Page 1

Installation and
Configuration Guide
ProCurve Wireless Access Point 10ag
Power over Ethernet Devices
www.procurve.com
Page 2

Page 3

ProCurve Wireless Access Point
10ag
Installation and Configuration Guide
Page 4

© Copyright 2007 Hewlett-Packard Development Company, L.P. The information contained herein is subject
to change without notice.
This document contains proprietary information, which is
protected by copyright. No part of this document may be
photocopied, reproduced, or translated into another
language without the prior written consent of HewlettPackard.
Publication Number
5991-8615
November 2007
Open Source Software Acknowledgement
This software incorporates open source components that
are governed by the GNU General Public License (GPL). In
accordance with this license, ProCurve Networking will
make available a complete, machine readable copy of the
source code components covered by the GNU GPL upon
receipt of a written request. Send a request to:
Hewlett-Packard Company, L.P.
ProCurve Access Point 10ag
GNU GPL Source Code
Attn: ProCurve Networking Support
MS: 5551
Roseville, CA 95747 USA
Applicable Products
ProCurve Wireless Access Point 10ag NA (J9140A)
ProCurve Wireless Access Point 10ag WW (J9141A)
Disclaimer
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY
OF ANY KIND WITH REGARD TO THIS MATERIAL,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not
be liable for errors contained herein or for incidental or
consequential damages in connection with the furnishing,
performance, or use of this material.
The only warranties for HP products and services are set
forth in the express warranty statements accompanying
such products and services. Nothing herein should be
construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions
contained herein.
Hewlett-Packard assumes no responsibility for the use or
reliability of its software on equipment that is not furnished
by Hewlett-Packard.
Warranty
A copy of the specific warranty terms applicable to your
Hewlett-Packard products and replacement parts can be
obtained from your HP Sales and Service Office or
authorized dealer.
Safety
Before installing and operating these products, please read
the “
Installation Precautions” in Chapter 2 and “Safety
Information” in Appendix C.
Hewlett-Packard Company
8000 Foothills Boulevard, m/s 5552
Roseville, California 95747-5552
http://www.procurve.com
Page 5

Contents
1 Introducing the ProCurve Wireless Access Point 10ag
Package Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
Front of the Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
LEDs on the Front Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Back of the Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
LAN Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Power Connector . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
Reset to Default Button . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Antennas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-7
Access Point Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
2 Installing the Access Point
Before You Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Installation Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Wireless Client Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Safety Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Installation Precautions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Summary of Installation Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
Installation Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Step 1. Preconfigure the Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
a. Prepare the Management Computer . . . . . . . . . . . . . . . . . . . . . . 2-4
b. Connect the Management Computer to the Access Point . . . . 2-5
c. Connect to the Web Interface and Change the IP Address . . . . 2-6
Step 2. Prepare the Installation Site . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Cabling Infrastructure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Installation Location . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Network Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
Step 3. Verify the Access Point Completes Initialization . . . . . . . . . . . 2-9
LED Behavior . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Step 4. Position the Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
i
Page 6

Step 5. Connect the Access Point to a Power Source . . . . . . . . . . . . . 2-11
Step 6. Connect the Network Cable . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-12
Using the RJ-45 Connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-12
3 Getting Started With Access Point Configuration
Introducing the Management Web Interface . . . . . . . . . . . . . . . . . . . . . . . . 3-1
Logging On to the Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-2
Navigating Around the Web Interface . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
Tasks for Your First Web Browser Interface Session . . . . . . . . . . . . . . . . . 3-5
Default Configuration Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-6
4 Setting Up the Access Point
Configuring Basic Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-1
Configuring Wireless Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-3
Creating a Wireless Profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
Editing a Wireless Profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Deleting a Wireless Profile . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Configuring Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
Wireless Security Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-8
Encryption . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Key Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Deciding Which Security Profile to Use . . . . . . . . . . . . . . . . . . . . . . . . 4-10
Configuring the Access Point with Your Preferred Security Profile 4-11
Using No Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-11
Configuring WEP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-12
Configuring WPA-PSK (TKIP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-14
Configuring WPA2-PSK (AES) . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-15
Configuring WPA-PSK (TKIP) / WPA2-PSK (AES) . . . . . . . . . . . 4-16
Configuring WPA (TKIP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-18
Configuring WPA2 (AES) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-19
Configuring 802.1X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-20
Controlling Access to the Wireless Network . . . . . . . . . . . . . . . . . . . . . . . 4-22
Setting Up Local MAC Authentication . . . . . . . . . . . . . . . . . . . . . . . . . 4-23
Setting Up Remote MAC Authentication . . . . . . . . . . . . . . . . . . . . . . . 4-24
ii
Page 7

Configuring Advanced Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-25
Setting the SNMP Community Names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-28
5 Managing the Access Point
Viewing Device Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-1
Changing the Management Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
If You Forget Your Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Updating the Access Point Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Where to Download Software Updates . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Update Precautions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Software Update Procedure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-7
Viewing the List of Connected Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-7
Backing Up and Restoring Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-8
Rebooting the Access Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-9
6 Troubleshooting
Basic Troubleshooting Tips . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-1
Diagnosing with the LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-3
Hardware Diagnostic Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Testing the Access Point by Resetting It . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Checking the Access Point’s LEDs . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Testing Twisted-Pair Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Testing Access Point-to-Device Network Communications . . . . . . . . 6-6
Testing End-to-End Network Communications . . . . . . . . . . . . . . . . . . 6-6
Restoring Factory Default Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-6
HP Customer Support Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-8
Before Calling Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-8
A Specifications
Physical . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-1
Electrical . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-1
Japanese Power Cord Statement . . . . . . . . . . . . . . . . . . . . . . . . . . A-1
Environmental . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-2
iii
Page 8

Connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-2
Safety . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-2
EMC Compliance (Class B) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-2
Radio Signal Certification . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-2
Immunity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-3
Wireless . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-3
Receiver Sensitivity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-4
B Access Point Port and Network Cables
Access Point Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-1
Twisted-Pair Cables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-1
Twisted-Pair Cable/Connector Pin-Outs . . . . . . . . . . . . . . . . . . . . . . . . . . . B-2
Straight-Through Twisted-Pair Cable for
10 Mbps or 100 Mbps Network Connections . . . . . . . . . . . . . . . . . . . . B-3
Cable Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-3
Pin Assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-3
Crossover Twisted-Pair Cable for
10 Mbps or 100 Mbps Network Connection . . . . . . . . . . . . . . . . . . . . . B-4
Cable Diagram . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-4
Pin Assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-4
C Safety and EMC Regulatory Statements
Safety Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-1
Informations concernant la sécurité . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-2
Hinweise zur Sicherheit . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-3
Considerazioni sulla sicurezza . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-5
Consideraciones sobre seguridad . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-6
Safety Information (Japan) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-8
Safety Information (Korea) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-9
Safety Information (China) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-10
EMC Regulatory Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-11
Notice for U.S.A. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-11
Regulatory Model Identification Number . . . . . . . . . . . . . . . . . . C-12
Notice for Canada . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-12
iv
Page 9

Notice for European Community . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-13
EU Declaration of Conformity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-16
Notice for Japan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-17
Notice for Taiwan . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-17
D Recycle Statements
Waste Electrical and Electronic Equipment (WEEE) Statements . . . . . . D-1
E Open Source Licenses
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . E- 1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . E- 1
GPL2 (GNU General Public License, v.2). . . . . . . . . . . . . . . . . . . . . . . . . . . E- 2
LGPL (GNU Lesser General Public License) . . . . . . . . . . . . . . . . . . . . . . . . E- 8
Index
v
Page 10

Page 11

Introducing the ProCurve
1
Wireless Access Point 10ag
The ProCurve Wireless Access Point 10ag is a dual-radio 802.11a and
802.11b/g access point that offers maximum flexibility in deployment and
optimum throughput for high-density usage areas. Designed for small business
networking environments, it provides high-speed, reliable wireless
networking and comprehensive security and management features.
ProCurve Wireless Access Point 10ag NA (J9140A)
ProCurve Wireless Access Point 10ag WW (J9141A)
The Access Point 10ag has one 10/100Base-TX RJ-45 port. This port also
supports Power over Ethernet (PoE) based on the IEEE 802.3af standard. The
access point supports wireless connectivity at speeds up to 54 Mbps based on
the IEEE 802.11a and IEEE 802.11g standards. It is designed to be used
primarily for connecting wireless clients and devices to a wired primary
network.
1-1
Page 12

Introducing the ProCurve Wireless Access Point 10ag
This chapter describes the Access Point 10ag, including:
■ Package Contents
■ Front of the Access Point
■ Back of the Access Point
■ Access Point Features
Throughout this manual, the ProCurve Access Point 10ag will be referred to
as the ‘access point’.
1-2
Page 13

Introducing the ProCurve Wireless Access Point 10ag
Package Contents
Package Contents
Before installing and using the access point, verify that the package you
received is complete. A complete Access Point 10ag package includes the
following items:
■ ProCurve Product Documentation CD-ROM
(contains PDF file copies of the documentation for the Access Point 10ag,
including this Installation and Configuration Guide)
■ Read Me First
■ Ethernet cable
■ AC power adapter
If any of the above items are damaged or missing, please contact the vendor
from which you purchased the access point.
Front of the Access Point
ProCurve Wireless Access Point 10ag
Power LED
Diag LED
LAN LEDs
Wireless LEDs
1-3
Page 14
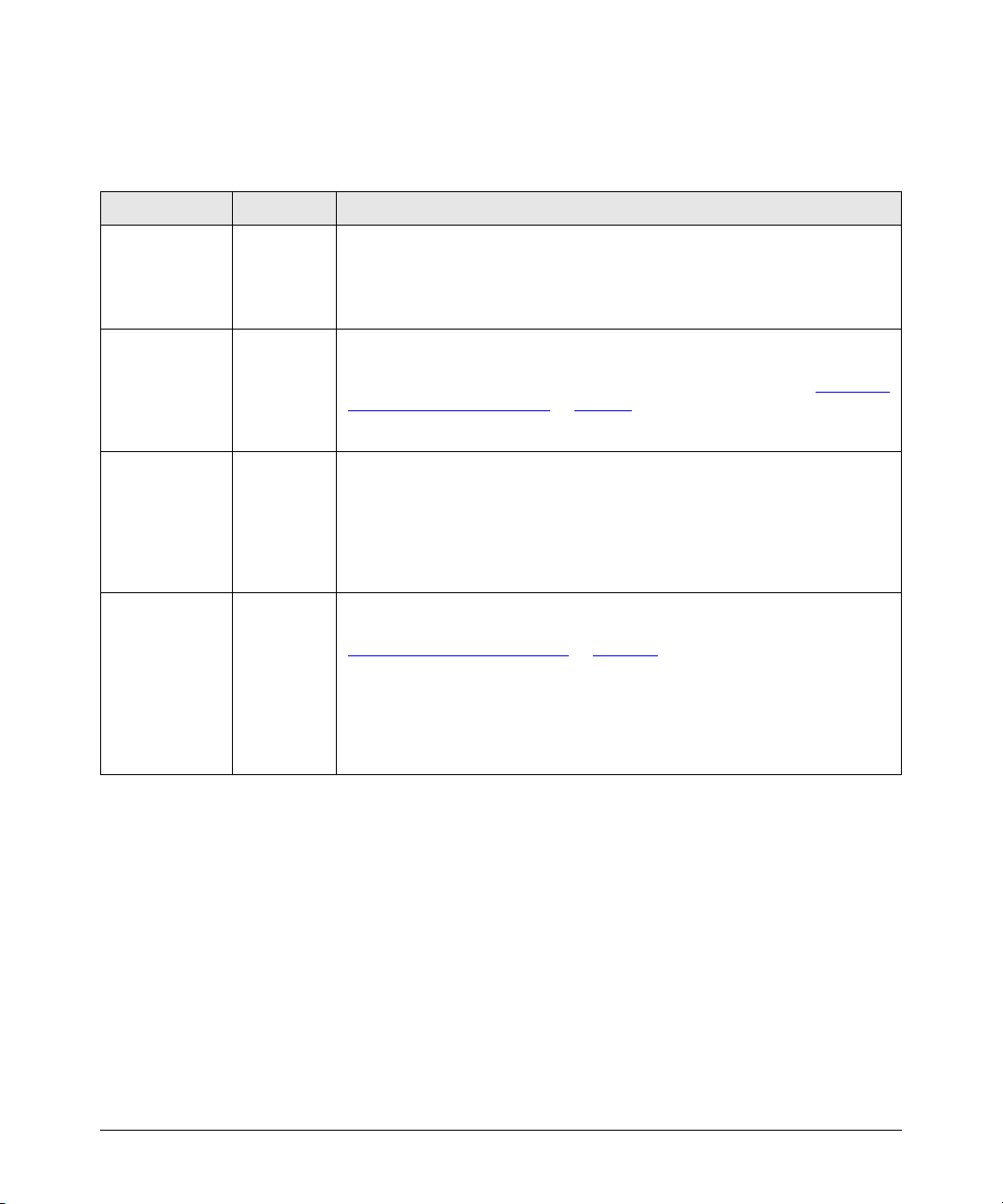
Introducing the ProCurve Wireless Access Point 10ag
Front of the Access Point
LEDs on the Front Panel
Table 1-1. Access Point LEDs
LED Label State Meaning
Power Green The access point is receiving power.
Off The access point is NOT receiving power. If the power adapter is connected to a
power source, verify that the power jack is connected properly to the power
connector on the back panel of the access point.
Diag Blinking
amber
Off Normal state
LAN Off The RJ-45 port has no network cable connected, or is not receiving a link signal.
Blinking or
solid green
Link/Act
(802.11a)
Link/Act
(802.11b/g)
Blinking
slowly
Blinking fast
or solid
green
Reset to factory default is in progress. Blinking stops when the access point has
completed resetting to factory defaults and is about to reboot. For more information
on resetting to factory default using the Reset to Default button, refer to “
Factory Default Configuration” on page 6-6.
The RJ-45 port has a link indication from a 10 Mbps or 100 Mbps device and is
transmitting or receiving traffic. The LED blinking rate is proportional to the traffic
rate. If there is no traffic, the blinking rate will be once every five seconds. As the
traffic rate increases, the blinking rate also increases until the LED is solid on, which
indicates there no available bandwidth on the port.
The wireless interface may be disabled. To verify, check the radio status on the
Information page. For instructions on enabling the wireless interface, refer to
“
Configuring Advanced Settings” on page 4-25.
The wireless interface is enabled and transmitting or receiving traffic.
The LED blinking rate is proportional to the traffic rate. If there is no traffic, the
blinking rate will be once every second. As the traffic rate increases, the blinking
rate also increases until the LED is solid green, which indicates there no available
bandwidth on the interface.
Restoring
1-4
Page 15

