Raritan Dominion KX2-864, Dominion KX2-832 User Manual

Dominion KX II (KX2-832 and KX2-864)
User Guide
Release 2.1.8
Copyright © 2009 Raritan, Inc.
DKX2-v2.1.8-0J-E
April 2009
255-62-4023-00
This document contains proprietary information that is protected by copyright. All rights reserved. No
part of this document may be photocopied, reproduced, or translated into another language without
express prior written consent of Raritan, Inc.
© Copyright 2009 Raritan, Inc., CommandCenter®, Dominion®, Paragon® and the Raritan company
logo are trademarks or registered trademarks of Raritan, Inc. All rights reserved. Java® is a
registered trademark of Sun Microsystems, Inc. Internet Explorer® is a registered trademark of
Microsoft Corporation. Netscape® and Netscape Navigator® are registered trademarks of Netscape
Communication Corporation. All other trademarks or registered tradema rks a re the prope rty of their
respective holders.
FCC Information
This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a commercial installation. This equipment generates, uses, and can
radiate radio frequency energy and if not installed and used in accordance with the instructions, may
cause harmful interference to radio communications. Operation of this equipment in a residential
environment may cause harmful interference.
VCCI Information (Japan)
Raritan is not responsible for damage to this product resulting from accident, disaster, misuse, abuse,
non-Raritan modification of the product, or other events outside of Raritan's rea son able control or not
arising under normal operating conditions.
Contents
Chapter 1 Introduction 1
Dominion KX II Help.......................................................................................................................1
Related Documentation.......................................................................................................1
What's New in the Help..................................................................................................................2
Dominion KX II Overview...............................................................................................................3
Virtual Media..................................................................................................................................5
Product Photos ..............................................................................................................................6
Product Features ...........................................................................................................................8
Hardware.............................................................................................................................8
Software...............................................................................................................................9
Terminology...................................................................................................................................9
Package Contents........................................................................................................................11
Chapter 2 Installation and Configuration 12
Overview......................................................................................................................................12
Default Login Information.............................................................................................................12
Getting Started.............................................................................................................................13
Step 1: Configure KVM Target Servers.............................................................................13
Step 2: Configure Network Firewall Settings.....................................................................24
Step 3: Connect the Equipment.........................................................................................25
Step 4: Configure the Dominion KX II ...............................................................................28
Valid Special Characters for Target Names......................................................................32
Step 5 (Optional): Configure Keyboard Language............................................................35
Chapter 3 Working with Target Servers 37
Interfaces..................................................................................................................... ................37
Dominion KX II Local Console Interface............................................................................38
Dominion KX II Remote Console Interface........................................................................38
Multi-Platform Client Interface...........................................................................................50
Virtual KVM Client........................................................................................................................51
Overview............................................................................................................................51
Connecting to a KVM Target Server .................................................................................51
VKC Toolbar and Shortcut Keys........................................................................................52
Switching Between KVM Target Servers ..........................................................................53
Power Controlling a Target Server....................................................................................54
Disconnecting KVM Target Servers ..................................................................................55
Choosing USB Profiles......................................................................................................55
Connection Properties.......................................................................................................56
Connection Information .....................................................................................................58
Keyboard Options..............................................................................................................58
iii

Contents
Video Properties................................................................................................................63
Mouse Options...................................................................................................................67
VKC Virtual Media.............................................................................................................72
Tool Options ......................................................................................................................72
View Options......................................................................................................................74
Help Options......................................................................................................................75
Chapter 4 Virtual Media 76
Overview......................................................................................................................................77
Prerequisites for Using Virtual Media..........................................................................................79
File Server Setup (File Server ISO Images Only)........................................................................80
Using Virtual Media......................................................................................................................81
Connecting to Virtual Media.........................................................................................................83
Local Drives.......................................................................................................................83
Conditions when Read/Write is Not Available...................................................................84
CD-ROM/DVD-ROM/ISO Images......................................................................................84
Disconnecting Virtual Media........................................................................................................86
Chapter 5 USB Profiles 87
Overview......................................................................................................................................87
CIM Compatibility.........................................................................................................................88
Available USB Profiles.................................................................................................................88
Selecting Profiles for a KVM Port ................................................................................................95
Chapter 6 User Management 96
User Groups.................................................................................................................................96
User Group List..................................................................................................................97
Relationship Between Users and Groups .........................................................................97
Adding a New User Group.................................................................................................97
Modifying an Existing User Group...................................................................................104
Users..........................................................................................................................................105
User List...........................................................................................................................105
Adding a New User..........................................................................................................106
Modifying an Existing User..............................................................................................106
Logging a User Off (Force Logoff)...................................................................................107
Authentication Settings..............................................................................................................108
Implementing LDAP/LDAPS Remote Authentication......................................................109
Returning User Group Information from Active Directory Server....................................112
Implementing RADIUS Remote Authentication...............................................................113
Returning User Group Information via RADIUS..............................................................115
RADIUS Communication Exchange Specifications.........................................................115
User Authentication Process...........................................................................................117
iv
Contents
Changing a Password................................................................................................................119
Chapter 7 Device Management 120
Network Settings........................................................................................................................120
Network Basic Settings....................................................................................................121
LAN Interface Settings.....................................................................................................123
Device Services.........................................................................................................................125
Modem Settings.........................................................................................................................125
Configuring Date/Time Settings.................................................................................................127
Event Management....................................................................................................................129
Configuring Event Management - Settings......................................................................129
Event Management - Destinations ..................................................................................131
Power Supply Setup ..................................................................................................................135
Configuring Ports.......................................................................................................................137
Configuring Standard Target Servers..............................................................................138
Configuring Powerstrip Targets (Non-PX).......................................................................138
Configuring Blade Chassis..............................................................................................145
Configuring USB Profiles (Port Page).............................................................................167
Configuring Dominion KX II Local Port Settings..............................................................169
Chapter 8 Powerstrip Outlet Control 174
Overview....................................................................................................................................174
Turning Outlets On/Off and Cycling Power ...............................................................................175
Chapter 9 Security Management 178
Security Settings........................................................................................................................178
Login Limitations..............................................................................................................179
Strong Passwords ...........................................................................................................180
User Blocking...................................................................................................................181
Encryption & Share..........................................................................................................182
Checking Your Browser for AES Encryption .............................................................................185
Configuring IP Access Control...................................................................................................185
SSL Certificates.........................................................................................................................188
Chapter 10 Maintenance 191
Audit Log....................................................................................................................................191
Device Information.....................................................................................................................192
Backup and Restore ..................................................................................................................193
USB Profile Management..........................................................................................................195
Handling Conflicts in Profile Names................................................................................196
v

