Page 1

Broadband VPN Router
VRT-311 / VRT-311S
User’s Manual
Page 2

Copyright
Copyright (C) 2004 PLANET Technology Corp. All rights reserved.
The products and programs described in this User’s Manual are licensed products of PLANET
Technology, This User’s Manual contains proprietary information protected by copyright, and
this User’s Manual and all accompanying hardware, software, and documentation are copyrighted.
No part of this User’s Manual may be copied, photocopied, reproduced, translated, or reduced
to any electronic medium or machine-readable form by any means by electronic or mechanical.
Including photocopying, recording, or information storage and retrieval systems, for any purpose other than the purchaser's personal use, and without the prior express written permission
of PLANET Technology.
Disclaimer
PLANET Technology does not warrant that the hardware will work properly in all environments
and applications, and makes no warranty and representation, either implied or expressed, with
respect to the quality, performance, merchantability, or fitness for a particular purpose.
PLANET has made every effort to ensure that this User’s Manual is accurate; PLANET disclaims liability for any inaccuracies or omissions that may have occurred.
Information in this User’s Manual is subject to change without notice and does not represent a
commitment on the part of PLANET. PLANET assumes no responsibility for any inaccuracies
that may be contained in this User’s Manual. PLANET makes no commitment to update or keep
current the information in this User’s Manual, and reserves the right to make improvements to
this User’s Manual and/or to the products described in this User’s Manual, at any time without
notice.
If you find information in this manual that is incorrect, misleading, or incomplete, we would
appreciate your comments and suggestions.
CE mark Warning
This is a class B device, In a domestic environment, this product may cause radio interference,
in which case the user may be required to take adequate measures.
Trademarks
The PLANET logo is a trademark of PLANET Technology. This documentation may refer to
numerous hardware and software products by their trade names. In most, if not all cases, these
designations are claimed as trademarks or registered trademarks by their respective companies.
Revision
User’s Manual for PLANET Broadband VPN Router:
Model: VRT-311 / VRT-311S
Rev: 1.0 (May. 2004)
Part No. EM-VRT311V1
ii
Page 3

Table of Contents
CHAPTER 1 INTRODUCTION..........................................................................1
VRT-311 /VRT-311S Features...............................................................................1
Package Contents.................................................................................................3
Physical Details.....................................................................................................4
CHAPTER 2 INSTALLATION...........................................................................8
Requirements........................................................................................................8
Procedure..............................................................................................................8
CHAPTER 3 SETUP........................................................................................10
Overview..............................................................................................................10
Configuration Program.......................................................................................11
Setup Wizard.......................................................................................................14
LAN Screen..........................................................................................................17
CHAPTER 4 PC CONFIGURATION...............................................................19
Overview..............................................................................................................19
Windows Clients.................................................................................................19
Macintosh Clients...............................................................................................30
Linux Clients........................................................................................................30
Other Unix Systems............................................................................................30
CHAPTER 5 OPERATION AND STATUS......................................................31
Operation.............................................................................................................31
Status Screen......................................................................................................31
Connection Status - PPPoE...............................................................................33
Connection Status - PPTP..................................................................................35
Connection Status - Telstra Big Pond..............................................................36
Connection Details - SingTel RAS.....................................................................37
Connection Details - Fixed/Dynamic IP Address.............................................39
CHAPTER 6 INTERNET FEATURES.............................................................41
Overview..............................................................................................................41
WAN Port Configuration.....................................................................................42
Advanced Internet...............................................................................................45
Dynamic DNS (Domain Name Server)...............................................................49
Virtual Servers.....................................................................................................51
Options.................................................................................................................53
CHAPTER 7 SECURITY CONFIGURATION..................................................54
Overview..............................................................................................................54
Admin Login........................................................................................................54
Access Control....................................................................................................56
Firewall Rules......................................................................................................60
Logs......................................................................................................................64
E-mail...................................................................................................................67
Security Options.................................................................................................69
Scheduling...........................................................................................................71
i
Page 4

Services...............................................................................................................72
CHAPTER 8 VPN (IPSEC)..............................................................................73
Overview..............................................................................................................73
Common VPN Situations....................................................................................75
VPN Configuration..............................................................................................77
VPN Examples.....................................................................................................87
Certificates.........................................................................................................105
CRLs...................................................................................................................109
Status.................................................................................................................110
CHAPTER 9 MICROSOFT VPN....................................................................112
Overview............................................................................................................112
Server Setup......................................................................................................112
Client Database.................................................................................................113
Status Screen....................................................................................................115
Windows Client Setup......................................................................................116
CHAPTER 10 OTHER FEATURES & SETTINGS.......................................124
Overview............................................................................................................124
Config File..........................................................................................................125
Network Diagnostics........................................................................................126
PC Database......................................................................................................127
Remote Administration.....................................................................................131
Routing...............................................................................................................133
Upgrade Firmware.............................................................................................138
UPnP...................................................................................................................139
APPENDIX A TROUBLESHOOTING...........................................................140
Overview............................................................................................................140
General Problems.............................................................................................140
Internet Access..................................................................................................140
APPENDIX B SPECIFICATIONS.................................................................142
VRT-311 / VRT-311S..........................................................................................142
FCC Statement..................................................................................................142
CE Marking Warning.........................................................................................143
ii
Page 5
1
Chapter 1
Introduction
This Chapter provides an overview of VRT-311 / VRT-311S's features and capabilities.
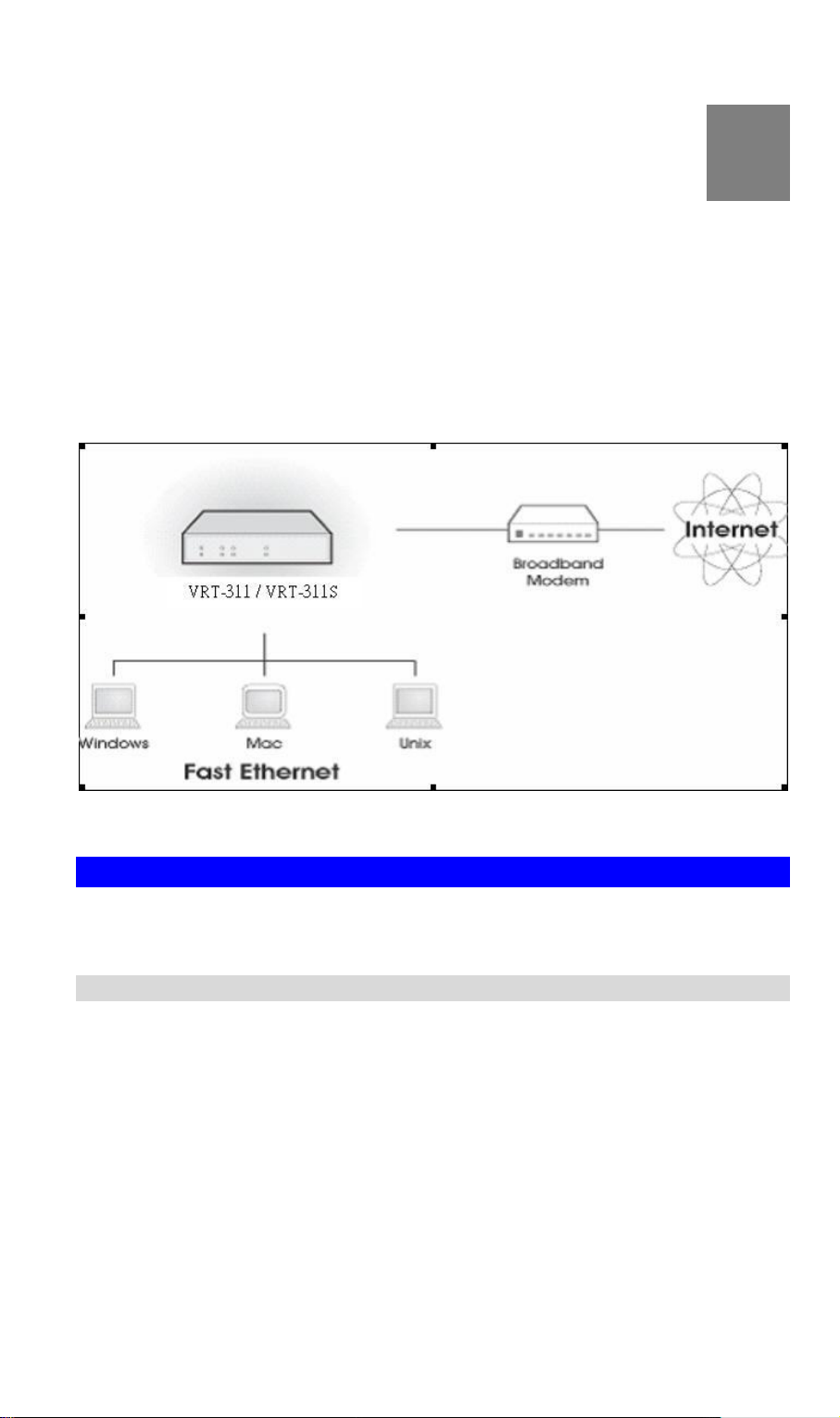
Congratulations on the purchase of your new VRT-311 / VRT-311S . VRT-311 / VRT-311S is
a multi-function device providing the following services:
• Shared Broadband Internet Access for all LAN users.
• VPN Gateway for IPSec VPN connections to remote PCs or sites.
• 3-Port Switching Hub for 10BaseT or 100BaseT connections.
Figure 1: VRT-311 / VRT-311S
VRT-311 / VRT-311S Features
VRT-311 / VRT-311S incorporates many advanced features, carefully designed to provide
sophisticated functions while being easy to use.
Internet Access Features
• Shared Internet Access. All users on the LAN or WLAN can access the Internet
through VRT-311 / VRT-311S, using only a single external IP Address. The local (invalid)
IP Addresses are hidden from external sources. This process is called NAT (Network Address Translation).
• DSL & Cable Modem Support. VRT-311 / VRT-311S has a 100BaseT Ethernet port
for connecting a DSL or Cable Modem. All popular DSL and Cable Modems are supported. SingTel RAS and Big Pond (Australia) login support is also included.
• PPPoE, PPTP, SingTel RAS and Telstra Big Pond Support. The Internet (WAN
port) connection supports PPPoE (PPP over Ethernet), PPTP (Peer-to-Peer Tunneling Protocol), SingTel RAS and Telstra Big Pond (Australia), as well as "Direct Connection" type
services.
1
Page 6

VRT-311 User Guide
• Fixed or Dynamic IP Address. On the Internet (WAN port) connection, VRT-311 /
VRT-311S supports both Dynamic IP Address (IP Address is allocated on connection) and
Fixed IP Address.
Advanced Internet Functions
• Communication Applications. Support for Internet communication applications, such
as interactive Games, Telephony, and Conferencing applications, which are often difficult
to use when behind a Firewall, is included.
• Special Internet Applications. Applications which use non-standard connections or
port numbers are normally blocked by the Firewall. The ability to define and allow such
applications is provided, to enable such applications to be used normally.
• Virtual Servers. This feature allows Internet users to access Internet servers on your
LAN. The required setup is quick and easy.
• Multi-DMZ. For each WAN (Internet) IP address allocated to you, one (1) PC on your
local LAN can be configured to allow unrestricted 2-way communication with Servers or
individual users on the Internet. This provides the ability to run programs which are incompatible with Firewalls.
• Physical DMZ Port. PCs connected to the DMZ port are effectively isolated from your
LAN, while connected to the Internet. This provides additional security for your LAN
while allowing your Servers to be accessed from the Internet.
• URL Filter. Use the URL Filter to block access to undesirable Web sites by LAN users.
• Internet Access Log. See which Internet connections have been made.
• VPN Pass through Support. PCs with VPN (Virtual Private Networking) software
using PPTP, L2TP and IPSec are transparently supported - no configuration is required.
LAN Features
• 3-Port Switching Hub. VRT-311 / VRT-311S incorporates a 3-port 10/100BaseT
switching hub, making it easy to create or extend your LAN.
• DHCP Server Support. Dynamic Host Configuration Protocol provides a dynamic IP
address to PCs and other devices upon request. VRT-311 / VRT-311S can act as a DHCP
Server for devices on your local LAN and WLAN.
• Multi Segment LAN Support. LANs containing one or more segments are supported,
via VRT-311's / VRT-311S RIP (Routing Information Protocol) support and built-in static
routing table.
• DMZ Port. Used when allowing Servers on your LAN to be accessed from the Internet,
the DMZ port provides additional protection for both your Servers and your LAN.
Configuration & Management
• Easy Setup. Use your WEB browser from anywhere on the LAN or WLAN for configu-
ration.
• Remote Management. VRT-311 / VRT-311S can be managed from any PC on your
LAN. And, if the Internet connection exists, it can also (optionally) be configured via the
Internet.
• UPnP Support. UPnP (Universal Plug and Play) allows automatic discovery and con-
figuration of VRT-311 / VRT-311S. UPnP is by supported by Windows ME, XP, or later.
• Configuration File Backup & Restore. You can backup (download) VRT-311 /
VRT-311S 's configuration file to your PC, and restore (upload) a previously-saved configuration file to VRT-311 / VRT-311S.
2
Page 7

Introduction
Security Features
• Password - protected Configuration. Optional password protection is provided to
prevent unauthorized users from modifying the configuration data and settings.
• NAT Protection. An intrinsic side effect of NAT (Network Address Translation) tech-
nology is that by allowing all LAN users to share a single IP address, the location and even
the existence of each PC is hidden. From the external viewpoint, there is no network, only
a single device - VRT-311 / VRT-311S.
• Stateful Inspection Firewall. All incoming data packets are monitored and all incom-
ing server requests are filtered, thus protecting your network from malicious attacks from
external sources.
• Protection against DoS attacks. DoS (Denial of Service) attacks can flood your
Internet connection with invalid packets and connection requests, using so much bandwidth
and so many resources that Internet access becomes unavailable. VRT-311 / VRT-311S incorporates protection against DoS attacks.
• Rule-based Policy Firewall. To provide additional protection against malicious pack-
ets, you can define your own firewall rules. This can also be used to control the Internet
services available to LAN users.
IPSec VPN Gateway Features
• IPSec.. Support for IPSec standards, including IKE and certificates.
• Tunnels. Up to 100 VPN tunnels can be created for VRT-311, and up to 10 VPN tunnels
can be created for VRT-311S..
• High performance. High performance encryption engine maintains high throughput
even when using 3DES.
Microsoft VPN Gateway Support
• PPTP Server. VRT-311 / VRT-311S emulates a Microsoft PPTP VPN Server, allowing
clients to use the Microsoft VPN client provided in Windows.
• Windows Client Support. Remote users can use the Microsoft VPN client (VPN
Adapter) provided in recent versions of Windows.
• Easy Setup. For both the Administrator and remote users, the Microsoft VPN is much
easier to configure than IPSec VPN.
Package Contents
The following items should be included:
• VRT-311 / VRT-311S Unit
• Power Adapter
• Quick Installation Guide
• CD-ROM containing the on-line manual.
If any of the above items are damaged or missing, please contact your dealer immediately.
3
Page 8

VRT-311 User Guide
Physical Details
Front-mounted LEDs
Figure 2: VRT-311’s Front Panel
Figure 3: VRT-311S’s Front Panel
Power On - Power on.
Off - No power.
Status (Red) On - Error condition.
Off - Normal operation.
Blinking - This LED blinks during start up.
LAN
DMZ
Each port has 2 LEDs
• LNK/ACT
• On - Corresponding LAN (hub) port is active.
• Off - No active connection on the corresponding LAN (hub) port.
• Flashing - Data is being transmitted or received via the corre-
sponding LAN (hub) port.
• 100
• On - Corresponding LAN (hub) port is using 100BaseT.
• Off - Corresponding LAN (hub) port connection is using
10BaseT, or no active connection.
• LNK/ACT
• On - DMZ port is active.
• Off - No active connection to the DMZ port.
• Flashing - Data is being transmitted or received via the DMZ
port.
• 100
• On - DMZ port is using 100BaseT.
• Off - DMZ port connection is using 10BaseT, or no active con-
nection.
WAN On - Connection to the modem attached to the WAN (Internet) port is
established.
4
Page 9

Off - No connection to a modem on the WAN (Internet) port.
Flashing - Data is being transmitted or received via the WAN port.
Introduction
PPPoE
(For VRT-311
only)
On - PPPoE connection established.
Off - No PPPoE connection.
5
Page 10

VRT-311 User Guide
Rear Panel
Figure 4: VRT-311 Rear Panel
Figure 5: VRT-311S Rear Panel
Reset Button
WAN port
(10/100BaseT)
DMZ port
10/100BaseT
LAN connections
This button has two (2) functions:
• Reboot. When pressed and released, VRT-311 / VRT-311S will
reboot (restart).
• Clear All Data. This button can also be used to clear ALL data
and restore ALL settings to the factory default values.
To Clear All Data and restore the factory default values:
1. Power Off.
2. Hold the Reset Button down while you Power On.
3. Keep holding the Reset Button for a few seconds, until the RED
LED has flashed TWICE.
4. Release the Reset Button. VRT-311 / VRT-311S is now using
the factory default values.
Connect the DSL or Cable Modem here. If your modem came with a
cable, use the supplied cable. Otherwise, use a standard LAN cable.
PCs or devices connected to the DMZ port are isolated from the
LAN.
If you have a server you wish to make available to the public, you can
connect it here. To use multiple servers, use a standard LAN cable to
connect the DMZ port to a normal port on another hub, and connect
your servers to the hub.
Use standard LAN cables (RJ45 connectors) to connect your PCs to
these ports.
Power port
Note:
Any LAN port on VRT-311 / VRT-311S will automatically function
as an "Uplink" port when required. Just connect any port to a normal
port on the other hub, using a standard LAN cable.
Connect the supplied power adapter here.
6
Page 11