Introducing the ProCurve Wireless Access Point 10ag
Back of the Access Point
ProCurve Wireless Access Point 10ag
Back of the Access Point
DC power connector
Network port
10/100Base-TX RJ-45
port and PoE input
Reset to Default
button
LAN Port
The access point includes one 10/100Base-TX port. This port uses Auto-MDIX,
which means that you can use either a straight-through or a crossover twistedpair cable to connect the access point to a switch, a hub, or a workstation.
Power Connector
The access point does not have a power switch. If the AC power adapter will
be used, the access point is powered on when the AC power adapter is
connected to the power connector, and the power adapter is connected to an
active AC power source.
1-5
Page 16

Introducing the ProCurve Wireless Access Point 10ag
Back of the Access Point
The access point's power adapter automatically adjusts to any voltage from
100 to 240 volts and either 50 or 60 Hz. There are no voltage range settings
required.
CAUTION Use only the AC power adapter supplied with the access point. Use of other
adapters, including adapters that came with other ProCurve Networking
products, may result in damage to the equipment.
The access point may also receive Power over Ethernet (PoE) from a switch
or another network device that supplies power over the network cable based
on the IEEE 802.3af standard.
Note that if the access point is connected to a PoE source device (through the
LAN port) and a local power source (through the AC power adapter) at the
same time, PoE will be disabled automatically.
Reset to Default Button
Use the Reset to Default button to reboot the access point or to restore the
access point to factory default settings. To reach the button, you will need a
pointed object, such as the tip of a ballpoint pen or a straightened paper clip.
■ Reboot the access point: Rebooting the access point can help clear any
temporary error conditions. To reboot the access point, press the Reset
to Default button for one to three seconds. All the LEDs will go off (except
the Power LED), then after another second, the LEDs will turn on and
blink. Note that when the access point is rebooted, any associated wireless client will be disconnected temporarily. Connection will be restored
automatically after the access point completes rebooting.
CAUTION Do NOT press the Reset to Default button for more than five (5) seconds.
Doing so will restore all access point settings to factory default.
■ Restore to factory settings: Restoring the access point to factory
settings will clear all configuration changes you have made through the
Web interface, including the IP address, access control list, and other
settings. Use this function only if you want to completely reconfigure the
access point. For detailed information, see Restoring Factory Default
Configuration in Chapter 6.
1-6
Page 17

Introducing the ProCurve Wireless Access Point 10ag
Back of the Access Point
Antennas
The access point includes internal diversity antennas for wireless communications. A diversity antenna system uses two identical antennas to receive and
transmit signals, helping to avoid multipath fading effects. When receiving,
the access point checks both antennas and selects the one with the strongest
signal. When transmitting, it uses the antenna previously selected for
receiving. The access point never transmits from both antennas at the same
time.
1-7
Page 18

Introducing the ProCurve Wireless Access Point 10ag
Access Point Features
Access Point Features
The wireless features of the Access Point 10ag include:
■ dual-radio design with IEEE 802.11a and IEEE 802.11b/g radios
■ supports up to 54 Mbps data rate on the wireless interface
■ supports 10/100Mbps data rate on the Ethernet interface with Auto-MDIX
■ supports up to eight (8) Service Set IDentifier (SSID) interfaces
■ independent security settings per SSID interface
■ supports up to 128 wireless clients and devices
■ advanced security through 64-bit and 128-bit WEP encryption, Wi-Fi
Protected Access (WPA and WPA2), IEEE 802.1X, remote authentication
via a RADIUS server, and MAC address filtering features to protect your
sensitive data and authenticate only authorized users to your network
■ access control list
■ secured authentication of wireless clients through the client’s Web
browser
■ dual power source options, including AC power adapter (included with
device) and PoE (IEEE 802.3af)
■ reset to factory default parameters
1-8
Other basic features of the Access Point 10ag include:
■ one 10/100Base-TX RJ-45 port
■ full-duplex operation for the 10/100 RJ-45 port
■ easy management through a built-in graphical interface that can be
accessed from common Web browsers
■ RADIUS Accounting for logging user activity on the network
■ download of new access point software for software updates
■ backing up and restoring of configuration file
Page 19

Introducing the ProCurve Wireless Access Point 10ag
Access Point Features
Notes ■ Transmit power is regulated by international standards and users are
forbidden to change its maximum limit.
■ The AP10ag is compliant with IEEE 802.11d and will automatically limit
the available channels and transmit-power level based on the Country/
Region setting. Clients associating with the AP10ag will receive configuration information during the initial handshaking to enable compliant
operation in the country/region of use.
1-9
Page 20

Page 21
Installing the Access Point
This chapter provides information on the requirements for installing the
access point and guides you through the steps required for the proper installation of the device.
Topics covered include:
■ Before You Begin
■ Installation Precautions
■ Installation Procedures
Before You Begin
Before starting with the installation, make sure that you have the required
items for the installation ready. In addition, verify that the wireless clients and
devices on the network have the required components for wireless communication with the access point.
2
Installation Requirements
To install the access point, you need the following:
■ Access point
■ Power adapter (included in the access point package) or PoE switch
■ Ethernet cable
If the default IP address 192.168.1.14 is not compatible with your network
settings, you will need to change it before you can set up the access point. To
change the IP address, you will need to connect a computer with TCP/IP and
a 10Mbps or 100Mbps network interface card directly to the access point.
The access point is managed through a browser-based interface. You will need
a common Web browser to access the management interface.
2-1
Page 22
Installing the Access Point
Installation Precautions
The access point may receive power using either the power adapter or Power
over Ethernet (PoE) from a switch or other network device that supplies
power over the network cable based on the IEEE 802.3af standard. If you want
to use PoE to supply power to the access point, you will also need IEEE
802.3af-compliant power sourcing equipment (PSE).
Wireless Client Requirements
For wireless clients and devices on the network to be able to communicate
with the access point, they must have at least the following:
■ An operating system that supports TCP/IP networking protocols (for
example, Windows 2000/XP, UNIX, Mac OS 8.5 or later).
■ An 802.11a, 802.11b, or 802.11g wireless network interface card
Safety Information
Before you continue, read Appendix C, “Safety and EMC Regulatory State-
ments”.
Installation Precautions
Follow these precautions when installing the access point:
CAUTION ■ Use only the AC power adapter supplied with the access point. Use of
other adapters, including adapters that came with other ProCurve
Networking products, may result in damage to the equipment.
■ You can alternatively power the access point through a network connec-
tion to a switch or other network connection device that provides Power
over Ethernet. However, note that if the access point is connected to a
power source using its AC power adapter, Power over Ethernet is
disabled.
■ Make sure that the power source circuits are properly grounded, then use
the power adapter supplied with the access point to connect it to the
power source.
■ When using the access point's AC power adapter, note that the AC outlet
should be near the access point and should be easily accessible in case
the access point must be powered off.
2-2
Page 23
Installing the Access Point
Summary of Installation Tasks
■ Ensure that the access point does not overload the power circuits, wiring,
and over-current protection. To determine the possibility of overloading
the supply circuits, add together the ampere ratings of all devices installed
on the same circuit as the access point, and then compare the total with
the rating limit for the circuit. The maximum ampere ratings are usually
printed on devices near the AC power connectors.
■ When using either the AC power adapter or PoE power, do not install the
access point in an environment where the operating ambient temperature
might exceed 40°C (104°F).
■ Make sure airflow around the sides of the access point is not restricted.
Summary of Installation Tasks
Follow these easy steps to install your access point. The rest of this chapter
provides details on these steps.
1. Preconfigure the access point (page 2-4
). The access point ships with
a default IP address of 192.168.1.14 and a subnet mask of 255.255.255.0. If
this IP address is already assigned to another device on the network or if
the IP address settings are not compatible with your network, you will
need to configure its IP address before installation.
2. Prepare the installation site (page 2-7
). Make sure that the physical
environment into which you will be installing the access point is properly
prepared, including having the correct network cabling ready to connect
to the access point and having an appropriate location for the access
point.
3. Verify that the access point completes its system initialization
(page 2-9
). Before deployment, verify correct access point operation.
Turn on the access point and observe the LEDs.
4. Position the access point (page 2-10
). The access point can be installed
on a flat surface, such as a desktop, or mounted on a wall (mounting
screws and bracket are not included in the access point package).
5. Connect the power to the access point (page 2-11
). Once the access
point is mounted, plug it into a nearby main power source using the
supplied AC adapter, or connect it to a switch that provides Power over
Ethernet.
2-3
Page 24
Installing the Access Point
Installation Procedures
6. Connect to the network (page 2-12). Using the appropriate network
cable, connect the access point to a network port, such as a switch port.
If PoE is used, this may have been completed in the prior step.
At this point, your access point is fully installed. See the rest of this chapter if
you need detailed information on any of these installation steps.
Installation Procedures
Step 1. Preconfigure the Access Point
In its factory default configuration, the access point is assigned a static IP
address of 192.168.1.14 and a subnet mask of 255.255.255.0 (the built-in DHCP
client is disabled).
■ If your network uses the same IP address class or range, and the IP address
192.168.1.14 is not assigned to any other network device, you do not need
to change the IP address settings of your access point. Continue to the
next step, “
■ If your network uses a different IP address class or range, you will need
to change the IP address settings of the access point so that it can work
on your network. Refer to the instructions below.
Step 2. Prepare the Installation Site” on page 2-7
a. Prepare the Management Computer
You will need to prepare a management computer that you want to use to
preconfigure the access point. The management computer must have the
following minimum specifications:
■ Network interface card with TCP/IP installed
■ A common Web browser
Note The following instructions are for preparing a management computer running
Microsoft Windows XP. If your computer is running a different version of
Windows, the procedures may be slightly different.
To prepare the management computer:
1. Choose a computer on your local network that you want to use to access
and manage the access point.
2-4
Page 25

Installing the Access Point
Installation Procedures
2. On this computer, click Start > Connect to > Show all connections.
The Network Connections window appears.
3. Right-click Local Area Connection, and then click Properties. The
Local Area Connection Properties window appears.
4. Click Internet Protocol (IP), and then click Properties.
Note Remember to write down your computer's current IP address settings. You
will need to change them back after you configure the IP address settings of
the access point.
5. On the General tab of the Internet Protocol (IP) Properties window, click
Use the following IP address.
6. In IP address, type an IP address that is on the same range as the default
IP address (192.168.1.14) of the access point. For example, you can type
192.168.1.123.
7. In Subnet mask, type 255.255.255.0.
8. Click OK.
You are now ready to connect the management computer to the access point.
b. Connect the Management Computer to the Access Point
In this step, you will physically connect the management computer to the
access point to prepare for preconfiguration.
1. Connect one end of the Ethernet cable that is supplied with the access
point to the LAN port on the management computer.
2. Connect the other end of the Ethernet cable to the LAN port on the back
panel of the access point.
3. Connect the supplied power adapter to the power connector on the back
of the access point.
4. Connect the other end of the power adapter to a power source.
The LEDs on the front panel of the access point flash as the device boots up.
When it has completed booting up, check the LEDs again:
■ The Power LED should be green.
■ One LAN LED - either Link/Act (100Mbps) or Link/Act (10Mbps) - should
be green.
2-5
Page 26

Installing the Access Point
Installation Procedures
c. Connect to the Web Interface and Change the IP Address
1. Start your Web browser.
2. In the address or location bar, enter http://192.168.1.14. The logon dialog
box appears.
3. In User Name, type admin.
4. In Password, type password. The Web interface appears, showing the
Information page.
5. On the menu, click Basic Settings.
6. Configure the IP address settings.
• (Recommended) If you want to assign a fixed IP address to the access
point, select Disable in DHCP Client, and then enter the IP Address,
IP Subnet Mask, and Default Gateway that you want to assign to it.
These settings must be compatible with your network to ensure that
the access point can communicate with other network devices.
• If you have a DHCP server on the network and you want the access
point to automatically obtain an IP address from the DHCP server,
click Enable in DHCP Client. You do not have to configure other
settings, but you will need to check the DHCP server periodically to
determine the IP address that the access point is using.
7. In Country/Region, select the country/region where you are operating
the access point.
Note You must select the correct country/region for the location in which you
operate the access point, so that it uses only the authorized radio channels for
wireless network devices.
8. Click Apply.
You have completed configuring your access point's IP address settings so
that it can work on your network. Remember to return your computer's IP
address settings to its original settings.
Disconnect the access point from the management computer. You are now
ready to find a suitable location for the access point and to connect the access
point to the network.
2-6
Page 27

