Page 1
General Description
The MAX66100 contains a 64-bit unique identifier (UID)
and a 13.56MHz ISO 15693 RF interface in a single
chip. The UID is revealed during the inventory process.
The MAX66100 supports all ISO 15693-defined data
rates, modulation indices, subcarrier modes, the selected state, application family identifier (AFI), and data
storage format identifier (DSFID). AFI and DSFID are
factory programmed with customer-supplied data.
Applications
Driver Identification (Fleet Application)
Access Control
Asset Tracking
Features
♦ Fully Compliant with ISO 15693 and ISO 18000-3
Mode 1 Standard
♦ 13.56MHz ±7kHz Carrier Frequency
♦ 64-Bit Unique, Factory-Programmed UID
♦ Supports AFI and DSFID Function
♦ Write: 10% or 100% ASK Modulation Using 1/4
(26kbps) or 1/256 (1.6kbps) Pulse-Position Coding
♦ Read: Load Modulation Using Manchester Coding
with 423kHz and 484kHz Subcarrier in Low
(6.6kbps) or High (26kbps) Data-Rate Mode
♦ Compatible with Existing ISO 15693 Products on
the Market
♦ Powered Entirely Through the RF Field
♦ Operating Temperature: -25°C to +50°C
MAX66100
ISO 15693-Compliant 64-Bit UID
________________________________________________________________
Maxim Integrated Products
1
Ordering Information
Typical Operating Circuit
19-5622; Rev 0; 1/11
For pricing, delivery, and ordering information, please contact Maxim Direct at 1-888-629-4642,
or visit Maxim’s website at www.maxim-ic.com.
+
Denotes a lead(Pb)-free/RoHS-compliant package.
PART TEMP RANGE PIN-PACKAGE
MAX66100E-000AA+ -25°C to +50°C ISO Card
MAX66100K-000AA+ -25°C to +50°C Key Fob
Mechanical Drawings appear at end of data sheet.
EVALUATION KIT
AVAILABLE
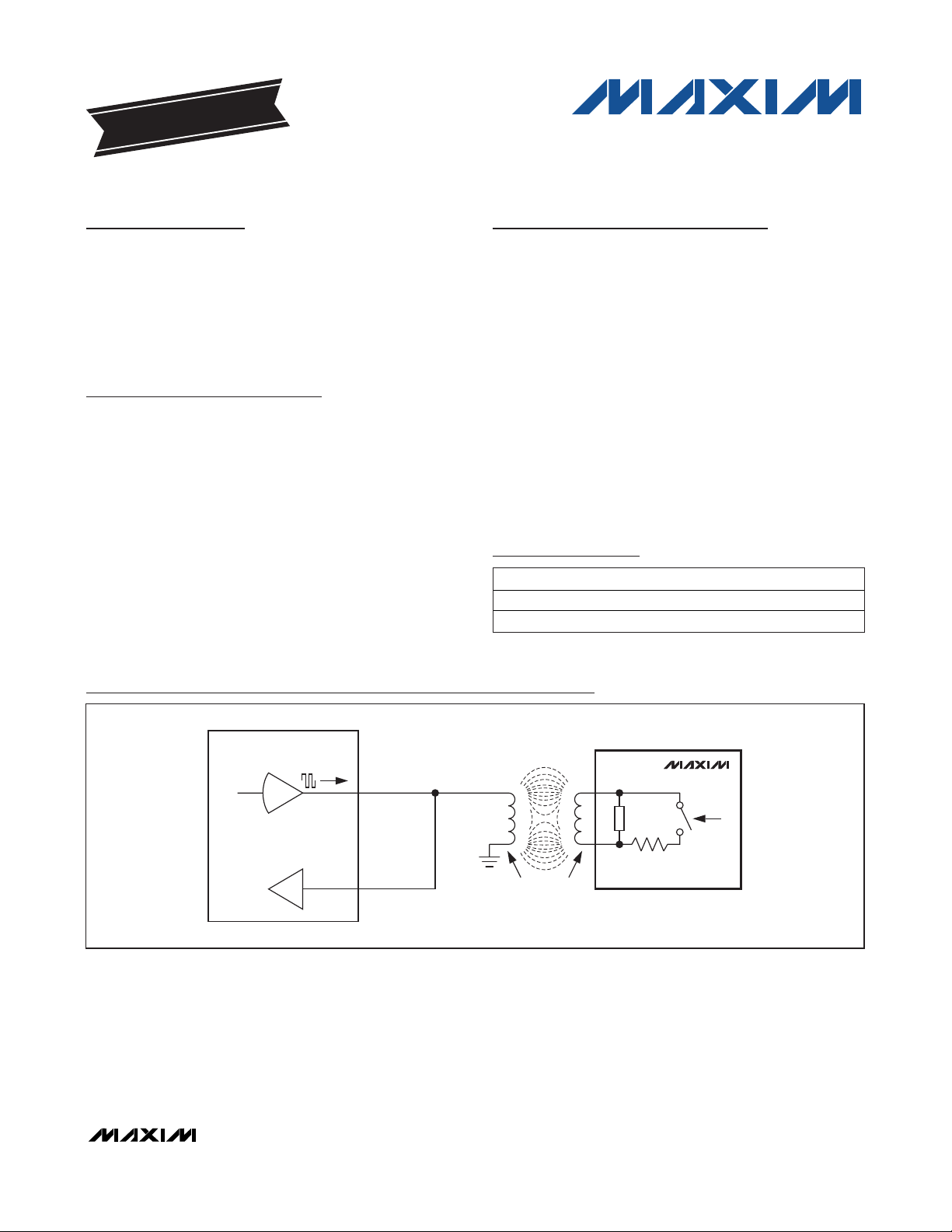
13.56MHz READER
TX_OUT
TRANSMITTER
RX_IN
MAGNETIC
COUPLING
ANTENNA
IC LOAD
SWITCHED
LOAD
MAX66100
Page 2
Detailed Description
The MAX66100 contains a 64-bit unique identifier (UID)
and a 13.56MHz ISO 15693 RF interface in a single
chip. The UID is accessed through standard ISO
15693 function commands. The data rate can be as
high as 26.69kbps. The MAX66100 supports AFI and
DSFID. Applications of the MAX66100 include driver
identification (fleet application), access control, and
asset tracking.
Overview
Figure 1 shows the relationships between the major
control and memory sections of the MAX66100.
