Raritan DOMINION KX II DKX2-0E-E, Dominion KX II, Dominion KX2-116, Dominion KX2-432 User Manual

Dominion KX II
User Guide
Release 2.0.5
Copyright © 2007 Raritan, Inc.
DKX2-0E-E
September 2007
255-62-4023-00
This document contains proprietary information that is protected by copyright. All rights reserved.
No part of this document may be photocopied, reproduced, or translated into another language
without express prior written consent of Raritan, Inc.
© Copyright 2007 Raritan, Inc., CommandCenter®, Dominion®, Paragon® and the Raritan company
logo are trademarks or registered trademarks of Raritan Computer, Inc. All rights reserved. Java® is a
registered trademark of Sun Microsystems, Inc. Internet Explorer® is a registered trademark of
Microsoft Corporation. Netscape® and Netscape Navigator® are registered trademarks of Netscape
Communication Corporation. All other trademarks or registered trademarks are the property of their
respective holders.
FCC Information
This equipment has been tested and found to comply with the limits for a Class A digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a commercial installation. This equipment generates, uses, and can
radiate radio frequency energy and if not installed and used in accordance with the instructions, may
cause harmful interference to radio communications. Operation of this equipment in a residential
environment may cause harmful interference.
VCCI Information (Japan)
Raritan is not responsible for damage to this product resulting from accident, disaster, misuse, abuse,
non-Raritan modification of the product, or other events outside of Raritan's reasonable control or not
arising under normal operating conditions.
Contents
Chapter 1 Introduction 1
Dominion KX II Overview ....................................................................................................................... 2
Virtual Media............................................................................................................................................. 3
Product Photos........................................................................................................................................... 3
Product Features........................................................................................................................................ 4
Hardware ........................................................................................................................................4
Software........................................................................................................................................... 5
Terminology............................................................................................................................................... 6
Package Contents ......................................................................................................................................7
User Guide.................................................................................................................................................. 7
Organization of Information......................................................................................................... 8
Related Documentation................................................................................................................. 9
Chapter 2 Getting Started 10
Login Information ................................................................................................................................... 10
Default IP Address.................................................................................................................................. 10
Supported Operating Systems (Clients)............................................................................................... 10
Supported Browsers................................................................................................................................ 11
Supported Operating Systems and CIMs (Target Servers)................................................................ 12
D2CIM-USB G2 Note ..............................................................................................................................13
Chapter 3 Installation and Configuration
Overview .................................................................................................................................................. 14
Step 1: Configure Target Servers........................................................................................................... 15
Supported Video Resolutions..................................................................................................... 15
Desktop Background ................................................................................................................... 16
Mouse Settings.............................................................................................................................. 16
Operating System Mouse and Video Settings.......................................................................... 16
Windows XP / Windows 2003 Settings ..................................................................................... 17
Windows 2000 Settings................................................................................................................ 18
Windows Vista .............................................................................................................................18
Linux Settings (Red Hat 9).......................................................................................................... 19
Linux Settings (Red Hat 4).......................................................................................................... 21
SUSE Linux 10.1 Settings............................................................................................................. 22
Make Linux Settings Permanent ................................................................................................ 23
Sun Solaris Settings...................................................................................................................... 23
14
iii

Contents
IBM AIX 5.3 Settings.................................................................................................................... 26
Make UNIX Settings Permanent ................................................................................................27
Apple Macintosh Settings ........................................................................................................... 27
Step 2 (Optional): Configure Keyboard Language ............................................................................. 27
Change the Keyboard Layout Code (Sun Targets).................................................................. 28
Step 3: Configure Network Firewall Settings...................................................................................... 28
Step 4: Connect the Equipment .............................................................................................................29
1. AC Power .................................................................................................................................. 29
2. Network Ports........................................................................................................................... 30
3. Local Access Port (local PC).................................................................................................... 30
4. Target Server Ports................................................................................................................... 31
Step 5: Dominion KX II Initial Configuration...................................................................................... 31
Changing the Default Password ................................................................................................ 32
Valid Special Characters..............................................................................................................32
Assigning an IP Address............................................................................................................. 33
Naming Target Servers................................................................................................................ 34
Specifying Power Supply Auto-detection.................................................................................35
Note to CC-SG Users ...................................................................................................................36
Remote Authentication........................................................................................................................... 36
Note to CC-SG Users ...................................................................................................................36
Supported Protocols..................................................................................................................... 36
Note on Microsoft Active Directory ..........................................................................................36
Authentication vs. Authorization .............................................................................................. 37
Users, Groups, and Access Permissions............................................................................................... 38
Users............................................................................................................................................... 38
Groups ........................................................................................................................................... 38
Relationship between Users and Groups.................................................................................. 39
Chapter 4 Connecting to the Dominion KX II 40
User Interfaces .........................................................................................................................................40
KX II Local Console: KX II Devices....................................................................................................... 41
Dominion KX II Remote Console: Dominion KX II Devices ............................................................. 42
Multi-Platform Client (MPC): KX I and Dominion KX II Devices.................................................... 43
Raritan Remote Client (RRC): KX I Devices Only............................................................................... 44
Language Support................................................................................................................................... 44
Java Runtime Environment (JRE).......................................................................................................... 44
Launching the Dominion KX II .............................................................................................................45
Dominion KX II Console Layout................................................................................................ 46
Dominion KX II Console Navigation ........................................................................................46
Logging Out.................................................................................................................................. 47
Dominion KX II Console Menu Tree......................................................................................... 47
Managing Favorites................................................................................................................................. 49
Manage Favorites Menu.............................................................................................................. 50
Favorites List................................................................................................................................. 51
Discover Devices - Local Subnet ................................................................................................ 53
iv

Contents
Discover Devices - KX Subnet .................................................................................................... 55
Add New Favorite ....................................................................................................................... 56
Chapter 5 Accessing Target Servers 57
Port Access Page...................................................................................................................................... 58
Connecting to a Target Server ............................................................................................................... 59
Port Action Menu .................................................................................................................................... 60
Switching between Target Servers........................................................................................................ 61
Disconnecting Target Servers ................................................................................................................ 61
Power Controlling a Target Server .......................................................................................................62
Power Cycle a Target Server....................................................................................................... 62
Power On a Target Server........................................................................................................... 62
Power Off a Target Server........................................................................................................... 63
Chapter 6 Virtual KVM Client 64
Overview .................................................................................................................................................. 65
Options...................................................................................................................................................... 66
Menu Tree ..................................................................................................................................... 66
Toolbar........................................................................................................................................... 66
Mouse Pointer Synchronization ............................................................................................................67
Mouse Synchronization Tips ...................................................................................................... 68
Connection Menu .................................................................................................................................... 69
Properties Dialog.......................................................................................................................... 69
Connection Info ............................................................................................................................ 71
Exit.................................................................................................................................................. 72
Keyboard Menu....................................................................................................................................... 73
Send Ctrl+Alt+Delete ...................................................................................................................73
Keyboard Macros ......................................................................................................................... 73
Creating a Keyboard Macro........................................................................................................ 74
Running a Keyboard Macro........................................................................................................76
Modifying a Keyboard Macro .................................................................................................... 76
Removing a Keyboard Macro..................................................................................................... 76
Video Menu.............................................................................................................................................. 77
Refresh Screen............................................................................................................................... 77
Auto-sense Video Settings .......................................................................................................... 77
Calibrate Color..............................................................................................................................78
Video Settings............................................................................................................................... 78
Mouse Menu ............................................................................................................................................81
Synchronize Mouse...................................................................................................................... 81
Single Mouse Cursor.................................................................................................................... 82
Standard ........................................................................................................................................83
Intelligent ......................................................................................................................................83
Absolute......................................................................................................................................... 83
v

