, and cn= monitor
Default Value
Syntax DirectoryString
Example nsslapd-privatenamespaces: cn=config
2.3.1.85 . nsslapd-pwpolicy- loca l (Enable Subtr ee - and Use r- Le ve l Pa sswo rd P olicy)
Turns fine-grained (s ubtree- and user-level) pass word policy on and off.
If this attribute has a value of off, all entries (except for cn=Directory Manager) in the directory is
subjected to the global pass word policy; the server ignores any defined subtree/us er level password
policy.
If this attribute has a value of on, the server checks for pas sword policies at the subtree- and user-level
and enforce those policies.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-pwpolicy-local: off
2.3.1.86 . nsslapd-readonly (Rea d O nly)
This attribute s ets whether the whole server is in read-only mode, meaning that neither data in the
databases nor configuration information can be modified. Any attempt to modify a database in read-only
mode returns an error indicating that the server is unwilling to perform the operation.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-readonly: off
2.3.1.87 . nsslapd-referra l (Re fe rra l)
This multi-valued attribute specifies the LDAP URLs to be returned by the suffix when the server
receives a request for an entry not belonging to the local tree; that is, an entry whose suffix does not
match the value specified on any of the suffix attributes. For example, ass ume the server contains only
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 4 1
Page 42

entries:
ou=People,dc=exam ple,dc=com
but the request is for this entry:
ou=Groups,dc=example,dc=com
In this case, the referral would be passed back to the client in an attempt to allow the LDAP client to
locate a server that contains the requested entry. Although only one referral is allowed per Directory
Server instance, this referral can have multiple values.
NOT E
To use SSL and T LS communications, the referral attribute should be in the form
ldaps://server-location.
Start T LS does not support referrals.
For more information on managing referrals, see the " Configuring Directory Databases " chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid LDAP URL in the form ld ap://server-
location
Default Value
Syntax DirectoryString
Example nsslapd-referral: ldap://ldap.example.com
2.3.1.88 . nsslapd-referra lmode (Re fe rra l Mode )
When s et, this attribute sends back the referral for any request on any s uffix.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid LDAP URL in the form >l dap://server-
location
Default Value
Syntax DirectoryString
Example nsslapd-referralmode: ldap://ldap.example.com
2.3.1.89 . nsslapd-reservedescriptors (Re se rve d File D escriptors)
This attribute s pecifies the number of file descriptors that Directory Server res erves for managing nonclient connections , such as index management and managing replication. The number of file des criptors
that the server reserves for this purpos e subtracts from the total number of file des criptors available for
servicing LDAP client connections (See Section 2.3.1.77, “ns slapd-maxdes criptors (Maximum File
Descriptors )”).
Most installations of Directory Server should never need to change this attribute. However, consider
increas ing the value on this attribute if all of the following are true:
The server is replicating to a large number of cons umer servers (more than 10 ), and/or the server is
maintaining a large number of index files (more than 30).
The server is servicing a large number of LDAP connections .
There are error mess ages reporting that the server is unable to open file des criptors (the actual
error mess age differs depending on the operation that the server is attempting to perform), but these
error mess ages are not related to managing client LDAP connections .
Increasing the value on this attribute may res ult in more LDAP clients being unable to access the
directory. Therefore, the value on this attribute is increas ed, also increas e the value on the nsslapd-
maxdescriptors attribute. It may not be pos sible to increase the nsslapd-maxdescriptors value if
the s erver is already us ing the maximum number of file descriptors that the operating system allows a
process to use; see the operating system documentation for details. If this is the case, then reduce the
load on the server by causing LDAP clients to search alternative directory replicas. See Section 2.3.1.38,
“ns slapd-conntablesiz e” for information about file descriptor us age for incoming connections .
To assist in computing the number of file des criptors s et for this attribute, use the following formula:
4 2 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 43

nsslapd-reservedescriptor = 20 + (NldbmBackends * 4) + NglobalIndex +
ReplicationDescriptor + ChainingBackendDescriptors + PTADescriptors +
SSLDescriptors
NldbmBackends is the number of ldbm databases .
NglobalIndex is the total number of configured indexes for all databases including system indexes.
(By default 8 system indexes and 17 additional indexes per database).
ReplicationDescriptor is eight (8) plus the number of replicas in the s erver that can act as a supplier
or hub (NSupplierReplica).
ChainingBackendDescriptors is NchainingBackend times the nsOperationConnectionsLimit (a
chaining or database link configuration attribute; 10 by default).
PTADescriptors is 3 if PTA is configured and 0 if PT A is not configured.
SSLDescriptors is 5 (4 files + 1 listensocket) if SSL is configured and 0 if SSL is not configured.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to 65535
Default Value 64
Syntax Integer
Example nsslapd-reservedes criptors: 64
2.3.1.90 . nsslapd-return- exact- ca se (Re tu rn E xact Ca se)
Returns the exact cas e of attribute type names as reques ted by the client. Although LDAPv3-compliant
clients must ignore the case of attribute names, some client applications require attribute names to
match exactly the case of the attribute as it is listed in the schema when the attribute is returned by the
Directory Server as the result of a s earch or modify operation. However, most client applications ignore
the cas e of attributes; therefore, by default, this attribute is dis abled. Do not modify it unles s there are
legacy clients that can check the cas e of attribute names in results returned from the server.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-return-exact-case: off
2.3.1.91 . nsslapd-rewrit e-rfc127 4
This attribute is deprecated and will be removed in a later vers ion.
This attribute is used only for LDAPv2 clients that require attribute types to be returned with their RFC
1274 names. Set the value to o n for those clients. The default is off.
2.3.1.92 . nsslapd-rootdn (Ma na ge r D N)
This attribute s ets the dis tinguis hed name (DN) of an entry that is not subject to access control
res trictions , administrative limit restrictions for operations on the directory, or resource limits in general.
There does not have to be an entry corresponding to this DN, and by default there is not an entry for
this DN, thus values like cn=Directory Manager are acceptable.
For information on changing the root DN, see the "Creating Directory Entries" chapter in the Directory
Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid dis tinguis hed name
Default Value
Syntax DN
Example nsslapd-rootdn: cn=Directory Manager
2.3.1.93. nssla pd- ro ot pw (Root Pa ssword)
This attribute s ets the password as sociated with the Manager DN. When the root pass word is provided,
it is encrypted according to the encryption method selected for the nsslapd-rootpwstoragescheme
attribute. When viewed from the server console, this attribute shows the value * * * * * . When viewed
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 4 3
Page 44

attribute. When viewed from the server console, this attribute shows the value * * * * * . When viewed
from the d se.ldif file, this attribute shows the encryption method followed by the encrypted string of
the password. The example s hows the password as displayed in the dse.ldif file, not the actual
password.
WARNING
When the root DN is configured at server setup, a root pass word is required. However, it is
possible for the root pas sword to be deleted from dse.ldif by directly editing the file. In this
situation, the root DN can only obtain the same access to the directory is allowed for anonymous
acces s. Always make sure that a root pas sword is defined in dse.ld if when a root DN is
configured for the database. The pwdhash command-line utility can create a new root pass word.
For more information, see Section 7.3.12, “pwdhash (Prints Encrypted Pas swords)”.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid password encrypted by any one of the
encryption methods which are described in
Section 2.3.1.142, “pas swordStorageScheme
(Password Storage Scheme)”.
Default Value
Syntax DirectoryString {encryption_method
}encrypted_Password
Example nsslapd-rootpw: {SSHA}9Eko69APCJfF
2.3.1.94 . nssla pd- ro ot pwst oragescheme (Root Password St or age S che me)
This attribute s ets the encryption method used for the root pass word.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any encryption method as described in
Section 2.3.1.142, “pas swordStorageScheme
(Password Storage Scheme)”.
Default Value SSHA
Syntax DirectoryString
Example nsslapd-rootpws toragescheme: SSHA
2.3.1.95 . nsslapd-saslpath
Sets the abs olute path to the directory containing the Cyrus -SASL SASL2 plug-ins . On HP-UX sys tems,
the Directory Server cannot use the system SASL libraries becaus e they are either not provided or are
not the correct version. Setting this attribute allows the server to use custom or non-s tandard SASL
plug-in libraries . This is usually set correctly during ins tallation, and Red Hat strongly recommends not
changing this attribute. If the attribute is not present or the value is empty, this means the Directory
Server is us ing the system provided SASL plug-in libraries which are the correct vers ion.
If this parameter is set, the server us es the specified path for loading SASL plugins. If this parameter is
not s et, the server uses the S ASL_PATH environment variable. If neither nsslapd-saslpath or
SASL_PAT H are set, the server attempts to load SASL plugins from the default location,
/usr/lib/sasl2.
Changes made to this attribute will not take effect until the server is restarted.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Path to plugins directory.
Default Value Platform dependent
Syntax DirectoryString
Example nsslapd-sas lpath: /us r/lib/s asl2
2.3.1.96 . nsslapd-sche ma- ignore - trailing- spa ce s (Ig nore T ra iling Spaces in Object C lass
Names)
Ignores trailing s paces in object class names. By default, the attribute is turned off. If the directory
contains entries with object clas s values that end in one or more spaces, turn this attribute on. It is
preferable to remove the trailing spaces becaus e the LDAP standards do not allow them.
For performance reasons, server res tart is required for changes to take effect.
4 4 Cha pter 2. Co re Server Con fig uration Reference
Page 45

An error is returned by default when object classes that include trailing spaces are added to an entry.
Additionally, during operations such as add, modify, and import (when object class es are expanded and
missing superiors are added) trailing s paces are ignored, if appropriate. This means that even when
nsslapd-schema-ignore-trailing-spaces is on, a value s uch as top is not added if top is already
there. An error mess age is logged and returned to the client if an object class is not found and it
contains trailing spaces.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-schema-ignore-trailing-s paces : on
2.3.1.97 . nsslapd-sche macheck (Schema Checking)
This attribute s ets whether the database schema is enforced when entries are added or modified. When
this attribute has a value of on, Directory Server will not check the schema of existing entries until they
are modified. The databas e schema defines the type of information allowed in the database. The default
schema can be extended using the object class es and attribute types . For information on how to extend
the s chema us ing the Directory Server Cons ole, see the "Extending the Directory Schema" chapter in
the Directory Server Administrator's Guide.
WARNING
Red Hat s trongly discourages turning off s chema checking. This can lead to severe
interoperability problems. T his is typically used for very old or non-standard LDAP data that must
be imported into the Directory Server. If there are not a lot of entries that have this problem,
consider us ing the extensibleObj ect object class in those entries to dis able s chema
checking on a per entry basis .
NOT E
Schema checking works by default when database modifications are made using an LDAP client,
such as ldapm odify or when importing a database from LDIF using ldif 2db. If schema
checking is turned off, every entry has to be verified manually to see that they conform to the
schema. If schema checking is turned on, the server s ends an error message listing the entries
which do not match the schema. Ensure that the attributes and object class es created in the LDIF
statements are both spelled correctly and identified in dse.ldif. Either create an LDIF file in the
schema directory or add the elements to 99user.ldif.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-schemacheck: on
2.3.1.98 . nsslapd-sche madir
This is the absolute path to the directory containing the Directory Server instance-s pecific s chema files .
When the server starts up, it reads the schema files from this directory, and when the schema is
modified through LDAP tools, the s chema files in this directory are updated. T his directory must be
owned by the server user ID, and that user must have read and write permissions to the directory. The
default value is the schema subdirectory of the Directory Server instance-s pecific configuration directory,
/etc/di rsrv/slap d-instance_name/schema .
Changes made to this attribute will not take effect until the server is restarted.
2.3.1.99 . nsslapd-sche mar eplace
Determines whether modify operations that replace attribute values are allowed on the cn=sch em a
entry.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off | replication-only
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 4 5
Page 46

Default Value replication-only
Syntax DirectoryString
Example nsslapd-schemareplace: replication-only
2.3.1.10 0. nssla pd-securelistenhost
This attribute allows multiple Directory Server instances to run on a multihomed machine (or makes it
possible to limit listening to one interface of a multihomed machine). T here can be multiple IP address es
associated with a s ingle hostname, and these IP addresses can be a mix of both IPv4 and IPv6. This
parameter can be us ed to restrict the Directory Server instance to a single IP interface; this parameter
also specifically sets what interface to use for SSL/TLS traffic rather than regular LDAP connections .
If a hostname is given as the nsslapd-securelistenhost value, then the Directory Server res ponds to
requests for every interface associated with the hostname. If a single IP interface (either IPv4 or IPv6) is
given as the nsslapd-securelistenhost value, Directory Server only responds to requests sent to
that s pecific interface. Either an IPv4 or IPv6 addres s can be used.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any secure hostname, IPv4 or IPv6 address
Default Value
Syntax DirectoryString
Example nsslapd-securelistenhost: ldaps.example.com
2.3.1.10 1. nssla pd-securePort (Encr ypt ed Port Numbe r)
This attribute s ets the T CP/IP port number used for SSL/TLS communications . This selected port must
be unique on the host sys tem; make s ure no other application is attempting to use the s ame port
number. Specifying a port number of les s than 10 24 requires that Directory Server be started as root.
The server s ets its uid to the nsslapd-localuser value after startup.
The server only listens to this port if it has been configured with a private key and a certificate, and
nsslapd-security is set to on; otherwise, it does not listen on this port.
The server has to be res tarted for the port number change to be taken into account.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to 65535
Default Value 636
Syntax Integer
Example nsslapd-securePort: 636
2.3.1.10 2. nssla pd-securit y (Securit y)
This attribute s ets whether the Directory Server is to accept SSL/TLS communications on its encrypted
port. T his attribute should be set to on for secure connections. T o run with security on, the s erver must
be configured with a private key and s erver certificate in addition to the other SSL/TLS configuration.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsslapd-security: off
2.3.1.10 3. nsslapd- sizelimit (S ize Limit )
This attribute s ets the maximum number of entries to return from a search operation. If this limit is
reached, ns-slapd returns any entries it has located that match the search request, as well as an
exceeded siz e limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the number
found. To set a no limit value whereby the Directory Server waits indefinitely for the search to complete,
specify a value of -1 for this attribute in the dse.ldif file.
This limit applies to everyone, regardless of their organization.
4 6 Cha pter 2. Co re Server Con fig uration Reference
Page 47

NOT E
A value of -1 on this attribute in dse.ldif file is the s ame as leaving the attribute blank in the
server console, in that it causes no limit to be us ed. This cannot have a null value in dse.ldif
file, as it is not a valid integer. It is poss ible to s et it to 0, which returns size lim it exceeded
for every search.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value 20 00
Syntax Integer
Example nsslapd-siz elimit: 2000
2.3.1.10 4 . nsslapd- ssl- che ck- hostname (Ve rify Host na me for O ut bound C onnect ions)
This attribute s ets whether an SSL-enabled Directory Server should verify authenticity of a request by
matching the hostname agains t the value assigned to the common name (cn) attribute of the s ubject
name (subjectDN field) in the certificate being presented. By default, the attribute is set to on. If it is on
and if the hos tname does not match the cn attribute of the certificate, appropriate error and audit
mess ages are logged.
For example, in a replicated environment, messages similar to the following are logged in the supplier
server's log files if it finds that the peer server's hos tname does not match the name specified in its
certificate:
[DATE] - SSL alert: ldap_sasl_bind("",LDAP_SASL_EXTERNAL) 81 (Netscape runtime
error -12276 Unable to com municate securely with peer: requested domain name does not
m atch the server's certificate.)
[DATE] NSMMReplicationPlugin - agmt="cn=SSL Replication Agreem ent to host1"
(host1.example.com :636):
Replication bind with SSL client authentication failed:
LDAP error 81 (Can't contact LDAP server)
Red Hat recommends turning this attribute on to protect Directory Server's outbound SSL connections
agains t a man in the middle (MITM) attack.
NOT E>
DNS and reverse DNS must be set up correctly in order for this to work; otherwise, the server
cannot resolve the peer IP addres s to the hostname in the subject DN in the certificate.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsslapd-ss l-check-hostname: on
2.3.1.10 5. nssla pd-t hrea dnumber (T hrea d Number)
Defines the number of operation threads that the Directory Server creates at startup. T he nsslapdthreadnumber value s hould be increased if there are many directory clients performing time-cons uming
operations such as add or modify, as this ensures that there are other threads available for servicing
short-lived operations s uch as simple s earches. This value may also need increased if there are many
replication agreements or chained backends (database links). This attribute is not available from the
server console.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum number of threads supported
by the system
Default Value 30
Syntax Integer
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 4 7
Page 48