Figure 2 shows the applicable ISO 15693 commands
and their purpose. The network function commands
allow the master to identify all slaves in its range and to
change their state, e.g., to select one for further communication. The protocol for these is described in the
Network Function Commands
section. All data is read
and written least significant bit (LSb) first, starting with
the least significant byte (LSB).
Parasite Power
As a wireless device, the MAX66100 is not connected to
any power source. It gets the energy for operation from
the surrounding RF field, which must have a minimum
strength as specified in the
Electrical Characteristics
table.
Unique Identification Number (UID)
Each MAX66100 contains a factory-programmed and
locked identification number that is 64 bits long
(Figure 3). The lower 36 bits are the serial number of the
chip. The next 8 bits store the device feature code, which
is 01h. Bits 45 to 48 are 0h. The code in bit locations 49 to
56 identifies the chip manufacturer, according to ISO/IEC
7816-6/AM1. This code is 2Bh for Maxim. The code in the
upper 8 bits is E0h. The UID is read accessible through
the Inventory and Get System Information commands.
MAX66100
ISO 15693-Compliant 64-Bit UID
2 _______________________________________________________________________________________
ABSOLUTE MAXIMUM RATINGS
ELECTRICAL CHARACTERISTICS
(TA= -25°C to +50°C.) (Note 1)
Stresses beyond those listed under “Absolute Maximum Ratings” may cause permanent damage to the device. These are stress ratings only, and functional
operation of the device at these or any other conditions beyond those indicated in the operational sections of the specifications is not implied. Exposure to
absolute maximum rating conditions for extended periods may affect device reliability.
Note 1: System requirement.
Note 2: Production tested at 13.56MHz only.
Note 3: Guaranteed by simulation; not production tested.
Note 4: Measured from the time at which the incident field is present with strength greater than or equal to H
(MIN)
to the time at
which the MAX66100’s internal power-on reset signal is deasserted and the device is ready to receive a command frame.
Not characterized or production tested; guaranteed by simulation only.