Contents
Virtual Media........................................................................................................................................... 84
Tools Menu............................................................................................................................................... 84
Options ..........................................................................................................................................84
View Menu............................................................................................................................................... 85
View Toolbar.................................................................................................................................85
Scaling............................................................................................................................................ 85
Target Screen Resolution............................................................................................................. 85
Help Menu................................................................................................................................................ 86
About Raritan Virtual KVM Client............................................................................................ 86
Chapter 7 Virtual Media 87
Overview .................................................................................................................................................. 88
Prerequisites for Using Virtual Media.................................................................................................. 90
Using Virtual Media................................................................................................................................ 91
Opening a KVM Session......................................................................................................................... 92
Connecting to Virtual Media .................................................................................................................93
Local Drives ..................................................................................................................................93
Conditions when Read-Write is not Available.........................................................................94
CD-ROM/DVD-ROM/ISO Images ............................................................................................. 94
Disconnecting Virtual Media................................................................................................................. 95
File Server Setup (File Server ISO Images Only)................................................................................. 96
Chapter 8 User Management 98
User Management Menu........................................................................................................................ 98
User List.................................................................................................................................................... 99
Add New User....................................................................................................................................... 100
Modify Existing User................................................................................................................. 101
User Group List .....................................................................................................................................102
Add New User Group .......................................................................................................................... 103
Setting Permissions.................................................................................................................... 105
Setting Port Permissions............................................................................................................ 106
Group-based IP ACL (Access Control List)............................................................................ 106
Modify Existing User Group ....................................................................................................109
Set Permissions for Individual Group..................................................................................... 110
Change Password.................................................................................................................................. 111
Authentication Settings ........................................................................................................................112
Implementing LDAP Remote Authentication........................................................................ 115
Returning User Group Information from Active Directory Server..................................... 117
Implementing RADIUS Remote Authentication ...................................................................118
Returning User Group Information via RADIUS.................................................................. 119
RADIUS Communication Exchange Specifications...............................................................120
vi

Contents
Chapter 9 Device Management 121
Device Management Menu ..................................................................................................................121
Network Settings................................................................................................................................... 122
Network Basic Settings.............................................................................................................. 123
Network Miscellaneous Settings.............................................................................................. 124
LAN Interface Settings .............................................................................................................. 125
Date/Time Settings ................................................................................................................................ 128
Event Management ...............................................................................................................................129
Event Management - Settings................................................................................................... 130
SNMP Configuration................................................................................................................. 130
Syslog Configuration................................................................................................................. 131
Event Management - Destinations........................................................................................... 132
SNMP Agent Configuration ..................................................................................................... 133
SNMP Trap Configuration........................................................................................................ 133
Power Supply Setup Page .................................................................................................................... 136
Port Configuration Page....................................................................................................................... 138
Power Control........................................................................................................................................ 140
Connect the Power Strip............................................................................................................ 140
Name the Power Strip (Port Page for Power Strips) .............................................................141
Associate Target Servers to Outlets (Port Page).....................................................................143
Note for D2CIM-VUSB CIM Usage ......................................................................................... 145
Chapter 10 Security Settings 146
Security Settings Menu......................................................................................................................... 146
Security Settings ....................................................................................................................................147
Login Limitations ....................................................................................................................... 148
Strong Passwords....................................................................................................................... 149
User Blocking.............................................................................................................................. 150
Encryption & Share.................................................................................................................... 151
Checking Your Browser for AES Encryption......................................................................... 153
vii

Contents
IP Access Control................................................................................................................................... 153
Chapter 11 Maintenance 156
Maintenance Menu................................................................................................................................ 156
Maintenance Features (Local/Remote Console)................................................................................ 156
Audit Log................................................................................................................................................ 157
Device Information................................................................................................................................159
Backup and Restore............................................................................................................................... 160
CIM Upgrade ......................................................................................................................................... 162
Firmware Upgrade................................................................................................................................ 163
Upgrade Report ..................................................................................................................................... 165
Reboot .....................................................................................................................................................165
Chapter 12 Diagnostics 167
Diagnostics Menu.................................................................................................................................. 167
Network Interface Page........................................................................................................................ 168
Network Statistics Page........................................................................................................................ 169
Ping Host Page....................................................................................................................................... 171
Trace Route to Host Page ..................................................................................................................... 172
KX Diagnostics....................................................................................................................................... 173
Chapter 13 KX II Local Console 176
KX II Local Console............................................................................................................................... 176
Physical Connections................................................................................................................. 177
Reset Button ................................................................................................................................ 177
Starting the KX II Local Console .........................................................................................................178
Simultaneous Users....................................................................................................................178
Security and Authentication..................................................................................................... 179
KX II Local Console Interface ................................................................................................... 179
Available Resolutions................................................................................................................ 179
Accessing Target Servers...................................................................................................................... 180
Server Display............................................................................................................................. 180
Hotkeys........................................................................................................................................ 181
Accessing a Target Server ......................................................................................................... 181
Returning to the KX II Local Console Interface .....................................................................181
Local Port Administration.................................................................................................................... 182
Local Port Settings (KX II Local Console Only) .....................................................................182
Factory Reset (KX II Local Console Only)...............................................................................185
viii

Contents
Chapter 14 CC Unmanage 187
Overview ................................................................................................................................................ 187
Removing Dominion KX II from CC-SG Management.................................................................... 188
Appendix A Specifications 190
Environmental Requirements.............................................................................................................. 190
Physical Specifications............................................................................................................... 191
Electrical Specifications............................................................................................................. 192
Computer Interface Modules (CIMs) ...................................................................................... 192
Remote Connection ............................................................................................................................... 193
KVM Properties ..................................................................................................................................... 193
TCP and UDP Ports Used..................................................................................................................... 194
Target Server Connection Distance and Video Resolution.............................................................. 195
Network Speed Settings .......................................................................................................................195
Appendix B Updating the LDAP Schema 197
Returning User Group Information.................................................................................................... 197
From LDAP................................................................................................................................. 197
From Microsoft Active Directory............................................................................................. 197
Setting the Registry to Permit Write Operations to the Schema..................................................... 198
Creating a New Attribute..................................................................................................................... 198
Adding Attributes to the Class............................................................................................................ 199
Updating the Schema Cache................................................................................................................ 201
Editing rciusergroup Attributes for User Members ......................................................................... 201
Appendix C Informational Notes
Overview ................................................................................................................................................ 205
Non-US Keyboards ...............................................................................................................................205
French Keyboard........................................................................................................................ 205
Caret Symbol (Linux Clients only) ..........................................................................................205
Accent Symbol (Windows XP Clients only) ........................................................................... 206
Numeric Keypad........................................................................................................................ 206
Tilde Symbol............................................................................................................................... 206
Java Runtime Environment (JRE).............................................................................................207
Keyboard Language Preference (Fedora Linux Clients)....................................................... 207
205
ix