Introduction
Using the DMZ Port
The DMZ port is intended for connection of a server you wish to make available to the public.
To use multiple servers, use a standard LAN cable to connect the DMZ port to a normal port on
another hub, and connect your servers to the hub.
Please note the following points regarding the DMZ port.
• Although physically attached to the hub ports, the DMZ port is not part of the built-in hub.
It is a separate single port which is isolated from the hub.
• PCs connected to the DMZ port are on the same LAN segment as PCs connected to the
Hub ports. They must use the same IP address range.
• PCs connected to the DMZ port are NOT visible to PCs on the hub (LAN) ports. So you
cannot use Microsoft networking or other networking protocols to connect to PCs on the
DMZ. The connection must be made via the Internet.
• PCs connected to the DMZ port still share the WAN port IP address for Internet access.
• To make PCs on the DMZ port available from the Internet, the "Virtual Server" (Port
Forwarding) feature must be configured to send incoming traffic to the appropriate server.
Advantages of the DMZ Port
If running any Servers on your LAN, you should connect them to the DMZ port, for the following reasons:
• Traffic passing between the DMZ and LAN passes through the firewall. The firewall will
protect your LAN if your Server is compromised and used to launch an attack on your
LAN.
• When using the Virtual Servers feature, (see Virtual Servers in Chapter 6) a firewall rule to
allow incoming traffic from the Internet (WAN) to the DMZ is automatically created.
If the Server is connected to the LAN (hub) ports, you must add the firewall rule manually.
7
Page 12
2
Chapter 2
Installation
This Chapter covers the physical installation of VRT-311 / VRT-311S.
Requirements
• Network cables. Use standard 10/100BaseT network (UTP) cables with RJ45 connectors.
• TCP/IP protocol must be installed on all PCs.
• For Internet Access, an Internet Access account with an ISP, and a Broadband modem
(usually, DSL or Cable modem).
Procedure
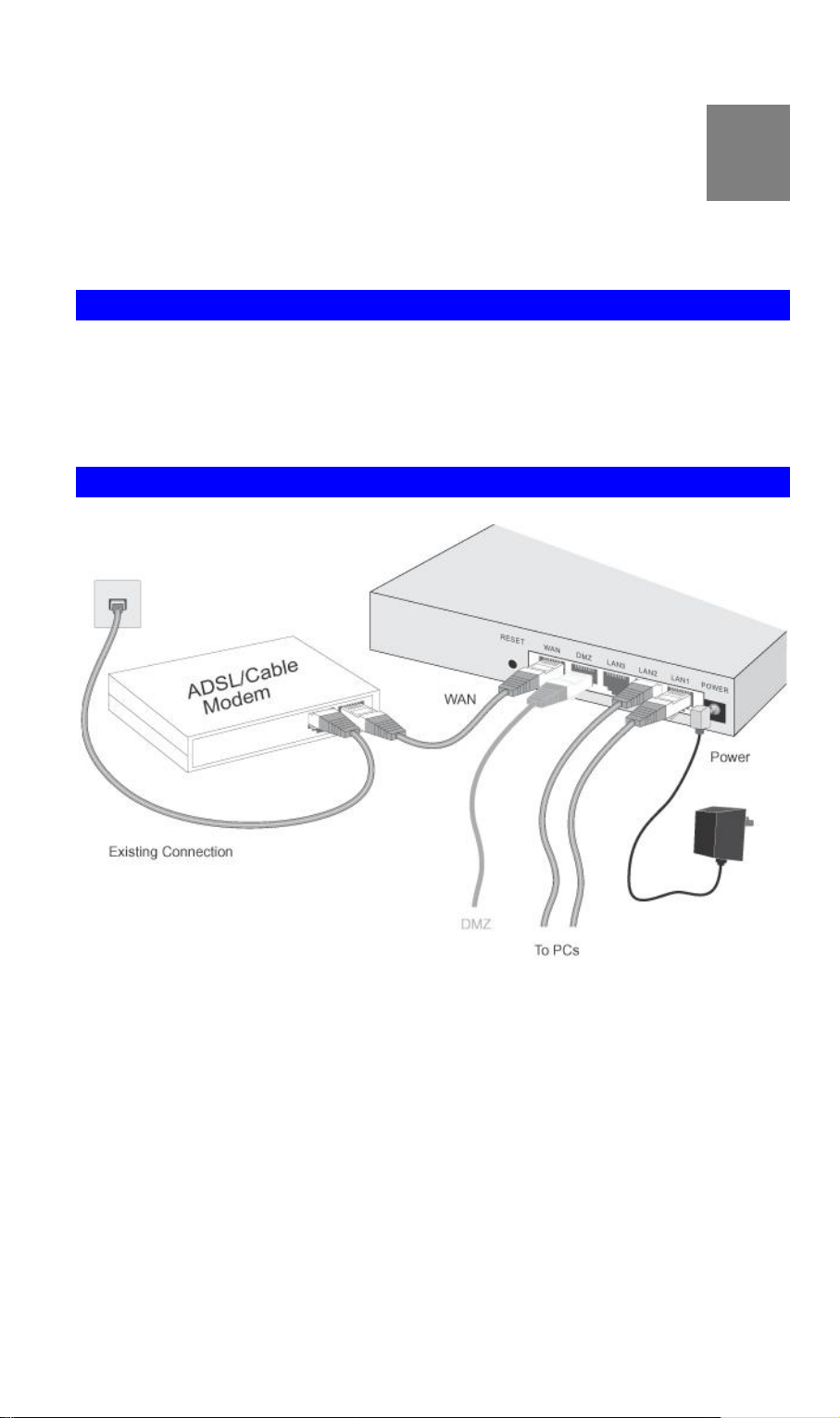
Figure 6: Installation Diagram
1. Choose an Installation Site
Select a suitable place on the network to install VRT-311 / VRT-311S.
Ensure VRT-311 / VRT-311S and the DSL/Cable modem are powered OFF.
2. Connect LAN Cables
• Use standard LAN cables to connect PCs to the Switching Hub ports on VRT-311 / VRT-
311S. Both 10BaseT and 100BaseT connections can be used simultaneously.
• If required, you can connect any LAN port to another Hub. Any LAN port on VRT-311 /
VRT-311S will automatically function as an "Uplink" port when required. Just connect any
LAN port to a normal port on the other hub, using a standard LAN cable.
8
Page 13

Installation
• If desired, connect a PC (server) to the DMZ port. To use multiple servers, use a standard
LAN cable to connect the DMZ port to a normal port on another hub, and connect your
servers to the hub. PCs connected to the DMZ port are isolated from your LAN.
3. Connect WAN Cable
Connect the Broadband modem to the WAN port on VRT-311 / VRT-311S. Use the cable
supplied with your Broadband modem. If no cable was supplied, use a standard LAN cable.
4. Power Up
• Power on the Broadband modem.
• Connect the supplied power adapter to VRT-311 / VRT-311S and power up.
Use only the power adapter provided. Using a different one may cause hardware damage
5. Check the LEDs
• The Power LED should be ON.
• The Status LED should blink during start up, then turn Off. If it stays on, there is a hard-
ware error.
• For each LAN (PC) connection, the LAN Link/Act LED should be ON (provided the PC is
also ON.)
• If a PC is connected to the DMZ port, the DMZ port's Link/Act LED should be ON (pro-
vided the PC is also ON.)
• The WAN LED should be ON.
For more information, refer to Front-mounted LEDs in Chapter 1.
9
Page 14
3
Chapter 3
Setup
This Chapter provides Setup details of VRT-311 / VRT-311S.
Overview
This chapter describes the setup procedure for:
• Internet Access
• LAN configuration
PCs on your local LAN may also require configuration. For details, see Chapter 4 - PC Configuration.
Other configuration may also be required, depending on which features and functions of VRT311 / VRT-311S you wish to use. Use the table below to locate detailed instructions for the
required functions.
To Do this: Refer to:
Configure PCs on your LAN. Chapter 4:
PC Configuration
Check VRT-311 / VRT-311S operation and Status. Chapter 5:
Operation and Status
Use any of the following Internet features:
• WAN Port
• Advanced Setup
• Dynamic DNS
• Virtual Servers
• Options
Change any of the following Security-related settings:
• Admin Login
• Access Control
• Firewall Rules
• Logs
• E-mail
• Security Options
• Scheduling
• Services
Chapter 6:
Internet Features
Chapter 7:
Security Configuration
Use the IPSec VPN features:
• VPN Policies
• Certificates
• CRLs
• VPN Status
Chapter 8:
VPN (IPSec)
10
Page 15

Setup
Use the Microsoft VPN feature:
• PPTP Server in VRT-311 / VRT-311S.
• User and Client setup.
• Checking VPN connection Status.
Configure or use any of the following:
• Configuration File backup and restore.
• Network Diagnostic
• PC Database
• Remote Administration
• Routing
• Upgrade Firmware
• UPnP
Where use of a certain feature requires that
PCs or other LAN devices be configured, this
is also explained in the relevant chapter.
Configuration Program
Chapter 9:
Microsoft VPN
Chapter 9:
Other Features and Settings
VRT-311 / VRT-311S contains an HTTP server. This enables you to connect to it, and configure it, using your Web Browser. Your Browser must support JavaScript. The configuration
program has been tested on the following browsers:
• Netscape V4.08 or later
• Internet Explorer V4 or later
Preparation
Before attempting to configure VRT-311 / VRT-311S, please ensure that:
• Your PC can establish a physical connection to VRT-311 / VRT-311S. The PC and VRT-
311 / VRT-311S must be directly connected (using the Hub ports on VRT-311 / VRT311S) or on the same LAN segment.
• VRT-311 / VRT-311S must be installed and powered ON.
• If VRT-311 / VRT-311S’s default IP Address (192.168.0.1) is already used by another
device, the other device must be turned OFF until VRT-311 / VRT-311S is allocated a new
IP Address during configuration.
Using UPnP
If your Windows system supports UPnP, an icon for VRT-311 / VRT-311S will appear in the
system tray, notifying you that a new network device has been found, and offering to create a
new desktop shortcut to the newly-discovered device.
• Unless you intend to change the IP Address of VRT-311 / VRT-311S, you can accept the
desktop shortcut.
• Whether you accept the desktop shortcut or not, you can always find UPnP devices in My
Network Places (previously called Network Neighborhood).
11
Page 16
VRT-311 User Guide
• Double - click the icon for VRT-311 / VRT-311S (either on the Desktop, or in My Network
Places) to start the configuration. Refer to the following section Setup Wizard for details of
the initial configuration process.
Using your Web Browser
To establish a connection from your PC to VRT-311 / VRT-311S:
1. After installing VRT-311 / VRT-311S in your LAN, start your PC. If your PC is already
running, restart it.
2. Start your WEB browser.
3. In the Address box, enter "HTTP://" and the IP Address of VRT-311 / VRT-311S, as in
this example, which uses VRT-311 / VRT-311S 's default IP Address:
HTTP://192.168.0.1
If you can't connect
If VRT-311 / VRT-311S does not respond, check the following:
• VRT-311 / VRT-311S is properly installed, LAN connection is OK, and it is
powered ON. You can test the connection by using the "Ping" command:
• Open the MS-DOS window or command prompt window.
• Enter the command:
ping 192.168.0.1
If no response is received, either the connection is not working, or your
PC's IP address is not compatible with VRT-311 / VRT-311S’s IP Address. (See next item.)
• If your PC is using a fixed IP Address, its IP Address must be within the range
192.168.0.2 to 192.168.0.254 to be compatible with VRT-311 / VRT-311S 's
default IP Address of 192.168.0.1. Also, the Network Mask must be set to
255.255.255.0. See Chapter 4 - PC Configuration for details on checking your
PC's TCP/IP settings.
• Ensure that your PC and VRT-311 / VRT-311S are on the same network
segment. (If you don't have a router, this must be the case.)
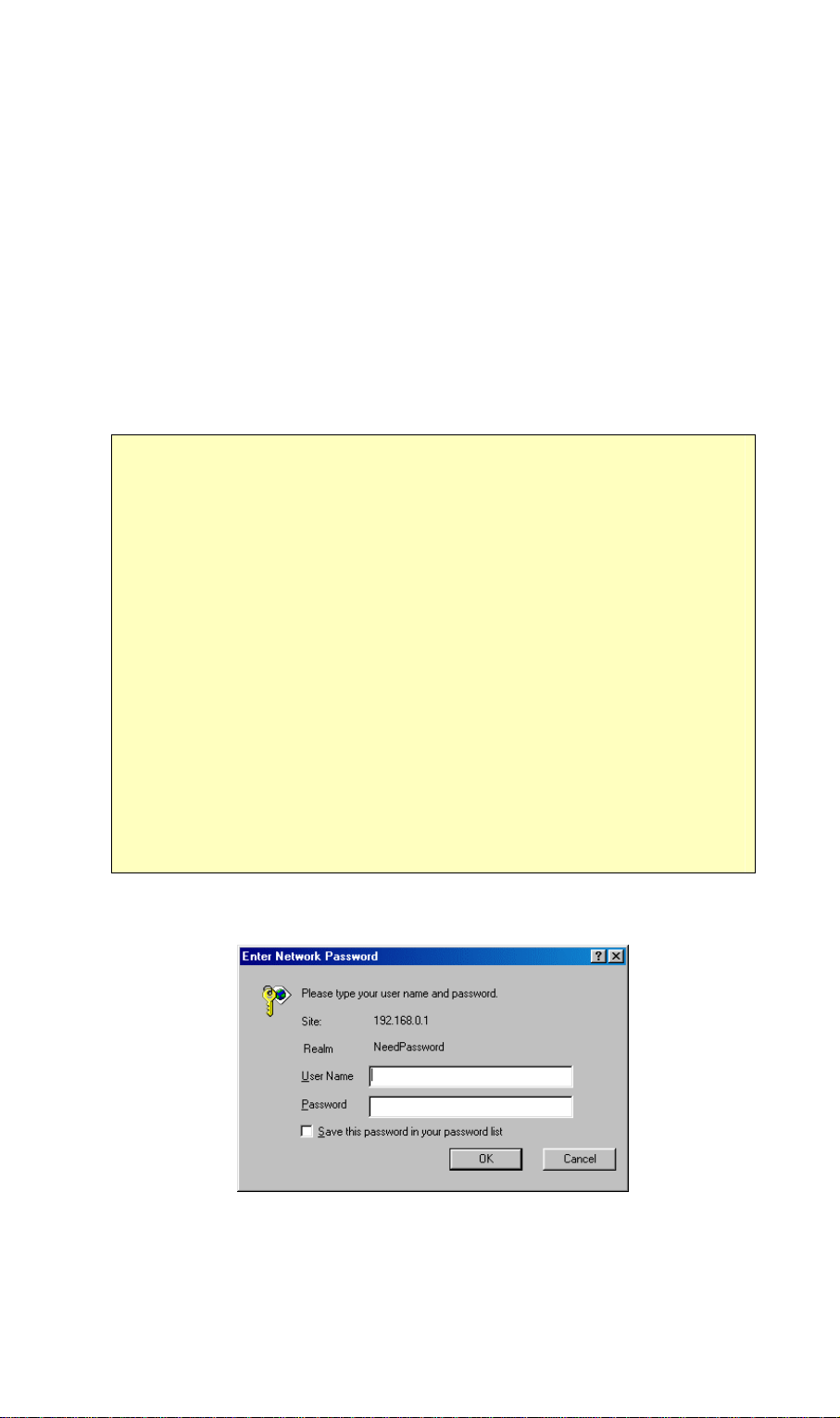
4. You will be prompted for a username and password, as shown below.
Figure 7: Password Dialog
• Enter admin for the User Name, and leave the Password blank.
12
Page 17

