Page 1
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
________________________________________________________________
Maxim Integrated Products
1
19-5540; Rev 0; 12/10
For pricing, delivery, and ordering information, please contact Maxim Direct at 1-888-629-4642,
or visit Maxim’s website at www.maxim-ic.com.
General Description
The MAX66020 combines 1024 bits of user EEPROM, a
64-bit unique identifier (UID), and a 13.56MHz RF interface (ISO/IEC 14443 Type B, Parts 2-4) in a plastic key
fob. The memory is organized as 16 blocks of 8 bytes
plus two more blocks for data and control registers.
Four adjacent user EEPROM blocks form a memory
page (pages 0 to 3). Memory protection features are
write protection and EPROM emulation, which the user
can set for each individual memory page. Memory
access is accomplished through the block transmission
protocol (ISO/IEC 14443-4), where requests and
responses are exchanged through I-blocks once a
device is in the ACTIVE state. The data rate can be as
high as 847.5kbps. The reader must support a frame
size of 19 bytes. The device supports an application
family identifier (AFI) and a card identifier (CID).
ISO/IEC 14443 functions not supported are chaining,
frame-waiting time extension, and power indication.
Applications
Driver Identification (Fleet Application)
Access Control
Asset Tracking
Features
♦ Fully Compliant ISO/IEC 14443 (Parts 2-4) Type B
Interface
♦ 13.56MHz ±7kHz Carrier Frequency
♦ 1024-Bit User EEPROM with Block Lock Feature,
Write-Cycle Counter, and Optional EPROMEmulation Mode
♦ 64-Bit UID
♦ Read and Write (64-Bit Block)
♦ Supports AFI and CID Function
♦ 10ms Maximum Programming Time
♦ To Fob: 10% ASK Modulation at 105.9kbps,
211.9kbps, 423.75kbps, or 847.5kbps
♦ From Fob: Load Modulation Using BPSK
Modulated Subcarrier at 105.9kbps, 211.9kbps,
423.75kbps, or 847.5kbps
♦ 200,000 Write/Erase Cycles (Minimum)
♦ 40-Year Data Retention (Minimum)
♦ Powered Entirely Through the RF Field
♦ Operating Temperature: -25°C to +50°C
Ordering Information
+
Denotes a lead(Pb)-free/RoHS-compliant package.
PART TEMP RANGE PIN-PACKAGE
MAX66020K-000AA+ -25°C to +50°C Key Fob
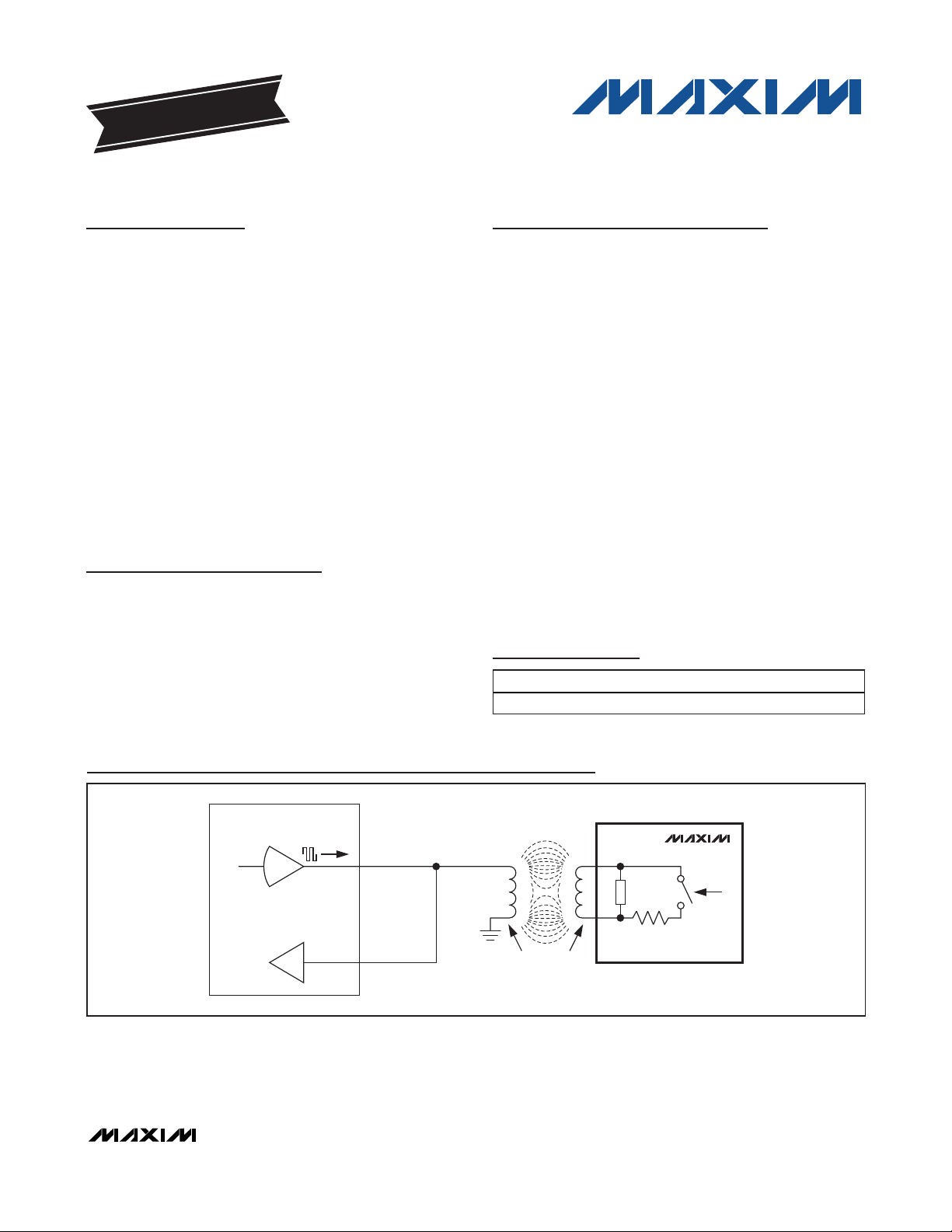
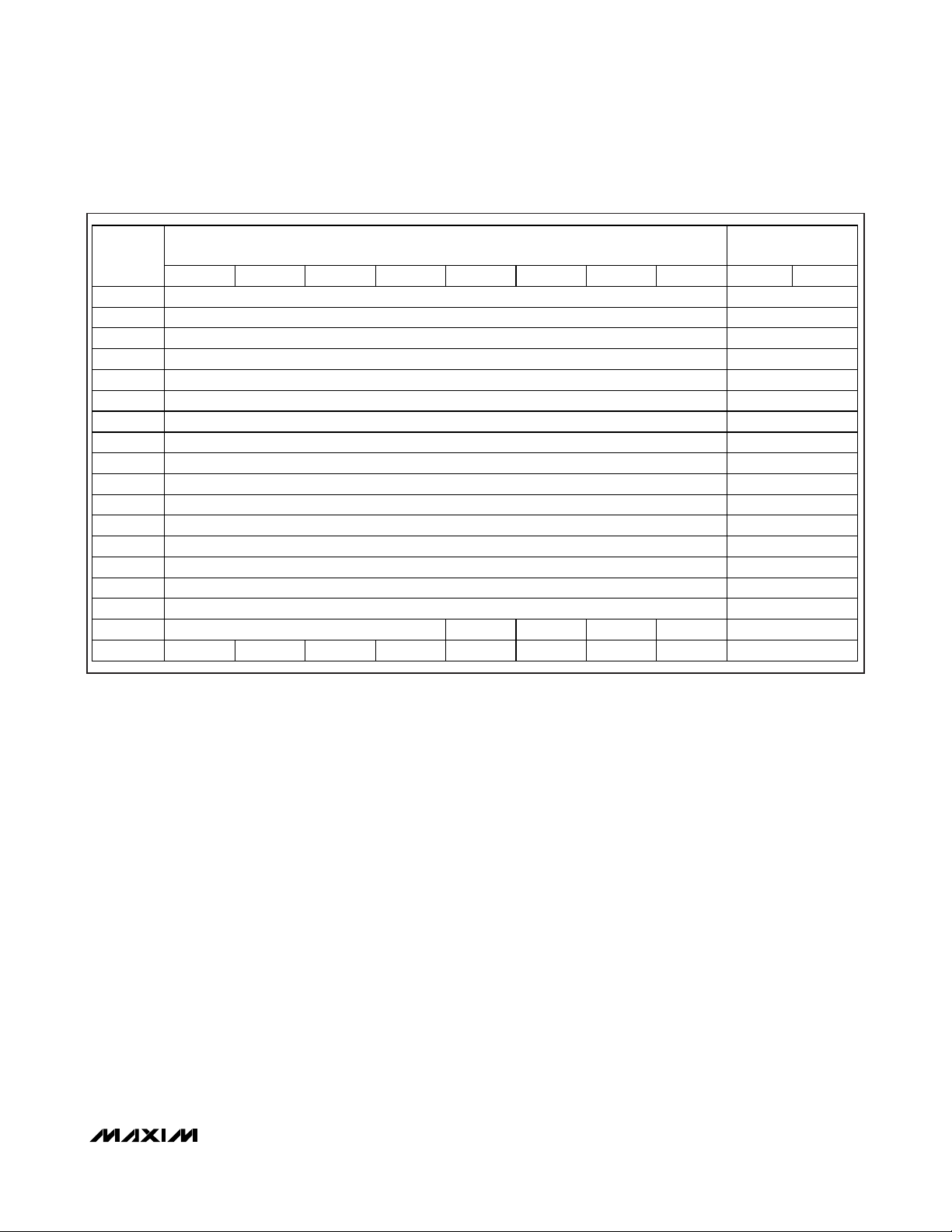
Typical Operating Circuit
Key Fob Mechanical Drawing appears at end of data sheet.
EVALUATION KIT
AVAILABLE
13.56MHz READER
TX_OUT
TRANSMITTER
RX_IN
MAGNETIC
COUPLING
MAX66020
IC LOAD
SWITCHED
ANTENNA
LOAD
Page 2
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
2 _______________________________________________________________________________________
ABSOLUTE MAXIMUM RATINGS
ELECTRICAL CHARACTERISTICS
(TA= -25°C to +50°C.) (Note 1)
Stresses beyond those listed under “Absolute Maximum Ratings” may cause permanent damage to the device. These are stress ratings only, and functional
operation of the device at these or any other conditions beyond those indicated in the operational sections of the specifications is not implied. Exposure to
absolute maximum rating conditions for extended periods may affect device reliability.
Note 1: System requirement.
Note 2: Measured from the time at which the incident field is present with strength greater than or equal to H
(MIN)
to the time at
which the MAX66020’s internal power-on reset signal is deasserted and the device is ready to receive a command frame.
Not characterized or production tested; guaranteed by simulation only.
Maximum Incident Magnetic Field Strength ..........141.5dBµA/m
Operating Temperature Range ...........................-25°C to +50°C
Relative Humidity ..............................................(Water Resistant)
Storage Temperature Range ...............................-25°C to +50°C
PARAMETER SYMBOL CONDITIONS MIN TYP MAX UNITS
EEPROM
Programm ing Time t
Endurance N
Data Retention t
RF INTERFACE
Carrier Frequency f
Operating Magnetic Field Strength H At +25°C (Note 1) 123.5 137.5 dBμA/m
Power-Up Time t
PROG
CYCLE
RET
POR
9 10 ms
At +25°C 200,000 Cycles
40 Years
(Note 1) 13.553 13.560 13.567 MHz
C
(Note 2) 1.0 ms
Page 3
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
_______________________________________________________________________________________ 3
Detailed Description
The MAX66020 combines 1024 bits of user EEPROM,
128 bits of user and control registers, a 64-bit UID, and
a 13.56MHz RF interface (ISO/IEC 14443 Type B, Parts
2-4) in a single key fob. The memory is organized as 18
blocks of 8 bytes each. Four adjacent user EEPROM
blocks form a memory page (pages 0 to 3). Memory
protection features include write protection and EPROM
emulation, which the user can set for each individual
memory page. The memory of the MAX66020 is
accessed through the ISO/IEC 14443-4 block transmission protocol, where requests and responses are
exchanged through I-blocks once a device is in the
ACTIVE state. The reader must support a frame size of
at least 19 bytes. The data rate can be as high as
847.5kbps. The MAX66020 supports AFI and CID.
Functions not supported are chaining, frame-waiting
time extension, and power indication. Applications of
the MAX66020 include driver identification (fleet application), access control, and asset tracking.
Overview
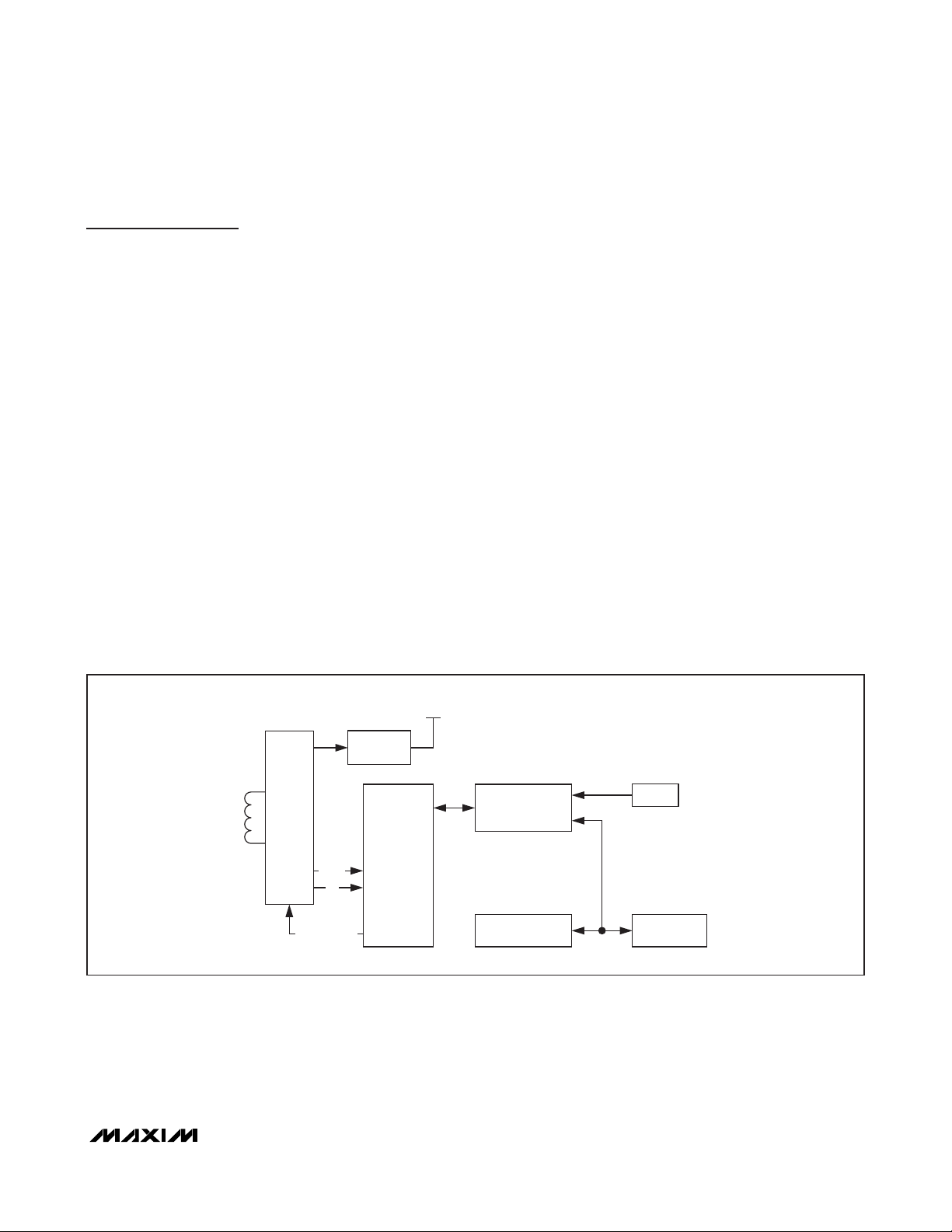
Figure 1 shows the relationships between the major
control and memory sections of the MAX66020. The
device has three main data components: 64-bit UID,
four 256-bit pages of user EEPROM, and two 8-byte
blocks of user and control registers. Figure 2 shows the
hierarchical structure of the ISO/IEC 14443 Type Bcompliant access protocol. The master must first apply
network function commands to put the MAX66020 into
the ACTIVE state before the memory and control functions become accessible. The protocol required for
these network function commands is described in the
Network Function Commands
section. Once the
MAX66020 is in the ACTIVE state, the master can issue
any one of the available memory and control function
commands. Upon completion of such a command, the
MAX66020 returns to the ACTIVE state and the master
can issue another memory and control function command or deselect the device, which returns it to the
HALT state. The protocol for these memory and control
function commands is described in the
Memory and
Control Function Commands
section. All data is read
and written least significant bit (LSb) first, starting with
the least significant byte (LSB).
Parasite Power
As a wireless device, the MAX66020 is not connected
to any power source. It gets the energy for operation
from the surrounding RF field, which needs to have a
minimum strength as specified in the
Electrical
Characteristics
table.
Figure 1. Block Diagram
RF
FRONT-
END
DATA
f
c
MODULATION
VOLTAGE
REGULATOR
ISO 14443
FRAME
FORMATTING
AND
ERROR
DETECTION
INTERNALSUPPLY
MEMORY AND
FUNCTION
CONTROL
REGISTER
BLOCK
UID
USER
EEPROM
Page 4
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
4 _______________________________________________________________________________________
Figure 2. Hierarchical Structure of ISO/IEC 14443 Type B Protocol
MSb LSb
64 57 56 49 48 45 44 37 36 1
E0h 2Bh 0h FEATURE CODE (02h) 36-BIT IC SERIAL NUMBER
Figure 3. 64-Bit UID
Unique Identification Number (UID)
Each MAX66020 contains a factory-programmed and
locked identification number that is 64 bits long
(Figure 3). The lower 36 bits are the serial number of
the chip. The next 8 bits store the device feature
code, which is 02h. Bits 45 to 48 are 0h. The code in
bit locations 49 to 56 identifies the chip manufacturer,
according to ISO/IEC 7816-6/AM1. This code is 2Bh
for Maxim. The code in the upper 8 bits is E0h. The
UID is read accessible through the Get UID and Get
System Information commands. The lower 32 bits of
the UID are transmitted in the PUPI field of the ATQB
response to the REQB, WUPB, or SLOT-MARKER
command. By default, the upper 32 bits of the UID are
factory programmed into the application data field,
which is transmitted as part of the ATQB response.
This way the master receives the complete UID in the
first response from the slave. See the
Network
Function Commands
section for details.
Detailed Memory Description
The memory of the MAX66020 is organized as 18
blocks of 8 bytes each. Figure 4 shows the memory
map. The first 16 blocks (block numbers 00h to 0Fh in
hexadecimal counting) are the user EEPROM, the area
for application-specific data. Four adjacent blocks are
referred to as a page. Blocks 00h to 03h are page 0,
blocks 04h to 07h are page 1, blocks 08h to 0Bh are
page 2, and blocks 0Ch to 0Fh are page 3.
MAX66020
COMMAND LEVEL:
NETWORK
FUNCTION COMMANDS
AVAILABLE COMMANDS: DATA FIELD AFFECTED:
REQUEST (REQB)
WAKEUP (WUPB)
SLOT-MARKER
HALT (HLTB)
SELECT (ATTRIB)
DESELECT (DESELECT)
AFI, ADMINISTRATIVE DATA
AFI, ADMINISTRATIVE DATA
(ADMINISTRATIVE DATA)
PUPI
PUPI, ADMINISTRATIVE DATA
(ADMINISTRATIVE DATA)
GET SYSTEM INFORMATION
WRITE SINGLE BLOCK
LOCK BLOCK
READ SINGLE BLOCK
MEMORY AND CONTROL
FUNCTION COMMANDS
READ SINGLE BLOCK WITH
BLOCK SECURITY STATUS
CUSTOM READ BLOCK
WRITE AFI
LOCK AFI
GET UID
64-BIT UID, AFI, CONSTANTS
DATA OF SELECTED MEMORY BLOCK, APPLICABLE PROTECTION CONTROL REGISTER
PROTECTION CONTROL REGISTER
SELECTED MEMORY BLOCK
SELECTED MEMORY BLOCK, APPLICABLE PROTECTION CONTROL REGISTER
SELECTED MEMORY BLOCK, INTEGRITY BYTES
AFI BYTE
AFI-LOCK BYTE
64-BIT UID
Page 5
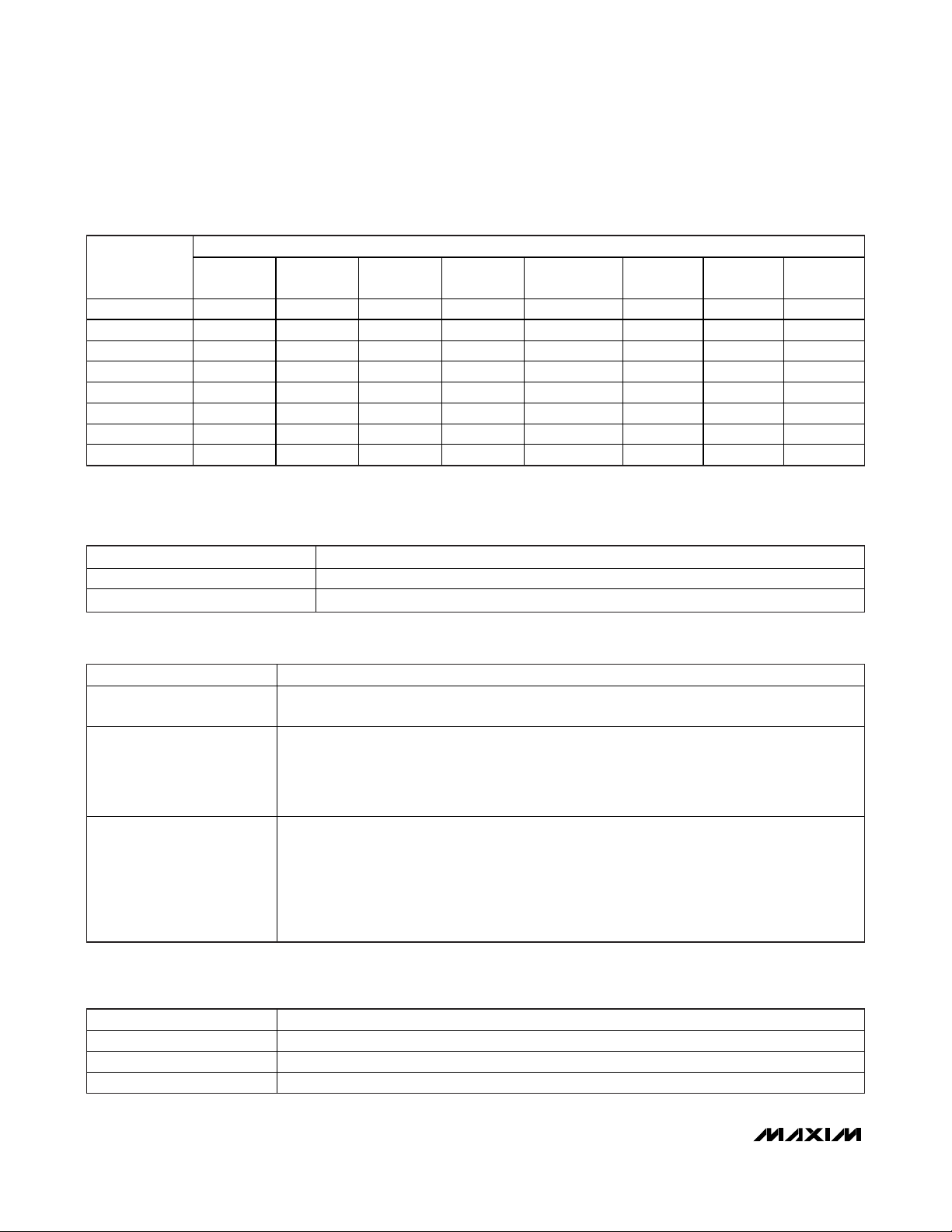
Block 10h provides storage for user-programmable
parameters that are defined by the ISO/IEC 14443 standard. These are application data field and AFI. The
remaining bytes (U1, U2, U3) are not defined by the
communication standard; the application software can
use them, e.g., for proprietary markings. Block 11h contains control bytes that determine the operation of the
individual pages (EPROM-emulation mode, write protection of individual blocks), or to write protect the application data field, the AFI, and U1. The S-Lock byte, if
programmed to a suitable code, only protects itself from
future changes. The self-protection feature can be used
to permanently mark the fob as being “special,” as
defined by the application. Table 1 illustrates the relationship between the controlling register in block 11h
and the memory area affected. Tables 2 and 3 specify
the code assignments to achieve the protection.
Besides the storage for 8 data bytes, each memory
block has 2 integrity bytes, which are not memory
mapped. The integrity bytes function as a MAX66020maintained, 16-bit write-cycle counter. Having
reached its maximum value of 65,535, the write-cycle
counter stops incrementing, but does not prevent
additional write cycles to the memory block. The
integrity bytes can be read through the Custom Read
Block command.
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
_______________________________________________________________________________________ 5
Figure 4. Memory Map
BLOCK
NUMBER
00h Page 0 User EEPROM R/(W) Write-Cycle Counter
01h Page 0 User EEPROM R/(W) Write-Cycle Counter
02h Page 0 User EEPROM R/(W) Write-Cycle Counter
03h Page 0 User EEPROM R/(W) Write-Cycle Counter
04h Page 1 User EEPROM R/(W) Write-Cycle Counter
05h Page 1 User EEPROM R/(W) Write-Cycle Counter
06h Page 1 User EEPROM R/(W) Write-Cycle Counter
07h Page 1 User EEPROM R/(W) Write-Cycle Counter
08h Page 2 User EEPROM R/(W) Write-Cycle Counter
09h Page 2 User EEPROM R/(W) Write-Cycle Counter
0Ah Page 2 User EEPROM R/(W) Write-Cycle Counter
0Bh Page 2 User EEPROM R/(W) Write-Cycle Counter
0Ch Page 3 User EEPROM R/(W) Write-Cycle Counter
0Dh Page 3 User EEPROM R/(W) Write-Cycle Counter
0Eh Page 3 User EEPROM R/(W) Write-Cycle Counter
0Fh Page 3 User EEPROM R/(W) Write-Cycle Counter
10h ISO/IEC 14443 Appl icat ion Data Field AFI U1 U2 U3 Write-Cycle Counter
11h BP1 BP2 BP3 BP4 ADF-Lock AFI-Loc k U1-Lock S-Lock Write-Cycle Counter
(SEQUENCE LEFT TO RIGHT AS WRITTEN TO OR READ FROM DEVICE)
0 1 2 3 4 5 6 7 LSB MSB
DATA BYTE NUMBER
INTEGRITY BYTES
Page 6
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
6 _______________________________________________________________________________________
Table 1. Memory Protection Matrix
Legend (Table 1):
Table 2. BP1 to BP4 Protection Code Assignments
*
If programmed to a locking (protecting) code, the controlling register irreversibly protects itself from further changes. See Tables 2
and 3 for additional details.
Note: Do not program the upper nibble of BP4 to 9 or 5, because this blocks the read access to blocks 0Ch to 0Fh.
Table 3. Protection Code Assignments for ADF-Lock, AFI-Lock, U1-Lock, S-Lock
CONTROLLING
REGISTER*
BP1 E, W — — — — — — —
BP2 — E, W — — — — — —
BP3 — — E, W — — — — —
BP4 — — — E, W — — — —
ADF-Lock — — — — W — — —
AFI-Loc k — — — — — W — —
U1-Lock — — — — — — W —
S-Lock — — — — — — — W
BLOCKS
00h TO 03h
BLOCKS
04h TO 07h
BLOCKS
08h TO 0Bh
AFFECTED MEMORY AREA
BLOCKS
0Ch TO 0Fh
APPLICATION
DATA FIELD
AFI U1 S-LOCK
CODE DESCRIPTION
E ERPOM-Emulation Mode
W Write Protection
CODE DESCRIPTION
00000000b
(00h)
00001010b
(0Ah)
1010<b3><b2><b1><b0>b
(Axh)
Unlocked (factory default)
EPROM-Emulation Mode (irreversible)
BP1: blocks 00h to 03h
BP2: blocks 04h to 07h
BP3: blocks 08h to 0Bh
BP4: bloc ks 0Ch to 0Fh
Write-Protect Block Mode. Once set to Ah, the upper nibble cannot be changed to any other
value (irreversible). The bits of the lower nibble can still be changed only from 0 (unlocked) to 1
(locked) to write protect blocks individually.
b0: block 00h (BP1), block 04h (BP2), block 08h (BP3), block 0Ch (BP4)
b1: block 01h (BP1), block 05h (BP2), block 09h (BP3), block 0Dh (BP4)
b2: block 02h (BP1), block 06h (BP2), block 0Ah (BP3), block 0Eh (BP4)
b3: block 03h (BP1), block 07h (BP2), block 0Bh (BP3), block 0Fh (BP4)
CODE DESCRIPTION
00000000b (00h) Unlocked (factory default)
10101010b (AAh) Locked (irreversible)
All other codes Unlocked
Page 7
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
_______________________________________________________________________________________ 7
ISO/IEC 14443 Type B
Communication Concept
The communication between the master and the
MAX66020 (slave) is based on the exchange of data
packets. The master initiates every transaction; only
one side (master or slaves) transmits information at any
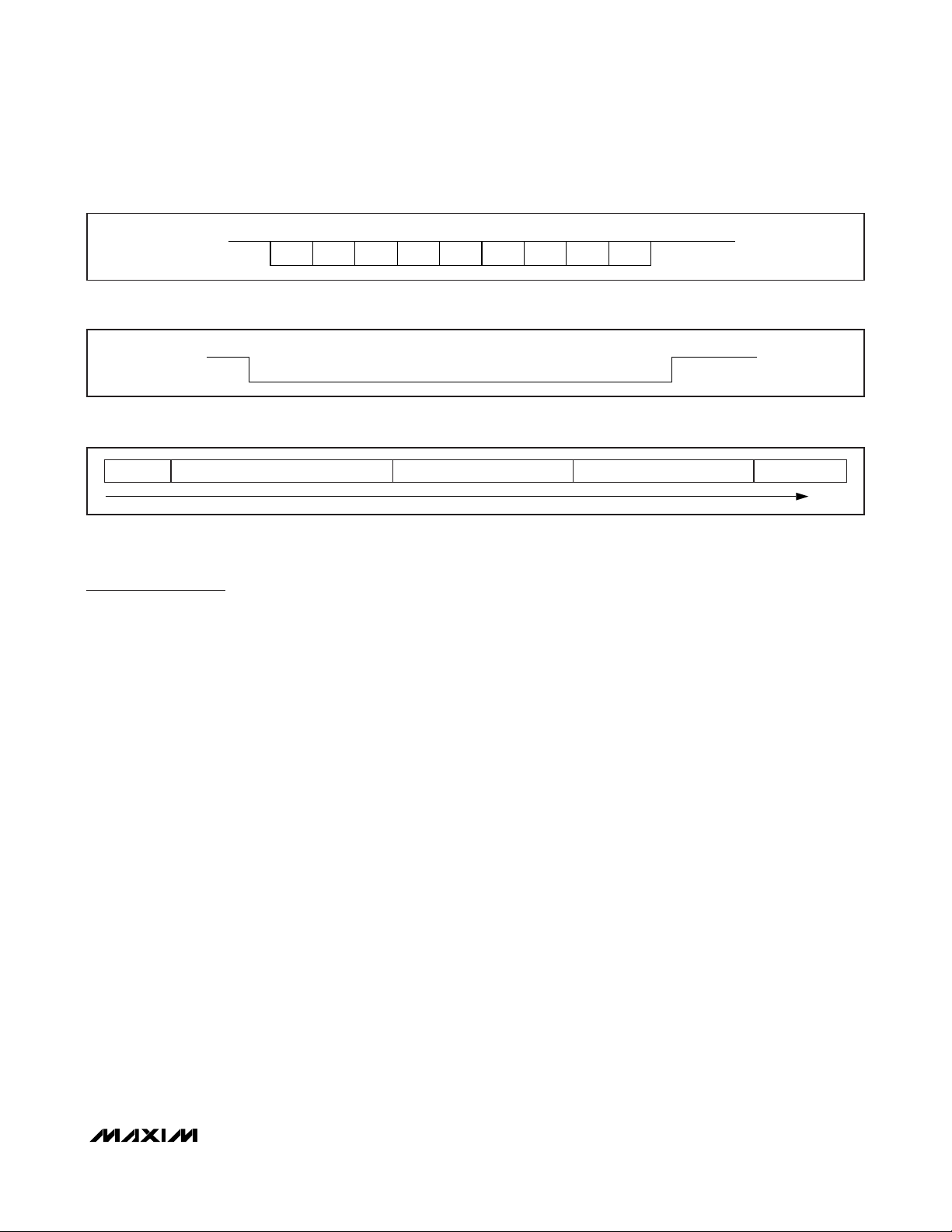
time. Data packets are composed of characters, which
always begin with a START bit and typically end with
one or more STOP bits (Figure 5). The least significant
data bit is transmitted first. Data characters have 8 bits.
Each data packet begins with a start-of-frame (SOF)
character and ends with an end-of-frame (EOF) character. The EOF/SOF characters have 9 all-zero data bits
(Figure 6). The SOF has 2 STOP bits, after which data
characters are transmitted. A data packet with at least
3 bytes between SOF and EOF is called a frame
(Figure 7). The last two data characters of an
ISO/IEC 14443 Type B frame are an inverted 16-bit
CRC of the preceding data characters generated
according to the CRC-16-CCITT polynomial. This CRC
is transmitted with the LSB first. For more details on the
CRC-16-CCITT, refer to ISO/IEC 14443-3, Annex B.
With network function commands, the command code,
parameters, and response are embedded between
SOF and CRC. With memory function commands, command code, and parameters are placed into the information field of I-blocks (see the
Block Types
section),
which in turn are embedded between SOF and EOF.
For transmission, the frame information is modulated on a
carrier frequency, which is 13.56MHz for ISO/IEC 14443 .
The subsequent paragraphs are a concise description
of the required modulation and coding. For full details
including SOF/EOF and subcarrier on/off timing, refer to
ISO/IEC 14443-3, Sections 7.1 and 7.2.
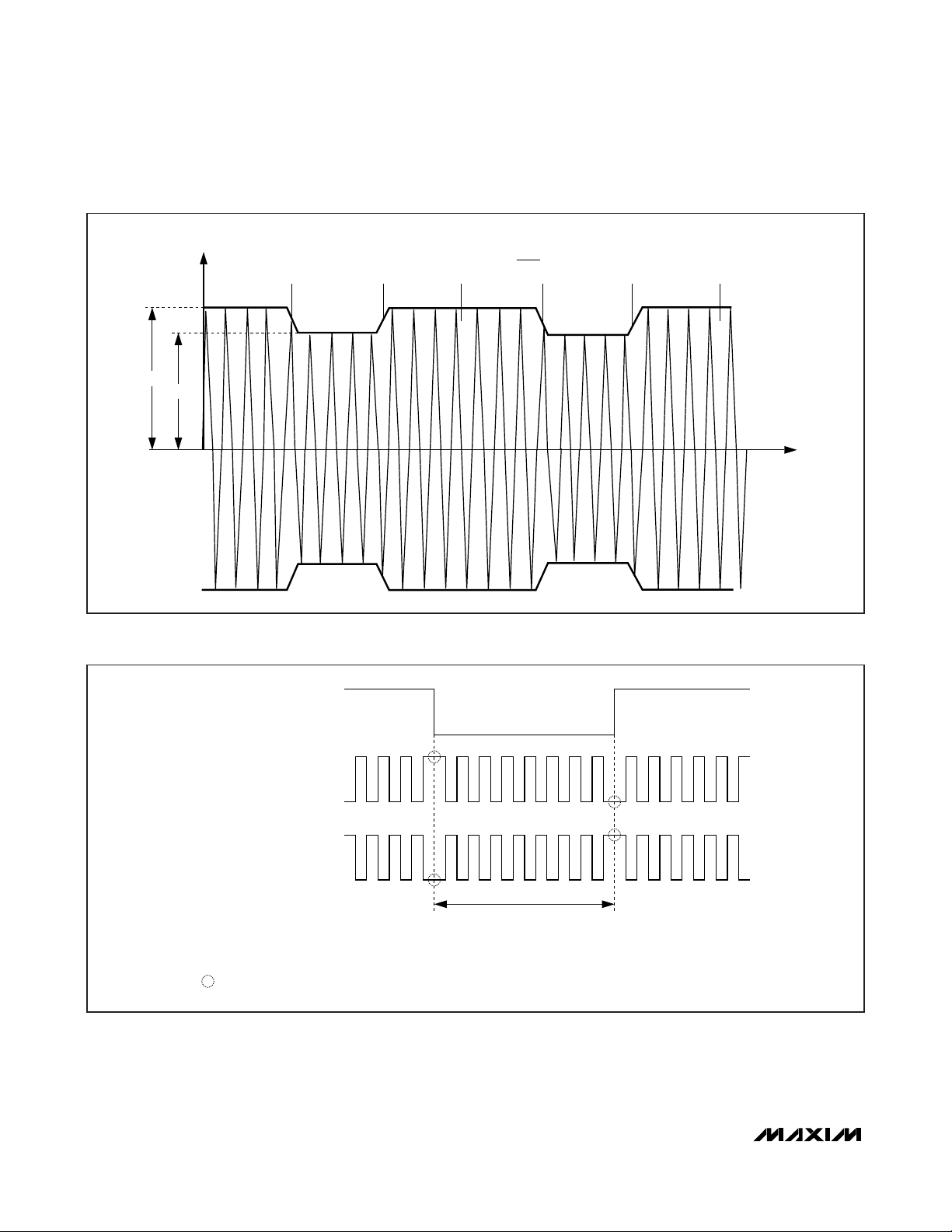
The path from master to slave uses amplitude modula-
tion with a modulation index between 8% and 14%
(Figure 8). In this direction, a START bit and logic 0 bit
correspond to a modulated carrier; STOP bit and
logic 1 bit correspond to the unmodulated carrier. EOF
ends with an unmodulated carrier instead of STOP bits.
The path from slave to master uses an 847.5kHz subcarrier, which is modulated using binary phase-shift key
(BPSK) modulation. Depending on the data rate, the
transmission of a single bit takes eight, four, two, or one
subcarrier cycles. The slave generates the subcarrier
only when needed; i.e., starting shortly before an SOF
and ending shortly after an EOF. The standard defines
the phase of the subcarrier before the SOF as 0° reference, which corresponds to logic 1. The phase of the
subcarrier changes by 180° whenever there is a binary
transition in the character to be transmitted (Figure 9).
The first phase transition represents a change from
logic 1 to logic 0, which coincides with the beginning of
the SOF. The BPSK modulated subcarrier is used to
modulate the load on the fob’s antenna (Figure 10).
START
1
0
BIT 1
BIT 2 BIT 3 BIT 4 BIT 5 BIT 6 BIT 7 BIT 8
LSb MSb
STOP
Figure 5. ISO/IEC 14443 Data Character Format
START
1
0
BIT 1 BIT 2 BIT 3 BIT 4 BIT 5 BIT 6 BIT 7 BIT 9
STOP/IDLE
BIT 8
Figure 6. ISO/IEC 14443 SOF/EOF Character Format
SOF ONE OR MORE DATA CHARACTERS
CRC (LSB) CRC (MSB) EOF
TIME
Figure 7. ISO/IEC 14443 Frame Format
Page 8
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
8 _______________________________________________________________________________________
Figure 9. Uplink: BPSK Modulation of the 847.5kHz Subcarrier
A
B
CARRIER AMPLITUDE
t
11 1100
MODULATION INDEX M = = 0.08 TO 0.14
A - B
A + B
Figure 8. Downlink: 8% to 14% Amplitude Modulation
DATA TO BE TRANSMITTED
847kHz SUBCARRIER
BPSK MODULATION
INDICATES 180° PHASE CHANGE (POLARITY REVERSAL)
OR
CAN BE REDUCED TO FOUR, TWO, OR ONE SUBCARRIER CYCLES FOR COMMUNICATION IN THE ACTIVE STATE.
110
TRANSMISSION OF A SINGLE BIT
POWER-UP DEFAULT = EIGHT CYCLES OF 847kHz (9.44μs)
Page 9