Contents
Macintosh Keyboard............................................................................................................................. 208
Mouse Pointer Synchronization (Fedora) .......................................................................................... 208
Resolving Fedora Core Focus .............................................................................................................. 209
SUSE/VESA Video Modes.................................................................................................................... 209
CIMs ........................................................................................................................................................ 210
Windows 3-Button Mouse on Linux Targets..........................................................................210
Virtual Media......................................................................................................................................... 210
Dell OpTiplex and Dimension Computers............................................................................. 210
Virtual Media not Refreshed after Files Added..................................................................... 210
Target BIOS Boot Time with Virtual Media ........................................................................... 210
CC-SG...................................................................................................................................................... 211
Virtual KVM Client Version not Known from CC-SG Proxy Mode ...................................211
Proxy Mode and MPC ............................................................................................................... 211
Appendix D FAQs 212
General Questions ................................................................................................................................. 213
Remote Access .......................................................................................................................................215
Universal Virtual Media....................................................................................................................... 217
Ethernet and IP Networking................................................................................................................ 218
Servers..................................................................................................................................................... 222
Installation.............................................................................................................................................. 224
Local Port................................................................................................................................................ 226
Power Control........................................................................................................................................ 228
Scalability................................................................................................................................................ 229
Computer Interface Modules (CIMs).................................................................................................. 230
Security ...................................................................................................................................................231
Manageability ........................................................................................................................................233
Miscellaneous......................................................................................................................................... 234
Troubleshooting..................................................................................................................................... 235
Index 237
x

Table of Figures
Figure 1: Dominion KX II Configuration ........................................................................................ 2
Figure 2: Dominion KX2-116..............................................................................................................3
Figure 3: Dominion KX2-432..............................................................................................................4
Figure 4: Dominion KX II CIMs: D2CIM-VUSB (left); D2CIM-PWR (right)........................... 4
Figure 5: Terminology and Topology............................................................................................... 6
Figure 6: Solaris Mouse Configuration..........................................................................................24
Figure 7: Dominion KX II Connections ......................................................................................... 29
Figure 8: Network Settings............................................................................................................... 33
Figure 9: Port Configuration ............................................................................................................ 35
Figure 10: Authentication/Authorization Flow Diagram ...........................................................37
Figure 11: Dominion KX II Remote Console Login Page ...........................................................45
Figure 12: Sample Menu Hierarchy (breadcrumbs) ....................................................................46
Figure 13: KX II Console Menu Tree (Local and Remote)..........................................................47
Figure 14: Port Access........................................................................................................................ 49
Figure 15: Favorites List .................................................................................................................... 51
Figure 16: Edit (Favorite Information)............................................................................................52
Figure 17: Discover Devices - Local Subnet ..................................................................................53
Figure 18: Discover Devices - KX Subnet ......................................................................................55
Figure 19: Add New Favorite ...........................................................................................................56
Figure 20: Port Access........................................................................................................................ 58
Figure 21: Port Action Menu ............................................................................................................59
Figure 22: Port Action Menu (power options) .............................................................................. 62
Figure 23: Virtual KVM Client Window .......................................................................................65
Figure 24: Virtual KVM Client Menu Tree ................................................................................... 66
Figure 25: Dual Mouse Cursors .......................................................................................................67
Figure 26: Properties Dialog............................................................................................................. 69
Figure 27: Connection Info............................................................................................................... 71
Figure 28: Keyboard Macros.............................................................................................................74
Figure 29: Add Keyboard Macro .....................................................................................................74
Figure 30: Keyboard Macro Example..............................................................................................75
Figure 31: New Macro in Keyboard Menu ....................................................................................75
Figure 32: Video Settings..................................................................................................................79
Figure 33: Single Mouse Cursor Message .....................................................................................82
Figure 34: (Tools) Options ................................................................................................................84
Figure 35: Virtual Media Connection............................................................................................. 89
Figure 36: Open KVM Session ........................................................................................................92
Figure 37: Map Virtual Media Drive ..............................................................................................93
xi

Table of Figures
Figure 38: Map Virtual Media CD/ISO Image..............................................................................
94
Figure 39: File Server Setup .............................................................................................................96
Figure 40: User List ............................................................................................................................99
Figure 41: User Page......................................................................................................................... 100
Figure 42: User Group List..............................................................................................................102
Figure 43: Group Page .....................................................................................................................104
Figure 44: Group-based IP Access Control List.......................................................................... 107
Figure 45: IP ACL Example............................................................................................................. 108
Figure 46: Modify Group ................................................................................................................109
Figure 47: Change Password .......................................................................................................... 111
Figure 48: Authentication Settings ...............................................................................................113
Figure 49: Authentication Settings (LDAP).................................................................................115
Figure 50: Authentication Settings (RADIUS) ...........................................................................118
Figure 51: Network Settings........................................................................................................... 122
Figure 52: Network Settings (Network Basic Settings)............................................................. 123
Figure 53: Network Settings (Network Miscellaneous Settings)............................................124
Figure 54: Network Settings (LAN Interface Settings) ............................................................. 125
Figure 55: Date/Time Settings........................................................................................................128
Figure 56: Event Management - Settings ..................................................................................... 130
Figure 57: Syslog Configuration.................................................................................................... 131
Figure 58: Event Management - Destinations.............................................................................132
Figure 59: Power Supply Setup ..................................................................................................... 136
Figure 60: Port Configuration ........................................................................................................ 138
Figure 61: Power Strip Connections .............................................................................................140
Figure 62: Port Page (power strips) ............................................................................................... 141
Figure 63: Port Page (KVM ports) .................................................................................................143
Figure 64: Port Page (Target Server Settings for D2CIM-VUSB)............................................ 145
Figure 65: Security Settings............................................................................................................147
Figure 66: Security Settings (Strong Passwords)........................................................................149
Figure 67: Security Settings (User Blocking) ..............................................................................151
Figure 68: Security Settings (Encryption & Share) ....................................................................151
Figure 69: Security Settings (Encryption Mode Warning Message).......................................152
Figure 70: IP Access Control........................................................................................................... 154
Figure 71: Audit Log ........................................................................................................................ 157
Figure 72: Device Information....................................................................................................... 159
Figure 73: Backup/Restore ..............................................................................................................160
Figure 74: CIM Upgrade from KX Flash ...................................................................................... 162
Figure 75: Firmware Upgrade ........................................................................................................163
Figure 76: Firmware Upgrade Review..........................................................................................164
Figure 77: Firmware Upgrade Successful .................................................................................... 164
Figure 78: Upgrade Report.............................................................................................................. 165
Figure 79: Reboot.............................................................................................................................. 166
xii