Setup
• These are the default values. Both the name and password can (and should) be changed,
using the Admin Login screen. Once you have changed either the name or the password,
you must use the current values.
13
Page 18
VRT-311 User Guide
Setup Wizard
The first time you connect to VRT-311 / VRT-311S, the Setup Wizard will run automatically.
(The Setup Wizard will also run if VRT-311 / VRT-311S 's default setting are restored.)
1. Step through the Wizard until finished.
• You need to know the type of Internet connection service used by your ISP. Check the
data supplied by your ISP.
• The common connection types are explained in the tables below.
2. On the final screen of the Wizard, run the test and check that an Internet connection can be
established.
3. If the connection test fails:
• Check your data, the Cable/DSL modem, and all connections.
• Check that you have entered all data correctly.
• If using a Cable modem, your ISP may have recorded the MAC (physical) address of
your PC. Run the Wizard, and on the Cable Modem screen, use the "Clone MAC address" button to copy the MAC address from your PC to VRT-311 / VRT-311S.
Common Connection Types
Cable Modems
Type Details ISP Data required
Dynamic
IP Address
Static (Fixed)
IP Address
DSL Modems
Type Details ISP Data required
Dynamic
IP Address
Your IP Address is allocated
automatically, when you
connect to you ISP.
Your ISP allocates a permanent IP Address to you.
Your IP Address is allocated
automatically, when you
connect to you ISP.
Usually, none.
However, some ISP's may
require you to use a particular
Hostname, Domain name, or
MAC (physical) address.
IP Address allocated to you,
mask and gateway (if provided),
and DNS address.
Some ISP's may also require
you to use a particular Hostname, Domain name, or MAC
(physical) address.
None.
Static (Fixed)
IP Address
PPPoE You connect to the ISP only
Your ISP allocates a permanent IP Address to you.
when required. The IP address
is usually allocated automatically.
IP Address allocated to you,
mask and gateway (if provided),
and DNS address.
User name and password.
14
Page 19
Setup
PPTP Mainly used in Europe.
You connect to the ISP only
when required. The IP address
is usually allocated automatically, but may be Static
(Fixed).
Other Modems (e.g. Broadband Wireless)
Type Details ISP Data required
Dynamic
IP Address
Static (Fixed)
IP Address
Your IP Address is allocated
automatically, when you
connect to you ISP.
Your ISP allocates a permanent IP Address to you.
Big Pond Cable (Australia)
For this connection method, the following data is required:
• User Name
• Password
• Big Pond Server IP address
• PPTP Server IP Address.
• User name and password.
• IP Address allocated to you,
if Static (Fixed).
Usually, none.
However, some ISP's may
require you to use a particular
Hostname, Domain name, or
MAC (physical) address.
IP Address allocated to you,
mask and gateway (if provided),
and DNS address.
SingTel RAS
For this connection method, the following data is required:
• User Name
• Password
• RAS Plan
15
Page 20
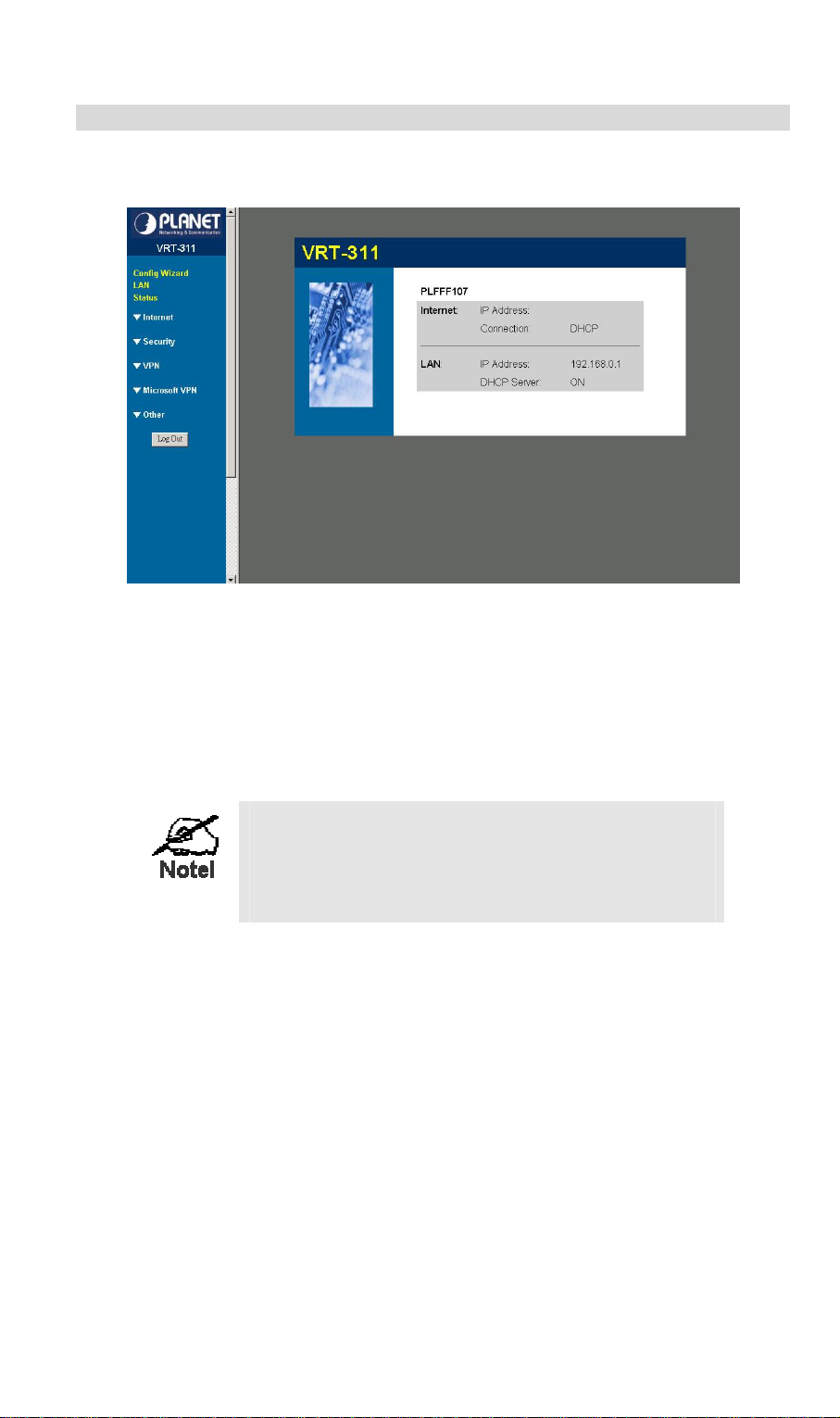
VRT-311 User Guide
Home Screen
After finishing or exiting the Setup Wizard, you will see the Home screen. When you connect
in future, you will see this screen when you connect. An example screen is shown below.
Figure 8: Home Screen
Navigation & Data Input
• Use the menu bar on the top of the screen, and the "Back" button on your Browser, for
navigation.
• Changing to another screen without clicking "Save" does NOT save any changes you may
have made. You must "Save" before changing screens or your data will be ignored.
On each screen, clicking the "Help" button will
display help for that screen.
From any help screen, you can access the list of all
help files (help index).
16
Page 21
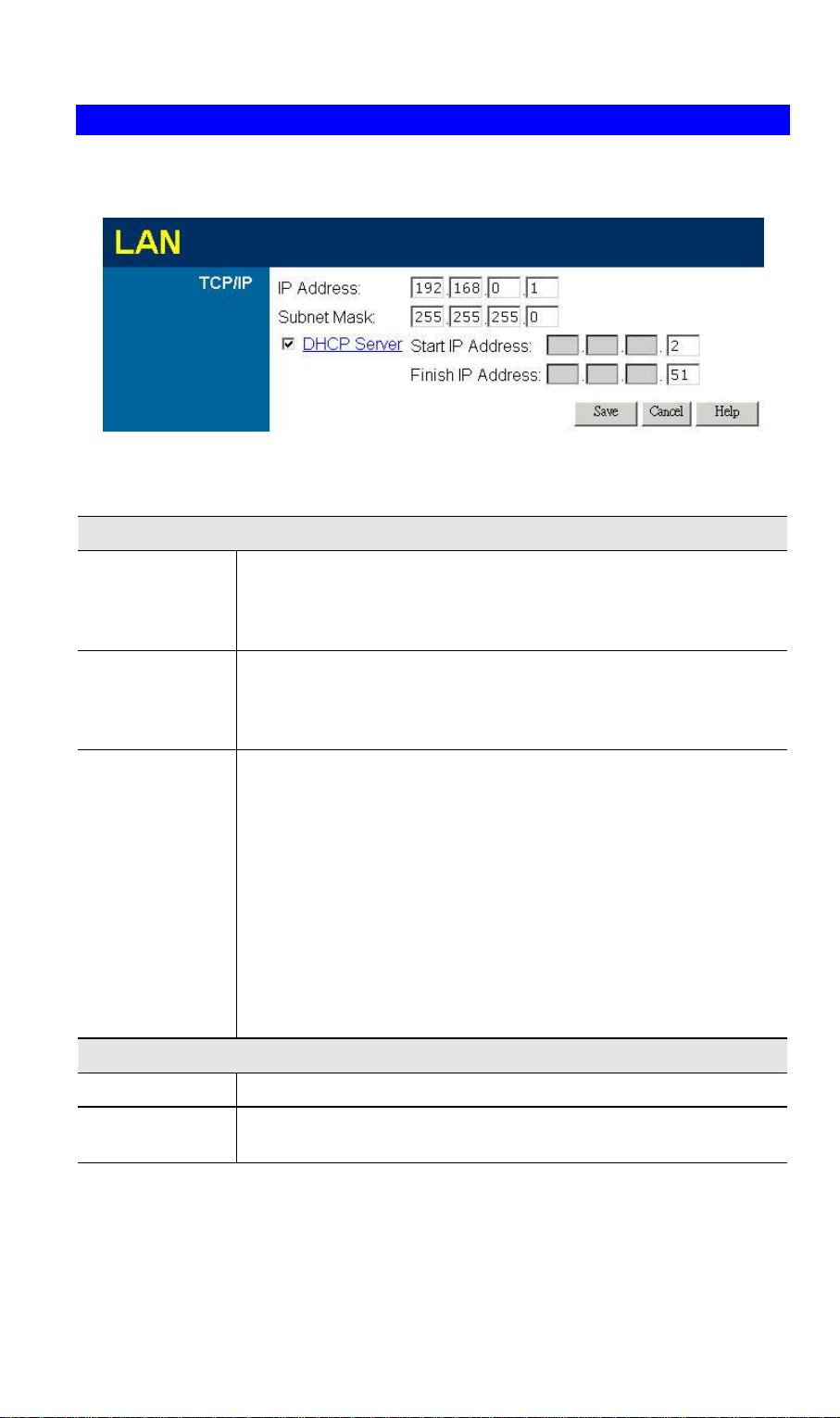
LAN Screen
Use the LAN link on the main menu to reach the LAN screen An example screen is shown
below.
Figure 9: LAN Screen
Data - LAN Screen
TCP/IP
Setup
IP Address
Subnet Mask
DHCP Server
Buttons
Save
IP address for VRT-311 / VRT-311S, as seen from the local LAN. Use
the default value unless the address is already in use or your LAN is
using a different IP address range. In the latter case, enter an unused IP
Address from within the range used by your LAN.
The default value 255.255.255.0 is standard for small (class "C")
networks. For other networks, use the Subnet Mask for the LAN
segment to which VRT-311 / VRT-311S is attached (the same value as
the PCs on that LAN segment).
• If Enabled, VRT-311 / VRT-311S will allocate IP Addresses to
PCs (DHCP clients) on your LAN when they start up. The default
(and recommended) value is Enabled.
• If you are already using a DHCP Server, this setting must be
Disabled, and the existing DHCP server must be re-configured to
treat VRT-311 / VRT-311S as the default Gateway. See the
following section for further details.
• The Start IP Address and Finish IP Address fields set the values
used by the DHCP server when allocating IP Addresses to DHCP
clients. This range also determines the number of DHCP clients
supported.
See the following section for further details on using DHCP.
Save the data on screen.
Cancel
The "Cancel" button will discard any data you have entered and reload
the file from VRT-311 / VRT-311S.
17
Page 22