Contents
Upgrading CIMs.........................................................................................................................196
Upgrading Firmware ..................................................................................................................197
Upgrade History.........................................................................................................................199
Rebooting...................................................................................................................................199
Stopping CC-SG Management..................................................................................................201
Chapter 11 Diagnostics 203
Network Interface Page .............................................................................................................203
Network Statistics Page.............................................................................................................204
Ping Host Page..........................................................................................................................206
Trace Route to Host Page .........................................................................................................206
Device Diagnostics ....................................................................................................................208
Chapter 12 Command Line Interface (CLI) 210
Overview....................................................................................................................................210
Accessing the Dominion KX II Using CLI...................................................................................211
SSH Connection to the Dominion KX II.....................................................................................211
SSH Access from a Windows PC....................................................................................211
SSH Access from a UNIX/Linux Workstation..................................................................212
Telnet Connection to the Dominion KX II...................................................................................212
Enabling Telnet................................................................................................................212
Access Telnet from a Windows PC.................................................................................212
Logging In..................................................................................................................................213
Navigation of the CLI .................................................................................................................214
Completion of Commands...............................................................................................214
CLI Syntax -Tips and Shortcuts.......................................................................................214
Common Commands for All Command Line Interface Levels........................................215
Initial Configuration Using CLI...................................................................................................215
Setting Parameters..........................................................................................................215
Setting Network Parameters............................................................................................216
CLI Prompts...............................................................................................................................216
CLI Commands..........................................................................................................................216
Security Issues ................................................................................................................217
Administering the Dominion KX II Console Server Configuration Commands..........................218
Configuring Network ..................................................................................................................218
Interface Command.........................................................................................................219
Name Command...........................................................................................................219
IPv6 Command................................................................................................................220
Chapter 13 Dominion KX II Local Console 221
Overview....................................................................................................................................221
Using the Dominion KX II Local Console...................................................................................221
Simultaneous Users ........................................................................................................221
vi
Contents
Dominion KX II Local Console Interface....................................................................................222
Security and Authentication.......................................................................................................222
Available Resolutions.................................................................................................................223
Port Access Page (Local Console Server Display) ...................................................................224
Hot Keys and Connect Keys......................................................................................................226
Connect Key Examples...................................................................................................226
Special Sun Key Combinations .................................................................................................227
Accessing a Target Server ........................................................................................................228
Returning to the Dominion KX II Local Console Interface.........................................................228
Local Port Administration...........................................................................................................228
Configuring Dominion KX II Local Console Local Port Settings......................................229
Dominion KX II Local Console Factory Reset.................................................................232
Resetting the Dominion KX II Using the Reset Button ..............................................................233
Appendix A Specifications 234
Physical Specifications ..............................................................................................................234
Environmental Requirements ....................................................................................................237
Computer Interface Modules (CIMs)..........................................................................................237
Supported CIMs and Operating Systems (Target Servers).......................................................239
Certified Modems.......................................................................................................................245
Devices Supported by the KX2-832 and KX2-864 Extended Local Port...................................245
Target Server Connection Distance and Video Resolution.......................................................245
KX2-832 and KX2-864 Extended Local Port Recommended Maximum Distances..................246
Remote Connection...................................................................................................................246
Supported Video Resolutions....................................................................................................246
Supported Keyboard Languages...............................................................................................247
Supported Operating Systems (Clients)....................................................................................248
Supported Browsers ..................................................................................................................250
TCP and UDP Ports Used.........................................................................................................250
Network Speed Settings ............................................................................................................252
Appendix B Updating the LDAP Schema 254
Returning User Group Information.............................................................................................254
From LDAP......................................................................................................................254
From Microsoft Active Directory ......................................................................................254
vii