Step 2. Prepare the Installation Site
Cabling Infrastructure
Ensure that the cabling infrastructure meets the necessary network specifications. Refer to Table 2-1
more information cabling, refer to Appendix B
Table 2-1. Network Cable to Use With the Access Point
Port Type Cable Type Length Limit
Twisted-Pair Cables
for information on the cable type and length. For
Installing the Access Point
Installation Procedures
.
10/100Base-TX Category 5, 100-ohm unshielded twisted-pair
(UTP)
Installation Location
Before installing the access point, plan its location and orientation relative to
other devices and equipment:
■ Try to place the access point in the center of your wireless network.
Normally, the higher you place the antennas, the better the performance.
You may need to reposition the access point after testing the signal
strength on several wireless clients and devices to ensure that the access
point’s location provides optimal reception throughout the service area.
■ Choose a location that allows easy viewing of the front panel LEDs and
access to the port and connector on the back panel.
■ At the back of the access point, leave at least 7.6 cm (3 inches) of space
for the twisted-pair cabling and the power cord.
■ On the sides of the access point, leave at least 7.6 cm (3 inches) for cooling.
100 meters
Note: Since the 10Base-T operation is through
the 10/100Base-TX port on the access point, if
you ever want to upgrade the ports on other
devices to 100Base-TX, it would be best to
cable the 10/100Base-TX port on the access
point initially with category 5 cable.
Network Topology
The Access Point 10ag is designed to provide wireless clients and devices
access to a wired LAN. An integrated wired and wireless LAN is called an
Infrastructure configuration. A Basic Service Set (BSS) consists of a group of
wireless PC users and an access point that is directly connected to the wired
2-7
Page 28
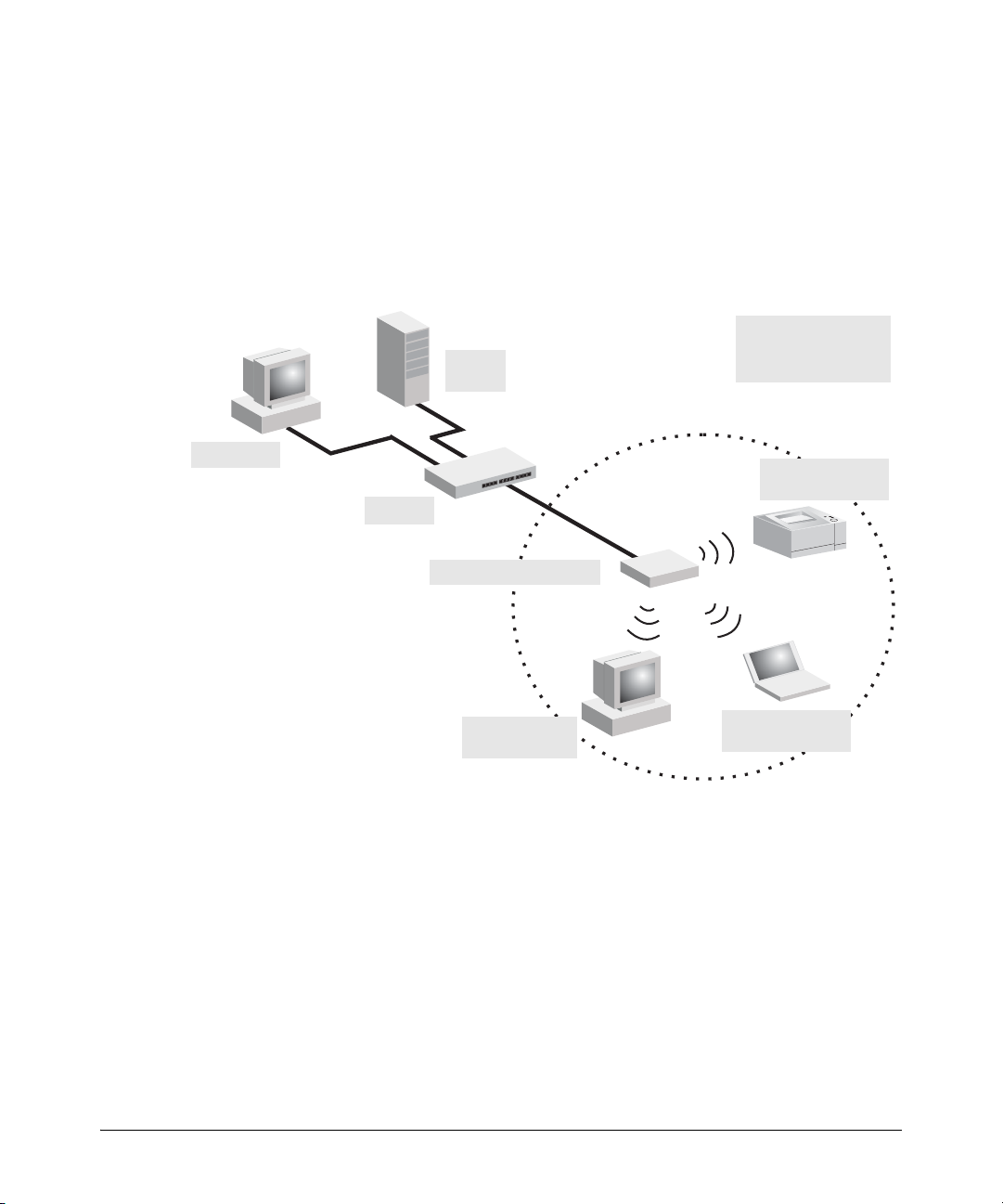
Installing the Access Point
Installation Procedures
LAN. Each wireless PC in a BSS can communicate with any computer in its
wireless group, or access other computers or network resources in the wired
LAN through the access point.
The infrastructure configuration extends the accessibility of wireless PCs to
the wired LAN and can be used for access to central network resources, or
for connections between mobile workers, as shown in the following figure.
Figure 2-1. Infrastructure Wireless LAN
Wired LAN Extension
File
Server
to Wireless Clients
and Devices
Desktop PC
Switch
Access Point 10ag
Desktop PC
Wireless Client
Network Printer
Wireless Device
Notebook PC
Wireless Client
2-8
Page 29

Installing the Access Point
Installation Procedures
Step 3. Verify the Access Point Completes Initialization
Before deploying the access point to its network location, you should first
verify that it is working properly by plugging in the AC adapter, or connecting
it to a switch that provides Power over Ethernet, and verifying that it
completes its system initialization.
1. Connect a network cable from a PoE source device (such as a switch) to
the RJ-45 port on the back of the access point, or connect the supplied
power adapter to the power connector on the back of the access point,
and then into a properly grounded electrical outlet.
Connect the power adapter to
the power connector
Or connect a network
cable to a PoE switch
Note The Access Point 10ag does not have a power switch. It is powered on when
the power adapter is connected to the access point and to a power source, or
when a network cable is connected to the access point and to a network device
that provides Power over Ethernet.
For safety, when connecting to an electrical outlet, the power outlet should
be located near the access point.
Use only the AC power adapter supplied with the access point. Use of other
adapters, including adapters that came with other ProCurve Networking
products, may result in damage to the equipment.
2-9
Page 30
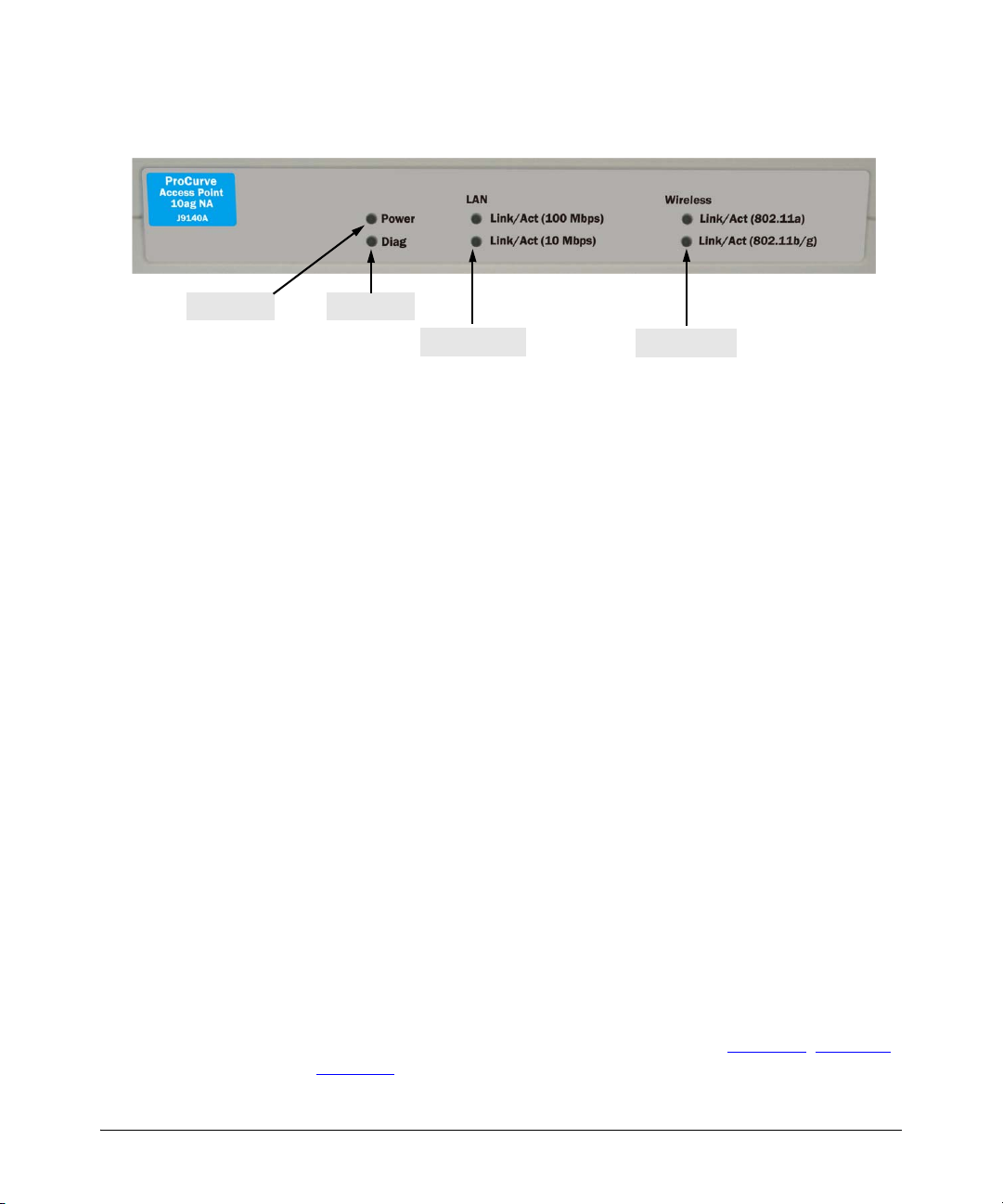
Installing the Access Point
Installation Procedures
2. Check the LEDs on the access point as described below.
Power LED
Diag LED
LAN LEDs
Wireless LEDs
When the access point is powered on, it performs its system initialization.
The system initialization takes between 30 seconds and one minute to
complete.
LED Behavior
During the system initialization:
• The Power LED first turns on immediately, then both LAN LEDs blink
once, then one LAN LED (depending on the speed of the connected
device) turns on, and then the two Wireless LEDs turn on and off
several times during the initialization phase.
• If RJ-45 port is not connected to any network device (for example,
during predeployment), both LAN LEDs remain off before the two
Wireless LEDs turn on and off.
When the system initialization completes successfully:
•The Power LED remains green.
•The LAN and Wireless LEDs on the front panel of the access point go
into their normal operational mode:
– If the RJ-45 network port and radio interfaces are connected to
active network devices, the LEDs should be blinking at a rate
proportional to the traffic rate. If there is no network activity, the
LEDs should still be blinking at approximately one-second intervals.
– If the RJ-45 network port is not connected to an active network
device, the LEDs should be off.
2-10
If the LED display is different than what is described above, the system
initialization has not completed correctly. Refer to Chapter 6
, “Trouble-
shooting” for diagnostic help.
Page 31

Installing the Access Point
Installation Procedures
Step 4. Position the Access Point
Unplug the access point from its power source, and then place it in the
network location that you have chosen. The access point can be installed on
a flat surface (for example, on a desktop) or wall-mounted (mounting kit is
not included). When deciding where to position the access point, choose a
location that:
■ Allows easy viewing of the front panel LED indicator lights, and access to
the rear panel connectors, if necessary.
■ Is centrally located to the wireless computers that will connect to the
access point. A good location will optimize wireless connections to
computers in both horizontal and vertical directions, allowing wider
coverage.
When positioning the access point, ensure:
■ It is out of direct sunlight and away from sources of heat.
■ Cabling is away from power lines, fluorescent lighting fixtures, and
sources of electrical noise such as radios, transmitters and broadband
amplifiers.
■ There are no thick walls or metal shielding between the access point and
the wireless clients and devices. In ideal conditions, the access point has
a range of approximately 100 meters. If there are any obstructions
between the wireless devices, the range is reduced and transmission
speed is lower.
■ Water or moisture cannot enter the case of the unit.
■ Airflow around the unit and through the vents on the side of the case is
not restricted. The access point should have a minimum of 25 mm (1 in.)
clearance.
Step 5. Connect the Access Point to a Power Source
1. Plug the included power adapter into the access point’s power connector
and into a nearby AC power source.
Alternatively, connect the Ethernet port on the access point to a switch
or other network device that provides Power over Ethernet.
Note If you connect the access point to an AC power source and a PoE power source
at the same time, PoE will be disabled automatically.
2. Re-check the LEDs during the system initialization. See “LED Behavior”
on page 2-10
.
2-11
Page 32

Installing the Access Point
Installation Procedures
Step 6. Connect the Network Cable
Connect the network cable, described under ““Cabling Infrastructure” on
page 2-7
access point.
Using the RJ-45 Connectors
To connect:
Push the RJ-45 plug into the LAN port
until the tab on the plug clicks into
place. When power is on, one of the
two LAN LEDs should turn on to
confirm a valid network connection.
If neither LAN LED turns on, see
“
Diagnosing with the LEDs” in
Chapter 5
Congratulations! You have
completed installing your access
point. You are now ready to start
configuring your access point
settings.
Please continue to Chapter 3
“
Getting Started With Access Point Configuration” for an introduction of the
Web interface and a summary of essential configuration tasks that you should
perform.
, from the network device or your patch panel to the LAN port on the
.
Category 5 cable for 10/100 Mbps ports (UTP)
Maximum distance: 100 meters
RJ-45
connector
,
2-12
Page 33

Getting Started With Access Point Configuration
This chapter provides instructions for logging on to the Web interface and a
summary of the essential configuration tasks you need to perform to get the
access point up and running on your network.
Topics discussed include:
■ Introducing the Management Web Interface
■ Tasks for Your First Web Browser Interface Session
■ Default Configuration Parameters
Introducing the Management Web
3
Interface
The access point is managed through a Web browser-based interface that you
can access from any PC or workstation on the same subnet as the access point.
Open a compatible browser and type the access point’s IP address as the URL.
(See “
Step 1. Preconfigure the Access Point” on page 2-4 for information on
setting the IP address.)
Note You can use the Web browser interface to access IP addressing only if the
access point already has an IP address that is reachable through your network.
No additional software installation is required to make this interface available;
it is included in the access point’s onboard software.
You will need a common Web browser to access the management interface.
The Web browser that you will use for management must have JavaScript
enabled to support the interactive features of the Web interface. It must also
support HTTP uploads to use the software update feature.
3-1
Page 34

Getting Started With Access Point Configuration
Introducing the Management Web Interface
Note To ensure proper screen refresh when using Internet Explorer with Windows
XP, be sure that the browser options are configured as follows: Under the
menu “Tools > Internet Options > Temporary Internet Files > Settings,”
the setting for item “Check for newer versions of stored pages” should be
set to “Automatically.”
s
Logging On to the Web Interface
To log on to the Web interface:
1. Start your Web browser.
2. In the address or location bar, enter the IP address that you assigned to
the access point when you preconfigured it in “
Access Point” on page 2-4.
A logon dialog box appears.
3. In User name, type admin.
4. In Password, type password.
5. Click OK to log on.
Step 1. Preconfigure the
The ProCurve Access Point 10ag Web interface appears, showing the Information page.
3-2
Page 35