VRT-311 User Guide
DHCP
What DHCP Does
A DHCP (Dynamic Host Configuration Protocol) Server allocates a valid IP address to a
DHCP Client (PC or device) upon request.
• The client request is made when the client device starts up (boots).
• The DHCP Server provides the Gateway and DNS addresses to the client, as well as
allocating an IP Address.
• VRT-311 / VRT-311S can act as a DHCP server.
• Windows 95/98/ME and other non-Server versions of Windows will act as a DHCP client.
This is the default Windows setting for the TCP/IP network protocol. However, Windows
uses the term Obtain an IP Address automatically instead of "DHCP Client".
• You must NOT have two (2) or more DHCP Servers on the same LAN segment. (If your
LAN does not have other Routers, this means there must only be one (1) DHCP Server on
your LAN.)
Using VRT-311 / VRT-311S 's DHCP Server
This is the default setting. The DHCP Server settings are on the LAN screen. On this screen,
you can:
• Enable or Disable VRT-311 / VRT-311S 's DHCP Server function.
• Set the range of IP Addresses allocated to PCs by the DHCP Server function.
You can assign Fixed IP Addresses to some devices
while using DHCP, provided that the Fixed IP Addresses
are NOT within the range used by the DHCP Server.
Using another DHCP Server
You can only use one (1) DHCP Server per LAN segment. If you wish to use another DHCP
Server, rather than VRT-311 / VRT-311S 's, the following procedure is required.
1. Disable the DHCP Server feature in VRT-311 / VRT-311S. This setting is on the LAN
screen.
2. Configure the DHCP Server to provide VRT-311 / VRT-311S 's IP Address as the Default
Gateway.
To Configure your PCs to use DHCP
This is the default setting for TCP/IP under Windows 95/98/ME.
See Chapter 4 - Client Configuration for the procedure to check these settings.
18
Page 23
4
Chapter 4
PC Configuration
This Chapter details the PC Configuration required on the local ("Internal")
LAN.
Overview
For each PC, the following may need to be configured:
• TCP/IP network settings
• Internet Access configuration
Windows Clients
This section describes how to configure Windows clients for Internet access via VRT-311 /
VRT-311S.
The first step is to check the PC's TCP/IP settings.
VRT-311 / VRT-311S uses the TCP/IP network protocol for all functions, so it is essential that
the TCP/IP protocol be installed and configured on each PC.
TCP/IP Settings - Overview
If using the default VRT-311 / VRT-311S settings, and the default Windows TCP/IP settings, no changes need to be made.
• By default, VRT-311 / VRT-311S will act as a DHCP Server, automatically providing a
suitable IP Address (and related information) to each PC when the PC boots.
• For all non-Server versions of Windows, the default TCP/IP setting is to act as a DHCP
client.
If using a Fixed (specified) IP address, the following changes are required:
• The Gateway must be set to the IP address of VRT-311 / VRT-311S.
• The DNS should be set to the address provided by your ISP.
If your LAN has a Router, the LAN Administrator must reconfigure the Router itself. Refer to Chapter 8 - Other
Features and Operations for details.
19
Page 24
Broadband VPN Router User’s Manual
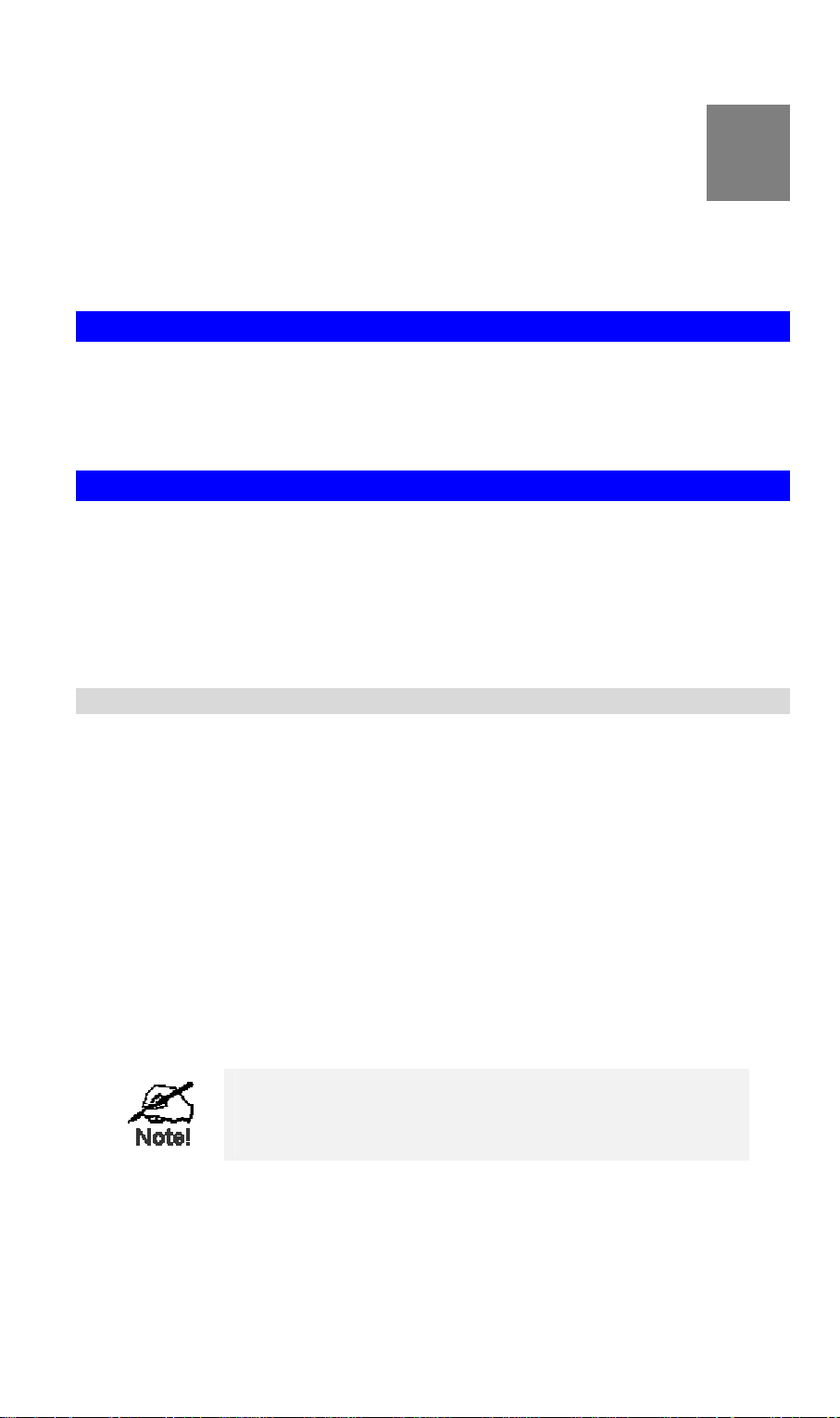
Checking TCP/IP Settings - Windows 9x/ME:
1. Select Control Panel - Network. You should see a screen like the following:
Figure 10: Network Configuration
2. Select the TCP/IP protocol for your network card.
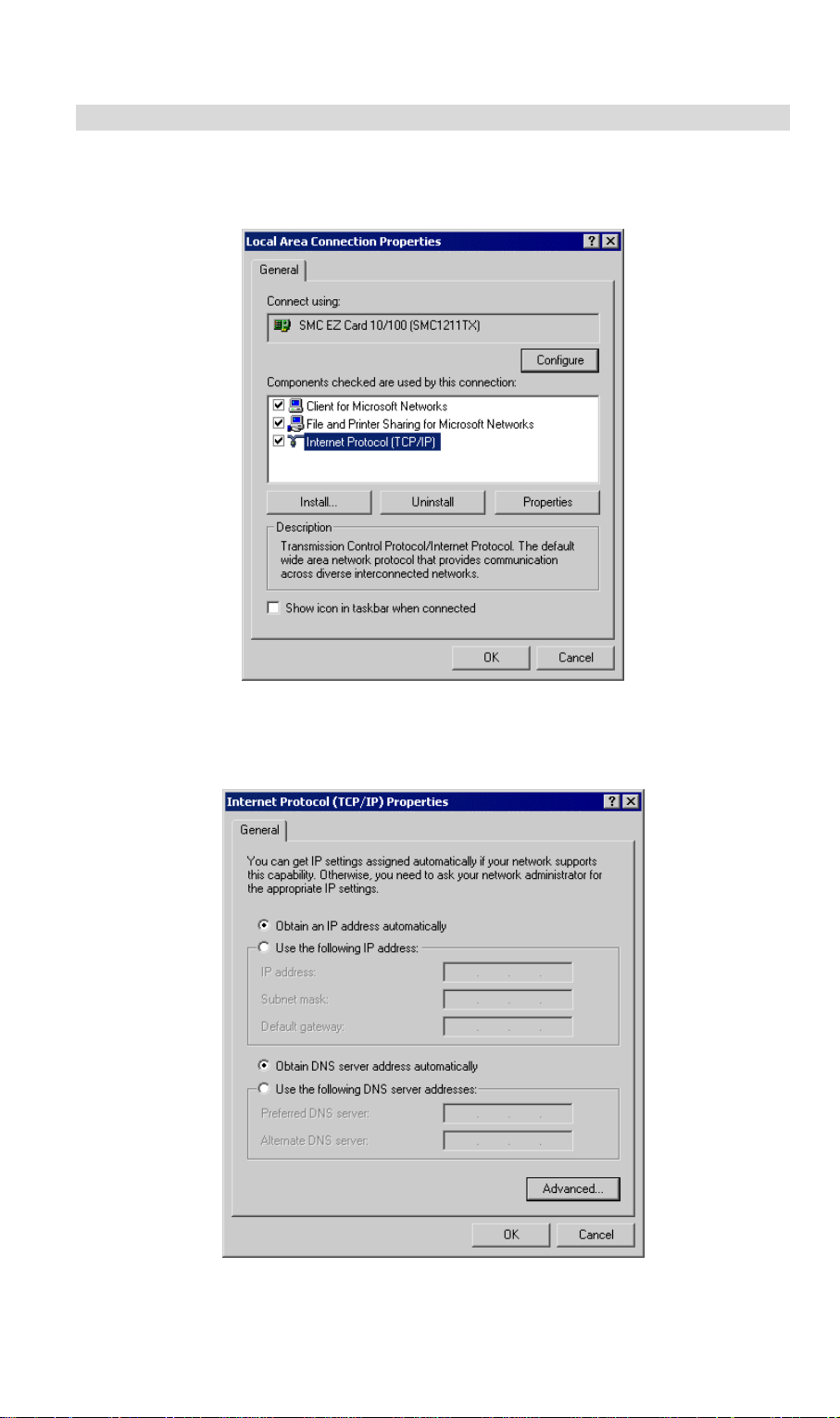
3. Click on the Properties button. You should then see a screen like the following.
Figure 11: IP Address (Win 95)
Ensure your TCP/IP settings are correct, as follows:
Using DHCP
To use DHCP, select the radio button Obtain an IP Address automatically. This is the default
Windows setting. Using this is recommended. By default, VRT-311 / VRT-311S will act as a
DHCP Server.
Restart your PC to ensure it obtains an IP Address from VRT-311 / VRT-311S.
Using "Specify an IP Address"
If your PC is already configured, check with your network administrator before making the
following changes:
20
Page 25
PC Configuration
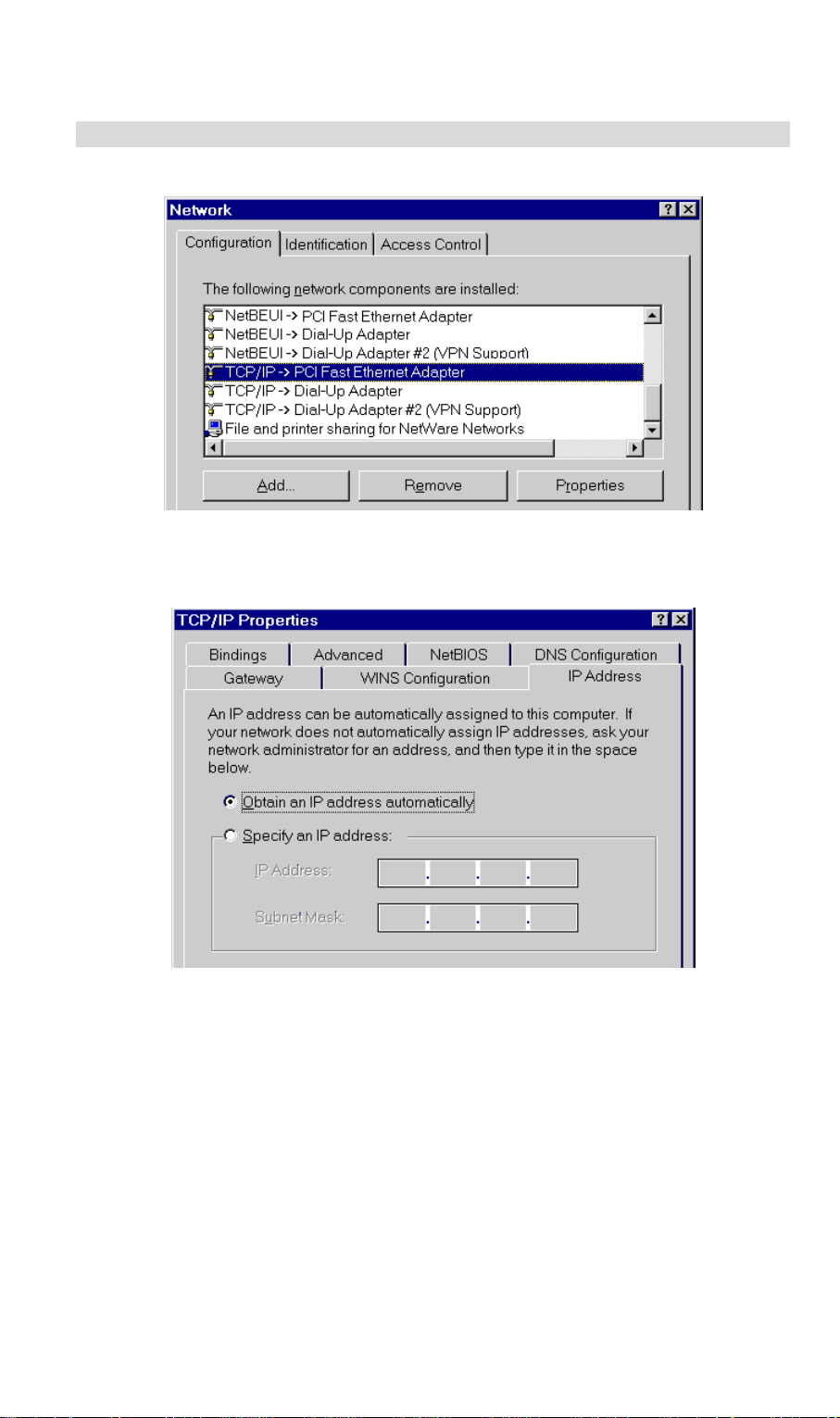
• On the Gateway tab, enter VRT-311 / VRT-311S 's IP address in the New Gateway field
and click Add, as shown below. Your LAN administrator can advise you of the IP Address
they assigned to VRT-311 / VRT-311S.
Figure 32: Gateway Tab (Win 95/98)
• On the DNS Configuration tab, ensure Enable DNS is selected. If the DNS Server Search
Order list is empty, enter the DNS address provided by your ISP in the fields beside the
Add button, then click Add.
Figure 3: DNS Tab (Win 95/98)
21
Page 26
Broadband VPN Router User’s Manual
Checking TCP/IP Settings - Windows NT4.0
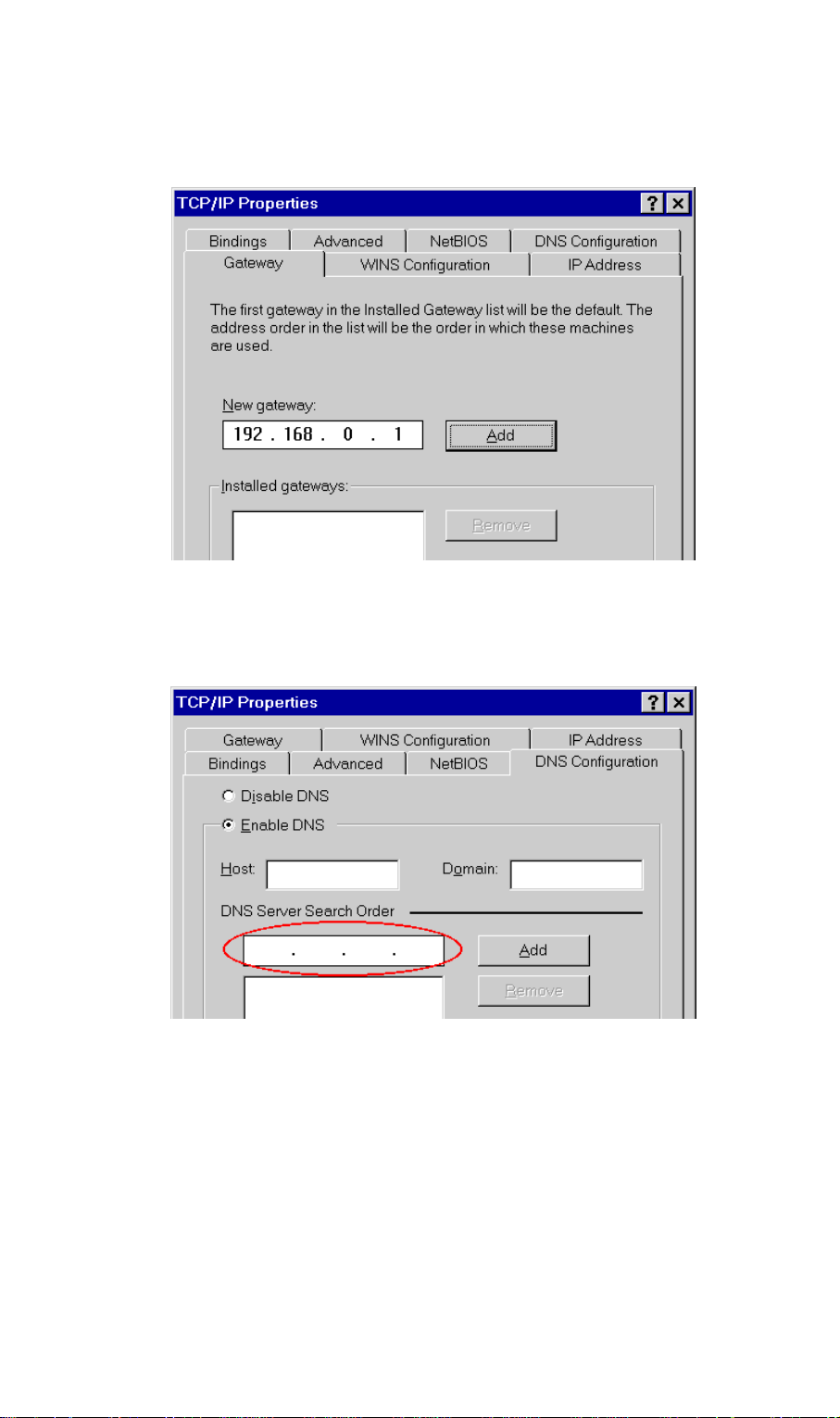
1. Select Control Panel - Network, and, on the Protocols tab, select the TCP/IP protocol, as
shown below.
Figure 14: Windows NT4.0 - TCP/IP
2. Click the Properties button to see a screen like the one below.
Figure 15: Windows NT4.0 - IP Address
3. Select the network card for your LAN.
22
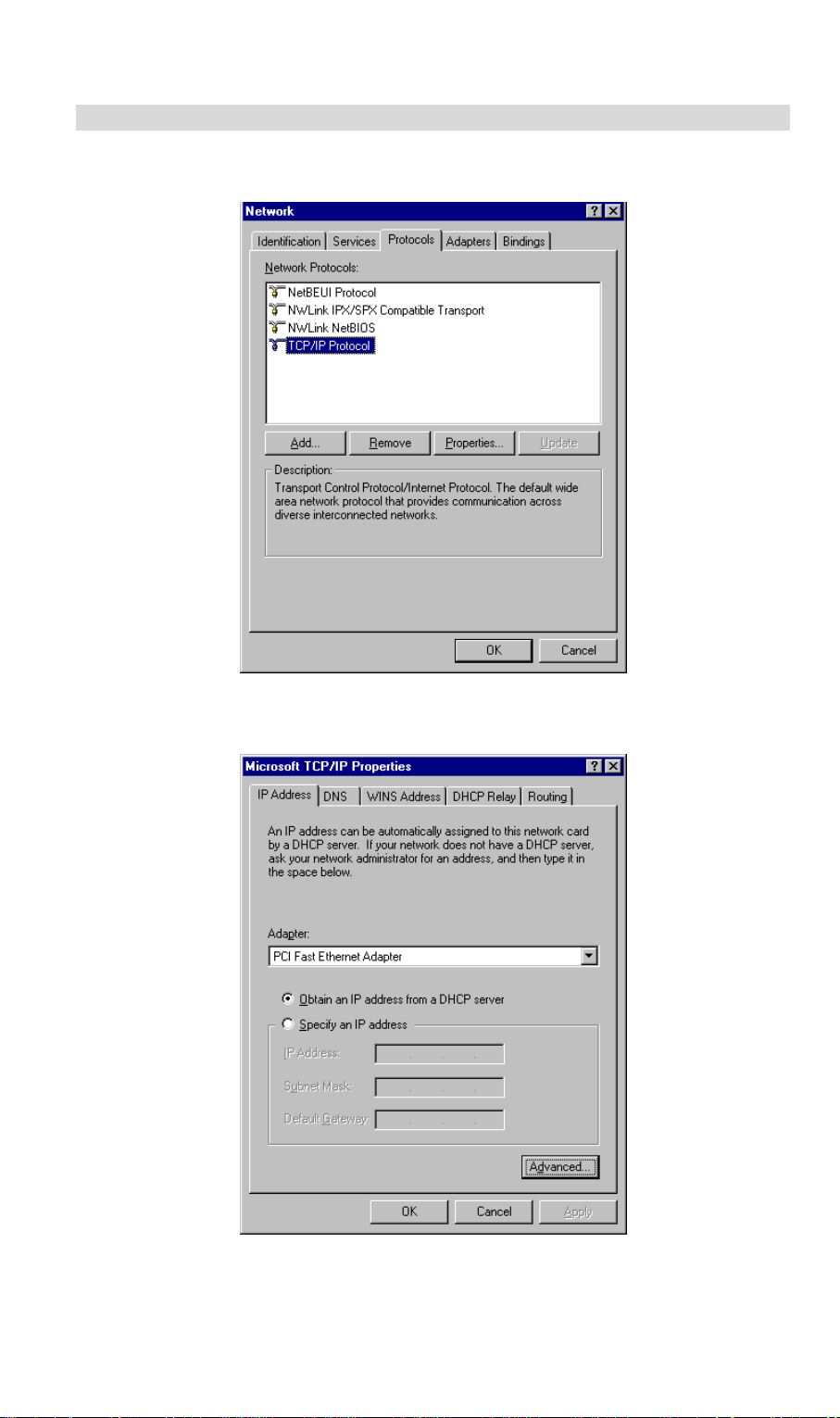
Page 27
PC Configuration
4. Select the appropriate radio button - Obtain an IP address from a DHCP Server or Specify
an IP Address, as explained below.
Obtain an IP address from a DHCP Server
This is the default Windows setting. Using this is recommended. By default, VRT-311 / VRT311S will act as a DHCP Server.
Restart your PC to ensure it obtains an IP Address from VRT-311 / VRT-311S.
Specify an IP Address
If your PC is already configured, check with your network administrator before making the
following changes.
1. The Default Gateway must be set to the IP address of VRT-311 / VRT-311S. To set this:
• Click the Advanced button on the screen above.
• On the following screen, click the Add button in the Gateways panel, and enter VRT-
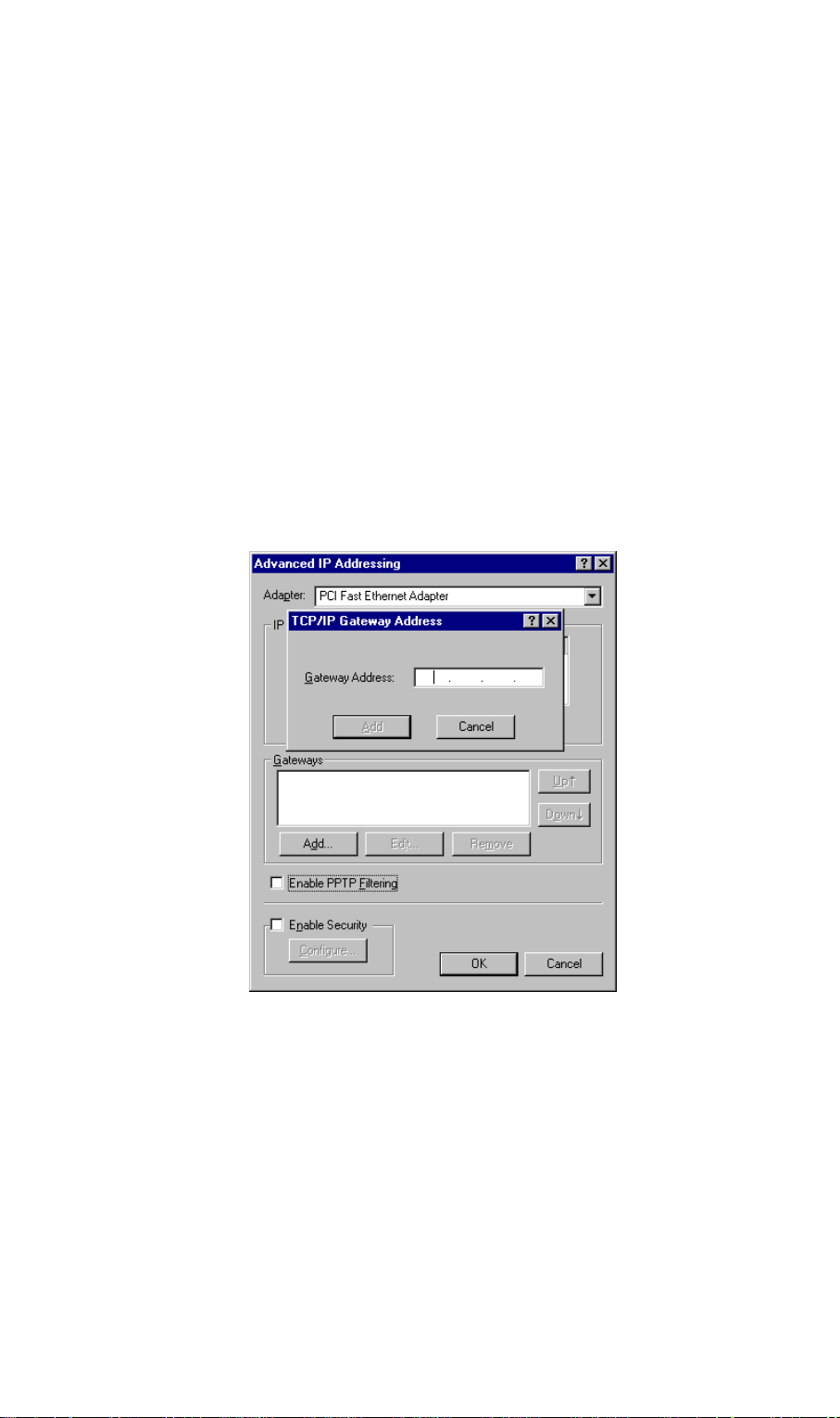
311 / VRT-311S 's IP address, as shown in Figure below.
• If necessary, use the Up button to make VRT-311 / VRT-311S the first entry in the
Gateways list.
Figure 16: Windows NT4.0 - Add Gateway
2. The DNS should be set to the address provided by your ISP, as follows:
• Click the DNS tab.
• On the DNS screen, shown below, click the Add button (under DNS Service Search
Order), and enter the DNS provided by your ISP.
23
Page 28

Broadband VPN Router User’s Manual
Figure17: Windows NT4.0 - DNS
24
Page 29
PC Configuration
Checking TCP/IP Settings - Windows 2000:
1. Select Control Panel - Network and Dial-up Connection.
2. Right - click the Local Area Connection icon and select Properties. You should see a
screen like the following:
Figure18: Network Configuration (Win 2000)
3. Select the TCP/IP protocol for your network card.
4. Click on the Properties button. You should then see a screen like the following.
Figure19: TCP/IP Properties (Win 2000)
25
Page 30