ISO/IEC 14443 Block
Transmission Protocol
Before the master can send a data packet to access the
memory, the MAX66020 must be in the ACTIVE state.
The protocol to put the MAX66020 into the ACTIVE state
is explained in the
Network Function Commands
section. While in the ACTIVE state, the communication
between the master and the MAX66020 follows the
block transmission protocol as specified in Section 7 of
ISO/IEC 14443-4. Such a block (Figure 11) consists of
three parts: the prologue field, the information field, and
the epilogue field. The prologue can contain up to 3
bytes, called the protocol control byte (PCB), card identifier (CID), and the node address (NAD). Epilogue is
another name for the 16-bit CRC that precedes the EOF.
The information field is the general location for data.
Block Types
The standard defines three types of blocks: I-block,
R-block, and S-block. Figures 12, 13, and 14 show the
applicable PCB bit assignments.
The I-block is the main tool to access the memory. For
I-blocks, bit 2 must be 1 and bit 6, bit 7, and bit 8 must
be 0. Bit 5, marked as CH, is used to indicate chaining,
a function that is not used or supported by the
MAX66020. Therefore, bit 5 must always be 0. Bit 4,
marked as CID, is used by the master to indicate
whether the prologue field contains a CID byte. The
MAX66020 processes blocks with and without CID as
defined in the standard. The master must include the
CID byte if bit 4 is 1. Bit 3, marked as NAD, is used to
indicate whether the prologue field contains an NAD
byte, a feature not supported by the MAX66020.
Therefore, bit 3 must always be 0. Bit 1, marked as #, is
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
_______________________________________________________________________________________ 9
Figure 10. Uplink: Load Modulation of the RF Field by the BPSK Modulated Subcarrier
PROLOGUE FIELD INFORMATION FIELD EPILOGUE FIELD
PCB CID NAD (DATA)
CRC
(LSB)
CRC
(MSB)
1 BYTE 1 BYTE 1 BYTE 0 OR MORE BYTES 1 BYTE 1 BYTE
Figure 11. ISO/IEC 14443-4 Type B Block Format
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
MSb LSb
0 0 0 CH CID NAD 1 #
Figure 12. Bit Assignments for I-Block PCB
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
MSb LSb
1 0 1 AN CID 0 1 #
Figure 13. Bit Assignments for R-Block PCB
DATA*
*DEPENDING ON THE INITIAL PHASE, THE DATA POLARITY MAY BE INVERSE.
10 1
TRANSMISSION OF A SINGLE BIT
SHOWN AS EIGHT CYCLES OF THE 847kHz SUBCARRIER
Page 10