Contents
Setting the Registry to Permit Write Operations to the Schema ...............................................255
Creating a New Attribute............................................................................................................255
Adding Attributes to the Class ...................................................................................................256
Updating the Schema Cache.....................................................................................................258
Editing rciusergroup Attributes for User Members.....................................................................258
Appendix C Informational Notes 262
Overview....................................................................................................................................262
Java Runtime Environment (JRE) .............................................................................................262
IPv6 Support Notes....................................................................................................................263
Keyboards..................................................................................................................................264
Non-US Keyboards..........................................................................................................264
Macintosh Keyboard........................................................................................................267
Mouse Pointer Synchronization (Fedora)..................................................................................267
Dell Chassis Cable Lengths and Video Resolutions .................................................................268
Resolving Fedora Core Focus...................................................................................................268
Running VKC on Fedora with FireFox 3.0.x and JRE 1.5.0_16................................................268
SUSE/VESA Video Modes ........................................................................................................269
USB Ports and Profiles..............................................................................................................269
VM-CIMs and DL360 USB Ports.....................................................................................269
Help for Choosing USB Profiles ......................................................................................270
CIMs...........................................................................................................................................272
Windows 3-Button Mouse on Linux Targets....................................................................272
Windows 2000 Composite USB Device Behavior for Virtual Media................................272
Virtual Media..............................................................................................................................273
Virtual Media Not Refreshed After Files Added...............................................................273
Target BIOS Boot Time with Virtual Media......................................................................273
CC-SG .......................................................................................................................................273
Virtual KVM Client Version Not Known from CC-SG Proxy Mode..................................273
Single Mouse Mode - Connecting to a Dominion KX II Target Under CC-SG Control Via
VKC Using Firefox...........................................................................................................273
MPC and VKC Connection Settings................................................................................273
Proxy Mode and MPC .....................................................................................................273
Moving Between Ports of the Dominion KX II .................................................................274
viii
Contents
Appendix D FAQs 275
General Questions.....................................................................................................................276
Remote Access..........................................................................................................................278
Universal Virtual Media..............................................................................................................280
USB Profiles...............................................................................................................................281
Ethernet and IP Networking.......................................................................................................283
IPv6 Networking.........................................................................................................................290
Servers.......................................................................................................................................292
Blade Servers ............................................................................................................................293
Installation..................................................................................................................................296
Local Port...................................................................................................................................298
Extended Local Port (Dominion KX2-832 and KX2-864 Models Only) .....................................300
Power Control............................................................................................................................301
Scalability...................................................................................................................................302
Computer Interface Modules (CIMs)..........................................................................................303
Security......................................................................................................................................304
Manageability.............................................................................................................................305
Miscellaneous............................................................................................................................306
Index 307
ix
Chapter 1
Introduction
In This Chapter
Dominion KX II Help..................................................................................1
What's New in the Help .............................................................................2
Dominion KX II Overview...........................................................................3
Virtual Media
Product Photos..........................................................................................6
Product Features.......................................................................................8
Terminology...............................................................................................9
Package Contents...................................................................................11
Dominion KX II Help
The Dominion KX II help provides information on how to install, set up,
and configure the Dominion KX II. It also includes information on
accessing target servers and power strips, using virtual media, managing
users and security, and maintaining and diagnosing the Dominion KX II.
A PDF version of the help can be downloaded from the Raritan
Firmware and Documentation page
http://www.raritan.com/support/firmware-and-documentation/ on the
Ra
website for the most up-to-date user guides available.
ritan web
..............................................................................................5
site. Raritan recommends that you refer to the Raritan
Related Documentation
The Dominion KX II help is accompanied by a Dominion KX II Quick
Setup Guide, which can be found on the Raritan Firmware and
Documentation page
d-d
http://www.raritan.com/support/firmware-an
ocumentation/ of Raritan's
website. Installation requirements and instructions for client applications
used with the Dominion KX II can be found in the KVM and Serial Client
User Guide, also found on the Raritan website. Where applicable,
specific client functions used with the Dominion KX II are included in this
help.
1

Chapter 1: Introduction
What's New in the Help
The following information has been added based on enhancements and
changes to the equipment and/or user documentation.
• Information on the new Extended Local port feature on the KX2-832
and KX2-864 has been added to the help.
• Information on features specific to the KX2-832 and KX2-864 has
been updated in the Help as needed.
• Specifications specific to the KX2-832 and KX2-864 have been
added to the Help.
Please see the release notes for a more detailed explanation of the
changes applied to this version of the help.
2

Chapter 1: Introduction
Dominion KX II Overview
The Dominion KX II is an enterprise-class, secure, digital KVM
(Keyboard, Video, Mouse) switch that provides BIOS-level (and up)
access and control of servers from anywhere in the world via a web
browser. Up to 64 servers can be controlled with a standard Dominion
KX II. With the Dominion KX II 8-user model, up to 32 servers can be
controlled with the KX2-832 and up to 64 servers can be controlled with
the KX2-864.
The Dominion KX II supports up to 8 video channels, allowing up to eight
concurrent users to connect to eight different video targets at any given
point in time. At the rack, the Dominion KX II provides BIOS-level control
of up to 64 servers and other IT devices from a single keyboard, monitor,
and mouse. The integrated remote access capabilities of the Dominion
KX II provide the same levels of control of your servers via a web
browser.
The Dominion KX II is easily installed using standard UTP (Cat 5/5e/6)
cabling. Its advanced features include virtual media, 128-bit encryption,
dual power supplies, remote power control, dual Ethernet, LDAP,
RADIUS, Active Directory, Syslog integration, external modem
capabilities, and web management. The Dominion KX II 8-user model
also provides an Extended Local port located on the back of the device.
These features enable you to deliver higher up-time, better productivity,
and bulletproof security - at any time from anywhere.
The Dominion KX II products can operate as standalone appliances and
do not rely on a central management device. For larger data centers and
enterprises, numerous Dominion KX II devices (along with Dominion SX
devices for remote serial console access and Dominion KSX for
remote/branch office management) can be integrated into a single logical
solution using Raritan's CommandCenter Secure Gateway (CC-SG)
management unit.
3