Table of Figures
Figure 80: Reboot Confirmation....................................................................................................
166
Figure 81: Network Interface .........................................................................................................168
Figure 82: Network Statistics (statistics)...................................................................................... 169
Figure 83: Network Statistics (interfaces)....................................................................................170
Figure 84: Network Statistics (route) ............................................................................................170
Figure 85: Ping Host......................................................................................................................... 171
Figure 86: Trace Route to Host....................................................................................................... 172
Figure 87: KX Diagnostics...............................................................................................................174
Figure 88: Diagnostics Scripts........................................................................................................ 174
Figure 89: File Download................................................................................................................175
Figure 90: Dominion KX II Local Console...................................................................................176
Figure 91: Local User Panel on Dominion KX II ........................................................................177
Figure 92: Reset Button (back of unit).......................................................................................... 177
Figure 93: Local Console Port Access ...........................................................................................180
Figure 94: Local Port Settings......................................................................................................... 182
Figure 95: Factory Reset (Local Console Only)........................................................................... 185
Figure 96: Device Managed by CC-SG Message........................................................................ 187
Figure 97: Remove from CC-SG Management ...........................................................................188
Figure 98: Confirm CC Unmanage................................................................................................ 188
Figure 99: Device Removed from CC Management ..................................................................189
Figure 100: Change Schema Master.............................................................................................. 198
Figure 101: Create New Attribute..................................................................................................199
Figure 102: Adding the Attributes ................................................................................................200
Figure 103: Adding the Attributes to the Class ..........................................................................200
Figure 104: ADSI Edit......................................................................................................................201
Figure 105: ADSI Edit (CN=Users)................................................................................................202
Figure 106: Administrator Properties (attribute editor)............................................................ 203
Figure 107: User Properties............................................................................................................. 204
Figure 108: Edit Attribute (adding user to KX II group)........................................................... 204
xiii


Chapter 1
Introduction
In This Chapter
Dominion KX II Overview................................................................................2
Virtual Media .....................................................................................................3
Product Photos...................................................................................................3
Product Features................................................................................................4
Terminology .......................................................................................................6
Package Contents...............................................................................................7
User Guide..........................................................................................................7
1
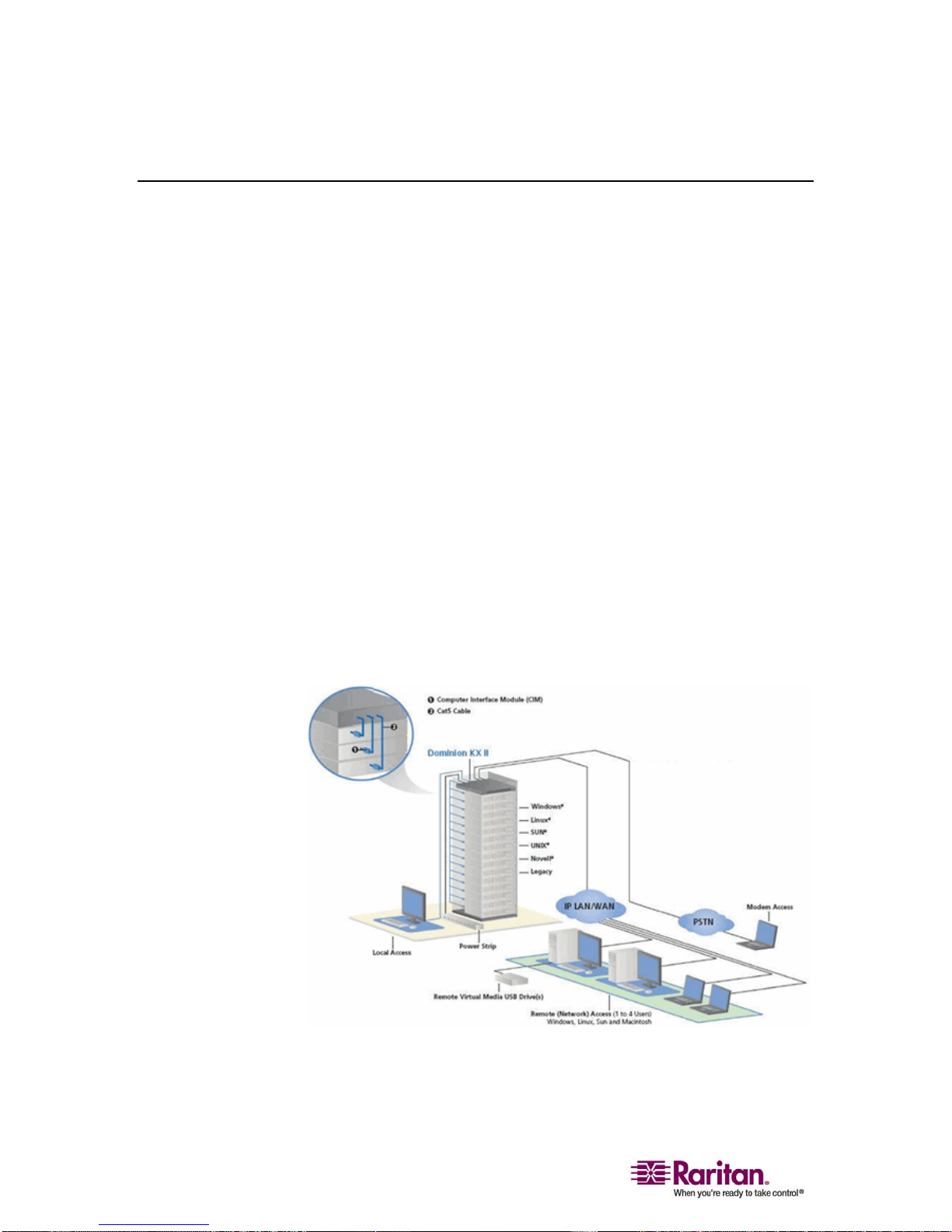
Dominion KX II Overview
Dominion KX II Overview
Dominion KX II is an enterprise-class, secure, digital KVM (Keyboard,
Video, Mouse) switch that provides BIOS-level (and up) access, and
control of up to 64 servers from anywhere in the world via Web browser.
At the rack, Dominion KX II provides BIOS-level control of up to 64
servers and other IT devices from a single keyboard, monitor, and
mouse. The integrated remote access capabilities of the Dominion KX II
provide the same levels of control of your servers via Web browser.
Dominion KX II is easily installed using standard UTP (Cat 5/5e/6)
cabling. Its advanced features include virtual media, 128-bit encryption,
dual power supplies, remote power control, dual Ethernet, LDAP,
RADIUS, Active Directory, Syslog integration, and Web management.
These features enable you to deliver higher uptime, better productivity,
and bulletproof security - at any time from anywhere.
Dominion KX II products can operate as standalone appliances and do
not rely on a central management device. For larger data centers and
enterprises, numerous Dominion KX II units (along with Dominion SX
units for remote serial console access and Dominion KSX for
remote/branch office management) can be integrated into a single logical
solution using Raritan's CommandCenter Secure Gateway (CC-SG)
management appliance.
Figure 1: Dominion KX II Configuration
2