Maximum Incident Magnetic Field Strength ..........141.5dBµA/m
Operating Temperature Range ...........................-25°C to +50°C
Relative Humidity ..............................................(Water Resistant)
Storage Temperature Range ...............................-25°C to +50°C
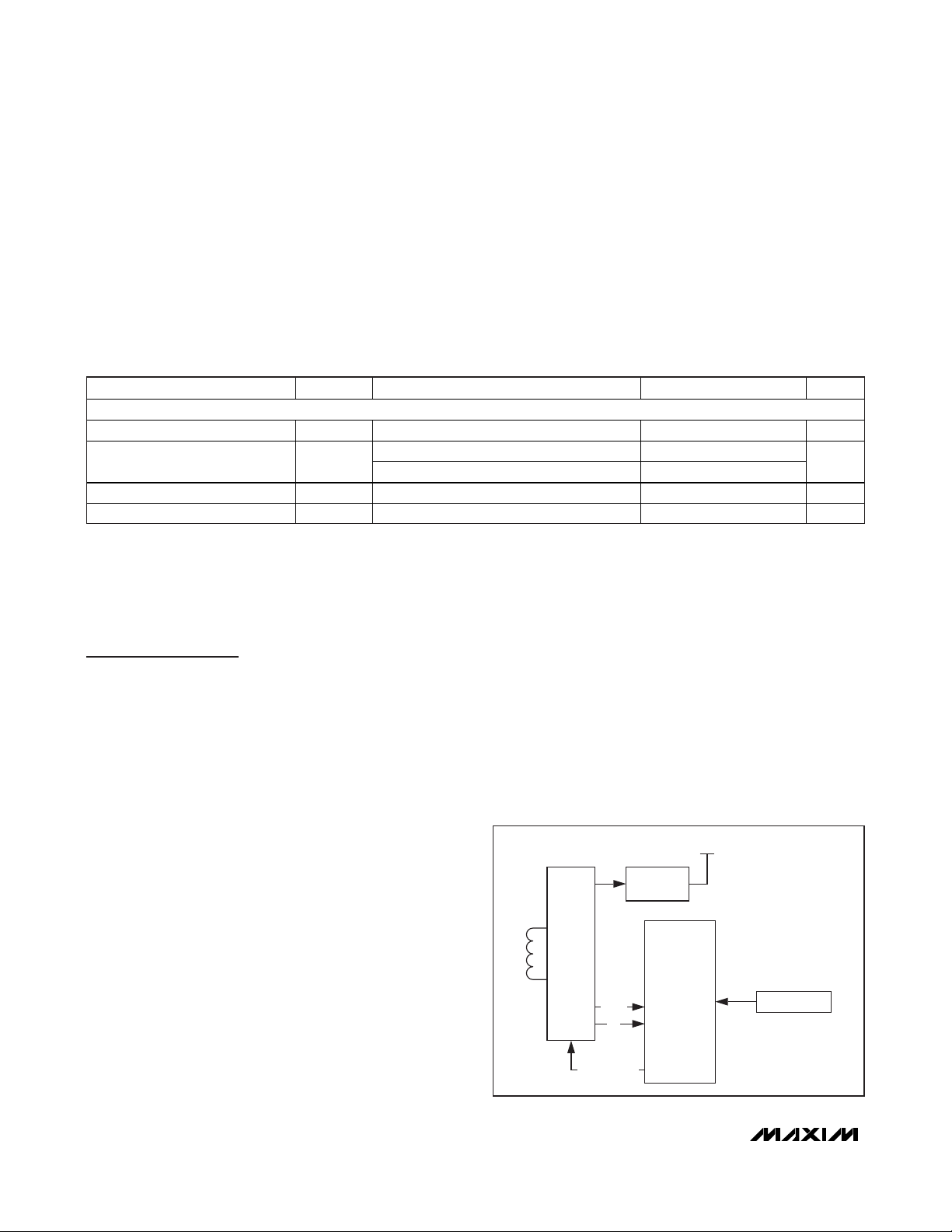
Figure 1. Block Diagram
RF INTERFACE
Carrier Frequency f
Activation Field Strength
(Note 3)
Maximum Field Strength H
Power-Up Time t
PARAMETER SYMBOL CONDITIONS MIN TYP MAX UNITS
(Notes 1, 2) 13.553 13.560 13.567 MHz
C
H
MIN
MAX
POR
At 25°C, MAX66100E 110.5
At 25°C, MAX66100K 122.0
At 25°C (Note 3) 137.5 dBμA/m
(Notes 3, 4) 1.0 ms
dBμA/m
RF
FRONT-
END
DATA
f
c
MODULATION
INTERNAL SUPPLY
VOLTAGE
REGULATOR
ISO 15693
FRAME
FORMATTING
AND
ERROR
DETECTION
UID, AFI, DSFID
Page 3
MAX66100
ISO 15693-Compliant 64-Bit UID
_______________________________________________________________________________________ 3
COMMAND TYPE:
Figure 2. ISO 15693 Commands Overview
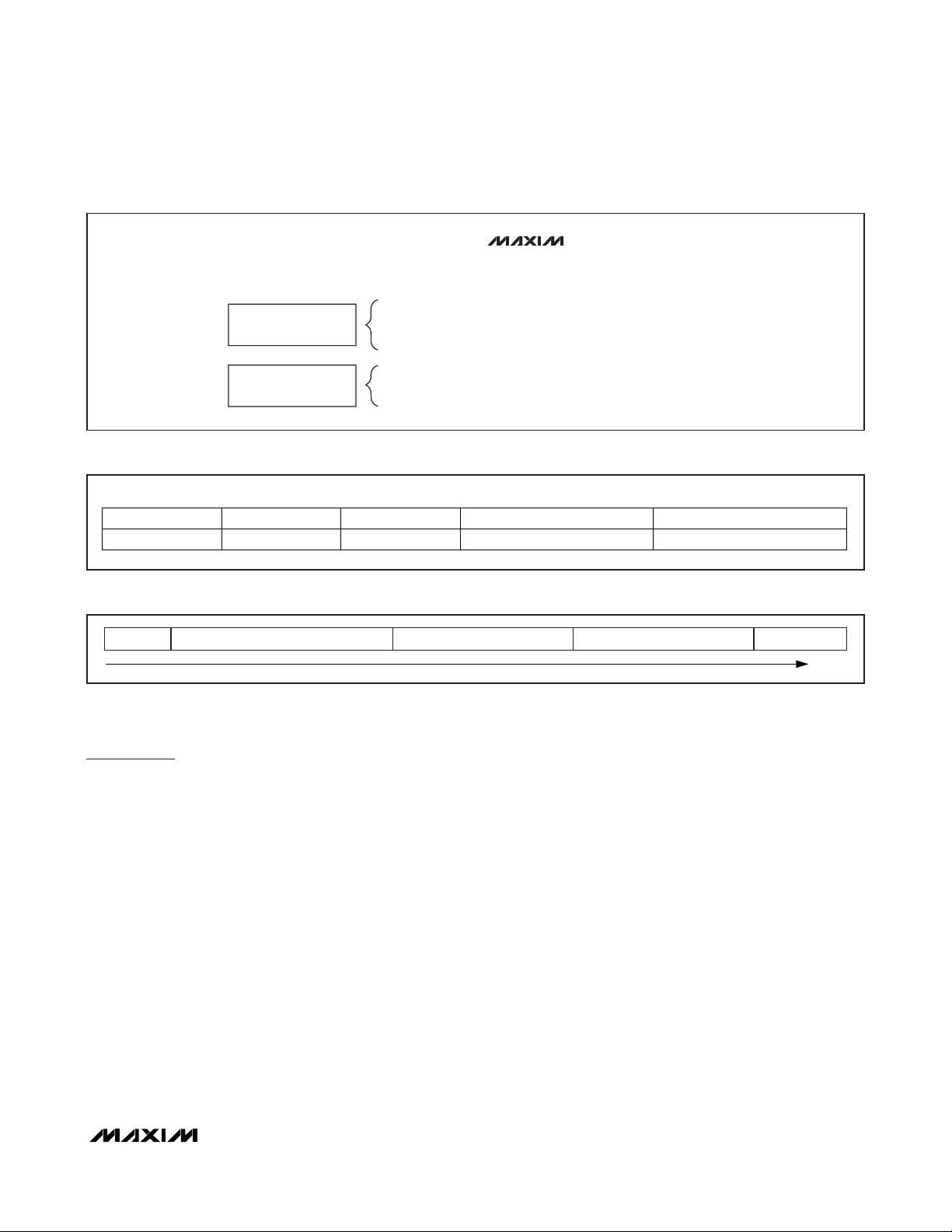
MSb LSb
64 57 56 49 48 45 44 37 36 1
E0h 2Bh 0h FEATURE CODE (01h) 36-BIT IC SERIAL NUMBER
Figure 3. 64-Bit UID
SOF 1 OR MORE DATA BYTES CRC (LSB) CRC (MSB) EOF
TIME
Figure 4. ISO 15693 Frame Format
ISO 15693 Communication
Concept
The communication between the master and the
MAX66100 (slave) is based on the exchange of data
packets. The master initiates every transaction; only
one side (master or slaves) transmits information at any
time. Each data packet begins with a start-of-frame
(SOF) pattern and ends with an end-of-frame (EOF)
pattern. A data packet with at least 3 bytes between
SOF and EOF is called a frame (Figure 4). The last 2
bytes of an ISO 15693 frame are an inverted 16-bit
CRC of the preceding data generated according to the
CRC-16-CCITT polynomial. This CRC is transmitted with
the LSB first. For more details on the CRC-16-CCITT,
refer to ISO 15693 Part 3, Annex C.
For transmission, the frame information is modulated on
a carrier frequency, which is 13.56MHz for ISO 15693.
The subsequent paragraphs are a concise description
of the required modulation and coding. For full details
including graphics of the data coding schemes and
SOF/EOF timing, refer to ISO 15693-2, Sections 7.2,
7.3, and 8.