MAX66020
the block number field. The block number is used to
ensure that the response received relates to the
request sent. This function is important in the error handling, which is illustrated in Annex B of ISO/IEC 14443-
4. The rules that govern the numbering and handling of
blocks are found in Sections 7.5.3 and 7.5.4 of
ISO/IEC 14443-4. The MAX66020 ignores I-blocks that
have bit 5 or bit 3 set to 1.
For R-blocks, the states of bit 2, bit 3, bit 6, bit 7, and
bit 8 are fixed and must be transmitted as shown in
Figure 13. The function of bit 1 (block number) and bit 4
(CID indicator) is the same as for I-blocks. Bit 5,
marked as AN, is used to acknowledge (if transmitted
as 0) or not to acknowledge (if transmitted as 1) the
reception of the last frame for recovery from certain
error conditions. The MAX66020 fully supports the function of the R-block as defined in the standard. For
details and the applicable rules, refer to Sections 7.5.3
and 7.5.4 and Annex B of ISO/IEC 14443-4.
For S-blocks, the states of bit 1, bit 2, bit 3, and bit 7
and bit 8 are fixed and must be transmitted as shown in
Figure 14. The function of bit 4 (CID indicator) is the
same as for I-blocks. Bit 5 and bit 6, when 00b, specify
whether the S-block represents a deselect command. If
bit 5 and bit 6 are 11b, the S-block represents a framewaiting time extension (WTX) request, a feature to tell
the master that the response is going to take longer than
specified by the frame-waiting time (FWT) (see the
ATQB Response
section). However, the MAX66020
does not use this feature and consequently, the only use
of the S-block is to transition the device from the ACTIVE
state to the HALT state using the DESELECT command
(see the
Network Function Commands
section).
Card Identifier
Figure 15 shows the bit assignment within the card
identifier byte. The purpose of bits 4 to 1 is to select
one of multiple slave devices that the master has elevated to the ACTIVE state. The CID is assigned to a
slave through Param 4 of the ATTRIB command (see
the
Network Function Commands
section). While in
ACTIVE state, a compliant slave only processes blocks
that contain a matching CID and blocks without CID if
the assigned CID is all zeros. If the master includes a
CID, then the slave’s response also includes a CID
byte. Blocks with a nonmatching CIDs are ignored.
According to the standard, the slave can use bits 8 and
7 to inform the master whether power-level indication is
supported, and, if yes, whether sufficient power is available for full functionality. Since the MAX66020 does not
support power-level indication, the power-level bits are
always 00b. When the master transmits a CID byte, the
power-level bits must be 00b.
Information Field
Since the MAX66020 does not generate WTX requests,
the information field (Figure 11) is found only with
I-blocks. The length of the information field is calculated
by counting the number of bytes of the whole block
minus length of prologue and epilogue field. The
ISO/IEC 14443 standard does not define any rules for
the contents of the information field. The MAX66020
assumes that the first byte it receives in the information
field is a command code followed by 0 or more command-specific parameters. When responding to an
I-block, the first byte of the information field indicates
success (code 00h) followed by command-specific
data or failure (code 01h) followed by one error code.
Memory and Control
Function Commands
The commands described in this section are transmitted using the block transmission protocol. The data of a
block (from prologue to epilogue) is embedded
between SOF and EOF, as shown in Figure 16. The CID
field (shaded) is optional. If the request contains a CID,
the response also contains a CID.
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
10 ______________________________________________________________________________________
Figure 14. Bit Assignments for S-Block PCB
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
MSb LSb
0 0 00
(POWER LEVEL) (FIXED) CARD IDENTIFIER VALUE
Figure 15. Bit Assignments for CID Byte in I-Blocks
PCB CIDSOF INFORMATION FIELD CRC (MSB)CRC (LSB) EOF
Figure 16. Frame Format for Block Transmission Protocol
MSb LSb
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
1 1 CID 0 1 0
Page 11