Chapter 1: Introduction
Virtual Media
All Dominion KX II models support virtual media. The benefits of virtual
media - mounting of remote drives/media on the target server to support
software installation, and diagnostics - are now available in all of the
Dominion KX II models.
Each Dominion KX II comes equipped with virtual media to enable
remote management tasks using the widest variety of CD, DVD, USB,
internal and remote drives and images. Unlike other solutions, the
Dominion KX II supports virtual media access of hard drives and
remotely mounted images for added flexibility and productivity.
Virtual media sessions are secured using 128-bit AES or RC4 encryption.
The new D2CIM-VUSB CIM (computer interface module) supports
virtual media sessions to target servers supporting the USB 2.0 interface.
This new CIM also supports Absolute Mouse Synchronization as well as
remote firmware update.
Product Photos
Figure 2: Dominion KX2-116
3

Product Features
Figure 3: Dominion KX2-432
Figure 4: Dominion KX II CIMs: D2CIMVUSB (left); D2CIM-PWR (right)
Product Features
Hardware
• Integrated KVM-over-IP remote access
• 1U or 2U (KX2-464) rack-mountable; brackets included
• Dual power supplies with failover; auto-switching power supply
• 16, 32, or 64 (on KX2-464) server ports
• Multiple user capacity (1/2/4 remote users; 1 local user)
• UTP (Cat5/5e/6) server cabling
• Dual Ethernet ports (10/100/1000 LAN) with failover
with power failure warning
• Field upgradeable
• Local user port for in-rack access
4
PS/2 keyboard/mouse ports

Chapter 1: Introduction
One front and three back panel USB 2.0 ports for supported USB
devices
Fully concurrent with remote user access
Local Graphical User Interface (GUI) for administration
• Centralized access security
• Integrated power control
• LED indicators for dual power status, network activity, and remote
user status
• Hardware reset button
Software
• Virtual media with D2CIM-VUSB CIM
• Absolute Mouse Synchronization with D2CIM-VUSB CIM
• Plug-and-Play
• Web-based access and management
• Intuitive Graphical User Interface (GUI)
• 128-bit encryption of complete KVM signal, including video and
virtual media
• LDAP, Active Directory, RADIUS, or internal authentication and
authorization
• DHCP or fixed IP addressing
• SNMP and Syslog management
• Power control associated directly with servers to prevent mistakes
• Integration with Raritan's CommandCenter Secure Gateway (CC-
SG) management appliance
• CC Unmanage feature to remove device from CC-SG control
5
Terminology
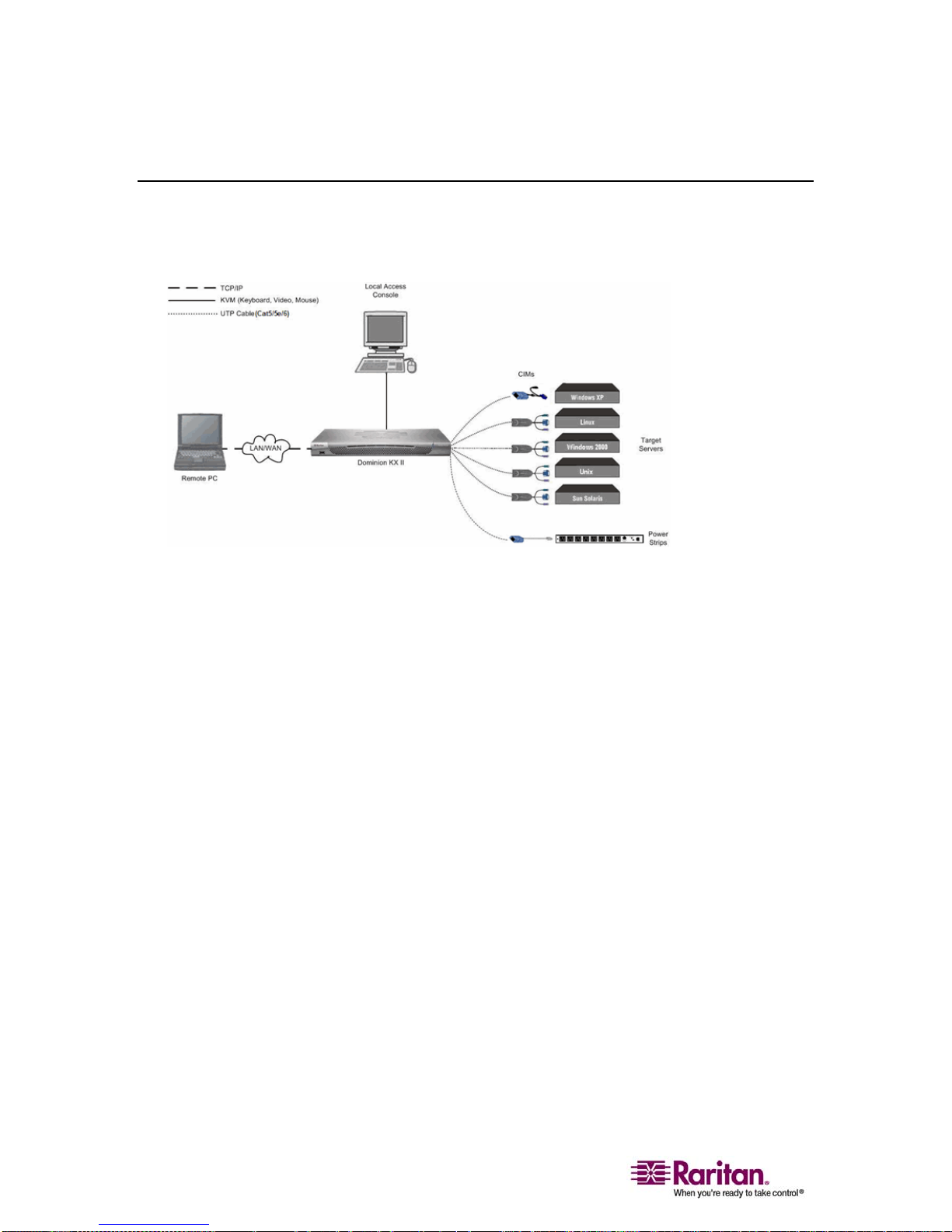
Terminology
This manual uses the following terminology for the components of a
typical Dominion KX II configuration:
Figure 5: Terminology and Topology
Remote PC
(client)
Networked computers used to access and control target
servers connected to the Dominion KX II. Refer to
Supported Operating Systems (Clients) (on page
10) for a
list of the Operating Systems supported by Dominion KX
II remotely.
Local Access
Console
(client)
An optional user console (consisting of a keyboard,
mouse, and multi-sync VGA monitor) attached directly to
Dominion KX II to control target servers locally (directly
at the rack, not through the network).
CIMs
(Computer Interface
Modules)
Dongles that connect to each target server and Raritan
power strip. Available for all of the supported Operating
Systems. Refer to Supported CIMs for information about
the CIMs supported by Dominion KX II.
Target Servers Servers with video cards and user interfaces (e.g.,
Windows, Linux, Solaris, etc.) accessed remotely via
Dominion KX II. Refer to Supported Operating Systems
and CIMs (Target Servers) for a list of the supported
Operating Systems and CIMs.
Power Strips Raritan power strips accessed remotely via the Dominion
KX II.
6