Broadband VPN Router User’s Manual
5. Ensure your TCP/IP settings are correct, as described below.
Using DHCP
To use DHCP, select the radio button Obtain an IP Address automatically. This is the default
Windows setting. Using this is recommended. By default, VRT-311 / VRT-311S will act as a
DHCP Server.
Restart your PC to ensure it obtains an IP Address from VRT-311 / VRT-311S.
Using a fixed IP Address ("Use the following IP Address")
If your PC is already configured, check with your network administrator before making the
following changes.
• Enter VRT-311 / VRT-311S 's IP address in the Default gateway field and click OK. (Your
LAN administrator can advise you of the IP Address they assigned to VRT-311 / VRT311S.)
• If the DNS Server fields are empty, select Use the following DNS server addresses, and
enter the DNS address or addresses provided by your ISP, then click OK.
26
Page 31

PC Configuration
Checking TCP/IP Settings - Windows XP
1. Select Control Panel - Network Connection.
2. Right click the Local Area Connection and choose Properties. You should see a screen
like the following:
Figure20: Network Configuration (Windows XP)
3. Select the TCP/IP protocol for your network card.
4. Click on the Properties button. You should then see a screen like the following.
27
Page 32

Broadband VPN Router User’s Manual
Figure21: TCP/IP Properties (Windows XP)
5. Ensure your TCP/IP settings are correct.
Using DHCP
To use DHCP, select the radio button Obtain an IP Address automatically. This is the default
Windows setting. Using this is recommended. By default, VRT-311 / VRT-311S will act as a
DHCP Server.
Restart your PC to ensure it obtains an IP Address from VRT-311 / VRT-311S.
Using a fixed IP Address ("Use the following IP Address")
If your PC is already configured, check with your network administrator before making the
following changes.
• In the Default gateway field, enter VRT-311 / VRT-311S 's IP address and click OK. Your
LAN administrator can advise you of the IP Address they assigned to VRT-311 / VRT311S.
• If the DNS Server fields are empty, select Use the following DNS server addresses, and
enter the DNS address or addresses provided by your ISP, then click OK.
28
Page 33

PC Configuration
Internet Access
To configure your PCs to use VRT-311 / VRT-311S for Internet access:
• Ensure that the DSL modem, Cable modem, or other permanent connection is functional.
• Use the following procedure to configure your Browser to access the Internet via the LAN,
rather than by a Dial-up connection.
For Windows 9x/ME/2000
1. Select Start Menu - Settings - Control Panel - Internet Options.
2. Select the Connection tab, and click the Setup button.
3. Select "I want to set up my Internet connection manually, or I want to connect through a
local area network (LAN)" and click Next.
4. Select "I connect through a local area network (LAN)" and click Next.
5. Ensure all of the boxes on the following Local area network Internet Configuration screen
are unchecked.
6. Check the "No" option when prompted "Do you want to set up an Internet mail account
now?".
7. Click Finish to close the Internet Connection Wizard.
Setup is now completed.
For Windows XP
1. Select Start Menu - Control Panel - Network and Internet Connections.
2. Select Set up or change your Internet Connection.
3. Select the Connection tab, and click the Setup button.
4. Cancel the pop-up "Location Information" screen.
5. Click Next on the "New Connection Wizard" screen.
6. Select "Connect to the Internet" and click Next.
7. Select "Set up my connection manually" and click Next.
8. Check "Connect using a broadband connection that is always on" and click Next.
9. Click Finish to close the New Connection Wizard.
Setup is now completed.
Accessing AOL
To access AOL (America On Line) through VRT-311 / VRT-311S, the AOL for Windows
software must be configured to use TCP/IP network access, rather than a dial-up connection.
The configuration process is as follows:
• Start the AOL for Windows communication software. Ensure that it is Version 2.5, 3.0 or
later. This procedure will not work with earlier versions.
• Click the Setup button.
• Select Create Location, and change the location name from "New Locality" to "VRT-311 /
VRT-311S ".
• Click Edit Location. Select TCP/IP for the Network field. (Leave the Phone Number blank.)
• Click Save, then OK.
Configuration is now complete.
• Before clicking "Sign On", always ensure that you are using the "VRT-311 / VRT-311S "
location.
29
Page 34

Broadband VPN Router User’s Manual
Macintosh Clients
From your Macintosh, you can access the Internet via VRT-311 / VRT-311S. The procedure is
as follows.
1. Open the TCP/IP Control Panel.
2. Select Ethernet from the Connect via pop-up menu.
3. Select Using DHCP Server from the Configure pop-up menu. The DHCP Client ID field
can be left blank.
4. Close the TCP/IP panel, saving your settings.
Note:
If using manually assigned IP addresses instead of DHCP, the required changes are:
• Set the Router Address field to VRT-311 / VRT-311S 's IP Address.
• Ensure your DNS settings are correct.
Linux Clients
To access the Internet via VRT-311 / VRT-311S, it is only necessary to set VRT-311 / VRT311S as the "Gateway".
Ensure you are logged in as "root" before attempting any changes.
Fixed IP Address
By default, most Unix installations use a fixed IP Address. If you wish to continue using a fixed
IP Address, make the following changes to your configuration.
• Set your "Default Gateway" to the IP Address of VRT-311 / VRT-311S.
• Ensure your DNS (Name server) settings are correct.
To act as a DHCP Client (recommended)
The procedure below may vary according to your version of Linux and X -windows shell.
1. Start your X Windows client.
2. Select Control Panel - Network
3. Select the "Interface" entry for your Network card. Normally, this will be called "eth0".
4. Click the Edit button, set the "protocol" to "DHCP", and save this data.
5. To apply your changes
• Use the "Deactivate" and "Activate" buttons, if available.
• OR, restart your system.
Other Unix Systems
To access the Internet via VRT-311 / VRT-311S:
• Ensure the "Gateway" field for your network card is set to the IP Address of VRT-311 /
VRT-311S.
• Ensure your DNS (Name Server) settings are correct.
30
Page 35

5
Chapter 5
Operation and Status
This Chapter details the operation of VRT-311 / VRT-311S and the status
screens.
Operation
Once both VRT-311 / VRT-311S and the PCs are configured, operation is automatic.
However, there are some situations where additional Internet configuration may be required:
• If using Internet-based Communication Applications, it may be necessary to specify which
PC receives an incoming connection. Refer to Chapter 6 - Internet Features for further details.
• Applications which use non-standard connections or port numbers may be blocked by
VRT-311 / VRT-311S 's built-in firewall. You can define such applications as Special Ap-
plications to allow them to function normally. Refer to Chapter 6 - Internet Features for
further details.
• Some non-standard applications may require use of the DMZ feature. Refer to Chapter 6 -
Internet Features for further details.
Status Screen
Use the Status link on the main menu to view this screen.
Figure 224: Status Screen
31
Page 36

Broadband VPN Router User’s Manual
Data - Status Screen
Internet
Connection Method
Broadband Modem
Internet Connection
Internet IP Address
"Connection Details"
Button
LAN
IP Address
Network Mask
DHCP Server
This indicates the current connection method, as set in the Setup
Wizard.
This shows the connection status of the modem.
Current connection status:
• Active
• Idle
• Unknown
• Failed
If there is an error, you can click the "Connection Details" button
to find out more information.
This IP Address is allocated by the ISP (Internet Service Provider).
Click this button to open a sub-window and view a detailed
description of the current connection. Depending on the type of
connection, a "log" may also be available.
The IP Address of VRT-311 / VRT-311S.
The Network Mask (Subnet Mask) for the IP Address above.
This shows the status of the DHCP Server function - either "En-
abled" or "Disabled".
System
Device Name
Firmware Version
"System Data"
Button
Buttons
Connection Details
System Data
Restart Router
Refresh Screen
For additional information about the PCs on your LAN, and the IP
addresses allocated to them, use the PC Database option on the
Other menu.
This displays the current name of VRT-311 / VRT-311S.
The current version of the firmware installed in VRT-311 / VRT-
311S.
Clicking this button will open a Window which lists all system
details and settings.
View the details of the current Internet connection. The subscreen displayed will depend on the connection method used. See
the following sections for details of each sub-screen.
Display all system information in a sub-window.
Restart (reboot) the Router. You will have to wait for the restart to
be completed before continuing.
Update the data displayed on screen.
32
Page 37

Operation and Status
• The "Clear Log" button wi
ll restart the Log, while the R
e-
Connection Status - PPPoE
If using PPPoE (PPP over Ethernet), a screen like the following example will be displayed
when the "Connection Details" button is clicked.
Data - PPPoE Screen
Connection
Physical Address
IP Address
Network Mask
PPPoE Link Status
Connection Log
Connection Log
Figure23: PPPoE Status Screen
The hardware address of this device, as seen by remote devices on
the Internet. (This is different to the hardware address seen by
devices on the local LAN.)
The IP Address of this device, as seen by Internet users. This
address is allocated by your ISP (Internet Service Provider).
The Network Mask associated with the IP Address above.
This indicates whether or not the connection is currently estab-
lished.
• If the connection does not exist, the "Connect" button can be
used to establish a connection.
• If the connection currently exists, the "Disconnect" button
can be used to break the connection.
• The Connection Log shows status messages relating to the
existing connection.
• The most common messages are listed in the table below.
33
Page 38

Broadband VPN Router User’s Manual
fresh button will update the messages shown on screen.
Buttons
Connect
Disconnect
Clear Log
If not connected, establish a connection to your ISP.
If connected to your ISP, hang up the connection.
Delete all data currently in the Log. This will make it easier to
read new messages.
Refresh
Update the data on screen.
Connection Log Messages
Message Description
Connect on Demand Connection attempt has been triggered by the "Connect auto-
matically, as required" setting.
Manual connection Connection attempt started by the "Connect" button.
Reset physical connection Preparing line for connection attempt.
Connecting to remote
server
Remote Server located ISP's Server has responded to connection attempt.
Start PPP Attempting to login to ISP's Server and establish a PPP con-
Attempting to connect to the ISP's server.
nection.
PPP up successfully Able to login to ISP's Server and establish a PPP connection.
Idle time-out reached The connection has been idle for the time period specified in
the "Idle Time-out" field. The connection will now be termi-
nated.
Disconnecting The current connection is being terminated, due to either the
"Idle Time-out" above, or "Disconnect" button being clicked.
Error: Remote Server not
found
Error: PPP Connection
failed
ISP's Server did not respond. This could be a Server problem,
or a problem with the link to the Server.
Unable to establish a PPP connection with the ISP's Server.
This could be a login problem (name or password) or a Server
problem.
Error: Connection to
Server lost
Error: Invalid or unknown
packet type
The existing connection has been lost. This could be caused by
a power failure, a link failure, or Server failure.
The data received from the ISP's Server could not be proc-
essed. This could be caused by data corruption (from a bad
link), or the Server using a protocol which is not supported by
this device.
34
Page 39

Operation and Status
Connection Status - PPTP
If using PPTP (Peer-to-Peer Tunneling Protocol), a screen like the following example will be
displayed when the "Connection Details" button is clicked.
Data - PPTP Screen
Connection
Physical Address
IP Address
PPTP Status
Connection Log
Connection Log
Figure24: PPTP Status Screen
The hardware address of this device, as seen by remote devices on the
Internet. (This is different to the hardware address seen by devices on
the local LAN.)
The IP Address of this device, as seen by Internet users. This address
is allocated by your ISP (Internet Service Provider).
This indicates whether or not the connection is currently established.
• If the connection does not exist, the "Connect" button can be
used to establish a connection.
• If the connection currently exists, the "Disconnect" button can be
used to break the connection.
• The Connection Log shows status messages relating to the
existing connection.
• The "Clear Log" button will restart the Log, while the Refresh
button will update the messages shown on screen.
Buttons
Connect
If not connected, establish a connection to your ISP.
35
Page 40

Broadband VPN Router User’s Manual
buttons unless the setting "Connect automatically, as re
quired"
Disconnect
Clear Log
Refresh
If connected to your ISP, hang up the connection.
Delete all data currently in the Log. This will make it easier to read
new messages.
Update the data on screen.
Connection Status - Telstra Big Pond
An example screen is shown below.
Figure25: Telstra Big Pond Status Screen
Data - Telstra Big Pond Screen
Connection
Physical Address
IP Address
Connection Status
The hardware address of this device, as seen by remote devices.
(This is different to the hardware address seen by devices on the
local LAN.)
The IP Address of this device, as seen by Internet users. This
address is allocated by your ISP (Internet Service Provider).
This indicates whether or not the connection is currently established.
• If the connection does not exist, the "Connect" button can be
used to establish a connection.
• If the connection currently exists, the "Disconnect" button can
be used to break the connection.
• Normally, it is not necessary to use the Connect and Disconnect
36
Page 41

Connection Log
Connection Log
Buttons
Operation and Status
is disabled.
• The Connection Log shows status messages relating to the
existing connection.
• The Clear Log button will restart the Log, while the Refresh
button will update the messages shown on screen.
Connect
Disconnect
Clear Log
Refresh
If not connected, establish a connection to Telstra Big Pond.
If connected to Telstra Big Pond, terminate the connection.
Delete all data currently in the Log. This will make it easier to read
new messages.
Update the data on screen.
Connection Details - SingTel RAS
If using the SingTel RAS access method, a screen like the following example will be displayed
when the "Connection Details" button is clicked.
Figure26: Connection Details - SingTel RAS
Data - SingTel RAS Screen
Internet
RAS Plan
Physical Address
The RAS Plan which is currently used.
The hardware address of this device, as seen by remote devices on the
Internet. (This is different to the hardware address seen by devices on
the local LAN.)
37
Page 42

Broadband VPN Router User’s Manual
IP Address
Network Mask
Default Gateway
DNS IP Address
DHCP Client
Buttons
Release/Renew
Button will display
EITHER
"Release"
OR
"Renew"
The IP Address of this device, as seen by Internet users. This address
is allocated by your ISP (Internet Service Provider).
The Network Mask associated with the IP Address above.
The IP Address of the remote Gateway or Router associated with the
IP Address above.
The IP Address of the Domain Name Server which is currently used.
This will show "Enabled" or "Disabled", depending on whether or not
this device is functioning as a DHCP client.
If "Enabled" the "Remaining lease time" field indicates when the IP
Address allocated by the DHCP Server will expire. The lease is
automatically renewed on expiry; use the "Renew" button if you wish
to manually renew the lease immediately.
This button is only useful if the IP address shown above is allocated
automatically on connection. (Dynamic IP address). If you have a
Fixed (Static) IP address, this button has no effect.
• If the ISP's DHCP Server has NOT allocated an IP Address for
VRT-311 / VRT-311S, this button will say "Renew". Clicking
the "Renew" button will attempt to re-establish the connection
and obtain an IP Address from the ISP's DHCP Server.
• If an IP Address has been allocated to VRT-311 / VRT-311S (by
the ISP's DHCP Server), this button will say "Release". Clicking
the "Release" button will break the connection and release the IP
Address.
Refresh
Update the data shown on screen.
38
Page 43

Operation and Status
"Release"
Connection Details - Fixed/Dynamic IP Address
If your access method is "Direct" (no login), a screen like the following example will be displayed when the "Connection Details" button is clicked.
Figure27: Connection Details - Fixed/Dynamic IP Address
Data - Fixed/Dynamic IP address Screen
Internet
Physical Address
IP Address
Network Mask
Default Gateway
DNS IP Address
DHCP Client
The hardware address of this device, as seen by remote devices on the
Internet. (This is different to the hardware address seen by devices on
the local LAN.)
The IP Address of this device, as seen by Internet users. This address
is allocated by your ISP (Internet Service Provider).
The Network Mask associated with the IP Address above.
The IP Address of the remote Gateway or Router associated with the
IP Address above.
The IP Address of the Domain Name Server which is currently used.
This will show "Enabled" or "Disabled", depending on whether or not
this device is functioning as a DHCP client.
If "Enabled" the "Remaining lease time" field indicates when the IP
Address allocated by the DHCP Server will expire. The lease is
automatically renewed on expiry; use the "Renew" button if you wish
to manually renew the lease immediately.
Buttons
Release/Renew
Button will display
EITHER
This button is only useful if the IP address shown above is allocated
automatically on connection. (Dynamic IP address). If you have a
Fixed (Static) IP address, this button has no effect.
• If the ISP's DHCP Server has NOT allocated an IP Address for
39
Page 44

Broadband VPN Router User’s Manual
OR
"Renew"
Refresh
VRT-311 / VRT-311S, this button will say "Renew". Clicking
the "Renew" button will attempt to re-establish the connection
and obtain an IP Address from the ISP's DHCP Server.
• If an IP Address has been allocated to VRT-311 / VRT-311S (by
the ISP's DHCP Server), this button will say "Release". Clicking
the "Release" button will break the connection and release the IP
Address.
Update the data shown on screen.
40
Page 45

6
Chapter 6
Internet Features
This Chapter explains when and how to use VRT-311 / VRT-311S's "Internet"
Features.
Overview
The following advanced features are provided.
• WAN Port Confuguration
• Advanced Internet
• Communication Applications
• Special Applications
• Multi-DMZ
• URL filter
• Dynamic DNS
• Virtual Servers
• Options
41
Page 46

Broadband VPN Router User’s Manual
WAN Port Configuration
The WAN Port Configuration screen provides an alternative to using the Wizard. It can be
accessed from the Internet menu. An example screen is shown below.
Figure28: WAN Port Configuration Screen
Data – WAN Port Configuration Screen
Identification
Hostname
Domain name
MAC Address
Normally, there is no need to change the default name, but if your ISP
requests that you use a particular “Hostname”, enter it here.
If your ISP provided a domain name, enter it here. Otherwise, this
may be left blank.
Also called Network Adapter Address or Physical Address. This is a
low-level identifier, as seen from the WAN port.
Normally there is no need to change this, but some ISPs require a
particular value, often that of the PC initially used for Internet access.
You can use the Copy from PC button to copy your PC's address into
this field, the Default button to insert the default value, or enter a
value directly.
42
Page 47

IP Address
Internet Features
IP Address
is assigned automatically
Also called Dynamic IP Address. This is the default, and the most
common.
Leave this selected if your ISP allocates an IP Address to VRT-311 /
VRT-311S upon connection.
Specified
IP Address
Also called Static IP Address. Select this if your ISP has allocated
you a fixed IP Address. If this option is selected, the following data
must be entered.
• IP Address.
The IP Address allocated by the ISP.
• Network Mask (Not required for PPPoE)
This is also supplied by your ISP. It must be compatible with the
IP Address above.
• Gateway IP Address (Not required for PPPoE)
The address of the router or gateway, as supplied by your ISP.
NAT
Enable NAT
NAT (Network Address Translation) is the technology which allows
all PCs on your LAN to share the Internet IP address allocated to the
WAN port on this Router. From the Internet, all PCs appear to have
the same IP address.
For normal operation, this setting must be ENABLED.
Disable NAT Disabling NAT will disable Internet access, unless all PCs have
valid Internet IP addresses.
DNS
Automatically
obtain from
Server
Use this DNS
If you wish to use this device for Routing ONLY (and NOT for
Internet access), then NAT should be disabled.
The DNS (Domain Name Server) address will be obtained automatically from your ISP's server. Note that if using a fixed IP address,
with no login (login is set to "None"), then no Server is used, and this
option cannot be used.
If this option is selected, you must enter the IP address of the DNS
(Domain Name Server) you wish to use.
Note: If the DNS is unavailable, the "Backup DNS", entered on the
Internet - Options screen, will be used.
43
Page 48