The path from master to slave uses amplitude modulation (Figure 5); the modulation index can be either in
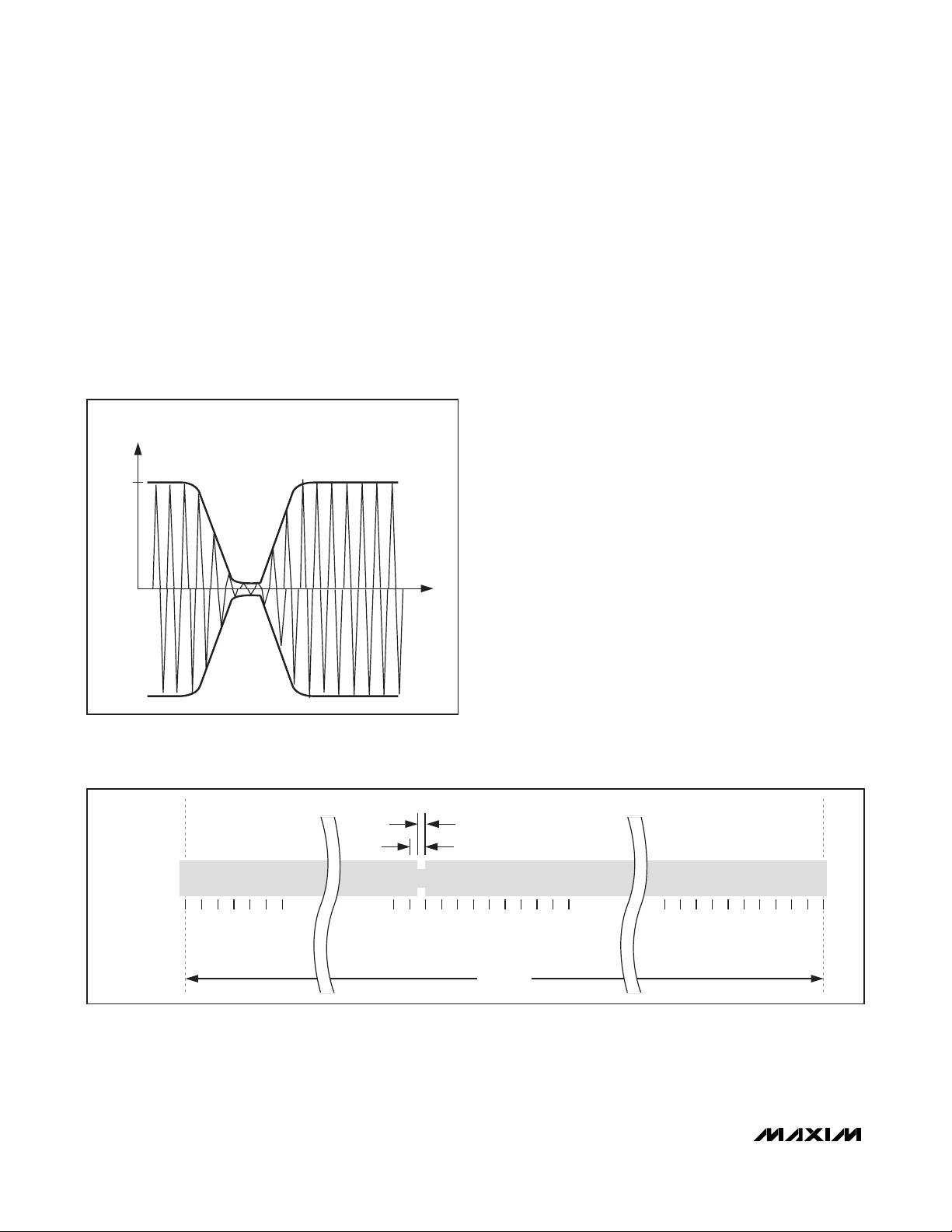
the range of 10% to 30% or 100% (ISO 15693-2,
Section 7.1). The standard defines two pulse-position
coding schemes that must be supported by a compliant device. Scheme A uses the “1 out of 256” method
(Figure 6), where the transmission of 1 byte takes
4.833ms, equivalent to a data rate of 1655bps. The
location of a modulation notch during the 4.833ms conveys the value of the byte. Scheme B uses the “1 out of
4” method (Figure 7), where the transmission of 2 bits
takes 75.52µs, equivalent to a data rate of 26,484bps.
The location of a modulation notch during the 75.52µs
conveys the value of the 2 bits. A byte is transmitted as
a concatenation of four 2-bit transmissions, with the
least significant 2 bits of the byte being transmitted
first. The transmission of the SOF pattern takes the
same time as transmitting 2 bits in Scheme B. The SOF
pattern has two modulation notches, which makes it
NETWORK
FUNCTION COMMANDS
MAX66100
AVAILABLE COMMANDS: DATA FIELD AFFECTED:
INVENTORY
STAY QUIET
SELECT
RESET TO READY
UID, AFI, DSFID, ADMINISTRATIVE DATA
UID
UID
UID
MEMORY FUNCTION
COMMANDS
GET SYSTEM INFORMATION UID, AFI, DSFID, CONSTANTS
Page 4
MAX66100
distinct from any 2-bit pattern. The position of the second notch tells whether the frame uses the “1 out of
256” or “1 out of 4” coding scheme (Figures 8 and 9,
respectively). The transmission of the EOF pattern
takes 37.76µs; the EOF is the same for both coding
schemes and has one modulation notch (Figure 10).
The path from slave to master uses one or two subcar-
riers, as specified by the Subcarrier_flag bit in the
request data packet. The standard defines two data
rates for the response, low (approximately 6600bps)
and high (approximately 26,500bps). The Data_rate_flag
bit in the request data packet specifies the response
data rate. The data rate varies slightly depending on the
use of one or two subcarriers. The LSb is transmitted
first. A compliant device must support both subcarrier
modes and data rates.
In the single subcarrier case, the subcarrier frequency
is 423.75kHz. One bit is transmitted in 37.76µs (high
data rate) or 151µs (low data rate). The modulation is
the on/off key. For a logic 0, the subcarrier is on during
the first half of the bit transmission time and off for the
second half. For a logic 1, the subcarrier is off during
the first half of the bit transmission time and on for the
second half. See Figure 11 for more details.
In the two subcarrier cases, the subcarrier frequencies
are 423.75kHz and 484.28kHz. The bit duration is the
same as in the single subcarrier case. The modulation
is equivalent to binary FM. For a logic 0, the lower subcarrier is on during the first half of the bit transmission
time, switching to the higher subcarrier for the second
half. For a logic 1, the higher subcarrier is on during the
first half of the bit transmission time, switching to the
lower subcarrier for the second half. See Figure 12 for
details. The transmission of the SOF pattern takes the
same time as transmitting 4 bits (approximately 151µs
at a high data rate or approximately 604µs at a low data
rate). The SOF is distinct from any 4-bit data sequence.
The EOF pattern is equivalent to a SOF being transmitted backwards. The exact duration of the SOF and EOF
varies slightly depending on the use of one or two subcarriers (see Figures 13 and 14, respectively).