Example nsslapd-threadnumber: 60
2.3.1.10 6. nssla pd-t imelimit (Time Limit)
This attribute s ets the maximum number of seconds allocated for a search request. If this limit is
reached, Directory Server returns any entries it has located that match the search request, as well as an
exceeded time limit error.
When no limit is set, ns-slapd returns every matching entry to the client regardless of the time it takes .
To set a no limit value whereby Directory Server waits indefinitely for the s earch to complete, specify a
value of -1 for this attribute in the dse.ldif file. A value of zero (0) caus es no time to be allowed for
searches . The smallest time limit is 1 s econd.
NOT E
A value of -1 on this attribute in thedse.ldif is the s ame as leaving the attribute blank in the
server console in that it causes no limit to be used. However, a negative integer cannot be set in
this field in the server cons ole, and a null value cannot be used in the dse.ldif entry, as it is
not a valid integer.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range -1 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 360 0
Syntax Integer
Example nsslapd-timelimit: 3600
2.3.1.10 7. nssla pd-t mpdir
This is the absolute path of the directory the server uses for temporary files. T he directory must be
owned by the server user ID and the user must have read and write access. No other user ID should
have read or write acces s to the directory. The default value is /tmp.
Changes made to this attribute will not take effect until the server is restarted.
2.3.1.10 8. nssla pd-versionst ring
This attribute s ets the s erver version number. T he build data is automatically appended when the
vers ion string is displayed.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any valid s erver version number.
Default Value
Syntax DirectoryString
Example nsslapd-versionstring: Red Hat-Directory/8.1
2.3.1.10 9. nssla pd-wo rkingdir
This is the absolute path of the directory that the server uses as its current working directory after
startup. This is the value that the server would return as the value of the ge tcwd() function, and the
value that the s ystem process table shows as its current working directory. T his is the directory a core
file is generated in. The server us er ID must have read and write access to the directory, and no other
user ID should have read or write acces s to it. The default value for this attribute is the same directory
containing the error log, which is usually /var/log/di rsrv/slapd-instance_name.
Changes made to this attribute will not take effect until the server is restarted.
2.3.1.11 0. nsSSLclient a ut h (C lie nt Aut he nt ica tion)
This attribute s ets whether client authentication (also called certificate-bas ed authentication) is allowed
to the Directory Server. If this attribute is s et to required, then the Console cannot be set to require
SSL because certificate-based authentication is not supported in the Console.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values off | allowed | required
Default Value off
4 8 Cha pter 2. Co re Server Con fig uration Reference
Page 49

Syntax DirectoryString
Example nsSSLclientauth: allowed
2.3.1.11 1. passwordAllowCha ngeT ime
This attribute s pecifies the length of time that must pass before the user is allowed to change his
password.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any integer
Default Value
Syntax DirectoryString
Example passwordAllowChangeT ime: 5h
2.3.1.11 2. passwordChan ge (Pa ssword C ha nge )
Indicates whether users may change their passwords.
This can be abbreviated to pwdAllowUserChange.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example passwordChange: on
2.3.1.11 3. passwordC he ckSynt ax (Check Pa sswor d Syntax)
This attribute s ets whether the password syntax is checked before the pas sword is saved. The
password syntax checking mechanism checks that the pas sword meets or exceeds the pas sword
minimum length requirement and that the string does not contain any trivial words, such as the us er's
name or user ID or any attribute value s tored in the uid, cn, sn, givenname, ou, or mail attributes of the
user's directory entry.
Pass word syntax includes several different categories for checking:
Minimum number of digit characters (0 -9)
Minimum number of ASCII alphabetic characters , both upper- and lower-case
Minimum number of uppercase ASCII alphabetic characters
Minimum number of lowercas e ASCII alphabetic characters
Minimum number of special ASCII characters , such as !@ #$
Minimum number of 8-bit characters
Maximum number of times that the same character can be immediately repeated, such as aaa bbb
Minimum number of character categories required per password; a category can be upper- or lowercase letters , special characters, digits, or 8-bit characters
This can be abbreviated to pwdCheckSyntax.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example passwordCheckSyntax off
2.3.1.11 4 . passwordExp (Password Expira tion)
Indicates whether user passwords expire after a given number of s econds . By default, user pas swords
do not expire. Once pass word expiration is enabled, set the number of seconds after which the
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 4 9
Page 50

password expires us ing the passwordMaxAge attribute.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example passwordExp: on
2.3.1.11 5. passwordExpira tionT ime
This attribute s pecifies the length of time that pas ses before the user’s pas sword expires.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values Any date, in integers
Default Value none
Syntax GeneralizedTime
Example passwordExpirationT ime: 200 90 90 11953
2.3.1.11 6. passwordExpWar ned
This attribute is used to indicate that a password expiration warning has been sent to the user.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values true | false
Default Value none
Syntax DirectoryString
Example passwordExpWarned: true
2.3.1.11 7. passwordGraceLimit (Pa sswor d Expira tion)
This attribute is only applicable if pass word expiration is enabled. After the user's password has
expired, the s erver allows the user to connect for the purpose of changing the pass word. This is called
a grace login. The server allows only a certain number of attempts before completely locking out the
user. This attribute is the number of grace logins allowed. A value of 0 means the server does not allow
grace logins.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values 0 (off) to any reasonable integer
Default Value 0
Syntax Integer
Example passwordGraceLimit: 3
2.3.1.11 8. passwordGraceUserTime
This attribute counts the number of attempts the us er has made with the expired pas sword.
This is an operational attribute, meaning its value is managed by the s erver and the attribute is not
returned in default searches .
Pa ra met e r De script ion
Entry DN cn=config
Valid Values none to any reasonable integer
Default Value none
Syntax Integer
Example passwordGraceUs erT ime: 1
2.3.1.11 9. passwordHist ory (Pa ssword History)
Enables password history. Password his tory refers to whether us ers are allowed to reuse pass words .
By default, password history is disabled, and users can reus e passwords. If this attribute is set to on,
the directory s tores a given number of old pas swords and prevents users from reusing any of the
50 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 51

stored passwords. Set the number of old passwords the Directory Server s tores using the
passwordInHistory attribute.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example passwordHistory: on
2.3.1.12 0. passwordInHistory (Number of Passwords to Remembe r)
Indicates the number of pas swords the Directory Server s tores in history. Pass words that are stored in
history cannot be reused by users. By default, the password history feature is disabled, meaning that
the Directory Server does not s tore any old passwords, and so us ers can reuse passwords. Enable
password history using the passwordHistory attribute.
To prevent users from rapidly cycling through the number of pas swords that are tracked, use the
passwordMinAge attribute.
This can be abbreviated to pwdInHistory.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 2 to 24 pas swords
Default Value 6
Syntax Integer
Example passwordInHistory: 7
2.3.1.12 1. passwordIsG loba lPolicy (Password Policy a nd Re plicat ion )
This attribute controls whether password policy attributes are replicated.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example passwordIsGlobalPolicy: off
2.3.1.12 2. passwordKeepHistory
This attribute s ets whether a pas sword history is maintained for users.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values 0 (no his tory) or 1 (keep history)
Default Value 0
Syntax DirectoryString
Example passwordKeepHistory: 1
2.3.1.12 3. passwordLockout (Account Lockout )
Indicates whether users are locked out of the directory after a given number of failed bind attempts. By
default, users are not locked out of the directory after a series of failed bind attempts. If account lockout
is enabled, set the number of failed bind attempts after which the user is locked out us ing the
passwordMaxFailure attribute.
This can be abbreviated to pwdLockOut.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 51
Page 52

Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example passwordLockout: off
2.3.1.12 4 . passwordLockoutDur at ion (Lockout D ura t ion)
Indicates the amount of time in seconds during which users are locked out of the directory after an
account lockout. The account lockout feature protects agains t hackers who try to break into the directory
by repeatedly trying to guess a us er's pas sword. Enable and disable the account lockout feature using
the passwordLockout attribute.
This can be abbreviated to pwdLockoutDuration.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 360 0
Syntax Integer
Example passwordLockoutDuration: 3600
2.3.1.12 5. passwordMa xAge (Password Maximum Age)
Indicates the number of seconds after which user pas swords expire. To use this attribute, pas sword
expiration has to be enabled using the passwordExp attribute.
This can be abbreviated to pwdMaxAge.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 864 0 00 0 (10 0 days)
Syntax Integer
Example passwordMaxAge: 100
2.3.1.12 6. passwordMa xFa ilur e (Maximum Pa ssword Fa ilures)
Indicates the number of failed bind attempts after which a us er is locked out of the directory. By default,
account lockout is disabled. Enable account lockout by modifying the passwordLockout attribute.
This can be abbreviated to pwdMaxFailure.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to maximum integer bind failures
Default Value 3
Syntax Integer
Example passwordMaxFailure: 3
2.3.1.12 7. passwordMa xRepeat s (Password Synta x)
Maximum number of times the same character can appear s equentially in the pass word. Zero (0) is off.
Integer values reject any pass word which used a character more than that number of times ; for example,
1 rejects characters that are us ed more than once (aa) and 2 rejects characters used more than twice
(aa a).
Pa ra met e r De script ion
Entry DN cn=config
52 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 53

Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMaxRepeats : 1
2.3.1.12 8. passwordMin8B it (Pa ssword Synt ax)
This s ets the minimum number of 8-bit characters the password must contain.
NOT E
The 7-bit checking for userPassword must be disabled to use this.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMin8Bit: 0
2.3.1.12 9. passwordMinAge (Pa ssword Minimum Age )
Indicates the number of seconds that must pass before a user can change their pass word. Use this
attribute in conjunction with the passwordInHistory (number of passwords to remember) attribute to
prevent users from quickly cycling through pass words so that they can us e their old pas sword again. A
value of zero (0) means that the us er can change the pas sword immediately.
This can be abbreviated to pwdMaxFailure.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to valid maximum integer
Default Value 0
Syntax Integer
Example passwordMinAge: 150
2.3.1.130 . passwordMinAlphas (Pa sswor d Syntax)
This attribute s ets the minimum number of alphabetic characters password must contain.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMinAlphas: 4
2.3.1.131 . passwordMinCat egories (Pa sswor d Syntax)
This s ets the minimum number of character categories that are repres ented in the pas sword. The
categories are lower, upper, digit, special, and 8-bit. For example, if the value of this attribute were s et to
2, and the user tried to change the pas sword to aaaa a, the server would reject the pas sword because
it contains only lower cas e characters, and therefore contains characters from only one category. A
password of aAaAaA would pas s becaus e it contains characters from two categories, uppercase and
lowercas e. The default is 3, which means that if password syntax checking is enabled, valid passwords
have to have three categories of characters.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 5
Default Value 0
Syntax Integer
Example passwordMinCategories: 2
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 53
Page 54

2.3.1.132 . PasswordMinDigit s (Password Synt a x)
This s ets the minimum number of digits a pass word must contain.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMinDigits: 3
2.3.1.133. passwordMinLengt h (Password Minimum Length)
This attribute s pecifies the minimum number of characters that must be used in Directory Server user
password attributes. In general, shorter pass words are easier to crack. Directory Server enforces a
minimum pas sword of eight characters. T his is long enough to be difficult to crack but short enough that
users can remember the password without writing it down.
This can be abbreviated to pwdMinLength.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 2 to 512 characters
Default Value 6
Syntax Integer
Example passwordMinLength: 6
2.3.1.134 . Pa sswor dMinLowe rs (Pa sswor d Syntax)
This attribute s ets the minimum number of lower cas e letters password must contain.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMinLowers : 1
2.3.1.135 . PasswordMinSpecials (Pa ssword Synt ax)
This attribute s ets the minimum number of special, or not alphanumeric, characters a password must
contain.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMinSpecials: 1
2.3.1.136 . PasswordMinT oke nLength (Password Synt a x)
This attribute s ets the s mallest attribute value length that is used for trivial words checking. For example,
if the PasswordMinTokenLength is set to 3, then a givenname of DJ does not result in a policy that
rejects DJ from being in the password, but the policy rejects a pass word containing the givenname of
Bob.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to 64
Default Value 3
Syntax Integer
Example passwordMinTokenLength: 3
54 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 55

2.3.1.137 . PasswordMinUppers (Password Synt a x)
This s ets the minimum number of uppercas e letters pass word mus t contain.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to 64
Default Value 0
Syntax Integer
Example passwordMinUppers : 2
2.3.1.138 . passwordMust Change (Pa ssword Mu st Cha nge)
Indicates whether users must change their passwords when they first bind to the Directory Server or
when the password has been reset by the Manager DN.
This can be abbreviated to pwdMustChange.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example passwordMustChange: off
2.3.1.139 . passwordRe se tDur at ion
This attribute s ets the amount of time that mus t pas s after login failures before the s erver resets the
password retry count to z ero.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 60 0
Syntax Integer
Example passwordResetDuration: 60 0
2.3.1.14 0. passwordRe se tFailure Count (Re se t Pa sswor d Fa ilure Count After)
Indicates the amount of time in seconds after which the password failure counter res ets. Each time an
invalid password is sent from the user's account, the pas sword failure counter is incremented. If the
passwordLockout attribute is set to on, users are locked out of the directory when the counter reaches
the number of failures s pecified by the passwordMaxFailure attribute (within 600 seconds by default).
After the amount of time specified by the passwordLockoutDuration attribute, the failure counter is
res et to z ero (0).
This can be abbreviated to pwdFailureCountInterval.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 60 0
Syntax Integer
Example passwordResetFailureCount: 60 0
2.3.1.14 1. passwordRe t ryC ount
This attribute counts the number of cons ecutive failed attempts at entering the correct pass word.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 55
Page 56

This is an operational attribute, meaning its value is managed by the s erver and the attribute is not
returned in default searches .
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 0 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value 0
Syntax Integer
Example passwordRetryCount: 3
2.3.1.14 2. passwordS tora ge Scheme (Pa ssword S tora ge Scheme )
This attribute s ets the type of encryption us ed to store Directory Server passwords.
The following encryption types are s upported by the Directory Server:
CLEAR means the pas sword is stored in cleartext, with no hashing or encryption. This scheme must
be us ed in order to use SASL DIGEST-MD5.
SSHA (Salted Secure Hash Algorithm), the default, is the recommended method because it is the
most s ecure. T here are several bit sizes available: 140 bits (the default), 256, 384 , and 512.
SHA (Secure Hash Algorithm) is included only for backward compatibility with 4.x Directory Servers ;
do not use this algorithm.
MD5 (Mess age Digest algorithm 5) is a commonly us ed standard hashing algorithm.
CRYPT, the UNIX crypt algorithm, is provided for compatibility with UNIX pass words.
NOT E
Pass words cannot be encrypted using the NS-MTA-MD5 pass word s torage scheme. The
storage s cheme is still present but only for reasons of backward compatibility.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
2.3.1.14 3. passwordUnlock (Unlock Account )
Indicates whether users are locked out of the directory for a s pecified amount of time or until the
administrator resets the pass word after an account lockout. The account lockout feature protects
agains t hackers who try to break into the directory by repeatedly trying to guess a us er's pas sword. If
this passwordUnlock attribute is set to off and the operational attribute accountUnlockTime has a
value of 0, then the account is locked indefinitely.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example passwordUnlock: off
2.3.1.14 4. passwordWarning (Send War ning)
Indicates the number of seconds before a user's password is due to expire that the user receives a
password expiration warning control on their next LDAP operation. Depending on the LDAP client, the
user may also be prompted to change their password at the time the warning is sent.
This can be abbreviated to pwdExpireWarning.
For more information on pass word policies, see the " Managing Us ers and Pas swords" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to the maximum 32 bit integer value
(214 74 8364 7) in seconds
Default Value 864 0 0 (1 day)
Syntax Integer
56 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 57