The command descriptions in this section only show
the information field of the I-blocks used to transmit
requests and responses. Since the MAX66020 neither
supports chaining nor generates WTX requests, when it
receives an I-block, the MAX66020 responds with an
I-block. The block number in the I-block response is the
same as in the I-block request.
Error Indication
Depending on the complexity of a function, various
error conditions can occur. In case of an error, the
response to a request begins with a 01h byte followed
by one error code.
Table 4 shows a matrix of commands and potential
errors. If there was no error, the information field of
the response begins with 00h followed by command-
specific data, as specified in the detailed command
description.
If the MAX66020 does not recognize a command, it
does not generate a response.
Detailed Command Descriptions
Get System Information
This command allows the master to retrieve technical
information about the MAX66020. In the response, the
least significant UID byte is transmitted first. The
response is adapted from ISO 15693-3, Section 10. The
IC reference code indicates the die revision in hexadecimal format, such as A1h, A2h, B1h, etc. To receive
the system information, issue a request with the command code 2Bh in the request information field.
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 11
Table 4. Error Code Matrix
Response Information Field for the Get System Information Command (No Error)
ERROR DESCRIPTION
Invalid block number 10h
Already loc ked 11h
Write access failed because block is locked 12h
ERROR
CODE
Write Single Block
Get System Information
FAILING COMMANDS
Lock Block
Read Single Block
Block Security Status
Read Single Block with
Custom Read Block
Get UID
Write AFI
Lock AFI
INDICATOR
00h 0Fh (8 B ytes) (1 Byte) (1 B yte) 12h 07h (1 Byte)
INFO
FLAGS
UID U1 AFI
NUMBER OF
BLOCKS
MEMORY BLOCK
SIZE
IC REFERENCE
Page 12

