Page 1

Polycom® DMA™ 7000 System
Operations Guide
5.1 | November 2012 | 3725-76302-001L1
Page 2

Trademark Information
Polycom®, the Polycom “Triangles” logo, and the names and marks associated with Polycom’s products are
trademarks and/or service marks of Polycom, Inc., and are registered and/or common-law marks in the United
States and various other countries.
All other trademarks are the property of their respective owners.
Java is a registered trademark of Oracle America, Inc., and/or its affiliates.
Patent Information
The accompanying product may be protected by one or more U.S. and foreign patents and/or pending patent
applications held by Polycom, Inc.
End User License Agreement
Use of this software constitutes acceptance of the terms and conditions of the Polycom DMA 7000 system end-user
license agreement (EULA).
The EULA is included in the release notes document for your version, which is available on the Polycom Support
page for the Polycom DMA 7000 system.
© 2009-2012 Polycom, Inc. All rights reserved.
Polycom, Inc.
6001 America Center Drive
San Jose CA 95002
USA
No part of this document may be reproduced or transmitted in any form or by any means, electronic or
mechanical, for any purpose, without the express written permission of Polycom, Inc. Under the law, reproducing
includes translating into another language or format.
As between the parties, Polycom, Inc., retains title to and ownership of all proprietary rights with respect to the
software contained within its products. The software is protected by United States copyright laws and international
treaty provision. Therefore, you must treat the software like any other copyrighted material (e.g., a book or sound
recording).
Every effort has been made to ensure that the information in this manual is accurate. Polycom, Inc., is not
responsible for printing or clerical errors. Information in this document is subject to change without notice.
ii
Page 3

Contents
1 Polycom® DMA™7000 System Overview . . . . . . . . . . . . . 1
Introduction to the Polycom DMA System . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
The Polycom DMA System’s Primary Functions . . . . . . . . . . . . . . . . . . 2
The Polycom DMA System’s Three Configurations . . . . . . . . . . . . . . . 5
System Capabilities and Constraints . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
System Port Usage . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Polycom Solution Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Working in the Polycom DMA System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Third-Party Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
Open Source Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16
2 Polycom® DMA™ System Initial Configuration Summary . . 23
Add Required DNS Records for the Polycom DMA System . . . . . . . . . . . 24
License the Polycom DMA System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26
Set Up Signaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Configure the Call Server and Optionally Create a Supercluster . . . . . . . . 28
Set Up Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Set Up MCUs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29
Connect to Microsoft Active Directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32
Set Up Conference Templates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
Test the System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33
3 System Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Security Certificates Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
How Certificates Work . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35
Forms of Certificates Accepted by the Polycom DMA System . . . . . . 36
How Certificates Are Used by the Polycom DMA System . . . . . . . . . 37
Frequently Asked Questions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Certificate Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38
Certificate Information Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40
Certificate Signing Request Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 40
Polycom, Inc. iii
Page 4

DMA Operations Guide
Add Certificates Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Certificate Details Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41
Certificate Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42
Install a Certificate Authority’s Certificate . . . . . . . . . . . . . . . . . . . . . . 43
Create a Certificate Signing Request in the DMA System . . . . . . . . . . 44
Install a Certificate in the DMA System . . . . . . . . . . . . . . . . . . . . . . . . . 45
Remove a Certificate from the DMA System . . . . . . . . . . . . . . . . . . . . 47
Security Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48
The Consequences of Enabling Maximum Security Mode . . . . . . . . . . . . . 54
Login Policy Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Local Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57
Session . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58
Local User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59
Banner . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60
Reset System Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61
4 Local Cluster Configuration . . . . . . . . . . . . . . . . . . . . . . . . 63
Network Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64
Routing Configuration Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68
Time Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69
Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70
Signaling Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71
Add Guest Port Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 77
Edit Guest Port Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78
Add Guest Prefix Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79
Edit Guest Prefix Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Logging Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Local Cluster Configuration Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Add Licenses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82
Configure Signaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83
Configure Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86
5 Device Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Active Calls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Call Details Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91
Add Device Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96
Edit Device Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98
Edit Devices Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Add Alias Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
iv Polycom, Inc.
Page 5

Contents
Edit Alias Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Associate User Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Site Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101
Site Link Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102
External Gatekeeper . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Add External Gatekeeper Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . 104
Edit External Gatekeeper Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . 106
External SIP Peer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108
Add External SIP Peer Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109
Edit External SIP Peer Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 114
SIP Peer Postliminary Output Format Options . . . . . . . . . . . . . . . . . . 119
Add Authentication Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Edit Authentication Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123
Add Outbound Registration Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . 124
Edit Outbound Registration Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . 125
External SBC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127
Add External SBC Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128
Edit External SBC Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129
6 MCU Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
MCUs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131
Add MCU Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137
Edit MCU Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142
Add Session Profile Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
Edit Session Profile Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146
ISDN Gateway Selection Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147
MCU Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149
MCU Pools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152
Add MCU Pool Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
Edit MCU Pool Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154
MCU Pool Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155
MCU Pool Orders . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156
Add MCU Pool Order Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Edit MCU Pool Order Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
MCU Selection Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 159
MCU Availability and Reliability Tracking . . . . . . . . . . . . . . . . . . . . . 160
MCU Pool Order Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162
7 Integrations with Other Systems . . . . . . . . . . . . . . . . . . . 163
Microsoft Active Directory Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163
Polycom, Inc. v
Page 6

DMA Operations Guide
Microsoft Active Directory Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
Active Directory Integration Procedure . . . . . . . . . . . . . . . . . . . . . . . . 169
Understanding Base DN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173
Adding Passcodes for Enterprise Users . . . . . . . . . . . . . . . . . . . . . . . . 174
About the System’s Directory Queries . . . . . . . . . . . . . . . . . . . . . . . . . 176
Microsoft Exchange Server Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 180
Microsoft Exchange Server Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182
Exchange Server Integration Procedure . . . . . . . . . . . . . . . . . . . . . . . . 183
Resource Management System Integration . . . . . . . . . . . . . . . . . . . . . . . . 185
Resource Management System Page . . . . . . . . . . . . . . . . . . . . . . . . . . 186
Join Resource Management System Dialog Box . . . . . . . . . . . . . . . . . 187
Resource Management System Integration Procedures . . . . . . . . . . 188
Juniper Networks SRC Integration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189
Juniper Networks SRC Page . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190
Juniper Networks SRC Integration Procedure . . . . . . . . . . . . . . . . . . 191
8 Conference Manager Configuration . . . . . . . . . . . . . . . . 193
Conference Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193
Conference Templates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Two Types of Templates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195
Template Priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
About Conference IVR Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197
About Cascading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198
Conference Templates List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199
Add Conference Template Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 200
Edit Conference Template Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 210
Select Layout Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 219
Conference Templates Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . 220
Shared Number Dialing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221
Add Virtual Entry Queue Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 223
Add Direct Dial Virtual Entry Queue Dialog Box . . . . . . . . . . . . . . . 224
Edit Virtual Entry Queue Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . 225
Edit Direct Dial Virtual Entry Queue Dialog Box . . . . . . . . . . . . . . . . 225
9 Superclustering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
About Superclustering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227
DMAs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 229
Join Supercluster Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232
Supercluster Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233
vi Polycom, Inc.
Page 7

Contents
10 Call Server Configuration . . . . . . . . . . . . . . . . . . . . . . . . 237
About the Call Server Capabilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 238
Call Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239
Domains . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242
Dial Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 243
Test Dial Rules Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245
The Default Dial Plan and Suggestions for Modifications . . . . . . . . . 246
Add Dial Rule Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 250
Edit Dial Rule Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 252
Preliminary/Postliminary Scripting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 254
Script Debugging Dialog Box for Preliminaries/Postliminaries . . . . 257
Sample Preliminary and Postliminary Scripts . . . . . . . . . . . . . . . . . . 258
Hunt Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261
Add Hunt Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Edit Hunt Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 262
Add Alias Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263
Edit Alias Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Device Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264
Add Device Authentication Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . 266
Edit Device Authentication Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . 267
Registration Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 268
Registration Policy Scripting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 270
Script Debugging Dialog Box for Registration Policy Scripts . . . . . . 273
Sample Registration Policy Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . 273
Prefix Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 276
Add Simplified ISDN Gateway Dialing Prefix Dialog Box . . . . . . . . 277
Edit Simplified ISDN Gateway Dialing Prefix Dialog Box . . . . . . . . 278
Edit Vertical Service Code Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 279
Embedded DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 279
History Retention Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 281
11 Site Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
About Site Topology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283
Sites . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 285
Site Information Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 286
Add Site Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 287
Edit Site Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292
Add Subnet Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 297
Edit Subnet Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 298
Polycom, Inc. vii
Page 8

DMA Operations Guide
12 Users and Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 311
Site Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Add Site Link Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 299
Edit Site Link Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 300
Site-to-Site Exclusions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
Add Site-to-Site Exclusion Wizard . . . . . . . . . . . . . . . . . . . . . . . . . . . . 301
Territories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 302
Add Territory Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 303
Edit Territory Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 304
Network Clouds . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 305
Add Network Cloud Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 306
Edit Network Cloud Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 307
Site Topology Configuration Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . 307
User Roles Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 312
Adding Users Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313
Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 314
Add User Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 317
Edit User Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 320
Select Associated Endpoints Dialog Box . . . . . . . . . . . . . . . . . . . . . . . 322
Conference Rooms Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 323
Add Conference Room Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . 325
Edit Conference Room Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . 329
Add Dial-out Participant Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . 332
Edit Dial-out Participant Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . 333
Users Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 333
Conference Rooms Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 335
Groups . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 338
Import Enterprise Groups Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . 339
Edit Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341
Enterprise Groups Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 342
Login Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 344
Change Password Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 345
13 System Management and Maintenance . . . . . . . . . . . . . . 347
Management and Maintenance Overview . . . . . . . . . . . . . . . . . . . . . . . . . 347
Administrator Responsibilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 348
Administrative Best Practices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 348
Auditor Responsibilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 349
Auditor Best Practices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 349
viii Polycom, Inc.
Page 9

Contents
Recommended Regular Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 349
Dashboard . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 352
Active Directory Integration Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . 353
Call Server Active Calls Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 353
Call Server Registrations Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 354
Cluster Info Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 354
Conference History – Max Participants Pane . . . . . . . . . . . . . . . . . . . 355
Conference Manager MCUs Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 355
Conference Manager Usage Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 355
Exchange Server Integration Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . 356
License Status Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 357
Resource Management System Integration Pane . . . . . . . . . . . . . . . . 357
Signaling Settings Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 357
Supercluster Status Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 358
Territory Status Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 358
User Login History Pane . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 358
Alerts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
Alert 1001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
Alert 1002 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 359
Alert 1003 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Alert 1004 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Alert 1101 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Alert 1102 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 360
Alert 1103 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 361
Alert 1104 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 361
Alert 2001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 362
Alert 2002 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 362
Alert 2004 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 362
Alert 2101 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
Alert 2102 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
Alert 2103 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363
Alert 2104 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 364
Alert 2105 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 364
Alert 2106 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365
Alert 2107 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365
Alert 2201 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365
Alert 2202 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 366
Alert 2203 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 366
Alert 3001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 366
Alert 3101 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367
Polycom, Inc. ix
Page 10

DMA Operations Guide
Alert 3102 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367
Alert 3103 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367
Alert 3104 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368
Alert 3105 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368
Alert 3201 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368
Alert 3202 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
Alert 3301 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
Alert 3302 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
Alert 3303 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369
Alert 3304 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 370
Alert 3305 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 370
Alert 3401 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 370
Alert 3402 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 371
Alert 3403 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 371
Alert 3404 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 371
Alert 3405 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
Alert 3406 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
Alert 3601 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372
Alert 3602 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 373
Alert 3603 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 373
Alert 3604 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 373
Alert 3605 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Alert 3606 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Alert 4001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Alert 4002 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374
Alert 4003 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375
Alert 4004 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375
Alert 5001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375
Alert 5002 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 376
Alert 6001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 376
Alert 7001 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 376
System Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 377
System Logs Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 378
Troubleshooting Utilities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 380
Backing Up and Restoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 381
Backup and Restore Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 384
Upgrading the Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 388
Basic Upgrade Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 390
Incompatible Software Version Supercluster Upgrades . . . . . . . . . . 395
Factors to Consider for an Incremental Supercluster Upgrade . . . . 396
x Polycom, Inc.
Page 11

Contents
Simplified Supercluster Upgrade (Complete Service Outage) . . . . . 397
Complex Supercluster Upgrade (Some Service Maintained) . . . . . . 402
Adding a Second Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 402
Expanding an Unpatched System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 403
Expanding a Patched System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 404
Replacing a Failed Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 405
Shutting Down and Restarting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 406
14 System Reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 407
Alert History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 407
Call History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 408
Export History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 409
Conference History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 410
Export History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 410
Associated Calls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 411
Conference Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 411
Property Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
Call Detail Records (CDRs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
Exporting CDR Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 412
Call Record Layouts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 413
Conference Record Layouts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 415
Registration History Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 417
Registration History Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
Active Directory Integration Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 418
Orphaned Groups and Users Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 421
Orphaned Groups and Users Procedures . . . . . . . . . . . . . . . . . . . . . . 421
Conference Room Errors Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 422
Exporting Conference Room Errors Data . . . . . . . . . . . . . . . . . . . . . . 424
Enterprise Passcode Errors Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 424
Exporting Enterprise Passcode Errors Data . . . . . . . . . . . . . . . . . . . . 426
Network Usage Report . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 426
Exporting Network Usage Data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 427
15 Polycom DMA System SNMP Support . . . . . . . . . . . . . . . . 431
SNMP Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 431
SNMP Versions Supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 432
List of Available SNMP MIBs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 433
SNMP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 433
Add Notification User Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . 436
Edit Notification User Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 438
Polycom, Inc. xi
Page 12

DMA Operations Guide
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 539
Add Notification Agent Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . 439
Edit Notification Agent Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . 440
SNMP Procedures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 441
The Polycom DMA System MIB . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 442
xii Polycom, Inc.
Page 13

1
Polycom® DMA
Overview
This chapter provides an overview of the Polycom® Distributed Media
Application™ (DMA™) 7000 system. It includes these topics:
• Introduction to the Polycom DMA System
• Polycom Solution Support
• Working in the Polycom DMA System
• Third-Party Software
™
7000 System
Introduction to the Polycom DMA System
The Polycom DMA system is a highly reliable and scalable video collaboration
infrastructure solution based on the Polycom
The following topics introduce you to the system:
• The Polycom DMA System’s Primary Functions
• The Polycom DMA System’s Three Configurations
• System Capabilities and Constraints
• System Port Usage
Polycom, Inc. 1
®
Proxias™ application server.
Page 14

DMA Operations Guide Introduction to the Polycom DMA System
The Polycom DMA System’s Primary Functions
Conference Manager
The Polycom DMA system’s Conference Manager uses advanced routing
policies to distribute voice and video calls among multiple media servers
(Multipoint Control Units, or MCUs), creating a single virtual resource pool.
This greatly simplifies video conferencing resource management and uses
MCU resources more efficiently.
The Polycom DMA system integrates with your Microsoft® Active
Directory®, automating the task of provisioning users with virtual meeting
rooms (VMRs) for video conferencing. Combined with its advanced resource
management, this makes reservationless video conferencing on a large scale
feasible and efficient, reducing or eliminating the need for conference
scheduling.
The Polycom DMA system’s ability to handle multiple MCUs as a single
resource pool makes multipoint conferencing services highly scalable. You can
add MCUs on the fly without impacting end users and without requiring reprovisioning.
The Conference Manager continually monitors the resources used and
available on each MCU and intelligently distributes conferences among them.
If an MCU fails, loses its connection to the system, or is taken out of service,
the Polycom DMA system distributes new conferences to the remaining
MCUs. The consequences for existing calls and conferences depend on
whether they’re H.323 or SIP:
• H.323 calls and conferences on the failed MCU are terminated. But callers
simply need to redial the same number they used for their initial dial-in.
Conference Manager relocates their new conference to the best available
MCU (provided there is still sufficient MCU capacity).
• SIP calls on the failed MCU are automatically moved to another MCU or
MCUs (if available), up to the capacity available.
Call Server
The Polycom DMA system’s Call Server provides the following functionality:
• H.323 gatekeeper
• SIP registrar and proxy server
• XMPP server (client-to-client connectivity, including chat and presence
information, for clients logged into the server)
• H.323 <—> SIP transition gateway
• Dial plan and prefix services
• Device authentication
2 Polycom, Inc.
Page 15

Introduction to the Polycom DMA System Polycom® DMA™7000 System Overview
• Bandwidth management
The Call Server can also be integrated with a Juniper Networks Service
Resource Controller (SRC) to provide bandwidth and QoS assurance services.
RealPresence Platform API
This version of the Polycom DMA system optionally allows an API client
application, developed by you or a third party, to access the RealPresence
Platform Application Programming Interface (API). This API access is licensed
separately. It provides programmatic access to the Polycom DMA system for
the following:
• Provisioning
• Conference control and monitoring
• Call control and dial-out
• Billing and usage data retrieval
• Resource availability queries
The API uses XML encoding over HTTPS transport and adheres to a
Representational State Transfer (REST) architecture.
No separate license is needed in order for a Polycom RealPresence Resource
Manager system to integrate with the DMA system via the API. This
integration provides the full programmatic access to the DMA system
described above, and enables users of the RealPresence Resource Manager
scheduling interface to:
• Schedule conferences using the DMA system’s MCU resources.
• Set up Anytime conferences. Anytime conferences are referred to as preset
dial-out conferences in the DMA system (see “Edit Conference Room
Dialog Box” on page 329)
Note
Integrating the Polycom RealPresence Resource Manager system with the DMA
system via the API is separate and distinct from integrating the DMA system with a
Polycom CMA or RealPresence Resource Manager system.
• The former enables RealPresence Resource Manager users to obtain
information from and use functionality of the DMA system that would otherwise
be accessible only in the DMA system’s management interface.
• The latter enables the DMA system to retrieve site topology and user-to-device
associations from the CMA or RealPresence Resource Manager system.
For convenience, however, when you perform the former operation, the latter
integration is automatically performed for you so that the DMA system will have the
site topology and user-to-device information that the RealPresence Resource
Manager system expects it to have.
Polycom, Inc. 3
Page 16

DMA Operations Guide Introduction to the Polycom DMA System
SVC Conferencing Support
This version of the Polycom DMA system supports the Annex G extension of
the H.264 standard, known as H.264 Scalable Video Coding (SVC), for both
point-to-point and multipoint (VMR) calls.
SVC is sometimes referred to as layered media because the video streams
consist of a base layer that encodes the lowest available quality representation
plus one or more enhancement layers that each provide an additional quality
improvement. SVC supports three dimensions of scalability: temporal (frames
per second), spatial (resolution and aspect ratio), and quality (signal-to-noise
ratio).
The video stream to a device can be tailored to fit the bandwidth available and
device capabilities by adjusting the number of enhancement layers sent to the
device.
For multipoint conferencing, the MCU doesn't have to do processing-intensive
mixing and transcoding to optimize the experience for each device. Instead, it
simply passes through to each device the enhancement layers that provide the
best quality the device can support.
Polycom’s SVC solution focuses on the temporal and spatial dimensions. It
offers a number of advantages over standard AVC conferencing, including:
• Improved video quality at lower bandwidths
• Improved audio and video error resiliency (good audio quality with more
than 50% packet loss, good video quality with more than 25% packet loss)
• Lower end-to-end latency (typically less than half that of AVC)
• More efficient use of bandwidth
• Lower infrastructure cost and operational expenses
• Easier to provision, control, and monitor
• Better security (end-to-end encryption)
Polycom’s SVC solution is supported by the Polycom RealPresence Platform
and Environments, including the latest generation of Polycom MCUs and
RealPresence room, personal, desktop, and mobile endpoints. Existing RMX
MCUs with MPMx cards can be made SVC-capable with a software upgrade,
and doing so triples their HD multipoint conferencing capacity.
See also:
“Introduction to the Polycom DMA System” on page 1
4 Polycom, Inc.
Page 17