Getting Started With Access Point Configuration
Introducing the Management Web Interface
Figure 3-1. Information Page (Web Interface Home Page)
Note The Web interface does not have a Log Off button. To end your Web interface
session safely, close the Web browser.
Navigating Around the Web Interface
The Web interface provides logical window groups for easy access to common
setup, management, and advanced configuration features. This section
describes each of the logical window groups, submenus, screen elements and
parameters.
3-3
Page 36

Getting Started With Access Point Configuration
Introducing the Management Web Interface
Figure 3-2. Web Interface Elements
Menu
Information Pane
The Web interface has two primary sections:
■ The menu: Located on the left-hand side of the page, the menu contains
links to the primary configuration options on the Web interface. Menu
items are grouped into three categories:
• Information (default home page): Shows information about the
access point, including the MAC address, software version, current
IP address settings, and configured wireless networks.
• Setup: Contains options for configuring the essential access point
settings, such as basic IP address settings, basic wireless settings,
security settings, and access control.
• Management: Contains options for performing administrative tasks
on the access point, including changing the password, updating the
software, backing up and restoring settings, viewing the list of associated wireless clients and devices, and rebooting the access point.
3-4
Page 37

Getting Started With Access Point Configuration
Tasks for Your First Web Browser Interface Session
■ The information pane: Shows related configuration options for each
item on the menu. For example, if you click IP Settings on the menu, the
information pane loads the parameters that you can set or edit, and then
save for your desired configuration change to take effect.
Tasks for Your First Web Browser
Interface Session
The first time you access the Web browser interface, there are a number of
basic tasks that you should perform. Table 3-1
specific instructions on the how perform the procedure, refer to the page
number listed in the right column.
In setting up your access point for network installation, this manual covers
many of the tasks that should be considered for proper security and management. Each of these tasks are detailed in their respective sections, however,
this summary is provided as an aid for establishing your network.
Table 3-1. Basic Web Interface Tasks
lists these essential tasks. For
To Learn How to Do This Task Refer to
Change the default password “Changing the Management Password” on page 5-3
Set the correct country/region code “Configuring Basic Settings” on page 4-1
Control access to the wireless network “Controlling Access to the Wireless Network” on
page 4-22
Set wireless security from No Security (default) to at least WPA/
WPA2
“Configuring Security Settings” on page 4-7
3-5
Page 38

Getting Started With Access Point Configuration
Default Configuration Parameters
Default Configuration Parameters
Table 3-2 lists some of the default settings with which the access point is
configured, including the basic IP address and wireless configuration parameters. Information on how to update each parameter is provided later in this
guide.
Table 3-2. Default Parameters
Parameter Default Description
Username admin The name of the manager.
Password password The password for the manager.
IP Address 192.168.1.14 IP address compatible with your network.
Subnet Mask 255.255.255.0 Subnet mask compatible with your network.
Default Gateway not set IP address of the next-hop gateway node for network traffic that needs
to be able to reach off-subnet destinations.
Radio Mode 802.11 b/g The default radio mode.
Radios Disabled Both radios are disabled.
SSID wireless-g A pre-configured Service Set Identifier (SSID), also called a wireless
Note: The IP address and subnet mask assigned to the access point must be compatible with the IP addressing used
on your network. For more information on IP addressing, see “
network name.
Configuring Basic Settings” on page 4-1.
3-6
Page 39

Setting Up the Access Point
This chapter provides information on how configure the access point’s
network, wireless, and security settings to ensure its proper operation on the
network. It also describes how to configure advanced options, such as the
wireless radio settings and the built-in SNMP agent.
Topics discussed in this chapter include:
■ Configuring Basic Settings
■ Configuring Wireless Settings
■ Configuring Security Settings
■ Controlling Access to the Wireless Network
■ Configuring Advanced Settings
4
Configuring Basic Settings
Basic settings refer to the IP address settings and the country/region code
assigned to the access point.
Note If the access point's IP address settings are already compatible with your
network, you do not need to change them.
4-1
Page 40

Setting Up the Access Point
Configuring Basic Settings
Figure 4-1. Basic Settings Page
To configure the access point’s basic settings:
1. On the menu, click Basic Settings.
2. Configure the IP address settings.
• Assign an IP address (recommended) – If you want to assign a fixed
IP address to the access point, select Disable for the DHCP Client,
and then enter the IP Address, IP Subnet Mask, and Default Gateway
that you want to assign to it. These settings must be compatible with
your network to ensure that the access point can communicate with
other network devices.
• Enable the built-in DHCP client – If you have a DHCP server on the
network and you want the access point to automatically obtain an IP
address from the DHCP server, click Enable in DHCP Client. You do
not have to configure other settings, but you will need to check the
DHCP server from time to time to determine the IP address that the
access point is using. You need this IP address to connect to the Web
interface.
Note If you enable the built-in DHCP client and the access point fails to obtain an
IP address from the DHCP server after 10 seconds (for example, the DHCP
server is unreachable), the access point will automatically use 192.168.1.14, its
default IP address.
4-2
Page 41

Setting Up the Access Point
Configuring Wireless Settings
3. In Country/Region, select the country or region where you are installing
the access point (if you have not done so earlier).
Notes ■ You must select the correct country/region for the location in which you
operate the access point, so that it uses only the authorized radio channels
for wireless network devices.
■ The radios are disabled if the Country/Region option is not set. Once this
option is configured, the radios can be enabled.
■ When resetting to factory defaults, the Access Point 10ag must have its
Country/Region setting configured.
4. Click Apply.
Configuring Wireless Settings
Wireless settings define the SSID, wireless channel, wireless mode, and data
rate that each wireless interface uses. The access point comes with one
predefined wireless profile (SSID wireless-g), which allows
802.11b/g wireless clients to associate with it. You can edit this existing
wireless profile, or you can create new ones.
4-3
Page 42

Setting Up the Access Point
Configuring Wireless Settings
Figure 4-2. Wireless Settings Page
4-4
Page 43

Setting Up the Access Point
Configuring Wireless Settings
Creating a Wireless Profile
Note The access point ships with one preconfigured wireless profile for 802.11b/g.
Figure 4-3. Add Wireless Profile Page
To create a new wireless profile:
1. On the menu, click Wireless Settings. The Wireless Settings page
appears.
2. Click Add.
3. In Wireless Network Name (SSID), type a unique SSID that you want
to assign to the wireless profile.
4. In SSID Broadcast, click Enable if you want to allow all wireless clients
and devices within the range of the access point to see the SSID. Otherwise, click Disable.
5. In Channel/Frequency, select the wireless channel and frequency that
you want this wireless profile to use. The range of channels and frequencies available depends on the wireless mode that you selected.
6. In Mode, select the wireless mode that you want this wireless profile to
use. Available options include:
• g and b: Select to allow connections from 802.11g and 802.11b clients
only.
4-5
Page 44

Setting Up the Access Point
Configuring Wireless Settings
•g only: Select to allow connections from 802.11g clients only.
• a only: Select to allow connections from 802.11a clients only.
• b only: Select to allow connections from 802.11b clients only.
7. In Data Rate, select the maximum speed at which the access point can
transmit traffic for this wireless profile. If you want the access point to
automatically use the optimum data rate for the associated wireless
clients and devices, select Best.
8. Click Apply. A confirmation message appears.
9. Click OK to finish creating the wireless profile.
Note For the access point to operate using this wireless profile, the radio interface
configured for the SSID must be enabled. Check the radio status on the
Information page. If the radio is disabled, refer to “
Settings” on page 4-25 for instructions on how to enable it.
Configuring Advanced
Editing a Wireless Profile
To edit an existing wireless profile:
1. On the menu, click Wireless Settings.
4-6
2. Click the option button for the wireless profile that you want to edit. For
example, if you want to edit the wireless-g profile, click the option button
next to it.
3. Click Edit.
4. Modify the following settings as required:
• Wireless Network Name (SSID)
• SSID Broadcast
• Channel/Frequency
• Mode
• Data Rate
5. Click Apply.
Deleting a Wireless Profile
To delete a wireless profile:
1. On the menu, click Wireless Settings under Setup. The SSID List page
appears.
Page 45

Setting Up the Access Point
Configuring Security Settings
2. Select the option button for the wireless profile that you want to delete.
3. Click Delete.
The message Please wait... appears. After a few seconds, the SSID List
refreshes and the wireless profile you chose to delete disappears from the list
of SSIDs.
Configuring Security Settings
Unlike wired networks, anyone with a compatible wireless adapter can
receive wireless data transmissions from your network well beyond your
walls. To prevent outsiders from eavesdropping on your network traffic or
from entering your network to access your computers and files, you should
configure the security features of your access point.
Figure 4-4. Security Settings Page
Wireless Security Overview
By default, the access point is configured as an “open system,” with no
security. This means that the access point broadcasts a beacon frame, advertising each configured wireless network (SSID). If a wireless client has a
4-7
Page 46

configured WLAN of “any,” it can read the SSID from the beacon and use it to
allow immediate connection to the access point. Wireless devices are
permitted to connect with the access point without first verifying that users
are authorized to access the network.
In addition, user data is transmitted over the air without being encrypted, and
is subject to being intercepted by wireless devices anywhere within range that
want to eavesdrop on the wireless network.
Configure your wireless network security to protect against eavesdroppers
and to prevent unauthorized access to the wireless network. Wireless network
security requires attention to three main areas:
■ Authentication: Verifying that devices attempting to connect to the
network are authorized users before granting them access.
■ Encryption: Encrypting data that passes between the access point and
devices (to protect against interception and eavesdropping).
■ Key Management: Assigning unique data encryption keys to each wire-
less device session, and periodically changing the encryption keys to
minimize risk of their potential discovery.
Authentication
The two ways of authenticating users on the Access Point 10ag are:
■ MAC Authentication: Based on the user's wireless device MAC address.
■ 802.1X Authentication: Based on the user credentials, such as; username/
password, digital certificates, etc.
MAC Authentication. MAC authentication of users can be done either
using a remote authentication server like a RADIUS server or by creating a
local database on the access point itself. MAC authentication is not as secure
as 802.1X authentication, as it is easy to decipher and spoof for unauthorized
network access.
802.1X Authentication. User 802.1X authentication can be implemented
using a remote authentication server, such as a RADIUS server. The user's
credentials are exchanged with the servers using a mechanism called “Extensible Authentication Protocol (EAP)”. EAP is a public-key encryption system
to ensure that only authorized network users can access the network. In
wireless communications using EAP, a user requests connection to a WLAN
through an access point, which then requests the identity of the user and
transmits that identity to an authentication server such as RADIUS. The server
asks the access point for proof of identity, which the access point gets from
the user and sends back to the server to complete the authentication.
Page 47

Setting Up the Access Point
Configuring Security Settings
The Access Point 10ag supports all EAP types tested by the WiFi Alliance; TLS,
TTLS, PEAP0/MSCHAPv2, PEAP1/GTC and SIM. EAP types that do not
provide key management (like MD5) are not suitable for wireless networks.
802.1X authentication can be used with WEP, TKIP and AES encryption
ciphers. It is possible to use a combination of both MAC authentication and
802.1X authentication simultaneously on the same WLAN.
Encryption
The access point supports three types of encryption:
■ Wired Equivalent Privacy (WEP): Key lengths of 64 bits and 128 bits are
possible. WEP provides the least secure method of encryption (static WEP
is not secure, as it can be easily compromised).
■ Temporal Key Integrity Protocol (TKIP): Intermediate security between
WEP and AES with key length of 256 bits. Provides a more-secure method
of encryption than WEP (security is much better than WEP, but not as
robust as AES).
■ Advanced Encryption Standard (AES): AES is a symmetric 128-bit block
data encryption technique that works on multiple layers of the network.
It is the most effective encryption system currently available for wireless
networks.
Key Management
Keys for encrypting the data can be managed either dynamically using 802.1X
authentication or statically using pre-shared keys between the access point
and device. Dynamic key management provides significantly better security
when compared to using static keys.
4-9
Page 48

Setting Up the Access Point
Configuring Security Settings
Deciding Which Security Profile to Use
Table 4-1 shows a summary of available security profiles. Use this table as a
reference when deciding on which security profile best suits your network.
Remember that certain security profiles may require additional software or
hardware. 802.1X, for example, requires a RADIUS server to be configured on
the network. Additionally, not all wireless network cards support WPA.
Choose a security profile that provides the highest level of security while
maintaining compatibility with most, if not all, existing wireless devices on
the network.
Table 4-1. Summary of Wireless Security
Security Profile Client Support Implementation Considerations
None
(NOT RECOMMENDED)
WEP Built-in support on all 802.11a,
WPA-PSK (TKIP) Requires WPA-enabled system
WPA2-PSK (AES) Requires WPAs-enabled
802.1X (RECOMMENDED) Requires WPA-enabled system
Built-in support on all 802.11a,
802.11b, and 802.11g devices
802.11b, and 802.11g devices
and network card driver (native
support provided in Windows
XP)
system and network card driver
(native support provided in
Windows XP)
and network card driver (native
support provided in
Windows XP)
When you have decided which security profile to implement on your network,
refer to the next section, ”
Security Profile”.
No key management, data encryption, or user
authentication is used
• Provides only weak security
• Requires manual key management
• Provides dynamically generated keys that are periodically refreshed
• Provides similar shared key user authentication
• Provides robust security in small networks
• Provides robust security in small networks
• Requires manual management of pre-shared key
• Wireless devices may require hardware upgrade to be
WPA2 compliant
• Provides dynamically generated keys that are periodically refreshed
• Requires configured RADIUS server
• Provides backward compatibility to the original WPA
Configuring the Access Point with Your Preferred
4-10
Page 49

Setting Up the Access Point
Configuring Security Settings
Configuring the Access Point with Your Preferred Security Profile
Wireless security options are available on the Security Settings page. By
default, the Security Settings page shows None as the selected security
profile. When you click other security options, the page refreshes, and then
displays additional options for that security profile.
Note The security profile for each SSID must be set separately. For example, if you
set wireless-a to use WPA2, it will only be applied to wireless-a. If you want
other SSIDs to use WPA2 as well, you need to configure each SSID separately.
CAUTION When access point configuration parameters are changed, wireless clients and
devices may be temporarily disconnected until the new configuration parameters are enabled. This includes any changes to a WLAN or radio parameter.
Using No Security
No security mode transmits data over the wireless connection without any
form of encryption for data privacy. This mode may be appropriate for systems
that provide simple internet and printer access, as on a guest network. It may
also be appropriate where additional security is provided by the use of
encrypted VPN tunnels between the wireless client device and a network VPN
server. If this mode is used, it may be desirable to prevent advertising availability of the network to other devices by configuring the WLAN for closedsystem operation.
CAUTION Use this mode on a sensitive internal network only for: initial setup, testing,
or problem solving; or where VPN connections are mandated to provide endto- end security for the otherwise insecure wireless connection.
4-11
Page 50