Broadband VPN Router User’s Manual
Login
Login Method
Login User Name
Login Password
RAS Plan
Server Address
Connection
behavior
If your ISP does not use a login method (username, password) for
Internet access, leave this at the default value "None (Direct connection)"
Otherwise, check the documentation from your ISP, select the login
method used, and enter the required data.
• PPPoE - this is the most common login method, widely used
with DSL modems. Normally, your ISP will have provided some
software to connect and login. This software is no longer required, and should not be used.
• PPTP - this is mainly used in Europe. You need to know the
PPTP Server address as well as your name and password.
• Big Pond Cable - for Australia only.
• SingTel RAS - for Singapore only.
The User Name (or account name) provided by your ISP.
Enter the password for the login name above.
For SingTel customers only, select the RAS plan you are on.
If using PPTP or Big Pond Cable, enter the address of your ISP's
server.
For PPPoE or SingTel RAS, the Server address in not required.
Select the desired option:
• Automatic Connect/Disconnect
An Internet connection is automatically made when required, and
disconnected when idle for the time period specified by the
"Auto-disconnect Idle Time-out".
• Manual Connect/Disconnect
You must manually establish and terminate the connection.
• Keep alive (maintain connection)
The connection will never be disconnected by this device. If disconnected by your ISP, the connection will be re-established
immediately. (However, this does not ensure that your Internet IP
address will remain unchanged.)
Auto-disconnect
Idle Time-out
This field has no effect unless the setting above is Automatic Connect/Disconnect.
If Auto-disconnect is being used, enter the desired idle time-out
period (in minutes). After the connection to your ISP has been idle for
this time period, the connection will be terminated.
44
Page 49

Advanced Internet
Internet Features
Figure29: Internet Screen
This screen allows configuration of all advanced features relating to Internet access.
• Communication Applications
• Special Applications
• Multi-DMZ
• URL filter
Communication Applications
Most applications are supported transparently by VRT-311 / VRT-311S. But sometimes it is
not clear which PC should receive an incoming connection. This problem could arise with the
Communication Applications listed on this screen.
If this problem arises, you can use this screen to set which PC should receive an incoming
connection, as described below.
Communication Applications
Select an Application
This lists applications which may generate incoming connections,
where the destination PC (on your local LAN) is unknown.
45
Page 50

Broadband VPN Router User’s Manual
Send incoming calls to
This lists the PCs on your LAN.
• If necessary, you can add PCs manually, using the PC Data-
base option on the Other menu.
• For each application listed above, you can choose a destina-
tion PC.
• There is no need to "Save" after each change; you can set the
destination PC for each application, then click "Save".
Special Applications
If you use Internet applications which use non-standard connections or port numbers, you may
find that they do not function correctly because they are blocked by VRT-311 / VRT-311S 's
firewall. In this case, you can define the application as a "Special Application".
Special Applications Screen
This screen can be reached by clicking the Special Applications button on the Advanced Internet screen.
You can then define your Special Applications. You will need detailed information about the
application; this is normally available from the supplier of the application.
Also, note that the terms "Incoming" and "Outgoing" on this screen refer to traffic from the
client (PC) viewpoint
Figure30: Special Applications Screen
Data - Special Applications Screen
Checkbox
Name
Use this to Enable or Disable this Special Application as required.
Enter a descriptive name to identify this Special Application.
46
Page 51

Internet Features
Incoming
Ports
Outgoing
Ports
• Type - Select the protocol (TCP or UDP) used when you receive data
from the special application or service. (Note: Some applications use
different protocols for outgoing and incoming data).
• Start - Enter the beginning of the range of port numbers used by the
application server, for data you receive. If the application uses a single
port number, enter it in both the "Start" and "Finish" fields.
• Finish - Enter the end of the range of port numbers used by the applica-
tion server, for data you receive.
• Type - Select the protocol (TCP or UDP) used when you send data to
the remote system or service.
• Start - Enter the beginning of the range of port numbers used by the
application server, for data you send to it. If the application uses a single
port number, enter it in both the "Start" and "Finish" fields.
• Finish - Enter the end of the range of port numbers used by the applica-
tion server, for data you send to it. If the application uses a single port
number, enter it in both the "Start" and "Finish" fields.
Using a Special Application
• Configure the Special Applications screen as required.
• On your PC, use the application normally. Remember that only one (1) PC can use each
Special application at any time. Also, when 1 PC is finished using a particular Special Application, there may need to be a "Time-out" before another PC can use the same Special
Application. The "Time-out" period may be up to 3 minutes.
If an application still cannot function correctly,
try using the "DMZ" feature.
Multi-DMZ
This feature, if enabled, allows one (1) or more computers on your LAN to be exposed to all
users on the Internet. You can set a DMZ PC for each WAN IP address. If you only have 1
WAN IP addresses, only 1 DMZ PC can be used.
This allows unrestricted 2-way communication between the "DMZ PC" and other Internet users
or Servers.
• This allows almost any application to be used on the "DMZ PC".
• The "DMZ PC" will receive all "Unknown" connections and data.
• If the DMZ feature is enabled, you must select the PC to be used as the "DMZ PC".
• To use more than one (1) DMZ, your ISP must assign multiple fixed IP addresses to you.
You must enter each IP address; you can then assign a DMZ PC for each IP address.
The "DMZ PC" is effectively outside the Firewall, making it more vulnerable to attacks. For this reason, you
should only enable the DMZ feature when required.
47
Page 52

Broadband VPN Router User’s Manual
URL Filter
The URL Filter allows you to block access to undesirable Web site
• To use this feature, you must define "filter strings". If the "filter string" appears in a re-
quested URL, the request is blocked.
• Enabling the URL Filter also affects the Internet Access Log. If Enabled, the "Destination"
field in the log will display the URL. Otherwise, it will display the IP Address.
• The URL Filter can be Enabled or Disabled on the Advanced Internet screen.
URL Filter Screen
Click the "Configure URL Filter" button on the Advanced Internet screen to access the URL
Filter screen. An example screen is shown below.
Data - URL Filter Screen
Filter Strings
Current Entries
Add Filter String
Buttons
Delete/Delete All
Add
This lists any existing entries. If you have not entered any values, this
list will be empty.
To add an entry to the list, enter it here, and click the "Add" button.
An entry may be a Domain name (e.g. www.trash.com) or simply a
string. (e.g. ads/ )
Any URL which contains ANY entry ANYWHERE in the URL will be
blocked.
Use these buttons to delete the selected entry or all entries, as required.
Multiple entries can be selected by holding down the CTRL key while
selecting. (On the Macintosh, hold the SHIFT key while selecting.)
Use this to add the current Filter String to the site list.
Figure31: URL Filter Screen
48
Page 53

Internet Features
Address is recorded by the DDNS Service Provider. (You do
Dynamic DNS (Domain Name Server)
This free service is very useful when combined with the Virtual Server feature. It allows Internet users to connect to your Virtual Servers using a URL, rather than an IP Address.
This also solves the problem of having a dynamic IP address. With a dynamic IP address, your
IP address may change whenever you connect, which makes it difficult to connect to you.
The Service works as follows:
1. You must register for the service at one of the listed DDNS Service providers.
2. After registration, follow the Service Provider's procedure to request a Domain Name, and
have it allocated to you.
3. Enter your DDNS data on VRT-311 / VRT-311S 's DDNS screen (shown below).
4. VRT-311 / VRT-311S will then automatically ensure that your current IP Address is
recorded and updated at the DDNS server.
If the DDNS Service provides software to perform this "IP address update"; you should
disable the "Update" function, or not use the software at all.
5. From the Internet, users will be able to connect to your Virtual Servers (or DMZ PC) using
your Domain name, as shown on this screen.
Dynamic DNS Screen
Select Internet on the main menu, then Dynamic DNS, to see a screen like the following:
Figure32: DDNS Screen
Data - Dynamic DNS Screen
DDNS Service
DDNS Service
• You must register for the service at one of the listed Service
Providers. You can reach the Service provider's Web Site by selecting them in the list and clicking the "Web Site" button.
• Apply for a Domain Name, and ensure it is allocated to you.
• Details of your DDNS account (Name, password, Domain name)
must then be entered and saved on this screen.
• This device will then automatically ensure that your current IP
49
Page 54

Broadband VPN Router User’s Manual
NOT need to use the "Client" program provided by some DDNS
Service providers.)
• From the Internet, users will now be able to connect to your
Virtual Servers (or DMZ PC) using your Domain name.
DDNS Data
DDNS Service
User Name
Password/Key
Domain Name
DDNS Status
Select the desired DDNS Service provider.
Enter your Username for the DDNS Service.
Enter your current password for the DDNS Service.
Enter the domain name allocated to you by the DDNS Service. If you
have more than one name, enter the name you wish to use.
• This message is returned by the DDNS Server
• Normally, this message should be something like "Update suc-
cessful" or "IP address updated".
• If the message indicates some problem, you need to connect to
the DDNS Service provider and correct this problem.
50
Page 55

Internet Features
Virtual Servers
This feature allows you to make Servers on your LAN accessible to Internet users. Normally,
Internet users would not be able to access a server on your LAN because:
• Your Server does not have a valid external IP Address.
• Attempts to connect to devices on your LAN are blocked by the firewall in this device.
The "Virtual Server" feature solves these problems and allows Internet users to connect to your
servers, as illustrated below.
Figure33: Virtual Servers
IP Address seen by Internet Users
Note that, in this illustration, both Internet users are connecting to the same IP Address, but
using different protocols.
To Internet users, all virtual Servers on your LAN have the same IP Address.
This IP Address is allocated by your ISP.
This address should be static, rather than dynamic, to make it easier for Internet users to connect to your Servers.
However, you can use the DDNS (Dynamic DNS) feature to allow users to connect to your
Virtual Servers using a URL, instead of an IP Address.
Using the DMZ port for Virtual Servers
You should connect your Virtual Servers to the DMZ port, for the following reasons:
• Traffic passing between the DMZ and LAN passes through the firewall. The firewall will
protect your LAN if your Server is compromised and used to launch an attack on your
LAN.
51
Page 56

Broadband VPN Router User’s Manual
• For each enabled Virtual Server, a firewall rule to allow incoming traffic from the Internet
(WAN) to the DMZ is automatically created. If the Server is connected to the LAN (hub)
ports, you must add the firewall rule manually.
Note that the DMZ port is a normal port, not an "uplink" port. If connecting to a hub, connect
to the standard port on the hub.
Virtual Servers Screen
The Virtual Servers screen is reached by the Virtual Servers link on the Internet menu. An
example screen is shown below.
Figure34: Virtual Servers Screen
This screen lists a number of pre-defined Servers, providing a quick and convenient method to
set up the common server types.
Data - Virtual Servers Screen
Servers
Servers
Properties
Enable
PC (Server)
This lists a number of pre-defined Servers, plus any Servers you
have defined. Details of the selected Server are shown in the "Properties" area.
Use this to Enable or Disable support for this Server, as required.
• If Enabled, any incoming connections will be forwarded to the
selected PC.
• If Disabled, any incoming connection attempts will be blocked.
Select the PC for this Server. The PC must be running the appropri-
ate Server software.
Defining your own Virtual Servers
If the type of Server you wish to use is not listed on the Virtual Servers screen, you can use the
Firewall Rules to allow particular incoming traffic and forward it to a specified PC (Server).
52
Page 57

Internet Features
Connecting to the Virtual Servers
Once configured, anyone on the Internet can connect to your Virtual Servers. They must use the
Internet IP Address (the IP Address allocated to you by your ISP).
e.g.
http://203.70.212.52
ftp://203.70.212.52
It is more convenient if you are using a Fixed IP Address from your ISP, rather than Dynamic.
However, you can use the Dynamic DNS feature, described in the following section, to allow
users to connect to your Virtual Servers using a URL, rather than an IP Address.
Options
This screen allows advanced users to enter or change a number of settings. For normal operation, there is no need to use this screen or change any settings.
Data - Options Screen
Backup DNS
IP Address
MTU
MTU size
Enter the IP Address of the DNS (Domain Name Servers) here. These
DNS will be used only if the primary DNS is unavailable.
MTU (Maximum Transmission Unit) value should only be changed if
advised to do so by Technical Support.
• Enter a value between 1 and 1500.
• This device will still auto-negotiate with the remote server, to set
the MTU size. The smaller of the 2 values (auto-negotiated, or entered here) will be used.
• For direct connections (not PPPoE or PPTP), the MTU used is
always 1500.
Figure35: Options Screen
53
Page 58

7
Chapter 7
Security Configuration
This Chapter explains the settings available via the security configuration
section of the "Security" menu.
Overview
The following advanced configurations are provided.
• Admin Login
• Access Control
• Firewall Rules
• Logs
• E-mail
• Security Options
• Scheduling
• Services
Admin Login
The Admin Login screen allows you to assign a user name and password to VRT-311 / VRT311S .
Figure36: Admin Login Screen
1. The default login name is "admin". Change this to the desired value.
2. The default password is blank (no password). Enter the desired password in the New
Password and Verify Password fields.
3. Save your changes.
You will see a login prompt when you connect to VRT-311 / VRT-311S, as shown below.
54
Page 59

Security Configuration
Figure37: Password Dialog
Enter the "User Name" and "Password" you set on the Admin Login screen above.
55
Page 60

Broadband VPN Router User’s Manual
Access Control
This feature is accessed by the Access Control link on the Security menu.
The Access Control feature allows administrators to restrict the level of Internet Access avail-
able to PCs on your LAN. With the default settings, everyone has unrestricted Internet access.
To use this feature:
1. Set the desired restrictions on the "Default" group. All PCs are in the "Default" group
unless explicitly moved to another group.
2. Set the desired restrictions on the other groups ("Group 1", "Group 2", "Group 3" and
"Group 4") as needed.
3. Assign PC to the groups as required.
Restrictions are imposed by blocking "Services", or types of
connections. All common Services are pre-defined.
If required, you can also define your own Services.
Access Control Screen
To view this screen, select the Access Control link on the Security menu.
Figure38: Access Control Screen
56
Page 61

Data - Access Control Screen
Group
Security Configuration
Group
"Members" Button
Internet Access
Restrictions
Select the desired Group. The screen will update to display the
settings for the selected Group. Groups are named "Default",
"Group 1", "Group 2", "Group 3" and "Group 4", and cannot be renamed.
Click this button to add or remove members from the current
Group.
• If the current group is "Default", then members can not be
added or deleted. This group contains PCs not allocated to any
other group.
• To remove PCs from the Default Group, assign them to another
Group.
• To assign PCs to the Default Group, delete them from the
Group they are currently in.
See the following section for details of the Group Members screen.
Select the desired options for the current group:
• None - Nothing is blocked. Use this to create the least restric-
tive group.
• Block all Internet access - All traffic via the WAN port is
blocked. Use this to create the most restrictive group.
• Block selected Services - You can select which Services are to
block. Use this to gain fine control over the Internet access for
a group.
Block by Schedule
Services
Buttons
Members
Save
Cancel
View Log
If Internet access is being blocked, you can choose to apply the
blocking only during scheduled times. (If access is not blocked, no
Scheduling is possible, and this setting has no effect.)
To define the schedule, use the Schedule option on the menu.
This lists all defined Services. Select the Services you wish to
block. To select multiple services, hold the CTRL key while selecting. (On the Macintosh, hold the SHIFT key rather than CTRL.)
Click this button to add or remove members from the current
Group.
If the current group is "Default", then members can not be added or
deleted. This group contains PCs not allocated to any other group.
See the following section for details of the Group Members screen.
Save the data on screen.
Reverse any changes made since the last "Save".
Click this to open a sub-window where you can view the "Access
Control" log. This log shows attempted Internet accesses which
have been blocked by the Access Control feature.
57
Page 62

Broadband VPN Router User’s Manual
Clear Log
Click this to clear and restart the "Access Control" log, making new
entries easier to read.
58
Page 63

Security Configuration
Group Members Screen
This screen is displayed when the Members button on the Access Control screen is clicked.
Figure39: Group Members
Use this screen to add or remove members (PCs) from the current group.
• The "Del >>" button will remove the selected PC (in the Members list) from the current
group.
• The "<< Add" button will add the selected PC (in the Other PCs list) to the current group.
PCs not assigned to any group will be in the
"Default" group.
PCs deleted from any other Group will be added
to the "Default" group.
Access Control Log
To check the operation of the Access Control feature, an Access Control Log is provided. Click
the View Log button on the Access Control screen to view this log.
This log shows attempted Internet accesses which have been blocked by the Access Control
function.
Data shown in this log is as follows:
Date/Time
Name
Source IP address
MAC address
Date and Time of the attempted access.
If known, the name of the PC whose access was blocked. This name
is taken from the Network Clients database
The IP Address of the PC or device whose access request was
blocked
The hardware or physical address of the PC or device whose access
request was blocked
Destination
The destination URL or IP address
59
Page 64

Broadband VPN Router User’s Manual
Firewall Rules
For normal operation and LAN protection, it is not necessary to use this screen.
The Firewall will always block DoS (Denial of Service) attacks. A DoS attack does not attempt
to steal data or damage your PCs, but overloads your Internet connection so you can not use it the service is unavailable.
As well, you can use this screen to create Firewall rules to block or allow specific traffic. But
incorrect configuration may cause serious problems.
This feature is for advanced administrators only!
Firewall Rules Screen
Click the Firewall Rules option on the Security menu to see a screen like the following example.
This example contains two (2) rules for outgoing traffic.
Since the default rule for outgoing (LAN => WAN) traffic is "Allow",
having an "Allow" rule for LAN => WAN only makes sense in
combination with another rule.
For example, the screen below shows a rule blocking all traffic to
a MSN Game Server, followed by another rule allowing access by
a specific PC.
Figure40: Firewall Rules Screen
Data - Firewall Rules Screen
Rule List
View Rules for ..
Select the desired option; the screen will update and list any current
rules. If you have not defined any rules, the list will be empty.
60
Page 65