Write Single Block
The normal way to write data to the device is through
Write Single Block. This command uses one commandspecific parameter, which is the memory block number.
Valid block numbers are 00h to 11h. Writing a block
takes t
PROG
. If this command is processed without any
error, the response information field consists of an indicator byte with the code 00h. The response is transmitted after the memory is updated.
Depending on the protection settings of the memory
location to be updated, the MAX66020 manipulates
data as it arrives in a buffer. Upon receiving a Write
Single Block command for a write-protected location,
e.g., a self-locking nibble or byte in memory block 11h,
the buffer is loaded with the data already in memory,
rather than the data transmitted in the request.
Similarly, if the target memory block is in EPROM mode,
the buffer is loaded with the bitwise logical AND of the
transmitted data and data already in memory. In all
other cases, the data sent by the master arrives in the
buffer unaltered.
Lock Block
This command permanently locks (write protects) the
selected block and reports the success of the operation
in the response. Locking a block takes t
PROG
. If this
command is processed without any error, the response
information field consists of an indicator byte with the
code 00h. The response is transmitted after the protection byte is updated. The block protection can alternatively be achieved by directly writing to memory block
11. Before using the Lock Block command, the final
block data should be defined and written to the device.
Read Single Block
This command allows for retrieving the data of a single
memory block. This command uses one command-specific parameter, which is the memory block number.
Valid block numbers are 00h to 11h.
MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
12 ______________________________________________________________________________________
Request Information Field for the Write Single Block Command
Request Information Field for the Lock Block Command
Request Information Field for the Read Single Block Command
Response Information Field for the Read Single Block Command (No Error)
COMMAND BLOCK NUMBER NEW BLOCK DATA
21h (1 Byte) (8 Bytes)
Command Block Number
22h (1 Byte)
COMMAND BLOCK NUMBER
INDICATOR MEMORY DATA
20h (1 Byte)
00h (8 Bytes)
Page 13

MAX66020
Read Single Block with Block
Security Status
This command allows for retrieving the security status
of a memory block followed by the memory block’s
data. This command uses one command-specific parameter, which is the memory block number. Valid block
numbers are 00h to 11h.
Custom Read Block
This command allows for retrieving the data of a single
block, followed by the block’s integrity bytes. This command uses one command-specific parameter, which is
the memory block number. Valid block numbers are
00h to 11h.
Request Information Field for the Read Single Block with Block Security Status Command
Response Information Field for the Read Single Block with Block Security
Status Command (No Error)
Request Information Field for the Custom Read Block Command
Response Information Field for the Custom Read Block Command (No Error)
00h = The memory block is not protected.
01h = The memory block is write protected.
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 13
COMMAND BLOCK NUMBER
B0h (1 Byte)
INDICATOR
00h (1 Byte) (8 Bytes)
SECURITY STATUS
(SEE CODES BELOW)
MEMORY DATA
COMMAND BLOCK NUMBER
A4h (1 Byte)
INDICATOR MEMORY DATA INTEGRITY BYTES
00h (8 Bytes) (2 Bytes)
Page 14