Introduction to the Polycom DMA System Polycom® DMA™7000 System Overview
The Polycom DMA System’s Three Configurations
Two-server Cluster Configuration
The Polycom DMA system is designed to be deployed as a pair of co-located
redundant servers that share the same virtual IP address(es). The two-server
cluster configuration of the Polycom DMA system has no single point of
failure within the system that could cause the service to become unavailable.
The two servers communicate over the private network connecting them. To
determine which one should host the public virtual IP address, each server
uses three criteria:
• Ability to ping its own public physical address
• Ability to ping the other server’s public physical address
• Ability to ping the default gateway
In the event of a tie, the server already hosting the public virtual address wins.
Failover to the backup server takes about five seconds in the event of a graceful
shutdown and about twenty seconds in the event of a power loss or other
failure. In the event of a single server (node) failure, two things happen:
• All calls that are being routed through the failed server are terminated
(including SIP calls, VMR calls, and routed mode H.323 calls). These users
simply need to redial the same number, and they’re placed back into
conference or reconnected to the point-to-point call they were in. The
standby server takes over the virtual signaling address, so existing
registrations and new calls are unaffected.
• Direct mode H.323 point-to-point calls are not dropped, but the
bandwidth management system loses track of them. This could result in
overuse of the available network bandwidth.
• If the failed server is the active web host for the system management
interface, the active user interface sessions end, the web host address
automatically migrates to the remaining server, and it becomes the active
web host. Administrative users can then log back into the system at the
same URL. The system can always be administered via the same address,
regardless of which server is the web host.
The internal databases within each Polycom DMA system server are fully
replicated to the other server in the cluster. If a catastrophic failure of one of
the database engines occurs, the system automatically switches itself over to
use the database on the other server.
Polycom, Inc. 5
Page 18

DMA Operations Guide Introduction to the Polycom DMA System
Single-server Configuration
The Polycom DMA system is also available in a single-server configuration.
This configuration offers all the advantages of the Polycom DMA system
except the redundancy and fault tolerance at a lower price. It can be upgraded
to a two-server cluster at any time.
This manual generally assumes a redundant two-server cluster. Where there
are significant differences between the two configurations, those are spelled
out.
Superclustering
To provide geographic redundancy and better network traffic management,
up to five geographically distributed Polycom DMA system clusters (twoserver or single-server) can be integrated into a supercluster. All five clusters
can be Call Servers (function as gatekeeper, SIP proxy, SIP registrar, and
gateway). Up to three can be designated as Conference Managers (manage an
MCU resource pool to host conference rooms).
The superclustered Polycom DMA systems can be centrally administered and
share a common data store. Each cluster maintains a local copy of the data
store, and changes are replicated to all the clusters. Most system configuration
is supercluster-wide. The exceptions are cluster-specific or server-specific
items like network settings and time settings.
Note
Technically, a standalone Polycom DMA system (two-server or single-server) is a
supercluster that contains one cluster. All the system configuration and other data
that’s shared across a supercluster is kept in the same data store. At any time,
another Polycom DMA system can be integrated with it to create a two-cluster
supercluster that shares its data store.
It’s important to understand the difference between two co-located servers forming
a single DMA system (cluster) and two geographically distributed DMA clusters
(single-server or two-server) joined into a supercluster.
A single two-server DMA system (cluster) has the following characteristics:
• A single shared virtual IP address and FQDN, which switches from one server
to the other when necessary to provide local redundancy and fault tolerance.
• A single management interface and set of local settings.
• Ability to manage a single territory, with no territory management backup.
• A single set of Call Server and Conference Manager responsibilities.
A supercluster consisting of two DMA clusters (single-server or two-server) has the
following characteristics:
• Separate IP addresses and FQDNs for each cluster.
• Separate management interfaces and sets of local settings for each cluster.
• Ability for each cluster to manage its own territory, with another cluster able to
serve as backup for that territory.
• Different Call Server and Conference Manager responsibilities for each territory
and thus each cluster.
6 Polycom, Inc.
Page 19

Introduction to the Polycom DMA System Polycom® DMA™7000 System Overview
System Capabilities and Constraints
The following capabilities and constraints apply to the entire supercluster:
• Number of sites: 500
• Number of clusters in a supercluster: 5 (not counting an integrated
Polycom RealPresence Resource Manager or CMA system)
• Number of MCUs enabled for conference rooms: 64
• Number of territories enabled for conference rooms (Conference Manager
enabled): 3
• Number of concurrent VMR calls: 1200 per territory (Conference
Manager), up to 3600 total
• Size of Active Directory supported: 1,000,000 users and 1,000,000 groups
(up to 10,000 groups may be imported)
The following capabilities and constraints apply to each cluster in the
supercluster:
• Number of registrations: 15000
System Port Usage
• Number of concurrent H.323 calls: 5000
• Number of concurrent SIP calls: 5000
• Total number of concurrent calls: 5000
• Number of network usage data points retained: 8,000,000
• Number of IRQ messages sent per second: 100
The table below lists the inbound ports that may be open on the Polycom DMA
system, depending on signaling and security settings, integrations, and
system configuration.
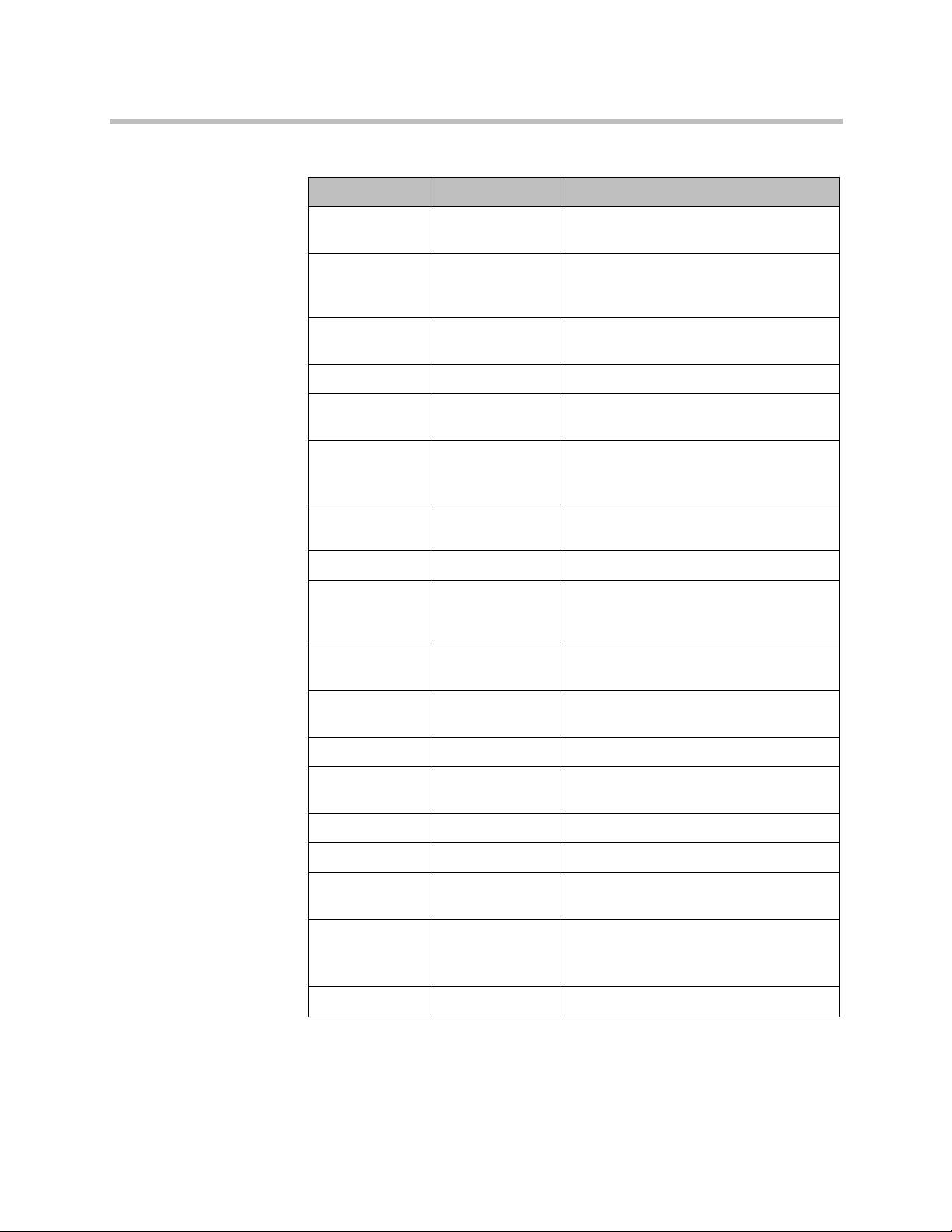
Table 1-1 Inbound port usage
Port Protocol Description
22 TCP SSH. Only available if Linux console
access is enabled (see “Security Settings”
on page 48).
80 TCP HTTP. Redirects to 443 (HTTP access is
not allowed). Disabled in maximum
security mode.
443 TCP HTTPS. Redirects to 8443.
1718 UDP H.323 RAS. Default port; can be changed
(see “Signaling Settings” on page 71).
Polycom, Inc. 7
Page 20
DMA Operations Guide Introduction to the Polycom DMA System
Table 1-1 Inbound port usage (continued)
Port Protocol Description
1719 UDP H.323 RAS. Default port; can be changed
(see “Signaling Settings” on page 71).
1720 TCP H.323 H.225 signaling. Default port; can
be changed (see “Signaling Settings” on
page 71).
1935 TCP/UDP XMPP. Traditional RTMP, Flash
communication server.
1936 TCP/UDP XMPP. Flash communication server.
4449 TCP LDAP. OpenDJ replication
(superclustering).
5060 TCP/UDP Unencrypted SIP. Default port; can be
changed or disabled (see “Signaling
Settings” on page 71).
5061 TCP SIP TLS. Default port; can be changed
(see “Signaling Settings” on page 71).
5080 TCP/UDP XMPP. Tomcat or jetty servlet container.
5222 TCP Unencrypted XMPP. Default port; can be
changed or disabled (see “Signaling
Settings” on page 71).
5223 TCP XMPP TLS. Default port; can be changed
(see “Signaling Settings” on page 71).
5269 TCP/UDP XMPP. Server to server communications
for federation.
7070 TCP XMPP HTTP connections.
8088 TCP XMPP. Traditional RTMP tunneled over
HTTP.
8443 TCP HTTPS. Management interface access.
8444 TCP HTTPS. Supercluster communication.
8989 TCP LDAP. OpenDJ replication
(superclustering).
9090 TCP HTTPS. Upgrade status monitoring (only
while upgrade process is running).
XMPP server administration console.
36000-61000 TCP H.323 H.245 port range.
8 Polycom, Inc.
Page 21
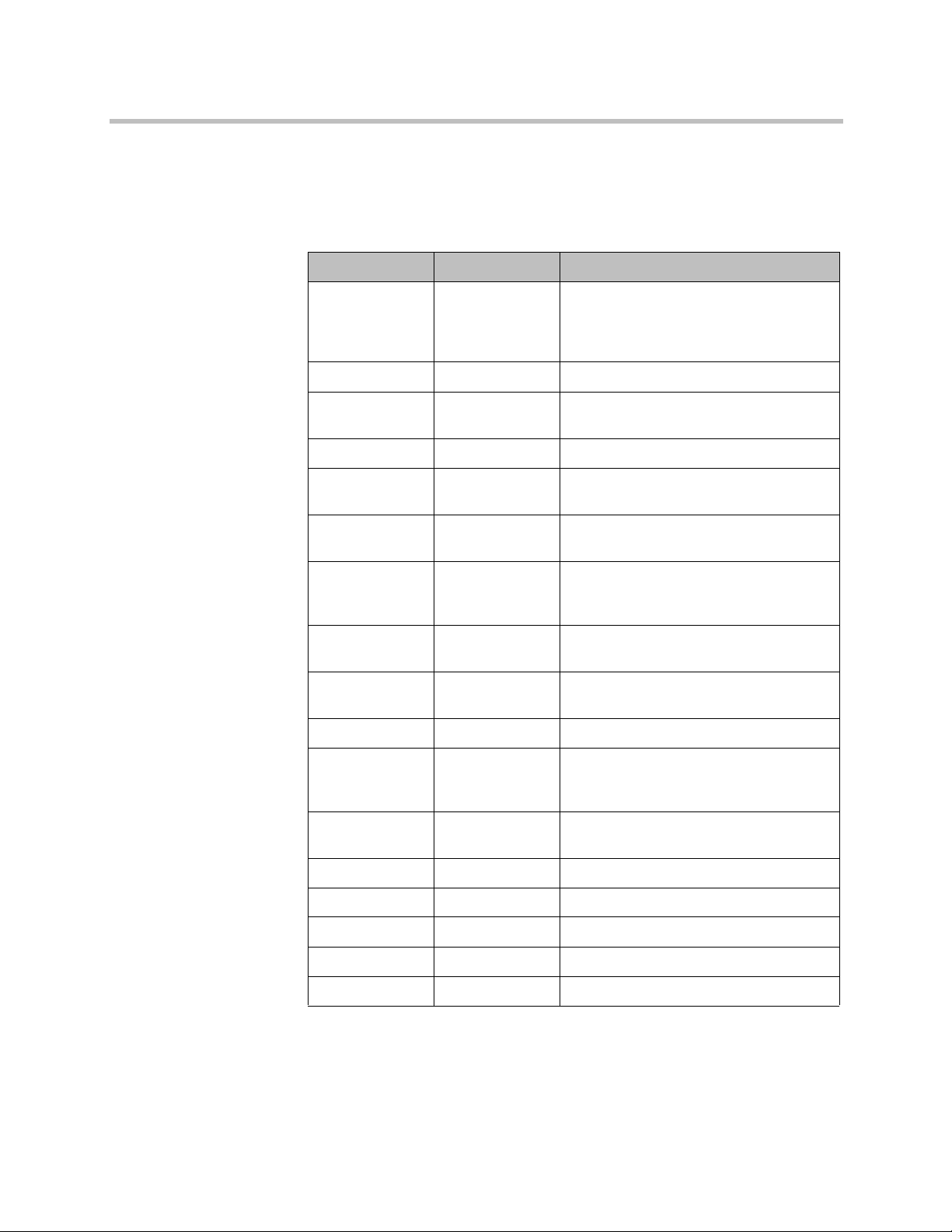
Introduction to the Polycom DMA System Polycom® DMA™7000 System Overview
The table below lists the remote ports to which the Polycom DMA system may
connect, depending on signaling and security settings, integrations, and
system configuration.
Table 1-2 Outbound port usage
Port Protocol Description
80 TCP HTTP. MCUs, Exchange Web Services
(calendaring). Only available if
unencrypted connections are enabled
(see “Security Settings” on page 48).
389 TCP LDAP. Active Directory integration.
443 TCP HTTPS. MCUs, Exchange Web Services
(calendaring).
389 TCP LDAP. Active Directory integration.
1718 UDP H.323 RAS. Default port; can be changed
(see “Signaling Settings” on page 71).
1719 UDP H.323 RAS. Default port; can be changed
(see “Signaling Settings” on page 71).
1720 TCP H.323 H.225 signaling. Default port; can
be changed (see “Signaling Settings” on
page 71).
3268 TCP Global Catalog. Active Directory
integration.
3269 TCP Secure Global Catalog. Active Directory
integration.
4449 TCP OpenDJ replication (superclustering).
5060 TCP/UDP Unencrypted SIP. Default port; can be
changed or disabled (see “Signaling
Settings” on page 71).
5061 TCP SIP TLS. Default port; can be changed
(see “Signaling Settings” on page 71).
8443 TCP HTTPS. Management interface access.
8444 TCP Supercluster communication.
8989 TCP OpenDJ replication (superclustering).
36000-61000 TCP H.323 H.245 port range.
32768-61000 TCP/UDP XMPP. Ephemeral port range.
Polycom, Inc. 9
Page 22

DMA Operations Guide Polycom Solution Support
Polycom Solution Support
Polycom Implementation and Maintenance services provide support for
Polycom solution components only. Additional services for supported thirdparty Unified Communications (UC) environments integrated with Polycom
solutions are available from Polycom Global Services and its certified Partners.
These additional services will help customers successfully design, deploy,
optimize, and manage Polycom visual communications within their UC
environments.
Professional Services for Microsoft Integration is mandatory for Polycom
Conferencing for Microsoft Outlook and Microsoft Office Communications
Server or Lync Server 2010 integrations. For more information, please visit
www.polycom.com/services/professional_services/ or contact your local
Polycom representative.
Working in the Polycom DMA System
This section includes some general information you should know when
working in the Polycom DMA system.
Accessing the Polycom DMA System
The Polycom DMA system’s management interface is accessed by pointing a
compatible browser equipped with Adobe® Flash® Player to the system’s
host name or IP address (a two-server cluster or an IPv6-only single-server
cluster has a virtual host name and IP address, and we strongly recommend
always using the virtual address). Minimum requirements:
• Microsoft Internet Explorer® 7 or newer, or Mozilla Firefox® 3 or newer,
or Google Chrome 11 or newer
• Adobe Flash Player 9.0.124 or newer
• 1280x1024 minimum display resolution (1680x1050 or greater
recommended)
Note
The Polycom DMA system’s Flex-based management interface requires Adobe
Flash Player. For stability and security reasons, we recommend always using the
latest version of Flash Player.
Even so, be aware that your browser’s Flash plugin may hang or crash from time to
time. Yo ur browser should alert you when this happens and enable you to reload
the plugin. In some cases, you may need to close and restart your browser.
In the Google Chrome browser, use the Adobe Flash plugin, not the built-in Flash
support.
10 Polycom, Inc.
Page 23

Working in the Polycom DMA System Polycom® DMA™7000 System Overview
Field Input Requirements
While every effort was made to internationalize the Polycom DMA system, not
all system fields accept Unicode entries. If you work in a language other than
English, be aware that some fields accept only ASCII characters.
Settings Dialog Box
The Settings dialog box shows your user name and information about the
server you’re logged into. Click the button to the right of the menus to
display it.
In addition, you can change the text size used in the system interface and the
maximum number of columns in the Dashboard. Note that larger text sizes
will affect how much you can see in a given window or screen size and may
require frequent scrolling.
Polycom DMA System User Roles and Their Access Privileges
The Polycom DMA system has three system user roles (see “User Roles
Overview” on page 312) that provide access to the management and
operations interface and, if available, the separately licensed RealPresence
Platform Application Programming Interface (API). The functions you can
perform and parts of the interface or API resources you can access depend on
your user role or roles, as shown in the tables below.
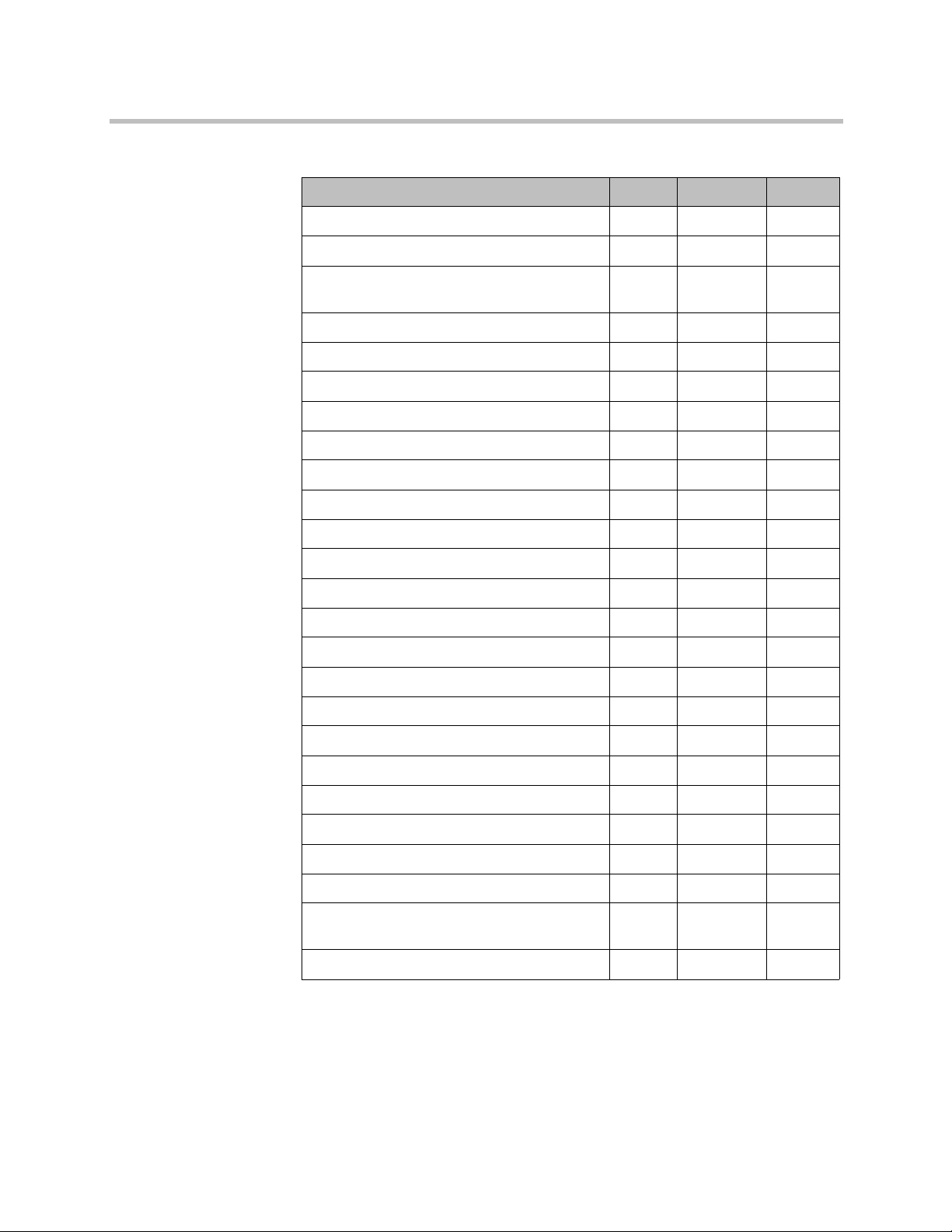
Table 1-3 Management interface access privileges
Menu/Icon Admin Provisioner Auditor
Home. Returns to the Dashboard.
Network >
Active Calls
Endpoints
1
DMAs
• •
• • •
• •
• •
Polycom, Inc. 11
Page 24