Setting Up the Access Point
Configuring Security Settings
Figure 4-5. No Security (Default) Page
To use no security (not recommended):
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click None.
4. Click Apply to save your changes.
Repeat this procedure for every SSID that you want to use no security.
Configuring WEP
Wired Equivalent Privacy (WEP) provides a basic level of security, preventing
unauthorized access to the network and encrypting data transmitted between
wireless clients and the access point. WEP uses static shared keys (fixedlength alphanumeric strings) that are manually distributed to all clients that
want to use the network.
CAUTION WEP has been found to be unreliable and is not be recommended for a high
level of network security. For more robust wireless security, the access point
provides Wi-Fi Protected Access (WPA or WPA2) for improved data encryption and user authentication.
4-12
Page 51

Figure 4-6. WEP Options
To us e WEP :
Setting Up the Access Point
Configuring Security Settings
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click WEP.
4. Under Security Encryption (WEP), configure the authentication type
and encryption strength.
• Authentication: Select Open System to allow association of wire-
less clients and devices without requiring authentication. Select
Shared Key to establish a rudimentary form of user authentication.
Select Automatic if Shared Key authentication is to be supported,
but not required. Default is Automatic.
CAUTION Shared Key mode is unreliable, in that it utilizes the static WEP encryption
key (transmitted openly) for client authentication. This allows the WEP
encryption key to be easily discovered by anyone who might eavesdrop on the
wireless network. If static WEP is configured, it is recommended to select
Open System authentication.
4-13
Page 52

Setting Up the Access Point
Configuring Security Settings
• Encryption Strength: Set the length of the encryption key that will
be used. Select 64 bits or 128 bits. Note that the same size of
encryption key must be supported on all wireless clients and devices.
Default is 64 bits.
5. Under Security Encryption (WEP) Key, enter up to four strings of
character keys. The number of characters required updates automatically
based on how you set Authentication and Encryption Strength.
6. Click Apply to save your changes.
Configuring WPA-PSK (TKIP)
Wi-Fi Protected Access (WPA) is an early version of the 802.11i security
standard. Temporal key integrity protocol (TKIP) is designed for WPA to
enhance WEP.
WPA-PSK (TKIP) employs a pre-shared key (PSK), which is used for an initial
check of credentials and a 128-bit “temporal key”, which combines the client’s
MAC address and a 16-octet initialization vector to produce the encryption
key. This ensures unique key encryption. TKIP uses RC4 to perform the
encryption and changes temporal keys every 10,000 packets and distributes
them, thereby greatly improving the security of the network.
To use this security profile, your wireless clients and devices must support
WPA.
Note If your wireless network has a mix of devices (some support WPA2 and others
support the original WPA), you should use WPA-PSK (TKIP)/WPA2-PSK
(AES). Refer to “
16 for more information.
Configuring WPA-PSK (TKIP) / WPA2-PSK (AES)” on page 4-
4-14
Page 53

Figure 4-7. WPA-PSK (TKIP) Options
To use WPA-PSK (TKIP):
Setting Up the Access Point
Configuring Security Settings
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click WPA-PSK (TKIP).
4. In the Password Phrase box under Security Options (WPA-PSK), enter
a string of at least 8 characters to a maximum of 63 characters. The string
that you enter here will be used as the shared secret key for WPA-PSK.
5. Click Apply to save your changes.
Configuring WPA2-PSK (AES)
WPA2-PSK (AES) employs a pre-shared key (PSK), which is used for an initial
check of credentials, and CCMP, an IEEE802.1X encryption method that uses
the Advanced Encryption Algorithm (AES).
To use this security profile, your wireless clients and devices must support
WPA.
4-15
Page 54

Setting Up the Access Point
Configuring Security Settings
Figure 4-8. WPA2-PSK (AES) Options
To use WPA2-PSK (AES):
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click WPA2-PSK (AES).
4. In the Password Phrase box under Security Options (WPA-PSK), enter
a string of at least 8 characters to a maximum of 63 characters. The string
that you enter here will be used as the shared secret key for WPA-PSK.
5. Click Apply to save your changes.
Configuring WPA-PSK (TKIP) / WPA2-PSK (AES)
This security profile combines WPA-PSK (TKIP) and WPA2-PSK (AES). It uses
a pre-shared key (PSK), which is used for an initial check of credentials, and
a mixed cipher mode of TKIP and AES.
4-16
Page 55

Figure 4-9. WPA-PSK (TKIP) / WPA2-PSK (AES) Options
To use WPA-PSK (TKIP) / WPA2-PSK (AES):
Setting Up the Access Point
Configuring Security Settings
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click WPA-PSK (TKIP) / WPA2-PSK (AES).
4. In the Password Phrase box under Security Options (WPA-PSK), enter
a string of at least 8 characters to a maximum of 63 characters. The string
that you enter here will be used as the shared secret key for WPA-PSK.
5. Click Apply to save your changes.
4-17
Page 56

Setting Up the Access Point
Configuring Security Settings
Configuring WPA (TKIP)
This security profile uses TKIP as the encryption cipher and 802.1X as the
authentication mechanism. In this way, each device is going to utilize a unique
master key to derive the encryption between the access point and device.
Figure 4-10. WPA (TKIP) Options
4-18
To use WPA (TKIP):
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click WPA (TKIP).
4. In the Key Update Interval box, define the time interval (in seconds)
for regenerating a group key.
5. Under RADIUS Server, configure the RADIUS server settings:
• RADIUS Server IP: Type the IP address of the RADIUS server on the
network.
• RADIUS Port: Type the User Datagram Protocol (UDP) port number
used by the RADIUS server for accounting messages. Setting the port
number to zero disables RADIUS authentication.
Page 57

Setting Up the Access Point
Configuring Security Settings
• RADIUS Secret: Type a shared text string used to encrypt messages
between the access point and the RADIUS server. Make sure that the
same text string is specified on the RADIUS Accounting server. Do
not use blank spaces in the string. (Maximum length: 20 characters)
6. Click Apply to save your changes.
Repeat the same procedure for each SSID to which you want to assign WPA
(TKIP) as its security profile.
Configuring WPA2 (AES)
This security profile uses AES as the encryption cipher and 802.1X as the
authentication mechanism. In this way, each device is assigned a unique
master key to derive the encryption between the access point and device, and
the encryption keys can be automatically and periodically changed to further
reduce the possibility of their discovery.
Figure 4-11. WPA2 (AES) Options
To use WPA2 (AES):
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
4-19
Page 58

Setting Up the Access Point
Configuring Security Settings
3. In the Key Update Interval box, define the time interval (in seconds)
for regenerating a group key.
4. Under RADIUS Server, configure the RADIUS server settings:
• RADIUS Server IP: Type the IP address of the RADIUS server on the
network.
• RADIUS Port: Type the User Datagram Protocol (UDP) port number
used by the RADIUS server for accounting messages. Setting the port
number to zero disables RADIUS authentication.
• RADIUS Secret: Type a shared text string used to encrypt messages
between the access point and the RADIUS server. Make sure that the
same text string is specified on the RADIUS Accounting server. Do
not use blank spaces in the string. (Maximum length: 20 characters)
5. Click Apply to save your changes.
Repeat the same procedure for each SSID to which you want to assign WPA2
(AES) as its security profile.
Configuring 802.1X
802.1X is a standard framework for network access control that uses a central
RADIUS server for user authentication. This control feature prevents unauthorized access to the network by requiring an 802.1X client application to
submit user credentials for authentication.
4-20
The 802.1X standard uses the Extensible Authentication Protocol (EAP) to
pass user credentials (either digital certificates, user names and passwords,
or other) from the client to the RADIUS server. Client authentication is then
verified on the RADIUS server before the access point grants the client access
to the network.
Page 59

Figure 4-12. 802.1X Options
To use 802.1X:
Setting Up the Access Point
Configuring Security Settings
1. On the menu, click Security Settings. The Security Settings page
appears.
2. In SSID, select the SSID for which you want to set the security profile.
3. Under Security Options, click 8021.X.
4. Under Security Options (802.1X), configure the RADIUS server settings:
• RADIUS Server IP: Type the IP address of the RADIUS server on the
network.
• RADIUS Port: Type the User Datagram Protocol (UDP) port number
used by the RADIUS server for accounting messages. Setting the port
number to zero disables RADIUS authentication.
• RADIUS Secret: Type a shared text string used to encrypt messages
between the access point and the RADIUS server. Make sure that the
same text string is specified on the RADIUS Accounting server. Do
not use blank spaces in the string. (Maximum length: 20 characters)
5. Click Apply to save your changes.
Repeat the same procedure for each SSID to which you want to assign 802.1X
as its security profile.
4-21
Page 60

Setting Up the Access Point
Controlling Access to the Wireless Network
Controlling Access to the Wireless
Network
You can configure the access point to authenticate client MAC addresses
against a database stored locally on the access point or remotely on a RADIUS
server. Client MAC addresses on the local database can be specified as allowed
or denied access the network. This enables the access point to control which
devices can associate with the access point.
Note Access control settings for each SSID/wireless interface need to be configured
separately. Enabling access control for one SSID will not enable access control
for other SSIDs.
Figure 4-13. Access Control Page
There are two options for setting up access control on the wireless network:
■ Local MAC authentication, and
■ Remote MAC authentication
Note You can only use one type of MAC authentication at any given time.
4-22
Page 61

Controlling Access to the Wireless Network
Before setting up either type of MAC authentication, you should list down the
MAC addresses of the wireless clients and devices that you want to allow or
deny access.
Setting Up the Access Point
Setting Up Local MAC Authentication
Local MAC authentication allows you to add entries to the built-in MAC
authentication database and to take certain actions based on a wireless client’s
MAC address. The MAC list can be configured to allow or deny network access
to specific clients.
Note You can add up to 16 MAC addresses per SSID to the local MAC authentication
database.
To enable local MAC authentication:
1. On the menu, click Access Control.
2. In SSID, select the SSID to which you want to configure access.
3. In MAC Authentication, select Enable.
4. In MAC Authentication Type, select Local.
5. In Access Control, select the access option that you want to configure
for the wireless device. Options include:
• Allow: Click to permit access to all MAC addresses specified in the
[MAC Address List] below.
• Deny: Click to deny access to all MAC addresses specified in the
[MAC Address List] below.
6. In the MAC Address box, enter the MAC or physical address of the
wireless device that you want to allow or deny. A MAC address consists
of six pairs of alphanumeric characters, for example, 00 11 AA 22 BB 33.
7. Click Add. The page refreshes and the MAC address that you entered
appears under MAC Address List.
Repeat steps 5 to 6 for each wireless device that you want to allow or deny.
8. Click Apply to save your changes.
The message Please wait... appears as the address is added to the list. When
the access point has completed the process, the MAC address appears in the
MAC Address List table.
To delete a MAC address from the list, click the Delete button next to it.
4-23
Page 62

Setting Up the Access Point
Controlling Access to the Wireless Network
To disable local MAC authentication:
1. On the menu, click Access Control.
2. In SSID, select the SSID to which you want to configure access.
3. In MAC Authentication, select Disable.
4. Click Apply to save your changes.
Setting Up Remote MAC Authentication
Remote MAC Authentication makes use of a Remote Authentication Dial-in
User Service (RADIUS) server to perform client authentication. RADIUS is an
authentication protocol that uses software running on a central server to
control access to RADIUS-aware devices on the network. An authentication
server contains a database of user credentials for each user that requires
access to the network. It is also used to implement IEEE 802.1X (802.1X)
network access control and Wi-Fi Protected Access (WPA) wireless security.
If a RADIUS is available on the network, you can configure the access point
to perform remote MAC authentication.
Figure 4-14. Remote MAC Authentication Page
4-24
Page 63

Setting Up the Access Point
Configuring Advanced Settings
Note This guide assumes that you have already configured the RADIUS server(s)
to support the access point. The configuration of RADIUS server software is
beyond the scope of this guide. Refer to the documentation provided with the
RADIUS server software.
To enable remote MAC authentication:
1. On the menu, click Access Control.
2. In SSID, select the SSID to which you want to configure access.
3. In MAC Authentication, select Enable.
4. In MAC Authentication Type, select Remote.
5. Under RADIUS Server, enter the following information:
• RADIUS Server IP: The IP address of the RADIUS server on the
network.
• RADIUS Port: The port number used to communicate with the
RADIUS server.
• RADIUS Secret: The shared secret used to gain access to the
RADIUS server.
6. Click Apply to save your changes.
To disable remote MAC authentication:
1. On the menu, click Access Control.
2. In SSID, select the SSID to which you want to configure access.
3. In MAC Authentication, select Disable.
4. Click Apply to save your changes.
Configuring Advanced Settings
Advanced settings include options for enabling and disabling the wireless
radios and Wi-Fi Multimedia (WMM), and for fine tuning the access point’s
radio operation.
4-25
Page 64

Setting Up the Access Point
Configuring Advanced Settings
Figure 4-15. Advanced Settings Page
To configure the advanced settings:
1. On the menu, click Advanced Settings.
2. In Radio, select the radio for which you want to configure the advanced
settings. Available options are 802.11a and 802.11b/g.
3. In Status, click Enable if you want to turn on the radio interface that you
selected in the previous step. Default is Disable.
Note If you have SSIDs that are configured to use the selected radio, you need to
enable the radio interface for the SSIDs to work.
4. In WMM Support, click Enable if you want the access point to prioritize
certain types of traffic above other traffic. When enabled, WiFi Multimedia
(WMM) provides basic Quality of Service (QoS) to wireless network. You
should enable this option if your network requires prioritization for voice
or video traffic (for example, if network users use Voice over IP applications).
5. Configure the following advanced settings for the SSID that you selected:
• RTS Threshold: Sets the packet size threshold at which a Request to
Send (RTS) signal must be sent to a receiving device prior to the
sending device starting communication. The access point sends RTS
frames to a receiving device to negotiate the sending of a data frame.
4-26
Page 65