ISO 15693-Compliant 64-Bit UID
4 _______________________________________________________________________________________
Figure 5. Downlink Modulation (e.g., Approximately 100%
Amplitude Modulation)
Figure 6. Downlink Data Coding (Case “1 Out of 256”)
CARRIER
AMPLITUDE
100%
t
PULSE-
MODULATED
CARRIER
01234 . . . . . 2
~ 9.44μs
~ 18.88μs
....... ........2
2
5
~ 4.833ms
.....
2
2
5
2
2
5
5
5
3
4
5
Page 5
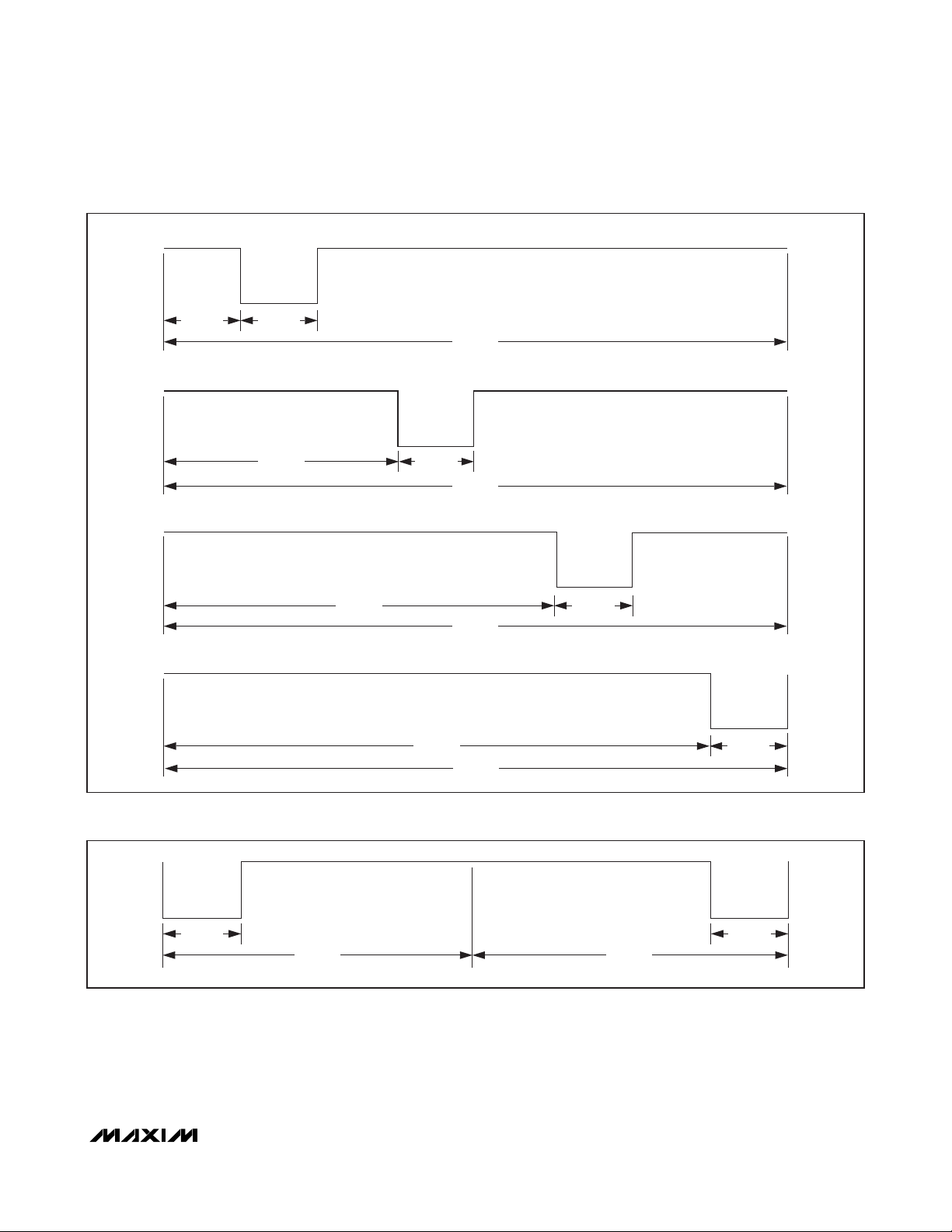
MAX66100
ISO 15693-Compliant 64-Bit UID
_______________________________________________________________________________________ 5
Figure 8. Downlink SOF for “1 Out of 256” Coding (Carrier Not Shown)
Figure 7. Downlink Data Coding (Case “1 Out of 4”) (Carrier Not Shown)
PULSE POSITION “00”
~ 9.44μs ~ 9.44μs
PULSE POSITION “01” (1 = LSb)
~ 28.32μs
PULSE POSITION “10” (0 = LSb)
PULSE POSITION “11”
~ 47.20μs
~ 75.52μs
~ 9.44μs
~ 75.52μs
~ 9.44μs
~ 75.52μs
~ 66.08μs
~ 75.52μs
~ 9.44μs
~ 37.76μs ~ 37.76μs
~ 9.44μs
~ 9.44μs
Page 6

MAX66100
ISO 15693-Compliant 64-Bit UID
6 _______________________________________________________________________________________
Figure 9. Downlink SOF for “1 Out of 4” Coding (Carrier Not Shown)
Figure 10. Downlink EOF (Identical for Both Coding Schemes) (Carrier Not Shown)
Figure 11. Uplink Coding, Single Subcarrier Case (High Data-Rate Timing)
~ 9.44μs
~ 37.76μs ~ 37.76μs
~ 9.44μs
~ 37.76μs
423.75kHz, ~ 18.88μs ~ 18.88μs
~ 9.44μs~ 9.44μs
~ 9.44μs
TRANSMITTING A ZERO
~ 37.76μs
TRANSMITTING A ONE
423.75kHz, ~ 18.88μs~ 18.88μs
~ 37.76μs
Page 7

MAX66100
ISO 15693-Compliant 64-Bit UID
_______________________________________________________________________________________ 7
Figure 12. Uplink Coding, Two Subcarriers Case (High Data-Rate Timing)
Figure 13. Uplink SOF, Single Subcarrier Case (High Data-Rate Timing)
Figure 14. Uplink SOF, Two Subcarriers Case (High Data-Rate Timing)
484.28kHz, ~ 18.58μs423.75kHz, ~ 18.88μs
~ 37.46μs
484.28kHz, ~ 18.58μs 423.75kHz, ~ 18.88μs
~ 37.46μs
423.75kHz 423.75kHz
~ 56.64μs ~ 56.64μs ~ 37.76μs
TRANSMITTING A ZERO
TRANSMITTING A ONE
~ 55.75μs ~ 56.64μs ~ 37.46μs
423.75kHz 423.75kHz484.28kHz484.28kHz
Page 8

MAX66100
ISO 15693-Compliant 64-Bit UID
8 _______________________________________________________________________________________
ISO 15693 Slave States and
Address Modes
Initially, the master has no information whether there are
any RF devices in the field of its antenna. The master
learns the UIDs of the slaves in its field from the
responses to the Inventory command, which does not
use the Address_flag and the Select_flag bits. The state
transitions are controlled by network function commands. Figure 15 shows details.