DMA Operations Guide Working in the Polycom DMA System
Table 1-3 Management interface access privileges
Menu/Icon Admin Provisioner Auditor
MCU > MCUs
MCU > MCU Pools
MCU > MCU Pool Orders
Site Statistics
Site Link Statistics
Site Topology > Sites
Site Topology > Site Links
Site Topology > Site-to-Site Exclusions
Site Topology > Network Clouds
Site Topology > Territories
External Gatekeeper
External SIP Peer
External SBC
1
• •
1
• •
1
• •
1
1
• •
1
• •
1
• •
1
• •
1
• •
1
• •
1
• •
1
• •
1
• •
• •
User >
2
Users
• •
Groups
1
Login Sessions
• •
Change Password
Reports >
Call History
Conference History
Registration History
Network Usage
Microsoft Active Directory Integration
Enterprise Passcode Errors
Orphaned Groups and Users
Conference Room Errors
3
•
3
•
3
•
•
• • •
• • •
• • •
• • •
• •
• •
12 Polycom, Inc.
Page 25
Working in the Polycom DMA System Polycom® DMA™7000 System Overview
Table 1-3 Management interface access privileges
Menu/Icon Admin Provisioner Auditor
Maintenance
System Log Files
4
• •
Troubleshooting Utilities > Ping,
Traceroute, Top, I/O Stats, SAR
Shutdown and Restart
Software Upgrade
Backup and Restore
Admin > Conference Manager >
Conference Settings
Conference Templates
Shared Number Dialing
Admin > Call Server >
Call Server Settings •
Domains
Dial Rules
Hunt Groups
Device Authentication
Registration Policy
1
Prefix Service
• •
•
•
•
•
•
•
•
•
•
• •
•
•
Embedded DNS
History Retention Settings
Admin > Integrations >
Microsoft Active Directory •
Microsoft Exchange Server
Polycom RealPresence Resource
Manager or CMA System
Juniper Networks SRC
Polycom, Inc. 13
•
• •
•
•
•
Page 26
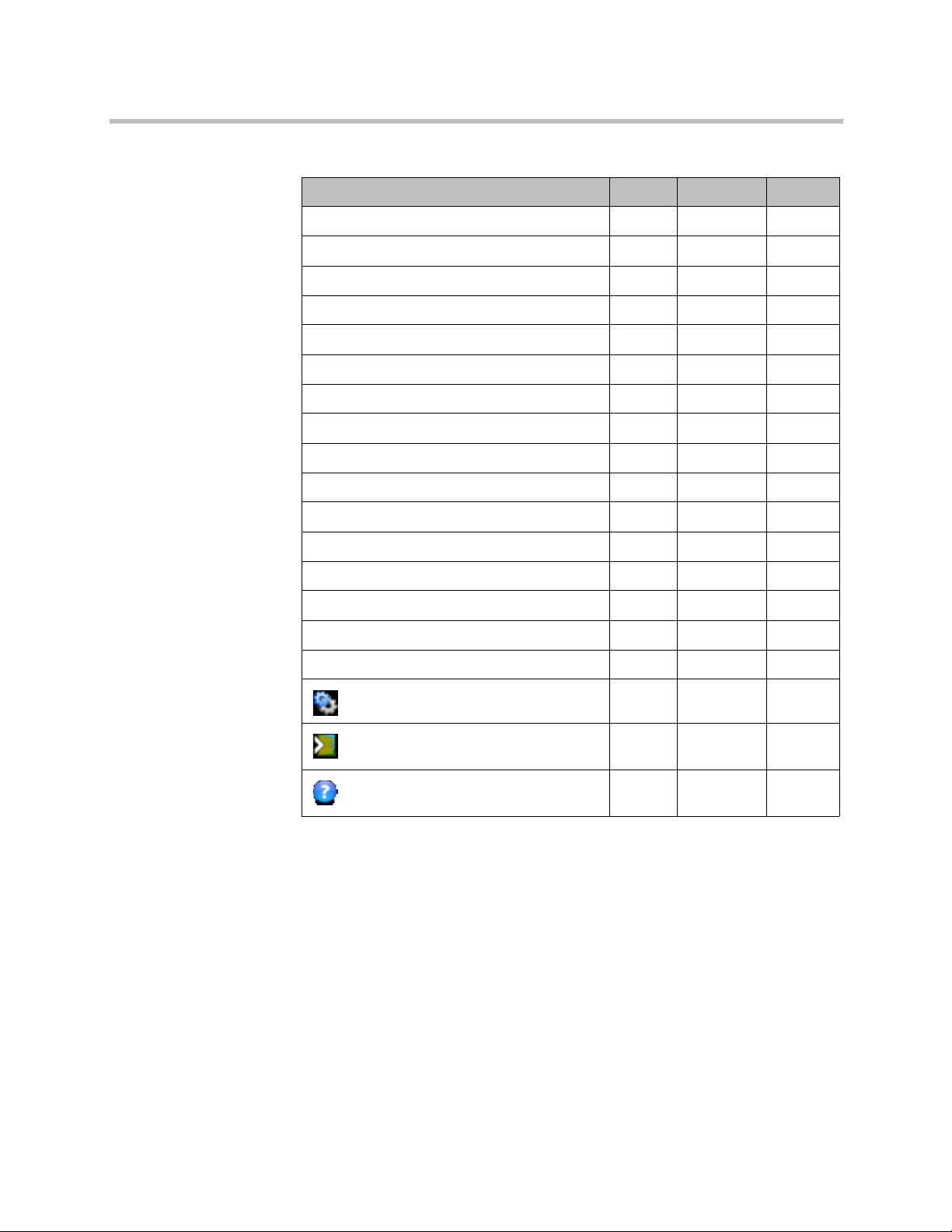
DMA Operations Guide Working in the Polycom DMA System
Table 1-3 Management interface access privileges
Menu/Icon Admin Provisioner Auditor
Admin > Login Policy Settings >
Local Password
Session
Local User Account
Banner
Admin > Local Cluster >
Network Settings
Signaling Settings
Time Settings
Licenses
Logging Settings
Security Settings
Certificates
Help >
About DMA 7000 • • •
Help Contents
Settings. Displays Settings dialog box.
•
•
•
•
•
•
•
•
• •
•
•
• • •
• • •
Log Out. Logs you out of the Polycom
DMA system.
Help. Opens the online help topic for the
page you’re viewing.
1. Provisioners have view-only access.
2. Must be an enterprise user to see enterprise users. Provisioners can’t add or remove roles
or endpoints, and can’t edit user accounts with explicitly assigned roles (Administrator,
Provisioner, or Auditor), but can manage their conference rooms.
3. Must be an enterprise user to view this report.
4. Administrators can’t delete log archives.
14 Polycom, Inc.
• • •
• • •
Page 27

Working in the Polycom DMA System Polycom® DMA™7000 System Overview
Table 1-4 API resource access privileges
Conference
Room
API Resource Admin Provisioner Auditor
1 2
user
conference-room
conference-template
1 2
3
• • •
• • •
• •
Owner
billing
conference
participant
conference-observer
participant-observer
mcu
mcu-pool
mcu-pool-order
territory
call-server-configuration
device
device-observer
group
status
subscription
user-role
1
• • •
1
• • •
1
• • •
1
• •
1
• • •
• • •
• •
• •
• •
• •
• •
• •
• •
• •
• • •
• •
1. Conference Room Owners can only access resources that they own and can’t use PUT,
POST, or DELETE methods on their user account or conference rooms.
2. Provisioners can’t add or remove roles or associated endpoints, and can’t edit user
accounts with explicitly assigned roles (Administrator, Provisioner, or Auditor), but can
manage their conference rooms.
3. Provisioners can GET a list of conference templates, but can’t GET a specific conference
template.
Polycom, Inc. 15
Page 28

DMA Operations Guide Third-Party Software
Third-Party Software
Open Source Software
The Polycom DMA system uses several open source software packages,
including the CentOS operating system. CentOS is an enterprise-class Linux
distribution that contains hundreds of open-source components. For more
information about CentOS, visit http://www.centos.org/.
The packages containing the source code and the licenses for all the opensource software, including CentOS and its components, are included on the
Polycom DMA system software DVD, mostly in the
Modifying Open Source Code
The LGPL v2.1 license allows you to modify the LGPL code we use, recompile
the modified code, and re-link it with our proprietary code. Note that although
you’re free to modify the LGPL modules used in the Polycom DMA system in
any way you wish, we cannot be responsible if the changes you make impair
the system.
/SRPMS
directory.
To replace an LGPL library with your modified version
1 On the DMA DVD, find the source code for the module you want to
modify.
2 Modify the source code and compile it.
3 Go to Admin > Local Cluster > Security Settings, select Allow Linux
console access, and click Update.
4 Contact Polycom Global Services for the root password for the Polycom
DMA server.
5 Use ssh to log into the server as root.
6 Upload the modified software via wget or scp.
7 Find the module you’re replacing and install the new version to that
location.
8 Reboot the system.
License Information
The following table contains license information for the open source software
packages used in the Polycom DMA system. Note that the source code and the
licenses for all the open-source software, including CentOS and its
components, are included on the Polycom DMA system software DVD. This
list is provided as a convenient reference.
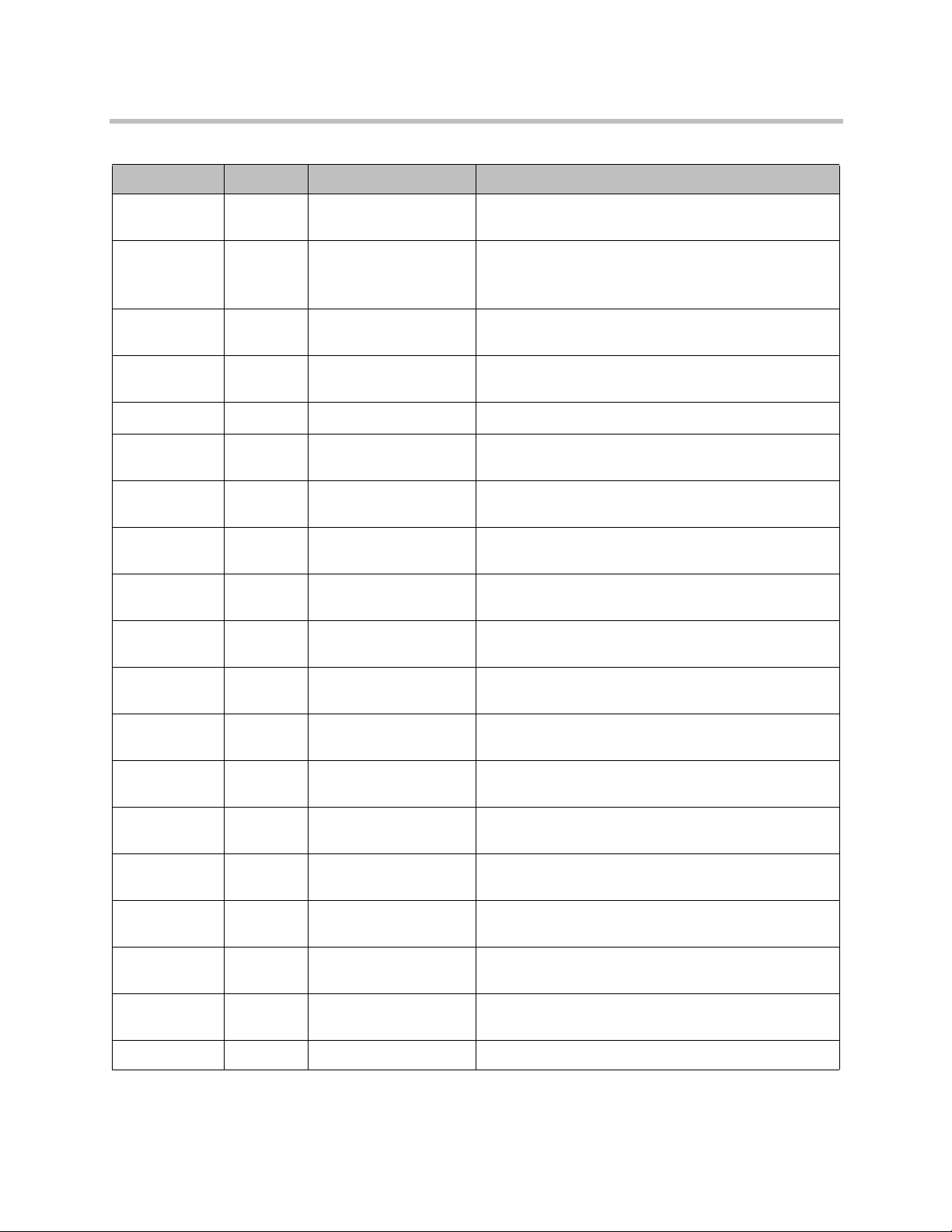
16 Polycom, Inc.
Page 29
Third-Party Software Polycom® DMA™7000 System Overview
Software Version License Link
Axis 1.4.2 Apache License,
Version 2
bsf 2.3.0-rc1 Apache License,
Version 2
CentOs 5.8 GPLv2 and multiple
others
cxf 2.4.2 Apache License,
Version 2
Cluster-glue 1.0.5 GPLv2 http://www.gnu.org/licenses/old-licenses/gpl-2.0.html
commons-
beanutils
commons-
collections
commons-
configuration
commons-
digester
commons-
discovery
1.7 Apache License,
Version 2
3.2 Apache License,
Version 2
1.5 Apache License,
Version 2
1.6 Apache License,
Version 2
0.2 Apache License,
Version 2
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
https:/www.redhat.com/licenses/gpl.html
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
commonsfileupload
commonshttpclient
commons-io 1.4 Apache License,
commons-jexl 1.0 Apache License,
commonsjxpath
commons-lang 2.3 Apache License,
commonslogging
commons-pool 1.3 Apache License,
corosync 1.2.5 BSD http://opensource.org/licenses/bsd-license.php
Polycom, Inc. 17
1.2.1 Apache License,
Version 2
3.0.1 Apache License,
Version 2
Version 2
Version 2
1.2 Apache License,
Version 2
Version 2
1.0.4 Apache License,
Version 2
Version 2
http://commons.apache.org/fileupload/license.html
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
Page 30
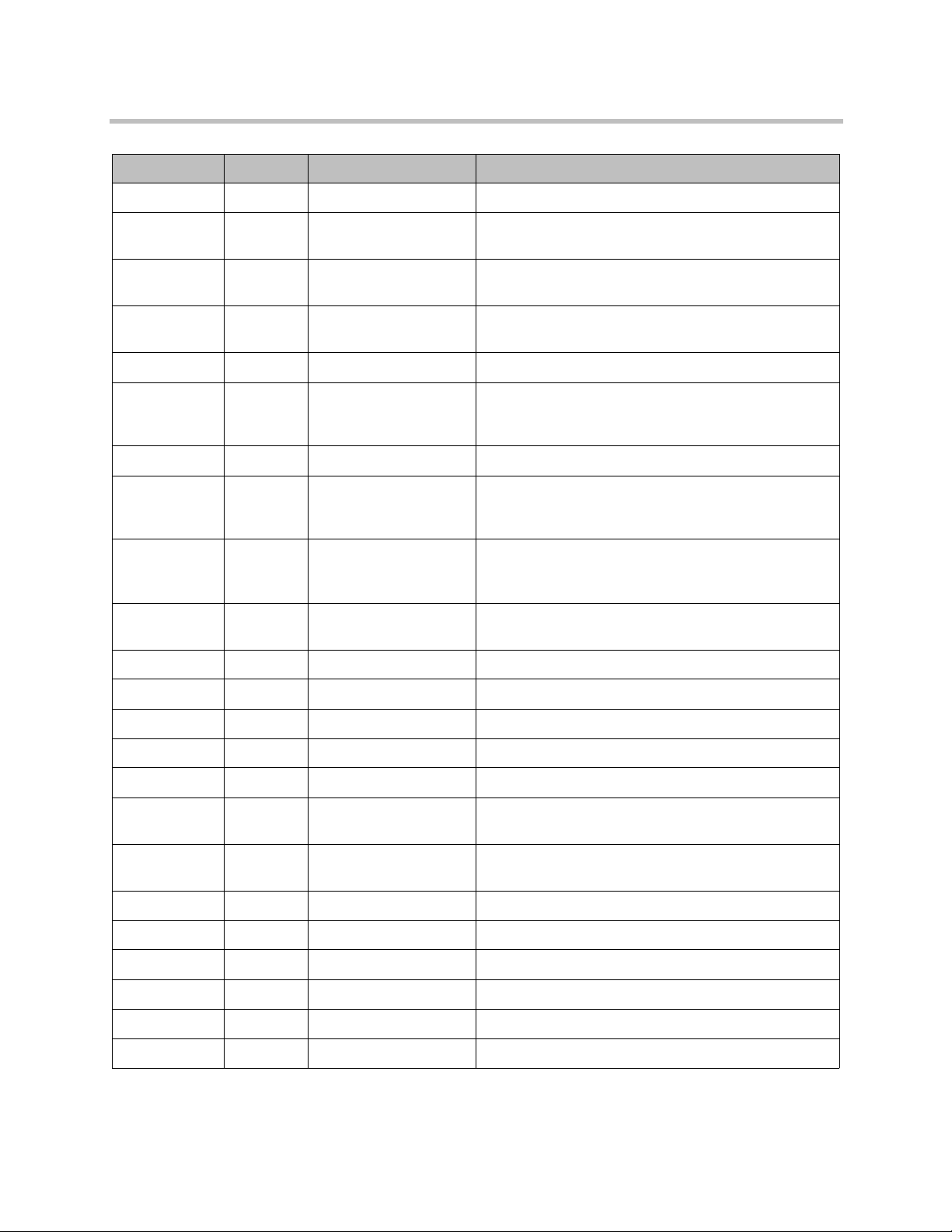
DMA Operations Guide Third-Party Software
Software Version License Link
dom4j 1.5.2 BSD-style http://www.dom4j.org/license.html
drools 4.0.0 Apache License,
Version 2
Hibernate
Annotations
Hibernate
(core)
Hsqldb 2.0.1-rc1 BSD-style http://hsqldb.org/web/hsqlLicense.html
JAF 1.1 Oracle Corporation
jamon 2.2 BSD-style http://jamonapi.sourceforge.net/#JAMonLicense
Java JRE 1.7.0.9 Oracle Corporation
JavaMail 1.4 Oracle Corporation
jaxb2-basicsruntime
JBOSS AS 4.2.1 GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
4.2.1.GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
3.2.4 SP 1 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Binary Code License
Agreement
Binary Code License
Agreement
Binary Code License
Agreement
0.6.0 BSD-style http://confluence.highsource.org/display/J2B/License
http://www.apache.org/licenses/LICENSE-2.0
http://www.oracle.com/technetwork/java/javase/
downloads/java-se-archive-license-1382604.html
http://www.java.com/en/download/license.jsp
http://www.oracle.com/technetwork/java/
javasebusiness/downloads/java-archive-downloadseeplat-419426.html#javamail-1.4-oth-JPR
Jboss-aop 1.5.5 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Jboss-cache 1.4.1.sp14 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Jboss-jaxws 2.0.0.GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Jboss-jmx 4.2.1.GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Jboss-
remoting
Jboss-
serialization
Jgroups 2.4.8.GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
jcifs 1.3.2 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
jna 3.0.9 b0 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
joesnmp 0.3.4 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
jsr31 1-api 1.1.1 CDDL http://www.opensource.org/licenses/cddl1.php
libesmtp 1.0.4 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
18 Polycom, Inc.
2.2.2.sp1 LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
4.2.1.GA LGPLv2.1 http://www.gnu.org/licenses/old-licenses/lgpl-2.1.html
Page 31