Setting Up the Access Point
Configuring Advanced Settings
After receiving an RTS frame, the device sends a CTS (clear to send)
frame to notify the sending device that it can start sending data.
(Default is 2347)
• Fragmentation Length: Configures the minimum packet size that
can be fragmented when passing through the access point. Fragmentation of the PDUs (Package Data Unit) can increase the reliability of
transmissions because it increases the probability of a successful
transmission due to smaller frame size. If there is significant interference present, or collisions due to high network utilization, try setting
the fragment size to send smaller fragments. This speeds the retransmission of smaller frames. It is more efficient to set the fragment size
larger if very little or no interference is present because it requires
overhead to send multiple frames. If set to 2346, this feature is
disabled. Range: 256-2346, even numbers. (Default is 2346)
• Beacon Interval: The rate at which beacon frames are transmitted
from the access point. The beacon frames allow wireless clients and
devices to maintain contact with the access point. They may also carry
power-management information. Range: 20-1000 ms (Default is 100)
• DTIM Interval: The Delivery Traffic Indication Message (DTIM)
interval helps keep marginal clients connected by sending “wake up”
frames. Range: 1- 255 (Default is 1).
• Preamble Type: Sets the length of the signal preamble used at the
start of a data transmission. Using a short preamble can increase data
throughput on the access point, but requires all connected devices be
able to support a short preamble. (Default is Long)
– Long: Sets the preamble to long. Using a long preamble ensures
the access point can support all 802.11b and 802.11g devices
– Short: Sets the preamble according to the capability of devices
that are currently associated. Uses a short preamble if all associated devices can support it, otherwise a long preamble is used.
6. Click the Apply button right below the preamble type settings to save
your changes.
Note There are two Apply buttons on the Advanced Settings page: the first is for
the advanced wireless settings and the second is for the SNMP community
settings. Make sure you click the correct Apply button for the settings that
you want to save.
4-27
Page 66

Setting Up the Access Point
Setting the SNMP Community Names
Setting the SNMP Community Names
You can manage the access point from a network management station running
a Simple Network Management Protocol (SNMP) management application,
such as ProCurve Manager.
The access point SNMP agent supports SNMP versions 1 and 2c. Management
access from SNMP v1 or v2c stations is controlled by community names. To
communicate with the access point, an SNMP v1 or v2c management station
must first submit a valid community name for authentication.
The default community names are public for read-only access and private for
read/write access. If you intend to support SNMP v1 or v2c managers, you
should change the default community names to prevent unauthorized access.
Figure 4-16. SNMP Community Section on the Advanced Settings Page
4-28
SNMP Community
Section
To change the default SNMP community names:
1. On the menu, click Advanced Settings under Setup. The Advanced
Settings page appears.
2. Configure the SNMP community settings under the SNMP Community
section located at the lower portion of the page.
Page 67

Setting the SNMP Community Names
Setting Up the Access Point
• To establish a public read-only SNMP community, type a name text
string to replace the default community name (public) in the
Read Only text field.
• To establish a private read-write SNMP community, type a name text
string to replace the default community name (private) in the
Read/Write text field.
3. Click the Apply button under the SNMP Community section to save your
changes and activate the new SNMP community names.
4-29
Page 68

Page 69

Managing the Access Point
This chapter describes management tasks that you may periodically perform,
including changing the management password and updating the software.
Topics discussed in this chapter include:
■ Viewing Device Information
■ Changing the Management Password
■ Updating the Access Point Software
■ Viewing the List of Connected Devices
■ Backing Up and Restoring Configuration
■ Rebooting the Access Point
Viewing Device Information
5
Device information is available on the Information page, which is the default
home page that loads after you log on to the Web interface. To access the
Information page when you are already logged on, click Information on the
menu.
5-1
Page 70

Managing the Access Point
Viewing Device Information
Figure 5-1. Information Page
The Information page displays three types of device information:
■ Access Point Information
• MAC Address: The physical layer address for the Ethernet port
interface
• Region: Shows the country/region that was set on the Basic Settings
page
• Software Version: Shows the version number for the runtime soft-
ware. Software version is shown as WM.XX.XX, where XX.XX is the
version number (for example, WM.01.02).
■ Current IP Settings
• IP Address: Shows the IP address of the management interface for
this device
• Subnet Mask: Shows the subnet mask configured for the manage-
ment interface
• Default Gateway: Shows the IP address of the next-hop gateway
node for network traffic that needs to be able to reach off-subnet
destinations.Gateway address
• DHCP Client: Shows whether the built-in DHCP client is Enabled or
Disabled.
5-2
Page 71

Changing the Management Password
■ Radio Settings: Shows the status of each radio interface and a summary
of their configuration settings, including WMM Support, RTS Threshold,
Beacon Interval, and other radio settings.
■ Current Wireless Settings: Shows a table that lists all configured SSIDs on
the access point and the wireless modes, channels, and security settings
that they use.
Managing the Access Point
Changing the Management Password
Management access to the Web interface is controlled through an administrator password. To prevent unauthorized users from accessing the Web
interface and modifying the access point's settings, the interface is passwordprotected.
The default manager user name is admin and the default password is password.
CAUTION You should change the default Web interface password immediately after
your first logon. This will help prevent unauthorized users from logging on to
the Web interface and changing the access point settings to compromise your
network.
Figure 5-2. Change Password Page
5-3
Page 72

Managing the Access Point
Changing the Management Password
To change the default Web interface password:
1. On the menu, click Change Password. The Change Password page
appears.
2. In Set Password, type your new password.
Note The password is case-sensitive and must be between 1 and 32 alphanumeric
characters long.
3. In Repeat New Password, type your new password again to confirm.
4. In Restore Default Password, click No.
5. Click Apply to save your changes.
Your new password is instantly applied, and the logon dialog box appears after
you save your new password. Enter your new password in the password box
to log back onto the Web interface.
5-4
Page 73

Updating the Access Point Software
Managing the Access Point
If You Forget Your Password
If you forget your password, you will need to reset the access point to factory
default, and then log back on to the access point using the default user name
(admin) and password (password).
For detailed information, refer to “
on page 6-6
.
Restoring Factory Default Configuration”
Updating the Access Point Software
The software update function allows you to install on the access point any
new access point software that HP may release. To install the new software,
you will first need to download the software from the HP Web site to the
management computer.
Before performing a software update, take note of the current software
version (shown on the Information page). The software version is shown as
WM.XX.XX, where XX.XX is the version number (for example, WM.01.02). You
need to know this to be able to verify that the update has been completed
successfully.
Where to Download Software Updates
The ProCurve support site periodically provides access point software
updates through the ProCurve Web site (www.procurve.com). At
www.procurve.com, select “Software updates”. Under “Latest software”,
select “Wireless access points”. Check for available software updates for
ProCurve Wireless Access Point 10ag.
5-5
Page 74

Managing the Access Point
Updating the Access Point Software
Update Precautions
CAUTION Here are a few things that you can do to ensure that the software update
process will be completed successfully:
■ Do not use your Web browser until the update process has completed.
■ Do not interrupt the Web browser by closing the window, clicking a link,
or loading a new page.
■ Do not interrupt the software update by turning off your computer or the
access point.
After a software update, the access point will automatically reboot and apply
the updated code.
Note Updating the software will not change the current configuration of the access
point. The access point configuration is contained in a separate file that can
also be transferred, for example, for archive purposes or to be used in another
access point of the same model. You should save a copy of the configuration
file before updating your access point software. See “
Restoring Configuration” on page 5-8 for information on saving the access
point’s configuration file.
Backing Up and
Figure 5-3. Update Software Page
5-6
Page 75

Viewing the List of Connected Devices
Managing the Access Point
Software Update Procedure
To update the access point software:
1. On the menu, click Update Software under Management. The Update
Software page appears.
2. Click Browse. The Choose File dialog box appears.
3. Go to the folder where you saved the software update file, select the file,
and then click Open. The Choose File dialog box disappears.
4. Click Update. A progress bar appears.
When the software update is complete, the access point reboots itself, and
then redirects you to the Information page.
5. Check the value for Software Version and verify that it shows a later
version than what was installed before the update.
Viewing the List of Connected Devices
You can view which wireless devices are connected to the access point
anytime by accessing the Connected Devices page on the Web interface.
To access the page, click Connected Devices on the menu. A table appears,
which lists the following information about each associated wireless device:
■ MAC address: Displays the MAC or physical address of the associated
wireless device
■ Channel: Displays the current radio channel on which the wireless device
is receiving broadcast signal
■ Data rate: Displays the transmission speed at which the wireless device
is receiving data from the access point. Data rates shown on this page will
depend on the type of associated wireless device. 802.11a and 802.11g
devices can have data rates up to 54Mbps, while 802.11b devices can only
have up to 11Mbps.
■ RSSI: Displays the received signal strength of the wireless device on the
current wireless channel. The higher the RSSI, the better the signal. The
strongest signal will have an RSSI of 100.
5-7
Page 76

Managing the Access Point
Backing Up and Restoring Configuration
Figure 5-4. Connected Devices Page
5-8
Backing Up and Restoring Configuration
To back up the current access point configuration:
1. On the menu, click Back Up Settings. The Back Up Settings page
appears.
2. Click Back Up under Save a Copy of Current Settings. A browser dialog
box appears, as your browser attempts to download the configuration file
from the access point.
3. Click Save. The Save As dialog box appears.
4. Choose a location where to save the configuration file and, if you want,
change the file name. The default file name is AP10ag_backup.cfg. If
you are changing the file name, you should include the current date in the
file name for ease of identification.
5. Click Save.
6. Start Windows Explorer, and then browse to the location where you save
the configuration file, and then verify that it has been downloaded
successfully.
Page 77

Managing the Access Point
Rebooting the Access Point
To restore a backup configuration:
1. On the menu, click Back Up Settings. The Back Up Settings page
appears.
2. Click Browse under Restore Saved Setting from a File.
3. When the Choose File dialog box appears, browse to the location where
you saved the backup configuration file.
4. Select the backup file (default file name is AP10ag_backup.cfg), and
then click Open.
5. Click Restore. A confirmation message appears.
CAUTION Restoring settings from a backup configuration file will overwrite all current
access point settings, including the IP address, password, and access control.
Make sure that you are restoring the correct backup file.
6. Click OK to restore settings from the backup file and overwrite the
current settings. The message Please wait... appears as the access point
restores the backup configuration file. When the access point has
completed the restore process, the following message appears:
Access Point is rebooting......
PLEASE WAIT until re-directed to Information page.
The browser refreshes, and the Information page appears.
Rebooting the Access Point
If you feel that the access point is not operating normally, try rebooting the
device. This clears memory resources in use and can help restore normal
operation.
Note that rebooting the access point will temporarily disconnect any wireless
clients and devices that are connected to it. If you have users on the network
that are connected to the Internet through the access point, they will be
temporarily disconnected. Their connection will be restored as soon as the
access point has completed rebooting.
You can reboot the access point by pressing the Reset to Default button (on
the rear of the access) for one to three seconds. Alternatively, you can click
Reboot Access Point on the Web interface to perform the same action.
5-9
Page 78

Managing the Access Point
Rebooting the Access Point
Refer to the procedure below for instructions on how to reboot the access
point from the Web interface.
Figure 5-5. Reboot Page
5-10
To reboot the access point:
1. On the menu, click Reboot Access Point.
2. In Reboot access point, click Yes.
3. Click Apply. A confirmation message appears.
4. Click OK. The following message appears:
Access Point is rebooting......
PLEASE WAIT until re-directed to Information page.
When the access point has rebooted, the logon dialog box appears.
5. Enter your user name and password to log back on to the Web interface.
Page 79

Troubleshooting
This chapter describes how to troubleshoot your ProCurve Wireless
Access Point 10ag. Note that this document describes troubleshooting mostly
from a hardware perspective.
This chapter describes the following:
■ Basic Troubleshooting Tips
■ Diagnosing with the LEDs
■ Hardware Diagnostic Tests
■ Restoring Factory Default Configuration
■ HP Customer Support Services
Basic Troubleshooting Tips
6
Most problems are caused by the following situations. Check for these items
first when starting your troubleshooting:
■ Connecting to devices that have a fixed full-duplex configuration.
By default, the RJ-45 port uses auto-negotiation to determine the duplex
mode. That is, when connecting to attached devices, the access point will
operate in one of two ways to determine the link speed and the communication mode (half duplex or full duplex):
• If the connected device is also configured to use auto-negotiation, the
access point will automatically negotiate both link speed and communication mode.
• If the connected device has a fixed configuration, for example
100 Mbps, at half or full duplex, the access point will automatically
sense the link speed, but will default to a communication mode of half
duplex.
Because the Access Point 10ag behaves in this way (in compliance with
the IEEE 802.3-2005 standard), if a device connected to the access point
has a fixed configuration at full duplex, the device will not connect
correctly to the access point. The result will be high error rates and very
inefficient communications between the access point and the device.
6-1
Page 80

Troubleshooting
Basic Troubleshooting Tips
All devices connected to the Access Point 10ag should be configured to
auto-negotiate. To correct this problem you have to manually set the
access point’s RJ-45 port to match the duplex mode used by the attached
device.
■ Faulty or loose cables. Look for loose or obviously faulty connections.
If the cables appear to be OK, make sure the connections are secure. If
that does not correct the problem, try a different cable.
■ Non-standard cables. Non-standard and miswired cables may cause
network collisions and other network problems, and can seriously impair
network performance. Use a new correctly-wired cable or compare your
cable to the cable in Appendix B
, Access Point Port and Network Cables
for pinouts and correct cable wiring. A category 5 cable tester is a
recommended tool for every 100Base-TX network installation.
■ Improper network topologies. It is important to make sure you have a
valid network topology. Common topology faults include excessive cable
length and excessive repeater delays between end nodes. If you have
network problems after recent changes to the network, change back to
the previous topology. If you no longer experience the problems, the new
topology is probably at fault. A sample network topology is shown at the
end of Chapter 2
■ Mobile users cannot connect to the network. Make sure that the
.
access point and wireless clients and devices are configured with compatible security settings. Check to ensure that the wireless device is within
the maximum range supported by the access point. Also verify that the
wireless device has been configured with an IP address compatible with
the attached network, either manually or via DHCP.
6-2
For more information on possible network problems and their solutions, see
“Technical Support” and “Reference Library” pages at www.procurve.com.
Page 81

Diagnosing with the LEDs
Troubleshooting
Diagnosing with the LEDs
Table 6-1 shows LED patterns on the access point that indicate problem
conditions.
1. Check in the table for the LED pattern that you see on your access point.
2. Refer to the corresponding diagnostic tip on the next few pages.
Table 6-1. LED Error Indicators
LED Pattern Indicating Problems
Power LED Radio LEDs LAN LED
Off with power cord plugged in * * 1
Off without power cord plugged in,
but linked to a PoE source
Prolonged on or off during
initialization
* This LED is not important for the diagnosis.
†
Initialization takes between 30 seconds and one minute after a power on or reset.
†
On Off * 4
On * Off with cable
On * On, but the port is not
Prolonged on or off
**2
Prolonged on or off
during
initialization
during initialization
†
communicating
connected
Diagnostic
†
Tip s
3
5
6
6-3
Page 82