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
14 ______________________________________________________________________________________
Write AFI
This command writes the AFI byte and reports the success of the operation in the response. The AFI byte can
alternatively be defined by writing to the proper location in memory block 10h using the Write Single Block
command. If this command is processed without any
error, the response information field consists of an indicator byte with the code 00h.
Lock AFI
This command permanently locks (write protects) the
AFI byte and reports the success of the operation in the
response. Before using the Lock AFI command, the AFI
byte should be written to the device using the Write AFI
command. The AFI byte can alternatively be locked by
writing the AFI-Lock byte in memory block 11h to AAh,
using the Write Single Block command. To lock the AFI,
issue a request with the command code 28h in the
request information field. If this command is processed
without any error, the response information field consists of an indicator byte with the code 00h.
Get UID
This command allows the master to retrieve the
device’s unique identification number, UID. In the
response, the least significant UID byte is transmitted
first. To read the UID, issue a request with the command code 30h in the request information field.
ISO/IEC 14443-3 Type B Initialization
and Anticollision Protocol
Before an ISO/IEC 14443-compliant RF device gives
access to its memory, a communication path between
the master and the RF device must be established.
Initially, the master has no information whether there
are any RF devices in the field of its antenna. To find
out whether there are one or more RF devices compliant to a known standard in the field, the master uses a
standard-specific initialization and anticollision protocol. The ISO/IEC 14443 Type B protocol defines six
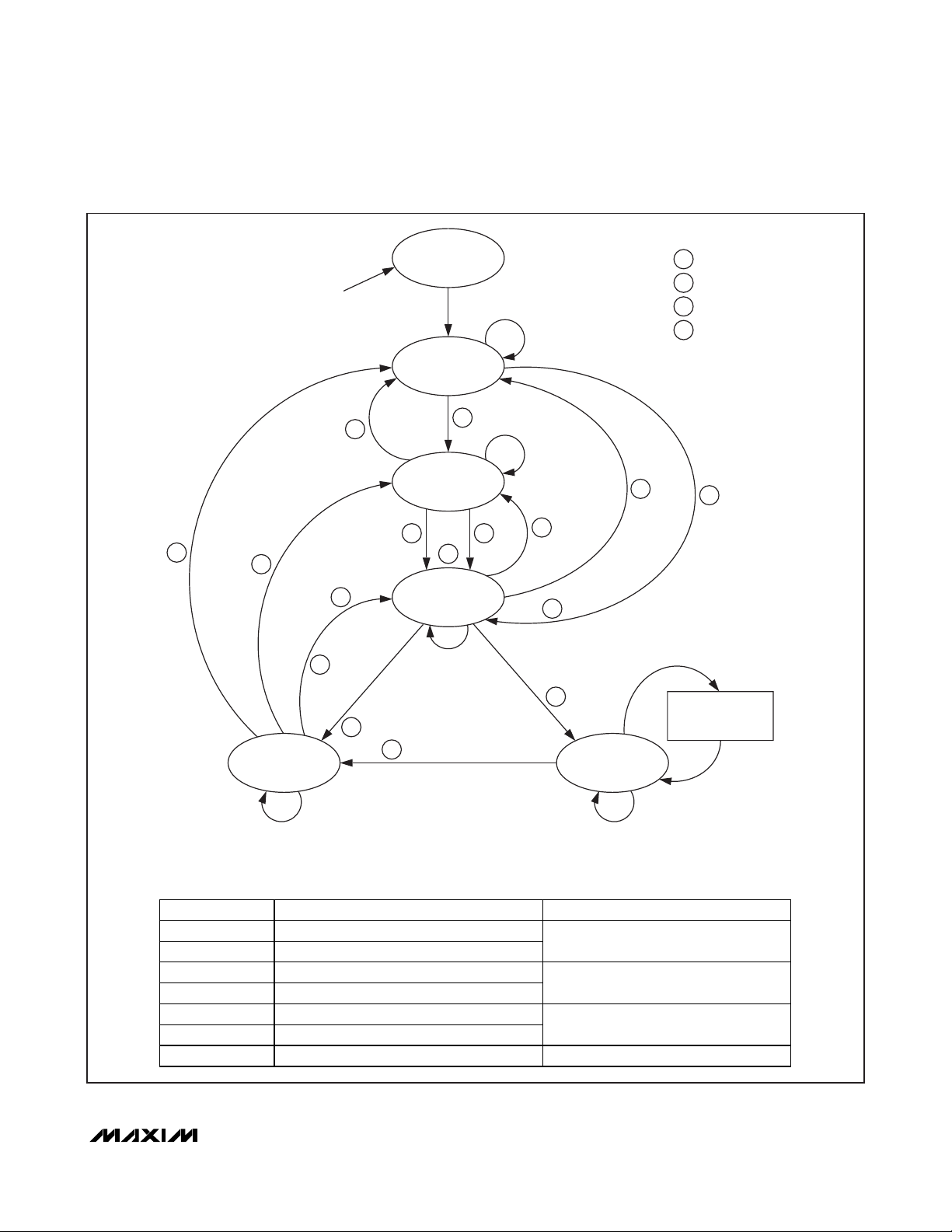
states: POWER-OFF, IDLE, WAITING FOR SLOTMARKER, READY, HALT, and ACTIVE. Figure 17
shows these states and the conditions under which a
slave transitions between states. For most cases, letters surrounded by small circles reference the condition under which a transition occurs. The conditions
are explained in the legend to Figure 17. Table 5
explains terms that are used in the anticollision protocol and in the network function command description.
Request Information Field for the Write AFI Command
Response Information Field for the Get UID Command (No Error)
COMMAND AFI VALUE
27h (1 Byte)
INDICATOR UID
00h (8 Bytes)
Page 15
MAX66020
Figure 17. ISO/IEC 14443 Type B State Transitions Diagram
NAME DE SCRIPTION RESULT
A (AFI MISMATCH) REQB/WUPB WITH NONMATCHING AFI
a WUPB WITH NONMATCHING AFI
RETURN TO IDLE
B (BYPASS SM) REQB/WUPB WITH MATCHING AFI AND [(N = 1) OR [R = 1)]
b WUPB WITH MATCHING AFI AND [(N = 1) OR [R = 1)]
TRANSITION DIRECTLY TO READY
S (SLOT-MARKER) REQB/WUPB WITH MATCHING AFI AND (N 1) AND (R 1)
s WUPB WITH MATCHING AFI AND (N 1) AND (R 1)
WAIT FOR MATCHING SLOT NUMBER
MS (MATCHING SLOT) SLOT-MARKER COMMAND WITH SLOT NUMBER = R TRANSITION TO READY WITH MATCHING SLOT-MARKER
CONDITIONS LEGEND:
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 15
RESPONSE LEGEND:
POWER-OFF
OUT OF FIELD
(FROM ANY STATE)
A
a
s
1
b
3
COMMAND OR CASE
HLTB WITH
MATCHING PUPI
4
(SPECIAL CASE OF A BLOCK TRANSMISSION
IN FIELD
IDLE
S
WAITING FOR
SLOT-MARKER*
BMS
1
READY
ANY OTHER
DESELECT
PROTOCOL FUNCTION)
ANY OTHER
COMMAND
OR CASE
ANY OTHER
COMMAND
OR CASE
A
S
1
ATTRIB WITH
MATCHING PUPI
2
ACTIVEHALT
ATQB RESPONSE1
ATTRIB RESPONSE2
HLTB RESPONSE3
DESELECT RESPONSE4
B
EXECUTIVE BLOCK
TRANSMISSION
PROTOCOL FUNCTION
ANY OTHER COMMAND
*WHEN ENTERING “WAITING FOR SLOT-MARKER,” EACH TAG SELECTS A RANDOM NUMBER R IN THE RANGE OF 1 TO “NUMBER OF SLOTS.”
ANY OTHER COMMAND
Page 16

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
16 ______________________________________________________________________________________
Table 5. ISO/IEC 14443 Type B Technical Terms
TERM DESCRIPTION
ACTIVE One of the sla ve ’s six states. In this state, the memory and control function commands and dese lect apply.
ADC Applicat ion Data Coding. 2-Bit field of the 3rd protocol info byte of the ATQB response.
AFI Application Family Identifier. 1-Byte field used in the REQB/WUPB request to preselect slaves.
ATQB An swer to Request, Type B. Respon se to REQB, WUPB, and SLOT-MARKER command.
ATTRIB Slave Selection Command, Type B. Used to transition a slave from READY to the ACTIVE state.
BPSK Binary Phase-Shift Keying Modulation
CID
EOF End of Frame
DESELECT Slave Deselection Command. Transitions the slave from the ACTIVE state to the HALT state.
fc Carrier Frequency = 13.56MHz
FO Frame Option. 2-Bit field of the 3rd protocol info byte of the ATQB response.
fs Subcarrier Frequency = fc/16 = 847.5kHz
FWI Frame-Waiting Time Integer. 4-bit field of the 3rd protocol info byte of the ATQB response.
FWT Frame-Waiting Time. Calculated from FWI.
HALT One of the slave’s six states. The master puts a slave in this state to park it.
HLTB Halt Command, T ype B
IDLE One of the slave’s six states. In this state, the slave has power and is waiting for action.
INF Information Field for Higher Layer Protocol (per ISO/IEC 14443-4)
MBLI
N Number of Anticollision Slots (or response probability per slot)
NAD Node Address (per ISO/IEC 14443-4)
POWER-OFF One of the slave’s six states. In this state, the slave has no power and consequently cannot do anything.
PUPI Pseudo Unique Identifier. 4-Byte field of the ATQB response.
R 4-Bit Random Number Chosen by a Sla ve When Processing the REQB or WUPB Command
READY
REQB Request Command, Type B. Used to probe the RF field for the presence of slave devices.
RF Radio Frequency
S Slot Number. 4-Bit field sent to slave with SLOT-MARKER command.
SLOT-MARKER Command used in the time-slot approach to identif y slaves in the RF field
SOF Start of Frame
TR0 Guard Time per ISO/IEC 14443-2
TR1 Synchronization Time per ISO/IEC 14443-2
WAITING FOR
SLOT-MAR KER
WUPB Wake-Up Command, Type B. Similar to REQB, required to wake up s laves in the HALT state.
Card Identifier. 4-Bit temporary identification number as signed to a slave through the ATTRIB command, used
in conjunction with the block transmission protocol.
Max imum Buffer Length Index of Slave (per ISO/IEC 14443-4). 4-Bit field of the first protocol info byte of the
ATQB response.
One of the slave’s six states; official name is READY-DECLARED SUBSTATE. In this state, the slave has
identified itself and is waiting for transition to ACTIVE (memory and control functions) or HALT (parking).
One of the slave’s six states; official name is READY-REQUESTED SUBSTATE. In this state, the slave is
waiting to be called by its random number R to transit ion to READY.
Page 17

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 17
ISO/IEC 14443 Type B States and
Transitions
POWER-OFF State
This state applies if the slave is outside the master’s RF
field. A slave transitions to the POWER-OFF state when
leaving the power-delivering RF field. When entering
the RF field, the slave automatically transitions to the
IDLE state.
IDLE State
The purpose of the IDLE state is to have the slave population ready to participate in the anticollision protocol.
When transitioning to the IDLE state, the slave does not
generate any response. To maintain this state, the slave
must continuously receive sufficient power from the
master’s RF field to prevent transitioning into the
POWER-OFF state. While in the IDLE state, the slave listens to the commands that the master sends, but reacts
only on the REQB and WUPB commands, provided that
they include a matching AFI value. If the master sends
a command with a nonmatching AFI byte (conditions A
and a), a transition to IDLE is also possible from the
HALT state, the READY state, and the WAITING FOR
SLOT-MARKER state. From IDLE, a slave can transition
to the higher states READY (condition B) or WAITING
FOR SLOT-MARKER (condition S). For details, see the
REQB/WUPB
command description in the
Network
Function Commands
section.
WAITING FOR SLOT-MARKER State
(READY REQUESTED SUBSTATE)
The WAITING FOR SLOT-MARKER state is used in the
time-slot anticollision approach. A slave can transition
to WAITING FOR SLOT-MARKER from the IDLE, HALT,
or READY state upon receiving a REQB or WUPB command with a matching AFI (conditions S and s), provided that both the number of slots specified in the
REQB/WUPB command and the random number that
the slave has chosen are different from 1. To maintain
this state, the slave must continuously receive sufficient
power from the master’s RF field to prevent transitioning
into the POWER-OFF state. A slave in the WAITING
FOR SLOT-MARKER state listens to the commands that
the master sends, but reacts only on the REQB, WUPB,
and SLOT-MARKER commands. From WAITING FOR
SLOT-MARKER, a slave can transition to the higher
state READY under condition B (bypassing the SlotMARKER), or MS (matching slot, SLOT-MARKER command with a slot number that matches the random
number R). Condition A (AFI mismatch) returns the
slave to the IDLE state.
READY State (READY DECLARED SUBSTATE)
The READY state applies to a slave that has met the criteria in the anticollision protocol to send an ATQB
response. A slave can transition to READY from IDLE or
HALT (conditions B and b) or from WAITING FOR
SLOT-MARKER (conditions B and MS). When transitioning to the READY state, the slave transmits an ATQB
response. To maintain this state, the slave must continuously receive sufficient power from the master’s RF
field to prevent transitioning into the POWER-OFF state.
A slave in the READY state listens to the commands
that the master sends, but reacts only on the REQB,
WUPB, ATTRIB and HLTB commands. From READY, a
slave can transition to ACTIVE (ATTRIB command with
matching PUPI), HALT (HLTB command with matching
PUPI), or IDLE (condition A).
HALT State
The HALT state is used to silence slaves that have
been identified and shall no longer participate in the
anticollion protocol. This state is also used to park
slaves after communication in the ACTIVE state was
completed. A slave transitions to the HALT state either
from READY (HLTB command with matching PUPI) or
from ACTIVE (DESELECT command with matching
CID). When transitioning to the HALT state, the slave
transmits a response that confirms the transition. To
maintain this state, the slave must continuously receive
sufficient power from the master’s RF field to prevent
transitioning into the POWER-OFF state. The normal
way out of the HALT state is through the WUPB command. From HALT, a slave can transition to IDLE (condition a), READY (condition b), or WAITING FOR
SLOT-MARKER (condition s).
ACTIVE State
The ACTIVE state enables the slave to process commands sent through the block transmission protocol.
When entering the ACTIVE state, the slave confirms the
transition with a response. The only way for a slave to
transition to the ACTIVE state is from the READY state
(ATTRIB command with a matching PUPI). In the
ATTRIB command, the master assigns a 4-bit CID that
is used to address one of multiple slaves that could all
be in the ACTIVE state. To maintain this state, the slave
must continuously receive sufficient power from the
master’s RF field to prevent transitioning into the
POWER-OFF state. The normal way out of the ACTIVE
state is through the DESELECT command, which transitions the slave to the HALT state.
Page 18