Third-Party Software Polycom® DMA™7000 System Overview
Software Version License Link
libnet 1.1.4
libxml2 1.2.3 MIT License http://www.opensource.org/licenses/mit-license.html
Log4j 1.2.14 Apache License,
Version 2
neethi 3.0.1 Apache License,
Version 2
NSS Part of
Centos
distrib.
NSS Tools Part of
Centos
distrib.
NTP Part of
Centos
distrib.
OpenDJ 2.5.0 CDDL-1.0 http://www.opensource.org/licenses/cddl1.php
openSSH Part of
Centos
distrib.
openSSL Part of
Centos
distrib.
Python Part of
Centos
distrib.
Mozilla Public License
v1.1
Mozilla Public License
v1.1
Open Software License
v3.0
OpenSSH http://www.openssh.org
OpenSSL http://www.openssl.org/source/license.html
Python Software
Foundation License
Version 2
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.mozilla.org/projects/security/pki/nss/
faq.html#q3.1
http://www.mozilla.org/projects/security/pki/nss/
faq.html#q3.1
http://www.opensource.org/licenses/ntp-license.php
http://python.org/download/releases/2.6.2/license
Quartz 1.5.2 Apache License,
Version 2
sudo 1.7.2p1 ISCL https://www.isc.org/software/license
Xerces2 See
JBoss.
OpenFire Apache License,
Rhino Mozilla Public License,
Polycom, Inc. 19
Apache License,
Version 2
Version 2
v1.1
http://www.apache.org/licenses/LICENSE-2.0
http://www.apache.org/licenses/LICENSE-2.0
http://www.igniterealtime.org/builds/openfire/docs/latest/
LICENSE.html
http://www.mozilla.org/MPL/MPL-1.1.html AND
https://developer.mozilla.org/en/Rhino_License
Page 32

DMA Operations Guide Third-Party Software
Software Version License Link
Web App
Solution, Inc.
Flex 3
dashboard
xmlschemacore
The Open Source packages below are included in the Polycom DMA system as a consequence of being embedded
in the Java Platform, Standard Edition Embedded, version 6.0. License text is available at
http://downloads.polycom.com/Oracle/THIRDPARTYLICENSEREADME.TXT
CS
CodeViewer
Crimson v1.1.1 Apache 1.1
Xalan J2 Apache 2.0
NSIS 1.0j (see license file)
IAIK PKCS
Wrapper
Document
Object Model
(DOM)
2.0 Apache License,
v1.0 BSD-like
v. Level 3 W3C SOFTWARE
Creative Commons
Attribution-
Noncommercial-Share
Alike 3.0 Unported
License, with a Creative
Commons Plus License
for commercial rights to
the work.
Version 2
BSD-like
NOTICE AND LICENSE
http://creativecommons.org/licenses/by-nc-sa/3.0/
http://www.adobe.com/communities/guidelines/ccplus/
commercialcode_plus_permission.html
http://www.apache.org/licenses/LICENSE-2.0
Xalan, Xerces Apache 1.1
W3C XML
Conformance
Test Suites
W3C XML
Schema Test
Collection
Mesa 3-D
graphics
library
20 Polycom, Inc.
v.
20020606
v. 1.16.2 W3C SOFTWARE
v. 5 The core Mesa library is
W3C SOFTWARE
NOTICE AND LICENSE
NOTICE AND LICENSE
licensed according to
the terms of the
XFree86copyright (an
MIT-style license). The
Mesa source code is
licensed under SGI
FREE SOFTWARE
LICENSE B (Version
1.1 [02/22/2000])
Page 33

Third-Party Software Polycom® DMA™7000 System Overview
Software Version License Link
Byte Code
Engineering
Library (BCEL)
Regexp
Regular
Expression
Package
CUP Parser
Generator for
Java
JLex Lexical
Analyzer
Generator for
Java
SAX v. 2.0.1 Public Domain
Cryptix Cryptix General License
W3C XML
Schema Test
Collection
Stax API BEA License (unique
v. 5 Apache 1.1
v. 1.2 Apache 1.1
v. 0.10k (general permissive
license)
v. 1.2.5 (general permissive
license)
W3C DOCUMENT
NOTICE AND LICENSE
terms)
X Window
System
dom4j v. 1.6 BSD-like
Retroweaver (general permissive
Stripper BSD-like
libpng official
PNG reference
library
Libungif - An
uncompressed
GIF library
Ant Apache 2.0
XML Resolver
Library
ICU4J ICU License
NekoHTML Apache-like (1.1)
Jing (general permissive)
(general permissive
license)
license)
(general permissive
license)
(general permissive
license)
Apache 2.0
Polycom, Inc. 21
Page 34

DMA Operations Guide Third-Party Software
Software Version License Link
RelaxNGCC (general permissive)
RELAX NG
Object Model/
Parser
XFree86VidMode
Extension
RelaxNGCC version 2003-May-08 of
XML Security Apache 1.1
Regexp
Regular
Expression
Package
Zlib (general permissive)
Mozilla Rhino Netscape Public
Apache Derby Apache 2.0
7-Zip See file. Some files are
v. 1.2 Apache 1.1
MIT License
Version 1.1 of Project
Licence (BSD-like)
the Info-ZIP copyright
and license
License Version 1.1
LGPLv2.1; some have
unRAR restriction;
some are licensed
under AES code
license.
ftp://ftp.info-zip.org/pub/infozip/license.html
UPX GPL
LZMA
Software
Development
Kit
22 Polycom, Inc.
Common Public
License (CPL)
Page 35

Polycom® DMA™ System Initial Configuration Summary
2
This chapter describes the configuration tasks required to complete your
implementation of a new Polycom
(DMA™) 7000 system once installation and initial network configuration are
complete.
This chapter assumes you’ve completed the server configuration procedure in
the Getting Started Guide (available at support.polycom.com), logged into the
Polycom DMA system’s management interface, and verified that the
Supercluster Status pane of the Dashboard shows (for a two-server
configuration) two servers in the cluster, with healthy enterprise and private
network status for both.
Initial configuration includes the following topics:
System configuration
• Add Required DNS Records for the Polycom DMA System
• License the Polycom DMA System
• Set Up Signaling
• Configure the Call Server and Optionally Create a Supercluster
• Set Up Security
• Set Up MCUs
• Connect to Microsoft Active Directory
®
Distributed Media Application™
• Set Up Conference Templates
Confirming configuration
• Test the System
Each topic describes the task, provides background and overview information
for it, and where appropriate, links to specific step-by-step procedures to
follow in order to complete the task.
Polycom, Inc. 23
Page 36

DMA Operations Guide Add Required DNS Records for the Polycom DMA System
Note
These topics outline the configuration tasks that are generally required. You may
wish to complete other optional configuration tasks, including:
• Enable cascading of conferences (see “About Cascading” on page 198).
• Configure calendaring service (“Microsoft Exchange Server Integration” on
page 180).
Add Required DNS Records for the Polycom DMA System
Note
If you’re not familiar with DNS administration, the creation of various kinds of DNS
resource records (A/AAAA,NAPTR, NS, and SRV), your enterprise’s DNS
implementation, and tuning for load balancing (if needed), please consult with
someone who is.
In order to access your Polycom DMA system by its host name instead of by
IP address, you (or your DNS administrator) must first create an A (address)
resource record (RR) for IPv4 and/or AAAA record for IPv6 on your DNS
server(s).
For a two-server cluster configuration, at a minimum, create a record for the
virtual host name and IP address. This address is shared between the servers
in a two-server cluster configuration. For administrative convenience, we
recommend that you also create alias records for the physical host name(s) and
IP address(es). For a superclustered system, A/AAAA records for each
physical host name, physical IP address, virtual host name, and virtual IP
address are mandatory.
Note
Depending on local DNS configuration, the host name could be the Polycom DMA
system’s fully qualified domain name (FQDN) or a shorter name that DNS can
resolve. For some features, such as Microsoft Exchange Server integration, it’s
imperative that the virtual host’s FQDN can be resolved in DNS, especially by the
Exchange server.
If you’re using split network interfaces, we recommend creating alias records for
both the management and signaling host names and addresses.
The DNS server(s) should also have entries for your Microsoft® Active
Directory® server (if different from the DNS server) and any external
gatekeepers or SIP peers.
You may need to create additional DNS records as described below.
24 Polycom, Inc.
Page 37

Add Required DNS Records for the Polycom DMA System Polycom® DMA™ System Initial Configuration Summary
Additional DNS Records for SIP Proxy
To support the use of your Polycom DMA system as a SIP proxy server and
ease future network administrative burdens, create the following DNS records
(for each cluster in a supercluster, if applicable):
• Optionally, NAPTR records that describe the transport protocols
supported by the SIP proxies at a domain and identify the preferred
protocol. Configure these statically to match the system’s SIP transport
protocol configuration.
• SRV records for each transport protocol that identify the host names of the
SIP proxies that service a particular domain. Configure these statically to
point to the host names of the Call Servers in the domain. Here are
example records for two clusters:
_sips._tcp.example.com. 86400 IN SRV 10 1001 5061 dma-asia.example.com.
_sips._tcp.example.com. 86400 IN SRV 10 1002 5061 dma-europe.example.com.
_sip._tcp.example.com. 86400 IN SRV 20 1001 5060 dma-asia.example.com.
_sip._tcp.example.com. 86400 IN SRV 20 1002 5060 dma-europe.example.com.
_sip._udp.example.com. 86400 IN SRV 30 1001 5060 dma-asia.example.com.
_sip._udp.example.com. 86400 IN SRV 30 1002 5060 dma-europe.example.com.
To enable access from the public internet, create corresponding SRV records,
visible from outside the firewall, for the public address of each SIP session
border controller (SBC).
For more information about the use of DNS in SIP, refer to RFCs 3263 and 2782.
Additional DNS Records for H.323 Gatekeeper
To support the use of your Polycom DMA system as an H.323 gatekeeper and
ease future network administrative burdens, create SRV records that identify
the host names of the gatekeepers that service a particular domain. These
records are necessary in order to enable the optional inbound URL dialing
feature. Configure them statically to point to the host names of the Call Servers
in the domain. Here are example records for two clusters:
_h323ls._udp.example.com. 86400 IN SRV 0 1 1719 dma-asia.example.com.
_h323ls._udp.example.com. 86400 IN SRV 0 1 1719 dma-europe.example.com.
_h323cs._tcp.example.com. 86400 IN SRV 0 1 1720 dma-asia.example.com.
_h323cs._tcp.example.com. 86400 IN SRV 0 1 1720 dma-europe.example.com.
To enable access from the public internet, create corresponding SRV records,
visible from outside the firewall, for the public address of each H.323 session
border controller (SBC).
For more information about the use of DNS in H.323, refer to the H.323
specification, Annex O, and the H.225.0 specification, Appendix IV.
Polycom, Inc. 25
Page 38

DMA Operations Guide License the Polycom DMA System
Additional DNS Records for the Optional Embedded DNS Feature
To support DNS publishing by your Polycom DMA system’s embedded DNS
servers (see “Embedded DNS” on page 279), a DNS NS record is needed for
each cluster in the supercluster. These records identify the Polycom DMA
system’s embedded DNS servers as authoritative for the specified logical host
name. Here are example records for two clusters:
callservers.example.com. 86400 IN NS dma-asia.example.com.
callservers.example.com. 86400 IN NS dma-europe.example.com.
Your enterprise DNS must also have the zone callservers.example.com
defined and be configured to forward requests for names in that zone to any
of the clusters in the supercluster. The way you do this depends on the DNS
server software being used.
Queries to the enterprise DNS for callservers.example.com are referred to the
specified DMA clusters. Their embedded DNS servers create and manage A
records for each site in the site topology. When responsibility for a site moves
from one cluster to another, the A records are updated so that the site’s domain
name is mapped to the new cluster.
Verify That DNS Is Working for All Addresses
To confirm that DNS can resolve all the host names and/or FQDNs, ping each
of them, either from a command prompt on the PC you’re using to access the
system or from one of the clusters you’re setting up (go to Troubleshooting
Utilities > Ping).
If you have access to a Linux PC and are familiar with the dig command, you
can use it to query the enterprise DNS server to verify that all the records
(A/AAAA, NS, and SRV) are present and look correct.
License the Polycom DMA System
A Polycom DMA system is licensed at the cluster level (single-server or
two-server). A cluster’s license specifies:
• The maximum number of concurrent calls that can touch the cluster. In a
supercluster configuration, note that:
— A single call may touch more than one cluster. It consumes a license
on each cluster it touches.
— Each cluster may be licensed for a different number of calls.
— If your superclustering strategy (see “About Superclustering” on
page 227) calls for a cluster to be primary for one territory and backup
for another, it must be licensed for the call volume expected when it
has to take over the territory for which it’s the backup.
26 Polycom, Inc.
Page 39

Set Up Signaling Polycom® DMA™ System Initial Configuration Summary
• Whether the RealPresence Platform Application Programming Interface
(API) is enabled. The API provides an API client application with
programmatic access to the Polycom DMA system (see “RealPresence
Platform API” on page 3). In a supercluster, all clusters must have the
same API licensing status.
Note
An API license isn’t required in order for a Polycom RealPresence
Resource Manager system to access the API. It’s only needed for a client
application you or a third party develop.
You should have received either one or two license numbers for each cluster,
depending on whether you ordered a single-server or two-server cluster.
You must obtain an activation key code for each server from the Polycom
Resource Center (PRC). You enter the server’s serial number and the license
number that you were given for that server, and the PRC generates an
activation key for that server. For a cluster, you repeat the process using the
other server’s serial number and its license number. Installing the activation
keys activates the licenses for your system.
Set Up Signaling
Caution
An activation key is linked to a specific server’s serial number. For a two-server
cluster, you must generate the activation key for each server using that server’s
serial number.
Licensing will fail if you generate both activation keys from the same server serial
number.
To activate the system license, follow the procedure in “Licenses” on page 70.
Signaling setup includes enabling H.323, SIP, or both, and optionally setting
the prefix for dialing into the system.
Note
The addition of the Call Server and superclustering features to the Polycom DMA
system required significant changes to the signaling internals. One consequence of
these changes is that the Polycom DMA system can no longer register to an
external gatekeeper as an MCU. Instead, it can neighbor to an external gatekeeper
as another gatekeeper. As a result, if you’re upgrading from a version that didn’t
include the Call Server functionality or that operated in what was known as “legacy
signaling mode,” you need to reconfigure your external gatekeeper.
Polycom, Inc. 27
Page 40

DMA Operations Guide Configure the Call Server and Optionally Create a Supercluster
To configure signaling, follow the procedure in “Configure Signaling” on
page 83.
Configure the Call Server and Optionally Create a Supercluster
Configuring the Polycom DMA system’s Call Server function consists of the
following high-level tasks:
1 Integrate with a Polycom RealPresence Resource Manager or CMA
system (see “Resource Management System Integration” on page 185) or
enter site topology information (see “Site Topology” on page 283).
2 If deploying a supercluster of multiple geographically distributed
Polycom DMA clusters:
a Set the Security Configuration page security options before
superclustering (see “Security Settings” on page 48). But wait until
after superclustering to do the rest of the security setup tasks.
Set Up Security
b Depending on security settings, you may need to install certificates
before superclustering (see “Certificate Procedures” on page 42).
c Create a supercluster (see “About Superclustering” on page 227) and
configure supercluster options.
3 Create territories and assign sites to them (if you integrated with a
Polycom RealPresence Resource Manager or CMA system, this must be
done on that system). Assign the primary and backup cluster responsible
for each territory, and designate which territories can host conference
rooms (see “Territories” on page 302).
4 Add any external devices, such as a neighbor gatekeeper or SIP peer (see
“Call Server Configuration” on page 237).
5 Configure the dial plan (see “Dial Rules” on page 243).
The first step in securing your Polycom DMA system is to locate it in a secure
data center with controlled access, but that topic is beyond the scope of this
document.
Secure setup of the Polycom DMA system consists of the following high-level
tasks (some of which assume you’re integrating with Active Directory and
some of which overlap with other initial setup topics):
28 Polycom, Inc.
Page 41

Set Up MCUs Polycom® DMA™ System Initial Configuration Summary
1 As the default local administrative user (admin), create a local user
account for yourself with the Administrator role, log in using that
account, and delete the admin user account. See “Adding Users
Overview” on page 313 and “Users Procedures” on page 333.
2 Create the Active Directory service account (read-only user account) that
the Polycom DMA system will use to read and integrate with Active
Directory. See “Active Directory Integration Procedure” on page 169.
3 Assign the Administrator role to your named enterprise account, and
remove the Polycom DMA system’s user roles (see “User Roles
Overview” on page 312) from the service account used to integrate with
Active Directory. See “Connect to Microsoft Active Directory” on page 32
and “Microsoft Active Directory Integration” on page 163.
4 Log out and log back in using your enterprise user ID and password.
5 Verify that the expected enterprise users are available in the Polycom
DMA system and that conference room IDs were successfully created for
them. If necessary, adjust integration settings and correct errors. See
“Microsoft Active Directory Integration” on page 163, “Users
Procedures” on page 333, and “Conference Room Errors Report” on
page 422.
Set Up MCUs
6 Obtain and install a security certificate from a trusted certificate
authority. See “Security Certificates Overview” on page 35 and
“Certificate Procedures” on page 42.
7 Document your current configuration for comparison in the future. We
recommend saving screen captures of all the configuration pages.
8 Manually create a backup, download it, and store it in a safe place. See
“Backing Up and Restoring” on page 381.
Note
The Polycom DMA system can interact with MCUs, or media servers, in either or
both of the following two ways:
• MCUs may be made available to system’s Conference Manager to manage for
multi-point conferencing (hosting virtual meeting rooms, or VMRs).
• MCUs may be registered with the system’s Call Server as standalone MCUs
and/or gateways.
This configuration summary assumes you want to do both.
Make sure your RMX MCUs are configured to accept encrypted (HTTPS)
management connections (required for maximum security mode).
Polycom, Inc. 29
Page 42

DMA Operations Guide Set Up MCUs
Make sure that each MCU is in a site belonging to a territory for which the
Polycom DMA system is responsible. If you’re deploying a supercluster (see
“Configure the Call Server and Optionally Create a Supercluster” on page 28
and “About Superclustering” on page 227), make sure that each territory has
a primary and backup cluster assigned to it. If the primary cluster becomes
unavailable, the MCUs registered to it can re-register to the backup.
If you’re deploying a supercluster, verify that you’ve enabled the hosting of
conference rooms in the right territories and assigned clusters to those
territories. See “Configure the Call Server and Optionally Create a
Supercluster” on page 28.
Standalone MCUs can register themselves to the Polycom DMA system’s Call
Server. To make an MCU available as a conferencing resource, either add it to
the appropriate Polycom DMA cluster’s Conference Manager manually or, if
it’s already registered with the Call Server, edit its entry to enable it for
conference rooms and provide the additional configuration information
required. See “MCU Management” on page 131.
You must organize MCUs configured as conferencing resources into one or
more MCU pools (logical groupings of media servers). Then, you can define
one or more MCU pool orders that specify the order of preference in which
MCU pools are used.
Note
If you have a Polycom RealPresence Resource Manager system that’s going to use
the DMA system API to schedule conferences on the DMA system’s conferencing
resources (MCU pools), you must create MCU pools and pool orders specifically for
the use of the RealPresence Resource Manager system. The pool orders should be
named in such a way that:
• They appear at the top of the pool order list presented in the RealPresence
Resource Manager system.
• Users of that system will understand that they should choose one of those pool
orders.
If the RealPresence Resource Manager system is also going to be used to directly
schedule conferences on MCUs, those MCUs should not be part of the
conferencing resources (MCU pools) available to the DMA system.
Every conference room (VMR) is associated with an MCU pool order. The
pool(s) to which an MCU belongs, and the pool order(s) to which a pool
belongs, are used to determine which MCU is used to host a conference. See
“MCU Pools” on page 152 and “MCU Pool Orders” on page 156 for
information about how to use pools and pool orders, as well as the rules that
the system uses to choose an MCU for a user.
The Polycom DMA system uses conference templates to define the
conferencing experience associated with a conference room or enterprise
group. You can create standalone templates (recommended), setting the
conferencing parameters directly in the Polycom DMA system, or link
templates to RMX conference profiles (see “Conference Templates” on
page 195).
30 Polycom, Inc.
Page 43