ISO 15693 defines four states in which a slave can be
plus three address modes. The states are power-off,
ready, quiet, and selected. The address modes are
nonaddressed, addressed, and selected. The
addressed mode requires that the master include the
slave’s UID in the request, which increases the size of
the requests by 8 bytes. Table 1 shows which address
mode is applicable depending on the slave’s state and
how to set the Address_flag and the Select_flag bits for
each address mode.
ISO 15693 States and Transitions
Power-Off State
This state applies if the slave is outside the master’s RF
field. A slave transitions to the power-off state when
leaving the power-delivering RF field. When entering
the RF field, the slave automatically transitions to the
ready state.
Ready State
In this state, a slave has enough power to perform any
of its functions. The purpose of the ready state is to have
the slave population ready to process the inventory
command as well as other commands sent in the
addressed or nonaddressed mode. A slave can exit the
ready state and transition to the quiet or the selected
state upon receiving the Stay Quiet or Select command
sent in the addressed mode.
Quiet State
In this state, a slave has enough power to perform any
of its functions. The purpose of the quiet state is to
silence slaves that the master does not want to communicate with. Only commands sent with the addressed
mode are accepted and processed. This way the master can use the nonaddressed mode for communication
with remaining slaves in the ready state, which minimizes the size of the request data packets. As long as
no additional slaves arrive in the RF field, it is safe for
the master to continue communicating in the nonaddressed mode. A slave can exit the quiet state and
transition to the ready or the selected state upon receiving the Reset to Ready or Select command sent in the
addressed mode.
Selected State
In this state, a slave has enough power to perform any
of its functions. The purpose of the selected state is to
isolate the slave that the master wants to communicate
with. Commands are accepted and processed regardless of the address mode in which they are sent, including the Inventory command. With multiple slaves in the
RF field, the master can put one slave in the selected
state and leave all the others in the ready state. This
method requires less communication than using the
quiet state to single out the slave for communication.
For a slave in the selected state, the master can use the
selected mode, which keeps the request data packets
as short as with the nonaddressed mode. A new slave
entering the RF field cannot disturb the communication,
since it stays in the ready state. A slave can exit the
Table 1. Slave States and Applicable Address Modes
ADDRESS MODES
NONADDRESSED MODE
SLAVE STATES
Power-Off (Inactiv e) (Inactive) (Inacti ve)
Ready Yes Yes No
Quiet No Yes No
Selected Yes Yes Yes
(Address_flag = 0;
Select_flag = 0)
ADDRESS ED MODE
(Address_flag = 1;
Select_flag = 0)
SELECTED MODE
(Address_flag = 0;
Select_flag = 1)
Page 9

selected state and transition to the ready or the quiet
state upon receiving the Reset to Ready command sent
in any address mode or the Stay Quiet command sent
in the addressed mode. A slave also transitions from
selected to ready upon receiving a Select command if
the UID in the request is different from the slave’s own
UID. In this case the master’s intention is to transition
another slave with the matching UID to the selected
state. If the slave already in the selected state does not
recognize the command (e.g., due to a bit error), two
slaves could be in the selected state. To prevent this
from happening, the master should use the Reset to
Ready or the Stay Quiet command to transition a slave
out of the selected state.
MAX66100
ISO 15693-Compliant 64-Bit UID
_______________________________________________________________________________________ 9
Figure 15. ISO 15693 State Transitions Diagram
RESPONSE LEGEND:
RESPONSE TO
RESPONSE TO
NO RESPONSE
RESET TO READY
SELECT
ADDRESS MODE LEGEND:
POWER-OFF
[N] NONADDRESSED
[A] ADDRESSED
[S] SELECTED
OUT OF FIELD
RESET TO READY [A]
MATCHING UID
NOTE 2
NOTE 1: THE SLAVE PROCESSES THE INVENTORY COMMAND AND OTHER COMMANDS PROVIDED THAT THEY ARE SENT IN THE [N] OR [A] ADDRESS MODE.
NOTE 2: THE SLAVE PROCESSES ONLY COMMANDS SENT IN THE [A] ADDRESS MODE.
NOTE 3: THE SLAVE PROCESSES THE INVENTORY COMMAND AND OTHER COMMANDS IN ANY ADDRESS MODE.
OUT OF FIELD
READY
SELECT [A]
MATCHING UID
STAY QUIET [A]
MATCHING UID
STAY QUIET [A] MATCHING UID
SELECT [A] MATCHING UID
IN FIELD
NOTE 1
OUT OF FIELD
RESET TO READY
[N, A, S]
SELECT [A],
NONMATCHING UID
SELECTEDQUIET
NOTE 3
Page 10

MAX66100
Request Flags
The command descriptions on the subsequent pages
begin with a byte called request flags. The ISO 15693
standard defines two formats for the request flags byte.
The state of the Inventory_flag bit controls the function
of the bits in the upper half of the request flags byte.
The function of the request flags byte is as follows.
Inventory_flag Bit Not Set
Bits 8, 4: No Function. These bits have no function.
They must be transmitted as 0.
Bit 7: Options Flag (Option_flag). This bit is used with
block read commands to include the block security status in the response. If not applicable for a command,
the Option_flag bit must be 0.
Bit 6: Address Flag (Address_flag). This bit specifies
whether all slaves in the master’s field that are in the
selected or ready state process the request (bit = 0) or
only the single slave whose UID is specified in the
request (bit = 1). If the Address_flag bit is 0, the
request must not include a UID. The combination of
both the Select_flag and Address_flag bits being set
(= 1) is not valid.
Bit 5: Select Flag (Select_flag). This bit specifies
whether the request is processed only by the slave in
the selected state (bit = 1) or by any slave according to
the setting of the Address_flag bit (bit = 0).