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
18 ______________________________________________________________________________________
Network Function Commands
To transition slaves devices between states, the
ISO/IEC 14443 Type B standard defines six network
function commands, called REQB, WUPB, SLOTMARKER, HLTB, ATTRIB, and DESELECT. The master
issues the commands in the form of request frames and
the slaves respond by transmitting response frames.
With network function commands, command code,
parameters and response are embedded between SOF
and CRC. This section describes the format of the
response and request frames and the coding of the
data fields inside the frames as detailed as necessary
to operate the MAX66020. Not all of the fields and
cases that the standard defines are relevant for the
MAX66020. For a full description of those fields refer to
the ISO/IEC 14443-3, Section 7.
REQB/WUPB Command
The REQUEST command, Type B (REQB) and the
WAKEUP command, Type B (WUPB) are the general
tools for the master to probe the RF field for the presence
of slave devices and to preselect them for action based
on the value of the application family identifier (AFI). An
ISO/IEC 14443 Type B-compliant slave watches for these
commands while in the IDLE state, WAITING FOR SLOTMARKER state, and READY state. In the HALT state, the
slave only acts upon receiving a WUPB command. The
REQB or WUPB command is transmitted as a frame, as
shown in Figure 18. Besides the command code, the
request includes two parameters, AFI and PARAM. The
response to REQB/WUPB is named ATQB. See the
ATQB Response
section for details.
The ISO/IEC 14443 standard defines rules for the
assignment of the AFI codes and the behavior of the
slaves when receiving a REQB/WUPB request. If the
request specifies an AFI of 00h, a slave must process
the command regardless of its actual AFI value. If the
least significant nibble of the AFI in the request is
0000b, the slave must process the command only if the
most significant nibble of the AFI sent by the master
matches the most significant nibble of the slave’s AFI.
For all other AFI values, the slave processes the command only if the AFI in the request and the slave match.
The AFI code can be programmed and locked by the
user. For details see the
Memory and Control Function
Commands
section.
The bit assignments of the PARAM byte are shown in
Figure 19. Bits 5 to 8 are reserved and must be transmitted as 0. Bit 4, if 0, indicates that the request is a
REQB command; bit 4, if 1, defines a WUPB command.
Bits 1, 2, and 3 specify the number of slots (N) to be
used in the anticollision protocol. Table 6 shows the
codes. In the case of N = 1, the SLOT-MARKER command does not apply and all slaves with a matching AFI
transition to the READY state. With multiple slaves in the
field, this leads to a data collision, since the response
frames are transmitted simultaneously. If N is larger than
1, each slave in the field selects its own 4-bit random
number, R, in the range of 1 to N. A slave that happens
COMMANDSOF AFI CRCPARAM EOF
05h (1 BYTE) (2 BYTES)(1 BYTE)
Figure 18. REQB/WUPB Request Frame
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4
REQB/
WUPB
BIT 3 BIT 2 BIT 1
MSb LSb
0 0 00
(FIXED) N
Figure 19. Bit Assignments for PARAM Byte
Table 6. Number of Slots Codes
BIT 3 BIT 2 BIT 1 N
0 0 0 1
0 0 1 2
0 1 0 4
0 1 1 8
1 0 0 16
1 0 1 (RESERVED)
1 1 X (RESERVED)
Page 19

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 19
to choose R = 1 responds to the REQB/WUPB request.
The larger N is the lower the probability of colliding
response frames; however, if N is 16 and there is only a
single slave in the field, it can take up to 15 SLOTMARKER commands to get a response. The method to
identify all slaves in the field relying solely on the random number R and the REQB/WUPB command is
called the “probabilistic approach.” For mode information about the anticollision process, see the
Anticollision
Examples
section.
SLOT-MARKER Command
Instead of relying on the fact that a participating slave
chooses a new random number for every REQB/WUPB
command, in the “time-slot approach” the master calls
the slaves by their random number R using the SLOTMARKER command. Before this can be done, the master must have issued the REQB/WUPB command with a
number of slots (N) value greater than 1. The master
can send up to (N - 1) SLOT-MARKER commands.
Figure 20 shows the format of the SLOT-MARKER
request frame. The AFI field is not needed since the
slaves have already been preselected through the preceding REQB/WUPB request. The response to the
SLOT-MARKER command is called ATQB. See the
ATQB Response
section for details.
The bits marked as “nnnn” specify the slot number as
defined in the Table 7. Any sequence of the allowable
slot numbers is permitted.
ATQB Response
The response for both the REQB/WUPB and the SLOTMARKER command is called ATQB, which stands for
“answer to request, Type B.” Figure 21 shows the format of the ATQB response. The PUPI field (pseudounique identifier) is used by the master to address a
slave for transitioning to the ACTIVE or HALT state. The
data reported as PUPI is the least significant 4 bytes of
the 64-bit UID. The application data field reports userdefined data that is relevant for distinguishing otherwise
equal slaves in the RF field. Application data is the first
4 bytes of memory block 10h. By default, the application data field is factory programmed to reflect the most
significant 4 bytes of the 64-bit UID. This allows the
master to obtain the full 64-bit UID in the first response
from the slave. However, since this field is not factory
locked, it may be written to any value.
The protocol info field provides the master with administrative information, such as data rate, frame size,
ISO/IEC 14443-4 compliance, frame waiting time, and
whether the slave supports CID and NAD in the
ISO/IEC 14443-4 block transmission protocol. Figure 22
COMMANDSOF CRC EOF
nnnn0101b (2 BYTES)
Figure 20. SLOT-MARKER Request Frame
INDICATORSOF CRC EOF
50h
APPLICATION DATA
(4 BYTES) (2 BYTES)
PROTOCOL INFO
(3 BYTES)
PUPI
(4 BYTES)
Figure 21. ATQB Response Frame
Table 7. Slot Numbering
BIT 8 BIT 7 BIT 6 BIT 5 SLOT NUMBER
0 0 0 1 2
0 0 1 0 3
0 0 1 1 4
… … … … …
1 1 1 0 15
1 1 1 1 16
Page 20

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
20 ______________________________________________________________________________________
shows where this information is located in the protocol
info field and what the values are.
The bit-rate capability of the MAX66020 ranges from
105.9kbps to 847.5kbps in both directions (request and
response); request and response bit rate need not be
the same. The maximum frame size (upper nibble of the
2nd byte) of any request/response specifies 24 bytes.
The largest frame that occurs with the MAX66020 is 19
bytes (Get System Information response). The protocol
type (lower nibble of the 2nd byte) specifies that the
MAX66020 supports the ISO/IEC 14443-4 block transmission protocol. The FWI code 0110b specifies a
frame waiting time of 19.3ms. Note that a slave may
respond long before the maximum frame waiting time is
expired. The ADC code 00b specifies that the
MAX66020 uses proprietary coding for the application
data field. The FO code 01b implies that the MAX66020
supports CID, but does not support the NAD field in the
ISO/IEC 14443-4 block transmission protocol.
HLTB Command
The HLTB command is the only network function command to silence a slave by parking it in the HALT state.
If, based on the ATQB response, the master does not
want to further communicate with the slave, the master
issues the HLTB command. Figures 23 and 24 show
the format of the HLTB request frame and the corresponding response frame. The data to be used in the
PUPI field must match the PUPI information that the
slave has transmitted in the ATQB response. While in
the HALT state, the slave only responds to the WUPB
request.
ATTRIB Command
The ATTRIB command is the only way to select a slave
and make it process commands that are transmitted
according to the ISO/IEC 14443 block transmission protocol. If, based on the ATQB response, the master
wants to communicate with the slave, the master must
put the slave into the ACTIVE state using the slave
selection command ATTRIB. The normal way for the
master to move a slave out of the ACTIVE state is by
sending a DESELECT command, which uses an
S-block to convey a network function command.
Figure 25 shows the format of the ATTRIB request
frame. The data to be used in the PUPI field must
match the PUPI information that the slave has transmitted in the ATQB response. Param 1 tells the slave how
much time the master needs to switch from transmit to
receive (TR0), how much time the master needs to synchronize to the slave’s subcarrier (TR1), and whether
the master is capable of receiving response frames
without SOF and/or EOF.
The MAX66020 ignores the data of Param 1. To ease
requirements for ISO/IEC 14443 Type B readers, the
MAX66020 has TR0 and TR1 fixed at 128/fs (151µs; fs
is the subcarrier frequency of 847.5kHz) and always
begins and ends its responses with SOF and EOF,
respectively.
1ST BYTE 2ND BYTE
3RD BYTE,
UPPER NIBBLE
3RD BYTE,
BIT 4, BIT 3
3RD BYTE,
BIT 2, BIT 1
BIT RATE CAB ILI TY MAXIMUM FRAME SIZE, PROTOCOL TYPE FWI ADC FO
77h 11h 0110b 00b 01b
Figure 22. Protocol Info Field Details
COMMANDSOF CRC EOF
1Dh (2 BYTES)
PUPI
(4 BYTES)
PARAM 1
(1 BYTE)
PARAM 2
(1 BYTE)
PARAM 3
01h
PARAM 4
(1 BYTE)
HLINF
(≥ 0 BYTES)
Figure 25. ATTRIB Request Frame
COMMANDSOF CRC EOF
50h (2 BYTES)
PUPI
(4 BYTES)
Figure 23. HLTB Request Frame
INDICATORSOF CRC EOF
00h (2 BYTES)
Figure 24. HLTB Response Frame
Page 21