Set Up MCUs Polycom® DMA™ System Initial Configuration Summary
Both methods allow you to specify most conference parameters:
• General information such as line rate, encryption, auto termination, and
H.239 settings
• Video settings such as mode (presentation or lecture) and layout
• IVR settings
• Conference recording settings
If you want to create DMA system templates linked to conference profiles on
the RMX MCUs, make sure the profiles used by the Polycom DMA system
exist on all the RMX MCUs and are defined the same on all of them.
Polycom, Inc. 31
Page 44

DMA Operations Guide Connect to Microsoft Active Directory
Connect to Microsoft Active Directory
Connecting to Microsoft® Active Directory® simplifies the task of deploying
conferencing to a large organization. All Polycom DMA system access to the
Active Directory server is read-only and minimally impacts the directory
performance. See “Microsoft Active Directory Integration” on page 163.
Note
If you’re not knowledgeable about enterprise directories in general and your specific
implementation in particular, please consult with someone who is. Active Directory
integration is a non-trivial matter.
Before integrating with Active Directory, be sure that one or more DNS servers
are specified (this should have been done during installation and initial setup).
See “Network Settings” on page 64.
If you’re deploying a supercluster of multiple geographically distributed
Polycom DMA clusters, verify that you’ve assigned clusters to the territories
in your site topology (see “Configure the Call Server and Optionally Create a
Supercluster” on page 28) and decide which cluster is to be responsible for
Active Directory integration.
Active Directory integration automatically makes the enterprise users
(directory members) into Conferencing Users in the Polycom DMA system,
and can assign each of them a conference room (virtual meeting room, or
VMR). The conference room IDs are typically generated from the enterprise
users’ phone numbers.
Note
Creating conference rooms for enterprise users is optional. If you want to integrate
with Active Directory to load user and group information into the Polycom DMA
system, but don’t want to give all users the ability to host conferences, you can do
so. You can manually add conference rooms for selected users at any time. See
“Conference Rooms Procedures” on page 335.
Once the Polycom DMA system is integrated with Active Directory, it reads
the directory information nightly, so that user and group information is
updated automatically as people join and leave the organization. The system
caches certain data from Active Directory. In a superclustered system, one
cluster is responsible for updating the cache, which is shared with all the
clusters.
Between updates, clusters access the directory only to authenticate passwords
(for instance, for management interface login); all other user information (such
as user search results) comes from the cache. You can manually update the
cache at any time.
32 Polycom, Inc.
Page 45

Set Up Conference Templates Polycom® DMA™ System Initial Configuration Summary
Enterprise groups can have their own conference templates that provide a
custom conferencing experience (see “Conference Templates” on page 195).
They can also have their own MCU pool order, which preferentially routes
conferences to certain MCUs (see “MCU Pool Orders” on page 156).
You can assign Polycom DMA system roles to an enterprise group, applying
the roles to all members of the group and enabling them to log into the
Polycom DMA system’s management interface with their standard network
user names and passwords.
See “User Roles Overview” on page 312, “Groups” on page 338, and
“Enterprise Groups Procedures” on page 342.
There are security concerns that need to be addressed regarding user accounts,
whether local or enterprise. See the high-level process described in “Set Up
Security” on page 28.
Set Up Conference Templates
Test the System
The Polycom DMA system uses conference templates and global conference
settings to manage system and conference behavior, and it has a default
conference template and default global conference settings.
After you’ve added MCUs to the system, you may want to change the global
conference settings or create additional templates that specify different
conference properties.
If you integrate with Active Directory, you can use templates to provide
customized conferencing experiences for various enterprise groups.
When you add a custom conference room to a user (either local or enterprise),
you can choose which template that conference room uses.
To add conference templates, see “Conference Templates Procedures” on
page 220. To change conference settings, see “Conference Settings” on
page 193. To customize the conferencing experience for an enterprise group,
see “Enterprise Groups Procedures” on page 342.
On the Signaling Settings page (see “Signaling Settings” on page 71), verify
that:
• If you enabled H.323, the H.323 Signaling Status section indicates that the
signaling status is Active and the port assignments are correct.
• If you enabled SIP, the SIP Signaling Status section shows that the correct
protocols and listening ports are enabled.
Polycom, Inc. 33
Page 46

DMA Operations Guide Test the System
Have some endpoints register with the Polycom DMA Call Server and make
point-to-point calls to each other.
On the Dashboard (see “Dashboard” on page 352), verify that:
• The information in the Cluster Info pane looks correct, including the time,
network settings, and system resource information.
• The Supercluster Status pane shows the correct number of servers and
clusters, and the network interfaces that should be working (depending on
your IP ty pe and spl it net work set tings ) ar e up ( green up a rrow ) and in fu ll
duplex mode, with the speed correct for your enterprise network.
• The Call Server Registrations pane shows that the endpoints that
attempted to register did so successfully.
• The Call Server Active Calls pane shows that the endpoints that made
calls did so successfully, and the call limits per cluster and total are correct
for your licenses.
• The Conference Manager MCUs pane shows that the MCUs you added
are connected and in service.
• The information on the Active Directory Integration pane looks correct,
including the status, cache refresh data, and enterprise conference room
count.
Set up some multipoint conferences by having endpoints dial into enterprise
users’ conference rooms (preferably including a custom conference room).
Verify that conferencing works satisfactorily, that the system status is good,
and that the Conference Manager Usage pane accurately presents the status.
When you’re satisfied that the Polycom DMA system is configured and
working properly, manually create a backup, download it, and store it in a safe
place. See “Backing Up and Restoring” on page 381.
34 Polycom, Inc.
Page 47

System Security
This chapter describes the following Polycom® Distributed Media
Application™ (DMA™) 7000 system security topics:
• Security Certificates Overview
• Certificate Settings
• Certificate Procedures
3
• Security Settings
• The Consequences of Enabling Maximum Security Mode
• Login Policy Settings
• Reset System Passwords
Security Certificates Overview
How Certificates Work
X.509 certificates are a security technology that assists networked computers
in determining whether to trust each other.
• A single, centralized certificate authority (CA) is established. Typically,
this is either an enterprise’s IT department or a commercial certificate
authority.
• Each computer on the network is configured to trust the central certificate
authority.
• Each server on the network has a public certificate that identifies it.
• The certificate authority signs the public certificates of those servers that
clients should trust.
Polycom, Inc. 35
Page 48

DMA Operations Guide Security Certificates Overview
• When a client connects to a server, the server shows its signed public
certificate to the client. Trust is established because the certificate has been
signed by the certificate authority, and the client has been configured to
trust the certificate authority.
Forms of Certificates Accepted by the Polycom DMA System
X.509 certificates come in several forms (encoding and protocol). The
following table shows the forms that can be installed in the Polycom DMA
system.
Protocol /
Encoding
File Type
Description and Installation Method
PEM
(Base64-encoded
ASCII text)
DER
(binary format
using ASN.1
Distinguished
Encoding Rules)
PKCS #7
protocol
P7B file
CER (single
certificate) file
Certificate text Encoded certificate text copied from
PKCS #12
protocol
PFX file
PKCS #7
protocol
P7B file
Certificate chain containing:
• A signed certificate for the system,
authenticating its public key.
• The CA’s public certificate.
• Sometimes intermediate
certificates.
Upload file or paste into text box.
Signed certificate for the system,
authenticating its public key.
Upload file or paste into text box.
CA’s email or secure web page.
Paste into text box.
Certificate chain containing:
• A signed certificate for the system,
authenticating its public key.
• A private key for the system.
• The CA’s public certificate.
Upload file.
Certificate chain containing:
• A signed certificate for the system,
authenticating its public key.
• The CA’s public certificate.
• Sometimes intermediate
certificates.
Upload file.
CER (single
certificate) file
36 Polycom, Inc.
Signed certificate for the system,
authenticating its public key.
Upload file.
Page 49

Security Certificates Overview System Security
How Certificates Are Used by the Polycom DMA System
The Polycom DMA system uses X.509 certificates in the following ways:
1 When a user logs into the Polycom DMA system’s browser-based
management interface, the Polycom DMA system (server) offers an X.509
certificate to identify itself to the browser (client).
The Polycom DMA system’s certificate must have been signed by a
certificate authority (see “Certificate Procedures” on page 42).
The browser must be configured to trust that certificate authority (beyond
the scope of this documentation).
If trust can’t be established, most browsers allow connection anyway, but
display a ‘nag’ dialog to the user, requesting permission.
2 When the Polycom DMA system connects to a Microsoft Active Directory
server, it may present a certificate to the server to identify itself.
If Active Directory is configured to require a client certificate (this is not
the default), the Polycom DMA system offers the same SSL server
certificate that it offers to browsers connecting to the system management
interface. Active Directory must be configured to trust the certificate
authority, or it rejects the certificate and the connection fails.
3 When the Polycom DMA system connects to a Microsoft Exchange server
(if the calendaring service is enabled; see
Integration”
identify itself.
Unless the Allow unencrypted calendar notifications from Exchange
server security option is enabled (see “Security Settings” on page 48), the
Polycom DMA system offers the same SSL server certificate that it offers
to browsers connecting to the system management interface. The
Microsoft Exchange server must be configured to trust the certificate
authority. Otherwise, the Microsoft Exchange Server integration status
(see “Dashboard” on page 352) remains Subscription pending
indefinitely, the Polycom DMA system does not receive calendar
notifications, and incoming meeting request messages are only processed
approximately every 4 minutes.
4 When the Polycom DMA system connects to an RMX MCU configured
for secure communications (this is not the default), a certificate may be
used to identify the RMX MCU (server) to the Polycom DMA system
(client).
5 When performing call signaling requiring TLS, the Polycom DMA system
presents its certificate to the connecting client (one-way TLS). Unless the
Skip certificate validation for encrypted signaling security option is
enabled (see “Security Settings” on page 48), the system uses the installed
CA certificates to authenticate the connecting client’s certificate as well
(mTLS or two-way TLS).
on page 180), it may present a certificate to the server to
“Microsoft Exchange Server
Polycom, Inc. 37
Page 50

DMA Operations Guide Certificate Settings
Frequently Asked Questions
Q. Is it secure to send my certificate request through email?
A. Yes. The certificate request, signed certificate, intermediate certificates,
and authority certificates that are sent through email don’t contain any
secret information. There is no security risk in letting untrusted third
parties see their contents.
As a precaution, you can verify the certificate fingerprints (which can be
found in the Certificate Details popup) with the certificate authority via
telephone. This ensures that a malicious third party didn’t substitute a
fake email message with fake certificates.
Q. Why doesn’t the information on the Certificate Details popup match
the information that I filled out in the signing request form?
A. Commercial certificate authorities routinely replace the organizational
information in the certificate with their own slightly different description
of your organization.
Q. I re-installed the Polycom DMA system software. Why can’t I re-install
my signed public certificate?
See also:
Certificate Settings
A. X.509 certificates use public/private key pair technology. The public
key is contained in your public certificate and is provided to any web
browser that asks for it. The private key never leaves the Polycom DMA
system.
As part of software installation, the Polycom DMA system generates a
new public/private key pair. The public key from your old key pair can’t
be used with the new private key.
To re-use your signed public certificate, try restoring from backup. Both
the public and private keys are saved as part of a backup file.
Alternatively, if the certificate you want to reinstall is a PKCS#12
certificate, it contains a private key and will replace both the public key
and the private key generated at installation time.
“System Security” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
The following table describes the fields on the Certificate Settings page.
38 Polycom, Inc.
Page 51

Certificate Settings System Security
Table 3-1 Fields on the Certificate Settings page
Column Description
Enable OCSP Enables the use of Online Certificate Status Protocol as
a means of obtaining the revocation status of a
certificate presented to the system.
If OCSP responder URL is not specified, the system
checks the certificate’s AuthorityInfoAccess (AIA)
extension fields for the location of an OCSP responder:
• If there is none, the certificate fails validation.
• Otherwise, the system sends the OCSP request to
the responder identified in the certificate.
If OCSP responder URL is specified, the system sends
the OCSP request to that responder.
The responder returns a message indicating whether
the certificate is good, revoked, or unknown.
If OCSP certificate is specified, the response message
must be signed by the specifi ed cert ificat e’ s p rivate k ey.
OCSP responder URL Identifies the responder to be used for all OCSP
requests, overriding the AIA field values.
If OCSP certificate is specified, the response message
must be signed by the specifi ed cert ificat e’ s p rivate k ey.
OCSP certificate Select a certificate to require OCSP response
messages to be signed by the specified certificate’s
private key.
Store OCSP
Configuration
Identifier Common name of the certificate.
Purpose Kind of certificate:
Saves the OCSP configuration.
• Server SSL is the DMA system’s public certificate,
which it presents to identify itself. By default, this is
a self-signed certificate, not trusted by other
devices.
• Trusted Root CA is the root certificate of a certificate
authority that the DMA system trusts.
• Intermediate CA is a CA certificate that trusted root
CAs issue themselves to sign certificate signing
requests (reducing the likelihood of their root
certificate being compromised). If the DMA system
trusts the root CA, then the chain consisting of it, its
intermediate CA certificates, and the server
certificate will all be trusted.
Expiration Expiration date of certificate.
Polycom, Inc. 39
Page 52

DMA Operations Guide Certificate Settings
See also:
“Security Certificates Overview” on page 35
“Certificate Information Dialog Box” on page 40
“Certificate Signing Request Dialog Box” on page 40
“Add Certificates Dialog Box” on page 41
“Certificate Details Dialog Box” on page 41
“Certificate Procedures” on page 42
Certificate Information Dialog Box
The Certificate Information dialog box appears when you click Create
Certificate Signing Request in the Actions list (if a signing request has
already been issued, you’re first asked whether to use the existing one or create
a new one). The following table describes the fields in the dialog box.
Table 3-2 Fields in the Certificate Information dialog box
Field Description
Common name (CN) Defaults to the FQDN of the system’s management
Organizational unit
(OU)
Organization (O) Optional.
City or locality (L) Optional.
State (ST) Optional.
Country (C) Two-character country code.
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Certificate Signing Request Dialog Box
interface, as defined by the virtual host name and
domain specified on the Network page. Editable.
Subdivision of organization. Specify up to three OUs.
Optional.
The Certificate Signing Request dialog box appears when you create a
request in the Certificate Information dialog box.
The Summary section at the top displays the information the Certificate
Information dialog box.
40 Polycom, Inc.
Page 53

Certificate Settings System Security
The Encoded Request box below displays the encoded certificate request text,
which you can select and copy.
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Add Certificates Dialog Box
The Add Certificates dialog box appears when you click Add Certificates in
the Actions list. It lets you install signed certificates or certificate chains. You
can do so in two ways:
• Upload a PFX, PEM, or P7B certificate file.
• Paste PEM-format certificate text into the dialog box.
The following table describes the fields in the dialog box.
Table 3-3 Fields in the Add Certificates dialog box
Field Description
Upload certificate If checked, the Password field and Upload file button
Password Enter the password, if any , assigned to the certificate file
Upload file Click the button to browse to the file you want to upload.
Paste certificate If checked, the text field below enables you to paste in
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Certificate Details Dialog Box
The Certificate Details dialog box appears when you click Display Details in
the Actions list. It displays information about the certificate selected in the list,
as outlined in the following table.
enable you to upload a PFX, PEM, or P7B certificate
file.
when it was created.
the text of PEM certificate files.
Polycom, Inc. 41
Page 54

DMA Operations Guide Certificate Procedures
Table 3-4 Sections in the Certificate Details dialog box
Section Description
Certificate Info Purpose and alias of the certificate.
Issued To Information about the entity to which the certificate was
issued and the certificate serial number.
Issued By Information about the issuer.
Validity Issue and expiration date s.
Fingerprints SHA1 and MD5 fingerprints (checksums) for confirming
certificate.
Subject Alternative
Names
Extended Key Usage Indicates the purposes for which the certificate can be
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Certificate Procedures
Certificate procedures include the following:
Additional identities bound to the subject of the
certificate.
For the Polycom DMA system, this should include the
virtual and physical FQDNs, short host names, and IP
addresses of the system.
used.
The Polycom DMA system’s certificate is used for both
server and client connections, so this should always
contain at least serverAuth and clientAuth.
• Install your chosen certificate authority’s public certificate, if necessary, so
that the Polycom DMA system trusts that certificate authority.
• Create a certificate signing request to submit to the certificate authority.
• Install a public certificate signed by your certificate authority that
identifies the Polycom DMA system.
• Remove a signed certificate or a certificate authority’s certificate.
42 Polycom, Inc.
Page 55

Certificate Procedures System Security
Note
If you’re configuring the Polycom DMA system to support Polycom’s solution for the
Microsoft OCS or Lync environment, you can use Microsoft’s Certificate Wizard to
request and obtain a PFX file (a password-protected PKCS12 file containing a
private key and public key for the system, and the CA’s certificate).
Once you have the PFX file, you’re ready to install it.
See Polycom’s solution deployment guide for information about using the
Certificate Wizard and other steps needed to implement the solution.
Install a Certificate Authority’s Certificate
This procedure is not necessary if you obtain a certificate chain that includes a
signed certificate for the Polycom DMA system, your certificate authority’s
public certificate, and any intermediate certificates.
Use this procedure to add a trusted certificate authority, either an in-house or
commercial CA.
Caution
Installing or removing certificates requires a system restart and terminates all active
conferences.
When you install or remove a certificate, the change is made to the certificate store
immediately, but the system can’t implement the change until it restarts and reads
the changed certificate store.
For your convenience, you’re not required to restart and apply a change
immediately. This permits you to perform multiple installs or removals before
restarting and applying the changes. But when you’re finished making changes, you
must select Restart to Apply Saved Changes to restart the system and finish your
update. Before you begin, make sure there are no active conferences and you’re
prepared to restart the system when you’re finished.
To install a certificate for a trusted root CA
1 Go to Admin > Local Cluster > Certificates.
The installed certificates are listed. The Trusted Root CA entries, if any,
represent the certificate authorities whose public certificates are already
installed on the DMA system and are thus trusted.
2 If you’re using a certificate authority that isn’t listed, obtain a copy of
your certificate authority’s public certificate.
The certificate must be either a single X.509 certificate or a PKCS#7
certificate chain. If it’s ASCII text, it’s in PEM format, and starts with the
text
-----BEGIN CERTIFICATE-----
. If it’s a file, it can be either PEM or
DER encoded.
3 In the Actions list, select Add Certificates.
Polycom, Inc. 43
Page 56

DMA Operations Guide Certificate Procedures
4 In the Add Certificates dialog box, do one of the following:
— If you have a file, click Upload certificate, enter the password (if any)
for the file, and browse to the file or enter the path and file name.
— If you have PEM-format text, copy the certificate text, click Paste
certificate, and paste it into the text box below.
5 Click OK.
6 Verify that the certificate appears in the list as a Trusted Root CA.
7 Click Restart to Apply Saved Changes, and when asked to confirm that
you want to restart the system so that certificate changes can take effect,
click OK.
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Create a Certificate Signing Request in the DMA System
The procedure below creates a certificate signing request (CSR) that you can
submit to your chosen certificate authority. This method uses the private key
generated at software installation time.
To create a certificate signing request
1 Go to Admin > Local Cluster > Certificates.
By default, the system is configured to use a self-signed certificate.
2 To see details of the public certificate currently being used to identify the
system to other computers:
a In the list, select the Server SSL certificate.
b In the Actions list, select Display Details.
The Certificate Details dialog box appears. If this is the default
self-signed certificate, Organizational Unit is Self Signed Certificate.
c To close the dialog box, click OK.
3 In the Actions list, select Create Certificate Signing Request.
If you’ve created a signing request before, you’re asked if you want to use
your existing certificate request or generate a new one. Elect to generate a
new one.
44 Polycom, Inc.
Page 57

Certificate Procedures System Security
4 In the Certificate Information dialog box, enter the identifying
information for your Polycom DMA system (see “Certificate Information
Dialog Box” on page 40) and click OK.
The Certificate Signing Request dialog box displays the encoded request
(see “Certificate Signing Request Dialog Box” on page 40).
5 Copy the entire contents of the Encoded Request box (including the text
-----BEGIN NEW CERTIFICATE REQUEST----CERTIFICATE REQUEST-----
) and submit it to your certificate authority.
Depending on the certificate authority, your CSR may be submitted via
email or by pasting into a web page.
6 Click OK to close the dialog box.
When your certificate authority has processed your request, it sends you
a signed public certificate for your Polycom DMA system. Some certificate
authorities also send intermediate certificates and/or root certificates.
Depending on the certificate authority, these certificates may arrive as
email text, email attachments, or be available on a secure web page.
The Polycom DMA system accepts PKCS#7 or PKCS#12 certificate chains
or single certificates.
and
-----END NEW
Caution
When you submit the CSR to your CA, make sure that the CA doesn’t modify any of
the predefined SAN fields or the X.509v3 Key Usage or Extended Key Usage fields.
Changes to these fields may make your system unusable. Contact Polycom
technical support if you have any questions about this.
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Install a Certificate in the DMA System
The procedure below installs the certificate or certificate chain provided by the
certificate authority. It assumes that you’ve received the certificate or
certificate chain in one of the following forms:
• A PFX, P7B, or single certificate file that you’ve saved on your computer.
Polycom, Inc. 45
Page 58