Chapter 1: Introduction
4
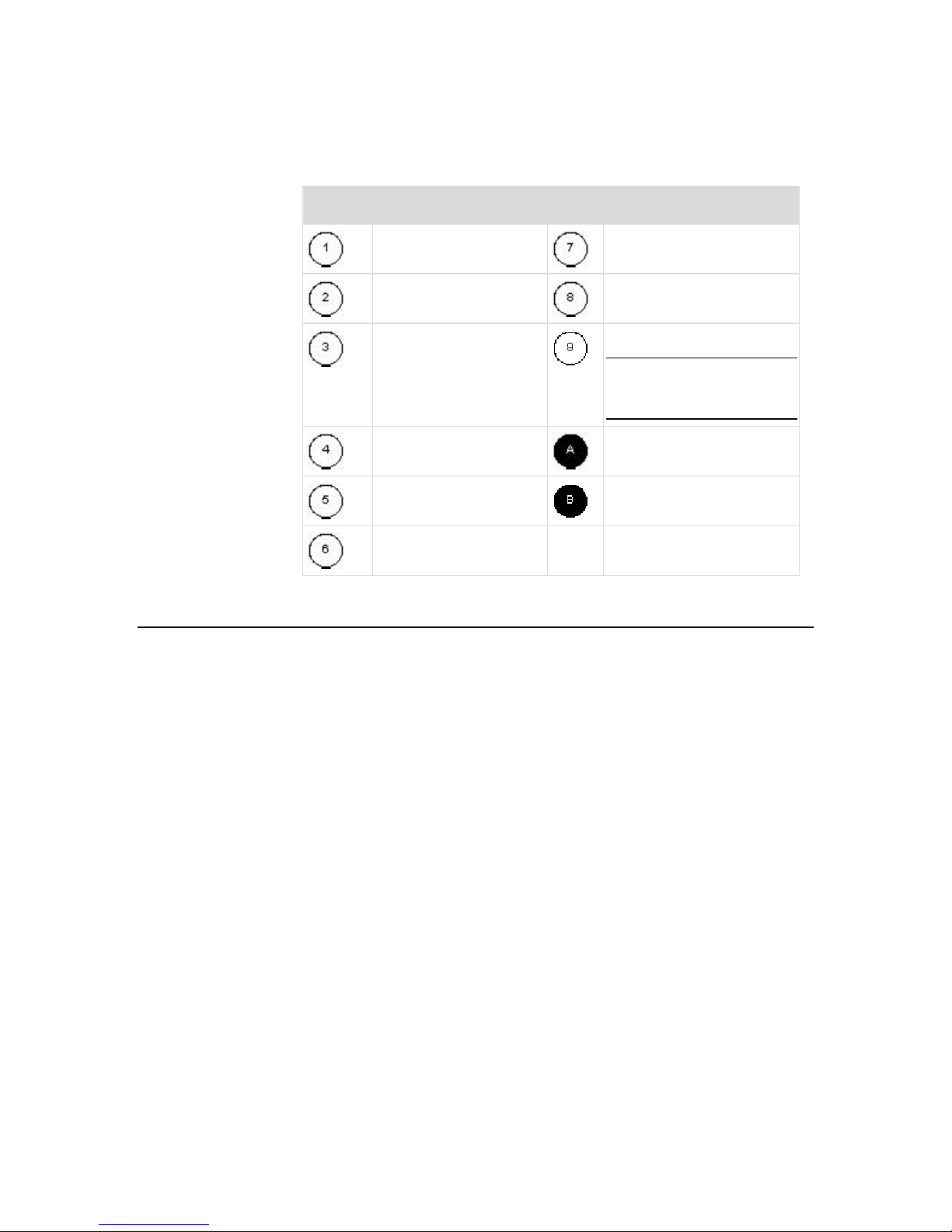
Chapter 1: Introduction
Diagram key
Cat5 cable
Remote virtual media USB
drive(s)
Virtual Media
Computer Interface
Module (CIM)
Dominion KX II
Power strip
Local access
Note: KX2-832 and
KX2-864 also use an
Extended Local port.
Remote KVM and serial
devices
Modem
Remote (network)
access
IP LAN/WAN
PSTN
All Dominion KX II models support virtual media. The benefits of virtual
media - mounting of remote drives/media on the target server to support
software installation and diagnostics - are now available in all of the
Dominion KX II models.
Each Dominion KX II comes equipped with virtual media to enable
remote management tasks using the widest variety of CD, DVD, USB,
internal and remote drives and images. Unlike other solutions, the
Dominion KX II supports virtual media access of hard drives and
remotely mounted images for added flexibility and productivity.
Virtual media sessions are secured using 128-bit AES or RC4
encryption.
The D2CIM-VUSB CIM and D2CIM-DVUSB (computer interface module)
support virtual media sessions to KVM target servers supporting the USB
2.0 interface. These CIMs also support Absolute Mouse
Synchronization™ as well as remote firmware update.
The black connector on the DVUSB CIM is used for keyboard and
mouse. The gray connector is used for virtual media. Keep both plugs of
the CIM connected to the device. The device may not operate properly if
both plugs are not connected to the target server.
5