Example passwordWarning: 864 00
2.3.1.14 5. ret ryC ountRese t Time
This attribute s pecifies the length of time that pas ses before the passwordRetryCount attribute is
res et.
Pa ra met e r De script ion
Entry DN cn=config
Valid Range 1 to any reasonable integer
Default Value none
Syntax Integer
Example retryCountResetTime: 15
2.3.2. cn=change log5
Multi-master replication changelog configuration entries are stored under the cn= changelog5 entry.
The changelog behaves much like a databas e, and it has many of attributes als o us ed by the ldbm
databases .
The primary cache-related memory attribute, nsslapd-cachememsize, has a default value of 104 85760
bytes , which is 10 MB. This parameter is tuned for a single backend replicated to a s ingle consumer.
When more backends are replicated or when one backend is replicated to more than one cons umer,
tune the nsslapd-cachememsize so that its value is 50 00 0 00 times the number of replication
agreements initiated from the server (5000000 * no_of_repl_agreements).
The relationship between the values as signed to the nsslapd-dbcachesize and nsslapd-
cachememsize parameters s hould be the s ame as the relationship that is des cribed in the database
tuning section.
The cn=ch angelog5,cn=config entry is an instance of the e xtensibleO bje ct object class .
NOT E
Two different types of changelogs are maintained by Directory Server. The first type, which is
stored here and referred to as the changel og, is used by multi-master replication; the s econd
changelog, which is actually a plug-in and referred to as the retro changelog, is for compatibility
with some legacy applications. See Section 3.1.29, “Retro Changelog Plug-in” for further
information about the Retro Changelog Plug-in.
2.3.2.1. nsslapd- cha ngelogdir
This required attribute specifies the name of the directory in which the changelog databas e is created.
Whenever a changelog configuration entry is created, it must contain a valid directory; otherwise, the
operation is rejected. T he GUI proposes by default that this databas e be s tored in
/var/li b/dirsrv/slapd-instance_name/changelog db.
WARNING
If the cn=ch ang elog5 entry is removed, the directory specified in the nsslapd-changelogdir
parameter, including any subdirectories, are removed, with all of their contents.
NOT E
For performance reasons, store this database on a different phys ical disk.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=changelog5,cn=config
Valid Values Any valid path to the directory storing the
changelog
Default Value None
Syntax DirectoryString
Example nsslapd-changelogdir:
/var/lib/dirsrv/slapd-instance_name/changelogdb
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 57
Page 58

2.3.2.2. nsslapd- cha ngelogmaxage (Max Cha ngelog Age )
This attribute s ets the maximum age of any entry in the changelog. The changelog contains a record for
each directory modification and is us ed when synchronizing cons umer servers . Each record contains a
timestamp. Any record with a timestamp that is older than the value specified in this attribute is removed.
If this attribute is abs ent, there is no age limit on changelog records. For information on the changelog,
see Section 2.3.2.1, “nsslapd-changelogdir”.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=changelog5,cn=config
Valid Range 0 (meaning that entries are not removed
according to their age) to maximum 32-bit integer
(214 74 8364 7)
Default Value 0
Syntax DirectoryString IntegerAgeID where AgeID is s for
seconds, m for minutes, h for hours , d for days,
and w for weeks
Example nsslapd-changelogmaxage: 30d
2.3.2.3. nsslapd -change logma xe nt rie s (Ma x C ha nge log Records)
This attribute s ets the maximum number of records the changelog may contain. If this attribute is abs ent,
there is no maximum number of records the changelog can contain. For information on the changelog,
see Section 2.3.2.1, “nsslapd-changelogdir”.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=changelog5,cn=config
Valid Range 0 (meaning that the only maximum limit is the disk
siz e) to maximum 32-bit integer (2147483647)
Default Value 0
Syntax Integer
Example nsslapd-changelogmaxentries : 500 0
2.3.2.4 . cha nges
This attribute contains the changes made to the entry for add and modify operations in LDIF format.
OID 2.16.840 .1.113730.3.1.8
Syntax Binary
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.5. change Log
This attribute contains the dis tinguis hed name of the entry which contains the set of entries comprising
the s erver’s changelog.
OID 2.16.840 .1.113730.3.1.35
Syntax DN
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.6. change Numbe r
This attribute is always pres ent. It contains an integer which uniquely identifies each change made to a
directory entry. T his number is related to the order in which the change occurred. The higher the
number, the later the change.
OID 2.16.840 .1.113730.3.1.5
Syntax Integer
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.7. change Time
58 Chap ter 2 . Core Server Co nfiguration Referen ce
Page 59

This attribute defines a time, in a YYMMDDHHMMSS format, when the entry was added.
OID 2.16.840 .1.113730.3.1.77
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.3.2.8. change Type
This attribute s pecifies the type of LDAP operation, add, de lete, m odify, or m od rdn. For example:
changeType: modify
OID 2.16.840 .1.113730.3.1.7
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.9. dele t eOldRdn
In the cas e of m odrdn operations, this attribute specifies whether the old RDN was deleted.
OID 2.16.840 .1.113730.3.1.10
Syntax Boolean
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.10 . filt e rInfo
This is used by the changelog for processing replication.
OID 2.16.840 .1.113730.3.1.206
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.3.2.11 . ne wRdn
In the cas e of m odrdn operations, this attribute specifies the new RDN of the entry.
OID 2.16.840 .1.113730.3.1.9
Syntax DN
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.12 . ne wSupe rior
In the cas e of m odrdn operations, this attribute specifies the newSuperior attribute of the entry.
OID 2.16.840 .1.113730.3.1.11
Syntax DN
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.2.13. ta rget Dn
This attribute contains the DN of the entry that was affected by the LDAP operation. In the case of a
m odr dn operation, the targetDn attribute contains the DN of the entry before it was modified or moved.
OID 2.16.840 .1.113730.3.1.6
Syntax DN
Multi- or Single-Valued Multi-valued
Defined in Changelog Internet Draft
2.3.3. cn=encryption
Encryption related attributes are stored under the cn=e ncryption,cn= config entry. T he
cn=encryption,cn=conf ig entry is an ins tance of the nsslapdEncr yption Config object class .
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 59
Page 60

2.3.3.1. nsSSLS essionT imeout
This attribute s ets the lifetime duration of a TLS/SSL. The minimum timeout value is 5 seconds. If a
smaller value is set, then it is automatically replaced by 5 seconds. A value greater than the maximum
value in the valid range below is replaced by the maximum value in the range.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=encryption, cn=config
Valid Range 5 seconds to 24 hours
Default Value 0 , which means use the maximum value in the
valid range above.
Syntax Integer
Example nsSSLSessionT imeout: 5
2.3.3.2. nsSSLclienta ut h
This attribute s ets how clients may us e certificates to authenticate to the Directory Server for SSL
connections.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=encryption, cn=config
Valid Values off | allowed | required
off means disallow certificate-bas ed
authentication
allowed means clients may us e certificates or
other forms of authentication
required means clients must us e certificates for
authentication
Default Value allowed
Syntax DirectoryString
Example nsSSLclientauth: allowed
2.3.3.3. nsSSL2
Supports SSL version 2. SSLv2 is deprecated, and Red Hat strongly discourages us ing it.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=encryption, cn=config
Valid Values on | off
Default Value off
Syntax DirectoryString
Example nsSSL2: off
2.3.3.4 . nsSSL3
Supports SSL version 3.
The server has to be res tarted for changes to this attribute to go into effect.
Pa ra met e r De script ion
Entry DN cn=encryption, cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nsSSL3: on
2.3.3.5. nsSSL3ciphe rs
This multi-valued attribute specifies the s et of encryption ciphers the Directory Server uses during SSL
communications. For more information on the ciphers s upported by the Directory Server, see the
"Managing SSL" chapter in the Directory Server Administrator's Guide.
60 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 61

Pa ra met e r De script ion
Entry DN cn=encryption, cn=config
Valid Values For SSLv3:
rsa_null_md5
rsa_rc4 _128_md5
rsa_rc4 _40_md5
rsa_rc2_40 _md5
rsa_des _sha
rsa_fips_des_sha
rsa_3des _sha
rsa_fips_3des _sha
For T LS:
tls_rsa_export1024 _with_rc4_56_sha
tls_rsa_export1024 _with_des_cbc_sha
Default Value
Syntax DirectoryString
Use the plus (+) symbol to enable or minus (-)
symbol to disable, followed by the ciphers . Blank
spaces are not allowed in the list of ciphers .
To enable all ciphers — except rsa_null_m d5,
which must be specifically called — specify +all.
Example nsslapd-SSL3ciphers:
+RSA_NULL_MD5,+RC4_56_SHA,-RC4_56_SHA
For more information, see the "Managing SSL" chapter in the Directory Server Administrator's Guide
2.3.4 . cn=fe atures
There are not attributes for the cn=features entry itself. This entry is only used as a parent container
entry, with the nsContainer object clas s.
The child entries contain an oid attribute to identify the feature and the directoryServerFe ature
object class, plus optional identifying information about the feature, such as specific ACLs. For example:
dn: oid=2.16.840.1.113730.3.4.9,cn=features,cn=config
objectClass: top
objectClass: directoryServerFeature
oid: 2.16.840.1.113730.3.4.9
cn: VLV Request Control
aci: (targetattr != "aci")(version 3.0; acl "VLV Request Control"; allow( read,
search, com pare, proxy ) userdn = "ldap:///all";)
creatorsName: cn=server,cn=plugins,cn=config
modifiersName: cn=server,cn=plugins,cn=config
createTimestamp: 20090129132357Z
modifyTimestamp: 20090129132357Z
2.3.4 .1 . oid
The oid attribute contains an object identifier ass igned to a directory service feature. oid is used as the
naming attribute for these directory features.
OID 2.16.840 .1.113730.3.1.215
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.3.5. cn=mapping t re e
Configuration attributes for s uffixes , replication, and Windows s ynchronization are s tored under
cn=m apping tree,cn=config. Configuration attributes related to s uffixes are found under the
suffix subentry cn=suffix, cn=m apping tree ,cn=con fig.
For example, a suffix is the root entry in the directory tree, such as dc=e xam ple,dc= com.
Replication configuration attributes are stored under cn=r eplica, cn=suffix, cn=mapping
tree ,cn=config .
Replication agreement attributes are stored under cn=replicationAgreementName, cn =replica,
cn=suffix,cn =m appin g tree,cn= config.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 61
Page 62

Windows synchroniz ation agreement attributes are s tored under cn=syncAgreementName,
cn=replica, cn =suffix,cn=m apping tre e,cn=confi g.
2.3.6. Suffix Configura tion At t ribu te s unde r cn="suffixNa me"
Suffix configuration attributes are stored under the cn=suffix entry. The cn =suffix entry is an ins tance of
the nsMappingT ree object class which inherits from the extensible Object object clas s. For suffix
configuration attributes to be taken into account by the server, thes e object class es (in addition to the
top object class) must be present in the entry.
The suffix DN should be quoted because the s uffix DN contains characters s uch as equals signs (=),
commas (,), and s pace characters that must be quoted or escaped to appear as a value in another DN.
2.3.6.1. nsslapd- st ate
Determines how the suffix handles operations.
Pa ra met e r De script ion
Entry DN cn=suffix, cn=mapping tree, cn=config
Valid Values backend | disabled | referral | referral on update
backend means the backend (database) is used
to process all operations .
disabled means the database is not available for
processing operations. T he server returns a " No
such search object" error in response to
requests made by client applications.
referral means a referral is returned for reques ts
made to this suffix.
referral on update means the databas e is used
for all operations except update requests, which
receive a referral.
Default Value backend
Syntax DirectoryString
Example nsslapd-state: backend
2.3.6.2. nsslapd- ba cke nd
Gives the name of the database or database link used to process requests. This attribute can be multivalued, with one database or database link per value. This attribute is required when the value of the
nsslapd-state attribute is s et to backend or refer ral on update. The value should be the name
of the backend databas e entry instance under cn=ldbm database,cn=plugins,cn=con fig. For
example:
o=NetscapeRoot,cn=ldbm database,cn=plugins,cn=config
Pa ra met e r De script ion
Entry DN cn=suffix, cn=mapping tree, cn=config
Valid Values Any valid partition name
Default Value None
Syntax DirectoryString
Example nsslapd-backend: userRoot
2.3.7. Replication Attr ibut e s under cn= re plica , cn="suffixD N", cn=mapping tree, cn=config
Replication configuration attributes are stored under cn=r eplica, cn=suffix, cn=mapping tree,
cn=config. The cn=replica entry is an ins tance of the nsDS5R epl ica object class . For
replication configuration attributes to be taken into account by the server, this object clas s (in addition to
the top object class) must be pres ent in the entry. For further information about replication, see the
"Managing Replication" chapter in the Directory Server Administrator's Guide.
2.3.7.1. nsDS 5Flags
This attribute s ets replica properties that were previously defined in flags. At pres ent only one flag
exists, which sets whether the log changes.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
62 Cha p ter 2. Core Server Configu ra tio n Reference
Page 63

cn=config
Valid Values 0 | 1
0 means no changes are logged
1 means changes are logged
Default Value 0
Syntax Integer
Example nsDS5Flags: 0
2.3.7.2. nsds5 De bugReplica Timeout
This attribute gives an alternate timeout period to us e when the replication is run with debug logging.
This can set only the time or both the time and the debug level:
nsds5debugreplicatimeout: seconds[:debuglevel]
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values Any numeric s tring
Default Value
Syntax DirectoryString
Example nsds5debugreplicatimeout: 60:8192
2.3.7.3. nsD S5 ReplConflict
Although this attribute is not in the cn=re plica entry, it is used in conjunction with replication. This
multi-valued attribute is included on entries that have a change conflict that cannot be resolved
automatically by the synchronization proces s. T o check for replication conflicts requiring administrator
intervention, perform an LDAP search for (nsDS5ReplC onflict=* ). For example:
ldapsearch -D cn=directory manager -w password -s sub -b dc=example,dc=com
"(|(objectclass=nsTombstone)(nsDS5ReplConflict=* ))" dn nsDS5ReplConflict
nsUniqueID
Using the search filter "(objectcla ss=nsT om bstone)" als o shows tombstone (deleted) entries.
The value of the nsDS5ReplConflict contains more information about which entries are in conflict,
usually by referring to them by their nsUniqueID. It is poss ible to search for a tombstone entry by its
nsUniqueID. For example:
ldapsearch -D cn=directory manager -w password -s sub -b dc=example,dc=com
"(|(objectclass=nsTombstone)(nsUniqueID=66a2b699-1dd211b2-807fa9c3-a58714648))"
2.3.7.4 . nsD S5 Replica Aut oRe ferra l
This attribute s ets whether the Directory Server follows configured referrals for the databas e.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values on | off
Default Value
Syntax DirectoryString
Example nsDS5ReplicaAutoReferral: on
2.3.7.5. nsDS 5Re plicaB indD N
This multi-valued attribute specifies the DN to use when binding. Although there can be more than one
value in this cn=r epl ica entry, there can only be one s upplier bind DN per replication agreement.
Each value should be the DN of a local entry on the cons umer server. If replication suppliers are us ing
client certificate-based authentication to connect to the consumers, configure the certificate mapping on
the consumer to map the subjectDN in the certificate to a local entry.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values Any valid DN
Default Value
Syntax DirectoryString
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 63
Page 64