DMA Operations Guide Certificate Procedures
• PEM-format encoded text that you received in an email or on a secure web
page.
Caution
Installing or removing certificates requires a system restart and terminates all active
conferences.
When you install or remove a certificate, the change is made to the certificate store
immediately, but the system can’t implement the change until it restarts and reads
the changed certificate store.
For your convenience, you’re not required to restart and apply a change
immediately. This permits you to perform multiple installs or removals before
restarting and applying the changes. But when you’re finished making changes, you
must select Restart to Apply Saved Changes to restart the system and finish your
update. Before you begin, make sure there are no active conferences and you’re
prepared to restart the system when you’re finished.
To install a signed certificate that identifies the Polycom DMA system
1 When you receive your certificate(s), return to Admin > Local Cluster >
Certificates.
2 In the Actions list, select Add Certificates.
3 In the Add Certificates dialog box, do one of the following:
— If you have a PFX, P7B, or single certificate file, click Upload
certificate, enter the password (if any) for the file, and browse to the
file or enter the path and file name.
— If you have PEM-format text, copy the certificate text, click Paste
certificate, and paste it into the text box below. You can paste multiple
PEM certificates one after the other.
4 Click OK.
5 To verify that the new signed certificate has replaced the default
self-signed certificate:
a In the list of certificates, once again select the Server SSL certificate.
b In the Actions list, select Display Details.
The Certificate Details dialog box appears.
c Confirm from the information under Issued To and Issued By that the
self-signed default certificate has been replaced by your signed public
certificate from the certificate authority.
d Click OK to close the dialog box.
6 Click Restart to Apply Saved Changes, and when asked to confirm that
you want to restart the system so that certificate changes can take effect,
click OK.
46 Polycom, Inc.
Page 59

Certificate Procedures System Security
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
Remove a Certificate from the DMA System
There are two kinds of certificate removal:
• Removing the certificate of a Trusted Root CA so that the system no longer
trusts certificates signed by that certificate authority.
• Removing the signed certificate currently in use as the Server SSL
certificate so that the system reverts to using the default self-signed Server
SSL certificate.
Removing a signed certificate also removes the certificate of the Trusted
Root CA that signed it, along with any intermediate certificates provided
by that certificate authority.
Both procedures are described below.
Caution
Installing or removing certificates requires a system restart and terminates all active
conferences.
When you install or remove a certificate, the change is made to the certificate store
immediately, but the system can’t implement the change until it restarts and reads
the changed certificate store.
For your convenience, you’re not required to restart and apply a change
immediately. This permits you to perform multiple installs or removals before
restarting and applying the changes. But when you’re finished making changes, you
must select Restart to Apply Saved Changes to restart the system and finish your
update. Before you begin, make sure there are no active conferences and you’re
prepared to restart the system when you’re finished.
To remove a Trusted Root CA’s certificate
1 Go to Admin > Local Cluster > Certificates.
2 In the certificates list, select the certificate you want to delete.
3 In the Actions list, select Display Details and confirm that you’ve
selected the correct certificate. Then click OK.
4 In the Actions list, select Delete Certificate.
5 When asked to confirm, click Yes.
A dialog box informs you that the certificate has been deleted.
6 Click OK.
Polycom, Inc. 47
Page 60

DMA Operations Guide Security Settings
7 Click Restart to Apply Saved Changes, and when asked to confirm that
you want to restart the system so that certificate changes can take effect,
click OK.
To remove a signed certificate and revert to the default self-signed certificate
1 Go to Certificates.
2 In the Actions list, select Revert to Default Certificate.
3 When asked to confirm, click Yes.
A dialog box informs you that the system has reverted to a self-signed
certificate.
4 Click OK.
5 Click Restart to Apply Saved Changes, and when asked to confirm that
you want to restart the system so that certificate changes can take effect,
click OK.
6 After the system restarts, log back in, return to Admin > Local Cluster >
Certificates, and verify that the system has reverted to the default
self-signed certificate:
Security Settings
a In the list of certificates, select the Server SSL certificate.
b In the Actions list, select Display Details.
The Certificate Details dialog box appears.
c Confirm from the information under Issued To and Issued By that the
default self-signed certificate has replaced the CA-signed certificate.
d Click OK to close the dialog box.
See also:
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Certificate Procedures” on page 42
The Security Settings page lets you switch between high security mode and a
custom security mode in which one or more insecure capabilities are allowed.
It also lets you switch to, but not from, a maximum security mode.
48 Polycom, Inc.
Page 61

Security Settings System Security
Caution
We recommend always using the High security setting unless you have a specific
and compelling need to allow one of the insecure capabilities.
We recommend the new Maximum security setting only for those environments
where the most stringent security protocols must be adhered to.
Enabling Maximum security is irreversible and has significant consequ ences
(see “The Consequences of Enabling Maximum Security Mode” on page 54). Don’t
choose this setting unless you know what you’re doing and are prepared for the
consequences.
Note
All clusters in a supercluster must have the same security settings. Before
attempting to join a supercluster, make sure the cluster’s security settings match
those of the other members of the supercluster. You can’t change a cluster’s
security settings while it’s part of a supercluster.
The following table describes the options in the Security Settings page.
Table 3-5 Fields on the Security Settings page
Field Description
Maximum security An extremely high security mode suitable for use where
very strict security requirements apply.
Once this mode is enabled, it’s no longer possible to
reduce the security level. See caution above.
High security Recommended setting for normal operation.
Custom security Lets you enable one or more of the unsecured methods
of network access listed below it.
Allow Linux console
access
Enables the Linux user root to log into the system using
SSH. This direct Linux access isn’t needed for normal
operation, routine maintenance, or even
troubleshooting, all of which can be done through the
administrative GUI.
In extreme circumstances, this option might enable
expert Polycom Global Services personnel to more fully
understand the state of a troubled system or correct
problems. Enable this option only when asked to do so
by Polycom Global Services.
Polycom, Inc. 49
Page 62

DMA Operations Guide Security Settings
Table 3-5 Fields on the Security Settings page (continued)
Field Description
Allow unencrypted
connections to the
Active Directory
Allow unencrypted
connections to MCUs
Normally, the Polycom DMA system connects to Active
Directory using SSL or TLS encryption. But if the Active
Directory server or servers (including domain controllers
if you import global groups) aren’t configured to support
encryption, the Polycom DMA system can only connect
using an unencrypted protocol. This option allows such
connections if an encrypted connection can’t be
established.
This configuration causes an extreme security flaw: the
unencrypted passwords of enterprise users are
transmitted over the network, where they can easily be
intercepted.
Use this option only for diagnostic purposes. By toggling
it, you can determine whether encryption is the cause of
a failure to connect to Active Directory or to load group
data. If so, the solution is to correctly configure the
relevant servers, not to allow ongoing use of
unencrypted connections.
Normally, the Polycom DMA system uses only HTTPS
for the conference control connection to RMX MCUs,
and therefore can’t control an RMX MCU that accepts
only HTTP (the default). This option enables the system
to fall back to HTTP for RMX MCUs not configured for
HTTPS.
We recommend configuring your MCUs to accept
encrypted connections rather than enabling this option.
When unencrypted connections are used, the RMX
login name and password are sent unencrypted over
the network.
Allow unencrypted
calendar notifications
from Exchange server
50 Polycom, Inc.
Normally, if calendaring is enabled, the Polycom DMA
system gives the Microsoft Exchange server an HTTPS
URL to which the Exchange server can deliver calendar
notifications. In that case, the Polycom DMA system
must have a certificate that the Exchange server
accepts in order for the HTTPS connection to work.
If this option is selected, the Polycom DMA system does
not require HTTPS for calendar notifications.
We recommend installing a certificate trusted by the
Exchange server and using an HTTPS URL for
notifications rather than enabling this option.
Page 63

Security Settings System Security
Table 3-5 Fields on the Security Settings page (continued)
Field Description
Allow basic
authentication to
Exchange server
Skip certificate
validation for server
connecting
Normally, if calendaring is enabled, the Polycom DMA
system authenticates itself with the Exchange server
using NTLM authentication.
If this option is selected, the Polycom DMA system still
attempts to use NTLM first. But if that fails or isn’t
enabled on the Exchange server, then the DMA system
falls back to HTTP Basic authentication (user name and
password).
We recommend using NTLM authentication rather than
enabling this option.
In order for either NTLM or HTTP Basic authentication
to work, they must be enabled on the Exchange server.
Normally, when the Polycom DMA system connects to a
server, it validates that server’s certificate.
This option configures the system to accept any
certificate presented to it without validating it.
We recommend using valid certificates for all servers
that the system may need to contact rather than
enabling this option. Depending on system
configuration, this may include:
MCUs
Active Directory
Exchange
RealPresence Resource Manager or CMA system
Other DMA systems
Skip certificate
validation for encrypted
signaling
Polycom, Inc. 51
Normally, during encrypted call signaling (SIP over
TLS), the Polycom DMA system requires the remote
party (endpoint or MCU) to present a valid certificate.
This is known as mTLS or two-way TLS.
This option configures the system to accept any
certificate (or none).
We recommend installing valid certificates on your
endpoints and MCUs rather than enabling this option.
Page 64

DMA Operations Guide Security Settings
Table 3-5 Fields on the Security Settings page (continued)
Field Description
Skip certificate
validation for user login
sessions
Allow forwarding of IPv6
ICMP destination
unreachable messages
Allow IPv6 ICMP echo
reply messages to
multicast addresses
This option may be configured in any security mode.
If this option is turned off, you can only connect to the
Polycom DMA system if your browser presents a client
certificate issued by a CA that the system trusts (this is
known as mTLS for administrative connections).
Turn this option off only if:
• You’ve implemented a complete public key
infrastructure (PKI) system, including a CA server,
client software (and optionally hardware, tokens, or
smartcards), and the appropriate operational
procedures.
• The CA’ s public certificate is installed in the Polycom
DMA system so that it trusts the CA.
• All authorized users, including yourself, have a
client certificate signed by the CA that authenticates
them to the Polycom DMA system.
If this option is off, the Polycom DMA system has an
internal firewall rule that blocks outbound destination
unreachable messages.
If this option is on, that firewall rule is disabled.
Note: The Polycom DMA system currently doesn’t send
such messages, regardless of this setting.
If this option is off, the Polycom DMA system doesn't
reply to echo request messages sent to multicast
addresses (multicast pings).
If this option is on, the system responds to multicast
pings.
52 Polycom, Inc.
Page 65

Security Settings System Security
Table 3-5 Fields on the Security Settings page (continued)
Field Description
Disable enhanced
support
Enhanced support allows Polycom Global Services
personnel to securely access the system when normal
access methods aren’t possible. For example,
enhanced support could allow support of a DMA system
when console access is disabled and system errors
prevent access to the management interface.
Using the enhanced support feature, expert Polycom
Global Services personnel can enable console access
when necessary using Single Packet Authorization
(SPA) technology. This is a more secure method than
console access, so the default is to not disable it.
We strongly recommend leaving this setting off so that
the enhanced support feature remains available. If
neither enhanced support nor console access is
available, recovering from a serious problem may
require re-imaging the system, resulting in a loss of
data.
This setting is automatically turned on if Maximum
security is enabled.
To change the security settings
1 Go to Admin > Local Cluster > Security Settings.
2 To switch from a custom setting back to the recommended security mode,
click High security.
3 To switch from the recommended security mode to a custom setting:
a Click Custom security.
b Check the unsecured network access method(s) that you want to
enable.
4 Click Update.
A dialog box informs you that the configuration has been updated.
Note
If you turn off Skip certificate validation for user login sessions, the system
notifies you that if you don’t log back in within 5 minutes, the setting will be
automatically turned back on. This is a safety precaution to ensure that at least one
user is still able to access the system.
5 Click OK.
Polycom, Inc. 53
Page 66

DMA Operations Guide The Consequences of Enabling Maximum Security Mode
See also:
“System Security” on page 35
“Certificate Settings” on page 38
“The Consequences of Enabling Maximum Security Mode” on page 54
“Login Policy Settings” on page 57
“Reset System Passwords” on page 61
The Consequences of Enabling Maximum Security Mode
Enabling the Maximum security setting is irreversible and has the following
significant consequences:
• All unencrypted protocols and unsecured access methods are disabled,
and the enhanced support feature is disabled.
• The boot order is changed so that the server(s) can’t be booted from the
optical drive or a USB device.
• A BIOS password is set.
• The port 443 redirect is removed, and the system can only be accessed by
the full URL (https://<IP>:8443/dma7000, where <IP> is one of the
system's management IP addresses or a host name that resolves to one of
those IP addresses).
• For all server-to-server connections, the system requires the remote party
to present a valid X.509 certificate. Either the Common Name (CN) or
Subject Alternate Name (SAN) field of that certificate must contain the
address or host name specified for the server in the Polycom DMA system.
Polycom RMX MCUs don’t include their management IP address in the
SAN field of the CSR (Certificate Signing Request), so their certificates
identify them only by the CN. Therefore, in the Polycom DMA system, an
RMX MCU's management interface must be identified by the host name
or FQDN specified in the CN field, not by IP address.
Similarly, an Active Directory server certificate often specifies only the
FQDN. Therefore, in the Polycom DMA system, the Active Directory must
be identified by FQDN, not by IP address.
• SIP signaling is not supported.
• Superclustering is not supported.
• The Polycom DMA system can’t be integrated with Microsoft Exchange
Server and doesn’t support virtual meeting rooms (VMRs) created by the
Polycom Conferencing Add-in for Microsoft Outlook.
• Integration with a Polycom RealPresence Resource Manager or CMA
system is not supported.
54 Polycom, Inc.
Page 67

The Consequences of Enabling Maximum Security Mode System Security
• On the Banner page, Enable login banner is selected and can’t be
disabled.
• On the Login Sessions page, the Terminate Session action is not
available.
• On the Troubleshooting Utilities menu, Top is removed.
• In the Add User and Edit User dialog boxes, conference and chairperson
passwords are obscured.
• After Maximum security is enabled, users must change their passwords.
• If the system is not integrated with Active Directory, each local user can
have only one assigned role (Administrator, Provisioner, or Auditor).
If some local users have multiple roles when you enable Maximum
security, they retain only the highest-ranking role (Administrator >
Auditor > Provisioner).
• If the system is integrated with Microsoft Active Directory, only one local
user can have the Administrator role, and no local users can have the
Provisioner or Auditor role.
If there are multiple local administrators when you enable Maximum
security, the system prompts you to choose one local user to retain the
Administrator role. All other local users, if any, become conferencing
users only and can’t log into the management interface.
Each enterprise user can have only one assigned role (Administrator,
Provisioner, or Auditor). If some enterprise users have multiple roles (or
inherit multiple roles from their group memberships), they retain only the
lowest-ranking role (Administrator > Auditor > Provisioner).
• Local user passwords have stricter limits and constraints (each is set to the
noted default if below that level when you enable Maximum security):
— Minimum length is 15-30 characters (default is 15).
— Must contain 1 or 2 (default is 2) of each character type: uppercase
alpha, lowercase alpha, numeric, and non-alphanumeric (special).
— Maximum number of consecutive repeated characters is 1-4 (default is
2).
— Number of previous passwords that a user may not re-use is 8-16
(default is 10).
— Minimum number of characters that must be changed from the
previous password is 1-4 (default is 4).
— Password may not contain the user name or its reverse.
— Maximum password age is 30-180 days (default is 60).
— Minimum password age is 1-30 days (default is 1).
Polycom, Inc. 55
Page 68

DMA Operations Guide The Consequences of Enabling Maximum Security Mode
• Other configuration settings ha ve stri cter limi ts and constraints (each is set
to the noted default if below that level when you enable Maximum
security):
— Session configuration limits:
» Sessions per system is 4-80 (default is 40).
» Sessions per user is 1-10 (default is 5).
» Session timeout is 5-60 minutes (default is 10).
— Local account configuration limits:
» Local user account is locked after 2-10 failed logins (default is 3)
due to invalid password within 1-24 hours (default is 1).
» Locked account remains locked either until unlocked by an
administrator (the default) or for a duration of 1-480 minutes.
• Software build information is not displayed anywhere in the interface.
• You can’t restore a backup made before Maximum security was enabled.
• File uploads may fail when using the Mozilla Firefox browser unless the
proper steps have been taken. See below.
Enabling File Uploads in Maximum Security with Mozilla Firefox
The Mozilla Firefox browser uses its own certificate database instead of the
certificate database of the OS. If you use only that browser to access the
Polycom DMA system, the certificate(s) needed to securely connect to the
system may be only in the Firefox certificate database and not in the Windows
certificate store. This causes a problem for file uploads.
File upload via the Polycom DMA system’s Flash-based interface bypasses the
browser and creates the TLS/SSL connection itself. Because of that, it uses the
Windows certificate store, not the Firefox certificate database. If the
certificate(s) establishing trust aren’t there, the file upload silently fails.
To avoid this problem, you must import the needed certificates into Internet
Explorer (and thus into the Windows certificate store). And, when accessing
the system with Firefox, you must use its fully qualified host name.
First, start Internet Explorer and point it to the Polycom DMA system. If you
don’t receive a security warning, the needed certificates are already in the
Windows certificate store.
If you receive a warning, import the needed certificates. The details for doing
so depend on the version of Internet Explorer and on your enterprise’s
implementation of certificates.
In Internet Explorer 7, elect to continue to the site. Then click Certificate Error
to the right of the address bar and click View Certificates to open the
Certificate dialog box. From there, you can access the Certificate Import
Wizard.
56 Polycom, Inc.
Page 69

Login Policy Settings System Security
The entire trust chain must be imported (the system’s signed certificate,
intermediate certificates, if any, and the root CA’s certificate). When importing
a certificate, let Internet Explorer automatically select a certificate store.
See also:
“System Security” on page 35
“Security Certificates Overview” on page 35
“Certificate Settings” on page 38
“Security Settings” on page 48
“Login Policy Settings” on page 57
“Reset System Passwords” on page 61
Login Policy Settings
The following pages, under Admin > Login Policy Settings, let you configure
various aspects of user access to the system:
Local Password
• Local Password
• Session
• Local User Account
• Banner
See also:
“System Security” on page 35
“Certificate Settings” on page 38
“Security Settings” on page 48
The Local Password page lets you increase system security by specifying age,
length, and complexity requirements for the passwords of local administrator,
auditor, and provisioner users. These rules don’t apply to conferencing users’
conference and chairperson passcodes, or to Active Directory users.
The following table describes the fields on the Local Password page.
Polycom, Inc. 57
Page 70

DMA Operations Guide Login Policy Settings
Table 3-6 Fields on the Local Password Settings page
Field Description
Password Management
Maximum password
age (days)
Minimum password age
(days)
Minimum length Specify the number of characters a password must
Minimum changed
characters
Reject previous
passwords
Password Complexity
Allow user name or its
reverse form
Lowercase letters Specify the number of lowercase letters (a-z) that a
Uppercase letters Specify the number of uppercase letters (A-Z) that a
Numbers Specify the number of digit characters (0-9) that a
Specify at what age a password expires (30-180 days).
Specify how frequently a password can be changed
(1-30 days).
contain (8-30).
Specify the number of characters that must be different
from the previous password (1-4).
Specify how many of the user’s previous passwords the
system remembers and won’t permit to be reused
(8-30).
Turns off the protection against a password containing
the user’s login name or its reverse.
password must contain.
password must contain.
password must contain.
Special characters Specify the number of non-alphanumeric keyboard
characters that a password must contain.
Maximum consecutive
repeated characters
Specify how many sequential characters may be the
same.
See also:
“System Security” on page 35
“Login Policy Settings” on page 57
Session
The Session page lets you increase system security by limiting the number and
length of login sessions.
You can see the current login sessions and terminate sessions by going to
User > Login Sessions. See “Login Sessions” on page 344.
The following table describes the fields on the Session page.
58 Polycom, Inc.
Page 71