Troubleshooting
Diagnosing with the LEDs
Diagnostic Tips
Tip Problem Solution
1 The access point
is not plugged
into an active AC
power source, or
the access
point’s AC power
adapter may
have failed.
2 The access point
is not receiving
power from the
PoE source.
3 The access point
has experienced
a software
failure during
initialization.
1. Verify that the power cord is plugged into an active power source and to the access
point's AC power adapter. Make sure these connections are secure.
2. Try power-cycling the access point by unplugging and plugging the power cord back
in.
3. If the Power LED is still not on, verify that the AC power source works by plugging
another device into the outlet. Or try plugging the access point into a different outlet
or try a different power cord.
If the power source and power cord are OK and this condition persists, the access point’s
AC power adapter may have failed. Call your HP-authorized network reseller, or use the
electronic support services from HP to get assistance.
1. Verify that access point’s 10/100Base-TX port is attached to a PoE source device.
2. Verify that the PoE source device is powered on, and that the PoE function has been
administratively enabled on the source port attached to the access point.
After a power on or reset, the LEDs indicate stages of the system initialization. If there is
a software failure during initialization, the LED pattern indicates at which stage the failure
occurred. The normal LED sequence during initialization is as follows:
Stage 1. Power LED on. System initialization has started.
Stage 2. Both LAN LEDs blink once. The boot ROM has successfully initialized.
Stage 3. One LAN LED on. The operating system kernel has successfully loaded.
Stage 4. LAN LED on only. The operating system is mounting the file system.
Stage 5. LAN and 11a/b/g LEDs on. Radio drivers have been successfully loaded.
Stage 6. LAN, 11a/b/g, and 11b/g LEDs on. The access point software is initializing.
Stage 7. Normal LED operation. Initialization has completed successfully.
The entire initialization sequence takes between 30 seconds (normal reset) and one
minute (factory default reset). If one of the above LED patterns display longer than one
minute, a failure has occurred. Do the following:
1. Reset the access point by power cycling the access point.
2. If the fault indication reoccurs, take note of the LED pattern and contact your HPauthorized network reseller, or use the electronic support services from HP to get
assistance.
4 Wireless link has
been
administratively
disabled.
5 The
10/100Base-TX
network
connection is not
working
properly.
6-4
Verify that the wireless port has not been disabled through an access point configuration
change. You can use the Web browser interface to determine the state of the wireless
port and re-enable the port if necessary. Also verify that the country/region code has
been set.
Try the following procedures:
• Verify that both ends of the cabling, at the access point and the connected device, are
connected properly.
• Verify the connected device and access point are both powered on
correctly.
• Verify duplex operation (see page 6-1).
• If these procedures don’t resolve the problem, try using a different cable.
and operating
Page 83

Hardware Diagnostic Tests
Troubleshooting
Hardware Diagnostic Tests
Testing the Access Point by Resetting It
If you believe that the access point is not operating correctly, you can reset
the access point. To reset the access point, either:
■ Unplug and plug in the power cord (power-cycling).
■ Press the Reset to Default button on the back of the access point for one
to three seconds (until the LEDs start to blink rapidly).
CAUTION If you press the Reset to Default button for more than five seconds, you will
reset the board and reload the factory default settings. See “
Default Configuration” on page 6-6.
Power-cycling the access point and pressing the Reset to Default (button for
one to three seconds) both cause the access point to perform its system
initialization, which normally resolves any temporary operational problems.
Restoring Factory
Checking the Access Point’s LEDs
The system initialization is successful when the Power LED is on and the other
LEDs are in a normal operating state after approximately one minute. If the
LED pattern is different than this for longer than one minute, there may be a
problem with the access point.
See “
Diagnosing with the LEDs” on page 6-3 for information on interpreting
the LED patterns.
Testing Twisted-Pair Cabling
Network cables that fail to provide a link or provide an unreliable link between
the access point and the connected network device may not be compatible
with the IEEE 802.3 Type 10Base-T, or 100Base-TX standards. The twistedpair cables attached to the Access Point 10ag must be compatible with the
appropriate standards. To verify that your cable is compatible with these
standards, use a qualified cable test device.
6-5
Page 84

Troubleshooting
Restoring Factory Default Configuration
Testing Access Point-to-Device Network Communications
You can perform the following communication test to verify that the network
is operating correctly between the access point and any connected device that
can respond correctly to the communication test.
■ Ping Test -- a network layer test used on IP networks that sends test
packets to any device identified by its IP address
Testing End-to-End Network Communications
Both the access point and the cabling can be tested by running an end-to-end
communications test -- a test that sends known data from one network device
to another through the access point. You can run a PING test to verify that the
entire communication path between the two network devices is functioning
correctly.
Restoring Factory Default Configuration
As part of your troubleshooting process on the Access Point 10ag, it may
become necessary to return the access point’s configuration to its factory
default settings. This process momentarily interrupts the access point’s operation and reboots the access point. When restoring the factory default configuration, all settings are cleared, including the manager password and any IP
address.
CAUTION Restoring factory defaults removes all access point configuration changes that
you have made from the factory default settings. This includes the IP address,
password, access control list, and radio interface settings. Returning the
configuration of these features to their factory default settings may result in
network connectivity issues.
If the access point has a valid configuration, and you are restoring the factory
default settings for a reason other than configuration problems, you should
save the access point configuration prior to performing the factory default
reset. Then, after the reset and resolution of the original problem, you can
restore the saved configuration to the access point.
6-6
Page 85

Restoring Factory Default Configuration
Troubleshooting
You can restore factory default configuration either by pressing the Reset to
Default button on the rear panel, or by clicking the Erase button on the Back
Up Settings page.
To restore to factory default using the Reset to Default button:
1. Using a pointed object such as the tip of a ballpoint pen or a straightened
clip, press the Reset to Default button for more than five seconds. The
LEDs flash rapidly (about 10 times per second).
2. As soon as the LEDs (except the Power LED) shut off, release the Reset
to Default button.
The access point resets to factory defaults and reboots.
To restore to factory default from the Web interface:
1. Log on to the Web interface.
2. On the menu, click Back Up Settings. The Back Up Settings page
appears.
3. Under Revert to Factory Default Settings, click Erase. The following
confirmation message appears:
Loading the Factory Default Settings will erase all the current settings.
4. Click OK to continue.
The following message appears:
Please wait....
Access Point is rebooting......
PLEASE WAIT until re-directed to Information page.
When the access point has completed restoring its settings to factory default,
the Web interface refreshes and displays the Information page. If the access
point was using an IP address other than the default, you may see a Page Not
Found message in your browser. This is because the access point has already
reverted to its default IP address, 192.168.1.14, which may be incompatible with
your current network settings.
6-7
Page 86

Troubleshooting
HP Customer Support Services
HP Customer Support Services
If you are still having trouble with your access point, Hewlett-Packard offers
support 24 hours a day, seven days a week through the use of a number of
automated electronic services. The ProCurve Networking Web site,
www.procurve.com, provides up-to-date support information under “Technical support.”
Additionally, your HP-authorized network reseller can provide you with assistance, both with services that they offer and with services offered by HP.
Before Calling Support
To make the support process most efficient, before calling your networking
dealer or HP Support, you first should retrieve the following information:
Information Item Information Location
• product identification • the front of the access point,
• details about the access point’s status
including the software version and a
copy of the access point configuration
• copy of your network topology map, including network addresses assigned to
the relevant devices
Access Point 10ag (J9140A or J9141A)
• Web interface: Information page
• your network records
6-8
Page 87

Specifications
Physical
Width: 178 mm
Depth: 103 mm
Height: 34 mm
Weight: 285 g
A
Electrical
Adapter
AC voltage: 100-240 volts, 0.5A, 50/60 Hz
DC voltage: 12 volts, 1.25A (max)
Power consumption: 15 watts (max)
Note: Power can also be provided to the access point through the Ethernet
port based on IEEE 802.3af Power over Ethernet (PoE) specifications. The
access point is a Class 3 device, that is, the maximum power required is in the
range of 6.49 to 12.95 watts. When both PoE is provided and the adapter is
plugged in, PoE is turned off.
Japanese Power Cord Statement
A-1
Page 88

Specifications
Environmental
Operating Non-Operating
Temperature: 0°C to 40°C (32°F to 104°F) PoE mode -40°C to 70°C (-40°F to 158°F)
Relative humidity:
(non-condensing)
Maximum altitude: 3.05 Km (10,000 ft)
15% to 95% 10% to 90%
Connectors
■ The 10/100 Mbps RJ-45 twisted-pair port is compatible with the
IEEE 802.3u 100Base-TX and IEEE 802.3 Type 10Base-T standards.
Note: To provide Power over Ethernet to the access point, all 4 pairs of
wires must be connected for any network cable attached to this port.
Safety
Complies with:
■ IEC 60950-1: 2001
■ EN 60950-1: 2002
■ UL 60950-1 1st Ed.
■ CAN/CSA-C22.2 No. 60950-1-03
EMC Compliance (Class B)
A-2
Complies with:
■ FCC Part 15.107 and 15.109
■ ICES-003 (Canada)
■ VCCI
Radio Signal Certification
Complies with:
■ FCC Part 15, Subpart C and E
■ RSS-210 (Canada), Issue 7 (June 2007)
■ EN300.328 v1.7.1 (2006-10)
■ EN 301.893 V1.2.3 (2003-08)
Page 89

Specifications
■ ARIB RCR STD-T66 (Ch 1~13), STD-33 (Ch 14), STD-71 (802.11a)
■ DGT LP0002 (Taiwan)
Immunity
■ EN 301.489-1 v1.6.1 (2005-09)
■ EN 301.489-17 V1.2.1 (2002-08)
■ EN 60601-1-2
Wireless
802.11a
Radio Standard: IEEE 802.11a
Radio Technology: Orthogonal Frequency Division Multiplexing (OFDM)
Data Rate: 6, 9, 12, 18, 24, 36, 48, 54 Mbps per channel
Operating Frequency: 5.15 ~ 5.25 GHz (lower band) US, Canada, Japan, ETSI
5.25 ~ 5.35 GHz (middle band) Taiwan, Japan, ETSI
5.725~5.85 GHz (upper band) US, Canada, Taiwan
5.47 ~ 5.725 GHz ETSI
Maximum Channels: FCC/IC/NCC: 9, ETSI: 19, MKK: 8
Modulation Type: BPSK, QPSK, 16QAM, 64QAM
Media Access Protocol: CSMA/CA with ACK
Transmit Output Power: 18 dBm (max)
802.11b/g
Radio Standard: IEEE 802.11b/g
Radio Technology: Direct Sequence Spread Spectrum (DSSS)
Orthogonal Frequency Division Multiplexing (OFDM)
Data Rate: 1, 2, 5.5, 6, 9, 11, 12, 18, 24, 36, 48, 54 Mbps per channel
Operating Frequency: 2.4 ~ 2.4835 GHz (US, Canada, Taiwan, ETSI)
2.4 ~ 2.497 GHz (Japan)
Maximum Channels: FCC/IC/NCC: 1-11, ETSI: 1-13, MKK: 1-13 (802.11g), 1-14 (802.11b)
Modulation Type: BPSK, QPSK, 16QAM, 64QAM / OFDM, BPSK, QPSK, CCK / DSSS
Media Access Protocol: CSMA/CA with ACK
Transmit Output Power: 18 dBm (max)
A-3
Page 90

Specifications
Antenna Type and Gain
Antenna Type: Dipole
Antenna Gain: 2.4GHz ~ 2.5GHz 1.78 (dBi)
5.15GHz ~ 5.25GHz 1.65 (dBi) FCC/IC/MKK/ETSI
5.25GHz ~ 5.35GHz 1.4 (dBi) ETIS/ECC/MKK
5.470GHz ~ 5.725GHz 2.28 (dBi) ETSI
5.725GHz ~ 5.85GHz 1.78 (dBi) FCC/IC/NCC
Receiver Sensitivity
Radio ProCurve Access Point 10ag NA (J9140A) ProCurve Access Point 10ag (J9141A)
802.11b
(typical)
802.11g
(typical)
802.11a
(typical)
11Mbps @ -87dBm; 5.5Mbps @ -91dBm;
2Mbps @ -92dBm; 1Mbps @ -97dBm
54Mbps @ -74dBm; 48Mbps @ -75dBm;
36Mbps @-80dBm; 24Mbps @ -83dBm;
18Mbps @-86dBm; 12Mbps @ -88dBm;
9Mbps @ -90dBm; 6Mbps @ -91dBm
54Mbps @ -70dBm; 48Mbps @ -72dBm;
36Mbps @-78dBm; 24Mbps @ -81dBm;
18Mbps @-85dBm; 12Mbps @ -87dBm;
9Mbps @ -89dBm; 6Mbps @ -90dBm
11Mbps @ -87dBm; 5.5Mbps @ -89dBm;
2Mbps @ -91dBm; 1Mbps @ -94dBm
54Mbps @ -75dBm; 48Mbps @ -77dBm;
36Mbps @ -81dBm; 24Mbps @ -84dBm;
18Mbps @-87dBm; 12Mbps @ -88dBm;
9Mbps @ -89dBm; 6Mbps @ -90dBm
54Mbps @ -70dBm; 48Mbps @ -72dBm;
36Mbps @-78dBm; 24Mbps @ -81dBm;
18Mbps @-84dBm; 12Mbps @ -87dBm;
9Mbps @ -88dBm; 6Mbps @ -89dBm
A-4
Page 91

Access Point Port and Network Cables
This appendix includes access point connector information and network
cable information for cables that should be used with the Access Point 10ag,
including minimum pin-out information and specifications for twisted-pair
cables.
Note Incorrectly wired cabling is the most common cause of problems for LAN
communications. You should work with a qualified LAN cable installer for
assistance with your cabling requirements.
Access Point Ports
The fixed RJ-45 10/100Base-TX port on the access point accepts 100-ohm
unshielded twisted-pair cable with RJ-45 connectors as described on the next
page.
B
Twi sted- Pair C ables
10 Mbps Operation Category 5 100-ohm unshielded twisted-pair (UTP),
complying with IEEE 802.3 Type 10Base-T specifications,
fitted with RJ-45 connectors
100 Mbps Operation Category 5 100-ohm UTP cable, complying with IEEE
802.3u 100Base-TX specifications, fitted with RJ-45 connectors
B-1
Page 92