Example nsDS5ReplicaBindDN: cn=replication manager,
cn=config
2.3.7.6. nsDS 5Re plicaC ha nge Count
This read-only attribute shows the total number of entries in the changelog and whether they still remain
to be replicated. When the changelog is purged, only the entries that are still to be replicated remain.
See Section 2.3.7.10, “nsDS5ReplicaPurgeDelay” and Section 2.3.7.13,
“ns DS5ReplicaT ombstonePurgeInterval” for more information about purge operation properties.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Range -1 to maximum 32-bit integer (2147483647)
Default Value
Syntax Integer
Example nsDS5ReplicaChangeCount: 675
2.3.7.7. nsDS 5Re plicaId
This attribute s ets the unique ID for suppliers in a given replication environment.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Range 0 to 65534
Default Value
Syntax Integer
Example nsDS5ReplicaId: 1
2.3.7.8. nsDS 5Re plicaLegacyConsumer
If this attribute is abs ent or has a value of false, then it means that the replica is not a legacy
consumer.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values true | false
Default Value fals e
Syntax DirectoryString
Example nsDS5ReplicaLegacyCons umer: false
2.3.7.9. nsDS 5Re plicaNa me
This attribute s pecifies the name of the replica with a unique identifier for internal operations. If it is not
specified, this unique identifier is allocated by the server when the replica is created.
NOT E
It is recommended that the server be permitted to generate this name. However, in certain
circumstances, for example, in replica role changes (master to hub etc.), this value needs to be
specified. Otherwis e, the server will not use the correct changelog database, and replication fails.
This attribute is des tined for internal use only.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values
Default Value
Syntax DirectoryString (a UID identifies the replica)
Example nsDS5ReplicaName: 66a2b699-1dd211b2-
807fa9c3-a58714 64 8
2.3.7.10 . nsDS5 Re plica Purge De la y
64 Cha pter 2. Co re Server Con fig uration Reference
Page 65

This attribute controls the maximum age of deleted entries (tombstone entries) and state information.
The Directory Server stores tombstone entries and state information so that when a conflict occurs in a
multi-master replication proces s, the s erver resolves the conflicts bas ed on the timestamp and replica ID
stored in the change sequence numbers.
An internal Directory Server housekeeping operation periodically removes tombstone entries which are
older than the value of this attribute (in seconds). State information which is older than the
nsDS5ReplicaPurgeDelay value is removed when an entry which contains the the s tate information is
modified.
Not every tombstone and s tate information may be removed because, with multi-master replication, the
server may need to keep a small number of the latest updates to prime replication, even if they are older
than the value of the attribute.
This attribute s pecifies the interval, in seconds, to perform internal purge operations on an entry. When
setting this attribute, ensure that the purge delay is longer than the longest replication cycle in the
replication policy to preserve enough information to res olve replication conflicts and to prevent the
copies of data stored in different s ervers from diverging.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Range 0 (keep forever) to maximum 32-bit integer
(214 74 8364 7)
Default Value 60 4800 [1 week (60 x60 x24x7)]
Syntax Integer
Example nsDS5ReplicaPurgeDelay: 60 4800
2.3.7.11 . nsDS5 Re plica Referra l
This multi-valued attribute specifies the us er-defined referrals . This should only be defined on a
consumer. User referrals are only returned when a client attempts to modify data on a read-only
consumer. This optional referral overrides the referral that is automatically configured by the consumer
by the replication protocol.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values Any valid LDAP URL
Default Value
Syntax DirectoryString
Example nsDS5ReplicaReferral: ldap://ldap.example.com
2.3.7.12 . nsDS5 Re plica Root
This attribute s ets the DN at the root of a replicated area. This attribute must have the same value as
the s uffix of the database being replicated and cannot be modified.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values Suffix of the database being replicated, which is
the s uffix DN
Default Value
Syntax DirectoryString
Example nsDS5ReplicaRoot: "dc=example,dc=com"
2.3.7.13. nsDS5ReplicaT ombstone Pur geInt er val
This attribute s pecifies the time interval in s econds between purge operation cycles .
Periodically, the s erver runs an internal housekeeping operation to purge old update and state
information from the changelog and the main database. See Section 2.3.7.10,
“ns DS5ReplicaPurgeDelay”.
When s etting this attribute, remember that the purge operation is time-cons uming, especially if the s erver
handles many delete operations from clients and s uppliers.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 65
Page 66

cn=config
Valid Range 0 to maximum 32-bit integer (2147483647) in
seconds
Default Value 864 0 0 (1 day)
Syntax Integer
Example nsDS5ReplicaTombstonePurgeInterval: 864 00
2.3.7.14 . nsDS5ReplicaT ype
Defines the type of replication relationship that exis ts between this replica and the others.
Pa ra met e r De script ion
Entry DN cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values 0 | 1 | 2 | 3
0 means unknown
1 means primary (not yet us ed)
2 means consumer (read-only)
3 cons umer/s upplier (updatable)
Default Value
Syntax Integer
Example nsDS5ReplicaType: 2
2.3.7.15 . nsDS5 Re plica ReapActive
This read-only attribute specifies whether the background tas k that removes old tombstones (deleted
entries) from the database is active. See Section 2.3.7.13, “ns DS5ReplicaT ombstonePurgeInterval” for
more information about this task. A value of 0 means that the task is inactive, and a value of 1 means
that the task is active. T he server ignores the modify reques t if this value is set manually.
Pa ra met e r De script ion
Entry DN cn=replica,cn=" suffixDN”,cn=mapping
tree,cn=config
Valid Values 0 | 1
Default Value
Syntax Integer
Example nsDS5ReplicaReapActive: 0
2.3.7.16 . nsds5Ta sk
This attribute is used to launch a replication tas k, such as dumping the database contents to LDIF. This
is used internally by the Directory Server supplier.
2.3.7.17 . nsStat e
This attribute s tores information on the state of the clock. It is designed only for internal use to ensure
that the server cannot generate a change s equence number (c sn) inferior to existing ones required for
detecting backward clock errors.
2.3.8. Replication Attr ibut e s under cn= Replica tionAgree mentName, cn= re plica ,
cn= "suffixName", cn=ma pping t re e, cn=config
The replication attributes that concern the replication agreement are stored under
cn=ReplicationAgreementName, cn=replica, cn =suffixDN, cn=m appin g tree, cn=config.
The cn=ReplicationAgreementName entry is an ins tance of the nsDS5Repl ication Agreem ent
object class. Replication agreements are configured only on supplier replicas.
2.3.8.1. cn
This attribute is used for naming. Once this attribute has been s et, it cannot be modified. This attribute is
required for setting up a replication agreement.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid cn
66 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 67

Default Value
Syntax DirectoryString
Example cn: MasterAtoMasterB
2.3.8.2. descript ion
Free form text description of the replication agreement. This attribute can be modified.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any string
Default Value
Syntax DirectoryString
Example description: Replication Agreement between
Server A and Server B.
2.3.8.3. nsD S5 Replica BindDN
This attribute s ets the DN to use when binding to the consumer during replication. The value of this
attribute must be the s ame as the one in cn= replica on the consumer replica. This may be empty if
certificate-based authentication is us ed, in which cas e the DN used is the subject DN of the certificate,
and the consumer must have appropriate client certificate mapping enabled. This can also be modified.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid DN (can be empty if client certificates
are used)
Default Value
Syntax DirectoryString
Example nsDS5ReplicaBindDN: cn=replication manager,
cn=config
2.3.8.4 . nsD S5 Replica Bin dMe thod
This attribute s ets the method for the server to us e to bind to the consumer server.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values SIMPLE | SSLCLIENTAUTH
The SIMPLE bind method requires a DN and
password.
Default Value SIMPLE
Syntax DirectoryString
Example nsDS5ReplicaBindMethod: SIMPLE
2.3.8.5. nsDS 5Re plicaB usyWa it Time
This attribute s ets the amount of time in seconds a supplier should wait after a consumer sends back a
busy response before making another attempt to acquire access. The default value is three (3)
seconds. If the attribute is set to a negative value, Directory Server s ends the client a message and an
LDAP_UN WILLING_T O_PERFORM error code.
The nsDS5ReplicaBusyWaitTime attribute works in conjunction with the
nsDS5ReplicaSessionPauseTime attribute. The two attributes are des igned so that the
nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval
specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance
to gain consumer access before the previous supplier can re-access the consumer.
Set the nsDS5ReplicaBusyWaitTime attribute at any time by using cha ngetype:m odify with the
replace operation. The change takes effect for the next update ses sion if one is already in progress.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid integer
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 67
Page 68

Default Value 3
Syntax Integer
Example nsDS5ReplicaBusyWaitTime: 3
2.3.8.6. nsDS 5Re plicaC ha nge sSentSince St artup
This read-only attribute shows the number of changes sent to this replica since the server s tarted.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Range 0 to maximum 32-bit integer (2147483647)
Default Value
Syntax Integer
Example nsDS5ReplicaChangesSentSinceStartup: 647
2.3.8.7. nsDS 5Re plicaC re de nt ials
This attribute s ets the credentials for the bind DN (specified in the nsDS5ReplicaBindDN attribute) on
the remote server containing the consumer replica. The value for this attribute can be modified. When
certificate-based authentication is us ed, this attribute may not have a value. The example s hows the
dse.ldif entry, not the actual pass word. If this value over LDAP or us ing the Console, set it to the
cleartext credentials, and let the server encrypt the value.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid password, which is then encrypted
using the DES reversible password encryption
schema.
Default Value
Syntax DirectoryString {DES} encrypted_password
Example nsDS5ReplicaCredentials:{DES}
9Eko69APCJfF08A0aD0 C
2.3.8.8. nsDS 5Re plicaHost
This attribute s ets the hostname for the remote server containing the consumer replica. Once this
attribute has been s et, it cannot be modified.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid host s erver name
Default Value
Syntax DirectoryString
Example nsDS5ReplicaHost: ldap2.example.com
2.3.8.9. nsDS 5Re plicaLast InitEnd
This optional, read-only attribute states when the initialization of the consumer replica ended.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values YYYYMMDDhhmmssZ is the date/time in
Generalized Time form at which the connection
was opened. This value gives the time in relation
to Greenwich Mean T ime. The hours are set with
a 24 -hour clock. The Z at the end indicates that
the time is relative to Greenwich Mean T ime.
Default Value
Syntax GeneralizedTime
Example nsDS5ReplicaLastInitEnd: 20090 50 412160 3Z
2.3.8.10 . nsDS5 Re plica La st Init St a rt
This optional, read-only attribute states when the initialization of the consumer replica s tarted.
68 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 69

Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values YYYYMMDDhhmmssZ is the date/time in
Generalized Time form at which the connection
was opened. This value gives the time in relation
to Greenwich Mean T ime. The hours are set with
a 24 -hour clock. The Z at the end indicates that
the time is relative to Greenwich Mean T ime.
Default Value
Syntax GeneralizedTime
Example nsDS5ReplicaLastInitStart: 20 09050 30 30 40 5
2.3.8.11 . nsDS5 Re plica La st Init St a tus
This optional, read-only attribute provides s tatus for the initialization of the cons umer. There is typically
a numeric code followed by a short s tring explaining the status. Zero (0) means success .
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values 0 (Consumer Initialization Succeeded), followed
by any other s tatus mess age.
Default Value
Syntax String
Example nsDS5ReplicaLastUpdateStatus : 0 T otal update
succeeded
2.3.8.12 . nsDS5 Re plica La st Upda t eE nd
This read-only attribute states when the most recent replication schedule update ended.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values YYYYMMDDhhmmssZ is the date/time in
Generalized Time form at which the connection
was opened. This value gives the time in relation
to Greenwich Mean T ime. The hours are set with
a 24 -hour clock. The Z at the end indicates that
the time is relative to Greenwich Mean T ime.
Default Value
Syntax GeneralizedTime
Example nsDS5ReplicaLastUpdateEnd:
2009050 2175801Z
2.3.8.13. nsDS5ReplicaL astUpdate St a rt
This read-only attribute states when the most recent replication schedule update started.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values YYYYMMDDhhmmssZ is the date/time in
Generalized Time form at which the connection
was opened. This value gives the time in relation
to Greenwich Mean T ime. The hours are set with
a 24 -hour clock. The Z at the end indicates that
the time is relative to Greenwich Mean T ime.
Default Value
Syntax GeneralizedTime
Example nsDS5ReplicaLastUpdateStart:
2009050 41220 55Z
2.3.8.14 . nsDS5ReplicaL astUpdate St a tus
This read-only attribute provides the s tatus for the most recent replication s chedule updates. The format
is a numeric code followed by a short string. Zero (0) means success.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 69
Page 70

Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values 0 (no replication sess ions started), followed by
any other error or s tatus mess age
Default Value
Syntax DirectoryString
Example nsDS5ReplicaLastUpdateStatus : 0 replica
acquired success fully
2.3.8.15 . nsDS5 Re plica Port
This attribute s ets the port number for the remote server containing the replica. Once this attribute has
been set, it cannot be modified.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Port number for the remote server containing the
replica
Default Value
Syntax Integer
Example nsDS5ReplicaPort:389
2.3.8.16 . nsDS5 Re plica ReapActive
This read-only attribute specifies whether the background tas k that removes old tombstones (deleted
entries) from the database is active. See Section 2.3.7.13, “ns DS5ReplicaT ombstonePurgeInterval” for
more information about this task. A value of zero (0) means that the tas k is inactive, and a value of 1
means that the task is active. If this value is set manually, the server ignores the modify request.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values 0 | 1
Default Value
Syntax Integer
Example nsDS5ReplicaReapActive: 0
2.3.8.17 . nsDS5 BeginReplica Refresh
Initializes the replica. This attribute is absent by default. However, if this attribute is added with a value of
start, then the server initializ es the replica and removes the attribute value. To monitor the status of
the initialization procedure, poll for this attribute. When initializ ation is finished, the attribute is removed
from the entry, and the other monitoring attributes can be used for detailed status inquiries.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values stop | start
Default Value
Syntax DirectoryString
Example nsDS5BeginReplicaRefresh: start
2.3.8.18 . nsDS5 Re plica Root
This attribute s ets the DN at the root of a replicated area. This attribute must have the same value as
the s uffix of the database being replicated and cannot be modified.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Suffix of the database being replicated - s ame as
suffixDN above
Default Value
Syntax DirectoryString
Example nsDS5ReplicaRoot: "dc=example,dc=com"
70 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 71