Chapter 1: Introduction
Package Contents
Each Dominion KX II ships as a fully-configured stand-alone product in
a standard 1U (2U for KX2-464) 19" rackmount chassis. Each Dominion
KX II unit ships with the following contents:
(1) Dominion KX II Unit
(1) Dominion KX II Quick Installation and Setup
Guide
(1) Raritan User Manuals CD-ROM
(1) Rackmount Kit
(2) AC Power Cords
(1) Cat5 Network Cable
(1) Cat5 Network Crossover Cable
(1) Set of 4 Rubber Feet (for desktop use)
User Guide
(1) Application Note
(1) Warranty Card
The Dominion KX II User Guide provides the information to install, set
up and configure, access target servers and power strips, use virtual
media, manage users and security, and maintain and diagnose the
Dominion KX II.
This user guide is specific to Dominion KX II (version 2.0); for
information pertaining to version 1.4, refer to the Dominion KX 1.4 User
Guide.
7

User Guide
Organization of Information
The user guide is organized as follows:
• Chapter 1, Introduction. Overview, features, terminology, and
package contents
• Chapter 2, Getting Started. Login information; default IP Address;
supported operating systems, browsers, and CIMs
• Chapter 3, Installation and Configuration. Target server
configuration; firewall settings; physical device connections; initial
KX II unit configuration; remote authentication; and users, groups,
and access permissions
• Chapter 4, Connecting to the Dominion KX II. User interfaces;
starting the KX II Remote Console; Dominion KX II Favorites
• Chapter 5, Accessing Target Servers. Access, control, and switching
between target servers
• Chapter 6, Virtual KVM Client. Target server control, mouse pointer
synchronization, keyboard macros, and video settings
• Chapter 7, Virtual Media. Virtual media configuration and access
• Chapter 8, User Management. User and group management,
passwords, group-based IP access control, and authentication
settings
• Chapter 9, Device Management. Network settings, date/time, event
management, power supply setup, port configuration, and power
control
• Chapter 10, Security Settings. Security settings and IP access control
• Chapter 11, Maintenance. Audit log; device information; backup and
restore; firmware and CIM upgrades; and reboot
• Chapter 12, Diagnostics. Network interface, network statistics, ping
host, trace route to host, and KX diagnostics
• Chapter 13, KX II Local Console. Starting the KX II Local Console,
accessing target servers, and local port administration
• Chapter 14, CC Unmanage. Removing the KX II from CC-SG control
• Appendix A, Specifications. Physical specifications; ports used;
target server connection distance and video resolution; and network
speed settings
• Appendix B, Updating the LDAP Schema. Update LDAP schema
(for experienced users)
• Appendix C, Informational Notes. Important notes on Dominion KX
8
II usage

Chapter 1: Introduction
• Appendix D, FAQs. General questions, remote access, universal
virtual media, Ethernet and IP networking, servers, installation, local
port, power control, scalability, Computer Interface Modules (CIMs),
security, manageability, miscellaneous, and troubleshooting
Related Documentation
For more information about the Raritan Multi-Platform Client (MPC),
refer to the Raritan Multi-Platform Client (MPC) and Raritan Remote
Client (RRC) User Guide.
For more information about the entire Raritan product line, refer to the
Raritan User Manuals & Quick Setup Guides CD ROM or Raritan's Web
site http://www.raritan.com/support/productdocumentation
9

Chapter 2
In This Chapter
Login Information............................................................................................10
Default IP Address ..........................................................................................10
Supported Operating Systems (Clients).......................................................10
Supported Browsers ........................................................................................11
Supported Operating Systems and CIMs (Target Servers)........................12
D2CIM-USB G2 Note ......................................................................................13
Login Information
• The default Dominion KX II login user name is admin and the
• Passwords are case sensitive and must be entered in the exact case
Getting Started
default password is raritan. This user has administrative privileges.
combination in which they were created. For example, the default
password raritan must be entered entirely in lowercase letters.
• The first time you start the Dominion KX II you are required to
change the default password.
Tip: For backup and business continuity purposes, it is strongly recommended
that you create a backup administrator user name and password and keep that
information in a secure location.
Default IP Address
Dominion KX II ships with the default IP address of 192.168.0.192.
Supported Operating Systems (Clients)
The following operating systems are supported on the Dominion KX II
Remote Console, Virtual KVM Client™, and Multi-Platform Client
(MPC):
Client OS Virtual Media (VM) Support on
Windows XP Yes
Client
Windows 2000 SP4 Yes
Windows Vista Yes
10