Chapter 1: Introduction
Product Photos
Dominion KX II
KX2-832
6

Chapter 1: Introduction
KX2-864
7

Chapter 1: Introduction
Product Features
Hardware
• Integrated KVM-over-IP remote access
• 1U or 2U rack-mountable (brackets included)
• Dual power supplies with failover; autoswitching power supply with
power failure warning
• 8, 16, 32, or 64 (on KX2-464) server ports
• 32 (KX2-832) or 64 (KX2-864) server ports
• Up to 8 video channels, depending on the device model, that allows
up to 8 users to connect to the Dominion KX II at once
• Multiple user capacity (1/2/4/8 remote users; 1 local user)
• UTP (Cat5/5e/6) server cabling
• Dual Ethernet ports (10/100/1000 LAN) with failover
• Field upgradable
• Local User port for in-rack access
PS/2 keyboard/mouse ports. KX2-832 and KX2-864 are USB
only.
One front and three back panel USB 2.0 ports for supported USB
devices
Fully concurrent with remote user access
Local graphical user interface (GUI) for administration
• Extended Local Port provides extended reach to in-rack access on
KX2 devices
• Centralized access security
• Integrated power control
• LED indicators for dual power status, network activity, and remote
user status
• Hardware Reset button
• Serial port to connect to an external modem
8

Chapter 1: Introduction
Software
• Virtual media with D2CIM-VUSB and D2CIM-DVUSB CIMs
• Absolute Mouse Synchronization with D2CIM-VUSB CIM and
D2CIM-DVUSB CIMs
• Plug-and-Play
• Web-based access and management
• Intuitive graphical user interface (GUI)
• 128-bit encryption of complete KVM signal, including video and
virtual media
• LDAP, Active Directory, RADIUS, or internal authentication and
authorization
• DHCP or fixed IP addressing
• SNMP and Syslog management
• IPv4 and IPv6 support
• Power control associated directly with servers to prevent mistakes
• Integration with Raritan's CommandCenter Secure Gateway
(CC-SG) management unit
• CC Unmanage feature to remove device from CC-SG control
Terminology
This manual uses the following terminology for the components of a
typical Dominion KX II configuration:
9
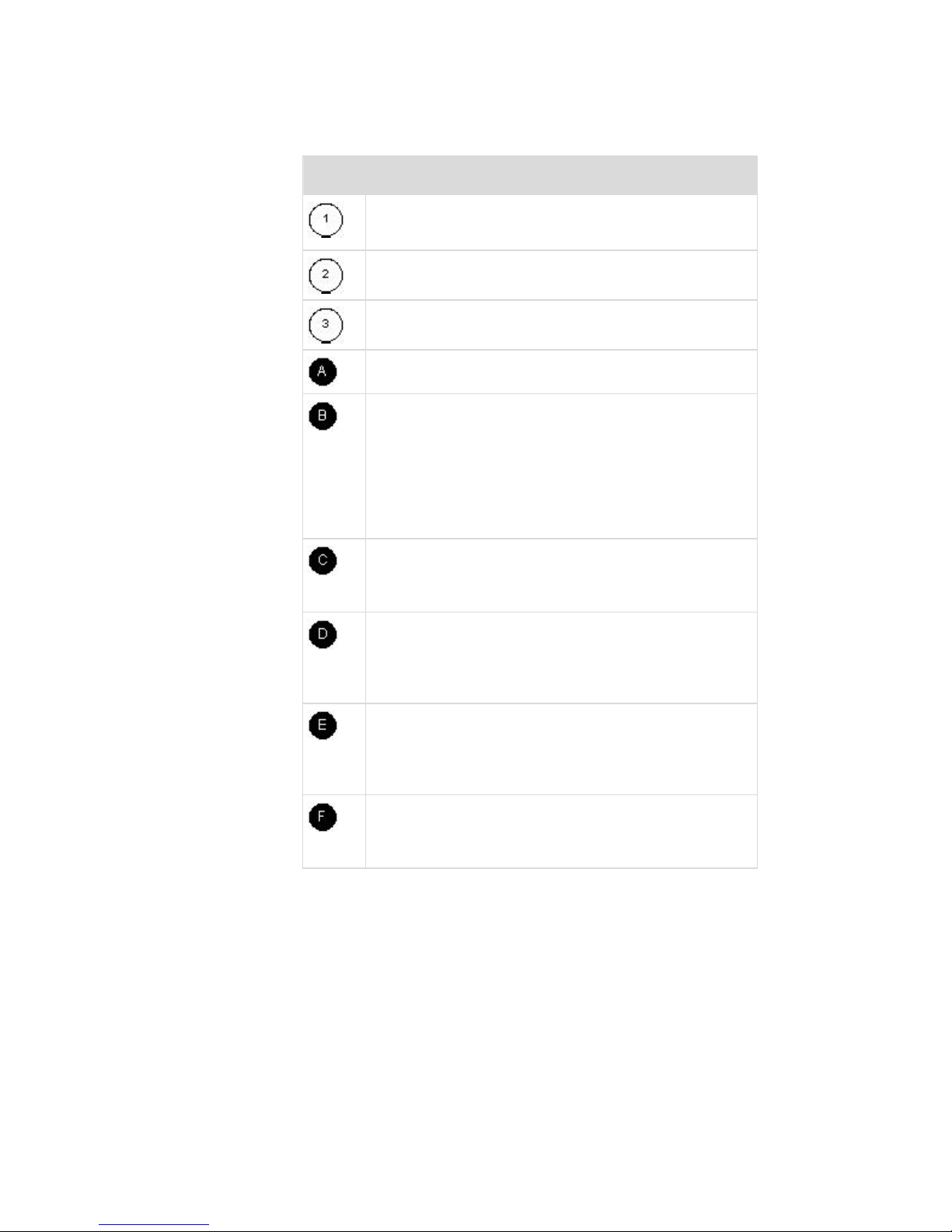
Chapter 1: Introduction
Diagram Key
TCP/IP
IPv4 and/or IPv6
KVM (Keyboard, Video, Mouse)
UTP Cable (Cat5/5e/6)
Dominion KX II
Local Access Console
Local User - an optional user console (consisting of a
keyboard, mouse, and multi-sync VGA monitor)
attached directly to the Dominion KX II to control KVM
target servers (directly at the rack, not through the
network). An Extended Local Port is also provided on
the DKX2-832 and DKX2-864 models.
Remote PC
Networked computers used to access and control KVM
target servers connected to the Dominion KX II.
CIMS
Dongles that connect to each target server or power
strip. Available for all of the supported operating
systems.
Target Servers
KVM Target Servers - servers with video cards and
user interfaces (for example, Windows, Linux, Solaris,
etc.) accessed remotely via the Dominion KX II.
Dominion PX Power Strips
Raritan power strips accessed remotely via the
Dominion KX II.
See Supported CIMs and Operating Systems (Target Servers) (on
page 239) for a list of the supported operating systems and CIMs, and
see Supported Oper
of the operating systems
ating Systems (Clients) (on page 248)for a list
supported by the Dominion KX II remotely.
10