2.3.8.19 . nsDS5 Re plica Se ssionPa use T ime
This attribute s ets the amount of time in seconds a supplier should wait between update ses sions. The
default value is 0. If the attribute is set to a negative value, Directory Server sends the client a message
and an LDAP_UNWILLING_T O_PE RFORM error code.
The nsDS5ReplicaSessionPauseTime attribute works in conjunction with the
nsDS5ReplicaBusyWaitTime attribute. The two attributes are des igned so that the
nsDS5ReplicaSessionPauseTime interval is always at least one second longer than the interval
specified for nsDS5ReplicaBusyWaitTime. The longer interval gives waiting suppliers a better chance
to gain consumer access before the previous supplier can re-access the consumer.
If either attribute is specified but not both, nsDS5ReplicaSessionPauseTime is s et automatically to
1 s econd more than nsDS5ReplicaBusyWaitTime.
If both attributes are s pecified, but nsDS5ReplicaSessionPauseTime is les s than or equal to
nsDS5ReplicaBusyWaitTime, nsDS5ReplicaSessionPauseTime is set automatically to 1 s econd
more than nsDS5ReplicaBusyWaitTime.
When s etting the values , ensure that the nsDS5ReplicaSessionPauseTime interval is at least 1
second longer than the interval specified for nsDS5ReplicaBusyWaitTime. Increas e the interval as
needed until there is an acceptable distribution of consumer acces s among the s uppliers.
Set the nsDS5ReplicaSessionPauseTime attribute at any time by using cha ngetype:m odify with
the replace operation. The change takes effect for the next update ses sion if one is already in
progress .
If Directory Server has to reset the value of nsDS5ReplicaSessionPauseTime automatically, the value
is changed internally only. The change is not visible to clients , and it is not saved to the configuration file.
From an external viewpoint, the attribute value appears as originally set.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid integer
Default Value 0
Syntax Integer
Example nsDS5ReplicaSessionPaus eT ime: 0
2.3.8.20 . nsDS5 Re plica t edAtt ribut eList
This allowed attribute specifies any attributes that are not replicated to a consumer server. Fractional
replication allows databas es to be replicated across s low connections or to les s secure consumers
while still protecting sensitive information. By default, all attributes are replicated, and this attribute is not
pres ent. For more information on fractional replication, see the " Managing Replication" chapter in the
Directory Server Administrator's Guide.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Range
Default Value
Syntax DirectoryString
Example nsDS5ReplicatedAttributeList: (objectclass=*) $
EXCLUDE salary userPassword manager
2.3.8.21 . nsDS5 Re plica T imeout
This allowed attribute specifies the number of seconds outbound LDAP operations waits for a response
from the remote replica before timing out and failing. If the s erver writes Warning: tim ed out
waiting mes sages in the error log file, then increas e the value of this attribute.
Find out the amount of time the operation actually lasted by examining the acces s log on the remote
machine, and then set the nsDS5ReplicaTimeout attribute accordingly to optimize performance.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Range 0 to maximum 32-bit integer value (21474 8364 7)
in seconds
Default Value 60 0
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 71
Page 72

Syntax Integer
Example nsDS5ReplicaTimeout: 600
2.3.8.22 . nsDS5 Re plica T ra nsport Info
This attribute s ets the type of transport used for transporting data to and from the replica. The attribute
values can be either SSL, which means that the connection is established over SSL, or LDAP, which
means that regular LDAP connections are used. If this attribute is abs ent, then regular LDAP
connections are used. This attribute cannot be modified once it is set.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values SSL | LDAP
Default Value abs ent
Syntax DirectoryString
Example nsDS5ReplicaTrans portInfo: LDAP
2.3.8.23. nsDS5ReplicaUp date InP rogress
This read-only attribute states whether or not a replication update is in progress .
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values true | false
Default Value
Syntax DirectoryString
Example nsDS5ReplicaUpdateInProgress : true
2.3.8.24 . nsDS5ReplicaUp date Schedule
This multi-valued attribute specifies the replication schedule and can be modified. Changes made to this
attribute take effect immediately. Modifying this value can be useful to pause replication and res ume it
later. For example, if this value to 000 0-0001 0, this in effect causes the server to s top s ending
updates for this replication agreement. T he s erver continues to s tore them for replay later. If the value is
later changed back to 0000-2359 01234 56, this makes replication immediately resume and sends all
pending changes.
Pa ra met e r De script ion
Entry DN cn=ReplicationAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Range Time schedule presented as XXXX-YYYY
0123456, where XXXX is the starting hour, YYYY
is the finishing hour, and the numbers 0123456
are the days of the week starting with Sunday.
Default Value 0 000 -2359 0123456 (all the time)
Syntax Integer
Example nsDS5ReplicaUpdateSchedule: 00 0 0-2359
0123456
2.3.8.25 . nsDS5 0 ruv
This attribute s tores the last replica update vector (RUV) read from the consumer of this replication
agreement. It is always present and must not be changed.
2.3.8.26 . nsruvRe plica La st Modifie d
This attribute contains the most recent time that an entry in the replica was modified and the changelog
was updated.
2.3.9. Synchron iza t ion Att ributes unde r cn=syncAgree men tName,
cn= WindowsReplica ,cn="suffixName", cn=ma pping t re e, cn=config
The synchroniz ation attributes that concern the synchroniz ation agreement are stored under
cn=syncAgreementName, cn=WindowsRepl ica, cn=suffixDN, cn=ma pping tree, cn=co nfi g.
The cn=syncAgreementName entry is an instance of the nsDSWindo wsReplicationAgreem ent
object class. For synchronization agreement configuration attributes to be taken into account by the
server, this object clas s (in addition to the top object class ) must be present in the entry.
Synchronization agreements are configured only on databas es that are enabled to synchroniz e with
72 Cha p ter 2. Core Server Configu ra tio n Reference
Page 73

Windows Active Directory servers.
Table 2 .7 . List of Attribut es Shared Be twee n Re plicat ion and Synchroniz at ion Agre e ments
cn nsDS5ReplicaLastUpdateEnd
description nsDS5ReplicaLastUpdateStart
nsDS5ReplicaBindDN (the Windows sync
manager ID)
nsDS5ReplicaLastUpdateStatus
nsDS5ReplicaBindMethod nsDS5ReplicaPort
nsDS5ReplicaBusyWaitTime nsDS5ReplicaRoot
nsDS5ReplicaChangesSentSinceStartup nsDS5ReplicaSes sionPauseTime
nsDS5ReplicaCredentials (the Windows sync
manager pass word)
nsDS5ReplicaTimeout
nsDS5ReplicaHost (the Windows host) ns DS5ReplicaT rans portInfo
nsDS5ReplicaLastInitEnd nsDS5ReplicaUpdateInProgress
nsDS5ReplicaLastInitStart nsDS5ReplicaUpdateSchedule
nsDS5ReplicaLastInitStatus ns DS50ruv
2.3.9.1. nsds7 DirectoryRe plica Subtree
The suffix or DN of the Directory Server subtree that is being synchroniz ed.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid s uffix or subs uffix
Default Value
Syntax DirectoryString
Example nsDS7DirectoryReplicaSubtree:
ou=People,dc=example,dc=com
2.3.9.2. nsds7 DirsyncCookie
This s tring is created by Active Directory Dirsync and gives the s tate of the Active Directory Server at
the time of the last synchronization. The old cookie is s ent to Active Directory with each Directory Server
update; a new cookie is returned along with the Windows directory data. This means only entries which
have changed s ince the last synchronization are retrieved.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica, cn=suffixDN, cn=mapping tree,
cn=config
Valid Values Any string
Default Value
Syntax DirectoryString
Example nsDS7DirsyncCookie::khDKJFBZsjBDSCkjsdhIU74DJJVBXDhfvjmfvbhzxj
2.3.9.3. nsds7Ne wWinG roupSyncEnabled
This attribute s ets whether a new group created in the Windows sync peer is automatically
synchroniz ed by creating a new group on the Directory Server.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values on | off
Default Value
Syntax DirectoryString
Example nsDS7NewWinGroupSyncEnabled: on
2.3.9.4 . nsds7Ne wWinUserSyncEna ble d
This attribute s ets whether a new entry created in the Windows sync peer is automatically s ynchronized
by creating a new entry on the Directory Server.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 73
Page 74

Valid Values on | off
Default Value
Syntax DirectoryString
Example nsDS7NewWinUserSyncEnabled: on
2.3.9.5. nsds7 WindowsDomain
This attribute s ets the name of the Windows domain to which the Windows sync peer belongs.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid domain name
Default Value
Syntax DirectoryString
Example nsDS7WindowsDomain: DOMAINWORLD
2.3.9.6. nsds7 WindowsReplica Subtree
The suffix or DN of the Windows subtree that is being s ynchronized.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values Any valid s uffix or subs uffix
Default Value
Syntax DirectoryString
Example nsDS7WindowsReplicaSubtree: cn=Users ,
dc=domain, dc=com
2.3.9.7. winSyncInt erval
This attribute s ets how frequently, in seconds , the Directory Server polls the Windows sync peer to look
for changes in the Active Directory entries. If this entry is not set, the Directory Server checks the
Windows server every five (5) minutes, meaning the default value is 300 (30 0 seconds).
This value can be set lower to write Active Directory changes over to the Directory Server fas ter or
raised if the directory searches are taking too long.
Pa ra met e r De script ion
Entry DN cn=syncAgreementName, cn=replica,
cn=suffixDN, cn=mapping tree, cn=config
Valid Values 1 to the maximum 32-bit integer value
(214 74 8364 7)
Default Value 30 0
Syntax Integer
Example winSyncInterval: 600
2.3.10. cn =monitor
Information us ed to monitor the s erver is s tored under cn=monitor. This entry and its children are
read-only; clients cannot directly modify them. The server updates this information automatically. This
section des cribes the c n=m onitor attributes. The only attribute that can be changed by a us er to set
acces s control is the aci attribute.
If the nsslapd-counters attribute in cn=config is s et to on (the default setting), then all of the
counters kept by the Directory Server instance increment using 64 -bit integers, even on 32-bit machines
or with a 32-bit version of Directory Server. For the cn=monitor entry, the 64 -bit integers are us ed with
the opsinitiated, opscompleted, entriessent, and bytessent counters.
NOT E
The nsslapd-counters attribute enables 64-bit support for thes e specific database and s erver
counters. The counters which use 64-bit integers are not configurable; the 64-bit integers are
either enabled for all the allowed counters or disabled for all allowed counters .
connectio n
74 Cha pter 2. Co re Server Con fig uration Reference
Page 75

This attribute lis ts open connections . These are given in the following format:
connection: A:YYYYMMDDhhmmssZ:B:C:D:E
For example:
connection: 31:20010201164808Z:45:45::cn=directory m anager
A is the connection number, which is the number of the slot in the connection table ass ociated with
this connection. T his is the number logged as slot=A in the acces s log message when this
connection was opened, and usually corresponds to the file descriptor ass ociated with the
connection. The attribute dTableSize shows the total siz e of the connection table.
YYYYMMDDhhmmssZ is the date and time, in GeneralizedT ime form, at which the connection was
opened. This value gives the time in relation to Greenwich Mean T ime.
B is the number of operations received on this connection.
C is the number of completed operations .
D is r if the s erver is in the process of reading BER from the network, empty otherwise. T his value is
usually empty (as in the example).
E this is the bind DN. This may be empty or have value of N ULLDN for anonymous connections .
currentConnections
This attribute s hows the number of currently open and active Directory Server connections .
totalC onnections
This attribute s hows the total number of Directory Server connections. This number includes
connections that have been opened and closed since the server was las t started in addition to the
currentConnections.
dT ableSize
This attribute s hows the s ize of the Directory Server connection table. Each connection is associated
with a s lot in this table, and usually corresponds to the file descriptor used by this connection. See
Section 2.3.1.38, “ns slapd-conntablesize” for more information.
re adWaite rs
This attribute s hows the number of connections where some requests are pending and not currently
being s erviced by a thread in Directory Server.
opsinitiat e d
This attribute s hows the number of Directory Server operations initiated.
opscomple ted
This attribute s hows the number of Directory Server operations completed.
entriessent
This attribute s hows the number of entries sent by Directory Server.
byt essent
This attribute s hows the number of bytes s ent by Directory Server.
currenttime
This attribute s hows the current time, given in Greenwich Mean Time (indicated by Genera lizedT im e
syntax Z notation; for example, 20090202131 102Z).
st ar tT ime
This attribute s hows the Directory Server start time given in Greenwich Mean Time, indicated by
GeneralizedT ime syntax Z notation. For example, 20090202131102 Z.
version
This attribute s hows the Directory Server vendor, vers ion, and build number. For example, Red
Hat/8.1.1 B2009.27 4.08.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 75
Page 76

thre ads
This attribute s hows the number of threads used by the Directory Server. This should correspond to
nsslapd-threadnumber in cn =config.
nba ckE nds
This attribute s hows the number of Directory Server database backends.
ba cke ndMonit orDN
This attribute s hows the DN for each Directory Server database backend. For further information on
monitoring the database, see the following sections:
Section 3.4.8, “Databas e Attributes under cn=attributeName, cn=encrypted attributes ,
cn=databas e_name, cn=ldbm databas e, cn=plugins, cn=config”
Section 3.4.4, “Database Attributes under cn=database, cn=monitor, cn=ldbm database, cn=plugins,
cn=config”
Section 3.4.6, “Databas e Attributes under cn=monitor, cn=NetscapeRoot, cn=ldbm databas e,
cn=plugins, cn=config”
Section 3.5.4, “Database Link Attributes under cn= monitor, cn=databas e ins tance name, cn=chaining
database, cn=plugins, cn=config”
2.3.11. cn =replicat ion
This entry has no attributes . When configuring legacy replication, thos e entries are stored under this
cn=replication node, which serves as a placeholder.
2.3.12. cn =sa sl
Entries which contain SASL mapping configurations are stored under
cn=m apping,cn=sasl,cn =co nfig. The cn =sasl entry is an ins tance of the nsContainer object
class. Each mapping underneath it is an instance of the nsSaslMa pping object clas s.
2.3.12.1 . nsSaslMapBase DNTe mpla te
This attribute contains the search base DN template used in SASL identity mapping.
Pa ra met e r De script ion
Entry DN cn=mapping_name, cn=mapping, cn=sas l,
cn=config
Valid Values Any valid DN
Default Value
Syntax IA5String
Example nsSaslMapBaseDNTemplate:
ou=People,dc=example,dc=com
2.3.12.2 . nsSaslMapFilt e rT emplat e
This attribute contains the search filter template used in SASL identity mapping.
Pa ra met e r De script ion
Entry DN cn=mapping_name, cn=mapping, cn=sas l,
cn=config
Valid Values Any string
Default Value
Syntax IA5String
Example nsSaslMapFilterT emplate: (cn=\1)
2.3.12.3. nsSa slMapRe ge xString
This attribute contains a regular express ion us ed to map SASL identity strings.
Pa ra met e r De script ion
Entry DN cn=mapping_name, cn=mapping, cn=sas l,
cn=config
Valid Values Any valid regular expression
Default Value
Syntax IA5String
76 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 77

Example nsSaslMapRegexString: \(.*\)
2.3.13. cn=SNMP
SNMP configuration attributes are stored under cn =SNMP,cn=c onfig. T he cn =SNMP entry is an
instance of the nsSN MP object clas s.
2.3.13.1. nssnmpe na ble d
This attribute s ets whether SNMP is enabled.
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values on | off
Default Value on
Syntax DirectoryString
Example nssnmpenabled: off
2.3.13.2. nssnmpo rga niz ation
This attribute s ets the organization to which the Directory Server belongs .
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values Organization name
Default Value
Syntax DirectoryString
Example nssnmporganization: Red Hat, Inc.
2.3.13.3. nssnmploca t ion
This attribute s ets the location within the company or organiz ation where the Directory Server res ides .
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values Location
Default Value
Syntax DirectoryString
Example nssnmplocation: B14
2.3.13.4 . nssnmpconta ct
This attribute s ets the email address of the pers on responsible for maintaining the Directory Server.
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values Contact email addres s
Default Value
Syntax DirectoryString
Example nssnmpcontact: jerome@example.com
2.3.13.5. nssnmpd escript ion
Provides a unique des cription of the Directory Server instance.
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values Description
Default Value
Syntax DirectoryString
Example nssnmpdes cription: Employee directory ins tance
2.3.13.6. nssnmpma st erhost
nssnmpmasterhost is deprecated. This attribute is deprecated with the introduction of net-snmp. The
attribute still appears in dse.ldif but without a default value.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 77
Page 78

Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values machine hos tname or localhos t
Default Value <blank>
Syntax DirectoryString
Example nssnmpmasterhos t: localhost
2.3.13.7. nssnmpma st erport
The nssnmpmasterport attribute was deprecated with the introduction of net-snmp. The attribute still
appears in dse.ldif but without a default value.
Pa ra met e r De script ion
Entry DN cn=SNMP, cn=config
Valid Values Operating system dependent port number. See
the operating s ystem documentation for further
information.
Default Value <blank>
Syntax Integer
Example nssnmpmasterport: 199
2.3.14. SNMP St a tistic Att ribut es
Table 2.8, “SNMP Statistic Attributes ” contains read-only attributes which list the statistics available for
LDAP and SNMP clients . Unless otherwise noted, the value for the given attribute is the number of
requests received by the s erver or results returned by the server s ince s tartup. Some of thes e attributes
are not used by or are not applicable to the Directory Server but are still required to be present by SNMP
clients.
If the nsslapd-counters attribute in cn=config is s et to on (the default setting), then all of the
counters kept by the Directory Server instance increment using 64 -bit integers, even on 32-bit machines
or with a 32-bit version of Directory Server. All of the SNMP statistics attributes use the 64-bit integers, if
it is configured.
NOT E
The nsslapd-counters attribute enables 64-bit integers for thes e specific database and server
counters. The counters which use 64-bit integers are not configurable; 64-bit integers are either
enabled for all the allowed counters or dis abled for all allowed counters.
78 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 79

Table 2 .8 . SNMP Sta tistic Attribut es
Attribut e D escription
AnonymousBinds This s hows the number of anonymous bind
requests .
UnAuthBinds This shows the number of unauthenticated
(anonymous) binds.
SimpleAuthBinds T his shows the number of LDAP simple bind
requests (DN and password).
StrongAuthBinds T his shows the number of LDAP SASL bind
requests , for all SASL mechanis ms.
BindSecurityErrors This s hows the number of number of times an
invalid password was given in a bind request.
InOps This s hows the total number of all requests
received by the s erver.
ReadOps Not us ed. This value is always 0.
CompareOps This s hows the number of LDAP compare
requests .
AddEntryOps This s hows the number of LDAP add requests .
RemoveEntryOps T his shows the number of LDAP delete reques ts.
ModifyEntryOps This shows the number of LDAP modify requests .
ModifyRDNOps T his shows the number of LDAP modify RDN
(modrdn) requests .
ListOps Not us ed. This value is always 0.
SearchOps This s hows the number of LDAP search
requests .
OneLevelSearchOps This s hows the number of one-level search
operations.
WholeSubtreeSearchOps This s hows the number of subtree-level search
operations.
Referrals This s hows the number of LDAP referrals
returned.
Chainings Not used. This value is always 0 .
SecurityErrors T his shows the number of errors returned that
were s ecurity related, such as invalid passwords,
unknown or invalid authentication methods , or
stronger authentication required.
Errors This shows the number of errors returned.
Connections T his shows the number of currently open
connections.
ConnectionSeq T his shows the total number of connections
opened, including both currently open and closed
connections.
BytesRecv T his shows the number of bytes received.
BytesSent T his shows the number of bytes sent.
Entries Returned This s hows the number of entries returned as
search results .
ReferralsReturned T his provides information on referrals returned
as search res ults (continuation references ).
MasterEntries Not used. This value is always 0.
CopyEntries Not used. This value is always 0.
CacheEntries
[ ]
If the server has only one database backend, this
is the number of entries cached in the entry
cache. If the server has more than one database
backend, this value is 0, and s ee the monitor
entry for each one for more information.
CacheHits
[a]
If the server has only one database backend, this
is the number of entries returned from the entry
cache, rather than from the database, for s earch
res ults. If the server has more than one databas e
backend, this value is 0, and s ee the monitor
entry for each one for more information.
SlaveHits Not used. This value is always 0.
a
CacheEntries a nd CacheHits ar e up da ted every ten ( 10 ) s eco nd s. R ed Hat str ong ly en co urag es us ing the d atab as e b ac kend
sp ec ifi c m on ito r en trie s fo r thi s a nd o ther d atab ase inf or mati on.
[a]
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 79
Page 80

2.3.15. cn =t asks
Some core Directory Server tasks can be initiated by editing a directory entry using LDAP tools. These
task entries are contained in cn=tasks. Each tas k can be invoked by updating an entry such as the
following:
dn: cn=task_id, cn=task_type, cn=tasks, cn=config
...
In Red Hat Directory Server deployments before Directory Server 8.0, many Directory Server tasks were
managed by the Administration Server. These tasks were moved to the core Directory Server
configuration in version 8.0 and are invoked and administered by Directory Server under the cn=tasks
entry.
There are seven tas ks that are managed under the cn=tasks entry:
cn=import
cn=export
cn=backup
cn=restore
cn=index
cn=schema reload tas k
cn=memberof task
The common attributes for thes e tas ks are listed in Section 2.3.15.1, “Task Invocation Attributes for
Entries under cn=tasks ”.
The cn=tasks entry itself has no attributes and serves as the parent and container entry for the
individual task entries.
IMPORTANT
Task entries are not permanent configuration entries. They only exist in the configuration file for
as long as the task operation is running or until the ttl period expires. Then, the entry is deleted
automatically by the server.
2.3.15.1 . T ask Invocation Attr ibut e s for Entries unde r cn=t a sks
Five tasks which administer Directory Server ins tances have configuration entries which initiate and
identify individual operations . These task entries are instances of the same object class,
extensible Object, and have certain common attributes which des cribe the state and behavior of
Directory Server tasks. The task types can be import, export, backup, restore, index, schema reload, and
memberof.
cn
The cn attribute is used to identify a new task operation to initiate. The cn attribute value can be
anything, as long as it defines a new task.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values Any string
Default Value
Syntax DirectoryString
Example cn: example tas k entry name
nsT a skSt a tus
This attribute contains changing information about the status of the task, such as cumulative statis tics
or its current output message. The entire contents of the attribute may be updated periodically for as
long as the proces s is running.
This attribute value is set by the server and should not be edited.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values Any string
Default Value
80 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 81

Syntax case-exact s tring
Example nsTaskStatus : Loading entries ....
nsT a skLog
This entry contains all of the log messages for the task, including both warning and information
mess ages . New messages are appended to the end of the entry value, so this attribute value grows
larger, without erasing the original contents, by default.
Successful task operations , which have an nsTaskExitCode of 0, are only recorded in the nsTaskLog
attribute. Any non-zero response, which indicates an error, may be recorded in the error log as an error,
but the error message is only recorded in the nsTaskLog attribute. For this reason, us e the information
in the nsTaskLog attribute to find out what errors actually occurred.
This attribute value is set by the server and should not be edited.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values Any string
Default Value
Syntax Case-exact s tring
Example nsTaskLog: example...
nsT a skExitC ode
This attribute contains the exit code for the task. This attribute only exis ts after the task is completed
and any value is only valid if the tas k is complete. The result code can be any LDAP exit code, as listed
in Section 5.4, “LDAP Result Codes”, but only a 0 value equals success ; any other result code is an
error.
This attribute value is set by the server and should not be edited.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values
0 (success ) to 97
[ ]
Default Value
Syntax Integer
Example nsTaskExitCode: 0
nsT a skCurrent It em
This attribute s hows the number of s ubtas k which the task operation has completed, assuming the task
can be broken down into s ubtas ks. If there is only one task, then nsTaskCurrentItem is 0 while the
task is running, and 1 when the task is complete. In this way, the attribute is analogous to a progress
bar. When the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task
is completed.
This attribute value is set by the server and should not be edited.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values 0 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value
Syntax Integer
Example nsTaskCurrentItem: 148
nsT a skT ot alIte ms
This attributes shows the total number of s ubtas ks that must be completed for the task operation. When
the nsTaskCurrentItem attribute has the same value as nsTaskTotalItems, then the task is
completed.
This attribute value is set by the server and should not be edited.
a
Any r esp on se o ther than 0 i s a n er ro r.[a]
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 81
Page 82

Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values 0 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value
Syntax Integer
Example nsTaskT otalItems: 152
nsT a skCancel
This attribute allows a task to be aborted while in progress. T his attribute can be modified by users.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values true | false
Default Value
Syntax Case-insensitive string
Example nsTaskCancel: true
ttl
This attribute s ets the amount of time (in s econds) the task entry will remain in the DSE after the tas k
has finished or aborted. Setting a ttl attribute allows the tas k entry to be polled for new status
information without miss ing the exit code. Setting the ttl attribute to 0 means that the entry is not
cached.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=task_type, cn=tasks ,
cn=config
Valid Values 0 (cannot be cached) to the maximum 32 bit
integer value (2147483647)
Default Value
Syntax DirectoryString
Example ttl: 120
2.3.15.2 . cn=impor t
An LDIF file or multiple LDIF files can be imported through the command line by creating a special task
entry which defines the parameters of the task and initiates the task. As s oon as the task is complete,
the task entry is removed from the directory.
The cn=im port entry is a container entry for import task operations . The cn=im port entry itself has
no attributes, but each of the tas k entries within this entry, such as cn=task_ID, cn=im port,
cn=tasks, cn=confi g, uses the following attributes to define the import task.
An import tas k entry under cn=im port must contain the LDIF file to import (in the nsFilename attribute)
and the name of the instance into which to import the file (in the nsInstance attribute). Additionally, it must
contain a unique cn to identify the task. For example:
dn: cn=example im port, cn=im port, cn=tasks, cn=config
objectclass: extensibleObject
cn: example im port
nsFilename: /home/files/exam ple.ldif
nsInstance: userRoot
As the import operation runs, the task entry will contain all of the s erver-generated task attributes listed
in Section 2.3.15.1, “T ask Invocation Attributes for Entries under cn=tas ks”.
There are some optional attributes which can be us ed to refine the import operation, similar to the
options for the ld if2 db and ld if2db.pl s cripts :
nsIncludeSuffix, which is analogous to the -s option to specify the s uffix to import
nsExcludeSuffix, analogous to the -x option to specify a suffix or s ubtree to exclude from the import
nsImportChunkSize, analogous to the -c option to override s tarting a new pass during the import
and merge the chunks
nsImportIndexAttrs , which sets whether to import attribute indexes (with no corollary in the s cript
options )
82 Cha p ter 2. Core Server Configu ra tio n Reference
Page 83

nsUniqueIdGenerator, analogous to the -g option to generate unique ID numbers for the entries
nsUniqueIdGeneratorNamespace, analogous to the -G option to generate a unique, name-based ID
for the entries
nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to import into the Directory
Server instance. To import multiple files, add multiple instances of this attribute. For example:
nsFilename: file1.ldif
nsFilename: file2.ldif
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values Any string
Default Value
Syntax Case-exact s tring, multi-valued
Example nsFilename: /home/jsmith/example.ldif
nsInstance
This attribute s upplies the name of the databas e ins tance into which to import the files , such as
NetscapeRoot or slapd-exam ple.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values The name of a Directory Server ins tance (any
string)
Default Value
Syntax Case-exact s tring
Example nsInstance: userRoot
nsInclude Su ffix
This attribute identifies a specific suffix or s ubtree to import from the LDIF file.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values Any DN
Default Value
Syntax DN, multi-valued
Example nsIncludeSuffix: ou=people,dc=example,dc=com
nsExcludeSuffix
This attribute identifies suffixes or subtrees in the LDIF file to exclude from the import.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values Any DN
Default Value
Syntax DN, multi-valued
Example nsExcludeSuffix:
ou=machines,dc=example,dc=com
nsImport ChunkSize
This attribute defines the number of chunks to have during the import operation, which overrides the
server's detection during the import of when to start a new pass and merges the chunks.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values 0 to the maximum 32 bit integer value
(214 74 8364 7)
Default Value
Syntax Integer
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 83
Page 84

Example nsImportChunkSize: 10
nsImport Inde xAt trs
This attribute s ets whether to index the attributes that are imported into databas e ins tance.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values true | false
Default Value true
Syntax Case-insensitive string
Example nsImportIndexAttrs : true
nsUnique IdG ener at or
This s ets whether to generate a unique ID for the imported entries. By default, this attribute generates
time-bas ed IDs.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values none (no unique ID) | empty (time-based ID) |
deterministic namespace (name-based ID)
Default Value empty
Syntax Case-insensitive string
Example nsUniqueIdGenerator:
nsUnique IdG ener at or Name spa ce
This attributes defines how to generate name-based IDs; the attribute sets the namespace to use to
generate the IDs. This option is useful to import the same LDIF file into two Directory Server ins tances
when the entries need to have the same IDs.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=import, cn=tasks , cn=config
Valid Values Any string
Default Value
Syntax Case-insensitive string
Example nsUniqueIdGeneratorNamespace: example
2.3.15.3. cn=e xport
A database or multiple databases can be exported through the command line by creating a special task
entry which defines the parameters of the task and initiates the task. As s oon as the task is complete,
the task entry is removed from the directory.
The cn=export entry is a container entry for export task operations. T he cn =export entry itself has
no attributes, but each of the tas k entries within this entry, such as cn=task_ID, cn=expor t,
cn=tasks, cn=confi g, uses the following attributes to define the export tas k.
An export task entry under cn=export mus t contain the name of the database to export (in the
nsInstance attribute) and the name of the LDIF file to write the output to (in the ns Filename attribute).
Additionally, it must contain a unique cn to identify the task. For example:
dn: cn=example export, cn=export, cn=tasks, cn=config
objectclass: extensibleObject
cn: example export
nsInstance: userRoot
nsFilename: /home/files/exam ple.ldif
As the export operation runs , the task entry will contain all of the server-generated task attributes lis ted
in Section 2.3.15.1, “T ask Invocation Attributes for Entries under cn=tas ks”.
There are some optional attributes which can be us ed to refine the export operation, similar to the
options for the db 2ld if and db 2ldif.pl s cripts :
nsIncludeSuffix, analogous to the -s option, to specify the suffixes to include in the exported LDIF
files
nsExcludeSuffix, analogous to the -x option, to exclude the s pecified suffixes from the exported LDIF
files
nsUseOneFile, analogous to the -M option, to break up the exported suffixes into individual LDIF files
84 Cha pter 2. Co re Server Con fig uration Reference
Page 85

nsExportReplica, analogous to the -r option, to indicate whether the exported database is used in
replication
nsPrintKey, analogous to the -N option, to s et whether to print the entry IDs as the entries are
processed by the export operation
nsUseId2Entry, analogous to the -C option, to set whether to us e only the main index, id2entry, to
list the entries to export
nsNoWrap, analogous to the -U option, to set whether to wrap long lines in the LDIF file
nsDumpUniqId, analogous to the -u option, to s et whether to include the unique IDs with the entries
when they are exported
nsFilename
The nsFilename attribute contains the path and filenames of the LDIF files to which to export the
Directory Server ins tance databas e.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values Any string
Default Value
Syntax Case-exact s tring, multi-valued
Example nsFilename: /home/jsmith/example.ldif
nsInstance
This attribute s upplies the name of the databas e ins tance from which to export the databas e, such as
NetscapeRoot or userRo ot.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values The name of a Directory Server ins tance (any
string)
Default Value
Syntax Case-exact s tring, multi-valued
Example nsInstance: userRoot
nsInclude Su ffix
This attribute identifies a specific suffix or s ubtree to export to an LDIF file.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values Any DN
Default Value
Syntax DN, multi-valued
Example nsIncludeSuffix: ou=people,dc=example,dc=com
nsExcludeSuffix
This attribute identifies suffixes or subtrees in the databas e to exclude from the exported LDIF file.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values Any DN
Default Value
Syntax DN, multi-valued
Example nsExcludeSuffix:
ou=machines,dc=example,dc=com
nsUse OneFile
This attribute s ets whether to export all Directory Server instances to a single LDIF file or separate LDIF
files.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 85
Page 86