Chapter 2: Getting Started
Red Hat Linux 9.0 Yes; Locally held ISO image, Remote File
Server mounting directly from KX
Red Hat Enterprise
Workstation 3.0 and 4.0
SUSE Linux Professional 9.2
and 10
Fedora™ Core 5 and above Yes; Locally held ISO image, Remote File
Mac No
Solaris No
Supported Browsers
Dominion KX II supports the following browsers:
• Internet Explorer 6 and 7
• Firefox 1.5 and 2.0
• Mozilla 1.7
• Safari 2.0
Yes; Locally held ISO image, Remote File
Server mounting directly from KX
Yes; Locally held ISO image, Remote File
Server mounting directly from KX
Server mounting directly from KX
11
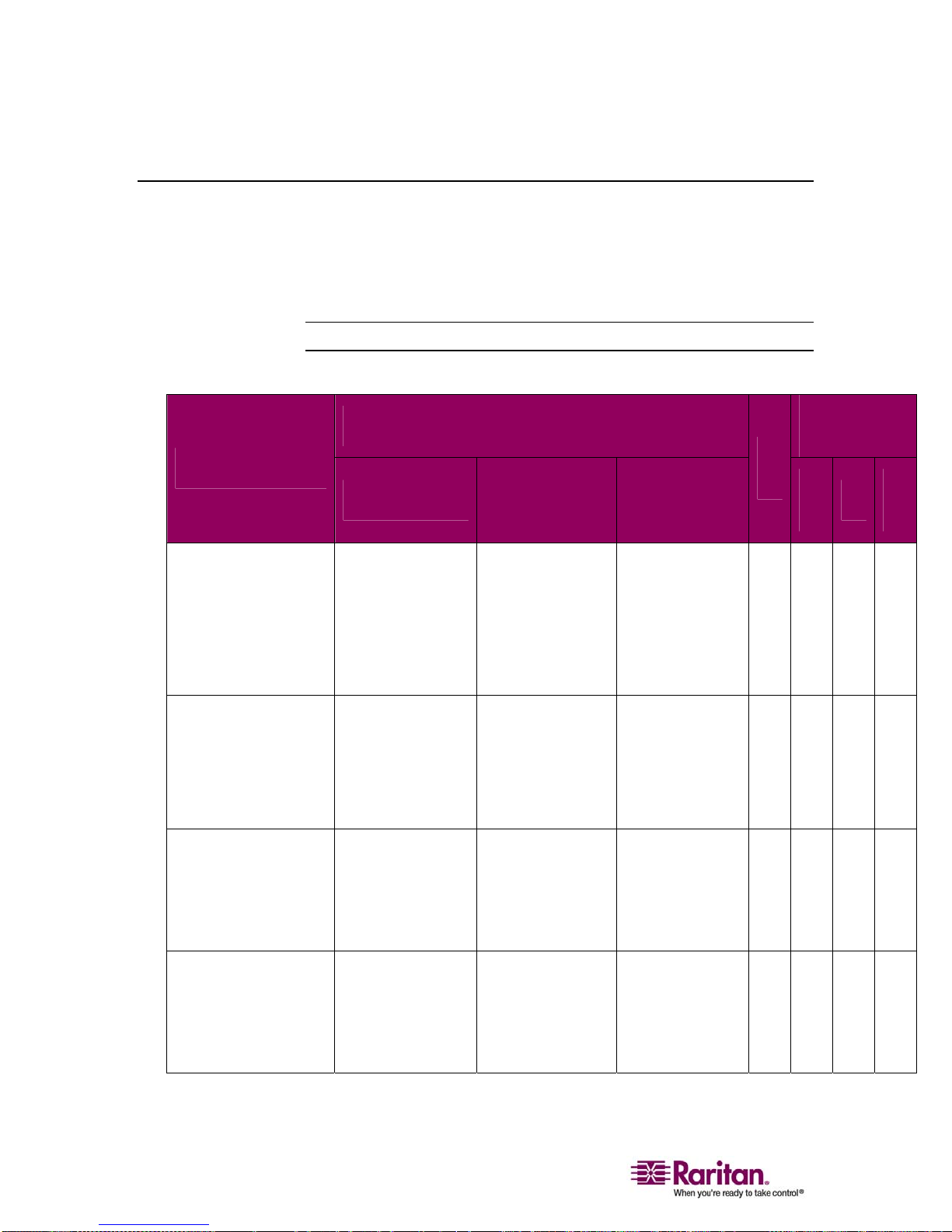
Supported Operating Systems and CIMs (Target Servers)
Supported Operating Systems and CIMs (Target Servers)
In addition to the new Dominion KX II D2CIMs, most Paragon® and
Dominion KX I CIMs are supported. The following table displays the
supported target server operating systems, CIMs, virtual media, and
mouse modes:
Note: D2CIM-VUSB is not supported on Sun (Solaris) targets.
Target Server
Windows XP
Windows 2000
Windows 2000 Server
Windows 2003 Server
Windows Vista
Red Hat Linux 9.0
Red Hat Enterprise
Workstation 3.0 and
4.0
SUSE Linux
Professional 9.2 and
10
Supported CIMs
Paragon CIMs
P2CIM-PS2
P2CIM-AUSB
UKVMPD
UUSBPD
P2CIM-PS2
P2CIM-AUSB
UKVMPD
UUSBPD
P2CIM-PS2
P2CIM-AUSB
UKVMPD
UUSBPD
Dominion KX I
DCIMs
DCIM-PS2
DCIM-USB
DCIM-USB G2
DCIM-PS2
DCIM-USB
DCIM-USB G2
DCIM-PS2
DCIM-USB
DCIM-USB G2
Dominion KX
II
D2CIMs
D2CIM-VUSB
D2CIM-VUSB
(excluding Red
Hat Enterprise
Workstation 3.0)
D2CIM-VUSB
Mouse
Modes
V
M
A
M
IM
S
M
9 9 9 9
9
9
9
9
Fedora Core 3
and above
12
P2CIM-PS2
P2CIM-AUSB
UKVMPD
UUSBPD
DCIM-PS2
DCIM-USB
DCIM-USB G2
D2CIM-VUSB
9
9
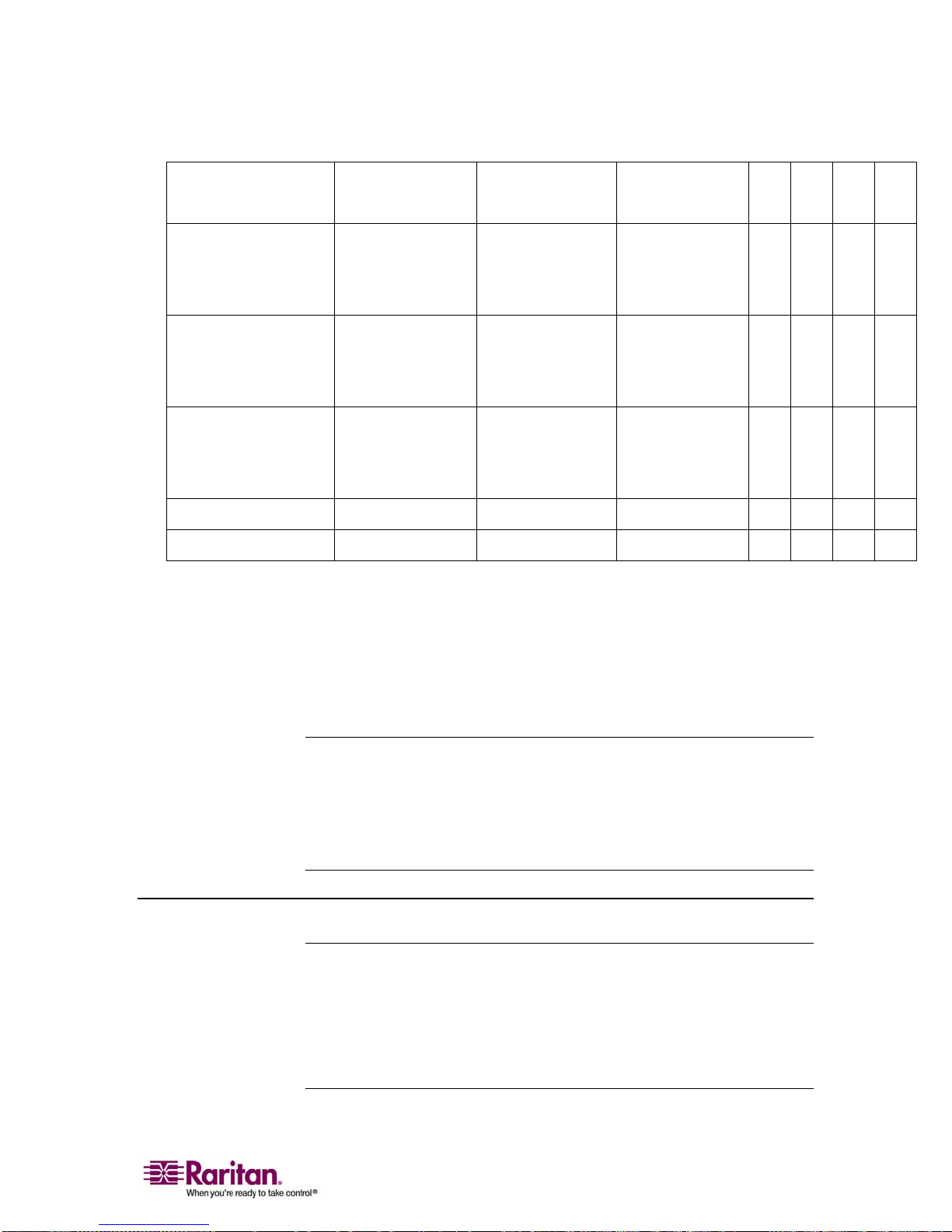
Chapter 2: Getting Started
Mac OS
P2CIM-AUSB
UUSBPD
All Solaris OSs
P2CIM-SUN
supported in
Dominion KX I
P2CIM-SUSB
P2CIM-PS2
IBM AIX
P2CIM-AUSB
UUSBPD
P2CIM-PS2
HP UX
P2CIM-AUSB
UUSBPD
Remote Power Strips
Serial Devices P2CIM-SER
Legend:
• VM: Virtual Media (D2CIM-VUSB only)
DCIM-USB
D2CIM-VUSB
9 9
DCIM-USB G2
DCIM-SUN
DCIM-SUSB
DCIM-USB G2
DCIM-USB
DCIM-USB G2
DCIM-PS2
DCIM-USB
DCIM-USB G2
DCIM-PS2
D2CIM-PWR
9
9
9
• AM: Absolute Mouse Synchronization (D2CIM-VUSB only)
• IM: Intelligent Mouse Mode
• SM: Standard Mouse Mode
• 9: Supported
Note: The DCIM-USB G2 provides a small slide switch on the back of the CIM.
Move the switch to P for PC-based USB target servers; move the switch to S for
Sun USB target servers.
A new switch position takes effect only after the CIM is power-cycled. To powercycle the CIM, remove the USB connector from the target server and plug it
back in a few seconds later.
D2CIM-USB G2 Note
Note: The DCIM-USB G2 provides a small slide switch on the back of the CIM.
Move the switch to P for PC-based USB target servers; move the switch to S for
Sun USB target servers.
A new switch position takes effect only after the CIM is power-cycled. To powercycle the CIM, remove the USB connector from the target server and plug it
back in a few seconds later.
13