Security Configuration
Data
Add
Edit
Move
Delete
For each rule, the following data is shown:
• Name - The name you assigned to the rule.
• Source - The traffic covered by this rule, defined by the source IP
address. If the IP address is followed by ... this indicates there is
range of IP addresses, rather than a single address.
• Destination - The traffic covered by this rule, defined by destina-
tion IP address. If the IP address is followed by ... this indicates
there is range of IP addresses, rather than a single address.
• Action - Action will be "Forward" or "Block"
To add a new rule, click the "Add" button, and complete the resulting
screen. See the following section for more details.
To Edit or modify an existing rule, select it and click the "Edit" button.
There are 2 ways to change the order of rules
• Use the up and down indicators on the right to move the selected
rule. You must confirm your changes by clicking "OK". If you
change your mind before clicking "OK", click "Cancel" to reverse
your changes.
• Click "Move" to directly specify a new location for the selected
rule.
To delete an existing rule, select it and click the "Delete" button.
View Log
System Rules
Clicking the "View Log" button will open a new window and display
the Firewall log.
Clicking the "System Rules" button will open a new window and
display the default firewall rules currently applied by the system. These
rules cannot be edited, but any rules you create will take precedence
over the default rules.
61
Page 66

Broadband VPN Router User’s Manual
Define Firewall Rule
Clicking the "Add" button in the Firewall Rules screen will display a screen like the example
below.
Figure41: Define Firewall Rule
Data - Define Firewall Rule Screen
Name
Type
Source IP
Enter a suitable name for this rule.
This determines the source and destination ports for traffic cov-
ered by this rule. Select the desired option.
These settings determine which traffic, based on their source IP
address, is covered by this rule.
Select the desired option:
• Any - All traffic from the source port is covered by this rule.
• Single address - Enter the required IP address in the "Start IP
address" field". You can ignore the "Subnet Mask" field.
• Range address - If this option is selected, you must complete
both the "Start IP address" and "Finish IP address" fields.
You can ignore the "Subnet Mask" field.
• Subnet address - If this option is selected, enter the required
mask in the "Subnet Mask" field.
62
Page 67

Security Configuration
Dest IP
Services
Action
Log
These settings determine which traffic, based on their destination
IP address, is covered by this rule.
Select the desired option:
• Any - All traffic from the source port is covered by this rule.
• Single address - Enter the required IP address in the "Start IP
address" field". You can ignore the "Subnet Mask" field.
• Range address - If this option is selected, you must complete
both the "Start IP address" and "Finish IP address" fields.
You can ignore the "Subnet Mask" field.
• Subnet address - If this option is selected, enter the required
mask in the "Subnet Mask" field.
Select the desired Service or Services. This determines which
packets are covered by this rule, based on the protocol (TPC or
UDP) and port number. If necessary, you can define a new Service on the "Services" screen, by defining the protocols and port
numbers used by the Service.
Select the desired action for packets covered by this rule:
This determines whether packets covered by this rule are logged.
Select the desired option.
63
Page 68

Broadband VPN Router User’s Manual
Logs
The Logs record various types of activity on VRT-311 / VRT-311S. This data is useful for
troubleshooting, but enabling all logs will generate a large amount of data and adversely affect
performance.
Since only a limited amount of log data can be stored in VRT-311 / VRT-311S, log data can
also be E-mailed to your PC or sent to a Syslog Server.
Figure42: Logs Screen
64
Page 69

Data - Logs Screen
Enable Logs
Security Configuration
Incoming Traffic
Outgoing Traffic
Select the desired option:
• All IP traffic - this will log all incoming TCP/IP connections, of
any type. This will generate the largest logs, and fill the internal
log buffer more quickly.
• All TCP/UDP/ICMP traffic - These 3 protocols are used by most
internet traffic. TCP is used by HTTP, FTP, Telnet, E-mail and
other common Internet protocols and applications. UDP is used by
Video streams and other communications where speed is more important than guaranteed delivery. ICMP is used by the "ping" and
"trace route" applications, and other network diagnostics.
Select the desired option:
• All IP traffic - - this will log all outgoing TCP/IP connections, of
any type. This will generate the largest logs, and fill the internal
log buffer more quickly.
• All TCP/UDP/ICMP traffic - These 3 protocols are used by most
internet traffic. TCP is used by HTTP, FTP, Telnet, E-mail and
other common Internet protocols and applications. UDP is used by
Video streams and other communications where speed is more important than guaranteed delivery. ICMP is used by the "ping" and
"trace route" applications, and other network diagnostics.
Because most connections are logged, the logs will still be large.
• Selected Traffic only - This selection will reduce the size of the
log considerably. Only HTTP connections are logged. Select the
traffic you wish to include:
• Attempted access to blocked sites - This will only log Web
connections which are blocked by the URL filter.
• Websites and news groups - This logs successful (allowed)
connections to Web Sites and newsgroup servers.
System Log
VPN
View Log Button
Select the desired option:
• Router operations (start up, get time etc) - This option will log
normal Router operations.
• Connections to the Web - based interface of this Router - This
option will log each connection to the Router itself, whenever the
Web-based management interface is used.
• Other connections and traffic to this Router - This option will
log other traffic sent to the Router itself, such as "pings" or RIP
(Router Information Protocol) packets.
• Known DoS attacks and Port Scans - This will log details of
DoS (Denial of Service) attacks which have been blocked by the
built-in Firewall. This Firewall uses "Stateful Inspection" technology to block packets which are individually valid, but collectively
form an attack. Port scans, where a series of ports are checked to
see if they are open (available) are also logged.
If enabled, the VPN log will record incoming and outgoing VPN
connections.
Use this to view each log, as required.
65
Page 70

Broadband VPN Router User’s Manual
Clear Log
Button
Timezone
Timezone
Syslog Server
Enable Syslog
Syslog Server
Include
Use this to restart the required log. This makes it easier to read the
latest entries.
Select the correct Timezone for your location. This is required for the
date/time shown on the logs to be correct.
If enabled, log data will be sent to your Syslog Server.
Enter the IP address of your Syslog Server.
Select the logs you wish to be included in the data sent to the Syslog
Server.
66
Page 71

Security Configuration
Data – E-Mail Screen
E-Mail Alerts
Send E-Mail alert
E-Mail Logs
Send Logs by E-Mail
Include
Send
Figure43: E-Mail Screen
If enabled, an E-mail will be sent immediately if a DoS (Denial of
Service) attack is detected. If enabled, the E-mail address
information must be provided.
If enabled, logs will be logs to the specified E-mail address. You
need to select the Logs to be E-mailed, and complete the E-mail
address settings on this screen.
Select the log items to be included in the E-mail.
Select the desired option for sending the log by E-mail.
• When log is full - The time is not fixed. The log will be sent
when the log is full, which will depend on the volume of traffic.
• Every day, Every Monday... - The log is sent on the interval
specified.
• If "Every day" is selected, the log is sent at the time
specified.
• If the day is specified, the log is sent once per week, on
the specified day.
• Select the time of day you wish the E-mail to be sent.
• If the log is full before the time specified to send it, it
will be sent regardless.
67
Page 72

Broadband VPN Router User’s Manual
E-mail address
Subject
SMTP Server
Port No.
Enter the E-mail address the Log is to be sent to. The E-mail will
also show this address as the Sender's address.
Enter the text string to be shown in the "Subject" field for the Email.
Enter the address or address or IP address of the SMTP (Simple
Mail Transport Protocol) Server you use for outgoing E-mail.
Enter the port number used to connect to the SMTP Server. The
default value is 25.
68
Page 73

Security Options
This screen allows you to set Firewall and other security-related options.
Figure44: Security Options Screen
Security Configuration
Data - Security Options Screen
Firewall
Enable DoS
Firewall
Threshold
If enabled, DoS (Denial of Service) attacks will be detected and
blocked. The default is enabled. It is strongly recommended that this
setting be left enabled.
Note:
• A DoS attack does not attempt to steal data or damage your PCs,
but overloads your Internet connection so you can not use it - the
service is unavailable.
• This device uses "Stateful Inspection" technology. This system can
detect situations where individual TCP/IP packets are valid, but
collectively they become a DoS attack.
This setting affects the number of "half-open" connections allowed.
• A "half-open" connection arises when a remote client contacts the
Server with a connection request, but then does not reply to the
Server's response.
• While the optimum number of "half-open" connections allowed
(the "Threshold") depends on many factors, the most important
factor is the available bandwidth of your Internet connection.
• Select the setting to match the bandwidth of your Internet connec-
tion.
69
Page 74

Broadband VPN Router User’s Manual
Options
Respond to ICMP
(ping)
Allow VPN passthrough
Drop fragmented
IP packets
The ICMP protocol is used by the "ping" and "trace route" programs,
and by network monitoring and diagnostic programs.
• If checked, VRT-311 / VRT-311S will respond to ICMP packets
received from the Internet.
• If not checked, ICMP packets from the Internet will be ignored.
Disabling this option provides a slight increase in security.
If enabled, PCs on the LAN can use VPN software to connect to
remote clients via the Internet connection. The protocols supported
are:
• IPSec
IPSec protocol is used to establish a secure connection, and is
widely used by VPN (Virtual Private Networking) programs.
• PPTP
PPTP (Point to Point Tunneling Protocol) is widely used by VPN
(Virtual Private Networking) programs.
• L2TP
L2TP is a protocol developed by Cisco for VPNs (Virtual Private
Networks).
If enabled, fragmented IP packets are discarded, forcing retransmission of these packets. In some situations, this could prevent
successful communication.
Normally, this setting should be disabled.
Block TCP Flood
Block UDP Flood
Block nonstandard packets
A TCP flood is excessively large number of TCP connection requests.
This is usually a DoS (Denial of Service) attack.
This setting should normally be enabled.
A UDP flood is excessively large number of UDP packets. This is
usually a DoS (Denial of Service) attack.
This setting should normally be enabled.
Abnormal packets are often used by hackers and in DoS attacks, but
may also be generated by mis-configured network devices. (PCs will
normally not generate non-standard packets.)
This setting should normally be enabled.
70
Page 75

Security Configuration
Scheduling
• This schedule can be (optionally) applied to any Access Control Group.
• Blocking will be performed during the scheduled time (between the "Start" and "Finish"
times.)
• Two (2) separate sessions or periods can be defined.
• Times must be entered using a 24 hr clock.
• If the time for a particular day is blank, no action will be performed.
Define Schedule Screen
This screen is accessed by the Scheduling link on the Security menu.
Figure45: Define Schedule Screen
Data - Define Schedule Screen
Day
Session 1
Session 2
Start Time
Finish Time
Each day of the week can scheduled independently.
Two (2) separate sessions or periods can be defined. Session 2 can be
left blank if not required.
Enter the start using a 24 hr clock.
Enter the finish time using a 24 hr clock.
71
Page 76

Broadband VPN Router User’s Manual
Services
Services are used in defining traffic to be blocked or allowed by the Access Control or Firewall
Rules features. Many common Services are pre-defined, but you can also define your own
services if required.
To view the Services screen, select the Services link on the Security menu.
Data - Services Screen
Available Services
Available Services
Delete Button
Add New Service
Name
Type
Start Port
Finish Port
This lists all defined Services.
Use this to delete the selected Service from the list.
Note that you can only delete Services you have added; the pre-
defined services can not be deleted.
Enter a suitable name for this Service.
Select the correct type for this Service.
If the "Type" (above) is TCP, UDP, or TCP/UDP, enter the port
number for this Service. If a port range is required, enter the beginning of the range here, and the end of the range in the "Finish Port"
field.
If the "Type" (above) is TCP, UDP, or TCP/UDP, this field can be
used to enter the end of range of port numbers. This can be left blank
if not required.
Figure46: Services Screen
ICMP Type
If the "Type" (above) is ICMP, enter the ICMP type here. Otherwise,
this field should be left blank.
72
Page 77

8
Chapter 8
VPN (IPSec)
This Chapter describes the VPN capabilities and configuration required for
common situations.
Overview
This section describes the VPN (Virtual Private Network) support provided by your VRT-311 /
VRT-311S.
A VPN (Virtual Private Network) provides a secure connection between 2 points, over an
insecure network - typically the Internet. This secure connection is called a VPN Tunnel.
There are many standards and protocols for VPNs. The standard implemented in VRT-311 /
VRT-311S is IPSec.
IPSec
IPSec is a near-ubiquitous VPN security standard, designed for use with TCP/IP networks. It
works at the packet level, and authenticates and encrypts all packets traveling over the VPN
Tunnel. Thus, it does not matter what applications are used on your PC. Any application can
use the VPN like any other network connection.
IPsec VPNs exchange information through logical connections called SAs (Security Associations). An SA is simply a definition of the protocols, algorithms and keys used between the two
VPN devices (endpoints).
Each IPsec VPN has two SAs - one in each direction. If IKE (Internet Key Exchange) is used
to generate and exchange keys, there are also SA's for the IKE connection as well as the IPsec
connection.
There are two security modes possible with IPSec:
• Transport Mode - the payload (data) part of the packet is encapsulated through encryp-
tion but the IP header remains in the clear (unchanged).
VRT-311 / VRT-311S does NOT support Transport Mode.
• Tunnel Mode - everything is encapsulated, including the original IP header, and a new IP
header is generated. Only the new header in the clear (i.e. not protected). This system provides enhanced security.
VRT-311 / VRT-311S always uses Tunnel Mode.
IKE
IKE (Internet Key Exchange) is an optional, but widely used, component of IPsec. IKE provides a method of negotiating and generating the keys and IDs required by IPSec. If using IKE,
only a single key is required to be provided during configuration. Also, IKE supports using
Certificates (provided by CAs - Certification Authorities) to authenticate the identify of the
remote user or gateway.
If IKE is NOT used, then all keys and IDs (SPIs) must be entered manually, and Certificates
can NOT be used. This is called a "Manual Key Exchange".
When using IKE, there are 2 phases to establishing the VPN tunnel:
73
Page 78

Broadband VPN Router User’s Manual
• Phase I is the negotiation and establishment up of the IKE connection.
• Phase II is the negotiation and establishment up of the IPsec connection.
Because the IKE and IPsec connections are separate, they have different SAs (security associations).
Policies
VPN configuration settings are stored in Policies.
Note that different vendors use different terms. Generally, the terms "VPN Policy", "IPSec
Policy", and "IPSec Proposal" have the same meaning. However, some vendors separate IKE
Policies (Phase 1 parameters) from IPSec Policies (Phase 2 parameters).
For VRT-311 / VRT-311S; each VPN policy contains both Phase 1 and Phase 2 parameters (if
IKE is used). Each policy defines:
• The address of the remote VPN endpoint
• The traffic which is allowed to use the VPN connection.
• The parameters (settings) for the IPsec SA (Security Association)
• If IKE is used, the parameters (settings) for the IKE SA (Security Association)
Generally, you will need at least one (1) VPN Policy for each remote site for which you wish to
establish VPN connections.
It is possible, and sometimes necessary, to have multiple Policies for the same remote site.
However, you should only Enable one (1) policy at a time. If multiple policies for the same
remote site are enabled, the policies are examined in the order in which they are listed, and the
first matching policy will be used. While it is possible to change the order of the policies, it
may not be easy to get the desired action from multiple policies.
VPN Configuration
The general rule is that each endpoint must have matching Policies, as follows:
VPN Endpoint
address
Traffic Selector
Each VPN endpoint must be configured to initiate or accept connections to the remote VPN client or Gateway.
Usually, this requires having a fixed Internet IP address. However, it is
possible for a VPN Gateway to accept incoming connections from a
remote client where the client's IP address is not known in advance.
This determines which outgoing traffic will cause a VPN connection to
be established, and which incoming traffic will be accepted. Each
endpoint must be configured to pass and accept the desired traffic from
the remote endpoint.
If connecting 2 LANs, this requires that:
• Each endpoint must be aware of the IP addresses used on the other
endpoint.
• The 2 LANs MUST use different IP address ranges.
IKE parameters
IPsec parameters
If using IKE (recommended), the IKE parameters must match (except
for the SA lifetime, which can be different).
The IPsec parameters at each endpoint must match.
74
Page 79

Microsoft VPN
Common VPN Situations
VPN Pass-through
Figure47: VPN Pass-through
Here, a PC on the LAN behind the VRT-311 / VRT-311S is using VPN software, but the VRT311 / VRT-311S is NOT acting as a VPN endpoint. It is only allowing the VPN connection.
• The PC software can use any VPN protocol supported by the remote VPN.
• The remote VPN Server must support client PCs which are behind a NAT router, and so
have an IP address which is not valid on the Internet.
• The VRT-311 / VRT-311S requires no VPN configuration, since it is not acting as a VPN
endpoint.
Client PC to VPN Gateway
Figure48: Client PC to VPN Server
In this situation, the PC must run appropriate VPN client software in order to connect, via the
Internet, to VRT-311 / VRT-311S. Once connected, the client PC has the same access to LAN
resources as PCs on the local LAN (unless restricted by the network administrator).
• IPsec is not the only protocol which can be used in this situation, but VRT-311 / VRT311S supports IPsec ONLY.
• Windows 2000 and Windows XP include a suitable IPsec VPN client program. Configuration of this client program for use with VRT-311 / VRT-311S is covered later in this
document.
75
Page 80

Broadband VPN Router User’s Manual
Connecting 2 LANs via VPN
Figure49: Connecting 2 VPN Gateways
This allows two (2) LANs to be connected. PCs on each endpoint gain secure access to the
remote LAN.
• The 2 LANs MUST use different IP address ranges.
• The VPN Policies at each end determine when a VPN tunnel will be established, and what
systems on the remote LAN can be accessed once the VPN connection is established.
• It is possible to have simultaneous VPN connections to many remote sites.
76
Page 81

Microsoft VPN
VPN Configuration
This section covers the configuration required on VRT-311 / VRT-311S when using Manual
Key Exchange (Manual Policies) or IKE (Automatic Policies).
Details of using Certificates are covered in a later section.
VPN Policies Screen
To view this screen, select VPN Policies from the VPN menu. This screen lists all existing
VPN policies. If no policies exist, the list will be empty.
Figure50: VPN Policies Screen
Note that the order of policies is important if you have more than one policy for a particular site.
In that case, the first matching policy (for the traffic under consideration) will be used.
Data - VPN Policies Screen
VPN List
Policy Name
Enable
Remote VPN
Endpoint
Key Type
Operations
Add
Edit
The name of the policy. When creating a policy, you should select a
suitable name.
This indicates whether or not the policy is currently enabled. Use the
"Enable/Disable" button to toggle the state of the selected policy.
The IP address of the remote VPN endpoint (Gateway or client).
This will indicate "Manual" (manual key exchange) or "IKE" (Internet
Key Exchange)
To add a new policy, click the "Add" button. See the following section
for details.
To Edit or modify an existing policy, select it and click the "Edit" button.
77
Page 82