Chapter 1: Introduction
Package Contents
Each Dominion KX II ships as a fully-configured stand-alone product in a
standard 1U (2U for DKX2-864) 19" rackmount chassis. Each Dominion
KX II device ships with the following contents:
Amount
Item
included
1 Dominion KX II device
1 Dominion KX II Quick Setup Guide
1 Rackmount kit
1 AC power cords
1 Cat5 network cable
1 Cat5 network crossover cable
1 Set of 4 rubber feet (for desktop use)
1 Application note
1 Warranty card
11
Chapter 2
Overview
Installation and Configuration
In This Chapter
Overview..................................................................................................12
Default Login Information ........................................................................12
Getting Started ........................................................................................13
This section provides a brief overview of the installation process. Each
step is further detailed in the remaining sections of this chapter.
To install and configure the Dominion KX II:
• Step 1: Configure KVM Target Servers (on page 13)
• Step 2: Con
• Step 3: Con
• Step 4: Con
• Step 5 (Opti
figure Network Firewall Settings (on page 24)
nect the Equipment (on page 25)
figure the Dominion KX II (on page 28)
onal): Configure Keyboard Language (on page 35)
Also includ
Specifically, the default IP address, user name, and password. See
Default Login Information (on page 12).
ed in this section is the default login information you will need.
Default Login Information
Default Value
User name The default user name is admin. This user has
administrative privileges.
Password The default password is raritan.
Passwords are case sensitive and must be entered
in the exact case combination in which they were
created. For example, the default password raritan
must be entered entirely in lowercase letters.
The first time you start the Dominion KX II, you are
required to change the default password.
IP address The Dominion KX II ships with the default IP
address of 192.168.0.192.
12

Chapter 2: Installation and Configuration
Default Value
Important: For backup and business continuity purposes, it is
strongly recommended that you create a backup administrator
user name and password and keep that information in a secure
location.
Getting Started
Step 1: Configure KVM Target Servers
KVM target servers are the computers that will be accessed and
controlled via the Dominion KX II. Before installing the Dominion KX II,
configure all KVM target servers to ensure optimum performance. This
configuration applies only to KVM target servers, not to the client
workstations (remote PCs) used to access the Dominion KX II remotely.
See Terminology (on page 9) for additional information.
Desktop Background
For optimal bandwidth efficiency and video performance, KVM target
servers running graphical user interfaces such as Windows, Linux,
X-Windows, Solaris, and KDE require configuration. The desktop
background need not be completely solid but desktop backgrounds
featuring photos or complex gradients might degrade performance.
13