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 21
Param 2 informs the slave about the data rate that shall
be used for communication in the ACTIVE state and the
maximum frame size that the master can receive.
Figure 26 shows the bit assignments for the Param 2
byte. The MAX66020 supports the data rates of
105.9kbps (code 00b), 211.9kbps (code 01b),
423.75kbps (code 10b), and 847.5kbps (code 11b).
The master can choose different data rates for request
and response. Since it does not support chaining, the
MAX66020 ignores the frame size capability and
assumes that the master can receive frames as large
as specified in the ATQB response.
The lower nibble of Param 3 is used to confirm the protocol type as specified in the lower nibble of the second
byte of the ATQB protocol info. Since ISO/IEC 14443-3
sets the upper nibble of Param 3 to 0000b, the Param 3
value to be used for the MAX66020 in the ATTRIB
request is 01h.
Param 4 assigns the slave the CID number that is used
with the block transmission protocol to address one of
several slaves in the ACTIVE state. Figure 27 shows the
Param 4 bit assignments. Since the MAX66020 supports the CID field, the master can assign any number
in the range from 0 to 14. According to ISO/IEC 144433, code 15 is reserved.
The ATTRIB request frame contains one optional field,
called higher layer information (HLINF). This field can
be used to include data as in the information field of the
ISO/IEC 14443 Type B block transmission protocol (see
Figure 11). If such data is present and the slave supports the HLINF field, then the slave processes the
HLINF data and returns the result in its response to the
ATTRIB request. Typically, the ATTRIB request is transmitted without HLINF field. The only HLINF data that the
MAX66020 accepts and processes is the Get UID command, code 30h.
If the ATTRIB request has a matching PUPI and a valid
CRC, the slave transmits an ATTRIB response frame, as
shown in Figure 28. The upper nibble of the indicator,
also referred to as MBLI, is 0000b, telling that the slave
does not provide any information on its internal input
buffer size; the lower nibble returns the card identifier
value that the master has just assigned to the slave.
The HL response field is optional. There are three
cases to be distinguished:
a) If there was no HLINF field in the ATTRIB request,
then there is no HL response field in the response.
b) If there was a Get UID command code (30h) in the
HLINF field of the ATTRIB request, then the HL
response field is identical to the Get UID response
information field (i.e., 00h followed by the 8-byte UID).
c) If the code in the HLINF field of the ATTRIB request
was different from 30h, then the response frame does
not contain an HL response field.
DESELECT Command
The DESELECT command is used to transition the slave
from the ACTIVE to the HALT state after the master has
completed the communication with the slave. There are
two versions of the deselect request frame, one without
CID and one with CID. Figure 29 shows both versions.
Figure 27 shows the CID format.
Logically, the DESELECT command is a special case of
the S-block of the block transmission protocol, as
defined in part 4 of the ISO/IEC 14443 standard. The
MAX66020 responds to a DESELECT command if the
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
MSB LSB
XXXX
RESPONSE DATA
RATE (UPLINK)
RECEIVER FRAME SIZE CAPABILITY
RESPONSE DATA
RATE (DOWNLINK)
Figure 26. Bit Assignments for Param 2 Byte
BIT 8 BIT 7 BIT 6 BIT 5 BIT 4 BIT 3 BIT 2 BIT 1
MSB LSB
0
(FIXED) CARD IDENTIFIER VALUE (CID)
0 00
Figure 27. Bit Assignments for Param 4 Byte
SOF
FRAME WITHOUT CID
CRC EOF
(2 BYTES)
COMMAND
C2h
SOF
FRAME WITH CID
CRC EOF
(2 BYTES)
CID
(1 BYTE)
COMMAND
CAh
Figure 29. DESELECT Request and Response Frames
INDICATORSOF CRC EOF
MBLI, CID (2 BYTES)
HL RESPONSE
(≥ 0 BYTES)
Figure 28. ATTRIB Response Frame
Page 22

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
22 ______________________________________________________________________________________
CID in the request and the CID in the device match. If
the DESELECT request does not include a CID, the
MAX66020 only responds to the request if its CID is
0000b.
The response frame to the DESELECT command is
identical to the request frame. The slave returns the
same data that it had received, confirming that the
slave addressed in the request has been transitioned to
the HALT sate.
Anticollision Examples
Probabilistic Anticollision
The master starts the anticollision process by issuing an
REQB or WUPB command. The WUPB command
involves any slave in the field with a matching AFI code.
The REQB command performs the same function, but is
ignored by slaves in the HALT state. Both commands
include the parameter N, which according to Table 6 is
used to set the probability of an ATQB response to 1/N.
If N = 1, all participating slaves respond with the ATQB
response. If N is greater than one, then each slave
selects a random number R in the range of 1 to N. If a
slave happens to choose R = 1, then it responds with
ATQB. If R is greater than 1, then the slave waits for
another REQB or WUPB command, which causes the
participating slaves to choose a new random number R.
The ATQB response contains a field named PUPI,
which is used to direct commands to a specific slave
during the anticollision process. When the master
receives an ATQB response, it should issue a matching
HLTB command to halt the slave or issue a matching
ATTRIB command to assign a CID and place the slave
in the ACTIVE state. If this is not done, the slaves continue to participate in the anticollision process. A slave
in the ACTIVE state ignores all REQB, WUPB, SLOTMARKER, ATTRIB, and HLTB commands, but responds
to the DESELECT command.
An ATQB response received with a CRC error indicates
a collision because two or more slaves have responded
at the same time. With probabilistic anticollision, the
master must issue another REQB command to cause
the slaves in the field that are not in the HALT or
ACTIVE state to select a new random number R. If one
of the slaves has chosen R = 1, it responds with ATQB.
A REQB without ATQB response does not guarantee that all slaves in the field have been identified.
Figure 30 shows an example of the time-slot anticollision, assuming that there are four slaves in IDLE state in
the field. The process begins with the master sending
an REQB request with N = 1, which forces all slaves to
respond with ATQB, resulting in a collision. Knowing that
slaves are present, the master now sends REQB with N
= 8. This causes all slaves to select a random number in
the range of 1 to 8. Only the slave that has chosen R = 1
responds, which is slave C in the example. Knowing that
there are more slaves in the field, the master continues
issuing REQB commands, which in the example, eventually identifies all slaves. Due to its statistical nature,
probabilistic anticollision is less likely to find every slave
in the field than the time-slot anticollision.
Time-Slot Anticollision
The master starts the anticollision process by issuing
an REQB or WUPB command. The WUPB command
involves any slave in the field with a matching AFI code.
The REQB command performs the same function, but is
ignored by slaves in the HALT state. Both commands
include the parameter N, which according to Table 6
specifies the number of slots to be used in the anticollision protocol.
If N = 1, all participating slaves respond with the ATQB
response. If N is greater than one, then each slave
selects a random number R in the range of 1 to N. If a
slave happens to choose R = 1, then it responds with
ATQB. If R is greater than 1, then the slave waits for a
TESTING FOR SLAVES ATTEMPT 1 ATTEMPT 2 ATTEMPT 3 ATTEMPT 4 ATTEMPT 5 ATTEMPT 6
MASTER
REQB
(N = 1)
REQB
(N = 8)
REQB
(N = 8)
REQB
(N = 8)
REQB
(N = 8)
REQB
(N = 8)
REQB
(N = 8)
SLAVE A ATQB (R = 3) (R = 7) (R = 1) ATQB (R = 3) (R = 6) (R = 8)
SLAVE B ATQB (R = 6) (R = 4) (R = 8) (R = 8) (R = 5) (R = 1) ATQB
SLAVE C ATQB (R = 1) ATQB (R = 8) (R = 2) (R = 4) (R = 3) (R = 4)
SLAVE D ATQB (R = 2) (R = 1) ATQB (R = 5) (R = 8) (R = 4) (R = 2)
Figure 30. Probabilistic Anticollision Example
Page 23

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
______________________________________________________________________________________ 23
SLOT-MARKER command with a slot number that is
equal to R and then responds with ATQB. The master
must try all slot numbers from 2 to N to ensure that no
slave is missed.
The ATQB response contains a field named PUPI,
which is used to direct commands to a specific slave
during the anticollision process. When the master
receives an ATQB response, it should issue a matching
HLTB command to halt the slave, or issue a matching
ATTRIB command to assign a CID and place the slave
in the ACTIVE state. A slave in the ACTIVE state ignores
all REQB, WUPB, SLOT-MARKER, ATTRIB, and HLTB
commands, but responds to the DESELECT command.
An ATQB response received with a CRC error indicates
a collision because two or more slaves have responded
at the same time. Typically the master continues issuing
SLOT-MARKER commands to test for slaves with random numbers R different from 1. If additional collisions
were encountered, the master must issue a new REQB
command, causing each slave in the field that is not in
the HALT or ACTIVE state to select a new random number R. The anticollision process then continues in this
manner until all slaves in the field have been identified
and put either into the HALT or ACTIVE state.
Figure 31 shows an example of the time-slot anticollision, assuming that there are four slaves in IDLE state
in the field. The process begins with the master sending an REQB request with N = 1, which forces all slaves
to respond with ATQB, resulting in a collision. Knowing
that slaves are present, the master now sends REQB
with N = 8. This causes all slaves to select a random
number in the range of 1 to 8. This does not prevent
two slaves from choosing the same value for R, but the
higher N is, the less likely this is to occur. In the example, slave C has chosen R = 1 and responds right after
REQB. The master now sends a SLOT-MARKER command with slot number 2 (SM2), which causes slave D
to respond. The master continues testing all slots, and,
if a slave with matching R is present, receives an
ATQB. In case the master detects a collision in a slot,
the slaves identified in the remaining slots need to be
put in the HALT or ACTIVE state first, before another
anticollision process is started. Note that there is no
need for the master to test the slots in numerical order,
as in the example.
CRC Generation
The ISO/IEC 14443 standard uses a 16-bit CRC, generated according to the CRC-16-CCITT polynomial function: X16+ X12+ X5+ 1 (Figure 32). This CRC is used
for error detection in request and response data packets and is always communicated in the inverted form.
After all data bytes are shifted into the CRC generator,
the state of the 16 flip-flops is parallel-copied to a shift
register and shifted out for transmission with the LSb
first. For more details on this CRC refer to ISO/IEC
14443-3, Annex B, CRC_B encoding.
TESTING FOR SLAVES SLOT 1 SLOT 2 SLOT 3 SLOT 4 S LOT 5 SLO T 6 SLOT 7 SLOT 8
MASTER
REQB
(N = 1)
REQB
(N = 8)
SM2 SM3 SM4 SM5 SM6 SM7 SM8
SLAVE A ATQB (R = 3) ATQB
SLAVE B ATQB (R = 6) ATQB
SLAVE C ATQB (R = 1) ATQB
SLAVE D ATQB (R = 2) ATQB
Figure 31. Time-Slot Anticollision Example
Page 24

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
24 ______________________________________________________________________________________
Key Fob Mechanical Drawing
Figure 32. CRC-16-CCITT Generator
MSb
1ST
STAGE
0
X
1
X
9TH
STAGE
8
X
9
X
2ND
STAGE
10TH
STAGE
X
10
X
2
3RD
STAGE
11TH
STAGE
TOP VIEW
POLYNOMIAL = X16 + X12 + X5 + 1
4TH
STAGE
3
X
STAGE
11
X
12TH
4
X
5TH
STAGE
54mm
6TH
STAGE
5
X
13TH
STAGE
12
X
14TH
STAGE
13
X
7TH
STAGE
6
X
15TH
STAGE
14
X
7
X
15
X
INPUT DATA
STAGE
LSb
16TH
STAGE
8TH
16
X
28mm
7.7mm
MAX66020K-000AA+
SIDE VIEW
1.6mm
Page 25

MAX66020
ISO/IEC 14443 Type B-Compliant
1Kb Memory Fob
Maxim cannot assume responsibility for use of any circuitry other than circuitry entirely embodied in a Maxim product. No circuit patent licenses are
implied. Maxim reserves the right to change the circuitry and specifications without notice at any time.
Maxim Integrated Products, 120 San Gabriel Drive, Sunnyvale, CA 94086 408-737-7600 ____________________
25
© 2010 Maxim Integrated Products Maxim is a registered trademark of Maxim Integrated Products, Inc.
Revision History
REVISION
NUMBER
0 12/10 Initial release —
REVISION
DATE
DESCRIPTION
PAGES
CHANGED
 Loading...
Loading...