Broadband VPN Router User’s Manual
Move
Enable/Disable
Copy
Delete
View Log
The order in which policies are listed is only important if you have
multiple polices for the same remote site. In that case, the first matching
policy is used. There are 2 ways to change the order of policies:
• Use the up and down indicators on the right to move the selected
row. You must confirm your changes by clicking "OK". If you
change your mind before clicking "OK", click "Cancel" to reverse
your changes.
• Click "Move" to directly specify a new location for the selected
policy.
Use this to toggle the On/Off state of the selected policy.
If you wish to create a policy which is similar to an existing policy, select
the policy and click the "Copy" button.
Remember that the new policy must have a different name, and there can
only be one active (enabled) policy for each remote VPN endpoint.
To delete an exiting policy, select it and click the "Delete" button.
Clicking the "View Log" button will open a new window and display the
VPN log.
Adding a New Policy
1. To create a new VPN Policy, click the Add New Policy button on the VPN Policies screen.
This will start the VPN Wizard, as shown below.
Figure51: VPN Wizard – Start Screen
• If you prefer to use a single setup screen instead of a Wizard, click the Setup Screen button.
This is recommended for experienced users only.
78
Page 83

• Otherwise, click Next to continue. You will see a screen like the following.
Microsoft VPN
General Settings
Policy Name
Enable Policy
Allow NetBIOS
traffic
Remote VPN
Endpoint
Figure52: VPN Wizard – General Screen
Enter a suitable name. This name is not supplied to the remote VPN. It is
used only to help you manage the policies.
Enable or disable the policy as required. For each remote VPN, only 1
policy can be enabled at any time.
Enable this if you require NetBIOS traffic to be transferred through the
VPN tunnel. NetBIOS is used by Microsoft (Windows) networking. This
setting should not be enabled unless necessary, because it increases
traffic volume.
The Internet IP address of the remote VPN endpoint (Gateway or client).
• Dynamic. Select this if the Internet IP address is unknown. In this
case, only incoming connections are possible.
• Fixed. Select this if the remote endpoint has a fixed Internet IP
address. If selected, enter the Internet IP address of the remote end-
point.
• Domain Name. Select this if the remote endpoint has a Domain
Name associated with it. If selected, enter the Domain Name of the
remote endpoint.
Keys
Select Manually assigned or IKE (Internet Key Exchange) as required.
If you are setting up both endpoints, using IKE is recommended.
2. Click Next to continue. You will see a screen like the following:
79
Page 84

Broadband VPN Router User’s Manual
Figure53: VPN Wizard - Traffic Selector Screen
• For outgoing VPN connections, these settings determine which traffic will cause a VPN
tunnel to be created, and which traffic will be sent through the tunnel.
• For incoming VPN connections, these settings determine which systems on your local LAN
will be available to the remote endpoint.
• The 2 VPN endpoints MUST use different address ranges.
If the addresses were in the same range, traffic intended for the remote VPN would be considered local LAN traffic. So it would not be forwarded to the Gateway.
Local IP addresses
Type
• Any - no additional data is required. Any IP address is accept-
able.
• For outgoing connections, this allows any PC on the LAN to
use the VPN tunnel.
• For incoming connections, this allows any PC using the re-
mote endpoint to access any PC on your LAN.
• Single address - enter an IP address in the "Start IP address"
field.
• Range address - enter the starting IP address in the "Start IP
address" field, and the finish IP address in the "Finish IP address" field.
• Subnet address - enter the desired IP address in the "Start IP
address" field, and the network mask in the "Subnet Mask" field.
The remote VPN must have these IP addresses entered as it's "Remote" addresses.
80
Page 85

Microsoft VPN
Remote IP addresses
Type
• Single address - enter an IP address in the "Start IP address"
field.
• Range address - enter the starting IP address in the "Start IP
address" field, and the finish IP address in the "Finish IP address" field.
• Subnet address - enter the desired IP address in the "Start IP
address" field, and the network mask in the "Subnet Mask" field.
The remote VPN should have these IP addresses entered as it's
"Local" addresses.
3. Click Next to continue. The screen you will see depends on whether you previously selected "Manual Key Exchange" or "IKE".
Manual Key Exchange
Figure54: VPN Wizard - Manual Key Exchange Screen
These settings must match the remote VPN. Note that you cannot use both AH and ESP.
Manually assigned Keys
AH Authentication
AH (Authentication Header) specifies the authentication protocol
for the VPN header, if used. (AH is often NOT used)
If AH is not enabled, the following settings can be ignored.
Keys
• The "in" key here must match the "out" key on the remote
VPN, and the "out" key here must match the "in" key on the
remote VPN.
• Keys can be in ASCII or Hex (0..9 A..F)
• For MD5, the keys should be 32 hex/16 ASCII characters.
• For SHA-1, the keys should be 40 hex/20 ASCII characters.
81
Page 86

Broadband VPN Router User’s Manual
SPI
• Each SPI (Security Parameter Index) must be unique.
• The "in" SPI here must match the "out" SPI on the remote
VPN, and the "out" SPI here must match the "in" SPI on the
remote VPN.
• Each SPI should be at least 3 characters.
ESP Encryption
ESP Authentication
ESP (Encapsulating Security Payload) provides security for the
payload (data) sent through the VPN tunnel. Generally, you will
want to enable both Encryption and Authentication.
Encryption Algorithm
• The 3DES algorithm provides greater security than DES, but is
slower.
• If using AES, you must select the Key Size. If using DES or
3DES, this field is ignored.
Key - In / Key - Out
• The "In" key here must match the "Out" key on the remote
VPN, and the "Out" key here must match the "In" key on the
remote VPN.
• For DES, keys should be 8 ASCII characters (16 HEX chars).
• For 3DES, keys should be 24 ASCII characters (48 HEX
chars).
• If using AES encryption, the key input size must match the Key
Size selected above.
Generally, you should enable ESP Authentication. There is little
difference between the available algorithms. Just ensure each
endpoint use the same setting.
• The "In" key here must match the "Out" key on the remote
VPN, and the "Out" key here must match the "In" key on the
remote VPN.
• Keys can be in ASCII or Hex (0 ~ 9 and A ~ F)
• For MD5, the keys should be 32 hex/16 ASCII characters.
• For SHA-1, the keys should be 40 hex/20 ASCII characters.
ESP SPI This is required if either ESP Encryption or ESP Authentica-
tion is enabled.
• Each SPI (Security Parameter Index) must be unique.
• The "in" SPI here must match the "out" SPI on the remote
VPN, and the "out" SPI here must match the "in" SPI on the
remote VPN.
• Each SPI should be at least 3 characters.
For Manual Key Exchange, configuration is now complete.
• Click "Next" to view the final screen.
• On the final screen, click "Finish" to save your settings, then "Close" to exit the Wizard.
82
Page 87

Microsoft VPN
IKE Phase 1
If you selected IKE, the following screen is displayed after the Traffic Selector screen. This
screen sets the parameters for the IKE SA.
Figure55: VPN Wizard - IKE Phase 1 Screen
IKE Phase 1 (IKE SA)
Local Identity
This setting must match the "Remote Identity" on the remote VPN.
Select the desired option, and enter the required data in the "Local
Identity Data" field.
• WAN IP Address - This is the most common method. If se-
• Fully Qualified Domain Name - enter the Domain Name
• Fully Qualified User name - This name does not have to a valid
• DER ANS.1 DN - This must be a DER ANS.1 Domain Name.
Remote Identity
This setting must match the "Local Identity" on the remote VPN.
Select the desired option, and enter the required data in the "Remote
Identity Data" field.
• IP Address - This is the most common method. If selected, no
• Fully Qualified Domain Name - enter the Domain Name
• Fully Qualified User name - This name does not have to a valid
• DER ANS.1 DN - This must be a DER ANS.1 Domain Name.
lected, no input is required.
assigned to this device.
Internet Domain Name. E-mail addresses are often used for this
entry.
input is required.
assigned to this device.
Internet Domain Name. E-mail addresses are often used for this
entry.
83
Page 88

Broadband VPN Router User’s Manual
Authentication
Authentication
Algorithm
Encryption
Algorithm
IKE Exchange
Mode
Direction
• RSA Signature requires that both VPN endpoints have valid
Certificates issued by a CA (Certification Authority).
• For Pre-shared key, enter the same key value in both endpoints.
The key should be at least 8 characters (maximum is 128 characters). Note that this key is used for the IKE SA only. The keys
used for the IPsec SA are automatically generated.
Select the desired option, and ensure that both endpoints have the
same settings.
Select the desired method, and ensure the remote VPN endpoint uses
the same method.
• The 3DES algorithm provides greater security than DES, but is
slower.
• If using AES, you must select the Key Size. If using DES or
3DES, this field is ignored.
Select the desired option, and ensure the remote VPN endpoint uses
the same mode.
• Main Mode provides identity protection for the hosts initiating
the IPSec session, but takes slightly longer to complete.
• Aggressive Mode provides no identity protection, but is quicker.
Select the desired option:
• Initiator - Only outgoing connections will be created. Incoming
connection attempts will be rejected.
• Responder - Only incoming connections will be accepted.
Outgoing traffic which would otherwise result in a connection
will be ignored.
• Both Directions - Both incoming and outgoing connections are
allowed.
IKE SA Life Time
This setting does not have to match the remote VPN endpoint; the
shorter time will be used. Although measured in seconds, it is common to use time periods of several hours, such 28,800 seconds.
DH Group
Select the desired method, and ensure the remote VPN endpoint uses
the same method. The smaller bit size is slightly faster.
IKE PFS
If enabled, PFS (Perfect Forward Security) enhances security by
changing the IPsec key at regular intervals, and ensuring that each key
has no relationship to the previous key. Thus, breaking 1 key will not
assist in breaking the next key.
This setting should match the remote endpoint.
IKE Keep Alive
Click Next to see the following IKE Phase 2 screen.
84
Page 89

Microsoft VPN
IKE Phase 2 Screen
This screen sets the parameters for the IPSec SA. When using IKE, there are separate connections (SAs) for IKE and IPSec.
Figure56: VPN Wizard - IKE Phase 2 Screen
IKE Phase 2 (IPsec SA)
IPsec SA Life Time
This setting does not have to match the remote VPN endpoint; the
shorter time will be used. Although measured in seconds, it is
common to use time periods of several hours, such 28,800 seconds.
IPSec PFS
If enabled, PFS (Perfect Forward Security) enhances security by
changing the IPsec key at regular intervals, and ensuring that each
key has no relationship to the previous key. Thus, breaking 1 key
will not assist in breaking the next key.
AH Authentication
AH (Authentication Header) specifies the authentication protocol
for the VPN header, if used.
AH is often NOT used. If you do enable it, ensure the algorithm
selected matches the other VPN endpoint.
ESP Encryption
ESP (Encapsulating Security Payload) provides security for the
payload (data) sent through the VPN tunnel. Generally, you will
want to enable both ESP Encryption and ESP Authentication.
Select the desired method, and ensure the remote VPN endpoint
uses the same method.
• The 3DES algorithm provides greater security than DES, but is
• If using AES, you must select the Key Size. If using DES or
slower.
3DES, this field is ignored.
ESP Authentication
Generally, you should enable ESP Authentication. There is little
difference between the available algorithms. Just ensure each
endpoint use the same setting.
85
Page 90

Broadband VPN Router User’s Manual
For IKE, configuration is now complete.
Click "Next" to view the final screen.
Figure57: VPN Wizard - Final Screen
On the final screen, click "Finish" to save your settings, then "Close" to exit the Wizard.
86
Page 91

Microsoft VPN
VPN Examples
This section describes some examples of using VRT-311 / VRT-311S in common VPN situations.
Example 1: Connecting 2 VRT-311 / VRT-311Ss
In this example, 2 LANs are connected via VPN.
Figure58: Connecting 2 VRT-311 / VRT-311Ss
Note
• The LANs MUST use different IP address ranges.
• Both endpoints have fixed WAN (Internet) IP addresses.
Configuration Settings
Setting LAN A Gateway LAN B Gateway Notes
Name Policy 1 Policy 1 Name does not affect
operation. Select a meaningful name.
Remote Endpoint 205.17.11.43 202.11.13.211 Other endpoint's WAN
(Internet) IP address.
Local
IP addresses
Remote
IP addresses
Key Exchange IKE IKE Must match
IKE SA Parameters
IKE Direction Both ways Both ways Does not have to match.
Local Identity IP address IP address IP address is the most
Any Any Use a more restrictive
definition if possible.
192.168.1.1 to
192.168.1.254
192.168.0.1 to
192.168.0.254
Address range on other
endpoint.
Use a more restrictive
definition if possible.
Either endpoint can block
1 direction.
common ID method
Remote Identity IP address IP address IP address is the most
common ID method
IKE Authentication
Pre-shared Key Pre-shared Key Certificates are not widely
87
Page 92

Broadband VPN Router User’s Manual
method used.
Pre-shared Key Xxxxxxxxxx Xxxxxxxxxx Must match
IKE Authentication
MD5 MD5 Must match
algorithm
IKE Encryption DES DES Must match
IKE Exchange
Main Mode Main Mode Must match
mode
DH Group Group 1 (768 bit) Group 1 (768 bit) Must match
IKE SA Life time 28800 28800 Does not have to match.
Shorter period will be
used.
IKE PFS Disable Disable Must match
IPSec SA Parameters
IPSec SA Life time 28800 28800 Does not have to match.
Shorter period will be
used.
IPSec PFS Disabled Disabled Must match
AH authentication Disabled Disabled AH is rarely used
ESP authentication Enable/MD5 Enable/MD5 Must match
ESP encryption Enable/DES Enable/DES Must match
88
Page 93

Microsoft VPN
Example 2: Windows 2000/XP Client to LAN
In this example, a Windows 2000/XP client connects to VRT-311 / VRT-311S and gains access
to the local LAN.
Figure59: Windows 2000/XP Client to VRT-311 / VRT-311S
To use 3DES encryption on Windows 2000, you
need Service Pack 3 or later installed.
VRT-311 / VRT-311S Configuration
Setting Value Notes
Name Win Client Name does not affect operation. Select a
meaningful name.
Remote Endpoint 172.16.9.10 Other endpoint's WAN (Internet) IP address.
Local
IP addresses
Remote
IP addresses
Key Exchange IKE Must match client PC
IKE SA Parameters
IKE Direction Both ways Using "Responder only" is not possible.
Local Identity IP address Required.
Remote Identity IP address Required
IKE Authentication
method
Pre-shared Key Xxxxxxxxxx Must match client PC
Subnet address:
192.168.0.0
255.255.255.0
172.16.9.10 For a single client, this address is the same as
Pre-shared Key Certificates are not widely used.
Allows access to entire LAN. Use a more
restrictive definition if possible.
the endpoint address.
IKE Authentication
algorithm
IKE Encryption 3DES Must match client PC
IKE Exchange
mode
SHA-1 Must match client PC
Main Mode Windows 2000 only supports Main Mode.
89
Page 94

Broadband VPN Router User’s Manual
DH Group Group 1 (768 bit) Must match client PC
IKE SA Life time 28800 Does not have to match client PC. Shorter
period will be used.
IKE PFS Disable Must match client PC
IPSec SA Parameters
IPSec SA Life time 28800 Do not have to match. Shorter period will be
used.
IPSec PFS Disable Must match client PC
AH authentication Disabled AH is rarely used
ESP authentication Enable/MD5 Must match client PC
ESP encryption Enable/DES Must match client PC
Windows Client Configuration
1. Select Start - Programs - Administrative Tools - Local Security Policy.
2. Right click IP Security Policy on Local Machine and select Create IP Security Policy
Figure60: Windows 2000/XP - Local Security Settings
3. Click "Next", then enter a policy name, for example "DUT To Win2K", then click "Next".
4. Step through the Wizard:
• Deselect Activate the default response rule. Click "Next",
• Leave Edit Properties checked. Click "Finish".
5. The following "Properties - Rules" screen will be displayed.
90
Page 95

Microsoft VPN
Figure61: Windows 2000/XP - Policy Properties
• Note that no rules are in use. Two 2 rules are required - incoming and outgoing.
• The outgoing rule will be added first.
6. Deselect the "Use Add Wizard" checkbox, then click "Add" to view the screen below.
Figure62: IP Filter List
7. Type "To DUT" for the name, then click "Add" to see a screen like the following.
91
Page 96

Broadband VPN Router User’s Manual
Figure63: Filter Properties: Addressing
8. Enter the Source IP address and the Destination IP address.
• Since this is the outgoing filter, the Source IP address is "My IP address" and the Des-
tination IP address is the address range used on the remote LAN.
• Ensure the Mirrored option is checked.
9. Click "OK" to save your settings and close this dialog.
Figure64: New Rule Properties: IP Filter List
10. On the resulting screen (above), ensure the "To DUT" filter is selected, then click the
Filter Action tab to see a screen like the following
92
Page 97

Microsoft VPN
Figure65: New Rule Properties: Filter Action
11. Select Require Security, then click the "Edit" button, to view the Require Security Properties screen.
Figure66: Require Security Properties
12. Select Negotiate security (this selects IKE), then click "Add".
93
Page 98

Broadband VPN Router User’s Manual
Figure67: Modify Security Method
13. On the resulting screen (above), select High [ESP] then click "OK" to save your changes
and return to the Require Security Properties screen.
Figure68: Require Security Properties
14. Ensure the following settings are correct, then click "OK" to return to the Filter Action tab
of the Edit Rule Properties screen.
VPN Setting Windows Setting
IKE enabled Negotiate security
AH disabled AH Integrity: <None>
ESP encryption: Enable/DES ESP Confidentially: DES
ESP authentication: Enable/MD5 ESP Integrity: MD5
94
Page 99

Microsoft VPN
15. Click the Tunnel Setting tab, then select The tunnel endpoint is specified by this IP address.
Enter the WAN (Internet) IP address of VRT-311 / VRT-311S, as shown below.
Figure69: Tunnel Setting
16. Click the Authentication Methods tab, then click the "Edit" to see the screen like the
example below.
Figure70: Authentication Method
17. Select Use this string to protect the key exchange (preshared key), then enter your preshared key in the field provided.
18. Click "OK" to save your changes and return to the Authentication Methods tab of the Edit
Rule Properties screen.
19. Click "Close" to return to the DUT to Win2K properties screen. The "To DUT" filter
should now be listed, as shown below.
95
Page 100

Broadband VPN Router User’s Manual
Figure71: Windows 2000/XP Client to VRT-311 / VRT-311S
20. To add the second (incoming) rule, click "Add". For the name, enter "To Win2K", then
click "Add".
Figure72: Windows 2000/XP Client to VRT-311 / VRT-311S
21. Enter the Source IP address and the Destination IP address as shown below.
• Since this is the incoming filter, the Source IP address is the address range used on the
remote LAN and the Destination IP address is "My IP address".
• Ensure the Mirrored option is checked.
96
 Loading...
Loading...