Chapter 2: Installation and Configuration
Mouse Settings
The Dominion KX II operates in several mouse modes:
• Absolute Mouse Mode
• Intelligent Mouse Mode (do not use an animated mouse)
• Standard Mouse Mode
Mouse parameters do not have to be altered for Absolute Mouse
Synchronization but D2CIM-VUSB or D2CIM-DVUSB is required for this
mode. For both the Standard and Intelligent mouse modes, mouse
parameters must be set to specific values, which are described here.
Mouse configurations will vary on different target operating systems.
Consult your OS documentation for additional detail.
Intelligent mouse mode generally works well on most Windows
platforms. Intelligent mouse mode may produce unpredictable results
when active desktop is set on the target. For additional information on
Intelligent mouse mode settings, see Intelligent Mouse Mode (on page
70).
Servers with i
not support absolute mouse technology.
Windows 2000® Settings
™
(D2CIM-VUSB only)
ternal KVM switches inside the blade chassis typically do
n
To configure KVM target servers running Microsoft Windows
2000:
1. Configure the mouse settings:
a. Choose Start > Control Panel > Mouse.
b. Click the Motion tab.
Set the acceleration to None.
Set the mouse motion speed setting to exactly the middle
speed.
Click OK.
2. Disable transition effects:
a. Select the Display option from the Control Panel.
b. Click the Effects tab.
Deselect the "Use the following transition effect for menus
and tooltips" option.
Click OK and close the Control Panel.
14
Chapter 2: Installation and Configuration
Windows XP®/Windows 2003®
To configure KVM target servers running Microsoft Windows
XP/2003:
Configure the mouse settings:
1.
a. Choose Start > Control Panel > Mouse.
b. Click the Pointer Options tab.
c. In the Motion group:
Set the mouse motion speed setting to exactly the middle
speed.
Disable the Enhanced pointer precision option.
Disable the Snap To option.
Click OK.
Note: When you are running Windows 2003 on your target server, if
you access the server via KVM and perform any one off the actions
listed below, mouse synchronization may be lost if it has been
previously enabled. You will need to select the Synchronize Mouse
command from the Mouse menu in the client to enable it again.
Following are the actions that may cause this to occur:
- Opening a text editor.
- Accessing the Mouse Properties, Keyboard Properties, and Phone
and Mode Options from the Windows Control Panel.
2. Disable transition effects:
a. Select the Display option from the Control Panel.
b. Click the Appearance tab.
c. Click the Effects button.
d. Deselect the "Use the following transition effect for menus and
tooltips" option.
e. Click OK.
3. Close the Control Panel.
15
Chapter 2: Installation and Configuration
Note: For KVM target servers running Windows 2000 or XP, you may
wish to create a user name that will be used only for remote connections
through the Dominion KX II. This will enable you to keep the target
server's slow mouse pointer motion/acceleration settings exclusive to the
Dominion KX II connection.
Windows XP and 2000 login pages revert to preset mouse parameters
that differ from those suggested for optimal Dominion KX II performance.
As a result, mouse synchronization may not be optimal for these
screens.
WARNING! Proceed only if you are comfortable adjusting the registry
on Windows KVM target servers. You can obtain better Dominion KX
II mouse synchronization at the login pages by using the Windows
registry editor to change the following settings:
HKey_USERS\.DEFAULT\Control Panel\Mouse: > MouseSpeed =
0;MouseThreshold 1=0;MouseThreshold 2=0.
Windows Vista® Settings
To configure KVM target servers running Microsoft Windows
Vista:
Configure the mouse settings:
1.
a. Choose Start > Settings > Control Panel > Mouse.
b. Click the Pointer Options tab.
c. In the Motion group:
Set the mouse motion speed setting to exactly the middle
speed.
Disable the "Enhanced pointer precision" option.
Click OK.
2. Disable animation and fade effects:
a. Select the System option from the Control Panel.
b. Select Performance Information then Tools > Advanced Tools >
Adjust to adjust the appearance and performance of Windows.
c. Click the Advanced tab.
d. Click the Settings button in the Performance group to open the
Performance Options dialog.
e. Under Custom options, deselect the following checkboxes:
Animation options:
16
Chapter 2: Installation and Configuration
Animate controls and elements inside windows
Animate windows when minimizing and maximizing
Fade options:
Fade or slide menus into view
Fade or slide ToolTips into view
Fade out menu items after clicking
3. Click OK and Close the Control Panel.
Linux Settings (Red Hat 9)
Note: The following settings are optimized for Standard Mouse mode
only.
To configure KVM target servers running Linux (graphical user
interface):
1. Configure the mouse settings:
a. Choose Main Menu > Preferences > Mouse. The Mouse
Preferences dialog appears.
b. Click the Motion tab.
c. Within the Speed group, set the Acceleration slider to the exact
center.
d. Within the Speed group, set the Sensitivity towards low.
e. Within the Drag & Drop group, set the Threshold towards small.
f. Close the Mouse Preferences dialog.
Note: If these steps do not work, issue the xset mouse 1 1 command
as described in the Linux command line instructions.
2. Configure the screen resolution:
a. Choose Main Menu > System Settings > Display. The Display
Settings dialog appears.
b. From the Display tab, select a Resolution supported by the
Dominion KX II.
c. From the Advanced tab, verify that the Refresh Rate is
supported by the Dominion KX II.
17
Chapter 2: Installation and Configuration
Note: Once connected to the target server, in many Linux graphical
environments, the <Ctrl> <Alt> <+> command will change the video
resolution, scrolling through all available resolutions that remain enabled
in the XF86Config or /etc/X11/xorg.conf, depending on your X server
distribution.
To configure KVM target servers running Linux (command line):
1. Set the mouse acceleration to exactly 1 and set the threshold to
exactly 1. Enter this command: xset mouse 1 1. This should be set
for execution upon login.
2. Ensure that each target server running Linux is using a resolution
supported by the Dominion KX II at a standard VESA resolution and
refresh rate.
3. Each Linux target server should also be set so the blanking times are
within +/- 40% of VESA standard values:
a. Go to the Xfree86 Configuration file XF86Config.
b. Using a text editor, disable all non-Dominion KX II supported
c. Disable the virtual desktop feature (not supported by the
resolutions.
Dominion KX II).
d. Check blanking times (+/- 40% of VESA standard).
e. Restart computer.
Note: If you change the video resolution, you must log off of the target
server and log back in for the video settings to take effect.
Note for Red Hat 9 KVM Target Servers
If you are running Red Hat 9 on the target server using a USB CIM, and
are experiencing problems with the keyboard and/or mouse, there is an
additional configuration setting you can try.
Tip: You might have to perform these steps even after a fresh OS
installation.
To configure Red Hat 9 servers using USB CIMs:
1. Locate the configuration file (usually /etc/modules.conf) in your
system.
2. Using the editor of your choice, make sure that the alias
usb-controller line in the modules.conf file is as follows:
alias usb-controller usb-uhci
Note: If there is another line using usb-uhci in the /etc/modules.conf
file, it needs to be removed or commented out.
18