Login Policy Settings System Security
Table 3-7 Fields on the Session Settings page
Field Description
Active system sessions Specify the number of simultaneous login sessions by
all users or select Unlimited.
Note: If this limit is reached, but none of the logged-in
users is an Administrator, the first Administrator user to
arrive is granted access, and the system terminates the
non-Administrator session that’s been idle the longest.
Local User Account
Active sessions per
user
Session timeout
(minutes)
Specify the number of simultaneous login sessions per
user ID or select Unlimited.
Specify the length of time after which the system
terminates a session for inactivity or select Unlimited.
See also:
“System Security” on page 35
“Login Policy Settings” on page 57
The Local User Account page lets you increase system security by:
• Locking out users who have exceeded the specified number and frequency
of login failures. The system locks the account either indefinitely or for the
length of time you specify.
• Disabling accounts that have been inactive a specified number of days.
The following table describes the fields on the Local User Account page.
Table 3-8 Fields on the Local User Account page
Field Description
Account Lockout
Enable account lockout Turns on lockout feature and enables lockout
configuration fields below.
Failed login threshold Specify how many consecutive login failures cause the
system to lock an account.
Failed login window
(hours)
Polycom, Inc. 59
Specify the time span within which the consecutive
failures must occur in order to lock the account.
Page 72

DMA Operations Guide Login Policy Settings
Table 3-8 Fields on the Local User Account page (continued)
Field Description
Banner
Customize user account
lockout duration
(minutes)
Account Inactivity
Customize account
inactivity threshold
(days)
If selected, specify how long the user’s account remains
locked.
If not selected, the lockout is indefinite, and a user with
a locked account must contact an Administrator to
unlock it.
Turns on disabling of inactive accounts and lets you
specify the inactivity threshold that triggers disabling.
See also:
“System Security” on page 35
“Login Policy Settings” on page 57
A login banner is a message that appears when users attempt to access the
system. They must acknowledge the message before they can log in.
The Banner page lets you enable the banner and select or create the message it
displays. The message may contain up to 1500 characters. If the system is in
Maximum Security mode, the login banner is enabled and can’t be disabled.
The following table describes the fields on the Banner page.
Table 3-9 Fields on the Banner page
Field Description
Enable login banner Enables the display of a login banner.
If this box is unchecked, the Message field is disabled.
The existing contents, if any, remain unchanged, but
aren’t displayed to users.
Message Select one of the messages from the list, or select
Custom and type or paste your own message into the
field below.
If you select one of the built-in samples, it’s copied into
the Message field, and you can then edit the copy.
When you do so, the system resets the list to Custom.
Y our edits don’t af fect the stored sample. You can revert
to the original version of the sample by re-selecting it
from the list.
60 Polycom, Inc.
Page 73

Reset System Passwords System Security
See also:
“System Security” on page 35
“Login Policy Settings” on page 57
Reset System Passwords
In an extremely high-security environment, security compliance policies may
require that all passwords be changed at certain intervals, including operating
system passwords.
The Reset System Passwords page is available only if the system is in
maximum security mode. It lets you change these operating system passwords
(such as the password for grub) to new, randomly-generated values. These are
passwords for logins that aren’t possible on a secure system. Resetting these
operating system passwords has no effect on authorized users of the
maintenance interface (Administrators, Auditors, and Provisioners) or
conferencing users.
To reset system passwords
1 Make sure there are no calls or conferences on the system.
2 Go to Admin > Local Cluster > Reset System Passwords.
3 Click Reset Passwords.
The system warns you that active calls and conferences will be terminated
and the system will restart, and asks you to confirm.
4 Click Yes.
The system informs you that the passwords have been reset and that
you’re being logged out. Then it restarts. This takes several minutes.
5 Wait a few minutes to log back in.
See also:
“System Security” on page 35
“Security Settings” on page 48
“The Consequences of Enabling Maximum Security Mode” on page 54
“Login Policy Settings” on page 57
Polycom, Inc. 61
Page 74

DMA Operations Guide Reset System Passwords
62 Polycom, Inc.
Page 75

Local Cluster Configuration
This chapter describes the following Polycom® Distributed Media
Application™ (DMA™) 7000 system configuration topics:
• Network Settings
• Time Settings
• Licenses
4
• Signaling Settings
• Logging Settings
• Local Cluster Configuration Procedures
These are cluster-specific settings that are not part of the data store shared
across superclustered systems. See “Introduction to the Polycom DMA
System” on page 1.
If you’re performing the initial configuration of your Polycom DMA system,
study “Polycom
before you continue.
®
DMA™ System Initial Configuration Summary” on page 23
Polycom, Inc. 63
Page 76

DMA Operations Guide Network Settings
Network Settings
The following table describes the fields on the Network Settings page. These
values are normally set in the USB Configuration Utility during system
installation and rarely need to be changed. See the Getting Started Guide.
Caution
Changing some network settings (host names, IP addresses, or domains) requires
a system restart and terminates all active conferences.
If the system is using a CA-provided identity certificate, changing some network
settings (host names or IP addresses) also requires you to update the certificate. (If
the system is using a self-signed certificate, an updated one is automatically
created.)
You can’t change these network settings while the system is part of a supercluster
or integrated with a Polycom RealPresence Resource Manager or CMA system.
You must first leave the supercluster or terminate the integration. If the cluster is
responsible for any territories (as primary or backup), reassign those territories.
After the change, rejoin the supercluster or Polycom RealPresence Resource
Manager or CMA system. See “Superclustering” on page 227 or “Resource
Management System Integration” on page 185.
Incorrect network information may make the system unuseable and the
management interface unreachable.
Note
This version of the Polycom DMA system eliminates the need for virtual host
name(s) and IP addresses in a single-server system or cluster. When a version 5.0
or earlier single-server DMA system is upgraded to version 5.1 or later, the previous
version's virtual host name(s) and IP addresses become the upgraded version's
physical host name(s) and IP addresses, so accessing the system doesn't change.
(Exception: If only IPv6 is enabled, the system must have two addresses, so a
single-server system must still have a virtual host name and IP address.)
64 Polycom, Inc.
Page 77

Network Settings Local Cluster Configuration
Table 4-1 Fields on the Network Settings page
Field Description
System IP type IP addressing supported (IPv4, IPv6, or both).
System server
configuration
System split network
setting
Server 1 Status, host name, and IP address(es) of the primary
Number of servers (1 or 2) in this cluster.
Caution: Once this is set to 2 server configuration, it
can’t be changed back to 1 server configuration. To
reconfigure a two-server system as two separate
single-server systems, you must use the USB
Configuration Utility. See the Getting S tarted Guide.
Specifies whether management and signaling traffic are
combined on one network interface or split onto
separate interfaces.
Caution: Split networking is for network configurations
in which signaling and management traffic are not on
the same network. To split the network configuration,
you must use different gateways and subnets for
management and signaling, and separate physical
connections for the management and signaling
networks (eth0 for management, eth2 for signaling).
If management and signaling traffic are combined on
the same network (subnet), both use the same physical
and virtual IP addresses and the same network
interface.
server. The IP type and network setting determine which
of the IP fields in this section are enabled.
Host names may contain only letters, numbers, and
internal dashes (hyphens), and may not include a
domain. The reserved values appserv* and dmamgk-*
may not be used for host names.
Server 2 Status, host name and IP address(es) of the secondary
server. The fields in this section duplicate those in the
Server 1 section and are enabled only in two-server
configuration.
Polycom, Inc. 65
Page 78

DMA Operations Guide Network Settings
Table 4-1 Fields on the Network Settings page (continued)
Field Description
Shared Management
Network Settings
Virtual host name Virtual host name and IP address(es) for the system’s
IPv4
IPv6
Subnet mask IPv4 network mask that defines the subnetwork of the
IPv6 prefix length IPv6 CIDR (Classless Inter-Domain Routing) value that
IPv4 gateway IPv4 address of gateway server for the subnetwork.
Name The name of the management network interface (eth0)
Enable
The settings in this section apply to the entire system
(both servers in two-server configuration), whether
management and signaling are combined or separate.
management (or combined) network interface.
For a one-server configuration, these fields are
disabled. (Exception: If only IPv6 is enabled, the system
must have two addresses, so a single-server system
must still have a virtual host name and IP address.)
Host names may contain only letters, numbers, and
internal dashes (hyphens), and may not include a
domain. The reserved values appserv* and dmamgk-*
may not be used for host names.
system’s management interface.
defines the subnetwork of the system’s management
interface.
is not editable, and it can’t be disabled.
The eth0 interface corresponds with the GB1 jack on
the server.
Auto-negotiation Turn on Auto-negotiation or set Speed and Duplex
Speed
Duplex
Show Link Details Click to see details about link settings and information.
66 Polycom, Inc.
manually.
This information may be useful to Polycom Global
Services when troubleshooting a network issue.
Page 79

Network Settings Local Cluster Configuration
Table 4-1 Fields on the Network Settings page (continued)
Field Description
Shared Signaling
Network Settings
General System
Network Settings
DNS search domains One or more fully qualified domain names, separated by
The settings in this section are enabled only if
management and signaling traffic are on separate
networks. If so, they apply to the entire system (both
servers in two-server configuration).
For a one-server configuration, the virtual host name
and IP fields are disabled. (Exception: If only IPv6 is
enabled, the system must have two addresses, so a
single-server system must still have a virtual host name
and IP address.)
The settings are the same as those in Shared
Management Network Settings, except that under
Signaling Link, the signaling network interface (eth2)
can be disabled. This capability exists for debugging
purposes.
The eth2 interface corresponds with the GB3 jack on
the server.
(The eth1 interface, which corresponds with the GB2
jack, is reserved for the private network connection
between the two servers in a two-server cluster.)
The settings in this section apply to the entire system
and aren’t specific to management or signaling.
commas or spaces. The system domain you enter
below is added automatically, so you need not enter it.
DNS 1 IP addresses of up to three domain name servers. We
DNS 2
DNS 3
Domain Fully qualified domain name for the system.
Polycom, Inc. 67
strongly recommend specifying at least one DNS
server. A DNS server must be specified in order to
connect to the Active Directory. See “Microsoft Active
Directory Integration” on page 163.
Page 80

DMA Operations Guide Network Settings
Table 4-1 Fields on the Network Settings page (continued)
Field Description
Signaling DSCP The Differentiated Services Code Point value (0 - 63) to
put in the DS field of IP packet headers.
The DSCP value is used to classify packets for quality
of service (QoS) purposes.
Default IPv6 gateway The interface to use for accessing the IPv6 gateway,
generally eth0. Optionally, the gateway’s address and
the interface, specified as:
<IPv6_address>%eth0
Default IPv4 gateway If management and signaling traffic are on separate
networks, select which of the two networks’ gateway
servers is the default.
Y our choice depends on your network configuration and
routing. Typically, unless all the endpoints, MCUs, and
other devices that communicate with the system are on
the same subnet, you’d select the signaling network.
See also:
“Local Cluster Configuration” on page 63
“Local Cluster Configuration Procedures” on page 82
Routing Configuration Dialog Box
In the Network page’s action list, the Routing Configuration command opens
the Routing Configuration dialog box, where you can add or delete network
routing rules (IPv4, IPv6, or both, depending on the System IP type setting on
the Network page). The Show raw routing configuration button lets you view
the operating system’s underlying routing configuration.
In a split network configuration, routing rules are necessary for proper routing
of network traffic. In a combined network configuration, the operating
system’s underlying routing configuration is likely sufficient unless you need
a special rule or rules for your particular network. If you aren’t sure, consult
the appropriate IT staff or network administrator for your organization.
The following table describes the fields in the Routing Configuration dialog
box. If System IP type is set to IPv4 + IPv6, the dialog box contains two
essentially identical sections, one for each IP type. Each section contains the
input fields listed below, a table showing the defined routing rules, and
buttons for adding and deleting routes.
68 Polycom, Inc.
Page 81

Time Settings Local Cluster Configuration
Table 4-2 Routing Configuration dialog box
Field Description
Host/Network The IP address of the destination network host or
segment.
Prefix length The prefix length that, together with the Host/Network
address, defines the subnet for this route.
For IPv4, a prefix length of 24 is equivalent to specifying
a subnet mask of 255.255.255.0. A prefix length of 16 is
equivalent to specifying a subnet mask of 255.255.0.0.
Interface In split network configuration, select the interface for
this route.
Via IP address of router for this route. Optional, and only
needed for non-default routers.
When you add a routing rule, it appears in the table below the input fields.
Select a rule and click Delete selected route to delete it. Click Show raw
routing configuration to display the operating system’s underlying routing
configuration.
Time Settings
See also:
“Network Settings” on page 64
The following table describes the fields on the Time Settings page. These
values are normally set in the USB Configuration Utility during system
installation and rarely need to be changed. See the Getting Started Guide.
Caution
Changing time settings requires a system restart and terminates all active
conferences.
You can’t change the system’s time settings while it’s integrated with a Polycom
RealPresence Resource Manager or CMA system or part of a supercluster. The
integration must first be terminated or the cluster removed from the supercluster.
See “Resource Management System Integration” on page 185 or “Superclustering”
on page 227 .
We strongly recommend specifying NTP servers.
Polycom, Inc. 69
Page 82

DMA Operations Guide Licenses
Table 4-3 Fields on the Time Settings page
Field Description
System time zone Time zone in which the system is located. We strongly
recommend selecting the time zone of a specific
geographic location (such as America/Denver), not one
of the generic GMT offsets (such as GMT+07 POSIX).
If you really want to use a generic GMT offset (for
instance, to prevent automatic daylight saving time
adjustments), note that they use the Linux/Posix
convention of specifying how many hours ahead of or
behind local time GMT is. Thus, the generic equivalent
of America/Denver (UTC-07:00) is GMT+07, not
GMT-07.
Licenses
Manually set system
time
NTP Servers Specify up to three time servers for maintaining system
We don’t recommend setting time and date manually.
time (we recommend three). Enter IP addresses or fully
qualified domain names.
See also:
“Local Cluster Configuration” on page 63
“Local Cluster Configuration Procedures” on page 82
The Polycom DMA system is licensed for the number of concurrent calls it can
handle and optionally for API access. See “License the Polycom DMA System”
on page 26 for more information about licensing.
The following table describes the fields on the Licenses page.
Table 4-4 Fields on the Licenses page
Field Description
Active License
Licensed calls The maximum number of concurrent calls that the
license enables.
Licensed capabilities Currently, the only separately licensed capability is
access to the RealPresence Platform API.
Note: An API license isn't required in order for a
Polycom RealPresence Resource Manager system to
access the API. It's only needed for a client application
you or a third party develop.
70 Polycom, Inc.
Page 83

Signaling Settings Local Cluster Configuration
Table 4-4 Fields on the Licenses page (continued)
Field Description
Activation Keys
A two-server cluster has two sets of the fields below, one for each server in the
cluster.
System serial number Th e serial number of the specified server.
Activation key The activation key you received from Polycom for this
server. The key for each server must be the correct one
for that server’s serial number.
See also:
“Local Cluster Configuration” on page 63
“Local Cluster Configuration Procedures” on page 82
Signaling Settings
On the Signaling Settings page, you can configure H.323, SIP, and XMPP
signaling.
H.323 and SIP Signaling
If H.323 signaling is enabled, the Polycom DMA system’s Call Server operates
as a gatekeeper, receiving registration requests and calls from H.323 devices.
If SIP signaling is enabled, Call Server operates as a SIP registrar and proxy
server, receiving registration requests and calls from SIP devices. If both are
enabled, the system automatically serves as a SIP <–> H.323 gateway.
Either H.323, SIP, or both must be enabled in order for the DMA system’s
Conference Manager to receive calls for multipoint conferences (virtual
meeting rooms, or VMRs) and distribute them among its pool of MCUs.
On this page, you can also:
• Turn on H.235 authentication for H.323 devices.
• Turn on SIP digest authentication for SIP devices.
• Click a Device authentication settings link to go to the Device
Authentication page, where you can configure SIP device authentication
and maintain the inbound device authentication list for both H.323 and
SIP devices (see “Device Authentication” on page 264).
Polycom, Inc. 71
Page 84

DMA Operations Guide Signaling Settings
Note
Y ou can turn authentication off and on for specific devices (assuming that it’ s tu rned
on here for that device type). See “Edit Device Dialog Box” on page 98.
• Configure specific ports or prefixes for “unauthorized” or “guest” SIP
calls that can only access specific resources (VMRs, VEQs, or a SIP peer).
H.323 Device Authentication
In an environment where H.235 authentication is used, H.323 devices include
their credentials (name and password) in registration and signaling (RAS)
requests. The Polycom DMA system authenticates requests as follows:
• If it’s a signaling request (ARQ, BRQ, DRQ) from an unregistered
endpoint, the Call Server doesn’t authenticate the credentials.
• If it’s a signaling request from a registered endpoint, or if the request is
from an MCU or neighbor gatekeeper, the Call Server attempts to
authenticate using its device authentication list (see “Device
Authentication” on page 264).
If the credentials can’t be authenticated, the Call Server rejects the registration
or signaling request. For call signaling requests, it also rejects the request if the
credentials differ from those with which the device registered.
SIP Device Authentication
The SIP digest authentication mechanism is described in RFC 3261, starting in
section 22, and in RFC 2617, section 3). When a SIP endpoint registers with or
calls the Polycom DMA system, if the request includes authentication
information, that information is checked against the Call Server’s local device
authentication list (see “Device Authentication” on page 264).
SIP authentication can be enabled at the port/transport level or (for
“unauthorized” access prefixes) the prefix level. If SIP authentication is
enabled and an endpoint’s request doesn’t include authentication information,
the Call Server responds with an authentication challenge containing the
required fields (see the RFCs). If the endpoint responds with valid
authentication information, the system accepts the registration or call.
Note
If inbound SIP authentication is turned on for a port or prefix, the Polycom DMA
system challenges any SIP message coming to the system via that port or with that
prefix. Any SIP peer and other device that interacts with the system by those means
must be configured to authenticate itself, or you must turn off Device
authentication for that specific device. See “Edit Device Dialog Box” on page 98.
72 Polycom, Inc.
Page 85

Signaling Settings Local Cluster Configuration
Untrusted SIP Call Handling Configuration
You can configure special handling for SIP calls from devices outside the
corporate firewall that aren’t registered with the Polycom DMA system and
aren’t from a federated division or enterprise. These calls ome to the DMA
system via session border controllers (SBCs) such as a Polycom RealPresence
Access Director or Acme Packet Session Border Controller device.
For security purposes, you can route such “unauthorized” or “guest” calls to
one or more specific VMRs (virtual meeting rooms) or VEQs (virtual entry
queues), or to a specific SIP peer. You do so by creating a separate set of
“guest” dial rules used only for these untrusted calls. See “Dial Rules” on
page 243.
Depending on the SBC and how it’s configured, such calls can be
distinguished in one of two ways:
• By port: The SBC routes untrusted calls to a specific port.
• By prefix: The SBC adds a specific prefix in the Request-URI of the first
INVITE message for the call.
The RealPresence Access Director SBC supports only the prefix method. The
Acme Packet Session Border Controller SBC can be configured for either.
In the SIP Settings section of the page, you can add one or more ports,
prefixes, or both for untrusted calls. For each entry, you can specify whether
authentication is required. Calls to an untrusted call prefix follow the
authentication setting for that prefix, not for the port on which they’re
received. For port entries, you can also specify the transport, and if TLS,
whether certificate validation is required (mTLS).
Note
If Skip certificate validation for encrypted signaling is turned off on the Security
Settings page, then Require certificate validation for TLS is turned on for both
authorized and unauthorized ports, and it can’t be turned off. See “Security
Settings” on page 48.
XMPP Signaling
If XMPP signaling is enabled, the Polycom DMA system’s Call Server operates
as an XMPP server, providing chat and presence services to the XMPP clients
that log into it.
Logins are accepted from any DMA user, local or Active Directory. Clients log
in by sending an XMPP login message to the virtual signaling address (IP or
FQDN) and XMPP port number of the DMA system, such as:
dma1.polycom.com:5223
Logged-in clients have presence and chat capability amongst themselves and
with clients logged into any federated XMPP service. Federation is automatic
and depends simply on DNS resolution of domains.
Polycom, Inc. 73
Page 86