Bit 3: Inventory Flag (Inventory_flag). This bit must
be 1 for the Inventory command only. For all other commands, this bit must be 0.
Bit 2: Data Rate Flag (Data_rate_flag). This bit specifies whether the response data packet is transmitted
using the low data rate (bit = 0) or the high data rate
(bit = 1).
Bit 1: Subcarrier Flag (Subcarrier_flag). This bit
specifies whether the response data packet is transmitted using a single subcarrier (bit = 0) or two subcarriers
(bit = 1).
Inventory_flag Bit Set
Bits 8, 7, 4: No Function. These bits have no function.
They must be transmitted as 0.
Bit 6: Slot Counter Flag (Nb_slots_flag). This bit
specifies whether the command is processed using a
slot counter (bit = 0) or without using the slot counter
(bit = 1).
Bit 5: Application Family Identifier Flag (AFI_flag).
To detect only slaves with a certain AFI value, the
AFI_flag bit must be 1 and the desired AFI value must
be included in the request. If the least significant nibble
of the AFI in the request is 0000b, slaves process the
command only if the most significant nibble of the AFI
matches. If the AFI in the request is 00h, all slaves
process the command regardless of their AFI.
Bit 3: Inventory Flag (Inventory_flag). This bit must
be 1 for the Inventory command only. For all other commands, this bit must be 0.
Bit 2: Data Rate Flag (Data_rate_flag). This bit specifies whether the response data packet is transmitted
using the low data rate (bit = 0) or the high data rate
(bit = 1).
Bit 1: Subcarrier Flag (Subcarrier_flag). This bit
specifies whether the response data packet is transmitted using a single subcarrier (bit = 0) or two subcarriers
(bit = 1).
ISO 15693-Compliant 64-Bit UID
10 ______________________________________________________________________________________
Request Flags, Inventory_flag Bit Not Set
Request Flags, Inventory_flag Bit Set
BIT 8 (MSb) BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1 (LSb)
0 Option_f lag Address_flag Select_flag 0
Inventory_flag
(= 0)
Data_rate_flag Subcarrier_flag
BIT 8 (MSb) BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1 (LSb)
0 0 Nb_s lots_flag AFI_flag 0
Inventory_flag
(= 1)
Data_rate_flag Subcarrier_flag
Page 11

MAX66100
ISO 15693-Compliant 64-Bit UID
______________________________________________________________________________________ 11
Network Function Commands
The command descriptions show the data fields of the
request and response data packets. To create the complete frame, an SOF, 16-bit CRC, and EOF must be
added (see Figure 4). The ISO 15693 standard defines
four network function commands: Inventory, Stay Quiet,
Select, and Reset to Ready. This section describes the
format of the request and response data packets.
Inventory
The Inventory command allows the master to learn the
UIDs and DSFIDs of all slaves in its RF field in an iterative process. It is the only command for which the
Inventory_flag bit must be 1. The Inventory command
uses two command-specific parameters, which are the
mask length and the mask pattern. The mask allows the
master to preselect slaves for responding to the
Inventory command. The LSb of the mask aligns with
the LSb of the slave’s UID. The master can choose not
to use a mask, in which case all slaves qualify, provided they are not excluded by the AFI criteria (see the
Request Flags
section). The maximum mask length is
60 (3Ch, if Nb_slots_flag = 0) or 64 (40h, if
Nb_slots_flag = 1). The mask pattern defines the least
significant bits (as many as specified by the mask
length) that a slave’s UID must match to qualify for
responding to the Inventory command (case
Nb_slots_flag = 1). If the slot counter is used
(Nb_slots_flag = 0), the value of the slot counter
extends the mask pattern at the higher bits for comparison to the slave’s UID. The slot counter starts at 0 after
the inventory request frame is transmitted and increments during the course of the Inventory command with
every subsequent EOF sent by the master. The pro-
cessing of an Inventory command ends when the master sends the SOF of a new frame.
Response data for the Inventory command (no error) is
transmitted only if a slave qualifies to respond. In case
of an error in the request, slaves do not respond.
When receiving the Inventory command, the slave
devices in the RF field enter the collision management
sequence. If a slave meets the conditions to respond, it
sends out a response data packet. If multiple slaves
qualify, e.g., AFI, mask, and slot counter are not used,
the response frames collide and are not readable. To
receive readable response frames with the UID and
DSFID, the master must eliminate the collision.
Not knowing the slave population, the master could
begin with a mask length of 0 and activate the slot
counter. By using this method and going through all 16
slots, the master has a chance to receive clean
responses (i.e., the slave is identified) as well as colliding responses. To prevent a slave that has been identified from further participating in the collision
management sequence, the master transitions it to the
quiet state. Next, the master issues another Inventory
command where the slot number that previously generated a collision is now used as a 4-bit mask, and runs
again through all 16 slots. If a collision is found, another
inventory command is issued, this time with a mask that
is extended at the higher bits by the slot counter value
that produced the collision. This process is repeated
until all slaves are identified. For a full description of the
Inventory command processing by the slave device
and the timing specifications, refer to ISO 15693 Part 3,
Sections 8 and 9.
Note 1: The AFI byte is transmitted only if the AFI_flag bit is set to 1. The AFI byte, if transmitted, narrows the range of slaves that
qualify for responding to the request.
Note 2: The mask pattern is transmitted only if the selection mask length is not 0. If the mask length is not an integer multiple of 8,
the MSB of the mask pattern must be padded with 0 bits. The LSb of the mask pattern is transmitted first.
Request Data for the Inventory Command
Response Data for the Inventory Command (No Error)
REQUEST FLAGS COMMAND
(1 Byte) 01h (1 Byte) (1 Byte) (Up to 8 Bytes)
AFI
(NOTE 1)
MASK LENGTH
MASK PATTERN
(NOTE 2)
RESPONSE FLAGS DSFID UID
00h (1 Byte) (8 Bytes)
Page 12

MAX66100
Stay Quiet
The Stay Quiet command addresses an individual slave
and transitions it to the quiet state. The request must be
sent in the addressed mode (Select_flag bit = 0,
Address_flag bit = 1). The slave transitioning to the
quiet state does not send a response.
Select
The Select command addresses an individual slave
and transitions it to the selected state. The request
must be sent in the addressed mode (Select_flag
bit = 0, Address_flag bit = 1). The slave transitioning to
the selected state sends a response. If there was a
slave with a different UID in the selected state, then that
slave transitions to the ready state without sending a
response.