Chapter 2: Installation and Configuration
3. Save the file.
4. Reboot the system in order for the changes to take effect.
Linux Settings (Red Hat 4)
Note: The following settings are optimized for Standard Mouse mode
only.
To configure KVM target servers running Linux (graphical user
interface):
1. Configure the mouse settings:
a. Choose Main Menu > Preferences > Mouse. The Mouse
Preferences dialog appears.
b. Open the Motion tab.
c. Within the Speed group, set the Acceleration slider to the exact
center.
d. Within the Speed group, set the Sensitivity towards low.
e. Within the Drag & Drop group, set the Threshold towards small.
f. Close the Mouse Preferences dialog.
Note: If these steps do not work, issue the xset mouse 1 1 command
as described in the Linux command line instructions.
2. Configure the screen resolution:
a. Choose Main Menu > System Settings > Display. The Display
Settings dialog appears.
b. On the Settings tab, select a Resolution supported by the
Dominion KX II.
c. Click OK.
Note: Once connected to the target server, in many Linux graphical
environments, the <Ctrl> <Alt> <+> command will change the video
resolution, scrolling through all available resolutions that remain enabled
in the XF86Config or /etc/X11/xorg.conf, depending on your X server
distribution
Note: If you change the video resolution, you must log out of the target
server and log back in for the video settings to take effect.
19
Chapter 2: Installation and Configuration
SUSE Linux 10.1 Settings
Note: Do not attempt to synchronize the mouse at the SUSE login
prompt. You must be connected to the target server to synchronize the
mouse cursors.
To configure the mouse settings:
1. Choose Desktop > Control Center. The Desktop Preferences dialog
appears.
2. Click Mouse. The Mouse Preferences dialog appears.
3. Open the Motion tab.
4. Within the Speed group, set the Acceleration slider to the exact
center position.
5. Within the Speed group, set the Sensitivity slider to low.
6. Within the Drag & Drop group, set the Threshold slider to small.
7. Click Close.
To configure the video:
1. Choose Desktop Preferences > Graphics Card and Monitor. The
Card and Monitor Properties dialog appears.
2. Verify that a Resolution and Refresh Rate is in use that is supported
by the Dominion KX II. See Supported Video Resolutions (on page
246) for more information.
Note: If you chang
e the vid
eo resolution, you must log out of the
target server and log back in for the video settings to take effect.
Make Linux Settings Permanent
Note: These steps may vary slightly depending on the specific version of
Linux in use.
To make your settings permanent in Linux (prompt):
1. Choose System Menu > Preferences > Personal > Sessions.
2. Click the Session Options tab.
3. Select the "Prompt on log off" checkbox and click OK. This option
prompts you to save your current session when you log out.
4. Upon logging out, select the "Save current setup" option from the
dialog.
5. Click OK.
20

Chapter 2: Installation and Configuration
Tip: If you do not want to be prompted upon log out, follow these
procedures instead.
To make your settings permanent in Linux (no prompt):
1. Choose Desktop > Control Center > System > Sessions.
2. Click the Session Options tab.
3. Deselect the "Prompt on the log off" checkbox.
4. Select the "Automatically save changes to the session" checkbox
and click OK. This option automatically saves your current session
when you log out.
Sun® Solaris Settings
To configure KVM target servers running Sun Solaris:
1. Set the mouse acceleration value to exactly 1 and the threshold to
exactly 1. This can be performed from:
The graphical user interface.
The command line xset mouse a t where a is the acceleration
and t is the threshold.
2. All KVM target servers must be configured to one of the display
resolutions supported by the Dominion KX II. The most popular
supported resolutions for Sun machines are:
Display resolution Vertical refresh rate Aspect ratio
1600 x 1200 60 Hz 4:3
1280 x 1024 60,75,85 Hz 5:4
1152 x 864 75 Hz 4:3
1024 x 768 60,70,75,85 Hz 4:3
800 x 600 56,60,72,75,85 Hz 4:3
720 x 400 85 Hz 9:5
640 x 480 60,72,75,85 Hz 4:3
21
 Loading...
Loading...