Valid Values true | false
Default Value fals e
Syntax Case-insensitive string
Example nsUseOneFile: true
nsExportRe plica
This attribute identifies whether the exported database will be used in replication. For replicas, the
proper attributes and settings will be included with the entry to initialize the replica automatically.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values true | false
Default Value fals e
Syntax Case-insensitive string
Example nsExportReplica: true
nsPrint Ke y
This attributes sets whether to print the entry ID number as the entry is process ed by the export task.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values true | false
Default Value true
Syntax Case-insensitive string
Example nsPrintKey: false
nsUse Id2 Entry
The nsUseId2Entry attribute uses the main database index, id2entry, to define the exported LDIF
entries.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values true | false
Default Value fals e
Syntax Case-insensitive string
Example nsUseId2Entry: true
nsNoWrap
This attribute s ets whether to wrap long lines in the LDIF file.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values true | false
Default Value fals e
Syntax Case-insensitive string
Example nsNoWrap: false
nsD umpUniqId
This attribute s ets that the unique IDs for the exported entries are not exported.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=export, cn=tasks , cn=config
Valid Values true | false
Default Value fals e
Syntax Case-insensitive string
Example nsDumpUniqId: true
2.3.15.4 . cn=backup
A database can be backed up through the command line by creating a s pecial task entry which defines
86 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 87

the parameters of the task and initiates the task. As s oon as the task is complete, the tas k entry is
removed from the directory.
The cn=ba ckup entry is a container entry for backup task operations. The cn=ba ckup entry itself has
no attributes, but each of the tas k entries within this entry, such as cn=task_ID, cn=backup,
cn=tasks, cn=confi g, uses the following attributes to define the backup task.
A backup task entry under cn=backup must contain the location of the directory to which to copy the
archive copy (in the nsArchiveDir attribute) and the type of database being backed up (in the
nsDatabas eTypes attribute). Additionally, it must contain a unique cn to identify the tas k. For example:
dn: cn=example backup, cn=backup, cn=tasks, cn=config
objectclass: extensibleObject
cn: example backup
nsArchiveDir: /export/backups/
nsDatabaseType: ldbm database
As the backup operation runs, the task entry will contain all of the server-generated task attributes listed
in Section 2.3.15.1, “T ask Invocation Attributes for Entries under cn=tas ks”.
nsArchive Dir
This attribute gives the location of the directory to which to write the backup.
The backup directory here s hould usually be the s ame as the one configured in the nsslapd-bakdir
attribute.
If this attribute is not included with the cn=backup tas k, the task will fail with an LDAP object clas s
violation error (65).
Pa ra met e r De script ion
Entry DN cn=task_name, cn=backup, cn=tasks , cn=config
Valid Values Any local directory location
Default Value
Syntax Case-exact s tring
Example nsArchiveDir: /export/backups
nsD at a ba seTypes
This attribute gives the kind of databas e being archived. Setting the database types signals what kind of
backup plug-in the Directory Server s hould use to archive the database.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=backup, cn=tasks , cn=config
Valid Values ldbm database
Default Value ldbm database
Syntax Case-exact s tring
Example nsDatabas eType: ldbm databas e
2.3.15.5 . cn=re st ore
A database can be res tored through the command line by creating a special task entry which defines the
parameters of the task and initiates the task. As s oon as the task is complete, the task entry is removed
from the directory.
The cn=re store entry is a container entry for task operations to restore a database. The
cn=restore entry itself has no attributes , but each of the tas k entries within this entry, such as
cn=task_ID, cn=re store, cn=tasks, cn=confi g, uses the following attributes to define the restore
task.
A restore task entry under cn= restore must contain the location of the directory from which to retrieve
the archive copy (in the ns ArchiveDir attribute) and the type of databas e being restored (in the
nsDatabas eTypes attribute). Additionally, it must contain a unique cn to identify the tas k. For example:
dn: cn=example restore, cn=restore, cn=tasks, cn=config
objectclass: extensibleObject
cn: example restore
nsArchiveDir: /export/backups/
nsDatabaseType: ldbm database
As the restore operation runs, the task entry will contain all of the s erver-generated tas k attributes listed
in Section 2.3.15.1, “T ask Invocation Attributes for Entries under cn=tas ks”.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 87
Page 88

nsArchive Dir
This attribute gives the location of the directory to which to write the backup.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=restore, cn=tasks, cn=config
Valid Values Any local directory location
Default Value
Syntax Case-exact s tring
Example nsArchiveDir: /export/backups
nsD at a ba seTypes
This attribute gives the kind of databas e being archived. Setting the database types signals what kind of
backup plug-in the Directory Server s hould use to archive the database.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=restore, cn=tasks, cn=config
Valid Values ldbm database
Default Value ldbm database
Syntax Case-exact s tring
Example nsDatabas eType: ldbm databas e
2.3.15.6 . cn=index
Directory attributes can be indexed though the command line by creating a special task entry which
defines the parameters of the task and initiates the task. As s oon as the task is complete, the task entry
is removed from the directory.
The cn=in dex entry is a container entry for index task operations. The cn=in dex entry itself has no
attributes, but each of the task entries within this entry, such as cn= task_ID, cn=index, cn=tasks,
cn=config, uses the following attributes to define the backup task.
An index task entry under cn=index can create a standard index by identifying the attribute to be
indexed and the type of index to create, both defined in the nsIndexAttribute attribute.
Alternatively, the index task can be used to generate virtual list view (VLV) indexes for an attribute us ing
the ns IndexVLVAttribute attribute. This is the same as running the vlvind ex script.
For example:
dn: cn=example presence index, cn=index, cn=tasks, cn=config
objectclass: extensibleObject
cn: example presence index
nsIndexAttribute: "cn:pres"
dn: cn=example VLV index, cn=index, cn=tasks, cn=config
objectclass: extensibleObject
cn: example VLV index
nsIndexVLVAttribute: "by MCC ou=people,dc=example,dc=com"
As the index operation runs, the tas k entry will contain all of the s erver-generated tas k attributes listed in
Section 2.3.15.1, “T ask Invocation Attributes for Entries under cn=tasks ”.
nsIndexAtt ribut e
This attribute gives the name of the attribute to index and the types of indexes to apply. The format of
the attribute value is the attribute name and a comma-separated list of index types , enclosed in double
quotation marks. For example:
nsIndexAttribute: attribute:index1,index2
Pa ra met e r De script ion
Entry DN cn=task_name, cn=index, cn=tas ks, cn=config
Valid Values
Any attribute
The index type, which can be pres (pres ence),
eq (equality), appro x (approximate), and sub
(substring)
Default Value
88 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 89

Syntax Case-insensitive string, multi-valued
Example
nsIndexAttribute: "cn:pres ,eq"
nsIndexAttribute: "des cription:sub"
nsIndexVLVAtt ribut e
This attribute gives the name of the target entry for a VLV index. A virtual list view is based on a
brows ing index entry (as described in the Administrator's Guide), which defines the virtual list base DN,
scope, and filter. T he nsIndexVLVAttribute value is the browsing index entry, and the VLV creation
task is run according to the browsing index entry parameters.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=index, cn=tas ks, cn=config
Valid Values
Any attribute
The index type, which can be pres (pres ence),
eq (equality), appro x (approximate), and sub
(substring)
Default Value
Syntax Case-insensitive string, multi-valued
Example
nsIndexAttribute: "cn:pres ,eq"
nsIndexAttribute: "des cription:sub"
2.3.15.7 . cn=schema re loa d t ask
The directory schema is loaded when the directory ins tance is started or res tarted. Any changes to the
directory schema, including adding custom schema elements , are not loaded automatically and available
to the instance until the server is restarted or by initiating a schema reload task.
Custom schema changes can be reloaded dynamically, without having to res tart the Directory Server
instance. This is done by initiating a schema reload tas k through creating a new task entry under the
cn=tasks entry.
The cus tom schema file can be located in any directory; if not specified with the schemadir attribute, the
server reloads the schema from the default /etc/dirsrv/slapd-instance_name/schema directory.
IMPORTANT
Any schema loaded from another directory must be copied into the schema directory or the
schema will be lost when the server.
The schema reload task is initiated though the command line by creating a special task entry which
defines the parameters of the task and initiates the task. As s oon as the task is complete, the task entry
is removed from the directory. For example:
dn: cn=example schema reload,cn=schema reload task, cn=tasks, cn=config
objectclass: extensibleObject
cn:example schema reload
schem adir: /export/schema
The cn=schem a re load task entry is a container entry for schema reload operations . The
cn=sche ma reload task entry its elf has no attributes, but each of the task entries within this entry,
such as cn=task_ID, cn= schema reload task, cn=tasks, cn=co nfi g, uses the schema reload
attributes to define the individual reload task.
cn
The cn attribute is used to identify a new task operation to initiate. The cn attribute value can be
anything, as long as it defines a new task.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=schema reload tas k,
cn=tasks , cn=config
Valid Values Any string
Default Value
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 89
Page 90

Syntax DirectoryString
Example cn: example reload task ID
sche madir
This contains the full path to the directory containing the cus tom schema file.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=schema reload tas k,
cn=tasks , cn=config
Valid Values Any local directory path
Default Value /etc/dirsrv/slapd-instance_name/schema
Syntax DirectoryString
Example schemadir: /export/s chema/
2.3.15.8 . cn=memberof t ask
The memberOf attribute is created and managed by the Directory Server automatically to dis play group
membership on the members ' us er entries. When the member attribute on a group entry is changed, all
of the members ' as sociated directory entries are automatically updated with their corresponding
memberOf attributes.
The cn=m em berof task (and the related fixup-m em berof.pl script) is used to create the initial
memberOf attributes on the member's us er entries in the directory. After the memberOf attributes are
created, then the MemberOf Plug-in manages the memberOf attributes automatically.
The memberOf update tas k must give the DN of the entry or s ubtree to run the update tas k agains t (s et
in the basedn attribute). Optionally, the task can include a filter to identify the members ' us er entries to
update (set in the filter attribute). For example:
dn: cn=example m emberof, cn=mem berof task, cn=tasks, cn=config
objectclass: extensibleObject
cn:example m emberof
basedn: ou=people,dc=example,dc=com
filter: (objectclass=groupOfNames)
As s oon as the task is complete, the task entry is removed from the directory.
The cn=m em berof task entry is a container entry for memberOf update operations. T he
cn=m em be rof task entry its elf has no attributes , but each of the tas k entries beneath this entry, such
as cn=task_ID, cn=m em berof task, cn=tasks, cn=config, uses its attributes to define the
individual update task.
ba sedn
This attribute gives the base DN to us e to s earch for the user entries to update the memberOf attribute.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=memberof task, cn=tasks ,
cn=config
Valid Values Any DN
Default Value
Syntax DN
Example basedn: ou=people, dc=example, dc=com
filt er
This attribute gives an optional LDAP filter to use to select which user entries to update the memberOf
attribute. Each member of a group has a corresponding us er entry in the directory.
Pa ra met e r De script ion
Entry DN cn=task_name, cn=memberof task, cn=tasks ,
cn=config
Valid Values Any LDAP filter
Default Value (objectclass=*)
Syntax DirectoryString
Example filter: (l=Sunnyvale)
2.3.16. cn =unique id gen er at or
90 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 91

The unique ID generator configuration attributes are s tored under cn=uniqueid
generator,cn=c onfig. The cn =uniqueid gen erator entry is an ins tance of the
extensible Object object clas s.
nsSta t e
This attribute s aves the s tate of the unique ID generator across server res tarts . This attribute is
maintained by the server. Do not edit it.
Pa ra met e r De script ion
Entry DN cn=uniqueid generator, cn=config
Valid Values
Default Value
Syntax DirectoryString
Example nsState: AbId0c3oMIDUntiLCyYNGgAAAAAAAAAA
2.4 . Configuration Object Classes
Many configuration entries simply us e the e xtensibleO bje ct object class , but some require other
object classes. T hese configuration object classes are lis ted here.
2.4 .1. cha nge LogEntry (Object Cla ss)
This object class is used for entries which store changes made to the Directory Server entries.
To configure Directory Server to maintain a changelog that is compatible with the changelog
implemented in Directory Server 4.1x, enable the Retro Changelog Plug-in. Each entry in the changelog
has the changeLogEntry object clas s.
This object class is defined in Changelog Internet Draft.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.1
Require d Att ributes
objectClas s Defines the object classes for the entry.
changeNumber Contains a number assigned arbitrarily to the
changelog.
changeTime The time at which a change took place.
changeType The type of change performed on an entry.
targetDn T he distinguished name of an entry added,
modified or deleted on a supplier s erver.
Allowe d At t ributes
changes Changes made to the Directory Server.
deleteOldRdn A flag that defines whether the old Relative
Distinguished Name (RDN) of the entry should be
kept as a dis tinguis hed attribute of the entry or
should be deleted.
newRdn New RDN of an entry that is the target of a
modrdn or moddn operation.
newSuperior Name of the entry that becomes the immediate
superior of the exis ting entry when processing a
MODDN operation.
2.4 .2. dire ct orySe rve rFea ture (O bje ct Cla ss)
This object class is used specifically for entries which identify a feature of the directory service. This
object class is defined by Directory Server.
Super ior Cla ss
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 91
Page 92

top
OID
2.16.840 .1.113730.3.2.40
Require d Att ributes
Attribut e D efinit ion
objectClas s Gives the object class es ass igned to the entry.
Allowe d At t ributes
Attribut e D efinit ion
cn Specifies the common name of the entry.
multiLineDescription Gives a text description of the entry.
oid Specifies the OID of the feature.
2.4 .3. nsBa cke ndInstance (Object C lass)
This object class is used for the Directory Server backend, or database, instance entry. This object
class is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.109
Require d Att ributes
Attribut e D efinit ion
objectClas s Defines the object classes for the entry.
cn Gives the common name of the entry.
2.4 .4 . nsCha ngelog4 C onfig (O bje ct Cla ss)
In order for Directory Server 8.1 to replicate between Directory Server 4.x servers , the Directory Server
8.1 instance must have a s pecial changelog configured. This object class defines the configuration for
the retro changelog.
This object class is defined for the Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.82
Allowe d At t ributes
Attribut e D efinit ion
cn (common Name) Gives the common name of the entry.
2.4 .5. nsCont ainer (O bje ct Cla ss)
Some entries do not define any specific entity, but they create a defined space within the directory tree
as a parent entry for similar or related child entries. These are container entries, and they are identified
by the nsCon tainer object class.
Super ior Cla ss
top
OID
92 Cha p ter 2. Core Server Configu ra tio n Reference
Page 93

2.16.840 .1.113730.3.2.104
Require d Att ributes
Attribut e D efinit ion
objectClas s Defines the object classes for the entry.
cn Gives the common name of the entry.
2.4 .6. nsDS5 Replica (Object Cla ss)
This object class is for entries which define a replica in database replication. Many of these attributes
are s et within the backend and cannot be modified.
Information on the attributes for this object class are lis ted with the core configuration attributes in
chapter 2 of the Directory Server Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.108
Require d Att ributes
objectClas s Defines the object classes for the entry.
nsDS5ReplicaId Specifies the unique ID for suppliers in a
replication environment.
nsDS5ReplicaRoot Specifies the s uffix DN at the root of a replicated
area.
Allowe d At t ributes
cn Gives the name for the replica.
nsDS5Flags Specifies information that has been previous ly set
in flags .
nsDS5ReplicaAutoReferral Sets whether the server will follow configured
referrals for the Directory Server database.
nsDS5ReplicaBindDN Specifies the DN to us e when a supplier s erver
binds to a consumer.
nsDS5ReplicaChangeCount Gives the total number of entries in the changelog
and whether they have been replicated.
nsDS5ReplicaLegacyCons umer Specifies whether the replica is a legacy
consumer.
nsDS5ReplicaName Specifies the unique ID for the replica for internal
operations.
nsDS5ReplicaPurgeDelay Specifies the time in s econds before the
changelog is purged.
nsDS5ReplicaReferral Specifies the URLs for user-defined referrals.
nsDS5ReplicaTombstonePurgeInterval Specifies the time interval in seconds between
purge operation cycles.
nsDS5ReplicaType Defines the type of replica, such as a read-only
consumer.
nsDS5Task Launches a replication tas k, such as dumping the
database contents to LDIF; this is used internally
by the Directory Server supplier.
nsState Stores information on the clock so that proper
change sequence numbers are generated.
2.4 .7. nsDS5 ReplicationAgree ment (Object C lass)
Entries with the nsDS5 Replicatio nAgreem ent object class store the information s et in a replication
agreement. Information on the attributes for this object class are in chapter 2 of the Directory Server
Configuration, Command, and File Reference.
This object class is defined in Directory Server.
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 93
Page 94

Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.103
Require d Att ributes
objectClas s Defines the object classes for the entry.
cn Used for naming the replication agreement.
Allowe d At t ributes
description Contains a free text description of the replication
agreement.
nsDS5BeginReplicaRefresh Initializes a replica manually.
nsds5debugreplicatimeout Gives an alternate timeout period to use when the
replication is run with debug logging.
nsDS5ReplicaBindDN Specifies the DN to us e when a supplier s erver
binds to a consumer.
nsDS5ReplicaBindMethod Specifies the method (SSL or s imple
authentication) to use for binding.
nsDS5ReplicaBusyWaitTime Specifies the amount of time in seconds a
supplier s hould wait after a consumer sends back
a bus y res pons e before making another attempt
to acquire acces s.
nsDS5ReplicaChangesSentSinceStartup The number of changes sent to this replica since
the s erver started.
nsDS5ReplicaCredentials Specifies the password for the bind DN.
nsDS5ReplicaHost Specifies the hostname for the cons umer replica.
nsDS5ReplicaLastInitEnd States when the initialization of the consumer
replica ended.
nsDS5ReplicaLastInitStart States when the initialization of the consumer
replica started.
nsDS5ReplicaLastInitStatus T he s tatus for the initialization of the consumer.
nsDS5ReplicaLastUpdateEnd States when the most recent replication s chedule
update ended.
nsDS5ReplicaLastUpdateStart States when the most recent replication schedule
update started.
nsDS5ReplicaLastUpdateStatus Provides the s tatus for the most recent replication
schedule updates.
nsDS5ReplicaPort Specifies the port number for the remote replica.
nsDS5ReplicaRoot Specifies the s uffix DN at the root of a replicated
area.
nsDS5ReplicaSessionPaus eT ime Specifies the amount of time in seconds a
supplier s hould wait between update s essions .
nsDS5ReplicatedAttributeList Specifies any attributes that will not be replicated
to a consumer server.
nsDS5ReplicaTimeout Specifies the number of s econds outbound LDAP
operations will wait for a response from the
remote replica before timing out and failing.
nsDS5ReplicaTrans portInfo Specifies the type of transport used for
trans porting data to and from the replica.
nsDS5ReplicaUpdateInProgress States whether a replication schedule update is in
progress .
nsDS5ReplicaUpdateSchedule Specifies the replication s chedule.
nsDS50ruv Manages the internal s tate of the replica via the
replication update vector.
nsruvReplicaLastModified Contains the most recent time that an entry in the
replica was modified and the changelog was
updated.
2.4 .8. nsDSWindowsRe plica t ionAgreeme nt (O bje ct Cla ss)
Stores the s ynchronization attributes that concern the s ynchronization agreement. Information on the
94 Cha pter 2. Co re Server Con fig uration Reference
Page 95

attributes for this object clas s are in chapter 2 of the Red Hat Directory Server Configuration, Command,
and File Reference.
This object class is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.503
Require d Att ributes
objectClas s Defines the object classes for the entry.
cn Gives the name of the synchronization
agreement.
Allowe d At t ributes
description Contains a text description of the synchroniz ation
agreement.
nsDS5BeginReplicaRefresh Initiates a manual s ynchronization.
nsds5debugreplicatimeout Gives an alternate timeout period to use when the
synchroniz ation is run with debug logging.
nsDS5ReplicaBindDN Specifies the DN to us e when the Directory
Server binds to the Windows s erver.
nsDS5ReplicaBindMethod Specifies the method (SSL or s imple
authentication) to use for binding.
nsDS5ReplicaBusyWaitTime Specifies the amount of time in seconds the
Directory Server s hould wait after the Windows
server s ends back a busy response before
making another attempt to acquire access.
nsDS5ReplicaChangesSentSinceStartup Shows the number of changes sent since the
Directory Server s tarted.
nsDS5ReplicaCredentials Specifies the credentials for the bind DN.
nsDS5ReplicaHost Specifies the hostname for the Windows domain
controller of the Windows server being
synchroniz ed.
nsDS5ReplicaLastInitEnd States when the last total update
(res ynchronization) of the Windows server
ended.
nsDS5ReplicaLastInitStart States when the last total update
(res ynchronization) of the Windows server
started.
nsDS5ReplicaLastInitStatus T he s tatus for the total update
(res ynchronization) of the Windows server.
nsDS5ReplicaLastUpdateEnd States when the most recent update ended.
nsDS5ReplicaLastUpdateStart States when the most recent update started.
nsDS5ReplicaLastUpdateStatus Provides the s tatus for the most recent updates.
nsDS5ReplicaPort Specifies the port number for the Windows
server.
nsDS5ReplicaRoot Specifies the root suffix DN of the Directory
Server.
nsDS5ReplicaSessionPaus eT ime Specifies the amount of time in seconds the
Directory Server s hould wait between update
sessions.
nsDS5ReplicaTimeout Specifies the number of s econds outbound LDAP
operations will wait for a response from the
Windows server before timing out and failing.
nsDS5ReplicaTrans portInfo Specifies the type of transport used for
trans porting data to and from the Windows
server.
nsDS5ReplicaUpdateInProgress States whether an update is in progress .
nsDS5ReplicaUpdateSchedule Specifies the s ynchronization schedule.
nsDS50ruv Manages the internal s tate of the Directory Server
sync peer using the replication update vector
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 95
Page 96

(RUV).
nsds7DirectoryReplicaSubtree Specifies the Directory Server suffix (root or sub)
that is synced.
nsds7DirsyncCookie Contains a cookie set by the s ync s ervice that
functions as an RUV.
nsds7NewWinGroupSyncEnabled Specifies whether new Windows group accounts
are automatically created on the Directory Server.
nsds7NewWinUserSyncEnabled Specifies whether new Windows user accounts
are automatically created on the Directory Server.
nsds7WindowsDomain Identifies the Windows domain being
synchroniz ed; analogous to nsDS5ReplicaHost
in a replication agreement.
nsds7WindowsReplicaSubtree Specifies the Windows s erver suffix (root or sub)
that is synced.
nsruvReplicaLastModified Contains the most recent time that an entry in the
Directory Server s ync peer was modified and the
changelog was updated.
winSyncInterval Sets how frequently, in seconds , the Directory
Server polls the Windows server for updates to
write over. If this is not set, the default is 300,
which is 300 s econds or five (5) minutes .
2.4 .9. nsMa ppingT re e (Object Cla ss)
A mapping tree maps a suffix to the backend. Each mapping tree entry uses the nsMappingT ree
object class. T his object clas s is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.110
Require d Att ributes
Attribut e D efinit ion
objectClas s Gives the object class es ass igned to the entry.
cn Gives the common name of the entry.
2.4 .10. nsSa slMa pping (O bje ct Class)
This object class is used for entries which contain an identity mapping configuration for mapping SASL
attributes to the Directory Server attributes.
This object class is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.317
Require d Att ributes
objectClas s Defines the object classes for the entry.
cn Gives the name of the SASL mapping entry.
nsSaslMapBaseDNTemplate Contains the search bas e DN template.
nsSaslMapFilterT emplate Contains the search filter template.
nsSaslMapRegexString Contains a regular expression to match SASL
identity s trings.
2.4 .11. nsslapdC onfig (O bje ct Cla ss)
The nssla pdC onfig object clas s defines the configuration object, cn= config, for the Directory
Server instance.
96 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 97

This object class is defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.39
Require d Att ributes
Attribut e D efinit ion
objectClas s Gives the object class es ass igned to the entry.
Allowe d At t ributes
Attribut e D efinit ion
cn Gives the common name of the entry.
2.4 .12. passwordpolicy (Object Cla ss)
Both local and global pass word policies take the passwordpolicy object class. This object class is
defined in Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.13
Require d Att ributes
Attribut e D efinit ion
objectClas s Gives the object class es ass igned to the entry.
Allowe d At t ributes
Attribut e D efinit ion
passwordMaxAge Sets the number of seconds after which user
passwords expire.
passwordExp Identifies whether the us er's pas sword expires
after an interval given by the password MaxAge
attribute.
passwordMinLength Sets the minimum number of characters that must
be us ed in pass words .
passwordKeepHistory Sets whether to keep a password history for a
user.
passwordInHistory Sets the number of passwords the directory
stores in the his tory.
passwordChange Identifies whether or not users is allowed to
change their own pass word.
passwordWarning Sets the number of seconds before a warning
mess age is sent to us ers whos e pas sword is
about to expire.
passwordLockout Identifies whether or not users are locked out of
the directory after a given number of failed bind
attempts .
passwordMaxFailure Sets the number of failed bind attempts after
which a user will be locked out of the directory.
passwordResetDuration Sets the period of time before the s erver resets
the retry count to zero.
passwordUnlock Sets whether a us er is locked out until the
password is reset by an administrator or whether
the us er can log in again after a given lockout
duration. The default is to allow a user to log back
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 97
Page 98

in after the lockout period.
passwordLockoutDuration Sets the time, in seconds, that users will be
locked out of the directory.
passwordCheckSyntax Identifies whether or not the password syntax is
checked by the s erver before the pas sword is
saved.
passwordMustChange Identifies whether or not to change their
passwords when they first login to the directory
or after the pass word is res et by the Directory
Manager.
passwordStorageScheme Sets the type of encryption used to store
Directory Server pass words .
passwordMinAge Sets the number of seconds that must pass
before a user can change their pas sword.
passwordResetFailureCount Sets the time, in seconds, after which the
password failure counter will be reset. Each time
an invalid pass word is s ent from the user's
account, the password failure counter is
incremented.
passwordGraceLimit Sets the number of grace logins permitted when a
user's password is expired.
passwordMinDigits Sets the minimum number of numeric characters
(0 through 9) which must be used in the
password.
passwordMinAlphas Sets the minimum number of alphabetic
characters that must be us ed in the password.
passwordMinUppers Sets the minimum number of upper case
alphabetic characters, A to Z , which must be used
in the pass word.
passwordMinLowers Sets the minimum number of lower case
alphabetic characters, a to z , which must be used
in the pass word.
passwordMinSpecials Sets the minimum number of s pecial ASCII
characters, such as !@#$., which must be used
in the pass word.
passwordMin8bit Sets the minimum number of 8-bit characters
used in the pass word.
passwordMaxRepeats Sets the maximum number of times that the same
character can be used in row.
passwordMinCategories Sets the minimum number of categories which
must be used in the pass word.
passwordMinTokenLength Sets the length to check for trivial words .
2.5. Legacy Attributes
The attributes were standard with Directory Server 4.x and older. This are still included with the schema
for compatibility, but are not for current vers ions of the Directory Server.
2.5.1 . Le ga cy S erver At tribut e s
These attributes were originally used to configure the s erver instance entries for Directory Server 4 .x
and older servers .
2.5.1 .1 . LD APServer (Object Cla ss)
This object class identifies the LDAP server information. It is defined by Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.35
Require d Att ributes
Attribut e D efinit ion
objectClas s Gives the object class es ass igned to the entry.
98 Cha pter 2. Co re S erver Con fig u ratio n Reference
Page 99

cn Specifies the common name of the entry.
Allowe d At t ributes
Attribut e D efinit ion
description Gives a text description of the entry.
l (localityName) Gives the city or geographical location of the
entry.
ou (organizationalUnitName) Gives the organizational unit or division to which
the account belongs.
seeAlso Contains a URL to another entry or s ite with
related information.
generation Store the server generation string.
changelogmaximumage Specifies changelog maximum age.
changeLogMaximumSize Specifies maximum changelog size.
2.5.1 .2 . cha ngeLogMa ximumAge
This s ets the maximum age for the changelog maintained by the server.
OID 2.16.840 .1.113730.3.1.200
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.1 .3. change LogMaximumConcurrentWrites
This attribute s ets the maximum number of concurrent writes that can be written to the changelog.
OID 2.16.840 .1.113730.3.1.205
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.1 .4 . change LogMaximumSize
This attribute s ets the maximum siz e for the changelog.
OID 2.16.840 .1.113730.3.1.201
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.1 .5 . ge ne ra tion
This attribute contains a byte vector that uniquely identifies that specific server and vers ion. This
number is used to distinguish between servers during replication.
OID 2.16.840 .1.113730.3.1.612
Syntax IA5String
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.1 .6 . nsS ynchUnique At tribute
This attribute is used for Windows synchronization.
OID 2.16.840 .1.113730.3.1.407
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.1 .7 . nsS ynchUserIDFormat
This attribute is used for Windows synchronization.
OID 2.16.840 .1.113730.3.1.406
Syntax DirectoryString
Red Hat D irectory S erver 8.1 Co nfigurati on a nd Co mman d Reference 99
Page 100

Multi- or Single-Valued Multi-valued
Defined in Directory Server
2.5.2 . Le ga cy Re plicat ion Attribut es
These attributes were originally used to configure replication for Directory Server 4.x and older s ervers.
Some forms of replication, like consumer-initiated replication, are no longer supported.
WARNING
These attributes are for reference only. Do not attempt to configure replication using thes e
attributes. See Section 2.4.6, “ns DS5Replica (Object Class)” and Section 2.4.8,
“ns DSWindowsReplicationAgreement (Object Class )” for attributes to configure replicas and
replication agreements.
2.5.2 .1 . cirRe plicaS ource (Object C lass)
The cirRe plicaSource is an object that is used for consumer-initiated replication. This object class
is defined by Directory Server.
Super ior Cla ss
top
OID
2.16.840 .1.113730.3.2.11
Require d Att ributes
Attribut e D efinit ion
objectClas s Defines the object classes for the entry.
cn Specifies the common name of the supplier
server.
Allowe d At t ributes
Attribut e D efinit ion
cirReplicaRoot Stores the root suffix to be replicated.
cirHost Identifies the host of the s upplier.
cirPort Identifies the port of the s upplier.
cirBindDN Specifies the bind DN.
cirUsePersistentSearch Specifies a flag whether or not to use the
pers istent search.
cirUseSSL Specifies a flag whether or not to use SSL.
cirBindCredentials Specifies a pass word of cirBindDN.
cirLastUpdateApplied Timestamp of the last replica update.
cirUpdateSchedule Schedule when the replica update occurs.
cirSyncInterval Identifies the interval to do s ynchronization.
cirUpdateFailedAt Stores the timestamp of the last failed update
attempt.
cirBeginORC Sets whether the databas e deletes its contents
before beginning replication.
replicaNickname Identifies the name for the replication agreement.
replicaEntryFilter Identifies the entries to be replicated.
replicatedAttributeList Identifies attribute list to be replicated.
2.5.2 .2 . cirB eginO RC
For online replication creation (ORC), the cons umer server can dump its entire databas e and allows the
supplier to s end it completely fres h information. The cirBeginORC attribute sets whether the consumer
deletes its database. Its values are either start or stop.
OID 2.16.840 .1.113730.3.1.90
Syntax DirectoryString
Multi- or Single-Valued Multi-valued
100 Chap ter 2. Core Server Confi gura tion Reference
 Loading...
Loading...