Reset to Ready
The Reset to Ready command addresses an individual
slave and transitions it to the ready state. To address a
slave in the quiet state, the request must be sent in the
addressed mode (Select_flag bit = 0, Address_flag
bit = 1). To address a slave in the selected state, the
request can be sent in any address mode. The slave
transitioning to the ready state sends a response.
Memory Function Commands
The command descriptions show the data fields of the
request and response data packets. To create the complete frame, an SOF, 16-bit CRC, and EOF must be
added (see Figure 4). ISO 15693 defines three address
modes, selected, addressed, and nonaddressed,
which are specified through the setting of the
Select_flag bit and the Address_flag bit. The memory
function commands can be issued in any address
mode. To access slaves in the quiet state, the
addressed mode is required. The addressed mode
requires that the master include the slave's UID in the
request.
Error Indication
In case of an error, the response to a request begins
with a response flags byte 01h followed by one error
code.
If there was no error, the response begins with a
response flags byte 00h followed by command-specific
data, as specified in the detailed command description.
If the MAX66100 does not recognize a command, it
does not generate a response.
ISO 15693-Compliant 64-Bit UID
12 ______________________________________________________________________________________
*
If this command is processed without any error, the slave responds with a response flags byte of 00h.
*
If this command is processed without any error, the slave responds with a response flags byte of 00h.
**
The UID is transmitted only in the addressed mode.
Request Data for the Stay Quiet Command
Request Data for the Select Command*
Request Data for the Reset to Ready Command*
REQUEST FLAGS COMMAND UID
(1 Byte) 02h (8 Bytes)
REQUEST FLAGS COMMAND UID
(1 Byte) 25h (8 Bytes)
REQUEST FLAGS COMMAND UID**
(1 Byte) 26h (8 Bytes)
Page 13

MAX66100
ISO 15693-Compliant 64-Bit UID
______________________________________________________________________________________ 13
Detailed Command Descriptions
In the request data graphics of this section, the UID
field is shaded to indicate that the inclusion of the UID
depends on the address mode.
Get System Information
The Get System Information command is the only command beyond the network function level that the
MAX66100 supports. It allows the master to retrieve
technical information about the MAX66100. The IC reference code indicates the die revision in hexadecimal
format, such as A1h, A2h, B1h, etc.
CRC Generation
The ISO 15693 standard uses a 16-bit CRC, generated
according to the CRC-16-CCITT polynomial function:
X16+ X12+ X5+ 1 (see Figure 16). This CRC is used
for error detection in request and response data packets and is always communicated in the inverted form.
After all data bytes are shifted into the CRC generator,
the state of the 16 flip-flops is parallel-copied to a shift
register and shifted out for transmission with the LSb
first. For more details on this CRC, refer to ISO/IEC
15693-3, Annex C.
Request Data for the Get System Information Command
Response Data for the Get System Information Command (No Error)
Figure 16. CRC-16-CCITT Generator
REQUEST FLAGS COMMAND UID
(1 Byte) 2Bh (8 Bytes)
RESPONSE
FLAGS
INFO
FLAGS
UID DSFID AFI
NUMBER OF
BLOCKS
MEMORY BLOCK
SIZE
00h 0Fh (8 Bytes) (1 Byte) (1 Byte) 00h 07h (1 Byte)
IC REFERENCE
MSb
1ST
STAGE
0
X
9TH
STAGE
8
X
2ND
STAGE
1
X
10TH
STAGE
9
X
X
POLYNOMIAL = X16 + X12 + X5 + 1
3RD
STAGE
2
X
11TH
STAGE
10
4TH
STAGE
3
X
12TH
STAGE
11
X
5TH
STAGE
4
X
13TH
STAGE
12
X
6TH
STAGE
5
X
14TH
STAGE
13
X
7TH
STAGE
6
X
15TH
STAGE
14
X
7
X
15
X
INPUT DATA
STAGE
LSb
16TH
STAGE
8TH
16
X
Page 14

MAX66100
ISO 15693-Compliant 64-Bit UID
14 ______________________________________________________________________________________
Command-Specific ISO 15693 Communication Protocol—Legend
Command-Specific ISO 15693 Communication Protocol—Color Codes
ISO 15693 Communication Examples
SYMBOL DESCRIPTION
GSY Command “Get System Information”
SOF Start of Frame
RQF Request F lags byte (always sent by master)
CRC-16
EOF End of Frame
RSF Response Flags byte (always sent by slave)
[UID]
Transm iss ion of an inverted CRC-16 (2 bytes)
generated according to CRC-16-CCITT
The tag’s unique 8-byte identificat ion number;
could be sent by either the master or the slave.
The brackets [ ] indicate that the transm iss ion
of the UID depends on the request flags (RQF).
Master-to-Slave Slave-to-Master
SYMBOL DESCRIPTION
IFLG Info Flags byte (alwa ys sent by s lave)
DSFID Data Storage Format Identifier byte
AFI Application Family Identifier byte
NBLK
MBS
ICR IC Reference byte (slave chip revision)
Number of B loc ks byte (slave memor y s ize
indicator)
Memory Block Size byte (slave memory block
size)
Get System Information
SOF
RQF GSY EOF (Carrier)[UID] CRC-16
Success
SOF EOFUID AFI ICRMBSIFLG NBLKDSFIDRSF = 00h
CRC-16
Page 15

MAX66100
ISO 15693-Compliant 64-Bit UID
______________________________________________________________________________________ 15
Mechanical Drawings
TOP VIEW
SIDE VIEW
TOP VIEW
28mm
54mm
MAX66100K-000AA+
KEY FOB
85.60mm
7.7mm
1.6mm
SIDE VIEW
3.49mm
14.29mm
53.98mm
MAX66100E-000AA+
0.76mm
ISO CARD
Page 16

MAX66100
ISO 15693-Compliant 64-Bit UID
Maxim cannot assume responsibility for use of any circuitry other than circuitry entirely embodied in a Maxim product. No circuit patent licenses are
implied. Maxim reserves the right to change the circuitry and specifications without notice at any time.
16
____________________Maxim Integrated Products, 120 San Gabriel Drive, Sunnyvale, CA 94086 408-737-7600
© 2011 Maxim Integrated Products Maxim is a registered trademark of Maxim Integrated Products, Inc.
Revision History
REVISION
NUMBER
0 1/11 Init ial relea se —
REVISION
DATE
DESCRIPTION
PAGES
CHANGED
 Loading...
Loading...