Access Point Port and Network Cables
Twisted-Pair Cable/Connector Pin-Outs
Twisted-Pair Cable/Connector Pin-Outs
The access point includes one 10/100Base-TX port. This port uses Auto-MDIX,
which means that you can use either straight-through or crossover twistedpair cables to connect the access point to a switch.
Other Wiring Rules:
■ All twisted-pair wires used for 10 Mbps, and 100 Mbps operation must be
twisted through the entire length of the cable. The wiring sequence must
conform to EIA/TIA 568-B (not USOC). See “Twisted-Pair Cable Pin
Assignments” later in this appendix for a listing of the signals used on each
pin.
■ For 10 Mbps connections to the ports, you can use Category 5 unshielded
twisted-pair cable, as supported by the IEEE 802.3 Type 10Base-T standard.
■ For 100 Mbps connections to the ports, use 100-ohm Category 5 UTP cable
only, as supported by the IEEE 802.3u Type 100Base-TX standard.
■ To provide Power over Ethernet to the access point, all 4 pairs must be
connected for any network cable attached to this port; the cable must
meet ISO/DIS 11801 Class D requirements and IEEE 802.3af requirements.
B-2
Page 93

Access Point Port and Network Cables
Twisted-Pair Cable/Connector Pin-Outs
Straight-Through Twisted-Pair Cable for 10 Mbps or 100 Mbps Network Connections
Because the 10/100 port on the access point supports Auto-MDIX operation,
you can use either a “straight-through” or “crossover” cable for network
connections to PCs, servers, hubs, or switches.
Cable Diagram
Note Pins 1 and 2 on connector “A” must be wired as a twisted pair to pins 1 and 2
on connector “B”.
Pins 3 and 6 on connector “A” must be wired as a twisted pair to pins 3 and 6
on connector “B”.
Pins 4, 5, 7, and 8 are not used for transmitting or receiving data, although they
must be wired straight-through in the cable to support Power over Ethernet.
.
Pin Assignments
Access Point End (MDI) Hub or Switch Port, or Other
MDI-X Port End
Signal Pins Pins Signal
receive +
receive transmit +
transmit -
1
2
3
6
1
2
3
6
transmit +
transmit receive +
receive -
B-3
Page 94

Access Point Port and Network Cables
Twisted-Pair Cable/Connector Pin-Outs
Crossover Twisted-Pair Cable for 10 Mbps or 100 Mbps Network Connection
Because the 10/100 port on the access point supports Auto-MDIX operation,
you can use either a “straight-through” or “crossover” cable for network
connections to PCs, servers, hubs, or switches.
Cable Diagram
Note Pins 1 and 2 on connector “A” must be wired as a twisted pair to pins 3 and 6
on connector “B”.
Pins 3 and 6 on connector “A” must be wired as a twisted pair to pins 1 and 2
on connector “B”.
Pins 4, 5, 7, and 8 are not used for transmitting or receiving data, although they
must be wired straight-through in the cable to support Power over Ethernet.
.
Pin Assignments
Access Point End (MDI) Computer, Transceiver, or
Other MDI Port End
Signal Pins Pins Signal
receive +
receive transmit +
transmit -
B-4
1
2
3
6
6
3
2
1
transmit transmit +
receive receive +
Page 95

Safety and EMC Regulatory Statements
Safety and EMC Regulatory Statements
Safety Information
Documentation reference symbol. If the product is marked with this
!
symbol, refer to the product documentation to get more information
about the product.
Safety Information
C
WARNING A WARNING in the manual denotes a hazard that can cause injury or
CAUTION A CAUTION in the manual denotes a hazard that can damage the
Grounding
Depending on the product model, your product will be classified either as a
safety class I or safety class II compliant device. Class I devices require a
connection to earth ground (3-terminal plug), while class II devices incorporate
a 2-terminal plug.
Class I: There must be an uninterruptible safety earth ground from the main
power source to the product's power cord or supplied power cord set.
Whenever it is likely that the protection has been impaired, disconnect the
power cord until the ground has been restored.
Class II: Safety class II-compliant devices include supplemental insulation to
protect against electric shock, and do not require a connection to earth
ground.
For LAN connections:
■ If your LAN covers an area served by more than one power distribution
system, be sure their safety grounds are securely interconnected.
death.
equipment or create a non-compliant condition.
Do not proceed beyond a WARNING or CAUTION notice until you have
understood the hazardous conditions and have taken appropriate steps.
C-1
Page 96

Safety and EMC Regulatory Statements
Informations concernant la sécurité
■ LAN cables may occasionally be subject to hazardous transient voltages
(such as lightning or disturbances in the electrical utilities power grid).
Handle exposed metal components of the network with caution.
■ This product and all interconnected equipment must be installed indoors
within the same building, including all associated LAN connections
as described by Environment A of the IEEE 802.3af standard.
Servicing
There are no user-serviceable parts inside this product. Any servicing, adjustment, maintenance, or repair must be performed only by service-trained
personnel.
This product does not have a power switch; it is powered on when the power
cord is plugged in.
Informations concernant la sécurité
Symbole de référence à la documentation. Si le produit est marqué
!
de ce symbole, reportez-vous à la documentation du produit afin
d'obtenir des informations plus détaillées.
C-2
WARNING Dans la documentation, un WARNING indique un danger susceptible
d'entraîner des dommages corporels ou la mort.
CAUTION Un texte de mise en garde intitulé CAUTION indique un danger
susceptible de causer des dommages à l'équipement.
Ne continuez pas au-delà d'une rubrique WARNING ou CAUTION
avant d'avoir bien compris les conditions présentant un danger
et pris les mesures appropriées.
Bases
Suivant le modèle, votre produit sera classé comme un équipement conforme
à la classe de sécurité I ou II. Les équipements de la classe I doivent être
raccordés à la terre (fiche 3 broches), tandis que les équipements de la classe
II intègrent une fiche 2 broches.
Classe I : La source d'alimentation principale doit être munie d'une prise de
terre de sécurité installée aux bornes du câblage d'entrée, sur le cordon
d'alimentation ou le cordon de raccordement fourni avec le produit. Lorsque
cette protection semble avoir été endommagée, débranchez le cordon
d'alimentation jusqu'à ce que la mise à la terre ait été réparée.
Page 97

Safety and EMC Regulatory Statements
Hinweise zur Sicherheit
Classe II : Les équipements conformes à la classe II incluent une isolation
supplémentaire pour la protection contre les chocs électriques et ne doivent
pas forcément être raccordés à la terre.
Pour les connexions LAN :
■ Si votre réseau local s'étend sur une zone desservie par plus d'un système
de distribution de puissance, assurez-vous que les prises de terre de
sécurité sont convenablement interconnectées.
■ Les câbles de réseaux locaux peuvent occasionnellement être soumis
à des surtensions transitoires dangereuses (telles que la foudre ou des
perturbations dans le réseau d'alimentation public). Manipulez les
composants métalliques du réseau avec précaution.
■ Ce produit et tous les équipements interconnectés doivent être installés
à l'intérieur, dans le même bâtiment, y compris toutes les connexions LAN,
comme indiqué dans la norme IEEE 802.3af (Environnement A).
Dépannage
Aucune pièce à l'intérieur de ce produit ne peut être réparée par l'utilisateur.
Tout dépannage, réglage, entretien ou réparation devra être
confié exclusivement à un personnel qualifié.
Cet appareil ne comporte pas de commutateur principal ; la mise sous tension
est effectuée par branchement du cordon d'alimentation.
Hinweise zur Sicherheit
Symbol für Dokumentationsverweis. Wenn das Produkt mit diesem
!
WARNING Eine WARNING in der Dokumentation symbolisiert eine Gefahr,
CAUTION CAUTION in der Dokumentation symbolisiert eine Gefahr, die dis
Symbol markiert ist, schlagen Sie bitte in der Produktdokumentation
nach, um mehr Informationen über das Produkt zu erhalten.
die Verletzungen oder sogar Todesfälle verursachen kann.
Gerät beschädigen kann.
Fahren Sie nach dem Hinweis WARNING oder CAUTION erst
fort, nachdem Sie den Gefahrenzustand verstanden und die
entsprechenden Maßnahmen ergriffen haben.
C-3
Page 98

Safety and EMC Regulatory Statements
Hinweise zur Sicherheit
Erdung
Je nach Produktmodell wird Ihr Produkt als Gerät nach Sicherheitsklasse I
oder Sicherheitsklasse II eingestuft. Für Geräte der Klasse I ist eine Verbindung mit Erdung (3-poliger Stecker) erforderlich, während Geräte der Klasse
II einen 2-poligen Stecker enthalten.
Klasse I: Es muss eine ununterbrochene Sicherheitserdung von der Hauptstromquelle bis zum Stromversorgungskabel des Produkts oder dem mitgelieferten Stromversorgungskabel vorhanden sein. Wenn es wahrscheinlich ist,
dass der Schutz nicht mehr besteht, trennen Sie das Stromkabel, bis die
Erdung wiederhergestellt wurde.
Klasse II: Geräte gemäß Sicherheitsklasse II weisen eine Zusatzisolierung
zum Schutz vor Stromschlägen auf und erfordern keine Erdungsverbindung.
Für LAN-Verbindungen:
■ Wenn Ihr LAN ein Gebiet umfasst, das von mehr als einem Stromvertei-
lungssystem beliefert wird, müssen Sie sich vergewissern, dass die Sicherheitserdungen fest untereinander verbunden sind.
■ LAN-Kabel können gelegentlich gefährlichen Übergangsspannungen
ausgesetzt werden (beispielsweise durch Blitz oder Störungen in dem
Starkstromnetz des Elektrizitätswerks). Bei der Handhabung exponier-ter
Metallbestandteile des Netzwerkes Vorsicht walten lassen.
■ Dieses Produkt und sämtliche angeschlossene Ausrüstung einschließlich
aller zugehörigen LAN-Verbindungen müssen in den Innenräumen
desselben Gebäudes installiert werden, wie in der Norm IEEE 802.3af für
Umgebung A beschrieben.
C-4
Wartung
Dieses Gerät enthält innen keine durch den Benutzer zu wartenden Teile.
Wartungs-, Anpassungs-, Instandhaltungs- oder Reparaturarbeiten dürfen
nur von geschultem Bedienungspersonal durchgeführt werden.
Dieses Gerät hat keinen Netzschalter; es wird beim Anschließen des Netzkabels eingeschaltet.
Page 99

Safety and EMC Regulatory Statements
Considerazioni sulla sicurezza
Considerazioni sulla sicurezza
Simbolo di riferimento alla documentazione. Se il prodotto
!
WARNING La dicitura WARNING denota un pericolo che può causare lesioni
è contrassegnato da questo simbolo, fare riferimento alla
documentazione sul prodotto per ulteriori informazioni su di esso.
o morte.
CAUTION La dicitura CAUTION denota un pericolo che può danneggiare
le attrezzature.
Non procedere oltre un avviso di WARNING o di CAUTION prima di
aver compreso le condizioni di rischio e aver provveduto alle misure
del caso.
Messa a terra
A seconda del modello, il prodotto sarà classificato come dispositivo di
sicurezza conforme alla classe I o alla classe II. I dispositivi di classe I
richiedono una connessione alla messa a terra (connettore a 3 terminali),
mentre quelli di classe II hanno un connettore a 2 terminali incorporato.
Classe I: deve essere presente una messa a terra di sicurezza di continuità
dalla fonte di alimentazione principale al cavo di alimentazione del prodotto
o al gruppo dei cavi di alimentazione. Se questa protezione non dovesse più
sembrare accoppiata, scollegare il cavo di alimentazione fino a che non viene
ripristinata la messa a terra.
Classe II: i dispositivi conformi alla sicurezza di classe II includono un
isolamento supplementare per la protezione dalle scosse elettriche e non
richiedono una connessione alla messa a terra.
Per le connessioni LAN:
■ se la vostra LAN copre un'area servita da più di un sistema di distribuzione
elettrica, accertatevi che i collegamenti a terra di sicurezza siano ben
collegati fra loro;
■ i cavi LAN possono occasionalmente andare soggetti a pericolose tensioni
transitorie (ad esempio, provocate da lampi o disturbi nella griglia
d'alimentazione della società elettrica); siate cauti nel toccare parti
esposte in metallo della rete.
■ Questo prodotto e tutti i dispositivi collegati, incluse le connessioni LAN
associate, devono essere installati all'interno dello stesso edificio come
descritto dallo standard IEEE 802.3af (Environment A).
C-5
Page 100

Safety and EMC Regulatory Statements
Consideraciones sobre seguridad
Manutenzione
Nessun componente di questo prodotto può essere riparato dall'utente. Qualsiasi lavoro di riparazione, messa a punto, manutenzione o assistenza va
effettuato esclusivamente da personale specializzato.
Questo apparato non possiede un commutatore principale; si mette scotto
tensione all'inserirsi il cavo d'alimentazione.
Consideraciones sobre seguridad
WARNING Una WARNING en la documentación señala un riesgo que podría
Símbolo de referencia a la documentación. Si el producto va
!
marcado con este símbolo, consultar la documentación del
producto a fin de obtener mayor información sobre el producto.
resultar en lesiones o la muerte.
CAUTION Una CAUTION en la documentación señala un riesgo que podría
Toma de tierra
Dependiendo del modelo del producto, este aparecerá clasificado como
dispositivo que cumple los requisitos de la categoría de seguridad I o de la
categoría de seguridad II. Los dispositivos de categoría de seguridad I
requieren una conexión a tierra (clavija de 3 terminales), mientras que los
dispositivos de categoría de seguridad II incorporan una clavija de 2 terminales.
Categoría I: debe haber una puesta a tierra continua desde la fuente principal
de energía hasta el cable de la corriente del producto o el grupo de cables
proporcionado. Siempre que quepa la posibilidad de que la protección haya
sido dañada, desconecte el cable de la corriente hasta que la toma de tierra
haya sido restaurada.
Categoría II: los dispositivos de categoría de seguridad II incluyen un
aislamiento adicional como protección contra descargas eléctricas y no
requieren una conexión a tierra.
Para conexiones LAN:
resultar en averías al equipo.
No proseguir después de un símbolo de WARNING o CAUTION hasta
no haber entendido las condiciones peligrosas y haber tomado las
medidas apropiadas.
C-6
 Loading...
Loading...