DMA Operations Guide Signaling Settings
See xmpp.org for more information.
Signaling Settings Fields
The following table describes the fields on the Signaling Settings page.
Table 4-5 Fields on the Signaling Settings page
Field Description
H.323 Settings
Enable H.323 signaling Enables the system to receive H.323 calls.
Caution: Disabling H.323 terminates any existing H.323
calls. When you click Update, the system prompts you
to confirm.
Status Indicates whether the system’s H.323 gatekeeper
functions are active.
H.225 port Specifies the port number the system’s gatekeeper uses
for call signaling.
We recommend using the default port number (1720),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the RAS port.
RAS port Specifies the port number the system’s gatekeeper uses
for RAS (Registration, Admission and Status).
We recommend using the default port number (1719),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the H.225 port.
H.245 open firewall
ports
H.323 multicast Enables the system to support gatekeeper discovery
Enable H.323 device
authentication
SIP Settings
Enable SIP signaling Enables the system to receive Session Initiation
Shows the port range used for H.245 so you can
configure your firewall accordingly. This is display only.
(GRQ messages from endpoints) as described in the
H.323 and H.225.0 specifications.
Check the box to turn on H.323 device authentication.
Click Device authentication settings to go to the
Device Authentication page and add authentication
credentials (see “Device Authentication” on page 264).
Protocol (SIP) calls.
Caution: Disabling SIP terminates any existing SIP
calls. When you click Update, the system prompts you
to confirm.
74 Polycom, Inc.
Page 87

Signaling Settings Local Cluster Configuration
Table 4-5 Fields on the Signaling Settings page (continued)
Field Description
Authorized ports
Unencrypted SIP
port
Enable
authentication
TLS port Specifies the port number the system uses for TLS.
To permit unencrypted SIP connections, select either
TCP or UDP/TCP from the list. Select None to disallow
unencrypted SIP connections.
We recommend using the default port number (5060),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the TLS port and
from any “unauthorized” or “guest” ports that your
SBC(s) may be configured to use for calls to the system.
Check the box to turn on SIP device authentication for
unencrypted SIP.
Click the Device authentication settings link to go to
the Device Authentication page to configure SIP
device authentication and add device authentication
credentials (see “Device Authentication” on page 264).
The settings on that page determine the realm used for
authentication and whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized) or
407 (Proxy Authentication Required).
We recommend using the default port number (5061),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the UDP/TCP port
and from any “unauthorized” or “guest” ports that your
SBC(s) may be configured to use for calls to the system.
If SIP signaling is enabled, TLS is automatically
supported. Unless unencrypted SIP connections are
specifically permitted, TLS must be used.
Enable
authentication
Require certificate
validation for TLS
Polycom, Inc. 75
Check the box to turn on SIP device authentication for
encrypted SIP.
Click the Device authentication settings link to go to
the Device Authentication page to configure SIP
device authentication and add device authentication
credentials (see “Device Authentication” on page 264).
The settings on that page determine the realm used for
authentication and whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized) or
407 (Proxy Authentication Required).
Check the box to enable mutual TLS (mTLS), requiring
each caller to present a valid certificate.
Page 88

DMA Operations Guide Signaling Settings
Table 4-5 Fields on the Signaling Settings page (continued)
Field Description
Unauthorized ports Lists the ports used by your SBC(s) for untrusted calls,
showing the transport type for each and, for TLS,
whether a certificate is required. The Authentication
column indicates whether calls to that port are passed
without challenge, challenged for authentication
credentials, or blocked.
Click Add to add a port to the list (see “Add Guest Port
Dialog Box” on page 77). Click Edit to edit the selected
entry (see “Edit Guest Port Dialog Box” on page 78) or
Delete to delete it.
Unauthorized prefixes Lists the prefixes used by your SBC(s) for untrusted
calls. The Strip Pref ix column indicates whether the
DMA system should immediately strip the prefix. The
Authentication column indicates whether calls to that
port are passed without challenge, challenged for
authentication credentials, or blocked.
Click Add to add a prefix to the list (see “Add Guest
Prefix Dialog Box” on page 79). Click Edit to edit the
selected entry (see “Edit Guest Prefix Dialog Box” on
page 80) or Delete to delete it.
XMPP Settings
Enable XMPP signaling Enables the system to act as an Extensible Messaging
and Presence Protocol (XMPP) server for chat and
presence services.
Caution: Disabling XMPP terminates any existing
XMPP logins. When you click Update, the system
prompts you to confirm.
Unencrypted XMPP
port
TLS port Specifies the port number the system uses for TLS.
If security settings permit unencrypted XMPP
connections (see “Security Settings” on page 48), you
can turn it on here.
We recommend using the default port number (5222),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the TLS port.
We recommend using the default port number (5223),
but you can use any value from 1024 to 65535 that’s not
already in use and is different from the UDP/TCP port.
If XMPP signaling is enabled, TLS is automatically
supported. Unless unencrypted XMPP connections are
specifically permitted, TLS must be used. See “Security
Settings” on page 48.
76 Polycom, Inc.
Page 89

Signaling Settings Local Cluster Configuration
See also:
“Local Cluster Configuration” on page 63
“Local Cluster Configuration Procedures” on page 82
Add Guest Port Dialog Box
The Add Guest Port dialog box appears when you click the Add button next
to the Unauthorized ports list in the SIP Settings section of the Signaling
Settings page. It let s you add a port to the li st of p orts us ed for “ unauthori zed”
or “guest” calls.
The following table describes the fields in the Add Guest Port dialog box.
Table 4-6 Add Guest Port dialog box
Field Description
Port The SIP signaling port number for this entry.
This is the port number that an SBC is configured to use
for untrusted calls to the DMA system via the transport
specified below.
Transport The transport supported on this port.
Require certificate
validation for TLS
Authentication Select one of the following:
For TLS transport, check this box to enable mutual TLS
(mTLS), requiring callers to present a valid certificate.
Note: If Skip certificate validation for encrypted
signaling is turned off on the Security Settings page,
then Require certificate validation for TLS is turned
on for both authorized and unauthorized ports, and it
can’t be turned off. See “Security Settings” on page 48 .
•None — The system doesn’t issue authentication
challenges or check authentication credentials for
calls to this port.
• Authenticate — The system issues authentication
challenges and checks authentication credentials
for calls to this port.
The settings on the Device Authentication page
(see “Device Authentication” on page 264)
determine the realm used for authentication and
whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized)
or 407 (Proxy Authentication Required).
•Block — The system blocks calls to this port.
Polycom, Inc. 77
Page 90

DMA Operations Guide Signaling Settings
See also:
“Signaling Settings” on page 71
“Local Cluster Configuration Procedures” on page 82
Edit Guest Port Dialog Box
The Edit Guest Port dialog box lets you edit an Unauthorized ports list entry
in the SIP Settings section of the Signaling Settings page.
The following table describes the fields in the Edit Guest Port dialog box.
Table 4-7 Edit Guest Port dialog box
Field Description
Port The SIP signaling port number for this entry.
This is the port number that an SBC is configured to use
for untrusted calls to the DMA system via the transport
specified below.
Transport The transport supported on this port.
Require certificate
validation for TLS
Authentication Select one of the following:
For TLS transport, check this box to enable mutual TLS
(mTLS), requiring callers to present a valid certificate.
Note: If Skip certificate validation for encrypted
signaling is turned off on the Security Settings page,
then Require certificate validation for TLS is turned
on for both authorized and unauthorized ports, and it
can’t be turned off. See “Security Settings” on page 48 .
•None — The system doesn’t issue authentication
challenges or check authentication credentials for
calls to this port.
• Authenticate — The system issues authentication
challenges and checks authentication credentials
for calls to this port.
The settings on the Device Authentication page
(see “Device Authentication” on page 264)
determine the realm used for authentication and
whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized)
or 407 (Proxy Authentication Required).
•Block — The system blocks calls to this port.
See also:
“Signaling Settings” on page 71
“Local Cluster Configuration Procedures” on page 82
78 Polycom, Inc.
Page 91

Signaling Settings Local Cluster Configuration
Add Guest Prefix Dialog Box
The Add Guest Prefix dialog box appears when you click the Add button next
to the Unauthorized prefixes list in the SIP Settings section of the Signaling
Settings page. It lets you add a prefix to the list of prefixes used for
“unauthorized” or “guest” calls.
The following table describes the fields in the Add Guest Prefix dialog box.
Table 4-8 Add Guest Prefix dialog box
Field Description
Prefix The prefix number for this entry.
This is the number that an SBC is configured to add to
the Request-URI of the first INVITE message for
untrusted calls to the DMA system.
Strip prefix Check this box to have the system immediately strip this
prefix from the INVITE message.
Authentication Select one of the following:
•None — The system doesn’t issue authentication
challenges or check authentication credentials for
calls with this prefix.
• Authenticate — The system issues authentication
challenges and checks authentication credentials
for calls with this prefix.
The settings on the Device Authentication page
(see “Device Authentication” on page 264)
determine the realm used for authentication and
whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized)
or 407 (Proxy Authentication Required).
•Block — The system blocks calls with this prefix.
See also:
“Signaling Settings” on page 71
“Local Cluster Configuration Procedures” on page 82
Polycom, Inc. 79
Page 92

DMA Operations Guide Signaling Settings
Edit Guest Prefix Dialog Box
The Edit Guest Prefix dialog box lets you edit an Unauthorized prefixes list
entry in the SIP Settings section of the Signaling Settings page.
The following table describes the fields in the Edit Guest Prefix dialog box.
Table 4-9 Edit Guest Prefix dialog box
Field Description
Prefix The prefix number for this entry.
This is the number that an SBC is configured to add to
the Request-URI of the first INVITE message for
untrusted calls to the DMA system.
Strip prefix Check this box to have the system immediately strip this
prefix from the INVITE message.
Authentication Select one of the following:
•None — The system doesn’t issue authentication
challenges or check authentication credentials for
calls with this prefix.
• Authenticate — The system issues authentication
challenges and checks authentication credentials
for calls with this prefix.
The settings on the Device Authentication page
(see “Device Authentication” on page 264)
determine the realm used for authentication and
whether the Call Server responds to
unauthenticated requests with 401 (Unauthorized)
or 407 (Proxy Authentication Required).
•Block — The system blocks calls with this prefix.
See also:
“Signaling Settings” on page 71
“Local Cluster Configuration Procedures” on page 82
80 Polycom, Inc.
Page 93

Logging Settings Local Cluster Configuration
Logging Settings
The following table describes the fields on the Logging Settings page.
Table 4-10 Fields on the Logging Settings page
Field Description
Logging level Leave the default, Production, unless advised to
change it by Polycom support. Debug is useful for
troubleshooting. Verbose debug is not recommended
for production systems.
Rolling frequency If rolling the logs daily (the default) produces logs that
are too large, shorten the interval.
Retention period The number of days to keep log archives. For most
systems, we recommend setting this to 7.
Alert when logs exceed The percentage of the 1 GB log file capacity in use at
which the system displays a warning on the dashboard.
Local log forwarding Enables you to forward selected log entries to a central
log management server (such as Graylog2).
Specify:
• The address of the destination server. It must be
running some version of syslog.
• The socket type (transport) for which the destination
server’s version of syslog is configured. Most
versions of syslog support only UDP , the default, but
syslog-ng also supports TCP.
• The facility value. Default is Local0.
• The log or logs to forward.
Note: The DMA system’s server .log entries are mapped
to syslog-compliant severities (a “warn” message from
server.log arrives at the destination server. with
syslog-compliant “warn” level). All other logs being
forwarded are assigned the syslog-compliant “notice”
severity.
Each log message is forwarded with its server-side
timestamp intact. The receiving syslog adds its own
timestamp, but preserving the DMA-applied timestamp
makes it easier to accurately troubleshoot time-sensitive
events.
See also:
“Local Cluster Configuration” on page 63
“Local Cluster Configuration Procedures” on page 82
Polycom, Inc. 81
Page 94

DMA Operations Guide Local Cluster Configuration Procedures
Local Cluster Configuration Procedures
This section describes the following Polycom DMA 7000 system configuration
procedures:
• Add Licenses
• Configure Signaling
• Configure Logging
Add Licenses
If you’re performing the initial configuration of your Polycom DMA system,
study “Polycom
before you continue. Other tasks are required that are described elsewhere.
Adding licenses to your Polycom DMA system is a two-step process:
• Request a software activation key code for each server.
• Enter the activation key codes into the system.
The procedures below describe the process.
To request a software activation key code for each server
1 Log into the Polycom DMA system as an administrator and go to Admin
> Local Cluster > Licenses.
2 Record the serial number for each Polycom DMA server:
Server A: ____________________________
Server B: ____________________________ (none for single-server system)
3 Go to http://www.polycom.com/activation.
®
DMA™ System Initial Configuration Summary” on page 23
4 If you don’t already have one, register for an account. Then log in.
5 Select Product Activation.
6 In the License Number field, enter the software license number listed on
the first (or only) server’s License Certificate (shipped with the product).
7 In the Serial Number field, enter the first (or only) server’s serial number
(which you recorded in step 2).
8 Click Generate.
9 When the activation key for the first (or only) server appears, record it:
Server A: __________-__________-_________-___________
10 If you have a single-server Polycom DMA system, you’re finished with
this procedure. Continue to the next procedure.
82 Polycom, Inc.
Page 95

Local Cluster Configuration Procedures Local Cluster Configuration
11 If you have a two-server cluster, repeat steps 6–8, this time entering the
second license number you received and the second server’s serial
number (also recorded in step 2).
Caution
An activation key is linked to a specific server’s serial number. For a two-server
cluster, you must generate the activation key for each server using that server’s
serial number. Licensing will fail if you generate both activation keys from the same
server serial number.
12 When the activation key for the second server appears, record it:
Server B: __________-__________-_________-___________
To enter license activation key codes
1 Go to Admin > Local Cluster > Licenses.
2 In the Activation key field for the first (or only) server, enter the
activation key code that was generated for that server’s serial number.
Configure Signaling
Caution
An activation key is linked to a specific server’s serial number. Each Activation
Key field is labeled with a serial number. For a two-server cluster, make sure that
the activation key code you enter for each server is the correct one for that server’s
serial number.
3 If you have a two-server cluster, in the Activation key field for the second
server, enter the activation key code that was generated for that server’s
serial number.
4 Click Update.
A dialog box informs you that the licenses have been updated.
5 Click OK.
See also:
“Licenses” on page 70
To configure signaling
1 Go to Admin > Local Cluster > Signaling Settings.
2 To make the system accessible via H.323 calls:
a Select Enable H.323 signaling.
Polycom, Inc. 83
Page 96

DMA Operations Guide Local Cluster Configuration Procedures
b Leave the default port numbers (1720 for H.225, 1719 for RAS) unless
you have a good reason for changing them.
c Select H.323 multicast to support gatekeeper discovery messages
from endpoints.
d To turn on H.235 authentication, select Enable H.323 device
authentication.
Device authentication credentials must be added on the Inbound
Authentication tab of the Device Authentication page. Click the
Device authentication settings link to go directly there.
3 To make the system accessible via SIP calls:
a Select Enable SIP signaling.
b If the system’s security settings permit unencrypted SIP connections,
optionally set Unencrypted SIP port to TCP or UDP/TCP.
You must have the Administrator role to change security settings. See
“Security Settings” on page 48.
Note
The system only answers UDP calls if that transport is enabled. But for
communications back to the endpoint, it uses the transport protocol that the
endpoint requested (provided that the transport is enabled, and for TCP, that
unencrypted connections are permitted).
For more information about this and other aspects of SIP, see RFC 3261.
c Leave the default port numbers (5060 for TCP/UDP, 5061 for TLS)
unless you have a good reason for changing them.
d To turn on SIP digest authentication for either the unencrypted or TLS
port, select the corresponding Enable authentication check box.
Device authentication credentials must be added on the Inbound
Authentication tab of the Device Authentication page. Click the
Device authentication settings link to go directly there.
e To enable mutual TLS (mTLS), select Require certificate validation
for TLS.
4 To enable the system to receive untrusted calls (see “Untrusted SIP Call
Handling Configuration” on page 73) from SIP session border controllers
(SBCs) configured to route such calls to special ports, do the following:
a Under Unauthorized ports, click Add.
The Add Guest Port dialog box opens.
b Specify the port number, the transport, whether authentication is
required, and for TLS, whether certificate validation is required
(mTLS). Click OK.
The new entry is added to the Unauthorized ports list.
84 Polycom, Inc.
Page 97

Local Cluster Configuration Procedures Local Cluster Configuration
c Repeat for each additional port on which to receive “unauthorized” or
“guest” calls.
5 To enable the system to receive untrusted calls (see “Untrusted SIP Call
Handling Configuration” on page 73) from SIP session border controllers
(SBCs) configured to add a specific prefix in the Request-URI of the
INVITE message for such calls, do the following:
a Under Unauthorized prefixes, click Add.
The Add Guest Prefix dialog box opens.
b Specify the prefix number, whether it should be stripped, and whether
authentication is required. Click OK.
The new entry is added to the Unauthorized prefixes list.
c Repeat for each additional prefix used for “unauthorized” or “guest”
calls.
6 To enable the system’s XMPP server:
a Select Enable XMPP signaling.
b If the system’s security settings permit unencrypted XMPP
connections, turn on Unencrypted XMPP port.
You must have the Administrator role to change security settings. See
“Security Settings” on page 48.
c Leave the default port numbers (5222 for unencrypted XMPP, 5223 for
TLS) unless you have a good reason for changing them.
7 Click Update.
A dialog box informs you that the configuration has been updated.
8 Click OK.
The system processes the configuration. The Status field shows the
current H.323 signaling state.
9 If you enabled the system to receive “unauthorized” or “guest” calls, do
the following:
a Go to Admin > Call Server > Dial Rules and click in the Dial rules for
unauthorized calls list to give it focus.
b Add one or more dial rules to be used for routing “unauthorized” or
“guest” calls. See “Dial Rules” on page 243.
An unauthorized call rule can route calls to a conference room ID
(virtual meeting room, or VMR), a virtual entry queue (VEQ), or a SIP
peer.
See also:
“Signaling Settings” on page 71
Polycom, Inc. 85
Page 98

DMA Operations Guide Local Cluster Configuration Procedures
Configure Logging
To configure logging
1 Go to Admin > Local Cluster > Logging Settings.
2 Change Rolling frequency and Retention period as desired.
3 If requested to do so by Polycom support, change Logging level.
4 Click Update.
A dialog box informs you that the configuration has been updated.
5 Click OK.
See also:
“Logging Settings” on page 81
86 Polycom, Inc.
Page 99

Device Management
This chapter describes the following Polycom® Distributed Media
Application™ (DMA™) 7000 system’s network device management pages:
• Active Calls
• Endpoints
• Site Statistics
5
Active Calls
• Site Link Statistics
• External Gatekeeper
• External SIP Peer
• External SBC
Other Network menu topics are addressed in the following chapters:
• “Superclustering” on page 227 (DMAs)
• “MCU Management” on page 131
• “Site Topology” on page 283
The Active Calls page lets you monitor the calls in progress (managed by the
Call Server) and disconnect an active call.
The search pane above the two lists lets you find calls matching the criteria you
specify. Click the down arrow to expand the search pane. You can search for
an originator or destination device by its name, alias, or IP address.
The system matches any string you enter against the beginning of the values
for which you entered it. If you enter “10.33.17” in the Originator field, it
displays calls from devices whose IP addresses are in that subnet. To search for
a string not at the beginning of the field, you can use an asterisk (*) as a
wildcard.
Leave a field empty (or select the blank entry from a list) to match all values.
Polycom, Inc. 87
Page 100

DMA Operations Guide Active Calls
Note
Specifying a filter that includes too many active calls can be a drain on system
resources.
The calls that match your search criteria (up to 500) appear in the lower list.
You can pin a call that you want to study. This moves it to the upper list, and
it remains there, even after the call ends, until you unpin it.
Details about the selected call are available in the Call Info, Originator,
Destination, and Bandwidth tabs of the pane on the right. This information
(and more) is also available in the Call Details dialog box, which appears
when you click Show Call Details (in the Actions list). See “Call Details
Dialog Box” on page 89 for descriptions of the data.
The following table describes the parts of the Active Calls list.
Table 5-1 Information in the Active Calls list
Column Description
(Pin State) Click to pin a call, moving it to the top list and keeping its
information available even if the call ends. Click again to
unpin it.
Start Time Time the call began (first signaling event).
Originator Source of the call (the device’s display name, if
available; otherwise, its name, alias, or IP address, in
that order of preference).
Dial String Dial string sent by originator, when available.
Destination Destination of the call (the device’s display name, if
available; otherwise, its name, alias, or IP address, in
that order of preference).
Bit Rate Bit rate (kbps) of the call. A down arrow indicates that
the call was downspeeded. Hover over it to see details.
Class of Service Class of service (Gold, Silver, or Bronze) of the call.
See also:
“Device Management” on page 87
“Call Details Dialog Box” on page 89
“Endpoints” on page 91
88 Polycom, Inc.
 Loading...
Loading...