Chapter 3
Overview
Installation and Configuration
In This Chapter
Overview...........................................................................................................14
Step 1: Configure Target Servers ...................................................................15
Step 2 (Optional): Configure Keyboard Language......................................27
Step 3: Configure Network Firewall Settings ..............................................28
Step 4: Connect the Equipment......................................................................29
Step 5: Dominion KX II Initial Configuration..............................................31
Remote Authentication ...................................................................................36
Users, Groups, and Access Permissions.......................................................38
This section provides a brief overview of the installation process. Each
step is further detailed in the remaining sections of this chapter.
¾
To install and configure Dominion KX II:
1. Configure the target servers.
2. (Optional) Configure the keyboard language.
3. Configure the network firewall settings.
4. Connect the equipment.
5. Configure the Dominion KX II unit.
14

Chapter 3: Installation and Configuration
Step 1: Configure Target Servers
Target servers are the computers that will be accessed and controlled via
the Dominion KX II. Before installing Dominion KX II, configure all
target servers to ensure optimum performance. This configuration
applies only to target servers, not to the client workstations (remote PCs)
used to access Dominion KX II remotely. Refer to Chapter 1:
Introduction, Terminology (see "
information.
¾
To configure the target servers:
• Check the video resolution.
• Check the desktop background.
• Adjust the mouse settings.
• Perform OS-specific mouse and video configuration.
Supported Video Resolutions
Terminology" on page 6) for additional
Ensure that each target server's video resolution and refresh rate are
supported by Dominion KX II and that the signal is non-interlaced.
Video resolution and cable length are important factors in the ability to
obtain mouse synchronization. Refer to Target Server Connection
Distance and Video Resolution (on page
195) for more information.
Dominion KX II supports these resolutions:
640x350 @70 Hz 720x400 @85 Hz 1024x768 @90 Hz
640x350 @85 Hz 800x600 @56 Hz 1024x768 @100 Hz
640x400 @56 Hz 800x600 @60 Hz 1152x864 @60 Hz
640x400 @84 Hz 800x600 @70 Hz 1152x864 @70 Hz
640x400 @85 Hz 800x600 @72 Hz 1152x864 @75 Hz
640x480 @60 Hz 800x600 @75 Hz 1152x864 @85 Hz
640x480 @66.6 Hz 800x600 @85 Hz 1152x870 @75.1 Hz
640x480 @72 Hz 800x600 @90 Hz 1152x900 @66 Hz
640x480 @75 Hz 800x600 @100 Hz 1152x900 @76 Hz
640x480 @85 Hz 832x624 @75.1 Hz 1280x960 @60 Hz
640x480 @90 Hz 1024x768 @60 Hz 1280x960 @85 Hz
640x480 @100 Hz 1024x768 @70 Hz 1280x1024 @60 Hz
15

Step 1: Configure Target Servers
640x480 @120 Hz 1024x768 @72 Hz 1280x1024 @75 Hz
720x400 @70 Hz 1024x768 @75 Hz 1280x1024 @85 Hz
720x400 @84 Hz 1024x768 @85 Hz 1600x1200 @60 Hz
Note: Composite Sync and Sync-on-Green video require an additional adapter.
Desktop Background
For optimal bandwidth efficiency and video performance, target servers
running graphical user interfaces such as Windows, Linux, X-Windows,
Solaris, and KDE require configuration. The desktop background need
not be completely solid; but desktop backgrounds featuring photos or
complex gradients might degrade performance.
Mouse Settings
The Dominion KX II operates in several mouse modes:
• Absolute Mouse Synchronization (see "
Absolute" on page 83)
(D2CIM-VUSB only)
• Intelligent Mouse Mode (see "
Intelligent" on page 83) (do not use an
animated mouse)
• Standard Mouse Mode (see "
Standard" on page 83)
For both the Standard and Intelligent mouse modes, mouse parameters
must be set to specific values, which are described later in this manual.
Mouse parameters do not have to be altered for Absolute Mouse
Synchronization; D2CIM-VUSB is required for this mode. Mouse
configurations will vary on different target operating systems; consult
your OS documentation for additional detail.
Intelligent mouse mode generally works well on most Windows
platforms. Intelligent mouse mode may produce unpredictable results
when active desktop is set on the target. For additional information on
Intelligent Mouse mode, refer to the Raritan Multi-Platform Client
(MPC) and Raritan Remote Client (RRC) User Guide (Appendix B:
Conditions for Intelligent Mouse Synchronization) available on Raritan's
Website http://www.raritan.com/support/productdocumentation, or on
the Raritan User Manuals & Quick Setup Guides CD ROM included with
your Dominion KX II shipment.
Operating System Mouse and Video Settings
This section provides video mode and mouse information specific to the
Operating System in use on the target server.
16
 Loading...
Loading...